- DL manuals
- 3Com
- Switch
- 2928 - Baseline Plus Switch PWR
- User Manual
3Com 2928 - Baseline Plus Switch PWR User Manual
3Com Baseline Switch 2900 Family
User Guide
Baseline Switch 2920-SFP Plus
Baseline Switch 2928-SFP Plus
Baseline Switch 2952-SFP Plus
Baseline Switch 2928-PWR Plus
Baseline Switch 2928-HPWR Plus
Manual Version:
6W102-20090810
www.3com.com
3Com Corporation
350 Campus Drive, Marlborough,
MA, USA 01752 3064
Summary of 2928 - Baseline Plus Switch PWR
Page 1
3com baseline switch 2900 family user guide baseline switch 2920-sfp plus baseline switch 2928-sfp plus baseline switch 2952-sfp plus baseline switch 2928-pwr plus baseline switch 2928-hpwr plus manual version: 6w102-20090810 www.3com.Com 3com corporation 350 campus drive, marlborough, ma, usa 01752...
Page 2
Copyright © 2009, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from 3com corporation. 3com corporation reserves th...
Page 3
About this manual organization 3com baseline switch 2900 family user guide is organized as follows: part contents 1 overview perform overview of 3com baseline switch 2900 family. 2 configuration wizard perform quick configuration of the device. 3 irf configure global parameters and stack ports, and ...
Page 4
Part contents 18 rmon configure rmon, and dissplay, create, modify, and clear rmon statistics. 19 energy saving display and configure the energy saving settings of an interface. 20 snmp configure snmp, and dissplay, create, modify, and clear snmp statistics. 21 interface statistics display and clear...
Page 6
Related documentation in addition to this manual, each 3com baseline switch 2900 documentation set includes the following: manual description 3com baseline switch 2900 family getting started guide this guide provides all the information you need to install and use the 3com baseline switch 2900 famil...
Page 7: Table of Contents
I table of contents 1 overview ·····················································································································································1-1 2 configuration through the web interface ··········································································...
Page 8: Overview
1-1 1 overview the 3com baseline switch 2900 family can be configured through the command line interface (cli), web interface, and snmp/mib. These configuration methods are suitable for different application scenarios. Z the web interface supports all switch 2900 series configurations. Z the cli pro...
Page 9
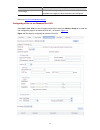
2-1 2 configuration through the web interface web-based network management operating environment 3com provides the web-based network management function to facilitate the operations and maintenance on 3com’s network devices. Through this function, the administrator can visually manage and maintain n...
Page 10
2-2 figure 2-2 default ip address of the device 2) a dhcp server exists in the subnet where the device resides if a dhcp server exists in the subnet where the device resides, the device will dynamically obtain its default ip address through the dhcp server. You can log in to the device through the c...
Page 11
2-3 figure 2-3 login page of the web interface z the pc where you configure the device is not necessarily a web-based network management terminal. A web-based network management terminal is a pc used to log in to the web interface and is required to be reachable to the device. Z after logging in to ...
Page 12
2-4 figure 2-4 web-based configuration interface (1) navigation tree (2) body area (3) title area z navigation tree: organizes the web-based nm functions as a navigation tree, where you can select and configure functions as needed. The result is displayed in the body area. Z body area: allows you to...
Page 13
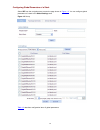
2-5 user level in table 2-2 indicates that users of this level or users of a higher level can perform the corresponding operations. Table 2-2 description of web-based nm functions function menu description user level wizard ip setup perform quick configuration of the device. Management display globa...
Page 14
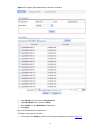
2-6 function menu description user level save save the current configuration to the configuration file to be used at the next startup. Configure initialize restore the factory default settings. Configure file manage ment file manageme nt manage files on the device, such as displaying the file list, ...
Page 15
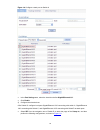
2-7 function menu description user level event view, create, modify, and clear event entries. Configure log display log information about rmon events. Configure energy saving energy saving display and configure the energy saving settings of an interface. Configure display and refresh snmp configurat...
Page 16
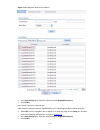
2-8 function menu description user level oui summary display the addresses of the ouis that can be identified by voice vlan. Monitor oui add add the address of an oui that can be identified by voice vlan. Configure oui remove remove the address of an oui that can be identified by voice vlan. Configu...
Page 17
2-9 function menu description user level remove delete the selected ipv4 static routes. Configure display information about the dhcp status, advanced configuration information of the dhcp relay agent, dhcp server group configuration, dhcp relay agent interface configuration, and the dhcp client info...
Page 18
2-10 function menu description user level radius setup display and configure radius parameters. Management display configuration information about local users. Monitor local user create, modify and remove a local user. Management display configuration information about user groups. Monitor users use...
Page 19
2-11 function menu description user level summary display classifier configuration information. Monitor create create a class. Configure setup configure the classification rules for a class. Configure classifie r remove delete a class or its classification rules. Configure summary display traffic be...
Page 20
2-12 the advance search function is also provided. You can click before search item, as shown in figure 2-5 . You can select match case and whole word, that is, the item to be searched must completely match the keyword, or you can select search in previous results. If you do not select exact search,...
Page 21
2-13 figure 2-7 about sort display on the page, you can click the blue items of each column to sort and display the records based on the item you selected. Figure 2-8 sort display configuration guidelines z the web-based console supports microsoft internet explorer 6.0 sp2 and higher, but it does no...
Page 22
2-14 z if the software version of the device changes, when you log in to the device through the web interface, you are recommended to delete the temporary internet files of ie; otherwise, the web page content may not be displayed correctly..
Page 23: Interface
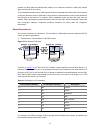
3-1 3 configuration through the command line interface z the 3com baseline switch 2900 family can be configured through the command line interface (cli), web interface, and snmp/mib, among which the web interface supports all switch 2900 series configurations. These configuration methods are suitabl...
Page 24
3-2 figure 3-1 console cable step2 plug the db-9 female connector of the console cable to the serial port of the console terminal or pc. Step3 connect the rj-45 connector of the console cable to the console port of the switch. (as shown below) figure 3-2 network diagram for configuration environment...
Page 25
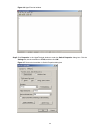
3-3 information and the use of the hyperterminal, refer to the hyperterminal help documentation in help and support center on the pc running the windows operating system. In the following configuration procedure, windows xp hyperterminal is used to communicate with the switch. 1) start the pc and ru...
Page 26
3-4 figure 3-4 set the serial port used by the hyperterminal connection step3 click ok after selecting a serial port. The following dialog box appears. Set bits per second to 38400, data bits to 8, parity to none, stop bits to 1, and flow control to none. Figure 3-5 set the serial port parameters st...
Page 27
3-5 figure 3-6 hyperterminal window step5 click properties in the hyperterminal window to enter the switch properties dialog box. Click the settings tab, set the emulation to vt100, and then click ok. Figure 3-7 set terminal emulation in switch properties dialog box.
Page 28
3-6 logging in to the cli the login process requires a user name and password. The default user name for first time configuration is admin, no password is required. User names and passwords are case sensitive. To logon to the cli interface: step1 press enter. The username prompt displays: login auth...
Page 29
3-7 description use the initialize command to delete the configuration file to be used at the next startup and reboot the device with the default configuration being used during reboot. Use the command with caution because this command deletes the configuration file to be used at the next startup an...
Page 30
3-8 password syntax password parameters none description use the password command to modify the login password of a user. Examples # modify the login password of user admin. Password change password for user: admin old password: *** enter new password: ** retype password: ** the password has been su...
Page 31
3-9 round-trip min/avg/max = 1/41/205 ms the above information shows that ip address 1.1.2.2 is reachable and the echo replies are all returned from the destination. The minimum, average, and maximum roundtrip intervals are 1 millisecond, 41 milliseconds, and 205 milliseconds respectively. Quit synt...
Page 32
3-10 z if the main configuration file is corrupted or does not exist, the device cannot be rebooted with the reboot command. In this case, you can specify a new main configuration file to reboot the device, or you can power off the device, and then power it on, and the system will automatically use ...
Page 33
3-11 copyright (c) 2004-2009 3com corp. And its licensors. All rights reserved. 3com baseline switch 2928-pwr plus uptime is 0 week, 0 day, 3 hours, 11 minutes 3com baseline switch 2928-pwr plus 128m bytes dram 128m bytes nand flash memory config register points to nand flash hardware version is rev...
Page 34
3-12 # download software package main.Bin from the tftp server and use the boot file in the package at the next startup. Upgrade 192.168.20.41 main.Bin runtime configuration example for upgrading the host software through the cli network requirements as shown in figure 3-8 , a switch 2900 series swi...
Page 35
3-13 file downloaded successfully. The specified file will be used as the boot file at the next reboot. # reboot the switch. Reboot after getting the new application file, reboot the switch to have the upgraded application take effect..
Page 36: Table of Contents
Table of contents 1 configuration wizard ································································································································1-1 overview ······················································································································...
Page 37: Configuration Wizard
1-1 1 configuration wizard ove the configuration wizard guides you through the basic service setup, including the system name, d management ip address (ip address of the vlan interface). Enter uration wizard homepage, as shown in rview system location, contact information, an basic service setup ing...
Page 38
1-2 e figure 1-2 system parameter configuration pag table 1-1 describes the system parameter configuration items. Table 1-1 system parameter configuration items item description sysname specify the system name. The system name appears at the top of the navigation tree. You can also set the system na...
Page 39
1-3 configuring management ip address modifying the management ip address used for the current login will tear down the connection to the device. Use the new management ip address to re-log in to the system. A management ip address is the ip address of a vlan interface, which can be used to access t...
Page 40
1-4 table 1-2 management ip address configuration items item description select vlan interface select a vlan interface. Available vlan interfaces are those configured in the page you enter by selecting network > vlan interface and selecting the create tab. Admin status enable or disable the vlan int...
Page 41
1-5 s figure 1-4 configuration finishe the page displays your configurations. Review the configurations and if you want to modify the settings click back to go back to the page. Click finish to confirm your settings and the system performs the configurations..
Page 42: Table of Contents
I table of contents 1 irf ·······························································································································································1-1 irf overview ··································································································...
Page 43: Irf
1-1 1 irf irf overview an intelligent resilient framework (irf) stack is a set of network devices. Administrators can group multiple network devices into a stack and manage them as a whole. Therefore, stack management can help reduce customer investments and simplify network management. Introduction...
Page 44
1-2 z the administrator can log in to any slave device from the master device of the stack, and perform various configurations for the slave device. Configuring an irf stack configuration task list perform the tasks in table 1-1 to configure an irf stack. Table 1-1 stack configuration task list task...
Page 45
1-3 configuring global parameters of a stack select irf from the navigation tree to enter the page shown in figure 1-2 . You can configure global parameters of a stack in the global settings area. Figure 1-2 set up table 1-2 describes configuration items of global parameters..
Page 46
1-4 table 1-2 configuration items of global parameters item description private net ip mask configure a private ip address pool for the stack. The master device of a stack must be configured with a private ip address pool to ensure that it can automatically allocate an available ip address to a slav...
Page 47
1-5 table 1-3 fields of topology summary fields description member id member id of the device in the stack: z value 0 indicates that the device is the master device of the stack. Z a value other than 0 indicates that the device is a slave device and the value is the member id of the slave device in ...
Page 48
1-6 figure 1-5 device summary (a slave device) return to stack configuration task list . Irf stack configuration example network requirements z as shown in figure 1-6 , switch a, switch b, switch c, and switch d are connected with one another. Z create a stack, where switch a is the master device, s...
Page 49
1-7 figure 1-7 configure global parameters for the stack on switch a z type 192.168.1.1 in the text box of private net ip. Z type 255.255.255.0 in the text box of mask. Z select enable from the build stack drop-down list. Z click apply. Now, switch a becomes the master device. # configure a stack po...
Page 50
1-8 figure 1-8 configure a stack port on switch a z in the port settings area, select the check box before gigabitethernet1/0/1. Z click enable. 2) configure the slave devices # on switch b, configure local ports gigabitethernet 1/0/2 connecting with switch a, gigabitethernet 1/0/1 connecting with s...
Page 51
1-9 figure 1-9 configure stack ports on switch b z in the port settings area, select the check boxes before gigabitethernet1/0/1, gigabitethernet1/0/2 , and gigabitethernet1/0/3. Z click enable. Now, switch b becomes a slave device. # on switch c, configure local port gigabitethernet 1/0/1 connectin...
Page 52
1-10 figure 1-10 configure a stack port on switch c z in the port settings area, select the check box before gigabitethernet1/0/1. Z click enable. Now, switch c becomes a slave device. # on switch d, configure local port gigabitethernet 1/0/1 connecting with switch b as a stack port. Z select irf fr...
Page 53
1-11 now, switch d becomes a slave device. 3) verify the configuration # display the stack topology on switch a. Z select irf from the navigation tree of switch a and click the topology summary tab. Z you can view the information as shown in figure 1-11 . Figure 1-11 verify the configuration configu...
Page 54: Table of Contents
I table of contents 1 summary ····················································································································································1-1 overview ·············································································································...
Page 55: Summary
1-1 1 summary overview the device summary module helps you understand the system information, port information, power information, and fan information on the device. The system information includes the basic system information, system resources state, and recent system operation logs. Displaying dev...
Page 56
1-2 basic system information the info area on the right of the page displays the basic system information including device name, product information, device location, contact information, serial number, software version, hardware version, bootrom version, and running time. The running time displays ...
Page 57
1-3 figure 1-2 device information select from the refresh period drop-down list: z if you select a certain period, the system refreshes the information at the specified interval. Z if you select manual, the system refreshes the information only when you click the refresh button..
Page 58: Table of Contents
I table of contents 1 device basic information configuration ·································································································1-1 overview ·································································································································...
Page 59
1-1 1 device basic information configuration overview the device basic information feature provides you the following functions: z set the system name of the device. The configured system name will be displayed on the top of the navigation bar. Z set the idle timeout period for a logged-in user. Tha...
Page 60
1-2 figure 1-2 configuring idle timeout period table 1-2 describes the idle timeout period configuration item. Table 1-2 idle timeout period configuration item item description idle timeout set the idle timeout period for a logged-in user..
Page 61: Table of Contents
I table of contents 1 system time configuration······················································································································1-1 overview ··························································································································...
Page 62: System Time Configuration
1-1 1 system time configuration overview the system time module allows you to display and set the device system time on the web interface. The device supports setting system time through manual configuration and automatic synchronization of ntp server time. An administrator can by no means keep time...
Page 63
1-2 table 1-1 shows the system time configuration items. Table 1-1 system time configuration items item description manual select to manually configure the system time, including the setting of year, month, day, hour, minute, and second. Source interface set the source interface for an ntp message. ...
Page 64
1-3 configuration procedure 1) configure device a # configure the local clock as the reference clock, with the stratum of 2. Enable ntp authentication, set the key id to 24, and specify the created authentication key anicekey is a trusted key. (configuration omitted.) 2) configure switch b # configu...
Page 65
1-4 z a device can act as a server to synchronize the clock of other devices only after its clock has been synchronized. If the clock of a server has a stratum level higher than or equal to that of a client’s clock, the client will not synchronize its clock to the server’s. Z the synchronization pro...
