- DL manuals
- 3Com
- Switch
- 4007
- Implementation Manual
3Com 4007 Implementation Manual
Summary of 4007
Page 1
Http://www.3com.Com/ switch 4007 implementation guide release 3.0.5 part no. 10013673 published may 2000
Page 2
3com corporation 5400 bayfront plaza santa clara, california 95052-8145 copyright © 2000, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) withou...
Page 3: Ontents
C ontents a bout t his g uide audience 31 scope of this guide 32 conventions 32 switch 4007 documentation 34 documentation comments 35 year 2000 compliance 35 p art i u nderstanding y our s witch 4007 s ystem 37 1 c onfiguration o verview physical configuration requirements and options 40 requiremen...
Page 4: Eme O
P art ii u nderstanding t he m anagement m odule 51 2 o verview of the m anagement m odule before you start 53 module overview 54 module components 54 module functions 55 impact on the network 56 3 i nstalling m anagement m odules before you start 57 installing modules 58 hot insert and hot swap 58 ...
Page 5
Setting up an ip address for telnet 73 connecting to remote devices 74 in-band connections 75 serial line internet protocol connections 75 configuring access to the web interface 76 entering commands 77 the command completion feature 77 listing command options 78 keystroke functions 80 configuring t...
Page 6
Creating a community table 96 configuring a trap destination 97 configuring the authentication alert setting 97 configuring trap options 97 viewing snmp extensions and traps 98 interpreting eme trap messages 98 obtaining more information about snmp 99 configuring the event log 100 using the file sys...
Page 7: III
Power class settings 117 using the default power class setting 117 setting power class 117 power class 10 warnings 118 budgeting power 118 allocating power for installed modules 118 increasing the unallocated power budget 119 determining chassis power budget 120 power supply output in non-fault-tole...
Page 8
7 p hysical p ort n umbering slot architecture 137 default port settings 138 configuring port status 139 allocating switch fabric capacity to slots 140 9-port gen switch fabric module 140 using table 33: examples 140 24-port gen switch fabric module 141 using table 34: examples 142 key guidelines fo...
Page 9
Flow control 157 important considerations 157 pace interactive access 158 important considerations 158 port monitoring 158 standards, protocols, and related reading 159 ethernet protocol 159 media specifications 159 related reading 160 9 b ridge -w ide and b ridge p ort p arameters bridging overview...
Page 10
How a single bridge interprets cbpdus 174 how multiple bridges interpret cbpdus 175 determining the root bridge 178 determining the root ports 178 determining the designated bridge and designated ports 178 spanning tree port states 180 reconfiguring the bridged network topology 182 resulting actions...
Page 11: Ip M
Broadcast and multicast limits 195 important considerations 196 garp vlan registration protocol (gvrp) 197 important considerations 197 standards, protocols, and related reading 198 10 c lass of s ervice (c o s) overview 200 key concepts 201 basic elements of the standard 201 format of prioritized p...
Page 12
Key implementation guidelines 215 processing ip multicast packets 217 effects of mac address aliasing 218 important considerations 219 operating as the querier 220 locating multicast routers 220 aging the igmp tables 221 standards, protocols, and related reading 221 12 t runking trunking overview 22...
Page 13: Lan
Resilient link define and modify 238 important considerations 238 resilient link state 239 important considerations 239 resilient link active port 239 important considerations 239 resilient link remove 239 important consideration 239 14 v irtual lan s (vlan s ) vlan overview 242 need for vlans 242 b...
Page 14
Port-based vlans 266 the default vlan 266 modifying the default vlan 267 trunking and the default vlan 268 user-configured port-based vlans 270 important considerations 270 example 1: a single vlan configuration 271 example 2: vlans with tagged backplane ports 272 example 3: vlans with tagged front-...
Page 15
15 p acket f iltering packet filtering overview 306 what can you filter? 306 when is a filter applied? — paths 307 input packet filtering: receive path 307 output packet filtering: transmit path 307 internal packet filtering: receive internal path 307 path assignment 308 key concepts 309 standard pa...
Page 16: Ip R
Port group filter 336 limits to filter size 336 storage rules for preprocessed packet filters 336 run-time storage of packet filters 336 using port groups in custom packet filters 337 port group packet filter example 337 port group filter operation 337 port group management and control functions 340...
Page 17
Variable length subnet masks (vlsms) 364 how vlsms work 364 guidelines for using vlsms 364 router interfaces 365 routing table 366 default route 368 routing models: port-based and vlan-based 368 key guidelines for implementing ip routing 369 configure trunks (optional) 369 configure ip vlans 370 est...
Page 18: (Vrrp)
Effects and consequences 383 rip-1 versus rip-2 383 important considerations 384 routing policies 384 how routing policies work 385 important considerations 387 implementing rip routing policies 387 rip metric adjustments 387 rip import policy conditions for specified interfaces 388 rip export polic...
Page 19: Ip M
Important considerations 403 vrrp and other networking operations 404 spanning tree protocol (stp) 405 dynamic routing protocols (rip, rip-2, ospf) 405 igmp queries 406 icmp redirect 407 quality of service 407 ip routing policies 407 dynamic host configuration protocol (dhcp) 407 using vrrp on your ...
Page 20
How a network supports ip multicast 426 ip multicast routing 426 supporting protocols in your module 427 ip multicast tunnels 427 supporting protocol in your module 428 ip multicast filtering 428 supporting protocol in your multilayer switching module 428 internet support for ip multicast 429 key co...
Page 21: (Ospf) R
Configuring igmp options 440 querying and snooping modes 440 important considerations 440 configuring dvmrp interfaces 440 important considerations 440 configuring dvmrp tunnels 441 important considerations 441 configuring dvmrp default routes 443 how default routes work 443 how to configure a defau...
Page 22
Autonomous system boundary routers 459 configuring an asbr 459 areas 461 types of areas 462 area border routers 464 routing databases 464 configuring route summarization in abrs 465 important considerations 465 default route metric 468 ospf interfaces 468 mode 468 priority 469 using priority to sele...
Page 23: Ipx R
Default memory allocation 485 current partition maximum size 485 allocated memory size 486 running out of memory — soft restarts 486 manual memory allocation 487 system memory allocation 487 stub default metrics 487 important considerations 488 virtual links 488 important considerations 490 ospf rou...
Page 24
How ipx routing works 510 ipx packet format 510 ipx packet delivery 512 sending node’s responsibility 513 router’s responsibility 514 terminology 515 key guidelines for implementation 516 procedural guidelines 516 general guidelines 516 ipx interfaces 517 important considerations 517 per-interface o...
Page 25
Ipx sap mode 530 important considerations 530 sap policies 530 sap import polices 531 sap export policies 531 sap policy parameters 531 ipx statistics 532 standards, protocols, and related reading 533 21 a pple t alk r outing appletalk overview 536 features 536 benefits 537 key concepts 538 appletal...
Page 26: Rsvp
Appletalk zones 554 important considerations 555 changing zone names 556 aging out the network range 556 forwarding appletalk traffic 558 enabling forwarding 558 disabling forwarding 558 important considerations 558 checksum error detection 559 important considerations 559 appletalk echo protocol (a...
Page 27
Defining flow classifiers 577 flow classifier information 578 specifying addresses and address masks 578 specifying ports and port ranges 579 defining nonflow classifiers 580 nonflow classifier information 580 qos controls 581 important considerations 582 assigning control numbers 583 specifying rat...
Page 28
23 d evice m onitoring chapter scope 614 device monitoring overview 616 key concepts and tools 616 administration console 616 web management tools 616 network management platform 617 smartagent embedded software 617 event logging 618 baselining 618 important considerations 618 displaying the current...
Page 29: 657
Important considerations 634 rmon-1 groups 635 statistics and axfddistatistics groups 636 history and axfddihistory groups 637 alarm group 637 host group 640 hosttopn group 640 matrix group 640 event group 641 rmon-2 groups 641 protocol directory group 642 protocol distribution group 642 address map...
Page 30
A t echnical s upport online technical services 659 world wide web site 659 3com ftp site 659 3com bulletin board service 660 access by analog modem 660 access by digital modem 660 3com facts automated fax service 661 support from your network supplier 661 support from 3com 661 returning products fo...
Page 31: Bout
A bout t his g uide this switch 4007 implementation guide provides information that you need to understand and use features of the switch 4007 after you install it and attach it to your network. Before you use this guide: ■ install your switch chassis and modular components. See the switch 4007 gett...
Page 32
32 a bout t his g uide scope of this guide the information in this guide pertains to release 3.0.5 software. Switch 4007 modules are pre-loaded with software at the factory. However, the software that was loaded on the components that you received may be an earlier release. Connect to each module an...
Page 33
Conventions 33 table 2 text conventions convention description screen displays this typeface represents information as it appears on the screen. Syntax the word “syntax” means that you evaluate the syntax provided and then supply the appropriate values. Example: to set the system date and time, use ...
Page 34
34 a bout t his g uide switch 4007 documentation the switch 4007 documentation set is comprised of many different titles. Some switch 4007 documents use the product name “corebuilder 9000” in their titles due to the heritage of the product line. Documents are available in three formats: ■ paper docu...
Page 35
Documentation comments 35 documentation comments your suggestions are very important to us. They help us to make our documentation more useful to you. Please send e-mail comments about this guide to: sdtechpubs_comments@ne.3com.Com please include the following information when you comment: ■ documen...
Page 36
36 a bout t his g uide.
Page 37: Nderstanding
I u nderstanding y our s witch 4007 s ystem chapter 1 configuration overview.
Page 39: Onfiguration
1 c onfiguration o verview this chapter lists the basic requirements for building a functional switch 4007, summarizes the system architecture, describes the management interface options, and provides a general configuration procedure. The chapter covers these topics: ■ physical configuration requir...
Page 40
40 c hapter 1: c onfiguration o verview physical configuration requirements and options the switch 4007 chassis provides the following features: ■ bays for two power supplies to provide from 820 watts to 1860 watts, depending on the type and quantity of installed modules. ■ power fault-tolerant mode...
Page 41
System architecture 41 options the switch 4007 offers the following options for high device availability: ■ you can install a second management module for redundant management and chassis controller functions ■ the switch provides intelligent n+1 power and environmental management systems. See the s...
Page 42
42 c hapter 1: c onfiguration o verview management options depending on the task you want to accomplish or what kind of information you need, you have the following management options on the switch 4007: ■ management module console ■ switching module administration console ■ web management software ...
Page 43
Management options 43 switching module administration console each switch fabric module and lan interface module has a built-in management interface called the administration console. It is a menu-driven cli that provides module-specific menus and parameters. (i.E., the menus are different between l...
Page 44
44 c hapter 1: c onfiguration o verview ■ webmanage framework — to group your access links to the devices that you manage ■ filter builder — to create and test filters for packets on your switch ■ form-specific help — to get more information about webconsole, deviceview, and performance forms after ...
Page 45
Management access 45 management access after you assign a unique ip address to the management module, you can access the system through the ip interface in one of the following ways: ■ through up to four remote telnet sessions to the administration console. (you can establish up to four remote (teln...
Page 46
46 c hapter 1: c onfiguration o verview modem port access you can access the management interfaces from your pc or macintosh using an external modem attached to the modem serial port. The system transmits characters that you have entered as output on the modem port. The system echoes characters that...
Page 47
System configuration process 47 system configuration process this guide assumes that you have completed the physical installation process for all items in the switch 4007 chassis successfully and that you are ready to begin configuring and managing your system. Use this switch 4007 implementation gu...
Page 48
48 c hapter 1: c onfiguration o verview ■ ethernet — to label ethernet ports, set the port mode, enable flow control, and control autonegotiation and other settings, see chapter 8. ■ bridge-wide and bridge port parameters — to set parameters for spanning tree protocol, ipx snap translation, and ip f...
Page 49
System configuration process 49 5 repeat steps 1through 4 (as applicable) for each module in your system. 6 take advantage of device monitoring features as you monitor network operations. You can use device monitoring features such as event logging, baselining, and roving analysis to analyze your ne...
Page 50
50 c hapter 1: c onfiguration o verview.
Page 51: Nderstanding
Ii u nderstanding t he m anagement m odule chapter 2 overview of the management module chapter 3 installing management modules chapter 4 configuring and using eme options chapter 5 managing the chassis power and temperature.
Page 53: Verview
2 o verview of the m anagement m odule this chapter introduces the management module for the switch 4007. It addresses these topics: ■ module overview ■ module components ■ module functions ■ impact on the network before you start before you install the management module or begin to explore the opti...
Page 54
54 c hapter 2: o verview of the m anagement m odule module overview the management module is an snmp-based network management module that: ■ provides chassis controller functions (such as power and temperature monitoring), as well as management functions (such as collecting and sending snmp traps). ...
Page 55
Module functions 55 module functions the management module provides the following management and control capabilities: ■ configurations — when you are logged in with administer access, you can configure the management module and monitor the chassis environment. ■ management module standby support — ...
Page 56
56 c hapter 2: o verview of the m anagement m odule ■ telnet support — you can connect a management module to any other telnet device. The management module also supports incoming telnet sessions so that you can manage an management module or another module from a workstation with telnet support or ...
Page 57: Nstalling
3 i nstalling m anagement m odules this chapter describes installation and setup procedures for the switch 4007 management modules. The sections are: ■ installing modules ■ creating a redundant configuration ■ verifying management module operation ■ making management connections ■ eme technical spec...
Page 58
58 c hapter 3: i nstalling m anagement m odules installing modules one management module (eme) is required in each chassis. A second is optional for redundancy. The slots for management modules are obviously in the upper portion of the chassis due to their smaller size. 3com recommends that you inst...
Page 59
Creating a redundant configuration 59 creating a redundant configuration to establish a redundant management configuration, you must have two management modules (emes) installed in the chassis. The slots for management modules are obviously in the upper portion of the chassis due to their smaller si...
Page 60
60 c hapter 3: i nstalling m anagement m odules thus, the system generally treats both emes as a single logical device. (however, for some management activities, such as image download and telnet connections, you must treat the two modules as separate devices.) the primary eme and the secondary eme ...
Page 61
Creating a redundant configuration 61 the standby led, located on front panel of the eme that fails over, continues to display active . This is because the two components that make up the eme (smc and scc) are independent of each other. Therefore, when the smc fails over, the scc on the same eme con...
Page 62
62 c hapter 3: i nstalling m anagement m odules verifying management module operation after you install a management module in the chassis and before you install other modules, verify that the management module is operating correctly. This section explains how to verify operation before you begin to...
Page 63
Making management connections 63 the display button the front panel of the management module includes a display button that is located next to the led display, and labeled dsply . The led display shows status information when you power on the management module, and shows pri when the management modu...
Page 64
64 c hapter 3: i nstalling m anagement m odules using an mdi-to-mdi crossover cable the 10base-t port is configured as an mdi or host port. To connect the management module to an mdi crossover (mdi-x) or switch port, use a standard rj-45 jumper cable. To connect the management module directly to a h...
Page 65
Making management connections 65 table 10 lists 9-pin-to-9-pin assignments for connecting your pc to the front panel of the management module. Table 11 lists 9-pin-to-25-pin assignments for connecting your pc to the front panel of the management module. Table 9 auxiliary port pinouts pin signal name...
Page 66
66 c hapter 3: i nstalling m anagement m odules using a modem the management module console port permits dial-in modem use. To use a dial-in modem: 1 ensure that the modem supports the at command set. 2 select one of the following baud rates: 300, 1200, 2400, 4800, 9600, 19200, or 38400. The factory...
Page 67
Making management connections 67 verifying network connectivity to verify that the chassis and all modules have been installed correctly: 1 confirm that communication can be established on all network segments that you have enabled. 2 confirm that the network activity led on each installed module co...
Page 68
68 c hapter 3: i nstalling m anagement m odules troubleshooting power-on problems table 14 lists common problems that can arise when you install your eme and possible solutions. Under normal conditions, when you install the eme, the status led lights and the character display shows the eme’s operati...
Page 69
Eme technical specifications 69 eme technical specifications table 15 lists general specifications, table 16 lists power specifications, table 17 lists environmental specifications, and table 18 lists mechanical specifications for the eme. Table 15 eme general specifications element specification co...
Page 70
70 c hapter 3: i nstalling m anagement m odules.
Page 71: Onfiguring
4 c onfiguring and u sing eme o ptions this chapter describes how to configure an installed management module (eme). This chapter contains the following sections: ■ quick reference configuration ■ connecting to the system ■ in-band connections ■ configuring the terminal ■ customizing your system ■ c...
Page 72
72 c hapter 4: c onfiguring and u sing eme o ptions quick reference configuration table 19 outlines the basic steps for configuring your management module (eme). Saving configuration values when you make configuration changes to the eme using any of the set commands, they take effect immediately and...
Page 73
Connecting to the system 73 connecting to the system this section addresses procedures and commands that you can use to prepare the system (the eme’s cli) to receive connections from terminals or remote workstations or receive requests for access to the embedded web server. This section also describ...
Page 74
74 c hapter 4: c onfiguring and u sing eme o ptions 3 use the set ip ip_address command to assign a unique ip address to the eme (rj-45 type connector). Example: cb9000> set ip ip_address 195.36.58.27 ethernet_port 4 use the set ip subnet_mask command to assign a subnet mask to the eme. For example,...
Page 75
Connecting to the system 75 3 log in to the remote device and manage the device using commands that are appropriate to that device. You can create one outgoing telnet session on each of the two console ports. 4 to log out of the remote device, use the appropriate command for that device. After you h...
Page 76
76 c hapter 4: c onfiguring and u sing eme o ptions 2 assign the terminal settings using the following command: set terminal stop_bits, terminal_type> set the terminal to match the remote terminal settings. 3 enable slip mode using the following command: set terminal mode slip where is auxiliary or ...
Page 77
Entering commands 77 entering commands this section describes ways to enter commands and display command options. The command completion feature the command completion feature allows the interface to accept abbreviated command input. You need only to enter a minimum number of characters to distingui...
Page 78
78 c hapter 4: c onfiguring and u sing eme o ptions listing command options to display a list of top-level menu options from the cb9000> prompt, type ? And press enter. Then, to display a list of submenus or options for any of those options, type one of the options followed by one space and ? And pr...
Page 79
Entering commands 79 you can continue using ? In this manner. Example: cb9000>> show ? Possible completions: chassis clock community eme event_log file host interface inventory ip login module power security servdiag snapshot snmp sntp terminal web cb9000>> show each command as a list of options ass...
Page 80
80 c hapter 4: c onfiguring and u sing eme o ptions keystroke functions you can alter your keyboard input using specific keyboard functions and control sequences. If you press enter in the middle of a command entry when a parameter is expected, the eme prompts you for additional information. Table 2...
Page 81
Configuring the terminal 81 configuring the terminal this section describes: ■ configuring the terminal to default settings ■ changing the terminal configuration ■ customizing terminal settings configuring the terminal to default settings configure the terminal that is attached to the serial port on...
Page 82
82 c hapter 4: c onfiguring and u sing eme o ptions 4 press enter. The eme displays the following message and prompt: welcome to administer service on cb9000. Cb9000> you are now logged in as the admin with full access to all commands.To show the current terminal settings, use the show terminal comm...
Page 83
Configuring the terminal 83 setting terminal hangup if you use a modem connection to log in to the eme, use the set terminal console hangup command. This command causes the eme to de-assert the rs-232 dtr signal when you log out of the eme. This forces the modem to hang up the connection and may hel...
Page 84
84 c hapter 4: c onfiguring and u sing eme o ptions example: cb9000> set terminal timeout system 10 after you set the timeout, the terminal automatically logs you out of the system if there is no terminal (keyboard) activity for the period of time that you have specified. In this example, logout occ...
Page 85
Configuring the terminal 85 characters are lost when connected to the eme through a modem. Make sure the stop_bits value on the terminal is set to 2stop_bits. The management prompt on the screen is not as you set it. You may be connected to a remote device. See the telnet and logout commands describ...
Page 86
86 c hapter 4: c onfiguring and u sing eme o ptions customizing your system you can alter the factory defaults to customize various aspects of your system, including its name, as associated contact name, and whether the eme runs diagnostics as part of its boot sequence. Assigning a unique name you c...
Page 87
Customizing your system 87 after you enter each command, the eme prompts you to enter a line of text, which can be up to 78 characters: cb9000>enter one line of text: the eme commands time out if you do not enter text within 15 seconds. Configuring the internal clock use the set clock date_time comm...
Page 88
88 c hapter 4: c onfiguring and u sing eme o ptions 15 [gmt+2:00] eet 16 [gmt+3:00] bt 17 [gmt+4:00] zp4 18 [gmt+5:00] zp5 19 [gmt+5:30] bombay/calcutta/madras/new dehli/colombo 20 [gmt+6:00] zp6 21 [gmt+7:00] wast 22 [gmt+8:00] cct 23 [gmt+9:00] jst 24 [gmt+9:30] darwin/adelaide 25 [gmt+10:00] east...
Page 89
Configuring user logins 89 configuring user logins this section describes the different commands for assigning user (network personnel) access levels and login functions:, setting up passwords, and adding or deleting user profiles. User access levels the eme provides three levels of user access: ■ a...
Page 90
90 c hapter 4: c onfiguring and u sing eme o ptions setting the password by default, the eme has no password. The first time that you log in, you press enter at the password: prompt. To set a password for the default log in username, use the set login password command. Setting a password for the def...
