- DL manuals
- 3Com
- Switch
- 3CRWX120695A, 3CRWX440095A
- Configuration Manual
3Com 3CRWX120695A, 3CRWX440095A Configuration Manual
Summary of 3CRWX120695A, 3CRWX440095A
Page 1
Http://www.3com.Com/ part no. 730-9502-0071, revision b published april 2005 wireless lan mobility system wireless lan switch and controller configuration guide 3crwx120695a, 3crwx440095a.
Page 2
3com corporation 350 campus drive marlborough, ma usa 01752-3064 copyright © 2004, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without writt...
Page 3: Ontents
C ontents a bout t his g uide conventions 17 documentation 18 documentation comments 19 1 u sing the c ommand -l ine i nterface overview 21 cli conventions 21 command prompts 22 syntax notation 22 text entry conventions and allowed characters 22 user globs, mac address globs, and vlan globs 24 port ...
Page 4: Vlan
Setting the wx switch enable password 37 authenticating at the console 38 customizing aaa with “globs” and groups 39 setting user passwords 39 adding and clearing local users for administrative access 40 configuring accounting for administrative users 40 displaying the aaa configuration 42 saving th...
Page 5: Ip I
4 c onfiguring and m anaging ip i nterfaces and s ervices mtu support 77 configuring and managing ip interfaces 78 adding an ip interface 78 disabling or reenabling an ip interface 78 removing an ip interface 78 displaying ip interface information 78 configuring the system ip address 79 designating ...
Page 6: Map A
Resetting the update interval to the default 97 enabling the ntp client 97 displaying ntp information 97 managing the arp table 98 displaying arp table entries 98 adding an arp entry 99 changing the aging timeout 99 pinging another device 100 logging in to a remote device 100 tracing a route 101 ip ...
Page 7
Radio profiles 133 configuring map access points 136 specifying the country of operation 136 configuring map port parameters 139 configuring a service profile 145 configuring a radio profile 147 configuring radio-specific parameters 154 mapping the radio profile to service profiles 157 assigning a r...
Page 8: Rf A
Changing the tkip countermeasures timer value 181 enabling psk authentication 181 displaying rsn settings 181 assigning the service profile to radios and enabling the radios 181 configuring wep 182 setting static wep key values 183 assigning static wep keys 184 encryption configuration scenarios 185...
Page 9: Igmp S
Configuring port fast convergence 212 displaying port fast convergence information 213 configuring backbone fast convergence 213 displaying the backbone fast convergence state 213 configuring uplink fast convergence 214 displaying uplink fast convergence information 214 displaying spanning tree info...
Page 10: Acl
11 c onfiguring and m anaging s ecurity acl s about security access control lists 231 overview of security acl commands 231 security acl filters 232 creating and committing a security acl 233 setting a source ip acl 233 setting an icmp acl 236 setting tcp and udp acls 238 determining the ace order 2...
Page 11: Aaa
Creating public-private key pairs 262 generating self-signed certificates 262 installing a key pair and certificate from a pkcs #12 object file 263 creating a csr and installing a certificate from a pkcs #7 object file 264 installing a ca’s own certificate 265 displaying certificate and key informat...
Page 12: Radius
Using a custom login page 307 using dynamic fields in webaaa redirect urls 310 configuring last-resort access 312 assigning authorization attributes 313 assigning attributes to users and groups 318 assigning a security acl to a user or a group 319 clearing a security acl from a user or group 320 ass...
Page 13: 802.1X
Deleting radius servers 348 configuring radius server groups 348 creating server groups 349 deleting a server group 351 radius and server group configuration scenario 352 15 m anaging 802.1x on the wx s witch managing 802.1x on wired authentication ports 355 enabling and disabling 802.1x globally 35...
Page 14
Displaying and clearing network sessions 370 displaying verbose network session information 371 displaying and clearing network sessions by username 371 displaying and clearing network sessions by mac address 372 displaying and clearing network sessions by vlan name 373 displaying and clearing netwo...
Page 15: Wx S
Displaying the running configuration 395 saving configuration changes 396 specifying the configuration file to use after the next reboot 396 loading a configuration file 397 resetting to the factory default configuration 397 backing up and restoring the system 398 managing configuration changes 400 ...
Page 16: Radius A
B s upported radius a ttributes attributes 423 supported standard and extended attributes 424 3com vendor-specific attributes 431 c m obility d omain t raffic p orts traffic ports 433 d o btaining s upport for your p roduct register your product 435 purchase value-added services 435 troubleshoot onl...
Page 17: Bout
A bout t his g uide this guide describes the configuration commands for the 3com wireless lan switch wx1200 or 3com wireless lan controller wx4400. This guide is intended for system integrators who are configuring the wx1200 or wx4400. If release notes are shipped with your product and the informati...
Page 18
18 a bout t his g uide this manual uses the following text and syntax conventions: documentation the mss documentation set includes the following documents. Wireless lan switch manager (3wxm) release notes these notes provide information about the system software release, including new features and ...
Page 19
Documentation comments 19 wireless lan switch manager reference manual this manual shows you how to plan, configure, deploy, and manage a mobility system wireless lan (wlan) using the 3com wireless lan switch manager (3wxm). Wireless lan switch and controller installation and basic configuration gui...
Page 20
20 a bout t his g uide.
Page 21: Sing
1 u sing the c ommand -l ine i nterface mobility system software (mss) operates a 3com mobility system wireless lan (wlan) consisting of 3com wireless switch manager software, wireless lan switches (wx1200), wireless lan controllers (wx4400), and managed access points (maps). Mss has a command-line ...
Page 22
22 c hapter 1: u sing the c ommand -l ine i nterface command prompts by default, the mss cli provides the following prompt for restricted users. The mmmm portion shows the switch model number. Wxmmmm> after you become enabled as an administrative user by typing enable and supplying a suitable passwo...
Page 23
Cli conventions 23 3com recommends that you do not use the same name with different capitalizations for vlans or access control lists (acls). For example, do not configure two separate vlans with the names red and red. The cli does not support the use of special characters including the following in...
Page 24
24 c hapter 1: u sing the c ommand -l ine i nterface check the bits that correspond to 1s (ones) in the mask. You specify the wildcard mask in dotted decimal notation. For example, the address 10.0.0.0 and mask 0.255.255.255 match all ip addresses that begin with 10 in the first octet. User globs, m...
Page 25
Cli conventions 25 mac address globs a media access control (mac) address glob is a similar method for matching some authentication, authorization, and accounting (aaa) and forwarding database (fdb) commands to one or more 6-byte mac addresses. In a mac address glob, you can use a single asterisk (*...
Page 26
26 c hapter 1: u sing the c ommand -l ine i nterface matching order for globs in general, the order in which you enter aaa commands determines the order in which mss matches the user, mac address, or vlan to a glob. To verify the order, view the output of the display aaa or display config command. M...
Page 27
Command-line editing 27 command-line editing mss editing functions are similar to those of many other network operating systems. Keyboard shortcuts table 4 lists the keyboard shortcuts available for entering and editing cli commands. History buffer the history buffer stores the last 63 commands you ...
Page 28
28 c hapter 1: u sing the c ommand -l ine i nterface wx1200# display i ifm display interfaces maintained by the interface manager igmp display igmp information interface display interfaces ip display ip information single-asterisk (*) wildcard character you can use the single-asterisk (*) wildcard c...
Page 29
Understanding command descriptions 29 for more information on help, see the help command description in the wireless lan switch and controller command reference . To see a subset of the online help, type the command for which you want more information. For example, the following command displays all...
Page 30
30 c hapter 1: u sing the c ommand -l ine i nterface the command access, which is either enabled or all. All indicates that anyone can access this command. Enabled indicates that you must enter the enable password before entering the command. The command history, which identifies the mss version in ...
Page 31: Onfiguring
2 c onfiguring aaa for a dministrative and l ocal a ccess 3com mobility system software (mss) supports authentication, authorization, and accounting (aaa) for secure network connections. As administrator, you must establish administrative access for yourself and optionally other local users before y...
Page 32
32 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess 5 customized authentication. You can require authentication for all users or for only a subset of users. Username globbing (see “user globs, mac address globs, and vlan globs” on page 24) allows different users or classes of user...
Page 33
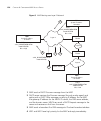
Overview 33 figure 1 typical 3com mobility system wx switch core router layer 2 switches wx switches b uilding 1 d ata center f loor 3 f loor 2 layer 2 or layer 3 switches radius or aaa servers f loor 1 wx switches map map map map map map.
Page 34
34 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess before you start before reading more of this chapter, read the wireless lan switch and controller installation and basic configuration guide for information about setting up a wx switch and the attached map access points for basi...
Page 35
About administrative access 35 about administrative access the authentication, authorization, and accounting (aaa) framework helps secure network connections by identifying who the user is, what the user can access, and the amount of network resources the user can consume. Access modes mss provides ...
Page 36
36 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess first-time configuration via the console administrators must initially configure the wx switch with a computer or terminal connected to the wx console port through a serial cable. Telnet access is not initially enabled. To config...
Page 37
First-time configuration via the console 37 setting the wx switch enable password there is one enable password for the entire wx switch. You can optionally change the enablepassword from the default. 3com recommends that you change the enable password from the default (no password) to prevent unauth...
Page 38
38 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess for connectivity information, see the wireless lan switch and controller installation and basic configuration guide . For 3com wireless switch manager information, see the wireless lan switch manager reference manual . Authentica...
Page 39
First-time configuration via the console 39 customizing aaa with “globs” and groups “globbing” lets you classify users by username or media access control (mac) address for different aaa treatments. A user glob is a string, possibly containing wildcards, for matching aaa and ieee 802.1x authenticati...
Page 40
40 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess adding and clearing local users for administrative access usernames and passwords can be stored locally on the wx switch. 3com recommends that you enforce console authentication after the initial configuration to prevent anyone w...
Page 41
Configuring accounting for administrative users 41 you can select either start-stop or stop-only accounting modes. The stop-only mode sends only stop records, whereas start-stop sends both start and stop records, effectively doubling the number of accounting records. In most cases, stop-only is enti...
Page 42
42 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess displaying the aaa configuration to display your aaa configuration, type the following command: wx1200# display aaa default values authport=1812 acctport=1813 timeout=5 acct-timeout=5 retrans=3 deadtime=0 key=(null) author-pass=(...
Page 43
Administrative aaa configuration scenarios 43 you can also type the load config command, which reloads the wx switch to the last saved configuration or loads a particular configuration filename. (for more information, see “managing configuration files” on page 394.) administrative aaa configuration ...
Page 44
44 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess local authentication for console users and radius authentication for telnet users this scenario illustrates how to enable local authentication for console users and radius authentication for telnet administrative users. To do so,...
Page 45
Administrative aaa configuration scenarios 45 natasha also enables backup radius authentication for telnet administrative users. If the radius server does not respond, the user is authenticated by the local database in the wx switch. Natasha types the following commands: wx1200# set authentication a...
Page 46
46 c hapter 2: c onfiguring aaa for a dministrative and l ocal a ccess.
Page 47: Onfiguring
3 c onfiguring and m anaging p orts and vlan s this chapter describes how to configure and manage ports and vlans. Configuring and managing ports you can configure and display information for the following port parameters: port type name speed and autonegotiation port state power over ethernet (poe)...
Page 48
48 c hapter 3: c onfiguring and m anaging p orts and vlan s all wx switch ports are network ports by default. You must set the port type for ports directly connected to map access ports and to wired user stations that must be authenticated to access the network. When you change port type, mss applie...
Page 49
Configuring and managing ports 49 setting a port for a directly connected map access point before configuring a port as a map access port, you must use the set system countrycode command to set the ieee 802.11 country-specific regulations on the wx switch. (see “specifying the country of operation” ...
Page 50
50 c hapter 3: c onfiguring and m anaging p orts and vlan s you cannot configure any gigabit ethernet port, or port 7 or 8 on a wx1200 switch, as a map port. To manage a map access point on a wx4400 switch, configure a distributed map connection on the switch. (see “configuring for a distributed map...
Page 51
Configuring and managing ports 51 to set ports 4 through 6 for map access point model ap7250 and enable poe on the ports, type the following command: wx1200# set port type ap 4-6 model ap7250 poe enable this may affect the power applied on the configured ports. Would you like to continue? (y/n) [n]y...
Page 52
52 c hapter 3: c onfiguring and m anaging p orts and vlan s the serial id of the ap2750, ap7250, ap8250, or ap8750 might be preceded by 4 digits and a slash (example: 0100/). Do not enter these digits or the slash. The model and radiotype parameters have the same options as they do with the set port...
Page 53
Configuring and managing ports 53 clearing a port to change a port’s type from map access port or wired authentication port, you must first clear the port, then set the port type. Caution: when you clear a port, mss ends user sessions that are using the port. Clearing a port removes all the port’s c...
Page 54
54 c hapter 3: c onfiguring and m anaging p orts and vlan s configuring a port name each wx switch port has a number but does not have a name by default. Setting a port name to set a port name, use the following command: set port port name name you can specify only a single port number with the comm...
Page 55
Configuring and managing ports 55 to display preference settings, use the following command: display port preference [port-list] to set the preference of port 2 on a wx4400 switch to copper and verify the change, type the following commands: wx4400# set port preference 2 rj45 wx4400# display port pr...
Page 56
56 c hapter 3: c onfiguring and m anaging p orts and vlan s to set the port speed on ports 1 and 3 through 5 to 10 mbps, type the following command: wx1200# set port speed 1,3-5 10 gigabit ports — autonegotiation and flow control wx gigabit ports use autonegotiation by default to determine capabilit...
Page 57
Configuring and managing ports 57 resetting a port you can reset a port by toggling its link state and poe state. Mss disables the port’s link and poe (if applicable) for at least one second, then reenables them. This feature is useful for forcing a map access point that is connected to two wx switc...
Page 58
58 c hapter 3: c onfiguring and m anaging p orts and vlan s (for more information about the fields in the output, see the wireless lan switch and controller command reference .) displaying poe state to display the poe state of a port, use the following command: display port poe [port-list] to displa...
Page 59
Configuring and managing ports 59 clearing statistics counters to clear all port statistics counters, use the following command: clear port counters the counters begin incrementing again, starting from 0. Monitoring port statistics you can display port statistics in a format that continually updates...
Page 60
60 c hapter 3: c onfiguring and m anaging p orts and vlan s to monitor port statistics beginning with octet statistics (the default), type the following command: wx1200# monitor port counters as soon as you press enter, mss clears the window and displays statistics at the top of the window. In this ...
Page 61
Configuring and managing ports 61 load sharing a wx switch balances the port group traffic among the group’s physical ports by assigning traffic flows to ports based on the traffic’s source and destination mac addresses. The switch assigns a traffic flow to an individual port and uses the same port ...
Page 62
62 c hapter 3: c onfiguring and m anaging p orts and vlan s to configure a port group named server2 containing ports 2 and 5 and add the ports to the default vlan, type the following commands: wx1200# set port-group name server2 2,5 mode on success: change accepted. Wx1200# set vlan default port ser...
