- DL manuals
- 3Com
- Wireless Access Point
- 3CRGPC10075
- User Manual
3Com 3CRGPC10075 User Manual
Summary of 3CRGPC10075
Page 1
Http://www.3com.Com/ part no. Duapoe10075baa01 published december 2004 officeconnect ® wireless 108 mbps 11g poe access point user guide 3crgpoe10075 (wl-529).
Page 2
3com corporation 350 campus drive marlborough, ma usa 01752-3064 copyright © 2004, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without writt...
Page 3: Ontents
C ontents a bout t his g uide conventions 1 related documentation 3 documentation comments 3 1 i ntroducing the o ffice c onnect w ireless a ccess p oint overview 5 features and capabilities 6 wireless and networking 6 security 12 configuration and management 15 package contents 16 physical features...
Page 4
3 c onfiguring the a ccess p oint navigating the web interface 27 menu and tabs 27 buttons 28 timeout setting 28 defining security profiles 28 configuring and enabling a profile 29 setting the primary profile 44 isolating wireless clients with different profiles 44 controlling access to the wireless...
Page 5
Viewing the device status 81 viewing profiles 82 viewing associated wireless stations 83 working with logs 83 viewing device statistics 85 working with the configuration file 86 backing up the configuration file 87 restoring settings from a backup 88 restoring settings to factory defaults 88 sending...
Page 6: Lan B
C w ireless lan b asics wireless modes 121 ad hoc mode 121 infrastructure mode 121 ssid/essid 121 bss/ssid 121 ess/essid 122 wireless channels 122 security settings 122 wep 122 wpa-psk 123 wpa-802.1x 123 802.1x 123 d c onfiguring the tcp/ip s ettings of w ireless s tations overview of tcp/ip 125 con...
Page 7
G lossary i ndex r egulatory n otices.
Page 9: Bout
A bout t his g uide this guide describes how to install and configure the officeconnect wireless 108 mbps 11g poe access point (3crgpoe10075). This guide is intended for use by those responsible for installing and setting up network equipment. Consequently, it assumes a basic working knowledge of la...
Page 10
2 a bout t his g uide table 1 notice icons icon notice type description information note information that describes important features or instructions caution information that alerts you to potential loss of data or potential damage to an application, system, or device warning information that alert...
Page 11
Related documentation 3 related documentation in addition to this guide, each officeconnect wireless 108 mbps 11g poe access point documentation set includes the following: ■ quick start guide this guide provides information to help you easily set up the access point in a network environment. ■ onli...
Page 12
4 a bout t his g uide.
Page 13: Ntroducing
1 i ntroducing the o ffice c onnect w ireless a ccess p oint this chapter provides an overview of the features and capabilities of the officeconnect® wireless 108 mbps 11g poe access point. It also identifies the contents of the access point kit and helps you get to know the physical features of the...
Page 14
6 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint figure 1 network architecture with officeconnect wireless access point features and capabilities the access point integrates standards-based features that provide for seamless integration into your existing network and simplify...
Page 15
Features and capabilities 7 poe support poe support makes it easier to overcome installation problems with difficult-to-wire or hard-to-reach locations. The same category 5 cable that connects the access point to the wired network also provides its power, so ac power outlet locations and extra cabli...
Page 16
8 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint wds support wireless distribution system (wds) allows you to build a completely wireless infrastructure using access points, instead of wires, to interconnect multiple networks. Wds also helps you create large wireless networks...
Page 17
Features and capabilities 9 figure 2 point-to-point wds ptmp mode, as shown in figure 3 , interconnects three or more wired networks using multiple access points that function as wireless bridges. In a ptmp configuration, one access point is configured as the master ap and set to ptmp mode. The othe...
Page 18
10 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint figure 3 point-to-multipoint wds secure wds communication the access point secures wds links using either wep or wpa-psk encryption. If you use wep, all aps in the system must use the same wep key. If you use wpa-psk, you must...
Page 19
Features and capabilities 11 figure 4 repeater wds as a client, the access point functions like a wireless card that is connected to a computer to provide a wireless interface. When operating in client mode, the access point can only communicate with a wireless router or an access point. Wired netwo...
Page 20
12 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint figure 5 client mode security table 2 lists the security features that the access point provides. Wired network ` ` status powe r lan wire les s statu s powe r lan wirele ss ethernet cable access point in client mode table 2 s...
Page 21
Features and capabilities 13 multiple ssids using multiple ssids provides you with more flexibility in configuring your wireless network, including supporting multiple security schemes simultaneously. For example, if you have a number of wireless stations that can only support wep encryption while t...
Page 22
14 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint figure 6 wireless stations using different security settings vlan support a virtual lan (vlan) is a network of computers that behave as if they are on the same local network, even if they are physically located on different se...
Page 23
Features and capabilities 15 figure 7 wireless stations segmented into different vlans based on ssids to enable the switch to forward packets from the wireless stations to the correct vlan, the access point inserts vlan membership information into the packets sent by the wireless stations before for...