Page 91
Configuring user logins 91 4 at the enter login name: prompt, enter the login name for the user that you want to add. 5 at the enter login password: prompt, enter the user’s login password. 6 at the verify - re-enter password: prompt, enter the new password again. The system acknowledges the new pas...
Page 92
92 c hapter 4: c onfiguring and u sing eme o ptions table 23 describes the fields in the show login display. Table 23 fields in the show login display column description index index number of each of the 10 available logins login name name assigned to each login access privilege level assigned to th...
Page 93
Configuring user logins 93 clearing login names you may want to clear login names from the eme periodically to help ensure system security. Only a user with administer access can clear other users. You can enter either the index number of the user or users that you want to clear or all to clear all ...
Page 94
94 c hapter 4: c onfiguring and u sing eme o ptions configuring snmp values the simple network management protocol (snmp) is a standard that is defined by the internet engineering task force (ietf). Snmp information is encapsulated in a udp and ip packet, which in turn, is encapsulated in an appropr...
Page 95
Configuring snmp values 95 setting a subnet mask use the set ip subnet_mask command to assign a subnet mask to the eme. For example, to set the subnet mask for a class b device, without subnetworks, enter a command similar to the following: cb9000> set ip subnet_mask 255.255.0.0 ethernet_port cautio...
Page 96
96 c hapter 4: c onfiguring and u sing eme o ptions creating a community table use the community table to define: ■ snmp stations on the network that access information from the eme ■ snmp stations that receive traps from the eme to enable the eme to receive snmp alarms, you must add the following i...
Page 97
Configuring snmp values 97 configuring a trap destination to set up a destination for snmp traps, use this command at the eme prompt: set snmp trap destination where is the community string of the selected trap where you want to send the trap and is the ip address of the trap receiver. Configuring t...
Page 98
98 c hapter 4: c onfiguring and u sing eme o ptions to enable or disable the trap filter link state, use these commands: set snmp trap filter link_state disable set snmp trap filter link_state enable to enable or disable the trap filter for detecting a spanning tree protocol topology change on one o...
Page 99
Configuring snmp values 99 table 24 describes the first two fields in the trap message. The remainder of the fields are dependent upon the type of trap that is received and are self-explanatory. Snmp traps are sent to the eme console when traps occur. An example of an snmp trap is when a device atte...
Page 100
100 c hapter 4: c onfiguring and u sing eme o ptions configuring the event log the eme maintains a log of informational events, nonfatal errors, and fatal errors that occur on all modules in the chassis. Event log entries are stored in the chronological order in which they are received. When two eme...
Page 101
Using the file system 101 using the file system the file system is an area on the management module that stores: ■ software configuration files ■ the event log the file system also acts as a temporary storage area for software images that are downloading through the management module to other module...
Page 102
102 c hapter 4: c onfiguring and u sing eme o ptions 82904 jul 25 1999 9:52:15 bladeconfig.06.01 82904 jul 25 1998 9:52:19 bladeconfig.05.01 number of files: 13 number of bytes in file system: 11945984 number of bytes used: 1157120 number of bytes available: 10788864 number of bytes cleaned: 1078886...
Page 103
Using the file system 103 before you clear the file system, you can store a copy of the event log on the file server with the upload eme event_log command, if you want to save the content of this file. Example: cb9000> clear file_system !!Warning!! This command will clear all files and reset the eme...
Page 104
104 c hapter 4: c onfiguring and u sing eme o ptions resetting system components certain situations require that you reset power to the entire chassis, certain switching modules, or the eme. This section describes the commands for performing such actions. Resetting the chassis use the reset chassis ...
Page 105
Resetting system components 105 resetting the eme use the following commands to reset the eme: ■ reset eme cold — use this command after you downgrade software releases. This command cycles the power (off/on) and runs the eme diagnostic (diags) software which updates the eme’s power on verification ...
Page 106
106 c hapter 4: c onfiguring and u sing eme o ptions 4 enter force as the password. 5 press the eme reset button within 5 seconds after you have pressed enter. A series of reports appear ending with the following message: nvram not initialized or corrupt. Loading factory defaults. You can now log in...
Page 107
Running diagnostic tests 107 running diagnostic tests use the servdiag command to run diagnostic tests on any switching module that you specify. This command is useful if you suspect a problem on the module or if you notice that the module is behaving inconsistently. The syntax for this command is: ...
Page 108
108 c hapter 4: c onfiguring and u sing eme o ptions reporting diagnostic errors if the servdiag test encounters an error, and if it is set to stop on the error, the module does not function. If this occurs, call your 3com reseller or 3com technical support immediately to obtain assistance. See “the...
Page 109
Obtaining technical assistance 109 the verbosity characteristic the verbosity characteristic determines the amount of output that the diagnostic test sends to the console. Two options are available: ■ normal — the test reports results at the end of the test or when it encounters an error. This is th...
Page 110
110 c hapter 4: c onfiguring and u sing eme o ptions.
Page 111: Anaging
5 m anaging the c hassis p ower and t emperature this chapter describes how to configure and manage the chassis power and temperature parameters using commands from the management module. This chapter contains the following topics: ■ managing power in the chassis ■ load-sharing power supplies ■ budg...
Page 112
112 c hapter 5: m anaging the c hassis p ower and t emperature managing power in the chassis the chassis provides a fault-tolerant, managed, intelligent power supply subsystem. This subsystem supports: ■ load-sharing power supplies ■ high power availability ■ eme-based power verification features th...
Page 113
Load-sharing power supplies 113 software-driven power management also provides protection against the possibility of a catastrophic power failure. If the chassis is operating in power non-fault-tolerant mode and a power supply fails, installed emes power off selected (low power class) modules until ...
Page 114
114 c hapter 5: m anaging the c hassis p ower and t emperature power non-fault-tolerant mode power non-fault-tolerant mode is: ■ a user-selectable mode in which 100 percent of the power that can be allocated to modules is available to them (no power is held in reserve). ■ the default mode for power ...
Page 115
Load-sharing power supplies 115 if a power supply fails while the chassis is running in fault-tolerant mode: ■ the eme automatically disables fault-tolerant mode. ■ power formerly reserved is made available by power class and slot location to power-enabled modules to prevent them from powering off (...
Page 116
116 c hapter 5: m anaging the c hassis p ower and t emperature enabling and disabling power to slots you can enable or disable power to any slot in your chassis, and the eme does not turn on power to the module in the disabled slot. Modules in disabled slots are not allocated power. All slots are en...
Page 117
Load-sharing power supplies 117 power class settings a power class setting is a value in the range of 1 through 10 that is assigned to each module. The highest setting is 10. Each module has a default power class setting, which you can change with an eme command. The eme uses the power class setting...
Page 118
118 c hapter 5: m anaging the c hassis p ower and t emperature power class 10 warnings the eme cannot automatically power off a module that is assigned a power class setting of 10. For example, if a power supply failure causes a power deficit (or if a chassis overheat condition develops), a module t...
Page 119
Budgeting power 119 the eme provides initial module power consumption values from the power consumption table that it maintains: ■ when an eme powers on a module, it adjusts the available power budget to reflect the power consumption of the newly powered-on module. ■ the eme then powers on remaining...
Page 120
120 c hapter 5: m anaging the c hassis p ower and t emperature determining chassis power budget to ensure optimal power fault-tolerance, determine the current power budget for the chassis as follows: 1 at the terminal prompt, enter: show power budget the show power budget command shows the amount of...
Page 121
Budgeting power 121 power supply output in non-fault-tolerant mode in table 28, values are rounded values that do not include system overhead (fans, backplane, signalling, and emes). Table 28 shows the power available in power non-fault-tolerant mode (by voltage type) when the power supply is 930 wa...
Page 122
122 c hapter 5: m anaging the c hassis p ower and t emperature overheat conditions an overheat condition exists when one of the chassis temperature sensors detects a chassis internal operating temperature that exceeds a predefined threshold. The allowable ambient temperature operating range is 0 °c ...
Page 123
Overheat conditions 123 enabling and disabling automatic module power-off to enable automatic module power-off in response to an overheat condition, use the set power overheat_auto_power_down command as follows: set power overheat_auto_power_down mode enable set power overheat_auto_power_down mode d...
Page 124
124 c hapter 5: m anaging the c hassis p ower and t emperature overheat power-off process the module overheat power-off process is as follows: 1 when any chassis temperature sensor detects an internal chassis operating temperature of 45 °c (113 °f) or higher, power management issues warning traps th...
Page 125
Saved power management configurations 125 overheat recovery process overheat recovery occurs when the temperature sensor that detected an overheat condition reports that internal chassis temperature is at or below the overheat threshold. When overheat recovery is initiated, modules that were powered...
Page 126
126 c hapter 5: m anaging the c hassis p ower and t emperature when the chassis powers on or after a chassis reset, the eme compares saved slot profile data for the modules that are installed in each successive slot with current slot profile data for those same modules. Module power is based on powe...
Page 127
Displaying operating conditions 127 displaying module information use the show module commands to display status information for a module and submodule that is installed in a specific slot or to display information for all modules and submodules that are installed in the chassis. The following show ...
Page 128
128 c hapter 5: m anaging the c hassis p ower and t emperature displaying power information use the show power commands to display the power budget, power modes, and power information on a per-slot basis. Table 31 lists the commands that display current power conditions in the chassis. When you ente...
Page 129
Displaying operating conditions 129 displaying chassis inventory information the show inventory command displays contents of a chassis, including hardware release numbers and serial numbers. You can display inventory with the following options: ■ show inventory chassis ■ show inventory module ■ show...
Page 130
130 c hapter 5: m anaging the c hassis p ower and t emperature.
Page 131: III
Iii u nderstanding y our s witching m odules chapter 6 module parameters chapter 7 physical port numbering chapter 8 ethernet chapter 9 bridge-wide and bridge port parameters chapter 10 class of service (cos) chapter 11 ip multicast filtering with igmp chapter 12 trunking chapter 13 resilient links ...
Page 132
Chapter 19 open shortest path first (ospf) routing chapter 20 ipx routing chapter 21 appletalk routing chapter 22 qos and rsvp chapter 23 device monitoring.
Page 133: Odule
6 m odule p arameters this chapter provides guidelines and other key information about how to implement module parameters. The chapter covers these topics: ■ module parameters overview ■ key concepts ■ if the module being hot-swapped is the same type as the module that was removed from a chassis, th...
Page 134
134 c hapter 6: m odule p arameters module parameters overview you use the module parameters to set values for specific functions, or to modify values that are set on a module during power-on. You can modify only some of the module parameters values. Features using the module parameters, you can set...
Page 135
Key concepts 135 key concepts this section explains how to set and modify module values for applicable parameters and defines terms that are used during each process. How to set and modify module parameters the module parameter values are set at the factory or during power-on. The basic steps for se...
Page 136
136 c hapter 6: m odule p arameters nvdata when you work with nvdata, you can: ■ restore the module’s nvdata values to their factory defaults, using the reset option. Use the reset option if you have problems with a new setting and want to start over again. ■ prepare the system (update the image nam...
Page 137: Hysical
7 p hysical p ort n umbering this chapter provides guidelines and other key information about port numbering in the switch 4007 system. The chapter covers these topics: ■ slot architecture ■ default port settings ■ allocating switch fabric capacity to slots ■ key guidelines for implementation ■ effe...
Page 138
138 c hapter 7: p hysical p ort n umbering default port settings table 32 describes the default backplane port settings of switch 4007 modules. Table 32 default port settings module factory default setting for front panel ports factory default setting for backplane ports notes switch fabric modules ...
Page 139
Default port settings 139 configuring port status you can enable (place on-line) or disable (place off-line) switch 4007 ports. When a port is enabled, frames are transmitted normally over that port. When a port is disabled, the port neither sends nor receives frames. Caution: before you can configu...
Page 140
140 c hapter 7: p hysical p ort n umbering allocating switch fabric capacity to slots this section describes how the capacities of the 9-port and 24-port gigabit ethernet switch fabric modules are distributed to the other switching module slots in the chassis. 9-port gen switch fabric module the cap...
Page 141
Allocating switch fabric capacity to slots 141 24-port gen switch fabric module the capacity of the 24-port gigabit ethernet switching fabric module (3cb9fg24t ) is distributed across the slots in the chassis. The module capacity is expressed in terms of backplane ports. When a switching module is i...
Page 142
142 c hapter 7: p hysical p ort n umbering using table 34: examples suppose you installed a 24-port switch fabric module. Next, you installed a 36-port fast ethernet layer 2 switching module in slot 4. After both module’s boot sequences were finished, you should see led #7 and #8 on the switch fabri...
Page 143
Effects of removing a module 143 effects of removing a module when you remove a module and leave the slot empty, a number of changes occur. Vlan changes when you remove a module, vlan changes occur as follows: ■ if you have a vlan that includes ports that are associated with the removed module, thos...
Page 144
144 c hapter 7: p hysical p ort n umbering effects of replacing modules when you remove a module and replace it with another module, a number of changes can occur, depending on the replacement module. Replacing modules of the same type if you remove a module and replace it with a module of the same ...
Page 145: Thernet
8 e thernet this chapter provides guidelines and other key information about how to implement ethernet ports. The chapter covers these topics: ■ ethernet overview ■ key concepts ■ key guidelines for implementation ■ port enable and disable (port state) ■ port labels ■ autonegotiation ■ port mode ■ f...
Page 146
146 c hapter 8: e thernet ethernet overview ethernet is a standardized, switched, packet-based network that supports an exponential hierarchy of three line speeds: ■ 10 mbps — ethernet ■ 100 mbps — fast ethernet ■ 1000 mbps — gigabit ethernet all speeds of ethernet are based on an ieee 802.3 standar...
Page 147
Ethernet overview 147 benefits ethernet, fast ethernet, and gigabit ethernet technologies allow you to configure and optimize: ■ link bandwidths ■ link availability link bandwidths as your network needs to support more users and increasingly bandwidth-intensive applications, you can configure ethern...
Page 148
148 c hapter 8: e thernet key concepts these concepts are important to implementing ethernet: ■ carrier sense multiple access with collision detection (csma/cd) — the standardized ethernet protocol that controls device access to the network ■ collision — when two or more stations attempt to transmit...
Page 149
Key concepts 149 ■ pace interactive access — an algorithm that controls traffic flow on a point-to-point link with an end station. In a typical half-duplex ethernet connection, you can never achieve high rates of utilization because of the randomness of collisions. If a switch and end station both t...
Page 150
150 c hapter 8: e thernet ethernet packet processing all frames on an ethernet network are received promiscuously by an ethernet port. A port can discard frames for either of the following reasons: ■ there is no buffer space available. ■ the frame is in error. Figure 1 shows the order in which frame...
Page 151
Key concepts 151 frames also may be delivered directly to an ethernet port by bridge, router, or management applications. However, a transmitted frame can be discarded for any of the following reasons: ■ the ethernet port is disabled. ■ there is no room on the transmit queue. ■ an error occurred dur...
Page 152
152 c hapter 8: e thernet key guidelines for implementation consider these important factors when you implement and configure ethernet networks: link bandwidths recommended link capacities in a network normally depend on the speed requirements of end-user workstations, as shown in table 35. In areas...
Page 153
Port enable and disable (port state) 153 port enable and disable (port state) you can enable ethernet ports (place them on-line) or disable them (place them off-line). Important considerations ■ because it stops all network traffic through the port, disabling a port may adversely affect a live netwo...
Page 154
154 c hapter 8: e thernet autonegotiation this feature enables some ports to identify and negotiate speed and duplex mode with a remote device. Important considerations ■ in most cases, if autonegotiation does not properly detect the remote port speed, the vendor of the remote device implemented eit...
Page 155
Autonegotiation 155 ■ 10/100base-tx ports — enabling autonegotiation causes both the port speed and duplex mode attributes to be autonegotiated. ■ 100base-fx ports — no autonegotiation of duplex mode occurs. The port speed is fixed at 100 mbps. The default duplex mode is half-duplex . ■ 1000base-sx ...
Page 156
156 c hapter 8: e thernet port mode you can change the port speed and duplex mode for 10/100base-tx ports and the duplex mode for 100base-fx ports. You cannot change the port speed or duplex mode for gigabit ethernet ports. Important considerations ■ when you configure duplex mode, configure both se...
Page 157
Flow control 157 flow control the flow control mode allows a fast ethernet port or a gigabit ethernet port to: ■ decrease the frequency with which it sends packets to a receiving device, if packets are being sent too rapidly. ■ send flow control packets to a sending device, to request that the devic...
Page 158
158 c hapter 8: e thernet pace interactive access pace interactive access (which is called pace access on layer 2 modules) prevents excessive network jitter (variation in the timing of packet delivery that can cause garbled sound, jerky images, and delays). Pace technology also improves timing and o...
Page 159
Standards, protocols, and related reading 159 standards, protocols, and related reading the system supports these ethernet standards: ■ ieee 802.3 — 10base-t ethernet over unshielded twisted pair (utp) ■ ieee 802.3u — 100base-t fast ethernet over utp or fiber-optic cable ■ ieee 802.3z — 1000base-sx ...
Page 160
160 c hapter 8: e thernet 1000base gigabit interface converter (gbic) ports are hot-swappable, that is, you can replace one gbic connector while the other connectors continue to carry traffic. To ensure optimal compatibility, performance, and regulatory compliance, use only gbic transceivers and con...
Page 161: Ridge
9 b ridge -w ide and b ridge p ort p arameters this chapter provides an overview of bridging concepts and implementation guidelines for modules in the switch 4007. The chapter covers these topics: ■ bridging overview ■ key bridging concepts ■ bridging implementation summary ■ key guidelines for impl...
Page 162
162 c hapter 9: b ridge -w ide and b ridge p ort p arameters bridging overview operating at the data link layer (layer 2) of the osi reference model, a bridge interconnects two or more lans and allows them to communicate as if they were one lan. Bridges examine incoming frames, make forwarding decis...
Page 163
Key bridging concepts 163 key bridging concepts before you configure bridge-wide or bridge port settings on your module, you may find it helpful to review the following concepts. Learning addresses bridges learn addresses so that they can, over time, more effectively determine which frames to forwar...
Page 164
164 c hapter 9: b ridge -w ide and b ridge p ort p arameters forwarding, filtering, and flooding a bridge filters, floods, or forwards frames by comparing: ■ the frame’s destination address to the source addresses in the bridge’s address table. ■ the destination bridge port (if known) to the port on...
Page 165
Bridging implementation summary 165 you can configure a single path topology purely with cabling. However, the spanning tree protocol (stp) gives you a way to configure redundant cable paths but yet maintain only one active path between two devices. Stp monitors the status of all paths and, if an ac...
Page 166
166 c hapter 9: b ridge -w ide and b ridge p ort p arameters ■ spanning tree protocol — you can configure bridge-wide and bridge port settings to enable stp to detect loops and calculate a network topology that reflects a single, loop-free path between any two devices. For conceptual information abo...
Page 167
Key guidelines for implementation 167 ■ resilient links (layer 2 switching modules only) — resilient links protect your network against an individual link or device failure by providing a secondary backup link that is inactive until needed. For more information about resilient links, seethe resilien...
Page 168
168 c hapter 9: b ridge -w ide and b ridge p ort p arameters port forwarding behavior table 40 summarizes the forwarding behavior of bridge ports based on the bridge and port stp states: when stp is removed from the port but is enabled for the bridge, the port is invisible to stp but can forward fra...
Page 169
Key guidelines for implementation 169 stp not compatible with resilient links if you want to define one or more resilient link pairs on a layer 2 switching module, stp cannot be enabled: ■ if stp is enabled and you define a resilient link pair, the module rejects it toward the end of the definition ...
Page 170
170 c hapter 9: b ridge -w ide and b ridge p ort p arameters stp terms and concepts this section provides a conceptual review of stp terms, parameters, and processes. To learn how you can manipulate stp parameters, see “stp bridge and port parameters” in this chapter. Configuration messages in order...
Page 171
Stp terms and concepts 171 the bridges that are chosen as the best path, called designated bridges, form the second level of the hierarchy. ■ a designated bridge relays network transmissions to the root bridge through its root port. Any port that transmits to the root bridge is a root port. ■ the de...
Page 172
172 c hapter 9: b ridge -w ide and b ridge p ort p arameters ■ bridges elect as the designated bridge on each lan the bridge with the least cost path to the root bridge. The designated bridge forwards frames between that lan and the path to the root bridge. For this reason, the root bridge is always...
Page 173
Stp terms and concepts 173 contents of cbpdus bridges use information in cbpdu to calculate a stp topology. The content of a cbpdu includes: ■ root id — the identification number of the root bridge. ■ cost — the cost of the least-cost path to the root from the transmitting bridge. One of the determi...
Page 174
174 c hapter 9: b ridge -w ide and b ridge p ort p arameters example 2. Root id is the same for message 1 and message 2, but cost is lower in message 1. The bridge saves message 1. Example 3. Root id and cost are the same for message 1 and message 2, but the transmitting bridge id is lower in messag...
Page 175
Stp terms and concepts 175 4 because the bridge now knows the root bridge, it can determine its distance to the root and elect a root port. It examines cbpdus from all ports to see which port has received a cbpdu with the smallest cost to the root. This port becomes the root port. 5 now that the bri...
