- DL manuals
- 3Com
- Switch
- LANPLEX 2500
- Operation Manual
3Com LANPLEX 2500 Operation Manual
Summary of LANPLEX 2500
Page 1
® lan plex ® 2500 o peration g uide part no. 801-00344-000 published november 1996 revision 03.
Page 2
Ii 3com corporation ■ 5400 bayfront plaza ■ santa clara, california ■ 95052-8145 © 3com corporation, 1996. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without...
Page 3: Ontents
C ontents a bout t his g uide introduction 1 how to use this guide 1 conventions 2 lanplex 2500 documentation 4 documentation feedback 5 p art i m anagement and a dministration 1 lan plex ® m anagement and a dministration o verview about the lanplex® 2500 system 1-1 user interfaces and the lanplex® ...
Page 4: : P
4 p hysical a ccess : p orts and c abling in-band and out-of-band management 4-2 management access 4-2 serial ports 4-2 ethernet and fddi ports 4-3 p art ii b ridging t echnology 5 t ransparent b ridging about transparent bridging 5-1 what makes a bridge 802.1d compliant? 5-1 how a bridge learns add...
Page 5: Lan
7 u ser - defined p acket f iltering about user-defined packet filtering 7-1 designing a packet filter 7-1 assigning packet filters to paths 7-2 packet filter examples 7-3 example 1: isolating ip segments 7-4 example 2: filtering appletalk phase ii packets 7-6 using address groups and port groups in...
Page 6: Fddi N
10 fddi n etworks about fddi networks 10-1 fddi network topologies 10-2 physical topology: a ring of trees 10-3 logical topology: the dual ring 10-4 fddi connection rules 10-4 dual homing 10-6 p art iv atm t echnology 11 atm n etworks about atm 11-1 atm basics 11-2 atm network interfaces 11-2 atm ce...
Page 7: Art
P art v a ppendixes a snmp mib s upport snmp mibs a-1 snmp mib compilers a-4 b t echnical s upport online technical services b-1 3com bulletin board service b-1 access by analog modem b-1 access by digital modem b-2 world wide web site b-2 3comforum on compuserve® online service b-2 3comfactssm auto...
Page 8: Bout
A bout t his g uide introduction this lanplex® 2500 operation guide provides all the information you need to understand how your lanplex® switching hub works in fddi, ethernet, and atm networking environments. Audience this guide is intended for the system or network administrator who is responsible...
Page 9
2 a bout t his g uide conventions table 2 and table 3 list conventions that are used throughout this guide. Asynchronous transfer mode (atm) technology chapter 11 snmp mib support appendix a 3com technical support appendix b definitions for operating the system glossary table 1 locating information ...
Page 10
Conventions 3 table 3 text conventions convention description “enter” vs. “type” the word “enter” means type something, and then press the return or enter key. Do not press the return or enter key when an instruction simply says “type.” “syntax” vs. “command” the word “syntax” indicates that the gen...
Page 11: Lanplex 2500
4 a bout t his g uide lanplex 2500 documentation the following documents comprise the lanplex 2500 documentation set. If you want to order additional documents or one that you do not have, contact your sales representative for assistance. ■ lanplex® 2500/2016 unpacking instructions describes how to ...
Page 12
Documentation feedback 5 ■ lanplex® 2500 intelligent switching administration console command quick reference contains administration console intelligent switching commands for the lanplex system. (folding card; shipped with your system/part no. 801-000318-000) ■ lanplex® 2500 extended switching adm...
Page 13: Anagement
I chapter 1 management and administration overview chapter 2 user access: what you see chapter 3 management access: protocols chapter 4 physical access: ports and cabling m anagement and a dministration.
Page 15: Lan
1 lan plex ® m anagement and a dministration o verview this chapter introduces you to how your lanplex® system is managed and administered. About the lanplex® 2500 system the lanplex 2500 system combines high port density, ethernet switching, ethernet-to-fddi bridging, fast ethernet switching, fddi ...
Page 16
1-2 c hapter 1: lan plex ® m anagement and a dministration o verview figure 1-1 osi reference model using the lanplex system’s own management application or an external snmp- based management application, the system can be managed and administered through various protocols and physical interfaces. U...
Page 17
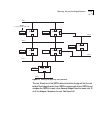
User interfaces and the lanplex® 2500 system 1-3 figure 1-2 user interfaces and protocols used to access the lanplex system application layer transport layer network layer data-link & physical layers snmp managers snmp tcp administration console application udp ethernet fddi smt tcp udp telnet, rlog...
Page 18
1-4 c hapter 1: lan plex ® m anagement and a dministration o verview.
