- DL manuals
- 3Com
- Switch
- CoreBuilder 7000
- Operation Manual
3Com CoreBuilder 7000 Operation Manual
Summary of CoreBuilder 7000
Page 1
Http://www.3com.Com/ corebuilder ® 7000 family atm switches operations guide software version 4.55 base and extended part no. Doa3700-0aaa02 published january 2000
Page 2
Ii 3com corporation 5400 bayfront plaza santa clara, california 95052-8145 copyright © 1999, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) wit...
Page 3: Ontents
C ontents a bout t his g uide finding specific information in this guide 14 conventions 14 documentation 15 corebuilder 7000 family atm switch documents 16 related documents 16 documentation road map 17 documentation comments 18 year 2000 compliance 18 1 atm n etwork b asics atm overview 19 atm cell...
Page 4: E-Iisp P
Integrated local management interface (ilmi) 36 ilmi management information base (mib) 37 atm interface management entity (ime) 37 basic ilmi functions 38 status information 38 uni address registration 38 access to service registry mib 41 ilmi connectivity polling 41 automatic configuration procedur...
Page 5: Atm C
Features of pnni 68 advantages of implementing a pnni network 69 when to use pnni 69 pnni vs. E-iisp 69 pnni routing 71 organizing a network hierarchy 71 peer group leader 74 one node’s view of the network 76 information exchange in pnni 77 peer group leader elections 80 uplinks in a hierarchical st...
Page 6
Setup message 106 call-proceeding message 106 connect message 107 add party message 107 signaling protocol profile 107 establishing a virtual channel 108 point-to-point calls 108 point-to-multipoint calls 109 displaying connections 109 signaling sequences 109 signaling timers 111 timer resolution 11...
Page 7: Atm S
6 atm s witching atm switching 132 traffic statistics 134 general switch statistics 134 physical statistics 134 atm statistics 134 aal5 control statistics 134 signaling statistics 134 ifc communications statistics 134 traffic management 135 frame discard capability 135 efci 135 7 lan e mulation v er...
Page 8
Lan emulation statistics display 152 lan emulation redundancy 153 lane services in the corebuilder 7000 family atm switch card 154 redundant lane services 154 lecs redundancy facility - configuring the lecs-order database 154 les redundancy facility - configuring the elan topology database 155 selec...
Page 9
Set default holding time 176 display current mpc configuration 177 set shortcut setup frame count 178 set shortcut setup frame time 179 set flow detection protocols 180 set initial retry time 181 set retry time maximum 182 set hold down time 182 8 v irtual n etworks virtual lan basics 185 vlans in t...
Page 10
Summary of improved switch redundancy features in version 4.5 207 system requirements 209 version 4.5 features 210 identifying the active switching module 210 conditions for switch-over to redundant module 210 switch-over reboot 210 communications between active and redundant switches 210 210 switch...
Page 11: 7000 F
B p rotocols and i nterfaces physical layer 223 sonet sts-3c physical layer interface 223 ds-3 physical layer interface 224 atm layer 226 atm cell structure 226 the atm layer 227 operation & maintenance (oam) 229 atm layer oam 229 atm adaptation layer (aal) 231 aal1 231 aal2 231 aal3/4 231 aal5 231 ...
Page 13: Bout
A bout t his g uide the corebuilder 7000 family atm switches operations guide provides all the information you need to understand the networking principles of the corebuilder ® 7000 family atm switch and how it is used in an atm network. It is applicable for both the base and extended versions of th...
Page 14
14 a bout t his g uide finding specific information in this guide this table shows the location of specific information in this guide: conventions table 1 through table 3 list conventions that are used throughout this guide. If you are looking for turn to information about atm network basics chapter...
Page 15
Documentation 15 documentation this section provides information about supporting documentation, including: corebuilder 7000 family atm switch documents related documents table 2 text conventions convention description screen displays this typeface represents information as it appears on the screen....
Page 16
16 a bout t his g uide corebuilder 7000 family atm switch documents the cd-rom that comes with your system contains on-line versions of the documents: corebuilder 7000 family atm switches installation and startup guide this guide describes how to install and setup a corebuilder 7000 family atm switc...
Page 17
Documentation 17 documentation road map the following table helps you locate the information you need. Corebuilder 7200 ethernet/atm interface card operation guide dua7200-0aaa01 corebuilder 7400 ethernet/atm interface card user guide dua7400-0aaa01 corebuilder 7600 fast ethernet interface card user...
Page 18
18 a bout t his g uide documentation comments your suggestions are very important to us. They help us make our documentation more useful to you. Please send e-mail comments about this guide to: sdtechpubs_comments@3com.Com please include the following information when commenting: document title docu...
Page 19: Atm N
1 atm n etwork b asics this chapter provides basic concepts and information about: atm overview atm cell structure atm layers functional planes designing atm networks atm network examples atm overview in 1986, the comité consulatif international télégraphique et téléphonique (ccitt), now known as th...
Page 20
20 c hapter 1: atm n etwork b asics overcoming the problems that exist in a shared-media networking technology, like ethernet, token ring, and fddi. Atm allows different types of physical layer technology to share the same higher layer — the atm layer. Atm cell structure unlike ethernet which transf...
Page 21
Atm layers 21 having all data in a fixed-length cell format speeds transmission dramatically by eliminating the need for protocol recognition and decoding. A good analogy is containerised shipping where uniform shape and weight of containers and standardized labelling considerably ease and quicken p...
Page 22
22 c hapter 1: atm n etwork b asics physical layer the physical layer in atm defines the mapping of cells, much in the same way that the traditional osi physical layer handles bits, defining physical media characteristics, line coding and framing. The atm physical layer transmits and receives atm ce...
Page 23
Functional planes 23 figure 3 uni functional/protocol model user plane transfers data for a user application between the devices. User application refers to a high-level (higher than atm) data transmission format such as ethernet data transmission, frame relay data transmission, or video data transm...
Page 24
24 c hapter 1: atm n etwork b asics implemented by the ilmi — integrated local management interface. The ilmi is described in the following sections. Designing atm networks an atm network uses the following pieces of equipment as basic building blocks: servers or end stations — these can be equipped...
Page 25
Atm network examples 25 workstations to the atm network. Workstations with atmlink adapters supporting connectivity to sonet/sdh for s-bus platform can be connected directly to the corebuilder 7000 family atm switch. The corebuilder 7000 family atm switch with a workgroup using ip over atm, you can ...
Page 26
26 c hapter 1: atm n etwork b asics classical ip atm network which may be segmented into ip subnets. A router supporting atm connectivity with rfc-1577 compliance provides connectivity between these subnets. The netbuilder ii router also supports connectivity to non-atm protocols through the ip laye...
Page 27
Atm network examples 27 figure 5 multiple switch ip routed network lan emulation atm networks lan emulation (otherwise known as lane or le) provides interoperability between devices on atm lans and traditional lans such as ethernet, and supports configurations that connect traditional lans over an a...
Page 28
28 c hapter 1: atm n etwork b asics building lan emulation atm networks a lan emulation network provides the ability to run network applications over atm and maintain the legacy lans’ well-established environment. The following network devices support lan emulation: a corebuilder 7000 atm family swi...
Page 29
Atm network examples 29 corebuilder 7000hd switches to form a robust network core with a very high bandwidth capable of serving the entire headquarters network. The redundant links between members of the core prevent a single point of failure; automatic activation of backup lane services ensures the...
Page 30
30 c hapter 1: atm n etwork b asics ..
Page 31
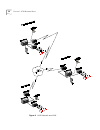
Atm network examples 31 figure 6 the corebuilder 7000 family switch in a headquarters network regional and branch offices the networks shown in figure 7 are installed in a regional and branch office of the enterprise. The network core in the basement data center of the regional office consists of tw...
Page 32
32 c hapter 1: atm n etwork b asics.
Page 33
Atm network examples 33 figure 7 regional and branch networks vp tunneling over wan the three enterprise networks illustrated are connected over a wan vp switch by means of vp tunneling. The full set of lane services are provided, including broadcast services to all stations in the enterprise. Figur...
Page 34
34 c hapter 1: atm n etwork b asics figure 8 lane network over wan.
Page 35: Etwork
2 n etwork i nterface m anagement this chapter provides basic concepts and information about: network interfaces integrated local management interface (ilmi) basic ilmi functions automatic configuration procedures network interfaces to enable individual atm devices to function together in an atm net...