Page 24
16 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint package contents the access point kit includes the following items: ■ one officeconnect wireless 108 mbps 11g poe access point ■ one power adapter ■ officeconnect wireless 108 mbps 11g poe access point quick start guide ■ one ...
Page 25
Physical features 17 physical features before setting up the access point, 3com recommends that you first familiarize yourself with the physical features of the device. Front panel the front panel of the access point includes leds that indicate the status of the device. For information on what these...
Page 26
18 c hapter 1: i ntroducing the o ffice c onnect w ireless a ccess p oint overview of setup and management tasks the following are tasks that you need to perform to get the access point up and running, and to enable wireless stations on the network to associate with it. 1 install the access point – ...
Page 27: Nstalling
2 i nstalling and c onnecting the a ccess p oint this chapter provides information on installing the access point and connecting it to the local network. It also lists the system requirements for wireless stations that will associate with the access point. Before you begin before starting with the i...
Page 28
20 c hapter 2: i nstalling and c onnecting the a ccess p oint this access point does not support 802.11a wireless clients. Security information warning: before you start, please read the “important safety information” section in appendix f . Vorsicht: bitte lesen sie den abschnitt “wichtige sicherhe...
Page 29
Powering on and connecting the access point 21 powering on and connecting the access point the procedure for connecting the ethernet cable to and powering on the access point depends on whether you want to use the supplied power adapter or poe. To use poe, you must have a power sourcing equipment (p...
Page 30
22 c hapter 2: i nstalling and c onnecting the a ccess p oint if you have an 802.3af-compliant power sourcing equipment (pse), do the following: 1 connect one end of a standard ethernet cable to the ethernet port on the back panel of the access point. And then, connect the other end to the p+data po...
Page 31
Accessing the web interface 23 with a dhcp server to connect to the web interface, you need to know the ip address that the dhcp server has assigned to the access point. To do this, use the 3com access point manager that is included on the cd-rom. Before continuing, check the sticker on the base of ...
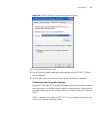
Page 32
24 c hapter 2: i nstalling and c onnecting the a ccess p oint figure 10 3com access point manager 4 click the access point name that corresponds to the name on the base of the access point. 5 click web management to start the web interface. If the web management button is unavailable, it means that ...
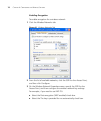
Page 33
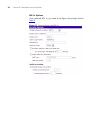
Accessing the web interface 25 to change the subnet mask for the access point: 1 click set ip address. The ip configuration screen appears. Figure 11 ip configuration screen 2 click fixed, and then configure the following ip settings: ■ ip address ■ subnet mask – this mask must be the same as the su...
Page 34
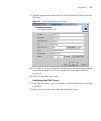
26 c hapter 2: i nstalling and c onnecting the a ccess p oint 6 click ok. Without a dhcp server if you do not have a dhcp server on the network, you need to reconfigure the tcp/ip settings of the admin computer to be able to connect to the access point’s web interface. 1 open the properties dialog b...
Page 35: Onfiguring
3 c onfiguring the a ccess p oint this chapter provides information on configuring the access point to enable wireless stations to successfully associate with it. Navigating the web interface the web interface has been designed to enable you to easily perform configuration tasks and view information...
Page 36
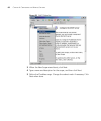
28 c hapter 3: c onfiguring the a ccess p oint interface. If there are more options for the menu selection, then tabs containing these additional options appear above the main part. Buttons ■ save – click this button to save changes that you have made to the access point settings. These changes will...
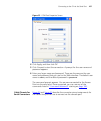
Page 37
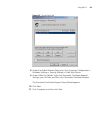
Defining security profiles 29 configuring and enabling a profile to define a security profile, you need to set the wireless security settings and the encryption and authentication methods. 1 on the menu, click security profiles. 2 under current profiles, select a profile, and then click configure. F...
Page 38
30 c hapter 3: c onfiguring the a ccess p oint ■ 802.1x – uses wep for encryption and a radius server on the network to perform client authentication for more information on configuring each encryption method, refer to “configuring encryption and authentication” on page 31 . 6 if you have a radius s...
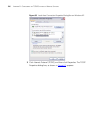
Page 39
Defining security profiles 31 configuring encryption and authentication this section lists the configuration options for each available encryption and authentication method. Wep options if you selected wep, you need to configure the settings listed in table 6 . Figure 14 security options for wep tab...
Page 40
32 c hapter 3: c onfiguring the a ccess p oint wpa-psk options if you selected wpa-psk, you need to configure the settings listed in table 7 . Figure 15 security options for wpa-psk passphrase to generate wep keys, type a word or group of printable characters in this text box, and then click generat...
Page 41
Defining security profiles 33 wpa encryption select your preferred wpa encryption level, and ensure that wireless stations have the same setting and key value. ■ tkip – unicast (point-to-point) transmissions and multicast (broadcast) transmissions are encrypted using tkip ■ tkip + 64 bit wep – unica...
Page 42
34 c hapter 3: c onfiguring the a ccess p oint wpa-802.1x options if you selected wpa-802.1x, you need to configure the settings listed in table 8 . Figure 16 security options for wpa-802.1x table 8 options for wpa-802.1x option description radius server address type the host name or ip address of t...
