- DL manuals
- 3Com
- Network Router
- MSR 20 Series
- Configuration Manual
3Com MSR 20 Series Configuration Manual
Summary of MSR 20 Series
Page 1
H3c msr 20/30/50 series routers configuration manual (v1.00) msr 20 series routers msr 30 series routers msr 50 series routers www.3com.Com part number: 10016324 rev. Aa august 2007.
Page 2
3com corporation 350 campus drive marlborough, ma usa 01752-3064 copyright © 2007, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without writt...
Page 3: Ontents
C ontents a bout t his g uide conventions 69 related documentation 70 1 atm and dsl i nterface c onfiguration atm and dsl interface 71 ima-e1/t1 interface configuration 72 overview 72 configuring an atm e1/t1 interface 73 configuring an ima group 73 atm ima-e1/t1 interface configuration example 74 t...
Page 4
3 e thernet i nterface c onfiguration general ethernet interface configuration 89 combo port configuration 89 basic ethernet interface configuration 89 configuring flow control on an ethernet interface 90 configuring loopback test on a layer 2 ethernet interface 91 configuring loopback on a layer 3 ...
Page 5
Displaying and maintaining ce1/pri interfaces 110 ct1/pri interface 110 overview 110 configuring ct1/pri interface in ct1 mode 111 configuring an ct1/pri interface operating as a pri interface 111 configuring other ct1/pri interface parameters 112 starting/stopping a bert test on ct1/pri interface 1...
Page 6
Assigning a transmission priority to an atm pvc 132 configuring pvc service map 133 configuring an atm class 133 configuring vp policing 136 configuring applications over atm 136 configuring ipoa 136 configuring ipoeoa 137 configuring pppoa 137 configuring pppoeoa 138 displaying and maintaining atm ...
Page 7
Dcc for dialup isdn bri line and leased line connection 192 router-to-router callback with dcc (ppp approach) 194 router-to-router callback with dcc (isdn approach) 197 router-to-pc callback with dcc 198 nt server-to-router callback with dcc 200 circular dial string backup and internet access with d...
Page 8
Overview 235 dte, dce, uni, and nni 235 virtual circuit 235 frame relay protocol parameters 236 frame relay address mapping 237 frame relay configuration task list 238 configuring dte side frame relay 238 configuring basic dte side frame relay 238 configuring frame relay address mapping 239 configur...
Page 9
11 mp o fr overview 265 configuring mpofr 265 mpofr configuration example 266 12 gvrp c onfiguration introduction to gvrp 271 garp 271 gvrp 274 protocols and standards 274 configuring gvrp 275 configuring gvrp functions 275 configuring garp timers 275 displaying and maintaining gvrp 276 gvrp configu...
Page 10
Introduction 312 configuration procedure 313 displaying and maintaining lapb and x.25 314 lapb configuration example 314 x.25 configuration examples 316 direct connection of two routers via serial interfaces (one mapping) 316 direct connection of two routers through serial interfaces (two mappings) ...
Page 11
Displaying and maintaining link aggregation 353 link aggregation configuration example 353 17 m odem c onfiguration overview 355 modem configuration 355 configuring the modem answer mode 356 configuring modem using the at commands 356 modem configuration example 356 troubleshooting 357 18 p ort m ir...
Page 12
Configuring pppoe client 395 introduction to pppoe client 395 configuration procedure 396 resetting/deleting a pppoe session 396 displaying and maintaining pppoe 397 pppoe configuration example 397 pppoe server configuration example 397 pppoe client configuration example 398 connecting a lan to the ...
Page 13
Configuring permanent link function on isdn bri link layer 432 specifying an isdn bri interface to be in permanent active state on physical layer 433 enabling remote powering on an isdn bri interface 433 displaying and maintaining isdn 434 isdn configuration example 434 connecting routers through is...
Page 14
Configuration example 474 configuring digest snooping 475 configuration prerequisites 475 configuration procedure 475 configuration example 476 configuring no agreement check 477 prerequisites 478 configuration procedure 478 configuration example 478 configuring protection functions 479 configuratio...
Page 15
Adding a port to the isolation group 507 displaying and maintaining isolation groups 508 port isolation configuration example 508 27 d ynamic r oute b ackup c onfiguration overview 511 concept 511 features 511 implementation 512 dynamic route backup configuration 512 creating dynamic route backup gr...
Page 16
Sdh frame structure 540 terms 540 multiplexing e1/t1 channels to form stm-1 541 calculating e1/t1 channel sequence numbers 541 overhead byte 542 cpos interface application scenario 543 configuring a cpos interface 544 configuring an e1 channel 545 configuring a t1 channel 545 displaying and maintain...
Page 17
Dhcp address allocation 566 allocation mechanisms 566 dynamic ip address allocation procedure 566 ip address lease extension 567 dhcp message format 567 dhcp options 568 dhcp options overview 568 introduction to dhcp options 568 self-defined options 569 protocols and standards 571 33 dhcp s erver c ...
Page 18
Configuring the dhcp relay agent 591 enabling dhcp 591 enabling the dhcp relay agent on interfaces 591 correlating a dhcp server group with relay agent interfaces 592 configuring the dhcp relay agent to send a dhcp-release request 593 configuring the dhcp relay agent security functions 593 configuri...
Page 19
39 ip a ccounting c onfiguration introduction to ip accounting 619 configuring ip accounting 619 configuration prerequisites 619 configuration procedure 619 ip accounting configuration example 620 network requirements 620 network diagram 621 configuration procedure 621 displaying and maintaining ip ...
Page 20
43 udp h elper c onfiguration introduction to udp helper 647 configuring udp helper 648 displaying and maintaining udp helper 648 udp helper configuration example 649 44 urpf c onfiguration urpf overview 651 basic concepts 651 processing flow 651 configuring urpf 652 45 f ast f orwarding c onfigurat...
Page 21
47 nat-pt c onfiguration nat-pt overview 679 nat-pt mechanism 680 implementing nat-pt 680 protocols and standards 681 nat-pt configuration task list 681 configuring nat-pt 681 configuration prerequisites 681 enabling nat-pt 682 configuring a nat-pt prefix 682 configuring mappings for ipv4 hosts acce...
Page 22
Configuring ipv4 over ipv4 tunnel 717 configuration prerequisites 717 configuration procedure 717 configuration example 718 configuring ipv4 over ipv6 tunnel 721 configuration prerequisites 721 configuration procedure 721 configuration example 722 configuring ipv6 over ipv6 tunnel 725 configuration ...
Page 23
Running and terminating ttyd on unix server 778 installing and using ttyd administration program ttyadm 780 installing and configuring sco unixware server 787 installing device drivers 787 configuration prerequisites 787 modifying system configuration file ttydefs 788 editing ttyd configuration file...
Page 24
54 t erminal a ccess faq 55 ip r outing o verview ip routing and routing table 815 routing 815 routing table 815 routing protocol overview 817 static routing and dynamic routing 817 classification of dynamic routing protocols 817 routing protocols and routing priority 818 load balancing and route ba...
Page 25
Configuring a large scale bgp network 851 configuration prerequisites 851 configuring bgp peer groups 851 configuring bgp community 852 configuring a bgp route reflector 853 configuring a bgp confederation 853 configuring bgp graceful restart 853 displaying and maintaining bgp configuration 855 disp...
Page 26
Configuring lsp parameters 900 configuring spf parameters 901 configuring dynamic host name mapping 902 configuring is-is authentication 902 configuring lsdb overload tag 903 logging the adjacency changes 904 enabling an interface to send small hello packets 904 enabling is-is trap 904 configuring i...
Page 27
Configuring lsa transmission delay time 947 configuring spf calculation interval 948 configuring lsa minimum repeat arrival interval 948 configuring lsa generation interval 948 disabling interfaces from sending ospf packets 949 configuring stub routers 949 configuring ospf authentication 950 adding ...
Page 28
Optimizing the rip network 981 configuring rip timers 982 configuring the split horizon and poison reverse 982 configuring the maximum number of load balanced routes 983 enabling checkzero field check on ripv1 messages 983 enabling source ip address check on incoming rip updates 984 configuring rip-...
Page 29
Configuration prerequisites 1008 configuration procedure 1009 detecting reachability of the static route’s nexthop 1009 detecting nexthop reachability through track 1009 displaying and maintaining static routes 1010 configuration example 1010 62 ip v 6 bgp c onfiguration ipv6 bgp overview 1015 ipv6 ...
Page 30
Resetting ipv6 bgp connections 1034 clearing ipv6 bgp information 1034 ipv6 bgp configuration examples 1034 ipv6 bgp basic configuration 1034 ipv6 bgp route reflector configuration 1036 6pe configuration 1037 troubleshooting ipv6 bgp configuration 1041 no ipv6 bgp peer relationship established 1041 ...
Page 31
Disabling interfaces from sending ospfv3 packets 1058 enabling the logging on neighbor state changes 1058 displaying and maintaining ospfv3 1059 ospfv3 configuration examples 1059 configuring ospfv3 areas 1059 configuring ospfv3 dr election 1063 troubleshooting ospfv3 configuration 1066 no ospfv3 ne...
Page 32
Multicast models 1088 multicast architecture 1089 multicast addresses 1089 multicast protocols 1092 multicast packet forwarding mechanism 1095 multi-instance multicast 1095 introduction to the multi-instance concept 1095 multi-instance application in multicast 1096 68 m ulticast r outing and f orwar...
Page 33
Configuration prerequisites 1123 configuring igmp message options 1123 configuring igmp query and response parameters 1124 configuring igmp fast leave processing 1126 displaying and maintaining igmp 1127 igmp configuration example 1127 troubleshooting igmp 1129 no membership information on the recei...
Page 34
Introduction to bsr admin-scope regions in pim-sm 1169 ssm model implementation in pim 1171 multi-instance pim 1172 protocols and standards 1173 configuring pim-dm 1173 pim-dm configuration task list 1173 configuration prerequisites 1173 enabling pim-dm 1173 enabling state refresh 1174 configuring s...
Page 35
Enabling ipv6 multicast routing 1212 configuring an ipv6 multicast routing policy 1212 configuring an ipv6 multicast forwarding range 1213 configuring the ipv6 multicast forwarding table size 1213 displaying and maintaining ipv6 multicast routing and forwarding 1214 troubleshooting ipv6 multicast ro...
Page 36
Configuring ipv6 pim-sm 1248 ipv6 pim-sm configuration task list 1248 configuration prerequisites 1249 enabling ipv6 pim-sm 1249 configuring a bsr 1250 configuring an rp 1252 configuring ipv6 pim-sm register messages 1254 configuring rpt-to-spt switchover 1255 configuring ipv6 pim-ssm 1256 ipv6 pim-...
Page 37
Enabling switch-group reuse log 1294 displaying and maintaining md-vpn 1294 md-vpn configuration example 1295 troubleshooting md-vpn configuration 1308 unable to establish a share-mdt 1308 unable to build an mvrf 1309 76 mpls b asics c onfiguration mpls overview 1311 basic concepts of mpls 1312 arch...
Page 38
Restarting mpls ldp 1334 gracefully restarting mpls ldp 1334 configuring mpls ip ttl processing 1334 configuration prerequisites 1334 configuring mpls ip ttl propagation 1334 specifying the type of path for icmp responses 1334 configuring mpls fast forwarding 1335 setting the interval for reporting ...
Page 39
Tuning mpls te tunnel setup 1372 configuration prerequisites 1372 configuration procedures 1372 configuring traffic forwarding 1374 configuration prerequisites 1374 configuration procedures 1374 configuring traffic forwarding tuning parameters 1377 configuration prerequisites 1377 configuration proc...
Page 40
Configuring martini mpls l2vpn 1434 configuration prerequisites 1434 configuration procedure 1435 configuring kompella mpls l2vpn 1435 configuration prerequisites 1435 configuration procedure 1435 displaying and maintaining mpls l2vpn 1438 displaying the operation of mpls l2vpn 1438 resetting bgp l2...
Page 41
Configuration prerequisites 1495 configuring policy routing 1495 applying policy routing 1495 configuring a static route 1495 configuring hovpn 1495 configuration prerequisites 1495 configuring hovpns 1495 configuring ospf sham link 1496 configuration prerequisites 1496 configuring a loopback interf...
Page 42
Configuring the ip address of hub 1564 configuring the pre-shared key of vam server for a vpn domain 1565 configuring keepalive parameters 1565 configuring the vam client 1565 vam client configuration task list 1566 creating a vam client 1566 specifying an interval for resending a vam packet 1566 sp...
Page 43
Configuring mandatory chap authentication 1611 specifying to perform lcp negotiation with users 1612 configuring the local address and the address pool for allocation 1613 configuring local authentication, usernames and passwords 1614 specifying to include accm in control messages 1614 displaying an...
Page 44
86 c ongestion m anagement congestion management overview 1649 congestion management policies 1649 comparison of congestion management technologies 1654 configuring fifo queuing 1656 configuring fifo queuing 1656 configuration example for fifo queuing 1656 configuring priority queuing 1657 configuri...
Page 45
88 c ongestion a voidance congestion avoidance overview 1683 configuring wred 1685 configuring wred through two methods 1685 wred parameters 1685 configuring wred on interface 1686 configuration prerequisites 1686 configuration procedure 1686 configuration example 1686 configuring wred through wred ...
Page 46
Creating and configuring a frame relay class 1716 configuring frame relay traffic shaping 1717 configuring frame relay traffic policing 1718 configuring frame relay congestion management 1719 configuring frame relay de rule list 1719 configuring frame relay queuing management 1720 configuring frame ...
Page 47
Configuring local user attributes 1767 tearing down user connections forcibly 1769 configuring radius 1769 creating a radius scheme 1769 specifying the radius authentication/authorization servers 1770 configuring the radius accounting servers and relevant parameters 1770 setting the shared key for r...
Page 48
Configuring an aspf 1798 aspf configuration task list 1798 enabling the firewall function 1798 configuring an aspf policy 1799 applying an aspf policy to an interface 1799 enabling the session logging function for aspf 1800 configuring port mapping 1800 displaying and maintaining an aspf 1800 aspf c...
Page 49
Symptom 2: internal server functions abnormally 1827 97 pki c onfiguration introduction to pki 1829 pki overview 1829 pki terms 1829 architecture of pki 1830 applications of pki 1831 operation of pki 1831 pki configuration task list 1832 configuring an entity dn 1832 configuring a pki domain 1833 su...
Page 50
Portal+ direct authentication configuration examples 1865 portal + re-dhcp authentication configuration examples 1867 layer 3 portal + layer 3 authentication configuration examples 1869 troubleshooting portal 1870 inconsistent keys on the access device and the portal server 1870 incorrect server por...
Page 51
Setting the nat keepalive timer 1907 configuring a dpd 1907 disabling next payload field checking 1908 displaying and maintaining ike 1908 ike configuration example 1909 example for configuring ike 1909 example for ike aggressive mode and nat traversal 1910 example for configuring ipsec/ike to work ...
Page 52
Working with the sftp directories 1947 working with sftp files 1948 displaying help information 1949 terminating the connection to the remote sftp server 1949 sftp configuration example 1949 104 ssl c onfiguration ssl overview 1953 ssl configuration task list 1954 configuring an ssl server policy 19...
Page 53
Vrrp for ipv4 configuration task list 1979 enabling users to ping virtual ip addresses 1980 configuring the association between virtual ip address and mac address 1980 creating standby group and configuring virtual ip address 1981 configuring router priority, preemption mode and tracking function 19...
Page 54
Enabling the nqa client 2017 creating an nqa test group 2017 configuring an nqa test group 2017 configuring the icmp-echo test 2017 configuring the dhcp test 2019 configuring the ftp test 2019 configuring the http test 2020 configuring the udp-jitter test 2021 configuring the snmp test 2023 configur...
Page 55
111 ntp c onfiguration ntp overview 2049 applications of ntp 2049 how ntp works 2050 ntp message format 2051 operation modes of ntp 2053 multiple instances of ntp 2055 configuring the operation modes of ntp 2055 configuring ntp server/client mode 2056 configuring the ntp symmetric mode 2056 configur...
Page 56
Mib overview 2086 snmp configuration 2086 trap configuration 2088 configuration prerequisites 2088 configuration procedure 2088 displaying and maintaining snmp 2090 snmp configuration example 2090 configuration example for snmp logging 2091 114 f ile s ystem m anagement c onfiguration file system ma...
Page 57
117 s ystem m aintaining and d ebugging system maintaining and debugging overview 2119 introduction to system maintaining and debugging 2119 introduction to system debugging 2120 system maintaining and debugging 2121 system maintaining 2121 system debugging 2122 system maintaining example 2122 118 b...
Page 58
120 u ser i nterface c onfiguration user interface overview 2155 brief introduction 2155 numbering user interfaces 2156 user interface configuration task list 2156 configuring asynchronous serial interface attributes 2157 configuring terminal attributes 2157 configuring modem attributes 2158 configu...
Page 59
Upgrading pse processing software online 2181 configuring a pd disconnection detection mode 2182 enabling the pse to detect nonstandard pds 2182 displaying and maintaining poe 2183 poe configuration example 2183 troubleshooting poe 2185 124 oap m odule c onfiguration oap module overview 2187 switch ...
Page 60
Configuring collaboration between the track module and application modules 2208 configuring track-vrrp collaboration 2208 configuring track-static routing collaboration 2209 configuring track-policy routing collaboration 2210 configure track-backup center collaboration 2211 displaying and maintainin...
Page 61
Voice protocols 2238 dial plan 2239 command view 2240 130 v o ip o verview introduction to voip 2243 131 v oice s ubscriber l ine c onfiguration signal tone 2245 fxs voice subscriber line 2246 fxs interface 2246 cid 2246 fxo voice subscriber line 2246 fxo interface 2246 cid 2246 busy tone detection ...
Page 62
Configuring dtmf detection 2260 configuring options related to dial plan 2261 configuring adjustment functions 2261 configuration task list 2261 configuring echo adjustment function 2262 configuring gain adjustment function 2263 configuring time adjustment function 2263 configuring comfort noise fun...
Page 63
Dial plan process 2289 regular expression 2291 introduction to number substitution 2292 configuration task list 2293 configuring a calling number permitted to call in 2293 enabling private line auto ring-down 2294 configuring a number match mode 2294 configuration prerequisites 2294 configuring a gl...
Page 64
Creating a ts set 2315 configuring the voice subscriber line for a ts set 2316 configuration prerequisites 2316 configuring basic functions for the voice subscriber line 2316 configuring the dtmf detection sensitivity 2316 configuring the volume adjustment function 2317 configuring the echo adjustme...
Page 65
136 h.323 c onfiguration introduction 2355 h.323 architecture 2357 h.323 fundamentals 2358 gatekeeper discovery 2358 registration 2358 address translation 2358 admission control 2358 call setup 2359 call proceeding 2359 alerting 2359 connection 2359 capability negotiation 2359 opening/closing logica...
Page 66
Failed to set up point-to-point calls 2383 failed to send register requests 2383 138 v o fr c onfiguration overview 2385 fundamental vofr architecture 2385 protocols and standards 2385 call flow in dynamic mode 2386 call flow in frf.11 trunk mode 2386 configuration task lists 2387 configuring vofr e...
Page 67
Enabling accounting function for two-stage dialing users 2415 enabling authentication function for two-stage dialing users 2415 enabling authorization function for two-stage dialing users 2416 configuring method of collecting digits of called number 2417 configuring number of digits in card number/p...
Page 68
Enabling/disabling incoming call barring using keys 2435 configuring incoming call barring using command lines 2435 configuration example 2435 configuring outgoing call barring 2435 configuration prerequisites 2436 enabling/disabling outgoing call barring using keys 2436 configuring outgoing call ba...
Page 69: Bout
A bout t his g uide this manual describes how to operate your h3c msr 20/30/50 series router. It includes the following sections about all of the major features of the routers. This manual is intended for the following readers: ■ network administrators ■ network engineers ■ users who are familiar wi...
Page 70
70 a bout t his g uide related documentation the following manuals offer additional information necessary for managing your msr 20/30/50 series router: ■ h3c msr 20/30/50 series routers installation manuals — covers setting up and initializing your router. ■ h3c msr 20/30/50 series routers command r...
Page 71: Atm
1 atm and dsl i nterface c onfiguration when configuring atm/dsl interface, go to these sections for information you are interested in: ■ “atm and dsl interface” on page 71 ■ “ima-e1/t1 interface configuration” on page 72 ■ “atm e3/t3 interface configuration” on page 76 ■ “atm oc-3c/stm-1 interface ...
Page 72
72 c hapter 1: atm and dsl i nterface c onfiguration low transmission cost feature of dsl. So far, dsl technologies have been widely adopted for broadband accessing. Atm interfaces available for the low-end and mid-range routers so far, the low-end and mid-range routers can provide the following atm...
Page 73
Ima-e1/t1 interface configuration 73 the configuration of ima-e1/t1 includes two parts: physical level parameters of atm e1/t1 interfaces and ima features. If no ima group is configured for transmitting atm cell streams, the cells are distributed directly over e1/t1 links. You can, however, assign m...
Page 74
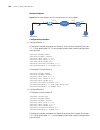
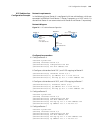
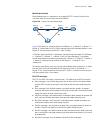
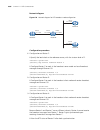
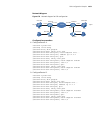
74 c hapter 1: atm and dsl i nterface c onfiguration atm ima-e1/t1 interface configuration example network requirements as shown in figure 1 , on the ima-8e1 interface module of the router, create two ima groups, each of which is assigned two links; create two pvcs, setting their peer ip address to ...
Page 75
Ima-e1/t1 interface configuration 75 network diagram figure 1 network diagram for ima-e1/t1 interface configuration configuration procedure # assign two links to ima group 1. System-view [sysname] interface atm 5/0 [sysname-atm5/0] undo ip address [sysname-atm5/0] ima ima-group 1 [sysname-atm5/0] in...
Page 76
76 c hapter 1: atm and dsl i nterface c onfiguration if the interface cannot be pinged, check whether: ■ the interface is down. ■ the aal5 encapsulation type of the pvc is incorrect. Atm e3/t3 interface configuration this section covers these topics: ■ “overview” on page 72 ■ “configuring an atm e3/...
Page 77
Adsl interface configuration 77 overview this section covers only the physical configurations of the interface. For more information about how to configure atm (including pvcs), refer to “atm configuration” on page 127 . Configuring an atm oc-3c/stm-1 interface follow these steps to configure an atm...
Page 78
78 c hapter 1: atm and dsl i nterface c onfiguration two types of adsl modules/cards are available: adsl over pots and adsl over isdn (adsl-i). Typical network topology for adsl routers the following figure shows a typical network topology for routers with adsl interfaces, where: ■ dslam at the cent...
Page 79
Adsl interface configuration 79 configuring an adsl interface n to have the adsl standard command take effect, you need to re-activate the interface either by performing the shutdown and undo shutdown commands or the activate and undo activate commands. Upgrading adsl2+ card software the upgradeable...
Page 80
80 c hapter 1: atm and dsl i nterface c onfiguration n when executing the bootrom update file command, do not use the all option unless absolutely necessary; use the part option instead. If you use the all option, you will find it hard to roll back to the old version once the upgrade fails. G.Shdsl ...
Page 81
Displaying and maintaining atm and dsl interfaces 81 displaying and maintaining atm and dsl interfaces n for those physical interfaces that are not connected to cables, shut down them using the shutdown command to avoid anomalies resulted from interference. Troubleshooting this section covers these ...
Page 82
82 c hapter 1: atm and dsl i nterface c onfiguration the ping command can test network connectivity. Extended ping command can be used to specify some options in the ip header in addition to that function. For more information about the ping command, see “system maintaining and debugging” on page 21...
Page 83: Pos I
2 pos i nterface c onfiguration when configuring pos interfaces, go to these sections for information you are interested in: ■ “overview” on page 83 ■ “configuring a pos interface” on page 83 ■ “displaying and maintaining pos interfaces” on page 84 ■ “pos interface configuration example” on page 85 ...
Page 84
84 c hapter 2: pos i nterface c onfiguration follow these steps to configure a pos interface: displaying and maintaining pos interfaces to do... Use the command... Remarks enter system view system-view -- enter pos interface view interface pos interface-number required set the clock mode clock { mas...
Page 85
Pos interface configuration example 85 n if a physical interface is idle or has no cable connection, shut down it with the shutdown command to avoid interface anomalies that may result from interference. As the command can disable the interface, use it with caution. Pos interface configuration examp...
Page 86
86 c hapter 2: pos i nterface c onfiguration connecting routers through pos interfaces across frame relay network requirements connect routers to a public frame relay network through pos interfaces. The routers are premise equipment that work as dte side of frame relay. Router a uses frame relay sub...
Page 87
Troubleshooting pos interfaces 87 # configure interface pos 1/0. [routerb] interface pos 1/0 [routerb-pos1/0] clock slave # configure frame relay encapsulation on the interface. [routerb-pos1/0] link-protocol fr [routerb-pos1/0] fr interface-type dte [routerb-pos1/0] ip address 10.10.10.2 255.255.25...
Page 88
88 c hapter 2: pos i nterface c onfiguration ■ the correct clock mode is configured on the pos interface. If not, enormous amount of crc errors can be generated. ■ check that the mtu configuration is appropriate..
Page 89: Thernet
3 e thernet i nterface c onfiguration when configuring ethernet interfaces, go to these sections for information you are interested in: ■ “general ethernet interface configuration” on page 89 ■ “configuring layer 2 ethernet interfaces” on page 92 ■ “configuring layer 3 ethernet interfaces” on page 9...
Page 90
90 c hapter 3: e thernet i nterface c onfiguration ■ half-duplex mode (half): in this mode, at a particular time, either the sending or receiving of data packets is allowed, but not both; ■ auto-negotiation mode (auto): in this mode, the transmission mode is negotiated between peer ethernet interfac...
Page 91
General ethernet interface configuration 91 configuring loopback test on a layer 2 ethernet interface you can enable loopback test to check whether the ethernet interface functions properly. Note that no data packets can be forwarded during the test. Loopback test falls into the following two catego...
Page 92
92 c hapter 3: e thernet i nterface c onfiguration configuring the working mode of an ethernet interface according to the layer at which the device processes received data packets, ethernet interfaces can work in bridge or route mode. Follow these steps to change the working mode of an ethernet inte...
Page 93
Configuring layer 2 ethernet interfaces 93 add ports to or removing ports from a link aggregation port group can only be achieved through operations on the link aggregation group. Manual port group is mainly used to synchronize the configurations among the ports in it. When you use the display curre...
Page 94
94 c hapter 3: e thernet i nterface c onfiguration n if you set the suppression ratio in interface view or port group view repeatedly, the last configuration takes effect. Configuring the interval for collecting ethernet interface statistics complete the following configuration tasks to configure th...
Page 95
Configuring layer 2 ethernet interfaces 95 ■ if loops are detected on a port that is of trunk or hybrid type, trap messages are sent to the terminal. If the loopback detection control function is also enabled on the port, the port will be blocked, trap messages will be sent to the terminal, and the ...
Page 96
96 c hapter 3: e thernet i nterface c onfiguration ■ across mode, where the ethernet interface only accepts crossover cables. ■ normal mode, where the ethernet interface only accepts straight-through cables. ■ auto mode, where the ethernet interface accepts both straight-through cables and crossover...
Page 97
Maintaining and displaying an ethernet interface 97 follow the following steps to set the mtu for an ethernet interface: n limited to the qos queue length (for example, the default length of an fifo queue is 75), too small an mtu will result in too many fragments, which will be discarded from the qo...
Page 99: Wan I
4 wan i nterface c onfiguration in terms of line type, wide area networks (wans) fall into these types: x.25, frame relay (fr), atm, and isdn. To interface to these networks, routers are designed with asynchronous serial interface, synchronous serial interface, atm interface, isdn bri interface, ce1...
Page 100
100 c hapter 4: wan i nterface c onfiguration configuring an asynchronous serial interface follow these steps to configure an asynchronous serial interface: n ■ you can use the speed command to configure the baud rate for an asynchronous serial interface. For details, refer to the “user interface co...
Page 101
Aux interface 101 aux interface overview the aux interface is fixed on your device. It can work as a regular asynchronous serial interface at speeds up to 115200 bps. With this interface, you can perform functions such as remote device configuration and line backup. Configuring an aux interface foll...
Page 102
102 c hapter 4: wan i nterface c onfiguration n in certain cases, configurations concerning ppp, dcc, ip address, firewall, and backup center are required for a usb interface. Refer to “configuring ppp” on page 367 , “dcc configuration” on page 153 , “ip addressing configuration” on page 623 , “fire...
Page 103
Am interface 103 n ■ to set the baud rate for a synchronous/asynchronous serial interface operating in asynchronous mode, use the speed command in user-interface view. Refer to “user interface configuration” on page 2155 for related information. ■ refer to corresponding volumes for information about...
Page 104
104 c hapter 4: wan i nterface c onfiguration theoretically, if the peer (usually an isp) uses a digital modem, the am interface can establish connection with v.90 modem standard to provide downstream rates up to 56 kbps and upstream rates up to 33.6 kbps. If the peer (usually a common user) uses an...
Page 105
Isdn bri interface 105 can be used to forward digital and analog information. The standardization efforts that itu-t made in provisioning the isdn services make the implementation of isdn become possible. The provisions of the recommendations i.430, q.921, and q.931 allow all the devices meeting itu...
Page 106
106 c hapter 4: wan i nterface c onfiguration ■ verify the type of the interface provided by your telecom service provider, whether it is isdn bri u or isdn bri s/t. Despite that itu-t i.411 has provided an isdn user-network interface reference model, there are some arguments in the position of the ...
Page 107
Ce1/pri interface 107 a ce1/pri interface in ce1/pri mode is physically divided into 32 timeslots numbered 0 to 31. Among them, timeslot 0 is used for transmitting synchronizing information. This interface can be used as either a ce1 interface or a pri interface. ■ when this interface is used as a c...
Page 108
108 c hapter 4: wan i nterface c onfiguration a ce1/pri interface in ce1/pri mode can be used as a ce1 interface where a serial interface is created upon creation of a channel set. You may bundle timeslots on a ce1/pri interface into up to 31 channel sets. For each channel set, the system automatica...
Page 109
Ce1/pri interface 109 ■ “dcc configuration” on page 153 ■ “configuring ppp” on page 367 ■ “ip addressing configuration” on page 623 ■ “backup center configuration” on page 1961 if the interface is to be used as a primary or secondary interface for backup ■ “firewall configuration” on page 1789 n the...
Page 110
110 c hapter 4: wan i nterface c onfiguration configuring error packets diffusion restraint n the support of this feature varies with device model. Refer to your specific device. Error packet diffusion refers to the situation when one timeslot receives a certain error packet, all the other timeslots...
Page 111
Ct1/pri interface 111 ■ when it is working as a pri interface, timeslot 24 is used as a d channel for signaling transmission. Therefore, only a group of timeslots except timeslot 24 can be chosen as the b channel. This timeslot group is bundled together with timeslot 24 to form a pri set. This pri s...
Page 112
112 c hapter 4: wan i nterface c onfiguration for the pri set, the system automatically creates a serial interface numbered serial number:23. This interface is logically equivalent to an isdn pri interface where you can make other configurations about: ■ “dcc configuration” on page 153 ■ “configurin...
Page 113
Ct1/pri interface 113 starting/stopping a bert test on ct1/pri interface bit error rate test (bert) is operating as follows: the local end sends out a pattern, which is to be looped over somewhere on the line and back to the local end. The local end then checks the received pattern for the bit error...
Page 114
114 c hapter 4: wan i nterface c onfiguration follow these steps to start/stop a bert test on a ct1/pri interface: configuring error packets diffusion restraint n the support of this feature varies with device model. Refer to your specific device. Error packet diffusion refers to the situation when ...
Page 115
E1-f interface 115 e1-f interface overview e1-f interfaces, fractional e1 interfaces, are simplified ce1/pri interfaces. They are a cost-effective alternative to ce1/pri interfaces where e1 access does not need multiple channel sets or isdn pri. Compared with a ce1/pri interface, an e1-f interface d...
Page 116
116 c hapter 4: wan i nterface c onfiguration configuring other e1-f interface parameters follow these steps to configure other e1-f interface parameters: displaying and maintaining e1-f interfaces set the interface to operate in unframed mode fe1 unframed required the default is framed mode. Set ot...
Page 117
T1-f interface 117 t1-f interface overview t1-f interfaces, fractional t1 interfaces, are simplified ct1/pri interfaces. They are a cost-effective alternative to ct1/pri interfaces where t1 access does not need multiple channel sets or isdn pri. Compared with a ct1/pri interface, a t1-f interface de...
Page 118
118 c hapter 4: wan i nterface c onfiguration starting/stopping a bert test on t1-f interface bert is operating as follows: the local end sends out a pattern, which is to be looped over somewhere on the line and back to the local end. The local end then checks the received pattern for the bit error ...
Page 119
Ce3 interface 119 follow these steps to start/stop a bert test on a t1-f interface: displaying and maintaining t1-f interfaces ce3 interface overview like e1, e3 also belongs to the digital carrier system of itu-t. It transmits data at 34.368 mbps and adopts hdb3 as the line code format. A ce3 inter...
Page 120
120 c hapter 4: wan i nterface c onfiguration depending on the networking requirements, you probably need to configure the ce3 interface with parameters about “configuring ppp” on page 367 , “vofr configuration” on page 2385 , “ip addressing configuration” on page 623 , and so on. Configuring a ce3 ...
Page 121
Ce3 interface 121 displaying and maintaining ce3 interfaces c caution: an interface is disabled when being shut down. So, perform operations of this type with caution. You can verify the configuration of a ce3 interface by using the display commands listed in the following table in any view. Enter c...
Page 122
122 c hapter 4: wan i nterface c onfiguration n ■ shutting down/bringing up a ce3 interface also shuts down/brings up the e1 lines demultiplexed from the ce3 interface, the serial interfaces formed by the e1 lines, and the serial interfaces created on e1 lines by means of timeslot bundling. ■ shutti...
Page 123
Ct3 interface 123 number/line-number:set-number for it. This interface operates at n × 64 kbps or n × 56 kbps and is logically equivalent to a synchronous serial interface where you can make other configurations. Configuring a ct3 interface (in t3 mode) follow these steps to configure a ct3 interfac...
Page 124
124 c hapter 4: wan i nterface c onfiguration depending on the networking requirements, you probably need to configure the ct3 interface with parameters about “configuring ppp” on page 367 , “vofr configuration” on page 2385 , “ip addressing configuration” on page 623 , and so on. Configuring other ...
Page 125
Ct3 interface 125 displaying and maintaining ct3 interfaces c caution: an interface is disabled when being shut down. So, perform operations of this type with caution. You can verify the configuration of a ct3 interface by using the display commands listed in the following table in any view. Place a...
Page 126
126 c hapter 4: wan i nterface c onfiguration note that: ■ shutting down/bringing up a ct3 interface also shuts down/brings up the t1 lines demultiplexed from the ct3 interface, the serial interfaces formed by the t1 lines, and the serial interfaces created on t1 lines by means of timeslot bundling....
Page 127: Atm C
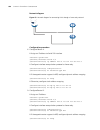
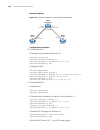
5 atm c onfiguration introduction to atm technology atm overview asynchronous transfer mode (atm) is a technology based on packet transmission mode while incorporating the high speed of circuit transmission mode. It can satisfy the need of various communication services. Atm was specified as a broad...
Page 128
128 c hapter 5: atm c onfiguration figure 6 atm protocol model the specific functions of various layers are as follows: ■ the physical layer mainly provides transmission channels for atm cells, forming continuous bit streams by adding the transmission overheads onto the cells from the atm layer. At ...
Page 129
Overview of ipoa, ipoeoa, pppoa and pppoeoa applications 129 ipoa ip over aal5 (ipoa) carries ip packets over aal5. Aal5 provides the ip hosts on the same network with the data link layer for communications. In addition, to allow these hosts to communicate on the same atm network, ip packets must be...
Page 130
130 c hapter 5: atm c onfiguration configuring atm complete these tasks to configure atm: configuring atm interface depending on the actual networking environment and system requirements, sometimes it may be necessary to modify certain parameters of an atm interface. Note that although these paramet...
Page 132
132 c hapter 5: atm c onfiguration n for details about the configuration of the radius scheme, refer to “aaa/radius/hwtacacs configuration” on page 1751 . Assigning a transmission priority to an atm pvc you can assign transmission priority to atm pvcs associated with the ubr, vbr-t, or vbr-nrt servi...
Page 133
Configuring an atm class 133 configuring pvc service map pvc service map allows different pvcs from the same pvc-group to carry ip packets of different priorities. Follow these steps to configure pvc service map: n ■ a primary pvc refers to the one based on which a pvc-group is created on an atm int...
Page 134
134 c hapter 5: atm c onfiguration to do... Use the command... Remarks enter system view system-view - create an atm class and enter atm class view atm class atm-class-name required specify atm aal5 encapsulation type for the pvc encapsulation aal5-encap optional by default, aal5snap encapsulation i...
Page 135
Configuring an atm class 135 as for the configurations performed to a pvc, note that: ■ the priorities of the same configurations performed to a pvc descend in this order: the configuration directly performed to the pvc, the configuration performed to the atm class applied to the pvc, and the config...
Page 136
136 c hapter 5: atm c onfiguration ■ all the configurations that are directly performed to the pvc, performed to the atm class applied to the pvc, and performed to the atm class applied to the atm interface take effect if they do not conflict. ■ for different configurations performed to a pvc, the a...
Page 137
Configuring applications over atm 137 note that a pvc cannot carry multiple protocols when the atm aal5 is encapsulated with aal5mux. Once ipoa is configured on the pvc, other protocols such as ipoeoa, pppoa and pppoeoa are not supported. Configuring ipoeoa follow these steps to enable ipoeoa on pvc...
Page 138
138 c hapter 5: atm c onfiguration n as for the next hop and the outbound interface, only the former is required when you configure a static route on a virtual-template interface. If you want to specify the outbound interface as well, make sure the physical interface bound to the virtual-template is...
Page 139
Displaying and maintaining atm 139 n as for the next hop and the outbound interface, only the former is required when you configure a static route on a virtual-template interface. If you want to specify the outbound interface as well, make sure the physical interface bound to the virtual-template is...
Page 140
140 c hapter 5: atm c onfiguration atm configuration examples n in the following examples, the network device, the digital subscriber line access multiplexer (dslam) and its configuration command sequence are ma 5100 multi-business access device and the corresponding command sequence under its confi...
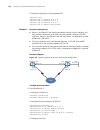
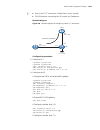
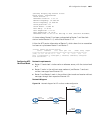
Page 141
Atm configuration examples 141 network diagram figure 7 network diagram for ipoa configuration configuration procedure 1 configure router a # enter the atm interface, and configure an ip address for it. System-view [routera] interface atm 1/0 [routera-atm1/0] ip address 202.38.160.1 255.255.255.0 # ...
Page 142
142 c hapter 5: atm c onfiguration system-view [routerc] interface atm 1/0 [routerc-atm1/0] ip address 202.38.160.3 255.255.255.0 # establish a pvc, running ip. [routerc-atm1/0] pvc to_a 0/60 [routerc-atm-pvc-atm1/0-0/60-to_a] map ip 202.38.160.1 [routerc-atm-pvc-atm1/0-0/60-to_a] quit [routerc-atm1...
Page 143
Atm configuration examples 143 [routerc] interface atm 1/0.1 [routerc-atm1/0.1] pvc to_adsl_a 0/60 [routerc-atm-pvc-atm1/0.1-0/60-to_adsl_a] map bridge virtual-ethernet 1 [routerc-atm-pvc-atm1/0.1-0/60-to_adsl_a] quit [routerc-atm1/0.1] pvc to_adsl_b 0/61 [routerc-atm-pvc-atm1/0.1-0/61-to_adsl_b] ma...
Page 144
144 c hapter 5: atm c onfiguration # create vt interface, configure pap authentication and ip address negotiation, and allocate an ip address for the remote end from the ip address pool. [routerc] interface virtual-template 10 [routerc-virtual-template10] ip address 202.38.160.1 255.255.255.0 [route...
Page 145
Atm configuration examples 145 both the wan port of router c and the dsl interface of adsl router adopt pppoeoa. Each host within the two ethernets uses pre-installed pppoe client program to make interactive pap authentication with routers, and obtains ip address from the router. Network diagram fig...
Page 146
146 c hapter 5: atm c onfiguration # create the ve interface to encapsulate ppp protocol. [routerc] interface virtual-ethernet 1 [routerc-virtual-ethernet1] pppoe-server bind virtual-template 10 [routerc-virtual-ethernet1] quit [routerc] interface virtual-ethernet 2 [routerc-virtual-ethernet2] pppoe...
Page 147
Atm configuration examples 147 [routera] dialer-rule 10 ip permit # create dialer port and configure the dial-up and ppp authentication: [routera] interface dialer0 [routera-dialer0] link-protocol ppp [routera-dialer0] ppp chap password hello [routera-dialer0] ppp chap user user1 [routera-dialer0] i...
Page 148
148 c hapter 5: atm c onfiguration [sysname] domain system [sysname-isp-system] scheme local [sysname-isp-system] ip pool 80 10.1.1.2 10.1.1.100 # configure a ve interface. [sysname] interface virtual-ethernet 1 # enable pppoe server on the vt specified on the virtual ethernet interface. [sysname-vi...
Page 149
Troubleshooting atm 149 [routera-atm-pvc-atm1/0-0/33-1] quit [routera-atm1/0] pvc 2 0/32 [routera-atm-pvc-atm1/0-0/32-2] map ip 202.38.160.3 [routera-atm-pvc-atm1/0-0/32-2] service ubr 100000 [routera-atm-pvc-atm1/0-0/33-1] transmit-priority 3 after two equal traffics that exceed the atm bandwidth a...
Page 150
150 c hapter 5: atm c onfiguration check the atm interfaces of the two sides to make sure that they are of the same type, for example, both are multimode fiber interfaces or both are single mode fiber interfaces, or both are multimode fiber interfaces but connected using single mode. If a multimode ...
Page 151
Troubleshooting atm 151 example, if one side uses snap whereas the other uses mux, they cannot communicate. You can enable the packet debugging function of atm to get some clues. Packet loss and crc errors and changes of interface state symptom: two routers are connected back-to-back, and a ping bet...
Page 152
152 c hapter 5: atm c onfiguration.
Page 153: Dcc C
6 dcc c onfiguration when configuring dcc, go to these sections for information you are interested in: ■ “introduction to dcc” on page 153 ■ “dcc configuration” on page 157 ■ “displaying and maintaining dcc” on page 179 ■ “dcc configuration example” on page 179 ■ “troubleshooting” on page 208 introd...
Page 154
154 c hapter 6: dcc c onfiguration ■ physical interface: an interface that physically exists. Examples are serial, bri, and asynchronous interfaces. ■ dialer interface: a logical interface created for configuring dcc parameters. A physical interface inherits the dcc configuration of a dialer interfa...
Page 155
Introduction to dcc 155 as shown in the above figure, a physical interface can be assigned to only one dialer interface, but each dialer interface can contain multiple physical interfaces and be mapped to multiple destination addresses. In addition, a physical interface does not necessarily belong t...
Page 156
156 c hapter 6: dcc c onfiguration use only one dialer bundle and configured with one dial string. The physical interfaces in a dialer bundle can be assigned different priorities. In the figure, interface dialer2 uses dialer bundle 2 that contains physical interfaces bri 1/0, bri 1/1 and serial 2/1....
Page 157
Dcc configuration 157 ■ “making basic configuration” on page 157 ■ “configuring dcc parameters” on page 157 identifying the topology of dcc application you need to identify: ■ which routers will provide dcc and how they are related to each other. ■ which interfaces on the routers will provide dcc, a...
Page 158
158 c hapter 6: dcc c onfiguration complete these tasks to configure basic parameters for dcc: configuring physical interfaces for a synchronous/asynchronous serial interface, you must set its operating mode depending on the connected modem. If the connected modem is asynchronous, set the interface ...
Page 159
Dcc configuration 159 resetting the idle-timeout timer if a link is present, or drops it without originating calls for link setup if no link is present. For dcc to send packets normally, you must configure a dial access control list (acl) and associate it with the concerned dial interface (physical ...
Page 160
160 c hapter 6: dcc c onfiguration ■ “configuring multiple interfaces to place calls to one or multiple remote ends” on page 163 ■ “configuring multiple interfaces to receive calls from one or multiple remote ends” on page 165 in the c-dcc implementation of dcc, the two dial parties can configure th...
Page 161
Dcc configuration 161 configuring an interface to receive calls from a remote end as shown in the following figure, an interface at the local end receives calls from a single remote end (the components in inverse color represent the routers irrelevant to the networking): figure 16 network diagram fo...
Page 162
162 c hapter 6: dcc c onfiguration configuring an interface to place calls to multiple remote ends as shown in the following figure, an interface at the local end places calls to multiple remote ends (the components in inverse color represent the routers irrelevant to the networking): figure 17 netw...
Page 163
Dcc configuration 163 configuring an interface to receive calls from multiple remote ends as shown in the following figure, an interface at the local end receives calls from multiple remote ends (the components in inverse color represent the routers irrelevant to the networking): figure 18 network d...
Page 164
164 c hapter 6: dcc c onfiguration figure 19 network diagram for multiple interfaces place calls to one or multiple remote ends in this scenario, interfaces if0, if1, and if2 at the locate end place dcc calls to interfaces if1, if2 and if3 at the remote end. If only one remote end is involved, use t...
Page 165
Dcc configuration 165 configuring multiple interfaces to receive calls from one or multiple remote ends as shown in the following figure, multiple interfaces at the local end receive calls from one or multiple remote ends (the components in inverse color represent the routers irrelevant to the netwo...
Page 166
166 c hapter 6: dcc c onfiguration configuring rs-dcc in rs-dcc approach, physical interface configuration is separated from logical configuration for calls and they can be combined dynamically for each call. When configuring rs-dcc for on-demand dial, you need to configure rs-dcc sets. Each rs-dcc ...
Page 167
Dcc configuration 167 if rs-dcc sets are used to configure rs-dcc parameters, you only need to configure link layer encapsulation and dialer bundle numbers on physical interfaces. Before configuring rs-dcc, be aware of the following: ■ in rs-dcc, a rs-dcc set is unable to apply the attribute informa...
Page 168
168 c hapter 6: dcc c onfiguration assigning physical interfaces to the dialer bundle a dialer bundle is a collection of physical interfaces with different priorities. When placing a call, dcc selects a physical interface from the bundle in priority order. Follow these steps to assign physical inter...
Page 169
Dcc configuration 169 implementing dcc with mp in dcc applications, you may configure load thresholds for links. If you set a link load threshold in the range 1 to 99, mp tunes allocated bandwidth according to actual traffic percentage as follows: ■ when the percentage of traffic on a link to bandwi...
Page 170
170 c hapter 6: dcc c onfiguration ■ in the rs-dcc approach, configure in dialer interface view at the calling end and in physical dial interface view at the called end. At the calling end, however, you are recommended to configure the same ppp parameters on physical dial interfaces as well to ensur...
Page 171
Dcc configuration 171 n ■ configure ppp callback after completing the basic configuration of c-dcc or rs-dcc. ■ ppp callback implementation requires authentication. You are recommended to configure pap or chap authentication on both physical and dialer interfaces on both callback client and server. ...
Page 172
172 c hapter 6: dcc c onfiguration service-type ppp command. You need to select either approach with the dialer callback-center command. You need to configure callback client usernames with the dialer route command, so that the callback server can authenticate whether a callback client is valid when...
Page 173
Dcc configuration 173 configuring ppp callback in the rs-dcc implementation configuring ppp callback in rs-dcc involves configuring ppp callback client and configuring ppp callback server. 1 configure ppp callback client in the rs-dcc implementation as a callback client, your router can place calls ...
Page 174
174 c hapter 6: dcc c onfiguration n to leave enough time for a server to call back, the interval between two calls on the client need to be at least 10 seconds longer than that of the server. It is recommended that the interval on the server be set to 5 seconds (the default) and that on the client ...
Page 175
Dcc configuration 175 configuring isdn caller identification callback with c-dcc configuring isdn caller identification callback with c-dcc involves configuring the server end and the client end. 1 configure the client of isdn caller identification callback follow these steps to configure the client...
Page 176
176 c hapter 6: dcc c onfiguration configuring isdn caller identification callback with rs-dcc configuring isdn caller identification callback with rs-dcc involves configuring the server end and the client end. 1 configure the client of isdn caller identification callback follow these steps to confi...
Page 177
Dcc configuration 177 after completing c-dcc configurations, follow these steps to configure isdn leased line: isdn bri interfaces support both 64 kbps and 128 kbps leased lines. For more information, refer to “configuring isdn bri” on page 422 . Configuring auto-dial auto-dial can be used with c-dc...
Page 178
178 c hapter 6: dcc c onfiguration configuring dcc timers and buffer queue length c-dcc and rs-dcc are available with some optional parameters. You may configure them appropriately to improve on-demand dial efficiency. This section covers these topics: ■ “dcc timers and buffer queue length” on page ...
Page 179
Displaying and maintaining dcc 179 configuration procedure follow these steps to configure dcc timers and buffer queue length on a dial interface: configuring traffic statistics interval follow these steps to configure traffic statistics interval for dcc: displaying and maintaining dcc dcc configura...
Page 180
180 c hapter 6: dcc c onfiguration ■ “router-to-pc callback with dcc” on page 198 ■ “nt server-to-router callback with dcc” on page 200 ■ “circular dial string backup and internet access with dcc” on page 202 c-dcc application network requirements on a network segment are located three routers: rout...
Page 181
Dcc configuration example 181 [routera] interface serial 2/1 [routera-serial2/1] physical-mode async [routera-serial2/1] async mode protocol [routera-serial2/1] dialer circular-group 0 [routera-serial2/1] quit # set interface serial 1/0 to work in asynchronous protocol mode and assign it to dialer c...
Page 182
182 c hapter 6: dcc c onfiguration # set interface serial 2/0 to work in asynchronous protocol mode. [routerc] interface serial 2/0 [routerc-serial2/0] physical-mode async [routerc-serial2/0] async mode protocol # assign an ip address to interface serial 2/0, associate dialer access group 1 with the...
Page 183
Dcc configuration example 183 configuration procedure 1 configure router a # configure a dial access control rule for dialer access group 1; create local user accounts userb and userc for router b and router c and configure ppp authentication for them. System-view [routera] dialer-rule 1 ip permit [...
Page 184
184 c hapter 6: dcc c onfiguration [routera] interface serial 2/0 [routera-serial2/0] physical-mode async [routera-serial2/0] async mode protocol [routera-serial2/0] dialer bundle-member 1 [routera-serial2/0] dialer bundle-member 2 [routera-serial2/0] link-protocol ppp [routera-serial2/0] ppp authen...
Page 185
Dcc configuration example 185 [routerb-dialer0] ppp pap local-user userb password simple userb [routerb-dialer0] quit # set interface serial 2/0 to work in asynchronous protocol mode, configure information for ppp authentication, and assign the interface to dialer bundle 1. [routerb] interface seria...
Page 186
186 c hapter 6: dcc c onfiguration [routerc-serial2/0] ppp pap local-user userc password simple userc [routerc-serial2/0] quit # configure the user-interface to be used and enable modem dialup on it. [routerc] user-interface tty1 [routerc-ui-tty1] modem both dcc application on isdn network requireme...
Page 187
Dcc configuration example 187 figure 25 network diagram for rs-dcc application on isdn configuration procedure solution 1: use c-dcc to set up connection via isdn bri or pri and configure dcc parameters on physical interfaces. 1 configure router a # configure a dial access control rule for dialer ac...
Page 188
188 c hapter 6: dcc c onfiguration system-view [routerc] dialer-rule 1 ip permit # assign an ip address to interface bri 1/0, enable c-dcc, and configure the dial string for calling router a. [routerc] interface bri 1/0 [routerc-bri1/0] ip address 100.1.1.3 255.255.255.0 [routerc-bri1/0] dialer enab...
Page 189
Dcc configuration example 189 # configure information for ppp authentication and the dial strings on interface dialer1. [routera-dialer1] dialer-group 1 [routera-dialer1] ppp authentication-mode pap [routera-dialer1] ppp pap local-user usera password simple usera [routera-dialer1] dialer number 8810...
Page 190
190 c hapter 6: dcc c onfiguration # configure a dial access control rule for dialer access group 2; create a local user account usera for router a and configure ppp authentication for it. System-view [routerc] dialer-rule 1 ip permit [routerc] local-user usera [routerc-luser-usera] password simple ...
Page 191
Dcc configuration example 191 network diagram figure 26 network for a dcc application with mp configuration procedure 1 configure router a # configure a dial access control rule for dialer access group 1; create a local user account userb for router b and configure ppp authentication for it; and set...
Page 192
192 c hapter 6: dcc c onfiguration [routera-bri1/1] link-protocol ppp [routera-bri1/1] ppp authentication-mode pap [routera-bri1/1] ppp pap local-user usera password simple usera # configure ppp authentication on bri 1/0 and assign it to dialer bundle 1. [routera-bri1/0] interface bri 1/0 [routera-b...
Page 193
Dcc configuration example 193 ■ on router a, the b2 channel on interface bri 1/0 is connected to the b1 channel on interface bri 1/0 on router c to provide a leased line, whereas the b1 channel is connected to router b through dialup. ■ interface bri 1/0 on router a is assigned the ip address of 100...
Page 194
194 c hapter 6: dcc c onfiguration [routerc-bri1/0] dialer enable-circular [routerc-bri1/0] dialer isdn-leased 1 router-to-router callback with dcc (ppp approach) network requirements figure 28 presents a scenario where: ■ router a and router b are interconnected via serial interfaces across pstn. ■...
Page 195
Dcc configuration example 195 [routera] user-interface tty1 [routera-ui-tty1] modem both 2 configure router b # configure a dial access control rule for dialer access group 2; and create a local user account usera for router a and configure ppp authentication for it. System-view [routerb] dialer-rul...
Page 196
196 c hapter 6: dcc c onfiguration [routera-serial2/0] physical-mode async [routera-serial2/0] async mode protocol [routera-serial2/0] dialer enable-circular [routera-serial2/0] dialer-group 1 [routera-serial2/0] dialer route ip 100.1.1.2 8810052 [routera-serial2/0] link-protocol ppp [routera-serial...
Page 197
Dcc configuration example 197 [routerb] user-interface tty2 [routerb-ui-tty2] modem both router-to-router callback with dcc (isdn approach) network requirements figure 29 presents a scenario where: ■ router a and router b are interconnected via isdn bri interfaces across an isdn network. ■ interface...
Page 198
198 c hapter 6: dcc c onfiguration [routerb-bri1/0] dialer-group 2 [routerb-bri1/0] dialer route ip 100.1.1.1 8810048 # enable the local end to place return calls for isdn calling number 8810048. [routerb-bri1/0] dialer call-in 8810048 callback router-to-pc callback with dcc network requirements fig...
Page 199
Dcc configuration example 199 # assign a name to your new connection and follow the instruction to complete the connection setup. # in the [network and dial-up connections] window, right-click on the connection just created, and in the popup menu select the properties option. # in the properties set...
Page 200
200 c hapter 6: dcc c onfiguration [router-serial2/0] link-protocol ppp [router-serial2/0] ppp authentication-mode pap [router-serial2/0] ppp pap local-user sysname password simple sysname # configure the interface to assign an ip address to the remote end. [router-serial2/0] remote address 100.1.1....
Page 201
Dcc configuration example 201 system-view [router] dialer-rule 1 ip permit [router] local-user usernt [router-luser-userc] password simple usernt [router-luser-userc] service-type ppp [router-luser-userc] quit # configure physical layer parameters for interface serial 2/0. [router] interface serial ...
Page 202
202 c hapter 6: dcc c onfiguration # in the [network connection type] dialog, select the accept incoming connections option, and click to set the device for incoming connections. Click . The [incoming virtual private connection] window appears. # select the allow virtual private connections option i...
Page 203
Dcc configuration example 203 same as those of router a and router b, except that router d uses an isdn dial string 8810048, rather than pstn dial strings, to provide services. Configure router c and router d to implement dcc with one dial string and use chap for authentication. Network diagram figu...
Page 204
204 c hapter 6: dcc c onfiguration system-view [routera] dialer-rule 1 ip permit [routera] local-user userb [routera-luser-userb] password simple userb [routera-luser-userb] service-type ppp [routera-luser-userb] quit # configure physical layer parameters for interface serial 2/0 and enable ppp addr...
Page 205
Dcc configuration example 205 # assign an ip address to interface dialer0 and configure it to assign ip addresses for ppp users. [routerb] interface dialer 0 [routerb-dialer0] link-protocol ppp [routerb-dialer0] ppp authentication-mode pap [routerb-dialer0] ppp pap local-user userb password simple u...
Page 206
206 c hapter 6: dcc c onfiguration the make new connection icon; and in the popup menu select the new connection...Option. The [network connection wizard] window appears. Click . # in the [network connection type] dialog, select the dial-up to the internet option, and click . The [internet connectio...
Page 207
Dcc configuration example 207 [routerc-luser-userd] service-type ppp [routerc-luser-userd] quit # configure physical layer parameters for interface bri 1/0 and enable ppp address negotiation. [routerc] interface bri 1/0 [routerc-bri1/0] ip address ppp-negotiate # configure ppp encapsulation and ppp ...
Page 208
208 c hapter 6: dcc c onfiguration [routerd-serial2/0:15] ip address 100.1.1.254 255.255.255.0 # configure ppp encapsulation and other ppp parameters on the serial interface. [routerd-serial2/0:15] link-protocol ppp [routerd-serial2/0:15] ppp authentication-mode chap [routerd-serial2/0:15] ppp chap ...
Page 209
Troubleshooting 209 ■ use the debugging dialer event and debugging dialer packet commands to locate the problem..
Page 210
210 c hapter 6: dcc c onfiguration.
Page 211: Dls
7 dls w c onfiguration dlsw overview introduction data link switching (dlsw) was jointly developed by advanced peer-to-peer networking (appn) and implementers workshop (aiw) for transmitting systems network architecture (sna) traffic over a tcp/ip network. Sna was developed by ibm in correspondence ...
Page 212
212 c hapter 7: dls w c onfiguration network cost. In addition, dlsw v2.0 provides enhancements by means of udp explorer frames sent in multicast and unicast modes. When the peer is also running dlsw v2.0, the two ends can use udp packets to explore reachability, and a tcp connection is established ...
Page 213
Configuring dlsw in an ethernet environment 213 (depending on the specific situation). Using udp packets reduces, to some degree, the tcp connections required, and thereby saves network resources. ■ setting up a single tcp connection when required a tcp connection is set up after the origin and targ...
Page 214
214 c hapter 7: dls w c onfiguration for more information on bridge and bridge set configuration, refer to “bridging configuration” on page 405 . Creating dlsw peers establishing a tcp connection is the first step in establishing a dlsw circuit. To establish a tcp connection, you need to specify the...
Page 215
Configuring dlsw in an ethernet environment 215 removing a local dlsw peer will remove all its remote dlsw peers at the same time. Mapping a bridge set to dlsw dlsw was developed based on the bridging technology. Bridging between different ethernet interfaces is possible if these interfaces are conf...
Page 216
216 c hapter 7: dls w c onfiguration note that the timer values should be modified only when necessary. Configuring llc2 parameters sna was designed to transmit llc2 frames over ethernet. By means of llc2 related commands, you can modify some llc2 parameters. Follow these steps to configure llc2 par...
Page 217
Configuring dlsw in an ethernet environment 217 enabling the multicast function of dlsw v2.0 before enabling the multicast function of dlsw v2.0, you first need to configure the multicast function of the router and the local dlsw peer. Dlsw v2.0 multicast must be enabled before the origin dlsw v2.0 ...
Page 219
Configuring dlsw in an sdlc environment 219 configuring an sdlc interface the sdlc is a link layer protocol relative to the sna. Its working principle is similar to that of hdlc. In order to make dlsw work normally, you need to configure an sdlc interface by specifying sdlc as the link layer protoco...
Page 220
220 c hapter 7: dls w c onfiguration dominant role and controls the whole connection process. The secondary station, whose role is secondary, is controlled by the primary station. Therefore, we need to configure a role for an sdlc interface. In the sdlc role configuration, the role of an interface s...
Page 221
Configuring dlsw in an sdlc environment 221 configuring an sdlc peer the following command is used to specify the mac address of the corresponding peer end for an sdlc virtual circuit so as to provide the destination mac address for sdlc-to-llc2 frame conversion. In dlsw configuration, a peer should...
Page 222
222 c hapter 7: dls w c onfiguration configuring an sdlc virtual mac address initially designed for llc2 protocols, dlsw establishes mappings with virtual circuits through mac addresses. Therefore, a mac address must be specified for an sdlc virtual circuit so that sdlc frames can be forwarded. Use ...
Page 223
Configuring dlsw in an sdlc environment 223 generally it is not required to change the idle-time encoding scheme of a synchronous serial interface, except when the synchronous serial interface is connected to an as/400 device. Configuring optional sdlc parameters follow these steps to configure opti...
Page 224
224 c hapter 7: dls w c onfiguration n a sap address refers to the address of one or more applications running on a computer or network device. Configuring local reachable mac or sap addresses to reduce the exploring time before the routers send information frames when network topology is stable, yo...
Page 225
Displaying and debugging dlsw 225 displaying and debugging dlsw dlsw configuration examples configuring lan-to-lan dlsw network requirements as illustrated in figure 36 , dlsw works in a lan-lan environment. Configure dlsw on router a and router b to enable communication between an ibm host with an ...
Page 226
226 c hapter 7: dls w c onfiguration configuration procedure 1 configure router a: # configure interface parameters on router a to ensure that the local dlsw peer 1.1.1.1 and remote peer 2.2.2.2 are pingable to each other (specific configuration steps omitted). # configure dlsw on router a. System-v...
Page 227
Dlsw configuration examples 227 network diagram figure 37 network diagram for sdlc-to-sdlc dlsw configuration configuration procedure 1 configure router a: # configure interface parameters on router a to ensure that the local dlsw peer 1.1.1.1 and remote peer 2.2.2.2 are pingable to each other (spec...
Page 228
228 c hapter 7: dls w c onfiguration [routerb-serial2/0] baudrate 9600 [routerb-serial2/0] code nrzi after this step, the sdlc lans across the wan are interconnected. Configuring dlsw for sdlc-lan remote media translation network requirements as shown in figure 38 , host a and host b are pu2.0 nodes...
Page 229
Dlsw configuration examples 229 system-view [routerb] dlsw local 2.2.2.2 [routerb] dlsw remote 1.1.1.1 [routerb] interface serial 2/0 [routerb-serial2/0] link-protocol sdlc [routerb-serial2/0] sdlc enable dlsw [routerb-serial2/0] sdlc status primary [routerb-serial2/0] sdlc mac-map local 0000-1234-5...
Page 230
230 c hapter 7: dls w c onfiguration network diagram figure 39 network diagram for dlsw configuration with vlan support configuration procedure 1 configure router a # configure interface parameters on router a to ensure that the local dlsw peer 1.1.1.1 and remote peer 2.2.2.2 are pingable to each ot...
Page 231
Dlsw configuration examples 231 [routerb-ethernet1/1] ip address 2.2.2.2 255.255.255.0 [routerb-ethernet1/1] quit [routerb] rip [routerb-rip-1] network 2.0.0.0 [routerb-rip-1] network 1.0.0.0 [routerb-rip-1] quit 3 configure lsw # create vlan 2, and assign ethernet 1/1 to it. System-view [lsw] vlan ...
Page 232
232 c hapter 7: dls w c onfiguration [routera] interface ethernet 1/1 [routera-ethernet1/1] bridge-set 1 [routera-ethernet1/1] quit # enable multicast. [routera] multicast routing-enable [routera] interface ethernet 1/0 [routera-ethernet1/0] pim dm [routera-ethernet1/0] igmp enable [routera-ethernet...
Page 233
Troubleshooting dlsw 233 segment. After both sides have established a correct route, the tcp connection can be created. Unable to establish a dlsw circuit symptom a dlsw circuit cannot be correctly established. The display dlsw circuit command shows that the virtual circuit cannot come into connecte...
Page 234
234 c hapter 7: dls w c onfiguration.
Page 235: Rame
8 f rame r elay c onfiguration when configuring frame relay, go to these sections for information you are interested in: ■ “frame relay terminologies” on page 235 ■ “frame relay configuration task list” on page 238 ■ “configuring dte side frame relay” on page 238 ■ “configuring dce side frame relay”...
Page 236
236 c hapter 8: f rame r elay c onfiguration svcs, which are automatically created and deleted by frame relay protocol. At present, the most frequently used in frame relay is the pvc mode, that is., manually configured virtual circuit. In the pvc mode, the availability of the virtual circuit should ...
Page 237
Frame relay terminologies 237 a dte sends a status-enquiry message at a certain interval to query the link status. The dce responds with a status response message upon receiving the message. If the dte does not receive any response within a specified time, it will record this error. If the number of...
Page 238
238 c hapter 8: f rame r elay c onfiguration frame relay configuration task list complete the following tasks to configure frame relay: configuring dte side frame relay configuring basic dte side frame relay follow these steps to configure dte side frame relay: task remarks “configuring dte side fra...
Page 239
Configuring dte side frame relay 239 configuring frame relay address mapping this section covers these topics: ■ “overview” on page 235 ■ “configuration procedure” on page 239 overview frame relay address mapping can be configured statically or set up dynamically. ■ static configuration means the ma...
Page 240
240 c hapter 8: f rame r elay c onfiguration ■ “configuration procedure” on page 239 overview when the frame relay interface type is dce or nni, the interface (either main interface or subinterface) must be manually configured with virtual circuits. When the frame relay interface type is dte, for th...
Page 241
Configuring dte side frame relay 241 configuring frame relay subinterface this section covers these topics: ■ “overview” on page 235 ■ “configuration procedure” on page 239 overview the frame relay module has two types of interfaces: main interface and subinterface. The subinterface is of logical st...
Page 242
242 c hapter 8: f rame r elay c onfiguration the methods to configure virtual circuit and address map for p2p subinterfaces and p2mp subinterfaces are different, as described below. ■ p2p subinterface since there is only one peer address for a p2p subinterface, the peer address is determined when a ...
Page 243
Configuring dte side frame relay 243 figure 42 typical implementation diagram of frame relay over ip the frame relay packets transmitted through gre tunnel fall into three categories: fr packet and inarp packet, both of which have ip header encapsulated, and lmi packet used to negotiate virtual circ...
Page 244
244 c hapter 8: f rame r elay c onfiguration frame relay routing table of the router. In one route entry, the ingress interface is tunnel interface and the egress interface is frame relay interface. In the other route entry, the ingress interface is frame relay interface and the egress interface is ...
Page 245
Configuring dce side frame relay 245 c caution: ■ with fr address mapping configured in fr interface view, packets destined for the destination are transmitted through specific dlci. With x.25 address mapping configured in x.25 template view, a call to the specific x.25 address is launched before a ...
Page 246
246 c hapter 8: f rame r elay c onfiguration configuring frame relay address mapping refer to “configuring frame relay address mapping” on page 239 . Configuring frame relay local virtual circuit refer to “configuring frame relay local virtual circuit” on page 239 . Configuring frame relay switching...
Page 247
Frame relay configuration example 247 frame relay configuration example this section provides these examples: ■ “interconnecting lans through frame relay network” on page 247 ■ “interconnecting lans through dedicated line” on page 249 interconnecting lans through frame relay network network requirem...
Page 248
248 c hapter 8: f rame r elay c onfiguration network diagram figure 43 network diagram for connecting lans through a frame relay network configuration procedure 1 configure router a: # assign an ip address to serial 2/0 interface. System-view [routera] interface serial 2/0 [routera-serial2/0] ip add...
Page 249
Frame relay configuration example 249 # otherwise, configure static address mapping. [routerb-serial2/0] fr map ip 202.38.163.251 70 3 configure router c: # assign an ip address. System-view [routerc] interface serial 2/0 [routerc-serial2/0] ip address 202.38.163.253 255.255.255.0 # configure interf...
Page 250
250 c hapter 8: f rame r elay c onfiguration 2 configure router b: # assign an ip address. System-view [routerb] interface serial 2/0 [routerb-serial2/0] ip address 202.38.163.252 255.255.255.0 # set the link layer protocol on the interface to frame relay. [routerb-serial2/0] link-protocol fr [route...
Page 251
Frame relay configuration example 251 network diagram figure 45 network diagram for interconnecting lans through an annex g dlci configuration procedure 1 configure router a: # create an x.25 template. System-view [routera] x25 template vofr # configure the local x.25 address. [routera-x25-vofr] x25...
Page 252
252 c hapter 8: f rame r elay c onfiguration system-view [routerb] x25 template vofr # configure the local x.25 address. [routerb-x25-vofr] x25 x121-address 20094 # configure the x.25 address mapping to the destination ip address. [routerb-x25-vofr] x25 map ip 202.38.163.251 10094 [routerb-x25-vofr]...
Page 253
Frame relay compression 253 ■ ensure that both local device and remote device have been encapsulated with frame relay protocol. ■ if two devices are directly connected, check the local device and remote device to ensure that one end is configured as frame relay dte interface and the other end as fra...
Page 254
254 c hapter 8: f rame r elay c onfiguration frf.20 frf.20 compresses the ip header of packets transmitted over frame relay. For example, you may use it to compress voice packets to save bandwidth, decrease load, and improve transmission efficiency on a frame relay network. Frf.20 classifies packets...
Page 255
Frame relay compression 255 displaying and maintaining frame relay compression frame relay compression configuration example network requirements router a and router b are connected through the frame relay network and frame relay compression function (frf.9) is enabled between them. Network diagram ...
Page 256
256 c hapter 8: f rame r elay c onfiguration system-view [routerb] interface serial 2/0 [routerb-serial2/0] link-protocol fr [routerb-serial2/0] ip address 10.110.40.2 255.255.255.0 [routerb-serial2/0] fr interface-type dte [routerb-serial2/0] fr map ip 10.110.40.1 100 compression frf9.
Page 257: Ultilink
9 m ultilink f rame r elay this section covers these topics: ■ “overview” on page 235 ■ “configuring multilink frame relay” on page 258 ■ “displaying and maintaining multilink frame relay” on page 259 ■ “multilink frame relay configuration examples” on page 259 ■ “mfr switched connection configurati...
Page 258
258 c hapter 9: m ultilink f rame r elay mfr interface and physical interface an mfr interface is a kind of logic interface. Multiple physical interfaces can be bundled into one mfr interface. One mfr interface corresponds to one bundle and one physical interface corresponds to one bundle link. The ...
Page 259
Displaying and maintaining multilink frame relay 259 displaying and maintaining multilink frame relay multilink frame relay configuration examples mfr direct connection configuration example network requirements router a and router b are directly connected through serial 2/0 and serial 2/1. The fram...
Page 260
260 c hapter 9: m ultilink f rame r elay network diagram figure 48 network diagram of mfr direct connection configuration procedure 1 configure router a # create and configure mfr interface 4 (mfr4) system-view [routera] interface mfr 4 [router‘a-mfr4] ip address 10.140.10.1 255.255.255.0 [routera-m...
Page 261
Multilink frame relay configuration examples 261 network diagram figure 49 network diagram for mfr switching configuration procedure 1 configure router a # configure interface mfr1 system-view [routera] interface mfr 1 [routera-mfr1] ip address 1.1.1.1 255.0.0.0 [routera-mfr1] quit # add serial 2/0 ...