Page 36
36 c hapter 2: n etwork i nterface m anagement figure 9 a typical network user network interface a user network interface (uni) operates between an atm user and a private atm switch, or between a private atm switch and the public carrier atm network. There is very little difference between a public ...
Page 37
Integrated local management interface (ilmi) 37 the ilmi functions for an atm interface provide status, configuration, statistics, and control information about physical and atm layer parameters of the atm interface. In addition, it provides for address registration across the uni. Ilmi communicatio...
Page 38
38 c hapter 2: n etwork i nterface m anagement basic ilmi functions this section discusses the following ilmi services provided by ime: status information uni address registration access to service registry mib ilmi connectivity polling status information the ime extracts the following status inform...
Page 39
Basic ilmi functions 39 of addressing information between the user and the network at the uni, at initialization and at other times, as required. Address registration is done in two phases. The network side ime supplies the network prefix of the address, and the user side ime appends the user part t...
Page 40
40 c hapter 2: n etwork i nterface m anagement international code designator is maintained by the british standards institute. The length of this field is two octets. E.164 atm format — specifies integrated services digital network numbers. A public network addressing standard utilizing up to a maxi...
Page 41
Basic ilmi functions 41 registered at the port, the member id can be used to access a virtual channel to display information about calls on that channel. Access to service registry mib ime provides a service to read the service registry table to retrieve the lan emulation configuration server (lecs)...
Page 42
42 c hapter 2: n etwork i nterface m anagement automatic configuration procedures this section discusses the following topics: auto-discovery auto-configuration modification of local attribute configuring a port on change of attachment automatic configuration refers to the ability of the corebuilder...
Page 43
Automatic configuration procedures 43 commands. The following table shows the various operational states that can occur when you disable either auto-discovery or auto-configuration: auto-discovery the auto-discovery procedure configures the two parameters: atm interface type and ime type. Atm interf...
Page 44
44 c hapter 2: n etwork i nterface m anagement the determination of the atm interface type and ime type is discussed in the following sections. Edge-device peer if the peer device is an edge-device or atm end-station (user) the parameters are determined as follows: atm interface type—the atm interfa...
Page 45
Automatic configuration procedures 45 table 8 shows the possible results of auto-discovery in this case. Auto-discovery sets the ime type by comparing the system id of the local switch with that of the peer switch. The switch with the larger system id is set to user-side and the switch with the smal...
Page 46
46 c hapter 2: n etwork i nterface m anagement if the peer is running e-iisp, the ime type is determined automatically as shown in table 11 but if the peer is running iisp you need to configure the local switch by lma. For more information on configuring the local switch by lma, see “display signali...
Page 47
Automatic configuration procedures 47 if the peer is running ilmi 4.0, the ime type is determined automatically as shown in table 14 but if the peer is running ilmi version 3.0 or 3.1 you need to configure the local switch by lma. For more information on configuring the local switch, see “update sig...
Page 48
48 c hapter 2: n etwork i nterface m anagement a summary of the lma settings (columns 3,4) needed to achieve a desired interface type and ime type (columns 1,2). Viewing auto-discovery results you can view: if auto-discovery is enabled or not. If auto-discovery or manual discovery was used. The ime ...
Page 49
Automatic configuration procedures 49 ilmi version ilmi versions 3.0, 3.1, and 4.0 are available on the corebuilder 7000 family atm switch. The ilmi version is selected to be ilmi 4.0 if both devices support ilmi 4.0 protocol, otherwise it will be set to ilmi 3.1. If you manually set the ilmi versio...
Page 50
50 c hapter 2: n etwork i nterface m anagement 3 the local change of attribute mechanism causes the ilmi in both switches to restart, and the flash values—uni 4.0 in both switches—are loaded as current values. Auto-configuration now sees that both a and b are uni 4.0 and makes no further change. The...
Page 51
Automatic configuration procedures 51 4 sends a coldstart trap to its peer ime entity to indicate the interface is restarting. 5 reinvokes any automatic configuration procedure. 6 performs address registration, if necessary. 7 declares ilmi connectivity to be re-established. Configuring a port on ch...
Page 52
52 c hapter 2: n etwork i nterface m anagement 5 performs address registration, if necessary. You can control the sensitivity of detecting a change of attachment by adjusting the link management polling rate through the lma (see “update ilmi channel polling interval” on page 139 in the management gu...
Page 53: E-Iisp P
3 e-iisp p rotocol this chapter provides basic concepts and information about: introducing enhanced interim interswitch protocol (e-iisp) iisp vs. E-iisp hierarchy in an e-iisp network planning a network with e-iisp e-iisp hierarchical routing algorithm introducing enhanced interim interswitch proto...
Page 54
54 c hapter 3: e-iisp p rotocol with iisp, routing decisions are made on a switch-by-switch basis. One switch sends a request for an svc to another, and the receiving switch searches its address table for the destination address. The request is passed on to another switch in the network if the desti...
Page 55
Hierarchy in an e-iisp network 55 hierarchy in an e-iisp network e-iisp also introduced the concept of hierarchy in a network design. Using e-iisp, most 3com atm networks are based in the atm address of 47.0.0.0.0.0.3c.0.0.A* i.E., utilizing the last four bytes of the switch portion of the atm addre...
Page 56
56 c hapter 3: e-iisp p rotocol figure 11 atm address components the atm address has 20 bytes, which are divided into a 13-byte network prefix and a 7-byte user part. These are further divided into fields shown in table 17. The afi and afi-specific fields should be the same. The default value is 47....
Page 57
Hierarchy in an e-iisp network 57 figure 12 fields available for switch address each of the fields rd and area is two bytes long and a byte is represented by two hexadecimal digits 0-f so that fields rd and area together are represented by eight hexadecimal digits. These eight digits represent the l...
Page 58
58 c hapter 3: e-iisp p rotocol configuring network atm addresses after the addressing scheme is established, you use either the integrated fast setup procedure or specific lma commands (see “update network prefix” on page 63 in the management guide) to register the network prefixes at each corebuil...
Page 59
Planning a network with e-iisp 59 lane redundancy hierarchical topology as discussed previously, the routing algorithm of e-iisp assumes that you have constructed your network with a hierarchical topology. As an example, create a hierarchical switch topology consisting of three trees. 1 in the a tre...
Page 60
60 c hapter 3: e-iisp p rotocol figure 13 hierarchical switch addressing in tree topology after you have set up the addressing scheme in this manner, the routing algorithm ensures that any switch in this network can find every tree in it (and therefore the location of every other switch) by first ac...
Page 61
E-iisp hierarchical routing algorithm 61 the user part corresponding to the user part of the atm destination address of the receiving atm user. 2 the corebuilder 7000 family atm switch compares the atm destination address with the full atm address of each of its uni neighbors. If a match is found, t...
Page 62
62 c hapter 3: e-iisp p rotocol is c.2.1. A* looks at its neighbors and notices that none of them begin with the c* prefix. The only option is to use the default port. Since b* has the shortest network prefix which is not longer than a* it is used as the default port. If no default port is found, a ...
Page 63
E-iisp hierarchical routing algorithm 63 the crankback mechanism eliminates the need for the original transmitting station to release and re-establish the call. The crankback mechanism works as follows: if a virtual channel fails to be established along one of the links, a release message will be se...
Page 64
64 c hapter 3: e-iisp p rotocol figure 14 alternate routes in an atm network alternate routes are desirable for the following reasons: dividing the load between nodes over several links reduces congestion (see next section) if one link fails, an alternate link can be used. If the node cannot be foun...
Page 65
E-iisp hierarchical routing algorithm 65 routing table as the routing algorithm establishes the internal connections, it also establishes a routing table. For each connection it establishes, the algorithm stores alternate links that it might have used instead of the one it did use. This table can be...
Page 66
66 c hapter 3: e-iisp p rotocol lane redundancy if you are going to provide lane redundancy in your network, pay special attention to creating alternate routes between nodes. Correct e-iisp planning for route failover/redundancy is required for lane redundancy to work (for more information about pla...
Page 67: Rivate
4 p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 this chapter provides basic concepts and information about: introducing pnni version 1.0 pnni vs. E-iisp pnni routing configuring the pnni network pnni signaling protocol pnni is available in version 4.5 extended only. Introducing pnn...