Page 43
Defining security profiles 35 wpa encryption select the preferred wpa encryption level, and ensure that wireless stations have the same setting and key value. ■ tkip – unicast (point-to-point) transmissions and multicast (broadcast) transmissions are encrypted using tkip ■ tkip + 64 bit wep – unicas...
Page 44
36 c hapter 3: c onfiguring the a ccess p oint 802.1x options if you selected 802.1x, you need to configure the settings listed in table 9 . Figure 17 security options for 802.1x.
Page 45
Defining security profiles 37 table 9 options for 802.1x option description radius server address type the host name or ip address of the radius server on the network radius port type the port number used for connections to the radius server. Client login name this read-only field displays the name ...
Page 46
38 c hapter 3: c onfiguring the a ccess p oint configuring radius mac authentication if you have a radius server set up on the network, you can use it to centralize the authentication of wireless stations based on their mac addresses. Authenticated stations will be allowed to associate with the acce...
Page 47
Defining security profiles 39 xx:xx:xx:xx:xx:xx is the station’s mac address) is added to the access point log. The wireless station’s status also appears as authenticated on the list of associated stations. If the wireless station’s mac address is not on the radius database, the entry xx:xx:xx:xx:x...
Page 48
40 c hapter 3: c onfiguring the a ccess p oint configuring uam universal access method (uam) is a client authentication method that is typically used in internet cafes, hot spots, and similar sites that provide internet access. Any wireless station attempting to connect to the internet using a web b...
Page 49
Defining security profiles 41 authentication. You can customize the welcome screen, or even link it to your organization’s web site. Figure 19 uam screen internal uam authentication to use internal uam authentication, do following: 1 ensure that the access point can log on to the radius server as a ...
Page 50
42 c hapter 3: c onfiguring the a ccess p oint c in radius server address, type the ip address or host name of the radius server that will authenticate clients. D in radius port, type the port number on the radius server that is configured for communication with radius clients. E in shared key, type...
Page 51
Defining security profiles 43 3 on your web server, create a welcome page that has a button or link to the uamlogon.Htm page on the access point. Users will enter their user name and password on the uamlogon.Htm page. 4 verify that the wireless security settings on the wireless stations match the se...
Page 52
44 c hapter 3: c onfiguring the a ccess p oint if the logon credentials are invalid, the user will not be able to access any other web page, except for the logon page. An entry xx:xx:xx:xx:xx:xx web authentication failed is added to the log, and the station’s status appears as authenticating on the ...
Page 53
Controlling access to the wireless network 45 devices that are on different vlans are isolated from each other. For vlan to work correctly, all network devices (for example, hubs, switches, routers, and gateways) must support the 802.1q standard. For an overview of the vlan support provided by the a...
Page 54
46 c hapter 3: c onfiguring the a ccess p oint determine the mac address of a wireless station on a windows computer: 1 on the start menu, click run. 2 in the open field, type cmd or command . A command prompt appears. 3 type ipconfig /all , and then press . 4 note the value for physical address und...
Page 55
Controlling access to the wireless network 47 figure 22 manually adding a trusted station to the list repeat steps 3 to 5 for each wireless station that you want to add to the access control list. To delete a mac address from the list, click the mac address under trusted wireless stations, and then ...
Page 56
48 c hapter 3: c onfiguring the a ccess p oint 4 click browse, and then browse to the location of the text-based access control list. Figure 23 uploading the text file that lists the trusted mac addresses 5 click the text file, and then click ok. 6 click upload file. The mac addresses in the text fi...
Page 57
Configuring system settings 49 figure 24 enabling mac address based access control backing up the access control list to ensure that you can easily restore the access control list if it accidentally erased, 3com recommends that you back it up periodically. To back up the access control list: 1 on th...
Page 58
50 c hapter 3: c onfiguring the a ccess p oint figure 25 system screen to configure the system settings: 1 on the menu, click system. 2 configure the identity of the access point on the network. You can edit the following settings: ■ access point name – this is the name that identifies the access po...
Page 59
Configuring system settings 51 ■ if you have a dhcp server on the network and you want the access point to automatically obtain its ip address from the dhcp server, click dhcp client. ■ if you do not have a dhcp server on the network, click fixed ip address. The access point will use its default ip ...
Page 60
52 c hapter 3: c onfiguring the a ccess p oint configuring the wireless settings the access point can function either as a standard wireless access point or a wireless client/repeater. Basic wireless settings basic wireless settings include the settings for the different modes supported by the acces...
Page 61
Configuring the wireless settings 53 3 in ap mode, select the appropriate mode for the access point. Available options include: ■ none – disables ap mode. If you want the access point to function as a bridge only, select this option. ■ access point – sets the device as a regular access point ■ clien...
Page 62
54 c hapter 3: c onfiguring the a ccess p oint do this to improve wireless security, especially if you have not defined a list of trusted wireless stations. 5 in bridge mode, select the appropriate mode. The following options are available: ■ none (disable) – disables bridge mode. Select this if you...