Page 63
Configuring and managing vlans 63 interoperating with cisco systems etherchannel load-sharing port groups are interoperable with cisco systems etherchannel capabilities. To configure a cisco catalyst switch to interoperate with a 3com wx switch, use the following command on the catalyst switch: set ...
Page 64
64 c hapter 3: c onfiguring and m anaging p orts and vlan s a wireless client cannot join a vlan if the physical network ports on the wx switch in the vlan are down. However, a wireless client that is already in a vlan whose physical network ports go down remains in the vlan even though the vlan is ...
Page 65
Configuring and managing vlans 65 vlan names to create a vlan, you must assign a name to it. Vlan names must be globally unique across a mobility domain to ensure the intended user connectivity as determined through authentication and authorization. Every vlan on a wx switch has both a vlan name, us...
Page 66
66 c hapter 3: c onfiguring and m anaging p orts and vlan s 802.1q tagging the tagging capabilities of the wx switch are very flexible. You can assign 802.1q tag values on a per-vlan, per-port basis. The same vlan can have different tag values on different ports. In addition, the same tag value can ...
Page 67
Configuring and managing vlans 67 tunnel affinity (a value that influences tunneling connections for roaming) creating a vlan to create a vlan, use the following command: set vlan vlan-num name name specify a vlan number from 2 to 4095, and specify a name up to 16 alphabetic characters long. Vlan 40...
Page 68
68 c hapter 3: c onfiguring and m anaging p orts and vlan s mss does not remove a port from other vlans when you add the port to a new vlan. If a new vlan causes a configuration conflict with an older vlan, remove the port from the older vlan before adding the port to the new vlan. For example, to a...
Page 69
Configuring and managing vlans 69 to clear port 6, which uses tag value 11, from vlan marigold, type the following command: wx1200# clear vlan marigold port 6 tag 11 this may disrupt user connectivity. Do you wish to continue? (y/n) [n]y success: change accepted. To completely remove vlan ecru, type...
Page 70
70 c hapter 3: c onfiguring and m anaging p orts and vlan s (for information about the fields in the output, see the wireless lan switch and controller command reference .) managing the layer 2 forwarding database a wx switch uses a layer 2 forwarding database (fdb) to forward traffic within a vlan....
Page 71
Managing the layer 2 forwarding database 71 displaying forwarding database information you can display the forwarding database size and the entries contained in the database. Displaying the size of the forwarding database to display the number of entries contained in the forwarding database, use the...
Page 72
72 c hapter 3: c onfiguring and m anaging p orts and vlan s to display all entries that begin with 00, type the following command: wx1200# display fdb 00:* * = static entry. + = permanent entry. # = system entry. Vlan tag dest mac/route des [cos] destination ports [protocol type] ---- ---- ---------...
Page 73
Port and vlan configuration scenario 73 configuring the aging timeout period the aging timeout period specifies how long a dynamic entry can remain unused before the software removes the entry from the database. You can change the aging timeout period on an individual vlan basis. You can change the ...
Page 74
74 c hapter 3: c onfiguring and m anaging p orts and vlan s success: change accepted. Wx1200# set port 5-6 name lobby success: change accepted. Wx1200# set port 7-8 name conf_room1 success: change accepted. Wx1200# display port status port name admin oper config actual type media ===================...
Page 75
Port and vlan configuration scenario 75 would you like to continue? (y/n) [n]y success: change accepted. Wx1200# display port status port name admin oper config actual type media =============================================================================== 1 mgmt up up auto 100/full network 10/100...
Page 76
76 c hapter 3: c onfiguring and m anaging p orts and vlan s port group: backbonelink is up ports: 7, 8 6 add port 1 to the default vlan (vlan 1) and verify the configuration change. Type the following commands: wx1200# set vlan default port 1 success: change accepted. Wx1200# display vlan config adm...
Page 77: Onfiguring
4 c onfiguring and m anaging ip i nterfaces and s ervices this chapter describes how to configure ip interfaces and services. Mtu support mobility system software (mss) supports standard maximum transmission units (mtus) of 1514 bytes for standard ethernet packets and 1518 bytes for ethernet packets...
Page 78
78 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices configuring and managing ip interfaces many features, including the following, require an ip interface on the wx switch: management access through telnet access by 3com wireless switch manager exchanging information and user data...
Page 79
Configuring the system ip address 79 configuring the system ip address you can designate one of the ip addresses configured on a wx switch to be the system ip address of the switch. The system ip address determines the interface or source ip address mss uses for system tasks, including the following...
Page 80
80 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices a destination can be a subnet or network. If two static routes specify a destination, the more specific route is always chosen (longest prefix match). For example, if you have a static route with a destination of 10.10.1.0/24, an...
Page 81
Configuring and managing ip routes 81 0.0.0.0/ 0 static 1 router 10.0.1.17 vlan:1:ip 0.0.0.0/ 0 static 2 router 10.0.2.17 vlan:2:ip 10.0.1.1/24 ip 0 direct vlan:1:ip 10.0.1.1/32 ip 0 local vlan:1:ip:10.0.1.1/24 10.0.1.255/32 ip 0 local vlan:1:ip:10.0.1.1/24 10.0.2.1/24 ip 0 direct vlan:2:ip 10.0.2.1...
Page 82
82 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices 0.0.0.0/ 0 static 1 router 10.0.1.17 down 0.0.0.0/ 0 static 2 router 10.0.2.17 vlan:2:ip 10.0.2.1/24 ip 0 direct vlan:2:ip 10.0.2.1/32 ip 0 direct vlan:2:ip:10.0.1.1/24 10.0.2.255/32 ip 0 direct vlan:2:ip:10.0.1.1/24 224.0.0.0/ 4...
Page 84
84 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices login timeouts when you access the ssh server on a wx switch, mss allows you 10 seconds to press enter for the username prompt. After the username prompt is displayed, mss allows 30 seconds to enter a valid username and password ...
Page 85
Managing the management services 85 to generate a 1024-byte ssh authentication key, type the following command: wx1200# crypto generate key ssh 1024 key pair generated you can verify the key using the following command: display crypto key ssh for example: wx1200# display crypto key ssh ec:6f:56:7f:d...
Page 86
86 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices changing the ssh service port number to change the ssh port the wx switch listens on for ssh connections, use the following command: set ip ssh port port-num caution: if you change the ssh port number from an ssh session, mss imm...
Page 88
88 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices to display the telnet server status and the tcp port number on which a wx switch listens for telnet traffic, type the following command: wx1200> display ip telnet server status port ---------------------------------- enabled 3 ch...
Page 90
90 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices if a browser connects to a wx switch from behind a proxy, then only the proxy ip address is shown. If multiple browsers connect using the same proxy, the proxy address appears only once in the output. Configuring and managing dns...
Page 91
Configuring and managing dns 91 configuring a default domain name you can configure a single default domain name for dns queries. The wx switch appends the default domain name to hostnames you enter in commands. For example, you can configure the wx switch to automatically append the domain name exa...
Page 92
92 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices (for information about the fields in the output, see the wireless lan switch and controller command reference .) configuring and managing aliases an alias is a string that represents an ip address. You can use aliases as shortcut...
Page 93
Configuring and managing time parameters 93 configuring and managing time parameters you can configure the system time and date statically or by using network time protocol (ntp) servers. In each case, you can specify the offset from coordinated universal time (utc) by setting the time zone. You als...
Page 94
94 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices to set the time zone to pst (pacific standard time), type the following command: wx1200# set timezone pst -8 timezone is set to 'pst', offset from utc is -8:0 hours. Displaying the time zone to display the time zone, use the foll...
Page 95
Configuring and managing time parameters 95 displaying the summertime period to display the summertime period, use the following command: display summertime for example, to display the summertime period, type the following command: wx1200# display summertime summertime is enabled, and set to 'pdt'. ...
Page 96
96 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices displaying the time and date to display the time and date, use the following command: display timedate for example: wx1200# display timedate sun feb 29 2004, 23:58:02 pst configuring and managing ntp the network time protocol (nt...
Page 97
Configuring and managing time parameters 97 adding an ntp server to add an ntp server to the list of ntp servers, use the following command: set ntp server ip-addr to configure a wx switch to use ntp server 192.168.1.5, type the following command: wx1200# set ntp server 192.168.1.5 removing an ntp s...
Page 98
98 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices ntp client: enabled current update-interval: 20(secs) current time: sun feb 29 2004, 23:58:12 timezone is set to 'pst', offset from utc is -8:0 hours. Summertime is enabled. Last ntp update: sun feb 29 2004, 23:58:00 ntp server p...
Page 99
Managing the arp table 99 this example shows two entries. The local entry (with local in the type field) is for the wx switch itself. The mac address of the local entry is the switch’s mac address. The arp table contains one local entry for each vlan configured on the switch. The dynamic entry is le...
Page 100
100 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices to reset the arp aging timeout to its default value, use the set arp agingtime 1200 command. Pinging another device to verify that another device in the network can receive ip packets sent by the wx switch, use the following com...
Page 101
Tracing a route 101 3com corporation. Username: when you press ctrl+t or type exit to end the client session, the management session returns to the local wx prompt: wx1200-remote> session 0 pty tty2.D terminated tt name tty2.D wx1200# use the following commands to manage telnet client sessions: disp...
Page 102
102 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices the traceroute facility determines the address of the first hop by examining the source address field of the icmp time-exceeded message. To identify the next hop, traceroute again sends a udp packet, but this time with a ttl val...
Page 103
Ip interfaces and services configuration scenario 103 ip interfaces and services configuration scenario this scenario configures ip interfaces, assigns one of the interfaces to be the system ip address, and configures a default route, dns parameters, and time and date parameters. 1 configure ip inte...
Page 104
104 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices =============================================================================== 3 configure a default route through a gateway router attached to the wx switch and verify the configuration change. Type the following commands: wx1...
Page 105
Ip interfaces and services configuration scenario 105 wx1200# display summertime summertime is enabled, and set to 'pdt'. Start : sun apr 04 2004, 02:00:00 end : sun oct 31 2004, 02:00:00 offset : 60 minutes recurring : yes, starting at 2:00 am of first sunday of april and ending at 2:00 am on last ...
Page 106
106 c hapter 4: c onfiguring and m anaging ip i nterfaces and s ervices.
Page 107: Onfiguring
5 c onfiguring and m anaging m obility d omain r oaming a mobility domain is a system of wx switches and managed access points (maps) working together to support roaming wireless users (clients). Tunnels and virtual ports between the wx switches in a mobility domain allow users to roam without any d...
Page 108
108 c hapter 5: c onfiguring and m anaging m obility d omain r oaming configuring a mobility domain the wx switches in a mobility domain use their system ip address for mobility domain communication. To support the services of the mobility domain, the system ip address of every wx switch requires ba...
Page 109
Configuring a mobility domain 109 configuring member wx switches on the seed to configure the list of members on the mobility domain seed for distribution to other member wx switches, use the following command on the seed wx switch: set mobility-domain member ip-addr for example, the following comma...
Page 110
110 c hapter 5: c onfiguring and m anaging m obility d omain r oaming wx1200# display mobility-domain status mobility domain name: pleasanton member state status --------------- ------------- -------------- 192.168.12.7 state_up member 192.168.14.6 state_up seed 192.168.15.5 state_up member displayi...
Page 111
Monitoring the vlans and tunnels in a mobility domain 111 this command has no effect if the wx switch member is not configured as part of a mobility domain or the current wx switch is not the seed. Monitoring the vlans and tunnels in a mobility domain tunnels connect wx switches. Tunnels are formed ...
Page 112
112 c hapter 5: c onfiguring and m anaging m obility d omain r oaming displaying roaming vlans and their affinities the command display roaming vlan displays all vlans in the mobility domain, the wx switches servicing the vlans, and their tunnel affinity values configured on each switch for the vlan...
Page 113
Understanding the sessions of roaming users 113 understanding the sessions of roaming users when a wireless client successfully roams from one map to another, its sessions are affected in the following ways: the wx treats this client session as a roaming session and not a new session. Radius account...
Page 114
114 c hapter 5: c onfiguring and m anaging m obility d omain r oaming if the client changes its encryption type or vlan name, mss might record a new session rather than a roamed session. Effects of timers on roaming an unsuccessful roaming attempt might be caused by the following timers. You cannot ...
Page 115
Mobility domain scenario 115 wx1200> display sessions network verbose user sess ip or mac vlan port/ name id address name radio ------------------------------ ---- ----------------- --------------- ----- shuttle2\exmpl 6* 10.3.8.55 default 3/1 client mac: 00:06:25:13:08:33 gid: sess-4-000404-98441-c...
Page 116
116 c hapter 5: c onfiguring and m anaging m obility d omain r oaming 5 to display the mobility domain configuration, type the following command: wx1200# display mobility-domain config this wx is the seed for domain sunflower. 192.168.253.11 is a member 192.168.111.112 is a member 6 to display the w...
Page 117: Onfiguring
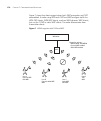
6 c onfiguring map a ccess p oints map access points contain radios that provide networking between your wired network and ieee 802.11 wireless users. A map access point connects to the wired network through a 10/100 ethernet link and connects to wireless users through radio signals. Map overview fi...
Page 118
118 c hapter 6: c onfiguring map a ccess p oints figure 2 example 3com network to configure map access points, perform the following tasks, in this order: specify the country of operation. Configure map access ports, distributed ap connections, and dual homing. If required, configure radio-specific ...
Page 119
Map overview 119 you do not need to set channels and power if you use rf auto-tuning to set these values. You do not need to specify an external antenna type unless a radio uses an external antenna. Configure ssid and encryption settings in a service profile. Map the service profile to a radio profi...
Page 120
120 c hapter 6: c onfiguring map a ccess p oints distributed map network requirements because distributed maps are not directly attached to a wx, they require additional support from the network in order to function. Information on the booting and operation sequence for distributed maps is covered i...
Page 121
Map overview 121 distributed maps and stp a distributed map is a leaf device. You do not need to enable stp on the port that is directly connected to the map. If spanning tree protocol (stp) is enabled on the port that is directly connected to a distributed map, you might need to change the stp conf...
Page 122
122 c hapter 6: c onfiguring map a ccess p oints resiliency and dual-homing options for maps maps can support a wide variety of resiliency options. Redundancy for data link connections and for wx services can be provided to the map. Bias on a wx switch, configurations for maps have a bias (low or hi...
Page 123
Map overview 123 if more than one switch has high bias, or the bias for all connections is the same, the switch that has the greatest capacity to add more active maps is preferred. For example, if one switch has 50 active maps while another switch has 60 active maps, and both switches are capable of...
Page 124
124 c hapter 6: c onfiguring map a ccess p oints continuing the dhcp process, map sends a dhcp request to one of the dhcp servers that sent an offer message, and receives an ack from the server. Map then configures itself with the information contained in the offer message from that server. 3 map se...
Page 125
Map overview 125 7 the wx that receives the find wx request determines the best wx for the map to use, based on the bias settings for the map on each switch. If more than one switch has high bias for the map or all switches have the same bias, the wx suggests the switch that has the highest capacity...