Page 68
68 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 any one node. These are the addresses of the nodes that any one node is physically or logically connected to. Qos metrics include information on available bandwidth, guaranteed cell delay, jitter, and other performance op...
Page 69
Pnni vs. E-iisp 69 advantages of implementing a pnni network there are many advantages of implementing a network with pnni. First, it creates a more stable network. Since the nodes are aware of every network problem (low bandwidth, no connection, etc.) less time is spent in finding the best route to...
Page 70
70 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 figure 15 looping in e-iisp this figure shows a sample network topology, in which the signal is sent as follows: switch e is transmitting to switch a. The signal is sent from e to c (see number 1 in figure 15). The link f...
Page 71
Pnni routing 71 switch d now has a decision to make. It does not know that switch b is connected to switch a. Switch d can either send the signal to switch f or to switch b. Should it choose to send to f (as shown in number 3), then switch f will send the signal to e (as shown in number 4). Switch e...
Page 72
72 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 for information on the atm address format, refer to "atm address format" on page 84 in the management guide. Once the node is put into a group, the groups are linked and a hierarchy is created. Each node and peer group ha...
Page 73
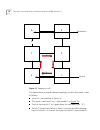
Pnni routing 73 in figure 16, a flat network, which has 17 nodes, is shown. Each node is denoted by a letter and 2 numbers (x.1.1). Figure 16 a network with no hierarchy a.1.1 a.1.2 a.1.3 a.1.4 a.1.5 a.1.6 a.1.7 a.1.8 a.1.9 a.2.0 a.2.1 a.2.2 a.2.3 a.2.4 a.2.5 a.2.6 a.2.7.
Page 74
74 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 in figure 17, the hierarchical network is created with the same nodes. Each node belongs to one of the peer groups. This example will also be used in later sections to describe the different aspects of pnni. Figure 17 low...
Page 75
Pnni routing 75 while complete information is transmitted downstream. This information is stored in the topology database. In this network topology, you can also see that there are 14 border nodes. Physical links and logical links in the lowest level hierarchy, any connection between two nodes is a ...
Page 76
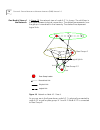
76 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 one node’s view of the network in figure 18, the network view of node a.3.1 is shown. The solid lines in the figure represent physical connections. The dotted line represents how the group is summarized in the hierarchy. ...
Page 77
Pnni routing 77 information exchange in pnni each node exchanges hello packets with its immediate neighbors and uses this information to determine its local state information. Hello messages in figure 17 there are 3 peer groups. A, b and c. Each group has different switches and workstations connecte...
Page 78
78 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 table 19 shows the list of information node a.1.2 collects from its neighbors after the hello protocols are sent. The learning does not stop here. After the hello message has been broadcasted, the nodes in the network sca...
Page 79
Pnni routing 79 in figure 20, node a.1.2 will not transmit information about a.2.1, because a.1.2 is in peer group a.1 and a.2.1 is in peer group a.2. After all the ptse information has been exchanged among all the members of the peer group, the topology databases of each of the peer group members a...
Page 80
80 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 figure 21 partial topology database readout peer group leader elections after the topology databases of each peer group are synchronized, the nodes ask each other for their priority level. The network manager assigns a pr...
Page 81
Pnni routing 81 hierarchy level where it will meet the leaders of b and c. Aggregated information is exchanged and each node will transmit down the hierarchy all that it has learned. At this point the complete topology database for each node has been filled. Figures 6 and 7 show the next two hierarc...
Page 82
82 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 figure 23 the entire network at this point, information from each group is distributed to the third level hierarchy. Each member in the 3rd level transfers the information as described previously to the other nodes in thi...
Page 83
Pnni routing 83 the hierarchy). Table 21 shows the updated topology database that node a.1.2 will have after receiving this new information. Table 21 updated database for node a.1.2 uplinks in a hierarchical structure when a hierarchy is created, uplinks from the lowest level to the higher levels ar...
Page 84: Esi
84 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 configuring the pnni network when configuring a pnni network, it is essential that each node has a unique address which represents a picture of where the node is in the hierarchy. Topics covered in this section include: a...
Page 85
Configuring the pnni network 85 atm addressing example if we take peer groups a, b, and c from figure 17 as an example, each node in the groups would have the following atm addresses as presented in table 23: the ptses and the priority levels are created based on this addressing scheme. For informat...
Page 86
86 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 parameters that the atm network must have to be able to guarantee the signal establishment. Call establishment consists of two operations: path selection connection setup at each point along the path path selection is mad...
Page 87
Pnni signaling protocol 87 pnni signaling protocol this section will cover pnni signaling. Topics that will be covered include: pnni signaling establishing a channel in pnni crankback and alternate routing pnni signaling as stated earlier, pnni is a signaling protocol used between networks, not user...
Page 88
88 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 mechanisms that ensure that the data will be transferred without having to send a disconnect message to the source. Establishing a channel in pnni with a flat network in this section, the example shown in figure 27 will b...
Page 89
Pnni signaling protocol 89 connection is established and the data is sent. These connections are permanent because they are established administratively, rather than on a demand basis. If the signal is to be established by demand, it is known as a soft pvc or soft pvcc. Alternate routing and crankba...
Page 90
90 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 the signal between nodes a.2.3 and a.2.2 has failed. A.2.3 will send a ptse message that will be flooded to all nodes in the network. At the same time, it will crankback the signal to the source, so that an alternate rout...
Page 91
Pnni signaling protocol 91 figure 30 alternate routing establishing a channel in a hierarchical network in this section, the example shown in figure 27 will be used. Node a.1.1 wants to establish a connection to send data to node a.2.6. V x x v a.1.1 a.1.2 a.1.3 a.1.4 a.1.5 a.1.6 a.1.7 a.1.8 a.1.9 a...
Page 92
92 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 figure 31 signaling in a hierarchical network there are many paths that the signal can take. Based on reachability, qos metrics and current information available about the links, the path from a.1.1 to a.2.6 is chosen. A ...
Page 93
Pnni signaling protocol 93 alternate routing and crankback occasionally, after the decision has been made by the switch to open a channel in a certain direction, the link may fail or the attributes may change. When the switch detects this change, it does not close the connection and send a disconnec...
Page 94
94 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0 figure 33 crankback in a hierarchy in figure 33, the signal crankedback 1 hop. In a hierarchical network the signal only has to crankback to the first node it can find that has an alternate path available. The hops in cra...
Page 95
Pnni signaling protocol 95 figure 34 alternate routing in a hierarchy in this example a new dtl is generated as shown and the signal is sent. At no point in the process is the call released. This saves time and prevents having to crankback completely to the source, thereby saving valuable resources....
Page 96
96 c hapter 4: p rivate n etwork - to -n etwork i nterface (pnni) v ersion 1.0
Page 97: Stablishing
5 e stablishing atm c hannels atm is a connection-oriented transport service, much like a telephone. Unlike ethernet, where data is sent out on a common bus, atm requires that a path or virtual channel be established to carry the call from the source station to the destination station before data tr...
Page 98
98 c hapter 5: e stablishing atm c hannels this section discusses the external link, established by signaling. For a discussion of the internal links, which are established by routing, see “routing — internal links” on page 125 in the management guide. A simple example of a virtual channel is shown ...
Page 99
Virtual channels 99 external links – atm connections each external link, referred to as an atm connection, is uniquely characterized by a pair of integers vpi and vci called the virtual path identifier and virtual channel identifier. The default range is vpi: 0-7; vci: 32-511vpi: 0-2 8 ; vci: 0-2 16...
Page 100
100 c hapter 5: e stablishing atm c hannels switched virtual channels a virtual channel can be set up either automatically by signalling, in which case it is called a switched virtual channel (svc), or, you can set it up manually through lma in which case it is called a permanent virtual channel (pv...
Page 101
Vp tunneling 101 . Vp tunneling as mentioned previously, a virtual path (vp) is a set of virtual channels with a common vpi value. A vp tunnel (virtual path tunnel) is a virtual path which has been extended to include a signaling channel and an ilmi channel, in addition to the call channels. Normall...
Page 102
102 c hapter 5: e stablishing atm c hannels one vp tunnel per port can be allocated to point-to-multipoint calls. Each of these vp tunnels is associated with a virtual uni; it has its own ilmi mib, ume management, and addressing operations (see “virtual uni” on page 104 in the management guide). The...