Page 66: Table of Contents
I table of contents 1 log management ·······································································································································1-1 overview ···················································································································...
Page 67: Log Management
1-1 1 log management overview system logs contain a large amount of network and device information, including running status and configuration changes. System logs are an important way for administrators to know network and device status. With system log information, administrators can take correspo...
Page 68
1-2 figure 1-1 set system logs related parameters table 1-2 describes the syslog configuration items. Table 1-2 syslog configuration items item description log buffer size set the number of logs that can be stored in the log buffer. Refresh period set the refresh period on the log information displa...
Page 69
1-3 figure 1-2 display syslog table 1-3 describes the syslog display items. Table 1-3 syslog display items item description time/date displays the time/date when system logs are generated. Source displays the module that generates system logs. Level displays the severity level of system logs. For th...
Page 70
1-4 severity level description value notification normal information that needs to be noticed 5 informational informational information to be recorded 6 debugging information generated during debugging 7 note: a smaller value represents a higher severity level. Return to log management configuration...
Page 71: Table of Contents
I table of contents 1 configuration management ······················································································································1-1 back up configuration ·············································································································...
Page 72: Configuration Management
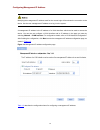
1-1 1 configuration management back up configuration configuration backup provides the following functions: z open and view the configuration file (.Cfg file or .Xml file) for the next startup z back up the configuration file (.Cfg file or .Xml file) for the next startup to the host of the current u...
Page 73
1-2 figure 1-2 configuration restore page z after you click the upper browse button in this figure, the file upload dialog box appears. You can select the .Cfg file to be uploaded, and then click apply. Z after you click the lower browse button in this figure, the file upload dialog box appears. You...
Page 74
1-3 initialize this operation will restore the system to factory defaults, delete the current configuration file, and reboot the device. Select device > configuration from the navigation tree, and then click the initialize tab to enter the initialize confirmation page as shown in figure 1-4 . Figure...
Page 75: Table of Contents
I table of contents 1 device maintenance ··································································································································1-1 software upgrade ············································································································...
Page 76: Device Maintenance
1-1 1 device maintenance software upgrade software upgrade allows you to obtain a target application file from the current host and set the file as the main boot file or backup boot file to be used at the next reboot. A boot file, also known as the system software or device software, is an applicati...
Page 77
1-2 table 1-1 software upgrade configuration items item description file specifies the filename of the local application file, which must be with an extension .Bin. Filename specifies a filename for the file to be saved on the device. The filename must have an extension, which must be the same as th...
Page 78
1-3 z if you select check configuration with next startup configuration file, the system will check the configuration before rebooting the device. If the check succeeds, the system will reboot the device; if the check fails, a dialog box appears, telling you that the current configuration and the sa...
Page 79
1-4 figure 1-5 the diagnostic information file is created click click to download, and the file download dialog box appears. You can select to open this file or save this file to the local host. Z the generation of the diagnostic file will take a period of time. During this process, do not perform a...
Page 80: Table of Contents
I table of contents 1 file management········································································································································1-1 overview ··················································································································...
Page 81: File Management
1-1 1 file management overview the device saves useful files (such as host software, configuration file) into the storage device, and the system provides the file management function for the users to manage those files conveniently and effectively. File management function provides the following ope...
Page 82
1-2 download dialog box appears. You can select to open the file or to save the file locally. You can download only one file at one time. Uploading a file select device > file management from the navigation tree to enter the file management page, as shown in figure 1-1 . In the upload file area, sel...
Page 83: Table of Contents
I table of contents 1 port management configuration··············································································································1-1 overview ······························································································································...
Page 84
1-1 1 port management configuration overview you can use the port management feature to set and view the operation parameters of a layer 2 ethernet port, including but not limited to its state, rate, duplex mode, link type, pvid, mdi mode, flow control settings, mac learning limit, and storm suppres...
Page 85
1-2 table 1-1 describes the port configuration items. Table 1-1 port configuration items item description port state enable or disable the port. Sometimes, after you modify the operation parameters of a port, you need to disable and then enable the port to have the modifications take effect. Speed s...
Page 86
1-3 item description mdi set the medium dependent interface (mdi) mode of the port. Two types of ethernet cables can be used to connect ethernet devices: crossover cable and straight-through cable. To accommodate these two types of cables, an ethernet port can operate in one of the following three m...
Page 87
1-4 item description broadcast suppression set broadcast suppression on the port. You can suppress broadcast traffic by percentage or by pps as follows: z ratio: sets the maximum percentage of broadcast traffic to the total bandwidth of an ethernet port. When this option is selected, you need to inp...
Page 88
1-5 viewing the operation parameters of a port select device > port management from the navigation tree. The summary tab is displayed by default. Select the parameter you want to view by clicking the radio button before it to display the setting of this parameter for all the ports in the lower part ...
Page 89
1-6 figure 1-3 the details tab port management configuration example network requirements as shown in figure 1-4 : z server a, server b, and server c are connected to gigabitethernet 1/0/1, gigabitethernet 1/0/2, and gigabitethernet 1/0/3 or the switch respectively. The rates of the network adapters...
Page 90
1-7 configuration procedure # set the rate of gigabitethernet 1/0/4 to 1000 mbps. Z select device > port management from the navigation tree, click the setup tab to enter the page shown in figure 1-5 , and make the following configurations: figure 1-5 configure the rate of gigabitethernet 1/0/4 z se...
Page 91
1-8 figure 1-6 batch configure port rate # display the rate settings of ports. Z click the summary tab. Z select the speed option to display the rate information of all ports on the lower part of the page, as shown in figure 1-7 ..
Page 92
1-9 figure 1-7 display the rate settings of ports.
Page 93: Table of Contents
I table of contents 1 port mirroring configuration ····················································································································1-1 introduction to port mirroring ··································································································...
Page 94: Port Mirroring Configuration
1-1 1 port mirroring configuration introduction to port mirroring port mirroring is to copy the packets passing through a port (called a mirroring port) to another port (called the monitor port) connected with a monitoring device for packet analysis. You can select to port-mirror inbound, outbound, ...
Page 95
1-2 perform the tasks described in table 1-1 to configure local port mirroring: table 1-1 local port mirroring configuration task list task remarks create a local mirroring group required refer to section creating a mirroring group for details. Configure the mirroring ports required refer to section...
Page 96
1-3 table 1-2 configuration items of creating a mirroring group item description mirroring group id id of the mirroring group to be created type specify the type of the mirroring group to be created: z local : creates a local mirroring group. Return to local port mirroring configuration task list . ...
Page 97
1-4 item description stream orientation set the direction of the traffic monitored by the monitor port of the mirroring group this configuration item is available when mirror port is selected is the port type drop-down list. Z both : mirrors both received and sent packets on mirroring ports. Z inbou...
Page 98
1-5 figure 1-5 create a local mirroring group z type in mirroring group id 1. Z select local in the type drop-down list. Z click apply. # configure the mirroring ports. Click modify port to enter the page for configuring ports for the mirroring group, as shown in figure 1-6 . Figure 1-6 configure th...
Page 99
1-6 z select 1 – local in the mirroring group id drop-down list. Z select mirror port in the port type drop-down list. Z select both in the stream orientation drop-down list. Z select gigabitethernet 1/0/1 and gigabitethernet 1/0/2 on the chassis front panel. Z click apply. A configuration progress ...
Page 100
1-7 z click apply. A configuration progress dialog box appears. Z after the configuration process is complete, click close in the dialog box. Configuration guidelines pay attention to the following points during local port mirroring configuration: z to ensure operation of your device, do not enable ...
Page 101: Table of Contents
I table of contents 1 user management······································································································································1-1 overview ····················································································································...
Page 102: User Management
1-1 1 user management overview in the user management part, you can: z set the username, password, and access level for an ftp or telnet user. Z set the super password for switching the current web user level to the management level. Z switch the current web user access level to the management level...
Page 103
1-2 table 1-1 configuration items for creating a user item description username set the username for a user access level set the access level for a user. Users of different levels can perform different operations. Web user levels, from low to high, are visitor, monitor, configure, and management. Z ...
Page 104
1-3 figure 1-2 super password table 1-2 describes the configuration items of specifying a super password. Table 1-2 super password configuration items item description create/remove set the operation type: z create: configure or modify the super password. Z remove: remove the current super password....
Page 105
1-4 figure 1-3 switch to the management level..
Page 106: Table of Contents
I table of contents 1 loopback test configuration···················································································································1-1 overview ···························································································································...
Page 107: Loopback Test Configuration
1-1 1 loopback test configuration overview you can check whether an ethernet port works normally by performing the ethernet port loopback test, during which the port cannot forward data packets normally. Ethernet port loopback test can be an internal loopback test or an external loopback test. Z in ...
Page 108
1-2 after selecting a testing type, you need to select a port on which you want to perform the loopback test from the chassis front panel. After that, click test to start the loopback test, and you can see the test result in the result text box, as shown in figure 1-2 . Figure 1-2 loopback test resu...
Page 109: Table of Contents
I table of contents 1 vct······························································································································································1-1 overview ········································································································...
Page 110: Vct
1-1 1 vct overview z the optical interface of a sfp port does not support this feature. Z a link in the up state goes down and then up automatically if you perform this operation on one of the ethernet interfaces forming the link. You can use the virtual cable test (vct) function to check the status...
Page 111
1-2 table 1-1 description on the cable test result item description cable status status and length of the cable. The status of a cable can be normal, abnormal, abnormal(open), abnormal(short), or failure. Z when a cable is normal, the cable length displayed is the total length of the cable. Z when a...
Page 112: Table of Contents
I table of contents 1 flow interval configuration ······················································································································1-1 overview ·······················································································································...
Page 113: Flow Interval Configuration
1-1 1 flow interval configuration overview with the flow interval module, you can view the average receiving rate and average sending rate of a port over the specified interval. Monitoring port traffic statistics setting the traffic statistics generating interval select device > flow interval from t...
Page 114
1-2 figure 1-2 port traffic statistics.
Page 115: Table of Contents
I table of contents 1 storm constrain configuration················································································································1-1 overview ····························································································································...
Page 116
1-1 1 storm constrain configuration overview the storm constrain function limits traffic of a port within a predefined upper threshold to suppress packet storms in an ethernet. With this function enabled on a port, the system detects the amount of broadcast traffic, multicast traffic, and unicast tr...
Page 117
1-2 figure 1-1 the storm constrain tab z the traffic statistics generating interval set here is the interval used by the storm constrain function for measuring traffic against the traffic thresholds. It is different from the interval set in the flow interval module, which is used for measuring the a...
Page 118
1-3 figure 1-2 add storm constrain settings for ports table 1-1 describes the port storm constrain configuration items. Table 1-1 port storm constrain configuration items item remarks control mode specify the action to be performed when a type of traffic exceeds the corresponding upper threshold. Av...
Page 119
1-4 item remarks trap select or clear the option to enable or disable the system to send trap messages both when an upper threshold is crossed and when the corresponding lower threshold is crossed after that. Log select or clear the option to enable or disable the system to output logs both when an ...
Page 120: Table of Contents
I table of contents 1 rmon ··························································································································································1-1 rmon overview ·····································································································...
Page 121: Rmon
1-1 1 rmon rmon overview remote monitoring (rmon) is used to realize the monitoring and management from the management devices to the managed devices on the network by implementing such functions as statistics and alarm. The statistics function enables a managed device to periodically or continuousl...
Page 122
1-2 rmon groups among the rmon groups defined by rmon specifications (rfc 2819), the realized public mib of the device supports the statistics group, history group, alarm group, and event group. Statistics group the statistics group defines that the system collects statistics on various traffic info...
Page 123
1-3 z log-trap: logging event information in the event log table and sending a trap to the nms. Z none: no action. Configuring rmon configuration task list configuring the rmon statistics function rmon statistics function can be implemented by either the statistics group or the history group, but th...
Page 124
1-4 configuring the rmon alarm function z if you need to configure that the managed device sends a trap to the nms when it triggers an alarm event, you should configure the snmp agent as described in snmp configuration before configuring the rmon alarm function. Z as the alarm variables that can be ...
Page 125
1-5 task remarks displaying rmon event logs if you have configured the system to log an event after the event is triggered when you configure the event group, the event is recorded into the rmon log. You can perform this task to display the details of the log table configuring a statistics entry sel...
Page 126
1-6 configuring a history entry select device > rmon from the navigation tree and click the history tab to enter the page, as shown in figure 1-3 . Click add to enter the page for adding a history entry, as shown in figure 1-4 . Figure 1-3 history entry figure 1-4 add a history entry table 1-6 descr...
Page 127
1-7 configuring an event entry select device > rmon from the navigation tree and click the event tab to enter the page, as shown in figure 1-5 . Click add to enter the page for adding an event entry, as shown in figure 1-6 . Figure 1-5 event entry figure 1-6 add an event entry table 1-7 describes th...
Page 128
1-8 figure 1-7 alarm entry figure 1-8 add an alarm entry figure 1-8 describes the items for configuring an alarm entry. Table 1-8 alarm entry configuration items item description statics item set the traffic statistics that will be collected and monitored, see table 1-9 for details. Alarm variable i...
Page 129
1-9 item description interval set the sampling interval. Sample item sample type set the sampling type, including: z absolute: absolute sampling, namely, to obtain the value of the variable when the sampling time is reached. Z delta: delta sampling, namely, to obtain the variation value of the varia...
Page 130
1-10 figure 1-9 rmon statistics information table 1-9 describes the fields of rmon statistics. Table 1-9 fields of rmon statistics item description number of received bytes total number of octets received by the interface, corresponding to the mib node etherstatsoctets. Number of received packets to...
Page 131
1-11 item description number of received packets smaller than 64 bytes total number of undersize packets (shorter than 64 octets) received by the interface, corresponding to the mib node etherstatsundersizepkts. Number of received packets larger than 1518 bytes total number of oversize packets (long...
Page 132
1-12 figure 1-10 rmon history sampling information table 1-10 describes the fields of rmon history sampling information. Table 1-10 fields of rmon history sampling information item description no number of the entry in the system buffer statistics are numbered chronologically when they are saved to ...
Page 133
1-13 displaying rmon event logs select device > rmon from the navigation tree and click the log tab to enter the page, as shown in figure 1-11 , which displays log information for all event entries. Figure 1-11 log return to display rmon running status . Rmon configuration example network requiremen...
Page 134
1-14 figure 1-13 add a statistics entry z select gigabitethernet1/0/1 from the interface name drop-down box. Z type user1-rmon in the text box of owner. Z click apply. # display rmon statistics for interface ethernet 1/0/1. Z click the icon corresponding to gigabitethernet 1/0/1. Z you can view the ...
Page 135
1-15 figure 1-14 display rmon statistics # create an event to start logging after the event is triggered. Z click the event tab, click add, and then perform the following configurations, as shown in figure 1-15 . Figure 1-15 configure an event group.
Page 136
1-16 z type 1-rmon in the text box of owner. Z select the check box before log. Z click apply. Z the page goes to the page displaying the event entry, and you can see that the entry index of the new event is 1, as shown in figure 1-16 . Figure 1-16 display the index of a event entry # configure an a...
