- DL manuals
- 3Com
- Software
- 10031370-01
- Setup Manual
3Com 10031370-01 Setup Manual
Summary of 10031370-01
Page 1
Communication server security setup guide commworks ready part number 10031370
Page 3
Communication server security setup guide commworks ready part no. 10031370-01 published november 2000
Page 4
3com corporation 5400 bayfront plaza santa clara, california 95052-8145 3com corporation (hereinafter 3com) limited use software license agreement read carefully: by exercising licensees rights to make and use copies of the software (as may be provided for below), licensee agrees to be bound by t...
Page 5
Compatibility. The software is only compatible with certain personal computers. The software may not be compatible with and is not warranted for non-compatible systems. Call 3com customer support for information on compatibility. Diskettes and documentation. 3com warrants that if the enclosed magnet...
Page 6
documentation means all guidebooks - either in printed or electronic format - and any other printed material provided by 3com with the software. license means the license purchased and granted in this agreement. License authentication procedures are described in the getting started guide accom...
Page 7
C ontents a bout t his g uide conventions........................................................................................................................ Ix year 2000 compliance .........................................................................................................X 1 i ntr...
Page 8
Viii.
Page 9
A bout t his g uide this chapter covers security issues over the network, assigning rights and permissions to users. If release notes are shipped with your product and the information there differs from the information in this guide, follow the instructions in the release notes. Most user guides and...
Page 10
X c hapter : a bout t his g uide year 2000 compliance for information on year 2000 compliance and 3com products, visit the 3com year 2000 web page: http://www.3com.Com/products/yr2000.Html keyboard key names if you must press two or more keys simultaneously, the key names are linked with a plus sign...
Page 11
1 i ntroducing s ecurity this chapter explains how security works and what functions it performs. It also provides reference information on pre-defined user groups, all permissions and permission definitions. Introduction the organization of this guide follows the concepts and steps required to set ...
Page 12
1-2 c hapter 1: i ntroducing s ecurity a complete description of all possible permissions appears in the security objects and permissions section later in this chapter. A permission can be: ■ grantedyou can do the action ■ deniedyou cannot do the action ■ inheritedyou can or cannot do the actio...
Page 13
Security glossary 1-3 case, simply remove permission from the sales user group to deny them access to monitoring feature of fax port 2. All other user groups, except those belonging to the sub-group sales user, can still monitor the modem. This illustrates that user groups with similar permissions c...
Page 14
1-4 c hapter 1: i ntroducing s ecurity set up here. There are two states of an account # in reference to a user. The account # is either active or forwarded. Table 1-1 icon listobject icons table 1-2 icon listpermission icons adding members to pre-defined user groups there are six pre-defined user...
Page 15
Security glossary 1-5 if you are satisfied with the pre-defined user groups and their permissions, you may not need to use this security module at all (except to add new users). For more information on the permissions for pre-defined groups, see the following section, pre-defined user groups. Pre-...
Page 16
1-6 c hapter 1: i ntroducing s ecurity server supervisors cannot create fax jobs unless they also belong the fax users group. Account supervisors account supervisors are created to provide added security for individuals who need it. Defined properties of accounts might prevent server supervisors (wh...
Page 17
Security glossary 1-7 commworks ip fax users members of this group have irrevocable permissions to create fax jobs. You must belong to this group to create fax jobs. Assistants members of this group can do the same actions to fax jobs as the person they assist. Default object permissions this sectio...
Page 18
1-8 c hapter 1: i ntroducing s ecurity ■ user profile owned by 'self' this group allows the creator of an object additional permissions for it. You can change these permissions as needed. For more information on the default permissions users have for objects owned by self, see the previous section. ...
Page 19
Security glossary 1-9 list cover pagesee that the cover page exists in the list of cover pages using the fax send dialog. Other cover page permissions are only useful when you have the list permission. Use cover pagesend the cover page with outbound faxes from the fax send dialog. View cover page...
Page 20
1-10 c hapter 1: i ntroducing s ecurity rename folderchange the folder's name from the folder properties dialog. View from folderview a fax from the folder in the fax image viewer. Phonebook permissions add to phonebookadd a recipient to a phonebook or phonebook group on the phonebooks window. De...
Page 21
Security glossary 1-11 edit user's phonebook entrychange the phonebook entry information for the user from the user's phonebook entry dialog. List usersee that the user exists on the authorized users dialog. Other user permissions are only useful when you have the list permission. View user profil...
Page 23
2 w orking w ith s ecurity this chapter explains how to use the security module to create groups and edit permissions. Starting security the example below will use the server administrator button menu to work with security features. Access is also available from the fax client screen. To start the s...