Page 19: Ser
2 u ser a ccess : w hat y ou s ee this chapter describes the applications you can use to gain access to your lanplex system and to perform administrative and management functions. About the user interfaces to the lanplex® 2500 you can use the following applications as the user interface to your lanp...
Page 20
2-2 c hapter 2: u ser a ccess : w hat y ou s ee figure 2-1 user interfaces for the lanplex system application layer transport layer network layer data-link & physical layers snmp tcp udp fddi smt tcp udp telnet, rlogin, ftp snmp/smt proxy agent snmp agent ip serial line serial line fddi smt telnet, ...
Page 21
The built-in lanplex® administration console 2-3 the built-in lanplex® administration console you can use the administration console to configure your lanplex system to operate effectively in your networking environment. You can also use the administration console to display network statistics. You ...
Page 22
2-4 c hapter 2: u ser a ccess : w hat y ou s ee external network management applications 3com’s transcend® enterprise manager is a network management software family suite that runs on unix and ms-dos platforms. It provides network management for a wide range of 3com products, including the lanplex ...
Page 23
External network management applications 2-5 figure 2-4 sample screen from transcend® enterprise manager status view software because the lanplex system is based on snmp standards, you can manage your system using third-party snmp-based network manager applications, such as sun microsystems sunnet m...
Page 24: Anagement
3 m anagement a ccess : p rotocols this chapter describes the underlying communication and management protocols used to deliver management and administration data to and from your lanplex system. About lanplex® 2500 protocols the lanplex 2500 system uses the following protocols: ■ virtual terminal p...
Page 25
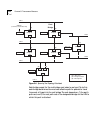
3-2 c hapter 3: m anagement a ccess : p rotocols figure 3-1 protocol stacks for the lanplex® system application layer transport layer network layer data-link & physical layers ethernet fddi smt serial line serial line ethernet fddi smt snmp managers administration console application administration ...
Page 26
Virtual terminal protocols 3-3 virtual terminal protocols a virtual terminal protocol is a software program, such as rlogin or telnet, that allows you to establish a management session from a pc or a unix workstation. Because rlogin and telnet run over tcp/ip, you must have at least one ip address c...
Page 27
3-4 c hapter 3: m anagement a ccess : p rotocols snmp simple network management protocol (snmp) is the standard management protocol for multivendor ip networks. Snmp supports transaction-based queries that allow the protocol to format messages and to transmit information between reporting devices an...
Page 28
Snmp 3-5 snmp traps an snmp trap is an asynchronous report of one of several events. To receive reports, you must configure the ip address of the network management station (nms) to which the reports are sent; otherwise, the reports are discarded. Through snmp and your network management software or...
Page 29
3-6 c hapter 3: m anagement a ccess : p rotocols access control access to system information through snmp is controlled by community strings. A community string is a character string included in each snmp protocol message sent between your lanplex system and external management applications like tra...
Page 30
Snmp and smt proxy agents 3-7 snmp and smt proxy agents a proxy agent acts as a management gateway. It converts requests and event reports from one protocol and object format to another protocol and object format. Your lanplex system contains a proxy agent that translates between snmp and fddi smt. ...
Page 31: Hysical
4 p hysical a ccess : p orts and c abling this chapter explains how you can manage your lanplex system through its physical interfaces. Figure 4-1 highlights the system’s physical access options in the osi reference model environment. Figure 4-1 physical access options for the lanplex® system applic...
Page 32
4-2 c hapter 4: p hysical a ccess : p orts and c abling in-band and out-of-band management if you manage your lanplex system and its attached lans over the same network that carries your regular data traffic, then you are managing your network in-band. This is often the most convenient and inexpensi...
Page 33
Management access 4-3 figure 4-2 access through the console port ethernet and fddi ports using the rlogin or telnet interfaces, you can access the administration console through any ethernet or fddi port if an ip address is assigned to the ports. The lanplex snmp agent can also be accessed through t...
Page 34
4-4 c hapter 4: p hysical a ccess : p orts and c abling figure 4-3 shows management access through any ethernet or fddi port. Figure 4-3 access to the lanplex system through any ethernet or fddi port workstation workstation fddi port ethernet port lanplex ® 2500 system.
Page 35: Ridging
Ii chapter 5 transparent bridging chapter 6 express switching chapter 7 user-defined packet filtering chapter 8 bridging extensions b ridging t echnology.
Page 36: Ransparent
5 t ransparent b ridging this chapter describes the operation of a transparent bridge, including how a transparent bridge: ■ learns addresses ■ ages addresses ■ forwards packets ■ prevents loops in a network about transparent bridging a transparent bridge allows two or more lans to be interconnected...