Page 103
Vp tunneling 103 have the same source and destination are assigned the same vpi value, they are switched more efficiently by the vp switch. Lane over wan the wan vp switch allocates the vpi values which are then used to establish the corebuilder vp tunnels. A corebuilder 7000hd vp tunnel is establis...
Page 104
104 c hapter 5: e stablishing atm c hannels figure 36 lan over wan virtual uni as defined in the basic uni specification, each ilmi mib is intended to maintain management information about a single interface. Each interface is assumed to connect a single user to a single switch port and all ilmi inf...
Page 105
Signaling — external links 105 signaling protocol atm uses the uni signaling standard protocol for dynamically establishing, maintaining and clearing svc connections between endpoints. The procedures are defined in terms of messages and the information elements that characterize the atm connection a...
Page 106
106 c hapter 5: e stablishing atm c hannels each message is composed of information elements that carry the details of the message. Displaying signaling messages to display signaling messages statistics, see “signaling statistics” on page 247 in the management guide. Setup message the setup signalin...
Page 107
Signaling — external links 107 call-proceeding suppression” on page 208 in the management guide). Connect message the connect signaling message is sent in response to the setup command. It indicates that the receiving side of the connection has accepted the requirements and the call setup is complet...
Page 108
108 c hapter 5: e stablishing atm c hannels displaying the signaling protocol profile to display or update the signaling protocol profile, see “update signaling protocol profile” on page 202 in the management guide. Establishing a virtual channel figure 37 shows the steps involved in establishing a ...
Page 109
Signaling — external links 109 point-to-multipoint calls a point-to-multipoint call is a collection of associated atm vc or vp links, with associated endpoint nodes. A connection is defined as a section of a call. A point-to-multipoint call has the following properties: the source endpoint serves as...
Page 110
110 c hapter 5: e stablishing atm c hannels figure 38 signaling message sequence for a point-to-point connection point-to-multipoint connection figure 39 shows the sequence of signaling messages for setting up a point-to-multipoint external link (connection) between a root station and a set of desti...
Page 111
Signaling — external links 111 figure 39 signaling message sequence for a point-to-multipoint connection signaling timers each signaling protocol comes with a set of timers, one for each type of message in the protocol. These timers determine when an expected response to a message is overdue. They a...
Page 112
112 c hapter 5: e stablishing atm c hannels table 28 q.2931 watchdog timers — user end timer name default time-out start timer stop timer t301 180 alerting received connect received t303 20 setup sent connect, call proceeding or release complete received t308 150 release sent release complete or rel...
Page 113
Signaling — external links 113 timer resolution all the timers in the q.2931 and q.Saal protocol are based on a common timer tick-length called the timer resolution. When the timer resolution is changed, all timers are affected. The corebuilder 7000 family atm switch is shipped with a default timer ...
Page 114
114 c hapter 5: e stablishing atm c hannels (see “update protocol timer resolution” on page 212 in the management guide). Signaling aal the signaling described previously takes place in signaling channels kept separate from the channels used for data transmission. The saal (signaling aal) is the ada...
Page 115
Signaling aal 115 sscop timers table 31 and table 32 present the sscop watchdog timers. Management data transfer md unassured transfer of management data table 30 sscop pdus according to type function pdu description table 31 sscop timers sscop timer description poll the maximum time between transmi...
Page 116
116 c hapter 5: e stablishing atm c hannels for stability, the timer no-response should be greater than the timer keep-alive and the timer no-response should be greater than the timer poll. Timer no-response and timer cc should be set to a value greater than the round trip delay. The timer idle may ...
Page 117
Call admission control 117 call admission control the corebuilder 7000 family atm switch uses call admission control (cac) algorithms during the establishment of a virtual channel to determine whether a connection request should be accepted or rejected. A connection request is accepted only when the...
Page 118
118 c hapter 5: e stablishing atm c hannels sustained cell rate (scr) — average cell rate over time, taking into account burst traffic the gcac algorithm consists of the following steps: 1 read the peak cell rate (pcr) and the sustained cell rate (scr) from the traffic contract of the call. 2 add up...
Page 119
Call admission control 119 figure 40 switch cell rate utilization for vbr and cbr service classes gcac for abr service class the gcac for the abr service is similar to that of the vbr service except that it is based on the minimum cell rate (mcr) parameter read from the traffic contract. Figure 41 s...
Page 120
120 c hapter 5: e stablishing atm c hannels uni signaling 4.0 features this section describes the features added in uni signaling 4.0 which are supported by the corebuilder 7000 family atm switch. These include: atm anycast capability signaling of individual qos parameters message conversion between...
Page 121
Uni signaling 4.0 features 121 signaling of individual qos parameters the corebuilder 7000 switch lets you indicate individual quality of service parameter values for a specific call. This information take precedence over the standard qos parameters and is passed over the network. If individual qual...
Page 122
122 c hapter 5: e stablishing atm c hannels message conversion between signaling protocols in order to transmit a signaling message across interfaces which have different signaling protocols at each end, the corebuilder 7000 switch performs message conversion. The conversion handles the follow signa...
Page 123
Quality of service parameters 123 the bandwidth available from the network may vary, but does not become less than mcr. The corebuilder 7000 switch forwards the abr information to the end users. Three information elements are involved in the signaling of abr capability: 1 atm traffic descriptor. Inc...
Page 124
124 c hapter 5: e stablishing atm c hannels this capability applies only when the setup message contains a broadband bearer capability, that is, when "abr" is indicated in the atm transfer capability field. Constant bit rate service class cbr, or constant bit rate service, is used by connections whi...
Page 125
Routing — internal links 125 unspecified bit rate service class the unspecified bit rate service class is intended for non-real time applications. These are applications that do not require tightly constrained delay and delay variation.Examples of these applications include: file transfer and e-mail...
Page 126
126 c hapter 5: e stablishing atm c hannels the following description of the routing method assumes that an external link of a virtual channel has already been established to an input port of the switch. In addition, the call’s destination address, which was embedded in the signaling setup message, ...
Page 127
Routing — internal links 127 but on a different branch. In case more than one neighbor’s address partially matches, the shortest address is chosen. If neither a full or partial match is found, the algorithm seeks a neighbor’s network prefix whose significant length is shorter than that of the switch...
Page 128
128 c hapter 5: e stablishing atm c hannels no vcc available — number of vccs exceed a limit no rate available — no available bandwidth resources unavailable — node internal resource problem the crankback mechanism eliminates the need for the original transmitting station to release and re-establish...
Page 129
Physical-link failure indicator 129 the recovery process proceeds in the following steps: 1 the link failure is detected and the system software is notified. 2 the ilmi service deletes atm addresses of devices on the failed link which were registered by ilmi. 3 the call control software releases any...
Page 130
130 c hapter 5: e stablishing atm c hannels : table 34 parameters in selecting link-failure sensitivity sensitivity time (seconds) speed of detection certainty of detection high 5 high low medium 15 medium medium low 30 low high.
Page 131: Atm S
6 atm s witching the previous two chapters presented the concept of virtual channel, what a virtual channel is and how it is built. This chapter discusses how atm data travels, or is switched, over a virtual channel. This chapter provides basic concepts and information about: atm switching traffic s...
Page 132
132 c hapter 6: atm s witching atm switching atm switching is performed at the atm layer through virtual channels. Individual cells are switched over the channel through the network based on the cell header. Figure 42 cell flow in atm switching figure 42 shows how a call is transferred over a virtua...
Page 133
Atm switching 133 the call is transferred as follows: 1 the edge device translates the ethernet frames into atm cells and forwards them to the atm output port. 2 the atm output port writes the vpi/vci values for the external link for the vc on the cell header and transmits the cells on the line that...
Page 134
134 c hapter 6: atm s witching traffic statistics the corebuilder ® 7000 family atm switch provides the following types of flow statistics general switch statistics physical statistics atm statistics aal5 control statistics signaling statistics ifc communications statistics general switch statistics...
Page 135
Traffic management 135 traffic management the corebuilder 7000 family atm switch provides several traffic management services for handling congestion including: frame discard capability efci frame discard capability the corebuilder 7000 atm switch can discard cells at the frame (aal protocol data un...
