- DL manuals
- 3Com
- Switch
- 3848 - SuperStack 3 Switch
- Implementation Manual
3Com 3848 - SuperStack 3 Switch Implementation Manual
Summary of 3848 - SuperStack 3 Switch
Page 1
Http://www.3com.Com/ part no. Dua1740-0baa02 published september 2004 superstack ® 3 switch 3812, switch 3824 and switch 3848 implementation guide 3c17401 3c17400 3cr17402-91.
Page 2
3com corporation 350 campus drive marlborough, ma usa 01752-3064 copyright © 2004, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without writt...
Page 3: Ontents
C ontents a bout t his g uide conventions 11 related documentation 12 documentation comments 13 1 s witch f eatures o verview what is management software? 15 switch features explained 16 aggregated links 16 auto-negotiation 16 configuration save and restore 17 multicast filtering 18 rapid spanning t...
Page 4
Aggregated links and your switch 27 aggregated link — manual configuration example 29 jumbo frames 30 implementing jumbo frames 30 jumbo frames — simple network example 30 3 u sing m ulticast f iltering what is an ip multicast? 33 benefits of multicast 34 multicast filtering 34 multicast filtering a...
Page 5: Lan
6 u sing t raffic m anagement what is traffic prioritization? 51 traffic prioritization and your switch 52 how traffic prioritization works 53 802.1d traffic classification 54 diffserv traffic classification 55 ip port traffic classification 56 traffic queues 56 limiting the rate of a port 57 traffi...
Page 6: Ip A
Server support 73 event log entries and traps 73 10 m aking y our n etwork s ecure securing access to the web interface 75 getting a digital certificate 76 securing access to the command line interface 76 access control lists 77 how access control list rules work 77 port security 78 what is network ...
Page 7
G lossary i ndex.
Page 9: Bout
A bout t his g uide this guide describes the features of the following switches: ■ 3com ® superstack ® 3 switch 3812 (3c17401) ■ 3com ® superstack ® 3 switch 3824 (3c17400) ■ 3com ® superstack ® 3 switch 3848 (3cr17402-91) it outlines how to use these features to optimize the performance of your net...
Page 10
10 a bout t his g uide most user guides and release notes are available in adobe acrobat reader portable document format (pdf) or html on the 3com world wide web site: http://www.3com.Com/.
Page 11
Conventions 11 conventions table 1 and table 2 list conventions that are used throughout this guide. Table 1 notice icons icon notice type description information note information that describes important features or instructions caution information that alerts you to potential loss of data or poten...
Page 12
12 a bout t his g uide related documentation in addition to this guide, each switch documentation set includes the following: ■ superstack 3 switch 3812, switch 3824, and switch 3848 getting started guide this guide contains: ■ all the information you need to install and set up the switch in its def...
Page 13
Documentation comments 13 documentation comments your suggestions are very important to us. They will help make our documentation more useful to you. Please e-mail comments about this document to 3com at: pddtechpubs_comments@3com.Com please include the following information when contacting us: ■ do...
Page 14
14 a bout t his g uide.
Page 15: Witch
1 s witch f eatures o verview this chapter contains introductory information about the switch management software and supported features. It covers the following topics: ■ what is management software? ■ switch features explained for detailed descriptions of the web interface operations and the comma...
Page 16
16 c hapter 1: s witch f eatures o verview switch features explained the management software provides you with the capability to change the default state of some of the switch features. This section provides a brief overview of these features — their applications are explained in more detail later i...
Page 17
Switch features explained 17 flow control is supported on ports operating in half duplex mode, and is implemented using the ieee std 802.3-2002 (incorporating 802.3x) on ports operating in full duplex mode. For more information about auto-negotiation and port capabilities, see chapter 2 “optimizing ...
Page 18
18 c hapter 1: s witch f eatures o verview parameters such as vlans and fast start may be set up as required. Other combinations of port settings, however, are not recommended as configuration restore will only perform a “best effort” restore of the configuration. For example, lacp automatic aggrega...
Page 19
Switch features explained 19 rstp allows you to implement alternative paths for network traffic in the event of path failure and uses a loop-detection process to: ■ discover the efficiency of each path. ■ enable the most efficient path. ■ disable the less efficient paths. ■ enable one of the less ef...
Page 20
20 c hapter 1: s witch f eatures o verview rmon remote monitoring (rmon) is an industry standard feature for traffic monitoring and collecting network statistics. The switch software continually collects statistics about the lan segments connected to the switch. If you have a management workstation ...