Page 262
262 c hapter 9: m ultilink f rame r elay [routerb-serial2/1] link-protocol fr mfr 1 [routerb-serial2/1] quit # add serial 2/2 and serial 2/3 to interface mfr2 [routerb] interface serial 2/2 [routerb-serial2/2] link-protocol fr mfr 2 [routerb-serial 2/2] quit [routerb] interface serial 2/3 [routerb-s...
Page 263: Ppp
10 ppp o fr this section covers these topics: ■ “overview” on page 235 ■ “configuring pppofr” on page 263 ■ “displaying and maintaining pppofr” on page 263 ■ “pppofr configuration example” on page 264 overview ppp over frame relay (pppofr) enables routers to establish end-to-end ppp sessions on a fr...
Page 264
264 c hapter 10: ppp o fr pppofr configuration example network requirements router a and router b connect through frame relay network, and enable pppofr between them. Network diagram figure 50 network diagram of pppofr configuration procedure 1 configure router a # create and configure virtual templ...
Page 265
11 mp o fr this section covers these topics: ■ “overview” on page 235 ■ “configuring mpofr” on page 265 ■ “mpofr configuration example” on page 266 overview multilink ppp over frame relay (mpofr) is pppofr making use of mp fragments to transmit mp fragments over frame relay stations. In mpofr config...
Page 266
266 c hapter 11: mp o fr c caution: ■ to ensure packet transmission quality over virtual-template (vt) interfaces, you can configure queue-independent qos features on vt interface and queue-dependent qos features on fr interface. For detailed information, refer to “qos overview” on page 1623 . ■ as ...
Page 267
Mpofr configuration example 267 to ensure voice quality, it is required to fragment the data packets to reduce voice jitter caused by transmission delay. Mpofr is adopted here, and mp is used to fragment data packets. Network diagram figure 51 net work diagram for mpofr implementation configuration ...
Page 268
268 c hapter 11: mp o fr [routera] traffic behavior liuliang [routera-behavior-liuliang] queue af bandwidth 20 [routera-behavior-liuliang] quit # configure class dial. [routera] traffic classifier dial [routera-classifier-dial] if-match acl 3002 [routera-classifier-dial] quit # configure class dial ...
Page 269
Mpofr configuration example 269 # enable real-time queue and policy on the interface to prevent interface congestion [routera-serial2/0] qos apply policy liuliang outbound [routera-serial2/0] qos rtpq start-port 16384 end-port 32767 bandwid th 20 cbs 1500 2 configure router b # configure acl rule sy...
Page 270
270 c hapter 11: mp o fr [routerb] interface virtual-template 2 [routerb-virtual-template2] ppp mp virtual-template 3 [routerb-virtual-template2] quit # create and configure virtual template interface virtual-template 3 [routerb] interface virtual-template 3 [routerb-virtual-template3] ppp mp lfi [r...
Page 271: Gvrp C
12 gvrp c onfiguration garp vlan registration protocol (gvrp) is a “garp” on page 271 application. It functions based on the operating mechanism of garp to maintain and propagate dynamic vlan registration information for the gvrp devices on the network. When configuring gvrp, go to these sections fo...
Page 272
272 c hapter 12: gvrp c onfiguration ■ a garp participant uses join messages to have its attributes registered on other devices. A garp participant also sends join messages to register attributes on other garp participants when it receives join messages from other garp participants or static attribu...
Page 273
Introduction to gvrp 273 n ■ the settings of garp timers apply to all garp applications, such as gvrp, on a lan. ■ unlike other three timers, which are set on a port basis, the leaveall timer is set in system view and takes effect globally. ■ a garp application entity may send leaveall messages at t...
Page 274
274 c hapter 12: gvrp c onfiguration gvrp gvrp enables a device to propagate local vlan registration information to other participant devices and dynamically update the vlan registration information from other devices to its local database about active vlan members and through which port they can be...
Page 275
Configuring gvrp 275 configuring gvrp n gvrp can only be configured at the trunk port. Gvrp configuration is broken down into: configuring gvrp functions and configuring garp timers. Configuring gvrp functions follow these steps to configure gvrp functions on a trunk port: configuring garp timers fo...
Page 276
276 c hapter 12: gvrp c onfiguration ■ the setting of each timer must be a multiple of five (in centiseconds). ■ the settings of the timers are correlated. If you fail to set a timer to a certain value, you can try to adjust the settings of the rest timers. Table 3 shows the relationship between the...
Page 277
Gvrp configuration example 277 # configure port ethernet 1/0 as a trunk port, allowing all vlans to pass. [devicea] interface ethernet 1/0 [devicea-ethernet1/0] port link-type trunk [devicea-ethernet1/0] port trunk permit vlan all # enable gvrp on ethernet 1/0, the trunk port. [devicea-ethernet1/0] ...
Page 278
278 c hapter 12: gvrp c onfiguration network diagram figure 54 network diagram for gvrp configuration configuration procedure 1 configure device a # enable gvrp globally. System-view [devicea] gvrp # configure port ethernet 1/0 as a trunk port, allowing all vlans to pass. [devicea] interface etherne...
Page 279
Gvrp configuration example 279 # display dynamic vlan information on device a. [devicea] display vlan dynamic no dynamic vlans exist! # display dynamic vlan information on device b. [deviceb] display vlan dynamic now, the following dynamic vlan exist(s): 2 gvrp configuration example iii network requ...
Page 280
280 c hapter 12: gvrp c onfiguration system-view [deviceb] gvrp # configure port ethernet 1/1 as a trunk port, allowing all vlans to pass. [deviceb] interface ethernet 1/1 [deviceb-ethernet1/1] port link-type trunk [deviceb-ethernet1/1] port trunk permit vlan all # enable gvrp on ethernet 1/1. [devi...
Page 281: Hdlc C
13 hdlc c onfiguration when configuring hdlc, go to these sections for information you are interested in: ■ “introduction to hdlc” on page 281 ■ “configuring hdlc” on page 282 introduction to hdlc hdlc overview high-level data link control (hdlc) is a bit-oriented link layer protocol. Its most promi...
Page 282
282 c hapter 13: hdlc c onfiguration ■ the checksum field can use a 16-bit crc to check the content of a frame. Configuring hdlc follow these steps to configure hdlc protocol: to do... Use the command... Remarks enter system view system-view - enter interface view interface interface-type interface-...
Page 283: X.25
14 x.25 and lapb c onfiguration when configuring lapb and x.25, go to these sections for information you are interested in: ■ “introduction to x.25 and lapb protocols” on page 283 ■ “configuring lapb” on page 285 ■ “configuring x.25” on page 286 ■ “x.25 pad remote access service” on page 305 ■ “conf...
Page 284
284 c hapter 14: x.25 and lapb c onfiguration figure 56 x.25 network model the x.25 protocol defines the lowest three layers of the osi (open system interconnection) reference model. As shown in the following figure, layer 3 (packet layer) provision of x.25 describes the packet format used by the pa...
Page 285
Configuring lapb 285 established between dte and dce by x.25 layer 2 (lapb) is multiplexed by x.25 layer 3, and those finally presented to users are several usable virtual circuits. The relation between packets and frames in the x.25 layers is shown in the following diagram. Figure 58 x.25 packet an...
Page 286
286 c hapter 14: x.25 and lapb c onfiguration configuring x.25 configuring x.25 interface parameters x.121 address if the device is used for x.25 switching, this task can be skipped. If it is connected to x.25 public packet network, you must set an x.121 address for the connected x.25 interface acco...
Page 287
Configuring x.25 287 x.25, and their numbers range from 1 to 4095. The number used to differentiate each virtual circuit (or logic channel) is called logic channel identifier (lci) or virtual circuit number (vcn). N strictly speaking, vc and lc are different. However, at the user end, they are gener...
Page 288
288 c hapter 14: x.25 and lapb c onfiguration for the meanings of these six parameters, refer to table 4 . Each range (except pvc range) is defined by two parameters respectively working as the upper limit and lower limit. The parameters are in the range of 1 to 4095 (including 1 and 4095), but they...
Page 289
Configuring x.25 289 cannot perform traffic control effectively and correctly unless correctly configured. Any inappropriate configuration will cause clear and reset events of x.25. As most public x.25 packet networks use the default window size and maximum packet size specified in itu-t x.25 recomm...
Page 290
290 c hapter 14: x.25 and lapb c onfiguration configuring x.25 interface supplementary parameters it is necessary to configure certain supplementary x.25 parameters in some special network environments. The section is related to these supplementary parameters. X.25 layer 3 delay timer x.25 protocol ...
Page 291
Configuring x.25 291 to meet the requirements of different networks, x.25 defines nine match types and their relevant alias string formats, as shown in the following table. 2 attributes related to the address code block in calling or called packets as defined in the x.25 protocol, a call packet must...
Page 292
292 c hapter 14: x.25 and lapb c onfiguration configuration procedure to configure x.25 interface supplementary parameters, use the following commands: configuring x.25 datagram transmission in the most frequently used x.25 service, data is transmitted between two hosts using the x.25 protocol throu...
Page 293
Configuring x.25 293 figure 61 interconnecting lans via x.25 lan 1 and lan 2 communicate with each other by sending the datagrams carrying internet protocol (ip) addresses. However, x.25 uses the x.121 address. Therefore, to solve the problem, the mapping between ip address and x.121 address needs t...
Page 294
294 c hapter 14: x.25 and lapb c onfiguration n ■ since the default two-way channel range: ltc=1, htc=1024 does not support pvc configuration, you need to specify a vc range using the x25 vc-range command to create a pvc. ■ if a pvc has no related parameters configured, its traffic control parameter...
Page 295
Configuring x.25 295 specify the maximum number of svcs allowed to associate with the same address mapping you can specify the maximum number of svcs allowed to set up for the same address mapping. Be default, an x.25 address mapping can only be associated with one vc. In case of busy traffic and sl...
Page 296
296 c hapter 14: x.25 and lapb c onfiguration for information about input window size, refer to “traffic control parameters” on page 288 . Configure x.25 user facility x.25 stipulates various user facilities, you can select and configure them. These configurations can be modified in two ways: ■ x.25...
Page 297
Configuring x.25 297 2 address-mapping-based configuration for cug configuration, refer to “configuring x.25 closed user group” on page 303 . Configure the data queue length of vc you can specify the sending and receiving queue lengths of vc for x.25 to adapt to different network environments. The d...
Page 298
298 c hapter 14: x.25 and lapb c onfiguration broadcast via x.25 generally, internetworking protocols will need to send some broadcast datagrams for specific purposes. On the broadcasting physical networks (such as ethernet), such requirements are naturally supported. However, for non-broadcasting n...
Page 299
Configuring x.25 299 configuring x.25 subinterface x.25 subinterface is a virtual interface that has its protocol address and vc. On a physical interface, you can create multiple subinterfaces to implement the interconnections of multiple networks through a physical interface. All subinterfaces unde...
Page 300
300 c hapter 14: x.25 and lapb c onfiguration enabling/disabling x.25 switching only affects call establishment, and not affects the established links. The switching routes can be configured after x.25 switching enabled. If you disable the switching (using undo x25 switching command) after configuri...
Page 301
Configuring x.25 301 vc-number). Different calls will be distributed on various lines in hunt group to implement load sharing. Note that x.25 hunt group selects different transmission lines only during vc call establishment. Once the whole vc completes the establishment and enters data transfer phas...
Page 302
302 c hapter 14: x.25 and lapb c onfiguration x.25 hunt group supports two call channel selection policies: round-robin mode and vc-number mode. However, a hunt group only uses one policy. ■ the round-robin mode uses a cyclic selection method to select next interface or xot channel inside hunt group...
Page 303
Configuring x.25 303 ■ a hunt group can have 10 synchronous serial interfaces, annex g dlci or xot channels at most. ■ xot channel cannot be added to the hunt group that uses vc-number channel selection policy. Configuring x.25 closed user group overview closed user group (cug) is a call restriction...
Page 304
304 c hapter 14: x.25 and lapb c onfiguration only of those incoming calls matching the mapping specified as preference rule, but lets other incoming calls with cug facilities pass through. The details are: 1 incoming suppression policy, in which the system lets the incoming calls without cug facili...
Page 305
X.25 pad remote access service 305 n the x25 cug-service and x25 local-cug commands are supported only on the x.25 dce interface, that is, you need to specify the interface as dce when encapsulating x.25 protocol on the serial interface. X.25 pad remote access service introduction to x.25 pad packet...
Page 306
306 c hapter 14: x.25 and lapb c onfiguration x.25 pad facilities are thus regarded procedures translators or network servers, helping different terminals access x.25 networks. The system implements x.29 and x.3 protocols in the x.25 pad protocol suite. In addition, it implements x.29-based telnet. ...
Page 307
Configuring x.25 over tcp (xot) 307 troubleshooting x.25 pad symptom: failed to log onto a remote device after placing an x.25 pad call to the remote device. The system prompted the destination address was unreachable. Solution: check that: ■ the two ends of the x.25 pad call are connected through a...
Page 308
308 c hapter 14: x.25 and lapb c onfiguration at present, since ip network is used widely, it is necessary, in practice, to carry x.25 data and implement the interconnection between x.25 networks via ip network. The traditional x.25 protocol belongs to layer 3 (network layer) of osi 7-layer model, a...
Page 309
Configuring x.25 over tcp (xot) 309 n ■ in svc mode, x.25 routes are required. ■ since the default two-way channel range: ltc=1, htc=1024 does not support pvc configuration, you need to specify a vc range using the x25 vc-range command to create a pvc. ■ for ip address configuration, refer to “ip ad...
Page 310
310 c hapter 14: x.25 and lapb c onfiguration to configure xot optional attributes, use the following commands: configuring x.25 over fr introduction to x.25 over fr x.25 over fr carries x.25 packets over fr to interconnect two x.25 networks across an fr network, as shown in the following figure. Fi...
Page 311
Configuring x.25 over fr 311 configuring svc application of x.25 over fr x.25 over fr is an extension to x.25 switching, so you need enable x.25 switch first. To configure svc application of x.25 over fr, use the following commands: configuring pvc application of x.25 over fr x.25 over fr is an exte...
Page 312
312 c hapter 14: x.25 and lapb c onfiguration configuring x2t introduction x.25 to tcp switch (x2t) connects x.25 to tcp/ip networks, allowing the access between x.25 and ip hosts. Figure 69 network diagram for x2t the x.25 terminal has an x.121 address to the ip host. Whenever the router receives a...
Page 313
Configuring x2t 313 destination ip address of the x2t route. After that, the router will extract the pure data from the x.25 packet and send them to the ip host through the tcp connection. The ip host can go through the ip address on the interface of the ip network to access the x.25 host. Whenever ...
Page 314
314 c hapter 14: x.25 and lapb c onfiguration displaying and maintaining lapb and x.25 lapb configuration example network requirements two routers are directly connected back to back via serial interfaces encapsulated with lapb that can transmit ip datagrams directly. Network diagram figure 70 direc...
Page 315
Lapb configuration example 315 system-view [routera] interface serial 2/0 # assign an ip address for the interface. [routera-serial2/0] ip address 10.1.1.2 255.0.0.0 # configure the link layer protocol of the interface as lapb, and specify it to work in dte mode. [routera -serial2/0] link-protocol l...
Page 316
316 c hapter 14: x.25 and lapb c onfiguration x.25 configuration examples direct connection of two routers via serial interfaces (one mapping) network requirements as shown in the following figure, two routers are directly connected; ip packets can be transmitted between serial interfaces over x.25 ...
Page 317
X.25 configuration examples 317 # assign an ip address for the interface. [routerb-serial2/0] ip address 202.38.60.2 255.255.255.0 # configure the link layer protocol of the interface as x.25, and specify it to operate in dce mode. [routerb-serial2/0] link-protocol x25 dce #assign an x.121 address f...
Page 318
318 c hapter 14: x.25 and lapb c onfiguration [routera-serial2/0] link-protocol x25 dte # assign an x.121 address for the interface. [routera-serial2/0] x25 x121-address 20112451 # configure address mappings to the peer. [routera-serial2/0] x25 map ip 202.38.161.2 x121-address 20112452 [routera-seri...
Page 319
X.25 configuration examples 319 connecting the router to x.25 public packet network network requirements as shown in the following figure, routers a, b, and c are connected to the same x.25 network. The requirements are: ■ the ip addresses of the interfaces serial 2/0 of the three routers are 168.17...
Page 320
320 c hapter 14: x.25 and lapb c onfiguration 2 configure router b # assign an ip address for the interface. System-view [routerb] interface serial 2/0 [routerb-serial2/0] ip address 168.173.24.2 255.255.255.0 # access public packet network, and configure the router to operate in dte mode. [routerb-...
Page 321
X.25 configuration examples 321 ■ it is required to exchange route information between lan 1 and lan 2 using rip, so that host a and host b can exchange information without any static route. Network diagram figure 74 carry ip datagrams over x.25 pvc configuration procedure 1 configure router a # con...
Page 322
322 c hapter 14: x.25 and lapb c onfiguration # configure interface ethernet 1/0. System-view [routerb] interface ethernet 1/0 [routerb-ethernet1/0] ip address 196.25.231.1 255.255.255.0 [routerb-ethernet1/0] quit # configure interface serial 2/0. [routerb] interface serial 2/0 [routerb-serial2/0] i...
Page 323
X.25 configuration examples 323 x.25 subinterface configuration example network requirements in the following figure, router a is configured with two subinterfaces, which are connected with router b and router c. Router d operates as an x.25 switch. It is desired that router a can communicate with r...
Page 324
324 c hapter 14: x.25 and lapb c onfiguration 4 configure router d as an x.25 switch system-view [routerd] interface serial 2/0 [routerd-serial2/0] link-protocol x25 dce [routerd-serial2/0] quit [routerd] interface serial 2/1 [routerd-serial2/1] link-protocol x25 dce [routerd-serial2/1] quit [router...
Page 325
X.25 configuration examples 325 system-view [routerd] interface serial 2/0 [routerd-serial2/0] link-protocol x25 dte ietf [routerd-serial2/0] x25 x121-address 2 [routerd-serial2/0] x25 map ip 1.1.1.1 x121-address 1 [routerd-serial2/0] ip address 1.1.1.2 255.0.0.0 3 configure router b # enable x.25 s...
Page 326
326 c hapter 14: x.25 and lapb c onfiguration [routerc] interface ethernet 1/0 [routerc-ethernet1/0] ip address 10.1.1.2 255.0.0.0 pvc application of xot network requirements router b and router c are connected through ethernet interfaces. Set up a tcp connection between them to deliver data between...
Page 327
X.25 configuration examples 327 [routerb] interface serial 2/0 [routerb-serial2/0] link-protocol x25 dce ietf [routerb-serial2/0] x25 vc-range in-channel 10 20 bi-channel 30 1024 [routerb-serial2/0] x25 xot pvc 1 10.1.1.2 interface serial 2/0 pvc 2 # configure ethernet 1/0. [routerb] interface ether...
Page 328
328 c hapter 14: x.25 and lapb c onfiguration [routera-serial2/0] link-protocol x25 dte [routera-serial2/0] x25 x121-address 1 [routera-serial2/0] x25 map ip 1.1.1.2 x121-address 2 [routera-serial2/0] ip address 1.1.1.1 255.0.0.0 2 configure router d # configure x.25 basic functions. System-view [ro...
Page 329
X.25 configuration examples 329 # configure serial 2/1 as fr interface. [routerc] interface serial 2/1 [routerc-serial2/1] link-protocol fr # configure the fr annex g dlci. [routerc-serial2/1] fr dlci 100 [routerc-fr-dlci-serial2/1-100] annexg dte # configure x.25 local switching. [routerc] x25 swit...
Page 330
330 c hapter 14: x.25 and lapb c onfiguration system-view [routerd] interface serial 2/0 [routerd-serial2/0] link-protocol x25 dte [routerd-serial2/0] x25 x121-address 2 [routerd-serial2/0] x25 vc-range bi-channel 10 20 [routerd-serial2/0] x25 pvc 1 ip 1.1.1.1 x121-address 1 [routerd-serial2/0] ip a...
Page 331
X.25 configuration examples 331 # configure an x.25 template. [routerc] x25 template switch [routerc-x25-switch] x25 vc-range bi-channel 10 20 # configure the pvc switching route for the template. [routerc-x25-switch] x25 switch pvc 1 interface serial 2/0 pvc 1 # configure fr interface serial 2/1. [...
Page 332
332 c hapter 14: x.25 and lapb c onfiguration network diagram figure 81 network diagram for typical x.25 hunt group configuration configuration procedure 1 configure router a # configure the link layer protocol of the interface serial 2/0 as x.25, and configure it to operate in dce mode. System-view...
Page 333
X.25 configuration examples 333 # enable x.25 switching. [routera] x25 switching # create x.25 hunt group hg1. [routera] x25 hunt-group hg1 round-robin # add interfaces serial 2/2, serial 2/1, and xot channel to the hunt group. [routera-hg-hg1] channel interface serial 2/2 [routera-hg-hg1] channel i...
Page 334
334 c hapter 14: x.25 and lapb c onfiguration [routerc-fr-dlci-serial2/0-100] x25-template vofr 4 configure router e. # configure the link layer protocol on serial 2/0 as x.25 and configure it to operate in dte mode. System-view [routere] interface serial 2/0 [routere-serial2/0] link-protocol x25 dt...
Page 335
X.25 configuration examples 335 network diagram figure 82 transmit ip data over x.25 hunt group configuration procedure in this example, since the network providers have configured load sharing on the packet switch, you only need to configure x.25 switching. Note that there have been two lines conne...
Page 336
336 c hapter 14: x.25 and lapb c onfiguration [routerb] interface serial 2/0 [routerb-serial2/0] link-protocol x25 dte [routerb-serial2/0] x25 x121-address 2222 [routerb-serial2/0] ip address 1.1.1.2 255.255.255.0 [routerb-serial2/0] x25 map ip 1.1.1.3 x121-address 3333 [routerb-serial2/0] x25 vc-pe...
Page 337
X.25 configuration examples 337 network diagram figure 83 network diagram for tcp/ip header compression protocol application configuration procedure 1 configure routera # configure the link layer protocol of serial 2/0 as x.25, and configure the interface to operate in dte mode. System-view [routera...
Page 338
338 c hapter 14: x.25 and lapb c onfiguration x.25 pad configuration example network requirements as shown in the following figure, router a is connected to router b through an x.25 network. It is required that router b could place x.25 pad calls to log onto router a and then configure router a. Net...
Page 339
X2t configuration example 339 # assign an x.121 address for the interface. [routerb-serial2/0] x25 x121-address 2 [routerb-serial2/0] quit [routerb] quit # place an x.25 pad call to router a. Pad 1 trying 1...Open username:pad1 password:pad1 x2t configuration example x2t svc configuration example ne...
Page 340
340 c hapter 14: x.25 and lapb c onfiguration # configure an x2t route. [router] translate ip 10.1.1.1 port 102 x25 2222 [router] translate x25 1111 ip 10.1.1.2 port 102 x2t pvc configuration example network requirements the router connects x.25 and ip networks together. In this connection, the x.25...
Page 341
Troubleshooting x.25 configuration 341 troubleshooting enable the debugging on both sides. If one side sends sabm frames and the other sends frmr frames cyclically, the two sides are working in the same mode (dte or dce). Change the working mode of one side to solve it. Failed to ping the other side...
Page 342
342 c hapter 14: x.25 and lapb c onfiguration continuous resets and clears of the vc established symptom the virtual circuit can be set up, but is frequently reset or cleared during data transmission. Analysis the symptom may be caused by erroneous flow control parameter settings. Troubleshooting ■ ...
Page 343
Troubleshooting x.25 configuration 343 analysis the physical status and protocol status of the interface are not up, or the pvc/xot configuration is not correct. Troubleshooting ■ first check whether the physical connection status and protocol status of the interface are up. ■ if the interface statu...
Page 344
344 c hapter 14: x.25 and lapb c onfiguration.
Page 345: Ink
15 l ink a ggregation o verview n link aggregation is not supported on msr 20 series routers. It is only supported on interfaces of 16fsw/24fsw modules of msr 30/msr 50 series routers. Link aggregation aggregates multiple physical ethernet ports into one logical link, also called a logical group, to...
Page 346
346 c hapter 15: l ink a ggregation o verview consistency considerations for ports in an aggregation to participate in traffic sharing, member ports in an aggregation must use the same configurations with respect to stp, qos, gvrp, vlan, port attributes, mac address learning, and so on, as shown in ...
Page 347
Approaches to link aggregation 347 manual link aggregation overview in the manual aggregation approach, aggregation groups are created administratively. On the ports in a manual aggregation group, lacp is disabled. Port states in a manual aggregation in a manual aggregation group, ports are either s...
Page 348
348 c hapter 15: l ink a ggregation o verview when the configuration of some port in a manual aggregation group changes, the system does not remove the aggregation; instead, it re-sets the selected/unselected state of the member ports and re-selects a master port. Static lacp link aggregation overvi...
Page 349
Load sharing in a link aggregation group 349 you need to maintain the basic configurations of these ports manually to ensure consistency. As one configuration change may involve multiple ports, this can become troublesome if you need to do that port by port. As a solution, you may add the ports to a...
Page 350
350 c hapter 15: l ink a ggregation o verview.
Page 351: Ink
16 l ink a ggregation c onfiguration this chapter covers these topics: ■ “configuring link aggregation” on page 351 ■ “displaying and maintaining link aggregation” on page 353 ■ “link aggregation configuration example” on page 353 configuring link aggregation when configuring link aggregation, go to...
Page 352
352 c hapter 16: l ink a ggregation c onfiguration ■ to guarantee a successful aggregation, ensure that the ports at the two ends of each link to be aggregated are consistent in selected/unselected state. Configuring a static lacp link aggregation group follow these steps to configure a static aggre...
Page 353
Displaying and maintaining link aggregation 353 entering aggregation port group view in aggregation port group view, you can make configuration for all the member ports in a link aggregation group at one time. Follow these steps to enter aggregation port group view: c caution: in aggregation port gr...
Page 354
354 c hapter 16: l ink a ggregation c onfiguration network diagram figure 87 network diagram for link aggregation configuration procedure n this example only describes how to configure link aggregation on device a. To achieve link aggregation, do the same on device b. 1 in manual aggregation approac...
Page 355: Odem
17 m odem c onfiguration when configuring modem, go to these sections for information you are interested in: ■ “overview” on page 355 ■ “modem configuration” on page 355 ■ “modem configuration example” on page 356 ■ “troubleshooting” on page 357 overview modem is a network device that is widely used...
Page 356
356 c hapter 17: m odem c onfiguration configuring the modem answer mode you need to configure the modem answer mode depending on the answer state of the connected external modem. When the modem is in auto-answer mode (aa led of the modem lights), configure the modem auto-answer command to prevent t...
Page 357
Troubleshooting 357 2.2.2.2/16, your device can automatically dial to the remote end through dcc for data transmission, as shown in the network diagram. For more information about dcc dialup, refer to “dcc configuration” on page 153 . Network diagram figure 88 network of the configuration for the ro...
Page 358
358 c hapter 17: m odem c onfiguration.
Page 359: Ort
18 p ort m irroring c onfiguration when configuring port mirroring, go to these sections for information you are interested in: ■ “port mirroring overview” on page 359 ■ “configuring local port mirroring” on page 360 ■ “displaying and maintaining port mirroring” on page 361 ■ “examples of typical po...
Page 360
360 c hapter 18: p ort m irroring c onfiguration configuring local port mirroring follow these steps to configure local port mirroring: n ■ a local mirroring group is effective only when it has both source ports and the destination port configured. ■ layer 2 ethernet ports, layer 3 ethernet interfac...
Page 361
Displaying and maintaining port mirroring 361 group. In this case, you need to remove the port mirroring group and then create another one. ■ only layer 2 ports support port mirroring. Displaying and maintaining port mirroring follow these steps to display and maintain port mirroring: examples of ty...
Page 362
362 c hapter 18: p ort m irroring c onfiguration system-view # create a local port mirroring group. [devicec] mirroring-group 1 local # add port ethernet 1/1 and ethernet 1/2 to the port mirroring group as source ports. Add port ethernet 1/3 to the port mirroring group as the destination port. [devi...
Page 363: Ppp
19 ppp and mp c onfiguration this document is organized as follows: ■ “ppp and mp configuration” on page 363 ■ “pppoe configuration” on page 393 when configuring ppp and mp, go to these sections for information you are interested in: ■ “introduction to ppp and mp” on page 363 ■ “configuring ppp” on ...
Page 364
364 c hapter 19: ppp and mp c onfiguration figure 91 pap authentication during pap authentication, the password is transmitted on the link in plain text. In addition, the authenticatee sends the username and the password repeatedly through the established ppp link until the authentication is over. S...
Page 365
Introduction to ppp and mp 365 figure 92 chap authentication operating mechanism of ppp ppp operates in the following procedure: 1 enter the establish phase before setting up a ppp link 2 perform lcp negotiation in the establish phase, which includes the operating mode (sp or mp), the authentication...
Page 366
366 c hapter 19: ppp and mp c onfiguration for the details of ppp, refer to rfc 1661. Mp multilink ppp (mp) provides an approach to increasing bandwidth. It allows multiple ppp links to form an mp bundle. After receiving a packet, mp segments (if the packet is large) the packet into fragments and di...
Page 367
Configuring ppp 367 ■ increase bandwidth, or dynamically increase/reduce bandwidth in combination with dial control center (dcc) ■ load sharing ■ backup ■ decrease transmission delay through fragmentation mp can work on any physical or virtual interfaces encapsulated with ppp, such as serial, isdn b...
Page 368
368 c hapter 19: ppp and mp c onfiguration n this chapter only discusses local authentication. For information about the remote aaa authentication, refer to “aaa/radius/hwtacacs configuration” on page 1751 . Configuring the local device to authenticate the peer using pap follow these steps to config...
Page 369
Configuring ppp 369 n for detailed description on how to create a local user and configure its attributes, and how to create a domain and configure its attributes, refer to “configuring local user attributes” on page 1767 . Configuring the local device to be authenticated by the peer using pap follo...
Page 370
370 c hapter 19: ppp and mp c onfiguration configuring ppp negotiation introduction to ppp negotiation parameters ppp negotiation parameters include: timeout interval negotiation, ip address negotiation and dns address negotiation. Timeout interval negotiation: in ppp negotiation, if, during the tim...
Page 371
Configuring ppp 371 configuring ip address negotiation follow these steps to configure ip address negotiation: 1 configuring the device as client follow these steps to configure the device as client: 2 configuring the device as server follow these steps to configure the device as server for ppp user...
Page 372
372 c hapter 19: ppp and mp c onfiguration follow the following steps to configure the device as server for ppp users that need authentication: note that the domain used in defining the pool address is the domain specified when performing ppp authentication. Configuring dns address negotiation follo...
Page 373
Configuring ppp 373 configuring ppp link quality control introduction to ppp link quality control ppp link quality control (lqc) can monitor the real-time quality of ppp links (including those in mp bundles). A link goes down when its quality drops below the close percentage and goes up when its qua...
Page 374
374 c hapter 19: ppp and mp c onfiguration enabling the ppp accounting statistics function following these steps to enable the ppp accounting statistics function: configuring mp configuring mp using a vt interface introduction when configuring mp via vt interface, you can do one of the following: ■ ...
Page 375
Configuring mp 375 configuring other optional parameters follow these steps to configure other optional parameters: to do... Use the command... Remarks enter system view system-view - create and enter vt interface interface virtual-template number required exit to system view quit - associate a phys...
Page 376
376 c hapter 19: ppp and mp c onfiguration n ■ after you have configured the ppp mp max-bind command or the ppp mp min-bind command, you must shutdown and then undo shutdown all the relevant physical interfaces before the modification takes effect. ■ when mp binding is only based on descriptors, use...
Page 377
Configuring ppp link efficiency mechanism 377 (including ip, udp, and rtp) headers or tcp headers. The following describes how compression operates by taking rtp header compression as an example. The real-time transport protocol (rtp) is virtually a udp protocol using fixed port number and format. T...
Page 378
378 c hapter 19: ppp and mp c onfiguration cause block and delay, consequently, the remote end cannot hear continuous speech. It is required by the interactive voice that the end-to-end delay cannot be larger than 100-150 ms. Dispatching a large packet of 1500 bytes through a 56-kbps line, perhaps w...
Page 379
Displaying and maintaining ppp/mp/ppp link efficiency mechanism 379 displaying and maintaining ppp/mp/ppp link efficiency mechanism enable stac-lzs compression on the interface ppp compression stac-lzs optional disabled by default currently, outbound expedite forwarding is not applicable on links wi...
Page 380
380 c hapter 19: ppp and mp c onfiguration ppp and mp configuration example pap authentication example network requirements as shown in figure 96 , router a and router b are interconnected through the interface serial 2/0, and router a is required to authenticate router b using pap. Network diagram ...
Page 381
Ppp and mp configuration example 381 [routera-serial2/0] ppp authentication-mode chap domain system [routera-serial2/0] ip address 200.1.1.1 16 [routera-serial2/0] quit [routera]domain system [routera-isp-system] authentication ppp local 2 configure router b. System-view [routerb] local-user user1 [...
Page 382
382 c hapter 19: ppp and mp c onfiguration ■ adopt binding authentication. Network diagram figure 97 network diagram for mp configuration configuration procedure 1 configure router a: # add the users for router b and router c system-view [routera] local-user router-b [routera-luser-router-b] passwor...
Page 383
Ppp and mp configuration example 383 [routera] domain system [routera-isp-system] authentication ppp local 2 configure router b: # add a user for router a system-view [routerb] local-user router-a [routerb-luser-router-a] password simple router-a [routerb-luser-router-a] quit # specify the virtual-t...
Page 384
384 c hapter 19: ppp and mp c onfiguration # configure the users in the domain to use the local authentication scheme. [routerc] domain system [routerc-isp-system] authentication ppp local three types of mp binding mode network requirements as showed in the figure below, router a and router b are co...
Page 385
Ppp and mp configuration example 385 [routera-serial2/0] ppp mp virtual-template 1 [routera-serial2/0] shutdown [routera-serial2/0] undo shutdown [routera-serial2/0] quit [routera] domain system [routera-isp-system] authentication ppp local [routera-isp-system] quit configure router b: # configure t...
Page 386
386 c hapter 19: ppp and mp c onfiguration 0 lost fragments, 0 reordered, 0 unassigned, 0 interleaved, sequence 0/0 rcvd/sent the bundled member channels are: serial2/1 serial2/0 check information about virtual access interfaces: [routera] display virtual-access ----------------slot 1---------------...
Page 387
Ppp and mp configuration example 387 system-view [routera] local-user rtb [routera-luser-rtb] password simple rtb [routera-luser-rtb] service-type ppp [routera-luser-rtb] quit # assign a virtual-template to user rtb [routera] ppp mp user rtb bind virtual-template 1 # create a virtual-template and co...
Page 388
388 c hapter 19: ppp and mp c onfiguration # create a virtual-template and configure the ip address [routerb] interface virtual-template 1 [routerb-virtual-template1] ip address 8.1.1.2 24 [routerb-virtual-template1] ppp mp binding authentication [routerb-virtual-template1] quit # configure serial 2...
Page 389
Ppp and mp configuration example 389 # check information about virtual access interfaces: [routerb] display virtual-access virtual-template1:0 current state : up line protocol current state : up description : virtual-template1:0 interface the maximum transmit unit is 1500 link layer protocol is ppp ...
Page 390
390 c hapter 19: ppp and mp c onfiguration [routera] interface mp-group 1 [routera-mp-group1] ip address 111.1.1.1 24 # configure serial 2/1. [routera-mp-group1] interface serial 2/1 [routera-serial2/1] link-protocol ppp [routera-serial2/1] ppp authentication-mode pap domain system [routera-serial2/...
Page 391
Ppp and mp configuration example 391 # configure serial 2/0. [routerb] interface serial 2/0 [routerb-serial2/0] link-protocol ppp [routerb-serial2/0] ppp authentication-mode pap domain system [routerb-serial2/0] ppp pap local-user rtb password simple rtb [routerb-serial2/0] ppp mp mp-group 1 [router...
Page 392
392 c hapter 19: ppp and mp c onfiguration 0.00% packet loss round-trip min/avg/max = 29/29/31 ms note that in this approach to mp binding, all users are bound together and the concept of virtual access is not involved. Troubleshooting ppp configuration symptom 1: link never turns into up state. Sol...
Page 393: Ppp
20 ppp o e c onfiguration when configuring pppoe, go to these sections for information you are interested in: ■ “introduction to pppoe” on page 393 ■ “configuring pppoe server” on page 394 ■ “configuring pppoe client” on page 395 ■ “displaying and maintaining pppoe” on page 397 ■ “pppoe configuratio...
Page 394
394 c hapter 20: ppp o e c onfiguration ■ dynamic ip address allocation. ■ multiple authentication methods such as local authentication and radius/tacacs+. Along with aspf and packet filter, it provides strong defense for your network. Pppoe server is applicable to campus networks where ethernet is ...
Page 395
Configuring pppoe client 395 n for a virtual template interface, if a static route is used, you are recommended to specify the next hop rather than the outgoing interface. If the outgoing interface must be specified, make sure that the physical interface bound in the virtual template is effective to...
Page 396
396 c hapter 20: ppp o e c onfiguration for more information on the configuration of pppoe session on virtual ethernet interface, refer to the relevant part of pppoeoa configuration in “atm and dsl interface configuration” on page 71 in access manual. Configuration procedure follow these steps to co...
Page 397
Displaying and maintaining pppoe 397 displaying and maintaining pppoe pppoe configuration example pppoe server configuration example network requirements in figure 100 , the hosts, acting as pppoe client, access the internet through the router. The router acts as the pppoe server, performing local a...
Page 398
398 c hapter 20: ppp o e c onfiguration system-view [sysname] local-user user1 [sysname-luser-user1] password simple pass1 [sysname-luser-user1] service-type ppp [sysname-luser-user1] quit # configure pppoe parameters on the router: [sysname] interface ethernet 1/0 [sysname-ethernet1/0] pppoe-server...
Page 399
Pppoe configuration example 399 configuration procedure 1 pap authentication: a configure router a as pppoe server # add a pppoe user. System-view [routera] local-user user2 [routera-luser-user2] password simple hello [routera-luser-user2] service-type ppp [routera-luser-user2] quit # configure the ...
Page 400
400 c hapter 20: ppp o e c onfiguration [routera-virtual-template1] ip address 1.1.1.1 255.0.0.0 [routera-virtual-template1] remote address 1.1.1.2 [routera-virtual-template1] quit # configure pppoe server. [routera] interface ethernet 1/0 [routera-ethernet1/0] pppoe-server bind virtual-template 1 b...
Page 401
Pppoe configuration example 401 network diagram figure 102 connect a lan to the internet through adsl configuration procedure 1 configure router a as pppoe client # configure the dialer interface. System-view [routera] dialer-rule 1 ip permit [routera] interface dialer 1 [routera-dialer1] dialer-gro...
Page 402
402 c hapter 20: ppp o e c onfiguration # add a pppoe user system-view [routerb] local-user user1 [routerb-luser-user1] password simple 123456 [routerb-luser-user1] service-type ppp [routerb-luser-user1] quit # configure the atm interface. [routerb] interface atm 1/0 [routerb-atm1/0] pvc 0/32 [route...
Page 403
Pppoe configuration example 403 using adsl as backup line network requirements the router is connected to the network center via ddn dedicated line and adsl, where the adsl is the backup of the ddn dedicated line. When a fault occurs to the ddn dedicated line, the router can still initiate a pppoe c...
Page 404
404 c hapter 20: ppp o e c onfiguration network diagram figure 104 accessing the internet through an adsl interface configuration procedure # configure a dialer interface system-view [router] dialer-rule 1 ip permit [router] interface dialer 1 [router-dialer1] dialer user mypppoe [router-dialer1] di...
Page 405: Ridging
21 b ridging c onfiguration when configuring bridging functionalities, go to the following sections for the information you are interested in: ■ “bridging overview” on page 405 ■ “bridging configuration task list” on page 409 ■ “displaying and maintaining bridging configurations” on page 412 ■ “tran...
Page 406
406 c hapter 21: b ridging c onfiguration segment, a bridge listens to all ethernet frames on the segments. When it receives an ethernet frame, it extracts the source mac address of the frame and creates a mapping entry between this mac address and the interface on which the ethernet frame was recei...
Page 407
Bridging overview 407 when host b responds to host b, the bridge also hears the ethernet frame from host b. As the frame is received on bridge interface 1, the bridge determines that host b is also attached to bridge interface 1, and creates a mapping between the mac address of host b and bridge int...
Page 408
408 c hapter 21: b ridging c onfiguration forwarding and filtering the bridge makes data forwarding or filtering decisions based on the following scenarios: ■ when host a sends an ethernet frame to host c, the bridge searches its bridge table and finds out that host c is attached to bridge interface...
Page 409
Bridging configuration task list 409 ■ when host a sends an ethernet frame to host c, if the bridge does not find a mac-to-interface mapping about host c in its bridge table, the bridge forwards the ethernet frame to all interfaces except the interface on which the frame was received, as shown in fi...
Page 410
410 c hapter 21: b ridging c onfiguration ■ when configuring transparent bridging over fr, you need to configure fr on the corresponding interface as the link layer protocol for interface encapsulation, configure the fr interface type (optional, dte by default) and configure a virtual circuit. When ...
Page 411
Configuring bridge table entries 411 configuring bridge table entries typically, a bridge dynamically creates and maintains a bridge table based on the correlations between the mac addresses it learned and the corresponding interfaces. The administrator, however, can manually configure some bridge t...
Page 412
412 c hapter 21: b ridging c onfiguration follow these steps to bridge routing: displaying and maintaining bridging configurations transparent bridging configuration examples transparent bridging over atm network requirements as shown in figure 112 , lan 1 and lan 2 are attached to router a and rout...
Page 413
Transparent bridging configuration examples 413 network diagram figure 112 network diagram for transparent bridging over atm configuration configuration procedure 1 configure router a [routera] bridge enable [routera] bridge 1 enable [routera] interface ethernet 1/0 [routera-ethernet1/0] bridge-set ...
Page 414
414 c hapter 21: b ridging c onfiguration [routera] interface ethernet 1/0 [routera-ethernet1/0] bridge-set 1 [routera-ethernet1/0] quit [routera] interface serial 2/0 [routera-serial2/0] link-protocol ppp [routera-serial2/0] bridge-set 1 2 configure router b system-view [routerb] bridge enable [rou...
Page 415
Transparent bridging configuration examples 415 [routerb] bridge 1 enable [routerb] interface virtual-template 1 [routerb-virtual-template1] bridge-set 1 [routerb-virtual-template1] quit [routerb] interface ethernet 1/0 [routerb-ethernet1/0] bridge-set 1 [routerb-ethernet1/0] quit [routerb] interfac...
Page 416
416 c hapter 21: b ridging c onfiguration [routerb-serial2/0] fr interface-type dte [routerb-serial2/0] bridge-set 1 [routerb-serial2/0] fr map bridge 50 broadcast transparent bridging x.25 network requirements as shown in figure 116 , lan 1 and lan 2 are attached to router a and router b respective...
Page 417
Transparent bridging configuration examples 417 network diagram figure 117 network diagram for transparent bridging over hdlc configuration configuration procedure 1 configure router a system-view [routera] bridge enable [routera] bridge 1 enable [routera] interface ethernet 1/0 [routera-ethernet1/0...
Page 418
418 c hapter 21: b ridging c onfiguration configuration procedure 1 configure router a [routera] bridge enable [routera] bridge 1 enable [routera] bridge 2 enable [routera] interface ethernet 1/0 [routera-ethernet1/0] bridge-set 1 [routera-ethernet1/0] quit [routera] interface ethernet 1/1 [routera-...
Page 419
Transparent bridging configuration examples 419 network diagram figure 119 network diagram for bridging with fr sub-interface support configuration procedure 1 configure router a system-view [routera] bridge enable [routera] bridge 1 enable [routera] bridge 2 enable [routera] interface ethernet 1/0 ...
Page 420
420 c hapter 21: b ridging c onfiguration [routerb-serial2/0] quit [routerb] interface serial 2/0.1 [routerb-serial2/0.1] fr dlci 50 [routerb-serial2/0.1] fr map bridge 50 broadcast [routerb-serial2/0.1] bridge-set 1 [routerb-serial2/0.1] quit [routerb] interface serial 2/0.2 [routerb-serial2/0.2] f...
Page 421: Isdn C
22 isdn c onfiguration when configuring isdn, go to these sections for information you are interested in: ■ “introduction to isdn” on page 421 ■ “configuring isdn” on page 422 ■ “displaying and maintaining isdn” on page 434 ■ “isdn configuration example” on page 434 ■ “troubleshooting” on page 441 i...
Page 422
422 c hapter 22: isdn c onfiguration (nippon telegraph and telephone corporation) in japan, etsi (european telecommunications standards institute) in europe, ni (national isdn), at&t 5ess, and ansi (american national standard institute) in north america. Besides the default dss1 isdn protocol, the r...
Page 423
Configuring isdn 423 configuring isdn pri follow these steps to configure isdn pri: set isdn protocol mode isdn protocol-mode mode optional an isdn bri interface operates in user mode by default. Currently, only bsv board can operate on the network side. Configure the negotiation parameters of isdn ...
Page 424
424 c hapter 22: isdn c onfiguration configuring the negotiation parameters of isdn layer 3 protocol follow these steps to configure the negotiation parameters of isdn layer 3 protocol: set isdn protocol mode isdn protocol-mode mode optional an isdn pri interface operates in user mode by default. Co...
Page 425
Configuring isdn 425 configure to disable isdn to carry the hlc information element in setup messages when placing voice calls isdn ignore hlc optional by default, hlc information element is carried in setup messages when placing voice call. Configure to disable isdn to carry the llc information ele...
Page 427
Configuring isdn 427 dss1 0 0 0 unknown 0 0 1 international number 0 1 0 national number 0 1 1 network specific number 1 0 0 subscriber number 1 1 0 abbreviated number 1 1 1 reserved for extension 0 0 0 0 unknown 0 0 0 1 isdn/telephony numbering plan (recommendation e.164) 0 0 1 1 data numbering pla...
Page 428
428 c hapter 22: isdn c onfiguration n the undefined bits in all the protocols are reserved for other purposes. Configuring the spid of the isdn ni protocol you may configure spid on the bri interfaces that are running the isdn ni protocol. Follow these steps to configure the spid parameters of the ...
Page 429
Configuring isdn 429 setting the called number or sub-address to be checked during a digital incoming call if a called number or subaddress is specified, the system will deny an incoming digital call if the calling party sends a wrong called number or subaddress or does not send at all. Follow these...
Page 430
430 c hapter 22: isdn c onfiguration setting the local management isdn b channel configured with isdn bch-local-manage command, the router operates in local b-channel management mode to select available b channels for calls. Despite this, the connected exchange has higher priority in b channel selec...
Page 431
Configuring isdn 431 configuring the sliding window size on the pri interface follow these steps to configure the size of the sliding window on the pri interface: configuring statistics about isdn message receiving/sending follow these steps to configure the statistics about isdn message receiving/s...
Page 432
432 c hapter 22: isdn c onfiguration configuring tei treatment on the bri interface follow these steps to configure tei treatment on the bri interface: configuring isdn bri leased line isdn leased lines are implemented by establishing mp semi-permanent connections. This requires that the pbxs of you...
Page 433
Configuring isdn 433 n on pri interfaces, q.921 layer negotiates to enter multi-framing state immediately after the user side and the network side connects correctly. On bri interfaces, however, the q.921 layer transits to the multi-framing state only after being triggered by a call and the q.921 li...
Page 434
434 c hapter 22: isdn c onfiguration n ■ the support for this function varies with device models. ■ this function is available to bsv interfaces operating in the network side mode. Currently, only bsv board can operate in the network side mode. For example, you can enable this function on a bsv inte...
Page 435
Isdn configuration example 435 network diagram figure 122 network diagram for isdn configuration configuration procedure 1 configure router a # create an isdn pri interface. System-view [routera] controller e1 1/0 [routera-e1 1/0] pri-set [routera-e1 1/0] quit # configure an isdn pri interface. [rou...
Page 436
436 c hapter 22: isdn c onfiguration network diagram figure 123 network diagram for isdn ni protocol configuration configuration procedure 1 configure router a # configure the dialing parameters on isdn bri interface. System-view [routera] interface bri 2/0 [routera-bri2/0] ip address 202.38.154.1 2...
Page 437
Isdn configuration example 437 network diagram figure 124 using isdn bri leased lines to implement mp bundling configuration procedure 1 configure router a. System-view [routera] interface bri2/0 [routera-bri2/0] link-protocol ppp [routera-bri2/0] ppp mp virtual-template 5 [routera-bri2/0] dialer en...
Page 438
438 c hapter 22: isdn c onfiguration configuring isdn 128k leased lines network requirements router a and router b are connected by connecting their isdn bri interfaces through a 128k leased line. Network diagram figure 125 network diagram for isdn 128k leased line connection configuration procedure...
Page 439
Isdn configuration example 439 0 broadcasts, 0 multicasts 2 errors, 0 runts, 0 giants, 2 crc, 0 align errors, 0 overruns, 0 dribbles, 0 aborts, 0 no buffers 0 frame errors output:0 packets, 0 bytes 0 errors, 0 underruns, 0 collisions 0 deferred display interface bri 2/0:1 bri2/0:1 current state :up ...
Page 440
440 c hapter 22: isdn c onfiguration as you can see, the state of interface bri 2/0:1 is up, its speed is 128 kbps, and channels (timeslots used) b1 and b2 are in use; the state of bri 2/0:2 is down, and the field of timeslots used is null. Interoperating with dms100 switches network requirements ro...
Page 441
Troubleshooting 441 [router-bri2/0] isdn spid service speech [router-bri2/0] quit # configure a dialer interface. [router] interface dialer 1 [router-dialer1] link-protocol ppp [router-dialer1] ppp pap local-user user password simple hello [router-dialer1] dialer threshold 0 in-out [router-dialer1] ...
Page 442
442 c hapter 22: isdn c onfiguration ■ check whether the dial-up configuration is correct. If dial-up is correctly configured and the maintaining information “q921 send data fail(l1 return failure).” is not output, isdn line may be not connected well..
Page 443: Mstp C
23 mstp c onfiguration when configuring mstp, go to these sections for information you are interested in: ■ “mstp overview” on page 443 ■ “configuring the root bridge” on page 459 ■ “configuring leaf nodes” on page 470 ■ “performing mcheck” on page 474 ■ “configuring protection functions” on page 47...
Page 444
444 c hapter 23: mstp c onfiguration basic concepts in stp 1 root bridge a tree network must have a root; hence the concept of “root bridge” has been introduced in stp. There is one and only one root bridge in the entire network, and the root bridge can change alone with changes of the network topol...
Page 445
Mstp overview 445 figure 127 a schematic diagram of designated bridges and designated ports n all the ports on the root bridge are designated ports. 4 path cost path cost is a reference value used for link selection in stp. By calculating the path cost, stp selects relatively “robust” links and bloc...
Page 446
446 c hapter 23: mstp c onfiguration upon initialization of a device, each port generates a bpdu with itself as the root bridge, in which the root path cost is 0, designated bridge id is the device id, and the designated port is the local port. ■ selection of the optimum configuration bpdu each devi...
Page 447
Mstp overview 447 n when the network topology is stable, only the root port and designated ports forward traffic, while other ports are all in the blocked state - they only receive stp packets but do not forward user traffic. Once the root bridge, the root port on each non-root bridge and designated...
Page 448
448 c hapter 23: mstp c onfiguration ■ initial state of each device the following table shows the initial state of each device. ■ comparison process and result on each device the following table shows the comparison process and result on each device. Table 13 initial state of each device device port...
Page 449
Mstp overview 449 device b ■ port bp1 receives the configuration bpdu of device a {0, 0, 0, ap1}. Device b finds that the received configuration bpdu is superior to the configuration bpdu of the local port {1, 0,1, bp1}, and updates the configuration bpdu of bp1. ■ port bp2 receives the configuratio...
Page 450
450 c hapter 23: mstp c onfiguration after the comparison processes described in the table above, a spanning tree with device a as the root bridge is stabilized, as shown in figure 129 . Device c ■ port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received ...
Page 451
Mstp overview 451 figure 129 the final computed spanning tree n to facilitate description, the spanning tree computing process in this example is simplified, while the actual process is more complicated. 2 the bpdu forwarding mechanism in stp ■ upon network initiation, every router regards itself as...
Page 452
452 c hapter 23: mstp c onfiguration change accordingly. However, the new configuration bpdu as the calculation result cannot be propagated throughout the network immediately. If the newly elected root port and designated ports start to forward data right away, a temporary loop is likely to occur. F...
Page 453
Mstp overview 453 ■ mstp supports mapping vlans to mst instances by means of a vlan-to-instance mapping table. Mstp can save communication overheads and resource usage by mapping multiple vlans to one mst instance. ■ mstp divides a switched network into multiple regions, each containing multiple spa...
Page 454
454 c hapter 23: mstp c onfiguration ■ the same vlan-to-instance mapping (vlan 1 is mapped to mst instance 1, vlan 2 to mst instance 2, and the rest to the command and internal spanning tree (cist). Cist refers to mst instance 0) ■ the same mstp revision level (not shown in the figure) multiple mst ...
Page 455
Mstp overview 455 the root bridge of the ist or an msti within an mst region is the regional root bridge of the mst or that msti. Based on the topology, different spanning trees in an mst region may have different regional roots. For example, in region d0 in figure 130 , the regional root of instanc...
Page 456
456 c hapter 23: mstp c onfiguration figure 131 port roles figure 131 helps understand these concepts. Where, ■ devices a, b, c, and d constitute an mst region. ■ port 1 and port 2 of device a connect to the common root bridge. ■ port 5 and port 6 of device c form a loop. ■ port 3 and port 4 of devi...
Page 457
Mstp overview 457 how mstp works mstp divides an entire layer 2 network into multiple mst regions, which are interconnected by a computed cst. Inside an mst region, multiple spanning trees are generated through computing, each spanning tree called an mst instance. Among these mst instances, instance...
Page 458
458 c hapter 23: mstp c onfiguration configuration task list before configuration, you need to know the position of each device in each mst instance: root bridge or leave node. In each instance, one, and only one device acts as the root bridge, while all others as leaf nodes. Task remarks “configuri...
Page 459
Configuring the root bridge 459 n if both gvrp and mstp are enabled on a device at the same time, gvrp packets will be forwarded along the cist. Therefore, if both gvrp and mstp are running on the same device and you wish to advertise a certain vlan within the network through gvrp, make sure that th...
Page 460
460 c hapter 23: mstp c onfiguration n two device belong to the same mst region only if they are configure to have the same mst region name, the same vlan-to-instance mapping entries in the mst region and the same mst region revision level, and they are interconnected via a physical link. The config...
Page 461
Configuring the root bridge 461 specifying the current device as the root bridge of a specific spanning tree follow these steps to specify the current device as the root bridge of a specific spanning tree: specifying the current device as a secondary root bridge of a specific spanning tree follow th...
Page 462
462 c hapter 23: mstp c onfiguration ■ alternatively, you can also specify the current device as the root bridge by setting by priority of the device to 0. For the device priority configuration, refer to “configuring the priority of the current device” on page 462 . Configuration example # specify t...
Page 463
Configuring the root bridge 463 c caution: ■ upon specifying the current device as the root bridge or a secondary root bridge, you cannot change the priority of the device. ■ during root bridge selection, if all devices in a spanning tree have the same priority, the one with the lowest mac address w...
Page 464
464 c hapter 23: mstp c onfiguration configuring the network diameter of a switched network any two stations in a switched network are interconnected through specific paths, which are composed of a series of devices. Represented by the number of devices on a path, the network diameter is the path th...
Page 465
Configuring the root bridge 465 forward delay time should be. Note that if the forward delay setting is too small, temporary redundant paths may be introduced; if the forward delay setting is too big, it may take a long time for the network to resume connectivity. We recommend that you use the defau...
Page 466
466 c hapter 23: mstp c onfiguration n ■ timeout time = timeout factor × 3 × hello time. ■ typically, we recommend that you set the timeout factor to 5, or 6, or 7 for a stable network. Configuration example # set the timeout factor to 6. System-view [sysname] stp timer-factor 6 configuring the maxi...
Page 467
Configuring the root bridge 467 configuring ports as edge ports if a port directly connects to a user terminal rather than another device or a shared lan segment, this port is regarded as an edge port. When a network topology change occurs, an edge port will not cause a temporary loop. Therefore, if...
Page 468
468 c hapter 23: mstp c onfiguration n ■ as for aggregated ports, all ports can be configured as connecting to point-to-point links. If a port works in auto-negotiation mode and the negotiation result is full duplex, this port can be configured as connecting to a point-to-point link. ■ if a port is ...
Page 469
Configuring the root bridge 469 n ■ in mstp mode, if a port is configured to recognize/send mstp packets in a mode other than auto, and if it receives a packet in the format different from the specified type, that port will become a designated port and remain in the discarding state to prevent the o...
Page 470
470 c hapter 23: mstp c onfiguration n ■ you must enable mstp for the device before any other mstp-related configuration can take effect. ■ to control mstp flexibly, you can use the stp disable or undo stp command to disable the mstp feature for certain ports so that they will not take part in spann...
Page 471
Configuring leaf nodes 471 instances. Setting an appropriate path cost allows vlan traffic flows to be forwarded along different physical links, thus to enable per-vlan load balancing. The device can automatically calculate the default path cost; alternatively, you can also configure the path cost f...
Page 472
472 c hapter 23: mstp c onfiguration n in the calculation of the path cost value of an aggregated link, 802.1d-1998 does not take into account the number of ports in the aggregated link. Whereas, 802.1t takes the number of ports in the aggregated link into account. The calculation formula is: path c...
Page 473
Configuring leaf nodes 473 configuring port priority the priority of a port is an import basis that determines whether the port can be elected as the root port of device. If all other conditions are the same, the port with the highest priority will be elected as the root port. On an mstp-compliant d...
Page 474
474 c hapter 23: mstp c onfiguration enabling output of port state transition information refer to “enabling the output of port state transition information” on page 469 . Enabling the mstp feature refer to “enabling the mstp feature” on page 469 . Performing mcheck ports on an mstp-compliant device...
Page 475
Configuring digest snooping 475 method 2: perform mcheck in ethernet interface view system-view [sysname] interface ethernet 1/0 [sysname-ethernet1/0] stp mcheck configuring digest snooping as defined in ieee 802.1s, interconnected devices are in the same region only when the region related configur...
Page 476
476 c hapter 23: mstp c onfiguration ■ with global digest snooping enabled, modification of vlan-to-instance mappings and removing of the current region configuration using the undo stp region-configuration command are not allowed. You can only modify the region name and revision level. ■ you need t...
Page 477
Configuring no agreement check 477 configuring no agreement check two types of packet are used for rapid state transition on designated rstp and mstp ports: ■ proposal: packets sent by designated ports to request rapid transition ■ agreement: packets used to acknowledge rapid transition requests bot...
Page 478
478 c hapter 23: mstp c onfiguration upstream device and thus sends no agreement packets to the upstream device. As a result, the designated port of the upstream device fails to transit rapidly and can only change to the forwarding state after a period twice the forward delay. In this case, you can ...
Page 479
Configuring protection functions 479 configuration procedure # enable no agreement check on ethernet 1/0 of device a. System-view [devicea] interface ethernet 1/0 [devicea-ethernet1/0] stp no-agreement-check configuring protection functions an mstp-compliant device supports the following protection ...
Page 480
480 c hapter 23: mstp c onfiguration the root bridge and secondary root bridge of a panning tree should be located in the same mst region. Especially for the cist, the root bridge and secondary root bridge are generally put in a high-bandwidth core region during network design. However, due to possi...
Page 481
Displaying and maintaining mstp 481 enabling tc-bpdu attack guard when receiving a tc-bpdu (a pdu used as notification of topology change), the device will delete the corresponding forwarding address entry. If someone forges tc-bpdus to attack the device, the device will receive a larger number of t...
Page 482
482 c hapter 23: mstp c onfiguration mstp configuration example network requirements configure mstp so that packets of different vlans are forwarded along different spanning trees. The specific configuration requirements are as follows: ■ all devices on the network are in the same mst regions. ■ pac...
Page 483
Mstp configuration example 483 n “permit:” beside each link in the figure is followed by the vlans the packets of which are permitted to pass this link. Configuration procedure 1 configuration on device a # enter mst region view. System-view [devicea] stp region-configuration [devicea-mst-region] re...
Page 484
484 c hapter 23: mstp c onfiguration # define device b as the root bridge of mst instance 3. [deviceb] stp instance 3 root primary # view the mst region configuration information that has taken effect. [deviceb] display stp region-configuration oper configuration format selector :0 region name :exam...
Page 485
Mstp configuration example 485 system-view [deviced] stp region-configuration [deviced-mst-region] region-name example [deviced-mst-region] instance 1 vlan 10 [deviced-mst-region] instance 3 vlan 30 [deviced-mst-region] instance 4 vlan 40 [deviced-mst-region] revision-level 0 # configure the region ...
Page 486
486 c hapter 23: mstp c onfiguration.
Page 487: Vlan C
24 vlan c onfiguration when configuring vlan, go to these sections for information you are interested in: ■ “introduction to vlan” on page 487 ■ “configuring basic vlan attributes” on page 489 ■ “configuring vlan interface basic attributes” on page 490 ■ “configuring a port-based vlan” on page 491 ■...
Page 488
488 c hapter 24: vlan c onfiguration a vlan is not restricted by physical factors, that is to say, hosts that reside in different network segments may belong to the same vlan, users in a vlan can be connected to the same switch, or span across multiple switches or routers. Vlan technology has the fo...
Page 489
Configuring basic vlan attributes 489 ■ the priority field, three bits in length, indicates the 802.1p priority of a packet. For information about packet priority, refer to “priority mapping” on page 1675 . ■ the cfi field, one bit in length, specifies whether or not the mac addresses are encapsulat...
Page 490
490 c hapter 24: vlan c onfiguration configuring vlan interface basic attributes hosts of different vlans cannot communicate directly. That is, routers or layer 3 switches are needed for packets to travel across different vlans. Vlan interfaces are used to forward vlan packets on layer 3. Vlan inter...
Page 491
Configuring a port-based vlan 491 n before creating a vlan interface, ensure that the corresponding vlan already exists. Otherwise, the specified vlan interface will not be created. Configuring a port-based vlan introduction to port-based vlan this is the simplest and yet the most effective way of c...
Page 492
492 c hapter 24: vlan c onfiguration configuring the access-port-based vlan there are two ways to configure access-port-based vlan: one way is to configure in vlan view, the other way is to configure in ethernet port view or port group view. Follow the following steps to configure the access-port-ba...
Page 493
Configuring a port-based vlan 493 n ■ ensure that you create a vlan first before trying to add an access port to the vlan. ■ refer to “aggregation port group” on page 349 for information about port group. Configuring the trunk-port-based vlan a trunk port may belong to multiple vlans, and you can on...
Page 494
494 c hapter 24: vlan c onfiguration configuring the hybrid-port-based vlan a hybrid port may belong to multiple vlans, and this configuration can only be performed in ethernet port view or port group view. Follow the following steps to configure the hybrid-port-based vlan: n ■ to configure a trunk ...
Page 495
Vlan configuration examples 495 vlan configuration examples network requirements ■ device a connects to device b through the trunk port ethernet 1/0; ■ the default vlan id of the port is 100; ■ this port allows packets from vlan 2, vlan 6 to vlan 50, and vlan 100 to pass through. Network diagram fig...
Page 496
496 c hapter 24: vlan c onfiguration display interface ethernet 1/0 ethernet1/0 current state: up ip packet frame type: pktfmt_ethnt_2, hardware address: 0000-5600-0000 description: ethernet1/0 interface loopback is not set unknown-speed mode, unknown-duplex mode link speed type is autonegotiation, ...
Page 497: Oice
25 v oice vlan c onfiguration when configuring voice vlan, go to these sections for information you are interested in: ■ “introduction to voice vlan” on page 497 ■ “configuring the voice vlan” on page 500 ■ “displaying and maintaining voice vlan” on page 501 ■ “voice vlan configuration examples” on ...
Page 498
498 c hapter 25: v oice vlan c onfiguration n ■ as the first 24 bits of a mac address (in binary format), an oui address is a globally unique identifier assigned to a vendor by ieee (institute of electrical and electronics engineers). ■ the default oui address can be configured/removed manually. Wor...
Page 499
Introduction to voice vlan 499 c caution: ■ if the voice traffic sent by an ip phone is tagged and that the access port has 802.1x authentication and guest vlan enabled, assign different vlan ids for the voice vlan, the default vlan of the access port, and the 802.1x guest vlan. ■ if the voice traff...
Page 500
500 c hapter 25: v oice vlan c onfiguration it is recommended that you do not mix voice packets with other types of data in a voice vlan. If necessary, please ensure that the security mode is disabled. Configuring the voice vlan configuration prerequisites ■ create the corresponding vlan before conf...
Page 501
Displaying and maintaining voice vlan 501 n ■ at the same time, only one vlan of a device can have the voice vlan feature enabled. ■ a port that has the link aggregation control protocol (lacp for short) enabled cannot have the voice vlan feature enabled at the same time. ■ a dynamic vlan becomes a ...
Page 502
502 c hapter 25: v oice vlan c onfiguration voice vlan configuration examples a configuration examples of the voice vlan under automatic mode network requirement ■ create vlan 2 and configure it as a voice vlan with an aging time of 100 minutes. ■ the voice traffic sent by the ip phones is tagged. C...
Page 503
Voice vlan configuration examples 503 [sysname] interface ethernet 1/1 [sysname-ethernet1/1] voice vlan mode auto # configure ethernet 1/1 as a hybrid port. [devicea-ethernet1/1] port link-type access please wait... Done. [devicea-ethernet1/1] port link-type hybrid # configure the default vlan of th...
Page 504
504 c hapter 25: v oice vlan c onfiguration ■ ethernet 1/1 works in manual mode. It only allows voice packets with an oui address of 0011-2200-0000, a mask of ffff-ff00-0000, and a descriptive string of “test” to be forwarded. Network diagram figure 142 voice vlan under manual mode configuration pro...
Page 505
Voice vlan configuration examples 505 [devicea-ethernet1/1] voice vlan enable verification # display information about the oui addresses, oui address masks, and descriptive strings. Display voice vlan oui oui address mask description 0001-e300-0000 ffff-ff00-0000 simens phone 0003-6b00-0000 ffff-ff0...
Page 506
506 c hapter 25: v oice vlan c onfiguration.
Page 507: Ort
26 p ort i solation c onfiguration when configuring port isolation, go to these sections for information you are interested in: ■ “introduction to port isolation” on page 507 ■ “configuring isolation groups” on page 507 ■ “displaying and maintaining isolation groups” on page 508 ■ “port isolation co...
Page 508
508 c hapter 26: p ort i solation c onfiguration n refer to “aggregation port group” on page 349 for information about port groups. Displaying and maintaining isolation groups port isolation configuration example networking requirement ■ users host a, host b, and host c are connected to ethernet 1/1...
Page 509
Port isolation configuration example 509 system-view [device] interface ethernet 1/1 [device-ethernet1/1] port-isolate enable [device-ethernet1/1] quit [device] interface ethernet 1/2 [device-ethernet1/2] port-isolate enable [device-ethernet1/2] quit [device] interface ethernet 1/3 [device-ethernet1...
Page 510
510 c hapter 26: p ort i solation c onfiguration.
Page 511: Ynamic
27 d ynamic r oute b ackup c onfiguration n currently, the dynamic route backup function is available to the following dialup interfaces: dialer interfaces, pri interfaces, bri interfaces, serial interfaces operating in the asynchronous mode, am interface, and aux interfaces. Overview concept as a n...
Page 512
512 c hapter 27: d ynamic r oute b ackup c onfiguration ■ allow a route to be learned by multiple links through configuring load balancing implementation through configuring the network segment to be monitored, a backup link can be enabled when the primary link fails. The dynamic route backup functi...
Page 513
Dynamic route backup configuration example 513 ■ refer to “dynamic route backup configuration” on page 511 for more information about the dialer route command. Enabling the dynamic route backup function on a backup interface n before enabling the dynamic route backup function on a backup interface, ...
Page 514
514 c hapter 27: d ynamic r oute b ackup c onfiguration network diagram figure 144 network diagram for dynamic route backup configuration configuration procedure 1 configure router a # configure a dialer rule. System-view [routera] dialer-rule 1 ip permit # configure dialup parameters for bri 3/0. [...
Page 515
Dynamic route backup configuration example 515 [routera] interface bri 3/0 [routera-bri3/0] rip metricin 2 # enable the dynamic route backup function. [routera-bri3/0] standby routing-group 1 2 configure router b # enable x.25 on router b. System-view [routerb] x25 switching # enable switching inter...
Page 516
516 c hapter 27: d ynamic r oute b ackup c onfiguration # configure the dynamic routing protocol rip. [routerc] rip [routerc-rip-1] network 10.0.0.0 [routerc-rip-1] network 20.0.0.0 [routerc-rip-1] network 30.0.0.0 [routerc-rip-1] import-route direct example ii network requirements ■ router a and ro...
Page 517
Dynamic route backup configuration example 517 [routera] interface serial 2/0 [routera-serial2/0] ip address 10.0.0.1 8 [routera-serial2/0] quit # configure the dynamic routing protocol ospf. [routera] ospf [routera-ospf-1] area 0 [routera-ospf-1-area-0.0.0.0] network 10.0.0.0 0.255.255.255 [routera...
Page 518
518 c hapter 27: d ynamic r oute b ackup c onfiguration [routerb] ospf [routerb-ospf-1] area 0 [routerb-ospf-1-area-0.0.0.0] network 10.0.0.0 0.255.255.255 [routerb-ospf-1-area-0.0.0.0] network 20.0.0.0 0.255.255.255 [routerb-ospf-1-area-0.0.0.0] network 40.0.0.0 0.0.0.0 [routerb-ospf-1-area-0.0.0.0...
Page 519
Dynamic route backup configuration example 519 [routera] interface dialer 0 [routera-dialer0] link-protocol ppp [routera-dialer0] ip address 20.0.0.1 24 [routera-dialer0] dialer user userb [routera-dialer0] dialer-group 1 [routera-dialer0] dialer bundle 1 [routera-dialer0] dialer number 8810052 [rou...
Page 520
520 c hapter 27: d ynamic r oute b ackup c onfiguration [routerb-dialer0] ip address 20.0.0.2 24 [routerb-dialer0] dialer user usera [routerb-dialer0] dialer-group 1 [routerb-dialer0] dialer bundle 1 [routerb-dialer0] dialer number 8810010 [routerb-dialer0] ppp authentication-mode pap [routerb-diale...
Page 521
Dynamic route backup configuration example 521 network diagram figure 147 network diagram for dynamic route backup configuration n this network diagram just illustrates a simple implementation. In real practice, the monitored network segments may be distributed on multiple devices. Configuration pro...
Page 522
522 c hapter 27: d ynamic r oute b ackup c onfiguration [routera-serial2/1:15] dialer-group 1 [routera-serial2/1:15] dialer route ip 10.0.0.0 mask 8 660220 [routera-serial2/1:15] standby routing-group 1 [routera-serial2/1:15] quit # configure the dynamic routing protocol rip. [routera] rip [routera-...
Page 523
Dynamic route backup configuration example 523 [routerb] interface ethernet 1/2 [routerb-ethernet1/2] ip address 12.0.0.1 255.0.0.0 [routerb-ethernet1/2] quit # configure the dynamic routing protocol rip. [routerb] rip [routerb-rip-1] network 1.0.0.0 [routerb-rip-1] network 2.0.0.0 [routerb-rip-1] n...