Page 126
126 c hapter 6: c onfiguring map a ccess p oints figure 3 map booting over layer 2 network 1 map sends a dhcp discover message from the map. 2 dhcp server receives the discover message (through a relay agent) and replies with a dhcp offer message containing ip address for the map, the gateway ip add...
Page 127
Map overview 127 5 map boots with software image and configuration from wx1 because it has fewer active map connections than wx3. Example map boot over layer 3 network figure 4 shows an example of the boot process for a map connected through a layer 3 network. Figure 4 map booting over layer 3 netwo...
Page 128
128 c hapter 6: c onfiguring map a ccess p oints 4 find wx message times out. Map then sends a dns request for 3comwx.Example.Com. 5 dns server sends the system ip address of the wx switch mapped to 3comwx.Example.Com. In this example, the address is for wx1. 6 map sends a unicast find wx message to...
Page 129
Map overview 129 (to configure a load-balancing group, see “configuring a load-balancing group” on page 144.) service profiles a service profile controls advertisement and encryption for an ssid. You can specify the following: whether ssids that use the service profile are beaconed whether the ssids...
Page 130
130 c hapter 6: c onfiguring map a ccess p oints cipher-wep40 disable does not use wep with 40-bit keys to encrypt traffic sent to wpa clients. Psk-phrase no passphrase defined uses dynamically generated keys rather than statically configured keys to authenticate wpa clients. Psk-raw no preshared ke...
Page 131
Map overview 131 (to configure a service profile, see “configuring a service profile” on page 145.) public and private ssids each radio can support the following types of ssids: encrypted ssid — clients using this ssid must use encryption. Use the encrypted ssid for secured access to your enterprise...
Page 132
132 c hapter 6: c onfiguring map a ccess p oints table 10 mac address allocations on map access points map access point model address allocation ethernet ports all models ethernet port 1 equals the map base mac address. Ethernet port 2 (if the map model has one) equals the map base mac address + 1. ...
Page 133
Map overview 133 models mp-101 and mp-122 are assigned blocks of four mac addresses each. Each radio on models mp-101 and mp-122 is assigned one mac address, which is shared by both the clear ssid and the encrypted ssid. Encryption encrypted ssids can use the following encryption methods: wi-fi prot...
Page 134
134 c hapter 6: c onfiguring map a ccess p oints (to configure a radio profile, see “configuring a radio profile” on page 147.) rf auto-tuning the rf auto-tuning feature dynamically assigns channel and power settings to map radios, and adjusts those settings when needed. Rf auto-tuning can perform t...
Page 135
Map overview 135 assign initial channel and power settings when a map radio is started. Periodically assess the rf environment and change the channel or power setting if needed. Change the transmit data rate or power to maintain at least the minimum data rate with all associated clients. By default,...
Page 136
136 c hapter 6: c onfiguring map a ccess p oints although these parameters have default values, 3com recommends that you change the values for each radio for optimal performance. For example, leaving the channel number on each radio set to its default value can result in high interference among the ...
Page 137
Configuring map access points 137 set system countrycode code for the country, you can specify one of the codes listed in table 13. Table 13 country codes country code australia au austria at belgium be brazil br canada ca china cn czech republic cz denmark dk finland fi france fr germany de greece ...
Page 138
138 c hapter 6: c onfiguring map a ccess p oints the current software version might not support all of the countries listed here. To verify the configuration change, use the following command: display system the following commands set the country code to us (united states) and verify the setting: po...
Page 139
Configuring map access points 139 wx1200# set system countrycode us success: change accepted. Wx1200# display system =============================================================================== product name: wx1200 system name: wx1200 system countrycode: us system location: system contact: system...
Page 140
140 c hapter 6: c onfiguring map a ccess p oints (for information about configuring rf auto-tuning settings on a radio, see chapter 8, “configuring rf auto-tuning,” on page 193.) table 14 lists how many maps you can configure on a wx switch, and how many maps a switch can boot. The numbers are for d...
Page 141
Configuring map access points 141 you cannot configure port 7 or 8 on a wx1200 switch, or any gigabit ethernet port, as a map port. To manage a map access point on a wx4400 switch, configure a distributed map connection on the switch. (see “configuring an indirectly connected map” on page 142.) to s...
Page 142
142 c hapter 6: c onfiguring map a ccess p oints antennatype command. (see “configuring the external antenna model” on page 156.) map radios configured for 802.11g also allow associations from 802.11b clients by default. (to disable support for 802.11b associations, see “disabling 802.11b client ass...
Page 143
Configuring map access points 143 supply power to an indirectly connected map, the set dap command does not use the poe parameter. To configure distributed map connection 2 for map model ap2750 with serial-id m9de48b123400 and radio type 802.11a, type the following command: wx1200# set dap 2 serial-...
Page 144
144 c hapter 6: c onfiguring map a ccess p oints changing map names the default name of a directly attached map is based on the port number of the map access port attached to the map. For example, the default name for a map on map access port 1 is map01. The default name of a distributed map is base...
Page 145
Configuring map access points 145 disabling or reenabling automatic firmware upgrades a map can automatically upgrade its boot firmware by loading the upgrade version of the firmware from a wx switch when the map is booting. Automatic firmware upgrades are enabled by default. To disable or reenable ...
Page 146
146 c hapter 6: c onfiguring map a ccess p oints (to display service profile information, see “displaying service profile information” on page 161.) to create a service profile and assign an ssid to it, use the following command: set service-profile name ssid-name ssid-name an ssid can be up to 32 a...
Page 148
148 c hapter 6: c onfiguring map a ccess p oints to assign the profile to one or more radios, use the set ap radio radio-profile command. (see “assigning a radio profile and enabling radios” on page 157.) changing radio parameters to change individual parameters controlled by a radio profile, use th...
Page 149
Configuring map access points 149 to change the dtim interval, use the following command: set radio-profile name dtim-interval interval the interval can be a value from 1 through 31. The default is 1. To change the dtim interval for radio profile rp1 to 2, type the following command: wx1200# set rad...
Page 150
150 c hapter 6: c onfiguring map a ccess p oints set radio-profile name frag-threshold threshold the threshold can be a value from 256 through 2346. The default is 2346. To change the fragmentation threshold for radio profile rp1 to 1500 bytes, type the following command: wx1200# set radio-profile r...
Page 151
Configuring map access points 151 can remain in buffer memory. To change the maximum receive lifetime, use the following command: set radio-profile name max-rx-lifetime time the time can be from 500 ms (0.5 second) through 250,000 ms (250 seconds). The default is 2000 ms (2 seconds). To change the m...
Page 152
152 c hapter 6: c onfiguring map a ccess p oints to guard against interference, an 802.11b/g radio in protection mode sends messages while 802.11g traffic at higher data rates is being sent, to inform 802.11b devices about the 802.11g traffic and reserve bandwidth for the traffic. Protection mode re...
Page 153
Configuring map access points 153 changing the preamble length value affects only the support advertised by the radio. Regardless of the preamble length setting (short or long), an 802.11b/g radio accepts and can generate 802.11b/g frames with either short or long preambles. If any client associated...
Page 154
154 c hapter 6: c onfiguring map a ccess p oints to disable the radios that are using radio profile rp1 and reset the beaconed-ssid parameter to its default value, type the following commands: wx1200# set radio-profile rp1 mode disable wx1200# clear radio-profile rp1 beaconed-ssid success: change ac...
Page 156
156 c hapter 6: c onfiguring map a ccess p oints configuring the external antenna model the mp-372 has connectors for attaching optional external 802.11a or 802.11b/g antennas. The 802.11b/g radios in map models mp-341 and mp-352 have an internal antenna but can use an external antenna. The mp-262 8...
Page 157
Disabling or reenabling radios 157 mapping the radio profile to service profiles to assign ssids to radios, you must map the service profiles for the ssids to the radio profile that is assigned to the radios. To map a radio profile to a service profile, use the following command: set radio-profile n...
Page 158
158 c hapter 6: c onfiguring map a ccess p oints to disable radio 2 on port 3 and 6, type the following command: wx1200# set ap 3,6 radio 2 mode disable success: change accepted. Disabling or reenabling all radios using a profile to disable or reenable all radios that are using a radio profile, use ...
Page 160
160 c hapter 6: c onfiguring map a ccess p oints to display configuration information for a distributed map access point configured on connection 1, type the following command: wx1200# display dap config 1 dap 1: serial-id: m9de48b012f00, map model: ap2750, bias: high, name: dap1 boot-download-enabl...
Page 161
Displaying map information 161 more information, see “resiliency and dual-homing options for maps” on page 122 and “map boot process” on page 123.) the dap field indicates the connection number of each map on the wx switch on which the command is typed. A hyphen ( - ) in the dap field indicates that...
Page 162
162 c hapter 6: c onfiguring map a ccess p oints to display information for service profile wpa_clients, type the following command: wx1200# display service-profile wpa_clients ssid-name: 3com ssid-type: crypto beacon: yes auth-fallthru: web-auth wep key 1 value: wep key 2 value: wep key 3 value: we...
Page 163
Displaying map information 163 the all option for the display ap status command displays information for all directly attached map access points and all distributed map access points configured on the switch. The following command displays the status of a distributed map access point: wx1200# displa...
Page 164
164 c hapter 6: c onfiguring map a ccess p oints wx1200# display ap counters 6 port: 6 radio: 1 ================================= lastpktxferrate 2 pkttxcount 91594255 numcntinpwrsave 4294966683 multipktdrop 0 lastpktrxsigstrength -54 multibytdrop 0 lastpktsignoiseratio 40 user sessions 5 tkip pkt t...
Page 165: Onfiguring
7 c onfiguring u ser e ncryption mobility system software (mss) encrypts wireless user traffic for all users who are successfully authenticated to join an encrypted ssid and who are then authorized to join a vlan. Overview mss supports the following types of encryption for wireless user traffic: wi-...
Page 166
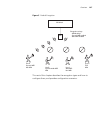
166 c hapter 7: c onfiguring u ser e ncryption the ssid type must be crypto (encrypted) for encryption to be used. If the ssid type is clear, wireless traffic is not encrypted, regardless of the encryption settings. Mss does not encrypt traffic in the wired part of the network. Mss does not encrypt ...
Page 167
Overview 167 figure 5 default encryption this rest of this chapter describes the encryption types and how to configure them, and provides configuration scenarios. Encryption settings: -wpa disabled -dynamic wep enabled -static wep disabled user d tkip wpa user c static wep non-wpa user b dynamic 40-...
Page 168
168 c hapter 7: c onfiguring u ser e ncryption configuring wpa wi-fi protected access (wpa) is a security enhancement to the ieee 802.11 wireless standard. Wpa provides enhanced encryption with new cipher suites and provides per-packet message integrity checks. Wpa is based on the 802.11i standard. ...
Page 169
Configuring wpa 169 figure 6 shows the client support when wpa encryption for tkip only is enabled. A radio using wpa with tkip encrypts traffic only for wpa tkip clients but not for ccmp or wep clients. The radio disassociates from these other clients. Figure 6 wpa encryption with tkip only encrypt...
Page 170
170 c hapter 7: c onfiguring u ser e ncryption figure 7 shows the client support when both wep encryption and tkip are enabled. A radio using wpa with tkip and wep encrypts traffic for wpa tkip clients, wpa wep clients, and non-wpa dynamic wep clients, but not for ccmp or static wep clients. The rad...
Page 171
Configuring wpa 171 tkip countermeasures wpa access points and clients verify the integrity of a wireless frame received on the network by generating a keyed message integrity check (mic). The michael mic used with tkip provides a holddown mechanism to protect the network against tampering. If the r...
Page 172
172 c hapter 7: c onfiguring u ser e ncryption wpa authentication methods you can configure an ssid to support one or both of the following authentication methods for wpa clients: 802.1x — the map access point and client use an extensible authentication protocol (eap) method to authenticate one anot...
Page 173
Configuring wpa 173 probe response (sent by a map radio) — the wpa ie in a probe response frame lists the same wpa information that is contained in the beacon frame. Association request or reassociation (sent by a client) — the wpa ie in an association request lists the authentication method and cip...
Page 174
174 c hapter 7: c onfiguring u ser e ncryption table 18 lists the encryption support for wpa and non-wpa clients. Configuring wpa to configure map access point radios to support wpa: 1 create a service profile for each ssid that will support wpa clients. 2 enable the wpa ie in the service profile. 3...
Page 175
Configuring wpa 175 to create a new service profile named wpa, type the following command: wx1200# set service-profile wpa success: change accepted. Enabling wpa to enable wpa, you must enable the wpa information element (ie) in the service profile. To enable the wpa ie, use the following command: s...
Page 176
176 c hapter 7: c onfiguring u ser e ncryption changing the tkip countermeasures timer value by default, mss enforces tkip countermeasures for 60,000 ms (60 seconds) after a second mic failure within a one-minute interval. To change the countermeasures timer value, use the following command: set ser...
Page 177
Configuring wpa 177 ?=+&% the quick brown fox jumps over the lazy sl" success: change accepted. As an alternative to entering a passphrase, which mss converts into a key, you can enter the key itself in raw hexadecimal format. To enter a psk key in raw format, use the following command: set service-...
Page 178
178 c hapter 7: c onfiguring u ser e ncryption wep key 1 value: wep key 2 value: wep key 3 value: wep key 4 value: wep unicast index: 1 wep multicast index: 1 shared key auth: no wpa enabled: ciphers: cipher-tkip, cipher-wep40 authentication: 802.1x tkip countermeasures time: 30000ms the wpa setting...
Page 179
Configuring wpa2 179 configuring wpa2 robust security network (rsn) provides wpa2 support. Wpa2 is based on the final ieee 802.11i amendment to the 802.11 standard. The primary difference between wpa and wpa2 is the type of encryption used. Wpa uses rc4 encryption (tkip) and wpa2 generally uses aes ...
Page 180
180 c hapter 7: c onfiguring u ser e ncryption to enable rsn in service profile wpa, type the following command: wx1200# set service-profile rsn rsn-ie enable success: change accepted. Specifying the rsn cipher suites to use rsn, at least one cipher suite must be enabled. You can enable one or more ...
Page 181
Configuring wpa2 181 changing the tkip countermeasures timer value to change the tkip countermeasures timer, see “changing the tkip countermeasures timer value” on page 181. The procedure is the same for wpa and rsn. Enabling psk authentication to enable psk authentication, see “enabling psk authent...
Page 182
182 c hapter 7: c onfiguring u ser e ncryption configuring wep wired-equivalent privacy (wep) is a security protocol defined in the 802.11 standard. Wep uses the rc4 encryption algorithm to encrypt data. To provide integrity checking, wep access points and clients check the integrity of a frame’s cy...
Page 183
Configuring wep 183 figure 8 shows an example of a radio configured to provide static and dynamic wep encryption for non-wpa clients. The radio uses dynamically generated keys to encrypt traffic for dynamic wep clients. The radio also encrypts traffic for static wep clients whose keys match the keys...