Page 21
Switch features explained 21 port security your switch supports the following port security modes, which you can set for an individual port or a range of ports: ■ no security port security is disabled and all network traffic is forwarded through the port without any restrictions. ■ learning off all ...
Page 22
22 c hapter 1: s witch f eatures o verview.
Page 23: Ptimizing
2 o ptimizing b andwidth there are many ways you can optimize the bandwidth on your network and improve network performance. If you utilize certain switch features you can provide the following benefits to your network and end users: ■ increased bandwidth ■ quicker connections ■ faster transfer of d...
Page 24
24 c hapter 2: o ptimizing b andwidth to communicate effectively, both devices at either end of a link must use the same duplex mode. If the devices at either end of a link support auto-negotiation, this is done automatically. If the devices at either end of a link do not support auto-negotiation, b...
Page 25
Aggregated links 25 ports at both ends of the link should be set to auto-negotiate. Aggregated links aggregated links are connections that allow devices to communicate using two member links in parallel. Aggregated links provide the following benefits: ■ they can potentially increase the bandwidth o...
Page 26
26 c hapter 2: o ptimizing b andwidth if a member link in an aggregated link fails, the traffic using that link is dynamically reassigned to the remaining member links in the aggregated link. Figure 2 shows the simplest case: two member links, that is the physical links, form an aggregated link. In ...
Page 27
Aggregated links 27 implementing 802.3ad aggregated links lacp can be enabled or disabled on a per port basis. You can implement 802.3ad aggregated links in two ways: ■ manual aggregations — you can manually add and remove ports to and from an aggregated link via web commands. However, if a port has...
Page 28
28 c hapter 2: o ptimizing b andwidth when using an aggregated link, note that: ■ to gather statistics about an aggregated link, you must add together the statistics for each port in the aggregated link. ■ if you wish to disable a single member link of an aggregated link, you must first physically r...
Page 29
Aggregated links 29 if the link state on any of the ports in an aggregated link becomes inactive due to link failure, then the switch will automatically redirect the aggregated link traffic to the remaining ports. Aggregated links therefore provide built-in resilience for your network. The switch al...
Page 30
30 c hapter 2: o ptimizing b andwidth 3 connect port 5 on the core switch to port 47. 4 connect port 7 on the core switch to port 48. Jumbo frames on a standard ethernet network, the maximum size of a frame is 1518 bytes (1522 bytes if the frame is vlan tagged); 1500 bytes for data and 18 bytes as h...
Page 31
Jumbo frames 31 figure 4 simple network with jumbo frames to create the network shown in figure 4 1 connect the servers to a jumbo frames compliant switch. In this example a switch 3812 has been used. 2 turn on the jumbo frames support for this switch. 3 configure the servers connected to the switch...
Page 32
32 c hapter 2: o ptimizing b andwidth.
Page 33: Sing
3 u sing m ulticast f iltering multicast filtering improves the performance of networks that carry multicast traffic. This chapter explains multicasts, multicast filtering, and how multicast filtering can be implemented on your switch. It covers the following topics: ■ what is an ip multicast? ■ mul...
Page 34
34 c hapter 3: u sing m ulticast f iltering a multicast packet is identified by the presence of a multicast group address in the destination address field of the packet’s ip header. Benefits of multicast the benefits of using ip multicast are that it: ■ enables the simultaneous delivery of informati...
Page 35
Multicast filtering 35 figure 5 the effect of multicast filtering multicast filtering and your switch your switch provides automatic multicast filtering support using igmp (internet group management protocol) snooping. It also supports igmp query mode. Snooping mode snooping mode allows your switch ...
Page 36
36 c hapter 3: u sing m ulticast f iltering igmp multicast filtering igmp is the system that all ip-supporting network devices use to register endstations with multicast groups. It can be used on all lans and vlans that contain a multicast capable ip router and on other network devices that support ...
Page 37
How igmp supports ip multicast 37 how igmp supports ip multicast igmp provides a way for routers and switches to learn where group members exist on a network, and thus provides a critical function in the ip multicast packet delivery process. Electing the querier on each subnetwork or broadcast domai...
Page 38
38 c hapter 3: u sing m ulticast f iltering join message rather than wait for a query, a host can also send an igmp report on its own initiative to inform the querier that it wants to begin receiving a transmission for a specific group (perhaps by clicking a go or start button on the client interfac...