Page 37
5-2 c hapter 5: t ransparent b ridging how a bridge learns addresses bridges learn addresses so that they can make intelligent decisions about which packets to forward from one bridge port to another. A bridge automatically learns addresses by listening on the network. For a bridge to learn the addr...
Page 38
How a bridge ages addresses 5-3 how a bridge ages addresses a source address remains in the address table as long as the station to which it relates regularly transmits through the bridge. If the station does not regularly transmit, the source address is “aged out” of the bridge’s table. Address agi...
Page 39
5-4 c hapter 5: t ransparent b ridging packet forwarding a bridge either filters, floods, or forwards packets by comparing the packet’s destination address to the addresses in the bridge’s address table, and by comparing the destination bridge port (if known) to the port on which the packet was rece...
Page 40
Packet forwarding 5-5 figure 5-2 forwarding, filtering, and flooding packets transmitting station address table bridge forwarding 1 packet enters bridge 2 packet’s destination address is compared to bridge’s address table 3 address is known and destination port is different from source 4 packet is f...
Page 41
5-6 c hapter 5: t ransparent b ridging spanning tree and the bridged network when transparent bridges are used to attach networks with redundant links, packets can loop and rapidly multiply on the attached lans. These additional packets create traffic that might unnecessarily clog the lan. A loop ex...
Page 42
Spanning tree and the bridged network 5-7 figure 5-3 packets looping and multiplying without spanning tree protocol the spanning tree algorithm the spanning tree algorithm detects loops and logically blocks (eliminates) redundant paths by putting some bridge ports in the blocking state so that only ...
Page 43
5-8 c hapter 5: t ransparent b ridging figure 5-4 spanning tree protocol implemented to block redundant links how the spanning tree algorithm works the spanning tree algorithm is based on the idea that bridges transmit messages to each other that allow them to calculate the spanning tree topology. T...
Page 44
Spanning tree and the bridged network 5-9 receiving information. Figure 5-5 shows the hierarchy of the spanning tree bridges and their ports. Figure 5-5 hierarchy of the root bridge and the designated bridge from the information that the cbpdus provide, the bridges: ■ elect a single bridge to be the...
Page 45
5-10 c hapter 5: t ransparent b ridging figure 5-6 shows a bridged network with its spanning tree elements. Figure 5-6 root and designated bridges and ports in a spanning tree topology cbpdu’s contents the specific information that bridges receive from the cbpdu allows them to calculate a spanning t...
Page 46
Spanning tree and the bridged network 5-11 the transmitting bridge id. If the cbpdus all have the same root id, cost, and transmitting bridge id, then the port identifier is used as a tiebreaker. Example 1. Message 1 has a lower root id, so the bridge saves the message. Example 2. Root id is the sam...
Page 47
5-12 c hapter 5: t ransparent b ridging this cbpdu looks like this: 85.0.85. 2 the bridge receives cbpdus on each of its ports from all other bridges. It saves the “best” cbpdu from each port. The best one is determined by comparing the information in each message arriving at a particular port to th...
Page 48
Spanning tree and the bridged network 5-13 figure 5-7 starting the spanning tree calculation the root id portion of the cbpdu determines which bridge will be the root bridge. The bridges transmit their cbpdus, receive each other’s cbpdus, and compare the cbpdus to each other. Because bridge b has th...
Page 49
5-14 c hapter 5: t ransparent b ridging figure 5-8 spanning tree topology calculated each bridge, except for the root bridge, must select a root port. To do this, each bridge determines the most cost-effective path for packets to travel from each of its ports to the root bridge. The cost depends on ...
Page 50
Spanning tree and the bridged network 5-15 if the bridge has more than one port attachment, the port with the lowest cost becomes the root port, and the other ports become either designated or backup ports. If bridges have redundant links to the same lan, then the port with the lowest port identifie...
Page 51
5-16 c hapter 5: t ransparent b ridging spanning tree port states as the spanning tree algorithm determines the spanning tree configura- tion, it places ports in the following states: listening, learning, forwarding, blocking, or disabled. As changes occur in the network, the port may transi- tion i...
Page 52
Spanning tree and the bridged network 5-17 figure 5-9 illustrates the factors that cause a port to change from one state to another. The arrows indicate the direction of movement between states. The numbers correspond to the factors that affect the transition. For example, for a port in the blocking...
Page 53
5-18 c hapter 5: t ransparent b ridging reconfiguring the bridged network topology the spanning tree algorithm reconfigures the bridged network topology when 1) bridges are added or removed, 2) the root bridge fails, or 3) the network administrator changes the bridging parameters that determine the ...
Page 54: Xpress
6 e xpress s witching this chapter describes these aspects of express switching mode: ■ technology and topology ■ address learning and aging ■ packet filtering and forwarding ■ advantages and constraints about express switching the lanplex 2500 system supports a mode of bridging called express switc...