Page 184
184 c hapter 7: c onfiguring u ser e ncryption to set the value of a wep key, use the following command: set service-profile name wep key-index num key value the key-index num parameter specifies the index you are configuring. You can specify a value from 1 through 4. The key value parameter specifi...
Page 185
Encryption configuration scenarios 185 encryption configuration scenarios the following scenarios provide examples of ways in which you can configure encryption for network clients: “enabling wpa with tkip” on page 185 “enabling dynamic wep in a wpa network” on page 187 “configuring encryption for m...
Page 186
186 c hapter 7: c onfiguring u ser e ncryption wx1200# display service-profile wpa ssid-name: mycorp ssid-type: crypto beacon: yes auth-fallthru: last-resort wep key 1 value: wep key 2 value: wep key 3 value: wep key 4 value: wep unicast index: 1 wep multicast index: 1 shared key auth: no wpa enable...
Page 187
Encryption configuration scenarios 187 enabling dynamic wep in a wpa network the following example shows how to configure mss to provide authentication and encryption for 801.X dynamic wep clients, and for 801.X wpa clients using tkip. This example assumes that pass-through authentication is used fo...
Page 188
188 c hapter 7: c onfiguring u ser e ncryption wx1200# display service-profile wpa-wep ssid-name: mycorp ssid-type: crypto beacon: yes auth-fallthru: last-resort wep key 1 value: wep key 2 value: wep key 3 value: wep key 4 value: wep unicast index: 1 wep multicast index: 1 long preamble: yes shared ...
Page 189
Encryption configuration scenarios 189 configuring encryption for mac clients the following example shows how to configure mss to provide psk authentication and tkip or 40-bit wep encryption for mac clients: 1 create an authentication rule that sends all mac users of ssid voice to the local database...
Page 190
190 c hapter 7: c onfiguring u ser e ncryption 5 create a service profile named wpa-wep-for-mac for ssid voice. Type the following command: wx1200# set service-profile wpa-wep-for-mac success: change accepted. 6 set the ssid in the service profile to voice. Type the following command: wx1200# set se...
Page 191
Encryption configuration scenarios 191 11 display the wpa configuration changes. Type the following command: wx1200# display service-profile wpa-wep-for-mac ssid-name: voice ssid-type: crypto beacon: yes auth-fallthru: last-resort wep key 1 value: wep key 2 value: wep key 3 value: wep key 4 value: w...
Page 192
192 c hapter 7: c onfiguring u ser e ncryption 14 save the configuration. Type the following command: wx1200# save config success: configuration saved..
Page 193: Onfiguring
8 c onfiguring rf a uto -t uning the rf auto-tuning feature dynamically assigns channel and power settings to map radios, and adjusts those settings when needed. Overview rf auto-tuning can perform the following tasks: assign initial channel and power settings when a map radio is started. Periodical...
Page 194
194 c hapter 8: c onfiguring rf a uto -t uning initial channel assignment — mss determines a radio’s initial channel based on rssi values, interference levels on each valid channel, and other parameters. Mss periodically reevaluates the channel and changes it if needed. Initial power assignment — th...
Page 195
Overview 195 power tuning by default, the switch evaluates the scan results for possible power changes every 300 seconds (5 minutes), and raises or lowers the default power level if needed. A radio can temporarily increase its power level from the default at any time to correct either of the followi...
Page 196
196 c hapter 8: c onfiguring rf a uto -t uning utilization, calculated based on the number of multicast packets per second that a radio can send on a channel while continuously sending fixed-size frames over a period of time. Phy error count, which is the number of frames received by the map radio t...
Page 197
Overview 197 rf auto-tuning parameters table 19 lists the rf auto-tuning parameters and their default settings. Table 19 defaults for rf auto-tuning parameters parameter default value radio behavior when parameter set to default value radio profile parameters channel-config enable when the radio is ...
Page 198
198 c hapter 8: c onfiguring rf a uto -t uning changing rf auto-tuning settings you can change the following rf auto-tuning settings: channel tuning power tuning minimum transport data rate changing channel tuning settings disabling or reenabling channel tuning rf auto-tuning for channels is enabled...
Page 199
Changing rf auto-tuning settings 199 to change the channel tuning interval, use the following command: set radio-profile name auto-tune channel-interval seconds to set the channel tuning interval for radios in radio profile rp2 to 2700 seconds (45 minutes), type the following command: wx1200# set ra...
Page 200
200 c hapter 8: c onfiguring rf a uto -t uning to set the power tuning interval for radios in radio profile rp2 to 240 seconds, type the following command: wx1200# set radio-profile rp2 auto-tune power-interval 240 success: change accepted. Changing the power backoff interval the default power backo...
Page 201
Displaying rf auto-tuning information 201 for example, to change the max-retransmissions threshold to 20 percent for radio 1 on the directly connected map access port on port 6, type the following command: wx1200# set ap 6 radio 1 auto-tune max-retransmissions 20 success: change accepted. Changing t...
Page 202
202 c hapter 8: c onfiguring rf a uto -t uning to display the rf auto-tuning and other settings in the default radio profile, type the following command: wx1200# display radio-profile default beacon interval: 100 dtim interval: 1 max tx lifetime: 2000 max rx lifetime: 2000 rts threshold: 2346 frag t...
Page 204
204 c hapter 8: c onfiguring rf a uto -t uning.
Page 205: Onfiguring
9 c onfiguring and m anaging s panning t ree p rotocol the purpose of the spanning tree protocol (stp) is to maintain a loop-free network. A loop-free path is accomplished when a device recognizes a loop in the topology and blocks one or more redundant paths. Overview mobility system software (mss) ...
Page 207
Changing standard spanning tree parameters 207 port cost port cost is a numeric value that stp adds to the total cost of a path to the root bridge. When a designated bridge has multiple equal-cost paths to the root bridge, the designated bridge uses the path with the lowest total cost. You can set t...
Page 208
208 c hapter 9: c onfiguring and m anaging s panning t ree p rotocol to change the bridge priority of vlan pink to 69, type the following command: wx1200# set spantree priority 69 vlan pink success: change accepted. Changing stp port parameters you can change the stp cost and priority of an individu...
Page 209
Changing standard spanning tree parameters 209 the command applies only to the ports you specify. The port cost on other ports remains unchanged. To reset the cost of ports 3 and 4 in the default vlan to the default value, type the following command: wx1200# clear spantree portcost 3-4 success: chan...
Page 212
212 c hapter 9: c onfiguring and m anaging s panning t ree p rotocol port fast convergence port fast convergence bypasses both the listening and learning stages and immediately places a port in the forwarding state. You can use port fast convergence on ports that are directly connected to servers, h...
Page 213
Configuring and managing stp fast convergence features 213 displaying port fast convergence information to display port fast convergence information, use the following command: display spantree portfast [port-list] to display port fast convergence information for all ports, type the following comman...
Page 215
Displaying spanning tree information 215 port list or a vlan name or number. For each vlan, only the ports contained in the vlan are listed in the command output. To list only the ports that are in the active (forwarding) state, enter the active option. To display stp information for vlan mauve, typ...
Page 216
216 c hapter 9: c onfiguring and m anaging s panning t ree p rotocol this command displays the same information as the display spantree command’s cost field in a concise format for all vlans. The display spantree command lists all the stp information separately for each vlan. To display the stp port...
Page 217
Displaying spanning tree information 217 designated_root 00-0b-0e-00-04-30 designated cost 0x0 designated_bridge 00-0b-0e-00-04-30 designated_port 38 top_change_ack false config_pending false port_inconsistency none port based information statistics config bpdu's xmitted(port/vlan) 0 (1) config bpdu...
Page 218
218 c hapter 9: c onfiguring and m anaging s panning t ree p rotocol last topology change occurred: tue jul 01 2003 22:33:36. Topology change false topology change time 35 topology change detected false topology change count 1 topology change last recvd. From 00-0b-0e-02-76-f6 other port specific in...
Page 219
Spanning tree configuration scenario 219 spanning tree configuration scenario this scenario configures a vlan named backbone for a wx switch's connections to the network backbone, adds ports 1 and 2 to the vlan, and enables stp on the vlan to prevent loops. 1 remove the network cables from ports 1 a...
Page 220
220 c hapter 9: c onfiguring and m anaging s panning t ree p rotocol wx1200# display spantree vlan 10 vlan 10 spanning tree mode pvst+ spanning tree type ieee spanning tree enabled designated root 00-0b-0e-00-04-0c designated root priority 32768 designated root path cost 0 we are the root root max a...
Page 221
Spanning tree configuration scenario 221 wx1200# display spantree vlan 10 vlan 10 spanning tree mode pvst+ spanning tree type ieee spanning tree enabled designated root 00-0b-0e-00-04-0c designated root priority 32768 designated root path cost 0 we are the root root max age 20 sec hello time 2 sec f...
Page 222
222 c hapter 9: c onfiguring and m anaging s panning t ree p rotocol.
Page 223: Onfiguring
10 c onfiguring and m anaging igmp s nooping internet group management protocol (igmp) snooping controls multicast traffic on a wx switch by forwarding packets for a multicast group only on the ports that are connected to members of the group. A multicast group is a set of ip hosts that receive traf...
Page 225
Changing igmp timers 225 robustness value — number used as a multiplier to adjust the igmp timers to the amount of traffic loss that occurs on the network. Set the robustness value higher to adjust for more traffic loss. Changing the query interval to change the igmp query interval timer, use the fo...
Page 226
226 c hapter 10: c onfiguring and m anaging igmp s nooping enabling router solicitation a wx switch can search for multicast routers by sending multicast router solicitation messages. This message invites multicast routers that receive the message and that support router solicitation to immediately ...
Page 228
228 c hapter 10: c onfiguring and m anaging igmp s nooping querier for vlan orange port querier-ip querier-mac ttl ---- --------------- ----------------- ----- 1 193.122.135.178 00:0b:cc:d2:e9:b4 23 igmp vlan member ports: 1,2, 4, 6, 5, 3, 8 igmp static ports: none igmp statistics for vlan orange: i...
Page 229
Displaying multicast information 229 displaying multicast queriers to display information about the multicast querier only without also displaying all the other multicast information, use the following command: display igmp querier [vlan vlan-id] to display querier information for vlan orange, type ...
Page 230
230 c hapter 10: c onfiguring and m anaging igmp s nooping use the group parameter to display receivers for a specific group or set of groups. For example, to display receivers for multicast groups 237.255.255.1 through 237.255.255.255, in all vlans, type the following command: wx1200# display igmp ...
Page 231: Onfiguring
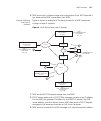
11 c onfiguring and m anaging s ecurity acl s a security access control list (acl) filters packets for the purpose of discarding them, permitting them, or permitting them with modification (marking) for class-of-service (cos) priority treatment. A typical use of security acls is to enable users to s...
Page 232
232 c hapter 11: c onfiguring and m anaging s ecurity acl s figure 9 setting security acls security acl filters a security acl filters packets to restrict or permit network traffic. These filters can then be mapped by name to authenticated users, ports, vlans, virtual ports, or distributed maps. You...
Page 233
Creating and committing a security acl 233 the order in which aces are listed in an acl is important. Mss applies aces that are higher in the list before aces lower in the list. (see “modifying a security acl” on page 246.) an implicit “deny all” rule is always processed as the last ace of an acl. I...
Page 234
234 c hapter 11: c onfiguring and m anaging s ecurity acl s for example, to create acl acl-1 that permits all packets from ip address 192.168.1.4, type the following command: wx1200# set security acl ip acl-1 permit 192.168.1.4 0.0.0.0 with the following basic security acl command, you can specify a...
Page 235
Creating and committing a security acl 235 wildcard masks when you specify source and destination ip addresses in an ace, you must also include a mask for each in the form source-ip-addr mask and destination-ip-addr mask. The mask is a wildcard mask. The security acl checks the bits in ip addresses ...
Page 236
236 c hapter 11: c onfiguring and m anaging s ecurity acl s use cos class 6 or 7 only for voip phones that use spectralink voice priority (svp), not for other types of traffic. For other types of voip phones, use cos class 4 or 5. Permitted packets are assigned to cos class 0 by default. (for more i...
Page 237
Creating and committing a security acl 237 the before 1 portion of the ace places it before any others in the acl, so it has precedence over any later aces for any parameter settings that are met. For more information about changing the order of aces or otherwise modifying security acls, see “modify...
Page 238
238 c hapter 11: c onfiguring and m anaging s ecurity acl s setting tcp and udp acls security acls can filter tcp and udp packets by source and destination ip address, precedence, and tos level. You can apply a tcp acl to established tcp sessions only, not to new tcp sessions. In addition, security ...
Page 240
240 c hapter 11: c onfiguring and m anaging s ecurity acl s committing a security acl to put the security acls you have created into effect, use the commit security acl command with the name of the acl. For example, to commit acl-99, type the following command: wx1200# commit security acl acl-99 suc...
Page 241
Creating and committing a security acl 241 viewing security acl details you can display the contents of one or all security acls that are committed. To display the contents of all committed security acls, type the following command: wx1200# display security acl info all acl information for all set s...
Page 242
242 c hapter 11: c onfiguring and m anaging s ecurity acl s acl hit-counters index counter acl-name ----- -------------------- -------- 1 31986 acl-red 2 0 acl-green clearing security acls the clear security acl command removes the acl from the edit buffer only. To clear a security acl, enter a spec...
Page 243
Mapping security acls 243 if you are configuring the attribute on a radius server, mss can receive the filter-id attribute with the profile value for an inbound acl and the outboundacl for an outbound acl. On the radius server, the value field of filter-id can specify up to two acls. Any of the foll...
Page 244
244 c hapter 11: c onfiguring and m anaging s ecurity acl s when assigned the filter-id attribute, an authenticated user with a current session receives packets based on the security acl. For example, to restrict incoming packets for natasha to those specified in acl-222, type the following command:...
Page 245
Mapping security acls 245 displaying acl maps to ports, vlans, and virtual ports two commands display the port, vlan, virtual port, and distributed map mapping of a specific security acl. For example, to show the ports, vlans, virtual ports, and distributed maps mapped to acl-999, type one of the fo...
Page 246
246 c hapter 11: c onfiguring and m anaging s ecurity acl s to stop the packet filtering of a user-based security acl, you must modify the user’s configuration in the local database on the wx switch or on the radius servers where packet filters are authorized. For information about deleting a securi...
Page 247
Modifying a security acl 247 adding another ace to a security acl the simplest way to modify a security acl is to add another ace. For example, suppose you wanted to modify an existing acl named acl-violet. Follow these steps: 1 to display all committed security acls, type the following command: wx1...
Page 248
248 c hapter 11: c onfiguring and m anaging s ecurity acl s 2 to add the deny ace to acl-111 and place it first, type the following commands: wx1200# set security acl ip acl-111 deny 192.168.254.12 0.0.0.255 before 1 wx1200# commit security acl acl-111 success: change accepted. 3 to view the results...
Page 249
Modifying a security acl 249 3 to view the results, type the following command: wx1200# display security acl info all acl information for all set security acl ip acl-111 (hits #4 0) ---------------------------------------------------- 1. Permit ip source ip 192.168.254.12 0.0.0.0 destination ip any ...