Page 39: Sing
4 u sing r esilience f eatures setting up resilience on your network helps protect critical links against failure, protects against network loops, and reduces network downtime to a minimum. The switch provides resilient links using the rapid spanning tree protocol (rstp). The protocol configures its...
Page 40
40 c hapter 4: u sing r esilience f eatures rapid spanning tree protocol the rapid spanning tree protocol makes your network more resilient to link failure and also provides a protection from loops — one of the major causes of broadcast storms. Rstp is enabled by default on your switch. To be fully ...
Page 41
What is stp? 41 ■ it is possible for some ports on a switch to operate in rstp (802.1w) mode, and other ports, for example those connected to a legacy switch, to operate in stp (802.1d) mode. ■ you have an option to force your switch to use the legacy 802.1d version of spanning tree, if required. Wh...
Page 42
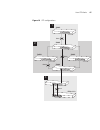
42 c hapter 4: u sing r esilience f eatures figure 7 traffic flowing through bridges c and a if a link failure is detected, as shown in figure 8 , the stp process reconfigures the network so that traffic from lan segment 2 flows through bridge b. Figure 8 traffic flowing through bridge b stp determi...
Page 43
How stp works 43 how stp works when enabled, stp determines the most appropriate path for traffic through a network. It does this as outlined in the sections below. Stp requirements before it can configure the network, the stp system requires: ■ communication between all the bridges. This communicat...
Page 44
44 c hapter 4: u sing r esilience f eatures ■ the identity of the port on each bridge that is to be the root port. The root port is the one that is connected to the root bridge using the most efficient path, that is, the one that has the lowest root path cost. Note that the root bridge does not have...
Page 45
How stp works 45 how rstp differs to stp rstp works in a similar way to stp, but it includes additional information in the bpdus. This information allows each bridge to confirm that it has taken action to prevent loops from forming when it wants to enable a link to a neighbouring bridge. This allows...
Page 46
46 c hapter 4: u sing r esilience f eatures ■ because bridge a is the root bridge, it is also the designated bridge for lan segment 1. Port 1 on bridge a is therefore selected as the designated bridge port for lan segment 1. ■ port 1 of bridges b, c, x and y have been defined as root ports because t...
Page 47
How stp works 47 figure 10 stp configurations 1 2 3 10mbps hub block block block block switch switch switch switch switch.
Page 48
48 c hapter 4: u sing r esilience f eatures using stp on a network with multiple vlans the ieee std 802.1d, 1998 edition does not take into account vlans when it calculates stp information — the calculations are only performed on the basis of physical connections. For this reason, some network confi...
Page 49: Sing
5 u sing the s witch d atabase what is the switch database? The switch database is used by the switch to determine where a packet should be forwarded to, and which port should transmit the packet if it is to be forwarded. The database contains a list of entries — each entry contains three items: ■ m...
Page 50
50 c hapter 5: u sing the s witch d atabase switch database entry states databases entries can have three states: ■ learned — the switch has placed the entry into the switch database when a packet was received from an endstation. Note that: ■ learned entries are removed (aged out) from the switch da...
Page 51: Sing
6 u sing t raffic m anagement using the traffic management capabilities of your switch allows your network traffic to be controlled and prioritized to ensure that high priority data is transmitted with minimum delay. Your switch has two features that allow you to manage the traffic on your network: ...
Page 52
52 c hapter 6: u sing t raffic m anagement ■ financial applications — used by accounts departments that need immediate access to large files and spreadsheets. ■ cad/cam design applications — used by design departments that need priority connections to server farms and other devices for transferring ...
Page 53
How traffic prioritization works 53 the 3com network supervisor application supplied on the cd-rom accompanying your switch is the main tool for configuring qos, and 3com recommends that you use this application to configure qos. You can also configure qos via the command line interface (cli), for a...
Page 54
54 c hapter 6: u sing t raffic m anagement ■ 802.1d (classification is done at layer 2 of the osi model). ■ diffserv code point (classification is done at layer 3 of the osi model). ■ ip port (classification is done at layer 4 of the osi model). These methods can be used together. If a packet is pri...
Page 55
How traffic prioritization works 55 figure 12 ieee 802.1d traffic types figure 12 illustrates ieee 802.1d traffic types as well as associated priority levels and how they are mapped to the eight supported traffic queues. Diffserv traffic classification diffserv is an alternative method of classifyin...