Page 524
524 c hapter 27: d ynamic r oute b ackup c onfiguration.
Page 525: Ogical
28 l ogical i nterface c onfiguration n this section introduces basic configurations about logical interfaces. For the configurations about the data link layer, network layer and some special features, refer to the relevant sections in the access volume and ip service volume. Logical interface overv...
Page 526
526 c hapter 28: l ogical i nterface c onfiguration authentication server/security server to permit/deny packets with a specific loopback interface address as their source ip addresses can permit/deny all the packets sourced from the corresponding device. In this way, the packet filtering rules are ...
Page 527
Sub-interface 527 sub-interface introduction to sub-interface sub-interfaces are logical virtual interfaces configured on a primary interface. The primary interface can be either a physical interface (such as a layer-3 ethernet interface) or a logical interface (such as an mfr interface). A sub-inte...
Page 528
528 c hapter 28: l ogical i nterface c onfiguration n ■ by default, no vlan is associated to sub-interfaces created by using the interface command. ■ ip parameters and ipx parameters can be configured on ethernet sub-interfaces. Refer to the “ip addressing configuration” on page 623 and “ipx configu...
Page 529
Sub-interface 529 2 configure relevant operation parameters on sub-interfaces of a wan interface with link-layer protocol being frame relay, you can configure: ■ frame relay address mapping different from the that of the wan interface (also known as the primary interface) ■ ip addresses in a network...
Page 530
530 c hapter 28: l ogical i nterface c onfiguration ■ x.25 address mapping different from that of the wan interface (also known as the primary interface) ■ ip addresses in a network segment different from the network segment that the wan interface resides ■ ipx network numbers and ipx operation para...
Page 531
Sub-interface 531 different switches but belonging to the same vlan can intercommunicate with each other. ■ work station a can intercommunicate with work station d, and work station b can intercommunicate with work station c, that is, devices connected to different switches and belonging to differen...
Page 532
532 c hapter 28: l ogical i nterface c onfiguration wan sub-interface configuration example network requirements ■ wan interface serial 1/0 of router a is connected to router b and router c through the public frame relay network. ■ allow lan 1 to access lan 2 and lan 3 at the same time through seria...
Page 533
Configuring mp-group interfaces 533 [sysname-serial1/0.1] fr dlci 50 [sysname-fr-dlci-serial1/0.1-50] quit [sysname-serial1/0.1] quit # create a point-to-point sub-interface serial 1/0.2 for serial 1/0. [sysname] interface serial 1/0.2 p2p # set the ip address of serial 1/0.2 to 202.38.161.1/24. [sy...
Page 534
534 c hapter 28: l ogical i nterface c onfiguration n refer to “configuring multilink frame relay” on page 258 for detailed information about mfr interface parameters. Vt and va interface introduction to vt and va interface a virtual template (vt) is a template used for configuring a virtual access ...
Page 535
Vt and va interface 535 n before removing a vt, make sure that all the virtual interfaces derived from the vt are removed and the vt is not being used. Configure vt operation parameters compared to normal physical interfaces, a vt supports only ppp on the link layer and ip on the network layer. You ...
Page 536
536 c hapter 28: l ogical i nterface c onfiguration troubleshooting before troubleshooting, you must determine the vt is used for creating virtual interfaces for vpn or mp. Then, you can locate the vt failures in a specified implementation. Symptom virtual interfaces cannot be created. Solution the ...
Page 537
Configuring ve 537 ■ the displaying and maintenance of a ve interface is similar to that of an ethernet interface. Refer to “maintaining and displaying an ethernet interface” on page 97 for the configuration procedure. ■ refer to “pppoe configuration” on page 393 for pppoeoa configuration..
Page 538
538 c hapter 28: l ogical i nterface c onfiguration.
Page 539: Cpos I
29 cpos i nterface c onfiguration when configuring atm/dsl interface, go to these sections for information you are interested in: ■ “overview” on page 539 ■ “configuring a cpos interface” on page 544 ■ “configuring an e1 channel” on page 545 ■ “configuring a t1 channel” on page 545 ■ “displaying and...
Page 540
540 c hapter 29: cpos i nterface c onfiguration sdh frame structure the frame structure of sdh signal stm-n is described in the following part. Low-speed tributary signals should distribute in one frame regularly and evenly for the convenience of adding/dropping them in high-speed signal. Itu-t spec...
Page 541
Overview 541 ■ administrative unit (au) and administrative unit group (aug): au is the information structure that provides adaptation between higher-order channel layer and multiplex section layer. Aug is a set of one or more aus that have fixed location in the payload of stm-n. Multiplexing e1/t1 c...
Page 542
542 c hapter 29: cpos i nterface c onfiguration the two tu-12s are called adjacent, if they have the same tug-3 number and tug-2 number but different tu-12 numbers with a discrepancy of 1. N the numbers in the aforementioned formula refer to the location numbers in a vc-4 frame. Tug-3 can be numbere...
Page 543
Overview 543 involved, however, the sending and receiving devices at network borders must use the same j0 byte. With the j0 byte, operators can detect and troubleshoot faults in advance or use less time to recover networks. ■ poh the payload of an stm-n frame includes path overhead (poh), which moni...
Page 544
544 c hapter 29: cpos i nterface c onfiguration figure 154 a cpos implementation configuring a cpos interface follow these steps to configure a cpos interface: internet transmission network access network n x 64 kbps n x 64 kbps n x 64 kbps n x 2 mbps e1 router a to do... Use the command... Remarks ...
Page 545
Configuring an e1 channel 545 n e1 configuration is supported on the cpos (e) interface module while t1 configuration is supported on the t1 cpos (t) interface module. Configuring an e1 channel follow these steps to configure an e1 channel: n e1 configuration is supported on the cpos (e) interface m...
Page 546
546 c hapter 29: cpos i nterface c onfiguration n t1 configuration is supported on the cpos (t) interface module. Displaying and maintaining cpos interfaces n ■ for those physical interfaces that are not connected to cables, shut down them with the shutdown command to avoid anomalies resulted from i...
Page 547
Troubleshooting cpos interfaces 547 perform the display interface serial command to check information on interface status. It shows that the physical state of the interface is up, but the link protocol is down; and loopback, though not configured, is detected on some interfaces. Solution: the fault ...
Page 548
548 c hapter 29: cpos i nterface c onfiguration.
Page 549: Arp C
30 arp c onfiguration when configuring arp, go to these sections for information you are interested in: ■ “arp overview” on page 549 ■ “configuring arp” on page 552 ■ “configuring gratuitous arp” on page 554 ■ “configuring arp source suppression” on page 555 ■ “configuring authorized arp” on page 55...
Page 550
550 c hapter 30: arp c onfiguration ■ hardware address length: length of a hardware address in bytes. For an ethernet address, the value of the hardware address length field is “6”. ■ protocol address length: length of a protocol address, in bytes. For an ip(v4) address, the value of the protocol ad...
Page 551
Arp overview 551 figure 156 arp address resolution process when host a and host b are not on the same subnet, host a first sends an arp request to the gateway. The destination ip address in the arp request is the ip address of the gateway. After obtaining the mac address of the gateway from an arp r...
Page 552
552 c hapter 30: arp c onfiguration configuring arp configuring a static arp entry a static arp entry is effective when the device works normally. However, when a vlan or vlan interface to which a static arp entry corresponds is deleted, the entry, if permanent, will be deleted, and if non-permanent...
Page 553
Configuring arp 553 enabling the arp entry check the arp entry check can control the device to learn multicast mac addresses. With the arp entry check enabled, the device cannot learn any arp entry with a multicast mac address. Configuring such a static arp entry is not allowed either; otherwise, th...
Page 554
554 c hapter 30: arp c onfiguration ■ set the maximum number of dynamic arp entries that ethernet 1/0 can learn to 1,000. ■ add a static arp entry, with the ip address being 192.168.1.1/24, the mac address being 00e0-fc01-0000, and the outbound interface being ethernet 1/0 of vlan 10. Configuration ...
Page 555
Configuring arp source suppression 555 configuring arp source suppression introduction to arp source suppression if hosts on a network attack the device by sending large amounts of ip packets whose ip addresses cannot be resolved, the following consequences will be resulted in: ■ the device sends la...
Page 556
556 c hapter 30: arp c onfiguration overwrite static arp entries, and dynamic arp entries cannot overwrite authorized arp entries. The aging mechanism of authorized arp entries is independent from that of dynamic arp entries. Configuring authorized arp enabling authorized arp follow these steps to e...
Page 557
Configuring authorized arp 557 [routera] dhcp enable [routera] dhcp server ip-pool 1 [routera-dhcp-pool-1] network 10.1.1.0 mask 255.255.255.0 [routera-dhcp-pool-1] quit # enter layer 3 ethernet interface view. [routera] interface ethernet 1/0 # configure the dhcp server to support authorized arp. [...
Page 558
558 c hapter 30: arp c onfiguration network diagram figure 158 network diagram for authorized arp configuration configuration procedure 1 configure router a # configure the ip address of ethernet 1/0. System-view [routera] interface ethernet 1/0 [routera-ethernet1/0] ip address 10.1.1.1 24 [routera-...
Page 559
Displaying and maintaining arp 559 [routerb] dhcp relay server-group 1 ip 10.1.1.1 # correlate ethernet 1/1 to dhcp server group 1. [routerb] interface ethernet 1/1 [routerb-ethernet1/1] dhcp relay server-select 1 # configure the dhcp server to support authorized arp. [routerb-ethernet1/1] dhcp upda...
Page 561: Roxy
31 p roxy arp c onfiguration when configuring proxy arp, go to these sections for information you are interested in: ■ “proxy arp overview” on page 561 ■ “enabling proxy arp” on page 561 ■ “displaying and maintaining proxy arp” on page 562 proxy arp overview for an arp request of a host on a network...
Page 562
562 c hapter 31: p roxy arp c onfiguration displaying and maintaining proxy arp proxy arp configuration examples proxy arp configuration example network requirements host a and host d are on the same subnet. But from the angle of the device, they are located in different subnets. Configure proxy arp...
Page 563
Proxy arp configuration examples 563 [router] interface ethernet 1/1 [router-ethernet1/1] ip address 192.168.20.99 255.255.255.0 [router-ethernet1/1] proxy-arp enable [router-ethernet1/1] quit local proxy arp configuration example in case of port isolation network requirements ■ host a and host b be...
Page 564
564 c hapter 31: p roxy arp c onfiguration [switch] interface ethernet 1/0 [switch-ethernet1/0] port-isolate enable group 2 [switch-ethernet1/0] interface ethernet 1/1 [switch-ethernet1/1] port-isolate enable group 2 [switch-ethernet1/1] interface ethernet 1/2 [switch-ethernet1/2] port-isolate uplin...
Page 565: Dhcp O
32 dhcp o verview this document is organized as follows: ■ “dhcp overview” on page 565 ■ “dhcp server configuration” on page 573 ■ “dhcp relay agent configuration” on page 589 ■ “dhcp client configuration” on page 599 ■ “dhcp snooping configuration” on page 601 ■ “bootp client configuration example”...
Page 566
566 c hapter 32: dhcp o verview relay agent. For information about the dhcp relay agent, refer to “introduction to dhcp relay agent” on page 589 . Dhcp address allocation allocation mechanisms dhcp supports three mechanisms for ip address allocation. ■ manual allocation: the network administrator as...
Page 567
Dhcp message format 567 address. Otherwise, the client sends a dhcp-decline message to the server to request an ip address again. ■ if there are multiple dhcp servers, ip addresses offered by other dhcp servers are assignable to other clients. Ip address lease extension the ip address dynamically al...
Page 568
568 c hapter 32: dhcp o verview ■ flags: the leftmost bit is defined as the broadcast (b) flag. This flag indicates whether the dhcp server sends a reply back by unicast or broadcast. If this flag is set to 0, the dhcp server sent a reply back by unicast; if this flag is set to 1, the dhcp server se...
Page 569
Dhcp options 569 ■ option 66: tftp server name option. It specifies a tftp server to be assigned to the client. ■ option 67: bootfile name option. It specifies the bootfile name to be assigned to the client. ■ option 150: tftp server ip address option. It specifies the tftp server ip address to be a...
Page 570
570 c hapter 32: dhcp o verview relay agent option (option 82) option 82 is the relay agent option in the option field of the dhcp message. It records the location information of the dhcp client. When a dhcp relay agent receives a client’s request, it adds option 82 to the request message and sends ...
Page 571
Protocols and standards 571 figure 169 sub-option 1 in verbose padding format n in the above figure, except that the vlan id field has a fixed length of 2 bytes, all the other padding contents of sub-option 1 are length variable. ■ sub-option 2: padded with the mac address of the interface that rece...
Page 572
572 c hapter 32: dhcp o verview.
Page 573: Dhcp S
33 dhcp s erver c onfiguration when configuring the dhcp server, go to these sections for information you are interested in: ■ “introduction to dhcp” on page 565 ■ “dhcp server configuration task list” on page 575 ■ “enabling dhcp” on page 575 ■ “enabling the dhcp server on an interface” on page 575...
Page 574
574 c hapter 33: dhcp s erver c onfiguration leaves are addresses statically bound to clients. For the same level address pools, a previously configured pool has a higher selection priority than a new one. At the very beginning, subnetworks inherit network parameters and clients inherit subnetwork p...
Page 575
Dhcp server configuration task list 575 if no ip address is assignable, the server will not respond. Dhcp server configuration task list to configure the dhcp server feature, perform the tasks described in the following sections: enabling dhcp enable dhcp before performing other configurations. Enab...
Page 576
576 c hapter 33: dhcp s erver c onfiguration configuring an address pool for the dhcp server configuration task list to configure an address pool, perform the tasks described in the following sections: creating a dhcp address pool to create a dhcp address pool, use the following commands: configurin...
Page 577
Configuring an address pool for the dhcp server 577 when the client with the mac address or id requests an ip address, the dhcp server will find the ip address from the binding for the client. A dhcp address pool now supports only one static binding, which can be a mac-to-ip or id-to-ip binding. To ...
Page 578
578 c hapter 33: dhcp s erver c onfiguration n ■ in dhcp address pool view, using the network command repeatedly overwrites the previous configuration. ■ using the dhcp server forbidden-ip command repeatedly can specify multiple ip address ranges not assignable. Configuring a domain name suffix for ...
Page 579
Configuring an address pool for the dhcp server 579 configuring wins servers and netbios node type for the client a microsoft dhcp client using netbios protocol contacts a windows internet naming service (wins) server for name resolution. Therefore, the dhcp server should assign a wins server addres...
Page 580
580 c hapter 33: dhcp s erver c onfiguration to configure the bims server ip address, port number, and shared key in the dhcp address pool, use the following commands: configuring gateways for the client dhcp clients that want to access hosts outside the local subnet request gateways to forward data...
Page 581
Configuring an address pool for the dhcp server 581 n specify an ip address for the network calling processor before performing other configuration. Configuring the tftp server and bootfile name for the client this task is to specify the ip address and name of a tftp server and the bootfile name in ...
Page 582
582 c hapter 33: dhcp s erver c onfiguration ■ define existing dhcp options. Some options have no unified definitions in rfc 2132; however, vendors can define such options as option 43 as needed. The self-defined dhcp option enables dhcp clients to obtain vendor-specific information. ■ expand existi...
Page 583
Configuring the dhcp server security functions 583 configuration prerequisites before performing this configuration, complete the following configuration on the dhcp server: ■ enable dhcp ■ configure the dhcp address pool enabling unauthorized dhcp server detection there are unauthorized dhcp server...
Page 584
584 c hapter 33: dhcp s erver c onfiguration configuring the dhcp server to support authorized arp a dhcp server can work in cooperation with authorized arp to block illegal clients, avoid learning incorrect arp entries and guard against attacks such as mac address spoofing. Only the clients that ha...
Page 585
Displaying and maintaining the dhcp server 585 configuring the handling mode for option 82 to enable the dhcp server to handle option 82, use the following commands: n to support option 82, it is required to perform configuration on both the dhcp server and relay agent. Refer to “configuring the dhc...
Page 586
586 c hapter 33: dhcp s erver c onfiguration ■ the dhcp server and client are on the same subnet and perform direct message delivery. ■ the dhcp server and client are not on the same subnet and communicate with each other via a dhcp relay agent. The dhcp server configuration for the two types is the...
Page 587
Dhcp server configuration examples 587 # exclude ip addresses from dynamic allocation (addresses of the dns server, wins server, and gateways). [routera] dhcp server forbidden-ip 10.1.1.2 [routera] dhcp server forbidden-ip 10.1.1.4 [routera] dhcp server forbidden-ip 10.1.1.126 [routera] dhcp server ...
Page 588
588 c hapter 33: dhcp s erver c onfiguration # enable dhcp. System-view [routera] dhcp enable # configure dhcp address pool 0. [routera] dhcp server ip-pool 0 [routera-dhcp-pool-0] network 10.1.1.0 mask 255.255.255.0 [routera-dhcp-pool-0] option 43 hex 80 0b 00 00 02 01 02 03 04 02 02 02 02 troubles...
Page 589: Dhcp R
34 dhcp r elay a gent c onfiguration when configuring the dhcp relay agent, go to these sections for information you are interested in: ■ “introduction to dhcp relay agent” on page 589 ■ “dhcp relay agent configuration task list” on page 591 ■ “configuring the dhcp relay agent” on page 591 ■ “displa...
Page 590
590 c hapter 34: dhcp r elay a gent c onfiguration figure 172 dhcp relay agent application no matter whether a relay agent exists or not, the dhcp server and client interact with each other in a similar way (see “dynamic ip address allocation procedure” on page 566 ). The following describes the for...
Page 591
Dhcp relay agent configuration task list 591 if a reply returned by the dhcp server contains option 82, the dhcp relay agent will remove the option 82 before forwarding the reply to the client. Dhcp relay agent configuration task list complete the following tasks to configure the dhcp relay agent: c...
Page 592
592 c hapter 34: dhcp r elay a gent c onfiguration n ■ if you enabled the dhcp relay agent on an ethernet subinterface, a client connected must also use a subinterface to guarantee normal communication with the relay agent. In this case, if the client is a pc, it cannot obtain an ip address. ■ if th...
Page 593
Configuring the dhcp relay agent 593 configuring the dhcp relay agent to send a dhcp-release request sometimes, you need to release a client’s ip address manually on the dhcp relay agent. With this task completed, the dhcp relay agent can actively send a dhcp-release request that contains the client...
Page 594
594 c hapter 34: dhcp r elay a gent c onfiguration ■ when using the dhcp relay security static command to bind an interface to a static binding entry, make sure that the interface is configured as a dhcp relay agent; otherwise, address entry conflicts may occur. Configuring dynamic binding update in...
Page 595
Configuring the dhcp relay agent 595 n ■ authorized arp can only be configured on layer 3 interfaces. ■ disabling the dhcp relay agent to support authorized arp will not delete dynamic bindings, but will notify authorized arp to delete the corresponding authorized arp entries. ■ since the dhcp relay...
Page 596
596 c hapter 34: dhcp r elay a gent c onfiguration n ■ to support option 82, it is required to perform related configuration on both the dhcp server and relay agent. Refer to “configuring the handling mode for option 82” on page 584 for dhcp server configuration of this kind. ■ if the handling strat...
Page 597
Troubleshooting dhcp relay agent configuration 597 address of ethernet1/2 is 10.1.1.2/24 that communicates with the dhcp server 10.1.1.1/24. As shown in the figure below, router a forwards messages between dhcp clients and the dhcp server. Network diagram figure 174 network diagram for dhcp relay ag...
Page 598
598 c hapter 34: dhcp r elay a gent c onfiguration analysis some problems may occur with the dhcp relay agent or server configuration. Enable debugging and execute the display command on the dhcp relay agent to view the debugging information and interface state information for locating the problem. ...
Page 599: Dhcp C
35 dhcp c lient c onfiguration when configuring the dhcp client, go to these sections for information you are interested in: ■ “introduction to dhcp client” on page 599 ■ “enabling the dhcp client on an interface” on page 599 ■ “displaying and maintaining the dhcp client” on page 600 ■ “dhcp client ...
Page 600
600 c hapter 35: dhcp c lient c onfiguration conflicted ip address is manually deleted and the interface is made up again by first executing the shutdown command and then the undo shutdown command or the dhcp client is enabled on the interface by executing the undo ip address dhcp-alloc and ip addre...
Page 601: Dhcp S
36 dhcp s nooping c onfiguration when configuring dhcp snooping, go to these sections for information you are interested in: ■ “dhcp snooping overview” on page 601 ■ “configuring dhcp snooping basic functions” on page 602 ■ “displaying and maintaining dhcp snooping” on page 602 ■ “dhcp snooping conf...
Page 602
602 c hapter 36: dhcp s nooping c onfiguration ensuring dhcp clients to obtain ip addresses from valid dhcp servers if there is an unauthorized dhcp server on a network, the dhcp clients may obtain invalid ip addresses. With dhcp snooping, the ports of a device can be configured as trusted or untrus...
Page 603
Dhcp snooping configuration example 603 network diagram figure 175 network diagram for dhcp snooping configuration configuration procedure # enable dhcp snooping. System-view [switchb] dhcp-snooping # specify ethernet1/1 as trusted. [switchb] interface ethernet 1/1 [switchb-ethernet1/1] dhcp-snoopin...
Page 604
604 c hapter 36: dhcp s nooping c onfiguration.
Page 605: Bootp C
37 bootp c lient c onfiguration while configuring a bootstrap protocol (bootp) client, go to these sections for information you are interested in: ■ “introduction to bootp client” on page 605 ■ “configuring an interface to dynamically obtain an ip address through bootp” on page 606 ■ “displaying and...
Page 606
606 c hapter 37: bootp c lient c onfiguration obtaining an ip address dynamically n a dhcp server can take the place of the bootp server in the following dynamic ip address acquisition. A bootp client dynamically obtains an ip address from a bootp server in the following way: 1 the bootp client broa...
Page 607
Bootp client configuration example 607 # configure ethernet1/1 to dynamically obtain an ip address by using bootp. System-view [routerb] interface ethernet 1/1 [routerb-ethernet1/1] ip address bootp-alloc n to make the bootp client to obtain an ip address from the dhcp server, you need to perform ad...
Page 608
608 c hapter 37: bootp c lient c onfiguration.
Page 609: Dns C
38 dns c onfiguration when configuring dns, go to these sections for information you are interested in: ■ “dns overview” on page 609 ■ “configuring the dns client” on page 611 ■ “configuring the dns proxy” on page 612 ■ “displaying and maintaining dns” on page 612 ■ “dns configuration examples” on p...
Page 610
610 c hapter 38: dns c onfiguration 4 the dns client returns the resolution result to the application after receiving a response from the dns server. Figure 176 dynamic domain name resolution figure 176 shows the relationship between user program, dns client, and dns server. The resolver and cache c...
Page 611
Configuring the dns client 611 n if an alias is configured for a domain name on the dns server, the device can resolve the alias into the ip address of the host. Dns proxy introduction to dns proxy a dns proxy forwards dns requests and replies between dns clients and a dns server. As shown in figure...
Page 612
612 c hapter 38: dns c onfiguration n the ip address you last assign to the host name will overwrite the previous one if there is any. You may create up to 50 static mappings between domain names and ip addresses. Configuring dynamic domain name resolution follow these steps to configure dynamic dom...
Page 613
Dns configuration examples 613 dns configuration examples static domain name resolution configuration example network requirements device uses the static domain name resolution to access host with ip address 10.1.1.2 through domain name host.Com. Network diagram figure 178 network diagram for static...
Page 614
614 c hapter 38: dns c onfiguration network diagram figure 179 network diagram for dynamic domain name resolution configuration procedure n ■ before performing the following configuration, make sure that there is a route between the device and the host, and configurations are done on both the device...
Page 615
Dns configuration examples 615 figure 180 create a zone # create a mapping between host name and ip address. Figure 181 add a host in figure 181 , right click zone com, and then select new host to bring up a dialog box as shown in figure 182 . Enter host name host and ip address 3.1.1.1..
Page 616
616 c hapter 38: dns c onfiguration figure 182 add a mapping between domain name and ip address 2 configure the dns client # enable dynamic domain name resolution. System-view [sysname] dns resolve # specify the dns server 2.1.1.2. [sysname] dns server 2.1.1.2 # configure com as the name suffix. [sy...
Page 617
Dns configuration examples 617 round-trip min/avg/max = 1/1/3 ms --- host.Com ping statistics --- 5 packet(s) transmitted 0 packet(s) received 100.00% packet loss dns proxy configuration example network requirements ■ specify device a as the dns server of device b (the dns client). ■ device a acts a...
Page 618
618 c hapter 38: dns c onfiguration # enable the domain name resolution function. System-view [deviceb] dns resolve # specify the dns server 2.1.1.2. [deviceb] dns server 2.1.1.2 4 configuration verification # execute the ping host.Com command on device b to verify that the host can be pinged after ...
Page 619: Ip A
39 ip a ccounting c onfiguration when configuring ip accounting, go to these sections for information you are interested in: ■ “introduction to ip accounting” on page 619 ■ “configuring ip accounting” on page 619 ■ “ip accounting configuration example” on page 620 ■ “displaying and maintaining ip ac...
Page 620
620 c hapter 39: ip a ccounting c onfiguration ip accounting configuration example network requirements as shown in figure 184 , the router is connected to host a and host b through ethernet interfaces. Enable ip accounting on ethernet1/0 of the router to count the ip packets from host a to host b, ...
Page 621
Ip accounting configuration example 621 network diagram figure 184 network diagram for ip accounting configuration configuration procedure ■ configure the router. # enable ip accounting. System-view [router] ip count enable # configure an ip accounting rule. [router] ip count rule 1.1.1.1 24 # set t...
Page 622
622 c hapter 39: ip a ccounting c onfiguration [router] display ip count inbound-packets interior 1 inbound streams information in interior list: srcip dstip protocol pkts bytes 1.1.1.1 2.2.2.2 icmp 4 240 [router] display ip count outbound-packets interior 1 outbound streams information in interior ...
Page 623: Ip A
40 ip a ddressing c onfiguration when assigning ip addresses to interfaces on your device, go to these sections for information you are interested in: ■ “ip addressing overview” on page 623 ■ “configuring ip addresses” on page 625 ■ “configuring ip unnumbered” on page 628 ■ “displaying and maintaini...
Page 624
624 c hapter 40: ip a ddressing c onfiguration special case ip addresses the following ip addresses are for special use, and they cannot be used as host ip addresses: ■ ip address with an all-zero net id: identifies a host on the local network. For example, ip address 0.0.0.16 indicates the host wit...
Page 625
Configuring ip addresses 625 while allowing you to create multiple logical networks within a single class a, b, or c network, subnetting is transparent to the rest of the internet. All these networks still appear as one. As subnetting adds an additional level, subnet-id, to the two-level hierarchy w...
Page 626
626 c hapter 40: ip a ddressing c onfiguration c caution: ■ the primary ip address you assigned to the interface can overwrite the old one if there is any. ■ you cannot assign secondary ip addresses to an interface using bootp, dhcp, or ppp address negotiation. ■ the primary and secondary ip address...
Page 627
Configuring ip addresses 627 configuration procedure # assign a primary ip address and a secondary ip address to ethernet1/0. System-view [router] interface ethernet 1/0 [router-ethernet1/0] ip address 172.16.1.1 255.255.255.0 [router-ethernet1/0] ip address 172.16.2.1 255.255.255.0 sub # set the ga...
Page 628
628 c hapter 40: ip a ddressing c onfiguration configuring ip unnumbered configuration prerequisites assign a primary ip address to the interface from which you want to borrow the ip address. Alternatively, you may configure the interface to obtain one through bootp, dhcp, or ppp negotiation. Config...
Page 629
Configuring ip unnumbered 629 network diagram figure 188 network diagram for ip unnumbered configuration configuration procedure 1 configure router a # assign a primary ip address to ethernet1/1. System-view [routera] interface ethernet 1/1 [routera-ethernet1/1] ip address 172.16.10.1 255.255.255.0 ...
Page 630
630 c hapter 40: ip a ddressing c onfiguration 3 ping a host attached to router b from router a to verify the configuration. [routera] ping 172.16.20.2 ping 172.16.20.2: 56 data bytes, press ctrl_c to break reply from 172.16.20.2: bytes=56 sequence=1 ttl=255 time=25 ms reply from 172.16.20.2: bytes=...
Page 631: Ip P
41 ip p erformance c onfiguration when configuring ip performance, go to these sections for the information you are interested in: ■ “ip performance overview” on page 631 ■ “enabling the device to forward directed broadcasts” on page 631 ■ “configuring tcp attributes” on page 633 ■ “configuring icmp...
Page 632
632 c hapter 41: ip p erformance c onfiguration n ■ you can reference an acl to forward only directed broadcasts permitted by the acl. ■ if you execute the ip forward-broadcast acl command on an interface repeatedly, the last execution overwrites the previous one. If the command executed last time d...
Page 633
Configuring tcp attributes 633 # configure an ip address for the interface ethernet 1/0. [routerb] interface ethernet 1/0 [routerb-ethernet1/0] ip address 2.2.2.1 24 [routerb-ethernet1/0] quit ■ configure the host # set the ip address of the network interface card (nic) connected to router a to 1.1....
Page 634
634 c hapter 41: ip p erformance c onfiguration a large amount of tcp semi-connections are established, resulting in heavy resource consumption and making the server unable to handle services normally. The syn cookie feature can prevent syn flood attacks. After receiving a tcp connection request, th...
Page 635
Configuring tcp attributes 635 n ■ with the protection against naptha attack enabled, the device will periodically check and record the number of tcp connections in each state. ■ with the protection against naptha attack enabled, if the device detects that the number of tcp connections in a state ex...
Page 636
636 c hapter 41: ip p erformance c onfiguration configuring icmp to send error packets sending error packets is a major function of icmp protocol. In case of network abnormalities, icmp packets are usually sent by the network or transport layer protocols to notify corresponding devices so as to faci...
Page 637
Configuring icmp to send error packets 637 ■ when receiving a packet with the destination being local and transport layer protocol being udp, if the packet’s port number does not match the running process, the device will send the source a “port unreachable” icmp error packet. ■ if the source uses “...
Page 638
638 c hapter 41: ip p erformance c onfiguration displaying and maintaining ip performance to do... Use the command... Remarks display current tcp connection state display tcp status available in any view display tcp connection statistics display tcp statistics display udp statistics display udp stat...
Page 639: Ip U
42 ip u nicast p olicy r outing c onfiguration when configuring ip unicast policy routing, go to these sections for information you are interested in: ■ “introduction to ip unicast policy routing” on page 639 ■ “ip unicast policy routing configuration” on page 639 ■ “displaying and maintaining ip un...
Page 640
640 c hapter 42: ip u nicast p olicy r outing c onfiguration there is an and relationship between if-match clauses on a node. That is to say, a packet must satisfy all matching rules specified by all if match clauses for the node before the action specified by the apply clause is taken. Currently, t...
Page 641
Configuring ip unicast policy routing 641 n you can use the apply output-interface command to configure two outgoing interfaces or the apply ip-address next-hop command two next hops. If you want to modify either of the two outgoing interfaces or next hops, you can execute the apply output-interface...
Page 642
642 c hapter 42: ip u nicast p olicy r outing c onfiguration the system policy routing is used to route packets generated by the local device. You can enable the interface policy routing and the system policy routing respectively. Only one policy can be referenced when system policy routing is enabl...
Page 643
Ip unicast policy routing configuration examples 643 ip unicast policy routing configuration examples configuring policy routing based on source address network requirements as shown in figure 190 , define policy aaa for policy routing so that tcp packets arriving at the interface ethernet 1/0 are f...
Page 644
644 c hapter 42: ip u nicast p olicy r outing c onfiguration [router] policy-based-route aaa permit node 5 [router-policy-based-route] if-match acl 3101 [router-policy-based-route] apply output-interface serial 2/0 [router-policy-based-route] quit # define node 10 of policy aaa so that policy routin...
Page 645
Ip unicast policy routing configuration examples 645 [routera] interface ethernet 1/0 [routera-ethernet1/0] ip address 192.1.1.1 255.255.255.0 [routera-ethernet1/0] ip policy-based-route lab1 [routera-ethernet1/0] quit # forward ip packets with a size of 64 to 100 bytes to the next hop 150.1.1.2 and...
Page 646
646 c hapter 42: ip u nicast p olicy r outing c onfiguration.
Page 647: Udp H
43 udp h elper c onfiguration when configuring udp helper, go to these sections for information you are interested in: ■ “introduction to udp helper” on page 647 ■ “configuring udp helper” on page 648 ■ “displaying and maintaining udp helper” on page 648 ■ “udp helper configuration example” on page ...
Page 648
648 c hapter 43: udp h elper c onfiguration configuring udp helper follow these steps to configure udp helper: c caution: ■ on the devices supporting the directed broadcast suppression function, the receiving of directed broadcasts to a directly connected network is disabled by default. As a result,...
Page 649
Udp helper configuration example 649 udp helper configuration example network requirements the ip address of the interface ethernet 1/0 on router a is 10.110.1.1/16, connecting to the network segment 10.110.0.0/16. Enable the forwarding of broadcast packets with udp destination port number 55 to the...
Page 650
650 c hapter 43: udp h elper c onfiguration.
Page 651: Urpf C
44 urpf c onfiguration when configuring urpf, go to these sections for information you are interested in: ■ “urpf overview” on page 651 ■ “configuring urpf” on page 652 urpf overview basic concepts unicast reverse path forwarding (urpf) protects a network against attacks based on source address spoo...
Page 652
652 c hapter 44: urpf c onfiguration ■ in loose approach, urpf does a reverse lookup for the outgoing interfaces of the packet. As long as an outgoing interface exists (no matter whether the outgoing interface is consistent with the incoming interface), the packet passes the check. Otherwise, the pa...
Page 653: Ast
45 f ast f orwarding c onfiguration when configuring fast forwarding, go to these sections for the information you are interested in: ■ “introduction to fast forwarding” on page 653 ■ “configuring fast forwarding” on page 654 ■ “displaying and maintaining fast forwarding” on page 654 introduction to...
Page 654
654 c hapter 45: f ast f orwarding c onfiguration fast forwarding can improve the packet forwarding efficiency greatly. The performance of fast forwarding is sometimes affected by some attributes, for example, packet queue management and packet header compression. Although fast forwarding can proces...
Page 655: 6 B
46 ip v 6 b asics c onfiguration when configuring ipv6 basics, go to these sections for information you are interested in: ■ “ipv6 overview” on page 655 ■ “ipv6 basics configuration task list” on page 664 ■ “configuring basic ipv6 functions” on page 665 ■ “configuring ipv6 ndp” on page 666 ■ “config...
Page 656
656 c hapter 46: ip v 6 b asics c onfiguration addresses, the size of basic ipv6 headers is 40 bytes and is only twice that of ipv4 headers (excluding the options field). Figure 194 comparison between ipv4 packet header format and basic ipv6 packet header format adequate address space the source and...
Page 657
Ipv6 overview 657 qos support the flow label field in the ipv6 header allows the device to label packets in a flow and provide special handling for these packets. Enhanced neighbor discovery mechanism the ipv6 neighbor discovery protocol is implemented through a group of internet control message pro...
Page 658
658 c hapter 46: ip v 6 b asics c onfiguration ■ unicast address: an identifier for a single interface, similar to an ipv4 unicast address. A packet sent to a unicast address is delivered to the interface identified by that address. ■ multicast address: an identifier for a set of interfaces (typical...
Page 659
Ipv6 overview 659 node may fill this address in the source address field of an ipv6 packet, but may not use it as a destination ipv6 address. Multicast address ipv6 multicast addresses listed in table 37 are reserved for special purpose. Besides, there is another type of multicast address: solicited...
Page 660
660 c hapter 46: ip v 6 b asics c onfiguration ■ “neighbor reachability detection” on page 661 ■ “duplicate address detection” on page 661 ■ “router/prefix discovery and address autoconfiguration” on page 662 ■ “redirection” on page 663 table 38 lists the types and functions of icmpv6 messages used ...
Page 661
Ipv6 overview 661 figure 196 address resolution the address resolution procedure is as follows: 1 node a multicasts an ns message. The source address of the ns message is the ipv6 address of an interface of node a and the destination address is the solicited-node multicast address of node b. The ns ...
Page 662
662 c hapter 46: ip v 6 b asics c onfiguration figure 197 duplicate address detection the dad procedure is as follows: 1 node a sends an ns message whose source address is the unassigned address :: and destination address is the corresponding solicited-node multicast address of the ipv6 address to b...
Page 663
Ipv6 overview 663 redirection when a host is started, its routing table may contain only the default route to the gateway. When certain conditions are satisfied, the gateway sends an icmpv6 redirect message to the source host so that the host can select a better next hop to forward packets (similar ...
Page 664
664 c hapter 46: ip v 6 b asics c onfiguration introduction to ipv6 dns in the ipv6 network, a domain name system (dns) supporting ipv6 converts domain names into ipv6 addresses, instead of ipv4 addresses. However, just like an ipv4 dns, an ipv6 dns also covers static domain name resolution and dyna...
Page 665
Configuring basic ipv6 functions 665 configuring basic ipv6 functions enabling the ipv6 packet forwarding function before ipv6-related configurations, you need to enable the ipv6 packet forwarding function. Otherwise, an interface cannot forward ipv6 packets even if an ipv6 address is configured, re...
Page 666
666 c hapter 46: ip v 6 b asics c onfiguration n ■ after an ipv6 site-local address or aggregatable global unicast address is configured for an interface, a link-local address will be generated automatically. The automatically generated link-local address is the same as the one generated by using th...
Page 667
Configuring ipv6 ndp 667 ■ configure an ipv6 address and link-layer address for a port in a vlan. Follow these steps to configure a static neighbor entry: c caution: you can adopt either of the two methods above to configure a static neighbor entry for a vlan interface. ■ after a static neighbor ent...
Page 668
668 c hapter 46: ip v 6 b asics c onfiguration n the values of the retrans timer field and the reachable time field configured for an interface are sent to hosts via ra messages. Furthermore, this interface sends ns messages at intervals of retrans timer and considers a neighbor reachable within the...
Page 669
Configuring ipv6 ndp 669 c caution: the maximum interval for sending ra messages should be less than or equal to the router lifetime in ra messages. The minimum interval for sending ra messages should be 0.75 times the maximum interval for sending ra messages or less. Configuring the number of attem...
Page 670
670 c hapter 46: ip v 6 b asics c onfiguration send an ns message reaches the maximum, the acquired address is considered usable. Follow these steps to configure the attempts to send an ns message for dad: configuring pmtu discovery configuring the interface mtu ipv6 routers do not support packet fr...
Page 671
Configuring ipv6 tcp properties 671 configuring the aging time for pmtu after the mtu of the path from the source host to the destination host is dynamically determined (refer to “ipv6 pmtu discovery” on page 663 ), the source host sends subsequent packets to the destination host on basis of this mt...
Page 672
672 c hapter 46: ip v 6 b asics c onfiguration ■ load sharing based on the hash algorithm: a certain algorithm based on the source ipv6 address and destination ipv6 address is adopted to select an ecmp route to forward packets. ■ load sharing based on polling: each ecmp route is used in turn to forw...
Page 673
Configuring ipv6 dns 673 enable sending of multicast echo replies if hosts are capable of replying multicast echo requests, host a can attack host b by sending an echo request with the source being host b to a multicast address, then all the hosts in the multicast group will send echo replies to hos...
Page 674
674 c hapter 46: ip v 6 b asics c onfiguration n the dns resolve and dns domain commands are the same as those of ipv4 dns. For details about the commands, refer to “dns configuration” on page 609 . Displaying and maintaining ipv6 basics configuration to do... Use the command... Remarks enter system...
Page 675
Ipv6 configuration example 675 n the display dns domain command is the same as the one of ipv4 dns. For details about the commands, refer to “dns configuration” on page 609 . Ipv6 configuration example network requirements two routers are directly connected through ethernet interfaces. Different typ...
Page 676
676 c hapter 46: ip v 6 b asics c onfiguration [routera-ethernet1/0] ipv6 address 2001::/64 eui-64 # assign an aggregatable global unicast address for interface ethernet 1/0. [routera-ethernet1/0] ipv6 address 3001::1/64 [routera-ethernet1/0] ipv6 address 4001::1/64 # allow interface ethernet 1/0 to...
Page 677
Ipv6 configuration example 677 nd router advertisements are sent every 600 seconds nd router advertisements live for 1800 seconds hosts use stateless autoconfig for addresses # display the ipv6 information of the interface on router b. [routerb-ethernet1/0] display ipv6 interface ethernet 1/0 ethern...
Page 678
678 c hapter 46: ip v 6 b asics c onfiguration --- 2001::20f:e2ff:fe00:2 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 2/2/4 ms ping ipv6 3001::2 ping 3001::2 : 56 data bytes, press ctrl_c to break reply from 3001::2 bytes=56 sequence=1 h...
Page 679: Nat-Pt C
47 nat-pt c onfiguration when configuring nat-pt, go to these sections for information you are interested in: ■ “nat-pt overview” on page 679 ■ “configuring nat-pt” on page 681 ■ “displaying and maintaining nat-pt” on page 686 ■ “nat-pt configuration example” on page 687 ■ “troubleshooting nat-pt” o...
Page 680
680 c hapter 47: nat-pt c onfiguration ■ “nat-pt mechanism” on page 680 ■ “implementing nat-pt” on page 680 nat-pt mechanism there are three nat-pt mechanisms to realize the translation between ipv4 and ipv6 addresses: “static nat-pt mapping” on page 680 , “dynamic nat-pt mapping” on page 680 , and ...
Page 681
Nat-pt configuration task list 681 translated into a valid ipv4 address, the destination ipv6 address is translated into an ipv4 address. Otherwise, the translation fails. 3 after the source and destination ipv6 addresses of the packet are translated into ipv4 addresses, the nat-pt device forwards t...
Page 682
682 c hapter 47: nat-pt c onfiguration enabling nat-pt follow these steps to enable nat-pt: configuring a nat-pt prefix a nat-pt prefix is used for configuring dynamic ipv4-to-ipv6 and ipv6-to-ipv4 mappings. You can configure such a dynamic ipv6-to-ipv4 mapping rule as follows: when a packet is sent...
Page 683
Configuring nat-pt 683 follow these steps to configure mappings for ipv4 hosts accessing ipv6 hosts: n ■ the natpt-prefix argument specified in the natpt v6bound dynamic prefix natpt-prefix interface interface-type interface-number command must have been configured with the natpt prefix command. ■ f...
Page 684
684 c hapter 47: nat-pt c onfiguration ■ combination 4: combination of a nat-pt prefix with an interface address if the destination ipv6 address of a packet contains a nat-pt prefix, the source ipv6 address will be translated into an ipv4 address of the specified interface. If combination 1 or combi...
Page 685
Configuring nat-pt 685 n ■ the natpt-prefix argument specified in the natpt v6bound dynamic prefix natpt-prefix interface interface-type interface-number command must have been configured with the natpt prefix command. ■ for acl configuration, refer to “configuring acls” on page 1881 . Configuring t...
Page 686
686 c hapter 47: nat-pt c onfiguration configuring the maximum number of sessions you can set the maximum number of concurrent sessions that the system allows. When the number of concurrent sessions reaches the maximum number, no new session will be established any longer. Follow these steps to conf...
Page 687
Nat-pt configuration example 687 nat-pt configuration example configuring dynamic ipv6-to-ipv4 mappings network requirements an ipv4 network is connected to an ipv6 network through a nat-pt device - router b. Dynamic ipv6-to-ipv4 mappings are configured on router b so that ipv6 hosts can access ipv4...
Page 688
688 c hapter 47: nat-pt c onfiguration # configure an interface address and enable nat-pt on the interface. System-view [routerb] ipv6 [routerb] interface serial 2/0 [routerb-serial2/0] ip address 8.0.0.1 255.255.255.0 [routerb-serial2/0] natpt enable [routerb-serial2/0] quit [routerb] interface ser...
Page 689
Nat-pt configuration example 689 configuration procedure ■ configure router a in the ipv4 network system-view [routera] interface serial 2/0 [routera-serial2/0] ip address 8.0.0.2 255.255.255.0 [routera-serial2/0] quit [routera] ip route-static 0.0.0.0 0 serial 2/0 ■ configure router c in the ipv6 n...
Page 690
690 c hapter 47: nat-pt c onfiguration [routerb] display natpt session all natpt session info: no ipv6source ipv4source pro ipv6destination ipv4destination 1 2001::0002 ^ 0 8.0.0.5 ^ 0 icmp 3001::0005 ^ 0 8.0.0.2 ^ 0 troubleshooting nat-pt symptom: nat-pt is abnormal. Solution: ■ enable debugging fo...
Page 691: Ual
48 d ual s tack c onfiguration when configuring dual stack, go to these sections for information you are interested in: ■ “dual stack overview” on page 691 ■ “configuring dual stack” on page 691 dual stack overview dual stack is the most direct approach to making ipv6 nodes compatible with ipv4 node...
Page 693: Unneling
49 t unneling c onfiguration when configuring tunneling, go to these sections for information you are interested in: ■ “introduction to tunneling” on page 693 ■ “tunneling configuration task list” on page 700 ■ “configuring an ipv6 manually configured tunnel” on page 700 ■ “configuring automatic ipv...
Page 694
694 c hapter 49: t unneling c onfiguration solutions are available. With their own characteristics, they are used to solve communication problems in different transition stages under different environments. Currently, there are three major transition technologies: dual stack (rfc2893), tunneling (rf...
Page 695
Introduction to tunneling 695 encapsulates an ipv4 header in the ipv6 packet and forwards it through the physical interface of the tunnel. 3 the encapsulated packet goes through the tunnel to reach the device at the destination end of the tunnel. The device at the destination end decapsulates the pa...
Page 696
696 c hapter 49: t unneling c onfiguration 2 automatic ipv4-compatible ipv6 tunnel an automatic ipv4-compatible ipv6 tunnel is a point-to-multipoint link. Ipv4-compatible ipv6 addresses are adopted at both ends of such a tunnel. The address format is 0:0:0:0:0:0:a.B.C.D/96, where a.B.C.D represents ...
Page 697
Introduction to tunneling 697 figure 206 principle of 6to4 tunnel and 6to4 relay 4 isatap tunnel with the application of the ipv6 technology, there will be more and more ipv6 hosts in the existing ipv4 network. The isatap tunneling technology provides a satisfactory solution for ipv6 application. An...
Page 698
698 c hapter 49: t unneling c onfiguration encapsulation and decapsulation packets to be transferred through a tunnel undergo an encapsulation process and decapsulation process. Figure 208 shows these two processes. Figure 208 principle of ipv4 over ipv4 tunnel ■ encapsulation the encapsulation proc...
Page 699
Introduction to tunneling 699 figure 209 principle of ipv4/ipv6 over ipv6 tunnel as shown in figure 209 , original data refers to ipv4 or ipv6 packets. Encapsulation and decapsulation the encapsulation process is as follows: 1 after receiving the original packet, the interface of router a connecting...
Page 700
700 c hapter 49: t unneling c onfiguration figure 210 network diagram for 6pe n “p” in the above figure refers to a backbone router in the network of a service provider. P is not directly connected with a ce and is required to have the basic mpls capability. When an isp wants to utilize the existing...
Page 701
Configuring an ipv6 manually configured tunnel 701 configuration procedure follow these steps to configure an ipv6 manually configured tunnel: n for the configuration of mtu of ipv6 packets sent over a tunnel interface, refer to the ipv6 mtu command in “configuring the interface mtu” on page 670 . C...
Page 702
702 c hapter 49: t unneling c onfiguration ■ if the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same subnet, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure static or d...
Page 703
Configuring an ipv6 manually configured tunnel 703 [routera] ipv6 # configure an ipv6 manually configured tunnel. [routera] interface tunnel 0 [routera-tunnel0] ipv6 address 3001::1/64 [routera-tunnel0] source ethernet 1/0 [routera-tunnel0] destination 192.168.50.1 [routera-tunnel0] tunnel-protocol ...
Page 704
704 c hapter 49: t unneling c onfiguration ff02::1:ffa8:3201 ff02::1:ff00:2 ff02::2 ff02::1 mtu is 1500 bytes nd reachable time is 30000 milliseconds nd retransmit interval is 1000 milliseconds hosts use stateless autoconfig for addresses # ping the ipv6 address of the peer tunnel interface from rou...
Page 705
Configuring automatic ipv4-compatible ipv6 tunnel 705 n for the configuration of the mtu of ipv6 packets sent over a tunnel interface, refer to the ipv6 mtu command in “configuring the interface mtu” on page 670 . C caution: ■ only one automatic tunnel can be created at the same tunnel source. ■ no ...
Page 706
706 c hapter 49: t unneling c onfiguration configuration example network requirements between router a and router b is an ipv4 network. It is required that an ipv6 connection be established through an automatic ipv4-compatible ipv6 tunnel between the two dual-stack routers. Network diagram figure 21...
Page 707
Configuring automatic ipv4-compatible ipv6 tunnel 707 [routerb] interface tunnel0 [routerb-tunnel0] ipv6 address ::2.1.1.2/96 [routerb-tunnel0] source serial 2/0 [routerb-tunnel0] tunnel-protocol ipv6-ipv4 auto-tunnel configuration verification after the above configurations, display the status of t...
Page 708
708 c hapter 49: t unneling c onfiguration 0.00% packet loss round-trip min/avg/max = 15/65/219 ms configuring 6to4 tunnel configuration prerequisites ip addresses are configured for interfaces such as vlan interface, ethernet interface, and loopback interface on the device so that they can communic...
Page 709
Configuring 6to4 tunnel 709 n for the configuration of the mtu of ipv6 packets sent over a tunnel interface, refer to the ipv6 mtu command in “configuring the interface mtu” on page 670 . C caution: ■ only one automatic tunnel can be configured at the same tunnel source. ■ no destination address nee...
Page 710
710 c hapter 49: t unneling c onfiguration # enable the ipv6 forwarding function. System-view [routera] ipv6 # configure an ipv4 address for ethernet 1/0. [routera] interface ethernet 1/0 [routera-ethernet1/0] ip address 2.1.1.1 24 [routera-ethernet1/0] quit # configure a route from ethernet1/0 of r...
Page 711
Configuring 6to4 tunnel 711 # configure an ipv6 address for ethernet1/1. [routerb] interface ethernet 1/1 [routerb-ethernet1/1] ipv6 address 2002:0501:0101:1::1/64 [routerb-ethernet1/1] quit # configure a 6to4 tunnel. [routerb] interface tunnel0 [routerb-tunnel0] ipv6 address 2002:0501:0101::1/64 [r...
Page 712
712 c hapter 49: t unneling c onfiguration network diagram figure 214 network diagram for a 6to4 relay configuration procedure the configuration on a 6to4 relay router is the same as that on an ordinary 6to4 router. However, a 6to4 relay router can be connected to not only a 6to4 network, but also a...
Page 713
Configuring 6to4 tunnel 713 [routera] interface tunnel0 [routera-tunnel0] ipv6 address 2002:0201:0101::1/64 [routera-tunnel0] source ethernet 1/0 [routera-tunnel0] tunnel-protocol ipv6-ipv4 6to4 [routera-tunnel0] quit # configure a static route whose destination address is 2001::/16 and next-hop is ...
Page 714
714 c hapter 49: t unneling c onfiguration configuration verification after the above configuration, ping host b from host a. D:\>ping6 -s 2002:201:101:1::2 2001::2 pinging 2001::2 from 2002:201:101:1::2 with 32 bytes of data: reply from 2001::2: bytes=32 time=13ms reply from 2001::2: bytes=32 time=...
Page 715
Configuring isatap tunnel 715 n for the configuration of the mtu of ipv6 packets sent over a tunnel interface, refer to the ipv6 mtu command in “configuring the interface mtu” on page 670 . C caution: ■ if the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same subnet,...
Page 716
716 c hapter 49: t unneling c onfiguration configuration procedure the following example shows how to configure an isatap tunnel between the router and the isatap host, which allows a separate isatap host to access the ipv6 network. ■ configuration on the isatap router # enable the ipv6 forwarding f...
Page 717
Configuring ipv4 over ipv4 tunnel 717 # a link-local address (fe80::5efe:2.1.1.2) in the isatap format is automatically generated for the isatap interface. Configure an ipv4 address for the isatap router on the isatap interface. C:\>ipv6 rlu 2 2.1.1.1 after carrying out the above command, look at th...
Page 718
718 c hapter 49: t unneling c onfiguration c caution: ■ if the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same subnet, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure ...
Page 719
Configuring ipv4 over ipv4 tunnel 719 network diagram figure 216 network diagram for an ipv4 over ipv4 tunnel configuration procedure ■ configuration on router a # configure an ipv4 address for ethernet1/0. System-view [routera] interface ethernet 1/0 [routera-ethernet1/0] ip address 10.1.1.1 255.25...
Page 720
720 c hapter 49: t unneling c onfiguration ■ configuration on router b # configure an ipv4 address for ethernet1/0. System-view [routerb] interface ethernet 1/0 [routerb-ethernet1/0] ip address 10.1.3.1 255.255.255.0 [routerb-ethernet1/0] quit # configure an ipv4 address for serial 2/1 (the physical...
Page 721
Configuring ipv4 over ipv6 tunnel 721 0 packets input, 0 bytes 0 input error 0 packets output, 0 bytes 0 output error [routerb] display interface tunnel2 tunnel2 current state: up line protocol current state: up description: tunnel2 interface the maximum transmit unit is 64000 internet address is 10...
Page 722
722 c hapter 49: t unneling c onfiguration n for the configuration of the mtu of ipv6 packets sent over a tunnel interface, refer to the ipv6 mtu command in “configuring the interface mtu” on page 670 . C caution: ■ if the addresses of the tunnel interfaces at the two ends of a tunnel are not in the...
Page 723
Configuring ipv4 over ipv6 tunnel 723 network diagram figure 217 network diagram for an ipv4 over ipv6 tunnel configuration procedure ■ configuration on router a # enable the ipv6 forwarding function. System-view [routera] ipv6 # configure an ipv4 address for ethernet1/0. [routera] interface etherne...
Page 724
724 c hapter 49: t unneling c onfiguration # configure a static route from router a through the interface tunnel 1 to group 2. [routera] ip route-static 30.1.3.0 255.255.255.0 tunnel 1 ■ configuration on router b # enable the ipv6 forwarding function. System-view [routerb] ipv6 # configure an ipv4 a...
Page 725
Configuring ipv6 over ipv6 tunnel 725 description: tunnel1 interface the maximum transmit unit is 64000 internet address is 30.1.2.1/24 primary encapsulation is tunnel, aggregation id not set tunnel source 2002::0001:0001, destination 2002::0002:0001 tunnel encapsulation-limit is disable tunnel prot...
Page 726
726 c hapter 49: t unneling c onfiguration configuration procedure follow these steps to configure an ipv6 over ipv6 tunnel: n for the configuration of the mtu of ipv6 packets sent over a tunnel interface, refer to the ipv6 mtu command in “configuring the interface mtu” on page 670 . To do... Use th...
Page 727
Configuring ipv6 over ipv6 tunnel 727 c caution: ■ if the addresses of the tunnel interfaces at the two ends of a tunnel are not in the same subnet, a forwarding route through the tunnel to the peer must be configured so that the encapsulated packet can be forwarded normally. You can configure stati...
Page 728
728 c hapter 49: t unneling c onfiguration [routera] interface serial 2/0 [routera-serial2/0] ipv6 address 2002::11:1 64 [routera-serial2/0] quit # create the interface tunnel 1. [routera] interface tunnel 1 # configure an ipv6 address for the interface tunnel 1. [routera-tunnel1] ipv6 address 2002:...
Page 729
Configuring ipv6 over ipv6 tunnel 729 # configure the tunnel encapsulation mode. [routerb-tunnel2] tunnel-protocol ipv6-ipv6 # configure a source address for the interface tunnel 2 (ip address of serial 2/1). [routerb-tunnel2] source 2002::22:1 # configure a destination address for the interface tun...
Page 730
730 c hapter 49: t unneling c onfiguration [routera] ping ipv6 2002:3::1 ping 2002:3::1 : 56 data bytes, press ctrl_c to break reply from 2002:3::1 bytes=56 sequence=1 hop limit=64 time = 31 ms reply from 2002:3::1 bytes=56 sequence=2 hop limit=64 time = 1 ms reply from 2002:3::1 bytes=56 sequence=3...
Page 731: 6 U
50 ip v 6 u nicast p olicy r outing c onfiguration when configuring ipv6 unicast policy routing, go to these sections for information you are interested in: ■ “introduction to ipv6 unicast policy routing” on page 731 ■ “configuring ipv6 unicast policy routing” on page 731 ■ “displaying and maintaini...
Page 732
732 c hapter 50: ip v 6 u nicast p olicy r outing c onfiguration there are six types of apply clauses: apply ipv6-precedence, apply output-interface, apply ipv6-address next-hop, apply default output-interface, apply ipv6-address default next-hop, and apply destination-based-forwarding. You can spec...
Page 733
Configuring ipv6 unicast policy routing 733 n ■ if a policy node has neither if-match nor apply clauses configured, all packets can pass it and will not match against any other node. The statistics of ipv6 unicast policy routing will not be changed, though. ■ if a policy node has if-match clauses bu...
Page 734
734 c hapter 50: ip v 6 u nicast p olicy r outing c onfiguration follow these steps to enable ipv6 system policy routing: enabling ipv6 interface policy routing interface policy routing is applied to packets arriving on an interface. Only one policy can be referenced when policy routing is enabled o...
Page 735
Ipv6 unicast policy routing configuration examples 735 ■ node 10 indicates packets matching acl 3102 do not go through policy routing. Network diagram figure 219 network diagram for policy routing based on source address configuration procedure # define acls, making acl 3001 match tcp packets, and a...
Page 736
736 c hapter 50: ip v 6 u nicast p olicy r outing c onfiguration [router] interface ethernet 1/0 [router-ethernet1/0] ipv6 address 10::110 64 [router-ethernet1/0] ipv6 policy-based-route aaa configuring policy routing based on packet size network requirements the policy lab1 is applied to the interf...
Page 737
Ipv6 unicast policy routing configuration examples 737 [routera-pbr6-lab1-10] apply ipv6-address next-hop 150::2 [routera-pbr6-lab1-10] quit [routera] ipv6 policy-based-route lab1 permit node 20 [routera-pbr6-lab1-20] if-match packet-length 101 1000 [routera-pbr6-lab1-20] apply ipv6-address next-hop...
Page 738
738 c hapter 50: ip v 6 u nicast p olicy r outing c onfiguration.
Page 739: Erminal
51 t erminal a ccess c onfiguration introduction to terminal access terminal access refers to the connection of a terminal to a router through an asynchronous interface for data exchange with a front-end processor (fep) or another terminal through the router. Three types of network devices are used ...
Page 740
740 c hapter 51: t erminal a ccess c onfiguration router transports data transparently between the connected service terminal and fep to implement service interaction and processing. The tty terminal access solution implements the fixed terminal number function and offers many enhanced functions suc...
Page 741
Introduction to terminal access 741 functions, configuration, and applications. Figure 221 shows a typical terminal access application. Figure 221 typical application of terminal access as shown in the figure above, the arrowhead of a dotted line indicates the direction of an established tcp connect...
Page 742
742 c hapter 51: t erminal a ccess c onfiguration terminal access features figure 222 shows a terminal access implementation. “idle connection timeout” on page 744 all - “terminal number fixing” on page 744 tty - “data encryption” on page 745 tty - “automatic link establishment” on page 745 tty, tel...
Page 743
Introduction to terminal access 743 figure 222 network diagram for terminal access source address binding the principle of source ip address binding is to configure an ip address on a stable interface (the loopback interface or dialer interface is recommended) and use this address as the source ip a...
Page 744
744 c hapter 51: t erminal a ccess c onfiguration 1. Select vty(0): chuxu_zhu 2. Select vty(1): chuxu_bei 0. Quit input your choice: fast vty service switching the characteristics of banking services require each bank branch to provide services such as deposit and corporate services. However, a term...
Page 745
Introduction to terminal access 745 data encryption due to the extensive use of terminal access in banking systems, the requirements of data security become higher and higher. The terminal access data encryption function can be used to encrypt the data transmitted between the router and feps to impr...
Page 746
746 c hapter 51: t erminal a ccess c onfiguration terminal display language configuration the initiator generally sends some unsolicited information, such as menus and link establishment information, to the terminal. To meet different language needs, the prompt information can be displayed in either...
Page 747
Introduction to terminal access 747 terminal buffer parameter configuration you can set the parameters of terminal buffer, including whether to clear the buffer before receiving data, receive buffer size, transmit buffer threshold, and the maximum size of data to be sent to the terminal at one time....
Page 748
748 c hapter 51: t erminal a ccess c onfiguration terminal access specifications specifications of the terminal access initiator specifications of the terminal access receiving router specifications of the terminal access receiving fep configuration task list you need to perform configuration on the...
Page 749
Tty terminal access configuration 749 used for implementing the extended functions of terminal access. Display and maintenance commands are used for displaying and debugging terminal access. In terms of view, the configuration commands can be classified as the commands available in user view, comman...
Page 750
750 c hapter 51: t erminal a ccess c onfiguration n ■ for details about the async mode flow command, refer to the async mode command in “wan interface configuration” on page 99 . ■ after a template is applied on an interface, you need to set the flow control mode of the user interface corresponding ...
Page 751
Tty terminal access configuration 751 configure the automatic link establishment time auto-link time optional 0 seconds by default; that is, no automatic link establishment is performed. Bind a vpn instance bind vpn-instance vpn-name optional not configured by default enable data encryption data pro...
Page 752
752 c hapter 51: t erminal a ccess c onfiguration n ■ if both the global source ip address and the source ip address for a vty are configured, the one for the vty is used. ■ the tcp parameters must be configured before tcp connections are established. If you configure the parameters after a tcp conn...
Page 753
Tty terminal access configuration 753 exchange with the router-side programs. To configure your fep, refer to the related sections in “fep installation and configuration” on page 771 . Configuration example for tty terminal access network requirements the deposit services run on the unix server, who...
Page 754
754 c hapter 51: t erminal a ccess c onfiguration [sysname] interface loopback 0 [sysname-loopback0] ip address 2.2.2.1 255.255.0.0 [sysname-loopback0] quit [sysname] rta source-ip 2.2.2.1 # apply the template to the asynchronous serial interfaces. [sysname] interface async 1/0 [sysname-async1/0] as...
Page 755
Telnet terminal access configuration 755 3 add a route on the fep. # route add 2.2.2.1 -netmask 255.255.0.0 1.1.247.88 telnet terminal access configuration configuring the telnet initiator follow these steps to perform basic telnet initiator configuration: n ■ for details about the async mode flow c...
Page 756
756 c hapter 51: t erminal a ccess c onfiguration ■ for details about the flow-control software command, refer to the flow-control command in “user interface configuration” on page 2155 . Follow these steps to perform advanced telnet initiator configuration: to do... Use the command... Remarks enter...
Page 757
Telnet terminal access configuration 757 n ■ if both the global source ip address and the source ip address of a vty are configured, the one of the vty is used. ■ the parameters for tcp connections must be configured before the tcp connections are established. If you configure the parameters after a...
Page 758
758 c hapter 51: t erminal a ccess c onfiguration ■ the ascii value of the hotkey must be different from the ascii value of any other hotkey configured on the device. Otherwise, hotkey conflicts will occur. For example, the hotkey value cannot be set to 17 or 19 because these two values are used for...
Page 759
Rtc terminal access configuration 759 [sysname-rta-template-temp2] vty 0 screencode e!8q # configure the hotkey for vty 0 as . [sysname-rta-template-temp2] vty 0 hotkey 1 96 13 # configure vty 1. [sysname-rta-template-temp2] vty 1 telnet remote 10.110.96.54 [sysname-rta-template-temp2] vty 1 descrip...
Page 760
760 c hapter 51: t erminal a ccess c onfiguration the initiator of asynchronous rtc terminal access is an rtc client connected to the monitoring device. The receiver of asynchronous rtc terminal access is the rtc server connected to the monitored device. An rtc client can initiate a connection reque...
Page 761
Rtc terminal access configuration 761 to do... Use the command... Remarks enter system view system-view - configure the global source ip address for tcp connections rta source-ip ip-address optional not configured by default enter terminal template view rta template template-name - configure the aut...
Page 762
762 c hapter 51: t erminal a ccess c onfiguration n ■ to implement terminal access authentication, terminal access authentication must be configured on both the rtc server and the rtc client, and the authentication passwords must be the same for the authentication to succeed. ■ the bind vpn-instance...
Page 763
Rtc terminal access configuration 763 configuring the rtc receiver (rtc server) follow these steps to perform basic rtc receiver (rtc server) configuration: n ■ for details about the async mode flow command, refer to the async mode command in “wan interface configuration” on page 99 . ■ after a temp...
Page 764
764 c hapter 51: t erminal a ccess c onfiguration to do... Use the command... Remarks enter system view system-view - configure the global source ip address for tcp connections rta source-ip ip-address optional not configured by default enter terminal template view rta template template-name - confi...
Page 765
Rtc terminal access configuration 765 n ■ the port number specified for the vty application on the rtc client must be the same as the listening port number specified on the rtc server. ■ the terminal-number argument of the command vty rtc-server remote configured on the rtc server must be the same a...
Page 766
766 c hapter 51: t erminal a ccess c onfiguration network diagram figure 226 network diagram for asynchronous rtc terminal access configuration configuration procedure 1 configure the rtc server. # enable terminal access. System-view [sysname] rta server enable # set the listening port of the server...
Page 767
Rtc terminal access configuration 767 [sysname-rta-template-rtcclient] vty 0 rtc-client remote 10.111.95.1 0 9000 [sysname-rta-template-rtcclient] vty 0 password simple 123 # apply the template to the interface. [sysname] interface async 1/0 [sysname-async1/0] async mode flow [sysname-async1/0] rta ...
Page 768
768 c hapter 51: t erminal a ccess c onfiguration [peb] rta rtc-server listen-port 9000 # configure the terminal access template. [peb] rta template rtcs # configure vty 0 on the rtc server. [peb-rta-template-rtcs] vty 0 rtc-server remote 169.254.2.1 2 # bind the vpn instance to the template. [peb-r...
Page 770
770 c hapter 51: t erminal a ccess c onfiguration.
Page 771: Fep I
52 fep i nstallation and c onfiguration to implement terminal access with an fep as the receiver, the router-side program serving as the initiator must work together with the fep-side programs serving as the server that receives connection requests from the initiator. This chapter covers the install...
Page 772
772 c hapter 52: fep i nstallation and c onfiguration insert the floppy disk into the floppy drive of the unix server and then run the mount command to mount the floppy drive. # mount /dev/fd0 /mnt copy the executable files to the unix server. # cp /mnt/ttyd /etc/ttyd # cp /mnt/ttyadmcmd /etc/ttyadm...
Page 773
Installing and configuring sco openserver server 773 ftp> put ttyd ftp> put ttyadmcmd transfer the program ttyadm to the unix server in text format. Then, exit ftp. Ftp> ascii ftp> put ttyadm ftp> bye 4 on the unix server, change the file modes of the programs to the executable mode. # chmod u+x /et...
Page 774
774 c hapter 52: fep i nstallation and c onfiguration ttyp50/ptyp50 devices exist. Generally, ttyp and ptyp devices are present in pairs and each pair shares the same device number. # ls -l /dev/ttyp50 /dev/ptyp50 if pseudo terminals exist, the console displays the following information: crw-rw-rw- ...
Page 775
Installing and configuring sco openserver server 775 modifying system configuration file inittab check whether the pseudo terminals are configured in file inittab. Taking ttyp50 as example, edit file /etc/inittab and check whether the following line is present: c50:234:respawn:/etc/getty ttyp50 m if...
Page 776
776 c hapter 52: fep i nstallation and c onfiguration mode 1 operating mode of the ttyd process. It can be 0 for many-to-one mode or 1 for one-to-one mode. Currently, it must be set to 1. Nodelay 1 specifies the ttyd process to support (with a value of 1) or not to support (with a value of 0) the no...
Page 777
Installing and configuring sco openserver server 777 determines which router and which terminal on the router a pseudo terminal corresponds to. This guarantees terminal number fixing. For example, the above sample entry shows that pseudo terminal ttyp30 on the unix server corresponds to the terminal...
Page 778
778 c hapter 52: fep i nstallation and c onfiguration compat 1 specifies to be compatible with the previous router versions, but some terminal access features will not be available. The default is 0, indicating incompatibility with the previous router versions. The ttyd configuration file supports d...
Page 781
Installing and configuring sco openserver server 781 3 - terminate a ttyd process. 4 - terminate all the ttyd processes corresponding to a specified router ip address. 5 - terminate the ttyd process corresponding to a specified terminal. 6 - set the log output level. 7 - update the ttyd configuratio...
Page 782
782 c hapter 52: fep i nstallation and c onfiguration press to return. 4 terminate all the ttyd processes corresponding to a specified router ip address. From the process management submenu, select option 4 to display the following information: enter router ip address: here, you can terminate all th...
Page 783
Installing and configuring sco openserver server 783 here, after you enter the process number or terminal name and press , the system will prompt you to enter the new log output level by displaying the following information: enter the new log output level: here, the log output level for the correspo...
Page 784
784 c hapter 52: fep i nstallation and c onfiguration displaying system resource information in the main interface, select option 3 to enter the system resource submenu. Then, you can display system resource information by selecting an option in the following. The screen displays: ******************...
Page 785
Installing and configuring sco openserver server 785 streams allocation: config alloc free total max fail stream 4096 134 3962 10692 135 0 queues 566 271 295 21387 273 0 mblks 2319 445 1874 761868 2149 1 buffer headers 2746 1279 1467 52307 2654 0 class 1, 64 bytes 192 9 183 240804 172 0 class 2, 128...
Page 786
786 c hapter 52: fep i nstallation and c onfiguration from the router status submenu, select option 2 to display detailed information of ttys on the corresponding router. Following is part of the screen display: tty6 detail statistic interface used : async6 current state : ok flow control : stop cur...
Page 787
Installing and configuring sco unixware server 787 enter a terminal name to display all the statistics about the terminal. The following displays: process id. Parent process no. Tty device name router ip port no. Terminal no. Debugging level 12676 12674 ttyp55 10.110.96.44 1219 6 0 statistics: total...
Page 788
788 c hapter 52: fep i nstallation and c onfiguration 7 select [advanced options]. 8 select [pseudo ttys]. The default value is 32. Change the value to 256. 9 compile the kernel. # /etc/conf/bin/idbuild -b 10 reboot the fep. # init 6 then, the system can support up to 256 pseudo terminals. ■ you can...
Page 789
Installing and configuring sun os server 789 modifying route configuration file the terminal access router is usually connected to the unix server through wans and therefore located on an ip segment different from that of the unix server, in which case you must configure a route on the unix server. ...
Page 790
790 c hapter 52: fep i nstallation and c onfiguration 4 reboot the system. # reboot the number of supported pseudo terminals is now 176. Modifying the maximum number of files a process can open by default, each sun os process can open up to 64 files. If a unix server is to be connected with a number...
Page 791
Installing and configuring ibm aix server 791 enabling ttyd autorun at system startup refer to “enabling ttyd autorun at system startup” on page 779 . Installing and using ttyd administration program ttyadm refer to “installing and using ttyd administration program ttyadm” on page 780 . Installing a...