Page 55
6-2 c hapter 6: e xpress s witching figure 6-1 express switching — flat topology traditional transparent bridging is preferable in environments that contain tree or mesh topologies that mix extended ethernet and fddi networks. See figure 6-2. Figure 6-2 traditional transparent bridging — tree topolo...
Page 56
Address learning 6-3 address learning in express switching mode, the lanplex 2500 system learns the source addresses only of stations not connected to the bridge’s backbone port. The bridge listens to the frames transmitted by stations and stores their addresses in a table. The address table is refe...
Page 57
6-4 c hapter 6: e xpress s witching using express switching mode in your network has these contraints: ■ directed (unicast) packets are not forwarded to an end-station that is not connected to the backbone until the bridge has learned that station’s address. Therefore, in certain circumstances, a st...
Page 58: Ser
7 u ser - defined p acket f iltering the lanplex system allows you to add a second layer of packet filtering on top of the standard filtering provided by a traditional transparent bridge. This chapter contains the following information on user-defined packet filters: ■ a general description ■ how to...
Page 59
7-2 c hapter 7: u ser - defined p acket f iltering the operators that you specify in the packet filter allow the filter to make a logical decisions about whether to forward or discard each packet. Table 7-2 describes your choices of operators. The operators and , or , and exclusive or are bit-wise o...
Page 60
About user-defined packet filtering 7-3 ■ placing a filter on the receive path prohibits a packet from accessing certain network segments unless it meets the forwarding criteria. A packet is discarded if it does not meet the forwarding criteria defined in the filter. See figure 7-1figure 7-1. Figure...
Page 61
7-4 c hapter 7: u ser - defined p acket f iltering example 1: isolating ip segments the network shown in figure 7-2 is composed of two types of protocols: ■ the internet protocol (ip), over which sun® workstations and a compute server communicate ■ appletalk® phase i protocol, over which apple® maci...
Page 62
About user-defined packet filtering 7-5 solution: to isolate the ip segments, define a packet filter that discards all appletalk packets received on the transmit path of ports that have only ip stations connected to them. (all ports would need a packet filter if the filter were installed on the rece...
Page 63
7-6 c hapter 7: u ser - defined p acket f iltering example 2: filtering appletalk phase ii packets if your macintosh computers use the appletalk phase ii protocol instead of the appletalk phase i protocol (as shown in example 1), then you must use a filter slightly more complicated. Appletalk phase ...
Page 64
About user-defined packet filtering 7-7 in this example, several simple expressions are combined to form the complete complex logical expression. Expressions can be differentiated as follows: expression 1: type field ■ operand 1 is the type field, which is a 2-byte value at offset 12 in the appletal...
Page 65
7-8 c hapter 7: u ser - defined p acket f iltering using address groups and port groups in a packet filter the section “about user-defined packet filtering” described how you can use packet filters to restrict the flow of packets based solely on the contents of the packet. The lanplex system also al...
Page 66
Using address groups and port groups in a packet filter 7-9 figure 7-6 adding an address to an address group if the address was never learned or has been aged, the port id associated with the address is set to “unknown.” broadcast and other multicast addresses are assumed to be in all groups. Becaus...
Page 67
7-10 c hapter 7: u ser - defined p acket f iltering groups. When the port is added to a group, the corresponding bit in the mask is set. See figure 7-7 figure 7-7 adding a port to a port group port table port fddi port 1 ethernet port 1 ethernet port 2 ethernet port 3 ethernet port 4 ethernet port 5...
Page 68
Using address groups and port groups in a packet filter 7-11 referencing address groups and port groups from a packet filter after you configure address and port groups, you can refer to them in a packet filter. The packet filter language defines several operands that relate to address and port grou...
Page 69
7-12 c hapter 7: u ser - defined p acket f iltering figure 7-8 network needing filtering to restrict server access the packet filter is designed to limit network traffic in these ways: ■ users in the accounting group must be able to communicate only with each other and with the accounting data serve...
Page 70
Using address groups and port groups in a packet filter 7-13 to implement packet filtering in the designed scheme for this network, take these steps: 1 set up address groups as follows: address group 1 — accounting address group 2 — engineering a address group 3 — engineering b note that the mail se...
Page 71
7-14 c hapter 7: u ser - defined p acket f iltering table in figure 7-9 on page 7-75 is for lanplex 2500 system engineering group a. 2 after setting up the address groups, generate the following filter: if (source address group mask and destination address group mask) = 0 then discard packet the exp...