Page 136
136 c hapter 6: atm s witching the efci bit in the payload type identifier (pti) field in the cell header is set when congestion is encountered. The efci bit is set based on one of the following defined output queue levels: 20% full, 50% full, 80% full. These output queue levels can be configured on...
Page 137: Lan E
7 lan e mulation v ersions 1.0 and 2.0 this chapter provides a general overview of lan emulation including the following topics: lan emulation overview emulated lan components emulated lan connections operation of the lan emulation lan emulation in the corebuilder 7000 lan emulation redundancy lane ...
Page 138
138 c hapter 7: lan e mulation v ersions 1.0 and 2.0 stacks (i.E. Appn, net bios, ipx, appletalk, etc.) as if they were running over a traditional lan. Since the protocol stacks are communicating with the mac driver (in layer 2), lane services has to offer the same mac driver service primitives, thu...
Page 139
Emulated lan components 139 figure 44 luni interface in relation to lane clients and services lan emulation client (lec) the lan emulation client (lec) performs data forwarding and address resolution, provides a mac level emulated ethernet service interface to higher level software, and implements t...
Page 140
140 c hapter 7: lan e mulation v ersions 1.0 and 2.0 lan emulation server (les) the lan emulation server (les) coordinates and controls an elan. It provides the central “directory” service of an elan to which a lec can turn to look up the atm address of another lec. The les directory contains a tabl...
Page 141
Emulated lan connections 141 configuring lane into your network lane can be configured in an atm network in several ways: to connect legacy end stations directly to other legacy systems, as well as to servers, routers, switches and other networking devices attached to the atm network. To connect bri...
Page 142
142 c hapter 7: lan e mulation v ersions 1.0 and 2.0 data vccs data vccs carry data frames between lecs and between a lec and the bus. Unicast data is normally sent from one lec to another lec by data-direct vccs. Data direct vccs are set up dynamically in a svc environment by a transmitting lec aft...
Page 143
Emulated lan connections 143 figure 46 vccs in lan emulation components frame ordering there are two paths for unicast frames between a sending lan emulation client and a receiving client: one via the bus and one via a data direct vcc between them. For a given lan destination, a sending client is ex...
Page 144
144 c hapter 7: lan e mulation v ersions 1.0 and 2.0 figure 47 the flush protocol operation of the lan emulation the following functions are performed by the lan emulation. The lan emulation clients (lec) and the lan emulation servers interact by way of a well-defined interface (luni). Connecting a ...
Page 145
Operation of the lan emulation 145 the establishment of a connection to the bus by the lan emulation client. The lecs connect and configuration phases may be bypassed for certain applications. The registration phase may also be bypassed if the lec performs required address registration during the jo...
Page 146
146 c hapter 7: lan e mulation v ersions 1.0 and 2.0 register all lan destinations for which it is responsible, or join as a proxy to other mac addresses. Address resolution address resolution is the procedure by which a lec associates a lan destination with the atm address of another lec or the bus...
Page 147
Lan emulation in the corebuilder 7000 147 . Updating elan parameters these elan parameters can be displayed and updated by management. Parallel commands exist for this purpose in both the lecs command set (see “update elan parameters in lecs database” on page 293 in the management guide) and in the ...
Page 148
148 c hapter 7: lan e mulation v ersions 1.0 and 2.0 standard addressing protocol. This is discussed in more detail in the next section. When the connection of lec to lecs is established, the lecs identifies an appropriate les using the search policies discussed below and transfers the les address t...
Page 149
Lan emulation in the corebuilder 7000 149 the atm address of the les with which it wishes to communicate over an elan the mac address of the les with which it wishes to communicate over an elan the elan name of the elan it wishes to join accordingly, there are three possible ways (search policies) t...
Page 150
150 c hapter 7: lan e mulation v ersions 1.0 and 2.0 figure 50 les and bus connections address resolution when a lec needs to forward a unicast data frame whose lan destination is not found in its local forwarding data base it attempts to locate a lec that represents the lan destination on the atm n...
Page 151
Lan emulation in the corebuilder 7000 151 destination in its fdb arp-cache. The way the les handles le_arp requests can be configured by management (see “configuring les le_arp policies” on page 151). Data-direct vcc on receipt of the destination lec address, the transmitting lec establishes a data-...
Page 152
152 c hapter 7: lan e mulation v ersions 1.0 and 2.0 . Le_arp response policy for route descriptors this is an additional policy for responding to le_arp requests when the specified elan is a token ring elan and when the lan destination is a route descriptor. This policy is used in conjunction with ...
Page 153
Lan emulation redundancy 153 lan emulation redundancy this section describes the concepts and planning of redundant lan emulation services and is relevant to networks that have more than one corebuilder 7000 family atm switch installed. The following topics are included: lane services in the corebui...
Page 154
154 c hapter 7: lan e mulation v ersions 1.0 and 2.0 lane services in the corebuilder 7000 family atm switch card as discussed in previous sections, the lan emulation services provided by a corebuilder 7000 family atm switch card are: lan emulation configuration server (lecs) — each corebuilder 7000...
Page 155
Lan emulation redundancy 155 established as the active lecs by associating its address with the “well-known” address. Then, a lec attempting to establish a connection to the lecs via the well-known address is redirected to establish a connection to the newly-activated lecs. Multiple active lecs in a...
Page 156
156 c hapter 7: lan e mulation v ersions 1.0 and 2.0 about the less associated with each elan and can take over as the active lecs at any time. Lma commands to enter the primary les by lma, see “add elan” on page 301 in the management guide; to enter a secondary les, see “assign redundant les to ela...
Page 157
Lan emulation redundancy 157 figure 51 atm connections between lecs and les if the primary les for an elan is marked operational, the lecs assigns it as the active les and the secondary as the redundant les, otherwise the secondary les is assigned as active. If both primary and secondary leses are n...
Page 158
158 c hapter 7: lan e mulation v ersions 1.0 and 2.0 : the lecs has determined that the primary les, les 1, is operational by connecting to it and has assigned it to be the active les in the elan. The connection has reported 20 lecs attached. Failure recovery - transferring control to the redundant ...
Page 159
Lan emulation redundancy 159 same secondary les to replace a failed active primary les and the topology databases remain the same. The split elan is an exception; it is discussed in the next section. If neither primary nor secondary les can be made active, an error message is issued to a lec wheneve...
Page 160
160 c hapter 7: lan e mulation v ersions 1.0 and 2.0 you verify if the lecs-based lane redundancy mode is enabled through the lma (see “display le service redundancy” on page 263 in the management guide). Lane redundancy start-up delay the lane redundancy mechanism does not begin operating at system...
Page 161
Lane security 161 if possible, the primary lecs should not be configured on a switch with primary less. Do not clump too many primary less on a single switch. Distribute less across the backbone there is an important pre-condition for lane redundancy to operate correctly. Under some circumstances, s...
Page 162
162 c hapter 7: lan e mulation v ersions 1.0 and 2.0 security check — you can run a security check on an individual lec to if it is authorized for an elan. Lma — the security feature is completely managed by the lma. Statistics — you can display the number of attempted lec connections that were reje...
Page 163
Lane security 163 have the join privilege, the les prevents the lec from joining the elan by sending it an access_denied response code. Best match verification—admitting individual lecs in a group the entry in an elan security table with the best (longest) match with a candidate lec address determin...
Page 164
164 c hapter 7: lan e mulation v ersions 1.0 and 2.0 lec 3 and lec 4 are rejected because there is no match in the table, and the elan default join privilege is reject. Security algorithm the algorithm for allowing a lec to join an elan is shown in figure 52: figure 52 lec admission algorithm factor...
Page 165
Lane security 165 all security tables are empty. Thus, if the switch has the factory default configuration, all lecs can join all elans. Lma security commands this section presents an overview of the lma lane security commands (see “lec not in elan security list” on page 356 in the management guide“...
Page 166
166 c hapter 7: lan e mulation v ersions 1.0 and 2.0 restore security configuration this operation restores the security configuration from the flash. It can also be used as an “undo” operation for any changes that were not saved to the flash (see “restore security configuration” on page 370 in the ...
Page 167
Lane version 2.0 167 multi protocol over atm (mpoa) the main objective of mpoa is to provide a method of allowing inter-subnet (or inter-elan) communication without requiring that every packet suffer the latency and delay that can be induced by a layer three router. The two device types mps (mpoa se...