Page 792
792 c hapter 52: fep i nstallation and c onfiguration modifying system configuration file inittab 1 check whether the pseudo terminal has been configured in the inittab configuration file. Take the device ttya6 as an example. Edit the file /etc/inittab and check whether this file contains the follow...
Page 793
Installing and configuring hp-ux server 793 installing and configuring hp-ux server installing device drivers using the floppy disk refer to “using a floppy disk” on page 771 . Using ftp refer to “using ftp” on page 772 . Configuration prerequisites adding vtys if there are not enough pseudo termina...
Page 794
794 c hapter 52: fep i nstallation and c onfiguration modifying system configuration file inittab 1 check whether the pseudo terminal has been configured in the inittab configuration file. Take the device ttypa as an example. Edit the file /etc/inittab and check whether this file contains the follow...
Page 796
796 c hapter 52: fep i nstallation and c onfiguration [root@redhat root]# ulimit -a core file size (blocks, -c) 0 data seg size (kbytes, -d) unlimited file size (blocks, -f) unlimited max locked memory (kbytes, -l) 4 max memory size (kbytes, -m) unlimited open files (-n) 2048 pipe size (512 bytes, -...
Page 798
798 c hapter 52: fep i nstallation and c onfiguration.
Page 799: Erminal
53 t erminal a ccess t roubleshooting prompts on terminals no. Prompt description 1 (tty tty-number: vty-number starting connect to server fail!) creating a socket failed because, for example, no wan ip address is configured on the router. 2 (tty tty-number: vty-number fail to connect server-name!) ...
Page 800
800 c hapter 53: t erminal a ccess t roubleshooting terminal access troubleshooting check if there is any prompt displayed on the terminal 1 if there is a prompt displayed on the terminal refer to “prompts on terminals” on page 799 or “check whether the router and unix server can ping each other” on...
Page 801
Terminal access troubleshooting 801 cables, which are blue, are for telecom carriers. “bank” means that the 8as/16as (rj-45) cables which are white and labeled with “dumb terminal” are used for terminal access in banks. The following table describes the pins of 8as/16as cables. Terminal access conve...
Page 802
802 c hapter 53: t erminal a ccess t roubleshooting figure 228 terminal access joint detail for detailed cable descriptions, refer to the related manuals. 2 3-wire, 5-wire, and 8-wire asynchronous serial interface cables when a 3-wire asynchronous serial interface cable is used, since dsr/dtr and fl...
Page 804
804 c hapter 53: t erminal a ccess t roubleshooting now, you can press the test hotkey on the terminal. If the tcp connection between the terminal and the unix server is correct, the terminal screen displays “terminal to unix test ok!”. This means a tcp connection has been established between the ap...
Page 805
Terminal access troubleshooting 805 you can also use the enable command to configure a pseudo terminal as an active terminal, or use the disable command to configure a pseudo terminal as a dumb terminal. # enable ttyp50 2 the inittab system file configuration is correct. X. Refer to the “view the de...
Page 806
806 c hapter 53: t erminal a ccess t roubleshooting 6 fail: the swap is not enough to store the data, so some data is discarded cause: data from the router is not written into the pty device (pseudo terminal), making the buffer full and subsequent data discarded. Typically, this is because the pty d...
Page 807
Terminal access troubleshooting 807 if you cannot locate the problem, save the debugging information of both the router and the unix server and send it to a customer service engineer to locate it. Change the corresponding pseudo terminal on the unix server if the above-mentioned procedure cannot sol...
Page 808
808 c hapter 53: t erminal a ccess t roubleshooting.
Page 809: Erminal
54 t erminal a ccess faq if there are insufficient stream resources on the unix server, modify kernel parameters. If an fep is connected to too many terminals, you need to modify the unix kernel of the fep to increase stream resources to avoid insufficient stream resources in operation. You can view...
Page 810
810 c hapter 54: t erminal a ccess faq 5 under the [configuration tunables] title, select [12 streams] to enter the level 4 interface. 6 set the [nstrpages] field to 2000 (the default is 500). 7 exit to the level 2 interface and select [relink kernel] to recompile the kernel. 8 exit scoadmin and reb...
Page 811
Terminal access troubleshooting 811 ■ the terminal has baud rates different from those of the asynchronous interface. ■ the corresponding device is not configured in file inittab. ■ the router and the unix server use different application modes, for example, the unix server may use the many-to-one m...
Page 812
812 c hapter 54: t erminal a ccess faq if other configurations are all correct but the log shows that some pseudo terminals cannot be opened, check whether the terminals are under directory /dev. If not, try to use another existent pseudo terminal or create the pseudo terminal. If yes, check whether...
Page 813
Terminal access troubleshooting 813 the terminal cannot display the login interface after configuration and no error message is logged on the unix server check the configuration file to see whether the same application mode is configured on the router and the unix server. This problem occurs if the ...
Page 814
814 c hapter 54: t erminal a ccess faq.
Page 815: Ip R
55 ip r outing o verview go to these sections for information you are interested in: ■ “ip routing and routing table” on page 815 ■ “routing protocol overview” on page 817 ■ “displaying and maintaining a routing table” on page 821 ip routing and routing table routing routing in the internet is achie...
Page 816
816 c hapter 55: ip r outing o verview ■ ip address of the next hop: specifies the address of the next router on the path. If only the outbound interface is configured, its address will be the ip address of the next hop. ■ priority for the route. Routes to the same destination but having different n...
Page 817
Routing protocol overview 817 figure 229 a sample routing table routing protocol overview static routing and dynamic routing static routing is easy to configure and requires less system resources. It works well in small, stable networks with simple topologies. Its major drawback is that you must per...
Page 818
818 c hapter 55: ip r outing o verview operational scope ■ interior gateway protocols (igps): work within an autonomous system, typically includes rip, ospf, and is-is. ■ exterior gateway protocols (egps): work between autonomous systems. The most popular one is bgp. N an autonomous system refers to...
Page 819
Routing protocol overview 819 n ■ the smaller the priority value, the higher the priority. ■ the priority for a direct route is always 0, which you cannot change. Any other type of routes can have their priorities manually configured. 256 represents a route from an untrustworthy source. ■ each stati...
Page 820
820 c hapter 55: ip r outing o verview protocol has its own route redistribution mechanism. For detailed information, refer to “routing policy configuration” on page 991 . Configuring load sharing load sharing is implemented in the following ways: ■ flow-based load sharing: after enabled with fast f...
Page 822
822 c hapter 55: ip r outing o verview configuration example bandwidth-based load sharing configuration example network requirements on router a, there are three equal-cost routes to the destination network 10.2.1.0 /24, as shown below: display fib destination/mask nexthop flag timestamp interface 1...
Page 823
Configuration example 823 # display bandwidths of the three interfaces. [sysname] display load-sharing ip address 10.2.1.0 24 there are/is totally 3 route entry(s) to the same destination network. Nexthop packet(s) bandwidth[kb] flow(s) interface 10.1.2.2 142824 100 0 atm1/0 10.1.1.2 285648 200 0 et...
Page 824
824 c hapter 55: ip r outing o verview.
Page 825: Bgp C
56 bgp c onfiguration border gateway protocol (bgp) is a dynamic inter-as route discovery protocol. When configuring bgp, go to these sections for information you are interested in: ■ “bgp overview” on page 825 ■ “bgp configuration task list” on page 840 ■ “configuring bgp basic functions” on page 8...
Page 826
826 c hapter 56: bgp c onfiguration a router advertising bgp messages is called a bgp speaker, which exchanges new routing information with other bgp speakers. When a bgp speaker receives a new route or a route better than the current one from another as, it will advertise the route to all the other...
Page 827
Bgp overview 827 open after a tcp connection is established, the first message sent by each side is an open message for peer relationship establishment. The open message contains the following fields: figure 232 bgp open message format ■ version: this 1-octet unsigned integer indicates the protocol ...
Page 828
828 c hapter 56: bgp c onfiguration ■ unfeasible routes length: the total length of the withdrawn routes field in octets. A value of 0 indicates neither route is being withdrawn from service, nor withdrawn routes field is present in this update message. ■ withdrawn routes: this is a variable length ...
Page 829
Bgp overview 829 bgp path attributes classification of path attributes path attributes fall into four categories: ■ well-known mandatory: must be recognized by all bgp routers and must be included in every update message. Routing information error occurs without this attribute. ■ well-known discreti...
Page 830
830 c hapter 56: bgp c onfiguration determine ass to route massages back. The number of the as closest with the receiver’s as is leftmost, as shown below: figure 236 as_path attribute in general, a bgp router does not receive routes containing the local as number to avoid routing loops. N the curren...
Page 831
Bgp overview 831 configured, the next_hop attribute will be modified. For load-balancing information, refer to “bgp route selection” on page 832 . Figure 237 next_hop attribute 4 med (multi_exit_disc) the med attribute is exchanged between two neighboring ass, each of which will not advertise the at...
Page 832
832 c hapter 56: bgp c onfiguration this attribute is exchanged between ibgp peers only, thus not advertised to any other as. It indicates the priority of a bgp router. Local_pref is used to determine the best route for traffic leaving the local as. When a bgp router obtains from several ibgp peers ...
Page 833
Bgp overview 833 ■ select the route with the shortest as-path ■ select origin igp, egp, incomplete routes in turn ■ select the route with the lowest med value ■ select routes learned from ebgp, confederation, ibgp in turn ■ select the route with the smallest next hop cost ■ select the route with the...
Page 834
834 c hapter 56: bgp c onfiguration figure 240 network diagram for bgp load balancing in the above figure, router d and router e are ibgp peers of router c. Router a and router b both advertise a route destined for the same destination to router c. If load balancing is configured and the two routes ...
Page 835
Bgp overview 835 route recursion. Router c has no idea about the route 8.0.0.0/8, so it discards the packet. Figure 241 ibgp and igp synchronization if synchronization is configured in this example, the ibgp router (router d) checks the learned ibgp route from its igp routing table first. Only the r...
Page 836
836 c hapter 56: bgp c onfiguration bgp route dampening uses a penalty value to judge the stability of a route. The bigger the value, the less stable the route. Each time a route flap occurs (the state change of a route from active to inactive is a route flap), bgp adds a penalty value (1000, which ...
Page 837
Bgp overview 837 besides using the well-known community attribute, you can define the extended community attribute using a community list to help define a routing policy. Route reflector ibgp peers should be fully meshed to maintain connectivity. Suppose there are n routers in an as, the number of i...
Page 838
838 c hapter 56: bgp c onfiguration when clients of a route reflector are fully meshed, route reflection is unnecessary because it consumes more bandwidth resources. The system supports using related commands to disable route reflection in this case. N after route reflection is disabled between clie...
Page 839
Bgp overview 839 3 the gr session between the gr restarter and its peer goes down when the gr restarter restarts bgp. The gr capable peer will mark all routes associated with the gr restarter as stale. However, during the configured gr time, it still uses these routes for packet forwarding, ensuring...
Page 840
840 c hapter 56: bgp c onfiguration protocols and standards ■ rfc1771: a border gateway protocol 4 (bgp-4) ■ rfc2858: multiprotocol extensions for bgp-4 ■ rfc3392: capabilities advertisement with bgp-4 ■ rfc2918: route refresh capability for bgp-4 ■ rfc2439: bgp route flap damping ■ rfc1997: bgp com...
Page 841
Configuring bgp basic functions 841 configuring bgp basic functions the section describes bgp basic configuration. N ■ this section does not differentiate between bgp and mp-bgp. ■ since bgp employs tcp, you need to specify ip addresses of peers, which may not be neighboring routers. ■ using logical...
Page 842
842 c hapter 56: bgp c onfiguration c caution: ■ it is required to specify for a bgp router a router id, a 32-bit unsigned integer and the unique identifier of the router in the as. ■ you can specify a router id manually. If not, the system selects an ip address as the router id. The selection seque...
Page 843
Controlling route distribution and reception 843 controlling route distribution and reception prerequisites before configuring this task, you have completed bgp basic configuration. Configuring bgp route redistribution bgp can advertise the routing information of the local as to peering ass, but it ...
Page 844
844 c hapter 56: bgp c onfiguration advertising a default route to a peer or peer group to advertise a default route to a peer or peer group, use the following commands: n with the peer default-route-advertise command executed, the router sends a default route with the next hop being itself to the s...
Page 845
Controlling route distribution and reception 845 c caution: only routes passing the specified filter can be advertised. Configuring bgp route reception policy to configure bgp routing reception policy, use the following commands: filter redistributed routes when advertising them filter-policy { acl-...
Page 846
846 c hapter 56: bgp c onfiguration c caution: ■ only routes permitted by the specified filter policy can be added into the local bgp routing table. ■ members of a peer group can have different inbound route filter policies from the peer group. Enabling bgp and igp route synchronization by default, ...
Page 848
848 c hapter 56: bgp c onfiguration c caution: ■ using a routing policy can set a preference for routes meeting its filtering conditions. Routes not meeting the conditions use the default preference. ■ if other conditions are identical, the route with the smallest med value is selected as the best e...
Page 849
Tuning and optimizing bgp networks 849 ■ the peer substitute-as command is used only in specific networking environments. Inappropriate use of the command may cause routing loops. Tuning and optimizing bgp networks this task involves the following parts: 1 configure bgp timers after establishing a b...
Page 850
850 c hapter 56: bgp c onfiguration configure bgp timers configure keepalive interval and holdtime timer keepalive keepalive hold holdtime optional the keepalive interval defaults to 60 seconds, holdtime defaults to 180 seconds. Configure keepalive interval and holdtime for a peer/peer group peer { ...
Page 851
Configuring a large scale bgp network 851 c caution: ■ the maximum keepalive interval should be 1/3 of the holdtime and no less than 1 second. The holdtime is no less than 3 seconds unless it is set to 0. ■ the intervals set with the peer timer command are preferred to those set with the timer comma...
Page 852
852 c hapter 56: bgp c onfiguration c caution: ■ you need not specify the as number when creating an ibgp peer group. ■ if there are peers in a peer group, you can neither change the as number of the group nor use the undo command to remove the as number ■ you need specify the as number for each pee...
Page 853
Configuring bgp graceful restart 853 configuring a bgp route reflector to configure a bgp route reflector, use the following commands: c caution: ■ in general, it is not required to make clients of a route reflector fully meshed. The route reflector forwards routing information between clients. If c...
Page 854
854 c hapter 56: bgp c onfiguration n one device can act as both the gr restarter and gr helper at the same time. N ■ in general, the maximum time allowed for the peer to reestablish a bgp session should be less than the holdtime carried in the open message. ■ the end-of-rib marker can be used to in...
Page 855
Displaying and maintaining bgp configuration 855 displaying and maintaining bgp configuration displaying bgp configuration to do... Use the command... Remarks display peer group information display bgp group [ group-name ] available in any view display advertised bgp routing information display bgp ...
Page 856
856 c hapter 56: bgp c onfiguration resetting bgp connections clearing bgp information bgp typical configuration examples bgp basic configuration network requirements in figure 246 are all bgp routers. Between router a and router b is an ebgp connection. Router b, router c and router d are ibgp full...
Page 857
Bgp typical configuration examples 857 system-view [routerb] bgp 65009 [routerb-bgp] router-id 2.2.2.2 [routerb-bgp] peer 9.1.1.2 as-number 65009 [routerb-bgp] peer 9.1.3.2 as-number 65009 [routerb-bgp] quit # configure router c. System-view [routerc] bgp 65009 [routerc-bgp] router-id 3.3.3.3 [route...
Page 858
858 c hapter 56: bgp c onfiguration you can find router b has established bgp connections to other routers. # display routing table information on router a. [routera] display bgp routing-table total number of routes: 1 bgp local router id is 1.1.1.1 status codes: * - valid, > - best, d - damped, h -...
Page 859
Bgp typical configuration examples 859 origin : i - igp, e - egp, ? - incomplete network nexthop med locprf prefval path/ogn *> 8.0.0.0 0.0.0.0 0 0 i *> 9.1.1.0/24 200.1.1.1 0 0 65009? *> 9.1.3.0/24 200.1.1.1 0 0 65009? * 200.1.1.0 200.1.1.1 0 0 65009? # display bgp routing table information on rout...
Page 860
860 c hapter 56: bgp c onfiguration network diagram figure 247 network diagram for bgp and igp interaction configuration configuration procedure 1 configure ip addresses for interfaces (omitted) 2 configure ospf (omitted) 3 configure the ebgp connection # configure router a. System-view [routera] bg...
Page 861
Bgp typical configuration examples 861 origin : i - igp, e - egp, ? - incomplete network nexthop med locprf prefval path/ogn *> 8.1.1.0/24 0.0.0.0 0 0 i *> 9.1.1.0/24 3.1.1.1 0 0 65009? *> 9.1.2.0/24 3.1.1.1 1563 0 65009? # configure ospf to redistribute routes from bgp on router b. [routerb] ospf [...
Page 862
862 c hapter 56: bgp c onfiguration 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 15/37/47 ms bgp load balancing and med attribute configuration network requirements this example describes how to configure bgp load balancing, and how to use the med attribute...
Page 863
Bgp typical configuration examples 863 # configure router c. System-view [routerc] bgp 65009 [routerc-bgp] router-id 3.3.3.3 [routerc-bgp] peer 200.1.2.2 as-number 65008 [routerc-bgp] peer 9.1.1.1 as-number 65009 [routerc-bgp] network 9.1.1.0 255.255.255.0 [routerc-bgp] quit # display bgp routing ta...
Page 864
864 c hapter 56: bgp c onfiguration [routerb] bgp 65009 [routerb-bgp] default med 100 # display bgp routing table information on router a. [routera] display bgp routing-table total number of routes: 3 bgp local router id is 1.1.1.1 status codes: * - valid, > - best, d - damped, h - history, i - inte...
Page 865
Bgp typical configuration examples 865 # configure router b. System-view [routerb] bgp 20 [routerb-bgp] router-id 2.2.2.2 [routerb-bgp] peer 200.1.2.1 as-number 10 [routerb-bgp] peer 200.1.3.2 as-number 30 [routerb-bgp] quit # configure router c. System-view [routerc] bgp 30 [routerc-bgp] router-id ...
Page 866
866 c hapter 56: bgp c onfiguration # apply the routing policy. [routera] bgp 10 [routera-bgp] peer 200.1.2.2 route-policy comm_policy export [routera-bgp] peer 200.1.2.2 advertise-community # display bgp routing table information on router b. [routerb] display bgp routing-table 9.1.1.0 bgp local ro...
Page 867
Bgp typical configuration examples 867 # configure router a system-view [routera] bgp 100 [routera-bgp] peer 192.1.1.2 as-number 200 # advertise network 1.0.0.0/8 to the bgp routing table [routera-bgp] network 1.0.0.0 [routera-bgp] quit # configure router b system-view [routerb] bgp 200 [routerb-bgp...
Page 868
868 c hapter 56: bgp c onfiguration # display the bgp routing table on router d [routerd] display bgp routing-table total number of routes: 1 bgp local router id is 200.1.2.1 status codes: * - valid, > - best, d - damped, h - history, i - internal, s - suppressed, s - stale origin : i - igp, e - egp...
Page 869
Bgp typical configuration examples 869 system-view [routera] bgp 65001 [routera-bgp] router-id 1.1.1.1 [routera-bgp] confederation id 200 [routera-bgp] confederation peer-as 65002 65003 [routera-bgp] peer 10.1.1.2 as-number 65002 [routera-bgp] peer 10.1.1.2 next-hop-local [routera-bgp] peer 10.1.2.2...
Page 870
870 c hapter 56: bgp c onfiguration [routere-bgp] confederation id 200 [routere-bgp] confederation 200 [routere-bgp] peer 10.1.4.1 as-number 65001 [routere-bgp] peer 10.1.5.1 as-number 65001 [routere-bgp] quit 4 configure the ebgp connection between as 100 and as 200. # configure router a. [routera]...
Page 871
Bgp typical configuration examples 871 *>i 9.1.1.0/24 10.1.3.1 0 100 0 100i [routerd] display bgp routing-table 9.1.1.0 bgp local router id : 4.4.4.4 local as number : 65001 paths: 1 available, 1 best bgp routing table entry information of 9.1.1.0/24: from : 10.1.3.1 (1.1.1.1) relay nexthop : 0.0.0....
Page 872
872 c hapter 56: bgp c onfiguration system-view [routerb] ospf [routerb-ospf] area 0 [routerb-ospf-1-area-0.0.0.0] network 192.1.1.0 0.0.0.255 [routerb-ospf-1-area-0.0.0.0] network 194.1.1.0 0.0.0.255 [routerb-ospf-1-area-0.0.0.0] quit [routerb-ospf-1] quit # configure router c system-view [routerc]...
Page 873
Bgp typical configuration examples 873 [routerd] bgp 200 [routerd-bgp] peer 194.1.1.2 as-number 200 [routerd-bgp] peer 195.1.1.2 as-number 200 [routerd-bgp] quit 4 configure different attribute values for the route 1.0.0.0/8 to make router d give priority to the route learned from router c. ■ specif...
Page 874
874 c hapter 56: bgp c onfiguration [routerc] acl number 2000 [routerc-acl-basic-2000] rule permit source 1.0.0.0 0.255.255.255 [routerc-acl-basic-2000] quit # define routing policy localpref on router c to set the local priority of route 1.0.0.0/8 to 200 (the default is 100). [routerc] route-policy...
Page 875
Troubleshooting bgp configuration 875 5 check whether a route to the peer is available in the routing table. 6 use the ping command to check connectivity. 7 use the display tcp status command to check the tcp connection. 8 check whether an acl disabling tcp port 179 is configured..
Page 876
876 c hapter 56: bgp c onfiguration.
Page 877: Is-Is C
57 is-is c onfiguration when configuring is-is, go to these sections for information you are interested in: ■ “is-is overview” on page 877 ■ “is-is configuration task list” on page 892 ■ “configuring is-is basic functions” on page 893 ■ “configuring is-is routing information control” on page 894 ■ “...
Page 878
878 c hapter 57: is-is c onfiguration ■ link state protocol data unit (lsp). Each is can generate an lsp which contains all the link state information of the is. Each is collects all the lsps in the local area to generate its own lsdb. ■ network protocol data unit (npdu). An npdu is a network layer ...
Page 879
Is-is overview 879 ■ extend each decimal number of the ip address to 3 digits by adding 0s from the left, like 168.010.001.001; ■ divide the extended ip address into 3 sections with 4 digits in each section to get the system id 1680.1000.1001. There are other methods to define a system id. Just make...
Page 880
880 c hapter 57: is-is c onfiguration 2 level-2 router the level-2 router establishes the neighbor relationships with the level-2 and level-1-2 routers in the same or in different areas. It maintains a level-2 lsdb which contains inter area routing information. All the level-2 and level-1-2 routers ...
Page 881
Is-is overview 881 backbone together with the level-2 routers. There is no area defined as the backbone in this topology. The backbone is composed of all contiguous level-2 and level-1-2 routers which can reside in different areas. Figure 255 is-is topology n the is-is backbone does not need to be a...
Page 882
882 c hapter 57: is-is c onfiguration routing information of other areas, the level-1 router can make a better routing choice for the packets destined outside the area. Is-is network type network type is-is supports two network types: ■ broadcast network, such as ethernet, token-ring. ■ point-to-poi...
Page 883
Is-is overview 883 is-is pdu format pdu header format the is-is packets are encapsulated into link layer frames. The protocol data unit (pdu) consists of two parts, the headers and the variable length field, where the headers can be further divided into the common header and the specific header. The...
Page 884
884 c hapter 57: is-is c onfiguration hello the hello packet is used by routers to establish and maintain the neighbor relationship. It is also called is-to-is hello pdu (iih). For broadcast network, the level-1 router uses the level-1 lan iih; and the level-2 router uses the level-2 lan iih. The p2...
Page 885
Is-is overview 885 figure 260 p2p iih format instead of the priority and lan id fields in the lan iih, the p2p iih has a local circuit id field. Lsp packet format the link state pdus (lsp) carries link state information. There are two types: level-1 lsp and level-2 lsp. The level-2 lsp is sent by th...
Page 886
886 c hapter 57: is-is c onfiguration figure 261 l1/l2 lsp format ■ pdu length: total length of the pdu in bytes. ■ remaining lifetime: lsp remaining lifetime in seconds. ■ lsp id: consists of the system id, the pseudonode id (one byte) and the lsp fragment number (one byte). ■ sequence number: lsp ...
Page 887
Is-is overview 887 figure 262 lsdb overload ■ is type: type of the router generating the lsp. Snp format the sequence number pdu (snp) confirms the latest received lsps. It is similar to the acknowledge packet, but more efficient. Snp contains complete snp (csnp) and partial snp (psnp), which are fu...
Page 888
888 c hapter 57: is-is c onfiguration figure 264 shows the psnp packet format. Figure 264 l1/l2 psnp format clv the variable fields of pdu are composed of multiple code-length-value (clv) triplets. Figure 265 shows the clv format. Figure 265 clv format table 42 shows different pdus contain different...
Page 889
Is-is overview 889 code 1 to 10 of clv are defined in iso 10589 (code 3 and 5 are not shown in the table), and others are defined in rfc 1195. Is-is features supported multiple instances and processes is-is supports multiple instances and processes. Multiple processes allow a designated is-is proces...
Page 890
890 c hapter 57: is-is c onfiguration (0 for a common lsp or non-zero for a pseudonode lsp), and lsp number (lsp fragment number) of the node or pseudo node that generated the lsp. The 1-byte lsp number field, allowing a maximum of only 256 fragments to be generated by an is-is router, limits the am...
Page 891
Is-is overview 891 ■ mode-1: it applies to a network where some routers do not support lsp fragment extension. In this mode, an adjacency is formed between the originating system and each virtual system, with the link cost from the originating system to each virtual system as 0. Thus, each virtual s...
Page 892
892 c hapter 57: is-is c onfiguration ■ rfc 3567 - intermediate system to intermediate system (is-is) cryptographic authentication ■ rfc 3719 - recommendations for interoperable networks using is-is ■ rfc 3786 - extending the number of is-is lsp fragments beyond the 256 limit ■ rfc 3787 - recommenda...
Page 893
Configuring is-is basic functions 893 configuring is-is basic functions configuration prerequisites before the configuration, accomplish the following tasks first: ■ configure the link layer protocol. ■ configure an ip address for each interface, and make sure all nodes are reachable. Configuration ...
Page 894
894 c hapter 57: is-is c onfiguration n if a router’s type is configured as level-1 or level-2, the type of interfaces must be the same, which cannot be changed using the isis circuit-level command. However, an interface’s type can be changed with this command when the router’s type is level-1-2 for...
Page 895
Configuring is-is routing information control 895 configuring is-is link cost there are three ways to configure the interface link cost, in descending order of interface costs: ■ interface cost: assign a link cost for a single interface. ■ global cost: assign a link cost for all interfaces. ■ automa...
Page 896
896 c hapter 57: is-is c onfiguration n in the case no interface cost is specified in interface view or system view and automatic cost calculation is enabled ■ when the cost style is wide or wide-compatible, is-is automatically calculates the interface cost based on the interface bandwidth, using th...
Page 897
Configuring is-is routing information control 897 n the cost of the summary route is the lowest cost among those summarized routes. Advertising a default route follow these steps to advertise a default route: n the default route is only advertised to routers at the same level. You can use a routing ...
Page 898
898 c hapter 57: is-is c onfiguration configuring is-is route leaking with this feature enabled, the level-1-2 router can advertise both level-1 and level-2 area routing information to the level-1 router. Follow these steps to configure is-is route leaking: n ■ if a filter policy is specified, only ...
Page 899
Tuning and optimizing is-is network 899 follow these steps to configure a dis priority for an interface: n if multiple routers in the broadcast network have the same highest dis priority, the router with the highest mac address becomes the dis. This rule applies even all routers’ dis priority is 0. ...
Page 900
900 c hapter 57: is-is c onfiguration ■ on a point-to-point link, if there is no response to an lsp sent by the local router within the specified retransmission interval, the lsp is considered lost, and the same lsp will be retransmitted. On broadcast links, responses to the sent lsps are not requir...
Page 901
Tuning and optimizing is-is network 901 n note the following when enabling lsp fragment extension ■ after lsp fragment extension is enabled in an is-is process, the mtus of all the interfaces with this is-is process enabled must not be less than 512; otherwise, lsp fragment extension will not take e...
Page 902
902 c hapter 57: is-is c onfiguration configuring dynamic host name mapping follow these steps to configure the dynamic host name mapping: n the local host name on the local is overwrites the remote host name on the remote is. Configuring is-is authentication for area authentication, the area authen...
Page 903
Tuning and optimizing is-is network 903 the authentication configured on an interface applies to the hello packet in order to authenticate neighbors. All interfaces within a network must share the same authentication password at the same level. Follow these steps to configure the authentication func...
Page 904
904 c hapter 57: is-is c onfiguration logging the adjacency changes follow these steps to configure this task: n with this feature enabled, the state information of the adjacency is displayed on the configuration terminal. Enabling an interface to send small hello packets follow these steps to enabl...
Page 905
Displaying and maintaining is-is configuration 905 the graceful restart interval on a router is used as the holdtime in the is-is hello pdus so that its neighbors can maintain the adjacencies within the interval after the router restarts. By setting the sa (suppress-advertisement) bit in the hello p...
Page 906
906 c hapter 57: is-is c onfiguration is-is configuration example is-is basic configuration network requirements as shown in figure 266 , router a, b, c and router d are in an is-is autonomous system. Router a and router b are level-1 routers, router d is a level-2 router, and router c is a level-1-...
Page 907
Is-is configuration example 907 configuration procedure 1 configure ip addresses for interfaces (omitted) 2 configure is-is # configure router a system-view [routera] isis 1 [routera-isis-1] is-level level-1 [routera-isis-1] network-entity 10.0000.0000.0001.00 [routera-isis-1] quit [routera] interfa...
Page 908
908 c hapter 57: is-is c onfiguration 3 verify the configuration # display the is-is lsdb information of each router to check the integrity of the lsp. [routera] display isis lsdb database information for isis(1) -------------------------------- level-1 link state database lspid seq num checksum hol...
Page 909
Is-is configuration example 909 ------------------------------------------------------------------------ 0000.0000.0003.00-00 0x00000007 0xbb56 910 100 0/0/0 0000.0000.0004.00-00* 0x00000005 0xd086 791 84 0/0/0 *-self lsp, +-self lsp(extended), att-attached, p-partition, ol-overload # display the is...
Page 910
910 c hapter 57: is-is c onfiguration 192.168.0.0/24 10 null s2/0 direct r/l/- 10.1.1.0/24 20 null s2/0 192.168.0.1 r/-/- 10.1.2.0/24 20 null s2/0 192.168.0.1 r/-/- 172.16.0.0/16 10 null eth1/0 direct r/l/- flags: d-direct, r-added to rm, l-advertised in lsps, u-up/down bit set dis selection configu...
Page 911
Is-is configuration example 911 [routerb] interface ethernet 1/0 [routerb-ethernet1/0] isis enable 1 [routerb-ethernet1/0] quit # configure router c. System-view [routerc] isis 1 [routerc-isis-1] network-entity 10.0000.0000.0003.00 [routerc-isis-1] is-level level-1 [routerc-isis-1] quit [routerc] in...
Page 912
912 c hapter 57: is-is c onfiguration [routerc] display isis interface interface information for isis(1) --------------------------------- interface: ethernet1/0 id ipv4.State ipv6.State mtu type dis 001 up down 1497 l1/l2 yes/no # display information about is-is interfaces of router d. [routerd] di...
Page 913
Is-is configuration example 913 id ipv4.State ipv6.State mtu type dis 001 up down 1497 l1/l2 yes/yes n after the dis priority configuration, you can see router a is the dis for level-1-2, and the pseudonode is 0000.0000.0001.01. # display information about is-is neighbors and interfaces of router c....
Page 914
914 c hapter 57: is-is c onfiguration network diagram figure 268 network diagram for is-is-based gr configuration configuration procedure 1 configure ip addresses of the interfaces on each router and configure is-is. Follow figure 268 to configure the ip address and subnet mask of each interface on ...
Page 915
Is-is configuration example 915 -------------------------------------------------------------------- is-is(1) level-1 restart status restart interval: 150 sa bit supported total number of interfaces = 1 restart status: restarting number of lsps awaited: 3 t3 timer status: remaining time: 239 t2 time...
Page 916
916 c hapter 57: is-is c onfiguration.
Page 917: Ospf C
58 ospf c onfiguration open shortest path first (ospf) is a link state based interior gateway protocol developed by the ospf working group of the internet engineering task force (ietf). At present, ospf version 2 (rfc2328) is used. When configuring ospf, go to these sections for information you are ...
Page 918
918 c hapter 58: ospf c onfiguration ■ multicast: supports packet multicasting on some types of links. Basic concepts autonomous system a set of routers using the same routing protocol to exchange routing information constitute an autonomous system (as). Ospf route computation ospf route computation...
Page 919
Introduction to ospf 919 lsa types ospf sends routing information in lsas, which, as defined in rfc 2328, have the following types: ■ router lsa: type-1 lsa, originated by all routers, flooded throughout a single area only. This lsa describes the collected states of the router’s interfaces to an are...
Page 920
920 c hapter 58: ospf c onfiguration in addition, as the topology of a large network is prone to changes, enormous ospf packets may be created, reducing bandwidth utilization. Each topology change makes all routers perform route calculation. To solve this problem, ospf splits an as into multiple are...
Page 921
Introduction to ospf 921 4 autonomous system border router (asbr) the router exchanging routing information with another as is an asbr, which may not reside on the boundary of the as. It can be an internal router or area border router. Figure 270 ospf router types backbone area and virtual links an ...
Page 922
922 c hapter 58: ospf c onfiguration figure 271 virtual link application 1 another application of virtual links is to provide redundant links. If the backbone area cannot maintain internal connectivity due to a physical link failure, configuring a virtual link can guarantee logical connectivity in t...
Page 923
Introduction to ospf 923 ■ a (totally) stub area cannot have an asbr because as external routes cannot be distributed into the stub area. ■ virtual links cannot transit (totally) stub areas. Nssa area similar to a stub area, an nssa area imports no as external lsa (type5 lsa) but can import type7 ls...
Page 924
924 c hapter 58: ospf c onfiguration ospf has two types of route summarization: 1 abr route summarization to distribute routing information to other areas, an abr generates type3 lsas on a per network segment basis for an attached non-backbone area. If contiguous network segments are available in th...
Page 925
Introduction to ospf 925 ■ nbma (non-broadcast multi-access): when the link layer protocol is frame relay, atm or x.25, ospf considers the network type as nbma by default. Packets on these networks are sent to unicast addresses. ■ p2mp (point-to-multipoint): by default, ospf considers no link layer ...
Page 926
926 c hapter 58: ospf c onfiguration become the new dr in a very short period by avoiding adjacency establishment and dr reelection. Meanwhile, other routers elect another bdr, which requires a relatively long period but has no influence on routing calculation. Other routers, also known as drothers ...
Page 927
Introduction to ospf 927 figure 276 ospf packet format ospf packet header ospf packets are classified into five types that have the same packet header, as shown below. Figure 277 ospf packet header ■ version: ospf version number, which is 2 for ospfv2. ■ type: ospf packet type from 1 to 5, correspon...
Page 928
928 c hapter 58: ospf c onfiguration figure 278 hello packet format major fields: ■ network mask: the network mask associated with the router’s sending interface. If two routers have different network masks, they cannot become neighbors. ■ hellointerval: the interval between the router’s hello packe...
Page 929
Introduction to ospf 929 figure 279 dd packet format major fields: ■ interface mtu: the size in bytes of the largest ip datagram that can be sent out the associated interface, without fragmentation. ■ i (initial) the init bit, which is set to 1 if the packet is the first packet in the sequence of da...
Page 930
930 c hapter 58: ospf c onfiguration figure 280 lsr packet format major fields: ■ ls type: the type number of the lsa to be requested, type 1 for example indicates the router lsa ■ link state id: determined by lsa type ■ advertising router: the id of the router that sent the lsa lsu packet lsu (link...
Page 931
Introduction to ospf 931 figure 282 lsack packet format lsa header format all lsas have the same header, as shown in the following figure. Figure 283 lsa header format major fields: ■ ls age: the time in seconds elapsed since the lsa was originated. A lsa ages in the lsdb (added 1 per second), but d...
Page 932
932 c hapter 58: ospf c onfiguration formats of lsas 1 router lsa figure 284 router lsa format major fields: ■ link state id: the id of the router that originated the lsa. ■ v (virtual link): set to 1 if the router that originated the lsa is a virtual link endpoint. ■ e (external): set to 1 if the r...
Page 933
Introduction to ospf 933 figure 285 network lsa format major fields: ■ link state id: the interface address of the dr ■ network mask: the mask of the network (a broadcast or nbma network) ■ attached router: the ids of the routers, which are adjacent to the dr, including the dr itself 3 summary lsa n...
Page 934
934 c hapter 58: ospf c onfiguration n a type3 lsa can be used to advertise a default route, having the link state id and network mask set to 0.0.0.0. 4 as external lsa an as external lsa originates from an asbr, describing routing information to a destination outside the as. Figure 287 as external ...
Page 935
Introduction to ospf 935 figure 288 nssa external lsa format ospf features supported multi-process with multi-process support, multiple ospf processes can run on a router simultaneously and independently. Routing information interactions between different processes seem like interactions between dif...
Page 936
936 c hapter 58: ospf c onfiguration after the restart, the gr restarter will send an ospf gr signal to its neighbors that will not reset their adjacencies with it. In this way, the gr restarter can restore the neighbor table upon receiving the responses from neighbors. After reestablishing neighbor...
Page 937
Ospf configuration task list 937 configuring area ids on pes can differentiate vpns. Sites in the same vpn are considered as directly connected. Pe routers then exchange ospf routing information like on a dedicated line, thus network management and ospf operation efficiency are improved. N for confi...
Page 938
938 c hapter 58: ospf c onfiguration “configuring ospf routing information control” on page 942 “configuring ospf route summarization” on page 943 optional “configuring ospf inbound route filtering” on page 943 optional “configuring abr type3 lsa filtering” on page 943 optional “configuring ospf lin...
Page 939
Configuring ospf basic functions 939 configuring ospf basic functions you need to enable ospf, specify an interface and area id first before performing other tasks. Prerequisites before configuring ospf, you have configured the link layer protocol, and ip addresses for interfaces, making neighboring...
Page 940
940 c hapter 58: ospf c onfiguration n ■ an ospf process id is unique, including the process id for ospf multi-instance, which cannot be the same as any previously configured id. ■ a network segment can only belong to one area. ■ it is recommended to configure a description for each ospf process to ...
Page 941
Configuring ospf network types 941 n ■ it is required to use the stub command on routers attached to a stub area. ■ it is required to use the nssa command on routers attached to an nssa area. ■ using the default-cost command only takes effect on the abr of a stub area or the abr/asbr of an nssa area...
Page 942
942 c hapter 58: ospf c onfiguration ■ if the two interfaces on a link are both configured as the broadcast, nbma or p2mp type, they cannot establish neighbor relationship unless they are on the same network segment. Configuring an nbma neighbor for nbma interfaces that cannot broadcast hello packet...
Page 943
Configuring ospf routing information control 943 configuring ospf route summarization ospf route summarization includes: ■ configure route summarization between ospf areas on an abr ■ configure route summarization when redistributing routes into ospf on an asbr follow these steps to configure route ...
Page 944
944 c hapter 58: ospf c onfiguration configuring ospf link cost follow these steps to configure the link cost for an interface: follow these steps to configure a bandwidth reference value: n if the cost value is not configured for an interface, ospf computes the interface cost value automatically: i...
Page 945
Configuring ospf routing information control 945 follow these steps to configure the maximum number of load-balanced routes: configuring ospf priority a router may run multiple routing protocols. The router sets a priority for each protocol, when a route found by several routing protocols, the route...
Page 946
946 c hapter 58: ospf c onfiguration n ■ using the import-route command cannot redistribute a default external route. To do so, you need to use the default-route-advertise command. ■ the default-route-advertise summary cost command is applicable only to vpn, and the default route is redistributed in...
Page 947
Configuring ospf network optimization 947 ■ lsa retransmit timer: interval within which if the interface receives no acknowledgement packets after sending a lsa to the neighbor, it will retransmit the lsa. Follow these steps to configure timers for ospf packets: n ■ the hello and dead intervals rest...
Page 948
948 c hapter 58: ospf c onfiguration configuring spf calculation interval link state database changes lead to spf calculations. When an ospf network changes frequently, a large amount of network resources will be occupied, reducing working efficiency of routers. You can adjust the spf calculation in...
Page 949
Configuring ospf network optimization 949 n with this command configured, when network changes are not frequent, lsas are generated at the minimum-interval. If network changes become frequent, lsa generation interval is incremented by incremental-interval•2 n-2 (n is the number of generation times) ...
Page 950
950 c hapter 58: ospf c onfiguration n a stub router has nothing to do with a stub area. Configuring ospf authentication by supporting packet authentication, ospf receives packets that pass the authentication only, so failed packets cannot establish neighboring relationship. Follow these steps to co...
Page 951
Configuring ospf network optimization 951 configuring the maximum number of external lsas in lsdb follow these steps to configure the maximum number of external lsas in the link state database: making external route selection rules defined in rfc1583 compatible the selection of an external route fro...
Page 952
952 c hapter 58: ospf c onfiguration enabling the advertisement and reception of opaque lsas with this feature enabled, the ospf router can receive and advertise the type 9, type 10 and type 11 opaque lsas. Follow these steps to enable the advertisement and reception of opaque lsas: configuring ospf...
Page 953
Configuring ospf graceful restart 953 configuring the non-ietf standard ospf gr restarter follow these steps to configure non-ietf standard ospf gr restarter: configuring the ospf gr helper follow these steps to configure the ospf gr helper: triggering ospf graceful restart performing main/backup sw...
Page 954
954 c hapter 58: ospf c onfiguration follow these steps to trigger ospf graceful restart: displaying and maintaining ospf configuration to do... Use the command... Remarks trigger ospf graceful restart reset ospf [ process-id ] process graceful-restart required available in user view to do... Use th...
Page 955
Ospf configuration examples 955 ospf configuration examples c caution: in these examples, only commands related to ospf configuration are described. Configuring ospf basic functions network requirements as shown in the following figure, all routers run ospf. The as is split into three areas, in whic...
Page 956
956 c hapter 58: ospf c onfiguration [routerb-ospf-1-area-0.0.0.2] network 10.3.1.0 0.0.0.255 [routerb-ospf-1-area-0.0.0.2] quit [routerb-ospf-1] quit # configure routerc system-view [routerc] ospf [routerc-ospf-1] area 1 [routerc-ospf-1-area-0.0.0.1] network 10.2.1.0 0.0.0.255 [routerc-ospf-1-area-...
Page 957
Ospf configuration examples 957 total nets: 5 intra area: 3 inter area: 2 ase: 0 nssa: 0 # display the link state database on routera [routera] display ospf lsdb ospf process 1 with router id 10.2.1.1 link state database area: 0.0.0.0 type linkstate id advrouter age len sequence metric router 10.2.1...
Page 958
958 c hapter 58: ospf c onfiguration configuring an ospf stub area network requirements figure 290 shows an as is split into three areas, where all routers run ospf. Routera and routerb act as abrs to forward routing information between areas. Routerd acts as the asbr, redistributing routes (static ...
Page 959
Ospf configuration examples 959 10.4.1.0/24 3 stub 10.4.1.1 10.4.1.1 0.0.0.1 10.5.1.0/24 17 inter 10.2.1.1 10.2.1.1 0.0.0.1 10.1.1.0/24 5 inter 10.2.1.1 10.2.1.1 0.0.0.1 routing for ases destination cost type tag nexthop advrouter 3.1.3.0/24 1 type2 1 10.2.1.1 10.5.1.1 total nets: 6 intra area: 2 in...
Page 960
960 c hapter 58: ospf c onfiguration # display ospf routing table information on routerc [routerc] display ospf routing ospf process 1 with router id 10.4.1.1 routing tables routing for network destination cost type nexthop advrouter area 0.0.0.0/0 65536 inter 10.2.1.1 10.2.1.1 0.0.0.1 10.2.1.0/24 6...
Page 961
Ospf configuration examples 961 # configure routerc [routerc] ospf [routerc-ospf-1] area 1 [routerc-ospf-1-area-0.0.0.1] nssa [routerc-ospf-1-area-0.0.0.1] quit [routerc-ospf-1] quit n it is recommended to configure the nssa command with the keyword default-route-advertise no-summary on router a (an...
Page 962
962 c hapter 58: ospf c onfiguration configuring ospf dr election network requirements in figure 292 : ■ router a, b, c and d are on the same network, running ospf. ■ configure router a as the dr, c as the bdr. Network diagram figure 292 ospf dr election configuration network diagram configuration p...
Page 963
Ospf configuration examples 963 # configure routerd system-view [routerd] router id 4.4.4.4 [routerd] ospf [routerd-ospf-1] area 0 [routerd-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255 [routerd-ospf-1-area-0.0.0.0] quit [routerd-ospf-1] quit # display neighbor information on routera [routera] ...
Page 964
964 c hapter 58: ospf c onfiguration # display information about neighbors on routerd. [routerd] display ospf peer ospf process 1 with router id 4.4.4.4 neighbors area 0.0.0.0 interface 192.168.1.4(ethernet1/0)’s neighbors router id: 1.1.1.1 address: 192.168.1.1 gr state: normal state: full mode:nbr...
Page 965
Ospf configuration examples 965 neighbor is up for 00:01:41 authentication sequence: [ 0 ] routera becomes the dr, router c the bdr. N the full neighbor state means router d has established the adjacency with the router. The 2-way neighbor state means the two routers are neither the dr nor the bdr, ...
Page 966
966 c hapter 58: ospf c onfiguration system-view [routera] ospf 1 router-id 1.1.1.1 [routera-ospf-1] area 0 [routera-ospf-1-area-0.0.0.0] network 10.0.0.0 0.255.255.255 [routera-ospf-1-area-0.0.0.0] quit [routera-ospf-1] area 1 [routera-ospf-1-area-0.0.0.1] network 192.168.1.0 0.0.0.255 [routera-osp...
Page 967
Ospf configuration examples 967 routing for network destination cost type nexthop advrouter area 172.16.1.1/16 1563 inter 192.168.1.2 2.2.2.2 0.0.0.0 10.0.0.0/8 1 stub 10.1.1.1 1.1.1.1 0.0.0.0 192.168.1.0/24 1562 stub 192.168.1.1 1.1.1.1 0.0.0.1 total nets: 3 intra area: 2 inter area: 1 ase: 0 nssa:...
Page 968
968 c hapter 58: ospf c onfiguration [routerb] interface ethernet 1/0 [routerb-ethernet1/0] ip address 192.1.1.2 255.255.255.0 [routerb-ethernet1/0] ospf dr-priority 0 [routerb-ethernet1/0] quit [routerb] router id 2.2.2.2 [routerb] ospf 100 [routerb-ospf-100] graceful-restart help 2000 [routerb-osp...
Page 969
Troubleshooting ospf configuration 969 5 on an nbma network, using the peer ip-address command to specify the neighbor manually is required. 6 on an nbma or a broadcast network, at least one connected interface must have a router priority higher than 0. Incorrect routing information symptom ospf can...
Page 970
970 c hapter 58: ospf c onfiguration.
Page 971: Rip C
59 rip c onfiguration when configuring rip, go to these sections for information you are interested in: ■ “rip overview” on page 971 ■ “configuring rip basic functions” on page 976 ■ “configuring rip advanced functions” on page 978 ■ “optimizing the rip network” on page 981 ■ “displaying and maintai...
Page 972
972 c hapter 59: rip c onfiguration ■ route time: time elapsed since the routing entry was last updated. The time is reset to 0 every time the routing entry is updated. ■ route tag: identifies a route, used in routing policy to flexibly control routes. For information about routing policy, refer to ...
Page 973
Rip overview 973 4 rip ages out routes by adopting an aging mechanism to keep only valid routes. Rip version rip has two versions, rip-1 and rip-2. Rip-1, a classful routing protocol, supports message advertisement via broadcast only. Rip-1 protocol messages do not carry mask information, which mean...
Page 974
974 c hapter 59: rip c onfiguration figure 295 rip-1 message format ■ command: the type of message. 1 indicates request, 2 indicates response. ■ version: the version of rip, 0x01 for rip-1. ■ afi: address family identifier, 2 for ip. ■ ip address: destination ip address of the route; can be a natura...
Page 975
Rip overview 975 figure 297 rip-2 authentication message ■ authentication type: 2 represents plain text authentication, while 3 represents md5. ■ authentication: authentication data, including password information when plain text authentication is adopted or including key id, md5 authentication data...
Page 976
976 c hapter 59: rip c onfiguration receiving no update acknowledge after the upper limit for sending update responses is reached, the router considers the neighbor unreachable. Rip features supported the current implementation supports the following rip features. ■ rip-1 and rip-2 ■ rip multi-insta...
Page 977
Configuring rip basic functions 977 configure the interface behavior follow these steps to configure the interface behavior: configure a rip version you can configure a rip version in rip or interface view. ■ if neither global nor interface rip version is configured, the interface sends rip-1 broadc...
Page 978
978 c hapter 59: rip c onfiguration configuring rip advanced functions in some complex network environments, you need to configure advanced rip functions. This section covers the following topics: ■ “configuring an additional routing metric” on page 978 ■ “configuring rip-2 route summarization” on p...
Page 979
Configuring rip advanced functions 979 configuring rip-2 route summarization the route summarization means that subnet routes in a natural network are summarized with a natural network that is sent to other networks. This function can reduce the size of routing tables. Configure rip-2 route automati...
Page 980
980 c hapter 59: rip c onfiguration disabling host route reception sometimes a router may receive many host routes from the same network, which are not helpful for routing and occupy a large amount of network resources. In this case, you can disable rip from receiving host routes to save network res...
Page 981
Optimizing the rip network 981 n ■ using the filter-policy import command filters incoming routes. Routes not passing the filtering will be neither installed into the routing table nor advertised to neighbors. ■ using the filter-policy export command filters outgoing routes, including routes redistr...
Page 982
982 c hapter 59: rip c onfiguration ■ “configuring rip-2 message authentication” on page 984 ■ “configuring a rip neighbor” on page 984 ■ “configuring trip” on page 985 ■ “configuring rip-to-mib binding” on page 986 finish the following tasks before configuring the rip network optimization. ■ config...
Page 983
Optimizing the rip network 983 information, refer to “frame relay configuration” on page 235 and “x.25 and lapb configuration” on page 283 . ■ disabling the split horizon function on a point-to-point link does not take effect. Configure the poison reverse the poison reverse function allows an interf...
Page 984
984 c hapter 59: rip c onfiguration enabling source ip address check on incoming rip updates you can enable source ip address check on incoming rip updates. ■ for a message received on an ethernet interface, rip compares the source ip address of the message with the ip address of the interface. If t...
Page 985
Optimizing the rip network 985 n you need not use the peer ip-address command when the neighbor is directly connected; otherwise the neighbor may receive both the unicast and multicast (or broadcast) of the same routing information. Configuring trip in a connection oriented network, a router may est...
Page 986
986 c hapter 59: rip c onfiguration n the maximum retransmission time (upper limit × interval) for a packet cannot be too long lest when its neighbor is down, the router still resends the packet. Configuring rip-to-mib binding follow these steps to bind rip to mib: displaying and maintaining rip con...
Page 987
Rip configuration example 987 configuration procedure 1 configure an ip address for each interface (omitted) 2 configure basic rip functions # configure router a. System-view [routera] rip [routera-rip-1] network 1.0.0.0 [routera-rip-1] network 2.0.0.0 [routera-rip-1] network 3.0.0.0 # configure rou...
Page 988
988 c hapter 59: rip c onfiguration n since rip-1 routing information has a long aging time, it will still exist before being aged out after rip-2 is configured. Configuring rip route redistribution network requirements as shown in figure 299 , two rip processes are running on router b, which commun...
Page 989
Rip configuration example 989 system-view [routerc] rip 200 [routerc-rip-200] network 3.0.0.0 [routerc-rip-200] network 4.0.0.0 [routerc-rip-200] network 5.0.0.0 [routerc-rip-200] version 2 [routerc-rip-200] undo summary # display the routing table of router a. [routera] display ip routing-table rou...
Page 990
990 c hapter 59: rip c onfiguration [routerb] rip 100 [routerb-rip-100] filter-policy 2000 export rip 200 # display the routing table on router a. [routera] display ip routing-table routing tables: public destinations : 7 routes : 7 destination/mask proto pre cost nexthop interface 1.1.1.0/24 direct...
Page 991: Outing
60 r outing p olicy c onfiguration a routing policy is used on a router for route inspection, filtering, attributes modifying when routes are received, advertised, or redistributed. When configuring routing policy, go to these sections for information you are interested in: ■ “introduction to routin...
Page 992
992 c hapter 60: r outing p olicy c onfiguration filters routing protocols can use six filters: acl, ip prefix list, as path acl, community list, extended community list and routing policy. Acl acl involves ipv4 acl and ipv6 acl. When defining an acl, you can specify ip addresses and subnets to matc...
Page 993
Routing policy configuration task list 993 each node comprises a list of if-match and apply clauses. The if-match clauses define the match criteria. The matching objects are some attributes of routing information. The different if-match clauses on a node is in logical and relationship. Only when the...
Page 994
994 c hapter 60: r outing p olicy c onfiguration to define an ipv4 prefix list, use the following commands: n if all items are set to the deny mode, no routes can pass the ipv4 prefix list. Therefore, you need to define the permit 0.0.0.0 0 less-equal 32 item following multiple deny mode items to al...
Page 995
Defining filtering lists 995 defining an as path acl you can define multiple items for an as path acl that is identified by number. During matching, the relation between items is logical or, that is, if the route matches one of these items, it passes the as path acl. To define an as path acl, use th...
Page 996
996 c hapter 60: r outing p olicy c onfiguration configuring a routing policy a routing policy is used to filter routing information according to some attributes, and modify some attributes of the routing information that matches the routing policy. Match criteria can be configured using filters abo...
Page 998
998 c hapter 60: r outing p olicy c onfiguration n ■ the if-match clauses of a route-policy are in logic and relationship, namely, routing information has to satisfy all if-match clauses before being executed with apply clauses. ■ you can specify no or multiple if-match clauses for a routing policy....
Page 999
Configuring a routing policy 999 n ■ the difference between ipv4 and ipv6 apply clauses is the command of setting the next hop for routing information. ■ the apply ip-address next-hop and apply ipv6 next-hop commands do not apply to redistributed ipv4 and ipv6 routes respectively. Set a cost type fo...
Page 1000
1000 c hapter 60: r outing p olicy c onfiguration displaying and maintaining the routing policy routing policy configuration example applying routing policy when redistributing ipv4 routes network requirements in figure 300 , router b exchanges routing information with router a using ospf, and with ...
Page 1001
Routing policy configuration example 1001 configuration procedure 1 configure ip addresses for interfaces (omitted) 2 configure is-is # configure router c. System-view [routerc] isis [routerc-isis-1] is-level level-2 [routerc-isis-1] network-entity 10.0000.0000.0001.00 [routerc-isis-1] quit [routerc...
Page 1002
1002 c hapter 60: r outing p olicy c onfiguration [routera] display ospf routing ospf process 1 with router id 192.168.1.1 routing tables routing for network destination cost type nexthop advrouter area 192.168.1.0/24 1 transit 192.168.1.1 192.168.1.1 0.0.0.0 routing for ases destination cost type t...
Page 1003
Routing policy configuration example 1003 routing for ases destination cost type tag nexthop advrouter 172.17.1.0/24 100 type2 1 192.168.1.2 192.168.2.2 172.17.2.0/24 1 type2 20 192.168.1.2 192.168.2.2 172.17.3.0/24 1 type2 1 192.168.1.2 192.168.2.2 192.168.2.0/24 1 type2 1 192.168.1.2 192.168.2.2 t...
Page 1004
1004 c hapter 60: r outing p olicy c onfiguration [routera] ipv6 route-static 20:: 32 serial 2/1 [routera] ipv6 route-static 30:: 32 serial 2/1 [routera] ipv6 route-static 40:: 32 serial 2/1 # configure a routing policy. [routera] ip ipv6-prefix a index 10 permit 30:: 32 [routera] route-policy stati...
Page 1005
Troubleshooting routing policy configuration 1005 troubleshooting routing policy configuration ipv4 routing information filtering failure symptom filtering routing information failed, while routing protocol runs normally. Analysis at least one item of the ip prefix list should be configured as permi...
Page 1006
1006 c hapter 60: r outing p olicy c onfiguration.
Page 1007: Tatic
61 s tatic r outing c onfiguration when configuring a static route, go to the following sections for information you are interested in: ■ “introduction” on page 1007 ■ “configuring a static route” on page 1008 ■ “detecting reachability of the static route’s nexthop” on page 1009 ■ “displaying and ma...
Page 1008
1008 c hapter 61: s tatic r outing c onfiguration application environment of static routing before configuring a static route, you need to know the following concepts: 1 destination address and mask in the ip route-static command, an ipv4 address is in dotted decimal format and a mask can be either ...
Page 1009
Detecting reachability of the static route’s nexthop 1009 ■ configure the link-layer attributes for related interfaces ■ configure the ip addresses for related interfaces configuration procedure follow these steps to configure a static route: n ■ when configuring a static route, the static route doe...
Page 1010
1010 c hapter 61: s tatic r outing c onfiguration network requirements to detect the reachability of a static route’s nexthop through a track entry, you need to create a track first. For detailed track configuration procedure, refer to “track configuration” on page 2207 . Configuration procedure fol...
Page 1011
Configuration example 1011 network diagram figure 302 network diagram for static route configuration configuration procedure 1 configuring ip addresses for interfaces (omitted) 2 configuring static routes # enter system view system-view # configure a default route on router a. [routera] ip route-sta...
Page 1012
1012 c hapter 61: s tatic r outing c onfiguration 1.1.1.0/24 direct 0 0 1.1.1.1 ethernet1/0 1.1.1.1/32 direct 0 0 127.0.0.1 inloopback0 1.1.4.0/30 direct 0 0 1.1.4.1 serial2/0 1.1.4.1/32 direct 0 0 127.0.0.1 inloopback0 1.1.4.2/32 direct 0 0 1.1.4.2 serial2/0 127.0.0.0/8 direct 0 0 127.0.0.1 inloopb...
Page 1013
Configuration example 1013 3 1 ms 1.1.2.2 trace complete..
Page 1014
1014 c hapter 61: s tatic r outing c onfiguration.
Page 1015: 6 Bgp C
62 ip v 6 bgp c onfiguration n this chapter describes only configuration for ipv6 bgp. For bgp related information, refer to “bgp configuration” on page 825 . When configuring ipv6 bgp, go to these sections for information you are interested in: ■ “ipv6 bgp overview” on page 1015 ■ “ipv6 bgp configu...
Page 1016
1016 c hapter 62: ip v 6 bgp c onfiguration ipv6 bgp configuration task list complete the following tasks to configure ipv6 bgp: task remarks “ipv6 bgp configuration” on page 1015 “configuring an ipv6 peer” on page 1017 required “advertising a local ipv6 route” on page 1017 optional “configuring a p...
Page 1017
Configuring ipv6 bgp basic functions 1017 configuring ipv6 bgp basic functions prerequisites before configuring this task, you need to ■ specify ip addresses for interfaces ■ enable ipv6 function. N you need create a peer group before configuring basic functions for it. For related information, refe...
Page 1019
Configuring ipv6 bgp basic functions 1019 router may fail to establish tcp connections to the peers when using the outbound interfaces of the best routes as the source interfaces. Configuring a non direct ebgp connection to a peer/peer group follow these steps to configure an ebgp connection to a pe...
Page 1020
1020 c hapter 62: ip v 6 bgp c onfiguration n refer to “bgp configuration” on page 825 for information about the log-peer-change command. Controlling route distribution and reception the task includes routing information filtering, routing policy application and route dampening. Prerequisites before...
Page 1021
Controlling route distribution and reception 1021 n with the peer default-route-advertise command used, the local router advertises a default route with itself as the next hop to the specified peer/peer group, regardless of whether the default route is available in the routing table. Configuring rou...
Page 1022
1022 c hapter 62: ip v 6 bgp c onfiguration n ■ only routes passing the specified policy can be added into the local ipv6 bgp routing table. ■ members of a peer group can have different inbound route policies. Configuring ipv6 bgp and igp route synchronization with this feature enabled and when a no...
Page 1023
Configuring ipv6 bgp route attributes 1023 configuring ipv6 bgp route attributes this section describes how to use ipv6 bgp route attributes to modify bgp routing policy. These attributes are: ■ ipv6 bgp protocol preference ■ default local_pref attribute ■ med attribute ■ next_hop attribute ■ as_pat...
Page 1024
1024 c hapter 62: ip v 6 bgp c onfiguration for routes to the ebgp peer by default, unless the peer next-hop-local command is configured. Configuring the med attribute follow these steps to configure the med attribute: configuring the as_path attribute follow these steps to configure the as_path att...
Page 1025
Adjusting and optimizing ipv6 bgp networks 1025 after establishing an ipv6 bgp connection, two routers send keepalive messages periodically to each other to keep the connection. If a router receives no keepalive message from the peer after the holdtime elapses, it tears down the connection. When est...
Page 1026
1026 c hapter 62: ip v 6 bgp c onfiguration n ■ timers configured using the timer command have lower priority than timers configured using the peer timer command. ■ the holdtime interval must be at least three times the keepalive interval. Configuring ipv6 bgp soft reset enable route refresh follow ...
Page 1027
Configuring a large scale ipv6 bgp network 1027 configuring a large scale ipv6 bgp network in a large-scale ipv6 bgp network, configuration and maintenance become no convenient due to too many peers. In this case, configuring peer groups makes management easier and improves route distribution effici...
Page 1028
1028 c hapter 62: ip v 6 bgp c onfiguration n ■ to create a pure ebgp peer group, you need to specify an as number for the peer group. ■ if a peer was added into an ebgp peer group, you cannot specify any as number for the peer group. Create a mixed ebgp peer group follow these steps to create a mix...
Page 1029
Configuring 6pe 1029 apply a routing policy to routes advertised to a peer/peer group follow these steps to apply a routing policy to routes advertised to a peer/peer group: n ■ when configuring ipv6 bgp community, you need to configure a routing policy to define the community attribute, and apply t...
Page 1030
1030 c hapter 62: ip v 6 bgp c onfiguration capability for sparsely populated ipv6 networks, allowing customer edge (ce) routers in these isolated ipv6 networks to communicate with ipv4 pe routers. Work mechanism of 6pe: ipv6 routing information from users is converted into ipv6 routing information ...
Page 1033
Displaying and maintaining ipv6 bgp configuration 1033 displaying and maintaining ipv6 bgp configuration displaying bgp to do... Use the command... Remarks display peer group information display bgp ipv6 group [ ipv6-group-name ] available in any view display ipv6 bgp advertised routing information ...
Page 1034
1034 c hapter 62: ip v 6 bgp c onfiguration resetting ipv6 bgp connections clearing ipv6 bgp information ipv6 bgp configuration examples n some ipv6 bgp configuration examples are similar to those of bgp, so refer to “bgp configuration” on page 825 for related information. Ipv6 bgp basic configurati...
Page 1035
Ipv6 bgp configuration examples 1035 system-view [routerb] ipv6 [routerb] bgp 65009 [routerb-bgp] router-id 2.2.2.2 [routerb-bgp] ipv6-family [routerb-bgp-af-ipv6] peer 9:1::2 as-number 65009 [routerb-bgp-af-ipv6] peer 9:3::2 as-number 65009 [routerb-bgp-af-ipv6] quit [routerb-bgp] quit # configure ...
Page 1036
1036 c hapter 62: ip v 6 bgp c onfiguration [routerb] display bgp ipv6 peer bgp local router id : 2.2.2.2 local as number : 65009 total number of peers : 3 peers in established state : 3 peer v as msgrcvd msgsent outq prefrcv up/down state 10::2 4 65008 3 3 0 0 00:01:16 established 9:3::2 4 65009 2 ...
Page 1037
Ipv6 bgp configuration examples 1037 system-view [routera] ipv6 [routera] bgp 100 [routera-bgp] router-id 1.1.1.1 [routera-bgp] ipv6-family [routera-bgp-af-ipv6] peer 100::2 as-number 200 [routera-bgp-af-ipv6] network 1:: 64 # configure router b system-view [routerb] ipv6 [routerb] bgp 200 [routerb-...
Page 1038
1038 c hapter 62: ip v 6 bgp c onfiguration ■ connect the two ipv6 networks through the ipv4/mpls network with the 6pe feature. Network diagram figure 306 network diagram for 6pe configuration configuration procedure 1 configure ce 1 # enable ipv6 packet forwarding. System-view [ce1] ipv6 # specify ...
Page 1039
Ipv6 bgp configuration examples 1039 # configure an ipv6 link-local address for serial2/0. [pe1] interface serial 2/0 [pe1-serial2/0] ipv6 address auto link-local [pe1-serial2/0] quit # configure an ip address for serial2/1 and enable mpls and ldp. [pe1] interface serial 2/1 [pe1-serial2/1] ip addre...
Page 1040
1040 c hapter 62: ip v 6 bgp c onfiguration [pe2] interface serial 2/1 [pe2-serial2/1] ip address 1.1.1.2 16 [pe2-serial2/1] mpls [pe2-serial2/1] mpls ldp [pe2-serial2/1] quit [pe2] interface serial 2/0 [pe2-serial2/0] ipv6 address auto link-local [pe2-serial2/0] quit [pe2] interface loopback 0 [pe2...
Page 1041
Troubleshooting ipv6 bgp configuration 1041 verify the configuration # display mpls lsp information on pe 1. Display mpls lsp -------------------------------------------------------------- lsp information: bgp ipv6 lsp -------------------------------------------------------------- fec : 1::1/128 in ...
Page 1042
1042 c hapter 62: ip v 6 bgp c onfiguration analysis to become ipv6 bgp peers, any two routers need to establish a tcp session using port 179 and exchange open messages successfully. Processing steps 1 use the display current-configuration command to verify the peer’s as number. 2 use the display bg...
Page 1043: 6 Is-Is C
63 ip v 6 is-is c onfiguration when configuring ipv6 is-is, go to these sections for information you are interested in: ■ “introduction to ipv6 is-is” on page 1043 ■ “configuring ipv6 is-is basic functions” on page 1043 ■ “configuring ipv6 is-is routing information control” on page 1044 ■ “displayin...
Page 1044
1044 c hapter 63: ip v 6 is-is c onfiguration ■ enable is-is configuration procedure follow these steps to configure the basic functions of ipv6 is-is: configuring ipv6 is-is routing information control configuration prerequisites you need to complete the ipv6 is-is basic function configuration befo...
Page 1045
Displaying and maintaining ipv6 is-is 1045 n ■ the ipv6 filter-policy export command, usually used in combination with the ipv6 import-route command, filters redistributed routes when advertising them to other routers. If no protocol is specified, routes redistributed from all routing protocol are f...
Page 1046
1046 c hapter 63: ip v 6 is-is c onfiguration ipv6 is-is configuration example network requirements as shown in figure 307 , router a, router b, router c and router d, all enabled with ipv6, reside in the same autonomous system. Configure ipv6 is-is on the routers to make them reachable to each othe...
Page 1047
Ipv6 is-is configuration example 1047 system-view [routerb] isis 1 [routerb-isis-1] is-level level-1 [routerb-isis-1] network-entity 10.0000.0000.0002.00 [routerb-isis-1] ipv6 enable [routerb-isis-1] quit [routerb] interface serial 2/0 [routerb-serial2/0] isis ipv6 enable 1 [routerb-serial2/0] quit ...
Page 1048
1048 c hapter 63: ip v 6 is-is c onfiguration.
Page 1049: 6 Ospf
64 ip v 6 ospf v 3 c onfiguration when configuring ospf, go to these sections for information you are interested in: ■ “introduction to ospfv3” on page 1049 ■ “ipv6 ospfv3 configuration task list” on page 1051 ■ “configuring ospfv3 basic functions” on page 1052 ■ “configuring ospfv3 area parameters”...
Page 1050
1050 c hapter 64: ip v 6 ospf v 3 c onfiguration figure 308 gives the ospfv3 packet header. Figure 308 ospfv3 packet header major fields: ■ version #: version of ospf, which is 3 for ospfv3. ■ type: type of ospf packet, from 1 to 5 are hello, dd, lsr, lsu, and lsack respectively. ■ packet length: pa...
Page 1051
Ipv6 ospfv3 configuration task list 1051 ■ ospfv3 packet timer ■ lsa delay timer ■ spf timer ospfv3 packet timer hello packets are sent periodically between neighboring routers for finding and maintaining neighbor relationships, or for dr/bdr election. The hello interval must be identical on neighbo...
Page 1052
1052 c hapter 64: ip v 6 ospf v 3 c onfiguration configuring ospfv3 basic functions prerequisites ■ make neighboring nodes accessible with each other at network layer. ■ enable ipv6 packet forwarding configuring ospfv3 basic functions to configure ospfv3 basic functions, use the following commands: ...
Page 1053
Configuring ospfv3 area parameters 1053 n ■ configure an ospfv3 process id when enabling ospfv3. The process id takes effect locally, without affecting packet exchange between routers. ■ when configuring a router id, make sure each router has a unique id. If a router runs multiple ospfv3 processes, ...
Page 1054
1054 c hapter 64: ip v 6 ospf v 3 c onfiguration ■ if you use the stub command with the keyword no-summary on an abr, the abr distributes a default summary lsa into the area rather than generating an as-external-lsa or inter-area-prefix-lsa. The stub area of this kind is also known as totally stub a...
Page 1055
Configuring ospfv3 routing information management 1055 to configure inbound route filtering, use the following commands: n use of the filter-policy import command can only filter routes computed by ospfv3. Only routes not filtered can be added into the local routing table. Configuring link costs for...
Page 1056
1056 c hapter 64: ip v 6 ospf v 3 c onfiguration configuring ospfv3 route redistribution to configure ospfv3 route redistribution, use the following commands: n ■ using the import-route command on a router makes the router become an asbr. ■ since ospfv3 is a link state based routing protocol, it can...
Page 1057
Tuning and optimizing an ospfv3 network 1057 n ■ the dead interval set on neighboring interfaces cannot be so small. Otherwise, a neighbor is so easy to be considered as down. ■ the lsa retransmission interval cannot be so small to avoid unnecessary retransmissions. Configuring the dr priority for a...
Page 1058
1058 c hapter 64: ip v 6 ospf v 3 c onfiguration disabling interfaces from sending ospfv3 packets to disable interfaces from sending ospfv3 packets, use the following commands: n ■ multiple processes can disable the same interface from sending ospfv3 packets. Using the silent-interface command disab...
Page 1059
Displaying and maintaining ospfv3 1059 displaying and maintaining ospfv3 ospfv3 configuration examples configuring ospfv3 areas network requirements in figure 309 , all routers run ospfv3. The as is split into three areas, in which, router b and router c act as abrs to forward routing information be...
Page 1060
1060 c hapter 64: ip v 6 ospf v 3 c onfiguration network diagram figure 309 ospfv3 area configuration configuration procedure 1 configure ipv6 addresses for interfaces (omitted) 2 configure ospfv3 basic functions # configure router a system-view [routera] ipv6 [routera] ospfv3 1 [routera-ospfv3-1] r...
Page 1061
Ospfv3 configuration examples 1061 [routerc] interface serial 2/0 [routerc-serial2/0] ospfv3 1 area 0 [routerc-serial2/0] quit [routerc] interface serial 2/1 [routerc-serial2/1] ospfv3 1 area 2 [routerc-serial2/1] quit # configure router d system-view [routerd] ipv6 [routerd] ospfv3 1 [routerd-ospfv...