Page 72
Using address groups and port groups in a packet filter 7-15 figure 7-9 address table for restricting server access address table 00010203040e 000102030403 000102030421 00010203040c 000102030411 000102030419 00010203041a 000102030412 00010203041d 000102030418 000102030401 00010203040f 000102030409 0...
Page 73
7-16 c hapter 7: u ser - defined p acket f iltering figure 7-10 address group filtering example globally administering packet filters you can create packet filters and group definitions in two ways: ■ locally, using the administration console. ■ on an external computer by creating files that contain...
Page 74: Lan
8 lan plex ® b ridging e xtensions this chapter describes lanplex® 2500 bridging extensions, a functionality that enhances bridge performance. These extensions include: ■ multicast packet firewalls ■ ip fragmentation ■ reduced packet flooding ■ network security enhancements multicast packet firewall...
Page 75
8-2 c hapter 8: lan plex ® b ridging e xtensions figure 8-1 illustrates the threshold mechanism for the multicast packet firewall. For information on setting this threshold, see the lanplex® 2500 administration console user guide. Figure 8-1 multicast packet firewall threshold mechanism ip fragmenta...
Page 76
Reducing packet flooding 8-3 ip fragmentation is specified in rfc 791 (internet protocol) and rfc 1122. For information on enabling ip fragmentation, see the lanplex® 2500 administration console user guide. Reducing packet flooding the lanplex 2500 system has functionality that enhances ieee 802.1d’...
Page 77
8-4 c hapter 8: lan plex ® b ridging e xtensions enhanced network security in addition to allowing you to design and use packet filters to improve network security (as described in chapter 7), the lanplex 2500 system allows you to use statically configured addresses as a form of network security. Fr...
Page 78: III
Iii chapter 9 fddi overview and implementation chapter 10 fddi networks fddi t echnology.
Page 79: Fddi O
9 fddi o verview and i mplementation this chapter discusses fddi concepts and terms. The final section shows how fddi is implemented in the lanplex® 2500 system. About fddi fiber distributed data interface (fddi) is a standards-based solution that provides fast and reliable data transfer on a local ...
Page 80
9-2 c hapter 9: fddi o verview and i mplementation the industry guideline for fddi technology is divided into four major standards: ■ physical medium dependent (pmd) — pmdspecifies the characteristics of the fiber optic medium, the connectors that attach stations to the fiber optic medium, the trans...
Page 81
Ports 9-3 figure 9-1 fddi relationship to osi reference model ports as parts of the physical layer, the phy and pmd entities work together to support each link between fddi stations. These entities provide the protocols that support the transmission and reception of signals between stations, as well...
Page 82
9-4 c hapter 9: fddi o verview and i mplementation each port is one of four types: a, b, m, and s. ■ a port — connects to the primary ring on the incoming fiber and the secondary ring on the outgoing fiber. A properly formed fddi dual ring is composed of a set of stations with the a port of one stat...
Page 83
Paths 9-5 paths fddi’s dual, counter-rotating ring is made up of a primary and secondary ring. Fddi stations can be connected to either ring or to both rings simultaneously. Data flows downstream on the primary ring in one direction from one station to its neighboring station. The secondary ring ser...
Page 84
9-6 c hapter 9: fddi o verview and i mplementation phy/pmd entities (m ports) are used for connecting other fddi stations, including other concentrators, in a tree topology. Attachments attachments refer to how a node, station, or concentrator is connected to an fddi network. They are classified as ...
Page 85
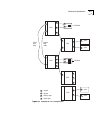
Nodes and attachments 9-7 figure 9-2 examples of fddi configurations sas duplex fiber cable fddi dual ding m dac a b m m a b s s sas s dac dac sac = a port = b port = master port = slave port a b m s sm-das b m m a m m sas s s sas nac dm-das m m m a m b m m m b a.
Page 86
9-8 c hapter 9: fddi o verview and i mplementation station management each fddi station has one station management (smt) entity to provide connection management, ring management, and operational management to the fddi network. Smt specifies a set of services and signaling mechanisms dedicated to fdd...
Page 87
Station management 9-9 frame-based protocols smt provides a number of frame-based services that are used by higher level management functions into manage stations on the network and to gather information about them. Frame-based protocols: ■ gather network statistics ■ detect, isolate, and resolve fa...
Page 88
9-10 c hapter 9: fddi o verview and i mplementation fddi and the lanplex 2500 system your lanplex 2500 system combines into one system the power of fddi and: ■ ethernet switching ■ ethernet-to-fddi transparent bridging ■ fddi switching ■ fast ethernet switching ■ atm switching. This combination dram...