Page 168
168 c hapter 7: lan e mulation v ersions 1.0 and 2.0 selective multicast groups lane version 2.0 has the ability to have multiple multicast groups on a particular elan. In lane 1.0 there is only a single bus which is used for the transmission of all broadcast, unknown and multicast traffic. Every le...
Page 169
Lane version 2.0 169 traffic for each elan, the direct data vc s encapsulate each packet with an llc header that includes the elan id for each packet. This feature requires new frame encapsulation format to be used by lane 2.0 that was not used in lane 1.0. This feature has a special tlv in register...
Page 170
170 c hapter 7: lan e mulation v ersions 1.0 and 2.0 figure 54 lane lcc multiplexed data frame format (lane 2.0 only) backward compatibility and mixture of lecs of both lane versions 1.0 and 2.0 lecs with lane version1 and lane version 2 can exist in the same elan. The lec with lane version 1.0 will...
Page 171
Mpoa devices configuration 171 mpoa devices configuration the switch allows configuration of mpoa entities: mps and mpc. The configuration is general so that all mpss and mpcs that request configuration receive the same parameters. Display current mps configuration displays all the current settings ...
Page 172
172 c hapter 7: lan e mulation v ersions 1.0 and 2.0 mpoa server configuration parameters . Set keep-alive time sets the mps-p1 keep-alive time parameter. Command actions command result set keep-alive lifetime sets the mps-p2 keep-alive lifetime parameter. Table 43 mpoa server configuration paramete...
Page 173
Mpoa devices configuration 173 command actions command result set internetwork layer protocols sets the mps-p3 protocols parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (1) mps: mpoa server configuration (3) mp2: set keep-alive lifetime enter a parameter at...
Page 174
174 c hapter 7: lan e mulation v ersions 1.0 and 2.0 command actions command result set initial retry time sets the mps-p4 initial retry time parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (1) mps: mpoa server configuration (4) mp3: set internetwork-layer ...
Page 175
Mpoa devices configuration 175 command actions command result set retry time maximum sets the mps-p5 retry time maximum parameter. Command actions command result set give up time sets the mps-p6 give-up time parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (...
Page 176
176 c hapter 7: lan e mulation v ersions 1.0 and 2.0 command actions command result set default holding time sets the mps-p7 default holding time parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (1) mps: mpoa server configuration (7) mp6: set give-up time en...
Page 177
Mpoa devices configuration 177 command actions command result display current mpc configuration displays all the current settings of the mpc variables. Command actions command result example enter: 2 5 2 1 the following information is displayed: enter menu sequence: (2) lem: lan emulation (5) mpa: m...
Page 178
178 c hapter 7: lan e mulation v ersions 1.0 and 2.0 mpoa client configuration parameters . Set shortcut setup frame count sets the mpc-p1 shortcut-setup frame count parameter. Mpoa client configuration ------------------------- mpc-p1 shortcut-setup frame count: 10 (a number) mpc-p2 shortcut-setup ...
Page 179
Mpoa devices configuration 179 command actions command result set shortcut setup frame time sets the mpc-p2 shortcut-setup frame time parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (2) mpc: mpoa client configuration (2) mp1: set shortcut-setup frame count ...
Page 180
180 c hapter 7: lan e mulation v ersions 1.0 and 2.0 command actions command result set flow detection protocols sets the mpc-p3 flow detection protocols parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (2) mpc: mpoa client configuration (3) mp2: set shortcu...
Page 181
Mpoa devices configuration 181 command actions command result set initial retry time sets the mpc-p4 initial retry time parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (2) mpc: mpoa client configuration (4) mp3: set flow detection protocols enter a paramete...
Page 182
182 c hapter 7: lan e mulation v ersions 1.0 and 2.0 command actions command result set retry time maximum sets the mpc-p5 retry time maximum parameter. Command actions command result set hold down time sets the mps-p6 hold down time parameter. Enter menu sequence: (2) lem: lan emulation (5) mpa: mp...
Page 183
Mpoa devices configuration 183 command actions command result enter menu sequence: (2) lem: lan emulation (5) mpa: mpoa devices configuration (2) mpc: mpoa client configuration (7) mp6: set hold down time enter a parameter at the prompt parameter format or range hold down time 30 - 1200 (seconds) di...
Page 184
184 c hapter 7: lan e mulation v ersions 1.0 and 2.0
Page 185: Irtual
8 v irtual n etworks this chapter discusses virtual networks and their implementation in the corebuilder ® 7000 family atm switch. The following topics are discussed: virtual lan basics vlans in the corebuilder 7000 virtual lans for three workgroups virtual lan basics just as an ethernet lan enables...
Page 186
186 c hapter 8: v irtual n etworks or removed from virtual lans by software without regard to their location; there is no need to change physical connections. The organization of the network into vlans also reduces congestion from broadcast frame transmissions. Broadcast frames are now sent only to ...
Page 187
Vlans in the corebuilder 7000 187 vlans in the corebuilder 7000 a vlan in the corebuilder 7000 family atm switch is defined simply as an emulated lan together with all ethernet segments and servers attached to it. The ethernet segments are represented in the elan by lecs. Figure 55 shows a diagram o...
Page 188
188 c hapter 8: v irtual n etworks ethernet, token ring, fddi and vlt (virtual lan trunk) so that vlans can include these types of lans. Through the integrated fast setup facility of the corebuilder 7000 family atm switch, vlans can be set up “chassis-wide”. Each port of each interface card installe...
Page 189
Vlans in the corebuilder 7000 189 vlans in a corebuilder 7600 card as an example, this section discusses how vlans are defined in the corebuilder 7600 fast ethernet interface card of the corebuilder 7000 family atm switch. Connecting ethernet segments to a vlan a vlan will usually contain some local...
Page 190
190 c hapter 8: v irtual n etworks . Figure 56 vlan connectivity through 7600 cards 7600 card 1 switch card 7600 card 2 bridge 1 bridge ports: 1 2 3 1 2 bridge 2 le client 1 (elan 1) le client 1 (elan 2) le client 2 (elan 1) le client 2 (elan 2) bridge 1 bridge 2 fast ethernet ports: 1 2 3 4 5 lans:...
Page 191
Vlans in the corebuilder 7000 191 figure 57 shows a different way of viewing the relation between elan and vlan. The vlan is based on the elan. Figure 57 elan-based virtual lan cb7600 modules marketing marketing virtual lan em ulated lan cb7600 modules lec2 lec3 les2 bus2 7000 chassis corebuilder co...
Page 192
192 c hapter 8: v irtual n etworks virtual lans for three workgroups figure 58 shows a network divided into three vlans: marketing, finance, and administration. Even though these workgroups are distributed over different floors, lan emulation allows them to be managed as if the users were in the sam...
Page 193: Evice
9 d evice m anagement this chapter explains how to access the corebuilder ® 7000 family atm switch for administration and management. The following topics are discussed in this chapter: n overview n local management application (lma) n snmp agent n chassis management — single ip n ethernet encapsula...
Page 194
194 c hapter 9: d evice m anagement n viewing the event log communication methods local management can operate via a terminal, workstation or pc running a terminal emulation program, and can use the following communication resources (see figure 59): n rs-232 serial link. N rs-232 serial link + modem...
Page 195
Snmp agent 195 snmp agent simple network management protocol (snmp) is a standard management protocol for multi-vendor ip networks. Each corebuilder 7000 family atm switch has one snmp agent that monitors objects on the switch and may report data to one or more network management systems. Management...
Page 196
196 c hapter 9: d evice m anagement managing by snmp you can manage the corebuilder 7000 family atm switch via snmp-based external network management applications running on a workstation (see figure 60). The 3com transcend © enterprise manager is the recommended graphical user interface tool for ce...
Page 197
Chassis management — single ip 197 security snmp security is currently provided through configurable community strings, one for read and one for write. The default community strings are: n read—“public” n write—“private” figure 60 snmp manager (transcend atm manager) chassis management — single ip t...
Page 198
198 c hapter 9: d evice m anagement a single ip supports the chassis-wide activities: n snmp via single ip n master/subagent architecture n integrative display for chassis in transcend tem 5.0 n tftp upload/download via single ip n unified software download for all installed cards n configuration up...