Page 176
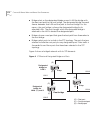
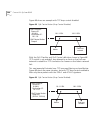
176 c hapter 9: b ridge -w ide and b ridge p ort p arameters figure 5 starting the spanning tree calculation lan 5 bridge a bridge b bridge c bridge d bridge e bridge f lan 1 lan 2 lan 3 lan 6 lan 4 12.0.12 10.0.10 20.0.20 81.0.81 29.0.29 35.0.35 xx.X.Xx = cbpdu (root id.Cost.Transmitter id) l2/3 l2...
Page 177
Stp terms and concepts 177 figure 6 spanning tree topology calculated lan 5 bridge a bridge b bridge c bridge d bridge e bridge f lan 1 lan 2 lan 3 lan 6 lan 4 10.11.12 10.0.10 10.11.20 10.12.81 10.11.29 10.11.35 root bridge (r) (b) (d) (r) (b) (r) (d) (r) (d) (d) (d) (d) (r) (b) = cbpdu (root id.Co...
Page 178
178 c hapter 9: b ridge -w ide and b ridge p ort p arameters determining the root bridge the root id portion of the cbpdu determines which bridge actually becomes the root bridge. In figure 5, notice how each bridge initially assumes that it is the root bridge and transmits a cbpdu that contains its...
Page 179
Stp terms and concepts 179 a designated bridge must be determined for lans 3, 4, and 6: ■ because bridges c, d, and f are all attached to lan 3, one of them must be the designated bridge for that lan: ■ the algorithm first compares the root id of these bridges, which is the same for all. ■ the cost ...
Page 180
180 c hapter 9: b ridge -w ide and b ridge p ort p arameters spanning tree port states because stp determines the network configuration based on events that occur, it places bridge ports in one of the five states at all times. Table 41 describes these states. Table 41 spanning tree protocol port sta...
Page 181
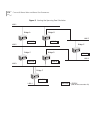
Stp terms and concepts 181 figure 7 illustrates the factors that cause a port to change from one state to another. The arrows indicate the direction of movement between states. The numbers correspond to the factors that affect the transition. Figure 7 factors involved in spanning tree port state tra...
Page 182
182 c hapter 9: b ridge -w ide and b ridge p ort p arameters reconfiguring the bridged network topology stp reconfigures the bridged network topology when any of the following occurs: ■ bridges are added or removed. ■ the root bridge fails. ■ you change any of the bridging parameters that determine ...
Page 183
Stp bridge and port parameters 183 stp bridge and port parameters on any switching module, if you want to use stp, you must first enable it on a bridge-wide basis and then on a per-port basis. This section describes the parameters that you can modify and their implications for your network. On layer...
Page 184
184 c hapter 9: b ridge -w ide and b ridge p ort p arameters bridge priority the bridge priority influences the choice of the root bridge and the designated bridge. The lower the bridge’s priority number, the more likely it is that the bridge is chosen as the root bridge or a designated bridge. The ...
Page 185
Stp bridge and port parameters 185 from a link until news of a topology change has spread to all parts of a bridged network. The delay gives enough time to turn off to all links that need to be turned off in the new topology before new links are turned on. Setting the value too low can result in tem...
Page 186
186 c hapter 9: b ridge -w ide and b ridge p ort p arameters bridge port stp parameters you can modify these stp parameters on each port: ■ port state ■ port path cost ■ port priority port state you can enable, disable, or remove stp for each bridge port on a module. This setting affects the operati...
Page 187
Mac address table design 187 mac address table design all modules recognize two different kinds of addresses: ■ static mac addresses — addresses that you manually add to the bridge address table using menu options. These addresses never age; you must add and remove them manually. ■ dynamic mac addre...
Page 188
188 c hapter 9: b ridge -w ide and b ridge p ort p arameters ■ you can remove individual mac addresses from selected ports. Typically, this action is only applied to the removal of static addresses because the module can quickly relearn dynamic addresses that you remove. ■ a static address is never ...
Page 189
Address aging 189 address aging this section explains how address aging works and identifies the slight differences in options and operation between layer 2 switching modules and multilayer switching modules. Address aging only applies to dynamic addresses. (static addresses are never aged from the ...
Page 190
190 c hapter 9: b ridge -w ide and b ridge p ort p arameters normal aging process each module records in its address table the source address of every received frame (that is not otherwise filtered or discarded) along with the appropriate port number. At the time the table entry is created, an aging...
Page 191
Address aging 191 the module reverts to using the bridge agingtime value as the aging interval after it receives a cbpdu from the root bridge that does not have the topology change flag set. Port down events when a multilayer switching module detects a port down event, it immediately flushes all add...
Page 192
192 c hapter 9: b ridge -w ide and b ridge p ort p arameters if stp state is “aging only” this option is available on layer 2 switching modules only. With this option selected, the module does not operate as an stp bridge but does use two of the stp parameters in certain circumstances related to agi...
Page 193
Address aging 193 ■ if the functioning forward delay is on the high end of the allowable range (4-30 seconds, 15 is the default), this allows more time for an stp network to stabilize but it also delays the transition of ports to the forwarding state because ports are held longer in each of the list...
Page 194
194 c hapter 9: b ridge -w ide and b ridge p ort p arameters frame processing all frames that are received on a physical interface and that are not either discarded or explicitly directed to the module itself are delivered to the corresponding bridge port. The bridge port either forwards each frame ...
Page 195
Ipx snap translation 195 ipx snap translation ipx snap translation (multilayer switching modules only) allows an alternative method of translating ipx packets from ethernet to fddi and vice-versa. ■ when ipx snap translation is enabled, any 802.3_raw ipx packets that are forwarded from ethernet to f...
Page 196
196 c hapter 9: b ridge -w ide and b ridge p ort p arameters important considerations ■ if the limit that you set is reached during a given second of time, all remaining frames that are received in that remainder of that second are dropped. ■ a value of zero means that there is no limit set on the p...
Page 197
Garp vlan registration protocol (gvrp) 197 garp vlan registration protocol (gvrp) to activate gvrp on a multilayer switching module, you enable the garp vlan registration protocol (gvrp) first on the bridge and then on individual bridge ports. On a port-by-port basis, gvrp allows the module to autom...
Page 198
198 c hapter 9: b ridge -w ide and b ridge p ort p arameters send updates, or if gvrp is disabled, or if the module is rebooted, all dynamic vlans are removed. ■ gvrp manages the active topology, not nontopological data such as vlan protocols. If a local bridge needs to classify and analyze frames b...
Page 199: Lass
10 c lass of s ervice (c o s) the ieee 802.1d media access control (mac) bridges standard has been amended in recent years to include various supplements. One such supplement standard is ieee 802.1p: traffic class expediting and dynamic multicast filtering. This chapter describes the traffic priorit...
Page 200
200 c hapter 10: c lass of s ervice (c o s) overview many network technologies, such as ethernet and fiber distributed data interface (fddi), have no inherent ability to distinguish between different types of traffic such as data, voice, and video, or even perhaps between different data applications...
Page 201
Key concepts 201 key concepts before you configure cos options in a layer 2 switching module, review the following key concepts. Basic elements of the standard the two basic elements of the ieee 802.1p standard are: ■ multiple processing queues in devices the standard does not require a specific num...
Page 202
202 c hapter 10: c lass of s ervice (c o s) format of prioritized packets priority level information can only be carried inside packets that are formatted according to the ieee 802.1q standard; such packets carry an extra 2 octets of data called a tag. The priority level information occupies 3 bits ...
Page 203
Cos in your system 203 cos in your system using the administration console on layer 2 switching modules, you can: ■ enable or disable cos (the setting affects all ports), which changes the number of hardware queues per port from one to two. ■ modify how the eight priority levels are assigned between...
Page 204
204 c hapter 10: c lass of s ervice (c o s) important considerations ■ in non-blocking situations, cos settings have no impact on traffic flow through the module. ■ in blocking situations, queue 1 (high priority) traffic on a given port is processed ahead of queue 2 traffic on that same port. Traffi...
Page 205
Cos in your system 205 for example, if you enter any whole number between 88 and 99 as the rate limit, the working rate limit will be 87.5; that is, for every 8 packets received on a given port, 7 packets are selected from queue 1 and 1 packet is selected from queue 2. Table 44 provides a reference ...
Page 206
206 c hapter 10: c lass of s ervice (c o s) handling tagged and untagged packets consider the following points about how a layer 2 module processes tagged and untagged packets with respect to cos information: ■ if cos is enabled and an untagged packet enters a port, the packet is always processed th...
Page 207: Ip M
11 ip m ulticast f iltering with igmp the internet group management protocol (igmp)provides a way for a switch 4007 layer 2 switching modules to forward ip multicast application traffic to certain ports and filter it on other ports to increase bandwidth efficiency in the network. This chapter provid...
Page 208
208 c hapter 11: ip m ulticast f iltering with igmp this chapter describes igmp functions on layer 2 switching modules. Igmp is also supported on multilayer switching modules, but is described in the context of ip multicast routing. See chapter 18for more information. The management interfaces displ...
Page 209
Overview 209 ■ igmp requires minimal configuration in network devices and hosts. For example: ■ snooping and querying functions can be easily enabled in switching devices. ■ ip-capable end stations do not usually require any special configuration because igmp is already part of the ip protocol stack...
Page 210
210 c hapter 11: ip m ulticast f iltering with igmp key concepts igmp plays a specific role in the overall delivery process for ip multicast traffic. Before you modify igmp parameters in a layer 2 switching module, review the following key concepts about ip multicast packets. Devices that generate i...
Page 211
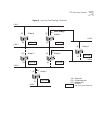
Key concepts 211 figure 9 protocols that coordinate the delivery of ip multicast traffic routers are not required for transmission of ip multicast packets between sources and group members. Compare figure 8 and figure 9; both represent valid designs in which igmp can help conserve bandwidth. Ip mult...
Page 212
212 c hapter 11: ip m ulticast f iltering with igmp routers and switches both construct filters on ports that do not require group traffic to be forwarded. On each device, one group’s traffic may be forwarded to one set of ports and another group’s traffic may be forwarded to a different set of port...
Page 213
Key concepts 213 how hosts use igmp each host uses igmp to communicate with the querier in a few different ways. Host membership reports hosts transmit host membership reports (hereafter called igmp reports) in response to queries. A host sends a separate report for each group that it wants to join ...
Page 214
214 c hapter 11: ip m ulticast f iltering with igmp if the switch flooded igmp reports, hosts on other segments would suppress their own reports for identical groups, which would cause the switch to set overly restrictive filters. Restricted forwarding of igmp reports is necessary to allow the switc...
Page 215
Key implementation guidelines 215 key implementation guidelines consider these points when you configure igmp options in a layer 2 switching module: ■ igmp snooping and querying works for ip multicast packets only. Other protocol-based multicast packets are flooded to all ports in compliance with th...
Page 216
216 c hapter 11: ip m ulticast f iltering with igmp ■ if you have configured open vlan mode and ip multicast packets are tagged (ieee 802.1q format), then the igmp tables in each vlan share information with each other. Vlans do not form barriers in the flow of ip multicast traffic, even though they ...
Page 217
Processing ip multicast packets 217 processing ip multicast packets table 45 summaries how a layer 2 switching module processes various types of igmp packets and other ip multicast packets. * except for the port on which the packet originated. Some ports may not be available for carrying traffic. Tw...
Page 218
218 c hapter 11: ip m ulticast f iltering with igmp effects of mac address aliasing operating as a layer 2 device, your module filters ip multicast traffic by referring to hexidecimal mac addresses that correspond to binary ip multicast group addresses. A multicast mac address is created by selectin...
Page 219
Effects of mac address aliasing 219 important considerations ■ to reduce the effects of mac address aliasing, verify that your ip multicast applications do not use binary group addresses in the range [224 – 239]. [0,128].0.X, where x equals 0 – 255. ■ see table 46 for several examples of permanent r...
Page 220
220 c hapter 11: ip m ulticast f iltering with igmp operating as the querier for a layer 2 switching module to offer itself as a potential igmp querier for its subnetwork or broadcast domains (vlans), you must: 1 enable the igmp snooping option. The module cannot send queries if snooping is disabled...
Page 221
Aging the igmp tables 221 aging the igmp tables if a switching module receives no host reports for a given group on a given port within a certain period of time (the aging interval), it ages that entry in its igmp tables and sets a filter for that group on that port. The aging interval is the period...
Page 222
222 c hapter 11: ip m ulticast f iltering with igmp.
Page 223: Runking
12 t runking this chapter provides guidelines, limitations, and other important information about how to implement the trunking function on switch 4007 modules. This chapter covers the following topics: ■ trunking overview ■ key concepts ■ key guidelines for implementation ■ automatic backplane trun...
Page 224
224 c hapter 12: t runking trunking overview a trunk (also known as an aggregated link) works at layer 2 and layer 3 of the open systems interconnection (osi) model and allows you to combine multiple fast ethernet and gigabit ethernet ports on interface modules into a single high-speed link between ...
Page 225
Trunking overview 225 trunks also enhance network availability because the trunk control message protocol (tcmp) detects and handles physical configuration errors in the point-to-point configuration. The interface module automatically distributes traffic across the ports that are associated with the...
Page 226
226 c hapter 12: t runking it is important to understand the relationships between ethernet, bridge, and vlan port-related information: ■ ethernet port information — each physical port is always listed individually, regardless of whether it is part of a trunk. ■ bridge port information — this inform...
Page 227
Key guidelines for implementation 227 each tcmp agent: ■ periodically transmits a tcmp hellomessage through every trunk port. ■ continuously listens for hellomessages from other trunk ports. ■ builds a list of ports that tcmp has detected. ■ uses this list to activate or deactivate trunk ports to ma...
Page 228
228 c hapter 12: t runking ■ when multiple links are trunked, it can be difficult to manage and troubleshoot individual port-to-port connections if a connectivity problem occurs. This issue may not be of concern in a server farm room. But if you use trunking extensively between wiring closets and da...
Page 229
Key guidelines for implementation 229 trunk capacity guidelines ■ the device-to-device burst-transmission rate across a trunk is limited to the speed of just one of the port-to-port links within the trunk. For example, the maximum burst rate over a 400-mbps pipeline with four trunked fast ethernet l...
Page 230
230 c hapter 12: t runking automatic backplane trunking provides automatic backplane trunking on both the switch fabric module and the managed interface modules (such as the 4-port gbic gen interface module). You can enable or disable this feature at the switch fabric module for any or all of the in...
Page 231
Defining trunks 231 ■ when automatic backplane trunking is enabled, consider these issues: ■ no trunking can be performed on the 2-port or 4-port gen interface module. ■ layer 2 and multilayer switching modules with multiple backplane ports can use the maximum trunk groups available from the switch ...
Page 232
232 c hapter 12: t runking ■ 3com recommends that the tcmp state be enabled . But devices can operate without tcmp. When tcmp is not in effect on a point-to-point link, its configuration validation is simply absent. ■ if your switch has more than one media type (for example, fast ethernet and gigabi...
Page 233
Modifying trunks 233 modifying trunks you can modify a trunk in two ways: ■ you can modify a trunk’s characteristics (for example, the operating mode or the tcmp state). ■ you can add or remove a port from the trunk. Important considerations ■ you must keep at least one port that you defined in the ...
Page 234
234 c hapter 12: t runking standards, protocols, and related reading the switch 4007 supports these ethernet standards: ■ ieee 802.3 — 10base-t ethernet over unshielded twisted pair (utp) ■ ieee 802.3u — 100base-t fast ethernet over utp or fiber ■ ieee 802.3z — 1000base-sx gigabit ethernet over mult...
Page 235: Esilient
13 r esilient l inks this chapter provides an overview, guidelines, and other important information about how to implement resilient links on layer 2 switching modules in your switch 4007 system. The chapter covers these topics: ■ resilient links overview ■ key concepts ■ key guidelines for implemen...
Page 236
236 c hapter 13: r esilient l inks resilient links overview resilient links protect your network against an individual link or device failure by providing a secondary backup link that is inactive until it is needed. A resilient link comprises a resilient link pair that contains a main link and a sta...
Page 237
Key concepts 237 features you can configure these features for resilient links: ■ define — specify a name and the ports that you want to associate with the link. ■ link state — enable or disable a resilient link pair. ■ active port — define either port as the port that carries network traffic. ■ mod...
Page 238
238 c hapter 13: r esilient l inks key guidelines for implementation consider these important factors when you implement and configure resilient links. General guidelines ■ create resilient links before you define your vlans. If you plan to create resilient links to be part of a vlan, create the res...
Page 239
Resilient link state 239 ■ if you have already defined other resilient links on your module, you cannot select ports that are part of an existing resilient link to be part of an additional resilient link pair. ■ you cannot select a trunked port nor the trunk itself as part of a resilient link. ■ the...
Page 240
240 c hapter 13: r esilient l inks.
Page 241: Irtual
14 v irtual lan s (vlan s ) this chapter provides guidelines and other key information about how to manage vlans on your switch 4007. This feature is available on layer 2 and multilayer switching modules. Differences in implementation between these two module groups are noted where applicable . The ...
Page 242
242 c hapter 14: v irtual lan s (vlan s ) you can manage vlan features in either of these ways: ■ from the bridge vlan menu of the administration console. (see the command reference guide.) you can use the administration console after you log in to the system and connect to a module slot. ■ from the...
Page 243
Vlan overview 243 ■ using the spanning tree algorithm in switching devices to control the flow of traffic among lans (for redundant links). These mechanisms work best only in certain types of lan topologies. Vlan technology provides a high-performance and easy-to-implement alternative to routers for...
Page 244
244 c hapter 14: v irtual lan s (vlan s ) the examples in this chapter represent the location of the switch fabric module logically to emphasize its central role in the configuration process. To create vlans in the switch 4007 environment, you configure these components: ■ layer 2 and multilayer swi...
Page 245
Vlan overview 245 features your switch 4007 supports the vlan features listed in table 48. Table 48 vlan features feature layer 2 modules and switch fabric module multilayer modules description vlan mode: allopen or allclosed yes yes on a per-module basis, establishes a less-restrictive vlan environ...
Page 246
246 c hapter 14: v irtual lan s (vlan s ) key concepts before you configure vlans, review the following key concepts. Related standards and protocols the following standards and protocols apply to the vlans that you can configure: ■ ieee 802.1q is a standard for vlans. It aims to: ■ define an archit...
Page 247
Key concepts 247 ■ garp vlan registration protocol (gvrp) — this protocol, which is defined in ieee 802.1q, defines dynamic registration of vlans that use ieee 802.1q tagging (the vlan id). Gvrp is supported for this release on multilayer switching modules. Tagging types the system supports per-port...
Page 248
248 c hapter 14: v irtual lan s (vlan s ) ■ for backplane ports and switch fabric module ports, you must use tagging when these ports are shared by multiple vlans. (only one vlan’s backplane ports can be untagged; in all other vlans defined across the backplane, the backplane ports must be tagged.) ...
Page 249
Key concepts 249 terminology review the following terms: ■ default vlan — the predefined port-based vlan interface on all switch fabric module ports and the ports of each switching module that always uses ■ vid 1 ■ protocol type unspecified (for multilayer switching modules) ■ the name default the d...
Page 250
250 c hapter 14: v irtual lan s (vlan s ) ■ vlan name — the name that you assign to the vlan. It can contain up to 32 ascii characters. If the name includes spaces, enclose the name in quotation marks. The default vlan always uses the name default. ■ dynamic vlan configuration — the method that enab...
Page 251
Key guidelines for implementation 251 if you define multiple interfaces for an ip vlan, you cannot subsequently modify that ip vlan to supply layer 3 address information. If only one routing interface is defined for the ip vlan, then (at release 3.0) you can supply layer 3 address information as lon...
Page 252
252 c hapter 14: v irtual lan s (vlan s ) vlans created by router port ip interfaces by default, the multilayer switching modules use a routing over bridging model, in which any frame is bridged before it is potentially routed. If you want to define ip routing interfaces that use a routing versus br...
Page 253
Key guidelines for implementation 253 design guidelines ■ before you create any vlans, draw your chassis configuration and carefully identify how the vlans that are associated with your modules are bridging (or, for multilayer switching modules, bridging or routing). Remember that each vlan constitu...
Page 254
254 c hapter 14: v irtual lan s (vlan s ) (example: if the backplane and switch fabric module ports for the default vlan are untagged, the backplane and switch fabric module ports for all other vlans must be tagged.) it is safer to tag the backplane and switch fabric module ports of all vlans, altho...
Page 255
Key guidelines for implementation 255 4 on each multilayer switching module with vlans that you want to perform routing, define a routing interface for each protocol-based or network-based vlan. Verify that the routing interface is defined to use the same network or subnetwork as any other module th...
Page 256
256 c hapter 14: v irtual lan s (vlan s ) number of vlans you must evaluate the number of vlans on a per-module basis. The module type determines the number of vlans that can be supported: ■ each layer 2 switching module supports a maximum of 127 port-based vlans. ■ each multilayer switching module ...
Page 257
Key guidelines for implementation 257 ■ decnet counts as one protocol suite for decnet vlans. ■ the unspecified type of protocol suite counts as one, whether or not the default vlan or port-based vlans are defined. Even if you have only the unspecified protocol suite on the system, the limit is stil...
Page 258
258 c hapter 14: v irtual lan s (vlan s ) vlan aware mode for multilayer switching modules only, vlan aware mode accommodates the difference in vlan resource usage as well as tagged-frame ingress rules between release 2.X and release 3.0. For more information on ingress rules, see “rules of vlan ope...
Page 259
Key guidelines for implementation 259 if you do not see the vlan internal resource error message, maintain the default vlan aware mode of allports . In this case, the module can accommodate the number of release 2.X vlans, but it now uses different ingress rules for tagged frames. The administration...