Page 1062
1062 c hapter 64: ip v 6 ospf v 3 c onfiguration *destination: 2001:2::/64 type : i cost : 1 nexthop : directly-connected interface: s2/1 *destination: 2001:3::/64 type : ia cost : 4 nexthop : fe80::f40d:0:93d0:1 interface: s2/1 3 configure area 2 as a stub area # configure router d [routerd] ospfv3...
Page 1063
Ospfv3 configuration examples 1063 [routerd] display ospfv3 routing e1 - type 1 external route, ia - inter area route, i - intra area route e2 - type 2 external route, * - selected route ospfv3 router with id (4.4.4.4) (process 1) ---------------------------------------------------------------------...
Page 1064
1064 c hapter 64: ip v 6 ospf v 3 c onfiguration [routera-ethernet1/0] ospfv3 1 area 0 [routera-ethernet1/0] quit # configure router b. System-view [routerb] ipv6 [routerb] ospfv3 [routerb-ospfv3-1] router-id 2.2.2.2 [routerb-ospfv3-1] quit [routerb] interface ethernet 1/0 [routerb-ethernet1/0] ospf...
Page 1065
Ospfv3 configuration examples 1065 # configure the dr priority of router a as 100. [routera] interface ethernet 1/0 [routera-ethernet1/0] ospfv3 dr-priority 100 [routera-ethernet1/0] quit # configure the dr priority of ethernet 1/0 as 0 on router b. [routerb] interface ethernet 1/0 [routerb-ethernet...
Page 1066
1066 c hapter 64: ip v 6 ospf v 3 c onfiguration 1.1.1.1 100 full/dr 00:00:34 eth1/0 0 2.2.2.2 0 2-way/drother 00:00:34 eth1/0 0 3.3.3.3 2 full/backup 00:00:32 eth1/0 0 troubleshooting ospfv3 configuration no ospfv3 neighbor relationship established symptom no ospf neighbor relationship can be estab...
Page 1067
Troubleshooting ospfv3 configuration 1067 5 in a stub area, all routers are configured with the stub command. 6 if a virtual link is configured, use the display ospf vlink command to check the neighbor state..
Page 1068
1068 c hapter 64: ip v 6 ospf v 3 c onfiguration.
Page 1069: 6 Rip
65 ip v 6 rip ng c onfiguration when configuring ripng, go to these sections for information you are interested in: ■ “introduction to ripng” on page 1069 ■ “configuring ripng basic functions” on page 1071 ■ “configuring ripng advanced functions” on page 1072 ■ “optimizing the ripng network” on page...
Page 1070
1070 c hapter 65: ip v 6 rip ng c onfiguration each ripng router maintains a routing database, including route entries of all reachable destinations. A route entry contains the following information: ■ destination address: ipv6 address of a host or a network. ■ next hop address: ipv6 address of a ne...
Page 1071
Configuring ripng basic functions 1071 ipv6 next hop address is the ipv6 address of the next hop. Figure 313 shows the format of the ipv6 prefix rte. Figure 313 ipv6 prefix rte format ■ ipv6 prefix: destination ipv6 address prefix. ■ route tag: route tag. ■ prefix len: length of the ipv6 address pre...
Page 1072
1072 c hapter 65: ip v 6 rip ng c onfiguration you need to enable ripng first before configuring other tasks, but it is not necessary for ripng related interface configurations, such as assigning an ipv6 address. Configuration prerequisites before the configuration, accomplish the following tasks fi...
Page 1073
Configuring ripng advanced functions 1073 the outbound additional metric is added to the metric of a sent route, the route’s metric in the routing table is not changed. The inbound additional metric is added to the metric of a received route before the route is added into the routing table, so the r...
Page 1074
1074 c hapter 65: ip v 6 rip ng c onfiguration configuring the ripng priority any routing protocol has its own protocol priority used for optimal route selection. You can set a priority for ripng manually. The smaller the value is, the higher the priority is. Follow these steps to configure a ripng ...
Page 1075
Optimizing the ripng network 1075 ■ configuring the maximum number of load balanced routes configuring ripng timers you can adjust ripng timers to optimize the performance of the ripng network. Follow these steps to configure ripng timers: n when adjusting ripng timers, you should consider the netwo...
Page 1076
1076 c hapter 65: ip v 6 rip ng c onfiguration information, refer to “frame relay configuration” on page 235 and “x.25 and lapb configuration” on page 283 . Configuring the poison reverse function the poison reverse function enables a route learned from an interface to be advertised via the interfac...
Page 1077
Ripng configuration example 1077 ripng configuration example network requirements as shown in figure 314 , all routers learn ipv6 routing information via ripng. Configure router b to filter the route (3::/64) learnt from router c, which means the route will not be added to the routing table of route...
Page 1078
1078 c hapter 65: ip v 6 rip ng c onfiguration # configure router c. System-view [routerc] ripng 1 [routerc-ripng-1] quit [routerc] interface ethernet 1/0 [routerc-ethernet1/0] ripng 1 enable [routerc-ethernet1/0] quit [routerc] interface ethernet 1/1 [routerc-ethernet1/1] ripng 1 enable [routerc-et...
Page 1079
Ripng configuration example 1079 dest 5::/64, via fe80::20f:e2ff:fe00:100, cost 1, tag 0, a, 5 sec [routera] display ripng 1 route route flags: a - aging, s - suppressed, g - garbage-collect ---------------------------------------------------------------- peer fe80::20f:e2ff:fe00:1235 on gigabitethe...
Page 1080
1080 c hapter 65: ip v 6 rip ng c onfiguration.
Page 1081: 6 S
66 ip v 6 s tatic r outing c onfiguration when configuring ipv6 static routing, go to these sections for information you are interested in: ■ “introduction to ipv6 static routing” on page 1081 ■ “configuring an ipv6 static route” on page 1081 ■ “displaying and maintaining ipv6 static routes” on page...
Page 1082
1082 c hapter 66: ip v 6 s tatic r outing c onfiguration configuring an ipv6 static route n while configuring a static route, you can configure either the output interface or the next-hop address depending on the situations ■ if the output interface is a broadcast interface, such as an ethernet inte...
Page 1083
Ipv6 static routing configuration example 1083 network diagram figure 315 network diagram for static route configuration configuration procedure 1 configure ipv6 addresses for all interfaces (omitted). 2 configure ipv6 static routes. # configure the default ipv6 route on router a. System-view [route...
Page 1084
1084 c hapter 66: ip v 6 s tatic r outing c onfiguration nexthop : ::1 preference : 0 interface : inloop0 cost : 0 destination : 1:: protocol : direct nexthop : 1::1 preference : 0 interface : eth1/0 cost : 0 destination : 1::1 protocol : direct nexthop : ::1 preference : 0 interface : inloop0 cost ...
Page 1085: Ulticast
67 m ulticast o verview n this manual chiefly focuses on the ip multicast technology and device operations. Unless otherwise stated, the term “multicast” in this document refers to ip multicast. Introduction to multicast as a technique coexisting with unicast and broadcast, the multicast technique e...
Page 1086
1086 c hapter 67: m ulticast o verview in unicast transmission, the traffic over the network is proportional to the number of hosts that need the information. If a large number of users need the information, the information source needs to send a copy of the same information to each of these users. ...
Page 1087
Introduction to multicast 1087 figure 318 multicast transmission assume that hosts b, d and e need the information. To receive the information correctly, these hosts need to join a receiver set, which is known as a multicast group. The routers on the network duplicate and forward the information bas...
Page 1088
1088 c hapter 67: m ulticast o verview n ■ a multicast source does not necessarily belong to a multicast group. Namely, a multicast source is not necessarily a multicast data receiver. ■ a multicast source can send data to multiple multicast groups at the same time, and multiple multicast sources ca...
Page 1089
Multicast architecture 1089 ssm model in the practical life, users may be interested in the multicast data from only certain multicast sources. The ssm model provides a transmission service that allows users to specify the multicast sources they are interested in at the client side. The radical diff...
Page 1090
1090 c hapter 67: m ulticast o verview n ■ the membership of a group is dynamic. Hosts can join or leave multicast groups at any time. ■ glop" is a mechanism for assigning multicast addresses between different autonomous systems (ass). By filling an as number into the middle two bytes of 233.0.0.0, ...
Page 1091
Multicast architecture 1091 figure 319 ipv6 multicast format ■ 0xff: 8 bits, indicating that this address is an ipv6 multicast address. ■ flags: 4 bits, of which the highest-order flag is reserved and set to 0; the definition and usage of the second bit can be found in rfc 3956; and definition and u...
Page 1092
1092 c hapter 67: m ulticast o verview figure 320 ipv4-to-mac address mapping the high-order four bits of a multicast ipv4 address are 1110, indicating that this address is a multicast address, and only 23 bits of the remaining 28 bits are mapped to a mac address, so five bits of the multicast ipv4 ...
Page 1093
Multicast architecture 1093 this section provides only general descriptions about applications and functions of the layer 2 and layer 3 multicast protocols in a network. For details of these protocols, refer to “mpls l2vpn configuration” on page 1425 and “mpls l3vpn configuration” on page 1459 . Cur...
Page 1094
1094 c hapter 67: m ulticast o verview on the forwarding mechanism, pim comes in two modes - dense mode (often referred to as pim-dm) and sparse mode (often referred to as pim-sm). ■ an inter-domain multicast routing protocol is used for delivery of multicast information between two ass. So far, mat...
Page 1095
Multicast packet forwarding mechanism 1095 multicast packet forwarding mechanism in a multicast model, a multicast source sends information to a host group, which is identified by a multicast group address in the destination address field of ip multicast packets. Therefore, to deliver multicast pack...
Page 1096
1096 c hapter 67: m ulticast o verview ■ the p device belongs to the public network. The ce devices belong to their respective vpns. Each ce device serves its own network and maintains only one set of forwarding mechanism. ■ the pe devices interface with the public network and the vpn networks, serv...
Page 1097: Ulticast
68 m ulticast r outing and f orwarding c onfiguration when configuring multicast routing and forwarding, go to the following sections for information you are interested in: ■ “multicast routing and forwarding overview” on page 1097 ■ “configuration task list” on page 1102 ■ “displaying and maintaini...
Page 1098
1098 c hapter 68: m ulticast r outing and f orwarding c onfiguration implementation of the rpf mechanism upon receiving a multicast packet that a multicast source s sends to a multicast group g, the router first searches its multicast forwarding table: 1 if the corresponding (s, g) entry exists, and...
Page 1099
Multicast routing and forwarding overview 1099 the destination address. The corresponding routing entry explicitly defines the rpf interface and the rpf neighbor. 2 then, the router selects one from these two optimal routes as the rpf route. The selection is as follows: ■ if configured to use the lo...
Page 1100
1100 c hapter 68: m ulticast r outing and f orwarding c onfiguration means that the interface on which the packet actually arrived is not the rpf interface. The rpf check fails and the packet is discarded. ■ a multicast packet from source arrives on pos5/1 of router c, and the corresponding forwardi...
Page 1101
Multicast routing and forwarding overview 1101 multicast information from source travels from router a to router b and then to router c. Multicast traceroute the multicast traceroute utility is used to trace the path that a multicast stream passes from the multicast source to the last-hop router. Co...
Page 1102
1102 c hapter 68: m ulticast r outing and f orwarding c onfiguration figure 327 multicast data transmission through a gre tunnel as shown in figure 327 , with a gre tunnel established between router a and router b, router a encapsulates multicast data in unicast ip packets, which are then forwarded ...
Page 1103
Configuring multicast routing and forwarding 1103 ■ the minimum ttl value required for a multicast packet to be forwarded ■ the maximum number of downstream nodes for a single route in a multicast forwarding table ■ the maximum number of routing entries in a multicast forwarding table enabling ip mu...
Page 1104
1104 c hapter 68: m ulticast r outing and f orwarding c onfiguration c caution: when configuring a multicast static route, you cannot designate an rpf neighbor by specifying an interface (by means of the interface-type interface-number command argument combination) if the interface type of that rout...
Page 1105
Configuring multicast routing and forwarding 1105 ■ specifying boundary interfaces, which form a closed multicast forwarding area, or ■ setting the minimum time to live (ttl) value required for a multicast packet to be forwarded. You can configure a forwarding boundary specific to a particular multi...
Page 1106
1106 c hapter 68: m ulticast r outing and f orwarding c onfiguration if the configured maximum number of routing entries in the multicast forwarding table is smaller than the current number, the routes in excess of the configured limit will not be deleted immediately; instead they must be deleted by...
Page 1107
Displaying and maintaining multicast routing and forwarding 1107 c caution: ■ the reset command clears the information in the multicast routing table or the multicast forwarding table, and thus may cause failure of multicast transmission. ■ when a routing entry is deleted from the multicast routing ...
Page 1108
1108 c hapter 68: m ulticast r outing and f orwarding c onfiguration configuration examples changing an rpf route network requirements ■ pim-dm runs in the network. All routers in the network support multicast. ■ router a, router b and router c run ospf. ■ typically, receiver can receive the multica...
Page 1109
Configuration examples 1109 # enable ip multicast routing on router b, enable pim-dm on each interface, and enable igmpv2 on ethernet 1/0. System-view [routerb] multicast routing-enable [routerb] interface ethernet 1/0 [routerb-ethernet1/0] igmp enable [routerb-ethernet1/0] pim dm [routerb-ethernet1...
Page 1110
1110 c hapter 68: m ulticast r outing and f orwarding c onfiguration # use the display multicast rpf-info command to view the information about the rpf route to source on router b. [routerb] display multicast rpf-info 50.1.1.100 rpf information about source 50.1.1.100: rpf interface: ethernet1/1, rp...
Page 1111
Configuration examples 1111 information by leveraging the unicast routing protocol. The specific configuration steps are omitted here. 2 enable ip multicast routing, and enable pim on each interface # enable ip multicast routing on router c, enable pim-dm on each interface, and enable igmpv2 on ethe...
Page 1112
1112 c hapter 68: m ulticast r outing and f orwarding c onfiguration [routerb] display multicast rpf-info 50.1.1.100 rpf information about source 50.1.1.100: rpf interface: ethernet1/2, rpf neighbor: 30.1.1.2 referenced route/mask: 50.1.1.0/24 referenced route type: multicast static route selection ...
Page 1113
Troubleshooting multicast routing and forwarding 1113 5 check that the multicast static route matches the specified routing policy. If a routing policy was specified when the multicast static route was configured, enter the display route-policy command to check the configured routing policy. Multica...
Page 1114
1114 c hapter 68: m ulticast r outing and f orwarding c onfiguration.
Page 1115: Igmp C
69 igmp c onfiguration when configuring igmp, go to the following sections for the information you are interested in: ■ “igmp overview” on page 1115 ■ “igmp configuration task list” on page 1119 ■ “configuring basic functions of igmp” on page 1120 ■ “adjusting igmp performance” on page 1123 ■ “displ...
Page 1116
1116 c hapter 69: igmp c onfiguration n for more information about dr, refer to “pim configuration” on page 1161 . Figure 330 joining multicast groups assume that host b and host c are expected to receive multicast data addressed to multicast group g1, while host a is expected to receive multicast d...
Page 1117
Igmp overview 1117 as igmpv1 does not specifically define a leave group mechanism, upon leaving a multicast group, an igmpv1 host stops sending reports with the destination address being the address of that multicast group. If no member of a multicast group exists on the subnet, the igmp router will...
Page 1118
1118 c hapter 69: igmp c onfiguration enhancements in igmpv3 built upon and being compatible with igmpv1 and igmpv2, igmpv3 provides hosts with enhanced control capabilities and provides enhancements of query and report messages. Enhancements in control capability of hosts igmpv3 has introduced sour...
Page 1119
Igmp configuration task list 1119 ■ a general query does not carry a group address, nor a source address; ■ a group-specific query carries a group address, but no source address; ■ a group-and-source-specific query carries a group address and one or more source addresses. 2 reports containing multip...
Page 1120
1120 c hapter 69: igmp c onfiguration n ■ configurations performed in igmp view are effective on all interfaces, while configurations performed in interface view are effective on the current interface only. ■ if a feature is not configured for an interface in interface view, the global configuration...
Page 1121
Configuring basic functions of igmp 1121 enabling igmp in a vpn instance follow these steps to enable igmp in a vpn instance: configuring igmp versions because the protocol packets of different igmp versions vary in structure and type, the same igmp version should be configured for all routers on th...
Page 1122
1122 c hapter 69: igmp c onfiguration configuring a static member of a multicast group after an interface is configured as a static member of a multicast group, it will act as a virtual member of the multicast group to receive multicast data addressed to that multicast group for the purpose of testi...
Page 1123
Adjusting igmp performance 1123 adjusting igmp performance n for the configuration tasks described in this section ■ configurations performed in igmp view are effective on all interfaces, while configurations performed in interface view are effective on the current interface only. ■ if the same feat...
Page 1124
1124 c hapter 69: igmp c onfiguration configuring igmp packet options on an interface follow these steps to configure igmp packet options on an interface: configuring igmp query and response parameters the igmp querier periodically sends igmp general queries at the “igmp query interval” to determine...
Page 1125
Adjusting igmp performance 1125 network caused by reports simultaneously sent by a large number of hosts when the corresponding timers expire simultaneously. ■ for igmp general queries, you can configure the maximum response time to fill their max response time field. ■ for igmp group-specific queri...
Page 1126
1126 c hapter 69: igmp c onfiguration n ■ if not statically configured, the other querier present interval is [igmp robustness variable] times [ igmp robustness variable ] plus [maximum response time for igmp general queries] divided by two. By default, the values of these three parameters are 60 (s...
Page 1127
Displaying and maintaining igmp 1127 configuring igmp fast leave processing on an interface follow these steps to configure igmp fast leave processing on an interface: c caution: the igmp fast leave feature is effective only if the device is running igmpv2 or igmpv3. Displaying and maintaining igmp ...
Page 1128
1128 c hapter 69: igmp c onfiguration ■ router b and router c connect to n2 through their respective ethernet 1/0, and to other devices in the pim domain through their respective pos5/0. ■ igmpv3 is required between router a and n1. Igmpv2 is required between the other two routers and n2, with route...
Page 1129
Troubleshooting igmp 1129 # enable ip multicast routing on router b, and enable igmp (version 2) and pim-dm on ethernet 1/0. System-view [routerb] multicast routing-enable [routerb] interface ethernet 1/0 [routerb-ethernet1/0] igmp enable [routerb-ethernet1/0] igmp version 2 [routerb-ethernet1/0] pi...
Page 1130
1130 c hapter 69: igmp c onfiguration solution 1 check that the networking is correct and interface connections are correct. 2 check that the interfaces and the host are on the same subnet. Use the display current-configuration interface command to view the ip address of the interface. 3 check that ...
Page 1131: Msdp C
70 msdp c onfiguration when configuring msdp, go to these sections for information you are interested in: ■ “msdp overview” on page 1131 ■ “configuring basic functions of msdp” on page 1138 ■ “configuring an msdp peer connection” on page 1140 ■ “configuring sa messages” on page 1141 ■ “displaying an...
Page 1132
1132 c hapter 70: msdp c onfiguration how msdp works msdp peers with one or more pairs of msdp peers configured in the network, an msdp interconnection map is formed, where the rps of different pim-sm domains are interconnected in series. Relayed by these msdp peers, an sa message sent by an rp can ...
Page 1133
Msdp overview 1133 will assume the role of common pim-sm routers on the “msdp interconnection map”. Implementing inter-domain multicast delivery by leveraging msdp peers as shown in figure 334 , an active source exists in the domain pim-sm 1, and rp 1 learns the existence of this number source throu...
Page 1134
1134 c hapter 70: msdp c onfiguration 4 sa messages are forwarded from one msdp peer to another, and finally the information of the multicast source traverses all pim-sm domains with msdp peers (pim-sm 2 and pim-sm 3 in this example). 5 upon receiving the sa message create by rp 1, rp 2 in pim-sm 2 ...
Page 1135
Msdp overview 1135 figure 335 diagram for rpf check for sa messages as illustrated in figure 335 , these msdp peers dispose of sa messages according to the following rpf check rules: 1 when rp 2 receives an sa message from rp 1 because the source-side rp address carried in the sa message is the same...
Page 1136
1136 c hapter 70: msdp c onfiguration an ebgp route exists between two msdp peers in different ass. Because the sa message is from an msdp peer (rp 7) in a different as, and the msdp peer is the next hop on the ebgp route to the source-side rp, rp 8 accepts the message and forwards it to its other p...
Page 1137
Msdp configuration task list 1137 from source encapsulated in the sa message. When the sa message reaches rp 2, rp 2 decapsulates the message. 4 receivers receive the multicast data along the rpt and directly joins the spt rooted at the multicast source. In this example, rp 2 forwards the multicast ...
Page 1138
1138 c hapter 70: msdp c onfiguration configuring basic functions of msdp n all the configuration tasks shall be implemented on rps in pim-sm domains, and each of these rps acts as an msdp peer. Configuration prerequisites before configuring the basic functions of msdp, complete the following tasks:...
Page 1139
Configuring basic functions of msdp 1139 creating an msdp peer connection an msdp peering relationship is identified by an address pair, namely the address of the local msdp peer and that of the remote msdp peer. An msdp peer connection must be created on both devices that are a pair of msdp peers. ...
Page 1140
1140 c hapter 70: msdp c onfiguration configuring an msdp peer connection configuration prerequisites before configuring msdp peer connection, complete the following tasks: ■ configuring any unicast routing protocol so that all devices in the domain are interoperable at the network layer ■ configuri...
Page 1141
Configuring sa messages 1141 n ■ before grouping multiple routers into an msdp mesh group, make sure that these routers are interconnected with one another. ■ if you configure more than one mesh group name on an msdp peer, only the last configuration is effective. Configuring msdp peer connection co...
Page 1142
1142 c hapter 70: msdp c onfiguration ■ acl as a filtering rule for sa request messages ■ acl as an sa message creation rule ■ acl as a filtering rule for receiving or forwarding sa messages ■ minimum ttl value of multicast packets encapsulated in sa messages ■ maximum sa message cache size configur...
Page 1143
Configuring sa messages 1143 send sa request messages to the designated msdp peers up receiving a join message of a new receiver. Follow these steps to configure sa message transmission and filtering: c caution: before you can enable the device to send sa requests, be sure to disable the sa message ...
Page 1144
1144 c hapter 70: msdp c onfiguration configuring sa message cache to reduce the time spent in obtaining the multicast source information, you can have sa messages cached on the router. However, the more sa messages are cached, the larger memory space of the router is used. With the sa cache mechani...
Page 1145
Msdp configuration examples 1145 msdp configuration examples example of leveraging bgp routes network requirements ■ two isps maintain their ass, as 100 and as 200 respectively. Ospf is running within each as, and bgp is running between the two ass. ■ pim-sm 1 belongs to as 100, while pim-sm 2 and p...
Page 1146
1146 c hapter 70: msdp c onfiguration network diagram figure 337 network diagram for configuration leveraging a bgp route (on routers) configuration procedure 1 configure the interface ip addresses and unicast routing protocol for each router configure the ip address and subnet mask for each interfa...
Page 1147
Msdp configuration examples 1147 system-view [routerc] multicast routing-enable [routerc] interface ethernet 1/0 [routerc-ethernet1/0] pim sm [routerc-ethernet1/0] quit [routerc] interface ethernet 1/1 [routerc-ethernet1/1] pim sm [routerc-ethernet1/1] quit [routerc] interface pos 5/0 [routerc-pos5/...
Page 1148
1148 c hapter 70: msdp c onfiguration # configure ibgp on router f, and redistribute ospf routes. [routerf] bgp 200 [routerf-bgp] router-id 3.3.3.3 [routerf-bgp] peer 192.168.3.1 as-number 200 [routerf-bgp] import-route ospf 1 [routerf-bgp] quit # inject bgp routing information into ospf on router c...
Page 1149
Msdp configuration examples 1149 bgp local router id is 2.2.2.2 status codes: * - valid, > - best, d - damped, h - history, i - internal, s - suppressed, s - stale origin : i - igp, e - egp, ? - incomplete network nexthop med locprf prefval path/ogn *> 1.1.1.1/32 192.168.1.1 0 0 100? *>i 2.2.2.2/32 ...
Page 1150
1150 c hapter 70: msdp c onfiguration 192.168.3.2 up 00:15:32 200 8 0 192.168.1.1 up 00:06:39 100 13 0 # view the brief information about msdp peering relationships on router f. [routerf] display msdp brief msdp peer brief information of vpn-instance: public net configured up listen connect shutdown...
Page 1151
Msdp configuration examples 1151 network diagram figure 338 network diagram for anycast rp application configuration configuration procedure 1 configure the interface ip addresses and unicast routing protocol for each router configure the ip address and subnet mask for each interface as per figure 3...
Page 1152
1152 c hapter 70: msdp c onfiguration [routerb-ethernet1/0] pim sm [routerb-ethernet1/0] quit [routerb] interface serial 2/0 [routerb-serial2/0] pim sm [routerb-serial2/0] quit [routerb] interface pos 5/0 [routerb-pos5/0] pim sm [routerb-pos5/0] quit the configuration on router a, router c, router d...
Page 1153
Msdp configuration examples 1153 you can use the display msdp brief command to view the brief information of msdp peering relationships between the routers. # view the brief msdp peer information on router b. [routerb] display msdp brief msdp peer brief information of vpn-instance: public net config...
Page 1154
1154 c hapter 70: msdp c onfiguration 1: ethernet1/0 protocol: pim-sm, uptime: - , expires: - # view the pim routing information on router d. [routerd] display pim routing-table no information is output on router d. Receiver 1 has left multicast group g, and source 1 has stopped sending multicast da...
Page 1155
Msdp configuration examples 1155 ■ pim-sm 1 belongs to as 100, while pim-sm 2 and pim-sm 3 belong to as 200. ■ each pim-sm domain has zero or one multicast source and one or more receivers. Ospf runs within each domain to provide unicast routes. ■ pim-sm 2 and pim-sm 3 are both pim stub domains, and...
Page 1156
1156 c hapter 70: msdp c onfiguration configure ospf for interconnection between the routers. Ensure the network-layer interoperation among router a, router b and router c in pim-sm 1, the network-layer interoperation between router d and router e in pim-sm 2, and the network-layer interoperation be...
Page 1157
Msdp configuration examples 1157 # configure router d and router f as msdp peers and static rpf peers of router c. [routerc] ip ip-prefix list-df permit 192.168.0.0 16 greater-equal 1 6 less-equal 32 [routerc] msdp [routerc-msdp] peer 192.168.3.2 connect-interface serial 2/0 [routerc-msdp] peer 192....
Page 1158
1158 c hapter 70: msdp c onfiguration peer’s address state up/down time as sa count reset count 192.168.1.1 up 01:07:09 ? 8 0 # view the brief msdp peer information on router f. [routerf] display msdp brief msdp peer brief information of vpn-instance: public net configured up listen connect shutdown...
Page 1159
Troubleshooting msdp 1159 solution 1 check that a route is available between the routers. Carry out the display ip routing-table command to check whether the unicast route between the routers is correct. 2 check that a unicast route is available between the two routers that will become msdp peers to...
Page 1160
1160 c hapter 70: msdp c onfiguration.
Page 1161: Pim C
71 pim c onfiguration when configuring pim, go to these sections for information you are interested in: ■ “pim overview” on page 1161 ■ “configuring pim-dm” on page 1173 ■ “configuring pim-sm” on page 1176 ■ “configuring pim-ssm” on page 1185 ■ “configuring pim common information” on page 1187 ■ “di...
Page 1162
1162 c hapter 71: pim c onfiguration ■ pim-dm assumes that at least one multicast group member exists on each subnet of a network, and therefore multicast data is flooded to all nodes on the network. Then, branches without multicast forwarding are pruned from the forwarding tree, leaving only those ...
Page 1163
Pim overview 1163 a prune process is first initiated by a leaf router. As shown in figure 340 , a router without any receiver attached to it (the router connected with host a, for example) sends a prune message, and this prune process goes on until only necessary branches are left in the pim-dm doma...
Page 1164
1164 c hapter 71: pim c onfiguration figure 341 assert mechanism as shown in figure 341 , after router a and router b receive an (s, g) packet from the upstream node, they both forward the packet to the local subnet. As a result, the downstream node router c receives two identical multicast packets,...
Page 1165
Pim overview 1165 ■ when a receiver is interested in the multicast data addressed to a specific multicast group, the router connected to this receiver sends a join message to the rp corresponding to that multicast group. The path along which the message goes hop by hop to the rp forms a branch of th...
Page 1166
1166 c hapter 71: pim c onfiguration figure 342 dr election as shown in figure 342 , the dr election process is as follows: 1 routers on the multi-access network send hello messages to one another. The hello messages contain the router priority for dr election. The router with the highest dr priorit...
Page 1167
Pim overview 1167 domain, and the position of the rp corresponding to each multicast group is calculated through the bsr mechanism. Figure 343 shows the positions of c-rps and the bsr in the network. Figure 343 bsr and c-rps rpt building figure 344 rpt establishment in a pim-sm domain as shown in fi...
Page 1168
1168 c hapter 71: pim c onfiguration the multicast data addressed to the multicast group g flows through the rp, reaches the corresponding dr along the established rpt, and finally is delivered to the receiver. When a receiver is no longer interested in the multicast data addressed to a multicast gr...
Page 1169
Pim overview 1169 switchover from rpt to spt initially, multicast traffic flows along an rpt from the rp to the receivers. Because the rpt is not necessarily the tree that has the shortest path, upon receiving the first multicast packet along the rpt (by default), or when detecting that the multicas...
Page 1170
1170 c hapter 71: pim c onfiguration figure 346 relationship between bsr admin-scope regions and the global scope zone in geographic space bsr admin-scope regions are geographically separated from one another. Namely, a router must not serve different bsr admin-scope regions. In other words, differe...
Page 1171
Pim overview 1171 relationships between bsr admin-scope regions and the global scope zone are as follows: ■ the global scope zone and each bsr admin-scope region have their own c-rps and bsr. These devices are effective only in their respective admin-scope regions. Namely, the bsr election and rp el...
Page 1172
1172 c hapter 71: pim c onfiguration construction of spt whether to build an rpt for pim-sm or an spt for pim-ssm depends on whether the multicast group the receiver is to join falls in the ssm group address range (ssm group address range reserved by iana is 232.0.0.0/8). Figure 348 spt establishmen...
Page 1173
Configuring pim-dm 1173 corresponding to that vpn instance for processing. Upon receiving a multicast data packet, the multicast router determines the vpn instance the data packet belongs to, and then forwards the packet as per the multicast routing table of that vpn instance or creates a multicast ...
Page 1174
1174 c hapter 71: pim c onfiguration pim-dm domain, you are recommended to enable pim-dm on all interfaces of non-border routers (border routers are pim-enabled routers located on the boundary of bsr admin-scope regions). Enabling pim-dm globally in the public instance follow these steps to enable p...
Page 1175
Configuring pim-dm 1175 configuring state refresh parameters to avoid the resource-consuming reflooding of unwanted traffic caused by timeout of pruned interfaces, the router directly connected with the multicast source periodically sends an (s, g) state refresh message, which is forwarded hop by ho...
Page 1176
1176 c hapter 71: pim c onfiguration n for the configuration of other timers in pim-dm, refer to “configuring pim common timers” on page 1190 . Configuring pim-sm n a device can serve as a c-rp and a c-bsr at the same time. Pim-sm configuration task list complete these tasks to configure pim-sm: con...
Page 1177
Configuring pim-sm 1177 ■ hash mask length for rp selection calculation ■ c-bsr priority ■ bootstrap interval ■ bootstrap timeout time ■ an acl rule defining a legal c-rp address range and the range of multicast groups to be served ■ c-rp-adv interval ■ c-rp timeout time ■ the ip address of a static...
Page 1178
1178 c hapter 71: pim c onfiguration c caution: all the interfaces in the same vpn instance on the same router must work in the same pim mode. Configuring a bsr n the bsr is dynamically elected from a number of c-bsrs. Because it is unpredictable which router will finally win a bsr election, the com...
Page 1179
Configuring pim-sm 1179 maliciously replaced, preventive measures are taken specific to the following two situations: 1 some malicious hosts intend to fool routers by forging bsr messages and change the rp mapping relationship. Such attacks often occur on border routers. Because a bsr is inside the ...
Page 1180
1180 c hapter 71: pim c onfiguration configuring an admin-scope c-bsr by default, a pim-sm domain has only one bsr. The entire network should be managed by this bsr. To manage your network more effectively and specifically, you can divide a pim-sm domain into multiple bsr admin-scope regions, with e...
Page 1181
Configuring pim-sm 1181 configuring global c-bsr parameters the bsr election winner advertises its own ip address and rp-set information throughout the region it serves through bootstrap messages. The bsr floods bootstrap messages throughout the network periodically. Any c-bsr that receives a bootst...
Page 1182
1182 c hapter 71: pim c onfiguration configuring an rp an rp can be manually configured or dynamically elected through the bsr mechanism. For a large pim network, static rp configuration is a tedious job. Generally, static rp configuration is just a backup means for the dynamic rp election mechanism...
Page 1183
Configuring pim-sm 1183 n ■ when configuring a c-rp, ensure a relatively large bandwidth between this c-rp and the other devices in the pim-sm domain. ■ an rp can serve multiple multicast groups or all multicast groups. Only one rp can forward multicast traffic for a multicast group at a moment. Ena...
Page 1184
1184 c hapter 71: pim c onfiguration configuring pim-sm register messages within a pim-sm domain, the source-side dr sends register messages to the rp, and these register messages have different multicast source or group addresses. You can configure a filtering rule to filter register messages so th...
Page 1185
Configuring pim-ssm 1185 should carry out these configurations on the routers that may win the dr election and on the c-rps that may win rp elections. Configuring rpt-to-spt switchover because the rpt is not necessarily the tree that has the shortest path, the multicast forwarding path needs to be s...
Page 1186
1186 c hapter 71: pim c onfiguration configuration prerequisites before configuring pim-ssm, complete the following task: ■ configure any unicast routing protocol so that all devices in the domain are interoperable at the network layer. Before configuring pim-ssm, prepare the following data: ■ the s...
Page 1187
Configuring pim common information 1187 whether the group address in the (s, g) channel subscribed by the receivers falls in the ssm group range. All pim-sm-enabled interfaces assume that multicast groups within this address range are using the ssm model. Follow these steps to configure an ssm group...
Page 1188
1188 c hapter 71: pim c onfiguration before configuring pim common information, prepare the following data: ■ an acl rule as multicast data filter ■ priority for dr election (global value/interface level value) ■ pim neighbor timeout time (global value/interface value) ■ prune delay (global value/in...
Page 1189
Configuring pim common information 1189 ■ holdtime: the timeout time of pim neighbor reachability state. When this timer times out, if the router has received no hello message from a neighbor, it assumes that this neighbor has expired or become unreachable. You can configure this parameter on all ro...
Page 1190
1190 c hapter 71: pim c onfiguration configuring hello options on an interface follow these steps to configure hello options for an interface: configuring pim common timers pim routers discover pim neighbors and maintain pim neighboring relationships with other routers by periodically sending out he...
Page 1191
Configuring pim common information 1191 router sets a join/prune timeout timer for each pruned downstream interface, and resumes the forwarding state of the pruned interface when this timer times out. When a router fails to receive subsequent multicast data from the multicast source s, the router wi...
Page 1192
1192 c hapter 71: pim c onfiguration configuring join/prune message limits a larger join/prune message size will result in loss of a larger amount of information when a message is lost; with a reduced join/message size, the loss of a single message will bring relatively minor impact. By controlling ...
Page 1193
Pim configuration examples 1193 pim configuration examples pim-dm configuration example network requirements ■ receivers receive vod information through multicast. The receiver groups of different organizations form stub networks, and one or more receiver hosts exist in each stub network. The entire...
Page 1194
1194 c hapter 71: pim c onfiguration network diagram figure 349 network diagram for pim-dm configuration configuration procedure 1 configure the interface ip addresses and unicast routing protocol for each router configure the ip address and subnet mask for each interface as per figure 349 . Detaile...
Page 1195
Pim configuration examples 1195 [routera] interface ethernet 1/0 [routera-ethernet1/0] igmp enable [routera-ethernet1/0] pim dm [routera-ethernet1/0] quit [routera] interface serial 2/0 [routera-serial2/0] pim dm [routera-serial2/0] quit the configuration on router b and router c is similar to the c...
Page 1196
1196 c hapter 71: pim c onfiguration assume that host a needs to receive the information addressed to a multicast group g (225.1.1.1/24). After the multicast source s (10.110.5.100/24) sends multicast packets to the multicast group g, an spt is established through traffic flooding. Routers on the sp...
Page 1197
Pim configuration examples 1197 pim-sm configuration example network requirements ■ receivers receive vod information through multicast. The receiver groups of different organizations form stub networks, and one or more receiver hosts exist in each stub network. The entire pim domain operates in the...
Page 1198
1198 c hapter 71: pim c onfiguration network diagram figure 350 network diagram for pim-sm domain configuration configuration procedure 1 configure the interface ip addresses and unicast routing protocol for each router configure the ip address and subnet mask for each interface as per figure 350 . ...
Page 1199
Pim configuration examples 1199 system-view [routera] multicast routing-enable [routera] interface ethernet 1/0 [routera-ethernet1/0] igmp enable [routera-ethernet1/0] pim sm [routera-ethernet1/0] quit [routera] interface serial 2/0 [routera-serial2/0] pim sm [routera-serial2/0] quit [routera] inter...
Page 1200
1200 c hapter 71: pim c onfiguration hash mask length: 30 state: accept preferred scope: not scoped uptime: 00:40:40 expires: 00:01:42 # view the bsr information and the locally configured c-rp information in effect on router e. [routere] display pim bsr-info vpn-instance: public net elected bsr add...
Page 1201
Pim configuration examples 1201 total 1 (*, g) entry; 1 (s, g) entry (*, 225.1.1.1) rp: 192.168.9.2 protocol: pim-sm, flag: wc uptime: 00:13:46 upstream interface: pos5/0 upstream neighbor: 192.168.9.2 rpf prime neighbor: 192.168.9.2 downstream interface(s) information: total number of downstreams: ...
Page 1202
1202 c hapter 71: pim c onfiguration rpf prime neighbor: 192.168.4.2 downstream interface(s) information: total number of downstreams: 1 1: pos5/2 protocol: pim-sm, uptime: 00:13:16, expires: 00:03:22 pim-ssm configuration example network requirements ■ receivers receive vod information through mult...
Page 1203
Pim configuration examples 1203 network diagram figure 351 network diagram for pim-ssm configuration configuration procedure 1 configure the interface ip addresses and unicast routing protocol for each router configure the ip address and subnet mask for each interface as per figure 351 . Detailed co...
Page 1204
1204 c hapter 71: pim c onfiguration system-view [routera] multicast routing-enable [routera] interface ethernet 1/0 [routera-ethernet1/0] igmp enable [routera-ethernet1/0] igmp version 3 [routera-ethernet1/0] pim sm [routera-ethernet1/0] quit [routera] interface serial 2/0 [routera-serial2/0] pim s...
Page 1205
Troubleshooting pim configuration 1205 [routera] display pim routing-table vpn-instance: public net total 0 (*, g) entry; 1 (s, g) entry (10.110.5.100, 232.1.1.1) protocol: pim-ssm, flag: uptime: 00:13:25 upstream interface: serial2/0 upstream neighbor: 192.168.1.2 rpf prime neighbor: 192.168.1.2 do...
Page 1206
1206 c hapter 71: pim c onfiguration the router does not have a router to the multicast source, or if pim-dm is not enabled on the router’s rpf interface to the multicast source, the router cannot create (s, g) entries. ■ when a multicast router receives a multicast packet, it searches the existing ...
Page 1207
Troubleshooting pim configuration 1207 analysis ■ when a router receives a multicast packet, it decrements the ttl value of the multicast packet by 1 and recalculates the checksum value. The router then forwards the packet to all outgoing interfaces. If the multicast minimum-ttl command is configure...
Page 1208
1208 c hapter 71: pim c onfiguration 3 check the configuration of static rps. Use the display pim rp-info command to check whether the same static rp address has been configured on all the routers in the entire network. No unicast route between bsr and c-rps in pim-sm symptom c-rps cannot unicast ad...
Page 1209: 6 M
72 ip v 6 m ulticast r outing and f orwarding c onfiguration when configuring ipv6 multicast routing and forwarding, go to the following sections for information you are interested in: ■ “ipv6 multicast routing and forwarding configuration” on page 1209 ■ “configuring ipv6 multicast routing and forw...
Page 1210
1210 c hapter 72: ip v 6 m ulticast r outing and f orwarding c onfiguration implementation of the rpf mechanism upon receiving an ipv6 multicast packet sent from a multicast source s to an ipv6 multicast group g, the router first searches its ipv6 multicast forwarding table: 1 if the corresponding (...
Page 1211
Configuration task list 1211 ■ for a bootstrap message from the bootstrap router (bsr), “packet source” means the bsr. For details about the concepts of spt, rpt, rp and bsr, refer to “ipv6 pim configuration” on page 1235 . Assume that ipv6 unicast routes exist in the network, and ipv6 multicast pac...
Page 1212
1212 c hapter 72: ip v 6 m ulticast r outing and f orwarding c onfiguration configuring ipv6 multicast routing and forwarding configuration prerequisites before configuring ipv6 multicast routing and forwarding, complete the following tasks: ■ configure an ipv6 unicast routing protocol so that all d...
Page 1213
Configuring ipv6 multicast routing and forwarding 1213 configuring an ipv6 multicast forwarding range ipv6 multicast packets do not travel infinitely in a network. The ipv6 multicast data of each ipv6 multicast group must be transmitted within a definite scope. Presently, you can define an ipv6 mult...
Page 1214
1214 c hapter 72: ip v 6 m ulticast r outing and f orwarding c onfiguration exceed the maximum number allowed by the system. This maximum value varies with different device models. If the configured maximum number of downstream nodes (namely the maximum number of outgoing interfaces) for a routing e...
Page 1215
Troubleshooting ipv6 multicast routing and forwarding 1215 c caution: ■ the reset command clears the information in the ipv6 multicast forwarding table or the multicast routing table, and thus may cause transmission failure of ipv6 multicast information. ■ when a forwarding entry is deleted from the...
Page 1216
1216 c hapter 72: ip v 6 m ulticast r outing and f orwarding c onfiguration ■ the multicast ipv6 boundary command is used to filter ipv6 multicast packets received on an interface. If an ipv6 multicast packet fails to match the ipv6 acl rule of this command, ipv6 pim will create no routing entry. ■ ...
Page 1217: Mld C
73 mld c onfiguration when configuring mld, go to the following sections for information you are interested in: ■ “mld overview” on page 1217 ■ “configuring basic functions of mld” on page 1224 ■ “adjusting mld performance” on page 1226 ■ “displaying and maintaining mld configuration” on page 1230 ■...
Page 1218
1218 c hapter 73: mld c onfiguration mld querier election of multiple ipv6 multicast routers on the same subnet, all the routers can hear mld listener report messages (often referred to as reports) from hosts, but only one router is needed for sending mld query messages (often referred to as queries...
Page 1219
Mld overview 1219 3 host c, which is on the same subnet, hears the report from host b for joining g1. Upon hearing the report, host c will suppress itself from sending a report message for the same ipv6 multicast group, because the mld routers (router a and router b) already know that at least one h...
Page 1220
1220 c hapter 73: mld c onfiguration as shown in figure 354 , the network comprises two ipv6 multicast sources, source 1 (s1) and source 2 (s2), both of which can send ipv6 multicast data to ipv6 multicast group g. Host b is interested only in the ipv6 multicast data that source 1 sends to g but not...
Page 1221
Mld overview 1221 mld query message an mld querier learns the multicast listening state of neighbor interfaces by sending mld query messages. Figure 355 shows the format of an mld query message. The dark blue area in the figure shows the format of an mldv1 message. Figure 355 format of mldv2 query m...
Page 1222
1222 c hapter 73: mld c onfiguration mld report message a host sends an mld report message to report the current multicast listening state figure 356 shows the format of an mld report message. Figure 356 format of mldv2 report message table 48 describes the fields in figure 356 . S flag indicating w...
Page 1223
Configuration task list 1223 protocols and standards mld-related specifications are described in the following documents: ■ rfc 2710: multicast listener discovery (mld) for ipv6 ■ rfc 3810: multicast listener discovery version 2 (mldv2) for ipv6 configuration task list n ■ configurations performed i...
Page 1224
1224 c hapter 73: mld c onfiguration configuring basic functions of mld configuration prerequisites before configuring the basic functions of mld, complete the following tasks: ■ configure any ipv6 unicast routing protocol so that all devices in the domain can be interoperable at the network layer. ...
Page 1225
Configuring basic functions of mld 1225 configuring a static member of an ipv6 multicast group after an interface is configured as a static member of an ipv6 multicast group, it will act as a virtual member of the ipv6 multicast group to receive ipv6 multicast data addressed to that ipv6 multicast g...
Page 1226
1226 c hapter 73: mld c onfiguration adjusting mld performance n for the configuration tasks described in this section, ■ configurations performed in mld view are globally effective, while configurations performed in interface view are effective on the current interface only. ■ if the same function ...
Page 1227
Adjusting mld performance 1227 configuring the router-alert option for mld messages globally follow these steps to configure the router-alert option for mld messages globally: configuring the router-alert option on an interface follow these steps to configure the router-alert option on an interface:...
Page 1228
1228 c hapter 73: mld c onfiguration 0, the host sends an mld membership report message to the corresponding ipv6 multicast group. Proper setting of the maximum response delay of mld query messages not only allows hosts to respond to mld query messages quickly, but also avoids burstiness of mld traf...
Page 1229
Adjusting mld performance 1229 n ■ if not configured manually, the other querier present timeout is determined by the formula: other querier present timeout interval (in seconds) = ([ mld query interval) ] times ([ mld querier robustness variable) ] plus ([ one half of the maximum response delay of ...
Page 1230
1230 c hapter 73: mld c onfiguration configuring mld fast leave processing on an interface follow these steps to configure the mld fast leave processing on an interface: displaying and maintaining mld configuration n you cannot use the reset mld group command to clear mld forwarding entries of stati...
Page 1231
Mld configuration example 1231 ■ mldv1 is required between router a and n1. Mldv2 is required between the other two routers (router b and router c) and n2, with router b as the mld querier. Network diagram figure 357 network diagram for mld configuration (on routers) configuration procedure 1 config...
Page 1232
1232 c hapter 73: mld c onfiguration # enable ipv6 multicast routing on router b, enable mld and ipv6 pim-dm on ethernet1/0, and set the mld version number to 2. System-view [routerb] multicast ipv6 routing-enable [routerb] interface ethernet 1/0 [routerb-ethernet1/0] mld enable [routerb-ethernet1/0...
Page 1233
Troubleshooting mld 1233 solution 1 check that the networking is correct and that interface connections are correct. 2 check that the interfaces and the host are on the same subnet. Carry out the display current-configuration interface command to display the ipv6 address of the interface. 3 check th...
Page 1234
1234 c hapter 73: mld c onfiguration.
Page 1235: 6 Pim C
74 ip v 6 pim c onfiguration when configuring ipv6 pim, go to these sections for information you are interested in: ■ “ipv6 pim overview” on page 1235 ■ “configuring ipv6 pim-dm” on page 1246 ■ “configuring ipv6 pim-sm” on page 1248 ■ “configuring ipv6 pim-ssm” on page 1256 ■ “configuring ipv6 pim c...
Page 1236
1236 c hapter 74: ip v 6 pim c onfiguration ■ ipv6 pim-dm assumes that at least one ipv6 multicast group member exists on each subnet of a network, and therefore ipv6 multicast data is flooded to all nodes on the network. Then, branches without ipv6 multicast forwarding are pruned from the forwardin...
Page 1237
Ipv6 pim overview 1237 ■ for a given ipv6 multicast stream, the interface that receives the ipv6 multicast stream is referred to as “upstream”, and the interfaces that forward the ipv6 multicast stream are referred to as “downstream”. A prune process is first initiated by a leaf router. As shown in ...
Page 1238
1238 c hapter 74: ip v 6 pim c onfiguration assert if multiple multicast routers exist on a multi-access subnet, duplicate ipv6 multicast packets may flow to the same subnet. To shutoff duplicate flows, the assert mechanism is used for election of a single ipv6 multicast forwarder on a multi-access ...
Page 1239
Ipv6 pim overview 1239 ■ ipv6 pim-sm assumes that no hosts need to receive ipv6 multicast data. In the ipv6 pim-sm mode, routers must specifically request a particular ipv6 multicast stream before the data is forwarded to them. The core task for ipv6 pim-sm to implement ipv6 multicast forwarding is ...
Page 1240
1240 c hapter 74: ip v 6 pim c onfiguration n ■ a dr is elected on a multi-access subnet by means of comparison of the priorities and ip addresses carried in hello messages. ■ mld must be enabled on a device that acts as a dr before receivers attached to this device can join ipv6 multicast groups th...
Page 1241
Ipv6 pim overview 1241 rps. The bsr then floods the rp-set to the entire ipv6 pim-sm domain. Based on the information in these rp-sets, all routers (including the drs) in the network can calculate the location of the corresponding rps. An ipv6 pim-sm domain can have only one bsr, but can have multip...
Page 1242
1242 c hapter 74: ip v 6 pim c onfiguration rpt establishment figure 362 rpt establishment in an ipv6 pim-sm domain as shown in figure 362 , the process of building an rpt is as follows: 1 when a receiver joins an ipv6 multicast group g, it uses an mld report message to inform the directly connected...
Page 1243
Ipv6 pim overview 1243 figure 363 ipv6 multicast source registration as shown in figure 363 , the ipv6 multicast source registers with the rp as follows: 1 when the ipv6 multicast source s sends the first ipv6 multicast packet to an ipv6 multicast group g, the dr directly connected with the multicas...
Page 1244
1244 c hapter 74: ip v 6 pim c onfiguration after the rpt-to-spt switchover, ipv6 multicast data can be directly sent from the source to the receivers. Ipv6 pim-sm builds spts through rpt-to-spt switchover more economically than ipv6 pim-dm does through the “flood and prune” mechanism. Assert ipv6 p...
Page 1245
Ipv6 pim overview 1245 figure 364 building an spt in ipv6 pim-ssm as shown in figure 364 , hosts b and c are ipv6 multicast information receivers. They send an mldv2 report message marked (include s, g) to the respective drs to announce that they are interested in the information of the specific ipv...
Page 1246
1246 c hapter 74: ip v 6 pim c onfiguration ■ draft-ietf-pim-dm-new-v2-02: protocol independent multicast-dense mode (pim-dm) ■ draft-ietf-pim-v2-dm-03: protocol independent multicast version 2 dense mode specification ■ draft-ietf-pim-sm-bsr-02: bootstrap router (bsr) mechanism for pim sparse mode ...
Page 1247
Configuring ipv6 pim-dm 1247 c caution: ■ all the interfaces of the same device must work in the same ipv6 pim mode. ■ ipv6 pim-dm cannot be used for ipv6 multicast groups in the ipv6 ssm group range. Enabling state refresh an interface without the state refresh capability cannot forward state refre...
Page 1248
1248 c hapter 74: ip v 6 pim c onfiguration configuring ipv6 pim-dm graft retry period in ipv6 pim-dm, graft is the only type of message that uses the acknowledgment mechanism. In an ipv6 pim-dm domain, if a router does not receive a graft-ack message from the upstream router within the specified ti...
Page 1249
Configuring ipv6 pim-sm 1249 configuration prerequisites before configuring ipv6 pim-sm, complete the following task: ■ configure any ipv6 unicast routing protocol so that all devices in the domain are interoperable at the network layer. Before configuring ipv6 pim-sm, prepare the following data: ■ ...
Page 1250
1250 c hapter 74: ip v 6 pim c onfiguration c caution: all the interfaces of the same device must work in the same ipv6 pim mode. Configuring a bsr n the bsr is dynamically elected from a number of c-bsrs. Because it is unpredictable which router will finally win a bsr election, the commands introdu...
Page 1251
Configuring ipv6 pim-sm 1251 perform neighbor check and rpf check on bsr messages and discard unwanted messages. 2 when a router in the network is controlled by an attacker or when an illegal router is present in the network, the attacker can configure such a router to be a c-bsr and make it win bsr...
Page 1252
1252 c hapter 74: ip v 6 pim c onfiguration a bootstrap message maintains the bsr state for a configurable period of time (bsr state timeout), during which no bsr election takes place. When the bsr state times out, a new bsr election process will be triggered among the c-bsrs. Follow these steps to ...
Page 1253
Configuring ipv6 pim-sm 1253 normally, you must perform this configuration on all the devices in the ipv6 pim-sm domain and specify the same rp address. Follow these steps to configure a static rp: configuring a c-rp in an ipv6 pim-sm domain, you can configure routers that intend to become the rp as...
Page 1254
1254 c hapter 74: ip v 6 pim c onfiguration based on the bsr mechanism. Thus, the dr does not need to know the rp address beforehand. Follow these steps to enable embedded rp: n the default embedded rp address ranges are ff7x::/12 and fffx::/12, where x represents any legal scope. For details about ...
Page 1255
Configuring ipv6 pim-sm 1255 messages so that the rp can serve specific ipv6 multicast groups. If an (s, g) entry is denied by the filtering rule, or the action for this entry is not defined in the filtering rule, the rp will send a register-stop message to the dr to stop the registration process fo...
Page 1256
1256 c hapter 74: ip v 6 pim c onfiguration ipv6 multicast traffic increases. Initially, an ipv6 pim-sm router forwards ipv6 multicast packets through the rpt. However, when the traffic rate of ipv6 multicast packets reaches a threshold (configurable on routers, but not on switches), the receiver-si...
Page 1257
Configuring ipv6 pim-ssm 1257 before configuring ipv6 pim-ssm, prepare the following data: ■ the ipv6 ssm group range enabling ipv6 pim-sm the ssm model is implemented based on some subsets of ipv6 pim-sm. Therefore, a router is ipv6 pim-ssm capable after you enable ipv6 pim-sm on it. When deploying...
Page 1258
1258 c hapter 74: ip v 6 pim c onfiguration ■ if an ipv6 multicast group falls in the ipv6 ssm group range, but members of this group send mldv1 joins, the device that receives these join messages will not trigger (*, g) joins. Configuring ipv6 pim common information n for the configuration tasks de...
Page 1259
Configuring ipv6 pim common information 1259 configuring an ipv6 pim filter no matter in an ipv6 pim-dm domain or an ipv6 pim-sm domain, routers can check passing-by ipv6 multicast data based on the configured filtering rules and determine whether to continue forwarding the ipv6 multicast data. In o...
Page 1260
1260 c hapter 74: ip v 6 pim c onfiguration the override-interval sets the length of time a downstream router is allowed to wait before sending a prune override message. When a router receives a prune message from a downstream router, it does not perform the prune action immediately; instead, it mai...
Page 1261
Configuring ipv6 pim common information 1261 configuring ipv6 pim common timers ipv6 pim routers discover ipv6 pim neighbors and maintain ipv6 pim neighboring relationships with other routers by periodically sending out hello messages. Upon receiving a hello message, an ipv6 pim router waits a rando...
Page 1262
1262 c hapter 74: ip v 6 pim c onfiguration configuring ipv6 pim common timers on an interface follow these steps to configure ipv6 pim common timers on an interface: n if there are no special networking requirements, we recommend that you use the default settings. Configuring join/prune message lim...
Page 1263
Displaying and maintaining ipv6 pim 1263 displaying and maintaining ipv6 pim ipv6 pim configuration examples ipv6 pim-dm configuration example network requirements ■ receivers receive vod information through multicast. The receiver groups of different organizations form stub networks, and at least o...
Page 1264
1264 c hapter 74: ip v 6 pim c onfiguration ■ host a and host c are ipv6 multicast receivers in two stub networks n1 and n2. ■ router d connects to the network that comprises the ipv6 multicast source (source) through ethernet 1/0. ■ router a connects to n1 through ethernet 1/0, and to router d thro...
Page 1265
Ipv6 pim configuration examples 1265 configure the ospfv3 protocol for interoperation among the routers in the ipv6 pim-dm domain. Ensure the network-layer interoperation among router a, router b, router c and router d in the ipv6 pim-dm domain and enable dynamic update of routing information among ...
Page 1266
1266 c hapter 74: ip v 6 pim c onfiguration pos5/1 1 30 1 3002::2 (local) carry out the display pim ipv6 neighbor command to view the ipv6 pim neighboring relationships among the routers. For example: # verify the ipv6 pim neighboring relationships on router d. [routerd] display pim ipv6 neighbor to...
Page 1267
Ipv6 pim configuration examples 1267 (4001::100, ff0e::101) protocol: pim-dm, flag: loc act uptime: 00:02:19 upstream interface: ethernet1/0 upstream neighbor: null rpf prime neighbor: null downstream interface(s) information: total number of downstreams: 3 1: serial2/0 protocol: pim-dm, uptime: 00:...
Page 1268
1268 c hapter 74: ip v 6 pim c onfiguration network diagram figure 366 network diagram for ipv6 pim-sm configuration (on routers) configuration procedure 1 configure the interface ipv6 addresses and ipv6 unicast routing protocol for each router configure the ip address and prefix length for each int...
Page 1269
Ipv6 pim configuration examples 1269 # enable ipv6 multicast routing on router a, enable ipv6 pim-sm on each interface, and enable mldv1 on ethernet 1/0, which connects router a to n1. System-view [routera] multicast ipv6 routing-enable [routera] interface ethernet 1/0 [routera-ethernet1/0] mld enab...
Page 1270
1270 c hapter 74: ip v 6 pim c onfiguration hash mask length: 126 state: accept preferred uptime: 00:04:22 expires: 00:01:46 # view the bsr information on router e and the locally configured c-rp information in effect. [routere] display pim ipv6 bsr-info elected bsr address: 1003::2 priority: 0 hash...
Page 1271
Ipv6 pim configuration examples 1271 protocol: pim-sm, flag: wc uptime: 00:03:45 upstream interface: pos5/0 upstream neighbor: 1003::2 rpf prime neighbor: 1003::2 downstream interface(s) information: total number of downstreams: 1 1: ethernet1/0 protocol: mld, uptime: 00:02:15, expires: 00:03:06 (40...
Page 1272
1272 c hapter 74: ip v 6 pim c onfiguration ipv6 pim-ssm configuration example network requirements ■ receivers receive vod information through multicast. The receiver groups of different organizations form stub networks, and one or more receiver hosts exist in each stub network. The entire ipv6 pim...
Page 1273
Ipv6 pim configuration examples 1273 network diagram figure 367 network diagram for ipv6 pim-ssm configuration (on routers) configuration procedure 1 configure the interface ipv6 addresses and ipv6 unicast routing protocol for each router configure the ip address and prefix length for each interface...
Page 1274
1274 c hapter 74: ip v 6 pim c onfiguration # enable ipv6 multicast routing on router a, and enable ipv6 pim-sm on each interface, and enable mldv2 on ethernet 1/0, which connects router a to n1. System-view [routera] multicast ipv6 routing-enable [routera] interface ethernet 1/0 [routera-ethernet1/...
Page 1275
Troubleshooting ipv6 pim configuration 1275 routing-table command to view the pim routing table information on each router. For example: # view the ipv6 pim multicast routing table information on router a. [routera] display pim ipv6 routing-table total 0 (*, g) entry; 1 (s, g) entry (4001::100, ff3e...
Page 1276
1276 c hapter 74: ip v 6 pim c onfiguration ■ ipv6 pim requires that the same ipv6 pim mode, namely dm or sm, must run on the entire network. Otherwise, the establishment of a multicast distribution tree will surely fail, resulting in abnormal multicast forwarding. Solution 1 check ipv6 unicast rout...
Page 1277
Troubleshooting ipv6 pim configuration 1277 no unicast route between bsr and c-rps in ipv6 pim-sm domain symptom c-rps cannot unicast advertise messages to the bsr. The bsr does not advertise bootstrap messages containing c-rp information and has no unicast route to any c-rp. An rpt cannot be establ...
Page 1278
1278 c hapter 74: ip v 6 pim c onfiguration.
Page 1279: Ulticast
75 m ulticast vpn c onfiguration when configuring multicast vpn, go to the following sections for the information you are interested in: ■ “multicast vpn overview” on page 1279 ■ “how md-vpn works” on page 1285 ■ “md-vpn configuration task list” on page 1292 ■ “displaying and maintaining md-vpn” on ...
Page 1280
1280 c hapter 75: m ulticast vpn c onfiguration figure 368 typical application of mpls l3vpns as shown in figure 368 , vpn a comprises site 1, site 2 and site 3, while vpn b comprises site 4, site 5 and site 6. A vpn involves the following three types of devices: ■ provider (p) device: device in the...
Page 1281
Multicast vpn overview 1281 introduction to multicast vpn figure 369 shows an example of multicast over an mpls vpns network, which carries three independent multicast services - vpn instance a, vpn instance b, and the public instance. A pe multicast device at the edge of the public network supports...
Page 1282
1282 c hapter 75: m ulticast vpn c onfiguration introduction to md-vpn n for details about the concepts of protocol independent multicast (pim), bootstrap router (bsr), candidate-bsr (c-bsr), rendezvous point (rp), candidate rp (c-rp), shortest path tree (spt) and rendezvous point tree (rpt), refer ...
Page 1283
Multicast vpn overview 1283 introduction to md-vpn main points in the implementation of md-vpn are as follows: 1 the public network of the service provider supports multicast. The pe devices need to support the public instance and multiple vpn instances, each instance running pim independently. Priv...
Page 1284
1284 c hapter 75: m ulticast vpn c onfiguration mti can be thought of an entrance/exit of the pool. The local pe device puts the private data into the transmission pool (the md) through the entrance (mti), and the transmission pool automatically duplicates the private data and transmits the data to ...
Page 1285
How md-vpn works 1285 n a vpn corresponds to a unique md, and an md serves a unique vpn. There is a one-to-one relationship between vpn, md, mti, share-group, and switch-group-pool. Pim neighboring relationships md-vpn figure 371 pim neighboring relationships md-vpn pim neighboring relationships are...
Page 1286
1286 c hapter 75: m ulticast vpn c onfiguration the mti on the ingress pe device. All that is known to the vpn instance is that the vpn data is sent out the mti and then the remote site can receive the data through the mti. Actually, when the remote site receives the multicast data, the data transmi...
Page 1287
How md-vpn works 1287 share-mdt establishment in a pim-dm network figure 373 share-mdt establishment in a pim-dm network as shown in figure 373 , pim-dm is running in the public network. The share-mdt establishment is as follows: pe 1 initiates a flood-prune process in the entire public network, wit...
Page 1288
1288 c hapter 75: m ulticast vpn c onfiguration c caution: all interfaces that belong to the same vpn, including those interfaces with vpn instance bindings and the mti on pe devices, must run the same pim mode. 1 if pim-dm is running in the vpns network, a flood-prune process needs to be initiated ...
Page 1289
How md-vpn works 1289 share-group address as the multicast group address, to convert it into a normal, public network multicast data packet (11.1.2.1, 239.1.1.1), and then passes the packet to the public instance on pe 2 to have it forwarded to the public network. 4 the multicast data packet (11.1.2...
Page 1290
1290 c hapter 75: m ulticast vpn c onfiguration figure 375 delivery of multicast data packets the private network multicast traffic is delivered across the public network as follows. 1 source sends customer multicast data (192.1.1.1, 225.1.1.1) to ce 1. 2 ce 1 forwards the private network multicast ...
Page 1291
How md-vpn works 1291 get flooded in the public network, causing bandwidth waste and extra burden on the pe devices. To optimize multicast transmission, the md solution establishes a dedicated switch-mdt between the pe devices with private network multicast receivers and multicast sources for any la...
Page 1292
1292 c hapter 75: m ulticast vpn c onfiguration ■ the traffic rate of the private network multicast data has fallen below the switching threshold and stayed lower than the threshold for a certain length of time. ■ the associated switch-group-pool is changed and the switch-group address for encapsula...
Page 1293
Configuring md-vpn 1293 configuring a share-group and an mti binding by running multiple instances on each pe device, you enable the pe device to work for multiple vpns. You need to configure the same share-group address for the same vpn instance on different pe devices. Once a share-group and an mt...
Page 1294
1294 c hapter 75: m ulticast vpn c onfiguration enabling switch-group reuse log for a given vpn, if the number of private network multicast streams to be switched to switch-mdts exceeds the number of addresses in the switch-group-pool, the vpn instance on the source-side pe device can reuse the addr...
Page 1295
Md-vpn configuration example 1295 md-vpn configuration example network requirements the network requirements for md-vpn configuration are listed in the table below: item network requirements multicast sources and receivers ■ in vpn a, s 1 is the multicast source, and r 1, r 2 and r 3 are receivers ■...
Page 1296
1296 c hapter 75: m ulticast vpn c onfiguration network diagram figure 376 network diagram for md-vpn configuration device interface ip address device interface ip address s 1 - 10.110.7.2/24 pe 3 eth0/1 192.168.8.1/24 s 2 - 10.110.8.2/24 eth0/2 10.110.5.1/24 r 1 - 10.110.1.2/24 eth0/3 10.110.6.1/24...
Page 1297
Md-vpn configuration example 1297 configuration procedure 1 configure pe 1 # configure a router id, enable ip multicast routing in the public instance, configure an mpls label switching router (lsr) id, and enable the label distribution protocol (ldp) capability. System-view [pe1] router id 1.1.1.1 ...
Page 1298
1298 c hapter 75: m ulticast vpn c onfiguration [pe1] interface ethernet 0/3 [pe1-ethernet0/3] ip binding vpn-instance a [pe1-ethernet0/3] ip address 10.110.2.1 24 [pe1-ethernet0/3] pim sm [pe1-ethernet0/3] quit # configure an ip address for loopback 1. [pe1] interface loopback 1 [pe1-loopback1] ip ...
Page 1299
Md-vpn configuration example 1299 [pe2] multicast routing-enable [pe2] mpls lsr-id 1.1.1.2 [pe2] mpls [pe2-mpls] quit [pe2] mpls ldp [pe2-mpls-ldp] quit # create vpn instance b, configure an rd for it, and create an ingress route and an egress route for it. [pe2] ip vpn-instance b [pe2-vpn-instance-...
Page 1300
1300 c hapter 75: m ulticast vpn c onfiguration [pe2] interface ethernet 0/2 [pe2-ethernet0/2] ip binding vpn-instance b [pe2-ethernet0/2] ip address 10.110.3.1 24 [pe2-ethernet0/2] pim sm [pe2-ethernet0/2] quit # bind ethernet 0/3 to vpn instance a, configure an ip address and enable pim-sm on the ...
Page 1301
Md-vpn configuration example 1301 [pe2-ospf-1-area-0.0.0.0] network 1.1.1.2 0.0.0.0 [pe2-ospf-1-area-0.0.0.0] network 192.168.0.0 0.0.255.255 [pe2-ospf-1-area-0.0.0.0] quit [pe2-ospf-1] quit # configure rip. [pe2] rip 2 vpn-instance a [pe2-rip-2] network 10.0.0.0 [pe2-rip-2] import-route bgp [pe2-ri...
Page 1302
1302 c hapter 75: m ulticast vpn c onfiguration # enable ip multicast routing in vpn instance b, configure a share-group address, associate an mti with the vpn instance, and define the address range of the switch-group-pool. [pe3-vpn-instance-b] multicast routing-enable [pe3-vpn-instance-b] multicas...
Page 1303
Md-vpn configuration example 1303 [pe3] interface loopback 2 [pe3-loopback2] ip binding vpn-instance b [pe3-loopback2] ip address 33.33.33.33 32 [pe3-loopback2] pim sm [pe3-loopback2] quit # configure loopback 2 as a c-bsr and c-rp for vpn b. [pe3] pim vpn-instance b [pe3-pim-b] c-bsr loopback 2 [pe...
Page 1304
1304 c hapter 75: m ulticast vpn c onfiguration # enable ip multicast routing, configure an mpls lsr id, and enable the ldp capability in the public instance. System-view [p] multicast routing-enable [p] mpls lsr-id 2.2.2.2 [p] mpls [p-mpls] quit [p] mpls ldp [p-mpls-ldp] quit # configure an ip addr...
Page 1305
Md-vpn configuration example 1305 [p] ospf 1 [p-ospf-1] area 0.0.0.0 [p-ospf-1-area-0.0.0.0] network 2.2.2.2 0.0.0.0 [p-ospf-1-area-0.0.0.0] network 192.168.0.0 0.0.255.255 5 configure ce a1 # enable ip multicast routing. System-view [cea1] multicast routing-enable # configure an ip address and enab...
Page 1306
1306 c hapter 75: m ulticast vpn c onfiguration # enable ip multicast routing. System-view [cea2] multicast routing-enable # configure an ip address, and enable igmp and pim-sm on ethernet 0/1. [cea2] interface ethernet 0/1 [cea2-ethernet0/1] ip address 10.110.9.1 24 [cea2-ethernet0/1] igmp enable [...
Page 1307
Md-vpn configuration example 1307 [cea3-ethernet0/1] igmp enable [cea3-ethernet0/1] pim sm [cea3-ethernet0/1] quit # configure an ip address and enable pim-sm on ethernet 0/2. [cea3] interface ethernet 0/2 [cea3-ethernet0/2] ip address 10.110.5.2 24 [cea3-ethernet0/2] pim sm [cea3-ethernet0/2] quit ...
Page 1308
1308 c hapter 75: m ulticast vpn c onfiguration display multicast-domain vpn-instance a share-group md local share-group information for vpn-instance: a share-group: 239.1.1.1 mtunnel address: 1.1.1.1 # view the share-group information of vpn instance a on pe 2. Display multicast-domain vpn-instance...
Page 1309
Troubleshooting md-vpn configuration 1309 ■ bgp and unicast route configurations are prerequisites for the mti interface of a vpn instance on a pe device to obtain an ip address automatically. Without an ip address correctly obtained by the mti, pim adjacencies cannot be established between the same...
Page 1310
1310 c hapter 75: m ulticast vpn c onfiguration.
Page 1311: Mpls B
76 mpls b asics c onfiguration when performing mpls basics configuration, go to these sections for information you are interested in: ■ “mpls overview” on page 1311 ■ “mpls configuration basics” on page 1318 ■ “ldp overview” on page 1321 ■ “configuring mpls basic capability” on page 1325 ■ “configur...
Page 1312
1312 c hapter 76: mpls b asics c onfiguration n for details about mpls architecture, refer to rfc 3031 “multiprotocol label switching architecture”. Basic concepts of mpls fec as a forwarding technology based on classification, mpls groups packets to be forwarded in the same manner into a class call...
Page 1313
Mpls overview 1313 figure 378 place of a label in a packet n currently, the device does not support the cell mode. Lsr label switching router (lsr) is a fundamental component on an mpls network. All lsrs support mpls. Lsp label switched path (lsp) means the path along which a fec travels through an ...
Page 1314
1314 c hapter 76: mpls b asics c onfiguration ■ the existing protocols that are extended to support label distribution, such as border gateway protocol (bgp) and resource reservation protocol (rsvp). In addition, you can configure static lsps. N ■ for information about cr-ldp and rsvp, refer to “mpl...
Page 1315
Mpls overview 1315 figure 380 structure of the mpls network the following describes how mpls operates: 1 first, the ldp protocol and the traditional routing protocol (such as ospf and isis) work together on each lsr to establish the routing table and the label information base (lib) for intended fec...
