- DL manuals
- 3Com
- Switch
- 3CBLSG48
- User Manual
3Com 3CBLSG48 User Manual
Summary of 3CBLSG48
Page 1
3com ® baseline switch 2948-sfp plus user guide 3cblsg48 www.3com.Com part number 10016089 rev. Aa published july 2007 10016089-aa front_matter.Fm page 1 tuesday, july 3, 2007 3:51 pm.
Page 2
3com corporation 350 campus drive marlborough, ma 01752-3064 copyright © 2007, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written p...
Page 3: Bout
A bout t his g uide this section provides an overview to the user guide. The user guide provides the following sections: getting started — provides introductory information about the switch 2948 and how they can be used in your network. It covers summaries of hardware and software features. Using th...
Page 4
Aggregating ports — provides information for configuring link aggregation which optimizes port usage by linking a group of ports together to form a single lag. Configuring vlans — provides information for configuring vlans. Vlans are logical subgroups with a local area network (lan) which combine us...
Page 5
This guide is intended for network administrators familiar with it concepts and terminology. Conventions table 1 lists conventions that are used throughout this guide. Table 1 notice icons if release notes are shipped with your product and the information there differs from the information in this g...
Page 6: Ontents
C ontents 1 g etting s tarted about the switch 2948 ....................................................................... 2 front panel detail ............................................................................... 3 led status indicators ......................................................
Page 7: Iewing
3 v iewing b asic s ettings viewing device settings .................................................................... 36 viewing color keys ........................................................................... 38 4 m anaging d evice s ecurity configuring system access .........................
Page 8: Configuringvlans
Viewing lacp ................................................................................. 103 defining lacp priority ..................................................................... 104 defining lacp port ......................................................................... 105 8 confi...
Page 9: 10 C
10 c onfiguring i gmp s nooping& q uery introduction .................................................................................... 132 defining igmp snooping & query ................................................... 132 11 c onfiguring s panning t ree viewing spanning tree ....................
Page 10: Anaging
14 m anaging s ystem f iles configuration file structure ............................................................. 170 backing up system files .................................................................. 171 restoring files .....................................................................
Page 11: In-
C p in- o uts console cable ................................................................................ 193 null modem cable ......................................................................... 194 pc-at serial cable ............................................................................
Page 12: Etting
G etting s tarted 1 this chapter contains introductory information about the 3com® baseline switch 2948-sfp plus and how they can be used in your net- work. It covers summaries of the hardware and software features, and the following topics: about the switch 2948 front panel detail led status indica...
Page 13
C hapter 1 : g etting s tarted the switch 2948 is a gigabit ethernet switching product that delivers flexible three-speed performance (10/100/1000) and advanced voice- optimized features such as auto-qos and auto-voice vlan. This makes the switch ideal for medium businesses and small enterprises see...
Page 14
C hapter 1 : g etting s tarted table 1 hardware features (continued) feature switch 948 flow control in full duplex operation, all ports are supported. The switch 2948 ports are capable of receiving, but not sending pause frames. Traffic prioritization supported (using the ieee std 802.Id, 1998 edit...
Page 15
C hapter 1 : g etting s tarted 4 the 2948-sfp plus 48-port ethernet switches provide led indicators on the front panel for your convenience to monitor the switch. Table 2 describes the meanings of the led. Led status indicators table description on the leds of the switch 2948 led label status descri...
Page 16
C hapter 1 : g etting s tarted table 3 contains the system specifications of the switch 2948. Table system specifications of the switch 2948 switch system specifications specification switch 948-sfp plus 48-port cblsg48 physical dimensions 44×440×265 mm (1.73 x 1.7.3 x 10.43 in.) (h×w×d) weight 2.0 ...
Page 17
C hapter 1 : g etting s tarted this section contains information that you need to install and set up your 3com switch. Warning: safety information. Before you install or remove any components from the switch or carry out any maintenance procedures, you must read the 3com switch family safety and reg...
Page 18
C hapter 1 : g etting s tarted setting up for management to make full use of the features offered by your switch, and to change and monitor the way it works, you have to access the management software that resides on the switch. This is known as managing the switch. Managing the switch can help you ...
Page 19
C hapter 1 : g etting s tarted 8 to manage your switch you can use one of the following methods: web interface management snmp management in addition, you can use the command line interface through the console port for basic operations of the switch including setting and viewing the ip address, conf...
Page 20
C hapter 1 : g etting s tarted 9 you can manage a switch using any network management workstation running the simple network management protocol (snmp) as shown in figure 3. For example, you can use the 3com network director software, available from the 3com website. Figure snmp management over the ...
Page 21
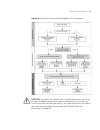
C hapter 1 : g etting s tarted 10 switch setup overview this section gives an overview of what you need to do to get your switch set up and ready for management when it is in its default state. The whole setup process is summarized in figure 4. Detailed procedural steps are contained in the sections...
Page 22
C hapter 1 : g etting s tarted 11 caution: to protect your switch from unauthorized access, you must change the default password as soon as possible, even if you do not intend to actively manage your switch. For more information on default users and changing default passwords, see “default users and...
Page 23
C hapter 1 : g etting s tarted 1 ip configuration the switch’s ip configuration is determined automatically using dhcp, or manually using values you assign. Automatic ip configuration using dhcp by default the switch tries to configure its ip information without requesting user intervention. It trie...
Page 24
C hapter 1 : g etting s tarted 1 if you use the automatic ip configuration method, you need to discover the automatically allocated ip information before you can begin management. Work through the “viewing ip information using the console port” on page 17. Manual ip configuration when you configure ...
Page 25
C hapter 1 : g etting s tarted 14 using the command line interface (cli) connecting to the console port you can access the switch through the console port to manually set the ip address, or to view the ip address that was assigned automati- cally (for example, by a dhcp server). For more information...
Page 26
C hapter 1 : g etting s tarted 1 connecting the workstation to the switch 1 connect the workstation to the console port using the console cable as shown in figure 5. Figure connecting a workstation to the switch using the console port workstation to connect the cable: a attach the cable’s rj-45 conn...
Page 27
C hapter 1 : g etting s tarted 1 manually set the ip address using the console port you are now ready to manually set up the switch with ip information us- ing the command line interface. You need to have the following information: ip address subnet mask default gateway 1 connect to the switch conso...
Page 28
C hapter 1 : g etting s tarted 1 viewing ip information using the console port this section describes how to view the automatically allocated ip infor- mation using the command line interface. The automatic ip configura- tion process usually completes within one minute after the switch is connected ...
Page 29
C hapter 1 : g etting s tarted 18 setting up web interface management this section describes how you can set up the web interface manage- ment over the network. Prerequisites ensure that you have already set up the switch with ip information as described in “methods of managing a switch” on page 8. ...
Page 30
C hapter 1 : g etting s tarted 19 web management over the network to manage a switch using the web interface over an ip network: 1 be sure that you know your switch’s ip address. See “ip configura- tion” on page 12, and “viewing ip information using the console port” on page 17. Check that your mana...
Page 31
C hapter 1 : g etting s tarted 0 default users and passwords upgrading software using the cli if you intend to manage the switch or to change the default pass- words, you must log in with a valid user name and password. The switch has one default user name. The default user is listed in table 5. Tab...
Page 32: Using The Com Web Interface
Using the com web interface this section provides an introduction to the user interface, and includes the following topics: starting the 3com web interface understanding the 3com web interface saving the configuration resetting the device restoring factory defaults logging off the device this sectio...