Page 137
1-17 z select number of received bytes from the statics item drop-down box. Z select gigabitethernet1/0/1 from the interface name drop-down box. Z type 10 in the text box of interval. Z select delta from the simple type drop-down box. Z type 1-rmon in the text box of owner. Z type 1000 in the text b...
Page 138: Table of Contents
I table of contents 1 energy saving configuration ···················································································································1-1 overview ··························································································································...
Page 139: Energy Saving Configuration
1-1 1 energy saving configuration overview energy saving allows you to configure a port to work at the lowest transmission speed, disable poe, or go down during a specified time range on certain days of a week. The port resumes working normally when the effective time period ends. Configuring energy...
Page 140
1-2 item description lowest speed set the port to transmit data at the lowest speed. If you configure the lowest speed limit on a port that does not support 10 mbps, the configuration cannot take effect. Shutdown shut down the port. An energy saving policy can have all the three energy saving scheme...
Page 141: Table of Contents
I table of contents 1 snmp ··························································································································································1-1 snmp overview······································································································...
Page 142: Snmp
1-1 1 snmp snmp overview simple network management protocol (snmp) offers the communication rules between a management device and the managed devices on the network; it defines a series of messages, methods and syntaxes to implement the access and management from the management device to the managed...
Page 143
1-2 informrequest; it supports more data types such as counter64; and it provides various error codes, thus being able to distinguish errors in more detail. Z snmpv3 offers an authentication that is implemented with a user-based security model (usm). You can set the authentication and privacy functi...
Page 144
1-3 subtree mask a subtree oid used with a subtree mask defines a view subtree. A subtree mask is in hexadecimal format. After it is converted to binary bits, each bit corresponds to a node of the oid. Z 1 means precise matching, that is, the oid of the mib object to be accessed must be identical wi...
Page 145
1-4 task remarks configuring an snmp community required configuring snmp trap function optional allows you to configure that the agent can send snmp traps to the nms, and configure information about the target host of the snmp traps. By default, an agent is allowed to send snmp traps to the nms. Con...
Page 146
1-5 figure 1-4 set up table 1-3 describes the configuration items for enabling snmp. Table 1-3 configuration items for enabling snmp item description snmp specify to enable or disable snmp. Local engine id configure the local engine id. The validity of a user after it is created depends on the engin...
Page 147
1-6 figure 1-5 view page creating an snmp view click add, the window appears as shown in figure 1-6 . Type the view name and click apply, and then you enter the page as shown in figure 1-7 . Figure 1-6 create an snmp view (1) figure 1-7 create an snmp view (2) table 1-4 describes the configuration i...
Page 148
1-7 table 1-4 configuration items for creating an snmp view item description view name set the snmp view name. Rule select to exclude or include the objects in the view range determined by the mib subtree oid and subtree mask. Mib subtree oid set the mib subtree oid (such as 1.4.5.3.1) or name (such...
Page 149
1-8 figure 1-9 configure an snmp community figure 1-10 create an snmp community table 1-5 describes the configuration items for configuring an snmp community. Table 1-5 configuration items for configuring an snmp community item description community name set the snmp community name. Access right con...
Page 150
1-9 figure 1-11 snmp group figure 1-12 create an snmp group table 1-6 describes the configuration items for creating an snmp group. Table 1-6 configuration items for creating an snmp group item description group name set the snmp group name. Security level select the security level for the snmp grou...
Page 151
1-10 item description acl associate a basic acl with the group to restrict the source ip address of snmp packets, that is, you can configure to allow or prohibit snmp packets with a specific source ip address, so as to restrict the intercommunication between the nms and the agent. Return to snmpv3 c...
Page 152
1-11 table 1-7 configuration items for creating an snmp user item description user name set the snmp user name. Security level select the security level for the snmp group. The available security levels are: z noauth/nopriv: no authentication no privacy. Z auth/nopriv: authentication without privacy...
Page 153
1-12 figure 1-15 traps configuration figure 1-16 add a target host of snmp traps table 1-8 describes the configuration items for adding a target host of snmp traps. Table 1-8 configuration items for adding a target host item description destination ip address set the destination ip address. Select t...
Page 154
1-13 return to snmpv1 or snmpv2c configuration task list or snmpv3 configuration task list . Snmp configuration example network requirements z as shown in figure 1-17 , the nms connects to the agent, switch, through an ethernet. Z the ip address of the nms is 1.1.1.2/24. Z the ip address of the vlan...
Page 155
1-14 figure 1-19 create an snmp view (1) z type view1 in the text box. Z click apply to enter the snmp rule configuration page, as shown in figure 1-20 . Figure 1-20 create an snmp view (2) z select the included radio box. Z type the mib subtree oid interfaces. Z click add. Z click apply. A configur...
Page 156
1-15 z click the group tab and then click add to enter the page as shown in figure 1-22 . Figure 1-22 create an snmp group z type group1 in the text box of group name. Z select view1 from the read view drop-down box. Z select view1 from the write view drop-down box. Z click apply. # configure an snm...
Page 157
1-16 z click the trap tab and enter the page as shown in figure 1-24 . Figure 1-24 enable the agent to send snmp traps z select the enable snmp trap check-box. Z click apply. # add target hosts of snmp traps. Z click add to enter the page as shown in figure 1-25 . Figure 1-25 add target hosts of snm...
Page 158
1-17 the configuration on nms must be consistent with that on the agent. Otherwise, you cannot perform corresponding operations. Snmpv3 adopts a security mechanism of authentication and privacy. You need to configure username and security level. According to the configured security level, you need t...
Page 159: Table of Contents
I table of contents 1 interface statistics·····································································································································1-1 overview ················································································································...
Page 160: Interface Statistics
1-1 1 interface statistics overview the interface statistics module displays statistics information about the packets received and sent through interfaces. Displaying interface statistics select device > interface statistics from the navigation tree to enter the interface statistics display page, as...
Page 161
1-2 field description outucastpkts number of unicast packets sent through the interface. Outnucastpkts number of non-unicast packets sent through the interface. Outdiscards number of valid packets discarded in the outbound direction. Outerrors number of invalid packets sent through the interface..
Page 162: Table of Contents
I table of contents 1 vlan configuration ··································································································································1-1 overview ····················································································································...
Page 163: Vlan Configuration
1-1 1 vlan configuration overview introduction to vlan ethernet is a network technology based on the carrier sense multiple access/collision detect (csma/cd) mechanism. As the medium is shared, collisions and excessive broadcasts are common on an ethernet. To address the issue, virtual lan (vlan) wa...
Page 164
1-2 the format of vlan-tagged frames is defined in ieee 802.1q-1999. In the header of a traditional ethernet data frame as shown in figure 1-2 , the field after the destination mac address and the source mac address fields (da&sa in the figure) is the type field indicating the upper layer protocol t...
Page 165
1-3 because the web interface is available only for port-based vlans, this chapter introduces only port-based vlans. Introduction to port-based vlan port-based vlans group vlan members by port. A port forwards traffic for a vlan only after it is assigned to the vlan. Port link type depending on the ...
Page 166
1-4 configuring a vlan configuration task list use one of the following two approaches or combine the following two approaches to configure a vlan: z approach i: modify a vlan, as shown in table 1-1 . Z approach ii: modify a port, as shown in table 1-2 . Table 1-1 vlan configuration task list (appro...
Page 167
1-5 figure 1-4 the create tab table 1-3 describes the configuration items of creating a vlan. Table 1-3 configuration items of creating vlans item description vlan ids ids of the vlans to be created id select the id of the vlan whose description string is to be modified. Click the id of the vlan to ...
Page 168
1-6 figure 1-5 the select vlan tab table 1-4 describes the configuration items of selecting vlans. Table 1-4 configuration items of selecting vlans item description display all vlans display a subnet of all configured vlans select one of the two radio buttons: z display all vlans: displays all confi...
Page 169
1-7 figure 1-6 the modify vlan tab table 1-5 describes the configuration items of modifying a vlan. Table 1-5 configuration items of modifying a vlan item description please select a vlan to modify select the vlan to be modified. Select a vlan in the drop-down list. The vlans available for selection...
Page 170
1-8 modifying ports select network > vlan from the navigation tree and click modify port to enter the page for modifying ports, as shown in figure 1-7 . Figure 1-7 the modify port tab table 1-6 describes the configuration items of modifying ports. Table 1-6 configuration items of modifying ports ite...
Page 171
1-9 item description link type set the link type of the selected ports, which can be access, hybrid, or trunk. This item is available when the link type option is selected in the select membership type area. Pvid delete set the pvid of the select ports; selecting delete is to restore the default vla...
Page 172
1-10 figure 1-9 configure gigabitethernet 1/0/1 as a trunk port and its pvid as 100 z select trunk in the link type drop-down list. Z select the pvid check box, and then type in pvid 100. Z select gigabitethernet 1/0/1 on the chassis front device panel. Z click apply. # create vlan 2, vlan 6 through...
Page 173
1-11 figure 1-10 create vlan 2, vlan 6 through vlan 50, and vlan 100 z type in vlan ids 2, 6-50, 100. Z click apply. # assign gigabitethernet 1/0/1 to vlan 100 as an untagged member. Click select vlan to enter the page for selecting vlans, as shown in figure 1-11 . Figure 1-11 set a vlan range z sel...
Page 174
1-12 z click select. Click modify vlan to enter the page for modifying the ports in a vlan, as shown in figure 1-12 . Figure 1-12 assign gigabitethernet 1/0/1 to vlan 100 as an untagged member z select 100 – vlan 0100 in the please select a vlan to modify: drop-down list. Z select the untagged radio...
Page 175
1-13 click modify port to enter the page for modifying the vlans to which a port belongs, as shown in figure 1-14 . Figure 1-14 assign gigabitethernet 1/0/1 to vlan 2, and vlan 6 through vlan 50 as a tagged member z select gigabitethernet 1/0/1 on the chassis front device panel. Z select the tagged ...
Page 176: Table of Contents
I table of contents 1 vlan interface configuration ··················································································································1-1 overview ··························································································································...
Page 177: Vlan Interface Configuration
1-1 1 vlan interface configuration overview for details about vlan, refer to vlan configuration. For hosts of different vlans to communicate, you must use a router or layer 3 switch to perform layer 3 forwarding. To achieve this, vlan interfaces are used. Vlan interfaces are virtual interfaces used ...
Page 178
1-2 figure 1-1 the create tab table 1-2 describes the configuration items of creating a vlan interface. Table 1-2 configuration items of creating a vlan interface item description input a vlan id: input the id of the vlan interface to be created. Before creating a vlan interface, make sure that the ...
Page 179
1-3 modifying a vlan interface z after you modify the ipv4 address for a selected vlan interface on the page for modifying vlan interfaces, you need to click the correct apply button to submit the modification. Z after you change the ip address of the vlan interface you are using to log in to the de...
Page 180
1-4 item description dhcp bootp manual configure the way in which the vlan interface gets an ipv4 address. Allow the vlan interface to automatically obtain an ip address by selecting the dhcp or bootp option, or manually assign the vlan interface an ip address by selecting the manual option. Modif y...
Page 181: Table of Contents
I table of contents 1 voice vlan configuration························································································································1-1 overview ·························································································································...
Page 182: Voice Vlan Configuration
1-1 1 voice vlan configuration overview a voice vlan is dedicated to voice traffic. After assigning the ports connecting to voice devices to a voice vlan, you can configure quality of service (qos) parameters for the voice traffic, thus improving transmission priority and ensuring voice quality. A d...
Page 183
1-2 when untagged packets are received from an ip phone: z in automatic mode, the system matches the source mac addresses in the untagged packets sent by the ip phone upon its power-on against the oui list. If a match is found, the system automatically assigns the receiving port to a voice vlan, iss...
Page 184
1-3 z if an ip phone sends tagged voice traffic and its access port is configured with 802.1x authentication and guest vlan, you must assign different vlan ids for the voice vlan, the default vlan of the access port, and the 802.1x guest vlan for the functions to operate normally. Z if an ip phone s...
Page 185
1-4 voice vlan working mode packet type packet processing mode untagged packets packets carrying the voice vlan tag the port does not check the source mac addresses of inbound packets. All types of packets can be transmitted in the voice vlan. Normal mode packets carrying other tags forwarded or dro...
Page 186
1-5 table 1-5 configuration task list for a port in manual voice vlan assignment mode task remarks configuring voice vlan globally optional configure the voice vlan to operate in security mode and configure the aging timer. Assigning the port to the voice vlan required note that after an access port...
Page 187
1-6 item description voice vlan aging time set the voice vlan aging timer. The voice vlan aging timer setting only applies to a port in automatic voice vlan assignment mode. The voice vlan aging timer starts as soon as the port is assigned to the voice vlan. If no voice packet has been received befo...
Page 188
1-7 item description select ports select the port on the chassis front panel. You can select multiple ports to configure them in bulk. The numbers of the selected ports will be displayed in the ports selected for voice vlan text box. To set the voice vlan assignment mode of a port to automatic, you ...
Page 189
1-8 item description description set the description of the oui address entry. Return to configuring voice vlan on a port in automatic voice vlan assignment mode . Return to configuring voice vlan on a port working in manual voice vlan assignment mode . Voice vlan configuration examples configuring ...
Page 190
1-9 figure 1-5 create vlan 2 z type in vlan id 2. Z click create. # configure gigabitethernet 1/0/1 as a hybrid port. Z select device > port management from the navigation tree, and click setup on the displayed page to enter the page shown in figure 1-6 ..
Page 191
1-10 figure 1-6 configure gigabitethernet 1/0/1 as a hybrid port z select hybrid from the link type dropdown list. Z select gigabitethernet 1/0/1 from the chassis front panel. Z click apply. # configure the voice vlan function globally. Z select network > voice vlan from the navigation tree and clic...
Page 192
1-11 z select enable in the voice vlan security drop-down list. (you can skip this step, because the voice vlan security mode is enabled by default) z set the voice vlan aging timer to 30 minutes. Z click apply. # configure voice vlan on gigabitethernet 1/0/1. Z click the port setup tab to enter the...
Page 193
1-12 figure 1-9 add oui addresses to the oui list z type in oui address 0011-2200-0000. Z select ffff-ff00-0000 inthe mask drop-down list. Z type in description string test. Z click apply. Verify the configuration z when the configurations described above are completed, the oui summary tab is displa...
Page 194
1-13 figure 1-11 current voice vlan information configuring a voice vlan on a port in manual voice vlan assignment mode network requirements z configure vlan 2 as a voice vlan that carries only voice traffic. Z the ip phone connected to hybrid port gigabitethernet 1/0/1 sends untagged voice traffic....
Page 195
1-14 figure 1-13 create vlan 2 z type in vlan id 2. Z click create. # configure gigabitethernet 1/0/1 as a hybrid port and configure its default vlan as vlan 2. Z select device > port management from the navigation tree, and click setup on the displayed page to enter the page shown in figure 1-14 ..
Page 196
1-15 figure 1-14 configure gigabitethernet 1/0/1 as a hybrid port z select hybrid from the link type dropdown list. Z select the pvid option and type 2 in the text box. Z select gigabitethernet 1/0/1 from the chassis front panel. Z click apply. # assign gigabitethernet 1/0/1 to vlan 2 as an untagged...
Page 197
1-16 figure 1-15 assign gigabitethernet 1/0/1 to vlan 2 as an untagged member z select gigabitethernet 1/0/1 from the chassis front panel. Z select the untagged option. Z type in vlan id 2. Z click apply. A configuration progress dialog box appears, as shown in figure 1-16 . Figure 1-16 configuratio...