Page 250
250 c hapter 11: c onfiguring and m anaging s ecurity acl s 3 to view details about these uncommitted aces, type the following command. The entire acl-111 is displayed, including its committed aces. Wx1200# display security acl info all editbuffer acl edit-buffer information for all set security acl...
Page 251
Enabling prioritization for voice over ip 251 for example, to enable voip support for telesym packets, which use udp port 3344, for all users in vlan corp_vlan, perform the following steps: 1 configure an ace in acl voip that assigns ip traffic from any ip address with source udp port 3344, addresse...
Page 252
252 c hapter 11: c onfiguring and m anaging s ecurity acl s wx1200# set security acl ip svp permit 0.0.0.0 255.255.255.255 3 commit the acl to the configuration: wx1200# commit security acl svp 4 map the acl to the outbound traffic direction of vlan corp_vlan: wx1200# set security acl map voip vlan ...
Page 253
Security acl configuration scenario 253 6 alternatively, you can map acl-99 to natasha’s sessions when you are using a remote radius server for authentication. To configure natasha for pass-through authentication to the radius server shorebirds, type the following command: wx1200# set authentication...
Page 254
254 c hapter 11: c onfiguring and m anaging s ecurity acl s.
Page 255: Anaging
12 m anaging k eys and c ertificates a digital certificate is a form of electronic identification for computers. The wx switch requires digital certificates to authenticate its communications to 3com wireless switch manager and web view, to webaaa clients, and to extensible authentication protocol (...
Page 256
256 c hapter 12: m anaging k eys and c ertificates tls allows the client to authenticate the wx switch (and optionally allows the wx switch to authenticate the client) through the use of digital signatures. Digital signatures require a public-private key pair. The signature is created with a private...
Page 257
About keys and certificates 257 when the wx switch needs to communicate with 3com wireless switch manager, web view, or an 802.1x or webaaa client, mss requests a private key from the switch’s certificate and key store: if no private key is available in the wx switch’s certificate and key store, the...
Page 258
258 c hapter 12: m anaging k eys and c ertificates public and private keys 3com’s identity-based networking uses public key cryptography to enforce the privacy of data transmitted over the network. Using public-private key pairs, users and devices can send encrypted messages that only the intended r...
Page 259
About keys and certificates 259 table 25 pkcs object files supported by 3com file type standard purpose pkcs #7 cryptographic message syntax standard contains a digital certificate signed by a ca. To install the certificate from a pkcs #7 file, use the crypto certificate command to prepare mss to re...
Page 260
260 c hapter 12: m anaging k eys and c ertificates creating keys and certificates you must create a public-private key pair, and request, accept, or generate a digital certificate to exchange with 3com wireless switch manager or web view for management access, or with 802.1x or webaaa users for netw...
Page 261
Creating keys and certificates 261 certificate signing request (csr)—the most secure method, because the wx switch’s public and private keys are created on the wx switch itself, while the certificate comes from a trusted source (ca). This method requires generating the key pair, creating a csr and s...
Page 262
262 c hapter 12: m anaging k eys and c ertificates creating public-private key pairs to use a self-signed certificate or certificate signing request (csr) certificate for wx switch authentication, you must generate a public-private key pair. To create a public-private key pair, use the following com...
Page 263
Creating keys and certificates 263 email address: admin@example.Com unstructured name: wx in wiring closet 120 you must include a common name (string) when you generate a self-signed certificate. The other information is optional. Use a fully qualified name if such names are supported on your networ...
Page 267
Key and certificate configuration scenarios 267 key and certificate configuration scenarios the first scenario shows how to generate self-signed certificates. The second scenario shows how to install ca-signed certificates using pkcs #12 object files, and the third scenario shows how to install ca-s...
Page 268
268 c hapter 12: m anaging k eys and c ertificates # crypto generate self-signed admin country name: us state name: ca locality name: san francisco organizational name: example organizational unit: it common name: wx 6 email address: admin@example.Com unstructured name: wx in wiring closet 4 self-si...
Page 269
Key and certificate configuration scenarios 269 -----begin certificate----- miicuzccabygawibagica+cwdqyjkozihvcnaqeebqawnjelmakga1uebhmc czajbgnvbagtaknbmrowgaydvqqdfbf0zwnochvic0b0cnb6lmnvbtaefw0w ... Lm8wmvylxp56m 4 display certificate information for verification: you must paste the entire block,...
Page 270
270 c hapter 12: m anaging k eys and c ertificates # display crypto certificate webaaa certificate: version: 3 serial number: 999 (0x3e7) subject: c=us, st=ca, l=pleas, o=mycorp, ou=sqa, cn=bobadmin/emailaddress=bobadmin, unstructuredname=bob signature algorithm: md5withrsaencryption issuer: c=us, s...
Page 271
Key and certificate configuration scenarios 271 you must paste the entire block, from the beginning -----begin certificate request----- to the end -----end certificate request-----. # copy tftp://192.168.253.1/2048web.P12 2048web.P12 success: received 637 bytes in 0.253 seconds [ 2517 bytes/sec] 4 e...
Page 272
272 c hapter 12: m anaging k eys and c ertificates # crypto pkcs12 admin 2048admn.P12 unwrapped from pkcs12 file: keypair device certificate ca certificate you must paste the entire block, from the beginning -----begin certificate request----- to the end -----end certificate request-----. # crypto p...
Page 273
Key and certificate configuration scenarios 273 you must paste the entire block, from the beginning -----begin certificate request----- to the end -----end certificate request-----. # crypto generate key eap 1024 key pair generated you must paste the entire block, from the beginning -----begin certi...
Page 274
274 c hapter 12: m anaging k eys and c ertificates 6 open the signed certificate file with a text editor. Copy the entire file from the first hyphen to the last. 7 to install the administrative certificate on the wx switch, type the following command to display a prompt: you must paste the entire bl...
Page 275
Key and certificate configuration scenarios 275 15 repeat step 12 through step 14 to install the ca’s certificate for eap (802.1x) and web aaa..
Page 276
276 c hapter 12: m anaging k eys and c ertificates.
Page 277: Onfiguring
13 c onfiguring aaa for n etwork u sers the following sections describe the mss authentication, authorization, and accounting (aaa) features in detail. About aaa for network users network users include the following types of users: wireless users — users who access the network by associating with an...
Page 278
278 c hapter 13: c onfiguring aaa for n etwork u sers each authentication rule specifies where the user credentials are stored. The location can be a group of radius servers or the switch’s local database. In either case, if mss has an authentication rule that matches on the required parameters, mss...
Page 279
About aaa for network users 279 last-resort — a network user requests access to the network, without entering a username or password. Mss checks for a last-resort authentication rule for the requested ssid (or for wired, if the user is on a wired authentication port). If a matching rule is found, ms...
Page 280
280 c hapter 13: c onfiguring aaa for n etwork u sers figure 10 authentication flowchart for network users last-resort? Web? None? Client associates with map radio or requests access from wired authentication port use fallthru authentication yes no yes yes yes yes no yes yes no no no no client reque...
Page 281
About aaa for network users 281 ssid name “any” in authentication rules for wireless access, you can specify the name any for the ssid. This value is a wildcard that matches on any ssid string requested by the user. For 802.1x and webaaa rules that match on ssid any, mss checks the radius servers or...
Page 282
282 c hapter 13: c onfiguring aaa for n etwork u sers for a user to be successfully authenticated by an 802.1x or webaaa rule, the username and password entered by the user must be configured on the radius servers used by the authentication rule or in the switch’s local database, if the local databa...
Page 283
About aaa for network users 283 the radius attributes supported by mss are described in “supported radius attributes” on page 423. Mss provides the following vsas, which you can assign to users configured in the local database or on a radius server: encryption-type — specifies the type of encryption...
Page 284
284 c hapter 13: c onfiguring aaa for n etwork u sers regardless of whether you configure the user and attributes on radius servers or the switch’s local database, the vlan attribute is required. The other attributes are optional. Accounting mss also supports accounting. Accounting collects and send...
Page 285
Aaa tools for network users 285 automatically uses the same aaa method (radius server group or local database) for authorization that you define for a user’s authentication. Local authorization control. You can override any aaa assignment of vlan or security acl for individual network users on a par...
Page 286
286 c hapter 13: c onfiguring aaa for n etwork u sers wildcard “any” for ssid matching authentication rules for wireless access include the ssid name, and must match on the ssid name requested by the user for mss to attempt to authenticate the user for that ssid. To make an authentication rule match...
Page 287
Aaa tools for network users 287 aaa rollover process a wx switch attempts aaa methods in the order in which they are entered in the configuration: 1 the first aaa method in the list is used unless that method results in an error. If the method results in a pass or fail, the result is final and the w...
Page 288
288 c hapter 13: c onfiguring aaa for n etwork u sers authentication by a radius server group as the first method for these users and configure local authentication last, in case the radius servers are unavailable. (see figure 11.) 1 to configure server-1 and server-2 at ip addresses 192.168.253.1 a...
Page 289
Aaa tools for network users 289 authentication proceeds as follows: 1 when user jose@example.Com attempts authentication, the wx switch sends an authentication request to the first aaa method, which is server-group-1. Because server-group-1 contains two servers, the first radius server, server-1, is...
Page 290
290 c hapter 13: c onfiguring aaa for n etwork u sers ways a wx switch can use eap network users with 802.1x support cannot access the network unless they are authenticated. You can configure a wx switch to authenticate users with eap on a group of radius servers and/or in a local user database on t...
Page 291
Aaa tools for network users 291 effects of authentication type on encryption method wireless users who are authenticated on an encrypted service set identifier (ssid) can have their data traffic encrypted by the following methods: wi-fi protected access (wpa) encryption non-wpa dynamic wired equival...
Page 292
292 c hapter 13: c onfiguring aaa for n etwork u sers wired users are not eligible for the encryption performed on the traffic of wireless users, but they can be authenticated by an eap method, a mac address, a web login page served by the wx switch, or a last-resort username. Configuring 802.1x aut...
Page 293
Configuring 802.1x authentication 293 configuring eap offload you can configure the wx switch to offload all eap processing from server groups. In this case, the radius server is not required to communicate using the eap protocols. For peap-ms-chap-v2 offload, you define a complete user profile in t...
Page 294
294 c hapter 13: c onfiguring aaa for n etwork u sers for example, the following command authenticates 802.1x user jose for wired authentication access via the local database: wx1200# set authentication dot1x jose wired peap-mschapv2 local success: change accepted. Binding user authentication to mac...
Page 295
Configuring 802.1x authentication 295 if the 802.1x reauthentication parameter or the radius session-timeout parameter is applicable, the user must log in before the 802.1x reauthentication timeout or the radius session-timeout for the machine’s session expires. Normally, these parameters apply only...
Page 296
296 c hapter 13: c onfiguring aaa for n etwork u sers *.*.Mycorp.Com (userglob for the user authentication rule) use more specific rules to direct machines and users to different server groups. For example, to direct users in nl.Mycorp.Com to a different server group than users in de.Mycorp.Com, use...
Page 297
Configuring 802.1x authentication 297 to set the bonded auth period, use the following command: set dot1x bonded-period seconds to reset the bonded auth period to its default value (0), use the following command: clear dot1x bonded-period bonded auth configuration example to configure bonded auth: c...
Page 298
298 c hapter 13: c onfiguring aaa for n etwork u sers in the following example, bob.Mycorp.Com uses bonded auth, and the bonded auth period is set to 60 seconds. Wx1200# show dot1x config 802.1x user policy ---------------------- 'host/bob-laptop.Mycorp.Com' on ssid 'mycorp' doing passthru 'bob.Myco...
Page 299
Configuring authentication and authorization by mac address 299 users authorized by mac address require a mac authorization password if radius authentication is desired. By default, mss assumes that the mac address for a mac user is also the password. Caution: use this method with care. Ieee 802.11 ...
Page 300
300 c hapter 13: c onfiguring aaa for n etwork u sers for example, the following command removes mac user 01:0f:03:04:05:06 from group macfans: wx1200# clear mac-user 01:0f:03:04:05:06 group success: change accepted. The clear mac-usergroup command removes the group. To remove a mac user profile fro...
Page 301
Configuring authentication and authorization by mac address 301 (for details about mac address globs, see “mac address globs” on page 25.) you can add authorization attributes to authenticated mac users with the following command: set mac-user mac-addr attr attribute-name value for example, to add t...
Page 302
302 c hapter 13: c onfiguring aaa for n etwork u sers for example, the following command sets the outbound authorization password for mac users on server bigbird to h00per: wx1200# set radius server bigbird author-password h00per success: change accepted. If the mac address is in the database, mss u...
Page 303
Configuring webaaa 303 webaaa process 1 a user attempts to access a url from a web browser. The web browser sends a dns request for the ip address of the requested url. 2 the wx switch intercepts the request and does the following: uses the mss dns proxy to obtain the requested ip address from the n...
Page 304
304 c hapter 13: c onfiguring aaa for n etwork u sers webaaa requirements and recommendations use the following information to ensure operation of the web aaa feature. Wx switch requirements install a webaaa certificate. You can install a certificate signed by a trusted third-party certificate autho...
Page 305
Configuring webaaa 305 user information must be configured in the wx switch’s local database or on a radius server. The username, password, and vlan are required. Additional radius attributes or 3com vsas are optional. The optional vsas include url, which redirects an authenticated user to a url oth...
Page 306
306 c hapter 13: c onfiguring aaa for n etwork u sers if the webaaa certificate on the wx switch is self-signed, configure the browser to trust the signature by installing the certificate on the browser, so that the browser does not display a dialog about the certificate each time the user tries to ...
Page 307
Configuring webaaa 307 using a custom login page by default, mss serves the 3com login page for web login. To serve a custom page instead, do the following: 1 copy and modify the 3com page, or create a new page. 2 create a subdirectory in the user files area of the wx switch’s nonvolatile storage, a...
Page 308
308 c hapter 13: c onfiguring aaa for n etwork u sers copying and modifying the 3com login page to copy and modify the 3com web login page: 1 configure an unencrypted ssid on a wx switch. The ssid is temporary does not need to be one you intend to use in your network. To configure the ssid, use the ...
Page 309
Configuring webaaa 309 2 from your pc, attempt to directly access the temporary ssid. The wx switch serves the login page. 3 in the browser, select file > save as to save the login page. 4 edit the login page: a change the page title: my corp webaaa b change the greeting and logo: src="mycorp/mylogo...
Page 310
310 c hapter 13: c onfiguring aaa for n etwork u sers wx1200# copy tftp://10.1.1.1/mycorp-login.Html mycorp-webaaa/mycorp-login.Html success: received 637 bytes in 0.253 seconds [ 2517 bytes/sec] wx1200# copy tftp://10.1.1.1/mycorp-logo.Jpg mycorp-webaaa/mycorp-logo.Jpg success: received 1202 bytes ...
Page 311
Configuring webaaa 311 a url string can also contain the literal characters $ and ?, if you use the values listed in table 31. You can configure a redirect url for a group of users or for an individual user. For example, the following command configures a redirect url containing a variable for the u...