Page 33
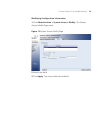
C hapter 2 : u sing t he 3 com w eb i nterface this section contains information on starting the 3com web interface. To access the 3com user interface: 1 open an internet browser. Enter the device ip address in the address bar and press enter. The enter network password page opens: figure enter netw...
Page 34
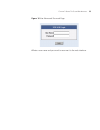
C hapter 2 : u sing t he 3 com w eb i nterface figure 3com web interface home page understanding the com web interface the 3com web interface home page contains the following views: tab view — provides the device summary configuration located at the top of the home page. Tree view — provides easy na...
Page 35
C hapter 2 : u sing t he 3 com w eb i nterface 4 figure 8 web interface components the following table lists the user interface components with their corresponding numbers: table interface components view description 1 tree view tree view provides easy navigation through the configurable device feat...
Page 36
C hapter 2 : u sing t he 3 com w eb i nterface this section provides the following additional information: device representation — provides an explanation of the user inter face buttons, including both management buttons and task icons. Using the web interface management buttons — provides instructi...
Page 37
C hapter 2 : u sing t he 3 com w eb i nterface configuration management buttons and icons provide an easy method of configuring device information: table 3com web interface configuration buttons using the web interface management buttons button button name description create creates configuration en...
Page 38
C hapter 2 : u sing t he 3 com w eb i nterface 3com contains screens and tables for configuring devices. This section contains the following topics: viewing configuration information adding configuration information modifying configuration information removing configuration information viewing confi...
Page 39
C hapter 2 : u sing t he 3 com w eb i nterface 8 adding configuration information the ip setup page enables you to add user-defined information to specific 3com web interface pages. For example, to configure ip setup: 1 click administration > ip setup. The ip setup page opens. Figure 11 ip setup pag...
Page 40
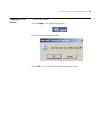
C hapter 2 : u sing t he 3 com w eb i nterface 9 modifying configuration information 1 click administration > system access > modify. The system access modify page opens. Figure 1 system access modify page modify the fields. Click apply. The access fields are modified..
Page 41
C hapter 2 : u sing t he 3 com w eb i nterface 0 removing configuration information 1 click administration > system access > remove. The system ac- cess remove page opens. Figure 1 system access remove page select the user account to be deleted. Click remove. The user account is deleted, and the dev...
Page 42
C hapter 2 : u sing t he 3 com w eb i nterface 1 saving the configuration configuration changes are only saved to the device once the user saves the changes to the flash memory. The save configuration tab allows the latest configuration to be saved to the flash memory. To save the device configurati...
Page 43
C hapter 2 : u sing t he 3 com w eb i nterface resetting the device the reset page enables resetting the device from a remote location. To prevent the current configuration from being lost, use the save con- figuration page to save all user-defined changes to the flash memory before resetting the de...
Page 44
C hapter 2 : u sing t he 3 com w eb i nterface figure 1 user name and password page 4 enter a user name and password to reconnect to the web interface..
Page 45
C hapter 2 : u sing t he 3 com w eb i nterface 4 restoring factory defaults the restore option appears on the reset page. The restore option restores the device to its factory default settings. To restore the device: 1 click administration > reset. The reset page opens. Figure 1 reset page the reset...
Page 46
C hapter 2 : u sing t he 3 com w eb i nterface logging off the device to log off the device: 1 click logout. The logout page opens. The following message appears: click ok. The 3com web interface home page closes..
Page 47: Viewing Basic Settings
Viewing basic settings this section contains information about viewing basic settings available from the web interface home page, including the device summary page and the color keys page. The device summary page displays general information, including the system name, location, and contact, the sys...
Page 48
C hapter 3: v iewing b asic s ettings product description — displays the device model number and name. System name — defines the user-defined device name. The field range is 0-160 characters. System location — defines the location where the system is currently running. The field range is 0-160 chara...
Page 49
C hapter 3: v iewing b asic s ettings 8 the color key page provides information about the rj45 or sfp port status. To view color keys: 1 click device summary > color key. The color key page opens. Figure 19 color key page viewing color keys the color key page contains the following fields: rj4 — dis...
Page 50
C hapter 3: v iewing b asic s ettings 9 table 9 describes the color and the port status: table 9 color key definitions color port status white unconnected. No link detected. Yellow lower speed on 10/100/1000m port. Green maximum speed 10/100/1000m rj45 or rj45 sfp. Indicates that a link was detected...
Page 51: Managing Device Security
Managing device security 4 the management security section provides information for configuring system access, defining radius authentication, port-based authentication and defining access control lists. This section includes the following topics: configuring system access defining radius clients de...
Page 52
C hapter 4: m anaging d evice s ecurity 41 network administrators can define users, passwords, and access levels for users using the system access interface. The multi-session web fea- ture is enabled on device and allows 10 users to be created and access the switch concurrently. Access levels provi...
Page 53
C hapter 4: m anaging d evice s ecurity 4 the system access summary page displays the current users and access levels defined on the device. To view system access settings: 1 click administration > system access > summary. The system access summary page opens. Figure 0 system access summary page vie...
Page 54
C hapter 4: m anaging d evice s ecurity 4 the system access setup page allows network administrators to define users, passwords, and access levels for users using the system access interface. Monitor users have no access to this page. 1 click administration > system access > setup. The system access...
Page 55
C hapter 4: m anaging d evice s ecurity 44 modifying system access the system access modify page allows network administrators to modify users, passwords, and access levels using the system access interface. Monitor users have no access to this page. 1 click administration > system access > modify. ...
Page 56
C hapter 4: m anaging d evice s ecurity 4 removing system access the system access remove page allows network administrators to remove users from the system access interface. Monitor users have no access to this page. To remove users: 1 click administration > system access > remove. The system acces...
Page 57
C hapter 4: m anaging d evice s ecurity 4 defining radius clients remote authorization dial-in user service (radius) servers provide additional security for networks. Radius servers provide a centralized authentication method for 802.1x. The default parameters are user-defined, and are applied to ne...
Page 58
C hapter 4: m anaging d evice s ecurity 4 authentication port — identifies the authentication port. The authentication port is used to verify the radius server authentication. The authenticated port default is 1812. Number of retries — defines the number of transmitted requests sent to the radius se...
Page 59
C hapter 4: m anaging d evice s ecurity 48 defining port-based authentication (80.1x) port-based authentication authenticates users on a per-port basis via an external server. Only authenticated and approved system users can transmit and receive data. Ports are authenticated via the radius server us...
Page 60
C hapter 4: m anaging d evice s ecurity 49 viewing 80.1x authentication the 802.1x summary page allows the network administrator to view port-based authentication settings. To view port-based authentication: 1 click security > 80.1x > summary. The 802.1x summary page opens. Figure 802.1x summary pag...
Page 61
C hapter 4: m anaging d evice s ecurity 0 defining 80.1x authentication reauthentication period — displays the time span (in seconds) in which the selected port is reauthenticated. The field default is 3600 seconds. Authenticator state — displays the current authenticator state. Termination cause — ...
Page 62
C hapter 4: m anaging d evice s ecurity 1 the 802.1x setup page contains the following fields: 80.1x global settings port based authentication state — indicates if port authentication is enabled on the device. The possible field values are: enabled — enables port-based authentication on the device. ...
Page 63
C hapter 4: m anaging d evice s ecurity 80.1x port settings admin port control — displays the admin port authorization state. Auto — enables port based authentication on the device. The interface moves between an authorized or unauthorized state based on the authentication exchange between the devic...