Page 260
260 c hapter 14: v irtual lan s (vlan s ) ■ you can configure overlapping vlans as long as the vlans have some distinguishing characteristic. For example, a bridge port can be shared by multiple vlans as long as there is a distinguishing characteristic for the shared port (for example, for multilaye...
Page 261
Vlan allopen or allclosed mode 261 vlan allopen or allclosed mode the vlan mode affects the way in which a module address table is used. You can select allopen or allclosed as the vlan mode for the switch fabric module or for any layer 2 or multilayer switching module. The default is allopen . Vlan ...
Page 262
262 c hapter 14: v irtual lan s (vlan s ) ■ allclosed — use this restrictive mode if you are concerned about security between vlans. Data cannot be forwarded between vlans (although data can still be routed between vlans). The allclosed mode implies that each vlan that you create has its own address...
Page 263
Vlan allopen or allclosed mode 263 modifying the vlan mode to change your vlan mode for a module: 1 for a multilayer switching module, delete all routing interfaces (including router port ip interfaces). You cannot change the mode if you have router interfaces defined on the module. 2 modify the vla...
Page 264
264 c hapter 14: v irtual lan s (vlan s ) mode requirements table 50 lists the requirements for defining vlans in allopen mode and allclosed mode. Table 50 mode requirements for static vlans type of static vlan requirements port-based (layer 2 and multilayer switching modules) for nonoverlapped port...
Page 265
Vlan allopen or allclosed mode 265 using allopen mode figure 13 shows an allopen configuration between two port-based vlans that share the same address table. In this example, although station-a and station-b share a common address table, they must still adhere to broadcast containment rules. If sta...
Page 266
266 c hapter 14: v irtual lan s (vlan s ) port-based vlans port-based vlans logically group together one or more bridge ports on the module. On multilayer switching modules, they use the generic protocol type unspecified. Each collection of bridge ports is designated as a vlan interface. The vlan in...
Page 267
Port-based vlans 267 modifying the default vlan the default vlan is always associated with a vid of 1, the unspecified protocol type (for multilayer switching modules), and the name default . Initially, the default vlan is also associated with all ports and no tagging. If necessary, you can modify t...
Page 268
268 c hapter 14: v irtual lan s (vlan s ) trunking and the default vlan another benefit of maintaining the default vlan (with any number of ports) involves trunking. 3com strongly recommends that you define your trunks before you define your vlans. Trunking with the default vlan intact trunking acti...
Page 269
Port-based vlans 269 ■ if you have vlans (but no default vlan) and you subsequently modify an existing trunk that has ports in one vlan, any port removed from the trunk is removed from the vlan and no longer has a vlan. For example, on a 12-port multilayer switching module: see chapter 12 for more i...
Page 270
270 c hapter 14: v irtual lan s (vlan s ) user-configured port-based vlans you can explicitly configure port-based vlan interfaces on the layer 2 and multilayer switching modules as well as the switch fabric module. Important considerations when you create this type of vlan interface, review these g...
Page 271
Port-based vlans 271 to define a port-based vlan interface, specify this information: ■ vid, or accept the next available vid. ■ bridge ports that are part of the vlan. (if you have trunk ports, specify the anchor port for the trunk.) ■ protocol type unspecified (on multilayer switching modules) ■ t...
Page 272
272 c hapter 14: v irtual lan s (vlan s ) in this example: ■ a single vlan spans multiple switching modules. (it can be a modified default vlan.) ■ the backplane ports of the switching modules and the switch fabric module are part of the vlan. ■ all traffic that passes between switching modules flow...
Page 273
Port-based vlans 273 figure 16 two vlans with tagged backplane ports table 51 lists the vlan definitions for these port-based vlans: table 51 port-based vlans with tagged backplane ports slot 1 module slot 2 module switch fabric module vlan1 (default): ■ vlan index 1 ■ vid 1 ■ ports 1–5, 21/22 ■ tag...
Page 274
274 c hapter 14: v irtual lan s (vlan s ) example 3: vlans with tagged front-panel ports the configuration in figure 17 shows multiple overlapping vlans that span two 20-port layer 2 switching modules and pass traffic through the switch fabric module (which resides in slot 7 but is logically represe...
Page 275
Port-based vlans 275 when the backplane port of module-yy receives the frame, the tag identifies and knows to which vlan the frame belongs. Figure 17 multiple vlan example with tagged front-panel ports switch fabric module vlan2 vlan3 tagged port xx (slot 3) yy (slot 5) zz (slot 6) switch 4007 chass...
Page 276
276 c hapter 14: v irtual lan s (vlan s ) table 52 lists the vlan definitions for these port-based vlans. Table 52 port-based vlans with tagged front-panel and backplane ports slot 3 module slot 5 module slot 6 module switch fabric module vlan2: ■ vlan index 2 ■ vid 20 ■ ports 1–3, 21/22 ■ tagging n...
Page 277
Port-based vlans 277 dynamic port-based vlans using gvrp for multilayer switching modules, garp vlan registration protocol (gvrp) can help you simplify the management of vlan configurations in your larger networks. Gvrp allows the multilayer switching module to: ■ dynamically create a port-based vla...
Page 278
278 c hapter 14: v irtual lan s (vlan s ) ■ in a gvrp environment, devices must be gvrp-enabled (that is, support gvrp). These devices could be end stations with 3com’s dynamicaccess ® software or other switches that explicitly enable gvrp. ■ vlans created dynamically with gvrp exist only as long as...
Page 279
Port-based vlans 279 example: gvrp figure 18 shows how a gvrp update (with the vid) sent from one end station is propagated throughout the network. Figure 18 sample configuration using gvrp lan 1 r r d lan 2 r d d station sending update with vid d = declaration of attribute r = registration of attri...
Page 280
280 c hapter 14: v irtual lan s (vlan s ) protocol-based vlans for multilayer switching modules, protocol-based vlans enable you to use protocol type and bridge ports as the distinguishing characteristics for your vlans. Important considerations when you create this type of vlan interface, review th...
Page 281
Protocol-based vlans 281 selecting a protocol suite the protocol suite describes which protocol entities can comprise a protocol-based vlan. For example, vlans on the multilayer switching module support the ip protocol suite, which has three protocol entities (ip, arp, and rarp). Table 53 lists the ...
Page 282
282 c hapter 14: v irtual lan s (vlan s ) your multilayer switching modules impose two important limits regarding the number of vlans and the number of protocols: ■ number of vlans supported — to determine the minimum number of vlans that the multilayer switching module can support, use the equation...
Page 283
Protocol-based vlans 283 2 configure an ip routing interface with a network address and subnet mask and specify the interface type vlan . 3 select the ip vlan interface index that you want to bind to that ip interface. If layer 3 information is provided in the ip vlan interface for which you are con...
Page 284
284 c hapter 14: v irtual lan s (vlan s ) the switch fabric module. The ip routing interfaces for ip vlan 3 reside on the same subnet (33.3.3.0). ■ vlan4, an ip vlan on the multilayer switching module in slot 5. ■ for this configuration to work, vlans 2, 3, and 4 define ip routing interfaces, enable...
Page 285
Protocol-based vlans 285 table 54 lists the vlan definitions for the modules in this configuration. Table 54 routing between 2 multilayer modules over the switch fabric module slot 3 module slot 5 module switch fabric module vlan1 (default): ■ vlan index 1 ■ vid 1 ■ ports 1–12, 13 ■ tagging none fro...
Page 286
286 c hapter 14: v irtual lan s (vlan s ) example 2: one-armed routing configuration figure 20 shows a one-armed router configuration. (the switch fabric module resides in slot 7 but is logically represented above the other modules.) in this configuration: ■ there are three layer 2 modules, a multil...
Page 287
Protocol-based vlans 287 figure 20 one-armed routing with multilayer module and layer 2 modules switch fabric module vlan2 vlan3 vlan4 20-port layer 2 module switch 4007 chassis port 1 port 21,22 port 5 port 21,22 port 9 port 21,22 port 13 port 13 tagged port t = vlan1 u = vlan2 t = vlan1 t = vlan2 ...
Page 288
288 c hapter 14: v irtual lan s (vlan s ) table 55 defines the vlans in this one-armed routing configuration. Table 55 vlan definitions for one-armed routing configuration slot 1 layer 2 module slot 2 layer 2 module slot 3 layer 2 module slot 4 multilayer module (routing) switch fabric (layer 2) mod...
Page 289
Network-based ip vlans 289 network-based ip vlans for ip vlans only, you can also configure network-layer subnetwork addresses. With this additional layer 3 information, you can create multiple independent ip vlans with the same bridge ports. Untagged frames are assigned to a network-based vlan acco...
Page 290
290 c hapter 14: v irtual lan s (vlan s ) ■ in allopen mode, you need not supply the ieee 802.1q tagging. However, to ensure line-speed throughput for overlapped network-based ip vlans in allopen mode, supply the ieee 802.1q tagging. Example: network-based vlans figure 21 shows two ip network-based ...
Page 291
Network-based ip vlans 291 figure 21 network-based vlans vlan5; ipx network 2 tagged port switch fabric module vlan2; ip vlan for 22.2.2.0 network vlan3; ipx network 1 vlan4; ip vlan for 44.4.4.0 network 12-port multilayer module switch 4007 chassis port 9 port 13 port 17 port 13 slot 3 12-port mult...
Page 292
292 c hapter 14: v irtual lan s (vlan s ) table 56 defines the vlans in this configuration: table 56 network-based ip vlans and ipx vlans slot 3 module slot 5 module switch fabric module vlan2: ■ vlan index 2, vid 20 ■ ports 1–8, 13 ■ protocol type ip ■ 22.2.2.0 layer 3 address ■ tagging none front-...
Page 293
Ignore stp mode 293 ignore stp mode when you use allclosed vlan mode on a multilayer switching module in your system, you can enable the module to ignore the spanning tree protocol (stp) mode on a per-vlan basis; that is, ignore stp blocked ports. (when stp detects multiple paths to a destination, i...
Page 294
294 c hapter 14: v irtual lan s (vlan s ) ip vlan2 has routing interfaces defined on both multilayer switching modules (22.2.2.2 on the first multilayer switching module and 22.2.2.3 on the second multilayer switching module). Figure 22 ignore stp mode switch fabric module vlan2; ip vlan for 22.2.2....
Page 295
Rules of vlan operation 295 rules of vlan operation after you select a vlan mode for your modules and create vlan interfaces with vlan characteristics such as ieee 802.1q or no tagging, port membership, protocol type, and layer 3 (network) address information, the system determines the details of vl...
Page 296
296 c hapter 14: v irtual lan s (vlan s ) figure 23 shows the flow chart for the release 3.0 vlan ingress rules for multilayer switching modules. Figure 23 flow chart for release 3.0 ingress rules incoming frame frame tagged? Receive port is in a vlan that matches both the frame’s vid and protocol t...
Page 297
Rules of vlan operation 297 the ingress rules for tagged frames also vary for the different releases. Table 57 summarizes the differences in ingress rules based on the releases. Table 57 ingress rules for ieee 802.1q tagged frames based on vlan mode and release vlan mode release 2.X release 3.0 acti...
Page 298
298 c hapter 14: v irtual lan s (vlan s ) egress rules these rules determine whether the outgoing frame is forwarded, filtered (dropped), or flooded. They also determine the frame’s tag status. The same standard bridging rules apply to both open and closed vlans, but they result in different behavio...
Page 299
Rules of vlan operation 299 for each port on which the frame is to be transmitted, if that port is tagged for the vlan associated with the frame, transmit the frame as a tagged frame; otherwise, transmit the frame as an untagged frame. If the transmit port is not a member of the assigned vlan, the f...
Page 300
300 c hapter 14: v irtual lan s (vlan s ) example 2: vlan exception flooding if data arrives on a bridge port for a certain protocol and vlans for that protocol are defined in the module but not on that bridge port, the default vlan defines the flooding domain for that data. This case is called vlan...
Page 301
Rules of vlan operation 301 the frames that are associated with these protocols have different ingress rules for assignment to the appropriate network-based vlan: ■ ip frames — these frames are assigned to the network-based ip vlan if the ip source address is consistent with the vlan subnet and the ...
Page 302
302 c hapter 14: v irtual lan s (vlan s ) modifying and removing vlans you can modify or remove any vlans on the modules in your system. Review the following guidelines before you modify or remove vlans: ■ when you modify vlan information for a vlan interface on your module, you have the option to c...
Page 303
Monitoring vlan statistics 303 monitoring vlan statistics when you display vlan statistics on multilayer switching modules, the module-generated statistics are valid only under either of these conditions: ■ when the vlans are defined for the same protocol type (or the type unspecified, for port-base...
Page 304
304 c hapter 14: v irtual lan s (vlan s ).
Page 305: Acket
15 p acket f iltering this chapter describes what packet filters are, how to create them, and how to use system utilities to apply them to ports of your switch 4007 system. The chapter covers these topics: ■ packet filtering overview ■ key concepts ■ important considerations ■ managing packet filter...
Page 306
306 c hapter 15: p acket f iltering the management interfaces display “ cb9000 ” and refer to the management module as the enterprise management engine (eme) because the heritage of the switch 4007 is the corebuilder ® 9000 switch. Packet filtering overview the packet filtering feature allows a swit...
Page 307
Packet filtering overview 307 figure 24 ethernet and fddi packet fields when is a filter applied? — paths packets travel on many different paths through the switch. You can control to which path a filter is applied. Input packet filtering: receive path input packet filtering applies to packets immed...
Page 308
308 c hapter 15: p acket f iltering path assignment after you create a packet filter, you can assign it to any combination of the transmit all , transmit multicast , receive all , receive multicast , and receive internal paths of each port. The filter executes a series of operations on the packet’s ...
Page 309
Key concepts 309 key concepts before you use packet filters, review the following key concepts and terms: ■ standard filters — packet filters that are supplied with the switch 4007 that the hardware executes at wire speed. You can load them from the administration console, or select them from the se...
Page 310
310 c hapter 15: p acket f iltering placing a filter on the receive path confines the packet to the segment that it originated from if it does not meet the forwarding criteria. Placing a filter on the transmit path prohibits a packet from accessing certain segments unless it meets the forwarding cri...
Page 311
Important considerations 311 important considerations ■ after you create a packet filter, you must: ■ assign the filter to the applicable ports ■ assign the filter to the applicable transmit and receive paths ■ define port groups, if needed ■ if you assign standard (hardware) filters on the receive ...
Page 312
312 c hapter 15: p acket f iltering ■ deleting packet filters — deleting a packet filter removes the filter from the module. A filter cannot be deleted if it is assigned. You must unassign the filter from any ports before you can delete the filter. Use the bridge packetfilter delete command. ■ editi...
Page 313
Tools for writing filters 313 tools for writing filters the following tools can be used to create packet filters. ■ ascii text editor ■ built-in line editor ■ web management filter builder tool ascii text editor you can create a new custom packet filter using an ascii-based text editor (such as emac...
Page 314
314 c hapter 15: p acket f iltering table 62 commands for the built-in packet filter editor command keys description list buffer ctrl+l displays each of the lines in the editing buffer, and then redisplays the line currently being edited. Next line ctrl+n moves cursor to start of next line. Previous...
Page 315
Tools for writing filters 315 web management filter builder tool filter builder is part of the web management tool suite. You can use filter builder as a standalone application on your unix or pc system to create your own custom filters and save them as ascii files. You then download the files conta...
Page 316
316 c hapter 15: p acket f iltering filter builder includes 10 predefined filters, which are displayed on the filter screen. Table 63 lists the filters by name, what each does, and whether the filter operates in the software or the hardware. You can distinguish predefined filters from the custom fil...
Page 317
Downloading custom packet filters 317 downloading custom packet filters downloading a packet filter to the switch 4007 is a two-step process. You log in to the eme and enter the download module command with a file type of filter . The eme does a tftp file transfer and sends the file to the module. T...
Page 318
318 c hapter 15: p acket f iltering loading a custom filter on the switch 4007 here are step-by-step directions to load the filter on an eme, and then to load and assign filters on the multilayer switching module: 1 log in to a switch 4007. 2 at the eme’s prompt, enter a download command using the f...
Page 319
The packet filtering language 319 the packet filtering language you define packet filters using a stack-oriented language, which uses a lifo (last in, first out) queue when the packet filter is running. The program places values (called operands) on the stack and tests them with various logical expr...
Page 320
320 c hapter 15: p acket f iltering procedure for writing a custom filter this section describes the process of writing a packet filter. Detailed examples are provided in “long custom filter example” later in this chapter. You write the instructions for the packet filter using the following syntax: ...
Page 321
The packet filtering language 321 table 64 describes the instructions and stacks of a packet filter. Table 64 packet filter instructions and stacks — descriptions and guidelines element descriptions and guidelines instructions each instruction in a packet filter definition must be on a separate line...
Page 322
322 c hapter 15: p acket f iltering the ethernet and fddi packet fields in figure 24 are used as operands in the packet filter. The two simplest operands are described in table 65. Packet filter opcodes opcodes are instructions used in packet filter definitions. The available opcodes are described i...
Page 323
The packet filtering language 323 pushliteral.Size 1 (.B) 2 (.W) 4 (.L) 6 (.A) bytes depending on the size of plus 1 byte for a total of 2, 3, 5, or 7 bytes pushes a literal constant onto the stack. The most significant byte of the is the first byte of the literal. Bytes are copied directly from the...
Page 324
324 c hapter 15: p acket f iltering pushliteral.Size 1 (.B) 2 (.W) 4 (.L) 6 (.A) bytes depending on the size of plus 1 byte for a total of 2, 3, 5, or 7 bytes pushes a literal constant onto the stack. The most significant byte of the is the first byte of the literal. Bytes are copied directly from t...
Page 325
The packet filtering language 325 pushtop (continued) 1 byte rather than use multiple pushfield .W 12 commands to look at the 12th offset where the ethernet type field resides, use multiple pushtop commands, as shown here: original filter: pushfield.W 12 pushliteral.W 0x6004 eq reject pushfield.W 12...
Page 326
326 c hapter 15: p acket f iltering pushdpgm 1 byte pushes the destination port group mask (dpgm) onto the top of the stack. The dpgm is a bitmap representing the groups to which the destination port of a packet belongs. Pushes 4 bytes on to the stack. Each port group mask is represented by a single...
Page 327
The packet filtering language 327 ge (greater than or equal to) 1 byte pops two values from the stack and performs an unsigned comparison. If the first is greater than or equal to the second, a byte containing the non-zero value is pushed onto the stack; otherwise, a byte containing 0 is pushed. The...
Page 328
328 c hapter 15: p acket f iltering reject 1 byte conditionally rejects the packet being examined. Pops a byte from the stack. If its value is non-zero, the packet is rejected and filter evaluation ends immediately; otherwise, the filter evaluation continues with the next instruction. Use reject wit...
Page 329
The packet filtering language 329 implementing sequential tests in a packet filter filter language expressions are normally evaluated to completion — a packet is accepted if the value remaining on the top of the stack is nonzero. Frequently, however, a single test is insufficient to filter packets e...
Page 330
330 c hapter 15: p acket f iltering figure 26 accept and reject instructions the following example shows the use of both accept and reject in a packet filter. This packet filter was created for a network that is running both phase i and phase ii appletalk software. The goal of the filter is to elimi...
Page 331
Common syntax errors 331 common syntax errors when you leave the administration console’s built-in editor or load a packet filter definition from across the network, the software examines the definition for syntax errors. Table 67 lists syntax errors and their causes. Table 67 common syntax errors s...
Page 332
332 c hapter 15: p acket f iltering invalid characters in number the number specified as an offset or literal is improperly formatted. Possible causes are 1) lack of white space setting off the number, and 2) invalid characters in the number. Note: the radix of the number is determined by the first ...
Page 333
Custom packet filter examples 333 custom packet filter examples the following examples of packet filters, which were built using the packet filter language, start with basic concepts. Destination address filter this filter operates on the destination address field of a frame. It allows packets to be...
Page 334
334 c hapter 15: p acket f iltering type filter this filter operates on the type field of a frame. It allows packets to be forwarded that are ip frames. To customize this filter to another type value, change the literal value loaded in the pushliteral.W instruction. Ethernet type ipx and multicast f...
Page 335
Custom packet filter examples 335 source address and type filter this filter operates on the source address and type fields of a frame. It allows xns packets to be forwarded that are from stations with an oui of 08-00-02. To customize this filter to another oui value, change the literal value loaded...
Page 336
336 c hapter 15: p acket f iltering port group filter see “using port groups in custom packet filters” for a port group filter example. Limits to filter size a packet filter program is stored in a preprocessed format to minimize the space that is required by the packet filter definition. Comments ar...
Page 337
Using port groups in custom packet filters 337 using port groups in custom packet filters you can use a port group (a list of module ports) as filtering criteria in a packet filter. A packet filter uses the group to make filtering decisions by accessing the group’s source port group mask and destina...
Page 338
338 c hapter 15: p acket f iltering if mac address 00-80-3e-12-34-56 is learned on port 3 and port 3 belongs to port group 1, it has a port group bit mask for port group 1 inserted into the port group mask table that is associated with the mac address in the bridge address table. The mask is 32 bits...
Page 339
Using port groups in custom packet filters 339 for example, port 1 has a packet filter using the dpgm assigned to port 1's rxall path and a broadcast frame is received on port 1. The bridge determines that the frame will be flooded to the vlan ports 2-5. The filter is processed 4 times: 1 once for t...