Page 198
1-17 figure 1-17 configure voice vlan on gigabitethernet 1/0/1 z select manual in the voice vlan port mode drop-down list. Z select enable in the voice vlan port state drop-down list. Z type in voice vlan id 2. Z select gigabitethernet 1/0/1 on the chassis front panel. Z click apply. # add oui addre...
Page 199
1-18 z type in description string test. Z click apply. Verify the configuration z when the configurations described above are completed, the oui summary tab is displayed by default, as shown in figure 1-19 . You can view the information about the newly-added oui address. Figure 1-19 current oui list...
Page 200
1-19 z in automatic voice vlan assignment mode, a hybrid port can process only tagged voice traffic. However, the protocol-based vlan function requires hybrid ports to process untagged traffic. Therefore, if a vlan is configured as the voice vlan and a protocol-based vlan at the same time, the proto...
Page 201: Table of Contents
I table of contents 1 mac address configuration ····················································································································1-1 overview ···························································································································...
Page 202: Mac Address Configuration
1-1 1 mac address configuration z currently, mac address configurations related to interfaces only apply to layer 2 ethernet interfaces. Z this manual covers only the management of static and dynamic mac address entries, not multicast mac address entries. Overview a device maintains a mac address ta...
Page 203
1-2 z broadcast mode: if the device receives a frame with the destination address being all fs, or no entry matches the destination mac address, the device broadcasts the frame to all the ports except the receiving port. Figure 1-1 mac address table of the device configuring mac addresses mac addres...
Page 204
1-3 figure 1-2 the mac tab figure 1-3 create a mac address entry table 1-1 shows the detailed configuration of creating a mac address entry..
Page 205
1-4 table 1-1 configuration items of creating a mac address entry item description mac set the mac address to be added type set the type of the mac address entry, which can be: z static : indicates static mac address entries that never age out z dynamic :indicates dynamic mac address entries that wi...
Page 206
1-5 mac address configuration example network requirements use the mac address table management function of the web-based nms. It is required to add a static mac address 00e0-fc35-dc71 under gigabitethernet 1/0/1 in vlan 1. Configuration procedure # create a static mac address entry. Select network ...
Page 207: Table of Contents
I table of contents 1 mstp configuration ··································································································································1-1 overview ····················································································································...
Page 208: Mstp Configuration
1-1 1 mstp configuration overview as a layer 2 management protocol, the spanning tree protocol (stp) eliminates layer 2 loops by selectively blocking redundant links in a network, and in the mean time, allows for link redundancy. Like many other protocols, stp evolves as the network grows. The later...
Page 209
1-2 root port on a non-root bridge, the port nearest to the root bridge is called the root port. The root port is responsible for communication with the root bridge. Each non-root bridge has one and only one root port. The root bridge has no root port. Designated bridge and designated port the follo...
Page 210
1-3 all the ports on the root bridge are designated ports. How stp works the devices on a network exchange bpdus to identify the network topology. Configuration bpdus contain sufficient information for the network devices to complete spanning tree calculation. Important fields in a configuration bpd...
Page 211
1-4 table 1-2 selection of the optimum configuration bpdu step actions 1 upon receiving a configuration bpdu on a port, the device performs the following: z if the received configuration bpdu has a lower priority than that of the configuration bpdu generated by the port, the device discards the rece...
Page 212
1-5 step description 3 the device compares the calculated configuration bpdu with the configuration bpdu on the port of which the port role is to be defined, and acts depending on the comparison result: z if the calculated configuration bpdu is superior, the device considers this port as the designa...
Page 213
1-6 device port name bpdu of port cp1 {2, 0, 2, cp1} device c cp2 {2, 0, 2, cp2} z comparison process and result on each device the following table shows the comparison process and result on each device. Table 1-5 comparison process and result on each device device comparison process bpdu of port af...
Page 214
1-7 device comparison process bpdu of port after comparison z port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received configuration bpdu is superior to the configuration bpdu of the local port {2, 0, 2, cp1}, and updates the configuration bpdu of cp1. Z ...
Page 215
1-8 figure 1-3 the final calculated spanning tree ap1 ap2 device a with priority 0 device b with priority 1 device c with priority 2 bp1 bp2 cp2 5 4 the spanning tree calculation process in this example is only a simplified process. The bpdu forwarding mechanism in stp z upon network initiation, eve...
Page 216
1-9 for this reason, as a mechanism for state transition in stp, the newly elected root ports or designated ports require twice the forward delay time before transiting to the forwarding state to ensure that the new configuration bpdu has propagated throughout the network. Z hello time is the time i...
Page 217
1-10 z mstp supports mapping vlans to mst instances (mstis) by means of a vlan-to-msti mapping table. Mstp can reduce communication overheads and resource usage by mapping multiple vlans to one msti. Z mstp divides a switched network into multiple regions, each containing multiple spanning trees tha...
Page 218
1-11 for example, all the devices in region a0 in figure 1-4 have the same mst region configuration as follows: z the same region name, z the same vlan-to-msti mapping configuration (vlan 1 is mapped to msti 1, vlan 2 to msti 2, and the rest to the common and internal spanning tree (cist, that is, m...
Page 219
1-12 common root bridge the common root bridge is the root bridge of the cist. In figure 1-4 , for example, the common root bridge is a device in region a0. Boundary port a boundary port is a port that connects an mst region to another mst region, or to a single spanning-tree region running stp, or ...
Page 220
1-13 figure 1-5 port roles connecting to the common root bridge port 1 port 2 master port alternate port designated port port 3 port 4 port 5 a b c d port 6 backup port mst region in figure 1-5 , devices a, b, c, and d constitute an mst region. Port 1 and port 2 of device a are connected to the comm...
Page 221
1-14 table 1-6 ports states supported by different port roles port role port state root port/master port designated port boundary port alternate port backup port forwarding √ √ √ — — learning √ √ √ — — discarding √ √ √ √ √ how mstp works mstp divides an entire layer 2 network into multiple mst regio...
Page 222
1-15 protocols and standards mstp is documented in: z ieee 802.1d: spanning tree protocol z ieee 802.1w: rapid spanning tree protocol z ieee 802.1s: multiple spanning tree protocol configuring mstp configuration task list perform the tasks described in table 1-7 to configure mstp. Table 1-7 mstp con...
Page 223
1-16 figure 1-7 configure an mst region table 1-8 describes the configuration items of configuring an mst region. Table 1-8 configuration items of configuring an mst region item description region name mst region name the mst region name is the bridge mac address of the device by default. Revision l...
Page 224
1-17 figure 1-8 configure mstp globally table 1-9 describes the configuration items of configuring mstp globally. Table 1-9 configuration items of configuring mstp globally item description enable stp globally select whether to enable stp globally. Other mstp configurations take effect only after yo...
Page 225
1-18 item description bridge diameter any two stations in a switched network are interconnected through a specific path composed of a series of devices. The bridge diameter (or the network diameter) is the number of devices on the path composed of the most devices. After you set the network diameter...
Page 226
1-19 configuring mstp on a port select network > mstp from the navigation tree, and then click port setup to enter the page for configuring mstp on ports, as shown in figure 1-9 . Figure 1-9 mstp configuration on a port table 1-10 describes the configuration items of configuring mstp on a port. Tabl...
Page 227
1-20 item description instance id port priority auto path cost instance manual path cost set the priority and path cost of the port in the current msti. Z the priority of a port is an important factor in determining whether the port can be elected as the root port of a device. If all other condition...
Page 228
1-21 table 1-11 protection types protection type description edged port set the port as an edge port. Some ports of access layer devices are directly connected to pcs or file servers, which cannot generate bpdus. You can set these ports as edge ports to achieve fast transition for these ports. You a...
Page 229
1-22 select a port (gigabitethernet 1/0/16 for example) on the chassis front panel (if aggregate interfaces are configured on the device, the page displays a list of aggregate interfaces below the chassis front panel. You can select aggregate interfaces from this list). The lower part of the page di...
Page 230
1-23 field description num of vlans mapped number of vlans mapped to the current msti porttimes major parameters for the port: z hello: hello timer z maxage: max age timer z fwdly: forward delay timer z msgage: message age timer z remain hop: remaining hops bpdu sent statistics on sent bpdus bpdu re...
Page 231
1-24 figure 1-11 network diagram for mstp configuration “permit:“ next to a link in the figure is followed by the vlans the packets of which are permitted to pass this link. Configuration procedure 1) configure switch a. # configure an mst region. Z select network > mstp from the navigation tree to ...
Page 232
1-25 figure 1-13 configure an mst region z set the region name to example. Z set the revision level to 0. Z select the manual radio button. Z select 1 in the instance id drop-down list. Z set the vlan id to 10. Z click apply to map vlan 10 to msti 1 and add the vlan-to-msti mapping entry to the vlan...
Page 233
1-26 figure 1-14 configure mstp globally (on switch a) z select enable in the enable stp globally drop-down list. Z select mstp in the mode drop-down list. Z select the check box before instance. Z set the instance id field to 1. Z set the root type field to primary. Z click apply. 2) configure swit...
Page 234
1-27 z set the root type field to primary. Z click apply. 3) configure switch c. # configure an mst region. (the procedure here is the same as that of configuring an mst region on switch a.) # configure mstp globally. Z select network > mstp from the navigation tree, and then click global to enter t...
Page 235
1-28 figure 1-15 configure mstp globally (on switch d) z select enable in the enable stp globally drop-down list. Z select mstp in the mode drop-down list. Z click apply. Guidelines follow these guidelines when configuring mstp: z two devices belong to the same mst region only if they are interconne...
Page 236
1-29 z configure ports that are directly connected to terminals as boundary ports and enable bpdu guard for them. In this way, these ports can rapidly transit to the forwarding state, and the network security can be ensured..
Page 237: Table of Contents
I table of contents 1 link aggregation and lacp configuration ····························································································1-1 overview ·····································································································································...
Page 238
1-1 1 link aggregation and lacp configuration overview link aggregation aggregates multiple physical ethernet ports into one logical link, also called an aggregation group. It allows you to increase bandwidth by distributing traffic across the member ports in the aggregation group. In addition, it p...
Page 239
1-2 the rate of an aggregate interface is the sum of the selected member ports’ rates. The duplex mode of an aggregate interface is consistent with that of the selected member ports. Note that all selected member ports use the same duplex mode. For how the state of a member port is determined, refer...
Page 240
1-3 link aggregation modes depending on the link aggregation procedure, link aggregation operates in one of the following two modes: z static aggregation mode z dynamic aggregation mode static aggregation mode lacp is disabled on the member ports in a static aggregation group. In a static aggregatio...
Page 241
1-4 z compare the system id (comprising the system lacp priority and the system mac address) of the actor with that of the partner. The system with the lower lacp priority wins out. If they are the same, compare the system mac addresses. The system with the smaller mac address wins out. Z compare th...
Page 242
1-5 table 1-2 static aggregation group configuration task list task remarks creating a link aggregation group required create a static aggregate interface and configure member ports for the static aggregation group automatically created by the system when you create the aggregate interface. By defau...
Page 243
1-6 figure 1-1 create a link aggregation group table 1-4 describes the configuration items of creating a link aggregation group. Table 1-4 configuration items of creating a link aggregation group item description enter link aggregation interface id assign an id to the link aggregation group to be cr...
Page 244
1-7 displaying information of an aggregate interface select network > link aggregation from the navigation tree. The summary tab is displayed by default, as shown in figure 1-2 . Figure 1-2 display information of an aggregate interface table 1-5 describes the fields on the summary tab. Table 1-5 fie...
Page 245
1-8 figure 1-3 the setup tab after finishing each configuration item, click the right apply button to submit the configuration. Table 1-6 describes the configuration items. Table 1-6 lacp priority configuration items item description select lacp enabled port(s) parameters set a port lacp priority. S...
Page 246
1-9 figure 1-4 display the information of lacp-enabled ports the upper part of the page displays a list of all lacp-enabled ports on the device and information about them. To view information about the partner port of a lacp-enabled port, select it in the port list, and then click view details. Deta...
Page 247
1-10 field/button description inactive reason reason code indicating why a port is inactive (that is, unselected) for receiving/transmitting user data. For the meanings of the reason codes, see the bottom of the page shown in figure 1-4 . Partner port name of the peer port partner port state state i...
Page 248
1-11 figure 1-5 network diagram for static link aggregation configuration configuration procedure you can create a static or dynamic link aggregation group to achieve load balancing. 1) approach 1: create a static link aggregation group # create static link aggregation group 1. Select network > link...
Page 249
1-12 z select gigabitethernet 1/0/1, gigabitethernet 1/0/2, and gigabitethernet 1/0/3 on the chassis front panel. Z click apply. 2) approach 2: create a dynamic link aggregation group # create dynamic link aggregation group 1. Select network > link aggregation from the navigation tree, and then clic...
Page 250
1-13 z reference port: select a port as the reference port from the ports that are in up state and with the same class-two configurations as the corresponding aggregate interface. The selection order is as follows: full duplex/high speed, full duplex/low speed, half duplex/high speed, and half duple...
Page 251: Table of Contents
I table of contents 1 lldp ···························································································································································1-1 overview ·········································································································...
Page 252: Lldp
1-1 1 lldp overview background in a heterogeneous network, it is important that different types of network devices from different vendors can discover one other and exchange configuration for interoperability and management sake. This calls for a standard configuration exchange platform. To address ...
Page 253
1-2 field description source mac address the mac address of the sending port. If the port does not have a mac address, the mac address of the sending bridge is used. Type the ethernet type for the upper layer protocol. It is 0x88cc for lldp. Data lldp data. Fcs frame check sequence, a 32-bit crc val...
Page 254
1-3 an lldpdu can carry up 28 types of tlvs, of which the chassis id tlv, port id tlv, ttl tlv, and end of lldpdu tlv (end tlv in the figure) are mandatory tlvs that must be carried and other tlvs are optional. Tlvs tlvs are type, length, and value sequences that carry information elements, where th...
Page 255
1-4 type description vlan name a specific vlan name on the port protocol identity protocols supported on the port currently, 3com switch 2900 supports receiving but not sending protocol identity tlvs. 3) ieee 802.3 organizationally specific tlvs table 1-5 ieee 802.3 organizationally specific tlvs ty...
Page 256
1-5 type description manufacturer name allows a med endpoint to advertise its vendor name. Model name allows a med endpoint to advertise its model name. Asset id allows a med endpoint to advertise its asset id. The typical case is that the user specifies the asset id for the endpoint to facilitate d...
Page 257
1-6 this is the fast sending mechanism of lldp. With this mechanism, a specific number of lldpdus are sent successively at the 1-second interval to help lldp neighbors discover the local device as soon as possible. Then, the normal lldpdu transit interval resumes. Receiving lldpdus an lldp-enabled p...
Page 258
1-7 task remarks configuring lldp settings on ports optional lldp settings include lldp operating mode, packet encapsulation, cdp compatibility, device information polling, trapping, and advertised tlvs. By default, z the lldp operating mode is txrx. Z the encapsulation format is ethernet ii. Z cdp ...
Page 259
1-8 figure 1-4 the port setup tab return to lldp configuration task list . Configuring lldp settings on ports select network > lldp from the navigation tree to enter the port setup tab, as shown in figure 1-4 . You can configure lldp settings on ports individually or in batch..