Page 64
C hapter 4: m anaging d evice s ecurity defining access control lists access control lists (acl) allow network managers to define classifi- cation actions and rules for specific ingress ports. Packets entering an ingress port, with an active acl are either admitted or denied entry. If they are denie...
Page 65
C hapter 4: m anaging d evice s ecurity 4 viewing mac based acls the mac based acl summary page displays information regarding mac based acls configured on the device. Ports are reactivated from the interface configuration page. To view mac based acls: 1 click device > acl > mac based acl > summary....
Page 66
C hapter 4: m anaging d evice s ecurity the mac based acl summary page contains the following fields: acl name — contains a list of the mac-based acls. Priority — indicates the rule priority, which determines which rule is matched to a packet on a first match basis. Source address — indicates the so...
Page 67
C hapter 4: m anaging d evice s ecurity configuring mac based acls the mac based acl setup page allows the network administrator to select, create, and define rules for mac-based access control lists. Monitor users have no access to this page. 1 click device > acl > mac based acl > setup. The mac ba...
Page 68
C hapter 4: m anaging d evice s ecurity source mask — indicates the source mac address wildcard mask.Wildcards are used to mask all or part of a source mac address. Wildcard masks specify which bits are used and which are ignored. A wildcard mask of ff:ff:ff:ff:ff:ff indicates that no bit is importa...
Page 69
C hapter 4: m anaging d evice s ecurity 8 vlan id — matches the packet’s vlan id to the ace. The possible field values are 1 to 4094. Cos — classifies traffic based on the cos tag value. Cos mask — defines the cos mask used to classify network traffic. Ethertype — provides an identifier that differe...
Page 70
C hapter 4: m anaging d evice s ecurity 9 modifying mac based acls the mac based acl modify page allows the network administrator to modify mac based acls settings. Monitor users have no access to this page. 1 click device > acl > mac based acl > modify. The mac based acl modify page opens. Figure 9...
Page 71
C hapter 4: m anaging d evice s ecurity 0 mask of ff:ff:ff:ff:ff:ff indicates that no bit is important. A wildcard of 00.00.00.00.00.00.00 indicates that all bits are important. For example, if the source mac address is e0:3b:4a:c2: ca:e2 and the wildcard mask is 00:00:00:00:00:ff, the first five by...
Page 72
C hapter 4: m anaging d evice s ecurity 1 removing mac based acls the mac based acl remove page allows the user to remove mac based acls. Monitor users have no access to this page. To remove mac based acls: 1 click device > acl > mac based acl > remove. The mac based acl remove page opens. Figure 0 ...
Page 73
C hapter 4: m anaging d evice s ecurity source address — matches the source mac address to which packets are addressed to the ace. Source mask — indicates the source mac address wildcard mask.Wildcards are used to mask all or part of a source mac address. Wildcard masks specify which bits are used a...
Page 74
C hapter 4: m anaging d evice s ecurity vlan id — matches the packet’s vlan id to the ace. The possible field values are 1 to 4094. Cos — classifies class of service of the packet. Cos mask — defines the wildcard bits to be applied to the cos. Ethertype — provides an identifier that differentiates a...
Page 75
C hapter 4: m anaging d evice s ecurity 4 viewing ip based acls the ip based acl summary page displays information regarding ip based acls configured on the device. To view ip based acls: 1 click device > acl > ip based acl > summary. The ip based acl summary page opens. Figure 1 ip based acl summar...
Page 76
C hapter 4: m anaging d evice s ecurity destination port — indicates the destination port that is matched packets. Enabled only when tcp or udp are selected in the protocol list. Flag set — indicates the tcp flag to which the packet is mapped. Source address — matches the source ip address to which ...
Page 77
C hapter 4: m anaging d evice s ecurity defining ip based acls access control lists (acl) allow network managers to define classification actions and rules for specific ingress ports. Your switch supports up to 128 acls. Packets entering an ingress port, with an active acl, are either admitted or de...
Page 78
C hapter 4: m anaging d evice s ecurity add rules to acl priority — defines the acl priority. Acls are checked on the first fit basis. The acl priority defines the acl order in the acl list. Protocol — indicates the protocol in the ace to which the packet is matched. The possible fields are: select ...
Page 79
C hapter 4: m anaging d evice s ecurity 8 for each tcp flag, the possible field values are: set — enables the tcp flag. Unset — disables the tcp flag. Don’t care — does not check the packet’s tcp flag. Source ip address — if selected, enables matching the source port ip address to which packets are ...
Page 80
C hapter 4: m anaging d evice s ecurity 9 ■ destination ip address — if selected, enables matching the destination port ip address to which packets are addressed to the ace, according to a wildcard mask. The field value is either user defined or any. If any is selected, accepts any destination ip ad...
Page 81
C hapter 4: m anaging d evice s ecurity 0 match dscp — matches the packet dscp value to the acl. Either the dscp value or the ip precedence value is used to match packets to acls. Match ip precedence— matches the packet ip precedence value to the ace. Either the dscp value or the ip precedence value...
Page 82
C hapter 4: m anaging d evice s ecurity 1 modifying ip based acls the ip based acl modify page allows the network administrator to modify ip based acls settings. Monitor users have no access to this page. Figure ip based acl modify page the ip based acl modify page contains the following fields: sel...
Page 83
C hapter 4: m anaging d evice s ecurity destination port — indicates the destination port that is matched packets. Enabled only when tcp or udp are selected in the protocol list. Tcp flags — if checked, enables configuration of tcp flags matched to the packet. The possible fields are: urg — urgent p...
Page 84
C hapter 4: m anaging d evice s ecurity destination ip address — matches the destination ip address to which packets are addressed to the acl. Wild card mask — indicates the destination ip address wildcard mask. Wildcards are used to filter a destination ip address. Masks specify which bits are used...
Page 85
C hapter 4: m anaging d evice s ecurity 4 removing ip based acls the ip based acl remove page allows the user to remove ip based acls. Monitor users have no access to this page. 1 click device > acl > ip based acl > remove. The ip based acl remove page opens. Figure 4 ip based acl remove page the ip...
Page 86
C hapter 4: m anaging d evice s ecurity destination port — defines the tcp/udp destination port. Flag set — sets the indicated tcp flag matched to the packet. Source address — indicates the source ip address. Source mask — indicates the source ip address mask. Destination address — indicates the des...
Page 87
C hapter 4: m anaging d evice s ecurity viewing acl binding the acl binding summary page displays the user-defined acls mapped to the interfaces. To view acl binding: 1 click device > acl > acl binding > summary. The acl binding summary page opens. Figure acl binding summary page the acl binding sum...
Page 88
C hapter 4: m anaging d evice s ecurity configuring acl binding the acl binding setup page allows the network administrator to bind specific ports to mac or ip based acls. The monitor user has no access to this page. To define acl binding: 1 click device > acl > acl binding > setup. The acl binding ...
Page 89
C hapter 4: m anaging d evice s ecurity 8 the acl binding setup page contains the following fields: select port(s) — indicates the ports to be configured. Select all — allows the user to assign the acl to all ports. Select none — removes the ports selected. Bind acl — assigns an access control list ...
Page 90
C hapter 4: m anaging d evice s ecurity 9 removing acl binding the acl binding remove page allows the network administrator to remove user-defined acls from a selected interface. The monitor user has no access to this page. To remove acl binding: 1 click device > acl > acl binding > remove. The acl ...