Page 89
Fddi and the lanplex 2500 system 9-11 figure 9-3 sample fddi configuration for the lanplex 2500 system a b a b a b b a a b a b b a b a b a b a sas server sas server (fddi link) das server lanplex ® 2500 system netbuilder ii ® router fddi dual ring duplex fiber cable lanplex ® 2500 system lanplex ® 2...
Page 90: Fddi N
10 fddi n etworks this chapter provides general information about fddi networks and describes the differences between physical and logical topologies. Also covered: fddi connection rules and dual homing. About fddi networks fddi networks have important differences from other types of lans. Fddi netw...
Page 91
10-2 c hapter 10: fddi n etworks fddi network topologies the term network topology refers to the ways that stations are interconnected within a network. An fddi network topology may be viewed at two distinct levels: ■ physical topology — a network’s physical topology is defined by the arrangement an...
Page 92
Fddi network topologies 10-3 physical topology: a ring of trees the fddi trunk ring consists of dual-attach stations (dass) and dual-attach connectors (dacs). The dacs on the ring allow you to attach trees. The trees consist of branches of single-attach stations (sass) and dass that are star-wired o...
Page 93
10-4 c hapter 10: fddi n etworks this means that subsets of legal topologies are also legal. Examples of legal fddi topologies include the dual ring with trees, the dual ring without trees, and the single tree. For information on legal topologies, see the section “fddi connection rules” later in thi...
Page 94
Fddi connection rules 10-5 rejected. The fddi smt standard cites detailed connection rules for a specific port (“this port”) to other ports, which are shown in table 10-1. Table 10-1 port connection rules port connection connection rules a to a undesirable peer connection that creates twisted primar...
Page 95
10-6 c hapter 10: fddi n etworks table 10-2 provides a connection rule matrix summarizing the validity of most types of connections. Dual homing when the operation of a dual attachment node is crucial to your network, a configuration called dual homing can provide added reliability. A network admini...
Page 96
Dual homing 10-7 figure 10-4 dual homing for additional information about dual homing, see the lanplex® 2500 getting started guide. Secondary system link set by configuration policy dual-homed node das primary link primary system duplex fiber cable fddi dual ring m a b m a b a b m m.
Page 97: Atm T
Iv chapter 11 atm networks atm t echnology.
Page 98: Atm N
11 atm n etworks this chapter provides general information about: ■ the basic concepts of atm and its architecture ■ how atm handles addressing, signaling and virtual connections ■ traffic management on the atm network ■ the basic concepts of lan emulation (lane) ■ atm and the lanplex system about a...
Page 99
11-2 c hapter 11: atm n etworks short, repetitive needs of voice transmission. Atm thus allows a free mixture of data and voice or video within the same application. ■ scalable technology — atm accommodates a wide range of transmission rates and applications. ■ seamless connectivity — atm is the fir...
Page 100
About atm 11-3 figure 11-1 shows atm network unis and nnis. Figure 11-1 atm network unis and nnis atm cell structure one of the challenges in defining atm was to determine a structure that could efficiently handle any type of traffic. Because atm must carry voice, data, and video traffic simultaneou...
Page 101
11-4 c hapter 11: atm n etworks figure 11-2 uni atm cell structure these fields make up an atm cell: ■ generic flow control (gfc)— controls the flow of traffic across the user-network interface (uni) and into the network. The mechanisms for using this field are still under development. ■ virtual pat...
Page 102
About atm 11-5 virtual connections in atm atm switching is performed at the atm layer by defining virtual connections. Virtual connections are communication channels that provide for sequential, unidirectional transport of atm cells. Multiple virtual connections can exist on a physical link. A conne...
Page 103
11-6 c hapter 11: atm n etworks permanent virtual circuits pvcs are established via network management and are left up indefinitely. Both point-to-point and point-to-multipoint connections can be estab- lished. Virtual paths and virtual channels as in traditional lan packets, the header of each atm ...
Page 104
Atm protocol architecture 11-7 figure 11-4 virtual connections atm protocol architecture atm layers do not map directly to the open systems interconnect (osi) reference model of traditional lan networks. Atm layers follow the bisdn reference model, shown in figure 11-5. . Figure 11-5 bisdn protocol ...
Page 105
11-8 c hapter 11: atm n etworks the primary layers of the bisdn reference model are: ■ the physical layer ■ the atm layer ■ the atm adaptation layer the physical layer the physical layer defines how cells are transported over the network. This are of influence includes physical interfaces, media, an...
Page 106
Atm protocol architecture 11-9 the atm adaptation layer (aal) the atm adaptation layer (aal) provides the user-oriented functions that are not included as part of the atm layer. These user-oriented functions allow the atm layer to support the transport of different types of higher layer protocols an...