Page 1316
1316 c hapter 76: mpls b asics c onfiguration structure of an lsr figure 381 structure of an lsr as shown in figure 381 , an lsr consists of two components: ■ control plane: implements label distribution and routing, establishes the lfib, and builds and tears lsps. ■ forwarding plane: forwards packe...
Page 1317
Mpls overview 1317 nonetheless, mpls can easily implement the seamless integration between ip networks and layer 2 networks of atm, frame relay, and the like, and offer better solutions to quality of service (qos), traffic engineering (te), and virtual private network (vpn) applications thanks to th...
Page 1318
1318 c hapter 76: mpls b asics c onfiguration the diff-serv model maps a service to a certain service class at the network edge according to the qos requirement of the service. The ds field (derived from the tos field) in the ip packet identifies the service uniquely. Then, each node in the backbone...
Page 1319
Mpls configuration basics 1319 ■ conservative: in this mode, an lsr keeps only label to fec bindings that are from its next hops for the fecs. In liberal mode, an lsr can adapt to route changes quickly; while in conservative mode, there are less label to fec bindings for an lsr to advertise and keep...
Page 1320
1320 c hapter 76: mpls b asics c onfiguration ■ with ip ttl propagation enabled at ingress, whenever a packet passes a hop along the lsp, its ip ttl gets decremented by 1. Therefore, the result of tracert will reflect the path along which the packet has traveled. ■ with ip ttl propagation disabled a...
Page 1321
Ldp overview 1321 n when an mpls echo request reaches the egress, the destination address in the ip header is set to an address on 127.0.0.0/8 (loopback address of the lsr) and the ttl is set to 1 so as to prevent further forwarding of the request. Ldp overview ldp basic concepts an ldp dictates the...
Page 1322
1322 c hapter 76: mpls b asics c onfiguration a label space id of 1 means per interface, a label space id of 0 means per platform. N currently, only per platform label space is supported. Ldp label distribution figure 383 illustrates how ldp distribute labels. Figure 383 label distribution in figure...
Page 1323
Ldp overview 1323 du mode in du mode, a downstream lsr advertises label binding information to its upstream lsr unsolicitedly after the ldp session is established, while the upstream lsr keeps the label binding information and processes the information based on its routing table information. Fundame...
Page 1324
1324 c hapter 76: mpls b asics c onfiguration after establishing sessions between them, lsrs send hello messages and keepalive messages to maintain those sessions. Lsp establishment and maintenance establishing an lsp is to bind fecs with labels and notify adjacent lsrs of the bindings. This is impl...
Page 1325
Configuring mpls basic capability 1325 maximum hop count a label request message or label mapping message can include information about its hop count, which increments by 1 for each hop. When this value exceeds the specified limit, ldp considers that a loop is present and the attempt to establish an...
Page 1326
1326 c hapter 76: mpls b asics c onfiguration n currently, these types of interfaces support mpls capability: serial interface, async interface, layer 3 ethernet interface (ethernet interface, ge interface, and xge interface), atm interface, pos interface, layer 3 virtual ethernet interface (that is...
Page 1327
Configuring a static lsp 1327 packet must be popped out on the node, and that the next node will perform ip forwarding. ■ a label value of 3 represents an implicit null label and never appears in the label stack. When an lsr finds that it is assigned an implicit null label, it directly performs a po...
Page 1328
1328 c hapter 76: mpls b asics c onfiguration n ■ support for the outgoing-interface interface-type interface-number keyword and argument combination varies by device. ■ if you specify the next hop when configuring a static lsp, and the address of the next hop is in the routing table, you must speci...
Page 1329
Configuring mpls ldp 1329 n ■ currently, these types of interfaces support ldp capability: serial interface, async interface, layer 3 ethernet interface (ethernet interface, ge interface, and xge interface), atm interface, pos interface, layer 3 virtual ethernet interface (that is, virtual-ethernet ...
Page 1330
1330 c hapter 76: mpls b asics c onfiguration n in the current implementation, ldp itself does no send any label information through remote sessions, and remote sessions are used only to transfer messages for l2vpns. For applications of remote sessions, refer to “configuring martini mpls l2vpn” on p...
Page 1331
Configuring mpls ldp 1331 configuring label advertisement, distribution and retention modes follow these steps to configure ldp label advertisement, distribution, and retention modes: configuring ldp loop detection follow these steps to configure ldp loop detection: n changing of the loop detection ...
Page 1332
1332 c hapter 76: mpls b asics c onfiguration follow these steps to configure ldp md5 authentication: enabling mtu signaling for correct path mtu detection, an ip router needs to know the mtu of each connected link. Ldp can automatically calculate the minimum mtu of all interfaces on an lsp. At ingr...
Page 1333
Configuring ldp gr 1333 c caution: ■ for ldp-enabled interfaces, configurations in mpls ldp vpn instance view affect only interfaces bound to vpn instances, while configurations in mpls ldp view do not affect any interfaces bound to vpn instances. When configuring the transport address of an ldp ins...
Page 1334
1334 c hapter 76: mpls b asics c onfiguration restarting mpls ldp after configuring gr parameters, you need to restart mpls ldp to validate the configurations. Follow these steps to reset mpls ldp: gracefully restarting mpls ldp to test mpls ldp gr without main/backup failover, you can gracefully re...
Page 1335
Configuring mpls fast forwarding 1335 in mpls, an ip router generally maintains public network routes only, and mpls packets with one-level labels carry public network payload. Therefore, you can configure this function. In mpls vpn, for asbrs and spes in hovpn applications (including spes in applic...
Page 1336
1336 c hapter 76: mpls b asics c onfiguration setting the interval for reporting statistics to view lsp statistics, you must set the interval for reporting statistics at first. Follow these steps to set the interval for reporting statistics: inspecting an mpls lsp enabling mpls trap follow these ste...
Page 1338
1338 c hapter 76: mpls b asics c onfiguration clearing mpls statistics mpls configuration example ldp session configuration example network requirements ■ router a, router b, and router c support mpls and use ospf as the igp for the mpls backbone. ■ a local ldp session is required between router a a...
Page 1339
Mpls configuration example 1339 network diagram figure 384 network diagram for ldp session configuration configuration procedure 1 configure the ip addresses of the interfaces configure the ip addresses and masks of the interfaces including the loopback interfaces as required in figure 384 . The fol...
Page 1340
1340 c hapter 76: mpls b asics c onfiguration [routerc-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255 [routerc-ospf-1-area-0.0.0.0] return after completing the above configurations, you will see that every router has learned the route to the lsr id of its peer when you execute the display ip routin...
Page 1341
Mpls configuration example 1341 [routerb] interface serial 1/0 [routerb-serial1/0] mpls [routerb-serial1/0] mpls ldp [routerb-serial1/0] quit [routerb] interface serial 1/1 [routerb-serial1/1] mpls [routerb-serial1/1] mpls ldp [routerb-serial1/1] quit # configure router c. [routerc] mpls lsr-id 3.3....
Page 1342
1342 c hapter 76: mpls b asics c onfiguration after completing the above configurations, you will find by issuing the following commands on router a that the remote ldp session with router c is already established: [routera] display mpls ldp session ldp session(s) in public network total number of s...
Page 1343
Troubleshooting mpls 1343 [routerc] mpls [routerc-mpls] lsp-trigger all [routerc-mpls] quit after completing the above configurations, you will see the lsps established when you execute the display mpls ldp lsp command. The following takes router a as an example: [routera] display mpls ldp lsp ldp l...
Page 1344
1344 c hapter 76: mpls b asics c onfiguration.
Page 1345: Mpls Te C
77 mpls te c onfiguration when configuring multiprotocol path label switching traffic engineering (mpls te), go to these sections for information you are interested in: ■ “mpls te overview” on page 1345 ■ “mpls te configuration task list” on page 1358 ■ “displaying and maintaining mpls te” on page 1...
Page 1346
1346 c hapter 77: mpls te c onfiguration ■ traffic oriented. These are performance objectives that enhance quality of service (qos) of traffic streams, such as minimization of packet loss, minimization of delay, maximization of throughput and enforcement of service level agreements (sla). ■ resource...
Page 1347
Mpls te overview 1347 basic concepts of mpls te lsp tunnel on an lsp, the nodes make forwarding decision for labeled packets based on label. The traffic thus is transparent to the transits nodes on the lsp. In this sense, an lsp can be regarded as a tunnel. Mpls te tunnel reroute and transmission ov...
Page 1348
1348 c hapter 77: mpls te c onfiguration they are different in that cr-ldp establishes lsps using tcp while rsvp-te using raw ip. Rsvp is a well-established technology in terms of its architecture, protocol procedures and support to services; while cr-ldp is an emerging technology with better scalab...
Page 1349
Mpls te overview 1349 for a new path to preempt an existing path, the setup priority of the new path must be greater than the holding priority of the existing path. To initiate a preemption, the resv message of rsvp-te is sent. To avoid flapping caused by improper preemptions between cr-lsps, the se...
Page 1350
1350 c hapter 77: mpls te c onfiguration ■ “rsvp refresh mechanism” on page 1352 ■ “psb, rsb and bsb timeouts” on page 1353 ■ “rsvp-te gr” on page 1353 overview currently, two qos models are available: integrated service (intserv) and differentiated service (diffserv). Resource reservation protocol ...
Page 1351
Mpls te overview 1351 make-before-break make-before-break is a mechanism to change mpls te tunnel attributes with minimum data loss and without extra bandwidth. Figure 385 diagram for make-before-break figure 385 presents a scenario where a path router a → router b → router c → router d is establish...
Page 1352
1352 c hapter 77: mpls te c onfiguration ■ hell messages: sent between any two directly connected rsvp neighbors to set up and maintain the neighbor relationship that has local significance on the link. The te extension to rsvp adds new objects to the path message and the resv message. These objects...
Page 1353
Mpls te overview 1353 refreshing mechanism was extended in rfc 2961 rsvp refresh overhead reduction extensions as follows to address the problems: 1 message_id extension rsvp itself uses raw ip to send messages. The message_id extension mechanism defined in rfc 2961 adds objects that can be carried ...
Page 1354
1354 c hapter 77: mpls te c onfiguration rsvp-te advertises its gr capability and relevant time parameters to its neighbors by extended rsvp hello packets. If a device and all its neighbors have the rsvp gr capability and have exchanged gr parameters, each of them can function as the gr helper of an...
Page 1355
Mpls te overview 1355 ospf and is-is support both approaches where te tunnels are considered point-to-point links and te tunnel interfaces can be set as outgoing interfaces. Igp shortcut, also known as autoroute announce, considers a te tunnel as a logical interface directly connected to the destina...
Page 1356
1356 c hapter 77: mpls te c onfiguration automatic bandwidth adjustment of mpls te fulfills this function. It can dynamically tune te tunnel bandwidth based on measured service traffic. Cr-lsp backup cr-lsp backup provides end-to-end path protection for the entire lsp without time limitation. This i...
Page 1357
Mpls te overview 1357 ■ link protection, where the plr and the mp are connected through a direct link and the primary lsp traverses this link. When the link fails, traffic is switched to the bypass lsp. As shown in figure 388 , the primary lsp is router a →router b → router c → router d, and the byp...
Page 1358
1358 c hapter 77: mpls te c onfiguration essentially, what ds-te does is to map traffic trunks with lsps, making each traffic trunk traverse the constraints-compliant path. Ds-te involves two concepts: ■ class type (ct): the set of traffic trunks crossing a link that is governed by a specific set of...
Page 1359
Configuring mpls te basic capabilities 1359 configuring mpls te basic capabilities mpls te basic capabilities are essential to mpls te feature configurations. After configuring the basic capabilities, you need to make other configurations in order to use mpls te depending on the actual requirements....
Page 1360
1360 c hapter 77: mpls te c onfiguration creating mpls te tunnel over static cr-lsp creating mpls te tunnels over static cr-lsps does not involve configuration of tunnel constraints or the issue of igp te extension or cspf. What you need to do is to create a static cr-lsp and a te tunnel using stati...
Page 1361
Configuring mpls te tunnel with dynamic signaling protocol 1361 n ■ the tunnel-name argument specifies the name of the mpls te tunnel carried over the static cr-lsp. ■ the tunnel-name argument in the static-cr-lsp ingress command is case sensitive. Suppose you create a tunnel interface with the inte...
Page 1362
1362 c hapter 77: mpls te c onfiguration ■ establish the path by using the signaling protocol rsvp-te or cr-ldp. N to form a tedb, you must configure the igp te extension for the nodes on the network to send te lsas. If the igp te extension is not configured, the cr-lsp is created based on igp routi...
Page 1363
Configuring mpls te tunnel with dynamic signaling protocol 1363 the ospf te extension uses opaque type 10 lsas to carry te attributes of links. Before configuring ospf te, you need to enable the opaque capability of ospf. In addition, for te lsas to be generated, at least one neighbor must be in ful...
Page 1364
1364 c hapter 77: mpls te c onfiguration n ■ for more information about is-is, refer to “is-is configuration” on page 877 . ■ is-is te does not support advertisement of secondary ip addresses. With is-is te enabled on an interface configured with multiple ip addresses, is-is te advertises only the p...
Page 1365
Configuring mpls te tunnel with dynamic signaling protocol 1365 configuring mpls te tunnel constraints follow these steps to configure mpls te tunnel constraints: establishing an mpls te tunnel with cr-ldp follow these steps to establish an mpls te tunnel with cr-ldp: add a node to the explicit path...
Page 1366
1366 c hapter 77: mpls te c onfiguration establishing an mpls te tunnel with rsvp-te follow these steps to establish an mpls te tunnel with rsvp-te: c caution: to use rsvp-te as the signaling protocol for setting up the mpls te tunnel, you must enable both mpls te and rsvp-te on the interface for th...
Page 1367
Configuring rsvp-te advanced features 1367 ■ “configuring the rsvp refreshing mechanism” on page 1368 ■ “configuring the rsvp hello extension” on page 1368 ■ “configuring rsvp-te resource reservation confirmation” on page 1369 ■ “configuring rsvp authentication” on page 1369 ■ “configuring rsvp-te g...
Page 1368
1368 c hapter 77: mpls te c onfiguration configuring the rsvp refreshing mechanism to enhance reliability of rsvp message transmission, the message_id extension mechanism is used to acknowledge rsvp messages. The message_id extension mechanism is also referred to as the reliability mechanism through...
Page 1369
Configuring rsvp-te advanced features 1369 n rsvp hello extension detects the reachability of rsvp neighboring nodes. It is defined in rfc 3209. Configuring rsvp-te resource reservation confirmation follow these steps to configure rsvp-te resource reservation confirmation: n ■ reservation confirmati...
Page 1370
1370 c hapter 77: mpls te c onfiguration tuning cr-lsp setup a cr-lsp is established through the signaling protocol based on the path calculated by cspf using tedb and constraints. Mpls te can affect cspf calculation in many ways to determine the path that a cr-lsp can traverse. Configuration prereq...
Page 1371
Tuning cr-lsp setup 1371 n for a tunnel, the tie breaker configured in mpls te tunnel interface view is preferred to the one configured in mpls view. If no tie breaker is configured in mpls te tunnel interface view, the one configured in mpls view applies. Configuring route pinning route pinning can...
Page 1372
1372 c hapter 77: mpls te c onfiguration configuring cr-lsp reoptimization dynamic cr-lsp optimization involves periodic calculation of paths that traffic trunks should traverse. If a better route is found for an existing cr-lsp, a new cr-lsp will be established to replace the old one, and services ...
Page 1373
Tuning mpls te tunnel setup 1373 ■ “configuring route and label recording” on page 1373 ■ “configuring tunnel setup retry” on page 1373 ■ “assigning priorities to a tunnel” on page 1374 configuring loop detection follow these steps to configure loop detection: configuring route and label recording f...
Page 1374
1374 c hapter 77: mpls te c onfiguration assigning priorities to a tunnel two priorities, setup priority and holding priority, are assigned to paths for mpls te to make preemption decision. For a new path to preempt an existing path, the setup priority of the new path must be greater than the holdin...
Page 1375
Configuring traffic forwarding 1375 n the interface-type argument in the ip route-static command must be tunnel. In addition, the preference value must be set. For more information about static routing, refer to “static routing and dynamic routing” on page 817 . Forwarding traffic along mpls te tunn...
Page 1376
1376 c hapter 77: mpls te c onfiguration forwarding traffic along mpls te tunnels through automatic route advertisement two approaches, igp shortcut and forwarding adjacency, are available to automatic route advertisement to advertise mpls te tunnel interface routes to igps, allowing traffic to be r...
Page 1377
Configuring traffic forwarding tuning parameters 1377 configuring traffic forwarding tuning parameters in mpls te, you may configure traffic forwarding tuning parameters such as the failed link timer and flooding thresholds to change paths that ip or mpls traffic flows traverse or to define type of ...
Page 1378
1378 c hapter 77: mpls te c onfiguration configuring flooding thresholds after bandwidths of links regulated by mpls te change, cspf may need to recalculate paths. This tends to be resource consuming as recalculation involves igp flooding. To reduce recalculations and flood only significant changes,...
Page 1379
Configuring automatic bandwidth adjustment 1379 n ■ the metric type configured in mpls te tunnel interface view takes priority over the one configured in mpls view. ■ if you do not configure the mpls te path metric-type command in mpls te tunnel interface view, the configuration in mpls view takes e...
Page 1380
1380 c hapter 77: mpls te c onfiguration the sampling interval configured in mpls view applies to all mpls te tunnels. The output rates of all mpls te tunnels are recorded every sampling interval to calculate the actual average bandwidth of an mpls te tunnel in one sampling interval. Once the mpls t...
Page 1381
Configuring frr 1381 n cr-lsp backup should be configured at the ingress node of a tunnel. The system routes the primary lsp and backup lsp automatically. You do not need to configure them. Configuring frr n the frr feature is not supported when the signaling protocol is cr-ldp. As mentioned earlier...
Page 1382
1382 c hapter 77: mpls te c onfiguration configuring a bypass tunnel on its plr after a tunnel is specified to protect an interface, its corresponding lsp becomes a bypass lsp. Setting up a bypass lsp must be manually performed on its headend, also called point of local repair (plr), which must be a...
Page 1383
Configuring frr 1383 c caution: bypass tunnels do not protect bandwidth by default. This can defeat your attempts to binding a primary lsp to a bypass tunnel. Therefore, when configuring a bypass tunnel, you must configure the bandwidth that it is intended to protect with the mpls te backup bandwidt...
Page 1384
1384 c hapter 77: mpls te c onfiguration displaying and maintaining mpls te displaying and maintaining mpls te to do... Use the command... Remarks display information about explicit paths display explicit-path [ pathname ] available in any view display information about static cr-lsps display mpls s...
Page 1385
Displaying and maintaining mpls te 1385 resetting automatic bandwidth adjustment n support for this feature varies by device. When resetting the automatic bandwidth adjustment function, the system clears information about output rate sampling and the remaining time for next bandwidth optimization. D...
Page 1386
1386 c hapter 77: mpls te c onfiguration mpls te configuration example mpls te using static cr-lsp configuration example network requirements ■ router a, router b, and router c run is-is. ■ establish a te tunnel using a static cr-lsp between router a and router c. Network diagram figure 390 set up m...
Page 1387
Mpls te configuration example 1387 [routerb] interface ethernet 1/0 [routerb-ethernet1/0] isis enable 1 [routerb-ethernet1/0] quit [routerb] interface ethernet1/1 [routerb-ethernet1/1] isis enable 1 [routerb-ethernet1/1] quit [routerb] interface loopback 0 [routerb-loopback0] isis enable 1 [routerb-...
Page 1388
1388 c hapter 77: mpls te c onfiguration [routerb-mpls] quit [routerb] interface ethernet 1/0 [routerb-ethernet1/0] mpls [routerb-ethernet1/0] mpls te [routerb-ethernet1/0] quit [routerb] interface ethernet 1/1 [routerb-ethernet1/1] mpls [routerb-ethernet1/1] mpls te [routerb-ethernet1/1] quit # con...
Page 1389
Mpls te configuration example 1389 description: tunnel0 interface the maximum transmit unit is 64000 internet address is 6.1.1.1/24 primary encapsulation is tunnel, aggregation id not set tunnel source unknown, destination 3.3.3.3 tunnel protocol/transport cr_lsp last 300 seconds input: 0 bytes/sec,...
Page 1390
1390 c hapter 77: mpls te c onfiguration n on an mpls te tunnel configured using a static cr-lsp, traffic is forwarded directly based on label at the transit nodes and egress node. Therefore, it is normal that the fec field in the sample output is empty on route b and router c. 7 create a static rou...
Page 1391
Mpls te configuration example 1391 [routera-isis-1] network-entity 00.0005.0000.0000.0001.00 [routera-isis-1] quit [routera] interface ethernet 1/0 [routera-ethernet1/0] isis enable 1 [routera-ethernet1/0] isis circuit-level level-2 [routera-ethernet1/0] quit [routera] interface loopback 0 [routera-...
Page 1392
1392 c hapter 77: mpls te c onfiguration [routerd-ethernet1/0] quit [routerd] interface loopback 0 [routerd-loopback0] isis enable 1 [routerd-loopback0] isis circuit-level level-2 [routerd-loopback0] quit perform the display ip routing-table command on each router. You can see that all nodes learnt ...
Page 1393
Mpls te configuration example 1393 [routerb-pos5/0] mpls rsvp-te [routerb-pos5/0] quit # configure router c. [routerc] mpls lsr-id 3.3.3.9 [routerc] mpls [routerc-mpls] mpls te [routerc-mpls] mpls rsvp-te [routerc-mpls] mpls te cspf [routerc-mpls] quit [routerc] interface ethernet 1/0 [routerc-ether...
Page 1394
1394 c hapter 77: mpls te c onfiguration # configure router d. [routerd] isis 1 [routerd-isis-1] cost-style wide [routerd-isis-1] traffic-eng level-2 [routerd-isis-1] quit 5 configure mpls te attributes of links # configure maximum link bandwidth and maximum reservable bandwidth on router a. [router...
Page 1395
Mpls te configuration example 1395 [routera-tunnel1] mpls te signal-protocol rsvp-te [routera-tunnel1] mpls te bandwidth 2000 [routera-tunnel1] mpls te commit [routera-tunnel1] quit 7 verify the configuration perform the display interface tunnel command on router a. You can find that the tunnel inte...
Page 1396
1396 c hapter 77: mpls te c onfiguration perform the display mpls te cspf tedb all command on router a to view information about links in tedb. [routera] display mpls te cspf tedb all maximum node supported: 128 maximum link supported: 256 current total node number: 4 current total link number: 6 id...
Page 1397
Mpls te configuration example 1397 [routera-mpls] mpls rsvp-te [routera-mpls] mpls rsvp-te hello [routera-mpls] interface ethernet 1/0 [routera-ethernet1/0] mpls [routera-ethernet1/0] mpls te [routera-ethernet1/0] mpls rsvp-te [routera-ethernet1/0] mpls rsvp-te hello [routera-ethernet1/0] quit # con...
Page 1398
1398 c hapter 77: mpls te c onfiguration system-view [routerb] mpls [routerb-mpls] mpls rsvp-te graceful-restart # configure router b. System-view [routerc] mpls [routerc-mpls] mpls rsvp-te graceful-restart # configure router c. System-view [routerc] mpls [routerc-mpls] mpls rsvp-te graceful-restart...
Page 1399
Mpls te configuration example 1399 network diagram figure 393 set up mpls te tunnels using cr-ldp configuration procedure 1 assign ip addresses and masks to interfaces (see figure 393 ) omitted 2 enable ospf to advertise host routes with lsr ids as destinations omitted. After configuration, you can ...
Page 1400
1400 c hapter 77: mpls te c onfiguration [routerb-mpls] mpls rsvp-te [routerb-mpls] mpls te cspf [routerb-mpls] quit [routerb] interface ethernet 1/0 [routerb-ethernet1/0] mpls [routerb-ethernet1/0] mpls te [routerb-ethernet1/0] mpls rsvp-te [routerb-ethernet1/0] quit [routerb] interface ethernet 1/...
Page 1401
Mpls te configuration example 1401 # configure router b. [routerb] ospf [routerb-ospf-1] opaque-capability enable [routerb-ospf-1] area 0 [routerb-ospf-1-area-0.0.0.0] mpls-te enable [routerb-ospf-1-area-0.0.0.0] quit [routerb-ospf-1] quit # configure router c. [routerc] ospf [routerc-ospf-1] opaque...
Page 1402
1402 c hapter 77: mpls te c onfiguration [routerc-ethernet1/1] mpls te max-reservable-bandwidth 5000 [routerc-ethernet1/1] quit # configure maximum link bandwidth and maximum reservable bandwidth on router d. [routerd] interface ethernet 1/0 [routerd-ethernet1/0] mpls te max-link-bandwidth 10000 [ro...
Page 1403
Mpls te configuration example 1403 [routerd] mpls ldp [routerd-mpls-ldp] quit [routerd] interface ethernet 1/0 [routerd-ethernet1/0] mpls ldp [routerd-ethernet1/0] quit perform the display mpls ldp session command on each router. You can find that an ldp session has been established and its state is...
Page 1404
1404 c hapter 77: mpls te c onfiguration tunnel state desc : cr-lsp is up tunnel attributes : lsp id : 1.1.1.9:2 session id : 10 admin state : up oper state : up ingress lsr id : 1.1.1.9 egress lsr id: 4.4.4.9 signaling prot : cr ldp resv style : - class type : class 0 tunnel bw : 2000 kbps reserved...
Page 1405
Mpls te configuration example 1405 maximum reservable bw : 625000 bytes/sec admin group : 0x0 global pool: unreserved bw [ 0] =625000 bytes/sec unreserved bw [ 1] =625000 bytes/sec unreserved bw [ 2] =625000 bytes/sec unreserved bw [ 3] =625000 bytes/sec unreserved bw [ 4] =625000 bytes/sec unreserv...
Page 1406
1406 c hapter 77: mpls te c onfiguration network diagram figure 394 cr-lsp backup configuration procedure 1 assign ip addresses and masks to interfaces (see figure 394 ) omitted 2 configure the igp protocol # enable is-is to advertise host routes with lsr ids as destinations on each node. (omitted) ...
Page 1407
Mpls te configuration example 1407 [routera] interface pos 5/1 [routera-pos5/1] mpls [routera-pos5/1] mpls te [routera-pos5/1] mpls rsvp-te [routera-pos5/1] quit n follow the same steps to configure router b, router c, and router d. 4 create an mpls te tunnel on router a # configure the mpls te tunn...
Page 1408
1408 c hapter 77: mpls te c onfiguration [routera] display mpls te tunnel path tunnel interface name : tunnel3 lsp id : 1.1.1.9 :6 hop information hop 0 10.1.1.1 hop 1 10.1.1.2 hop 2 2.2.2.9 hop 3 20.1.1.1 hop 4 20.1.1.2 hop 5 3.3.3.9 tunnel interface name : tunnel3 lsp id : 1.1.1.9 :2054 hop inform...
Page 1409
Mpls te configuration example 1409 perform the display ip routing-table command on router a. You can find a static route entry with tunnel3 as the outgoing interface. Frr configuration example network requirements on a primary lsp router a → router b → router c → router d, use frr to protect the lin...
Page 1410
1410 c hapter 77: mpls te c onfiguration perform the display ip routing-table command on each router. You should see that all nodes learnt the host routes of other nodes with lsr ids as destinations. Take router a for example: display ip routing-table routing tables: public destinations : 13 routes ...
Page 1411
Mpls te configuration example 1411 n follow the same steps to configure router c, router d, and router e. 4 create an mpls te tunnel on router a, the headend of the primary lsp # create an explicit path for the primary lsp. [routera] explicit-path pri-path [routera-explicit-path-pri-path] next hop 2...
Page 1412
1412 c hapter 77: mpls te c onfiguration affinity prop/mask : 0x0/0x0 explicit path name : pri-path tie-breaking policy : none metric type : none record route : enabled record label : enabled frr flag : enabled backupbw flag: not supported backupbw type : - backupbw : - route pinning : disabled retr...
Page 1413
Mpls te configuration example 1413 ------------------------------------------------------------------ fec in/out label in/out if vrf name 4.4.4.4/32 null/1024 -/eth1/0 [routerb] display mpls lsp ------------------------------------------------------------------ lsp information: rsvp lsp ------------...
Page 1414
1414 c hapter 77: mpls te c onfiguration lsp information: rsvp lsp ------------------------------------------------------------------- no : 1 ingresslsrid : 1.1.1.1 locallspid : 1 tunnel-interface : tunnel4 fec : 4.4.4.4/32 nexthop : 3.1.1.2 in-label : 1024 out-label : 1024 in-interface : ethernet1/...
Page 1415
Mpls te configuration example 1415 ingress lsr id : 1.1.1.1 egress lsr id: 4.4.4.4 signaling prot : rsvp resv style : se class type : class 0 tunnel bw : 0 kbps reserved bw : 0 kbps setup priority : 7 hold priority: 7 affinity prop/mask : 0/0 explicit path name : pri-path tie-breaking policy : none ...
Page 1416
1416 c hapter 77: mpls te c onfiguration [routerb] display mpls lsp verbose ------------------------------------------------------------------ lsp information: rsvp lsp ------------------------------------------------------------------ no : 1 ingresslsrid : 1.1.1.1 locallspid : 1 tunnel-interface : ...
Page 1417
Mpls te configuration example 1417 7 create a static route for routing mpls te tunnel traffic [routera] ip route-static 4.4.4.4 32 tunnel 4 preference 1 perform the display ip routing-table command on router a. You can find a static route entry with tunnel3 as the outgoing interface. Mpls te in mpls...
Page 1418
1418 c hapter 77: mpls te c onfiguration # configure pe 2. [pe2] system-view [pe2] interface loopback 0 [pe2-loopback0] ip address 3.3.3.3 255.255.255.255 [pe2-loopback0] quit [pe2] interface pos 5/1 [pe2-pos5/1] ip address 10.0.0.2 255.255.255.0 [pe2-pos5/1] quit [pe2] ospf [pe2-ospf-1] area 0 [pe2...
Page 1419
Mpls te configuration example 1419 [pe2] mpls lsr-id 3.3.3.3 [pe2] mpls [pe2-mpls] lsp-trigger all [pe2-mpls] quit [pe2] mpls ldp [pe2-mpls-ldp] quit [pe2] interface pos 1/1 [pe2-pos5/1] mpls [pe2-pos5/1] mpls ldp [pe2-pos5/1] quit after you complete the configuration, pes should be able to set up l...
Page 1420
1420 c hapter 77: mpls te c onfiguration 4 configure an mpls te tunnel # create a te tunnel with pe 1 as the headend and pe 2 as the tail. The signaling protocol is cr-ldp. [pe1] interface tunnel 1 [pe1-tunnel1] ip address 12.1.1.1 255.255.255.0 [pe1-tunnel1] tunnel-protocol mpls te [pe1-tunnel1] de...
Page 1421
Mpls te configuration example 1421 [pe2-ethernet1/0] ip address 192.168.2.1 255.255.255.0 [pe2-ethernet1/0] quit perform the display ip vpn-instance command on the pes to verify the configuration of the vpn instance. Take pe 1 for example: [pe1] display ip vpn-instance instance-name vpn1 vpn-instanc...
Page 1422
1422 c hapter 77: mpls te c onfiguration [ce2] bgp 65002 [ce2-bgp] peer 192.168.2.1 as-number 100 [ce2-bgp] quit # configure pe 2 to establish the egbp peer relationship with ce 2 and the ibgp relationship with pe 1. [pe2] bgp 100 [pe2-bgp] ipv4-family vpn-instance vpn1 [pe2-bgp-vpn1] peer 192.168.2...
Page 1423
Mpls te configuration example 1423 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 35/48/74 ms the sample output shows that ce 1 and ce 2 can reach each other. 7 verify the configuration perform the display mpls lsp verbose command on pe 1. You can find an lsp...
Page 1424
1424 c hapter 77: mpls te c onfiguration out-label : null in-interface : pos5/1 out-interface : ---------- lspindex : 10241 token : 0 lsrtype : egress outgoing token : 0 label operation : pop no : 4 vrfindex : fec : 3.3.3.3/32 nexthop : 10.0.0.2 in-label : null out-label : 3 in-interface : ---------...
Page 1425: Mpls L2Vpn C
78 mpls l2vpn c onfiguration when configuring mpls l2vpn, go to these sections for information you are interested in: ■ “mpls l2vpn overview” on page 1425 ■ “configuring mpls l2vpn” on page 1429 ■ “configuring a pe interface connecting a ce” on page 1430 ■ “configuring ccc mpls l2vpn” on page 1432 ■...
Page 1426
1426 c hapter 78: mpls l2vpn c onfiguration mpls l2vpn mpls l2vpn provides layer 2 vpn services on the mpls network. It allows carriers to establish l2vpns on different data link layer protocols, including atm, fr, vlan, ethernet and ppp. In addition, the mpls network provides traditional ip, mpls l...
Page 1427
Mpls l2vpn overview 1427 ■ provider edge router (pe): a pe resides on a service provider network and connects one or more ces to the network. On an mpls network, all vpn processing occurs on the pes. ■ provider (p) router: a p router is a backbone router on a service provider network. It is not dire...
Page 1428
1428 c hapter 78: mpls l2vpn c onfiguration the kompella draft defines a ce-to-ce mode for implementing mpls l2vpn on the mpls network. It uses extended bgp as the signaling protocol to advertise layer 2 reachability information and vc labels. In addition, mpls l2vpn can also be implemented by confi...
Page 1429
Configuring mpls l2vpn 1429 once ldp establishes an lsp between the two pes and the label exchange and the binding to ce are finished, a vc is set up and ready to transfer layer 2 data. To allow the exchange of vc labels between pes, the martini method extended ldp by adding the forwarding equivalen...
Page 1430
1430 c hapter 78: mpls l2vpn c onfiguration ■ enabling mpls l2vpn follow these steps to complete the above two tasks: configuring a pe interface connecting a ce mpls l2vpn supports these types of interfaces: ethernet interface/subinterface, ge interface/subinterface, 10ge interface, serial interface...
Page 1431
Configuring a pe interface connecting a ce 1431 configuring a pe interface connecting a ce to use hdlc follow these steps to configure a pe interface connecting a ce to use hdlc as the encapsulation protocol: configuring a pe interface connecting a ce to use fr follow these steps to configure a pe i...
Page 1432
1432 c hapter 78: mpls l2vpn c onfiguration n ■ a pe interface connecting a ce must be configured with the same vpi/vci number as that of the connected ce interface. ■ you cannot configure both atm main interface and sub-interface. ■ in mpls l2vpn, each subinterface can be configured with only one v...
Page 1433
Configuring svc mpls l2vpn 1433 configuring the remote ccc connection 1 configure the pes follow these steps to configure a pe: c caution: you do not need to configure two static lsps for each remote ccc connection. Instead, you only need to configure the incoming and outgoing labels, where the inco...
Page 1434
1434 c hapter 78: mpls l2vpn c onfiguration configuration prerequisites before configuring svc mpls l2vpn, complete these tasks: ■ configuring igp on the pes and p devices to guarantee the ip connectivity of the mpls backbone ■ configuring mpls basic capability and mpls ldp for the mpls backbone on ...
Page 1435
Configuring kompella mpls l2vpn 1435 ■ tunneling policy configuration procedure follow these steps to configure martini mpls l2vpn on the pe: n for remote peer configuration information, refer to “mpls basics configuration” on page 1311 . C caution: for a martini connection, there are two main param...
Page 1436
1436 c hapter 78: mpls l2vpn c onfiguration n for information about the configuration of bgp-l2vpn address family, refer to “mpls l3vpn configuration” on page 1459 . Configuring vpn follow these steps to configure vpn: n the command for creating a vpn and entering mpls l2vpn view is also available i...
Page 1437
Configuring kompella mpls l2vpn 1437 creating a ce connection ce id is used for identifying a ce uniquely in a vpn. To facilitate the configuration, it is recommended to encode the ce ids in continuous natural numbers starting from 1. The ce range of a ce indicates the maximum number of ces that the...
Page 1438
1438 c hapter 78: mpls l2vpn c onfiguration displaying and maintaining mpls l2vpn displaying the operation of mpls l2vpn resetting bgp l2vpn connections mpls l2vpn configuration example example for configuring a local ccc connection network requirements ■ the ces are connected with the pe through se...
Page 1439
Mpls l2vpn configuration example 1439 n ■ since a local ccc connection is bidirectional, one is enough. ■ the pe interfaces connecting the ces require no ip addresses. Network diagram figure 399 network diagram for configuring a local ccc connection configuration procedure 1 configure ce 1 system-vi...
Page 1440
1440 c hapter 78: mpls l2vpn c onfiguration [pe] interface serial 1/1 [pe-serial1/1] link-protocol ppp [pe-serial1/1] quit # create a local connection between ce 1 and ce 2. [pe] ccc ce1-ce2 interface serial 1/0 out-interface serial 1/1 3 configure ce 2 system-view [sysname] sysname ce2 [ce2] interf...
Page 1441
Mpls l2vpn configuration example 1441 ■ configure two static lsps on the p device for packets to be transferred in both directions. Network diagram figure 400 network diagram for configuring a remote ccc connection configuration procedure 1 configure ce 1 system-view [sysname] sysname ce1 [ce1] inte...
Page 1442
1442 c hapter 78: mpls l2vpn c onfiguration # configure interface pos 1/1, and enable mpls. [pe1] interface pos 1/1 [pe1-pos1/1] link-protocol ppp [pe1-pos1/1] ip address 10.1.1.1 24 [pe1-pos1/1] mpls [pe1-pos1/1] quit # create a remote connection from ce 1 to ce 2, using the interface connecting ce...
Page 1443
Mpls l2vpn configuration example 1443 system-view [sysname] sysname pe2 [pe2] interface loopback 0 [pe2-loopback0] ip address 10.0.0.3 32 [pe2-loopback0] quit [pe2] mpls lsr-id 10.0.0.3 [pe2] mpls [pe2-mpls] quit # enable mpls l2vpn globally. [pe2] mpls l2vpn # configure interface pos 1/1. [pe2] int...
Page 1444
1444 c hapter 78: mpls l2vpn c onfiguration [ce1] ping 100.1.1.2 ping 100.1.1.2: 56 data bytes, press ctrl_c to break reply from 100.1.1.2: bytes=56 sequence=1 ttl=255 time=180 ms reply from 100.1.1.2: bytes=56 sequence=2 ttl=255 time=60 ms reply from 100.1.1.2: bytes=56 sequence=3 ttl=255 time=10 m...
Page 1445
Mpls l2vpn configuration example 1445 the detailed configuration procedure is as follows: 1 configure ce 1 system-view [sysname] sysname ce1 [ce1] interface pos 1/0 [ce1-pos1/0] link-protocol ppp [ce1-pos1/0] ip address 100.1.1.1 24 2 configure pe 1 system-view [sysname] sysname pe1 [pe1] interface ...
Page 1446
1446 c hapter 78: mpls l2vpn c onfiguration el 100 receive-vpn-label 200 [pe1-pos1/0] quit 3 configure the p device system-view [sysname] sysname p [p] interface loopback 0 [p-loopback0] ip address 192.4.4.4 32 [p-loopback0] quit # configure the lsr id and enable mpls globally. [p] mpls lsr-id 192.4...
Page 1447
Mpls l2vpn configuration example 1447 system-view [sysname] sysname pe2 [pe2] interface loopback 0 [pe2-loopback0] ip address 192.3.3.3 32 [pe2-loopback0] quit # configure the lsr id and enable mpls globally. [pe2] mpls lsr-id 192.3.3.3 [pe2] mpls # configure the lsp establishment triggering policy....
Page 1448
1448 c hapter 78: mpls l2vpn c onfiguration after completing the above configurations, you can display svc l2vpn connection information on pe 1 or pe 2. There should be one l2vpn connection established. Ce 1 should be able to ping interface 100.1.1.2 of ce 2 and ce 2 should be able to ping interface...
Page 1449
Mpls l2vpn configuration example 1449 configuration procedure 1 configure ce 1 system-view [sysname] sysname ce1 [ce1] interface serial 2/0 [ce1-serial 2/0] link-protocol ppp [ce1-serial 2/0]] ip address 100.1.1.1 24 2 configure pe 1 system-view [sysname] sysname pe1 [pe1] interface loopback 0 [pe1-...
Page 1450
1450 c hapter 78: mpls l2vpn c onfiguration # on the interface connecting ce 1, namely serial 2/0, create a martini mpls l2vpn connection. The interface requires no ip address. [pe1] interface serial 2/0 [pe1-serial2/0] mpls l2vc 192.3.3.3 101 [pe1-serial2/0] quit 3 configure the p device system-vie...
Page 1451
Mpls l2vpn configuration example 1451 [p-ospf-1-area-0.0.0.0] quit [p-ospf-1] quit 4 configure pe 2 system-view [sysname] sysname pe2 [pe2] interface loopback 0 [pe2-loopback0] ip address 192.3.3.3 32 [pe2-loopback0] quit # configure the lsr id and enable mpls globally. [pe2] mpls lsr-id 192.3.3.3 [...
Page 1452
1452 c hapter 78: mpls l2vpn c onfiguration [pe2] interface serial 2/0 [pe2-serial2/0] mpls l2vc 192.2.2.2 101 [pe2-serial2/0] quit 5 configure ce 2 system-view [sysname] sysname ce2 [ce2] interface serial 2/0 [ce2-serial2/0] ip address 100.1.1.2 24 after completing the above configurations, you can...
Page 1453
Mpls l2vpn configuration example 1453 network diagram figure 403 network diagram for configuring kompella mpls l2vpn configuration procedure 1 configure igp on the mpls backbone this example uses ospf. The detailed configuration steps are omitted. After configuration, issuing the display ip routing-...
Page 1454
1454 c hapter 78: mpls l2vpn c onfiguration [pe1-bgp-af-l2vpn] quit [pe1-bgp] quit # configure pe 2. System-view [sysname] sysname pe2 [pe2] mpls l2vpn [pe2] bgp 100 [pe2-bgp] peer 1.1.1.9 as-number 100 [pe2-bgp] peer 1.1.1.9 connect-interface loopback 0 [pe2-bgp] l2vpn-family [pe2-bgp-af-l2vpn] pol...
Page 1455
Mpls l2vpn configuration example 1455 1 total connections, connections: 1 up, 0 down, 0 local, 1 remote, 0 unknown ce name: ce1, id: 1, rid type status peer-id route-distinguisher intf 2 rmt up 3.3.3.9 100:1 serial2/0 [ce1] ping 30.1.1.2 ping 30.1.1.2: 56 data bytes, press ctrl_c to break reply from...
Page 1456
1456 c hapter 78: mpls l2vpn c onfiguration [pe-mpls-l2vpn-ce-vpn1-ce2] connection ce-offset 1 interface serial 2/1 [pe-mpls-l2vpn-vpn1] quit 2 verify your configuration after completing the above configurations, you can issue the display mpls l2vpn connection command on the pe. You should see that ...
Page 1457
Troubleshooting mpls l2vpn 1457 ■ check whether the pes are configured with the remote argument and whether the peer addresses are correctly configured. Symptom 2: serial 1/0 and serial 1/1 are configured with different encapsulation types: one is hdlc and the other ppp. They create an ldp connectio...
Page 1458
1458 c hapter 78: mpls l2vpn c onfiguration.
Page 1459: Mpls L3Vpn C
79 mpls l3vpn c onfiguration when configuring mpls l3vpn, go to these sections for information you are interested in: ■ “mpls l3vpn overview” on page 1459 ■ “mpls l3vpn configuration task list” on page 1480 ■ “displaying and maintaining mpls l3vpn” on page 1499 ■ “mpls l3vpn configuration example” o...
Page 1460
1460 c hapter 79: mpls l3vpn c onfiguration a router or a host. It neither can “sense” the existence of any vpn nor needs to support mpls. ■ provider edge router (pe): a pe resides on a service provider network and connects one or more ces to the network. On an mpls network, all vpn processing occur...
Page 1461
Mpls l3vpn overview 1461 ■ a site is a group of ip systems with ip connectivity that does not rely on any service provider network to implement. ■ the classification of a site depends on the topology relationship of the devices, rather than the geographical positions, though the devices at a site ar...
Page 1462
1462 c hapter 79: mpls l3vpn c onfiguration figure 406 vpn-ipv4 address structure when a pe receives an ordinary ipv4 route from a ce, it must advertise the vpn route to the peer pe. The uniqueness of a vpn route is implemented by adding an rd to the route. A service provider can independently assig...
Page 1463
Mpls l3vpn overview 1463 import target attribute of the vpn instance, the pe adds the routes to the vpn routing table. In other words, vpn target attributes define which sites can receive vpn-ipv4 routes, and from which sites that a pe can receive routes. Like rds, vpn target attributes can be of tw...
Page 1464
1464 c hapter 79: mpls l3vpn c onfiguration if two sites (ces) belong to the same vpn and are connected to the same pe, each of them only needs to know how to reach the remote ce. The following takes figure 407 as an example to illustrate the vpn packet forwarding procedure. Figure 407 vpn packet fo...
Page 1465
Mpls l3vpn overview 1465 figure 408 network diagram for basic vpn networking scheme in figure 408 , for example, the vpn target for vpn 1 is 100:1 on the pes, while that for vpn 2 is 200:1. The two vpn 1 sites can communicate with each other, and the two vpn 2 sites can communicate with each other. ...
Page 1466
1466 c hapter 79: mpls l3vpn c onfiguration figure 409 network diagram for hub and spoke networking scheme in figure 409 , the spoke sites communicate with each other through the hub site. The arrows in the figure indicate the advertising path of routes from site 2 to site 1: ■ the hub pe can receiv...
Page 1467
Mpls l3vpn overview 1467 figure 410 network diagram for extranet networking scheme in figure 410 , vpn 1 and vpn 2 can access site 3 of vpn 1. ■ pe 3 can receive the vpn-ipv4 routes advertised by pe 1 and pe 2. ■ pe 1 and pe 2 can receive the vpn-ipv4 routes advertised by pe 3. ■ based on the above,...
Page 1468
1468 c hapter 79: mpls l3vpn c onfiguration routing information exchange from the local ce to the ingress pe after establishing an adjacency with the directly connected pe, a ce advertises its vpn routing information to the pe. The route between the ce and the pe can be a static route, rip route, os...
Page 1469
Mpls l3vpn overview 1469 in either case, you must enable mpls on the ce of the level 2 carrier. Moreover, the ce holds the vpn routes of the level 2 carrier, but it does not advertise the routes to the pe of the level 1 carrier; it only exchanges the routes with other pes of the level 2 carrier. A l...
Page 1470
1470 c hapter 79: mpls l3vpn c onfiguration multi-as vpn in some networking scenarios, multiple sites of a vpn may be connected to multiple isps in different ass, or to multiple ass of an isp. Such an application is called multi-as vpn. Rfc 2547bis presents three inter-provider vpn solutions: ■ vrf-...
Page 1471
Mpls l3vpn overview 1471 to excessive vpn-ipv4 routes on the pes. Moreover, the requirement to create a separate subinterface for each vpn also calls for higher performance of the pes. Inter-provider vpn option b in this kind of solution, two asbrs use mp-ebgp to exchange labeled vpn-ipv4 routes tha...
Page 1472
1472 c hapter 79: mpls l3vpn c onfiguration when every as needs to exchange a great amount of vpn routes, the asbrs may become bottlenecks hindering network extension. One way to solve the above problem is to make pes directly exchange vpn-ipv4 routes without the participation of asbrs: ■ two asbrs ...
Page 1473
Mpls l3vpn overview 1473 figure 416 network diagram for inter-provider vpn option c using rrs multi-role host the vpn attributes of the packets forwarded from a ce to a pe depend on the vpn instance bound to the inbound interface. Therefore, all ces whose packets are forwarded through the same inbou...
Page 1474
1474 c hapter 79: mpls l3vpn c onfiguration most of the current network schemes use the typical hierarchical architecture. For example, the man architecture contains typically three layers, namely, the core layer, convergence layer, and access layer. From the core layer to the access layer, the perf...
Page 1475
Mpls l3vpn overview 1475 the hierarchical pe consists of multiple upes and spes, which function together as a traditional pe. N with the hovpn solution, pe functions are implemented hierarchically. Hence, the solution is also called hierarchy of pe (hope). Upes and spes play different roles: ■ a upe...
Page 1476
1476 c hapter 79: mpls l3vpn c onfiguration figure 418 recursion of hopes figure 418 shows a three-level hope. The pe in the middle is called the middle-level pe (mpe). Mp-bgp runs between spe and mpe, as well as between mpe and upe. N the term of mpe does not really exist in a hovpn model. It is us...
Page 1477
Mpls l3vpn overview 1477 in the ospf vpn extension application, the mpls vpn backbone is considered the backbone area (area 0). Since ospf requires that the backbone area must be contiguous, the area 0 of each vpn site must be connected with the mpls vpn backbone. That is, if a vpn site contains an ...
Page 1478
1478 c hapter 79: mpls l3vpn c onfiguration belong to the same ospf domain, and the route advertisement between them should use type 3 lsas (inter-provider routes). To solve the above problems, pe uses an extended bgp/ospf interaction process called bgp/ospf interoperability to advertise routes from...
Page 1479
Mpls l3vpn overview 1479 figure 420 network diagram for sham link to solve the problem, you can establish a sham link between the two pes so that the routes between them over the mpls vpn backbone become an intra-area route. The sham link acts as an intra-area point-to-point link and is advertised t...
Page 1480
1480 c hapter 79: mpls l3vpn c onfiguration bgp as number substitution since bgp detects routing loops by as number, if ebgp runs between pes and ces, you must assign different as numbers to geographically different sites to ensure correct transmission of the routing information. The bgp as number s...
Page 1481
Configuring vpn instances 1481 configuring vpn instances vpn instances are used to isolate vpn routes from public network routes. Configuring vpn instances is required in all mpls l3vpn networking schemes. In addition, routes of a vpn instance are isolated from those of another. This feature allows ...
Page 1482
1482 c hapter 79: mpls l3vpn c onfiguration n when configured on an interface, the ip binding vpn-instance command clears the ip address of the interface. Therefore, you must re-configure the ip address of the interface after configuring the command. Configuring route related attributes of a vpn ins...
Page 1483
Configuring vpn instances 1483 ■ you can define the maximum number of routes for a vpn instance to support, preventing too many routes from being redistributed into the pe. The maximum number of routes supported by a pe may vary by device. ■ before associating a routing policy with a vpn instance, y...
Page 1484
1484 c hapter 79: mpls l3vpn c onfiguration configuring basic mpls l3vpn this section describes how to configure a simple mpls l3vpn, where only one carrier is involved, the mpls backbone is not inter-provider, and none of the pes or ces functions as a pe and a ce at the same time. Some special mpls...
Page 1485
Configuring basic mpls l3vpn 1485 n ■ perform this configuration on the pes. The configuration method on the ces is the same for configuring ordinary static routes. ■ for information about static route, refer to “static routing and dynamic routing” on page 817 . Configuring rip between pe and ce a r...
Page 1486
1486 c hapter 79: mpls l3vpn c onfiguration if you start multiple ospf processes on a router, you must specify different router ids for different ospf processes. Otherwise, multiple ospf processes may use the same router id, making ospf neighbors unable to identify those ospf processes. Follow these...
Page 1487
Configuring basic mpls l3vpn 1487 ■ for description and detailed configuration about is-is, refer to “is-is configuration” on page 877 . Configuring ebgp between pe and ce 1 on a pe follow these steps to configure ebgp between pe and ce on a pe: n normally, bgp detects routing loops by as number. In...
Page 1488
1488 c hapter 79: mpls l3vpn c onfiguration n ■ exchange of bgp routes for a vpn instance is the same as that of ordinary bgp routes. ■ the configuration task in bgp instance view is the same as that in bgp view. For detailed information, refer to “bgp configuration” on page 825 . ■ for information ...
Page 1489
Configuring basic mpls l3vpn 1489 n for information about bgp-l2vpn address family, refer to “mpls l2vpn configuration” on page 1425 . Configuring specific routing features for bgp-vpnv4 subaddress family follow these steps to configure specific routing features for bgp-vpnv4 subaddress family: conf...
Page 1490
1490 c hapter 79: mpls l3vpn c onfiguration configure the remote pe as the peer peer ip-address as-number as-number required specify the interface for tcp connection peer ip-address connect-interface interface-type interface-number required enter bgp-vpnv4 subaddress family view ipv4-family vpnv4 - ...
Page 1491
Configuring inter-provider vpn 1491 n for information about bgp routing, refer to “bgp configuration” on page 825 . Configuring inter-provider vpn if the mpls backbone on which the vpn routes rely spans multiple ass, you need to configure inter-provider vpn. There are three inter-provider vpn soluti...
Page 1492
1492 c hapter 79: mpls l3vpn c onfiguration in the inter-provider vpn option b solution, the asbr pes need to maintain all vpnv4 routing information and advertise the information to peer asbr pes. In this case, the asbr pes must receive all vpnv4 routing information without performing vpn target fil...
Page 1493
Configuring inter-provider vpn 1493 configuring the asbr pes in the inter-provider vpn option c solution, an inter-provider vpn lsp is required, and the routes advertised between the relevant pes and asbrs must carry mpls label information. An asbr-pe establishes common ibgp peer relationship with p...
Page 1494
1494 c hapter 79: mpls l3vpn c onfiguration configuring the routing policy after you configure and apply a routing policy on an asbr pe, it: ■ assigns mpls labels to the routes received from the pes in the same as before advertising them to the peer asbr pe. ■ assigns new mpls labels to the labeled ...
Page 1495
Configuring multi-role host 1495 configuring multi-role host to allow a ce to access multiple vpns at the same time, you need to configure the multi-role host feature on the pe. All configurations for the multi-role host feature are on the pe to which the ces are attached. N for configuration and co...
Page 1496
1496 c hapter 79: mpls l3vpn c onfiguration with the peer default-route-advertise vpn-instance command configured, the spe always advertises a default route using the local address as the next hop address to the upe, regardless of whether the default route is present in the local routing table or no...
Page 1497
Configuring multi-vpn-instance ce 1497 advertising routes of a loopback interface follow these steps to advertise routes of a loopback interface: creating a sham link follow these steps to create a sham link: n ■ if you start ospf but do not configure the router id, the system will automatically ele...
Page 1498
1498 c hapter 79: mpls l3vpn c onfiguration configuration prerequisites before configuring multi-vpn-instance ce, complete these tasks: ■ configuring vpn instances ■ configuring the link layer and network layer protocols on related interfaces to ensure ip connectivity. Configuration procedure multi-...
Page 1501
Mpls l3vpn configuration example 1501 n for commands to display information about a routing table, refer to “ip routing and routing table” on page 815 . Mpls l3vpn configuration example example for configuring mpls l3vpns network requirements ■ ce 1 and ce 3 belong to vpn 1, while ce 2 and ce 4 belo...
Page 1502
1502 c hapter 79: mpls l3vpn c onfiguration network diagram figure 422 configure mpls l3vpns configuration procedure 1 configure igp on the mpls backbone, enabling the pes and the p device to communicate # configure pe 1. System-view [pe1] interface loopback 0 [pe1-loopback0] ip address 1.1.1.9 32 [...
Page 1503
Mpls l3vpn configuration example 1503 system-view [p] interface loopback 0 [p-loopback0] ip address 2.2.2.9 32 [p-loopback0] quit [p] interface pos 5/0 [p-pos5/0] ip address 172.1.1.2 24 [p-pos5/0] quit [p] interface pos 5/1 [p-pos5/1] ip address 172.2.1.1 24 [p-pos5/1] quit [p] ospf [p-ospf-1] area...
Page 1504
1504 c hapter 79: mpls l3vpn c onfiguration dead timer due in 38 sec neighbor is up for 00:02:44 authentication sequence: [ 0 ] 2 configure mpls basic capability and mpls ldp on the mpls backbone to establish ldp lsps # configure pe 1. [pe1] mpls lsr-id 1.1.1.9 [pe1] mpls [pe1-mpls] lsp-trigger all ...
Page 1505
Mpls l3vpn configuration example 1505 ---------------------------------------------------------------- peer-id status lam ssnrole ft md5 ka-sent/rcv --------------------------------------------------------------- 2.2.2.9:0 operational du passive off off 5/5 ------------------------------------------...
Page 1506
1506 c hapter 79: mpls l3vpn c onfiguration # configure ip addresses for the ces as required in figure 422 . The detailed configuration steps are omitted. After completing the above configurations, you can issue the display ip vpn-instance command on the pes to view the configuration of the vpn inst...
Page 1507
Mpls l3vpn configuration example 1507 after completing the above configuration, if you issue the display bgp vpnv4 vpn-instance peer command on the pes, you should see that bgp peer relationship has been established between pe and ce, and has reached the state of established. The following takes pe ...
Page 1508
1508 c hapter 79: mpls l3vpn c onfiguration routing tables: vpn2 destinations : 3 routes : 3 destination/mask proto pre cost nexthop interface 10.2.1.0/24 direct 0 0 10.2.1.2 eth1/1 10.2.1.2/32 direct 0 0 127.0.0.1 inloop0 10.4.1.0/24 bgp 255 0 3.3.3.9 null0 ces of the same vpn should be capable of ...
Page 1509
Mpls l3vpn configuration example 1509 network diagram figure 423 configure mpls l3vpns using a gre tunnel configuration procedure 1 configure igp on the mpls backbone, enabling the pes and the p device to communicate this example uses ospf. The detailed configuration steps are omitted. After you com...
Page 1510
1510 c hapter 79: mpls l3vpn c onfiguration system-view [pe2] mpls lsr-id 2.2.2.9 [pe2] mpls [pe2-mpls] quit 3 configure vpn instances on pes to allow ces to access and apply tunneling policies to the pes, specifying to use a gre tunnel for vpn packet forwarding # configure pe 1. [pe1] tunnel-policy...
Page 1511
Mpls l3vpn configuration example 1511 [pe1] display ip vpn-instance total vpn-instances configured : 1 vpn-instance name rd create time vpn1 100:1 2006/08/13 09:32:45 [pe1] ping -vpn-instance vpn1 10.1.1.1 ping 10.1.1.1: 56 data bytes, press ctrl_c to break reply from 10.1.1.1: bytes=56 sequence=1 t...
Page 1512
1512 c hapter 79: mpls l3vpn c onfiguration [pe1] bgp 100 [pe1-bgp] peer 2.2.2.9 as-number 100 [pe1-bgp] peer 2.2.2.9 connect-interface loopback 0 [pe1-bgp] ipv4-family vpnv4 [pe1-bgp-af-vpnv4] peer 2.2.2.9 enable [pe1-bgp-af-vpnv4] quit [pe1-bgp] quit n the configurations for pe 2 are similar to th...
Page 1513
Mpls l3vpn configuration example 1513 127.0.0.0/8 direct 0 0 127.0.0.1 inloop0 127.0.0.1/32 direct 0 0 127.0.0.1 inloop0 the following takes pe 1 as an example: [pe1] display ip routing-table routing tables: public destinations : 11 routes : 11 destination/mask proto pre cost nexthop interface 1.1.1...
Page 1514
1514 c hapter 79: mpls l3vpn c onfiguration network diagram figure 424 configure inter-provider vpn option a configuration procedure 1 configure igp on the mpls backbone, implementing the connectivity in the backbone this example uses ospf. The detailed configuration steps are omitted. N the 32-bit ...
Page 1515
Mpls l3vpn configuration example 1515 system-view [pe1] mpls lsr-id 1.1.1.9 [pe1] mpls [pe1-mpls] lsp-trigger all [pe1-mpls] quit [pe1] mpls ldp [pe1-mpls-ldp] quit [pe1] interface pos 5/0 [pe1-pos5/0] mpls [pe1-pos5/0] mpls ldp [pe1-pos5/0] quit # configure mpls basic capability on asbr pe 1 and en...
Page 1516
1516 c hapter 79: mpls l3vpn c onfiguration after you complete the above configurations, each pe and the asbr pe in the same as should be able to establish neighbor relationship. Issuing the display mpls ldp session command on the devices, you can see that the session state field has a value of oper...
Page 1517
Mpls l3vpn configuration example 1517 [asbr-pe1-pos5/1] ip address 192.1.1.1 24 [asbr-pe1-pos5/1] quit # configure asbr pe 2, creating a vpn instance and binding the instance to the interface connected with asbr pe 1. Note that asbr pe 2 considers asbr pe 1 its ce. [asbr-pe2] ip vpn-instance vpn1 [a...
Page 1518
1518 c hapter 79: mpls l3vpn c onfiguration 5 establish ibgp peer relationship between each pe and the asbr pe in the same as and ebgp peer relationship between the asbr pes # configure pe 1. [pe1] bgp 100 [pe1-bgp] peer 2.2.2.9 as-number 100 [pe1-bgp] peer 2.2.2.9 connect-interface loopback 0 [pe1-...
Page 1519
Mpls l3vpn configuration example 1519 after you complete the above configurations, the ces should be able to learn the interface routes from each other and ping each other. Example for configuring inter-provider vpn option b network requirements ■ site 1 and site 2 belong to the same vpn. Ce 1 of si...
Page 1520
1520 c hapter 79: mpls l3vpn c onfiguration [pe1-isis-1] network-entity 10.111.111.111.111.00 [pe1-isis-1] quit # configure lsr id, enable mpls and ldp. [pe1] mpls lsr-id 2.2.2.9 [pe1] mpls [pe1-mpls] lsp-trigger all [pe1-mpls] label advertise non-null [pe1-mpls] quit [pe1] mpls ldp [pe1-mpls-ldp] q...
Page 1521
Mpls l3vpn configuration example 1521 # specify to inject direct routes to the vpn routing table of vpn1. [pe1] bgp 100 [pe1-bgp] ipv4-family vpn-instance vpn1 [pe1-bgp-vpn1] import-route direct [pe1-bgp-vpn1] quit 2 configure asbr-pe 1 # start is-is on asbr-pe 1. System-view [asbr-pe1] isis 1 [asbr...
Page 1522
1522 c hapter 79: mpls l3vpn c onfiguration # specify not to filter the received vpnv4 routes using the import target attribute. [asbr-pe1-bgp] ipv4-family vpnv4 [asbr-pe1-bgp-af-vpnv4] undo policy vpn-target # configure both ibgp peer 2.2.2.0 and ebgp peer 11.0.0.1 as vpnv4 peers. [asbr-pe1-bgp-af-...
Page 1523
Mpls l3vpn configuration example 1523 [asbr-pe2-bgp] peer 11.0.0.2 connect-interface serial 2/1 [asbr-pe2-bgp] peer 5.5.5.9 as-number 600 [asbr-pe2-bgp] peer 5.5.5.9 connect-interface loopback 0 # specify not to filter the received vpnv4 routes using the import target attribute. [asbr-pe2-bgp] ipv4-...
Page 1524
1524 c hapter 79: mpls l3vpn c onfiguration [pe2-vpn-instance-vpn1] vpn-target 3:3 export-extcommunity [pe2-vpn-instance-vpn1] quit # bind the interface connected with ce 1 to the created vpn instance. [pe2] interface ethernet 1/1 [pe2-ethernet1/1] ip binding vpn-instance vpn1 [pe2-ethernet1/1] ip a...
Page 1525
Mpls l3vpn configuration example 1525 network diagram figure 426 configure inter-provider vpn option c configuration procedure 1 configure pe 1 # run is-is on pe 1. System-view [pe1] isis 1 [pe1-isis-1] network-entity 10.111.111.111.111.00 [pe1-isis-1] quit # configure lsr id, enable mpls and ldp. [...
Page 1526
1526 c hapter 79: mpls l3vpn c onfiguration # configure interface loopback 0 and start is-is on it. [pe1] interface loopback 0 [pe1-loopback0] ip address 2.2.2.9 32 [pe1-loopback0] isis enable 1 [pe1-loopback0] quit # create vpn instance vpn1 and configure the rd and vpn target attributes. [pe1] ip ...
Page 1527
Mpls l3vpn configuration example 1527 [asbr-pe1-isis-1] network-entity 10.222.222.222.222.00 [asbr-pe1-isis-1] quit # configure lsr id, enable mpls and ldp. [asbr-pe1] mpls lsr-id 3.3.3.9 [asbr-pe1] mpls [asbr-pe1-mpls] lsp-trigger all [asbr-pe1-mpls] label advertise non-null [asbr-pe1-mpls] quit [a...
Page 1528
1528 c hapter 79: mpls l3vpn c onfiguration [asbr-pe1-bgp] peer 2.2.2.9 as-number 100 [asbr-pe1-bgp] peer 2.2.2.9 next-hop-local [asbr-pe1-bgp] peer 2.2.2.9 route-policy policy2 export # configure the capability to advertise labeled routes to ibgp peer 2.2.2.9 and to receive labeled routes from the ...
Page 1529
Mpls l3vpn configuration example 1529 # configure interface serial 1/1 and enable mpls on it. [asbr-pe2] interface serial 1/1 [asbr-pe2-serial1/1] ip address 11.0.0.1 255.0.0.0 [asbr-pe2-serial1/1] mpls [asbr-pe2-serial1/1] quit # create routing policies. [asbr-pe2] route-policy policy1 permit node ...
Page 1530
1530 c hapter 79: mpls l3vpn c onfiguration [pe2] mpls lsr-id 5.5.5.9 [pe2] mpls [pe2-mpls] lsp-trigger all [pe2-mpls] label advertise non-null [pe2-mpls] quit [pe2] mpls ldp [pe2-mpls-ldp] quit # configure interface serial 1/0, start is-is and enable mpls and ldp on the interface. [pe2] interface s...
Page 1531
Mpls l3vpn configuration example 1531 # configure peer 2.2.2.9 as a vpnv4 peer. [pe2-bgp] ipv4-family vpnv4 [pe2-bgp-af-vpnv4] peer 2.2.2.9 enable [pe2-bgp-af-vpnv4] quit # specify to inject direct routes to the routing table of vpn1. [pe2-bgp] ipv4-family vpn-instance vpn1 [pe2-bgp-vpn1] import-rou...
Page 1532
1532 c hapter 79: mpls l3vpn c onfiguration network diagram figure 427 configure carrier’s carrier configuration procedure 1 configure mpls l3vpn on the level 1 carrier backbone: start is-is as the igp, enable ldp between pe 1 and pe 2, and establish mp-ibgp peer relationship between the pes # confi...
Page 1533
Mpls l3vpn configuration example 1533 [pe1] interface loopback 0 [pe1-loopback0] isis enable 1 [pe1-loopback0] quit [pe1] interface pos 5/1 [pe1-pos5/1] ip address 30.1.1.1 24 [pe1-pos5/1] isis enable 1 [pe1-pos5/1] mpls [pe1-pos5/1] mpls ldp [pe1-pos5/1] mpls ldp transport-address interface [pe1-po...
Page 1534
1534 c hapter 79: mpls l3vpn c onfiguration [pe3-mpls] quit [pe3] mpls ldp [pe3-mpls-ldp] quit [pe3] isis 2 [pe3-isis-2] network-entity 10.0000.0000.0000.0001.00 [pe3-isis-2] quit [pe3] interface loopback 0 [pe3-loopback0] isis enable 2 [pe3-loopback0] quit [pe3] interface pos 5/1 [pe3-pos5/1] ip ad...
Page 1535
Mpls l3vpn configuration example 1535 [pe1] mpls ldp vpn-instance vpn1 [pe1-mpls-ldp-vpn-instance-vpn1] quit [pe1] isis 2 vpn-instance vpn1 [pe1-isis-2] network-entity 10.0000.0000.0000.0003.00 [pe1-isis-2] import-route bgp [pe1-isis-2] quit [pe1] interface pos 5/0 [pe1-pos5/0] ip binding vpn-instan...
Page 1536
1536 c hapter 79: mpls l3vpn c onfiguration [pe3-ethernet1/0] quit [pe3] bgp 100 [pe3-bgp] ipv4-family vpn-instance vpn1 [pe3-bgp-vpn1] peer 100.1.1.1 as-number 65410 [pe3-bgp-vpn1] import-route direct [pe3-bgp-vpn1] quit [pe3-bgp] quit n the configurations for pe 4 and ce 4 are similar to those for...
Page 1537
Mpls l3vpn configuration example 1537 5.5.5.9/32 bgp 255 0 4.4.4.9 null0 6.6.6.9/32 bgp 255 0 4.4.4.9 null0 10.1.1.0/24 isis 15 20 11.1.1.1 pos5/0 11.1.1.0/24 direct 0 0 11.1.1.1 pos5/0 11.1.1.1/32 direct 0 0 127.0.0.1 inloop0 11.1.1.2/32 direct 0 0 11.1.1.2 pos5/0 20.1.1.0/24 bgp 255 0 4.4.4.9 null...
Page 1538
1538 c hapter 79: mpls l3vpn c onfiguration issuing the display ip routing-table vpn-instance command on pe 3 and pe 4, you should see that the routes of the remote vpn customers are present in the vpn routing tables. Takes pe 3 as an example: [pe3] display ip routing-table vpn-instance vpn1 routing...
Page 1539
Mpls l3vpn configuration example 1539 network diagram figure 428 configure multi-role host configuration procedure 1 configure ce 1 # configure the ip addresses of the interfaces on ce 1. System-view [ce1] interface ethernet 1/1 [ce1-ethernet1/1] ip address 100.1.1.1 24 [ce1-ethernet1/1] quit [ce1] ...
Page 1540
1540 c hapter 79: mpls l3vpn c onfiguration [pe1-serial2/1] ip address 1.1.1.1 255.255.255.0 [pe1-serial2/1] quit # configure a static route and redistribute it into bgp, enabling responses from vpn2 to host a can be sent along the correct route in vpn1 of pe 1. [pe1] ip route-static vpn-instance vp...
Page 1541
Mpls l3vpn configuration example 1541 network diagram figure 429 configure hovpn configuration procedure 1 configure upe 1 # configure mpls basic capability and mpls ldp to establish ldp lsps. System-view [upe1] interface loopback 0 [upe1-loopback0] ip address 1.1.1.9 32 [upe1-loopback0] quit [upe1]...
Page 1542
1542 c hapter 79: mpls l3vpn c onfiguration [upe1] ospf [upe1-ospf-1] area 0 [upe1-ospf-1-area-0.0.0.0] network 172.1.1.0 0.0.0.255 [upe1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0 [upe1-ospf-1-area-0.0.0.0] quit [upe1-ospf-1] quit # configure vpn instances vpn1 and vpn2, allowing ce 1 and ce 2 to...
Page 1543
Mpls l3vpn configuration example 1543 system-view [ce2] interface ethernet 1/0 [ce2-ethernet1/0] ip address 10.4.1.1 255.255.255.0 [ce2-ethernet1/0] quit [ce2] bgp 65420 [ce2-bgp] peer 10.4.1.2 as-number 100 [ce2-bgp] import-route direct [ce2] quit 4 configure upe 2 # configure mpls basic capability...
Page 1544
1544 c hapter 79: mpls l3vpn c onfiguration # configure upe 2 to establish mp-ibgp peer relationship with spe 2 and to inject vpn routes. [upe2] bgp 100 [upe2-bgp] peer 3.3.3.9 as-number 100 [upe2-bgp] import-route direct [upe2-bgp] ipv4-family vpnv4 [upe2-bgp-af-vpnv4] peer 3.3.3.9 enable [upe2-bgp...
Page 1545
Mpls l3vpn configuration example 1545 [spe1] interface ethernet 1/1 [spe1-ethernet1/1] ip address 180.1.1.1 24 [spe1-ethernet1/1] mpls [spe1-ethernet1/1] mpls ldp [spe1-ethernet1/1] quit # configure the igp protocol, ospf, for example. [spe1] ospf [spe1-ospf-1] area 0 [spe1-ospf-1-area-0.0.0.0] netw...