Page 91
C hapter 4: m anaging d evice s ecurity 80 viewing broadcast storm broadcast storm limits the amount of multicast and broadcast frames accepted and forwarded by the device. When layer 2 frames are forwarded, broadcast and multicast frames are flooded to all ports on the relevant vlan. This occupies ...
Page 92
C hapter 4: m anaging d evice s ecurity 81 to view broadcast storm traffic: 1 click device > broadcast storm > summary. The broadcast storm setup page opens. Monitor users have no access to this page. Figure 8 broadcast storm summary page the broadcast storm summary page contains the following field...
Page 93
C hapter 4: m anaging d evice s ecurity 8 modifying broadcast storm the broadcast storm modify page allows the network administrator to modify broadcast storm settings. Monitor users have no access to this page. 1 click device > broadcast storm > modify. The broadcast storm modify page opens. Figure...
Page 94
C hapter 4: m anaging d evice s ecurity 8 broadcast rate threshold (10-00,000) — indicates the maximum rate (packets per second) at which broadcast or broadcast&multicast packets are forwarded. The range is 10-500,000. The default value is 100. Select port(s) — indicates the ports to be configured. ...
Page 95: General System Information
General system information this section contains information about configuring general system parameters, and includes the following: viewing system description configuring system name information configuring system time the device view page displays parameters for configuring general device informa...
Page 96
C hapter 5 : g eneral s ystem i nformation 8 the device view page contains the following fields: product description — displays the device model number and name. Not user-editable. System name — displays the user-defined device name. See “configuring system name information” page 86. System location...
Page 97
C hapter 5 : g eneral s ystem i nformation 8 the system name page allows the network administrator to provide a user-defined system name, location, and contact information for the device. Monitor users have read-only permissions on this page. To configure the system name: 1 click administration > sy...
Page 98
C hapter 5 : g eneral s ystem i nformation 8 define the fields. Click apply. The system name is enabled, and the device is updated. 4 be sure to save your configuration, or the changes will be lost when the switch is rebooted. To save the configuration, refer to “saving the configuration” on page 31...
Page 99
C hapter 5 : g eneral s ystem i nformation 88 the system time setup page contains the following sections: current time — displays the current time in mon-day-year hour: min:sec. Time zone: selects the time zone. Daylight saving — this check box enables and disables automatic daylight saving time (ds...
Page 100
C hapter 5 : g eneral s ystem i nformation 89 define the time zone for the ntp server option. Click the daylight saving box to enable or disable automatic dst option. 4 manually define the related fields for ntp server or local date and time. Click apply. The device is updated with the time settings...
Page 101: Onfiguring
C onfiguring p orts this section contains information for configuring port settings, and includes the following sections: viewing port settings defining port settings viewing port details the port administration summary page permits the network manager to view the current port and lag setting config...
Page 102
C hapter 6: c onfiguring p orts 91 to view port settings: 1 click port > administration > summary. The port administration summary page opens. Figure 4 port administration summary page the port administration summary page contains the following fields: port — indicates the selected port number. Port...
Page 103
C hapter 6: c onfiguring p orts 9 speed — displays the configured rate for the port. The port type determines what speed setting options are available. Port speeds can only be configured when auto-negotiation is disabled. The possible field values are: 10m — indicates the port is currently operating...
Page 104
C hapter 6: c onfiguring p orts 9 the port administration setup page allows network managers to configure port parameters for specific ports. Monitor users have no access to this page. To configure port settings: 1 click port > administration > setup. The port administration setup page opens. Figure...
Page 105
C hapter 6: c onfiguring p orts 94 speed — defines the configured rate for the port. The port speed determines what speed setting options are available. Port speeds can only be configured when auto negotiation is disabled. The possible field values are: 10 — indicates the port is currently operating...
Page 106
C hapter 6: c onfiguring p orts 9 the port detail page displays current port parameters for specific ports. To view port details: 1 click port > administration > detail. The port detail page opens. Figure 4 port detail page viewing port details the port detail page contains the following fields: sel...
Page 107
C hapter 6: c onfiguring p orts 9 speed — displays the configured rate for the port. The port type determines what speed setting options are available. Port speeds can only be configured when auto-negotiation is disabled. The possible field values are: 10 — indicates the port is currently operating ...
Page 108: Ggregating
A ggregating p orts this section contains information for configuring link aggregation, which optimizes port usage by linking a group of ports together to form a single lag. A link aggregated group (lag) aggregates ports or vlans into a single virtual port or vlan. Aggregating ports multiplies the b...
Page 109
C hapter 7: a ggregating p orts 98 viewing link aggregation the link aggregation summary page displays port usage by linking a group of ports together to form a single lag. Aggregating ports multiplies the bandwidth between the devices, increases port flexibility, and provides link redundancy. To vi...
Page 110
C hapter 7: a ggregating p orts 99 configuring link aggregation the link aggregation create page optimizes port usage by linking a group of ports together to form a single lag. Aggregating ports multiplies the bandwidth between the devices, increases port flexibility, and provides link redundancy. M...
Page 111
C hapter 7: a ggregating p orts 100 summary group id — displays the link aggregated group id. Type — displays the type of link aggregation for the group id. Member ports — displays the ports configured to the lag. Define the fields. Click apply. The lag configuration is defined, and the device is up...
Page 112
C hapter 7: a ggregating p orts 101 the link aggregation modify page includes the following fields: select aggregation to modify — selects the link aggregation group id to modify. Selected ports — allows the network manager to select ports to be added or removed from a current aggregation. The selec...
Page 113
C hapter 7: a ggregating p orts 10 the link aggregation remove page allows the network manager to remove group ids containing member ports. Monitor users have no access to this page. To remove link aggregation: 1 click ports > link aggregation > remove. The link aggregation remove page opens. Figure...
Page 114
C hapter 7: a ggregating p orts 10 lag ports can contain different media types if the ports are operating at the same speed. Aggregated links can be set up manually or automatically established by enabling lacp on the relevant links. Aggregate ports can be linked into link-aggregation port-groups. T...
Page 115
C hapter 7: a ggregating p orts 104 defining lacp prior- ity partner state — displays inactive or active partner oper key — displays the operational key value assigned to the port by the link partner. Group id — displays the group id lag ports can contain different media types if the ports are opera...
Page 116
C hapter 7: a ggregating p orts 10 lag ports can contain different media types if the ports are operating at the same speed. Aggregated links can be set up manually or auto- matically established by enabling lacp on the relevant links. Aggregate ports can be linked into link-aggregation port-groups....
Page 117: Onfiguring Vlans
C hapter 8: c onfiguring vlans 106 c onfiguring vlans 8 this section contains the following topics: ■ vlan overview ■ viewing vlan details ■ viewing vlan port details ■ creating vlans ■ modifying vlan settings ■ modifying port vlan settings ■ removing vlans vlans are logical subgroups with a local a...
Page 118
C hapter 8: c onfiguring vlans 107 vlans function at layer 2. Since vlans isolate traffic within the vlan, a layer 3 router working at a protocol level is required to allow traffic flow between vlans. Layer 3 routers identify segments and coordinate with vlans. Vlans are broadcast and multicast doma...
Page 119
C hapter 8: c onfiguring vlans 108 the vlan detail page provides information and global parameters on vlans configured on the system. 1 click device > vlan > vlan detail. The vlan detail page opens. Figure 53 vlan detail page the vlan detail page contains the following information: ■ select a vlan t...