Page 312
312 c hapter 13: c onfiguring aaa for n etwork u sers to verify configuration of a redirect url and other user attributes, type the display aaa command. Configuring last-resort access users who are not authenticated and authorized by 802.1x methods or a mac address can gain limited access to the net...
Page 313
Assigning authorization attributes 313 to verify the aaa configuration, type the following command: wx1200# display aaa ... Set authentication last-resort ssid guestssid local ... User last-resort-guestssid vlan-name = k3 assigning authorization attributes authorization attributes can be assigned to...
Page 314
314 c hapter 13: c onfiguring aaa for n etwork u sers table 32 authentication attributes for local users attribute description valid value(s) encryption-type type of encryption required for access by the client. Clients who attempt to use an unauthorized encryption method are rejected. One of the fo...
Page 315
Assigning authorization attributes 315 filter-id inbound or outbound acl to apply to the user. If configured in the wx switch’s local database, this attribute can be an access control list (acl) to filter outbound or inbound traffic. Use the following format: filter-id inboundacl.In or filter-id out...
Page 316
316 c hapter 13: c onfiguring aaa for n etwork u sers service-type type of access the user is requesting. One of the following numbers: 2—framed; for network user access 6—administrative; for administrative access to the wx switch, with authorization to access the enabled (configuration) mode. The u...
Page 317
Assigning authorization attributes 317 time-of-day (network access mode only) day(s) and time(s) during which the user is permitted to log into the network. After authorization, the user’s session can last until either the time-of-day range or the session-timeout duration (if set) expires, whichever...
Page 318
318 c hapter 13: c onfiguring aaa for n etwork u sers assigning attributes to users and groups you can assign authorization attributes to individual users or groups of users. Use any of the following commands to assign an attribute to a user or group in the local wx database and specify its value: s...
Page 319
Assigning authorization attributes 319 assigning a security acl to a user or a group once a security access control list (acl) is defined and committed, it can be applied dynamically and automatically to users and user groups through the 802.1x authentication and authorization process. When you assi...
Page 320
320 c hapter 13: c onfiguring aaa for n etwork u sers for example, the following command applies security acl acl-101 to packets coming into the wx from user jose: wx1200# set user jose attr filter-id acl-101.In success: change accepted. The following command applies the incoming filters of acl-101 ...
Page 321
Assigning authorization attributes 321 assigning encryption types to wireless users when a user turns on a wireless laptop or pda, the device attempts to find an access point and form an association with it. Because map access points support the encryption of wireless traffic, clients can choose an ...
Page 322
322 c hapter 13: c onfiguring aaa for n etwork u sers for example, the following command restricts the mac user group mac-fans to access the network by using only tkip: wx1200# set mac-usergroup mac-fans attr encryption-type 4 success: change accepted. You can also specify a combination of allowed e...
Page 323
Overriding or adding attributes locally with a location policy 323 overriding or adding attributes locally with a location policy during the login process, the aaa authorization process is started immediately after clients are authenticated to use the wx switch. During authorization, mss assigns the...
Page 324
324 c hapter 13: c onfiguring aaa for n etwork u sers any authorization attributes not changed by the location policy remain active. How the location policy differs from a security acl although structurally similar, the location policy and security acls have different functions. The location policy ...
Page 325
Overriding or adding attributes locally with a location policy 325 for example, the following command denies network access to all users matching *.Theirfirm.Com, causing them to fail authorization: wx1200# set location policy deny if user eq *.Theirfirm.Com the following command authorizes access t...
Page 326
326 c hapter 13: c onfiguring aaa for n etwork u sers displaying and positioning location policy rules the order of location policy rules is significant. Mss checks a location policy rule that is higher in the list before those lower in the list. Rules are listed in the order in which you create the...
Page 327
Configuring accounting for wireless network users 327 configuring accounting for wireless network users accounting records come in three types: start-stop, stop-only, and update for network users. The records provide information about network resource usage. To set accounting, type the following com...
Page 328
328 c hapter 13: c onfiguring aaa for n etwork u sers (for details about display accounting statistics output, see the wireless lan switch and controller command reference . For information about accounting update records, see “viewing roaming accounting records” on page 328. To configure accounting...
Page 329
Configuring accounting for wireless network users 329 the user started on wx1200-0013: wx1200-0013# display accounting statistics may 21 17:01:32 acct-status-type=start acct-authentic=2 user-name=administrator@example.Com acct-multi-session-id=session-4-1106424789 event-timestamp=1053536492 vlan-nam...
Page 330
330 c hapter 13: c onfiguring aaa for n etwork u sers vlan-name=default calling-station-id=00-06-25-09-39-5d nas-port-id=2/1 called-station-id=00-0b-0e-76-56-a0 if you configured accounting records to be sent to a radius server, you can view the records of user roaming at the radius server. (for mor...
Page 331
Avoiding aaa problems in configuration order 331 set authentication last-resort ssid guestssid local user nin password = 082c6c64060b (encrypted) filter-id = acl-999.In user last-resort-guestssid vlan-name = k2 mac-user 01:02:03:04:05:06 usergroup eastcoasters session-timeout = 99 for information ab...
Page 332
332 c hapter 13: c onfiguring aaa for n etwork u sers here is an example of a aaa configuration where the most-specific rules for 802.1x and webaaa are first and the rules with any are last: wx1200# display aaa ... Set authentication web ssid corpa ** corpasrvr set authentication web ssid any ** sg1...
Page 333
Configuring a mobility profile 333 wx1200# display aaa ... Set accounting dot1x ssid mycorp * start-stop group1 set authentication dot1x ssid mycorp * peap-mschapv2 local set authentication dot1x ssid mycorp example/* peap-mschapv2 group1 configuration for a correct processing order to avoid process...
Page 334
334 c hapter 13: c onfiguring aaa for n etwork u sers caution: when mobility profile attributes are enabled, a user is denied access if assigned a mobility-profile attribute in the local wx switch database or radius server and no mobility profile of that name exists on the wx switch. Use the followi...
Page 335
Network user configuration scenarios 335 example, example\jose is on port 5, which is not in the port list), the authorization fails and client example\jose is rejected. The mobility profile feature is disabled by default. You must enable mobility profile attributes on the wx switch to use it. You c...
Page 336
336 c hapter 13: c onfiguring aaa for n etwork u sers general use of network user commands the following example illustrates how to configure ieee 802.1x network users for authentication, accounting, acl filtering, and mobility profile assignment: 1 configure all 802.1x users of ssid mycorp at examp...
Page 337
Network user configuration scenarios 337 users at example are now restricted to ports 2 and 5, as specified in the tulip mobility profile configuration. 7 use the display aaa command to verify your configuration. Type the following command: wx1200# display aaa default values authport=1812 acctport=1...
Page 338
338 c hapter 13: c onfiguring aaa for n etwork u sers 4 save the configuration: wx1200# save config success: configuration saved. (for information about setting up radius servers for remote authentication, see chapter 14, “configuring communication with radius,” on page 343.) enabling peap-ms-chap-v...
Page 339
Network user configuration scenarios 339 6 save the configuration: wx1200# save config success: configuration saved. (for information about encryption keys and certificates, see chapter 12, “managing keys and certificates,” on page 255.) enabling peap-ms-chap-v2 offload the following example illustr...
Page 340
340 c hapter 13: c onfiguring aaa for n etwork u sers combining eap offload with pass-through authentication the following example illustrates how to enable peap-ms-chap-v2 offload for the marketing (mktg) group and radius pass-through authentication for members of engineering. This example assumes ...
Page 341
Network user configuration scenarios 341 overriding aaa-assigned vlans the following example shows how to change the vlan access of wireless users in an organization housed in multiple buildings. Suppose the wireless users on the faculty of a college english department have offices in building a and...
Page 342
342 c hapter 13: c onfiguring aaa for n etwork u sers.
Page 343: Onfiguring
14 c onfiguring c ommunication with radius for a list of the standard and extended radius attributes and 3com vendor-specific attributes (vsas) supported by mss, see “supported radius attributes” on page 423. Radius overview remote authentication dial-in user service (radius) is a distributed client...
Page 344
344 c hapter 14: c onfiguring c ommunication with radius figure 12 wireless client, map, wx switch, and radius servers in the example shown in figure 12, the following events occur: 1 the wireless user (client) requests an ieee 802.11 association from the map access point. 2 after the map access poi...
Page 345
Before you begin 345 (for information about mac client authentication, see “configuring mac authentication and authorization” on page 300.) before you begin to ensure that you can contact the radius servers you plan to use for authentication, send the ping command to each one to verify connectivity....
Page 346
346 c hapter 14: c onfiguring c ommunication with radius if a server does not respond before the last request attempt times out, mss holds down further requests to the server, for the duration of the dead time. For example, if you set the dead time to 5 minutes, mss stops sending requests to the unr...
Page 348
348 c hapter 14: c onfiguring c ommunication with radius for example, the following command names a radius server rs1 with the ip address 192.168.0.2 and the key testing123: wx1200# set radius server rs1 address 192.168.0.2 key testing123 success: change accepted. You can configure multiple radius s...
Page 349
Configuring radius server groups 349 subsequently, you can change the members of a group or configure load balancing. If you add or remove a radius server in a server group, all the radius dead timers for that server group are reset to the global default. Creating server groups to create a server gr...
Page 350
350 c hapter 14: c onfiguring c ommunication with radius however, if the local database is the first method in the list, followed by a radius server group, the wx switch responds to a failed search of the database by sending a request to the following radius server group. This exception is called lo...
Page 351
Configuring radius server groups 351 adding members to a server group to add radius servers to a server group, type the following command: set server group group-name members server-name1 [server-name2] [server-name3] [server-name4] the keyword members lists the radius servers contained in the named...
Page 352
352 c hapter 14: c onfiguring c ommunication with radius the members of the group remain configured, although no server groups are shown: wx1200# display aaa default values authport=1812 acctport=1813 timeout=5 acct-timeout=5 retrans=3 deadtime=0 key=(null) author-pass=(null) radius servers server a...
Page 353
Radius and server group configuration scenario 353 wx1200# display aaa default values authport=1812 acctport=1813 timeout=5 acct-timeout=5 retrans=3 deadtime=0 key=(null) author-pass=(null) radius servers server addr ports t/o tries dead state --------------------------------------------------------...
Page 354
354 c hapter 14: c onfiguring c ommunication with radius.
Page 355: Anaging
15 m anaging 802.1x on the wx s witch certain settings for ieee 802.1x sessions on the wx switch are enabled by default. For best results, change the settings only if you are aware of a problem with the wx switch’s 802.1x performance. For settings that you can reset with a clear command, mss reverts...
Page 356
356 c hapter 15: m anaging 802.1x on the wx s witch the default setting is enable, which permits 802.1x authentication to occur as determined by the set dot1x port-control command for each wired authentication port. The disable setting forces all wired authentication ports to unconditionally authori...
Page 357
Managing 802.1x encryption keys 357 managing 802.1x encryption keys by default, the wx switch sends encryption key information to a wireless supplicant (client) in an extensible authentication protocol over lan (eapol) packet after authentication is successful. You can disable this feature or change...
Page 358
358 c hapter 15: m anaging 802.1x on the wx s witch type the following command to reset the retransmission interval to the 5-second default: wx1200# clear dot1x tx-period success: change accepted. Managing wep keys wired-equivalent privacy (wep) is part of the system security of 802.1x. Mss uses wep...
Page 359
Setting eap retransmission attempts 359 to reenable wep rekeying, type the following command: wx1200# set dot1x wep-rekey enable success: wep rekeying enabled configuring the interval for wep rekeying the following command sets the interval for rotating the wep broadcast and multicast keys: set dot1...
Page 360
360 c hapter 15: m anaging 802.1x on the wx s witch managing 802.1x client reauthentication reauthentication of 802.1x wireless supplicants (clients) is enabled on the wx switch by default. By default, the wx switch waits 3600 seconds (1 hour) between authentication attempts. You can disable reauthe...
Page 361
Managing 802.1x client reauthentication 361 setting the 802.1x reauthentication period the following command configures the number of seconds that the wx switch waits before attempting reauthentication: set dot1x reauth-period seconds the default is 3600 seconds (1 hour). The range is from 60 to 1,6...
Page 362
362 c hapter 15: m anaging 802.1x on the wx s witch to reset the bonded auth period to its default value, use the following command: clear dot1x max-req (for more information about bonded auth, see “binding user authentication to machine authentication” on page 294.) managing other timers by default...
Page 363
Displaying 802.1x information 363 success: dot1x auth-server timeout set to 60. To reset the 802.1x authorization server timeout to the default, type the following command: wx1200# clear dot1x timeout auth-server success: change accepted. Setting the 802.1x timeout for a client use the following com...
Page 364
364 c hapter 15: m anaging 802.1x on the wx s witch 00:05:3c:07:6d:7c authenticated vlan-it example\smith 00:05:5d:7e:94:83 authenticated vlan-eng example\jgarcia 00:02:2d:86:bd:38 authenticated vlan-eng wong@exmpl.Com 00:05:5d:7e:97:b4 authenticated vlan-eng example\hosni 00:05:5d:7e:98:1a authenti...
Page 365
Displaying 802.1x information 365 viewing 802.1x statistics type the following command to display 802.1x statistics about connecting and authenticating: wx1200# display dot1x stats 802.1x statistic value ---------------- ----- enters connecting: 709 logoffs while connecting: 112 enters authenticatin...
Page 366
366 c hapter 15: m anaging 802.1x on the wx s witch.
Page 367: Anaging
16 m anaging s essions about the session manager a session is a related set of communication transactions between an authenticated user (client) and the specific station to which the client is bound. Packets are exchanged during a session. A wx switch supports the following kinds of sessions: admini...
Page 368
368 c hapter 16: m anaging s essions displaying and clearing all administrative sessions to view information about the sessions of all administrative users, type the following command: wx1200> display sessions admin tty username time (s) type ------- -------------------- -------- ---- tty0 3644 cons...
Page 369
Displaying and clearing administrative sessions 369 displaying and clearing administrative telnet sessions to view information about administrative telnet sessions, type the following command: wx1200> display sessions telnet tty username time (s) type ------- -------------------- -------- ---- tty3 ...
Page 371
Displaying and clearing network sessions 371 displaying verbose network session information in the display sessions network commands, you can specify verbose to get more in-depth information. For example, to display detailed information for all network sessions, type the following command: wx1200> d...
Page 372
372 c hapter 16: m anaging s essions for example, the following command shows all sessions of users whose names begin with e: wx1200# display sessions network user e* user sess ip or mac vlan port/ name id address name radio ------------------------------ ---- ----------------- --------------- examp...
Page 373
Displaying and clearing network sessions 373 for example, the following command displays the sessions for mac address 01:05:5d:7e:98:1a: wx1200> display sessions net mac-addr 01:05:5d:7e:98:1a user sess ip or mac vlan port/ name id address name radio --------------------------- ---- --------------- ...