Page 63
Configuring the wireless settings 55 configuring ptmp bridge settings figure 27 ptmp mode with the access point set as master if you set the access point to ptmp bridge mode, you need to set the other access points to ptp bridge mode, and specify the access point’s mac address in their ptp bridge ac...
Page 64
56 c hapter 3: c onfiguring the a ccess p oint figure 28 ptmp ap list screen for increased security, you can restrict the access points that can bridge with the officeconnect wireless access point. To do this: 1 under the bridge mode section of the basic tab, select the in ptmp mode, only allow spec...
Page 65
Configuring the wireless settings 57 advanced wireless settings advanced wireless settings include basic rate options, wireless separation, disassociation timeout, and beacon interval. Figure 29 advanced wireless settings screen basic rate the basic rate is used for broadcasting. It does not determi...
Page 66
58 c hapter 3: c onfiguring the a ccess p oint options ■ wireless separation – if selected, wireless stations that are associated with the access point are invisible to other wireless stations. In most business situations, this check box should be cleared. ■ worldwide mode (802.11d) – select this ch...
Page 67: Onfiguring
4 c onfiguring the w ireless s tations this chapter describes how to configure the wireless stations with the appropriate security settings to ensure successful association with the access point. It also provides information on how to configure other devices, such as the radius server, that may be r...
Page 68
60 c hapter 4: c onfiguring the w ireless s tations the only settings that must be configured on the wireless station are the wireless mode and ssid. For more information on these settings, refer to table 12 . For specific instructions on how to configure these settings, refer to the documentation t...
Page 69
Using wpa-psk 61 for specific instructions on how to configure these settings, refer to the documentation that came with the wireless network adapter that is installed on the wireless station. Using wpa-psk if you configured the access point to use wpa-psk for encryption and authentication, the wire...
Page 70
62 c hapter 4: c onfiguring the w ireless s tations ■ a client logon account for the access point must be configured on the radius server. ■ the access point normally uses its default name as its client logon name. However, the radius server may ignore this and use the ip address instead. ■ the shar...
Page 71
Using 802.1x 63 ■ configure the wireless stations for 802.1x setting up microsoft ias as radius server this section describes using microsoft internet authentication server as the radius server, since it is the most common radius server available that supports the eap-tls authentication method. The ...
Page 72
64 c hapter 4: c onfiguring the w ireless s tations installing the required services 1 from the start menu, click control panel. 2 double-click add/remove programs. 3 click add/remove windows components. 4 verify that the following components are selected: ■ certificate services – after enabling thi...
Page 73
Using 802.1x 65 7 type the required the information for the certificate authority, and then click next. Figure 31 ca identifying information screen 8 click next to use the ca’s default configuration. Windows setup displays a warning message that iis is running and must be stopped before continuing. ...
Page 74
66 c hapter 4: c onfiguring the w ireless s tations figure 32 dhcp dialog box 3 when the new scope wizard starts, click next. 4 type a name and description for the scope, and then click next. 5 define the ip address range. Change the subnet mask if necessary. Click next when done..
Page 75
Using 802.1x 67 figure 33 ip address range screen 6 add exclusions in the address fields if required. If no exclusions are required, leave it blank. Click next. 7 change the lease duration time, if necessary, and then click next. 8 select yes, i want to configure these options now, and click next. 9...
Page 76
68 c hapter 4: c onfiguring the w ireless s tations setting up the certificate authority server 1 from the start menu, point to programs > administrative tools, and then click certification authority. 2 on the certification authority screen, right-click policy settings, point to new, and then click ...
Page 77
Using 802.1x 69 figure 35 group policy tab 8 under the default domain policy tree, click computer configuration > windows settings > security settings > public key policies. 9 under public key policies, right-click automatic certificate request settings, point to new, and then click automatic certif...
Page 78
70 c hapter 4: c onfiguring the w ireless s tations figure 36 automatic certificate request setup wizard 12 verify that your certificate authority is selected, and then click next. 13 review the policy change information, and then click finish. 14 from the start menu, click run, and then enter cmd ....
Page 79
Using 802.1x 71 6 right-click remote access policies, and then click new remote access policy. 7 assuming that you are using eap-tls, name the policy eap-tls , and then click next. The select attribute screen appears. 8 click add. If you do not want to set any restrictions, click day-and-time-restri...
Page 80
72 c hapter 4: c onfiguring the w ireless s tations 14 to display the help file for eap, click yes. 15 click finish. Configuring remote access logon for users 1 from the start menu, point to programs > administrative tools, and then click active directory users and computers. 2 double-click the user...
Page 81
Using 802.1x 73 ask users to install the windows 2000 service pack 3 to gain the same functionality. If your wireless stations are running neither windows xp nor windows 2000, they need to use the 802.1x client software provided with the wireless adapters. For information on how to set up and config...
Page 82
74 c hapter 4: c onfiguring the w ireless s tations figure 39 welcome screen of microsoft certificate services 6 click user certificate request, select user certificate, and then click next. 7 click submit. A message appears, and then the certificate issued screen appears. 8 click install this certi...