Page 120
C hapter 8: c onfiguring vlans 109 the vlan port detail page provides displays vlan configured ports. To view vlan port details: 1 click device > vlan > port detail. The vlan port detail page opens. Figure 54 vlan port detail page viewing vlan port details the vlan port detail page contains the foll...
Page 121
C hapter 8: c onfiguring vlans 110 the vlan setup page allows the network administrator to create user- defined vlans. To view voice vlan settings: the monitor users have no access to this page. To create vlans: 1 click device > vlan > setup. The vlan setup page opens. Figure 55 vlan setup page crea...
Page 122
C hapter 8: c onfiguring vlans 111 rename the vlans the vlan rename page allows the network administrator to rename user-defined vlan name. The monitor users have no access to this page. To rename vlans: 1 click device > vlan > rename. The vlan rename page opens. Figure 56 vlan rename page the vlan ...
Page 123
C hapter 8: c onfiguring vlans 112 modifying vlan settings the modify vlan page allows the network manager to change vlan membership. The monitor users have no access to this page. To edit vlan settings: 1 click device > vlan > modify vlan. The modify vlan page opens. Figure 57 modify vlan page the ...
Page 124
C hapter 8: c onfiguring vlans 113 ■ select membership type — displays the membership type for each vlan. The possible field values are: untagged — indicates the interface is an untagged member of the vlan. Tagged — indicates the interface is a tagged member of a vlan. Vlan tagged packets are forwar...
Page 125
C hapter 8: c onfiguring vlans 114 modifying port vlan settings the modify vlan port page allows the network manager to modify port vlan settings. The monitor users have no access to this page. 1 click device > vlan > modify port. The modify vlan port page opens. Figure 58 modify vlan port page the ...
Page 126
C hapter 8: c onfiguring vlans 115 not available for selection — indicates the interface is not available for selection. Vlan id — enter the vlan id to which the port is assigned. All existing vlans — change the selected port setting in the tagged membership of all the existing vlans. 2 select a por...
Page 127
C hapter 8: c onfiguring vlans 116 the vlan remove page contains the following fields: id — displays the vlan id. Name — displays the user-defined vlan name. Select all — allows the user to select the entire table to be removed. 2 select the vlan id to be deleted. 3 click remove. The selected vlans ...
Page 128: Onfiguring
C hapter 9: c onfiguring ip and mac a ddress i nformation 117 9 c onfiguring ip and mac a ddress i nformation this section contains information for defining ip interfaces, and includes the following sections: defining ip addressing configuring arp settings configuring address tables defining ip addr...
Page 129
C hapter9: c onfiguring ip and mac a ddress i nformation 118 the ip setup page contains the following fields: ■ configuration method — indicates if the ip address has been configured statically or added dynamically. The possible field values are: static — indicates that the ip interface is configure...
Page 130
C hapter 9: c onfiguring ip and mac a ddress i nformation 119 the arp settings summary page displays the current arp settings. To view arp settings: 1 click administration > arp settings > summary. The arp settings summary page opens. Figure 61 arp settings summary page viewing arp settings the arp ...
Page 131
C hapter9: c onfiguring ip and mac a ddress i nformation 120 the arp settings setup page allows network managers to define arp parameters for specific interfaces. The monitor users have no access to this page. To configure arp entries: 1 click administration > arp settings > setup. The arp settings ...
Page 132
C hapter 9: c onfiguring ip and mac a ddress i nformation 121 the arp settings remove page provides parameters for removing arp entries from the arp table. The monitor user has no access to this page. To remove arp entries: 1 click administration > ip addressing > arp settings > remove. The arp sett...
Page 133
C hapter9: c onfiguring ip and mac a ddress i nformation 122 remove — removes a specific arp entry. The possible field values are: checked — removes the selected arp entries. Unchecked — maintains the current arp entries. Interface — indicates the vlan for which arp parameters are defined. Ip addres...
Page 134
C hapter 9: c onfiguring ip and mac a ddress i nformation 123 this section includes the following sections: viewing address table settings viewing port summary settings adding entries into address tables defining aging time removing address table ports removing address tables viewing address table s...
Page 135
C hapter9: c onfiguring ip and mac a ddress i nformation 124 the address table summary page contains the following fields: state — filters the list of mac addresses displayed according to the type of mac address configuration. Possible values are: all — displays all mac addresses. Static — displays ...
Page 136
C hapter 9: c onfiguring ip and mac a ddress i nformation 125 the port summary page allows the user to view the mac addresses assigned to specific ports. 1 click monitoring > address tables > port summary. The port summary page opens. Figure 65 port summary page viewing port summary settings the por...
Page 137
C hapter9: c onfiguring ip and mac a ddress i nformation 126 state — displays a port table display based on the type of address. Possible values are: static — indicates the mac address is statically configured. Dynamic — indicates the mac address is dynamically configured. Port index — indicates por...
Page 138
C hapter 9: c onfiguring ip and mac a ddress i nformation 127 the address table add page contains the following fields: vlan id — assigns a vlan id to the user-defined mac address. Mac address — defines a mac address to be assigned to the specific port and vlan id. No aging — indicates that the mac ...
Page 139
C hapter9: c onfiguring ip and mac a ddress i nformation 128 defining aging time the address table setup page allows the network manager to define the address table aging time. The aging time is the amount of time the mac addresses remain in the dynamic mac address table before they are timed out if...
Page 140
C hapter 9: c onfiguring ip and mac a ddress i nformation 129 removing address table ports the port remove page allows the network manager to remove ports from the address tables. The monitor users have no access to this page. To remove ports: 1 click monitoring > address tables > port remove. The p...
Page 141
C hapter9: c onfiguring ip and mac a ddress i nformation 130 ■ aging time —indicates that the mac address is aged out or not. Noaged — indicates that the address table entry is not aged out. Aging — indicates that the address table entry is aged out. 2 select the port(s) to display mac address on th...
Page 142
C hapter 9: c onfiguring ip and mac a ddress i nformation 131 the address table remove page contains the following fields: mac address — displays the current mac addresses listed in the mac address table. Vlan id — displays the vlan id attached to the mac address. State — displays the mac address co...
Page 143: Onfiguring
C hapter10: c onfiguring igmp s nooping & q uery 132 10 c onfiguring igmp s nooping & q uery this section contains information for configuring igmp snooping & query. When igmp snooping is enabled globally, all igmp packets are forwarded to the cpu. The cpu analyzes the incoming packets and determine...
Page 144
C hapter 10: c onfiguring igmp s nooping & q uery 133 the igmp snooping & query setup page contains the following fields: ■ igmp snooping status — indicates if igmp snooping is enabled on the device. The possible field values are: ■ disabled — indicates that igmp snooping is disabled on the device. ...
Page 145
C hapter10: c onfiguring igmp s nooping & q uery 134 disabled — disables igmp snooping on the vlan. This is the default value. Enabled — enables igmp snooping on the vlan. ■ igmp query status — indicates if igmp query is enabled on the vlan. The possible field values are: disabled — disables igmp qu...
Page 146: Configuring Spanning Tree
C hapter 11: c onfiguring s panning t ree 135 configuring spanning tree 11 this section contains information for configuring stp. The spanning tree protocol (stp) provides tree topography for any arrangement of bridges. Stp also provides a single path between end stations on a network, eliminating l...
Page 147
C hapter11: c onfiguring s panning t ree 136 viewing spanning tree the spanning tree summary page displays the current spanning tree parameters for all ports. To view spanning tree summary: 1 click device > spanning tree > summary. The spanning tree summary page opens. Figure 71 spanning tree summar...