Page 107
11-10 c hapter 11: atm n etworks receiving data, the sar reassembles the contents of the atm cell information fields into the higher-layer protocol data units. Interim local management interface (ilmi) communication protocol the ilmi communication protocol is an open management protocol that support...
Page 108
Integrating atm in legacy lans 11-11 address registration is performed in two phases: 1 the network side supplies the network portion of the address (network prefix). 2 the user side appends the end-system identifier (esi) of the address and registers the complete address with the network side. Eith...
Page 109
11-12 c hapter 11: atm n etworks figure 11-7 shows how atm operates in a lan network. Figure 11-7 atm in a lan network lan emulation (lane) lan emulation (lane) enables existing applications to access an atm network via protocol stacks as if they were operating over traditional lans. Because lane is...
Page 110
Lan emulation (lane) 11-13 figure 11-8 lan emulation sublayer in a traditional ieee 802.X lan, traffic is transmitted to all stations on the shared physical medium, with each station determining which packets it should receive and which packets should be discarded. In an atm network, each lan segmen...
Page 111
11-14 c hapter 11: atm n etworks figure 11-9 atm network using lan emulation three important concepts are illustrated in figure 11-9: ■ network nodes may be members of the same lan emulation service (atm lan segment) even if they are connected to different switches in the network, as long as the swi...
Page 112
Lan emulation (lane) 11-15 ■ lan emulation client (lec) —a set of functions implemented in an atm endpoint which serves as an interface between it and the atm network in support of lan emulation. ■ lan emulation server (les) — the set of functions implemented in the atm network support of lan emulat...
Page 113
11-16 c hapter 11: atm n etworks atm and the lanplex system your lanplex 2500 system brings you the power of atm by combining ethernet switching, ethernet-to-fddi bridging, fast ethernet switching, fddi switching, and atm switching in an integrated system. The lanplex uses two methods to adapt the e...
Page 114
Atm and the lanplex system 11-17 vlans, see chapter 2: vlans in the lanplex system in the lanplex 2500 extended switching user guide. Creating an emulated lan you can create an 802.3 emulated lan on atm by defining the lan’s servers (the bus and the les) and then configuring each lan emulated client...
Page 115
11-18 c hapter 11: atm n etworks figure 11-10 multiple elans configured on lanplex 2500 systems in this example, two bridge ports are connected to the same location, causing a bridge loop. A similar example would be the connection of two lanplex 2500 systems by means of two ethernet segments. Enabli...
Page 116: Ppendixes
V appendix a snmp mib support appendix b technical support a ppendixes.
Page 117: Snmp Mib S
A snmp mib s upport this appendix lists the snmp mibs supported by the lanplex system software and describes the supported snmp compilers. Snmp mibs snmp mib files are shipped with the lanplex system software as asn.1 files. The currently supported version of each mib is listed in this section. All ...
Page 118
A-2 a ppendix a: snmp mib s upport ■ bridge.Mib — bridge mib, rfc 1493 the following bridge mib attributes are not supported: ■ ethernet.Mib — ethernet mib, rfc 1398 the following ethernet mib attributes are not supported: ■ if.Mib — if mib, rfc 1573 ■ fddismt7.Mib — fddi smt 7.3 mib, rfc 1512 ■ lec...
Page 119
Snmp mibs a-3 ■ les.Mib — atm mib, af-lane-1129.001 the following les mib attributes are not supported: ■ lp.Mib — lanplex systems mib, version 1.3.0 the following lanplex systems mib trap is not supported: ■ lpopfddi.Mib — lanplex optional fddi mib, version 1.2.1, based on smt 7.3 the following lan...
Page 120
A-4 a ppendix a: snmp mib s upport snmp mib compilers asn.1 mib files are provided for each of the mib compilers listed in this section. Any warnings or exceptions related to a compiler are listed with it. ■ smic (version 1.0.9) ■ mosy (version 7.1) for the mib file lpopfddi.Mib, the mosy compiler r...
Page 121: Echnical
B t echnical s upport 3com provides easy access to technical support information through a variety of services. This appendix describes these services. Online technical services 3com offers worldwide product support 24 hours a day, seven days a week, through the following online systems: ■ 3com bull...
Page 122
B-2 a ppendix b: t echnical s upport access by digital modem isdn users can dial in to 3combbs using a digital modem for fast access up to 56 kbps. To access 3combbs using isdn, dial the following number: (408) 654 2703 world wide web site access the latest networking information on 3com’s world wid...
Page 123
Support from your network supplier b-3 3comfacts sm automated fax service 3com corporation’s interactive fax service, 3comfacts, provides data sheets, technical articles, diagrams, and troubleshooting instructions on 3com products 24 hours a day, seven days a week. Call 3comfacts using your touch-to...