Page 83
Using 802.1x 75 figure 40 wireless network connection properties screen 3 click the authentication tab. 4 verify that the enable network access control using ieee 802.1x check box is selected. 5 in eap type, verify that smart card or other certificate is selected. Configuring the encryption settings...
Page 84
76 c hapter 4: c onfiguring the w ireless s tations enabling encryption to enable encryption for a wireless network: 1 click the wireless networks tab. Figure 41 wireless networks tab 2 from the list of available networks, click the ssid for the access point, and then click configure. 3 on the wirel...
Page 85
Using 802.1x without wpa 77 figure 42 wireless network properties screen 4 click ok. Windows xp configuration for 802.1x is now complete. Using 802.1x without wpa the procedure for setting up 802.1x without wpa is almost the same as for wpa-802.1x. The only difference is that on the wireless station...
Page 86
78 c hapter 4: c onfiguring the w ireless s tations.
Page 87: Erforming
5 p erforming a dditional a dministrative t asks this chapter provides information on other tasks that you can perform after setting up and configuring the access point and wireless stations. Configuring administrator access to prevent unauthorized users from gaining access to the web interface, 3co...
Page 88
80 c hapter 5: p erforming a dditional a dministrative t asks figure 43 configure administrator access on the admin login screen changing the default logon account to prevent unauthorized users from accessing the web interface and modifying your settings, 3com recommends that you change the default ...
Page 89
Viewing information about the device 81 ■ allow admin connections via wired ethernet only – select this check box to prevent wireless access to the web interface. ■ enable http admin connections – select this check box to allow admin connections via http. If you enable this type of admin connection,...
Page 90
82 c hapter 5: p erforming a dditional a dministrative t asks viewing profiles to view a summary of the all current profiles (both enabled and disabled): 1 on the menu, click status. 2 click the profiles tab. Information about all current profiles, including the profile name, ssid, security settings...
Page 91
Viewing information about the device 83 figure 44 profiles screen viewing associated wireless stations to view the list of currently associated wireless stations: 1 on the menu, click status. 2 click the stations tab. Information about all currently associated stations, including the computer name, ...
Page 92
84 c hapter 5: p erforming a dditional a dministrative t asks to view the access point logs: 1 on the menu, click status. 2 click the logs tab. Log information appears on the logs screen, displaying: ■ client connection information, including the date and time when clients were authenticated, associ...
Page 93
Viewing information about the device 85 if you have a syslog server on the network, you can automate this process by configuring the access point to forward its log entries to the syslog server. For information, refer to “sending device logs to a syslog server” on page 88 . To save the logs to a fil...
Page 94
86 c hapter 5: p erforming a dditional a dministrative t asks information that is displayed on the statistics screen is described in the following tables. Working with the configuration file access point settings are saved to a configuration file that is stored on the device. To ensure that you can ...
Page 95
Working with the configuration file 87 use the config file screen under management to back up the configuration file and to restore your settings from a configuration backup. Figure 47 config file screen backing up the configuration file to back up the configuration file: 1 on the menu, click manage...
Page 96
88 c hapter 5: p erforming a dditional a dministrative t asks restoring settings from a backup to restore settings from a backup file: 1 on the config file screen, click browse under restore. The choose file dialog box appears. 2 click the backup file, and then click open. 3 click restore. A warning...
Page 97
Configuring the snmp agent 89 to disable sending of the device logs to a syslog server, click disable. Figure 48 sending device logs to a syslog server 4 in minimum severity level, specify the type of log information that will be sent to the syslog server. Available options include: ■ 1 - alert – se...
Page 98
90 c hapter 5: p erforming a dditional a dministrative t asks figure 49 snmp screen to configure the snmp agent that is built into the access point: 1 on the menu, click management. 2 click the snmp tab. 3 select the enable snmp check box. 4 in community, type the name snmp community name (normally,...
Page 99
Upgrading the firmware 91 ■ broadcast – broadcast traps to the network, making them available on any computer on the network ■ send to – send only to the specified computer. If you select this option, you also need to type the ip address of the computer. 8 in trap version, select the version that is...
Page 100
92 c hapter 5: p erforming a dditional a dministrative t asks the upgrade process can take up to two minutes, and is complete when the status led has stopped flashing and is permanently off. Make sure that you do not interrupt power to the access point during the upgrade process; if you do, the soft...
Page 101
Automating updates and configuration 93 to automate configuration: 1 on the menu, click advanced. 2 click the auto config/update tab. 3 under auto config, select the perform auto configuration on this ap next restart check box. 4 to allow other access points (that are also set to auto config) to cop...
Page 102
94 c hapter 5: p erforming a dditional a dministrative t asks ■ install fw if different version found – installs any firmware on the ftp server with a different version number, regardless of whether it is newer or older than the one installed ■ install later version only – checks only for firmware v...
Page 103
Detecting rogue access points 95 figure 52 rogue ap detection screen to enable detection of rogue access points: 1 on the menu, click advanced. 2 click the rogue ap detection tab. 3 select the enable rogue ap detection check box. 4 in scan every..., set the interval (in minutes) at which the access ...