Page 340
340 c hapter 15: p acket f iltering port group management and control functions this section describes the management and control functions that you use to define port groups. Defining port groups you can configure port groups from the bridge packetfilter portgroup menu of the administration console...
Page 341
Long custom filter example 341 ■ loading groups — the administration console has no explicit menu item for loading port groups that are defined in a file on a remote host. However, you can load groups by creating a script on a remote host (which includes your port group) and then running that script...
Page 342
342 c hapter 15: p acket f iltering packet filter solution the solution described here is to create a highly sophisticated packet filter that prevents only the broadcast packets from the market data servers from being forwarded onto the segments that are not part of an active trading floor. Before y...
Page 343
Long custom filter example 343 name “ip xns ticker bcast filter” # assign this filter in the multicast path # of a port only--this is very important. # # xns filtering section # pushfield.A 0 # apply pushliteral.A 0xffffffffffff# filter ne # only on broadcast traffic accept # pushfield.W 12 # get th...
Page 344
344 c hapter 15: p acket f iltering the rest of this section concentrates on the parts of the complex filter, showing you how to translate the pseudocode’s requirements into filter language. The large filter is broken down into subsets to show how you can create small filters that perform one or two...
Page 345
Long custom filter example 345 4 enter executable instruction #3: ne # not 0xffffffffffff 5 enter executable instruction #4: accept # accept packet and go no further this accepts all non-broadcast packets. 6 enter executable instruction #5: pushfield.W 12 # get the type field of the packet and # pla...
Page 346
346 c hapter 15: p acket f iltering 4 enter executable instruction #3: ge # compare if the value of the socket is greater than # or equal to the lower bound. 5 enter executable instruction #4: pushliteral.W 0x0898 # put the highest socket value on # top of the stack. 6 enter executable instruction #...
Page 347
Long custom filter example 347 4 add an and statement to compare the results of step 2 with the results of step 3: and # compare if ip and in range. This combination looks like this: combining all the filters together, the packet filters work to perform the solution to the problem: filtering the bro...
Page 348
348 c hapter 15: p acket f iltering 6 add an or statement: or # determine if the type field is either xns or ip 7 add a not statement to discard any matching packets: not # discard if (ip & in range) or (xns & in range) the complete packet filter discards ip and xns packets that are within the speci...
Page 349
Long custom filter example 349 name “optimized ip xns ticker bcast filter” # assign this filter in the multicast path # of a port only--this is very important. # # xns filtering section (assuming more xns traffic) pushfield.A 0 # pushliteral.A 0xffffffffffff# ne # accept # pushfield.W 12 # get the t...
Page 350
350 c hapter 15: p acket f iltering.
Page 351: Ip R
16 ip r outing this chapter provides guidelines and other key information about how to configure a multilayer switching module to route packets using the internet protocol (ip). The chapter covers these topics: ■ routing overview ■ key concepts ■ routing models: port-based and vlan-based ■ key guide...
Page 352
352 c hapter 16: ip r outing you can manage ip routing in either of these ways: ■ from the ip menu of the administration console. (see the switch 4007 command reference guide.) you can use the administration console after you log in to the system and connect to a slot that houses a multilayer switch...
Page 353
Routing overview 353 figure 27 shows where routers are typically used in a network. Routing connects subnetworks to the enterprise network, providing connectivity between devices within a workgroup, department, or building. Figure 27 typical routing architecture layer 2 switch layer 2 switch layer 2...
Page 354
354 c hapter 16: ip r outing routing in a subnetworked environment use your system to fit ethernet switching capability into subnetworked (subnetted) environments. When you put your system into such a network, the system streamlines your network architecture by routing traffic between subnetworks an...
Page 355
Routing overview 355 integrating bridging and routing your module integrates bridging and routing. You can assign multiple ports to each subnetwork. See figure 29. Figure 29 multiple ethernet ports per subnetwork bridging switches traffic between ports that are assigned to the same subnetwork. Traff...
Page 356
356 c hapter 16: ip r outing 3com bridging and routing the destination mac address determines whether the module bridges or routes a packet. Before a host system sends a packet to another host, the host system compares its own network address to the network address of the other host as follows: ■ if...
Page 357
Routing overview 357 figure 31 illustrates one 3com routing model: 1 the packet enters the module. 2 the bridging layer examines the destination address of the packet. The destination address corresponds to the address of one of the module ports that are configured for routing (as opposed to a learn...
Page 358
358 c hapter 16: ip r outing ip routing overview an ip router, unlike a bridge, operates at the network layer of the open systems interconnection (osi) reference model. The network layer is also referred to as layer 3. An ip router routes packets by examining the network layer address (ip address). ...
Page 359
Key concepts 359 features and benefits 3com routing in general and ip routing in particular provide the following features and benefits: ■ economy — because you can connect several segments to the same subnetwork with routing, you can increase the level of segmentation in your network without creati...
Page 360
360 c hapter 16: ip r outing if you define multiple interfaces for an ip vlan, you cannot subsequently modify that ip vlan to supply layer 3 address information. If only one routing interface is defined for the ip vlan, then you can supply layer 3 address information as long as it matches the layer ...
Page 361
Key concepts 361 dotted decimal notation the actual ip address is a 32-bit number that is stored in binary format. These 32 bits are segmented into 4 groups of 8 bits — each group is referred to as a field or an octet. Decimal notation converts the value of each field into a decimal number, and the ...
Page 362
362 c hapter 16: ip r outing subnetwork portion the ip address can also contain a subnetwork part at the beginning of the host part of the ip address. Thus, you can divide a single class a, b, or c network internally, allowing the network to appear as a single network to other external networks. The...
Page 363
Key concepts 363 traditionally, subnet masks were applied to octets in their entirety. However, one octet in the subnet mask can be further subdivided so that part of the octet indicates an extension of the network number, and the rest of the same octet indicates the host number, as shown in figure ...
Page 364
364 c hapter 16: ip r outing the subnet mask 255.255.255.255 is reserved as the default broadcast address. Variable length subnet masks (vlsms) with variable length subnet masks (vlsms), each subnetwork under a network can use its own subnet mask. Therefore, with vlsm, you can get more subnetwork sp...
Page 365
Key concepts 365 ■ make sure that the routers forward routes based on what is known as the longest match. For example, assume that the destination ip address of a packet is 158.101.26.48 and that the following four routes are in the routing table: ■ 158.101.26.0/24 ■ 158.101.3.10/16 ■ 158.101.26.32/...
Page 366
366 c hapter 16: ip r outing figure 37 routing interfaces to gain access to the module using tcp/ip or to manage the module using the simple network management protocol (snmp), set up an ip interface to manage your system and at least one virtual lan (vlan). See chapter 14 for information about how ...
Page 367
Key concepts 367 ■ gateway — the ip address of the router interface through which the packet travels on its next hop. ■ status — information that the routing protocol has about the route, such as how the route was put into the routing table. ■ time-to-live (ttl) — time-to-live measured in seconds be...
Page 368
368 c hapter 16: ip r outing default route in addition to the routes to specific destinations, a routing table can contain a defaultroute. The router uses the default route to forward packets that do not match any other routing table entry. A default route is often used in place of static routes to ...
Page 369
Key guidelines for implementing ip routing 369 your module, as a routing device, has the ability to implement either type of routing scheme, “routing over bridging” and “routing versus bridging”. Each kind of routing scheme requires its own interface type: ■ routing over bridging requires a vlan-bas...
Page 370
370 c hapter 16: ip r outing configure ip vlans if you want to use ip routing, you must first configure the vlan to use ip. An ip vlan is called a protocol-based vlan. Protocol-based vlans such as ip vlans group one or more switch ports together for one or more specified layer 3 protocols. You can a...
Page 371
Key guidelines for implementing ip routing 371 layer 3 module prompts you for this option, the menu identifies the available vlan indexes. Important consideration consider the following issue before you establish an ip interface: ■ before you assign ip addresses, map out the entire network and subne...
Page 372
372 c hapter 16: ip r outing enable ip routing to enable ip routing, use the ip routing command on the administration console or use the ip configuration form in the web management software. By default, ip routing is disabled on the multilayer switching module. You can use the routing information pr...
Page 373
Address resolution protocol (arp) 373 you do not need to implement arp — the module has arp capability built in, but you can manipulate and display the contents of the arp cache. When the host or router knows the ip address of the nexthop towards the packet destination, the host or router translates...
Page 374
374 c hapter 16: ip r outing target protocol address, the receiving device places its mac address in the target hardware address field and sends the packet back to the source hardware address. When the originating host or router receives this arp reply, it places the new mac address in its arp cache...
Page 375
Arp proxy 375 arp proxy arp proxy allows a host that has no routing ability to determine the mac address of a host on another network or subnet. When arp proxy is enabled and a workstation sends an arp request for a remote network, the module determines if it has the best route and then answers the ...
Page 376
376 c hapter 16: ip r outing figure 42 arp proxy internet control message protocol (icmp) because a router knows only about the next network hop, it is not aware of problems that may be closer to the destination. Destinations may be unreachable if: ■ hardware is temporarily out of service. ■ you spe...
Page 377
Internet control message protocol (icmp) 377 icmp performs these tasks: ■ creates more efficient routing (icmp redirect) — often the host route configuration specifies the minimum possible routing data that is needed to communicate (for example, the address of a single router). The host relies on ro...
Page 378
378 c hapter 16: ip r outing ■ the minimum value hex 80000000 directs neighboring hosts not to use the address, even though it may be advertised as a default router address. It may be useful to configure an address with a preference level of hex 80000000 (rather than setting its advertise flag to fa...
Page 379
Icmp redirect 379 use the administration console or the web management software to enable icmp redirect. Important considerations keep the following things in mind with icmp redirect: ■ icmp redirect determines if the sending interface is the same as the receiving interface. ■ icmp redirect determin...
Page 380
380 c hapter 16: ip r outing broadcast address you can set a broadcast address for each defined ip interface. Your module uses this broadcast address when forwarding directed broadcast packets, and when advertising rip packets. When you define an ip interface, the broadcast address is 255.255.255.25...
Page 381
Routing information protocol (rip) 381 rip operates using both active and passive devices. ■ active devices, usually routers, broadcast rip messages to all devices in a network or subnetwork and update their internal routing tables when they receive a rip message. ■ passive devices, usually hosts, l...
Page 382
382 c hapter 16: ip r outing compatibility mode the rip-1 compatibility mode determines how the software sends periodic rip-2 updates. (rip-1 always uses the advertisement list when sending rip-1 advertisements.) ■ when the module is configured to advertise rip-2 packets and compatibility mode is di...
Page 383
Routing information protocol (rip) 383 poison reverse is essentially another layer of protection against advertising reverse routes. ■ when you enable (default mode) poison reverse, the multilayer switching module advertises reverse routes in updates, but it sets the metrics to 16 (infinity). Settin...
Page 384
384 c hapter 16: ip r outing important considerations consider the following issues when you implement rip on your module: ■ use rip-2 rather than rip-1 if possible, because rip-2 uses subnet masking and the next hop field. Subnet mask advertising allows you to use vlsm. (see “variable length subnet...
Page 385
Routing policies 385 routing policies can control the entire flow of routing information among the network, the protocols, and the routing table manager. Routing policies are often referred to as route filters because defining policies for accepting and forwarding routes is very much like defining f...
Page 386
386 c hapter 16: ip r outing figure 62 shows the first level of decision-making in routing policies. Routing policies also contain two parameters that help further refine this system: metrics and administrative weight. ■ metric (cost) adjustment— specifies how many hops to assign to the route. The r...
Page 387
Routing policies 387 important considerations even though routing policies are not true routing protocols and are considered optional, they can increase network efficiency. ■ you can increase speed and security simply by limiting the number of devices from which the router receives data. ■ you can e...
Page 388
388 c hapter 16: ip r outing rip import policy conditions for specified interfaces table 75 lists the policy conditions for rip import policies: table 75 rip import policy conditions source router route (address/mask) action description specified router specified route/mask accept accept specified r...
Page 389
Routing policies 389 rip export policy conditions for specified interfaces table 76 lists the policy conditions for the rip export policies: multiple matched routing policies because you can use a wildcard parameter ( all ) to specify a source or target route, there are times when several policies c...
Page 390
390 c hapter 16: ip r outing setting up rip routing policies to configure a routing policy, follow these general steps: 1 establish an export policy that controls the advertisement of routes through rip, regardless of the source from which the route is learned. 2 establish an import policy that acce...
Page 391
Routing policies 391 creating rip routing policies to set a routing policy, you need to know the following parameters: ■ policy type — the determination whether to accept a route into the routing table (import) or advertise a route from the routing table (export) ■ source address — the routing devic...
Page 392
392 c hapter 16: ip r outing domain name system (dns) the domain name system (dns) client allows you to specify a hostname rather than an ip address when you perform various operations (for example, when you use ping or traceroute to contact an ip station). With dns, you can specify one or more name...
Page 393
User datagram protocol (udp) helper 393 user datagram protocol (udp) helper user datagram protocol (udp) helper allows tcp/ip applications to forward broadcast packets from your module (as a router) and to another part of the network. Two common uses of the udp helper feature are: ■ bootstrap protoc...
Page 394
394 c hapter 16: ip r outing configuring overlapped interfaces overlapped ip interfaces are multiple logical interfaces that are defined for a single physical port. You can specify how udp helper forwards packets from overlapped ip interfaces with one of these interface options: ■ first — the module...
Page 395
Standards, protocols, and related reading 395 standards, protocols, and related reading this section describes how to obtain more technical information about ip. Requests for comments (rfcs) documents called requests for comments (rfcs) contain information about the entire set of protocols that make...
Page 396
396 c hapter 16: ip r outing related reading for more information about the ip protocol suite, see the following books: ■ high speed networks: tcp/ip and atm design principles. William stallings, prentice hall, 1998 ■ local area networks: architectures and implementations. James martin, prentice hal...
Page 397: Irtual
17 v irtual r outer r edundancy p rotocol (vrrp) the virtual routing redundancy protocol (vrrp) can prevent a loss of network operations for end hosts due to the failure of the static default ip gateway. Vrrp accomplishes this by allowing you to designate a number of other routers as backup routers ...
Page 398
398 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) vrrp overview a critical component of ip networking is the way in which hosts and routing devices find the next-hop address in a connectionless environment. There are several different ways of determining the next-hop address, but they a...
Page 399
Vrrp overview 399 static route a static route is an ip address that is user-configured and fixed. Static routes are useful if the host only needs to access a few networks; in this case, static routes actually require less overhead than dynamic routing protocols. However, in today’s networking enviro...
Page 400
400 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) figure 45 simple vrrp configuration in the example shown in figure 45, router a is the default gateway for the workstation labeled pc, which provides access to the wide area network (wan) and to the device labeled server. Assume that no ...
Page 401
Key concepts 401 ■ virtual router master — the vrrp router that forwards packets sent to the ip addresses associated with the virtual router. Also called the master router. A virtual router is the master when: ■ you configure it (using the administration console, the web management console, or snmp)...
Page 402
402 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) for this scheme to work, the association between vrids and ip addresses must be coordinated among all vrrp routers across the lan: otherwise, the backup router does not have a valid set of ip addresses to use. Virtual router decision-mak...
Page 403
Important considerations 403 vrrp provides for this by making you assign each virtual router on the lan a priority value between 1 and 255. (255 means that the virtual router is the actual owner of the ip addresses.) if the master fails, the virtual router with the next-highest priority takes over m...
Page 404
404 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) ■ a backup router monitors the availability and state of the master, and: ■ does not respond to arp requests for the ip address or addresses associated with the virtual router. ■ discards packets that have a destination link layer mac ad...
Page 405
Vrrp and other networking operations 405 spanning tree protocol (stp) figure 46 earlier in this chapter shows how you can set up vrrp parallel routers to provide total redundancy in your inter-lan operations. However, because vrrp uses mac addresses in its advertisements, this topology can represent...
Page 406
406 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) figure 47 proper use of dynamic routing protocols with vrrp igmp queries ip multicast routers use igmp to query subnetworks in order to detect host members of multicast groups. Igmp specifies a querier election process in which one route...
Page 407
Using vrrp on your switch 4007 407 icmp redirect using icmp redirect in conjunction with vrrp might cause gateway access problems due to potential conflicts between actual mac addresses that icmp redirect uses and the virtual mac addresses that vrrp uses. Disable icmp redirect if you are using vrrp....
Page 408
408 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) see figure 48 for a graphic example of a vrrp topology on two switch 4007s. This sample topology directly connects end stations to a backbone switch 4007 16-slot chassis. The end stations can communicate with end stations on lans that ar...
Page 409
Using vrrp on your switch 4007 409 switch 4007 ba1 ip addr 22.2.52.16 33.3.52.16 ip addrs 44.4.53.16 55.5.53.16 vrrp vid 53 primary for subnets 44.4.53 55.5.53 lan switch 4007 ca3 ca4 ba2 ip addr 22.2.52.17 33.3.52.17 vrrp vid 53 backup for subnets 44.4.53 55.5.53 ca1 vrrp vid 52 backup for subnets ...
Page 410
410 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) spanning tree considerations to prevent the links from going into blocking mode on the external switch side, you must: ■ remove the ba1 and ba2 front panel ports in the protocol vlan from the default vlan. ■ set the spanning tree protoco...
Page 411
Using vrrp on your switch 4007 411 vrrp activity if the entire ba2 module goes down, then both backup virtual routers on ba1 switch over to master and the end stations’ ability to address one another on lan1 (the switch fabric module) and to address the end stations on lan2 (external switch) is main...
Page 412
412 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) problem the backplane port router of ba2 does not have the ability to address the 44.4.53 and 55.5.53 subnetworks on the front panel port router of ba1. With rip-2 or ospf: the routing protocol advertises a path to subnetworks 44.4.53 & ...
Page 413
Using vrrp on your switch 4007 413 figure 49 sample vrrp topology with a single virtual router in this topology, there is a single point of failure (because there is a one-armed router) between the left and right chassis. Loss of either the ca2 module in the left chassis, or the ca3 module in the ri...
Page 414
414 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) configuring vrrp this section provides details about configuring multiple vrrp routers, following the topology in figure 48. Router 1 is on the backplane port of a 12-port 10/100base-tx fast ethernet multilayer switching module in slot 3...
Page 416
416 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) configuring the ip interfaces ------------------------------------------------------------ cb9000@slot3.1 [12-e/fen-tx-l3] (): ip interface define enter ip address: 44.4.4.1 enter subnet mask [255.0.0.0]: 255.255.255.0 enter interface ty...
Page 417
Configuring vrrp 417 configuring the master router configuring router 2 as the backup router configuring router 2 as the backup router, as shown in figure 48, involves the following tasks: ■ configuring the protocol (ip) vlan of the backup router ■ configuring the ip interfaces ■ configuring the bac...
Page 419
Configuring vrrp 419 configuring the ip interfaces ------------------------------------------------------------ cb9000@slot5.1 [10-e/fen-fx-l3] (): ip int define 44.4.4.2 255.255.255.0 vlan 2 cb9000@slot5.1 [10-e/fen-fx-l3] (): ip int define 55.5.5.2 255.255.255.0 vlan 2 cb9000@slot5.1 [10-e/fen-fx-...
Page 420
420 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) configuring the backup router switching from master router to backup router to see how the backup router assumes master router responsibilities, disable the master router, then display the vrrp configuration. The display shows that the i...
Page 421
Configuring vrrp 421 disabling the master router displaying the results of the master router change ------------------------------------------------------------------------------------ cb9000@slot3.1 [12-e/fen-tx-l3] (): eth portstate 13 disable cb9000@slot5.1 [10-e/fen-fx-l3] (): ip vrrp detail all...
Page 422
422 c hapter 17: v irtual r outer r edundancy p rotocol (vrrp) standards, protocols, and related reading virtual router redundancy protocol is defined in the ietf request for comments (rfc) document rfc2338. Rfc2338 can be found at the following www site: http://www.Ietf.Cnri.Reston.Va.Us/rfc/rfc233...
Page 423: Ip M
18 ip m ulticast r outing this chapter provides conceptual information, configuration options, and implementation guidelines for ip multicast routing on switch 4007 multilayer switching modules. This chapter covers these topics: ■ ip multicast overview ■ how a network supports ip multicast ■ key con...
Page 424
424 c hapter 18: ip m ulticast r outing switch 4007 multilayer switching modules use two protocols to support ip multicast routing: the internet group management protocol (igmp) and the distance-vector multicast routing protocol (dvmrp). Igmp is also supported on layer 2 switching modules, but that ...
Page 425
Ip multicast overview 425 ip multicast group members can be scattered across multiple subnetworks; thus, successful transmission from a source to group members can occur within a campus lan, a man, or over a wan. As an extension to the standard ip network-level protocol, ip multicast was first defin...
Page 426
426 c hapter 18: ip m ulticast r outing how a network supports ip multicast to support ip multicast, the sending and receiving nodes, as well as the network infrastructure between them, must be multicast-enabled. Specifically, there must be cohesive support for ip multicast in the following componen...
Page 427
How a network supports ip multicast 427 supporting protocols in your module to communicate with other routers, switch 4007 multilayer switching modules support the distance-vector multicast routing protocol (dvmrp) version 3.6. Dvmrp functions and configuration options are explained later in this ch...