Page 260
1-9 z to configure lldp settings on ports individually, click the icon for the port you are configuring. On the page displayed as shown in figure 1-5 , you can modify or view the lldp settings of the port. Figure 1-5 the page for modifying lldp settings on a port z to configure lldp settings on port...
Page 261
1-10 figure 1-6 the page for modifying lldp settings on ports in batch table 1-8 describes the port lldp configuration items. Table 1-8 port lldp configuration items item description interface name displays the name of the port or ports you are configuring. Dldp state displays the lldp enabling stat...
Page 262
1-11 item description cdp operating mode set the cdp compatibility of lldp. Available options include: z disable: neither sends nor receives cdpdus. Z txrx: sends and receives cdpdus to enable lldp to be compatible with cdp on the port, you must enable cdp compatibility on the global setup tab and s...
Page 263
1-12 item description link aggregation select to include the link aggregation tlv in transmitted lldpdus. Mac/phy configuration/status select to include the mac/phy configuration/status tlv in transmitted lldpdus. Maximum frame size select to include the maximum frame size tlv in transmitted lldpdus...
Page 264
1-13 figure 1-7 the global setup tab table 1-9 describes the global lldp setup configuration items. Table 1-9 global lldp setup configuration items item description lldp enable select from the dropdown list to enable or disable global lldp. Cdp compatibility select from the dropdown list to enable o...
Page 265
1-14 item description ttl multiplier set the ttl multiplier. The ttl tlv carried in an lldpdu determines how long the device information carried in the lldpdu can be saved on a recipient device. You can configure the ttl of locally sent lldpdus to determine how long information about the local devic...
Page 266
1-15 information is organized by type and displayed in tabs as shown in figure 1-8 . You can click these tabs to display data you are interested in. Figure 1-8 the local information tab table 1-10 describes the local lldp information of a port. Table 1-10 local information of an lldp-enabled port fi...
Page 267
1-16 field description port pse priority available options include: z unknown, which indicates that pse priority of the port is unknown. Z critical, which is priority level 1. Z high, which is priority level 2 z low: which is priority level 3 figure 1-9 the neighbor information tab table 1-11 descri...
Page 268
1-17 field description system capabilities enabled the network function enabled on the system, which an be z repeater z bridge z router auto-negotiation supported the support of the neighbor for auto negotiation auto-negotiation enabled the enable status of auto negotiation on the neighbor. Opermau ...
Page 269
1-18 field description asset tracking identifier asset id advertised by the neighbor. This id is used for the purpose of inventory management and asset tracking. Poe pse power source the type of pse power source advertised by the neighbor, which can be: z primary z backup port pse priority available...
Page 270
1-19 displaying global lldp information select network > lldp from the navigation tree, and click the global summary tab to display global local lldp information and statistics, as shown in figure 1-12 . Figure 1-12 the global summary tab table 1-12 describes the global lldp information. Table 1-12 ...
Page 271
1-20 return to lldp configuration task list . Displaying lldp information received from lldp neighbors select network > lldp from the navigation tree and click the neighbor summary tab to display the global lldp neighbor information, as shown in figure 1-13 . Figure 1-13 the neighbor summary tab ret...
Page 272
1-21 configuration procedure 1) configure switch a # enable lldp on gigabitethernet 1/0/1 and gigabitethernet 1/0/2. (optional. By default, lldp is enabled on ethernet ports.) # set the lldp operating mode to rx on gigabitethernet 1/0/1 and gigabitethernet 1/0/2. Z select network > lldp from the nav...
Page 273
1-22 figure 1-16 the page for setting lldp on multiple ports z select rx from the lldp operating mode dropdown list. Z click apply. # enable global lldp. Z click the global setup tab, as shown in figure 1-17 . Figure 1-17 the global setup tab.
Page 274
1-23 z select enable from the lldp enable dropdown list. Z click apply. 2) configure switch b # enable lldp on port gigabitethernet 1/0/1. (optional. By default, lldp is enabled on ethernet ports.) # set the lldp operating mode to rx on gigabitethernet 1/0/1. Z select network > lldp from the navigat...
Page 275
1-24 z click the global setup tab. Z select enable from the lldp enable dropdown list. Z click apply. Configuration verification # display the status information of port gigabitethernet1/0/2 on switch a. Z select network > lldp from the navigation tree to enter the port setup tab. Z click the gigabi...
Page 276
1-25 cdp-compatible lldp configuration example network requirements as shown in figure 1-22 , port gigabitethernet 1/0/1 and gigabitethernet 1/0/2 of switch a are each connected to a cisco ip phone. On switch a configure vlan 2 as a voice vlan and configure cdp-compatible lldp to enable the cisco ip...
Page 277
1-26 figure 1-24 the page for configuring ports z select trunk in the link type drop-down list. Z click to select port gigabitethernet 1/0/1 and gigabitethernet 1/0/2 from the chassis front panel. Z click apply. # configure the voice vlan function on the two ports. Z select network > voice vlan from...
Page 278
1-27 figure 1-25 the page for configuring the voice vlan function on ports z select auto in the voice vlan port mode drop-down list. Z select enable in the voice vlan port state drop-down list. Z type the voice vlan id 2. Z click to select port gigabitethernet 1/0/1 and gigabitethernet 1/0/2 from th...
Page 279
1-28 figure 1-26 the port setup tab.
Page 280
1-29 figure 1-27 the page for modifying lldp settings on ports z select txrx from the lldp operating mode dropdown list. Z select txrx from the cdp operating mode dropdown list. Z click apply. # enable global lldp and cdp compatibility of lldp. Z click the global setup tab, as shown in figure 1-28 ....
Page 281
1-30 z select enable from the lldp enable dropdown list. Z select enable from the cdp compatibility dropdown list. Z click apply. Configuration verification # display information about lldp neighbors on switch a. Display information about lldp neighbors on switch a after completing the configuration...
Page 282: Table of Contents
I table of contents 1 igmp snooping ··········································································································································1-1 overview ·················································································································...
Page 283: Igmp Snooping
1-1 1 igmp snooping overview internet group management protocol snooping (igmp snooping) is a multicast constraining mechanism that runs on layer 2 devices to manage and control multicast groups. Principle of igmp snooping by analyzing received igmp messages, a layer 2 device running igmp snooping e...
Page 284
1-2 figure 1-2 igmp snooping related ports router a switch a switch b ge1/0/1 ge1/0/2 ge1/0/3 ge1/0/1 ge1/0/2 receiver receiver host a host b host c host d source multicast packets router port member port igmp snooping related ports include: z router port: a router port is a port on an ethernet swit...
Page 285
1-3 you can add or delete only dynamic ports rather than static ports. When receiving a general query the igmp querier periodically sends igmp general queries to all hosts and routers (224.0.0.1) on the local subnet to find out whether any active multicast group members exist on the subnet. Upon rec...
Page 286
1-4 forwarding entry for the member port corresponding to the host from the forwarding table when its aging timer expires. When an igmpv2 or igmpv3 host leaves a multicast group, the host sends an igmp leave message to the multicast router to announce that it has left the multicast group. When the s...
Page 287
1-5 task remarks configuring igmp snooping in a vlan required enable igmp snooping in the vlan and configure the igmp snooping version and querier feature. By default, igmp snooping is disabled in a vlan. Z igmp snooping must be enabled globally before it can be enabled in a vlan. Z when you enable ...
Page 288
1-6 table 1-2 igmp snooping configuration items item description igmp snooping globally enable or disable igmp snooping. Return to igmp snooping configuration task list . Configuring igmp snooping in a vlan select network > igmp snooping in the navigation tree to enter the basic configuration page s...
Page 289
1-7 item description drop unknown enable or disable the function of dropping unknown multicast packets. Unknown multicast data refer to multicast data for which no entries exist in the igmp snooping forwarding table. Z with the function of dropping unknown multicast data enabled, the switch drops al...
Page 290
1-8 table 1-4 configuration items for advanced igmp snooping features item description port select the port on which advanced igmp snooping features are to be configured. The port can be an ethernet port or layer-2 aggregate port. After a port is selected, advanced features configured on this port a...
Page 291
1-9 figure 1-7 details about an igmp snooping multicast entry table 1-5table 1-5table 1-5 describes the igmp snooping multicast entry information. Table 1-5 description of igmp snooping multicast entries item description vlan id id of the vlan to which the entry belongs source address multicast sour...
Page 292
1-10 figure 1-8 network diagram for igmp snooping configuration configuration procedure 1) configure ip addresses configure the ip address for each interface as per figure 1-8 . The detailed configuration steps are omitted. 2) configure router a enable ip multicast routing, enable pim-dm on each int...
Page 293
1-11 figure 1-9 create vlan 100 z type the vlan id 100. Z click apply to complete the operation. Z click the modify port tab to enter the configuration page shown in figure 1-10 ..
Page 294
1-12 figure 1-10 add a port to the vlan z select gigabitethernet 1/0/1, gigabitethernet 1/0/2, and gigabitethernet 1/0/3 in the select ports field. Z select the untagged radio button for select membership type. Z type the vlan id 100. Z click apply to complete the operation. # enable igmp snooping g...
Page 295
1-13 figure 1-11 enable igmp snooping globally z select enable and click apply to globally enable igmp snooping. # in vlan 100, enable igmp snooping and the function of dropping unknown multicast data. Z click the icon corresponding to vlan 100 to enter its configuration page and perform the followi...
Page 296
1-14 figure 1-13 configure igmp snooping on gigabitethernet 1/0/3. Z select gigabitethernet 1/0/3 from the port drop-down list. Z type the vlan id 100. Z select the enable radio buttion for fast leave. Z click apply to complete the operation. Configuration verification # display the igmp snooping mu...
Page 297
1-15 figure 1-14 igmp snooping multicast entry information displaying page z click the icon corresponding to the multicast entry (0.0.0.0, 224.1.1.1) to view details about this entry, as shown in figure 1-15 . Figure 1-15 details about an igmp snooping multicast entry as shown above, gigabitethernet...
Page 298: Table of Contents
I table of contents 1 routing configuration·······························································································································1-1 overview ·····················································································································...
Page 299: Routing Configuration
1-1 1 routing configuration the term “router” in this document refers to a switch supporting routing function. Overview routers are responsible for routing packets on the internet. A router selects an appropriate route according to the destination address of a received packet and forwards the packet...
Page 300
1-2 while configuring a static route, you can specify either the output interface or the next hop address as needed. The nexthop address cannot be a local interface’s ip address; otherwise, the route configuration will not take effect. Actually, it is necessary to identify next hop addresses for all...
Page 301
1-3 field description preference preference value for the ipv4 route the smaller the number, the higher the preference. Next hop nexthop ip address of the ipv4 route interface outgoing interface of the ipv4 route. Packets destined for the specified network segment will be sent out the interface. Cre...
Page 302
1-4 item description preference set a preference value for the static route. The smaller the number, the higher the preference. For example, specifying the same preference for multiple static routes to the same destination enables load sharing on the routes, while specifying different preferences en...
Page 303
1-5 figure 1-4 configure a default route make the following configurations on the page: z type 0.0.0.0 for destination ip address. Z select 0 (0.0.0.0) from the mask drop-down list. Z type 1.1.4.2 for next hop. Z click apply. # configure a static route to switch a and switch c respectively on switch...
Page 304
1-6 figure 1-5 configure a static route make the following configurations on the page: z type 1.1.2.0 for destination ip address. Z select 24 (255.255.255.0) from the mask drop-down list. Z type 1.1.4.1 for next hop. Z click apply. Z type 1.1.3.0 for destination ip address. Z select 24 (255.255.255....
Page 305
1-7 figure 1-6 configure a default route z type 0.0.0.0 for destination ip address. Z select 0 (0.0.0.0) from the mask drop-down list. Z type 1.1.5.5 for next hop. Z click apply. Verify the configuration # display the route table. Enter the ipv4 route page of switch a, switch b, and switch c respect...
Page 306
1-8 approximate round trip times in milli-seconds: minimum = 1ms, maximum = 1ms, average = 1ms precautions when configuring a static route, note the following: 1) if you do not specify the preference when configuring a static route, the default preference will be used. Reconfiguration of the default...
Page 307: Table of Contents
I table of contents 1 dhcp overview··········································································································································1-1 introduction to dhcp ······································································································...
Page 308: Dhcp Overview
1-1 1 dhcp overview after the dhcp client is enabled on an interface, the interface can dynamically obtain an ip address and other configuration parameters from the dhcp server. This facilitates configuration and centralized management. For details about the dhcp client configuration, refer to vlan ...
Page 309
1-2 z manual allocation: the network administrator assigns an ip address to a client like a www server, and dhcp conveys the assigned address to the client. Z automatic allocation: dhcp assigns a permanent ip address to a client. Z dynamic allocation: dhcp assigns an ip address to a client for a lim...
Page 310
1-3 ip address lease extension the ip address dynamically allocated by a dhcp server to a client has a lease. When the lease expires, the dhcp server will reclaim the ip address. If the client wants to use the ip address longer, it has to extend the lease duration. When the half lease duration elaps...
Page 311
1-4 z file: bootfile name and path information, defined by the server to the client. Z options: optional parameters field that is variable in length, which includes the message type, lease, domain name server ip address, and wins ip address. Dhcp options dhcp options overview the dhcp message adopts...
Page 312
1-5 option 82 is the relay agent option in the option field of the dhcp message. It records the location information of the dhcp client. When a dhcp relay agent or dhcp snooping device receives a client’s request, it adds option 82 to the request message before forwarding the message to the server. ...
Page 313
2-1 2 dhcp relay agent configuration introduction to dhcp relay agent application environment since dhcp clients request ip addresses via broadcast messages, the dhcp server and clients must be on the same subnet. Therefore, a dhcp server must be available on each subnet, which is not practical. Dhc...
Page 314
2-2 figure 2-2 dhcp relay agent work process as shown in figure 2-2 , the dhcp relay agent works as follows: 1) after receiving a dhcp-discover or dhcp-request broadcast message from a dhcp client, the dhcp relay agent fills the giaddr field of the message with its ip address and forwards the messag...
Page 315
2-3 task remarks configuring and displaying clients' ip-to-mac bindings optional create a static ip-to-mac binding, and view static and dynamic bindings. The dhcp relay agent can dynamically record clients’ ip-to-mac bindings after clients get ip addresses. It also supports static bindings, that is,...
Page 316
2-4 table 2-1 dhcp service and advanced dhcp relay agent configuration items item description dhcp service enable or disable global dhcp. Unauthorized server detect enable or disable unauthorized dhcp server detection. There are unauthorized dhcp servers on networks, which reply dhcp clients with wr...
Page 317
2-5 table 2-2 dhcp server group configuration items item description server group id type the id of a dhcp server group. You can create up to 20 dhcp server groups. Ip address type the ip address of a server in the dhcp server group. The server ip address cannot be on the same subnet as the ip addre...
Page 318
2-6 configuring and displaying clients' ip-to-mac bindings select network > dhcp from the navigation tree to enter the default dhcp relay page shown in figure 2-3 . In the user information field, click the user information button to view static and dynamic bindings, as shown in figure 2-6 . Click ad...