Page 374
374 c hapter 16: m anaging s essions for example, the following command clears the sessions of all users on vlan red: wx1200# clear sessions network vlan red displaying and clearing network sessions by session id you can display information about a session by session id. To find local session ids, e...
Page 375
Displaying and clearing network sessions 375 to clear network sessions by session id, type the following command with the appropriate local session id number. Clear sessions network session-id session-id for example, the following command deletes network session 9: wx1200# clear sessions network ses...
Page 376
376 c hapter 16: m anaging s essions.
Page 377: Ogue
17 r ogue d etection and c ountermeasures map radios automatically scan the rf spectrum for other devices transmitting in the same spectrum. The rf scans discover third-party transmitters in addition to other 3com radios. Mss considers the unknown transmitters to be devices of interest, which are po...
Page 378
378 c hapter 17: r ogue d etection and c ountermeasures rogue access points and users can also interfere with the operation of your enterprise network. Ad hoc users another type of rogue is a private wlan user group. The group might be using an access point or software that provides access point fun...
Page 379
Enabling countermeasures 379 countermeasures you can enable mss to use countermeasures against rogues. Countermeasures consist of packets that interfere with a client’s ability to use the rogue. Countermeasures are disabled by default. When you enable them, all devices of interest that are not in th...
Page 380
380 c hapter 17: r ogue d etection and c ountermeasures to specify the rogue to begin attacking, use the following command: set rfdetect countermeasures mac mac-addr the mac-addr is the bssid of the rogue. The mac address must be in the list of rogues generated by rf detection scans. Mss can issue c...
Page 381
Ignoring friendly third-party devices 381 wx1200#clear rfdetect countermeasures mac aa:bb:cc:11:22:33 success: clear rfdetect countermeasures mac aa:bb:cc:11:22:33 ignoring friendly third-party devices by default, when countermeasures are enabled, mss considers any unknown transmitter to be a rogue ...
Page 382
382 c hapter 17: r ogue d etection and c ountermeasures disabling or reenabling logging of rogues by default, the seed switch in the mobility domain generates a log message when a rogue is detected or disappears. To disable or reenable the log messages, use the following command: set rfdetect log {e...
Page 383
Displaying rf detection information 383 displaying rf detection information you can display information about countermeasures and the rogues detected by map radios. You also can display a list all transmitting devices detected by a specific radio. (for information about the fields in the output, see...
Page 384
384 c hapter 17: r ogue d etection and c ountermeasures the following example displays information about the bssids detected in the mobility domain managed by the seed switch: wx1200# display rfdetect mobility-domain total number of entries: 3 bssid wx-ipaddr port/radio rssi ssid > radio mac /channe...
Page 385
Displaying rf detection information 385 wx1200# display rfdetect data total number of entries: 7 bssid port/rad chan rssi age ssid ----------------- -------- ------ ---- --- -------- 00:06:25:09:39:4a 5/1 3 0 15 rack29ap 00:06:25:51:e9:ff 4/1 10 -85 15 arrow 00:06:25:51:e9:ff 5/1 10 -84 15 arrow 00:...
Page 386
386 c hapter 17: r ogue d etection and c ountermeasures the following command displays the devices detected by 3com radio 1 on the map connected to wx port 3: wx1200# display rfdetect visible ap 3 radio 1 total number of entries: 3 transmit mac chan rss ----------------- -------- ------- 00:06:25:51...
Page 387: Anaging
18 m anaging s ystem f iles a wireless switch (wx) contains nonvolatile storage. Mss allows you to manage the files in nonvolatile storage. In addition, you can copy files between the wx switch and a tftp server on the network. About system files generally, a wx switch’s nonvolatile storage contains...
Page 388
388 c hapter 18: m anaging s ystem f iles to display version information for a wx switch, type the following command: wx1200# display version mobility system software, version: 3.0.0 copyright (c) 2003,2004 by 3com, inc build information: (build#75) top 2004-06-30 07:25:00 model: wx1200 hardware mai...
Page 389
Working with files 389 displaying boot information boot information consists of the mss version and the names of the system image file and configuration file currently running on the wx switch. The boot command also lists the system image and configuration file that will be loaded after the next reb...
Page 390
390 c hapter 18: m anaging s ystem f iles the file area can contain subdirectories. Subdirectory names are indicated by a forward slash at the end of the name. In the following example, dangdir and old are subdirectories. To display a list of the files in nonvolatile storage and temporary files, typ...
Page 391
Working with files 391 copying a file you can perform the following copy operations: copy a file from a tftp server to nonvolatile storage. Copy a file from nonvolatile storage or temporary storage to a tftp server. Copy a file from one area in nonvolatile storage to another. Copy a file to a new fi...
Page 392
392 c hapter 18: m anaging s ystem f iles you can copy a file from a wx switch to a tftp server or from a tftp server to a wx switch, but you cannot use mss to copy a file directly from one tftp server to another. To copy the file floor2wx from nonvolatile storage to a tftp server, type the followin...
Page 393
Working with files 393 to copy file corpa-login.Html from a tftp server into subdirectory corpa in a wx switch’s nonvolatile storage, type the following command: wx1200# copy tftp://10.1.1.1/corpa-login.Html corpa/corpa-login.Html success: received 637 bytes in 0.253 seconds [ 2517 bytes/sec] deleti...
Page 394
394 c hapter 18: m anaging s ystem f iles corp_a/ 512 bytes may 21 2004, 19:15:48 file:dangcfg 13 kb may 16 2004, 18:30:44 dangdir/ 512 bytes may 16 2004, 17:23:44 old/ 512 bytes sep 23 2003, 21:58:48 total: 33 kbytes used, 207822 kbytes free =========================================================...
Page 395
Managing configuration files 395 displaying the running configuration to display the configuration running on the wx switch, use the following command: display config [area area] [all] the area area parameter limits the display to a specific configuration area. (for more information, see the wireles...
Page 396
396 c hapter 18: m anaging s ystem f iles # configuration nvgen'd at 2004-5-10 19:08:38 # image 2.1.0 # model wx1200 # last change occurred at 2004-5-10 16:31:14 set vlan 1 port 1 set vlan 10 name backbone tunnel-affinity 5 set vlan 10 port 7 set vlan 10 port 8 set vlan 3 name red tunnel-affinity 5 ...
Page 397
Managing configuration files 397 to configure a wx switch to load the configuration file floor2wx from nonvolatile storage following the next software reboot, type the following command: wx1200# set boot configuration-file floor2wx success: boot config set. Loading a configuration file to load confi...
Page 398
398 c hapter 18: m anaging s ystem f iles to back up the current configuration file named configuration and reset the wx switch to the factory default configuration, type the following commands: wx1200# copy configuration tftp://10.1.1.1/backupcfg success: sent 365 bytes in 0.401 seconds [ 910 bytes...
Page 399
Backing up and restoring the system 399 both commands have options to specify the types of files you want to back up and restore: critical—backs up or restores system files, including the configuration file used when booting, and certificate files. The size of an archive created by this option is ge...
Page 400
400 c hapter 18: m anaging s ystem f iles managing configuration changes the backup command places the boot configuration file into the archive. (the boot configuration file is the configured boot configuration in the show boot command’s output.) if the running configuration contains changes that ha...
Page 401
Upgrading the system image 401 the following command restores system-critical files on a switch, from archive sysa_bak: wx1200# restore system tftp:/10.10.20.9/sysa_bak success: received 11908 bytes in 0.150 seconds [ 79386 bytes/sec] success: restore complete. Upgrading the system image see the rel...
Page 402
402 c hapter 18: m anaging s ystem f iles.
Page 403: Roubleshooting
A t roubleshooting a wx s witch some common problems that occur during wx installation and basic configuration are simple to solve. However, to “recover” the system password, you must delete the existing wx configuration. Fixing common wx setup problems system logs provide a history of mss events. T...
Page 404
404 c hapter a: t roubleshooting a wx s witch table 36 wx setup problems and remedies symptom diagnosis remedy 3com wireless switch manager or a web browser (if you are using web view) warns that the wx switch’s certificate date is invalid. The switch’s time and date are currently incorrect, or were...
Page 405
Fixing common wx setup problems 405 client cannot access the network. This symptom has more than one possible cause: the client might be failing authentication or might not be authorized for a vlan. 1 type the display aaa command to ensure that the authentication rules on the wx switch allow the cli...
Page 406
406 c hapter a: t roubleshooting a wx s witch recovering the system password you can recover the system enable password if you have lost or forgotten it. Warning: recovering the system password will delete your configuration files. You set the wx switch password using the set enablepass command. If ...
Page 407
Configuring and managing the system log 407 log message components each log message contains the components shown in table 37. Logging destinations and levels a logging destination is the location to which logged event messages are sent for storage or display. By default, only session logging is dis...
Page 408
408 c hapter a: t roubleshooting a wx s witch specifying a severity level sends log messages for events or conditions at that level or higher to the logging destination. Table 39 lists the severity levels and their descriptions. (for defaults, see table 38, “system log destinations and defaults,” on...
Page 410
410 c hapter a: t roubleshooting a wx s witch for example, the following command displays all messages at the error severity level or higher: wx1200# display log buffer severity error sys jun 02 17:41:35. 176214 error nos_vms_port?Add: failed to set default vlan v1 an:4096 for port 3 rc 1 to filter ...
Page 411
Configuring and managing the system log 411 the console is always available, but it has the following limitations: console logging is slow. Messages logged to the console are dropped if the console output buffer overflows. Mss displays a message indicating the number of messages dropped. If you type...
Page 412
412 c hapter a: t roubleshooting a wx s witch setting telnet session defaults session logging is disabled by default, and the event level is set to information (info) or higher. To enable event logging to telnet sessions and change the default event severity level, use the following command: set log...
Page 413
Running traces 413 saving trace messages in a file to save the accumulated trace data for enabled traces to a file in the wx switch’s nonvolatile storage, use the following command: save trace filename to save trace data into the file trace1 in the subdirectory traces, type the following command: wx...
Page 414
414 c hapter a: t roubleshooting a wx s witch using the trace command tracing is used only for debugging mss. The command set trace area enables you to view messages about the status of a specific portion of the mss. There are many trace parameters that you can run. (see “list of trace areas” on pag...
Page 415
Running traces 415 tracing 802.1x sessions tracing 802.1x sessions can help diagnose problems with wireless clients. For example, to trace 802.1x activity for user tamara@example.Com at level 4, type the following command: wx1200# set trace dot1x user tamara@example.Com level 4 success: change accep...
Page 416
416 c hapter a: t roubleshooting a wx s witch because traces use the logging facility, any other logging target can be used to capture trace messages if its severity is set to debug. However, since tracing can be voluminous, 3com discourages this in practice. To enable trace output to the console, e...
Page 417
Running traces 417 wx1200# display log trace facility ? Select one of: kernel, aaa, syslogd, acl, apm, arp,aso, boot, cli, cluster, copp, crypto, dot1x, encap, ethernet, gateway, httpd, igmp, ip, misc, nose, np, rand, resolv, rib, roam, rogue, sm, snmpd, span, store, sys, tagmgr, tbridge, tcpssl, te...
Page 418
418 c hapter a: t roubleshooting a wx s witch using display commands to troubleshoot the wx switch, you can use display commands to display information about different areas of the mss. The following commands can provide helpful information if you are experiencing mss performance issues. Viewing vla...
Page 419
Using display commands 419 viewing aaa session statistics to view aaa session statistics, type the following command: wx1200# display aaa default values authport=1812 acctport=1813 timeout=5 acct-timeout=5 retrans=3 deadtime=5 key=(null) author-pass=(null) radius servers server addr ports t/o tries ...
Page 420
420 c hapter a: t roubleshooting a wx s witch viewing fdb information the display fdb command displays the hosts learned by the wx switch and the ports to which they are connected. To display forwarding database (fdb) information, type the following command: wx1200# display fdb * = static entry. + =...
Page 421
Capturing system information for technical support 421 capturing system information for technical support for problems you cannot solve yourself, use the display base-information command to generate a report of your wx switch’s configuration and status, which you can show to 3com technical support. ...
Page 422
422 c hapter a: t roubleshooting a wx s witch.
Page 423: Upported
B s upported radius a ttributes 3com mobility system software (mss) supports the standard and extended radius authentication and accounting attributes listed in table 41 on page 424. Also supported are 3com vendor-specific attributes (vsas), listed in table 42 on page 431. Attributes an attribute is...
Page 424
424 c hapter b: s upported radius a ttributes supported standard and extended attributes the radius attributes shown in table 41 are sent by wx switches to radius servers during authentication and accounting. Table 41 801.1x attributes attribute type, vendor id, vendor type rcv in access resp? Sent ...
Page 425
Supported standard and extended attributes 425 service- type 5 yes yes yes access type, which can be one of the following: 2—framed; for network user access 6—administrative; for administrative access to the wx switch, with authorization to access the enabled (configuration) mode. The user must ente...
Page 426
426 c hapter b: s upported radius a ttributes filter-id 11 yes no optional if configured in the wx switch’s local database, this attribute can be an access control list (acl) to filter outbound or inbound traffic. Use the following format: filter-id inboundacl.In or filter-id outboundacl.Out if you ...
Page 427
Supported standard and extended attributes 427 reply- message 18 yes no no string. Text that can be displayed to the user. Multiple reply-messages can be included. If any are displayed, they must appear in the order in which they appear in the packet. State 24 yes yes no can be sent by a radius serv...
Page 428
428 c hapter b: s upported radius a ttributes called- station-id 30 no yes yes for ieee 802.1x authenticators, stores the map access point mac address in uppercase ascii format, with octet values separated by hyphens (for example, 00-10-a4-23-19-c0). Calling- station-id 31 no yes yes for ieee 802.1x...
Page 429
Supported standard and extended attributes 429 acct-output- octets 43 no no yes number of octets sent on the port in the course of this service being provided. Can be present only in accounting-request records in which acct-status-type is set to acct-stop or acct-interim-update. Acct- session-id 44 ...
Page 430
430 c hapter b: s upported radius a ttributes acct-output- packets 48 no no yes number of packets sent in the course of this service being provided. Can be present only in accounting-request records in which acct-status-type is set to acct-stop or acct-interim-update. Acct-multi- session-id 50 no no...
Page 431
3com vendor-specific attributes 431 3com vendor-specific attributes the vendor-specific attributes (vsas) created by 3com are embedded according to the procedure recommended in rfc 2865, with vendor-id set to 43. Table 42 describes the 3com vsas, listed in order by vendor type number. (for attribute...
Page 432
432 c hapter b: s upported radius a ttributes ssid 26, 43, 6 yes no yes name of the ssid you want the user to use. The ssid must be configured in a service profile, and the service profile must be used by a radio profile assigned to 3com radios in the mobility domain. End-date 26, 43, 7 yes no no da...
Page 433: Obility
C m obility d omain t raffic p orts when deploying a mobility domain, you might attach the wx switches to subnets that have firewalls or access controls between them. Within a mobility domain, wx switches exchange information and other types of traffic, depending on your configuration of aaa and var...
Page 434
434 c hapter c: m obility d omain t raffic p orts.