Page 148
C hapter 11: c onfiguring s panning t ree 137 ■ edge port — indicates if edge port is enabled on the port. If edge port is enabled for a port, the port state is automatically placed in the forwarding state when the port link is up. Edge port optimizes the stp protocol convergence. Stp convergence ta...
Page 149
C hapter11: c onfiguring s panning t ree 138 priority — priority value of the port. The priority value influences the port choice when a bridge has two ports connected in a loop. The priority range is between 0 -240. Network administrators can assign stp settings to specific interfaces using the spa...
Page 150
C hapter 11: c onfiguring s panning t ree 139 priority — specifies the bridge priority value. When switches or bridges are running stp, each is assigned a priority. After exchanging bpdus, the device with the lowest priority value be comes the root bridge. The field range is 0-61440. The default val...
Page 151
C hapter11: c onfiguring s panning t ree 140 figure 73 spanning tree port setup page the spanning tree port setup page contains the following fields: status — specifies if stp is enabled on the port. The possible field values are: enabled —specifies that stp is enabled on the port. Disabled —specifi...
Page 152
C hapter 11: c onfiguring s panning t ree 141 enabled —specifies the edge port is enabled on the port. Disabled —specifies the edge port is disabled on the port. No change —maintains the current the edge port settings. This is the default value. Link type — specifies the rstp link type. The possible...
Page 153: Onfiguring
C hapter12: c onfiguring s nmp 142 12 c onfiguring snmp simple network management protocol (snmp) provides a method for managing network devices. The device supports the following snmp versions: snmp version 1 snmp version 2c the snmp agents maintain a list of variables, which are used to manage the...
Page 154
C hapter 12: c onfiguring s nmp 143 defining snmp communities access rights are managed by defining communities in the snmp com- munities setup page. When the community names are changed, access rights are also changed. Snmp communities are defined only for snmp v1 and snmp v2c. Monitor users have n...
Page 155
C hapter12: c onfiguring s nmp 144 snmp management management station — displays the management station ip address for which the snmp community is defined. Open access — provides snmp access to all the stations. Community string standard — displays pre-defined community strings. The possible field v...
Page 156
C hapter 12: c onfiguring s nmp 145 removing snmp communities the snmp communities remove page allows the system manager to remove snmp communities. Monitor users have no access to this page. To remove snmp communities: 1 click administration > snmp > communities > remove. The snmp communities remov...
Page 157
C hapter12: c onfiguring s nmp 146 ■ access mode — displays the access rights of the community. The possible field values are: read only — management access is restricted to read-only, and changes cannot be made to the community. Read write — management access is read-write and changes can be made t...
Page 158
C hapter 12: c onfiguring s nmp 147 the snmp traps setup page contains the following fields: ■ recipients ip address — defines the ip address to which the traps are sent. ■ community string — defines the community string of the trap manager. ■ trap version — defines the trap type. The possible field...
Page 159
C hapter12: c onfiguring s nmp 148 the snmp traps remove page contains the following fields: ■ remove — deletes the currently selected recipient. The possible field values are: checked — removes the selected recipient from the list of recipients. Unchecked — maintains the list of recipients. ■ recip...
Page 160: Onfiguring
Quality of service (qos) provides the ability to implement qos and priority queuing within a network. For example, certain types of traffic that require minimal delay, such as voice, video, and real-time traffic can be assigned a high priority queue, while other traffic can be assigned a lower prior...
Page 161
C hapter 13: c onfiguring q uality o f s ervice 150 the cos summary page displays cos default settings assigned to ports. To view cos settings: 1 click device > qos > cos > summary. The cos summary page opens. Figure78 cos summary page viewing cos settings the cos summary page contains the following...
Page 162
C hapter 13: c onfiguring q uality o f s ervice 151 the cos setup page contains information for enabling qos globally. Monitor users have no access to this page. To configure cos settings: 1 click device > qos > cos setup. The cos setup page opens. Figure79 cos setup page defining cos the cos setup ...
Page 163
C hapter 13: c onfiguring q uality o f s ervice 152 defining queuing algorithm the queue setup page provides two scheduling methods: strict and weighted round robin (wrr).When qos mode is disabled in the cos setup page, the scheduling method will be the default setting, wrr. Monitor users have no ac...
Page 164
C hapter 13: c onfiguring q uality o f s ervice 153 the cos to queue summary page contains a table that displays the cos values mapped to traffic queues. To view cos values to queues: 1 click device > qos > cos to queue > summary. The cos to queue summary page opens. Figure81 cos to queue summary pa...
Page 165
C hapter 13: c onfiguring q uality o f s ervice 154 to configure cos values to queues: 1 click device > qos > cos to queue > setup. The cos to queue setup page opens. Figure 82 cos to queue setup page the cos to queue setup page contains the following fields: restore defaults — restores the device f...
Page 166
C hapter 13: c onfiguring q uality o f s ervice 155 the dscp to cos summary page contains fields for mapping dscp settings to traffic queues. For example, a packet with a dscp tag value of 3 can be assigned to queue 4. To view the dscp queue: 1 click device > qos > dscp to cos > summary. The dscp to...
Page 167
C hapter 13: c onfiguring q uality o f s ervice 156 the dscp to cos setup page contains fields for mapping dscp settings to values of cos. For example, a packet with a dscp tag value of 3 can be assigned to cos 1. The monitor user has no access to this page. To map dscp to cos : 1 click device > qos...
Page 168
C hapter 13: c onfiguring q uality o f s ervice 157 configuring trust settings the trust setup page contains information for enabling trust on configured interfaces. The original device qos default settings can be reassigned to the interface in the trust setup page. To enable trust: 1 click device >...
Page 169
C hapter 13: c onfiguring q uality o f s ervice 158 viewing bandwidth settings the bandwidth summary page displays bandwidth settings for a specified interface. To view bandwidth settings: 1 click device > qos > bandwidth > summary. The bandwidth summary page opens. Figure 86 bandwidth summary page ...
Page 170
C hapter 13: c onfiguring q uality o f s ervice 159 egress shaping rates status — defines the shaping status. The possible field values are: enable — egress rate limiting is enabled on the interface. No limit — egress rate limiting is disabled on the interface. Cir — indicates cir as the interface s...
Page 171
C hapter 13: c onfiguring q uality o f s ervice 160 the bandwidth setup page contains the following fields: ingress rate limit enable ingress rate limit — enables setting an ingress rate limit. Ingress rate limit — indicates the traffic limit for the port. The possible field value is 128-500,032 kbi...
Page 172
C hapter 13: c onfiguring q uality o f s ervice 161 voice vlan allows network administrators to enhance the voip service by configuring ports to carry ip voice traffic from ip phones on a specific vlan. Voip traffic has a preconfigured oui prefix in the source mac address. Network administrators can...
Page 173
C hapter 13: c onfiguring q uality o f s ervice 162 the voice vlan summary page contains information about the voice vlan currently enabled on the device, including the ports enabled and included in the voice vlan. To view voice vlan settings: 1 click device > qos > voip > traffic setting > summary....
Page 174
C hapter 13: c onfiguring q uality o f s ervice 163 address table. The default time is 300 sec. For more information on defining mac address age out time, see defining aging time. Ports enabled for voice vlan — displays the ports on which voice vlan is enabled. Ports in the voice vlan — displays the...