Page 319
2-7 vlan-interface 2 is 10.1.1.1/24. Vlan-interface 2 is connected to the dhcp server whose ip address is 10.1.1.1/24. The switch forwards messages between dhcp clients and the dhcp server. Figure 2-8 network diagram for dhcp relay agent configuration configuration procedure 1) specify ip addresses ...
Page 320
2-8 figure 2-9 enable dhcp z click on the enable radio button next to dhcp service. Z click apply. # configure a dhcp server group. Z in the server group field, click add and then perform the following operations, as shown in figure 2-10 . Figure 2-10 add a dhcp server group z type 1 for server grou...
Page 321
2-9 z in the interface config field, click the icon of vlan-interface 1, and then perform the following operations, as shown in figure 2-11 . Figure 2-11 enable the dhcp relay agent on an interface and correlate it with a server group z click on the enable radio button next to dhcp relay. Z select 1...
Page 322: Dhcp Snooping Configuration
3-1 3 dhcp snooping configuration z a dhcp snooping enabled device does not work if it is between the dhcp relay agent and dhcp server, and it can work when it is between the dhcp client and relay agent or between the dhcp client and server. Z you are not recommended to enable the dhcp client, bootp...
Page 323
3-2 application environment of trusted ports configuring a trusted port connected to a dhcp server figure 3-1 configure trusted and untrusted ports as shown in figure 3-1 , a dhcp snooping device’s port that is connected to an authorized dhcp server should be configured as a trusted port to forward ...
Page 324
3-3 table 3-1 roles of ports device untrusted port trusted port disabled from recording binding entries trusted port enabled to record binding entries switch a gigabitethernet 1/0/1 gigabitethernet 1/0/3 gigabitethernet 1/0/2 switch b gigabitethernet 1/0/3 and gigabitethernet 1/0/4 gigabitethernet 1...
Page 325
3-4 task remarks displaying clients' ip-to-mac bindings optional display clients' ip-to-mac bindings recorded by dhcp snooping. Enabling dhcp snooping select network > dhcp from the navigation tree, and then click the dhcp snooping tab to enter the page shown in figure 3-3 . You can enable or disabl...
Page 326
3-5 configuring dhcp snooping functions on an interface select network > dhcp from the navigation tree, and then click the dhcp snooping tab to enter the page shown in figure 3-3 . You can view trusted and untrusted ports in the interface config field. Click the icon of a specific interface to enter...
Page 327
3-6 table 3-3 dhcp snooping user information configuration items item description ip address this field displays the ip address assigned by the dhcp server to the client. Mac address this field displays the mac address of the client. Type this field displays the client type, which can be: z dynamic:...
Page 328
3-7 figure 3-7 enable dhcp snooping z click on the enable radio button next to dhcp snooping. # configure dhcp snooping functions on gigabitethernet 1/0/1. Z click the icon of gigabitethernet 1/0/1 on the interface list. Perform the following operations on the dhcp snooping interface configuration p...
Page 329
3-8 figure 3-8 configure dhcp snooping functions on gigabitethernet 1/0/1 z click on the trust radio button next to interface state. Z click apply. # configure dhcp snooping functions on gigabitethernet 1/0/2. Z click the icon of gigabitethernet 1/0/2 on the interface list. Perform the following ope...
Page 330
3-9 z click on the untrust radio button for interface state. Z click on the enable radio button next to option 82 support. Z select replace for option 82 strategy. Z click apply..
Page 331: Table of Contents
I table of contents 1 service management ·································································································································1-1 overview ·····················································································································...
Page 332: Service Management
1-1 1 service management overview the service management module provides six types of services: ftp, telnet, ssh, sftp, http and https. You can enable or disable the services as needed. In this way, the performance and security of the system can be enhanced, thus secure management of the device can ...
Page 333
1-2 z encrypts the data exchanged between the https client and the device to ensure the data security and integrity, thus realizing the security management of the device; z defines certificate attribute-based access control policy for the device to control the access right of the client, in order to...
Page 334
1-3 item description sftp enable sftp service specifies whether to enable the sftp service. The sftp service is disabled by default. When you enable the sftp service, the ssh service must be enabled. Enable http service specifies whether to enable the http service. The http service is enabled by def...
Page 335: Table of Contents
I table of contents 1 diagnostic tools········································································································································1-1 overview ·················································································································...
Page 336: Diagnostic Tools
1-1 1 diagnostic tools overview ping you can use the ping function to check whether a device with a specified address is reachable, and to examine network connectivity. A successful execution of the ping command involves the following steps: 1) the source device sends an icmp echo request (echo-requ...
Page 337
1-2 diagnostic tool operations ping operation the web interface supports the ipv4 ping operations only. Select network > diagnostic tools from the navigation tree to enter the ping configuration page, as shown in figure 1-1 . Figure 1-1 ping configuration page type the ipv4 address of the destinatio...
Page 338
1-3 trace route operation z the web interface supports trace route on ipv4 addresses only. Z before performing the trace route operation on the web interface, on the device execute the commands of ip ttl-expires enable and ip unreachables enable to enable the sending of icmp timeout and destination ...
Page 339: Table of Contents
I table of contents 1 arp management ······································································································································1-1 arp overview·················································································································...
Page 340: Arp Management
1-1 1 arp management arp overview arp function the address resolution protocol (arp) is used to resolve an ip address into an ethernet mac address (or physical address). In an ethernet lan, when a device sends data to another device, it uses arp to translate the ip address of the destination device ...
Page 341
1-2 arp operation suppose that host a and host b are on the same subnet and host a sends a packet to host b, as shown in figure 1-2 . The resolution process is as follows: z host a looks into its arp table to see whether there is an arp entry for host b. If yes, host a uses the mac address in the en...
Page 342
1-3 static arp entry a static arp entry is manually configured and maintained. It cannot get aged or be overwritten by a dynamic arp entry. Using static arp entries enhances communication security. After a static arp entry is specified, only a specific mac address is associated with the specified ip...
Page 343
1-4 creating a static arp entry select network > arp management from the navigation tree to enter the default arp table page shown in figure 1-3 . Click add to enter the new static arp entry page. Select the advanced options checkbox to expand advanced configuration items, as shown in figure 1-4 . F...
Page 344
1-5 figure 1-5 network diagram for configuring static arp entries configuration procedure # create vlan 100. Z select network > vlan from the navigation tree, click the add tab, and then perform the following operations, as shown in figure 1-6 . Figure 1-6 create vlan 100 z type 100 for vlan id. Z c...
Page 345
1-6 figure 1-7 add gigabitethernet 1/0/1 to vlan 100 z select interface gigabitethernet 1/0/1 in the select ports field. Z click on the untagged radio button in the select membership type field. Z type 100 for vlan ids. Z click apply. A configuration progress dialog box appears, as shown in figure 1...
Page 346
1-7 figure 1-9 create vlan-interface 100 z type 100 for vlan id. Z select the configure primary ipv4 address checkbox. Z click on the manual radio botton. Z type 192.168.1.2 for ipv4 address. Z select 24 (255.255.255.0) for mask length. Z click apply to complete the configuration. # create a static ...
Page 347
1-8 z select the advanced options checkbox. Z type 100 for vlan id. Z select gigabitethernet1/0/1 for port. Z click apply to complete the configuration. Gratuitous arp introduction to gratuitous arp in a gratuitous arp packet, the sender ip address and the target ip address are both the ip address o...
Page 348
1-9 table 1-2 gratuitous arp configuration items item description disable gratuitous arp packets learning function enable or disable learning of arp entries according to gratuitous arp packets. Enabled by default. Send gratuitous arp packets when receiving arp requests from another network segment e...
Page 349
2-1 2 arp attack defense configuration although arp is easy to implement, it provides no security mechanism and thus is prone to network attacks. Currently, arp attacks and viruses are threatening lan security. The device can provide multiple features to detect and prevent such attacks. This chapter...
Page 350
2-2 figure 2-1 man-in-the-middle attack switch host a host b ip_a mac_a ip_b mac_b ip_c mac_c host c forged arp reply forged arp reply arp detection mechanism with arp detection enabled for a specific vlan, arp messages arrived on any interface in the vlan are redirected to the cpu to have their mac...
Page 351
2-3 after you enable arp detection based on static ip-to-mac bindings, the device, upon receiving an arp packet from an arp trusted/untrusted port, compares the source ip and mac addresses of the arp packet against the static ip-to-mac bindings. Z if an entry with a matching ip address but a differe...
Page 352
2-4 configuring arp detection if both the arp detection based on specified objects and the arp detection based on static ip-to-mac bindings/dhcp snooping entries/802.1x security entries are enabled, the former one applies first, and then the latter applies. Select network > arp anti-attack from the ...
Page 353
2-5 item description trusted ports select trusted ports. To add ports to the trusted ports list box, select one or multiple ports from the untrusted ports list box and click the button. To remove ports from the trusted ports list box, select one or multiple ports from the list box and click the >> b...
Page 354
2-6 if an entry with a matching ip address but a different mac address is found, the arp packet is considered invalid and discarded. If an entry with both matching ip and mac addresses is found, the arp packet is considered valid and can pass the detection..
Page 355: Table of Contents
I table of contents 1 802.1x ·························································································································································1-1 overview ·········································································································...
Page 356: 802.1X
1-1 1 802.1x overview the 802.1x protocol was proposed by the ieee 802 lan/wan committee for security of wireless lans (wlan).It has been widely used on ethernet as a common port access control mechanism. As a port-based access control protocol, 802.1x authenticates and controls accessing devices at...
Page 357
1-2 z between the device and the radius server, eap protocol packets can be exchanged in two modes: eap relay and eap termination. In eap relay mode, eap packets are encapsulated in eap over radius (eapor) packets on the device, and then relayed by device to the radius server. In eap termination mod...
Page 358
1-3 control direction in the unauthorized state, the controlled port can be set to deny traffic to and from the client or just the traffic from the client. Currently, your device can only be set to deny traffic from the client. Eap over lans eapol frame format eapol, defined in 802.1x, is intended t...
Page 359
1-4 eap packet format an eap-packet-type eapol frame carries an eap packet in its packet body field. The format of the eap packet is shown in figure 1-4 . Figure 1-4 eap packet format code: type of the eap packet, which can be request, response, success, or failure. Z an eap success/failure packet h...
Page 360
1-5 message-authenticator figure 1-7 shows the encapsulation format of the message-authenticator attribute. The message-authenticator attribute is used to prevent access requests from being snooped during eap or chap authentication. It must be included in any packet with the eap-message attribute; o...
Page 361
1-6 figure 1-8 802.1x authentication procedure in eap relay mode eapol eapor eapol-start eap-request / identity eap-response / identity eap-request / md5 challenge eap-success eap-response / md5 challenge radius access-request (eap-response / identity) radius access-challenge (eap-request / md5 chal...
Page 362
1-7 9) when receiving the radius access-request packet, the radius server compares the password information encapsulated in the packet with that generated by itself. If the two are identical, the authentication server considers the user valid and sends to the device a radius access-accept packet. 10...
Page 363
1-8 figure 1-9 802.1x authentication procedure in eap termination mode eapol eapor eapol-start eap-request / identity eap-response / identity eap-request / md5 challenge eap-success eap-response / md5 challenge handshake request ( eap-request / identity ) handshake response ( eap-response / identity...
Page 364
1-9 z server timeout timer: once a device sends a radius access-request packet to the authentication server, it starts this timer. If this timer expires but it receives no response from the server, it retransmits the request. Z handshake timer: after a client passes authentication, the device sends ...
Page 365
1-10 z with a hybrid port, the vlan assignment will fail if you have configured the assigned vlan to carry tags. Z with a hybrid port, you cannot configure an assigned vlan to carry tags after the vlan has been assigned. Acl assignment acls provide a way of controlling access to network resources an...
Page 366
1-11 configuring 802.1x globally from the navigation tree, select authentication > 802.1x to enter the 802.1x configuration page. Click the expansion mark + before advanced todisplay the complete 802.1x configuration page, as shown in figure 1-10 . In the 802.1x configuration area, you can view and ...
Page 367
1-12 item description quiet specify whether to enable the quiet timer. After an 802.1x user fails to be authenticated, the device will keep quiet for a period of time defined by quiet period. During the quiet period, the device will not perform 802.1x authentication on the user. Quiet period specify...
Page 368
1-13 figure 1-11 802.1x configuration on a port table 1-4 lists port 802.1x configuration items. Table 1-4 port 802.1x configuration items item description port select the port to be enabled with 802.1x authentication. Only ports not enabled with 802.1x authentication are available. Port control spe...
Page 369
1-14 configuration examples 802.1x configuration example network requirements as shown in figure 1-12 : z it is required to perform 802.1x authentication on port gigabitethernet 1/0/1 to control user access to the internet, configure the access control method as mac address based on the port, and en...
Page 370
1-15 figure 1-13 global 802.1x configuration perform the following configurations as shown in figure 1-13 . Z select the check box before enable 802.1x. Z select the authentication method as chap. Z click apply to finish the operation. # enable and configure 802.1x on port gigabitethernet 1/0/1. Z i...
Page 371
1-16 # configure the radius authentication servers. Z from the navigation tree, select authentication > radius. The radius server configuration page appears. Figure 1-15 radius authentication server configuration perform the following configurations as shown in figure 1-15 . Z select authentication ...
Page 372
1-17 z enter the secondary server ip address 10.1.1.1. Z select active as the secondary server’s status. Z click apply to finish the operation. # configure the scheme used for communication between the device and the radius servers. Z select the radius setup tab to enter the radius parameter configu...
Page 373
1-18 z from the navigation tree, select authentication > aaa. The domain setup page appears. Perform the following configurations as shown in figure 1-18 . Figure 1-18 create an isp domain z enter test in the domain name textbox. Z select enable to use the domain as the default domain. Z click apply...
Page 374
1-19 z select system from the name drop-down list to use it as the authentication scheme. Z click apply. A configuration progress dialog box appears, as shown in figure 1-20 . Figure 1-20 configuration progress dialog box z after the configuration process is complete, click close. # configure the aa...
Page 375
1-20 figure 1-22 configure the aaa accounting method for the isp domain z select the domain name test. Z select the default accounting checkbox and then select radius as the accounting mode. Z select system from the name drop-down list to use it as the accounting scheme. Z click apply. A configurati...
Page 376
1-21 configuration procedure 1) configure the ip addresses of the interfaces. (omitted) 2) configure the radius scheme system # configure the radius authentication server. Z from the navigation tree, select authentication > radius. The radius server configuration page appears. Figure 1-24 radius aut...
Page 377
1-22 z enter the primary server udp port number 1813. Z select active as the primary server status. Z click apply to finish the operation. # configure the scheme to be used for communication between the switch and the radius servers. Z select the radius setup tab to enter the radius parameter config...
Page 378
1-23 figure 1-27 create an isp domain perform the following configurations, as shown in figure 1-27 . Z enter test in the domain name textbox. Z select enable to use the domain the default domain. Z click apply to finish the operation. # configure the aaa authentication method for the isp domain. Z ...
Page 379
1-24 z select the default authn checkbox and then select radius as the authentication mode. Z select system from the name drop-down list to use it as the authentication scheme. Z click apply. The configuration progress dialog box appears, as shown in figure 1-29 . Figure 1-29 configuration progress ...
Page 380
1-25 figure 1-31 configure the aaa accounting method for the isp domain perform the following configurations, as shown in figure 1-31 . Z select the domain name test. Z select the accounting optional checkbox, and then select enable for this parameter. Z select the default accounting checkbox and th...