Page 104
96 c hapter 5: p erforming a dditional a dministrative t asks viewing detected rogue access points on the advanced screen, click rogue ap list. The screen displays information about unauthorized access points on the network, including why it was detected as rogue. Table 20 rogue access point list th...
Page 105: Roubleshooting
6 t roubleshooting this chapter lists some issues that you may encounter while installing, configuring, and using the access point, and provides information on how to resolve them. Basic connection checks ■ verify that the access point is connected to your switch or hub and that all the equipment is...
Page 106
98 c hapter 6: t roubleshooting forgotten password and reset to factory defaults if you can browse to the access point configuration screen but cannot log on because you have forgotten the password, follow the steps below to reset the access point to its factory default configuration. All your confi...
Page 107: Echnical
A t echnical s pecifications this appendix lists the technical specifications for the officeconnect wireless 108 mbps 11g poe access point. Hardware specifications table 21 hardware specifications component description cpu ar2312 radio-on-chip ar2112 dram 8 mb flash rom 2 mb ethernet port 1 x auto-m...
Page 108
100 a ppendix a: t echnical s pecifications wireless specifications table 22 wireless specifications specification description receive sensitivity at 11 mbps min. -85dbm receive sensitivity at 5.5 mbps min. -89dbm receive sensitivity at 2 mbps min. -90dbm receive sensitivity at 1 mbps min. -93dbm ma...
Page 109
Wireless specifications 101 operating range 802.11b indoors ■ 30 meters (100 ft) @ 11 mbps ■ 50 meters (165 ft) @ 5.5 mbps ■ 70 meters (230 ft) @ 2 mbps ■ 9 1 meters (300 ft) @ 1 mbps outdoors ■ 152 meters (500 ft) @ 11 mbps ■ 270 meter (885 ft) @ 5.5 mbps ■ 396 meters (1300 ft) @ 2 mbps ■ 457 meter...
Page 110
102 a ppendix a: t echnical s pecifications software specifications table 23 software specifications specification description wireless ■ access point support ■ roaming supported ■ ieee 802.11g/11b compliance ■ super g (up to 108mbps) ■ auto-sensing open system/shared key authentication ■ wireless c...
Page 111
Software specifications 103 management ■ web-based configuration ■ radius accounting ■ radius-on feature ■ radius accounting update ■ cli ■ message log ■ access control list file support ■ configuration file backup and restore ■ statistics support ■ device discovery program ■ windows utility other f...
Page 112
104 a ppendix a: t echnical s pecifications.
Page 113: Ommand
B c ommand l ine r eference this appendix describes how to use telnet and the serial port (rs232) to access the command line interface (cli) for configuration. It also provides a complete list of all commands that can be executed at the cli. You can use the cli to create scripts that automate basic ...
Page 114
106 a ppendix b: c ommand l ine r eference connecting to the cli via the serial port to connect to the cli via the serial port: 1 using a standard serial port cable, connect your computer to the serial (rs232) port on the access point. 2 start your communications program. For example, in windows, yo...
Page 115
Connecting to the cli via the serial port 107 figure 53 com port properties screen 4 click apply, and then click ok. 5 click connect to start the connection. A prompt for the user name and password appears. 6 enter your logon name and password. These are the same as the user name and password that y...
Page 116
108 a ppendix b: c ommand l ine r eference figure 54 pinouts for 9-pin to rs-232 25-pin figure 55 pinouts for 9-pin to 9-pin command reference table 24 lists all the commands that you use on the access point through the cli. Screen shell txd 3 rxd 2 ground 5 rts 7 cts 8 dsr 6 dcd 1 dtr 4 1 screen 3 ...
Page 117
Command reference 109 config profile configure profile del acl delete access control list del key delete encryption key find bss find bss find channel find available channel find all find all bss format format flash file system bootrom update boot rom image ftp software update via ftp get 11gonly di...
Page 118
110 a ppendix b: c ommand l ine r eference get config display current ap configuration get countrycode display country code get ctsmode display cts mode get ctsrate display cts rate get ctstype display cts type get domainsuffix display domain name server suffix get dtim display data beacon rate (dti...
Page 119
Command reference 111 get overridetxpower display tx power override get operationmode display operation mode get power display transmit power setting get quietackctsallow display if ack/cts frames are allowed during quiet period get quietduration display duration of quiet period get quietoffset disp...
Page 120
112 a ppendix b: c ommand l ine r eference get wirelessmode display wireless lan mode get 80211d display 802.11d mode get http display http enable/disable get httpport display http port number get https display https enable/disable get httpsport display https port number get syslog display syslog di...
Page 121
Command reference 113 get profilevlanid display profile vlan id get apprimaryprofile display ap primary profile get wdsprimaryprofile display wds primary profile get securitymode display security mode get accounting display accounting enable/disable get accountingport display accounting port number ...
Page 122
114 a ppendix b: c ommand l ine r eference help display cli command list lebradeb disable reboot during radar detection ls list directory mem system memory statistics np network performance ns network performance server ping ping radar! Simulate radar detection on current channel reboot reboot acces...