Page 428
428 c hapter 18: ip m ulticast r outing a multicast router is required at each end of the tunnel. At each tunnel entrance, the router encapsulates the ip multicast packets in standard ip unicast packets — that is, it puts them in a format that the unicast routers can understand. When these packets r...
Page 429
Key concepts 429 internet support for ip multicast the mbone is the internet’s experimental multicast backbone network. It is an interconnected set of internet routers, subnetworks, and tunnels that support the delivery of ip multicast traffic. The mbone was first configured in 1992 as a test zone t...
Page 430
430 c hapter 18: ip m ulticast r outing ip multicast groups users can join or leave an ip multicast group at any time. Users request and cancel membership through mechanisms built into their desktop application — perhaps visible to the user as go and quit buttons. There are no restrictions on the ph...
Page 431
Key concepts 431 reserved mac addresses iana also controls a reserved portion of the ieee-802 mac-layer multicast address space. All addresses in this block use hexadecimal format and begin with 01-00-5e. A simple procedure maps class d addresses to this block, so that ip multicasting can take advan...
Page 432
432 c hapter 18: ip m ulticast r outing how igmp supports ip multicast igmp provides a way for routers and switches to learn where group members exist on a network, and thus provides a critical function in the ip multicast packet delivery process. Electing the querier on each subnetwork or broadcast...
Page 433
How igmp supports ip multicast 433 join message rather than wait for a query, a host can also send an igmp report on its own initiative to inform the querier that it wants to begin receiving a transmission for a specific group (perhaps by clicking a go or start button on the client interface). This ...
Page 434
434 c hapter 18: ip m ulticast r outing how dvmrp supports ip multicast dvmrp is a distance-vector routing protocol that allows routers to establish shortest-path, source-rooted, ip multicast delivery trees. While it is similar to the routing information protocol (rip), one important difference is t...
Page 435
How dvmrp supports ip multicast 435 the term spanning tree applies to any loopless graph that spans intelligent nodes. The dvmrp spanning tree structure provides only one active path to connect any two multicast routers in the network. This approach provides a logical, efficient path to reach group ...
Page 436
436 c hapter 18: ip m ulticast r outing interface relationships the interface on which a router receives source-origin traffic for a given source-group pair is called the incoming or parent interface. Each interface over which the router forwards source-group traffic is called an outgoing or child i...
Page 437
How dvmrp supports ip multicast 437 inside the prune message is a prune lifetime, or prune timer, which is a period of time for which the prune message is valid. When the prune lifetime expires, the interface is added back into the multicast delivery tree — that is, until it generates another prune ...
Page 438
438 c hapter 18: ip m ulticast r outing key guidelines for implementation a switch 4007 multilayer switching module needs to have ip multicast routing features enabled only if network users that sit downstream of the module (from the perspective of the source location) require access to ip multicast...
Page 439
Key guidelines for implementation 439 6 view the various displays, routing table and cache to see how the module is processing ip multicast traffic. See “viewing the dvmrp routing table” and “viewing the dvmrp cache” later in this chapter. 7 use the traceroute option for troubleshooting or to determ...
Page 440
440 c hapter 18: ip m ulticast r outing configuring igmp options you can enable or disable igmp snooping and querying functions, set the interface time-to-live (ttl) threshold, and obtain summary and detail displays of igmp-related information. Querying and snooping modes your multilayer switching m...
Page 441
Configuring dvmrp tunnels 441 table 79 lists conventional numeric values and network objectives. Configuring dvmrp tunnels a dvmrp tunnel allows ip multicast packets to traverse a portion of your network infrastructure that is not multicast-aware. In multilayer switching modules, you can define tunn...
Page 442
442 c hapter 18: ip m ulticast r outing ■ you must define the tunnel on both end points — that is, on both the local module and the remote system — even though you specify the address of the remote router interface in the local module. ■ dvmrp interfaces and tunnels have similar characteristics (met...
Page 443
Configuring dvmrp default routes 443 configuring dvmrp default routes you can configure a default route for ip multicast traffic on any dvmrp routing interface in the module. How default routes work if an interface is configured as a default route, it advertises source 0.0.0.0 to neighboring dvmrp r...
Page 444
444 c hapter 18: ip m ulticast r outing viewing the dvmrp routing table your module records dvmrp route information in a table that you can access from the management interface. Your module learns source-based route information from neighboring dvmrp routers and also advertises routes that it learns...
Page 445
Using ip multicast traceroute 445 using ip multicast traceroute you can perform an ip multicast traceroute from a layer 3 module. The ability to trace the path of a ip multicast group packet from a source to a particular destination is desirable for troubleshooting purposes. Unlike unicast tracerout...
Page 446
446 c hapter 18: ip m ulticast r outing important considerations ■ when using ip multicast traceroute, the module assumes that it is the destination for the source-group traffic. You cannot enter a different destination address. ■ a response packet may be returned to your module before reaching the ...
Page 447: Pen
19 o pen s hortest p ath f irst (ospf) r outing this chapter provides guidelines and other key information about how to configure open shortest path first (ospf) on a multilayer switching module. This chapter covers these topics: ■ ospf overview ■ key concepts ■ key guidelines for implementing ospf ...
Page 448
448 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ospf overview the ospf link-state protocol dynamically responds to changes in network topology that occur within a group of networks and routers known as an autonomous system. Ospf tracks the states of links and routers in each autonomous...
Page 449
Ospf overview 449 ■ ospf interfaces —an ospf interface is an ip interface that you configure to send and receive ospf traffic. When you configure an ospf interface, you define the behavior and role of the interface within the ospf routing domain. For example, router priority determines designated ro...
Page 450
450 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ virtual links — all areas of an ospf routing domain must connect to the backbone area. In cases where an area does not have direct, physical access to the backbone, you can configure a logical connection to the backbone, called a virtua...
Page 451
Ospf overview 451 ■ ability to partition the network into more manageable areas — many autonomous systems in the internet are large and complicated to manage. Ospf allows them to be subdivided into smaller, more manageable networks or sets of contiguous networks called areas. You can think of an are...
Page 452
452 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ support for virtual links to noncontiguous areas — as discussed earlier, ospf can partition large autonomous systems into smaller, more manageable subdivisions, called areas. An ospf backbone is responsible for distributing routing info...
Page 453
Key concepts 453 key concepts before you configure ospf on your system, review the following key concepts and terms discussed in these sections: ■ autonomous systems ■ areas ■ neighbors and adjacency ■ router types ■ protocol packets ■ how ospf routing works autonomous systems an autonomous system c...
Page 454
454 c hapter 19: o pen s hortest p ath f irst (ospf) r outing router types ospf routers serve several different, often overlapping, functions: ■ internal routers — internal routers connect only to networks that belong to the same area. An internal router runs one copy of the ospf algorithm and maint...
Page 455
Key concepts 455 router ids the ospf router id identifies a router to other routers within an autonomous system. Ospf uses three types of router identifiers, which take the form of an ip address: ■ default — an arbitrary id that the system generates and uses as the default router id ■ interface — th...
Page 456
456 c hapter 19: o pen s hortest p ath f irst (ospf) r outing how ospf routing works this section summarizes how the ospf algorithm works for a router that meets these characteristics: ■ lies within an autonomous system area (an interior router) ■ is attached to a multiaccess network ■ is configured...
Page 457
Key concepts 457 electing the designated router ospf selects a designated router, which originates lsas on behalf of the network segment. These advertisements list all routers (including the designated router) that are attached to the segment. The designated router also floods lsa packets throughout...
Page 458
458 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ to a stub area — when a packet’s destination is in a stub area (an area that does not accept external route advertisements), ospf uses the area’s predefined default route. You configure default routing in area border routers that serve ...
Page 459
Autonomous system boundary routers 459 router placement and participation when you populate an area with ospf routers, consider the following guidelines: ■ because ospf uses a cpu-intensive algorithm, keep the maximum number of routers participating in ospf exchanges in any given area to around 50. ...
Page 460
460 c hapter 19: o pen s hortest p ath f irst (ospf) r outing the asbr then generates external link state advertisements for these ip interfaces. A router also becomes an asbr if you have configured either of the following on the box: ■ a default route metric ■ any static routes, including configuri...
Page 461
Areas 461 areas to reduce the amount of routing information that travels through a network, and the corresponding size of the ospf routers’ topology databases, subdivide ospf autonomous systems into areas. Each area has the following configurable parameters: ■ area id — a 32 bit number that identifi...
Page 462
462 c hapter 19: o pen s hortest p ath f irst (ospf) r outing types of areas all routers within the same area maintain and use identical link state advertisement (lsa) databases. The network shown in figure 54 later in this chapter contains four ospf areas within autonomous system a. There are three...
Page 463
Areas 463 figure 54 sample ospf routing application segment 9 router 4 router 3 router 2 router 1 router 6 autonomous system boundary router 1 router 5 area 0 (backbone) area 1 autonomous system a area border router 2 area 2 (stub) area 3 area border router 3 area border router 1 autonomous system b...
Page 464
464 c hapter 19: o pen s hortest p ath f irst (ospf) r outing area border routers each area (including the backbone area) includes all border routers that are connected to the area. In figure 54, for example, you define: ■ area border routers 1, 2, and 3 as being in backbone area 0 ■ area border rou...
Page 465
Areas 465 configuring route summarization in abrs the concept of route summarization is key in implementing a stable and scalable ospf internetwork. Route summarization is the consolidating of advertised addresses by area border routers (abrs). Instead of advertising routes to individual nodes withi...
Page 466
466 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ whenever there is a change in network topology (such as when a link is lost or comes online), routers in all affected areas must converge on the new topology. If your internetwork consists of unstable links, you can partition the as int...
Page 467
Areas 467 ■ because all routers connected to the backbone (abrs) must recompute routes whenever the topology changes for any link in the as, keeping the size of the backbone to a minimum is especially important in an autonomous system that may contain unstable links. At the very least, reducing the ...
Page 468
468 c hapter 19: o pen s hortest p ath f irst (ospf) r outing default route metric an ospf router always forwards an ip packet to the network that is the best match for the packet’s destination; best match means the longest or most specific match. A router that fails to find a specific match for a p...
Page 469
Ospf interfaces 469 priority you assign the interface priority to an ospf router to determine its status as a designated router. A router can function in one of three ways: ■ designated router (dr) — the router that has the highest priority value, unless a designated router already exists on the net...
Page 470
470 c hapter 19: o pen s hortest p ath f irst (ospf) r outing when a router interface within an area first comes online, it determines if a designated router exists for the area. If one exists, the new router accepts the designated router regardless of its own router priority. Therefore, if you want...
Page 471
Ospf interfaces 471 delay the transmit delay is the estimated time (in seconds) that it takes for the system to transmit a link state update packet on the interface. The system increases the age of the link state advertisements (lsas) that are contained in the update packets by the value that you sp...
Page 472
472 c hapter 19: o pen s hortest p ath f irst (ospf) r outing retransmit interval when a router sends a link state advertisement to its neighbor, it keeps a copy of the lsa until the neighbor acknowledges receipt of the lsa with a link state acknowledgment packet. If the sending router does not rece...
Page 473
Ospf interfaces 473 statistics you can display interface statistics for diagnostic and network debugging purposes. Viewing the statistics for a particular interface can provide valuable information, such as whether the router is overburdened, and the number of hello interval, dead interval, area id,...
Page 474
474 c hapter 19: o pen s hortest p ath f irst (ospf) r outing transmit delay ■ the default value for the transmit delay is 1 second. ■ set the transmit delay to an integer value greater than 0. ■ to set the transmit delay, take into account the transmission and propagation delays for the interface. ...
Page 475
Link state databases 475 link state databases ospf routers use the information that is contained in the link state advertisements (lsas) to build and maintain link state databases. Each link state database contains the link state advertisements from throughout the areas to which the router is attach...
Page 476
476 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ link id — identifies the object to which this router link connects for each link type. Possible values: ■ if link type is ptp, then this is the neighboring router’s router id. ■ if link type is transit, then this is the address of the d...
Page 477
Link state databases 477 summary link state advertisements area border routers can generate two types of summary link state advertisements: ■ summary link state advertisements that report the cost to a single subnetwork number outside the area. These advertisements are identified as type 3 in the li...
Page 478
478 c hapter 19: o pen s hortest p ath f irst (ospf) r outing external link state advertisements each autonomous system boundary router generates an external link state advertisement for each network destination (known to the router) outside the as. As boundary routers use these external link state ...
Page 479
Link state databases 479 each external link state advertisement includes this information: ■ lsid (link state id) — an ip network address: ■ for type 3 summary link advertisements, this is the ip network number. ■ for type 4 summary link advertisements, this is the asbr’s router id. ■ router id — id...
Page 480
480 c hapter 19: o pen s hortest p ath f irst (ospf) r outing neighbors neighbor routers are those that are physically attached to the same network segment. The ospf hello protocol establishes adjacencies among neighboring routers to facilitate the exchange of routing information. An adjacency descr...
Page 481
Neighbors 481 neighbor information your system can display a list of all neighbors for all ospf interfaces defined on the system. The list includes the following information: ■ index — the index number that corresponds to the ospf router interface for which neighbors have been discovered. ■ neighbor...
Page 482
482 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ loading — the router is sending requests for link state advertisements (lsas) that were discovered in the exchange state but not yet received. ■ full — the neighbor is now fully adjacent. This adjacency is now advertised in router lsas ...
Page 483
Neighbors 483 static neighbors on broadcast networks such as ethernet, the ospf hello protocol uses the broadcast capability to dynamically discover neighbors. On nonbroadcast networks, such as x.25 public data network, however, you may need to assist in neighbor discovery by statically defining nei...
Page 484
484 c hapter 19: o pen s hortest p ath f irst (ospf) r outing router ids each router that is configured for ospf has an ospf router id. The ospf router id uniquely identifies the router to other routers within an autonomous system. The router id determines the designated router in a broadcast networ...
Page 485
Ospf memory partition 485 ospf memory partition there are three choices for ospf memory allocation: ■ have the system intelligently determine the maximum ospfmemory partition size (partition size = 1 ). This is the default. ■ have ospf be part of system memory, growing as needed and without limit (p...
Page 486
486 c hapter 19: o pen s hortest p ath f irst (ospf) r outing the estimate (maxroutingtablesize) of the maximum number of routing table entries the system can hold for a given memory size is a hardcoded value. On extended memory systems this value is 51200. On systems without extended memory this va...
Page 487
Stub default metrics 487 manual memory allocation you can manually control the ospf current partition maximum size. You can enter any value between 4096 and the maximum memory available on your system, as shown in the ip ospf partition modify command prompt. You can also use manual memory allocation...
Page 488
488 c hapter 19: o pen s hortest p ath f irst (ospf) r outing a stub area can have multiple abrs and multiple exit points. However, all of the exit points and routers must contain the same external routing data so that the choice of an exit point does not need to be made for each external destinatio...
Page 489
Virtual links 489 the endpoints of a virtual link must be area border routers. You must configure the virtual link on both routers. Each router’s virtual link definition includes the other router’s router id and the transit area through which the routers connect. Figure 55 illustrates a virtual link...
Page 490
490 c hapter 19: o pen s hortest p ath f irst (ospf) r outing important considerations consider the following guidelines when you configure virtual links: ■ you must configure a virtual link for any area border router that has an interface connected to a location outside the backbone area. ■ you can...
Page 491
Ospf routing policies 491 ■ isolate suspect networks — misconfigured hosts can sometimes send inappropriate routing information, which can compromise network integrity. In such a case, you can define an import policy on an asbr that rejects all routes from the suspect network. ■ adjust route cost — ...
Page 492
492 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ with the ability to wildcard policy parameters (such as 0.0.0.0 to indicate all routers or all routes), occasions may arise when several policies match a route. In such cases, routers use the following procedure to determine which polic...
Page 493
Ospf routing policies 493 implementing import policies import policies control which non-self-originated routes (rip external routes) are accepted and stored in the routing table. Non-self-originated means that the router itself did not originate the route; it learned the route from an external link...
Page 494
494 c hapter 19: o pen s hortest p ath f irst (ospf) r outing figure 56 illustrates the import policy process. Figure 56 import policy process information that you define for an import policy includes: ■ the route or routes to which you want the policy to apply, specified by a network address and su...
Page 495
Ospf routing policies 495 ■ for routes that are accepted into the routing table as defined by the policy, you can define a new cost metric value for the route, or you can adjust the existing cost metric using one of these operators: ■ + adds the specified number to the existing cost metric ■ - subtr...
Page 496
496 c hapter 19: o pen s hortest p ath f irst (ospf) r outing import example 1: accept route the policy defined in table 81 imports route 243.140.28.0 into the routing table and assigns a cost of 10 to the route. Import example 2: reject route the policy defined in table 82 prohibits the router from...
Page 497
Ospf routing policies 497 when you define an export policy, you can configure the router to accept or reject routes. An accept export policy configures the router to place the specified route in external link state advertisements for propagation over the network. The routes are advertised with the c...
Page 498
498 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ■ when you specify rip or static as the origin protocol, you can specify the source address of the router that originated the rip or static route. For example, you can define an export policy to reject (that is, not advertise) all statica...
Page 499
Ospf routing policies 499 export policies for rip and static routes table 83 shows the export policies that can be applied to rip and statically defined routes. Table 83 ospf export policies for rip and static routes origin protocol source router route policy action metric adjustment external metric...
Page 500
500 c hapter 19: o pen s hortest p ath f irst (ospf) r outing export policies for direct interfaces table 84 shows the possible export policies that can be applied to directly connected router interfaces. Export example 1: prohibit advertisement of non-ospf interfaces the policy defined in table 85 ...
Page 501
Ospf routing policies 501 export example 2: prohibit advertisement of static address the policy defined in table 86 prohibits a router from advertising any static route originating from router 131.141.127.7. Although the router can learn all static routes that originate from router 131.141.127.7, th...
Page 502
502 c hapter 19: o pen s hortest p ath f irst (ospf) r outing export example 4: advertisement of direct interfaces the policy defined in table 88 configures a router to advertise direct interface 8 as a type 2 external metric with a cost increase of 2. Suppose a routing table entry exists for interf...
Page 503
Ospf routing policies 503 export example 6: advertisement of rip routes the policy defined in table 90 configures an autonomous system boundary router to advertise all routes that are imported from a rip network as type 2 external metrics with associated costs of 10. Table 90 export policy to accept...
Page 504
504 c hapter 19: o pen s hortest p ath f irst (ospf) r outing ospf statistics from the administration console and the web management interface, you can display general statistics for specific ospf interfaces. These statistics provide valuable information useful in troubleshooting network and system ...
Page 505
Standards, protocols, and related reading 505 standards, protocols, and related reading ospf as implemented on this system is described in the following internet engineering task force (ietf) request for comment (rfc) documents: ■ rfc 1583, moy, j., ospf version 2, march 1994. ■ rfc 1850, baker, f.,...
Page 506
506 c hapter 19: o pen s hortest p ath f irst (ospf) r outing.
Page 507: Ipx R
20 ipx r outing this chapter provides guidelines and other key information about how to implement internet packet exchange (ipx) protocol routing on multilayer switching modules. The chapter covers these topics: ■ ipx routing overview ■ key concepts ■ key guidelines for implementation ■ ipx interfac...
Page 508
508 c hapter 20: ipx r outing ipx routing overview you can route packets from your system to an external destination using the internet packet exchange (ipx) protocol. The ipx protocol is a netware lan communications protocol that moves data between servers and workstation programs that are running ...
Page 509
Ipx routing overview 509 features using the ipx protocol to route packets, you can create and support: ■ ipx interfaces ■ ipx routes (primary and secondary) ■ ipx servers (primary and secondary) ■ ipx forwarding ■ ipx rip mode ■ ipx sap mode benefits you can use ipx routing to: ■ provide services fo...
Page 510
510 c hapter 20: ipx r outing key concepts this section explains how ipx routing works and provides a glossary of ipx routing terms. How ipx routing works to route packets using the ipx protocol, take these general steps: 1 define an ipx protocol or a virtual lan (vlan) with a grouping of ports. 2 d...
Page 511
Key concepts 511 figure 59 shows the ipx packet format. Figure 59 ipx packet format the ipx packet contains the following elements: ■ checksum — a 16-bit checksum that is set to 1s. ■ packet length — a 2-byte field that indicates the packet’s length in bytes. This length includes both header and dat...
Page 512
512 c hapter 20: ipx r outing ■ source network — a 4-byte field that contains the source node network number. If a sending node sets this field to 0, the source’s local network number is unknown. ■ source node — a 6-byte field that contains the source node, physical address. Broadcast addresses are ...
Page 513
Key concepts 513 figure 60 shows an example of ipx format routing. Figure 60 ipx packet routing sending node’s responsibility when sending and destination nodes have the same network number, the sending node addresses and sends packets directly to the destination node. If sending and destination nod...
Page 514
514 c hapter 20: ipx r outing if the sending node is a router rather than a workstation, the node’s internal routing tables supply the destination’s network location. The destination router does not need to broadcast a rip request. Router’s responsibility a router handles a received ipx packet in on...
Page 515
Key concepts 515 terminology review the following ipx routing terms that are used extensively throughout this chapter: ■ address — unique 4-byte network address of a segment that is located in your multilayer switching module’s routing table. ■ age — the time in seconds since the network’s last upda...
Page 516
516 c hapter 20: ipx r outing key guidelines for implementation consider the guidelines in this section when you configure your multilayer switching module for ipx routing. Procedural guidelines complete the following steps to set up ipx routing on your multilayer switching module: 1 set up your vla...