Page 381
1-26 z click apply to finish the operation. # configure the acl to deny packets with destination ip address 10.0.0.1. Z select the advanced setup tab. Figure 1-33 acl rule configuration perform the following configurations, as shown in figure 1-33 . Z select 3000 from the select access control list(...
Page 382
1-27 z enter 0.0.0.0 in the destination wildcard text box. Z click add to finish the operation. 5) configure the 802.1x feature # enable the 802.1x feature globally. Z from the navigation tree, select authentication > 802.1x to enter the 802.1x configuration page. Figure 1-34 global 802.1x globally ...
Page 383
1-28 perform the following configurations as shown in figure 1-35 . Z select gigabitethernet1/0/1 from the port list. Z click apply to finish the operation. Configuration verification # after the user passes authentication and gets online, use the ping command to test whether acl 3000 takes effect. ...
Page 384: Table of Contents
I table of contents 1 aaa configuration ····································································································································1-1 overview ···················································································································...
Page 385: Aaa Configuration
1-1 1 aaa configuration overview introduction to aaa authentication, authorization, and accounting (aaa) provides a uniform framework for configuring these three security functions to implement network security management. Aaa usually uses a client/server model, where the client runs on the network ...
Page 386
1-2 configure an authentication server. If network usage information is expected to be recorded, you also need to configure an accounting server. As described above, aaa provides a uniform framework to implement network security management. It is a security mechanism that enables authenticated and a...
Page 387
1-3 table 1-1 aaa configuration task list task remarks configuring an isp domain optional create isp domains and specify one of them as the default isp domain. By default, there is an isp domain named system, which is the default isp domain. Configuring authentication methods for the isp domain opti...
Page 388
1-4 figure 1-2 domain setup page table 1-2 describes the configuration items for creating an isp domain. Table 1-2 isp domain configuration items item description domain name type the isp domain name, which is for identifying the domain. You can type a new domain name to create a domain, or specify ...
Page 389
1-5 figure 1-3 authentication method configuration page table 1-3 describes the configuration items for specifying the authentication methods for an isp domain. Table 1-3 authentication method configuration items item description select an isp domain select the isp domain for which you want to speci...
Page 390
1-6 configuring authorization methods for the isp domain select authentication > aaa from the navigation tree and then select the authorization tab to enter the authorization method configuration page, as shown in figure 1-4 . Figure 1-4 authorization method configuration page table 1-4 describes th...
Page 391
1-7 item description login authz name secondary method name configure the authorization method and secondary authorization method for login users. Options include: z local: performs local authorization. Z none: all users are trusted and authorized. A user gets the corresponding default rights of the...
Page 392
1-8 item description secondary method z none: performs no accounting. Z radius: performs radius accounting. You need to specify the radius scheme to be used. Z not set: restore the default, that is, local accounting. Lan-access accounting name secondary method configure the accounting method and sec...
Page 393
1-9 z select device > users from the navigation tree and then select the create tab to configure a local user as shown in figure 1-7 . Figure 1-7 configure a local user z enter telnet as the username. Z select management as the access level. Z enter abcd as the password. Z enter abcd to confirm the ...
Page 394
1-10 figure 1-8 configure isp domain test z enter test as the domain name. Z click apply. # configure the isp domain to use local authentication. Z select authentication > aaa from the navigation tree and then select the authentication tab and configure aaa authentication as shown in figure 1-9 . Fi...
Page 395
1-11 figure 1-10 configuration progress dialog box z after the configuration process is complete, click close. # configure the isp domain to use local authorization. Z select authentication > aaa from the navigation tree and then select the authorization tab and configure aaa authorization as shown ...
Page 396
1-12 figure 1-12 configure the isp domain to use local accounting z select the domain test. Z select the login accounting check box and select the accounting method local. Z click apply. A configuration progress dialog box appears. Z after the configuration process is complete, click close. Now, if ...
Page 397: Table of Contents
I table of contents 1 radius ·······················································································································································1-1 overview ···········································································································...
Page 398: Radius
1-1 1 radius overview remote authentication dial-in user service (radius) is protocol for implementing authentication, authorization, and accounting (aaa). For details about aaa, refer to aaa configuration. Introduction to radius radius is a distributed information interaction protocol using the cli...
Page 399
1-2 security and authentication mechanisms information exchanged between a radius client and the radius server is authenticated with a shared key, which is never transmitted over the network. This enhances the information exchange security. In addition, to prevent user passwords from being intercept...
Page 400
1-3 8) the radius server returns a stop-accounting response (accounting-response) and stops accounting for the user. 9) the user stops access to network resources. Radius packet format radius uses udp to transmit messages. It ensures the smooth message exchange between the radius server and the clie...
Page 401
1-4 2) the identifier field (1-byte long) is for matching request packets and response packets and detecting retransmitted request packets. The request and response packets of the same type have the same identifier. 3) the length field (2-byte long) indicates the length of the entire packet, includi...
Page 402
1-5 no. Attribute no. Attribute 21 (unassigned) 68 acct-tunnel-connection 22 framed-route 69 tunnel-password 23 framed-ipx-network 70 arap-password 24 state 71 arap-features 25 class 72 arap-zone-access 26 vendor-specific 73 arap-security 27 session-timeout 74 arap-security-data 28 idle-timeout 75 p...
Page 403
1-6 z vendor-id (four bytes): indicates the id of the vendor. Its most significant byte is 0 and the other three bytes contain a code complying with rfc 1700. Z vendor-type: indicates the type of the sub-attribute. Z vendor-length: indicates the length of the sub-attribute. Z vendor-data: indicates ...
Page 404
1-7 table 1-3 radius configuration task list task description configuring radius authentication servers required configure the information related to the primary and secondary radius authentication servers. By default, no radius authentication server is configured. Configuring radius accounting serv...
Page 405
1-8 table 1-4 radius server configuration item description server type specify the type of the server to be configured, which can be authentication server and accounting sever. Primary server ip specify the ip address of the primary server. If no primary server is specified, the text box displays 0....
Page 406
1-9 figure 1-6 radius parameter configuration table 1-5 lists the radius parameters. Table 1-5 radius parameters item description server type specify the type of the radius server supported by the device, including: z extended: specifies an extended radius server (usually an imc server). That is, th...
Page 407
1-10 item description timeout retransmission times set the maximum number of transmission attempts. The product of the timeout value and the number of retransmission attempts cannot exceed 75. Realtime-accounting interval set the real-time accounting interval, whose value must be n times 3 (n is an ...
Page 408
1-11 table 1-6 relationship between the real-time accounting interval and the number of users number of users real-time accounting interval (in minutes) 1 to 99 3 100 to 499 6 500 to 999 12 ú 1000 ú 15 return to radius configuration task list . Radius configuration example network requirements as sh...
Page 409
1-12 figure 1-8 configure the radius authentication server perform the following configurations, as shown in figure 1-8 . Z select authentication server as the server type. Z enter 10.110.91.146 as the ip address of the primary authentication server z enter 1812 as the udp port of the primary authen...
Page 410
1-13 figure 1-10 configure radius parameters z select extended as the server type. Z select the authentication server shared key check box and enter expert in the text box. Z enter expert in the confirm authentication shared key text box. Z select the accounting server shared key check box and enter...
Page 411
1-14 figure 1-11 create an isp domain perform the following configurations, as shown in figure 1-11 . Z enter test in the domain name textbox. Z select enable to use the domain as the default domain. Z click apply. # configure the aaa authentication method for the isp domain. Z select the authentica...
Page 412
1-15 figure 1-13 configuration progress dialog box z after the configuration process is complete, click close. # configure the aaa authorization method for the isp domain. Z select the authorization tab. Figure 1-14 configure the aaa authorization method for the isp domain perform the following conf...
Page 413
1-16 figure 1-15 configure the aaa accounting method for the isp domain perform the following configurations, as shown in figure 1-15 . Z select the domain name test. Z select the accounting optional checkbox and then select enable. Z select the default accounting checkbox and then select radius as ...
Page 414: Table of Contents
I table of contents 1 users ···························································································································································1-1 overview ········································································································...
Page 415: Users
1-1 1 users overview this module allows you to configure local users and user groups. Local user a local user represents a set of user attributes configured on a device (such as the user password, service type, and authorization attribute), and is uniquely identified by the username. For a user requ...
Page 416
1-2 figure 1-2 local user configuration page table 1-1 describes the configuration items for configuring a local user. Table 1-1 local user configuration items item description username specify a name for the local user. Password confirm specify and confirm the password of the local user. The settin...
Page 417
1-3 item description level select an authorization level for the local user, which can be visitor, monitor, configure, or management, in ascending order of priority. Vlan specify the vlan to be authorized to the local user after the user passes authentication. Acl specify the acl to be used by the a...
Page 418
1-4 table 1-2 user group configuration items item description group-name specify a name for the user group. Level select an authorization level for the user group, which can be visitor, monitor, configure, or management, in ascending order of priority. Vlan specify the vlan to be authorized to users...
Page 419: Table of Contents
I table of contents 1 pki configuration ······································································································································1-1 pki overview ·············································································································...
Page 420: Pki Configuration
1-1 1 pki configuration pki overview the public key infrastructure (pki) is a hierarchical framework designed for providing information security through public key technologies and digital certificates and verifying the identities of the digital certificate owners. Pki employs digital certificates, ...
Page 421
1-2 architecture of pki a pki system consists of entities, a ca, a registration authority (ra) and a pki repository, as shown in figure 1-1 . Figure 1-1 pki architecture entity an entity is an end user of pki products or services, such as a person, an organization, a device like a router or a switch...
Page 422
1-3 vpn a virtual private network (vpn) is a private data communication network built on the public communication infrastructure. A vpn can leverage network layer security protocols (for instance, ipsec) in conjunction with pki-based encryption and digital signature technologies to achieve confident...
Page 423
1-4 table 1-1 configuration task list for requesting a certificate manually task remarks creating a pki entity required create a pki entity and configure the identity information. A certificate is the binding of a public key and an entity, where an entity is the collection of the identity informatio...
Page 424
1-5 task remarks requesting a local certificate required when requesting a certificate, an entity introduces itself to the ca by providing its identity information and public key, which will be the major components of the certificate. A certificate request can be submitted to a ca in two ways: onlin...
Page 425
1-6 task remarks retrieving a certificate optional retrieve an existing certificate. Retrieving and displaying a crl optional retrieve a crl and display its contents. Creating a pki entity select authentication > pki from the navigation tree. The pki entity list page is displayed by default, as show...
Page 426
1-7 item description ip address type the ip address of the entity. Fqdn type the fully qualified domain name (fqdn) for the entity. An fqdn is a unique identifier of an entity on the network. It consists of a host name and a domain name and can be resolved to an ip address. For example, www.Whatever...
Page 427
1-8 figure 1-5 pki domain configuration page table 1-4 describes the configuration items for creating a pki domain. Table 1-4 pki domain configuration items item description domain name type the name for the pki domain. Ca identifier type the identifier of the trusted ca. An entity requests a certif...
Page 428
1-9 item description requesting url type the url of the ra. The entity will submit the certificate request to the server at this url through the scep protocol. The scep protocol is intended for communication between an entity and an authentication authority. In offline mode, this item is optional; w...
Page 429
1-10 item description crl url type the url of the crl distribution point. This item is available when the enable crl checking check box is selected. Note that when the url of the crl distribution point is not set, you should acquire the ca certificate and a local certificate, and then acquire a crl ...
Page 430
1-11 table 1-5 configuration item for generating an rsa key pair item description key length type the length of the rsa keys. Return to configuration task list for requesting a certificate manually . Destroying the rsa key pair select authentication > pki from the navigation tree, and then select th...
Page 431
1-12 table 1-6 configuration items for retrieving a pki certificate item description domain name select the pki domain for the certificate. Certificate type select the type of the certificate to be retrieved, which can be ca or local. Enable offline mode select this check box to retrieve a certifica...
Page 432
1-13 return to configuration task list for requesting a certificate automatically . Requesting a local certificate select authentication > pki from the navigation tree, and then select the certificate tab to enter the page displaying existing pki certificates, as shown in figure 1-6 . Click request ...
Page 433
1-14 retrieving and displaying a crl select authentication > pki from the navigation tree, and then select the crl tab to enter the page displaying crls, as shown in figure 1-13 . Figure 1-13 crl page z click retrieve crl to retrieve the crl of a domain. Z then, click view crl for the domain to disp...
Page 434
1-15 field description keyid pubic key identifier a ca may have multiple key pairs, and this field identifies which key pair is used for the crl signature. Return to configuration task list for requesting a certificate manually . Return to configuration task list for requesting a certificate automat...
Page 435
1-16 after the above configuration, make sure that the system clock of the switch is synchronous to that of the ca, so that the switch can request certificates and retrieve crls properly. 2) configure switch # create a pki entity. Z select authentication > pki from the navigation tree. The pki entit...
Page 436
1-17 figure 1-18 pki domain list figure 1-19 configure a pki domain z type torsa as the pki domain name. Z type myca as the ca identifier. Z select aaa as the local entity. Z select ca as the authority for certificate request. Z type http://4.4.4.133:446/c95e970f632d27be5e8cbf80e971d9c4a9a93337 as t...
Page 437
1-18 z select the certificate tab, and then click create key, as shown in figure 1-20 , and perform the configuration as shown in figure 1-21 . Figure 1-20 certificate list figure 1-21 generate an rsa key pair z click apply to generate an rsa key pair. # retrieve the ca certificate. Z select the cer...
Page 438
1-19 figure 1-23 retrieve the ca certificate z select torsa as the pki domain. Z select ca as the certificate type. Z click apply. # request a local certificate. Z select the certificate tab, and then click request cert, as shown in figure 1-24 , and then perform the following configurations as show...
Page 439
1-20 # retrieve the crl. Z after retrieving a local certificate, select the crl tab. Z click retrieve crl of the pki domain of torsa, as shown in figure 1-26 . Figure 1-26 retrieve the crl configuration guidelines when configuring pki, note that: 1) make sure the clocks of entities and the ca are sy...
Page 440: Table of Contents
I table of contents 1 port isolation group configuration ·········································································································1-1 overview ·····························································································································...
Page 441
1-1 1 port isolation group configuration overview usually, layer 2 traffic isolation is achieved by assigning ports to different vlans. To save vlan resources, port isolation is introduced to isolate ports within a vlan, allowing for great flexibility and security. Currently: z 3com switch 2900 seri...
Page 442
1-2 table 1-1 port isolation group configuration items item description config type specify the role of the port or ports in the isolation group. Z isolate port: assign the port or ports to the isolation group as an isolated port or ports. Z uplink-port: assign the port to the isolation group as the...
Page 443
1-3 figure 1-3 configure isolated ports for an isolation group z select isolate port for the port type. Z select gigabitethernet 1/0/2, gigabitethernet 1/0/3, and gigabitethernet 1/0/4 on the chassis front panel. Z click apply. A configuration progress dialog box appears. Z after the configuration p...
Page 444: Table of Contents
I table of contents 1 authorized ip configuration·····················································································································1-1 overview ·························································································································...