Page 56
56 c hapter 6: u sing t raffic m anagement figure 13 dscp service level mapping figure 13 illustrates how diffserv code point (dscp) service levels are mapped to the eight traffic queues. Ip port traffic classification the switch supports classification of traffic from legacy devices by classifying ...
Page 57
Limiting the rate of a port 57 the switch uses the following queuing mechanisms: ■ weighted round robin (wrr) — this method services all the traffic queues, giving priority to the higher priority queues. Under most circumstances, this method gives high priority precedence over low-priority, but in t...
Page 58
58 c hapter 6: u sing t raffic m anagement traffic prioritization and rate limiting are best used together if the egress rate rather than the ingress rate is limited on a port; the traffic rate leaving the switch is limited rather than the traffic arriving at the switch. This ensures that the traffi...
Page 59: Tatus
7 s tatus m onitoring and s tatistics this chapter contains details of the remote monitoring ( rmon ) feature that assists you with status monitoring and statistics. For detailed descriptions of the web interface operations and the command line interface (cli) commands that you require to manage the...
Page 60
60 c hapter 7: s tatus m onitoring and s tatistics the rmon groups the ietf define groups of ethernet rmon statistics. This section describes the four groups supported by the switch, and details how you can use them. Statistics the statistics group provides traffic and error statistics showing packe...
Page 61
Benefits of rmon 61 benefits of rmon using the rmon features of your switch has three main advantages: ■ it improves your efficiency using rmon allows you to remain at one workstation and collect information from widely dispersed lan segments or vlans. This means that the time taken to reach a probl...
Page 62
62 c hapter 7: s tatus m onitoring and s tatistics when using the rmon features of the switch, note the following: ■ the greater the number of rmon sessions, the greater the burden on the management resources of the switch. If you have many rmon sessions, the forwarding performance of the switch is ...
Page 63: Etting
8 s etting u p v irtual lan s setting up virtual lans (vlans) on your switch increases the efficiency of your network by dividing the lan into logical, rather than physical, segments which are easier to manage. This chapter explains more about the concept of vlans and explains how they can be implem...
Page 64
64 c hapter 8: s etting u p v irtual lan s figure 14 a network setup showing three vlans benefits of vlans the main benefit of vlans is that they provide a network segmentation system that is far more flexible than any traditional network. Using vlans also provides you with three other benefits: ■ v...
Page 65
Vlans and your switch 65 ■ vlans help to control traffic with traditional networks, congestion can be caused by broadcast traffic that is directed to all network devices whether they require it or not. Vlans increase the efficiency of your network because each vlan can be set up to contain only thos...
Page 66
66 c hapter 8: s etting u p v irtual lan s communication between vlans if the devices placed in a vlan need to communicate to devices in a different vlan, a router or layer 3 switching device with connections to both vlans needs to be installed. Communication between vlans can only take place if the...
Page 67
Vlan configuration examples 67 the ieee std 802.1q-1998 defines how vlans operate within an open packet-switched network. An 802.1q compliant packet carries additional information that allows a switch to determine to which vlan the port belongs. If a frame is carrying the additional information, it ...
Page 68
68 c hapter 8: s etting u p v irtual lan s figure 16 vlan configuration example: using untagged connections to set up the configuration shown in figure 16 : 1 configure the vlans define vlan 2 on the switch. Vlan 1 is the default vlan and already exists. 2 add ports to the vlans add ports 10, 11 and...
Page 69
Vlan configuration examples 69 figure 17 vlan configuration example: 802.1q tagged connections to set up the configuration shown in figure 17 : 1 configure the vlans on switch 1 define vlan 2. Vlan 1 is the default vlan and already exists. 2 add endstation ports on switch 1 to the vlans place the en...
Page 70
70 c hapter 8: s etting u p v irtual lan s 7 check the vlan membership for both switches the relevant ports should be listed in the vlan members summary. 8 connect the switches connect port 12 on switch 1 to port 11 on switch 2. The vlans are now configured and operational and the endstations in bot...
Page 71: Sing
9 u sing a utomatic ip c onfiguration this chapter explains more about ip addresses and how the automatic configuration option works. It covers the following topics: ■ how your switch obtains ip information ■ how automatic ip configuration works ■ important considerations for detailed information on...
Page 72
72 c hapter 9: u sing a utomatic ip c onfiguration how your switch obtains ip information your switch has two ways to obtain its ip address information: ■ automatic ip configuration (default) — the switch attempts to configure itself by communicating with a dhcp server on the network. ■ manual ip co...