Page 1546
1546 c hapter 79: mpls l3vpn c onfiguration [spe2-mpls] quit [spe2] mpls ldp [spe2-mpls-ldp] quit [spe2] interface ethernet 1/0 [spe2-ethernet1/0] ip address 180.1.1.2 24 [spe2-ethernet1/0] mpls [spe2-ethernet1/0] mpls ldp [spe2-ethernet1/0] quit [spe2] interface ethernet 1/1 [spe2-ethernet1/1] ip a...
Page 1547
Mpls l3vpn configuration example 1547 example for configuring ospf sham links network requirements ■ ce 1 and ce 2 belong to vpn 1 and are respectively connected to pe 1 and pe 2. ■ ce 1 and ce 2 are in the same ospf area. ■ vpn traffic between ce 1 and ce 2 is required to be forwarded through the m...
Page 1548
1548 c hapter 79: mpls l3vpn c onfiguration 20.1.1.2/32 direct 0 0 20.1.1.2 s2/1 30.1.1.0/24 ospf 10 3124 20.1.1.2 s2/1 100.1.1.0/24 direct 0 0 100.1.1.1 eth1/0 100.1.1.1/32 direct 0 0 127.0.0.1 inloop0 120.1.1.0/24 ospf 10 3125 20.1.1.2 s2/1 127.0.0.0/8 direct 0 0 127.0.0.1 inloop0 127.0.0.1/32 dir...
Page 1549
Mpls l3vpn configuration example 1549 [pe2-mpls-ldp] quit [pe2] interface serial 2/1 [pe2-serial2/1] ip address 10.1.1.2 24 [pe2-serial2/1] mpls [pe2-serial2/1] mpls ldp [pe2-serial2/1] quit # configure pe 2 to take pe 1 as the mp-ibgp peer. [pe2] bgp 100 [pe2-bgp] peer 1.1.1.9 as-number 100 [pe2-bg...
Page 1550
1550 c hapter 79: mpls l3vpn c onfiguration [pe2-ethernet1/0] ip address 120.1.1.2 24 [pe2-ethernet1/0] quit [pe2] ospf 100 vpn-instance vpn1 [pe2-ospf-100] domain-id 10 [pe2-ospf-100] area 1 [pe2-ospf-100-area-0.0.0.1] network 120.1.1.0 0.0.0.255 [pe2-ospf-100-area-0.0.0.1] quit [pe2-ospf-100] quit...
Page 1551
Mpls l3vpn configuration example 1551 path to the peer ce is now along the bgp route across the backbone, and that a route to the sham link destination address is present. Take pe 1 as an example: [pe1] display ip routing-table vpn-instance vpn1 routing tables: vpn1 destinations : 6 routes : 6 desti...
Page 1552
1552 c hapter 79: mpls l3vpn c onfiguration example for configuring bgp as number substitution network requirements as shown in figure 431 , ce 1 and ce 2 belong to vpn 1 and are connected to pe 1 and pe 2 respectively. In addition, they use the same as number 600. Network diagram figure 431 configu...
Page 1553
Mpls l3vpn configuration example 1553 resides; but has not learned the route to the vpn (100.1.1.0/24) behind ce 1. You should see the similar situation on ce 1. Display ip routing-table routing tables: public destinations : 8 routes : 8 destination/mask proto pre cost nexthop interface 10.1.1.0/24 ...
Page 1554
1554 c hapter 79: mpls l3vpn c onfiguration 2 configure bgp as number substitution # configure bgp as number substitution on pe 2. System-view [pe2] bgp 100 [pe2-bgp] ipv4-family vpn-instance vpn1 [pe2-bgp-vpn1] peer 10.2.1.1 substitute-as [pe2-bgp-vpn1] quit [pe2-bgp] quit you should see that among...
Page 1555
Mpls l3vpn configuration example 1555 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 66/79/109 ms.
Page 1556
1556 c hapter 79: mpls l3vpn c onfiguration.
Page 1557: Dvpn C
80 dvpn c onfiguration when configuring dvpn, go to these sections for information you are interested in: ■ “dvpn overview” on page 1557 ■ “dvpn configuration task list” on page 1562 ■ “displaying and maintaining dvpn” on page 1571 ■ “dvpn configuration example” on page 1571 dvpn overview the demand...
Page 1558
1558 c hapter 80: dvpn c onfiguration vam client vam clients are the nodes comprising a dvpn. A vam client registers its private address, public address, and vam id with the vam server and inquires of the vam server concerning information about other vam clients. Unless otherwise noted, the term “va...
Page 1559
Dvpn overview 1559 figure 432 spoke-hub/spoke-spoke networking diagram as shown in figure 432 , after a spoke registers with the vam server and gets information about the hub from the keepalive ack message, it establishes a permanent tunnel with the hub. Two spokes that are not behind nat gateways c...
Page 1560
1560 c hapter 80: dvpn c onfiguration registration acknowledgement (the identity authentication steps are skipped in this case). If authentication is required, the server sends to the client an identity authentication request, indicating the required authentication algorithm. In the case of chap aut...
Page 1561
Dvpn overview 1561 supported dvpn features n support for these features varies by device. Nat traversal of dvpn packets when the tunnel initiator resides behind a nat gateway, a spoke-spoke tunnel can be established traversing the nat gateway. If the other end of the tunnel is behind a nat gateway, ...
Page 1562
1562 c hapter 80: dvpn c onfiguration dvpn configuration task list configuring dvpn involves configuring vam, aaa, tunnel, ipsec/ike and routing. When making configuration, you are recommended to configure the dvpn server, dvpn client, and spoke devices in order. To configure dvpn, perform the tasks...
Page 1563
Configuring the vam server 1563 enabling the vam server follow these steps to enable the vam server feature: configuring the listening ip address and udp port number vam employs the client/server model. Operating at the application layer of the tcp/ip protocol stack, vam uses udp as its transport la...
Page 1564
1564 c hapter 80: dvpn c onfiguration n ■ the authentication algorithm of sha-1 is always used for connection requests from clients and connection responses from the server. Whether subsequent packets are to be authenticated depends on your configuration. ■ the encryption algorithm of aes-128 is alw...
Page 1565
Configuring the vam client 1565 configuring the pre-shared key of vam server for a vpn domain the pre-shared key is used to generate the public keys for security of the channels between the server and a client. In the connection initialization process, the pre-shared key is used to generate the init...
Page 1566
1566 c hapter 80: dvpn c onfiguration vam client configuration task list perform the tasks described in the following sections to configure the vam client: creating a vam client follow these steps to create a vam client specifying an interval for resending a vam packet if a client sends a vam protoc...
Page 1567
Configuring the vam client 1567 n currently, the public ip address of the vam server does not support dns. Specifying the secondary vam server follow these steps to specify the public ip address and udp port number of the secondary vam server: n currently, the public ip address of the vam server doe...
Page 1568
1568 c hapter 80: dvpn c onfiguration n for a vpn domain, all the vam clients and the vam server must be configured with the same pre-shared key. Enabling the vam client follow these steps to enable the vam client: configuring an ipsec profile ipsec profile is designed to improve the security of dat...
Page 1569
Configuring the dvpn tunnel parameters 1569 n ■ an ipsec profile depends on ike for sa negotiation. An ipsec profile can reference up to six security proposals. Ike searches for security proposals that match at both ends during negotiation. If no match is found, sas cannot be established and the pac...
Page 1570
1570 c hapter 80: dvpn c onfiguration n ■ if you configure the source address of a tunnel by specifying the source interface, the tunnel takes the primary ip address of the source interface as its source address. ■ tunnel interfaces of the same vpn domain must be configured with private addresses in...
Page 1571
Configuring a dvpn route 1571 ■ for details about the interface tunnel, ip address and source commands, refer to “tunneling configuration” on page 693 . ■ for details about the ospf network-type and ospf dr-priority commands, refer to “ospf configuration” on page 917 . ■ for details about vpn multi-...
Page 1572
1572 c hapter 80: dvpn c onfiguration network diagram figure 435 network diagram for dvpn configuration in full-mesh networks configuration procedure 1 configure the primary vam server (main) ■ configure ip addresses for the interfaces (omitted). ■ configure aaa. System-view # configure a radius sch...
Page 1573
Dvpn configuration example 1573 [mainserver] domain domain1 [mainserver-isp-domain1] authentication default radius-scheme radsun [mainserver-isp-domain1] accounting default radius-scheme radsun [mainserver-isp-domain1] quit [mainserver] domain default enable domain1 ■ configure the vam server. # spe...
Page 1574
1574 c hapter 80: dvpn c onfiguration [hub1-vam-client-name-dvpn1hub1] server primary ip-address 192.168.1.22 [hub1-vam-client-name-dvpn1hub1] server secondary ip-address 192.168.1.33 [hub1-vam-client-name-dvpn1hub1] pre-shared-key simple 123 # create a local user, setting the user name to dvpn1hub1...
Page 1575
Dvpn configuration example 1575 [hub1-tunnel1] ipsec profile vamp [hub1-tunnel1] quit # configure a tunnel interface tunnel 2 for vpn 2. [hub1] interface tunnel 2 [hub1-tunnel2] tunnel-protocol dvpn udp [hub1-tunnel2] vam client dvpn2hub1 [hub1-tunnel2] ip address 10.0.2.1 255.255.255.0 [hub1-tunnel...
Page 1576
1576 c hapter 80: dvpn c onfiguration [hub2-vam-client-name-dvpn2hub2] server primary ip-address 192.168.1.22 [hub2-vam-client-name-dvpn2hub2] server secondary ip-address 192.168.1.33 [hub2-vam-client-name-dvpn2hub2] pre-shared-key simple 456 # create a local user, setting the user name to dvpn2hub2...
Page 1577
Dvpn configuration example 1577 [hub2] ospf 100 [hub2-ospf-100] area 0 [hub2-ospf-100-area-0.0.0.0] network 192.168.1.2 0.0.0.255 [hub2-ospf-100-area-0.0.0.0] quit # configure ospf for the private networks. [hub2] ospf 200 [hub2-ospf-200] area 0 [hub2-ospf-200-area-0.0.0.0] network 10.0.1.2 0.0.0.25...
Page 1578
1578 c hapter 80: dvpn c onfiguration ■ configure dvpn tunnels # configure a tunnel interface tunnel 1 for vpn 1. [spoke1] interface tunnel 1 [spoke1-tunnel1] tunnel-protocol dvpn udp [spoke1-tunnel1] vam client dvpn1spoke1 [spoke1-tunnel1] ip address 10.0.1.3 255.255.255.0 [spoke1-tunnel1] source e...
Page 1579
Dvpn configuration example 1579 ■ configure the ipsec profile # configure the ipsec proposal. [spoke2] ipsec proposal vam [spoke2-ipsec-proposal-vam] encapsulation-mode tunnel [spoke2-ipsec-proposal-vam] transform esp [spoke2-ipsec-proposal-vam] esp encryption-algorithm des [spoke2-ipsec-proposal-va...
Page 1580
1580 c hapter 80: dvpn c onfiguration [spoke2-ospf-200-area-0.0.0.0] quit [spoke2] ospf 300 [spoke2-ospf-300] area 0 [spoke2-ospf-300-area-0.0.0.0] network 10.0.2.4 0.0.0.255 [spoke2-ospf-300-area-0.0.0.0] quit 7 configure spoke 3 ■ configure the ip addresses of the interfaces. (omitted) ■ configure...
Page 1581
Dvpn configuration example 1581 [spoke3-tunnel2] ipsec profile vamp [spoke3-tunnel2] quit ■ configure ospf # configure ospf for the public network. [spoke3] ospf 100 [spoke3-ospf-100] area 0 [spoke3-ospf-100-area-0.0.0.0] network 192.168.1.5 0.0.0.255 [spoke3-ospf-100-area-0.0.0.0] quit # configure ...
Page 1582
1582 c hapter 80: dvpn c onfiguration network diagram figure 436 network diagram for dvpn configuration in spoke-hub networks network procedure 1 configure the primary vam server ■ configure the ip addresses of the interfaces (omitted) ■ configure aaa system-view # configure a radius scheme named ra...
Page 1583
Dvpn configuration example 1583 [mainserver-isp-domain1] quit [mainserver] domain default enable domain1 ■ configure the vam server # specify the listening ip address of the server. [mainserver] vam server ip-address 192.168.1.22 # create vpn domain 1. [mainserver] vam server vpn 1 # set the pre-sha...
Page 1584
1584 c hapter 80: dvpn c onfiguration [hub1] ike peer vam [hub1-ike-peer-vam] pre-shared-key abcde [hub1-ike-peer-vam] quit # configure the ipsec profile. [hub1] ipsec profile vamp [hub1-ipsec-profile-vamp] proposal vam [hub1-ipsec-profile-vamp] ike-peer vam [hub1-ipsec-profile-vamp] sa duration tim...
Page 1585
Dvpn configuration example 1585 [hub2] ipsec proposal vam [hub2-ipsec-proposal-vam] encapsulation-mode tunnel [hub2-ipsec-proposal-vam] transform esp [hub2-ipsec-proposal-vam] esp encryption-algorithm des [hub2-ipsec-proposal-vam] esp authentication-algorithm sha1 [hub2-ipsec-proposal-vam] quit # co...
Page 1586
1586 c hapter 80: dvpn c onfiguration # create a local user named dvpn1spoke1, setting the password as dvpn1spoke1. [spoke1-vam-client-name-dvpn1spoke1] user dvpn1spoke1 password simple dvpn1spoke1 [spoke1-vam-client-name-dvpn1spoke1] client enable [spoke1-vam-client-name-dvpn1spoke1] quit ■ configu...
Page 1587
Dvpn configuration example 1587 [spoke2] vam client name dvpn1spoke2 [spoke2-vam-client-name-dvpn1spoke2] vpn 1 # specify the ip addresses of the vam servers and set the pre-shared key. [spoke2-vam-client-name-dvpn1spoke2] server primary ip-address 192.168.1.22 [spoke2-vam-client-name-dvpn1spoke2] s...
Page 1588
1588 c hapter 80: dvpn c onfiguration.
Page 1589: Gre C
81 gre c onfiguration when configuring gre, go to these sections for information you are interested in: ■ “gre overview” on page 1589 ■ “configuring a gre over ipv4 tunnel” on page 1593 ■ “configuring a gre over ipv6 tunnel” on page 1594 ■ “displaying and maintaining gre” on page 1596 ■ “gre over ip...
Page 1590
1590 c hapter 81: gre c onfiguration 4 upon the receipt of the packet, the tunnel interface encapsulates it in a gre packet and submits to the ip module. 5 the ip module encapsulates the packet in an ip packet, and then forwards the ip packet out through the corresponding network interface based on ...
Page 1591
Gre overview 1591 3 the gre module checks the key, checksum and sequence number, and then strips off the gre header and submits the payload to the ipx module. 4 the ipx module performs the subsequent forwarding processing for the packet. N encapsulation and decapsulation processes on both ends of th...
Page 1592
1592 c hapter 81: gre c onfiguration scope enlargement of the network running a hop-limited protocol figure 441 scope enlargement of the network when the hop count between two terminals exceeds 15, the terminals cannot communicate with each other. Using gre, you can hide some hops so as to enlarge t...
Page 1593
Configuring a gre over ipv4 tunnel 1593 configuring a gre over ipv4 tunnel configuration prerequisites interfaces on a device, such as vlan interfaces, ethernet interfaces, and loopback interfaces, are configured with ipv4 addresses and can communicate. These interfaces can be used as the source of ...
Page 1594
1594 c hapter 81: gre c onfiguration note that: ■ for the configuration of mtu value, refer to the mtu command in “tunneling configuration” on page 693 . ■ the source address and destination address of a tunnel uniquely identify a path. They must be configured at both ends of the tunnel and are mutu...
Page 1595
Configuring a gre over ipv6 tunnel 1595 note that: ■ for the configuration of ipv6 mtu value, refer to the ipv6 mtu command in “ipv6 basics configuration” on page 655 . ■ the source address and destination address of a tunnel uniquely identify a path. They must be configured at both ends of the tunn...
Page 1596
1596 c hapter 81: gre c onfiguration ■ if a device needs to reference a link aggregation group for the tunnel interface to receive and send packets, the link aggregation group must already exist. Otherwise, the tunnel interface cannot work properly and the tunnel cannot communicate. For devices that...
Page 1597
Gre over ipv4 tunnel configuration example 1597 [routera-ethernet1/0] ip address 10.1.1.1 255.255.255.0 [routera-ethernet1/0] quit # configure an ipv4 address for interface serial 2/0, the physical interface for the tunnel. [routera] interface serial 2/0 [routera-serial2/0] ip address 1.1.1.1 255.25...
Page 1598
1598 c hapter 81: gre c onfiguration [routerb-tunnel0] ip address 10.1.2.2 255.255.255.0 # configure the tunnel encapsulation mode. [routerb-tunnel0] tunnel-protocol gre # configure the source address of interface tunnel0 to be the ip address of interface serial 2/1. [routerb-tunnel0] source 2.2.2.2...
Page 1599
Gre over ipv6 tunnel configuration example 1599 [routera] interface serial 2/0 [routera-serial2/0] ipv6 address 2002::1:1 64 [routera-serial2/0] quit # create an interface named tunnel0. [routera] interface tunnel 0 # configure an ipv4 address for interface tunnel0. [routera-tunnel0] ip address 10.1...
Page 1600
1600 c hapter 81: gre c onfiguration # configure an ipv4 address for interface tunnel0. [routerb-tunnel0] ip address 10.1.2.2 255.255.255.0 # configure the tunnel encapsulation mode. [routerb-tunnel0] tunnel-protocol gre ipv6 # configure the source address of interface tunnel0 to be the ip address o...
Page 1601: L2Tp C
82 l2tp c onfiguration when configuring l2tp, go to these sections for information you are interested in: ■ “l2tp overview” on page 1601 ■ “l2tp configuration task list” on page 1607 ■ “displaying and maintaining l2tp” on page 1614 ■ “l2tp configuration example” on page 1614 ■ “troubleshooting l2tp”...
Page 1602
1602 c hapter 82: l2tp c onfiguration (usually, windows 2000 platform), however, limits the platforms that users can use. In general, a router or a vpn proprietary server is used as a gateway. Vpdn tunneling protocols are broken into three types: pptp, l2f, and l2tp, of which l2tp is widely used at ...
Page 1603
L2tp overview 1603 an lns, an end system of an l2tp tunnel, is the peer of an lac. It is the logical termination point of a ppp session that is tunneled by the lac. Technical specifications 1 l2tp architecture figure 448 shows the relationship between the ppp frame, control channel, and data channel...
Page 1604
1604 c hapter 82: l2tp c onfiguration 3 control message and data message l2tp supports two types of messages: control message and data message. ■ control messages are intended for establishment and maintenance of tunnels and sessions and for transmission control. Control messages are transmitted ove...
Page 1605
L2tp overview 1605 figure 451 typical l2tp network figure 452 shows the setup procedure of an l2tp call. Figure 452 l2tp call setup procedure setup procedure of an l2tp call follows: 1 the remote user makes a ppp call. 2 the remote user and the lac (router a) perform ppp lcp negotiation. 3 the lac a...
Page 1606
1606 c hapter 82: l2tp c onfiguration 7 if authentication of the tunnel is required, the lac sends a chap challenge to the lns. The lns returns a chap response and sends its chap challenge to the lac. Accordingly, the lac returns a chap response to the lns. 8 the tunnel passes authentication. 9 the ...
Page 1607
L2tp configuration task list 1607 6 reliability l2tp supports lns backup. When the connection to the primary lns is torn down, an lac can establish a new one with a secondary lns, enhancing the reliability and fault tolerance of vpn services. L2tp configuration task list complete the following tasks...
Page 1608
1608 c hapter 82: l2tp c onfiguration note that: ■ an l2tp group is intended to represent a group of parameters and is corresponding to one or one group of vpn users. This not only allows for flexible l2tp configuration on routers, but also facilitates one-to-one and one-to-many networking applicati...
Page 1609
Lns configuration 1609 for three times, it considers that the l2tp tunnel is down and tries to re-establish a tunnel with the peer. ■ a tunnel will be disconnected when there is no more user online, a network failure occurs, or a network administrator wants to tear it down. Either of the lac and the...
Page 1610
1610 c hapter 82: l2tp c onfiguration to do... Use the command... Remarks enter system view system-view - enable l2tp l2tp enable required disabled by default enable the l2tp multi-instance function l2tpmoreexam enable optional disabled by default configure virtual interface template parameters refe...
Page 1611
Lns configuration 1611 note that: ■ with the l2tp multi-instance function enabled, a router can serve as lns for multiple enterprises. The implementation of l2tp multi-instance enriches vpn network applications, especially in mpls-vpn. In practice, private routes of enterprises need the support of v...
Page 1612
1612 c hapter 82: l2tp c onfiguration once on the lns. Only when the two authentications succeed can an l2tp tunnel be set up. On an l2tp network, an lns authenticates users in three ways: proxy authentication, mandatory chap authentication, and lcp negotiation. If neither lcp re-negotiation nor man...
Page 1613
Lns configuration 1613 if you enable lcp negotiation but do not configure authentication for the corresponding virtual interface template, the lns will not perform addition authentication of users (in this case, users are authenticated only once on the lac) and will directly allocate addresses from ...
Page 1614
1614 c hapter 82: l2tp c onfiguration configuring local authentication, usernames and passwords if mandatory chap authentication is configured on the lns, you need to configure local users and their passwords. An lns determines whether a remote dial-up user is a valid vpn user by checking whether th...
Page 1615
L2tp configuration example 1615 nas-initiated vpn network requirements a vpn user accesses the corporate headquarters as follows: 1 the user dials in to nas through a medium supporting ppp. 2 the nas determines whether the user is a valid vpn client. If so, it initiates a tunneling request to the ln...
Page 1616
1616 c hapter 82: l2tp c onfiguration [lac] interface async 1/0 [lac-async1/0] ip address 1.1.1.1 255.255.255.0 [lac-async1/0] ppp authentication-mode chap [lac-async1/0] quit # enable l2tp. [lac] l2tp enable # create an l2tp group and configure its attributes. [lac] l2tp-group1 [lac-l2tp1] tunnel n...
Page 1617
L2tp configuration example 1617 # enable tunnel authentication and specify the tunnel authentication password. [lns-l2tp1] tunnel authentication [lns-l2tp1] tunnel password simple aabbcc client-initiated vpn network requirements a vpn user accesses the corporate headquarters as follows: 1 the user f...
Page 1618
1618 c hapter 82: l2tp c onfiguration # configure local authentication for the vpn users. [lns] domain system [lns-isp-system] authentication ppp local [lns-isp-system] ip pool 1 192.168.0.2 192.168.0.100 [lns-isp-system] quit # enable l2tp. [lns] l2tp enable # configure the virtual interface templa...
Page 1619
L2tp configuration example 1619 configuration procedure 1 configure the users create a dial-up connection on each host, using the access number of the lac as the dialup number. Dial-up users accept the ip addresses assigned by the lns. ■ on host a, enter vpdn1@aaa.Net as the username and 11111 as th...
Page 1620
1620 c hapter 82: l2tp c onfiguration [lac] interface virtual-template 100 [lac-virtual-template100] ppp authentication-mode chap domain aaa.Net [lac-virtual-template100] quit [lac] interface virtual-template 101 [lac-virtual-template101] ppp authentication-mode chap domain bbb.Net [lac-virtual-temp...
Page 1621
Troubleshooting l2tp 1621 [lns-isp-aaa.Net] ip pool 1 10.0.2.10 10.0.2.100 [lns-isp-aaa.Net] quit # create two virtual interface templates. [lns]interface virtual-template 1 [lns-virtual-template1] ip address 1.1.2.2 255.255.255.0 [lns-virtual-template1] remote address pool 1 [lns-virtual-template1]...
Page 1622
1622 c hapter 82: l2tp c onfiguration ■ no l2tp group is configured on the lns (usually a router) to receive calls from the tunnel peer. For details, refer to the description of the allow command. ■ tunnel authentication fails. For successful tunnel authentication, tunnel authentication must be enab...
Page 1623: S O
83 q o s o verview when configuring qos, go to these sections for information you are interested in: ■ “traffic classification, policing, and shaping” on page 1627 ■ “qos policy configuration” on page 1641 ■ “congestion management” on page 1649 ■ “priority mapping” on page 1675 ■ “congestion avoidan...
Page 1624
1624 c hapter 83: q o s o verview apart from traditional applications of www, e-mail and ftp, network users try to expand some new applications, such as tele-education, telemedicine, video telephone, videoconference and video-on-demand (vod), on the internet. And the enterprise users expect to conne...
Page 1625
Traffic management technologies 1625 when traffic arrives at wire speed, congestion may occur for network resource bottleneck. Besides the bottleneck of link bandwidth, congestion will also be caused by resources deficiency in normal packet forwarding, such as the deficiency of assignable processor ...
Page 1626
1626 c hapter 83: q o s o verview and congestion. Same as traffic policing, traffic shaping is implemented at the ip layer. ■ congestion management: handles resource competition during network congestion. Generally, it stores the packets in the queue first, and then takes a dispatching algorithm to ...
Page 1627: Raffic
84 t raffic c lassification , p olicing , and s haping traffic classification overview traffic classification traffic classification is the prerequisite and foundation for differentiated services, which uses certain rules to identify the packets with certain features. To discriminate flows, you can ...
Page 1628
1628 c hapter 84: t raffic c lassification , p olicing , and s haping figure 458 ds field and tos byte as shown in figure 458 , the tos byte of ip header contains 8 bits: the first three bits (0 to 2) indicates ip precedence, valued in the range 0 to 7; the following 4 bits (3 to 6) indicates tos pr...
Page 1629
Traffic evaluation and token bucket 1629 figure 459 measuring the traffic with token bucket measuring the traffic with token bucket whether or not the token quantity of the token bucket can satisfy the packets forwarding is the basis for token bucket to measure the traffic specification. If enough t...
Page 1630
1630 c hapter 84: t raffic c lassification , p olicing , and s haping and e bucket), which represents different bursting class permitted. In each evaluation, you may use different traffic control policies for different situations, such as “c bucket has enough tokens”; “tokens of c bucket are deficie...
Page 1631
Traffic evaluation and token bucket 1631 figure 460 ts diagram for example, in the implementation shown in figure 461 , router a sends packets to router b. And router b implements tp on those packets, and directly drops exceeding traffic. Figure 461 ts implementation to reduce packets dropping, gts ...
Page 1632
1632 c hapter 84: t raffic c lassification , p olicing , and s haping figure 462 lr processing diagram if token bucket is used to control the traffics, when there are tokens in token bucket, the packets can be sent in burst; if no tokens are available, packets will not be sent until new tokens gener...
Page 1634
1634 c hapter 84: t raffic c lassification , p olicing , and s haping configuring traffic policing applicable to all traffics follow these steps to configure traffic policing applicable to all traffics the action taken on a packet can be: ■ continue: has it to be dealt with by the next car policy. ■...
Page 1635
Traffic policing and traffic shaping configuration 1635 ■ remark-dscp-continue new-dscp: remarks the packet with a new dscp value and hands it over to the next car policy. It ranges from 0 to 63. When it is displayed in characters, its value can be af11, af12, af13, af21, af22, af23, af31, af32, af3...
Page 1636
1636 c hapter 84: t raffic c lassification , p olicing , and s haping configuring traffic shaping applicable to all traffics follow these steps to configure traffic shaping applicable to all traffics enter interface view or port group view enter interface view interface interface-type interface-numb...
Page 1637
Traffic policing and traffic shaping configuration 1637 configuration example for traffic shaping configure ts on the interface ethernet1/0 to shape the traffic transmitted from the interface (shaping the traffic exceeding 500 kbps). # enter system view. System-view # enter interface view. [sysname]...
Page 1638
1638 c hapter 84: t raffic c lassification , p olicing , and s haping configuration example for line rate on physical interface configure outbound line rate on interface ethernet1/0 to 500 kbps. # enter system view. System-view # enter interface view [sysname] interface ethernet1/0 # configure line ...
Page 1639
Traffic policing and shaping configuration example 1639 traffic policing and shaping configuration example configuration requirements ■ the interface ethernet1/0 of router a is connected with the interface ethernet1/1 of router b. ■ server, host a and host b can access the internet via router a and ...
Page 1640
1640 c hapter 84: t raffic c lassification , p olicing , and s haping configuration procedure 1 configure on router a # configure gts on the interface ethernet1/0 of router a to shape the traffic transmitted from the interface (shaping the traffic exceeding 0. 5 mbps) so as to reduce the packet drop...
Page 1641: S P
85 q o s p olicy c onfiguration introduction qos policy includes three elements: class, traffic behavior and policy. You can bind the specified class and traffic behavior through qos policy to configure qos. Classes a class is used to identify traffic. Class elements include class name and rule. You...
Page 1642
1642 c hapter 85: q o s p olicy c onfiguration introduction to qos policies introduction to each qos policies for the configuration of queue and congestion avoidance, refer to “configuring class-based queuing” on page 1661 . Qos policy configuration configuration prerequisites ■ the class name and r...
Page 1643
Qos policy configuration 1643 configuration example 1 network requirements configure a class test_class. The rule is to satisfy the data packet with ip priority to 6. 2 configuration procedure # enter system view. System-view # define a class and enter class mapping view. [sysname] traffic classifie...
Page 1644
1644 c hapter 85: q o s p olicy c onfiguration n traffic shaping for software forwarding does not support ipv6. Configuration example 1 network requirements configure a traffic behavior test_behavior and use traffic policing. The car of the traffic is 100 kbps. 2 configuration procedure # enter syst...
Page 1645
Qos policy configuration 1645 defining policy the corresponding relationship between the classes and traffic behaviors in this policy are defined. Each traffic behavior includes a group of qos actions. Follow these steps to specify the traffic behavior for the class in the policy n if an acl is defi...
Page 1646
1646 c hapter 85: q o s p olicy c onfiguration n if a qos policy is applied on the outbound direction of an interface, the qos policy is not valid on a local packet. The following are the definition and functions of a local packet ■ some internal packets are the important protocol packets to maintai...
Page 1647
Displaying and maintaining qos policy 1647 [sysname-ethernet1/0] qos apply policy test_policy inbound displaying and maintaining qos policy after the above configuration, you can execute the display command in any view to view the running status of qos policy and verify the result of the configurati...
Page 1648
1648 c hapter 85: q o s p olicy c onfiguration.
Page 1649: Ongestion
86 c ongestion m anagement congestion management overview as to a network device, congestion will occur on the interface where the arrival rate of packets is faster than the sending rate. If there is no enough buffer capacity to store those packets and then a part of them will be lost, which may cau...
Page 1650
1650 c hapter 86: c ongestion m anagement pq (priority queuing) figure 465 priority queuing priority queuing is designed for mission-critical applications. Those applications have an important feature, i.E. When congestion occurs they require preferential service to reduce the response delay. Pq can...
Page 1651
Congestion management overview 1651 cq (custom queuing) figure 466 custom queuing cq classifies packets into 17 classes in accordance with certain rules (corresponding to 17 queues). Based on their own classes, packets will enter the corresponding custom queues according to fifo policy. Of these 17 ...
Page 1652
1652 c hapter 86: c ongestion m anagement wfq (weighted fair queuing) figure 467 wfq diagram before further to weighted fair queuing, fair queuing (fq) is to be introduced first. Fq is designed for fairly sharing network resources, which will try to reduce the delay and jitter of all traffics to the...
Page 1653
Congestion management overview 1653 the bandwidth-occupying proportion for each traffic is: (priority + 1)/total quota of bandwidth, i.E. Bandwidth available for each traffic: 1/15, 2/15, 3/15, 4/15, 5/15. Because wfq can balance the delay and jitter of every flow when congestion occurs, it is effec...
Page 1654
1654 c hapter 86: c ongestion m anagement delay and jitter and ensuring the quality of audio or video service which is sensitive to delay. Figure 468 rtp queuing diagram as shown in the above figure, an rtp packet is sent into a high priority queue. Rtp packet is the udp packet whose port number is ...
Page 1655
Congestion management overview 1655 pq 4 provide service of absolute preference to data of different applications, and capable of ensuring the low delay for real-time applications (voip). Provide absolute preference to the packets of preferential business on their bandwidth-occupying. ■ need to be c...
Page 1656
1656 c hapter 86: c ongestion m anagement configuring fifo queuing fifo is the queue scheduling mechanism for interface by default, and the length of the queue can be changed by configuration command. Configuring fifo queuing follow these steps to configure fifo queuing configuration example for fif...
Page 1657
Configuring priority queuing 1657 system-view [sysname] interface ethernet1/0 [sysname-ethernet1/0] qos fifo queue-length 100 configuring priority queuing you may define multiple rules for a priority-list group and apply these rules to an interface. When a packet that needs to be forwarded out the i...
Page 1658
1658 c hapter 86: c ongestion m anagement priority queuing configuration example configuration requirement as shown in the diagram, both server and host a send data to host b through router a. Suppose server sends key service data and host a sends common service data. Congestion may occur on interfa...
Page 1659
Configuring custom queuing 1659 configuring custom queuing there are 16 groups (called custom-groups) of cqls (1 through 16), each specifying packet queuing rule, length of each queue, and bytes to be sent continuously for each queue during a poll. An interface can only use one group. Configuring cu...
Page 1660
1660 c hapter 86: c ongestion m anagement [sysname] qos cql 1 inbound-interface ethernet 1/0 queue 1 [sysname] qos cql 1 queue 1 serving 2000 # apply the priority-group 1 on the interface serial1/0. [sysname] interface serial 1/0 [sysname-serial 1/0] qos cq cql 1 configuring wfq configuring wfq when...
Page 1661
Configuring class-based queuing 1661 configuring class-based queuing the class-based queuing cbq configuration includes: 1 configure the maximum available bandwidth on the interface 2 define the class and define a group of traffic classification rules in the class view. 3 define traffic behavior, an...
Page 1662
1662 c hapter 86: c ongestion m anagement ■ default-class, adopting pre-defined traffic behavior of be. Configuring the maximum available bandwidth on the interface configuring the maximum available bandwidth on the interface the maximum available bandwidth discussed here refers to the maximum inter...
Page 1663
Configuring class-based queuing 1663 # configure the maximum available bandwidth on the interface ethernet1/0. [sysname-ethernet1/0] qos max-bandwidth 60 defining a class before you can define a class, you must first create its class name. Then you can configure matching rules in this class view. Co...
Page 1664
1664 c hapter 86: c ongestion m anagement n ■ this behavior can apply only in output direction of an interface or atm pvc. ■ the same traffic behavior must use the same standard to configure queue ef and queue af, either bandwidth or percentage. ■ under the same traffic behavior, queue ef, queue af ...
Page 1665
Configuring class-based queuing 1665 follow these steps to configure wfq: n configure that the traffic behavior of wfq can only be associated with the default class. 4 configuring maximum queue length configure maximum queue length and the drop type is tail drop. Follow these steps to configure maxi...
Page 1667
Configuring class-based queuing 1667 follow these steps to configure dscp lower-limit, upper-limit and discard probability of wred: dscp-value: dscp value. It can be in the range 0 to 63 or be one of the following keywords: ef, af11, af12, af13, af21, af22, af23, af31, af32, af33, af41, af42, af43, ...
Page 1668
1668 c hapter 86: c ongestion m anagement n ■ only after the queue af and wred commands are configured can this configuration be performed. ■ the configuration of wred ip-precedence will be deleted when wred configuration is deleted. ■ the configuration of drop parameter gets invalid if the configur...
Page 1669
Configuring class-based queuing 1669 applying policy configuration procedure the qos apply policy command maps a policy to a physical interface or atm pvc. One policy mapping can be applied on multiple physical interfaces or atm pvc. Follow these steps to apply a policy to the interface or atm pvc: ...
Page 1670
1670 c hapter 86: c ongestion m anagement ■ the policy configured with ts (e.G. Gts) and queue (e.G. Queue ef, queue af, queue wfq) features cannot be applied on the interface as the input direction policy. ■ only the output direction policy configured with queue (e.G. Queue ef, queue af, queue wfq)...
Page 1671
Configuring class-based queuing 1671 configuration. For the data streams with dscp domain being af11 and af21, af (assured forwarding) and minimum bandwidth 5% is defined. ■ for the data streams with dscp domain being ef, ef and minimum bandwidth 30% is specified. Before the configuration, make sure...
Page 1672
1672 c hapter 86: c ongestion m anagement # define traffic behavior, configure ef and minimum available bandwidth (bandwidth and delay guarantee also available). [routera] traffic behavior ef_behav [routera-behavior-ef_behav] queue ef bandwidth pct 30 [routera-behavior-ef_behav] quit # specify qos p...
Page 1673
Token function of qos 1673 rtp pq configuration example network requirement configure rtp queuing on the interface and set the maximum reserved bandwidth allocated for rtp priority queue to 70% of the available bandwidth. Configure rtp priority queuing on the serial port serial1/0. The starting port...
Page 1674
1674 c hapter 86: c ongestion m anagement mechanism at the underlying-layer queuing level. It can control the number of packets sent to the underlying interface queues based on the number of tokens. If ftp applies, you are recommended to set the number of tokens sent by an interface to 1. If the upp...
Page 1675: Riority
87 p riority m apping priority mapping overview when packets enter the router, the router will allocate a series of parameters such as 802. 1p priority and local priority for the packets according to its own supporting condition and corresponding rules. The local priority is defined as follows: ■ lo...
Page 1676
1676 c hapter 87: p riority m apping lp-dot1p default mapping relationship mapping relationship between port priority and local priority mapping relationship between local priority and queuing configuring priority mapping table the priority mapping table in the router can be modified as required. Fo...
Page 1677
Configuring priority mapping table 1677 configuration prerequisites new priority mapping relationship is determined. Configuration procedure follow these steps to configure priority mapping table: the 802. 1p priority mapping table is associated with the port priority trust mode. These mapping table...
Page 1678
1678 c hapter 87: p riority m apping [router-maptbl-dot1p-lp] import 4 5 export 2 [router-maptbl-dot1p-lp] import 6 7 export 3 configuring port priority the port priority is valued from 0 to 7. Users can set port priority as required. Configuration prerequisites port priority value of corresponding ...
Page 1679
Displaying and maintaining priority mapping 1679 ■ determine the priority mapping table of trusted priority. Refer to “configuring priority mapping table” on page 1676 for details. Configuration procedure follow these steps to configure port priority trust mode: configuration example network require...
Page 1680
1680 c hapter 87: p riority m apping priority mapping configuration example network example 1 network requirement ■ when processing packets, the router can select the queue to enter according to 802. 1p priority of packet; ■ use the user-defied mapping relationship as the mapping relationship as sho...
Page 1681
Priority mapping configuration example 1681 configuration procedure # enter system view system-view # enter the dot1p-lp priority mapping table view to modify mapping table parameter. [router] qos map-table dot1p-lp [router-maptbl-dot1p-lp] import 0 1 export 0 [router-maptbl-dot1p-lp] import 2 3 exp...
Page 1682
1682 c hapter 87: p riority m apping network diagram figure 473 network diagram of priority trust mode configuration procedure # enter system view system-view # configure port priority for ethernet 1/1 [router] interface ethernet 1/1 [router-ethernet1/1] qos priority 1 [router-ethernet1/1] quit # co...
Page 1683: Ongestion
88 c ongestion a voidance congestion avoidance overview excessive congestion can endanger network resources greatly, so some avoidance measures must be taken. The congestion avoidance refers to a traffic control mechanism that can monitor the occupancy status of network resources (such as the queues...
Page 1684
1684 c hapter 88: c ongestion a voidance unlike red, the random number of wred generated is based on priority. It uses ip precedence to determine the dropping policy thus the dropping probability of packets with high priority will relatively decrease. Red and wred employ the random packet dropping p...
Page 1685
Configuring wred 1685 figure 474 relation between wred and queue mechanism associating wred with wfq, the flow-based wred can be realized. Because different flow has its own queue during packet classification, the flow with small traffic always has a short queue length, so the packet dropping probab...
Page 1686
1686 c hapter 88: c ongestion a voidance ■ denominator for calculating dropping probability: serving as the denominator in the formula for calculating dropping probability. The larger the denominator, the smaller the dropping probability. Configuring wred on interface configuration prerequisites ■ d...
Page 1687
Configuring wred through wred table 1687 # enter interface view. [sysname] interface gigabitethernet 1/0 # apply wred. [sysname-gigabitethernet1/0] qos wfq # enable ip precedence-based wred. [sysname-gigabitethernet1/0] qos wred ip-precedence enable # set the low limit of the queue of the packet wit...
Page 1688
1688 c hapter 88: c ongestion a voidance c caution: this configuration is only applicable on the device installed with layer 2 ethernet interface card with the number of interfaces on it being 16 or 24. Displaying and maintaining wred after the above-mentioned configuration, you can use the display ...
Page 1689: Mpls Q
89 mpls q o s c onfiguration mpls qos overview n to understand the contents in this chapter, you should have some background knowledge related to mpls. Refer to “mpls basics configuration” on page 1311 for the description of mpls basic concepts and related configurations. The qos solution for mpls m...
Page 1690
1690 c hapter 89: mpls q o s c onfiguration ■ mpls cq. Refer to “configuring mpls cq” on page 1690 for configuration details. ■ mpls qos policy. Refer to “configuring mpls qos policy” on page 1691 for configuration details. N mpls qos configuration is only applicable on a layer 3 router interface. C...
Page 1691
Configuring mpls qos 1691 configuration example ■ configure classification rule for mpls-based cql 10, which sets the queue 1 to correspond with the exp value 1. ■ apply cql 10 on the interface ethernet1/0. Follow the steps below to perform configuration: system-view [sysname] qos cql 10 protocol mp...
Page 1692
1692 c hapter 89: mpls q o s c onfiguration mpls qos configuration example configuring qos for traffics in the same vpn network requirement as shown in figure 475 , the network is described as following: ■ both ce 1 and ce 2 belong to vpn 1. ■ the bandwidth of the pe 1-p link is 2m. ■ the bandwidth ...
Page 1693
Mpls qos configuration example 1693 n only mpls qos configuration is mentioned here. For mpls vpn configuration, see “mpls basics configuration” on page 1311 . Network diagram figure 475 network diagram for mpls qos configuration configuration procedure 1 configure pe 1 # define four classes, and ma...
Page 1694
1694 c hapter 89: mpls q o s c onfiguration [pe1-behavior-exp2] traffic behavior exp3 [pe1-behavior-exp3] remark mpls-exp 3 [pe1-behavior-exp3] traffic behavior exp4 [pe1-behavior-exp4] remark mpls-exp 4 [pe1-behavior-exp4] quit # define qos policy to specify traffic behaviors to different packet ty...
Page 1695
Mpls qos configuration example 1695 [p] qos policy queue [p-qospolicy-queue] classifier exp1 behavior af11 [p-qospolicy-queue] classifier exp2 behavior af21 [p-qospolicy-queue] classifier exp3 behavior af31 [p-qospolicy-queue] classifier exp4 behavior ef [p-qospolicy-queue] quit # apply the qos poli...
Page 1696
1696 c hapter 89: mpls q o s c onfiguration.
Page 1697: Dar C
90 dar c onfiguration n dar only applies to the packets forwarded by ip. Dar overview nowadays, internet has become the major media for enterprises to implement their businesses, which has stimulated the business-based applications. The simple mechanism that only checks ip headers in packets cannot ...
Page 1698
1698 c hapter 90: dar c onfiguration figure 476 fields of the ip datagram the protocol field in the header is 8-bit long. This field is called protocol domain. The values of protocol domain indicate the protocol type of ip packets. See the following table for values of protocol domain in the ip data...
Page 1699
Dar overview 1699 ■ more fragment bit: 0 indicates the packet is the last or only fragment, and 1 indicates there are more fragments after this one. Therefore, if the three-bit flag is 001, it means the datagram can be fragmented; if the three-bit flag is 000, it means this is the last fragment of i...
Page 1700
1700 c hapter 90: dar c onfiguration figure 479 tcp state transition the tcp protocols can be static or dynamic. The interaction between static protocols uses fixed port number, while the interaction between dynamic protocols uses the port number negotiated during the interaction process. Udp packet...
Page 1701
Dar overview 1701 ■ the header of http response message consists of status line and header. The status line consists of the http version, a space, a status code, a space, a status phrase. ■ headers of request message and response message both consist of several optional fields. The response message ...
Page 1702
1702 c hapter 90: dar c onfiguration figure 483 compound rtcp packet format as shown in the above figure, the random 32-bit prefix in the header exists only when the rtcp packet is encrypted. This is because the packet, if encrypted, no longer has the features of rtcp packet, and requires no special...
Page 1703
Dar overview 1703 dns tcp/udp 53 edonkey tcp 4662 exchange tcp 135 fasttrack tcp 1214 finger tcp 79 gnutella tcp 6346, 6347, 6348, 6349, 6355, 5634 gopher tcp/udp 70 h323 tcp 1300, 1718, 1719, 1720, 11000-11999 h323 udp 1300, 1718, 1719, 1720, 11720 imap tcp/udp 143, 220 irc tcp/udp 194 kerberos tcp...
Page 1704
1704 c hapter 90: dar c onfiguration configuring dar configuring matching rules of protocol when various policies are applied to corresponding data streams (e.G. Setting packet priority, allocating bandwidth for data streams), first, you need to classify the data streams with the dar function. Follo...
Page 1706
1706 c hapter 90: dar c onfiguration configuring dar packet statistics function with dar packet statistics function, users can timely monitor the packet number, data stream volume, historical mean rate and historical maximum rate of application protocol on each interface, thus to facilitate implemen...
Page 1707
Dar configuration examples 1707 dar configuration examples configuration requirement ■ router connects with ip 1 and ip 2 networks respectively via the interface ethernet1/0 and interface ethernet1/1. ■ match bt packets originated from ip 1 network on the interface ethernet 1/0 of the router. ■ perf...
Page 1708
1708 c hapter 90: dar c onfiguration.
Page 1709: Rame
91 f rame r elay q o s c onfiguration frame relay qos overview frame relay qos on a frame relay interface, the user can use the general qos to provide the services, such as traffic policing, traffic shaping, congestion management, and congestion avoidance. Furthermore, a frame relay network has its ...
Page 1710
1710 c hapter 91: f rame r elay q o s c onfiguration ■ excess burst size (ebs): the maximum that packet traffic of frame relay network could exceed the cbs within the interval of a tc. Upon network congestion, this part of excess traffic will be first discarded. Therefore, frame relay network does n...
Page 1711
Frame relay qos overview 1711 figure 488 fundamentals of fr class token bucket in the token bucket approach, a packet requiring traffic control is put into the token bucket for processing before transmission. If enough tokens are available in the token bucket for sending the packet, the packet will ...
Page 1712
1712 c hapter 91: f rame r elay q o s c onfiguration for example, to send an 800-byte packet, the router needs a 6400-bit token, where 6400 = 800 × 8. Given the cir of 64000 bps, the time needed to add the required tokens into the token bucket is 6400/64000 = 100 ms, that is, the tc for the packet i...
Page 1713
Frame relay qos overview 1713 frame relay packet whose backward explicit congestion notification (becn) flag bit is 1, indicating that congestion has occurred to the network, the token addition speed is decreased to cir, that is, 32 kbps, and the packet is sent at 32 kbps on the vc. Frame relay traf...
Page 1714
1714 c hapter 91: f rame r elay q o s c onfiguration and interval tc = cbs / cir allow = 125 ms. When the interval is in the range of 0 to 250ms, dte will transmit packets to dce at 64 kbps and dce will normally forward these packets at 64 kbps. When the interval is in the range of 250 to 500 ms, dt...
Page 1715
Frame relay qos overview 1715 the queuing priority, transmit the packets in the queue with low priority after those in the queue with high priority are transmitted. Frame relay virtual circuit queuing may be fifo, pq, cq, wfq, cbq and rtpq. Only rtpq can coexist with others. When frame relay traffic...
Page 1716
1716 c hapter 91: f rame r elay q o s c onfiguration configuring frame relay qos frame relay qos configuration tasks creating and configuring a frame relay class the system integrates the qos services on fr pvc into the fr class, which provides a set of flexible and complete solutions for fr traffic...
Page 1717
Configuring frame relay qos 1717 n ■ after creating the frame relay class using fr class command, the user will enter the frame relay class view under which you can configure the parameters like cir. ■ in frame relay class view, the user can configure the parameters for the qos, such as frame relay ...
Page 1718
1718 c hapter 91: f rame r elay q o s c onfiguration n ■ the function of frame relay traffic shaping is applied on the egress interfaces on a device. Usually it is applied at the dte end on a frame relay network. ■ frame relay traffic shaping does not support fast forwarding. Only when fast forwardi...
Page 1719
Configuring frame relay qos 1719 configuring frame relay congestion management frame relay congestion management includes the congestion management on the frame relay interface and the congestion management on the frame relay pvc. There are two ways to set the congestion threshold. One is to configu...
Page 1720
1720 c hapter 91: f rame r elay q o s c onfiguration n a router can support up to 10 de rule lists, and each of them can contain up to 100 de rules. Configuring frame relay queuing management configuring frame relay queuing management after the frame relay traffic shaping is enabled on a frame relay...
Page 1721
Configuring frame relay qos 1721 configuring frame relay interface queuing the user can configure these queuing types on a frame relay interface: fifo, pq, cq, wfq, cbq and rtpq. All of them are the queues owned by a general qos. For configurations of these queues, refer to “congestion management” o...
Page 1722
1722 c hapter 91: f rame r elay q o s c onfiguration divided fragments alternately. In this way, voice packets can be processed timely and smoothly and delay can be reduced. Follow these steps to configure frame relay fragmentation n ■ after configuration, associate the frame relay pvc where fragmen...
Page 1723
Frame relay qos configuration example 1723 frame relay qos configuration example frts configuration example network requirement ■ router connects to the frame relay network via the interface serial 2/0. ■ the average sending rate of the router is required to be 96 kbps, the maximum sending rate is 1...
Page 1724
1724 c hapter 91: f rame r elay q o s c onfiguration # create frame relay pvc and associate the frame relay class with the pvc. [router-serial2/0] fr dlci 16 [router-fr-dlci-serial2/0-16] fr-class 96k frame relay fragmentation configuration example network requirement router a and router b are conne...
Page 1725
Frame relay qos configuration example 1725 [routerb] interface serial 2/0 [routerb-serial2/0] link-protocol fr [routerb-serial2/0] ip address 10.1.1.1 255.0.0.0 [routerb-serial2/0] fr traffic-shaping # create dlci 16. [routerb-serial2/0] fr dlci 16 # apply the frame relay class named test1 to dlci 1...
Page 1726
1726 c hapter 91: f rame r elay q o s c onfiguration # create an fr class and apply the qos policy to it. [routera]fr class frclass [routera-fr-class-frclass] apply policy test outbound [routera-fr-class-frclass] quit # perform fr-related configuration on serial 2/1 interface. [routera] interface se...
Page 1727
Frame relay qos configuration example 1727 [routerb-qospolicy-test] classifier af11_31 behavior afwred [routerb-qospolicy-test] quit # create an fr class and apply the qos policy to it [routerb]fr class frclass [routerb-fr-class-frclass] apply policy test outbound [routerb-fr-class-frclass] quit # p...
Page 1728
1728 c hapter 91: f rame r elay q o s c onfiguration.
Page 1729: 802.1
92 802.1 x c onfiguration when configuring 802.1x, go to these sections for information you are interested in: ■ “802.1x overview” on page 1729 ■ “configuring 802.1x” on page 1740 ■ “configuring a guest vlan” on page 1743 ■ “displaying and maintaining 802.1x” on page 1743 ■ “802.1x configuration exa...
Page 1730
1730 c hapter 92: 802.1 x c onfiguration figure 498 architecture of 802.1x ■ supplicant system: a system at one end of the lan segment, which is authenticated by the authenticator system at the other end. A supplicant system is usually a user-end device and initiates 802.1x authentication through 80...
Page 1731
802.1x overview 1731 ■ the uncontrolled port is always open in both the inbound and outbound directions to allow eapol protocol frames to pass, guaranteeing that the supplicant can always send and receive authentication frames. ■ the controlled port is open to allow normal traffic to pass only when ...
Page 1732
1732 c hapter 92: 802.1 x c onfiguration figure 500 eapol frame format pae ethernet type: protocol type. It takes the value 0x888e. Protocol version: version of the eapol protocol supported by the eapol frame sender. Type: type of the eapol frame. Table 52 shows the defined types of eapol frames. Le...
Page 1733
802.1x overview 1733 figure 501 eap packet format ■ code: type of the eap packet, which can be request, response, success, or failure. An eap packet of the type of success or failure has no data field, and has a length of 4. An eap packet of the type of request or response has a data field in the fo...
Page 1734
1734 c hapter 92: 802.1 x c onfiguration message-authenticator figure 504 shows the encapsulation format of the message-authenticator attribute. The message-authenticator attribute is used to prevent access requests from being snooped during eap or chap authentication. It must be included in any pac...
Page 1735
802.1x overview 1735 figure 505 message exchange in eap relay mode 1 when a user launches the 802.1x client software and enters the registered username and password, the 802.1x client software generates an eapol-start frame and sends it to the authenticator to initiate an authentication process. 2 u...
Page 1736
1736 c hapter 92: 802.1 x c onfiguration 7 when receiving the eap-request/md5 challenge packet, the supplicant uses the offered challenge to encrypt the password part (this process is not reversible), creates an eap-response/md5 challenge packet, and then sends the packet to the authenticator. 8 aft...
Page 1737
802.1x overview 1737 figure 506 message exchange in eap termination mode different from the authentication process in eap relay mode, it is the authenticator that generates the random challenge for encrypting the user password information in eap termination authentication process. Consequently, the ...
Page 1738
1738 c hapter 92: 802.1 x c onfiguration multicasts eap-request/identity frames to the supplicant system at an interval defined by this timer. ■ supplicant timeout timer (supp-timeout): once an authenticator sends an eap-request/md5 challenge frame to a supplicant, it starts this timer. If this time...
Page 1739
802.1x overview 1739 ■ if the port link type is access, the port leaves its current vlan and joins the assigned vlan. ■ if the port link type is trunk, the assigned vlan is allowed to pass the current trunk port. The default vlan id of the port is that of the assigned vlan. ■ if the port link type i...
Page 1740
1740 c hapter 92: 802.1 x c onfiguration configuring 802.1x configuration prerequisites 802.1x provides a user identity authentication scheme. However, 802.1x cannot implement the authentication scheme solely by itself. Radius or local authentication must be configured to work with 802.1x. ■ configu...
Page 1741
Configuring 802.1x 1741 note that: ■ for 802.1x to take effect on a port, you must enable it both globally in system view and for the port in system view or ethernet interface view. ■ you can also enable 802.1x and set port access control parameters (that is, the port access control mode, port acces...
Page 1742
1742 c hapter 92: 802.1 x c onfiguration note that: ■ the 802.1x proxy detection function depends on the online user handshake function. Be sure to enable handshake before enabling proxy detection and to disable proxy detection before disabling handshake. ■ you can neither add an 802.1x-enabled port...
Page 1743
Configuring a guest vlan 1743 configuring a guest vlan configuration prerequisites ■ enable 802.1x ■ set the port access control method to portbased for the port ■ set the port access control mode to auto for the port ■ create the vlan to be specified as the guest vlan configuration procedure follow...
Page 1744
1744 c hapter 92: 802.1 x c onfiguration 802.1x configuration example network requirements ■ the access control method of macbased is required on the port to control supplicants. ■ all supplicants belong to default domain aabbcc.Net, which can accommodate up to 30 users. Radius authentication is per...
Page 1745
802.1x configuration example 1745 # add local access user localuser, enable the idle cut function, and set the idle cut interval. System-view [sysname] local-user [sysname-luser-localuser] service-type lan-access [sysname-luser-localuser] password simple localpass [sysname-luser-localuser] attribute...
Page 1746
1746 c hapter 92: 802.1 x c onfiguration [sysname] domain default enable aabbcc.Net [sysname] domain aabbcc.Net # set radius1 as the radius scheme for users of the domain and specify to use local authentication as the secondary scheme. [sysname-isp-aabbcc.Net] authentication default radius-scheme ra...
Page 1747
Guest vlan configuration example 1747 ■ authenticated supplicants are assigned to vlan5 and permitted to access the internet. Network diagrams figure 508 network diagram for guest vlan configuration figure 509 network diagram with vlan10 as the guest vlan internet update server authenticator server ...
Page 1748
1748 c hapter 92: 802.1 x c onfiguration figure 510 network diagram when the supplicant passes authentication configuration procedure # configure radius scheme 2000. System-view [sysname] radius scheme 2000 [sysname-radius-2000] primary authentication 10.11.1.1 1812 [sysname-radius-2000] primary acc...
Page 1749
Guest vlan configuration example 1749 # create vlan 10. [sysname] vlan 10 [sysname-vlan10] quit # specify port ethernet 1/3 to use vlan10 as its guest vlan. [sysname] dot1x guest-vlan 10 interface ethernet 1/1 you can use the display current-configuration or display interface ethernet 1/1 command to...
Page 1750
1750 c hapter 92: 802.1 x c onfiguration.
Page 1751: Aaa/radius/hwtacacs
93 aaa/radius/hwtacacs c onfiguration when configuring aaa/radius/hwtacacs, go to these sections for information you are interested in: ■ “aaa/radius/hwtacacs configuration overview” on page 1751 ■ “aaa/radius/hwtacacs configuration task list” on page 1760 ■ “configuring aaa” on page 1761 ■ “configu...
Page 1752
1752 c hapter 93: aaa/radius/hwtacacs c onfiguration speed and low cost, but the amount of information that can be stored is limited by the hardware. ■ remote authentication: both radius and hwtacacs protocols are supported. In this approach, the device (such as a router or switch) acts as the clien...
Page 1753
Aaa/radius/hwtacacs configuration overview 1753 introduction to radius as described previously, aaa is a management framework and can be implemented through multiple protocols. However, radius is usually used in practice. What is radius remote authentication dial-in user service (radius) is a distri...
Page 1754
1754 c hapter 93: aaa/radius/hwtacacs c onfiguration information in the authentication response message. For interaction among the host, radius client, and radius server, see figure 512 . Figure 512 basic message exchange process of radius the following is how radius operates: 1 the user enters the ...
Page 1755
Aaa/radius/hwtacacs configuration overview 1755 mechanisms, including the timer management mechanism, retransmission mechanism, and slave server mechanism. Figure 513 shows the radius packet structure. Figure 513 radius packet structure descriptions of fields are as follows: 1 the code field (1-byte...
Page 1756
1756 c hapter 93: aaa/radius/hwtacacs c onfiguration 4 the authenticator field (16-byte long) is used to authenticate the reply from the radius server, and is also used in the password hiding algorithm. There are two kinds of authenticators: request and response. 5 the attribute field carries inform...
Page 1757
Aaa/radius/hwtacacs configuration overview 1757 figure 514 segment of a radius packet containing an extended attribute introduction to hwtacacs what is hwtacacs huawei terminal access controller access control system (hwtacacs) is an enhanced security protocol based on tacacs (rfc 1492). Similar to ...
Page 1758
1758 c hapter 93: aaa/radius/hwtacacs c onfiguration figure 515 network diagram for a typical hwtacacs application basic message exchange process of hwtacacs the following takes telnet user as an example to describe how hwtacacs performs user authentication, authorization, and accounting. Figure 516...
Page 1759
Aaa/radius/hwtacacs configuration overview 1759 figure 516 basic message exchange process of hwtacacs for a telnet user 1 a user requests to access the nas. Upon receiving the request, the hwtacacs client sends a start-authentication packet to the tacacs server. 2 the hwtacacs server sends back an a...
Page 1760
1760 c hapter 93: aaa/radius/hwtacacs c onfiguration 6 the hwtacacs server sends back an authentication response indicating that the user has passed authentication. 7 the hwtacacs client sends the user authorization packet to the hwtacacs server. 8 the hwtacacs server sends back the authorization re...
Page 1761
Configuring aaa 1761 hwtacacs configuration task list configuring aaa by configuring aaa, you can provide network access service for legal users, protect the networking devices, and avoid unauthorized access and bilking. In addition, you can configure isp domains to perform aaa on accessing users. I...
Page 1762
1762 c hapter 93: aaa/radius/hwtacacs c onfiguration follow these steps to create an isp domain: n ■ you cannot delete the default isp domain unless you change it to a non-default isp domain (with the domain default disable command) first. ■ if a user enters a username without an isp domain name, th...
Page 1763
Configuring aaa 1763 authentication process neither sends authorization information to a supplicant nor triggers any accounting. You can configure aaa to use only authentication. If you do not perform any authentication configuration, the system-default isp domain uses the local authentication schem...
Page 1764
1764 c hapter 93: aaa/radius/hwtacacs c onfiguration n ■ the authentication scheme specified with the authentication default command is for all types of users and has a priority lower than that for a specific access mode. ■ with a radius authentication scheme configured, aaa accepts only the authent...
Page 1765
Configuring aaa 1765 n ■ the authorization scheme specified with the authorization default command is for all types of users and has a priority lower than that for a specific access mode. ■ radius authorization is special in that it takes effect only when the radius authorization scheme is the same ...
Page 1766
1766 c hapter 93: aaa/radius/hwtacacs c onfiguration authentication, you must use the same scheme setting for authorization and authentication; otherwise, the system will prompt you with an error message. Configuring an aaa accounting scheme for an isp domain in aaa, accounting is a separate process...
Page 1767
Configuring aaa 1767 n ■ with the accounting optional command configured, a user that will be disconnected otherwise can use the network resources even when there is no available accounting server or the communication with the current accounting server fails. ■ the accounting scheme specified with t...
Page 1768
1768 c hapter 93: aaa/radius/hwtacacs c onfiguration n ■ with the local-user password-display-mode cipher-force command configured, the password is always displayed in cipher text, regardless of the configuration of the password command. In this case, if you use the save command to save the configur...
Page 1769
Configuring radius 1769 hwtacacs authentication, the level of the commands that a user can use after logging in depends on the priority of the user, or the priority of user interface level as with other authentication methods. For an ssh user using rsa public key authentication, the commands that ca...
Page 1770
1770 c hapter 93: aaa/radius/hwtacacs c onfiguration c caution: a radius scheme can be referenced by more than one isp domain at the same time. Specifying the radius authentication/authoriz ation servers follow these steps to specify the radius authentication/authorization servers: n ■ in practice, ...
Page 1771
Configuring radius 1771 n ■ in practice, you can specify two radius servers as the primary and secondary accounting servers respectively; or specify one server to function as both. Besides, since radius uses different udp ports to receive authentication/authorization and accounting packets, the port...
Page 1772
1772 c hapter 93: aaa/radius/hwtacacs c onfiguration n the shared key configured on the device must be the same as that configured on the radius server. Setting the upper limit of radius request retransmission attempts since radius uses udp packets to carry data, the communication process is not rel...
Page 1773
Configuring radius 1773 when both the primary and secondary servers are available, the device sends request packets to the primary server. Once the primary server fails, the primary server transfers into the state of block, and the device turns to the secondary server. In this case: ■ if the seconda...
Page 1774
1774 c hapter 93: aaa/radius/hwtacacs c onfiguration n ■ some earlier radius servers cannot recognize usernames that contain an isp domain name; therefore before sending a username including a domain name to such a radius server, the device must remove the domain name. This command is thus provided ...
Page 1775
Configuring radius 1775 ■ real-time accounting interval (realtime-accounting): this timer defines the interval for performing real-time accounting of users. After this timer is set, the switch will send accounting information of online users to the radius server at the specified interval. Follow the...
Page 1776
1776 c hapter 93: aaa/radius/hwtacacs c onfiguration n if the system has no authentication scheme enabled with the accounting-on function when you execute the accounting-on enable command, you need to save the configuration and restart the device so that the command takes effect. Otherwise, the comm...
Page 1777
Configuring hwtacacs 1777 configuring hwtacacs creating a hwtacacs scheme the hwtacacs protocol is configured on a per scheme basis. Before performing other hwtacacs configurations, follow these steps to create a hwtacacs scheme and enter hwtacacs scheme view: n ■ up to 16 local hwtacacs schemes can...
Page 1778
1778 c hapter 93: aaa/radius/hwtacacs c onfiguration n ■ the ip addresses of the primary and secondary authorization servers cannot be the same. Otherwise, the configuration fails. ■ you can remove an authorization server only when no active tcp connection for sending authorization packets is using ...
Page 1779
Configuring hwtacacs 1779 setting the shared key for hwtacacs packets when using a hwtacacs server as an aaa server, you can set a key to secure the communications between the device and the hwtacacs server. The hwtacacs client and hwtacacs server use the md5 algorithm to encrypt packets exchanged b...
Page 1780
1780 c hapter 93: aaa/radius/hwtacacs c onfiguration setting timers regarding hwtacacs servers follow these steps to set timers regarding tacacs servers: n ■ for real-time accounting, a nas must transmit the accounting information of online users to the hwtacacs accounting server periodically. Note ...
Page 1781
Aaa/radius/hwtacacs configuration example 1781 displaying and maintaining radius displaying and maintaining hwtacacs aaa/radius/hwtac acs configuration example aaa for telnet/ssh users by a radius server n configuration of radius authentication, authorization, and accounting for ssh users is similar...
Page 1782
1782 c hapter 93: aaa/radius/hwtacacs c onfiguration ■ the radius server is responsible for both authentication and accounting. Its ip address is 10.1.1.1. ■ on the router, set both the shared keys for authentication and accounting packets to expert; the usernames sent to the radius containing domai...
Page 1783
Aaa/radius/hwtacacs configuration example 1783 [router-radius-rad] primary accounting 10.1.1.1 1813 [router-radius-rad] key authentication expert [router-radius-rad] key accounting expert [router-radius-rad] server-type extended [router-radius-rad] user-name-format with-domain [router-radius-rad] qu...
Page 1784
1784 c hapter 93: aaa/radius/hwtacacs c onfiguration [router] user-interface vty 0 4 [router-ui-vty0-4] authentication-mode scheme [router-ui-vty0-4] quit # create local user named telnet. [router] local-user telnet [router-luser-telnet] service-type telnet [router-luser-telnet] password simple aabb...
Page 1785
Aaa/radius/hwtacacs configuration example 1785 network diagram figure 519 configure aaa for ppp users by a tacacs server configuration procedure # configure the hwtacacs scheme. System-view [router] hwtacacs scheme hwtac [router-hwtacacs-hwtac] primary authentication 10.1.1.1 49 [router-hwtacacs-hwt...
Page 1786
1786 c hapter 93: aaa/radius/hwtacacs c onfiguration [router] interface ethernet 1/0 [router-ethernet1/0] ip address 10.1.1.2 255.255.255.0 troubleshooting aaa/radius/hwtac acs troubleshooting radius symptom1: user authentication/authorization always fails. Analysis: 1 a communication failure exists...
Page 1787
Troubleshooting aaa/radius/hwtacacs 1787 symptom3: a user is authenticated and authorized, but accounting for the user is not normal. Analysis: 1 the accounting port number is not correct. 2 configuration of the authentication/authorization server and the accounting server are not correct on the nas...
Page 1788
1788 c hapter 93: aaa/radius/hwtacacs c onfiguration.
Page 1789: Irewall
94 f irewall c onfiguration when configuring a firewall, go to these sections for information you are interested in: ■ “firewall overview” on page 1789 ■ “configuring a packet filter firewall” on page 1794 ■ “configuring an aspf” on page 1798 firewall overview a firewall blocks unauthorized accesses...
Page 1790
1790 c hapter 94: f irewall c onfiguration support for fragment filtering the current packet filter firewall supports fragment inspection and filtering. The packet filter firewall inspects the packet type (non-fragmented packet, first fragment, or non-first fragment), gets the layer 3 information of...
Page 1791
Firewall overview 1791 for untrusted sites, such protecting the network from being attacked by malicious java applets. ■ an aspf supports enhanced session logging. An aspf can record the information of each connection, including the duration, source and destination addresses of the connection, the p...
Page 1792
1792 c hapter 94: f irewall c onfiguration if a device is connected with the internal network and internet and protects servers on the internal network by means of an aspf, the device’s interface to the internal network is the internal interface and the device’s interface to the internet is the exte...
Page 1793
Firewall overview 1793 figure 521 schematic diagram of ftp detection the setup process of a ftp connection is as follows: assume that the ftp client initiates an ftp control channel connection through port 1333 to port 21 of the ftp server; as a result of negotiation, the server initiates a data cha...
Page 1794
1794 c hapter 94: f irewall c onfiguration configuring a packet filter firewall packet filter firewall configuration task list enabling the firewall function following these steps to enable the firewall function: configuring the default filtering action of the firewall the default filtering action c...
Page 1795
Configuring a packet filter firewall 1795 2 enable the ipv6 fragment inspection function after this function is enabled, if the first fragment is discarded when the ipv6 fragments of all interfaces match against ipv6 acl, all the non-first fragments will be discarded too. If not, the protocol inform...
Page 1796
1796 c hapter 94: f irewall c onfiguration fragment of each packet in order to obtain the match information of the subsequent fragments. The default mode is normal match mode. 1 configure ipv4 packet filtering on an interface: 2 configure ipv6 packet filtering on an interface ipv6 packet filtering i...
Page 1797
Configuring a packet filter firewall 1797 packet filter firewall configuration example network requirements ■ a company accesses the internet through serial 2/0 of router a, which connects the internal network through an ethernet port, ethernet 1/0. ■ the company provides www, ftp and telnet service...
Page 1798
1798 c hapter 94: f irewall c onfiguration [router-acl-adv-3001] rule permit ip source 129.1.1.1 0 [router-acl-adv-3001] rule permit ip source 129.1.1.2 0 [router-acl-adv-3001] rule permit ip source 129.1.1.3 0 [router-acl-adv-3001] rule permit ip source 129.1.1.4 0 # configure a rule to prohibit al...
Page 1799
Configuring an aspf 1799 configuring an aspf policy follow these steps to configure an aspf policy: n ■ if you enable tcp or udp detection without configuring application layer protocol detection, some packets may fail to get a response. Therefore, it is recommended that you enable application layer...
Page 1800
1800 c hapter 94: f irewall c onfiguration enabling the session logging function for aspf aspf provides an enhanced session logging function, which can record the information of each connection, including the duration, source and destination addresses of the connection, the port used by the connecti...
Page 1801
Configuring an aspf 1801 aspf configuration example network requirements ■ configure an aspf policy on router a to detect the ftp and http traffic flows passing through router a. ■ requirement: only return packets for ftp and http connections initiated by users on the internal network are permitted ...
Page 1802
1802 c hapter 94: f irewall c onfiguration [routera] acl number 2001 [routera-acl-basic-2001] rule deny source 2.2.2.2 0 [routera-acl-basic-2001] rule permit [routera-acl-basic-2001] quit # create an aspf policy that checks application layer protocols ftp and http, and set the idle timeout value for...
Page 1803: Mac A
95 mac a uthentication c onfiguration when configuring mac authentication, go to these sections for information you are interested in: ■ “mac authentication overview” on page 1803 ■ “related concepts” on page 1804 ■ “configuring mac authentication” on page 1804 ■ “displaying and maintaining mac auth...
Page 1804
1804 c hapter 95: mac a uthentication c onfiguration ■ if the type of username is fixed username, the device sends the same username and password configured locally to the radius server for authentication of each user. If the authentication succeeds, the user will be granted permission to access the...
Page 1805
Configuring mac authentication 1805 ■ the type of username and password of a local user must be consistent with that used for mac authentication. ■ all the letters in the mac address to be used as the username and password of a local user must be in lower case. ■ the service type of the local user m...