Page 199
Chassis management — single ip 199 100 elan9302_0 159 1516 9702400 47 00 00 00 00 00 3c 00 00 a0 00 00 00 00 c0 da 60 24 56 00 16 resident elans 101 elan9302_1 159 1516 9702400 47 00 00 00 00 00 3c 00 00 a0 00 00 00 00 c0 da 60 24 56 01 115 elan9302_15 159 1516 9702400 47 00 00 00 00 00 3c 00 00 a0 ...
Page 200
200 c hapter 9: d evice m anagement in addition, if you are working in the single-ip mode, you can reset the corebuilder 7x00 cards via the ncd chassis private mib in the ncdchassphysmoduletable table compatibility with previous versions the single-ip feature of version 4.0 is supported by version 5...
Page 201
Chassis management — single ip 201 rmon history as another example of chassis management via single-ip, you can use the transcend tm lan sentry tm facility to request rmon history ethernet flow statistics for the entire corebuilder 7000 chassis via the rmon mib in the corebuilder 7000 switch card an...
Page 202
202 c hapter 9: d evice m anagement n short sampling types of statistics you can request the following types of statistics for a port: n dropevents — the total number of events in which packets were dropped. N octets — the total number of octets of data received on the network interface. N packets —...
Page 203
Chassis management — single ip 203 n the port of the installed card whose statistics you want to view—in this case one of the fast ethernet ports of an installed corebuilder 7600 fast ethernet interface card n the type of statistics you want to view n the sampling rate figure 61 rmon history selecto...
Page 204
204 c hapter 9: d evice m anagement figure 62 rmon history of bytes sent ethernet encapsulation type as mentioned previously, the ethernet port on the front panel of the switch module is provided for the management of the corebuilder 7000 family atm switch either by local management via telnet or by...
Page 205
Service console 205 configure the corebuilder 7000 family atm switch to accept the encapsulation type being sent to it by the managing device. To perform this setup, use the system management setup menu (see “update ethernet encapsulation type” on page 83 in the management guide). Service console th...
Page 206
206 c hapter 9: d evice m anagement.
Page 207: Witch
10 s witch r edundancy this chapter covers the following topics: switch redundancy overview system requirements summary of improved switch redundancy features in version 4.5 version 4.5 features up to version 4.0 features switch redundancy overview a redundant switching module is a backup switching ...
Page 208
208 c hapter 10: s witch r edundancy pvc robustness, i.E., pvc connections are not lost during the switch-over. Single cells are lost. A switch is ready to re-establish svc connections after no more than 7 seconds. Manual database configuration is not required. Full configuration stored in the activ...
Page 209
System requirements 209 for proper functioning of switch redundancy in both base and enhanced modes, both switch engines must be hd (5 gbps) running the same software version 4.50; rev-c cannot be the redundant switch of an hd. System requirements hardware and software requirements for migration to ...
Page 210
210 c hapter 10: s witch r edundancy if one of the 4-port modules or the 7200 modules is installed in the corebuilder 7000 chassis, then the corebuilder 7000hd switch will only work with a maximum capacity of 2.5 gbps. Version 4.5 features identifying the active switching module during power up, bot...
Page 211
Version 4.5 features 211 protocol stack a udp/ip protocol stack is implemented as a simulated ethernet network over the communication channel described above. The small size of the messages transmitted necessitates fragmentation and reassembly. Fragmentation is performed on a full ethernet frame pri...
Page 212
212 c hapter 10: s witch r edundancy switch redundancy limitations hot removal of the active switching module from the chassis is not permitted. Switch-over will not occur in such a case. The switch card may be removed only when it is in redundant mode. Interface card hot insertion/extraction is all...
Page 213
Up to version 4.0 features 213 switch-over phases switch-over is carried out in three phases: resetting and uploading the software to the 4-port and 8-port modules. Initializing 4-port and 8-port modules. Resetting and initializing the 7x modules. During the switch-over, the redundant switching modu...
Page 214
214 c hapter 10: s witch r edundancy manual configuration of the redundant switch parameters listed in the table above must be done on a corebuilder 7000 other than the active one. Only upon configuration completion can the redundant switch be utilized in the active corebuilder 7000. Information bas...
Page 215
Up to version 4.0 features 215 publishing the new mac address a redundant switch that has become active sends a reverse arp (rarp) to publish its mac address to the network devices. For devices that do not learn mac addresses from a rarp, you will need to reset the ip address entry of the corebuilde...
Page 216
216 c hapter 10: s witch r edundancy switch-over example in corebuilder 7000 assume a corebuilder 7000 consisting of two switching modules as shown in figure 63. Figure 63 corebuilder 7000 with two switching modules (a - active, b- redundant) the lane parameters are evaluated by the active switch an...
Page 217: Echnical
A t echnical s upport 3com provides easy access to technical support information through a variety of services. This appendix describes these services. Information contained in this appendix is correct at time of publication. For the most recent information, 3com recommends that you access the 3com ...
Page 218
218 a ppendix a: t echnical s upport 3com ftp site download drivers, patches, software, and mibs across the internet from the 3com public ftp site. This service is available 24 hours a day, 7 days a week. To connect to the 3com ftp site, enter the following information into your ftp client: hostname...
Page 219
Support from your network supplier 219 access by digital modem isdn users can dial in to the 3com bbs using a digital modem for fast access up to 64 kbps. To access the 3com bbs using isdn, call the following number: 1 847 262 6000 3com facts automated fax service the 3com facts automated fax servic...
Page 220
220 a ppendix a: t echnical s upport when you contact 3com for assistance, have the following information ready: product model name, part number, and serial number a list of system hardware and software, including revision levels diagnostic error messages details about recent configuration changes, ...
Page 221
Returning products for repair 221 returning products for repair before you send a product directly to 3com for repair, you must first obtain an authorization number. Products sent to 3com without authorization numbers will be returned to the sender unopened, at the sender’s expense. To obtain an aut...
Page 222
222 a ppendix a: t echnical s upport.
Page 223: Rotocols
B p rotocols and i nterfaces this appendix provides you with basic concepts and information about interfaces and management protocols used in the atm system including the following topics: physical layer atm layer operation & maintenance (oam) atm adaptation layer (aal) physical layer traditionally,...
Page 224
224 a ppendix b: p rotocols and i nterfaces cell delineation: this function permits the identification of cell boundaries in the payload. It uses the header error control (hec) field in the cell header. Path signal identification: an integrity check is performed on the end-to-end signal. Cell mappin...
Page 225
Physical layer 225 cell scrambling: provides a solution to bit patterns in the atm cell payload (much like in the sonet). Cell scrambling can be enabled or disabled. Plcp framing and cell delineation: mapping of atm cells into the ds-3 is accomplished by inserting the 53 bytes of atm cells into the ...
Page 226
226 a ppendix b: p rotocols and i nterfaces atm layer atm cell structure the atm cell is 48 bytes of payload and 5 bytes of header, information totaling 53 bytes. The header contains enough information to allow the network to forward each cell to its proper destination. The cell header also provides...
Page 227
Atm layer 227 the atm cell header consists of the following fields : the atm layer atm is based on a layered architecture. In the protocol stack, the atm layer sits directly above the physical layer. Many physical layers can be specified, including several for 100 to 155 mbps. In the protocol hierar...
Page 228
228 a ppendix b: p rotocols and i nterfaces this layer does not retransmit lost or corrupted information. The atm layer also provides the capability to indicate the loss priority of the data carried in each cell (clp). The atm layer relies on the physical layer to provide for the transport of atm ce...
Page 229
Operation & maintenance (oam) 229 operation & maintenance (oam) the operation and maintenance (oam) functions associated with the 155 mbps uni provide for transmission and reception of maintenance and low level link performance monitoring between atm devices. The functions of the oam are handled at ...
Page 230
230 a ppendix b: p rotocols and i nterfaces uni while pt 101 is used to identify the connection between user end stations. End-to-end oam cells are passed by all intermediate nodes. The nodes in the path may monitor these cells. They can only be removed by the endpoint of the vpc (f4 flow) or vcc (f...
Page 231
Atm adaptation layer (aal) 231 atm adaptation layer (aal) atm adaptation layers (aals) define how to deal with the contents of cells. The aal performs segmentation and reassembly (sar) on cells. It formats data into the 48-byte atm cell payload, in effect adapting applications to the cell-based atm ...