Page 175
C hapter 13: c onfiguring q uality o f s ervice 164 voice vlan id — defines the voice vlan id number. Voice vlan aging time — indicates the amount of time after the last ip phone’s oui is aged out for a specific port. The port will age out after the bridge and voice aging time. The default time is o...
Page 176
C hapter 13: c onfiguring q uality o f s ervice 165 the voice vlan port setup page contains the following fields: voice vlan port mode — defines the voice vlan mode. The possible field values are: no changes — maintains the current voice vlan port settings. This is the default value. None — indicate...
Page 177
C hapter 13: c onfiguring q uality o f s ervice 166 to view voice vlan port detail settings: 1 click device > qos > voip > traffic setting > port detail. The voice vlan port details page opens. Figure 91 voice vlan port details page 2 click a port in the zoom view. The port is highlighted in blue, a...
Page 178
C hapter 13: c onfiguring q uality o f s ervice 167 the voice vlan oui summary page lists the organizationally unique identifiers (ouis) associated with the voice vlan. The first three bytes of the mac address contain a manufacturer identifier. The last three bytes contain a unique station id. Using...
Page 179
C hapter 13: c onfiguring q uality o f s ervice 168 to view vlan settings: 1 click device > qos > voip traffic setting > oui summary. The voice vlan oui summary page opens. Figure 92 voice vlan oui summary page the voice vlan oui summary page contains the following fields: oui list telephony oui(s) ...
Page 180
C hapter 13: c onfiguring q uality o f s ervice 169 the voice vlan oui modify page allows network administrators to add new ouis or to remove previously defined ouis from the voice vlan. The oui is the first half on the mac address and is manufacture specific. The last three bytes contain a unique s...
Page 181: Anaging
This section contains information about managing the configuration files and installing and backing up the switch firmware. This section includes the following topics: configuration file structure backing up system files restoring files upgrade the firmware image activating image files the configura...
Page 182
C hapter 14: m anaging s ystem f iles 171 the backup page permits network managers to backup the system configuration to a tftp or http server. The monitor users have no access to this page. 1 to keep your currently running configuration, click the saveconfiguration item on the left side of the page...
Page 183
C hapter 14: m anaging s ystem f iles 172 the restore page restores files from the tftp or http server. The monitor users have no access to this page. 1 click administration>backup&restore>restore. The restore page opens. Figure95 restore page the restore page contains the following fields: download...
Page 184
C hapter 14: m anaging s ystem f iles 173 the restore image page permits network managers to upgrade the switch firmware. Note: the bootcode can only be upgraded using the command line interface (cli). See “upgrading software using the cli”. The monitor user has no access to this page. To download t...
Page 185
C hapter 14: m anaging s ystem f iles 174 the active image page allows network managers to select and reset the image files. To upload system files: 1 click administration>firmwareupgrade>activeimage. The active image page opens. Figure97 active image page activatingimage files the active image page...
Page 186: Iewing
15 v iewing s tatistics the port statistics summary page contains fields for viewing information about device utilization and errors that occurred on the device. To view rmon statistics: 1 click ports>statistics>summary. The port statistics summary page opens. Figure98 port statistics summary page t...
Page 187
C hapter 15: v iewing s tatistics 176 refreshrate— defines the amount of time that passes before the interface statistics are refreshed. The possible field values are: no refresh — indicates that the port statistics are not refreshed. 15 sec — indicates that the port statistics are refreshed every 1...
Page 188
C hapter 15: v iewing s tatistics 177 fragments — displays the number of fragments (packets with less than 64 octets, excluding framing bits, but including fcs octets) received on the interface since the device was last refreshed. Jabbers — displays the total number of received packets that were lon...
Page 189: Anaging
16 m anaging d evice d iagnostics this section contains information for viewing and configuring port and cable diagnostics, and includes the following topics: configuring port mirroring viewing cable diagnostics port mirroring monitors and mirrors network traffic by forwarding copies of incoming and...
Page 190
C hapter 16: m anaging d evice d iagnostics 179 the port mirroring setup page contains parameters for configuring port mirroring. To enable port mirroring: 1 click monitoring>portmirroring>setup. The port mirroring setup page opens. Figure99 port mirroring setup page the port mirroring setup page co...
Page 191
C hapter 16: m anaging d evice d iagnostics 180 selectport — selects the port for mirroring or monitoring. A port unavailable for mirroring is colored grey. Summary — displays the current monitor and mirror ports. The fields displayed are: monitor — displays the monitor port. Mirror in — displays po...
Page 192
C hapter 16: m anaging d evice d iagnostics 181 the port mirroring remove page contains the following fields: monitor — displays the monitor port. Mirrorin — displays ports that are monitored on the rx. Mirrorout— displays ports that are monitored on the tx. 2 select the ports to be removed. 3 click...
Page 193
C hapter 16: m anaging d evice d iagnostics 182 the cable diagnostics summary page contains the following fields: ports — specifies the port to which the cable is connected. Testresult — displays the cable test results. Possible values are: open — indicates a cable is not connected, or the cable is ...
Page 194
C hapter 16: m anaging d evice d iagnostics 183 to test cables: 1 click monitoring>cablediagnostics>diagnostics. The diagnostics page opens. Figure102 diagnostics page the diagnostics page contains the following fields: select a port — specifies the port to be tested. Test result — displays the cabl...
Page 195: Etwork
A 3c om n etwork m anagement 3com has a range of network management applications to address networks of all sizes and complexity, from small and medium businesses through large enterprises. The applications include: 3com network supervisor 3com network director 3com network access manager 3com enter...
Page 196
A ppendix a : 3 c om n etwork m anagement 185 3com network director (3nd) is a standalone application that allows you to carry out key management and administrative tasks on midsized networks. By using 3nd you can discover, map, and monitor all your 3com devices on the network. It simplifies tasks s...
Page 197
A ppendix a : 3 c om n etwork m anagement 186 3com enterprise management suite (ems) delivers comprehensive management that is flexible and scalable enough to meet the needs of the largest enterprises and advanced networks. This solution provides particularly powerful configuration and change contro...
Page 198: Evice
B d evice s pecificationsand f eatures the 3com® baseline switch 2948-sfp plus has been designed to the following standards: function 8802-3, ieee 802.3 (ethernet), ieee 802.3u (fast ethernet), ieee 802.3ab (gigabit ethernet), ieee 802.1d (bridging) safety ul 60950-1, en 60950-1, csa 22.2 no. 60950-...
Page 199
A ppendix b : d evice s pecification and f eatures 188 linefrequency 50/60 hz inputvoltage 100–240 vac (auto range) currentrating switch 2948-sfp plus 1.5 amp (max) maximumpower consumption switch 2948-sfp plus 70 watts maxheatdissipation switch 2948-sfp plus 238.9 btu/hr this section describes the ...
Page 200
A ppendix b : d evice s pecification and f eatures 189 back pressure on half duplex links, the receiver may employ back pressure (i.E. Occupy the link so it is unavailable for additional traffic), to temporarily prevent the sender from transmitting additional traffic. This is used to prevent buffer ...
Page 201
A ppendix b : d evice s pecification and f eatures 190 table11 features of the baseline switch 2948-sfp plus feature description igmp snooping igmp snooping examines igmp frame contents, when they are forwarded by the device from work stations to an upstream multicast router. From the frame, the dev...
Page 202
A ppendix b : d evice s pecification and f eatures 191 table11 features of the baseline switch 2948-sfp plus feature description port-based virtual lans port-based vlans classify incoming packets to vlans based on their ingress port. Port mirroring port mirroring monitors and mirrors network traffic...