Page 73
Important considerations 73 important considerations this section contains some important points to note when using the automatic ip configuration feature. The dynamic nature of automatically configured ip information means that a switch may change its ip address whilst in use. Server support your s...
Page 74
74 c hapter 9: u sing a utomatic ip c onfiguration.
Page 75: Aking
10 m aking y our n etwork s ecure this chapter outlines the port security and switch management login features, explains the key benefits of using these features, and gives examples of how and why you would use them in your network. For detailed descriptions of the web interface operations and the c...
Page 76
76 c hapter 10: m aking y our n etwork s ecure once you have set up your switch to support https, you can optionally stop unencrypted administration by redirecting http accesses (port 80) to port 443 (the port used by https). The switch can be configured to redirect all attempts to administer the we...
Page 77
Access control lists 77 access control lists access control lists are a set of instructions that can be applied to filter traffic on vlans. They can be used to limit access to certain segments of the network and therefore, are useful for network security. Access control lists can be used to: ■ preve...
Page 78
78 c hapter 10: m aking y our n etwork s ecure as a result of the above rule, the packet matches the parameters of the rule and will be blocked. A destination mask of 0.0.0.0 will match all packets. Port security your switch supports the following port security modes, which you can set for an indivi...
Page 79
What is network login? 79 remote radius server in the network for authentication. This information must be successfully authenticated and authorized before the client device is granted access to the network. For further information about radius, see “what is radius?” on page 83 . The client device m...
Page 80
80 c hapter 10: m aking y our n etwork s ecure figure 18 network login operation when the client device and radius server have exchanged authentication information, the switch receives either an authentication succeeded or failed message from the server, and then configures the port to forward or fi...
Page 81
What is switch management login? 81 ■ network login is not supported on ports configured to operate as members of an aggregated link. ■ network login is not supported on ports configured to operate as members of a resilient link. ■ some client devices that are connected to the switch port may not su...
Page 82
82 c hapter 10: m aking y our n etwork s ecure benefits of radius authentication day-to-day network maintenance can become a substantial overhead. For example, regularly changing the administrative password on a manageable network device is a commonplace security measure. If the local switch databas...
Page 83
What is radius? 83 important considerations this section contains some important considerations when using radius authentication of switch management login on the switch. ■ before you enable radius authentication you must ensure that: ■ the switch is configured with a static ip address. ■ radius has...
Page 84
84 c hapter 10: m aking y our n etwork s ecure.
Page 85: Onfiguration
A c onfiguration r ules configuration rules for gigabit ethernet gigabit ethernet is designed to run over several media: ■ single-mode fiber optic cable, with connections up to 5 km (3.1 miles). ■ multimode fiber optic cable, with connections up to 550 m (1804 ft). ■ category 5 cabling, with connect...
Page 86
86 a ppendix a: c onfiguration r ules configuration rules for fast ethernet the topology rules for 100 mbps fast ethernet are slightly different to those for 10 mbps ethernet. Figure 20 illustrates the key topology rules and provides examples of how they allow for large-scale fast ethernet networks....
Page 87
Configuration rules for fast ethernet 87 ■ a total network span of 325 m (1066 ft) is allowed in single-repeater topologies (one hub stack per wiring closet with a fiber link to the collapsed backbone). For example, a 225 m (738 ft) fiber link from a repeater to a router or switch, plus a 100 m (328...
Page 88
88 a ppendix a: c onfiguration r ules.
Page 89: Etwork
B n etwork c onfiguration e xamples this chapter contains the following section: ■ simple network configuration examples ■ desktop switch example.
Page 90
90 a ppendix b: n etwork c onfiguration e xamples simple network configuration examples the following illustrations show some simple examples of how the switch 3812, switch 3824, or switch 3848 can be used in your network. Desktop switch example the example in figure 21 shows how a switch 3848 and a...
Page 91: Ip A
C ip a ddressing this chapter provides some background detail on the ip information that needs to be assigned to your switch to enable you to manage it across a network. The topics covered are: ■ ip addresses ■ subnets and subnet masks ■ default gateways ip addressing is a vast topic and there are w...
Page 92
92 a ppendix c: ip a ddressing if your network is internal to your organization only, you may use any arbitrary ip address. 3com suggests you use addresses in the series 192.168.100.X (where x is a number between 1 and 254) with a subnet mask 255.255.255.0. These suggested ip addresses are part of a...