Page 124
B-4 a ppendix b: t echnical s upport support from 3com if you are unable to receive support from your network supplier, technical support contracts are available from 3com. In the u.S. And canada, call (800) 876-3266 for customer service. If you are outside the u.S. And canada, contact your local 3c...
Page 125: Peration
O peration g lossary a port in fddi technology, each das contains two ports: a and b. The a port is connected to the primary ring on the incoming fiber and the secondary ring on the outgoing fiber. A properly formed trunk ring is composed of a set of stations with the a port of one station connected...
Page 126
2 o peration g lossary backplane in the lanplex system, the “motherboard” that performs various logic and control functions. Located in the back of the chassis, it supports three 100mbps fddi paths, three 4 or 16 mbps token ring paths, three 10mbps ethernet paths, and a vmebus. B port in fddi techno...
Page 127
O peration g lossary 3 cell an atm layer protocol data-unit (pdu), characterized by fixed-length rather than variable-length payloads. The standard atm cell is 48 bytes of payload with 5 bytes of header. Cell relay see atm. Client a single-user computer that requests application or network services ...
Page 128
4 o peration g lossary das dual attachment station. A station directly attached to fddi’s dual token rings. A das has four fiber attachments consisting of one receive and one transmit fiber for each ring. Rather than an individual user workstation, a das is most likely to be the device controlling l...
Page 129
O peration g lossary 5 backup ring is used for automatic recovery in case of failure. If a network fault occurs, only the stations on either side of the fault are affected. They detect the fault and automatically bypass it to maintain continuous transmission of data. Fddi paths the segments of an fd...
Page 130
6 o peration g lossary ilmi interim local management interface. Atm forum-defined interim specifications for network management functions between a piece of atm data terminal equipment (dte) and an atm switch over the user-to-network interface (uni). Based on a limited subset of snmp capabilities. I...
Page 131
O peration g lossary 7 les lan emulation server. The les implements the control coordination function for the emulated lan. It also provides a facility for registering and resolving mac addresses and route descriptors to atm addresses. Llc logical link control. The upper sublayer of the data link la...
Page 132
8 o peration g lossary nonvolatile memory computer memory that is preserved when power is lost. Also called nvram. Oam operation and maintenance cell. This cell contains atm maintenance and performance monitoring information. It does not form part of the upper- layer information transfer. Operating ...
Page 133
O peration g lossary 9 primary path see fddi paths. Primary ring one of two counter-rotating, fiber optic rings that serve as the root of an fddi network. The primary ring normally enters each station on the trunk ring through the a port and exits through the b port. See also secondary ring. Protoco...
Page 134
10 o peration g lossary the other) form used on data transmissions links. This port can be used for dedicated local management access. S port slave port. Each phy/pmd pair, designated a port, belongs to one of four types: a, b, m, or s. A single attachment station (sas or sac) has an s port intended...
Page 135
O peration g lossary 11 station an addressable logical and physical attachment in a ring that is capable of transmitting, receiving, and repeating information. An fddi station has one or more phy entities, one or more mac entities, and only one smt entity. Station id the unique identifier for an fdd...
Page 136: Ndex
I ndex 1 i ndex numerics 3com bulletin board service (3combbs) b-1 3com sales offices b-4 3comfacts b-3 3comforum b-2 a aal sublayer convergence (cs) 11-9 segmentation and reassembly (sar) 11-9 address aging 5-3, 8-3 with express switching 6-2 destination 5-4 learning 5-2, 6-3 learning with express ...
Page 137
2 i ndex d das 9-10 designated bridge 5-8 designated port 5-8, 5-9 disabled port state 5-17 dual homing 10-6 dual ring, fddi 10-4 dual-attachment stations 9-10 e emulated lan (elan) creating 11-16 described 11-17 eliminating bridge loops 11-17 express switching 6-1 to 6-4 address aging 6-2 address l...
Page 138
I ndex 3 managing lanplex from outside the network 2-4 protocols 3-1 to 3-4 managing lanplex systems protocols 3-1 to 3-4 master port 9-4 mib 3-5 events 3-5 fddi 3-5, 9-8 ilmi 11-10 lanplex 3-5 snmp a-1 to a-3 mib ii traps 3-5 multicast packet firewall defined 8-1 multicast storm 8-2 receivemulticas...
Page 139
4 i ndex r receive path 7-1 returning products for repair b-4 ring of trees 10-3 rlogin 3-3 root bridge 5-8 root port 5-8 s s port 9-4 security manual address assignment 8-4 slave port 9-4 smt 9-2, 9-8 snmp 3-4 to 3-6 management applications 2-5 mibs a-1 to a-3 traps 3-5 spanning tree algorithm 5-7 ...