Page 232
232 a ppendix b: p rotocols and i nterfaces errors. It is padded to align to 48 bytes (see figure 68). To indicate frame boundaries and determine when to reassemble and when to stop reassembling, the space bit for payload type (pt) in the cell header is zero except for the last cell in the packet (w...
Page 233
Atm adaptation layer (aal) 233 figure 67 service classes and aal types figure 68 aal5 frame format figure 69 segmentation — converting an atm frame to cells.
Page 234
234 a ppendix b: p rotocols and i nterfaces.
Page 235: Ore
C c ore b uilder ® 7000 f amily atm s witch s pecifications physical dimensions height: 38.8 cm (15.3 in) width: 3.81 cm (1.5 in) depth: 32.7 cm (12.8 in) weight: 1.7 kg (3.74 lb) environmental requirements operating temperature 0° to 40° c (32° to 104° f) operating humidity 10 to 90% relative humid...
Page 236
236 a ppendix c: c ore b uilder ® 7000 f amily atm s witch s pecifications power supply ac line frequency 47 to 63 hz input voltage options 110/220 volt auto selectable current rating 5/2.8 amps typical redundancy (optional) dual power supplies standards supported snmp mib ii (rfc 1213) atom mib (rf...
Page 237
237 corebuilder management and interface leds switch module pwr - power indication (green) fail - module fail indication (red) act - activity, module active and running (yellow) 10base-t status - ethernet port status (green) service port status - rs-232 (green) control port status - rs-232 (green) i...
Page 238
238 a ppendix c: c ore b uilder ® 7000 f amily atm s witch s pecifications.
Page 239: Afety
D s afety i nformation this appendix contains safety information about the corebuilder ® 7000 family atm switch, including: guidelines for avoiding bodily harm guidelines for avoiding equipment damage guidelines for avoiding bodily harm to avoid bodily harm as well as possible damage to your corebui...
Page 240
240 a ppendix d: s afety i nformation 3com recommends that you do not look into the laser while it is powered on, either by the naked eye or through any magnifying device. Class 1 laser products include atm single mode interface (oc-3, oc12) 8-port board atm interface module 4-port board atm interfa...
Page 241
Schäden am gerät 241 when handling replacement parts, 3com recommends that you always use a wrist strap connected to a proper ground. This helps prevent the part from being damaged by electrostatic discharge. Additionally, when not in use, the module should be stored in an antistatic bag. Cover ever...
Page 242
242 a ppendix d: s afety i nformation.
Page 243: Lossary
G lossary a abr available bit rate. An atm layer service category for which the limiting atm layer transfer characteristics provided by the network may change subsequent to connection establishment. Address prefix a string of 0 or more bits up to a maximum of 152 bits that is the lead portion of one...
Page 244
244 g lossary atm asynchronous transfer mode. A transfer method used for lan and wan. Atm carries voice, video, and data at speeds up to 2.2 gbps and can integrate geographically distant disparate networks. Also called cell relay. Atm adaptation layer (aal) a set of protocols that translate user tra...
Page 245
G lossary 245 c call an association between two or more users or between a user and a network entity that is established by the use of network capabilities. This association may have zero or more connections. Cell an atm layer protocol data unit (pdu) characterized by fixed, rather than variable, le...
Page 246
246 g lossary connection- oriented communications a form of packet-switching that requires a predefined circuit from source to destination to be established before data can be transferred. Crankback a mechanism used by atm networks when a connection setup request is blocked. The path is rolled back ...
Page 247
G lossary 247 quality of service class makes use of explicit forward congestion indication. Ethernet a csma/cd, 10 mbps, local area data network, developed by xerox corporation. It is one of the most popular baseband lans in use. Elan name the name assigned an elan (emulated local area network). Esi...
Page 248
248 g lossary ieee 802.3 ieee standard for ethernet local area networks. Ieee 802.1d ieee standard for bridging. Ifc communications interface card communications is the communications protocol between the switch card and the installed interface cards. In-band transmission of auxiliary information, e...
Page 249
G lossary 249 lec id lan emulation client identifier: this identifier, contained in the lan emulation header, indicates the id of the atm host or atm-lan bridge. It is unique for every atm client. Lecs lan emulation configuration server. This is the set of functions that provides an edge device with...
Page 250
250 g lossary luni lan emulation user to network interface. The standardized interface between a le client and a le server (les, lecs and bus). M maxcr maximum cell rate. This is the maximum capacity usable by connections belonging to the specified service category. Mib management information base. ...
Page 251
G lossary 251 operation and maintenance cell (oam) a cell that contains atm lm information. It does not form part of the upper layer information transfer. Out-of-band transmission of auxiliary information e.G., management messages, over a medium other than that used by the system users. P peer group...
Page 252
252 g lossary qos (quality of service) quality of service is defined on an end-to-end basis in terms of the following attributes of the end-end-to-end atm connection: cell loss ration, cell transfer delay and cell delay variation. Quality of service (qos) metrics parameters that are defined by the n...
Page 253
G lossary 253 summary address an address prefix that tells a node how to summarize reachability information. Superstack ii switch 2700 3com ethernet-to-atm switch used to connect ethernet network devices to each other and to an atm backbone. Svc switched virtual connection. A standard signaling prot...
Page 254
254 g lossary experienced by a ubr connection, or as to the cell transfer delay experienced by cells on the connection. Uni user-network interface. An interface point between atm end users and a private atm switch, or between a private atm switch and the public carrier atm network defined by physica...
Page 255: Ndex
I ndex 255 i ndex numbers 3com bulletin board service (3com bbs) 218 3com knowledgebase web services 217 3com transcend manager 196 3com url 217 3comfacts 219 a aal, see atm adaptation layer abr, see available bit rate ac line frequency 236 ac protection 235 access methods snmp 196 access to service...
Page 256
256 i ndex establishing at uni 38 atm edge device lec in 139 atm interface management entity, see ime atm layer atm cells 228 functions 228 in protocol stack 227 loss priority 228 multiplexing 228 oam cells 228 traffic management 228 atm network alternate routes in 63 classical ip 24 connecting brid...
Page 257
I ndex 257 database synchronization 79 default elan join privilege 162 elan parameters 146 virtual lan 188 designated transit list (dtl) 86 documentation comments 18 related 16 dommage causé à l'équipement 241 dommages corporels 240 downloading software files from active to redundant switch 208 ds-3...
Page 258
258 i ndex network 35 interim local management interface, see ilmi ip address 214 j jitter 68 k körperliche schäden 240 l lan emulation address resolution 146 address resolution protocol 152 atm network 27 broadcast frames 152 components see le components configuring into atm network 141 connection ...
Page 259
I ndex 259 m mac address 214, 216 publishing new 215 mac driver interfaces in atm stations 137 management connectors 237 overview 193 management information base, see mib manual configuration 50 manual discovery 47 member id 40 message conversion between signaling protocols 122 mib browsing 198 snmp...
Page 260
260 i ndex priority output queues 136 private network to network interface, see pnni protocol flush 143 stack 211 standard addressing 148 ptse, see pnni topology state element (ptse) public uni ds-3 physical layer interface 224 pvc 100 abr cbr connections 208 nrt-vbr 124 rt-vbr ubr q q.2931 watchdog...
Page 261
I ndex 261 setup signaling message 106 shared les 156 signaling 104 aal 114 messages 105 protocol 105 qos parameters 121 sscop message set 114 timers 111 uni version 49 signaling message add party 107 call-proceeding 106 connect 107 sequence 109 setup 106 signaling protocol profile 107 signaling pro...
Page 262
262 i ndex paths 143 unknown frames 152 unspecified bit rate (ubr) 125 url 217 user network interface, see uni v variable bit rate service category 117 vbr, see variable bit rate vccs control 141 control direct 149 control distribute 149 data 141, 142 data direct 151 multicast forward 149 point-to-p...
Page 263
3com corporation l imited w arranty the duration of the warranty for the corebuilder 7000/7000hd chassis and switch engine is: enhanced one-year limited -— return to factory for free repair. One year warranty with 90 days of advance hardware replacement service, subject to availability. The duration...
Page 264
(doa) and a replacement shall be provided by advance replacement. The replacement product will normally be shipped not later than three (3) business days after 3com’s verification of the doa product, but may be delayed due to export or import procedures. When an advance replacement is provided and c...