Page 93
Ip addresses 93 dotted decimal notation the actual ip address is a 32-bit number that is stored in binary format. These 32 bits are segmented into 4 groups of 8 bits — each group is referred to as a field or an octet. Decimal notation converts the value of each field into a decimal number, and the f...
Page 94
94 a ppendix c: ip a ddressing subnets and subnet masks you can divide your ip network into sub-networks also known as subnets. Support for subnets is important because the number of bits assigned to the device part of an ip address limits the number of devices that may be addressed on any given net...
Page 95
Subnets and subnet masks 95 as shown in this example, the 32 bits of an ip address and subnet mask are usually written using an integer shorthand. This notation translates four consecutive 8-bit groups (octets) into four integers that range from 0 through 255. The subnet mask in the example is writt...
Page 96
96 a ppendix c: ip a ddressing the subnet mask 255.255.255.255 is reserved as the default broadcast address. Default gateways a gateway is a device on your network which is used to forward ip packets to a remote destination. An alternative name for a gateway is a router. “remote” refers to a destina...
Page 97: Lossary
G lossary 3com network supervisor the 3com network management application used to manage 3com’s networking solutions. 10base-t the ieee specification for 10 mbps ethernet over category 3, 4 or 5 twisted pair cable. 100base-fx the ieee specification for 100 mbps fast ethernet over fiber-optic cable. ...
Page 98
98 g lossary fast ethernet is 100 mbps, and the bandwidth of gigabit ethernet is 1000 mbps. Baud the signalling rate of a line, that is, the number of transitions (voltage or frequency changes) made per second. Also known as line speed. Bridge a device that interconnects two lans of a different type...
Page 99
99 digital certificate digital certificates are blocks of data that are used to identify users and systems and encrypt their data. Digital certificates used by ssl adhere to the x.509 standard. Dns domain name system. This system maps a numerical internet protocol (ip) address to a more meaningful a...
Page 100
100 g lossary half duplex a system that allows packets to transmitted and received, but not at the same time. Contrast with full duplex. Hub a device that regenerates lan traffic so that the transmission distance of that signal can be extended. Hubs are similar to repeaters, in that they connect lan...
Page 101
101 igmp snooping a mechanism performed by an intermediate device, such as a layer 2 switch, that optimizes the flow of multicast traffic. The device listens for igmp messages and build mapping tables and associated forwarding filters, in addition to reducing the igmp protocol traffic. Internet grou...
Page 102
102 g lossary llc logical link control. A sublayer of the ieee data link layer that is located above the mac sublayer. The llc sublayer is responsible for mac sublayer addressing, flow control, error control, and framing. Latency the delay between the time a device receives a packet and the time the...
Page 103
103 nic network interface card. A circuit board installed in an endstation that allows it to be connected to a network. Post power on self test. An internal test that a switch carries out when it is powered-up. Protocol a set of rules for communication between devices on a network. The rules dictate...
Page 104
104 g lossary server a computer in a network that is shared by multiple endstations. Servers provide endstations with access to shared network services such as computer files and printer queues. Smtp simple mail transfer protocol. An ietf standard protocol used for transferring mail across a network...
Page 105
105 interconnection of networks. Originally a unix standard, tcp/ip is now supported on almost all platforms, and is the protocol of the internet. Tcp relates to the content of the data travelling through a network — ensuring that the information sent arrives in one piece when it reaches its destina...
Page 106
106 g lossary.
Page 107: Ndex
I ndex 107 i ndex numbers 802.1d priority levels 54 traffic classification 54 a access control lists 77 addresses classes 93 ip 91 aggregated links 16, 25 aging time, definition 50 alarm events 62 alarms (rmon group) 60, 61 automatic ip configuration 72 auto-negotiation 16, 24 b backup 17 bandwidth ...
Page 108
108 i ndex ip multicast addressing 33 ip routing address classes 93 j jumbo frames 30 l learned sdb entries 50 m mac (media access control) addresses ip address 92 manual configuration 72 masks subnet 94 matrix (rmon group) 61 max age 44 multicast filtering 33 igmp 36 multicasts, description 33 n ne...
Page 109
I ndex 109 subnet mask 94 sub-networks. See subnets switch database 49 switch management login 75 t topology rules for fast ethernet 86 topology rules with full duplex 87 traffic classification 802.1d 54 traffic prioritization 19, 51 802.1d 54 queues 56 v vlans 63 benefits 64 default 65 defining the...
Page 110
110 i ndex.