Page 517
Ipx interfaces 517 ipx interfaces an ipx interface has the following information associated with it: ■ ipx network address — a 4-byte address that you assign. Make each address unique within the network. ■ cost — a number between 1 and 65534 that the system uses to calculate route ticks. A tick is a...
Page 518
518 c hapter 20: ipx r outing ■ when you define an ipx interface, you define: ■ ipx address ■ cost ■ format ■ associated ipx vlan index ■ before you define the ipx (routing) interface, you must define a vlan and select ipx, ipx-ii, ipx-802.2, ipx-802.2 llc, or ipx-802.3-snap as the protocol to be su...
Page 519
Ipx routes 519 per-interface options you can set the netbios and oddlengthpadding options on each interface. For details about how to use these options, see the administering ipx routing chapter in the command reference guide. Netbios option this option determines whether the system handles ipx type...
Page 520
520 c hapter 20: ipx r outing ■ the maximum number of hops, or routers that a packet can cross, is 16, except for netbios packets, which can cross no more than 7 routers. ■ before you define static routes on your system, you must define at least one ipx interface. ■ static routes remain in the routi...
Page 521
Ipx routes 521 the system uses rip (one of the most widely used igps) to dynamically build routing tables. Rip operates with active and passive network devices. Active devices, usually routers, broadcast their rip messages to all devices in a network; they update their own routing tables when they r...
Page 522
522 c hapter 20: ipx r outing the routing table consists of the following elements: ■ interface—the interface number of the router that is used to reach a network segment ■ address —the network segments that the router knows about ■ hops to network —the number of routers that must be crossed to reac...
Page 523
Ipx servers 523 ipx servers your system creates and maintains a server information table that lists all the servers that reside on other ipx networks. You can: ■ use sap to exchange server information dynamically ■ make static entries in the server table important considerations consider the followi...
Page 524
524 c hapter 20: ipx r outing primary and secondary servers you can set up both primary and secondary servers in the server table. Secondary servers serve as a backup to the primary server set up on the same ipx server. To set up secondary servers on your system, see the switch 4007 command referenc...
Page 525
Ipx servers 525 maintaining server information when a router’s sap agent receives a sap broadcast response indicating a change in a server’s configuration, the agent updates its server information table and informs other sap agents. Examples of such a change are when a server is disconnected or beco...
Page 526
526 c hapter 20: ipx r outing figure 62 sample server information table this table contains the following data: ■ interface — the interface from which server information is received ■ server name — the name of the server ■ server type — the type of service that the server provides ■ network address ...
Page 527
Ipx rip mode 527 ipx rip mode you can exchange routing information on a netware network with the ipx rip mode option. This option selects the ipx rip mode that is appropriate for your network and selects the routers that use rip mode to create and maintain their dynamic routing tables. In ipx rip mo...
Page 528
528 c hapter 20: ipx r outing rip policies each router maintains a table of current routing information (the routing table). The routing protocols receive or advertise routes from the network. Rip policies control the flow of routing information among the network, the protocols, and the routing tabl...
Page 529
Ipx rip mode 529 rip policy parameters these parameters define sap policies: policy type — import (apply the policy to received services) or export (apply the policy to advertised services). Route origin — the origin of the route for this policy if it is an export policy: static, rip, or all. Route ...
Page 530
530 c hapter 20: ipx r outing ipx sap mode ipx sap provides routers and servers that contain sap mode agents with a means of exchanging network service information. Through sap, servers advertise their services and addresses. Routers gather this information and share it with other routers. With this...
Page 531
Ipx sap mode 531 sap import polices each time the router receives an advertised service, it compares the services to the import polices to decide whether to add the service to the service table or drop it. If the router accepts the service, the router adds it to the service table. The default import...
Page 532
532 c hapter 20: ipx r outing ■ action — whether this router accepts or rejects a service that matches the policy. ■ weight — the metric value that is associated with this policy. This parameter specifies the order of precedence for policies that match the same service. A higher value takes preceden...
Page 533
Standards, protocols, and related reading 533 standards, protocols, and related reading the following standards and protocols apply when you use ipx to route packets on your system: ■ ieee 802.2 ■ ieee 802.2 llc ■ ieee 802.3 ■ ieee 802.3-raw ■ ieee 802.3-snap ■ internet packet exchange (ipx) — rfc 1...
Page 534
534 c hapter 20: ipx r outing.
Page 535: Pple
21 a pple t alk r outing this chapter provides guidelines and other key information about how to implement appletalk routing on multilayer switching modules. The chapter covers these topics: ■ appletalk overview ■ key concepts ■ key implementation guidelines ■ appletalk interfaces ■ appletalk routes...
Page 536
536 c hapter 21: a pple t alk r outing appletalk overview appletalk is a suite of protocols defined by apple computer, inc., for connecting computers, peripheral devices, and other equipment to a network. Appletalk protocols support most of the functions that are offered by the open systems intercon...
Page 537
Appletalk overview 537 ■ appletalk zones — all resources on an appletalk network are grouped into zones. Zones make appletalk resources easier to identify and locate. Your system maintains a zone table which maps network numbers to zones and lets you display this zone table indexed by network number...
Page 538
538 c hapter 21: a pple t alk r outing ■ in theory, appletalk networks can support millions of nodes. ■ appletalk supports zones, which makes it easier for network administrators to define workgroups that consist of users and services that span multiple network segments. Key concepts before you conf...
Page 539
Key concepts 539 the appletalk six-layer protocol suite does not fully comply with the osi seven-layer model. However, appletalk provides many of the functions and services of osi. Appletalk has no specific protocols for the application layer because the lower levels provide printer and file service...
Page 540
540 c hapter 21: a pple t alk r outing transport layer protocols the transport layer and the session layer provide end-to-end services in the appletalk network. These services ensure that routers transmit data accurately between one another. Each layer includes four protocols that work together to s...
Page 541
Key concepts 541 a router uses these items to determine the best path along which to forward a data packet to its destination. The routing table contains an entry for each network that a router’s datagram can reach within 15 hops. The table is aged at set intervals as follows: 1 after a specified pe...
Page 542
542 c hapter 21: a pple t alk r outing figure 64 illustrates a simple appletalk network, and table 91 shows the corresponding routing table. Figure 64 a simple appletalk network table 91 routing table for router 24 in figure 64 network range distance (in hops) interface state 5–5 1 2 good 12–12 3 3 ...
Page 543
Key concepts 543 appletalk echo protocol (aep) appletalk nodes use the aep to send datagrams to other nodes in the network. The transmitted aep datagram causes the destination node to return, or echo, the datagram to the sending node. This protocol determines whether a node is accessible before any ...
Page 544
544 c hapter 21: a pple t alk r outing appletalk data stream protocol (adsp) the adsp works with the atp to ensure reliable data transmission. Unlike atp, however, adsp provides full-duplex, byte-stream delivery. Therefore, two nodes can communicate simultaneously. Asdp also includes flow control, s...
Page 545
Key concepts 545 appletalk network elements an appletalk network consists of different nodes and groups of networks. Nodes can include workstations, routers, printers, and servers that provide services for other computers, called clients. This section describes these elements of an appletalk network...
Page 546
546 c hapter 21: a pple t alk r outing named entities when a device on the network provides a service for other users, you can give the device a name. The name appears on the chooser menu of the macintosh with an associated icon. For example, the chooser of the macintosh can include a printer icon. ...
Page 547
Key implementation guidelines 547 ■ phase 1 network — an appletalk network that contains a single network number (such as network 2). Also known as non-extended networks, phase 1 networks do not allow two nodes on a single network segment to belong to different zones. ■ phase 2 network — an appletal...
Page 548
548 c hapter 21: a pple t alk r outing appletalk interfaces on the switch 4007, an appletalk interface defines the relationship between a virtual lan (vlan) and an appletalk network. An appletalk interface has these elements associated with it: ■ seed interface — you can configure the interface to b...
Page 549
Appletalk interfaces 549 important considerations before you configure appletalk interfaces, review the following guidelines and considerations: ■ your system can support up to 32 appletalk interfaces. ■ each seed interface supports up to 16 zones. ■ your system supports a maximum of 1 appletalk int...
Page 550
550 c hapter 21: a pple t alk r outing ■ a router does not advertise its routing table through an interface until that interface has an associated network number range. ■ an interface is not added to the routing table until it has an associated network number range. Changing the zone association for...
Page 551
Appletalk routes 551 important considerations before administering appletalk routes, review the following guidelines and considerations: ■ the rtmp table supports a maximum of 514 entries. ■ appletalk supports a maximum distance of 15 hops. ■ a hop count of 0 represents a network that is directly co...
Page 552
552 c hapter 21: a pple t alk r outing appletalk address resolution protocol (aarp) cache the appletalk address resolution protocol (aarp) maps the hardware address of an appletalk node to an appletalk protocol address. Aarp maps addresses for both extended and nonextended networks. Appletalk uses d...
Page 553
Appletalk address resolution protocol (aarp) cache 553 aarp registers a node’s dynamically assigned address on the network, as follows: ■ aarp randomly assigns an address. ■ to determine whether another node is already using the address, the system broadcasts aarp probe packets containing the addres...
Page 554
554 c hapter 21: a pple t alk r outing appletalk zones an appletalk zone is a logical collection of nodes on an appletalk intranetwork. A zone can include all nodes in a single network or a collection of nodes in different networks. You assign a unique name to each zone to identify it in the intrane...
Page 555
Appletalk zones 555 appletalk routers use the zone information protocol (zip) to map network numbers to zones. Each appletalk router maintains a zone information table (zit), which lists the zone-to-network mapping information. Creating zones within a network reduces the amount of searching that a r...
Page 556
556 c hapter 21: a pple t alk r outing changing zone names when you change the zone information for a network, all routers on the segment must update their zone information tables with the new information. Although no appletalk mechanism forces routers to update zone lists, you can successfully chan...
Page 557
Appletalk zones 557 to change the associated zones for a network segment without changing the segment’s network range, follow these steps: 1 remove all appletalk interfaces attached to the segment for which you want to redefine zone information. 2 wait a minimum of 10 minutes while routers on the in...
Page 558
558 c hapter 21: a pple t alk r outing forwarding appletalk traffic you can choose to enable or disable appletalk forwarding on your system. Enabling forwarding when you enable appletalk forwarding, you enable the forwarding of datagram delivery protocol (ddp) packets. Because appletalk uses this ne...
Page 559
Checksum error detection 559 checksum error detection you can enable or disable checksum generation and verification. The appletalk protocol uses checksums to detect errors in data transmissions. A checksum totals all data bytes and adds the sum to the checksum field of the data packet. The receivin...
Page 560
560 c hapter 21: a pple t alk r outing appletalk statistics you can view statistics for the following appletalk protocols: ■ datagram delivery protocol (ddp) ■ routing table maintenance protocol ■ zone information protocol ■ name binding protocol datagram delivery protocol (ddp) appletalk extends th...
Page 561
Appletalk statistics 561 ■ inshortddps — number of input ddp datagrams that were dropped because the system was not their final destination and their type was short ddp ■ intoofars — number of input datagrams that were dropped because the system was not their final destination and their hop count wo...
Page 562
562 c hapter 21: a pple t alk r outing ■ routelesschgs — number of times that rtmp changed the next internet router in a routing entry because the hop count advertised in a routing table was less than the current hop count for a particular network ■ routeoverflows — number of times that rtmp attempt...
Page 563
Appletalk statistics 563 ■ outexreplies — number of zip extended replies that have been sent ■ outgnireplies — number of zip getnetinfo reply packets that have been sent out of this port ■ outgnirequests — number of zip getnetinfo packets that have been sent ■ outlocalzones — number of transmitted z...
Page 564
564 c hapter 21: a pple t alk r outing standards, protocols, and related reading for more information about appletalk technology, see the following publications: ■ gursharan s. Sidhu, richard f. Andrews, and alan b. Oppenheimer, inside appletalk, second edition (addison-wesley publishing company, 19...
Page 565: and
22 q o s and rsvp this chapter provides guidelines and other key information about how to use quality of service (qos) and the resource reservation protocol (rsvp) on a multilayer switching module. The chapter covers these topics: ■ qos overview ■ key concepts ■ key guidelines for implementation ■ q...
Page 566
566 c hapter 22: q o s and rsvp qos overview quality of service (qos) is a layer 3 feature that allows you to establish control over network traffic. Qos provides policy-based services, which establish various grades of network service to accommodate different types of traffic, such as multimedia, v...
Page 567
Qos overview 567 benefits you can use qos on your multilayer switching module to provide the following benefits: ■ control a wide variety of ethernet network traffic by: ■ classifying traffic based on packet attributes such as protocol type, class type (802.1p), ip address, or tcp/udp socket ■ assig...
Page 568
568 c hapter 22: q o s and rsvp if you use qos with rsvp, you are opting for a more complex type of end-to-end qos that aims for a guaranteed quality of service. To use rsvp, you must be routing. In addition, rsvp is required at the desktop, which may present issues of desktop control and upgrade is...
Page 569
Key concepts 569 the ieee 802.1p standard addresses separate queuing of time-critical frames to reduce the jitter that is caused by multicast flooding. This standard also defines the generic attribute registration protocol (garp), a layer 2 transport mechanism that allows switches and end systems to...
Page 570
570 c hapter 22: q o s and rsvp ■ nonflow classifiers — apply to both switched and routed traffic. You define this type of classifier to handle specific link-level protocols (ip, tcp/ip, ipx, or appletalk), a cast type (broadcast, unicast, or multicast), and one or more ieee 802.1p priority tag valu...
Page 571
Key concepts 571 drop causes the multilayer switching module to drop all packets on all ports that are associated with the control and its classifier. To drop conforming packets for only a subset of ports, specify the receiveport or aggregate rate limit, set the rate limit to 0, and specify the grou...
Page 572
572 c hapter 22: q o s and rsvp ■ qos excess tagging — allows you to select an ieee 802.1p priority tag value for nonconforming excess packets (packets that exceed the rate limit). This option refers to any packets marked as excess that you want to tag. After you enable this option, select an ieee 8...
Page 573
Key guidelines for implementation 573 key guidelines for implementation consider the following guidelines when you configure qos on your layer 3 switching module. Procedural guidelines configure classifiers and controls in the following order: 1 define a classifier, or choose a predefined classifier...
Page 574
574 c hapter 22: q o s and rsvp the following items describe how qos control aggregate rate limit for flow classifiers works on ports that are in certain groups. ■ qos control aggregate behavior for flow classifiers works only on ports that are in certain groups. The aggregate ports are treated as o...
Page 575
Qos classifiers 575 ■ you can define up to 100 flow classifiers and up to 16 nonflow classifiers. Because the multilayer switching module predefines 16 nonflow classifiers, you must delete one of the existing nonflow classifiers (except the default classifier) before you can add your own nonflow cla...
Page 576
576 c hapter 22: q o s and rsvp assigning flow and nonflow classifier numbers each classifier requires a unique number in the range of from 1 through 498. When you define a classifier, the first information you supply is the classifier number. The number you specify dictates which type of classifier...
Page 577
Qos classifiers 577 defining flow classifiers you can define up to 100 flow classifiers per multilayer switching module for routed ip traffic. When you define a flow classifier (using a unique classifier number), you can create one or more address/port patterns (filters) for that classifier. Each ad...
Page 578
578 c hapter 22: q o s and rsvp flow classifier information you supply the following information when you define a flow classifier: ■ classifier number in the range of from 1 through 399 (20 and 23 are predefined) ■ classifier name (a unique name of up to 32 characters long) ■ cast type (unicast, mu...
Page 579
Qos classifiers 579 for the source or destination ip address mask, you specify how many parts of the ip address you want to match. Place a 255 in each portion of the mask that you want the software to recognize; place a 0 in any portion of the mask that you want the software to ignore. The following...
Page 580
580 c hapter 22: q o s and rsvp defining nonflow classifiers nonflow classifiers enable you to classify bridged or routed frames according to protocol, cast type, and ieee 802.1p priority tag values. You can define up to 16 nonflow classifiers per multilayer switching module. The module predefines 1...
Page 581
Qos controls 581 qos controls after you define a classifier, you assign it a control to apply any of the following values: ■ rate limit (to limit the amount of input bandwidth the classifier uses) ■ service level for conforming packets (a transmit priority that maps to a particular transmit queue) ■...
Page 582
582 c hapter 22: q o s and rsvp important considerations review the following considerations before you configure controls: ■ the multilayer switching module predefines controls 1 through 4 for some of the predefined nonflow classifiers. You can also modify one of these predefined controls. You cann...
Page 583
Qos controls 583 assigning control numbers each control must have a unique control number. When you define a control, the multilayer switching module provides the next-available control number, but you can specify any unreserved control number. The multilayer switching module supports control number...
Page 584
584 c hapter 22: q o s and rsvp ■ for the rate limit type receiveport or aggregate: ■ service level for nonconforming excess (packets exceeding the rate limit) ■ whether nonconforming excess are loss eligible ■ how the rate limit is expressed (percentage of port bandwidth or kbps) ■ rate-limit value...
Page 585
Qos controls 585 specifying rate limits a rate limit restricts the amount of input bandwidth that is used by incoming classified traffic (optionally, on a per-port basis). When you define a control, you can specify one of three rate limits: ■ none — no rate limit ■ receiveport — imposes a separate l...
Page 586
586 c hapter 22: q o s and rsvp after you specify how the rate limit is expressed, you can specify a burst size. The burst size is the maximum amount of data that you can transmit at the line rate before the transmission is policed. This value accommodates variations in speeds and allows you to occa...
Page 587
Qos controls 587 specifying tcp drop control the tcp drop control option lets you create a control for packets used to establish tcp connections. This control affects qos flow classifiers that have tcp traffic going from source ip addresses to destination ip addresses. Tcp drop control does not func...
Page 588
588 c hapter 22: q o s and rsvp figure 68 shows an example with tcp drop control disabled. Figure 68 qos control action (drop control disabled) with the qos classifier and qos control definition shown in figure 68 (tcp control is not enabled), any attempt by a client on the end-user network to estab...
Page 589
Qos controls 589 in this example, any attempt by a client on an end user network to establish a tcp connection to a server on the admin network still fails, but it is now possible for clients on the admin network to establish tcp connections to servers on any network without restriction. Setting the...
Page 590
590 c hapter 22: q o s and rsvp timer options the following options are available for the timer control: ■ specific day — select the specific start day and time, and the specific end day and time. The control is removed after the end time is reached. ■ daily — select a starting day and then a start ...
Page 591
Examples of classifiers and controls 591 examples of classifiers and controls the following examples show ways to implement flow and nonflow classifiers and their associated controls. In all examples, a multilayer switching module on the switch 4007 provides the illustrated connections. Example 1: t...
Page 592
592 c hapter 22: q o s and rsvp to/from classifier definition with two address and port patterns: the control definition for the to/from classifier: classifier field classifier definition classifier number 15 classifier name dbserver1 cast type unicast ip protocol type udp source ip address 168.101....
Page 593
Examples of classifiers and controls 593 example 2: filtering traffic to a destination in the following example, a flow classifier is defined to block access to the accounting network 192.1.0.0 (which includes subnetworks 192.1.1.0 and 192.1.2.0) from the research and development 168.20.30.0 subnetw...
Page 594
594 c hapter 22: q o s and rsvp classifier definition for filtering traffic to a specific destination: the control definition for this filtering classifier: classifier field classifier definition classifier number 26 classifier name ipfilter1 cast type all ip protocol type all source ip address 168....
Page 595
Examples of classifiers and controls 595 example 3: using two classifiers to filter traffic in the following example, two flow classifiers (1 and 3) are defined with controls to filter ip traffic. Classifier 1 permits ip traffic between two hosts (192.20.3.3. And 193.20.3.3), while classifier 3 drop...
Page 596
596 c hapter 22: q o s and rsvp first classifier definition for filtering traffic to/from a specific destination: the control definition for the first filtering classifier: classifier field classifier definition classifier number 1 classifier name 192.20.3.3_to_193.20.3.3 cast type all ip protocol t...
Page 597
Examples of classifiers and controls 597 second classifier definition for filtering traffic to/from a specific destination: the control definition for the second filtering classifier: classifier field classifier definition classifier number 3 classifier name 192.20.3.3_to_all cast type all ip protoc...
Page 598
598 c hapter 22: q o s and rsvp example 4: assigning high priority to specific traffic in the following example, a classifier is defined to give high priority to web server (http) traffic. In this configuration, all web servers have addresses that end in .222. This example can apply to any type of t...
Page 599
Examples of classifiers and controls 599 the control definition for this classifier is as follows: example 5: nonflow multimedia tagged traffic in this example, a nonflow classifier is defined to classify bridged multimedia traffic with an ieee 802.1p priority tag of 5 and control this traffic with ...
Page 600
600 c hapter 22: q o s and rsvp nonflow classifier definition for multimedia traffic with priority tagging: the control definition for this classifier is as follows: classifier field classifier definition classifier number 405 classifier name interactive multimedia cast type all (unicast, multicast ...
Page 601
Examples of classifiers and controls 601 example 6: bridged nonflow ip unicast traffic in this example, a nonflow classifier is defined to classify ip unicast traffic between clients and the server on the 168.101.0.0 network. The applied control handles this bridged traffic with a high-priority tran...
Page 602
602 c hapter 22: q o s and rsvp the control definition for this classifier is as follows: modifying and removing classifiers and controls you can modify or remove a previously defined classifier or control. When you modify or remove a classifier, you specify the classifier number; when you modify or...