Page 123
Command reference 115 set compproc set compression scheme set compwinsize set compression window size set countrycode set country code set ctsmode set cts mode set ctsrate set cts rate set ctstype set cts type set domainsuffix set domain name server suffix set dtim set data beacon rate (dtim) set en...
Page 124
116 a ppendix b: c ommand l ine r eference set overridetxpower set tx power override set operationmode set operation mode set password modify password set passphrase modify passphrase set power set transmit power set quietackctsallow allow ack/cts frames during quiet period set quietduration duratio...
Page 125
Command reference 117 set wlanstate set wlan state set wirelessmode set wireless lan mode set 80211d set 802.11d mode set http set http enable/disable set httpport set http port number set https set https enable/disable set httpsport set https port number set syslog set syslog disable/broadcast/unic...
Page 126
118 a ppendix b: c ommand l ine r eference set profilename set profile name set profilevlanid set profile lan id set apprimaryprofile set access point’s primary profile set wdsprimaryprofile set primary profile wds set securitymode set security mode set accounting set accounting enable/disable set a...
Page 127
Command reference 119 set sdset set debug level set sdadd add debug level set sddel del debug level start wlan start the current wlan stop wlan stop the current wlan timeofday display current time of day version software version table 24 console commands command description.
Page 128
120 a ppendix b: c ommand l ine r eference.
Page 129: Ireless
C w ireless lan b asics this appendix provides basic information on wireless local networks. Other terms related to wireless networks that are not included in this appendix can be found in the glossary starting on page 143 . Wireless modes there are two modes in which wireless local networks can ope...
Page 130
122 a ppendix c: w ireless lan b asics ess/essid a group of wireless stations and multiple access points, all using the same id (essid), form an extended service set (ess). Different access points within an ess can use different channels. To reduce interference, it is recommended that adjacent acces...
Page 131
Security settings 123 wpa-psk like wep, data is encrypted before transmission. Wpa is more secure than wep, and should be used if possible. The psk (pre-shared key) must be entered on each wireless station. The 256bit encryption key is derived from the psk, and changes frequently. Wpa-802.1x this ve...
Page 132
124 a ppendix c: w ireless lan b asics.
Page 133: Onfiguring
D c onfiguring the tcp/ip s ettings of w ireless s tations this appendix provides information on how to configure the tcp/ip settings of a wireless station on different windows platforms. Overview of tcp/ip transmission control protocol/internet protocol (tcp/ip) is probably the most widely known an...
Page 134
126 a ppendix d: c onfiguring the tcp/ip s ettings of w ireless s tations figure 56 local area connection properties dialog box on windows xp 3 click internet protocol (tcp/ip), and then click properties. The tcp/ip properties dialog box, as shown in figure 61 , appears..
Page 135
Configuring tcp/ip on windows xp 127 figure 57 internet protocol (tcp/ip) properties dialog box on windows xp 4 verify that the tcp/ip settings are correct. ■ if a dhcp server automatically assigns ip addresses on the network, click obtain an ip address automatically. ■ if static ip addresses are as...
Page 136
128 a ppendix d: c onfiguring the tcp/ip s ettings of w ireless s tations configuring tcp/ip on windows 2000 to configure the tcp/ip settings of a wireless station that is running windows 2000: 1 from the start menu, point to settings, and then click network and dial-up connections. 2 right-click th...
Page 137
Configuring tcp/ip on windows 2000 129 figure 59 internet protocol (tcp/ip) properties dialog box on windows 2000 4 verify that the tcp/ip settings are correct. ■ if a dhcp server automatically assigns ip addresses on the network, click obtain an ip address automatically. ■ if static ip addresses ar...
Page 138
130 a ppendix d: c onfiguring the tcp/ip s ettings of w ireless s tations configuring tcp/ip on windows me/98/95 to configure the tcp/ip settings of a wireless station that is running windows me, 9x, or 95: 1 from the start menu, point to settings, and then click control panel. 2 double-click networ...
Page 139
Configuring tcp/ip on windows nt 4.0 131 ■ if a dhcp server automatically assigns ip addresses on the network, click obtain an ip address automatically. ■ if static ip addresses are assigned to computers on the network, click specify an ip address, and then do the following: ■ in ip address, type an...
Page 140
132 a ppendix d: c onfiguring the tcp/ip s ettings of w ireless s tations figure 62 network dialog box on windows nt 3 select the tcp/ip component for the wireless network card, and then click properties. The microsoft tcp/ip properties dialog box, as shown in figure 61 , appears..
Page 141
Configuring tcp/ip on windows nt 4.0 133 figure 63 microsoft tcp/ip properties dialog box 4 verify that the tcp/ip settings are correct. ■ if a dhcp server automatically assigns ip addresses on the network, click obtain an ip address automatically. ■ if static ip addresses are assigned to computers ...
Page 142
134 a ppendix d: c onfiguring the tcp/ip s ettings of w ireless s tations.