Page 435: Btaining
D o btaining s upport for your p roduct register your product warranty and other service benefits start from the date of purchase, so it is important to register your product quickly to ensure you get full use of the warranty and other service benefits available to you. Warranty and other service be...
Page 436
436 c hapter d: o btaining s upport for your p roduct troubleshoot online you will find support tools posted on the 3com web site at http://www.3com.Com/ 3com knowledgebase helps you troubleshoot 3com products. This query-based interactive tool is located at http://knowledgebase.3com.Com and contain...
Page 437
Contact us 437 to send a product directly to 3com for repair, you must first obtain a return authorization number (rma). Products sent to 3com, without authorization numbers clearly marked on the outside of the package, will be returned to the sender unopened, at the sender’s expense. If your produc...
Page 438
438 c hapter d: o btaining s upport for your p roduct austria belgium denmark finland france germany hungary ireland israel italy 01 7956 7124 070 700 770 7010 7289 01080 2783 0825 809 622 01805 404 747 06800 12813 1407 3387 1800 945 3794 199 161346 luxembourg netherlands norway poland portugal sout...
Page 439: Lossary
G lossary 3com wireless switch manager™ (3wxm)™ a tool suite for planning, configuring, deploying, and managing a 3com mobility system wireless lan (wlan). Based on site and user requirements, 3wxm determines the location of wireless switches (wxs) and managed access points (maps) and can store and ...
Page 440
440 g lossary 802.2 an ieee lan specification that defines the logical link control (llc) sublayer, the upper portion of the data link layer. Llc encapsulation can be used by any lower-layer lan technology. Compare 802.3; ethernet ii. 802.3 an ieee lan specification for a carrier sense multiple acce...
Page 441
G lossary 441 802.11g a supplement to the ieee 802.11 wireless lan (wlan) specification, describing transmission through the physical layer (phy) based on orthogonal frequency division multiplexing (ofdm), at a frequency of 2.4 ghz and data rates of up to 54 mbps. 802.11i a draft supplement to the i...
Page 442
442 g lossary ad hoc network one of two ieee 802.11 network frameworks. In an ad hoc network, a set of wireless stations communicate directly with one another without using an access point (ap) or any connection to a wired network. With an ad hoc network, also known as a peer-to-peer network or inde...
Page 443
G lossary 443 authentication, authorization, and accounting see aaa. Authentication mobility the ability of a user (client) authenticated via extensible authentication protocol (eap) — plus an appropriate subprotocol and back-end authentication, authorization, and accounting (aaa) service — to roam ...
Page 444
444 g lossary bssid basic service set identifier. The 48-bit media access control (mac) address of the radio in the access point (ap) that serves the stations in a basic service set (bss). Ca see certificate authority (ca). Cbc-mac see ccmp. Cci co-channel interference. Obstruction that occurs when ...
Page 445
G lossary 445 chap challenge handshake authentication protocol. An authentication protocol that defines a three-way handshake to authenticate a user (client). Chap uses the md5 hash algorithm to generate a response to a challenge that can be checked by the authenticator. For wireless connections, ch...
Page 446
446 g lossary cryptography the science of information security. Modern cryptography is typically concerned with the processes of scrambling ordinary text (known as plain text or clear text) into encrypted text at the sender’s end of a connection, and decrypting the encrypted text back into clear tex...
Page 447
G lossary 447 des data encryption standard. A federally approved symmetric encryption algorithm in use for many years and replaced by the advanced encryption standard (aes). See also 3des. Dhcp dynamic host configuration protocol. A protocol that dynamically assigns ip addresses to stations, from a ...
Page 448
448 g lossary domain policy a collection of configuration settings that you can define once in 3com wireless switch manager (3wxm) and apply to many wireless switches (wxs). Each mobility domain group in the network has a default domain policy that applies to every wx switch in the mobility domain. ...
Page 449
G lossary 449 eap extensible authentication protocol. A general point-to-point protocol that supports multiple authentication mechanisms. Defined in rfc 2284, eap has been adopted by ieee 802.1x in an encapsulated form for carrying authentication messages in a standard message exchange between a use...
Page 450
450 g lossary enabled access permission to use all mobility system software (mss) command-line interface (cli) commands required for configuration and troubleshooting. Enabled access requires a separate enable password. Compare restricted access. Encryption any procedure used in cryptography to tran...
Page 451
G lossary 451 fdb see forwarding database (fdb). Federal communications commission see fcc. Fhss frequency-hopping spread-spectrum. One of two types of spread-spectrum radio technology used in wireless lan (wlan) transmissions. The fhss technique modulates the data signal with a narrowband carrier s...
Page 452
452 g lossary gmk group master key. A cryptographic key used to derive a group transient key (gtk) for the temporal key integrity protocol (tkip) and advanced encryption standard (aes). Greenfield network an original deployment of a telecommunications network. Gre tunnel a virtual link between two r...
Page 453
G lossary 453 hewlett-packard open view see hpov. Homologation the process of certifying a product or specification to verify that it meets regulatory standards. Hpov hewlett-packard open view. The umbrella network management system (nms) family of products from hewlett-packard. The 3com wireless sw...
Page 454
454 g lossary igmp snooping a feature that prevents the flow of multicast stream packets within a virtual lan (vlan) and forwards the multicast traffic through a path to only the clients that want to receive it. A wireless switch (wx) uses igmp snooping to monitor the internet group management proto...
Page 455
G lossary 455 internet authentication service see ias. Internet group management protocol see igmp. Interswitch link see isl. Isl interswitch link. A proprietary cisco protocol for interconnecting multiple switches and maintaining virtual lan (vlan) information as traffic travels between switches. W...
Page 456
456 g lossary location policy an ordered list of rules that overrides the virtual lan (vlan) assignment and security acl filtering applied to users during normal authentication, authorization, and accounting (aaa) — or assigns a vlan or security acl to users without these assignments. Defining locat...
Page 457
G lossary 457 managed access point™ (map™) a small hardware unit that functions as a wireless access point (ap) in a 3com mobility system. Using one or more radio transmitters, a map transmits and receives information as radio frequency (rf) signals to and from a wireless user (client). The map tran...
Page 458
458 g lossary message integrity code see mic. Mic message integrity code. The ieee term for a message authentication code (mac). See mac. Microsoft challenge handshake authentication protocol see ms-chap-v2. Minimum data transmit rate the lowest rate at which a managed access point (map) can transmi...
Page 459
G lossary 459 msdu mac service data unit. In ieee 802.11 communications, the data payload encapsulated within a mac protocol data unit (mpdu). Mss see mobility system software™ (mss™). Mtu maximum transmission unit. The size of the largest packet that can be transmitted over a particular medium. Pac...
Page 460
460 g lossary peap protected extensible authentication protocol. A draft extension to the extensible authentication protocol with transport layer security (eap-tls), developed by microsoft corporation, cisco systems, and rsa data security, inc. Tls is used in peap part 1 to authenticate the server o...
Page 461
G lossary 461 the pki uses the digital certificate to identify an individual or an organization. The private key is given only to the requesting party and is never shared, and the public key is made publicly available (as part of the digital certificate) in a directory that all parties can access. Y...
Page 462
462 g lossary power over ethernet see poe. Pre-master secret a key generated during the handshake process in transport layer security (tls) protocol negotiations and used to derive a master secret. Preshared key see psk. Prf pseudorandom function. A function that produces effectively unpredictable o...
Page 463
G lossary 463 ptk pairwise transient key. A value derived from a pairwise master key (pmk) and split into multiple encryption keys and message integrity code (mic) keys for use by a client and server as temporal session keys for ieee 802.11i robust security. See also 802.11i. Public key in cryptogra...
Page 464
464 g lossary radius remote authentication dial-in user service. A client-server security protocol described in rfc 2865 and rfc 2866. Radius extensions, including radius support for the extensible authentication protocol (eap), are described in rfc 2869. Originally developed by livingston enterpris...
Page 465
G lossary 465 roaming the ability of a wireless user (client) to maintain network access when moving between access points (aps). Robust security network see rsn. Rogue access point an access point (ap) that is not authorized to operate within a wireless network. Rogue access points subvert the secu...
Page 466
466 g lossary seed (1) an input to a pseudorandom number generator (prng), that is generally the combination of two or more inputs. (2) the wireless switch (wx) that distributes information to all the wx switches in a mobility domain™ group. Sentrysweep™ a radio frequency (rf) detection sweep that r...
Page 467
G lossary 467 ssl secure sockets layer protocol. A protocol developed by netscape for managing the security of message transmission over the internet. Ssl has been succeeded by transport layer security (tls) protocol, which is based on ssl. The sockets part of the term refers to the sockets method o...
Page 468
468 g lossary tls transport layer security protocol. An authentication and encryption protocol that is the successor to the secure sockets layer (ssl) protocol for private transmission over the internet. Defined in rfc 2246, tls provides mutual authentication with nonrepudiation, encryption, algorit...
Page 469
G lossary 469 u-nii unlicensed national information infrastructure. Three unlicensed frequency bands of 100 mhz each in the 5 ghz band, designated by the u.S. Federal communications commission (fcc) to provide high-speed wireless networking. The three frequency bands — 5.15 ghz through 5.25 ghz (for...
Page 470
470 g lossary vlan glob a 3com convention for applying the authentication, authorization, and accounting (aaa) attributes in the location policy on a wx switch to one or more users, based on a virtual lan (vlan) attribute. To specify all vlans, use the double-asterisk (**) wildcard characters. To ma...
Page 471
G lossary 471 wep wired-equivalent privacy protocol. A security protocol, specified in the ieee 802.11 standard, that attempts to provide a wireless lan (wlan) with a minimal level of security and privacy comparable to a typical wired lan. Wep encrypts data transmitted over the wlan to protect the v...
Page 472
472 g lossary wireless lan see wlan. Wireless switch™ (wx™) a switch in a 3com mobility system. A wx provides forwarding, queuing, tunneling, and some security services for the information it receives from its directly attached managed access points (maps). In addition, the wx coordinates, provides ...
Page 473
G lossary 473 x.509 an international telecommunications union telecommunication standardization sector (itu-t) recommendation and the most widely used standard for defining digital certificates. Xml extensible markup language. A simpler and easier-to-use subset of the standard generalized markup lan...
Page 474
474 g lossary.
Page 475: Ndex
I ndex numbers 3com technical support capturing system information for 421 3wxm keys and certificates requirement 255 802.11a 51, 140, 142 802.11b 51, 140, 142 802.11g 51, 140, 142 802.1q tagging 66 802.1x authentication 292 authentication port control 356 authorization 334 client reauthentication 3...
Page 476
476 i ndex sessions, displaying 367 telnet client sessions, displaying and clearing 369 telnet sessions, displaying and clearing 369 affinity 66 configuring 69 in roaming vlans 112 number 112 aging timeout arp 99 fdb 73 alert logging level 408 aliases 92 all access 30 antenna, external 141 arp aging...
Page 477
I ndex 477 ccmp 168 enabling 175, 180 certificate authority certificate source 256 enrolling with 264 certificate signing request (csr) 261 defined 259 generating 264 certificates configuration scenarios 267 creating 260 eap self-signed 262 invalid, troubleshooting 404 overview 255 pkcs #12 object f...
Page 478
478 i ndex priority assigned 235 countermeasures 377 displaying 383 enabling 379 enabling, against specific device 379 ignoring friendly devices 381 traps 382 countermeasures, tkip 171 configuring 176, 181 counters radio 163 see also statistics country, specifying 136 critical logging level 408 cryp...
Page 479
I ndex 479 error logging level 408 etherchannel interoperability 63 ethernet ports, numbering conventions 26 event-timestamp attribute 431 extensible authentication protocol (eap). See eap (extensible authentication protocol) external antenna 141 f fallthru authentication type changing 146 fast conv...
Page 480
480 i ndex displaying 78 removing 78 subnet masks for, notation conventions 23 system ip address 79 verifying 100 wildcard masks for, in security acls 235 ip interfaces, configuration scenario 103 ip phones 250 ip routes 79 default 82 displaying 80 static 82 tracing 101 k key pair, public-private 26...
Page 481
I ndex 481 mac authentication configuring 298 mac authorization password 301 mac user groups 299 mac users 299 machine authentication 294 map (managed access point) boot process 123 configuring 49, 51, 117, 193 defaults 136 denial of configuration information, troubleshooting 404 directly connected ...
Page 482
482 i ndex displaying by mac address 372 displaying by session id 374 displaying by username 371 displaying by vlan name 373 verbose information 371 see also sessions network time protocol. See ntp (network time protocol) network users assigning attributes to 318 authenticating and authorizing 285 c...
Page 483
I ndex 483 authorization 335 conventions for 26 port priority 207 configuring 209 port types clearing 53 configuring 47 resetting 53 ports administrative state 56 autonegotiation 56 blocked by stp, displaying 216 clearing acl maps from 320 filtering tcp and udp packets by 238 http 89 https 89 interf...
Page 484
484 i ndex global defaults 345 load-balancing servers 350 mapping security acls to user sessions 243, 320 offload authentication 293 parameters, setting individually 347 pass-through authentication, configuration scenario 337 password 345, 347 password, global 345, 346 server configuration 345 serve...
Page 485
I ndex 485 peap-ms-chap-v2 with pass-through authentication 340 port and vlan configuration 73 problems in configuration order 332 radius and server group configuration 352 radius authentication for telnet users 44 radius pass-through authentication configuration 337 security acl configuration 252 s...
Page 486
486 i ndex sntp. See ntp (network time protocol) software version, displaying 387 spanning tree protocol. See stp (spanning tree protocol) spectralink voice priority 250 ssh enabling 83 port number 86 ssid attribute description 432 ssids (service set identifiers) 131 beaconing 146 configuring 145 ss...
Page 487
I ndex 487 telnet administrative sessions, displaying and clearing 369 client sessions, displaying and clearing 369 disabling 87 logging to the current session 412 management port 433 port number 88 radius authentication, scenario 44 tftp, copying files 391 time intervals for 802.1x key transmission...
Page 488
488 i ndex see also usernames user passwords 39 user permissions 319 user sessions. See sessions user vlans 64 user-based security acls clearing maps 320 mapping 242 see also security acls user-name attribute 424 usernames case-sensitive 39 clearing sessions by 372 displaying network sessions by 371...
Page 489
I ndex 489 wep 802.1x keys rekey interval 359 rekeying 358 wi-fi protected access. See wpa (wi-fi protected access) wildcard masks 235 notation conventions 23 wildcards in mac address globs 25 in user globs 24 in vlan globs 25 masks for in security acls 235 wired authentication ports 47 802.1x setti...
Page 490
490 i ndex.
Page 494
494 c ommand i ndex set mac-user group 299 set mac-usergroup attr 299 set mac-usergroup attr encryption-type 321 set mac-usergroup attr filter-id 319 set mobility-domain member 109 set mobility-domain mode member seed-ip 109 set mobility-domain mode seed 108 set mobility-domain mode seed domain-name...
Page 495
C ommand i ndex 495 t telnet 100 traceroute 102.
Page 496
496 c ommand i ndex.