Page 24
2-2 c hapter 2: w orking w ith s ecurity sorting security information the security setup screen has a command bar at the top. This section will address some of the commands found in this area. The table below describes commands under the change item: table 2-1 change commands the table below describ...
Page 25
Starting security 2-3 setting up accounts in a new installation, two default accounts are created automatically: the account names are reserved, and are displayed as account #1 and system account. These accounts cannot be deleted. To view the list of accounts, click the plus sign (+) to expand t...
Page 26
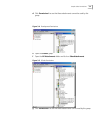
2-4 c hapter 2: w orking w ith s ecurity 3 enter the users name in the field and click add. The user properties screen appears: figure 2-4 user properties fields for this screen are described below: table 2-4 user properties fields field name description settings user id user name user name appears...
Page 27
Starting security 2-5 account status active: all account rules apply to this user. Forwarded: all inbound faxes and activity charges will be forwarded to the account named in the forwarded to field below. Active is the default setting. Long distance use this optional section if special codes are nee...
Page 28
2-6 c hapter 2: w orking w ith s ecurity setting up groups after manually creating users, creating groups provides structure to the security configuration. For example, a separate group may be created for each department so that the use of attachments, phonebooks or port devices is restricted. Setti...
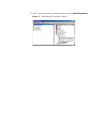
Page 29
Starting security 2-7 5 the add members screen opens in a window to the left of the main screen. Select users one-at-a-time or all at once. Click add member! And the names appear in the expanded groupname folder. Figure 2-7 members added if you select an inappropriate group type is selected, securit...
Page 30
2-8 c hapter 2: w orking w ith s ecurity deleting a user-defined group 1 in security setup, select the group you want to remove. 2 from the change menu, click delete group. 3 the group is removed from the list. Sub-groups users and objects can belong to more than one group. To view all groups to whi...
Page 31
Starting security 2-9 5 on the command bar, click permissions. The permissions window appears: figure 2-9 object permissions by user group 6 this screen shows that all inherited permissions have been transferred to all users in this group. Change one or two permissions to perform the next step. Figu...
Page 32
2-10 c hapter 2: w orking w ith s ecurity dominant permission when a user belongs to more than one group with different permissions, or is individually defined for specific objects, which permission is used? Rule 1. Individuals permissions overrule the permissions for a group. An individual permiss...
Page 33
Starting security 2-11 1. Change the permission in this screen. An explicit permission will override a group-inherited permission. 2. Make a specific group for sales attachments. These public attachments are accessible by all sales persons. Gallagan has permission to delete in this object group: fig...
Page 35
3 s ecurity p ermission e xamples this chapter shows two example procedures. These samples build on concepts discussed earlier in this guide. Sample sales permissions this sample uses a group of users called srsales and a group of attachments called salesattachments. This sample explains how to chan...
Page 36
3-2 c hapter 3: s ecurity p ermission e xamples d click salesattachments to expand the folder. Click permissions! Figure 3-2 default permissions e the default permissions for sales attachments shows that no permissions are granted. 2 grant the developers group permission to use the attachments in th...
Page 37
Sample sales permissions 3-3 d click permissions! To see that these attachments cannot be used by this group. Figure 3-4 development permissions e open the srsales group. F open the all attachments folder and click on salesattachments. Figure 3-5 srsales permissions g click permissions! To see that ...
Page 38
3-4 c hapter 3: s ecurity p ermission e xamples to change individual permissions 1 in the sorted by users window, select a user that does not belong to either the srsales group or the server supervisors pre-defined group. Double-click the user to display the objects. Check the groups to which a user...
Page 39
7 click change permissions! To allow this user use of the salesattachments. Figure 3-7 salesattachment permissions changed.
Page 41
1 i ndex a account # definition 1-3 account #1 2-3 account status user properties 2-5 accounts 1-2 creating 2-3 overview 1-2 add new user 2-2, 2-3 add to folder definition 1-9 add to phonebook definition 1-10 adding users to pre-defined groups 1-4 adding members to pre-defined user groups 1-4 all 'o...
Page 42
2 owned by self 1-7 pre-defined user groups 1-5 security 1-1, 2-1 owned by self definition 1-3 overview 1-7 owned by self object list 1-7 p password/confirm user properties 2-4 pause fax job definition 1-9 pause/resume all server modems definition 1-11 permission default object 1-7 modem list 1-1 ob...
Page 44
3com corporation 5400 bayfront plaza p.O. Box 58145 santa clara, ca 95052-8145 ©2000 3com corporation all rights reserved printed in the u.S.A. Part number 10031370-01.