Page 143: Btaining
E o btaining s upport for y our p roduct register your product warranty and other service benefits start from the date of purchase, so it is important to register your product quickly to ensure you get full use of the warranty and other service benefits available to you. Warranty and other service b...
Page 144
136 a ppendix e: o btaining s upport for y our p roduct troubleshoot online you will find support tools posted on the 3com web site at http://www.3com.Com/ 3com knowledgebase helps you troubleshoot 3com products. This query-based interactive tool is located at http://knowledgebase.3com.Com and conta...
Page 145
Contact us 137 to send a product directly to 3com for repair, you must first obtain a return authorization number (rma). Products sent to 3com, without authorization numbers clearly marked on the outside of the package, will be returned to the sender unopened, at the sender’s expense. If your produc...
Page 146
138 a ppendix e: o btaining s upport for y our p roduct austria belgium denmark finland france germany hungary ireland israel italy 01 7956 7124 070 700 770 7010 7289 01080 2783 0825 809 622 01805 404 747 06800 12813 1407 3387 1800 945 3794 199 161346 luxembourg netherlands norway poland portugal so...
Page 147: Afety
F s afety i nformation important safety information warning: warnings contain directions that you must follow for your personal safety. Follow all directions carefully. You must read the following safety information carefully before you install or remove the unit. Warning: the access point generates...
Page 148
140 a ppendix f: s afety i nformation warning: rj-45 ports. These are shielded rj-45 data sockets. They cannot be used as telephone sockets. Connect only rj-45 data connectors to these sockets. Wichtige sicherheitshinweise vorsicht: warnhinweise enthalten anweisungen, die sie zu ihrer eigenen sicher...
Page 149
Consignes importantes de sécurité 141 vorsicht: rj-45-anschlüsse. Dies sind abgeschirmte rj-45-datenbuchsen. Sie können nicht als telefonanschlußbuchsen verwendet werden. An diesen buchsen dürfen nur rj-45-datenstecker angeschlossen werden. Consignes importantes de sécurité avertissement: les averti...
Page 150
142 a ppendix f: s afety i nformation avertissement: débranchez l'adaptateur électrique avant de retirer cet appareil. Avertissement: ports rj-45. Il s'agit de prises femelles blindées de données rj-45. Vous ne pouvez pas les utiliser comme prise de téléphone. Branchez uniquement des connecteurs de ...
Page 151: Lossary
G lossary 802.11a the ieee specification for wireless ethernet which allows speeds of up to 54 mbps in the 5ghz range. The standard provides for 6, 12, 24, 36, 48 and 54 mbps data rates. The rates will switch automatically depending on range and environment. 802.11b the ieee specification for wirele...
Page 152
144 g lossary channel similar to any radio device, the officeconnect wireless 108 mbps 11g poe access point allows you to choose different radio channels in the wireless spectrum. A channel is a particular frequency within the 2.4ghz spectrum within which the gateway operates. Client the term used t...
Page 153
G lossary 145 they connect lans of the same type; however they connect more lans than a repeater and are generally more sophisticated. Ieee institute of electrical and electronics engineers. This american organization was founded in 1963 and sets standards for computers and communications. Ietf inte...
Page 154
146 g lossary network a network is a collection of computers and other computer equipment that are connected for the purpose of exchanging information or sharing resources. Networks vary in size, some are within a single room, others span continents. Network interface card (nic) a circuit board inst...
Page 155
G lossary 147 its destination. Ip relates to the address of the end station to which data is being sent, as well as the address of the destination network. Traffic the movement of data packets on a network. Wep wired equivalent privacy. A shared key encryption mechanism for wireless networking. Encr...
Page 156
148 g lossary.
Page 157: Ndex
I ndex numbers 3com access point manager 23, 88 802.1x client authentication 74 a access control 45 backing up trusted list 49 deleting a mac address 47 importing trusted list 47 mac address-based 48 manually adding a trusted station 46 administrator access configuring 79 connection types 80 logon a...
Page 158
150 i ndex viewing 83 m maximum throughput 6 microsoft ias as radius server 63 ca server setup 68 dhcp server setup 65 domain controller setup 63 required services 64 setting up as radius server 70 multiple ssids 13 benefits 13 o output power level 58 p package contents 16 physical features 17 back ...
Page 159
I ndex 151 uam configuring 40 external authentication 42 internal authentication 41 universal access method. See uam v vlan 14 vlan support 44 w wds 7, 8 supported encryption 10 web interface buttons 28 connecting 22 menu 27 navigating 27 tabs 27 timeout setting 28 wep key 40 key index 40 wireless b...
Page 160
152 i ndex.
Page 161
R egulatory n otices c hannel r estrictions use of the officeconnect wireless 108 mbps 11g poe access point is only authorized for the channels approved by each country. For proper installation, log on to the web interface, and then select your country from the drop-down list. Table 1 below details ...
Page 162
Ic s tatement this digital apparatus does not exceed the class b limits for radio noise emissions from digital apparatus set out in the interference-causing equipment standard entitled “digital apparatus”, ices-003 of industry canada. Cet appareil numérique respecte les limites de bruits radioélectr...