Page 445: Authorized Ip Configuration
1-1 1 authorized ip configuration overview the authorized ip function is to associate the http or telnet service with an acl to filter the requests of clients. Only the clients that pass the acl filtering can access the device. Configuring authorized ip select security > authorized ip from the navig...
Page 446
1-2 authorized ip configuration example authorized ip configuration example network requirements in figure 1-2 , configure switch to deny telnet and http requests from host a , while permit telnet and http requests from host b. Figure 1-2 network diagram for authorized ip configuration procedure # c...
Page 447
1-3 figure 1-4 configure an acl rule to permit host b make the following configurations on the page: z select 2001 from the select access control list (acl) drop-down list. Z select permit from the operation drop-down list. Z select the source ip address check box and then type 10.1.1.3. Z type 0.0....
Page 448
1-4 figure 1-5 configure authorized ip make the following configurations on the page: z select 2001 for ipv4 acl in the telnet field. Z select 2001 for ipv4 acl in the web(http) field. Z click apply..
Page 449: Table of Contents
I table of contents 1 acl configuration·····································································································································1-1 acl overview ···············································································································...
Page 450: Acl Configuration
1-1 1 acl configuration acl overview with the growth of network scale and network traffic, network security and bandwidth allocation become more and more critical to network management. Packet filtering can be used to efficiently prevent illegal access to networks and to control network traffic and ...
Page 451
1-2 table 1-2 depth-first match for ipv4 acls ipv4 acl category depth-first match procedure basic ipv4 acl 1) sort rules by source ip address wildcard mask and compare packets against the rule configured with more zeros in the source ip address wildcard mask. 2) in case of a tie, compare packets aga...
Page 452
1-3 acl step currently, the web interface does not support acl step configuration. Meaning of the step the step defines the difference between two neighboring numbers that are automatically assigned to acl rules by the device. For example, with a step of 5, rules are automatically numbered 0, 5, 10,...
Page 453
1-4 configuring a time range select qos > time range from the navigation tree and then select the create tab to enter the time range configuration page, as shown in figure 1-1 . Figure 1-1 the page for creating a time range table 1-4 describes the configuration items for creating a time range. Table...
Page 454
1-5 return to ipv4 acl configuration task list . Creating an ipv4 acl select qos > acl ipv4 from the navigation tree and then select the create tab to enter the ipv4 acl configuration page, as shown in figure 1-2 . Figure 1-2 the page for creating an ipv4 acl table 1-5 describes the configuration it...
Page 455
1-6 figure 1-3 the page for configuring an basic ipv4 acl table 1-6 describes the configuration items for creating a rule for a basic ipv4 acl. Table 1-6 configuration items for a basic ipv4 acl rule item description select access control list (acl) select the basic ipv4 acl for which you want to co...
Page 456
1-7 item description time range select the time range during which the rule takes effect. Available time ranges are those that have been configured. Return to ipv4 acl configuration task list . Configuring a rule for an advanced ipv4 acl select qos > acl ipv4 from the navigation tree and then select...
Page 457
1-8 table 1-7 describes the configuration items for creating a rule for an advanced ipv4 acl. Table 1-7 configuration items for an advanced ipv4 acl rule item description select access control list (acl) select the advanced ipv4 acl for which you want to configure rules. Available acls are advanced ...
Page 458
1-9 item description check established select this option to make the rule match packets used for establishing and maintaining tcp connections. These items are available only when you select 6 tcp from the protocol drop-down box. Operator port source to port operator port tcp/udp port destination to...
Page 459
1-10 figure 1-5 the page for configuring a rule for an ethernet frame header acl table 1-8 describes the configuration items for creating a rule for an ethernet frame header ipv4 acl. Table 1-8 configuration items for an ethernet frame header ipv4 acl rule item description select access control list...
Page 460
1-11 item description protocol type type filter protocol mask select the protocol type option and specify the link layer protocol type by configuring the following two items: z protocol type : indicates the frame type. It corresponds to the type-code field of ethernet_ii and ethernet_snap frames. Z ...
Page 461: Qos Configuration
2-1 2 qos configuration introduction to qos quality of service (qos) reflects the ability of a network to meet customer needs. In an internet, qos evaluates the ability of the network to forward packets of different services. The evaluation can be based on different criteria because the network may ...
Page 462
2-2 causes congestion easily occurs in complex packet switching circumstances in the internet. The following figure shows two common cases: figure 2-1 traffic congestion causes 100m>10m ( 100m+10m+50m)>100m 100m 100m 100m 50m 10m 10m ( 1) ( 2) z the traffic enters a device from a high speed link and...
Page 463
2-3 end-to-end qos figure 2-2 end-to-end qos model as shown in figure 2-2 , traffic classification, traffic policing, traffic shaping, congestion management, and congestion avoidance are the foundations for a network to provide differentiated services. Mainly they implement the following functions: ...
Page 464
2-4 network can either adopt the classification results from its upstream network or classify the packets again according to its own criteria. To provide differentiated services, traffic classes must be associated with certain traffic control actions or resource allocation actions. What traffic cont...
Page 465
2-5 z expedited forwarding (ef) class: in this class, packets are forwarded regardless of link share of other traffic. The class is suitable for preferential services requiring low delay, low packet loss, low jitter, and high bandwidth. Z assured forwarding (af) class: this class is divided into fou...
Page 466
2-6 figure 2-4 an ethernet frame with an 802.1q tag header as shown in figure 2-4 , the 4-byte 802.1q tag header consists of the tag protocol identifier (tpid, two bytes in length), whose value is 0x8100, and the tag control information (tci, two bytes in length). Figure 2-5 presents the format of t...
Page 467
2-7 sp queuing sp queuing is specially designed for mission-critical applications, which require preferential service to reduce response delay when congestion occurs. Figure 2-6 schematic diagram for sp queuing a typical switch provides eight queues per port. As shown in figure 2-6 , sp queuing clas...
Page 468
2-8 figure 2-7 schematic diagram for wrr queuing a typical switch provides eight output queues per port. Wrr assigns each queue a weight value (represented by w7, w6, w5, w4, w3, w2, w1, or w0) to decide the proportion of resources assigned to the queue. On a 100 mbps port, you can set the weight va...
Page 469
2-9 figure 2-8 evaluate traffic with the token bucket token bucket packets dropped packet classification packets to be sent through this interface packets sent tokens are put into the bucket at the set rate the evaluation for the traffic specification is based on whether the number of tokens in the ...
Page 470
2-10 figure 2-9 line rate implementation with a token bucket used for traffic control, when there are tokens in the token bucket, the bursty packets can be transmitted; if no tokens are available, packets cannot be transmitted until new tokens are generated in the token bucket. In this way, the traf...
Page 471
2-11 figure 2-10 priority mapping process introduction to priority mapping tables the device provides various types of priority mapping table, as listed below: z cos to dscp : 802.1p-precedence-to-dscp mapping table. Z cos to queue : 802.1p-precedence-to-local-precedence mapping table. Z dscp to cos...
Page 472
2-12 input dscp value local precedence (queue) cos 48 to 55 6 6 56 to 63 7 7 in the default dscp to dscp mapping table, an input value yields a target value equal to it. Qos configuration configuration task lists configuring a qos policy a qos policy involves three components: class, traffic behavio...
Page 473
2-13 task remarks creating a traffic behavior required create a traffic behavior. Configuring traffic mirroring and traffic redirecting for a traffic behavior configure a traffic behavior configuring actions for a behavior configuring other actions for a traffic behavior use either approach configur...
Page 474
2-14 table 2-9 priority mapping table configuration task list task remarks configuring priority mapping tables required set priority mapping tables. Configuring priority trust mode perform the task in table 2-10 to configure priority trust mode: table 2-10 priority trust mode configuration task list...
Page 475
2-15 table 2-11 configuration items of creating a class item description classifier name specify a name for the classifier to be created. Operator specify the logical relationship between rules of the classifier. Z and : specifies the relationship between the rules in a class as logic and. That is, ...
Page 476
2-16 table 2-12 shows the configuration items of configuring classification rules. Table 2-12 configuration items of configuring classification rules item description please select a classifier select an existing classifier in the drop-down list. Any define a rule to match all packets. Select the op...
Page 477
2-17 item description service vlan define a rule to match service vlan ids. If multiple such rules are configured for a class, the new configuration does not overwrite the previous one. You can configure multiple vlan ids each time. If the same vlan id is specified multiple times, the system conside...
Page 478
2-18 table 2-13 configuration items of creating a behavior item description behavior name specify a name for the behavior to be created. Return to qos policy configuration task list . Configuring traffic mirroring and traffic redirecting for a traffic behavior select qos > behavior from the navigati...
Page 479
2-19 configuring other actions for a traffic behavior select qos > behavior from the navigation tree and click setup to enter the page for setting a traffic behavior, as shown in figure 2-15 . Figure 2-15 the page for setting a traffic behavior table 2-15 describes the configuration items of configu...
Page 480
2-20 table 2-15 configuration items of configuring other actions for a traffic behavior item description please select a behavior select an existing behavior in the drop-down list. Filter configure the packet filtering action. After selecting the filter option, select one item in the following drop-...
Page 481
2-21 figure 2-17 the page for setting a policy table 2-17 describes the configuration items of configuring classifier-behavior associations for the policy. Table 2-17 configuration items of configuring classifier-behavior associations for the policy item description please select a policy select a c...
Page 482
2-22 figure 2-18 the page for applying a policy to a port table 2-18 describes the configuration items of applying a policy to a port. Table 2-18 configuration items of applying a policy to a port item description please select a policy select a created policy in the drop-down list. Direction set th...
Page 483
2-23 table 2-19 describes the configuration items of configuring queue scheduling on a port. Table 2-19 configuration items of configuring queue scheduling on a port item description wrr enable or disable the wrr queue scheduling mechanism on selected ports. Two options are available: z enable : ena...
Page 484
2-24 figure 2-20 the page for configuring line rate on a port table 2-20 describes the configuration items of configuring line rate on a port. Table 2-20 configuration items of configuring line rate on a port item description please select an interface type select the types of interfaces to be confi...
Page 485
2-25 figure 2-21 the page for configuring priority mapping tables table 2-18 describes the configuration items of configuring priority mapping tables. Table 2-21 configuration items of configuring priority mapping tables item description mapping type select the priority mapping table to be configure...
Page 486
2-26 figure 2-23 the page for configuring port priority figure 2-24 the page for modifying port priority table 2-22 describes the port priority configuration items. Table 2-22 port priority configuration items item description interface the interface to be configured. Priority set a local precedence...
Page 487
2-27 return to priority trust mode configuration task list . Configuration guidelines when configuring qos, note that: when an acl is referenced to implement qos, the actions defined in the acl rules, deny or permit, do not take effect; actions to be taken on packets matching the acl depend on the t...
Page 488
3-1 3 acl/qos configuration examples acl/qos configuration example network requirements as shown in figure 3-1 , in the network, the ftp server at ip address 10.1.1.1/24 is connected to the switch, and the clients access the ftp server through gigabitethernet 1/0/1 of the switch. Configure an acl an...
Page 489
3-2 figure 3-2 define a time range covering 8:00 to 18:00 every day z type the time range name test-time. Z select the periodic time range option, set the start time to 8:00 and the end time to 18:00, and then select the checkboxes sun through sat. Z click apply. 2) define an ipv4 acl for traffic to...
Page 490
3-3 figure 3-3 create an advanced ipv4 acl z type the acl number 3000. Z click apply. # define an acl rule for traffic to the ftp server. Z click advance setup. Perform configuration as shown in figure 3-4 ..
Page 491
3-4 figure 3-4 define an acl rule for traffic to the ftp server z select acl 3000 in the drop-down list. Z select the rule id option, and type rule id 2. Z select permit in the operation drop-down list. Z select the destination ip address option, and type ip address 10.1.1.1 and destination wildcard...
Page 492
3-5 z select qos > classifier from the navigation tree and click create. Perform configuration as shown in figure 3-5 . Figure 3-5 create a class z type the class name class1. Z click create. # define classification rules. Z click setup. Perform configuration as shown in figure 3-6 ..
Page 493
3-6 figure 3-6 define classification rules z select the class name class1 in the drop-down list. Z select the acl ipv4 option, and select acl 3000 in the following drop-down list. Z click apply. A configuration progress dialog box appears, as shown in figure 3-7 ..
Page 494
3-7 figure 3-7 configuration progress dialog box z after the configuration is complete, click close on the dialog box. # create a traffic behavior. Z select qos > behavior from the navigation tree and click create. Perform configuration as shown in figure 3-8 . Figure 3-8 create a traffic behavior z...
Page 495
3-8 figure 3-9 configure actions for the behavior z select behavior1 in the drop-down list. Z select the filter option, and then select deny in the following drop-down list. Z click apply. A configuration progress dialog box appears. Z after the configuration is complete, click close on the dialog b...
Page 496
3-9 figure 3-10 create a policy z type the policy name policy1. Z click create. # configure classifier-behavior associations for the policy. Z click setup. Perform configuration as shown in figure 3-11 . Figure 3-11 configure classifier-behavior associations for the policy z select policy1. Z select...
Page 497
3-10 figure 3-12 apply the qos policy in the inbound direction of gigabitethernet 1/0/1 z select policy1 in the please select a policy drop-down list. Z select inbound in the direction drop-down list. Z select port gigabitethernet 1/0/1. Z click apply. A configuration progress dialog box appears. Z ...
Page 498: Table of Contents
I table of contents 1 poe configuration ·····································································································································1-1 poe overview ··············································································································...
Page 499: Poe Configuration
1-1 1 poe configuration poe overview power over ethernet (poe) means that power sourcing equipment (pse) supplies power to powered devices (pds) from ethernet interfaces through twisted pair cables. Advantages z reliable: power is supplied in a centralized way so that it is very convenient to provid...
Page 500
1-2 3com baseline switch 2920-sfp plus is a single pse device, as so .This manual introduces the device with a single pse only. A pse can examine the ethernet cables connected to poe interfaces, search for pds, classify them, and supply power to them. When detecting that a pd is unplugged, the pse s...
Page 501
1-3 configuring poe ports select poe > poe from the navigation tree and click the setup tab, as shown in figure 1-2 . Figure 1-2 setup page table 1-1 describes the poe port configuration items. Table 1-1 poe port configuration items item description select port click to select ports to be configured...
Page 502
1-4 item description power priority set the power supply priority for a poe port. The priority levels of a poe port include low, high, and critical in ascending order. Z when the poe power is insufficient, power is first supplied to poe ports with a higher priority level. Z when the pse power is ove...
Page 503
1-5 figure 1-3 poe summary poe configuration example network requirements z as shown in figure 1-4 , gigabitethernet 1/0/1 and gigabitethernet 1/0/2 are connected to ip telephones. Z gigabitethernet 1/0/11 is connected to ap whose maximum power does not exceed 9000 milliwatts. Z the power supply pri...
Page 504
1-6 configuration procedure # enable poe on gigabitethernet 1/0/1 and gigabitethernet 1/0/2, and configure their power supply priority to critical. Z select poe > poe from the navigation tree and click the setup tab to perform the following configurations, as shown in figure 1-5 . Figure 1-5 configu...
Page 505
1-7 figure 1-6 configure the poe port supplying power to ap z click to select port gigabitethernet 1/0/11 from the chassis front panel. Z select enable from the power state drop-down list. Z select the check box before power max and type 9000. Z click apply. After the configuration takes effect, the...