Page 203
A ppendix b : d evice s pecification and f eatures 192 table11 features of the baseline switch 2948-sfp plus feature description tcp transport control protocol (tcp). Tcp connections are defined between 2 ports by an initial synchronization exchange. Tcp ports are identified by an ip address and a 1...
Page 204: In-
C p in- o uts a console cable is an 8-conductor rj45-to-db9 cable. One end of the cable has an rj-45 plug for connecting to the switch’s console port, and the other end has a db-9 socket connector for connecting to the serial port on the terminal, as shown in figure 102. Figure102 console cable cons...
Page 205
A ppendix c : p in- o uts 194 nullmodemcable rj-45 to rs-232 25-pin pc-atserialcable rj-45 to 9-pin modemcable rj-45 to rs-232 25-pin.
Page 206
A ppendix c : p in- o uts 195 10/100 and 1000base-t rj-45 connections. Table10pin assignments pinnumber 10/100 1000 ports configured as mdi 1 transmit data + bidirectional data a+ 2 transmit data − bidirectional data a− 3 receive data + bidirectional data b+ 4 not assigned bidirectional data c+ 5 no...
Page 207: Roubleshooting
D t roubleshooting this section describes problems that may arise when installing the switch and how to resolve these issues. This section includes the following topics: problemmanagement — provides information about problem management. Troubleshootingsolutions — provides a list of troubleshooting i...
Page 208
A ppendix d : t roubleshooting 197 table12 troubleshooting solutions problems possiblecause solution switch does not run; power is disconnected. Verify that the power cord is properly connected to the power led is off. Switch, and to the mains supply. Cannot connect to be sure the terminal emulator ...
Page 209
A ppendix d : t roubleshooting 198 table12 troubleshooting solutions problems possiblecause solution device is in a reboot loop software fault download and install a working or previous software version from the console. No connection and the incorrect ethernet cable, check pinout and replace if nec...
Page 210: Cli
E 3c om cli r eference g uide this section describes using the command line interface (cli) to manage the device. The device is managed through the cli from a direct connection to the device console port. Using the cli, network managers enter configuration commands and parameters to configure the de...
Page 211
A ppendix e : 3c om cli r eference g uide 200 3 press enter. The passwordprompt display password: the login information is verified, and displays the following cli menu: select menu option: if the password is invalid, the following message appears and login process restarts. Incorrect password the u...
Page 212
A ppendix e : 3c om cli r eference g uide 201 ? The ? Command displays a list of cli commands on the device. Syntax ? Defaultconfiguration this command has no default configuration. Userguidelines there are no user guidelines for this command. Example the following displays the list presented for th...
Page 213
A ppendix e : 3c om cli r eference g uide 202 ping the ping command sends icmp echo request packets to another node on the network. Syntax ping parameters ip address — ip address to ping. Defaultconfiguration this command has no default configuration. Userguidelines there are no user guidelines for ...
Page 214
A ppendix e : 3c om cli r eference g uide 203 summary the summary command displays the current ip configuration and software versions running on the device. It is intended for devices that support separate runtime and bootcode images. Syntax summary defaultconfiguration this command has no default c...
Page 215
A ppendix e : 3c om cli r eference g uide 204 the ipsetup command allows the user to define an ip address on the device either manually or via a dhcp server. Syntax ipsetup parameters auto — specifies the ip address is acquired automatically from the dynamic host configuration protocol (dhcp) server...
Page 216
A ppendix e : 3c om cli r eference g uide 205 the upgrade command starts a system download and thereby allowing a system upgrade. Syntax upgrade parameters tftp server ip address — defines the tftp server’s ip address. Source file name — specifies the source file name. Defaultconfiguration this comm...
Page 217
A ppendix e : 3c om cli r eference g uide 206 the initialize command resets the device configuration to factory defaults, including the ip configuration. Syntax initialize defaultconfiguration this command has no default configuration. Userguidelines the system prompts for confirmation of the reques...
Page 218
A ppendix e : 3c om cli r eference g uide 207 the reboot command simulates a power cycle of the device. Syntax reboot defaultconfiguration this command has no default configuration. Userguidelines there are no user guidelines for this command. Example reboot select menu option: reboot are you sure y...
Page 219
A ppendix e : 3c om cli r eference g uide 208 the logout command terminates the cli session. Syntax logout defaultconfiguration this command has no default configuration. Userguidelines there are no user guidelines for this command. Example layout select menu option: logout exiting session... Login:.
Page 220
A ppendix e : 3c om cli r eference g uide 209 password the password command changes the user’s password. Syntax password defaultconfiguration this command has no default configuration. Userguidelines the user needs to login to the session in order to change the password. Example select menu option: ...
Page 221: Lossary
F g lossary addressresolution protocol(arp) acls can limit network traffic and restrict access to certain users or devices by checking each packet for certain ip or mac (i.E., layer 2) information. Arp converts between ip addresses and mac (i.E., hardware) addresses. Arp is used to locate the mac ad...
Page 222
A ppendix f : g lossary 211 extensible authentication protocoloverlan (eapol) genericmulticast registrationprotocol (gmrp) ieee802.1d ieee802.1q ieee802.1p ieee802.1s eapol is a client authentication protocol used by this switch to verify the network access rights for any device that is plugged into...
Page 223
A ppendix f : g lossary 212 on each subnetwork, one igmp-capable device can act as the querier — that is, the device that asks all hosts to report on the ip multicast groups they wish to join or to which they already belong. The elected querier is the device with the lowest ip address in the subnetw...
Page 224
A ppendix f : g lossary 213 an algorithm that is used to create digital signatures. It is intended for use with 32 bit machines and is safer than the md4 algorithm, which has been broken. Md5 is a one-way hash function, meaning that it takes a message and converts it into a fixed string of digits, a...
Page 225
A ppendix f : g lossary 214 radius is a logon authentication protocol that uses software running on a central server to control access to radius-compliant devices on the network. Rmon provides comprehensive network monitoring capabilities. It eliminates the polling required in standard snmp, and can...
Page 226
A ppendix f : g lossary 215 udp provides a datagram mode for packet-switched communications. It uses ip as the underlying transport mechanism to provide access to ip-like services. Udp packets are delivered just like ip packets – connection-less datagrams that may be discarded before reaching their ...
Page 227: Btaining
G o btaining s upportfor y our 3c om p roducts 3com offers product registration, case management, and repair services through esupport.3com.Com. You must have a user name and password to access these services, which are described in this appendix. To take advantage of warranty and other service bene...
Page 228
A ppendix g : o btaining s upport for y our 3c om p roducts 217 contact your authorized 3com reseller or 3com for additional product and support information. See the table of access numbers later in this appendix. You are entitled to bug fix / maintenance releases for the version of software that yo...
Page 229
A ppendix g : o btaining s upport for y our 3c om p roducts 218 to send a product directly to 3com for repair, you must first obtain a return materials authorization number (rma). Products sent to 3com without authorization numbers clearly marked on the outside of the package will be returned to the...
Page 230
A ppendix g : o btaining s upport for y our 3c om p roducts 219 country telephonenumber country telephonenumber you can also obtain support in this region using this url: http://emea.3com.Com/support/email.Html you can also obtain non-urgent support in this region at these email addresses: technical...
Page 231: Egulatory
R egulatory n otices ices s tatement this equipment has been tested and found to comply with the limits for a class a digital device, pursuant to part 15 of the fcc rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a comm...