Page 603
Qos excess tagging 603 important considerations before you modify or remove classifiers or controls, review these guidelines: ■ you cannot remove the default classifier or the default control, but you can modify the default control. You can modify other predefined classifiers and the predefined cont...
Page 604
604 c hapter 22: q o s and rsvp example: qos excess tagging the following example shows how to use a classifier, control, and qos excess tagging to tag conforming qos multicast video traffic from a server as streaming multimedia 802.1p service and to tag any excess traffic as standard 802.1p service...
Page 605
Qos excess tagging 605 classifier definition for qos excess tagging: the accompanying control definition: classifier field classifier definition classifier number 25 classifier name videoserver1 cast type multicast ip protocol type udp source ip address 169.10.20.30 source ip address mask 255.255.25...
Page 606
606 c hapter 22: q o s and rsvp transmit queues and qos bandwidth qos uses four transmit queues: ■ control queue — the transmit queue for reserved network control traffic, such as rip or ospf updates, as well as rsvp data flows. This queue is always serviced first. Bandwidth for this queue is set vi...
Page 607
Rsvp 607 rsvp the resource reservation protocol (rsvp) is an ip service that prevents real-time traffic such as voice or video from overwhelming bandwidth resources. In general, rsvp supports qos ip flow specifications by placing and managing resource reservations across the network (setting admissi...
Page 608
608 c hapter 22: q o s and rsvp rsvp terminology familiarize yourself with the following rsvp terms: ■ rsvp flow — a data stream that operates in simplex, going one way from the origin to multiple destinations. The flows go from a set of senders to a set of receivers. ■ reservation style — the types...
Page 609
Rsvp 609 ■ never — the multilayer switching module never polices the flow, even if rsvp requests it. Example: rsvp figure 77 shows an rsvp configuration in which an rsvp reservation request (dotted lines) flows upstream along a multicast delivery tree (with routing-capable devices such as switch 400...
Page 610
610 c hapter 22: q o s and rsvp setting rsvp parameters if you enable rsvp, you specify the following information: ■ maximum total reservable bandwidth ■ maximum per-reservation bandwidth ■ policing option (edge, always, or never, with edge as the default) ■ service level for excess/policed traffic ...
Page 611
Rsvp 611 figure 78 rsvp information with installed flows total resv per resv policing excess excess loss bandwidth bandwidth option service eligible 50% 50% always low no session destination ip:port protocol senders receivers reservations 1 228.8.8.8:80 udp 1 1 1 2 230.2.2.2:20 udp 1 1 1 session-sen...
Page 612
612 c hapter 22: q o s and rsvp.
Page 613: Evice
23 d evice m onitoring this chapter provides descriptions and key operational information about device monitoring features and tools available in your switch 4007 modules. These features are available on switch 4007 layer 2 and multilayer switching modules. Differences in implementation between thes...
Page 614
614 c hapter 23: d evice m onitoring chapter scope device monitoring features for the switch 4007 enterprise switch are implemented on the enterprise management engine (eme) module, the layer 2 and multilayer switching modules, and the switch fabric modules. Features implemented on the eme module in...
Page 615
Chapter scope 615 you can perform device monitoring in either of these ways: ■ from the eme or administration console menus. You can manage features that are implemented in the eme module using the eme command line interface as described in the chapters in part ii of this guide. ■ from the respectiv...
Page 616
616 c hapter 23: d evice m onitoring device monitoring overview you can use the device monitoring features and tools described in this chapter to analyze your network periodically and to identify potential network problems before they become serious. To identify potential problems in your network, u...
Page 617
Key concepts and tools 617 network management platform the network management platform allows you to view the health of your overall network. With the platform, you can understand the logical configuration of your network and configure views of your network to understand how devices work together an...
Page 618
618 c hapter 23: d evice m onitoring event logging the event log messages display real-time information about the state of the system, a specific service, or both, and can help you diagnose site-specific problems. Event logging is implemented from the eme module. See the chapters in part ii of this ...
Page 619
Roving analysis 619 roving analysis roving analysis is the mirroring of fast ethernet, gigabit ethernet, or fiber distributed data interface (fddi) port traffic to another port of the same media type. This second port has an external rmon-1/rmon-2 probe or analyzer attached such as the 3com transcen...
Page 620
620 c hapter 23: d evice m onitoring key guidelines for implementation to enable the monitoring of ports on a system, follow these general steps: 1 add the port on which you want to attach the network analyzer. 2 start roving analysis. A select the port that you want to monitor. B enter the analyzer...
Page 621
Roving analysis 621 ■ if the physical port configuration changes in the system (that is, if you remove or rearrange modules), the mac address of the analyzer port remains fixed. If the module with the analyzer port is replaced with a different media type module, the rap configuration is cleared. ■ o...
Page 622
622 c hapter 23: d evice m onitoring ping the ping feature is a useful tool for network testing, performance measurement, and management. It uses the internet control message protocol (icmp) echo facility to send icmp echo request packets to the ip destination that you specify. Seechapter 16 for mor...
Page 623
Traceroute 623 strategies for using ping follow these strategies for using ping: ■ ping devices when your network is operating normally so that you have a performance baseline for comparison. ■ ping by ip address when: ■ you want to test devices on different subnetworks. This method allows you to pi...
Page 624
624 c hapter 23: d evice m onitoring traceroute operation to track the route of an ip packet, the traceroute feature launches udp probe packets with a small ttl value and then listens for an icmp time exceeded reply from a gateway. Probes start with a small ttl of 1 and increase the value by 1 until...
Page 625
Snmp 625 snmp overview the following sections provide an overview of snmp. Manager/agent operation snmp communication requires a manager (the station that is managing network devices) and an agent (the software in the devices that talks to management station). Snmp provides the language and the rule...
Page 626
626 c hapter 23: d evice m onitoring management information bases (mibs) define what can be monitored and controlled within a device (that is, what the manager can get and set). An agent can implement one or more groups from one or more mibs. See “management information base (mib)” later in this cha...
Page 627
Snmp 627 table 96 traps supported by snmp trap no. Trap name source indication 1 cold start mib ii the agent has started or been restarted. 2 link down mib ii the status of an attached communication interface has changed from up to down. 3 link up mib ii the status of an attached communication inter...
Page 628
628 c hapter 23: d evice m onitoring 22 port ler condition 3c fddi mib a status fddi port link error rate reaches a certain threshold. 23 port undesired connection 3c fddi mib a port connection does not math the connection policy. 24 port eb error condition 3c fddi mib elasticity buffer has overflow...
Page 629
Snmp 629 to minimize snmp traffic on your network, you can implement trap-based polling. Trap-based polling allows the management station to start polling only when it receives certain traps. Your management applications must support trap-based polling for you to take advantage of this feature. 34 p...
Page 630
630 c hapter 23: d evice m onitoring setting up snmp on your system access to system information through snmp is controlled by community strings. See part ii in this guide for information about configuring the community strings and trap reporting. You must also assign an ip address to the system eth...
Page 631
Remote monitoring (rmon) 631 ■ flushing all snmp trap destinations — when you flush the snmp trap reporting destinations, you remove all trap destination address information for the snmp agent. ■ set snmp smtproxytraps — controls snmp’s ability to alert you, by means of an snmp-to-smt proxy, of a si...
Page 632
632 c hapter 23: d evice m onitoring a typical rmon implementation has two components: ■ your system — your system’s built-in probe functionality examines all the lan traffic on its segments, and keeps a summary of statistics (including historical data) in its local memory. ■ management station — co...
Page 633
Remote monitoring (rmon) 633 rmon in your system your system supports rmon as follows: ■ rmon-1 support — the system software offers full-time embedded rmon support using snmp for seven rmon-1 groups. (rmon-1 defines 10 groups.) ■ rmon-2 support — the system software offers embedded rmon support for...
Page 634
634 c hapter 23: d evice m onitoring figure 80 shows an example of the rmon implementation. Figure 80 embedded rmon implemented on the system important considerations ■ to manage rmon, you must assign an ip address to the system through the eme management module. See the switch 4007 enterprise manag...
Page 635
Remote monitoring (rmon) 635 rmon-1 groups the system supports seven of the rmon-1 groups that the ietf defines. Table 97 briefly describes these groups. The layer 2 switching modules and switch fabric modules support four rmon-1 groups: groups 1, 2, 3, and 9. Multilayer switching modules support se...
Page 636
636 c hapter 23: d evice m onitoring statistics and axfddistatistics groups the statistics and axfddistatistics groups record frame statistics for ethernet and fddi interfaces. The information available per interface segment includes: ■ number of received octets ■ number of received packets ■ number...
Page 637
Remote monitoring (rmon) 637 history and axfddihistory groups the history and axfddihistory groups record periodic statistical samples for ethernet and fddi interfaces and store them for later retrieval. The information available per interface for each time interval includes: ■ number of received oc...
Page 638
638 c hapter 23: d evice m onitoring counters are useful when you compare their values at specific time intervals to determine rates of change. The time intervals can be short or long, depending on what you measure. Occasionally, counters can produce misleading results. Because counters are finite, ...
Page 639
Remote monitoring (rmon) 639 figure 81 shows a counter with thresholds set manually. Figure 81 manually set thresholds you can associate an alarm with the high threshold, the low threshold, or both. The actions that occur because of an alarm depend on the network management application. Rmon hystere...
Page 640
640 c hapter 23: d evice m onitoring host group the host group records the following statistics for each host (the host group detects hosts on the network by their physical mac addresses): ■ number of received packets ■ number of transmitted packets ■ number of received octets ■ number of transmitte...
Page 641
Remote monitoring (rmon) 641 event group the event group logs alarms or traps network event descriptions. Although alarm group thresholds trigger most events, other rmon groups may define event conditions. Rmon-2 groups the system software supports seven rmon-2 groups defined by the ietf in rfc 2021...
Page 642
642 c hapter 23: d evice m onitoring protocol directory group the protocoldir group provides information about the protocols that a particular rmon probe has or can interpret. It provides a common method of storing information about the protocols and makes it easier for a manager to monitor traffic ...
Page 643
Remote monitoring (rmon) 643 address map group the addressmap group maps each network address to a specific mac-level address and to a specific port on the network device. This group provides three scalar objects (to track address-mapping entry insertions, deletions, and the maximum number of entrie...
Page 644
644 c hapter 23: d evice m onitoring application-layer matrix group the almatrix group gathers statistics about pairs of hosts conversing over a monitored port based on protocol. (the rmon-2 network-layer matrix group gathers statistics based on the network address). This group features one control ...
Page 645
Management information base (mib) 645 mib files the organization of a mib allows a simple network management protocol (snmp) network management package, such as the transcend network control services application suite, to manage a network device without having a specific description of that device. ...
Page 646
646 c hapter 23: d evice m onitoring rmon statistics for gigabit ethernet are supported on layer 2 modules. The 4-port gigabit ethernet layer 3 switching module (gbic) supports the statistics, history, alarm, and event groups. Supported groups in this mib: ■ statistics (layers 2 and 3) ■ history (la...
Page 647
Management information base (mib) 647 a maximum of four different ports can be configured for the following rmon groups at any given time: ■ addressmap ■ alhost ■ almatrix ■ hosts ■ hosttopn ■ matrix ■ nlhost ■ nlmatrix ■ snmpv2-mib.Mib — used by other mibs, rfc 1907. Layer 2 and layer 3. ■ source-r...
Page 648
648 c hapter 23: d evice m onitoring figure 82 example of an rmon mib counter object the counter object information includes these items: ■ the name of the counter. In figure 82, the counter is called etherstatspkts (ethernet, statistics, packets). ■ access level. In figure 82, access is read-only. ...
Page 649
Management information base (mib) 649 when the system software performs an snmp get operation, the management application sends the oid to the agent, which in turn determines if the oid is supported. If the oid is supported, the agent returns information about the object. For example, to retrieve an...
Page 650
650 c hapter 23: d evice m onitoring figure 83 mib tree showing key mibs root iso(1) ccit(0) joint(2) standard(0) reg-authority(1) member-body(2) indent-org(3) dod(6) internet(1) directory(1) mgmt(2) experimental(3) private(4) mib(1) system(1) interfaces(2) at(3) ip(4) icmp(5) tcp(6) udp(7) egp(8) e...
Page 651
Management information base (mib) 651 mib-ii mib-ii defines various groups of manageable objects that contain device statistics as well as information about the device, device status, and the number and status of interfaces. The mib-ii data is collected from network devices using snmp. As collected,...
Page 652
652 c hapter 23: d evice m onitoring rmon-1 mib rmon-1 is a mib that enables the collection of data about the network itself, rather than about devices on the network. The ietf definition for the rmon-1 mib specifies several groups of information. These groups are described in table 102. Table 102 r...
Page 653
Management information base (mib) 653 rmon-2 mib rmon-1 and rmon-2 are complementary mibs. The rmon-2 mib extends the capability of the original rmon-1 mib to include protocols above the mac level. Because network-layer protocols (such as ip) are included, a probe can monitor traffic through routers...
Page 654
654 c hapter 23: d evice m onitoring 3com enterprise mibs 3com enterprise mibs allow you to manage unique and advanced functionality of 3com devices. These mibs are shipped with your system. Figure 83 shows some of the 3com enterprise mib names and numbers. The following mibs are included in 3com(43...
Page 655
Management information base (mib) 655 ■ 3cvlan.Mib — 3com vlan mib (43.10.1.14.1). Layer 2 and layer 3. ■ 3cweb.Mib — 3com web management mib (43.29.4.24). Layer 2 and layer 3. Mib names and numbers are usually retained when organizations restructure their businesses; therefore, some of the 3com ent...
Page 656
656 c hapter 23: d evice m onitoring.
Page 657: Eference
Iv r eference appendix a technical support index.
Page 659: Echnical
A t echnical s upport 3com provides easy access to technical support information through a variety of services. This appendix describes these services. Information contained in this appendix is correct at time of publication. For the most recent information, 3com recommends that you access the 3com ...
Page 660
660 a ppendix a: t echnical s upport to connect to the 3com ftp site, enter the following information into your ftp client: ■ hostname: ftp.3com.Com (or 192.156.136.12 ) ■ username: anonymous ■ password: you do not need a user name and password with web browser software such as netscape navigator an...
Page 661
Support from your network supplier 661 3com facts automated fax service the 3com facts automated fax service provides technical articles, diagrams, and troubleshooting instructions on 3com products 24 hours a day, 7 days a week. Call 3com facts using your touch-tone telephone: 1 408 727 7021 support...
Page 662
662 a ppendix a: t echnical s upport here is a list of worldwide technical telephone support numbers: country telephone number country telephone number asia pacific rim australia hong kong india indonesia japan malaysia new zealand pakistan philippines 1 800 678 515 800 933 486 61 2 9937 5085 001 80...
Page 663
Returning products for repair 663 returning products for repair before you send a product directly to 3com for repair, you must first obtain a return materials authorization (rma) number. Products sent to 3com without rma numbers will be returned to the sender unopened, at the sender’s expense. To o...
Page 665: Ndex
I ndex numbers 10base-t ethernet port 63 3com enterprise mibs 654 3com facts 661 499 (default classifier) 576 802.1p standard 568 priority tags 569 802.1q standard 247 802.1q tagging 439 a aarp (appletalk address resolution protocol) 547, 552 ac power supplies power requirements for 118 accept opcod...
Page 666
666 i ndex and (bit-wise and) opcode 327 appletalk address resolution protocol (aarp) 547, 552 addresses 553 and osi reference model 538 benefits of 537 changing zones 557 checksum 559 data link layer 539 data stream protocol (adsp) 544 echo protocol (aep) 543, 547 hop count 547 interfaces 548, 549,...
Page 667
I ndex 667 benefits qos 566 vlans 243 blocking port state 180 bootp (bootstrap protocol) 393 bridge designated 171 ipx snap translation enabling, disabling 195 least cost path 172 root 170 spanning tree bridge priority, setting 184 forward delay, setting 184 hello time, setting 184 maximum age, sett...
Page 668
668 i ndex connect command 106 connecting to remote devices from the eme 74 connector pinouts 65 console port 64 contact name, displaying 86 contact name, entering 86 continuous operations network, providing 147 controls, qos 585 assigning numbers 583 default 583 defining 573 definition of 570 prede...
Page 669
I ndex 669 dns (domain name system) 392 server problems 623 documentation cd-rom 34 comments 35 dot matrix display 62, 63 downloads 55 dpgm (destination port group mask) 337 drop service level 570 duplex mode, ethernet ports 156 dvmrp multicast routing table 444 dynamic route ip 367 ipx 524 dynamic ...
Page 670
670 i ndex extended network prefix 363 external link state advertisements, ospf 478 external lsas, and stub areas 487 external metrics, ospf type 1 478 type 2 478 external routes, ospf 478 f fabric backplane channels 41 fabric ports defining in vlans 248, 255 fast ethernet 146 media specifications 1...
Page 671
I ndex 671 h hangup terminal 83 hello interval, ospf 458, 474 hello packets, ospf 455, 456, 483 hello time 184 help for commands 78 high priority traffic sample qos configuration 598 hop count appletalk 547 ospf 450 host group, rmon 640 hosttopn group, rmon 640 hot swapping 58 hysteresis mechanism, ...
Page 672
672 i ndex ip address classes of 361 defined 360 derivation 360 division of network and host 360 dns 392 example 362 flow classifier 578 network layer 358 next hop 358 pinging 623 rip 381 routing table 366 subnet mask 362 subnetwork portion 362 ip hostnames pinging 623 ip interfaces defining 371 par...
Page 673
I ndex 673 learning state 184 leave-group message 213 led display button 63 leds network activity 67 limits rate (qos) 581 link aggregation, ethernet 147 link data, ospf 476 link state acknowledge packets, ospf 455 advertisements (lsas), ospf 453, 454, 456, 457, 461, 475 protocol, ospf 448 request p...
Page 674
674 i ndex modules displaying 127 effects of removals 143 effects of replacements 144 hot swapping 58 power class settings 117 monitoring, ethernet ports 158 multicast frames and packet filters 308 multimedia traffic, handling with qos 566 multimode fiber 159 multiple ip interfaces 359 n name eme, d...
Page 675
I ndex 675 operand 321 and opcodes 322 sizes supported 321 or opcode 327 osi reference model 358 appletalk routing and 538 ospf (open shortest path first) addresses addressing scheme 458 ranges 461, 465 adjacencies 456 and imported rip routes 491 area border routers 465, 467, 475, 477 areas 448, 451...
Page 676
676 i ndex stub areas 461, 462, 466, 487 stub default metrics 449, 487 summary 448 summary link state advertisements 477 transit areas 462 transmit delay 474 type 1 external metrics 478 type 2 external metrics 478 types of routers 454 variable length subnet mask 452 virtual links 450, 452, 454, 457,...
Page 677
I ndex 677 port group adding ports 340 as filtering criteria 337, 349 copying 340 deleting 340 displaying contents 340 listing 340 loading on system 341 removing ports 340 used in packet filter 337 port membership for vlans 249 port monitoring, ethernet 158 port numbering configuration guidelines 14...
Page 678
678 i ndex prioritization 199 priority queues 572 priority, ospf 473 probe, rmon 632 probeconfig group, rmon v2 644 procedures for establishing routing between vlans 283 qos 573 prompt, changing 83 protocol packets, ospf 455 protocol references 99 protocol suites for vlans 249, 280, 281 unspecified ...
Page 679
I ndex 679 replacing modules 144 requirements power 116 reservable bandwidth 608 reservation styles, rsvp 608 reset 105 reset eme cold 105 reset eme warm 105 reset module . Cold 104 reset module all cold 104 reset modules 104 resilient links active port 239 and server-to-switch connections 237 and s...
Page 680
680 i ndex routers area border 454, 464, 465, 475, 477 autonomous system boundary (asbrs), ospf 459 autonomous system boundary, ospf 475, 478 backbone, ospf 454 backup designated, ospf 454, 456 databases, ospf 464 default, ospf 468 designated, ospf 454, 457, 476 ids, ospf 455 interface 365 internal,...
Page 681
I ndex 681 serial line, and management access 45 servdiag command 107 servdiag command characteristics 108 servers, bandwidth to 147, 152 service levels, qos 581 definition 570 session layer appletalk 540 protocols, appletalk 543 session protocol, appletalk (asp) 544 set clock date_time 87 set eme c...
Page 682
682 i ndex static neighbors, ospf 483 static route ip 367, 372 ipx 524 statistics appletalk 560 baselining 618 nbp (name binding protocol) 563 ospf 504 ospf interface 473 ospf soft restart 486 rmon 636, 637 rtmp (routing table maintenance protocol) 561 vlan 303 zip (zone information protocol) 562 st...
Page 683
I ndex 683 transmit ports vlan rules for 299 transmit priorities, qos 570, 581 transparent bridging and aging addresses 163 ieee 802.1d compliant 198, 221 transport layer, appletalk 540 trap commands (snmp) flush 631 trap messages interpreting 98 trap receive 97 trap receivers 97 trap reporting conf...
Page 684
684 i ndex layer 2 vlans with tagged ports 272 layer 2 and layer 3 features 245 layer 2 vlans with overlapped and tagged ports 274 mode settings all open, all closed 261 modifying 302 modifying the vlan mode 263 network-based 289 vlans 290 non-tagging mode 247 null vlan 295 one-armed routing 286 ori...