Page 1806
1806 c hapter 95: mac a uthentication c onfiguration displaying and maintaining mac authentication n when packets with the same source mac address are sent to two mac authentication-enabled ports for mac authentication simultaneously, there may be a case where mac authentication succeeds on the two ...
Page 1807
Mac authentication configuration examples 1807 # configure isp domain aabbcc.Net, and specify to perform local authentication. [device] domain aabbcc.Net [device-isp-aabbcc.Net] authentication lan-access local [device-isp-aabbcc.Net] quit # enable mac authentication globally. [device] mac-authentica...
Page 1808
1808 c hapter 95: mac a uthentication c onfiguration ■ set the offline detect timer to 180 seconds and the quiet timer to 3 minutes. Network diagram figure 525 network diagram for mac authentication using radius configuration procedure 1 enable mac authentication on the device # configure the ip add...
Page 1809
Mac authentication configuration examples 1809 [device] mac-authentication timer offline-detect 180 [device] mac-authentication timer quiet 3 [device] mac-authentication user-name-format fixed account aaa passw ord simple 123456 2 verify the configuration # display global mac authentication informat...
Page 1810
1810 c hapter 95: mac a uthentication c onfiguration.
Page 1811: Nat C
96 nat c onfiguration when configuring nat, go to these sections for information you are interested in: ■ “nat overview” on page 1811 ■ “nat configuration task list” on page 1815 ■ “configuring address translation” on page 1816 ■ “configuring internal server” on page 1818 ■ “configuring nat log” on ...
Page 1812
1812 c hapter 96: nat c onfiguration figure 526 a basic nat operation ■ nat gateway lies between the private network and the public network. ■ the internal pc (with source ip address 192.168.1.3) sends an ip packet (ip packet 1) to the external server (with source ip address 10.1.1.2) through the na...
Page 1813
Nat overview 1813 nat functionalities many-to-many nat and nat control as depicted in figure 526 , when an internal network user accesses an external network, nat uses an external or public ip address to replace the original internal ip address. In figure 526 , this address is the outbound interface...
Page 1814
1814 c hapter 96: nat c onfiguration figure 527 an napt process as illustrated in the above figure, four data packets arrive at the nat gateway. Packets 1 and 2 have the same internal address but different source port numbers. Packets 3 and 4 have different internal addresses but the same source por...
Page 1815
Nat configuration task list 1815 streaming protocol (rtsp), h.323, netmeeting 3.01, and netbios over tcp/ip (nbt). N the support for the special protocols varies by device models. Nat multiple-instance this feature allows users from different mpls vpns to access external networks through the same ou...
Page 1816
1816 c hapter 96: nat c onfiguration n the support for the nat aging-time command or for the parameters in nat alg varies with device models. Configuring address translation introduction to address translation address translation is implemented by associating an acl with an address pool (or an inter...
Page 1817
Configuring address translation 1817 you need to associate an acl with an address pool, and deal with both ip addresses and port numbers. ■ nat multiple-instance you need to configure vpn instance vpn-instance-name in the rule of an acl to specify the mpls vpn users that need address translation. Na...
Page 1818
1818 c hapter 96: nat c onfiguration configuring internal server introduction to internal server to configure an internal server, you need to map an external ip address and port to the internal server. This is done through the nat server command. Internal server configurations include: external ip a...
Page 1819
Configuring nat log 1819 function, however, can enhance network security (for supervising purpose) by keeping records of the private network users that access the external network. Enabling nat log function follow these steps to enable nat log function: exporting nat logs nat logs can be exported in...
Page 1820
1820 c hapter 96: nat c onfiguration n ■ exporting nat logs to the information center occupies storage space. This approach is recommended when the volume of nat logs is small. ■ nat logs exporting to the information center are prioritized as informational, meaning that they are ordinary information...
Page 1821
Configuring connection-limit 1821 limiting connection number means that when the number of connections initiated by a user reaches a certain upper limit, the user cannot establish new connections either until the connection number reduces to a value not greater than the predefined lower limit as the...
Page 1822
1822 c hapter 96: nat c onfiguration binding a connection-limit policy to a nat module follow these steps to bind a connection-limit policy to a nat module c caution: ■ a nat module limits user connections based on the policy bound to it. Each nat module can be bound with one policy only. ■ the glob...
Page 1823
Nat configuration example 1823 n clearing the nat log buffer implies loss of all nat logs. In general, you are not recommended to use this command. Nat configuration example nat configuration example network requirements as illustrated in figure 529 , a company accesses the internet through serial 1...
Page 1824
1824 c hapter 96: nat c onfiguration network diagram figure 529 nat network diagram configuration procedure # configure an address pool and an acl. System-view [router] nat address-group 1 202.38.160.100 202.38.160.105 [router] acl number 2001 [router-acl-basic-2001] rule permit source 10.110.10.0 0...
Page 1825
Nat configuration example 1825 [router-serial1/0] nat server protocol tcp global 202.38.160.100 ins ide 10.110.10.4 smtp exporting nat logs to the information center network requirements ■ a host in the private network accesses device b in the public network through device a, which is enabled with n...
Page 1826
1826 c hapter 96: nat c onfiguration ......Omitted...... %@250005%jul 7 04:20:04:72 2005 devicea userlog/7/nat: icmp; 192.168.1.6:768--->1.1.1.1:12288; 2.2.2.2:768; [2005/07/07 04:20:03-0000/00/00 00:00:00]; operator 8: data flow created %@250006%jul 7 04:20:10:72 2005 devicea userlog/7/nat: icmp; 1...
Page 1827
Troubleshooting nat 1827 network diagram figure 531 export nat log to log server configuration procedure n the following only lists configurations pertinent to nat logs. Configurations regarding the ip addresses of the devices and nat function are omitted here. # specify to export the nat logs of de...
Page 1828
1828 c hapter 96: nat c onfiguration denied external access to the internal network. You can use the display acl command to verify this. For details about firewall, refer to “firewall configuration” on page 1789 ..
Page 1829: Pki C
97 pki c onfiguration when configuring pki, go to these sections for information you are interested in: ■ “introduction to pki” on page 1829 ■ “pki configuration task list” on page 1832 ■ “displaying and maintaining pki” on page 1840 ■ “pki configuration examples” on page 1840 ■ “troubleshooting pki...
Page 1830
1830 c hapter 97: pki c onfiguration a ca may publish multiple crls when the number of revoked certificates is so large that publishing them in a single crl may degrade network performance. Ca policy a ca policy is a set of criteria that a ca follows in managing certificate requests and in issuing, ...
Page 1831
Introduction to pki 1831 requests, certificates, secret keys, crls and logs while providing a simple query function. Ldap provides a way of accessing and managing pki information. An ldap server stores user information and digital certificates from the ra server and provides directory navigation ser...
Page 1832
1832 c hapter 97: pki c onfiguration pki configuration task list complete the following tasks to configure pki: configuring an entity dn a certificate is a binding of a public key and a set of identity information, where the set of identity information is referred to as a pki entity distinguished na...
Page 1833
Configuring a pki domain 1833 n ■ currently, up to two entities can be created on a device. ■ windows 2000 ca server has some restrictions on the data length of a certificate request. If the entity dn in a certificate request goes beyond a certain limit, the server does not respond to the certificat...
Page 1834
1834 c hapter 97: pki c onfiguration ■ ra generally, an independent ra is in charge of certificate request management. It receives the registration request from an entity, checks its qualification, and determines whether to ask the ca to sign a digital certificate. The ra only checks the application...
Page 1835
Submitting a pki certificate request 1835 n ■ currently, up to two pki domains can be created on a device. ■ the ca name is required only when you retrieve a ca certificate. It is not used when in local certificate request. Submitting a pki certificate request when requesting a certificate, an entit...
Page 1836
1836 c hapter 97: pki c onfiguration submitting a certificate request in manual mode in manual mode, you need to retrieve a ca certificate, generate a local rsa key pair and submit a local certificate request for an entity. The goal of retrieving a ca certificate is to verify the authenticity and va...
Page 1837
Retrieving a certificate manually 1837 ■ the pki request-certificate domain configuration will not be saved in the configuration file. Retrieving a certificate manually you can download an existing ca certificate or local certificate from the ca server and save it locally. To do so, you can use two ...
Page 1838
1838 c hapter 97: pki c onfiguration configuring crl-checking-disabled pki certificate validation follow these steps to configure crl-checking-disabled pki certificate validation: n ■ the crl update period refers to the interval at which the entity downloads crls from the crl access server. The crl ...
Page 1839
Deleting a certificate 1839 n for details about the public-key local destroy rsa command, refer to “ssh2.0 configuration” on page 1919 . Deleting a certificate when a certificate requested manually is about to expire or you want to request a new certificate, you need to delete the current local cert...
Page 1840
1840 c hapter 97: pki c onfiguration displaying and maintaining pki pki configuration examples c caution: ■ the scep plug-in is required when you use the windows server as the ca. In this case, when configuring the pki domain, you need to use the certificate request from ra command to specify that t...
Page 1841
Pki configuration examples 1841 configuration procedure on the ca server, complete the following configuration: 1 configure a ca server named myca. In this example, you need to configure theses basic attributes on the ca server at first: ■ nickname: name of the trusted ca. ■ subject dn: dn informati...
Page 1842
1842 c hapter 97: pki c onfiguration [router-pki-domain-torsa] certificate request url http://4.4.4.133:4 46/c95e970f632d27be5e8cbf80e971d9c4a9a93337 # set the registration authority to ca. [router-pki-domain-torsa] certificate request from ca # specify the entity for certificate request as aaa. [ro...
Page 1843
Pki configuration examples 1843 # use the following command to view information about the local certificate acquired. Display pki certificate local domain torsa certificate: data: version: 3 (0x2) serial number: 9a96a48f 9a509fd7 05fff4df 104ad094 signature algorithm: sha1withrsaencryption issuer: c...
Page 1844
1844 c hapter 97: pki c onfiguration applying rsa digital signature in ike negotiation network requirements ■ an ipsec tunnel is set up between router a and router b to secure the data streams between host a on the subnet 10.1.1.0/24 and host b on the subnet 11.1.1.0/24. ■ router a and router b use ...
Page 1845
Pki configuration examples 1845 [routera]pki domain 1 [routera-pki-domain-1] ca identifier ca1 [routera-pki-domain-1] certificate request url http://1.1.1.100/cert srv/mscep/mscep.Dll [routera-pki-domain-1] certificate request entity en [routera-pki-domain-1] ldap-server ip 1.1.1.102 # set the regis...
Page 1846
1846 c hapter 97: pki c onfiguration # set the registration authority to ra. [routerb-pki-domain-1] certificate request from ra # configure the url for the crl distribution. This is not necessary if crl checking is disabled. [routerb -pki-domain-1] crl url ldap://2.1.1.102 [routerb-pki-domain-1] qui...
Page 1847
Pki configuration examples 1847 networking diagram figure 535 diagram for configuring a certificate attribute-based access control policy configuration procedure n ■ for detailed information about ssl configuration, refer to “ssl configuration” on page 1953 . ■ for detailed information about https c...
Page 1848
1848 c hapter 97: pki c onfiguration n ctn aabbcc [router-pki-cert-attribute-group-mygroup2] quit 3 configure the certificate attribute-based access control policy # create the certificate attribute-based access control policy of myacp and add two access control rules. [router] pki certificate acces...
Page 1849
Troubleshooting pki 1849 failed to request a local certificate symptom failed to request a local certificate. Analysis possible reasons include these: ■ the network connection is not proper. For example, the network cable may be damaged or loose. ■ no ca certificate has been retrieved. ■ the current...
Page 1850
1850 c hapter 97: pki c onfiguration.
Page 1851: Ortal
98 p ortal c onfiguration when configuring portal, go to these sections for information you are interested in: ■ “portal overview” on page 1851 ■ “portal configuration task list” on page 1857 ■ “displaying and maintaining portal” on page 1860 ■ “portal configuration examples (on routers)” on page 18...
Page 1852
1852 c hapter 98: p ortal c onfiguration ■ security authentication mechanism is added in addition to portal authentication, which intends to verify anti-virus software is installed, virus bases are updated, unauthorized software is installed, or os patches are updated on access devices; ■ compared w...
Page 1853
Portal overview 1853 ■ for portal authentication, interacting with the portal server and the authentication/accounting server for identity authentication and accounting. ■ for portal+ authentication, interacting with the portal server, the authentication/accounting server and the security policy ser...
Page 1854
1854 c hapter 98: p ortal c onfiguration c caution: ■ since the portal client is identified by ip address, to avoid authentication failure resulted from address translation, be sure that there is no device with network address translation (nat) enabled between the authentication client, access devic...
Page 1855
Portal overview 1855 the mac address of the authentication client. In the non-layer-3 authentication mode, a user is uniquely identified by the combination of its ip address and mac address because the access device can learn the mac address of the authentication client. As mentioned above, it is po...
Page 1856
1856 c hapter 98: p ortal c onfiguration 5 the access device sends an authentication acknowledgment message to the portal server. 6 the portal server sends an authentication success message to the authentication client to notify it of login success. 7 the portal server sends an authentication acknow...
Page 1857
Portal configuration task list 1857 12 the access device checks arp packets to see whether the user ip address is changed. If so, the access device notifies the portal server of the change. 13 the portal server notifies the authentication client of login success. 14 the portal server sends a user ip...
Page 1858
1858 c hapter 98: p ortal c onfiguration ■ for portal+ authentication, you need to install and configure the security policy server while ensuring that the acl configured on the access device corresponds to the acl for restricted resources and the acl for unrestricted resources on the security polic...
Page 1859
Configuring an authentication subnet 1859 n ■ if both a vlan and an interface are configured in an authentication-free rule, the interface must belong to the vlan. ■ you cannot configure two or more portal-free rules with the same filtering conditions. Otherwise, the system prompts that the rule alr...
Page 1860
1860 c hapter 98: p ortal c onfiguration configuring the name of the resource to be protected n support for this feature varies with device. The access device transfers the configured name of the resource to be protected to the portal+ client in a portal+ packet, which can be used as an additional p...
Page 1861
Portal configuration examples (on routers) 1861 portal configuration examples (on routers) portal direct authentication configuration examples network requirements ■ the router is configured with direct portal authentication. Before portal authentication, users can access only the portal server. Aft...
Page 1862
1862 c hapter 98: p ortal c onfiguration [router-radius-rs1] primary authentication 192.168.0.112 [router-radius-rs1] primary accounting 192.168.0.112 [router-radius-rs1] key authentication radius [router-radius-rs1] key accounting radius # specify that the isp domain name should not be included in ...
Page 1863
Portal configuration examples (on routers) 1863 re-dhcp authentication configuration examples network requirements ■ the router is configured with re-dhcp authentication. Users obtain ip addresses through the dhcp server. Before portal authentication, they are assigned private ip addresses. After pa...
Page 1864
1864 c hapter 98: p ortal c onfiguration ■ url: http://192.168.0.111/portal. System-view [router] portal server newpt ip 192.168.0.111 key portal port 50100 url http://192.168.0.111/portal # configure the dhcp relay agent, and enable invalid address check on the dhcp relay agent. [router] dhcp enabl...
Page 1865
Portal configuration examples (on routers) 1865 configuration procedure n ■ ip addresses are configured for devices as required and routes are available between devices before the portal feature is enabled. ■ the following only describes the major configurations of the portal authentication supporte...
Page 1866
1866 c hapter 98: p ortal c onfiguration network diagram figure 542 network diagram for portal+ direct authentication configuration procedure n ip addresses are configured for devices as required and routes are available between devices before the portal+ feature is enabled. Configure the access dev...
Page 1867
Portal configuration examples (on routers) 1867 # configure the radius scheme named “rs1” in the isp domain. [router-isp-dm1] authentication portal radius-scheme rs1 [router-isp-dm1] authorization portal radius-scheme rs1 [router-isp-dm1] accounting portal radius-scheme rs1 [router-isp-dm1] quit # c...
Page 1868
1868 c hapter 98: p ortal c onfiguration ■ the security policy server is required for portal+ authentication. Network diagram figure 543 network diagram for portal+ re-dhcp authentication configuration procedure n ■ in re-dhcp authentication mode, you must configure a public ip address pool (for exa...
Page 1869
Portal configuration examples (on routers) 1869 # configure the access device as a dhcp relay agent, and enable invalid address check on the dhcp relay agent. [router] dhcp enable [router] dhcp relay server-group 0 ip 192.168.0.112 [router] interface ethernet 1/0 [router-ethernet1/0] ip address 20.2...
Page 1870
1870 c hapter 98: p ortal c onfiguration configuration procedure n ■ ip addresses are configured for devices as required and routes are available between devices before the portal+ feature is enabled. ■ the following only describes the configuration of portal+ layer 3 authentication. For the configu...
Page 1871
Troubleshooting portal 1871 solution use the display portal server command to display the key of the portal server on the access device and use the portal server command to modify the key in system view. Or view and modify the key of the access device on the portal server to ensure their keys are co...
Page 1872
1872 c hapter 98: p ortal c onfiguration.
Page 1873: Rsh C
99 rsh c onfiguration when configuring rsh, go to these sections for information you are interested in: ■ “introduction to rsh” on page 1873 ■ “configuring rsh” on page 1873 ■ “rsh configuration example” on page 1874 introduction to rsh remote shell (rsh) allows you to execute the internal and exter...
Page 1874
1874 c hapter 99: rsh c onfiguration rsh configuration example network requirements as shown in figure 546 , the router acts as the rsh client. The remote host runs windows 2000 and has had rsh daemon service started. The requirement is to set the time of the host remotely from the router. N windows...
Page 1875
Rsh configuration example 1875 figure 548 services window 3 check for the remote shell daemon entry. If it does not exist, install it first. 4 look at the status column to check whether the remote shell daemon service is started. In this example, the service is not started yet. 5 double-click on the...
Page 1876
1876 c hapter 99: rsh c onfiguration # configure the route to the remote host. The configuration procedure is omitted. # set the time of the host remotely. Rsh 192.168.1.10 command time trying 192.168.1.10 ... Press ctrl+k to abort the current time is: 6:56:42.57 enter the new time: 12:00 12:00
Page 1877: 100
100 ips ec c onfiguration this document is organized as follows: ■ “ipsec configuration” on page 1877 ■ “ike configuration” on page 1901 when configuring ipsec, go to these sections for information you are interested in: ■ “ipsec overview” on page 1877 ■ “ipsec configuration task list” on page 1880 ...
Page 1878
1878 c hapter 100: ips ec c onfiguration ■ authentication header (ah), protocol 51: ah provides data origin authentication, data integrity, and anti-replay services. It supports message digest (md5) and secure hash algorithm (sha-1). Ah is inserted behind the ip header to ensure data integrity and a...
Page 1879
Ipsec overview 1879 encapsulation modes ipsec can work in the following two modes: ■ tunnel mode: the whole ip packet is used to calculate the ah/esp header, which will be encapsulated into a new ip packet together with the esp-encrypted data. Generally, tunnel mode is used for communication between...
Page 1880
1880 c hapter 100: ips ec c onfiguration ■ aes: advanced encryption standard, encrypts a plain text with a 128-bit, 192-bit, or 256-bit key. Aes, 3des, and des are in descending order in terms of security. Higher security means more complex implementation and lower speed. Des is enough to meet gener...
Page 1881
Configuring acls 1881 3 set the association between data flows and ipsec proposals (that is, which data flows are to be protected by using which ipsec proposals), sa negotiation mode, peer ip addresses (namely the starting/ending point of the ipsec tunnel), required keys and sa lifetime by configuri...
Page 1882
1882 c hapter 100: ips ec c onfiguration configuring an ipsec proposal an ipsec proposal defines the security parameters for ipsec sa negotiation, including the security protocol, encryption/authentication algorithms, and encapsulation mode. Following these steps to configure an ipsec proposal: n ■ ...
Page 1883
Configuring an ipsec policy 1883 mode. As for the latter, these parameters are automatically negotiated through ike. You cannot change the generation mode of an existing ipsec policy; you can only delete the policy and then re-create it with the new mode. Configuring a manual ipsec policy the ipsec ...
Page 1884
1884 c hapter 100: ips ec c onfiguration n ■ an ipsec policy can reference only one acl. If you apply multiple acls to an ipsec policy, only the last one takes effect. ■ for manual sas, an ipsec policy can reference only one ipsec proposal. To change the referenced ipsec proposal, you can only remov...
Page 1885
Configuring an ipsec policy 1885 ■ configuring an ike-dependent ipsec policy by referencing an ipsec policy template the parameters configurable for an ipsec policy template are the same as those you can configure when directly configuring an ike-dependent ipsec policy. The difference is that more p...
Page 1886
1886 c hapter 100: ips ec c onfiguration n ■ you cannot change the parameters of an ipsec policy created by referencing an ipsec policy template directly in ipsec policy view. You can perform the required changes in ipsec policy template view. ■ an ipsec policy can reference only one acl. If you app...
Page 1887
Applying an ipsec policy group to an interface 1887 applying an ipsec policy group to an interface an ipsec policy group is a collection of ipsec policies with the same name but different sequence numbers. In an ipsec policy group, an ipsec policy with a smaller sequence number has a higher priority...
Page 1888
1888 c hapter 100: ips ec c onfiguration n ■ an ipsec policy group can be bound to an encryption card either before or after it is applied to an interface. ■ an encryption card can be bound with multiple ipsec policies or ipsec policy groups. An ipsec policy or an ipsec policy group can be bound to ...
Page 1889
Configuring the ipsec session idle timeout 1889 an encryption card failure. On contrary, the encryption switch fabric and the ipsec module can backup each other. The ipsec module can automatically substitute the encryption switch fabric for ipsec processing when the encryption switch fabric fails. F...
Page 1890
1890 c hapter 100: ips ec c onfiguration displaying and maintaining ipsec ipsec configuration example example for establishing sas in manual mode network requirements ■ an ipsec tunnel is established between router a and router b to protect data flows between subnet 10.1.1.0/24 (represented by host ...
Page 1891
Ipsec configuration example 1891 network diagram figure 551 network diagram for ipsec configuration configuration procedure 1 configure router a # define an acl to permit data flows from subnet 10.1.1.0/24 to the subnet 10.1.2.0/24. System-view [routera] acl number 3101 [routera-acl-adv-3101] rule p...
Page 1892
1892 c hapter 100: ips ec c onfiguration [routera-ipsec-policy-manual-map1-10] security acl 3101 # apply the ipsec proposal. [routera-ipsec-policy-manual-map1-10] proposal tran1 # configure the remote ip address of the tunnel. [routera-ipsec-policy-manual-map1-10] tunnel remote 2.2.3.1 # configure t...
Page 1893
Ipsec configuration example 1893 # specify the security proposal as esp. [routerb-ipsec-proposal-tran1] transform esp # specify the algorithms for the proposal. [routerb-ipsec-proposal-tran1] esp encryption-algorithm des [routerb-ipsec-proposal-tran1] esp authentication-algorithm sha1 [routerb-ipsec...
Page 1894
1894 c hapter 100: ips ec c onfiguration 10.1.1.0/24 (represented by host a) and subnet 10.1.2.0/24 (represented by host b). ■ the security protocol to be used is esp, encryption algorithm is des, and authentication algorithm is sha1-hmac-96. Network diagram see figure 551 . Configuration procedure ...
Page 1895
Ipsec configuration example 1895 # apply the acl. [routera-ipsec-policy-isakmp-map1-10] security acl 3101 # apply the ike peer. [routera-ipsec-policy-isakmp-map1-10] ike-peer peer [routera-ipsec-policy-isakmp-map1-10] quit # configure the ip address of the serial interface. [routera] interface seria...
Page 1896
1896 c hapter 100: ips ec c onfiguration # create an ipsec policy, specifying to use the ike negotiation mode. [routerb] ipsec policy use1 10 isakmp # apply the acl. [routerb-ipsec-policy-isakmp-use1-10] security acl 3101 # apply the ipsec proposal. [routerb-ipsec-policy-isakmp-use1-10] proposal tra...
Page 1897
Ipsec configuration example 1897 network diagram figure 552 network diagram for employing encryption cards for ipsec services configuration procedure 1 configure router a #define an acl to permit data flows from subnet 10.1.1.0/24 to subnet 10.1.2.0/24. System-view [routera] acl number 3101 [routera...
Page 1898
1898 c hapter 100: ips ec c onfiguration [routera-ike-peer-peer] remote-address 2.2.3.1 [routera-ike-peer-peer] quit # create an ipsec policy, specifying to use the ike negotiation mode. [routera] ipsec policy map1 10 isakmp # apply the ipsec proposal. [routera-ipsec-policy-isakmp-map1-10] proposal ...
Page 1899
Ipsec configuration example 1899 # specify the encapsulation mode as tunnel. [routerb-ipsec-proposal-tran1] encapsulation-mode tunnel # specify the security protocol as esp. [routerb-ipsec-proposal-tran1] transform esp # specify the algorithms. [routerb-ipsec-proposal-tran1] esp encryption-algorithm...
Page 1900
1900 c hapter 100: ips ec c onfiguration after above configuration, ike negotiation will be triggered to set up sas when there is any traffic between subnet 10.1.1.0/24 and subnet 10.1.2.0/24. If ike negotiation succeeds and sas are set up, the traffic between the two subnets will be ipsec protected...
Page 1901: 101
101 ike c onfiguration when configuring ike, go to these sections for information you are interested in: ■ “ike overview” on page 1901 ■ “ike configuration task list” on page 1903 ■ “displaying and maintaining ike” on page 1908 ■ “ike configuration example” on page 1909 ■ “troubleshooting ike” on pa...
Page 1902
1902 c hapter 101: ike c onfiguration dh the diffie-hellman (dh) algorithm is a public key algorithm. With this algorithm, two peers can exchange some data and then use the data to calculate the shared keys, rather than transmitting the keys directly. Due to the decryption complexity, a third party ...
Page 1903
Ike configuration task list 1903 above three messages. As aggressive mode exchanges less information and features higher negotiation speed, it is better for scenarios where the requirement for identity protection is lower. For scenarios with higher requirement for identity protection, main mode is r...
Page 1904
1904 c hapter 101: ike c onfiguration configuring a name for the local security gateway if the ike negotiation initiator uses the gateway name for ike negotiation (that is, the id-type name command is configured on the initiator), the ike local-name command is required on the local device. Following...
Page 1905
Configuring an ike peer 1905 n before an isakmp sa expires, ike will negotiate a new sa to replace it. Since dh calculation in the ike negotiation takes longer time especially on low-end devices, it is recommended to set the lifetime greater than 10 minutes to prevent the update from influencing nor...
Page 1906
1906 c hapter 101: ike c onfiguration note that: ■ after modifying the configuration of an ipsec ike peer, you need to run the reset ipsec sa and reset ike sa commands to clear the original ipsec and ike sas. Otherwise, sa re-negotiation will fail. ■ if the ip address of one end of an ipsec tunnel i...
Page 1907
Configuring keepalive timers 1907 its identity to the peer, whereas the peer uses the ip address configured with the remote-name ip-address command to authenticate the initiator. Therefore, the local ip address for a device must be identical to the remote ip address configured on its peer. Configuri...
Page 1908
1908 c hapter 101: ike c onfiguration ■ the difference between dpd and keepalive is that keepalive sends query packets periodically, whereas dpd sends a query packet only when an encrypted packet is to be sent and the dpd query triggering interval expires. Following these steps to configure a dpd: d...
Page 1909
Ike configuration example 1909 ike configuration example example for configuring ike network requirements ■ an ipsec tunnel is established through ike automatic negotiation between gateways router a and router b so that host a and host b communicate securely. ■ router a is configured with an ike pro...
Page 1910
1910 c hapter 101: ike c onfiguration [routera-ike-proposal-10] sa duration 5000 2 configure router b # configure an ike peer. System-view [routerb] ike peer peer [routerb-ike-peer-peer] pre-shared-key abcde [routerb-ike-peer-peer] remote-address 1.1.1.1 with the above configuration, router a and ro...
Page 1911
Ike configuration example 1911 [routera] acl number 3101 match-order auto [routera-acl-adv-3101] rule permit ip source any destination any [routera-acl-adv-3101] quit # configure an ip address pool. [routera] ip pool 1 10.0.0.2 10.0.0.10 # configure an ike peer. [routera] ike peer peer [routera-ike-...
Page 1912
1912 c hapter 101: ike c onfiguration system-view [routerb] ike local-name routerb # configure an acl. [routerb] acl number 3101 match-order auto [routerb-acl-adv-3101] rule permit ip source any destination any [routerb-acl-adv-3101] quit # configure an ike peer. [routerb] ike peer peer [routerb-ike...
Page 1913
Ike configuration example 1913 example for configuring ipsec/ike to work with adsl network requirements deploying ipsec in combination with adsl, this example reflects a popular application of ipsec. ■ router b is connected to the dlsam access side of the public network directly through adsl as the ...
Page 1914
1914 c hapter 101: ike c onfiguration [routera-ike-peer-peer] remote-name routerb [routera-ike-peer-peer] nat traversal [routera-ike-peer-peer] quit # configure an ipsec proposal named prop. [routera] ipsec proposal prop [routera-ipsec-proposal-prop] encapsulation-mode tunnel [routera-ipsec-proposal...
Page 1915
Ike configuration example 1915 [routerb] acl number 3101 [routerb-acl-adv-3101] rule 0 permit ip source 192.168.0.0 0.0.0.255 destination 172.16.0.0 0.0.0.255 [routerb-acl-adv-3101] quit # configure an ike proposal. [routerb] ike proposal 1 [routerb-ike-proposal-1] authentication-algorithm sha [rout...
Page 1916
1916 c hapter 101: ike c onfiguration [routerb] interface dialer 0 [routerb-dialer0] link-protocol ppp [routerb-dialer0] ppp pap local-user test password simple 123456 [routerb-dialer0] ip address ppp-negotiate [routerb-dialer0] dialer user 1 [routerb-dialer0] dialer-group 1 [routerb-dialer0] dialer...
Page 1917
Troubleshooting ike 1917 drop message from a.B.C.D due to notification type invalid_id_information solution check whether the acls of the ipsec policies configured on the interfaces at both ends are compatible. It is recommended to configure the acls to mirror each other. For more information about ...
Page 1918
1918 c hapter 101: ike c onfiguration analysis when multiple devices create different ipsec tunnels early or late, a device may have multiple peers. If the device is not configured with acl rule, the peers send packets to it to set up different ipsec tunnels in different protection granularity respe...
Page 1919: 102
102 ssh2.0 c onfiguration when configuring ssh2.0, go to these sections for information you are interested in: ■ “ssh2.0 overview” on page 1919 ■ “configuring the device as an ssh server” on page 1922 ■ “configuring the device as an ssh client” on page 1928 ■ “displaying and maintaining the ssh prot...
Page 1920
1920 c hapter 102: ssh2.0 c onfiguration asymmetric key algorithm asymmetric key algorithm means that a key pair exists at both ends. The key pair consists of a private key and a public key. The public key is effective for both ends, while the private key is effective only for the local end. Asymmet...
Page 1921
Ssh2.0 overview 1921 ■ if the negotiation is successful, the server and the client go on to key and algorithm negotiation; otherwise, the server breaks the tcp connection. N all the packets involved in the above steps are transferred in plain text. Key and algorithm negotiation ■ the server and the ...
Page 1922
1922 c hapter 102: ssh2.0 c onfiguration authenticate the client, and then sends a message to inform the success or failure of the authentication. N besides password authentication and publickey authentication, ssh2.0 provides another two authentication methods ■ password-publickey: performs both pa...
Page 1923
Configuring the device as an ssh server 1923 n as a client uses either rsa or dsa algorithm for authentication and different clients may support different algorithms, the server needs to generate both rsa and dsa key pairs for successful authentication. Enabling ssh server follow these steps to enab...
Page 1924
1924 c hapter 102: ssh2.0 c onfiguration ■ if you configure a user interface to support ssh, be sure to configure the corresponding authentication method with the authentication-mode scheme command. ■ for a user interface configured to support ssh, you cannot configure the authentication-mode passwo...
Page 1925
Configuring the device as an ssh server 1925 configuring a client public key n this configuration task is only necessary for ssh users using publickey authentication. For an ssh user that uses publickey authentication to login, the server must be configured with the client rsa or dsa host public key...
Page 1926
1926 c hapter 102: ssh2.0 c onfiguration importing a client public key from a public key file follow these steps to import a public key from a public key file: configuring an ssh user this configuration allows you to create an ssh user and specify the service type and authentication method. Follow t...
Page 1927
Configuring the device as an ssh server 1927 ■ the working folder of an sftp user is subject to the user authentication method. For a user using only password authentication, the working folder is the aaa authorized one. For a user using only publickey authentication or using both the publickey and ...
Page 1928
1928 c hapter 102: ssh2.0 c onfiguration n authentication will fail if the number of authentication attempts (including both publickey and password authentication) exceeds that specified in the ssh server authentication-retries command. Configuring the device as an ssh client ssh client configuratio...
Page 1929
Configuring the device as an ssh client 1929 disable first-time authentication for successful authentication of an ssh client not supporting first-time authentication, the server host public key must be configured on the client and the public key name must be specified. Follow these steps to disable...
Page 1930
1930 c hapter 102: ssh2.0 c onfiguration displaying and maintaining the ssh protocol to do... Use the command... Remarks establish a connection between the ssh client and the server, and specify the preferred key exchange algorithm, encryption algorithms, and hmac algorithms for them establish a con...
Page 1931
Ssh server configuration example 1931 ssh server configuration example when using password authentication network requirements ■ the host (ssh client) and the router (ssh server) are directly connected through ethernet interfaces. ■ the host runs ssh2.0 client software to securely log on to the rout...
Page 1932
1932 c hapter 102: ssh2.0 c onfiguration [router] user-interface vty 0 4 [router-ui-vty0-4] authentication-mode scheme # enable the user interfaces to support ssh. [router-ui-vty0-4] protocol inbound ssh [router-ui-vty0-4] quit #create a local user named client001, and set the user command privilege...
Page 1933
Ssh server configuration example 1933 figure 560 ssh client configuration interface from the window shown in figure 561 , click open. The following ssh client interface appears. If the connection is normal, you will be prompted to enter the username (client001) and password (aabbcc), as shown in fig...
Page 1934
1934 c hapter 102: ssh2.0 c onfiguration figure 561 ssh client interface when using publickey authentication network requirements ■ the host (ssh client) and the router (ssh server) are directly connected through the ethernet interfaces. ■ the host runs ssh2.0 client software to securely log on to t...
Page 1935
Ssh server configuration example 1935 [router] interface ethernet 1/1 [router-ethernet1/1] ip address 192.168.1.40 255.255.255.0 [router-ethernet1/1] quit # set the authentication mode for the user interface to aaa. [router] user-interface vty 0 4 [router-ui-vty0 4] authentication-mode scheme #enabl...
Page 1936
1936 c hapter 102: ssh2.0 c onfiguration figure 563 generate a client key pair (1) while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar shown in figure 564 . Otherwise, the process bar stops moving and the key pair generating process is sto...
Page 1937
Ssh server configuration example 1937 figure 564 generate a client key pair (2) after the key pair is generated, click save public key to save the key in a file by entering a file name (“key.Pub” in this case). Figure 565 generate a client key pair (3).
Page 1938
1938 c hapter 102: ssh2.0 c onfiguration likewise, to save the private key, click save private key. A warning window pops up to prompt you whether to save the private key without any protection. Click yes and enter the name of the file for saving the key (“private” in this case). Figure 566 generate...
Page 1939
Ssh server configuration example 1939 select connection/ssh/auth. The following window appears. Click browse... To bring up the file selection window, navigate to the private key file and click ok. Figure 568 ssh client configuration interface (2) from the window shown in figure 569 , click open. Th...
Page 1940
1940 c hapter 102: ssh2.0 c onfiguration figure 569 ssh client interface ssh client configuration example when using password authentication network requirements as shown in figure 570 , router a (the ssh client) needs to log in to router b (the ssh server) through the ssh protocol. The username of ...
Page 1941
Ssh client configuration example 1941 [routerb] interface ethernet 1/1 [routerb-ethernet1/1] ip address 10.165.87.136 255.255.255.0 [routerb-ethernet1/1] quit # set the authentication mode for the user interfaces to aaa. [routerb] user-interface vty 0 4 [routerb-ui-vty0 4] authentication-mode scheme...
Page 1942
1942 c hapter 102: ssh2.0 c onfiguration f257523777d033bee77fc378145f2ad [routera-pkey-key-code]d716d7db9fcabb4adbf6fb4fdb0ca25c761b308ef53009f71 01f7c62621216d5a572c379a32ac290 [routera-pkey-key-code]e55b394a217da38b65b77f0185c8db8095522d1ef044b465e 8716261214a5a3b493e866991113b2d [routera-pkey-key...
Page 1943
Ssh client configuration example 1943 [routerb] interface ethernet 1/1 [routerb-ethernet1/1] ip address 10.165.87.136 255.255.255.0 [routerb-ethernet1/1] quit # set the authentication mode for the user interfaces to aaa. [routerb] user-interface vty 0 4 [routerb-ui-vty0 4] authentication-mode scheme...
Page 1944
1944 c hapter 102: ssh2.0 c onfiguration ssh2 10.165.87.136 username: client002 trying 10.165.87.136 ... Press ctrl+k to abort connected to 10.165.87.136 ... The server is not authenticated. Continue? [y/n]:y do you want to save the server public key? [y/n]:n ****************************************...
Page 1945: 103
103 sftp s ervice when configuring sftp, go to these sections for information you are interested in: ■ “sftp overview” on page 1945 ■ “configuring an sftp server” on page 1945 ■ “configuring an sftp client” on page 1946 ■ “sftp configuration example” on page 1949 sftp overview the secure file transf...
Page 1946
1946 c hapter 103: sftp s ervice configuring the sftp connection idle timeout period once the idle period of an sftp connection exceeds the specified threshold, the system automatically tears the connection down, so that a user cannot occupy a connection for nothing. Follow these steps to configure ...
Page 1947
Configuring an sftp client 1947 working with the sftp directories sftp directory operations include: ■ changing or displaying the current working directory ■ displaying files under a specified directory or the directory information ■ changing the name of a specified directory on the server ■ creatin...
Page 1948
1948 c hapter 103: sftp s ervice working with sftp files sftp file operations include: ■ changing the name of a file ■ downloading a file ■ uploading a file ■ displaying a list of the files ■ deleting a file follow these steps to work with sftp files: return to the upper-level directory cdup optiona...
Page 1949
Sftp configuration example 1949 displaying help information this configuration task is to display a list of all commands or the help information of an sftp client command, such as the command format and parameters. Follow these steps to display a list of all commands or the help information of an sf...
Page 1950
1950 c hapter 103: sftp s ervice network diagram figure 572 network diagram for sftp configuration (on routers) configuration procedure 1 configure the sftp server (router b) # generate rsa and dsa key pairs and enable the ssh server. System-view [routerb] public-key local create rsa [routerb] publi...
Page 1951
Sftp configuration example 1951 [routerb] sftp server enable # 2 configure the client (router a) # configure an ip address for interface ethernet 1/1. System-view [routera] interface ethernet 1/1 [routera-ethernet1/1] ip address 192.168.0.2 255.255.255.0 [routera-ethernet1/1] quit [routera] quit # e...
Page 1952
1952 c hapter 103: sftp s ervice -rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubkey1 drwxrwxrwx 1 noone nogroup 0 sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 sep 01 06:55 pub drwxrwxrwx 1 noone nogroup 0 sep 02 06:30 new1 # change the directory name new1 to new2 and check that the directory name...
Page 1953: 104
104 ssl c onfiguration when configuring ssl, go to these sections for information you are interested in: ■ “ssl overview” on page 1953 ■ “ssl configuration task list” on page 1954 ■ “configuring an ssl server policy” on page 1954 ■ “configuring an ssl client policy” on page 1955 ■ “displaying and ma...
Page 1954
1954 c hapter 104: ssl c onfiguration key. An ssl session can be used to establish multiple connections, reducing session negotiation cost. ■ ssl change cipher spec protocol: used for notification between a client and the server that the subsequent packets are to be protected and transmitted based o...
Page 1955
Configuring an ssl client policy 1955 n if you enable client authentication here, you must request a local certificate for the client. Configuring an ssl client policy an ssl client policy is a set of ssl parameters for a client to use when connecting to the server. An ssl client policy takes effect...
Page 1956
1956 c hapter 104: ssl c onfiguration troubleshooting ssl ssl handshake failure symptom as the ssl server, the device fails to handshake with the ssl client. Analysis ssl handshake failure may result from the following causes: ■ no ssl server certificate exists, or the certificate is not trusted. ■ ...
Page 1957: 105
105 gr o verview when configuring gr, go to these sections for information you are interested in: ■ “introduction to graceful restart” on page 1957 ■ “basic concepts in graceful restart” on page 1957 ■ “graceful restart communication procedure” on page 1958 ■ “graceful restart mechanism for several ...
Page 1958
1958 c hapter 105: gr o verview gr time gr time is the time taken for the gr restarter and the gr helper to establish a session between them. Upon detection of the down state of a neighbor, the gr helper will preserve the topology and routing information sent from the gr restarter for a period as sp...
Page 1959
Graceful restart communication procedure 1959 figure 575 restarting process for the gr restarter as illustrated in figure 575 . The gr helper detects that the gr restarter has restarted its routing protocol and assumes that it will recover within the gr time. Before the gr time expires, the gr helpe...
Page 1960
1960 c hapter 105: gr o verview figure 577 the gr restarter obtains topology and routing information from the gr helper as illustrated in figure 577 , the gr restarter obtains the necessary topology and routing information from all its neighbors through the gr sessions between them and calculates it...
Page 1961: 106
106 b ackup c enter c onfiguration when configuring the backup center, go to these sections for information you are interested in: ■ “introduction to the backup center” on page 1961 ■ “introduction to backup center settings” on page 1963 ■ “configuring interface backup” on page 1963 ■ “configuring l...
Page 1962
1962 c hapter 106: b ackup c enter c onfiguration n ■ when a dialer interface acts as the pppoe client and the pppoe session works in permanent on-line mode, it can be configured as the main interface. ■ when a bri interface is used for the isdn leased line, it can be configured as the main interfac...
Page 1963
Introduction to backup center settings 1963 figure 580 diagram for load sharing mode in load sharing mode, you can set an upper threshold called enable-threshold and a lower threshold called disable-threshold and traffic can be shared among multiple interfaces: ■ when the traffic on the main interfa...
Page 1964
1964 c hapter 106: b ackup c enter c onfiguration remains down upon expiry of the delay. If the main interface goes up before that, failover does not take place. Follow these steps to configure main/backup mode: n ■ to configure multiple backup interfaces for a main interface, you can execute the st...
Page 1965
Configuring load sharing 1965 follow these steps to associate an interface with a track object: configuring load sharing the backup center detects the data traffic on the main interface to decide whether to bring up or shut down the backup interface. Follow these steps to configure load sharing: n w...
Page 1966
1966 c hapter 106: b ackup c enter c onfiguration backup center configuration example this section provides the following two configuration examples: ■ “multi-interface backup configuration example” on page 1966 ■ “multi-interface load sharing configuration example” on page 1967 multi-interface back...
Page 1967
Backup center configuration example 1967 # on router b configure a static route to the segment 192.168.1.0/24 where router a resides. System-view [routerb] ip route-static 192.168.1.0 24 serial 2/0 [routerb] ip route-static 192.168.1.0 24 serial 2/1 [routerb] ip route-static 192.168.1.0 24 serial 2/...
Page 1968
1968 c hapter 106: b ackup c enter c onfiguration figure 582 diagram for multi-interface load sharing configuration configuration procedure 1 configure the ip address for each interface on every router. Follow figure 582 to configure the ip address and subnet mask for each interface. The configurati...
Page 1969
Backup center configuration example 1969 4 verify the configuration on router a. # display the traffic statistics for the main interface taking part in load sharing. [routera-serial2/0] display standby flow interfacename : serial2/0 flow-interval(s) : 30 lastinoctets : 139 lastoutoctets : 22033 infl...
Page 1970
1970 c hapter 106: b ackup c enter c onfiguration.
Page 1971: 107
107 vrrp c onfiguration when configuring vrrp, go to these sections for information you are interested in: ■ “introduction to vrrp” on page 1971 ■ “configuring vrrp for ipv4” on page 1979 ■ “configuring vrrp for ipv6” on page 1984 ■ “ipv4-based vrrp configuration example” on page 1987 ■ “ipv6-based ...
Page 1972
1972 c hapter 107: vrrp c onfiguration figure 583 lan networking apparently, this approach to enabling hosts on a network to communicate with external networks is easy to configure but it imposes a very high requirement of performance stability on the device acting as the gateway. A common way to im...
Page 1973
Introduction to vrrp 1973 figure 584 network diagram for vrrp as shown in figure 584 , router a, router b, and router c form a virtual router, which has its own ip address. Hosts on the ethernet use the virtual router as the default gateway. The router with the highest priority of the three routers ...
Page 1974
1974 c hapter 107: vrrp c onfiguration once a backup router finds its priority higher than that of the router acting as the master, it sends vrrp advertisements to start a new master router election in the standby group and becomes the master. Accordingly, the original master router becomes a backup...
Page 1975
Introduction to vrrp 1975 format of vrrp packets vrrp uses multicast packets. The router acting as the master sends vrrp packets periodically to declare its existence. Vrrp packets are also used for checking the parameters of the virtual router and electing the master. Ipv4-based vrrp packet format ...
Page 1976
1976 c hapter 107: vrrp c onfiguration ipv6-based vrrp packet format figure 586 ipv6-based vrrp packet format as shown in figure 586 , an ipv6-based vrrp packet consists of the following fields: ■ version: version number of the protocol, 3 for vrrpv3. ■ type: type of the vrrp packet. Only one vrrp p...
Page 1977
Introduction to vrrp 1977 while the others are the backups. The master sends vrrp advertisement packets periodically to notify the backups that it is working properly, and each of the backups starts a timer to wait for advertisement packets from the master. ■ in preemption mode, when a backup receiv...
Page 1978
1978 c hapter 107: vrrp c onfiguration figure 587 vrrp in master/backup mode at the beginning, router a is the master and therefore can forward packets to external networks, while router b and router c are backups and are thus in the state of listening. If router a fails, router b and router c will ...
Page 1979
Configuring vrrp for ipv4 1979 figure 588 vrrp in load balancing mode a router can be in multiple standby groups and hold a different priority in different group. In figure 588 , three standby groups are present: ■ standby group 1: router a is the master; router b and router c are the backups. ■ sta...
Page 1980
1980 c hapter 107: vrrp c onfiguration enabling users to ping virtual ip addresses you can configure whether the master router responds to the received icmp echo requests, that is, whether the virtual ip address of a standby group can be successfully pinged. Follow these steps to enable a user to su...
Page 1981
Configuring vrrp for ipv4 1981 c caution: you should configure this function before creating a standby group. Otherwise, you cannot modify the mapping between the virtual ip address and the mac address. Creating standby group and configuring virtual ip address you need to configure a virtual ip addr...
Page 1982
1982 c hapter 107: vrrp c onfiguration segment that the interface ip address belongs to, the state of the standby group is always initialize though you can perform the configuration successfully, that is, vrrp does not take effect in this case. Configuring router priority, preemption mode and tracki...
Page 1983
Configuring vrrp for ipv4 1983 ■ the priority of a device is restored automatically if the state of the interface under tracking changes from down to up. ■ the priority of a device is restored automatically if the state of a track object changes from negative to positive. Configuring vrrp packet att...
Page 1984
1984 c hapter 107: vrrp c onfiguration configuring vrrp for ipv6 vrrp for ipv6 configuration task list complete these tasks to configure vrrp for ipv6: enabling users to ping virtual ipv6 addresses you can configure whether the master router responds to the received icmpv6 echo requests, that is, wh...
Page 1985
Configuring vrrp for ipv6 1985 when an ip address owner exists in a standby group, if you associate the virtual ipv6 address with the virtual mac address, two mac addresses are associated with an ipv6 address. In this case, you can associate the virtual ipv6 address of the standby group with the rea...
Page 1986
1986 c hapter 107: vrrp c onfiguration ■ a standby group is removed after you remove all the virtual ipv6 addresses in it. In addition, configurations on that standby group no longer take effect. Configuring router priority, preemption mode and interface tracking configuration prerequisites before c...
Page 1987
Ipv4-based vrrp configuration example 1987 you may configure different authentication modes and authentication keys for the standby groups on an interface. However, the members of the same standby group must use the same authentication mode and authentication key. Factors like excessive traffic or d...
Page 1988
1988 c hapter 107: vrrp c onfiguration network diagram figure 589 network diagram for single vrrp standby group configuration configuration procedure 1 configure router a system-view [routera] interface ethernet 1/0 [routera-ethernet1/0] ip address 202.38.160.1 255.255.255.0 # create standby group 1...
Page 1989
Ipv4-based vrrp configuration example 1989 [routera-ethernet1/0] display vrrp verbose ipv4 standby information: run method : virtual-mac virtual ip ping : enable interface : ethernet1/0 vrid : 1 adver. Timer : 1 admin status : up state : master config pri : 110 run pri : 110 preempt mode : yes delay...
Page 1990
1990 c hapter 107: vrrp c onfiguration vrrp interface tracking configuration example network requirements ■ host a needs to access host b on the internet, using 202.38.160.111/24 as its default gateway. ■ router a and router b belong to standby group 1 with the virtual ip address of 202.38.160.111. ...
Page 1991
Ipv4-based vrrp configuration example 1991 [routera-ethernet1/0] vrrp vrid 1 timer advertise 5 # set router a to work in preemption mode. The preemption delay is five seconds. [routera-ethernet1/0] vrrp vrid 1 preempt-mode timer delay 5 # set the interface to be tracked. [routera-ethernet1/0] vrrp v...
Page 1992
1992 c hapter 107: vrrp c onfiguration [routerb-ethernet1/0] display vrrp verbose ipv4 standby information: run method : virtual-mac virtual ip ping : enable interface : ethernet1/0 vrid : 1 adver. Timer : 5 admin status : up state : backup config pri : 100 run pri : 100 preempt mode : yes delay tim...
Page 1993
Ipv4-based vrrp configuration example 1993 router b becomes the master and packets sent from host a to host b are forwarded by router b. Multiple vrrp standby groups configuration example network requirements ■ in the segment 202.38.160.0/24, some hosts use 202.38.160.111/24 as their default gateway...
Page 1994
1994 c hapter 107: vrrp c onfiguration # create standby group 1. System-view [routerb] interface ethernet 1/0 [routerb-ethernet1/0] ip address 202.38.160.2 255.255.255.0 # create standby group 1 and configure its virtual ip address as 202.38.160.111. [routerb-ethernet1/0] vrrp vrid 1 virtual-ip 202....
Page 1995
Ipv6-based vrrp configuration example 1995 auth type : none virtual ip : 202.38.160.111 master ip : 202.38.160.1 interface : ethernet1/0 vrid : 2 adver. Timer : 1 admin status : up state : master config pri : 110 run pri : 110 preempt mode : yes delay time : 0 auth type : none virtual ip : 202.38.16...
Page 1996
1996 c hapter 107: vrrp c onfiguration network diagram figure 592 network diagram for single vrrp standby group configuration configuration procedure 1 configure router a system-view [routera] ipv6 [routera] interface ethernet 1/0 [routera-ethernet1/0] ipv6 address fe80::1 link-local [routera-ethern...
Page 1997
Ipv6-based vrrp configuration example 1997 [routerb-ethernet1/0] undo ipv6 nd ra halt 3 verify the configuration after the configuration, host b can be pinged through on host a. You can use the display vrrp ipv6 command to verify the configuration. # display detailed information of standby group 1 o...
Page 1998
1998 c hapter 107: vrrp c onfiguration preempt mode : yes delay time : 0 auth type : none virtual ip : fe80::10 virtual mac : 0000-5e00-0201 master ip : fe80::2 the above information indicates that if router a fails, router b becomes the master, and packets sent from host a to host b are forwarded b...
Page 1999
Ipv6-based vrrp configuration example 1999 [routera-ethernet1/0] vrrp ipv6 vrid 1 priority 110 # set the authentication mode of standby group 1 to simple and authentication key to hello. [routera-ethernet1/0] vrrp ipv6 vrid 1 authentication-mode simple hello # set the interval for router a to send v...
Page 2000
2000 c hapter 107: vrrp c onfiguration preempt mode : yes delay time : 5 auth type : simple text key : hello track if : ethernet1/1 pri reduced : 30 virtual ip : fe80::10 virtual mac : 0000-5e00-0201 master ip : fe80::1 # display detailed information of standby group 1 on router b. [routerb-ethernet...
Page 2001
Ipv6-based vrrp configuration example 2001 config pri : 100 run pri : 100 preempt mode : yes delay time : 5 auth type : simple text key : hello virtual ip : fe80::10 virtual mac : 0000-5e00-0201 master ip : fe80::2 the above information indicates that if the interface ethernet 1/1 on router a is not...
Page 2002
2002 c hapter 107: vrrp c onfiguration [routera-ethernet1/0] vrrp ipv6 vrid 1 priority 110 # create standby group 2 set its virtual ip address to fe80::20. [routera-ethernet1/0] vrrp ipv6 vrid 2 virtual-ip fe80::20 link-local 2 configure router b system-view [routerb] ipv6 [routerb] interface ethern...
Page 2003
Troubleshooting vrrp 2003 run method : virtual-mac virtual ip ping : enable interface : ethernet1/0 vrid : 1 adver. Timer : 100 admin status : up state : backup config pri : 100 run pri : 100 preempt mode : yes delay time : 0 auth type : none virtual ip : fe80::10 master ip : fe80::1 interface : eth...
Page 2004
2004 c hapter 107: vrrp c onfiguration ■ if it lasts long, you must ensure that these masters can receive vrrp packets and the packets received are legitimate. Solution: ping between these masters, and do the following: ■ if the ping fails, check network connectivity. ■ if the ping succeeds, check t...
Page 2005: 108
108 d evice m anagement n there are many types of storage media such as flash, compact flash (cf), universal serial bus (usb), and hard disk. Different devices support different types of storage device. Flash is exemplified in this document. File names in this document comply with the following rule...
Page 2006
2006 c hapter 108: d evice m anagement configuring device management registering the software n the support for this feature and the trial period vary with devices. Software register is provided on the device to protect the authorized users’ legal rights to use the software. Trial period is set on t...
Page 2007
Configuring device management 2007 c caution: ■ the precision of the rebooting timer is 1 minute. One minute before the rebooting time, the device will prompt “reboot in one minute” and will reboot in one minute. ■ the execution of the reboot, schedule reboot at, and schedule reboot delay commands c...
Page 2008
2008 c hapter 108: d evice m anagement n restart the device to validate the upgraded boot rom. Hot swapping of a card to install a hot-swapping-supporting card you can directly insert it into a slot. Follow these steps to remove a hot-swapping-supporting card when it is running. N this command is su...
Page 2009
Configuring device management 2009 configuring alarm buzzer you can enable the alarm buzzer function of the router. In this case, when the temperature of the card on the router is higher than the upper threshold, the buzzer sounds to notify you about the problem. Follow these steps to configure the ...
Page 2010
2010 c hapter 108: d evice m anagement c caution: a confirmation is required when you execute this command. If you fail to make a confirmation within 30 seconds or enter “n” to cancel the operation, the command will not be executed. Displaying and maintaining device management configuration n only u...
Page 2011
Device management configuration example 2011 ■ user can log in to the device via telnet to perform operations on device (that is, download the application program from ftp server and remotely upgrade device through command lines). Make sure that a route exists between user and device. Network diagra...
Page 2012
2012 c hapter 108: d evice m anagement password: 230 logged in successfully [ftp] # download the aaa.Bin program on ftp server to the flash of the device. [ftp] get aaa.Bin # clear the ftp connection and return to user view. [ftp] quit # reboot the device. The application program is upgraded now. Re...
Page 2013: 109
109 nqa o verview when configuring nqa, go to these sections for information you are interested in: ■ “nqa overview” on page 2013 ■ “nqa configuration task list” on page 2016 ■ “configuring the nqa server” on page 2016 ■ “enabling the nqa client” on page 2017 ■ “creating an nqa test group” on page 2...
Page 2014
2014 c hapter 109: nqa o verview supporting the collaboration function collaboration is implemented by establishing collaboration entries to monitor the detection results of the current test group. If the number of consecutive probe failures reaches a certain limit, nqa’s collaboration with other mo...
Page 2015
2015 a trap contains destination ip address, operation status, minimum and maximum round trip time (rtt), probes sent, and time when the last probe is performed successfully. You can trace network running status with traps. Basic concepts of nqa test group nqa can test multiple protocols. A test gro...
Page 2016
2016 c hapter 109: nqa o verview nqa test operation after you create a test group and enter the test group view, you can configure related test parameters. Test parameters vary with the test type. For details, see the configuration procedure below. To perform an nqa test successfully, perform the fo...
Page 2017
Enabling the nqa client 2017 originated by the nqa client by listening to the packets from the specified destination address and port number. Follow these steps to configure the nqa server: enabling the nqa client configurations on the nqa client take effect only when the nqa client is enabled. Foll...
Page 2018
2018 c hapter 109: nqa o verview to do... Use the command... Remarks enter system view system-view - enter nqa test group view nqa entry admin-name operation-tag - configure the test type as icmp-echo and enter test type view type icmp-echo required configure the destination address for a test opera...
Page 2019
Configuring an nqa test group 2019 configuring the dhcp test the dhcp test is mainly used to test the existence of a dhcp server on the network as well as the time necessary for the dhcp server to respond to a client request and assign an ip address to the client. Configuration prerequisites before ...
Page 2020
2020 c hapter 109: nqa o verview the ftp server. For the ftp server configuration, refer to “ftp configuration” on page 2105. Configuring the ftp test follow these steps to configure the ftp test: configuring the http test the http test is used to test the connection with a specified http server and...
Page 2021
Configuring an nqa test group 2021 configuring the http test follow these steps to configure the http test: n the tcp port number for the http server must be 80 in an http test. Otherwise, the test will fail. Configuring the udp-jitter test n you are not recommended to perform an nqa udp-jitter test...
Page 2022
2022 c hapter 109: nqa o verview ■ the source port sends packets at regular intervals to the destination port. ■ the destination port affixes a time stamp to each packet that it receives and then sends it back to the source port. ■ upon receiving the packet, the source port calculates the delay jitt...
Page 2023
Configuring an nqa test group 2023 n the number of probes made in a udp-jitter test depends on the probe count command, while the number of probe packets sent in each probe depends on the probe packet-number command. Configuring the snmp test the snmp query test is used to test the time the nqa clie...
Page 2024
2024 c hapter 109: nqa o verview configuring the tcp test n you are not recommended to perform an nqa tcp test on ports from 1 to 1023 (known ports). Otherwise, the nqa test will fail or the corresponding services of this port will be unavailable. The tcp test is used to test the tcp connection betw...
Page 2025
Configuring an nqa test group 2025 configuring the udp-echo test n you are not recommended to perform an nqa udp test on ports from 1 to 1023 (known ports). Otherwise, the nqa test will fail or the corresponding services of this port will be unavailable. The udp-echo test is used to test the roundtr...
Page 2026
2026 c hapter 109: nqa o verview configuring the dlsw test the dlsw test is used to test the response time of the dlsw device. Configuration prerequisites enable the dlsw function on the peer device before dlsw test. For the configuration of dlsw, refer to “dlsw configuration” on page 211. Configuri...
Page 2027
Configuring the collaboration function 2027 configuring the collaboration function collaboration is implemented by establishing collaboration entries to monitor the detection results of the current test group. If the number of consecutive probe failures reaches the threshold, the configured action i...
Page 2028
2028 c hapter 109: nqa o verview configuration prerequisites before configuring trap delivery, you need to configure the destination address of the trap message with the snmp-agent target-host command to create an nqa test group and related parameters. For the configuration of the snmp-agent target-...
Page 2029
Scheduling an nqa test group 2029 scheduling an nqa test group with this configuration, you can set the start time and time period for a test group to perform the test and start the test. Configuration prerequisites before scheduling an nqa test group, make sure: ■ test parameters corresponding to a...
Page 2030
2030 c hapter 109: nqa o verview c caution: after an nqa test group is scheduled, you cannot enter the test group view or test type view. Displaying and maintaining nqa nqa configuration examples icmp-echo test configuration example network requirements use the nqa icmp function to test whether the ...
Page 2031
Nqa configuration examples 2031 extend results: packet lost in test: 0% failures due to timeout: 0 failures due to disconnect: 0 failures due to no connection: 0 failures due to sequence error: 0 failures due to internal error: 0 failures due to other errors: 0 dhcp test configuration example networ...
Page 2032
2032 c hapter 109: nqa o verview username is admin, the login password is systemtest, and the file to be transferred to the ftp server is config.Txt. Network diagram figure 600 network diagram for ftp configuration procedure # create an ftp test group and configure related test parameters. System-vi...
Page 2033
Nqa configuration examples 2033 network diagram figure 601 network diagram for the http test configuration procedure # create an http test group and configure related test parameters. System-view [devicea] nqa entry admin test [devicea-nqa-admin-test] type http [devicea-nqa-admin-test-http] destinat...
Page 2034
2034 c hapter 109: nqa o verview configuration procedure 1 configure device b. # enable the nqa server and configure the listening ip address as 10.2.2.2 and port number as 9000. System-view [deviceb] nqa server enable [deviceb] nqa server udp-echo 10.2.2.2 9000 2 configure device a. # create a udp-...
Page 2035
Nqa configuration examples 2035 snmp test configuration example network requirements use the nqa snmp query function to test the time it takes device a to send an snmp query packet to the snmp agent and receive a response packet. Network diagram figure 603 network diagram for snmp test configuration...
Page 2036
2036 c hapter 109: nqa o verview tcp test configuration example network requirements use the nqa tcp function to test the time for establishing a tcp connection between the local port (device a) and the specified destination port (device b). The port number used is 9000. Network diagram figure 604 n...
Page 2037
Nqa configuration examples 2037 udp-echo test configuration example network requirements use the nqa udp-echo function to test the setup time for the udp connection between the local port (device a) and the specified destination port (device b). The port number is 8000. Network diagram figure 605 ne...
Page 2038
2038 c hapter 109: nqa o verview dlsw test configuration example network requirements use the nqa dlsw function to test the response time of the dlsw device. Network diagram figure 606 network diagram for the dlsw test configuration procedure # create a dlsw test group and configure related test par...
Page 2039: 110
110 n et s tream c onfiguration when configuring netstream, go to these sections for information you are interested in: ■ “netstream overview” on page 2039 ■ “configuring netstream statistics” on page 2041 ■ “configuring netstream aggregation statistics” on page 2041 ■ “configuring attributes of net...
Page 2040
2040 c hapter 110: n et s tream c onfiguration n xlog network log audit system (xlog) provides solutions for administrators to audit users’ logs through networking with network devices such as routers and switches. Xlog supports logs such as nat, flow, dig and netstreamv5. Introduction to netstream ...
Page 2041
Netstream configuration task list 2041 netstream configuration task list configuring netstream statistics configuration prerequisites before configuring this function, you must configure the netstream interface binding function. Configuring netstream statistics configuring netstream aggregation stat...
Page 2042
2042 c hapter 110: n et s tream c onfiguration configuring attributes of netstream udp packets configuring attributes of netstream udp packets you may configure the source interface, destination address, and destination port number for netstream udp packets, where the address of the source interface...
Page 2043
Configuring netstream statistics aging 2043 configuring netstream statistics aging introduction to netstream statistics aging in actual networking environments, enormous stream statistics may be produced in a very short time. To accommodate latest stream statistics, a mechanism called aging was intr...
Page 2044
2044 c hapter 110: n et s tream c onfiguration netstream configuration example configuring netstream network requirements configure netstream on router a to collect statistics in the inbound direction of interface ethernet 1/0 and in the outbound direction of interface ethernet 1/1 and sends the res...
Page 2045
Netstream configuration example 2045 setting to export version 5 and version 8 packets network requirements configure netstream on router a, set to export netstream cache entries in version 5 packets, and configure five aggregation modes. Version 5 packets are exported to port 5000 of nsc 3.1.1.2/16...
Page 2046
2046 c hapter 110: n et s tream c onfiguration [routera] ip netstream max-entry 5000 # configure the destination address, destination port, and source address for version 5 udp packets. [routera] ip netstream export host 3.1.1.2 5000 [routera] ip netstream export source interface ethernet 1/0 # conf...
Page 2047
Netstream configuration example 2047 # configure interface ethernet 1/1. [routerb] interface ethernet 1/1 [routerb-ethernet1/1] ip address 2.1.1.1 255.255.0.0 [routerb-ethernet1/1] quit # configure bgp. [routerb] bgp 150 [routerb-bgp] peer 1.1.1.1 as-number 100 [routerb-bgp] peer 2.1.1.2 as-number 2...
Page 2048
2048 c hapter 110: n et s tream c onfiguration.
Page 2049: 111
111 ntp c onfiguration when configuring ntp, go to these sections for information you are interested in: ■ “ntp overview” on page 2049 ■ “configuring the operation modes of ntp” on page 2055 ■ “configuring the local clock as a reference source” on page 2058 ■ “configuring optional parameters of ntp”...
Page 2050
2050 c hapter 111: ntp c onfiguration ■ for increment backup between a backup server and clients, timekeeping must be synchronized between the backup server and all the clients. Advantages of ntp: ■ ntp uses a stratum to describe the clock precision, and is able to synchronize time among all devices...
Page 2051
Ntp overview 2051 ■ when this ntp message arrives at device b, it is timestamped by device b. The timestamp is 11:00:01 am (t 2 ). ■ when the ntp message leaves device b, device b timestamps it. The timestamp is 11:00:02 am (t 3 ). ■ when device a receives the ntp message, the local time of device a...
Page 2052
2052 c hapter 111: ntp c onfiguration figure 611 clock synchronization message format main fields are described as follows: ■ li: 2-bit leap indicator. When set to 11, it warns of an alarm condition (clock unsynchronized); when set to any other value, it is not to be processed by ntp. ■ vn: 3-bit ve...
Page 2053
Ntp overview 2053 ■ receive timestamp: the local time at which the request arrived at the service host. ■ transmit timestamp: the local time at which the reply departed the service host for the client. ■ authenticator: authentication information. Operation modes of ntp devices running ntp can implem...
Page 2054
2054 c hapter 111: ntp c onfiguration active); the device that receives this message automatically enters the symmetric passive mode and sends a reply, with the mode field in the message set to 2 (symmetric passive). By exchanging messages, the symmetric peers mode is established between the two dev...
Page 2055
Configuring the operation modes of ntp 2055 to the default ntp multicast address 224.0.1.1, with the mode field in the messages set to 5 (multicast mode). Clients listen to the multicast messages from servers. After a client receives the first multicast message, the client and the server start to ex...
Page 2056
2056 c hapter 111: ntp c onfiguration upon the receipt of a message, rather than creating an association (static or dynamic). In the symmetric mode, static associations will be created at the symmetric-active peer side, and dynamic associations will be created at the symmetric-passive peer side; in ...
Page 2057
Configuring the operation modes of ntp 2057 modes of ntp” on page 2055 to enable ntp; otherwise, a symmetric-passive peer will not process ntp packets from a symmetric-active peer. ■ in the ntp-service unicast-peer command, ip-address must be a host address, rather than a broadcast address, a multic...
Page 2058
2058 c hapter 111: ntp c onfiguration configuring ntp multicast mode the multicast server periodically sends ntp multicast messages to multicast clients, which send replies after receiving the messages and synchronize their local clocks. .For devices working in the multicast mode, you need to config...
Page 2059
Configuring optional parameters of ntp 2059 n in this command, ip-address must be 127.127.1.U, where u ranges 0 to 3, representing the ntp process id. Configuring optional parameters of ntp configuring the interface to send ntp messages after you specify the interface used to send ntp messages, the ...
Page 2060
2060 c hapter 111: ntp c onfiguration ■ query: control query permitted. This level of right permits the peer device to perform control query to the ntp service on the local device but does not permit the peer device to synchronize its clock to the local device. The so-called “control query” refers t...
Page 2061
Configuring ntp authentication 2061 key. Namely, the ntp-service authentication enable command must work together with the ntp-service authentication-keyid command and the ntp-service reliable authentication-keyid command. Otherwise, the ntp authentication function cannot be normally enabled. ■ for ...
Page 2062
2062 c hapter 111: ntp c onfiguration configuring ntp authentication for a server follow these steps to configure ntp authentication for a server: n the procedure of configuring ntp authentication on a server is the same as that on a client, and the same authentication key must be configured on both...
Page 2063
Ntp configuration examples 2063 ■ device b works in the server/client mode and device a is to be used as the ntp server of device b, with device b as the client. Network diagram figure 616 network diagram for ntp server/client mode configuration configuration procedure 1 configuration on device a: #...
Page 2064
2064 c hapter 111: ntp c onfiguration as shown above, device b has been synchronized to device a, and the clock stratum level of device b is 3, while that of device a is 2. # view the ntp session information of device b, which shows that an association has been set up between device b and device a. ...
Page 2065
Ntp configuration examples 2065 # specify the local clock as the reference source, with the stratum level of 1. System-view [devicec] ntp-service refclock-master 1 # configure device b as a symmetric peer after local synchronization. [devicec] ntp-service unicast-peer 3.0.1.32 in the step above, dev...
Page 2066
2066 c hapter 111: ntp c onfiguration network diagram figure 618 network diagram for ntp broadcast mode configuration configuration procedure 1 configuration on router c: # specify the local clock as the reference source, with the stratum level of 2. System-view [routerc] ntp-service refclock-master...
Page 2067
Ntp configuration examples 2067 [routerd] display ntp-service status clock status: synchronized clock stratum: 3 reference clock id: 3.0.1.31 nominal frequency: 64.0000 hz actual frequency: 64.0000 hz clock precision: 2^7 clock offset: 0.0000 ms root delay: 31.00 ms root dispersion: 8.31 ms peer dis...
Page 2068
2068 c hapter 111: ntp c onfiguration configuration procedure 1 configuration on router c: # specify the local clock as the reference source, with the stratum level of 2. System-view [routerc] ntp-service refclock-master 2 # configure router c to work in the multicast server mode and send multicast ...
Page 2069
Ntp configuration examples 2069 because router a and router c are on different subnets, you must enable igmp on router b before router a can receive multicast messages from router c. # enable ip multicast routing and igmp. System-view [routerb] multicast routing-enable [routerb] interface ethernet 1...
Page 2070
2070 c hapter 111: ntp c onfiguration n refer to “igmp configuration” on page 1115 for how to configure igmp. Configuring ntp server/client mode with authentication network requirements ■ the local clock of device a is to be configured as a reference source, with the stratum level of 2. ■ device b w...
Page 2071
Ntp configuration examples 2071 [devicea] ntp-service authentication enable # set an authentication key. [devicea] ntp-service authentication-keyid 42 authentication-mode md5 anicekey # specify the key as key as a trusted key. [devicea] ntp-service reliable authentication-keyid 42 # view the ntp sta...
Page 2072
2072 c hapter 111: ntp c onfiguration network diagram figure 621 network diagram for configuration of ntp broadcast mode with authentication configuration procedure 1 configuration on router c: # specify the local clock as the reference source, with the stratum level of 3. System-view [routerc] ntp-...
Page 2073
Ntp configuration examples 2073 [routerd] display ntp-service status clock status: synchronized clock stratum: 4 reference clock id: 3.0.1.31 nominal frequency: 64.0000 hz actual frequency: 64.0000 hz clock precision: 2^7 clock offset: 0.0000 ms root delay: 31.00 ms root dispersion: 8.31 ms peer dis...
Page 2074
2074 c hapter 111: ntp c onfiguration network diagram figure 622 network diagram for mpls vpn time synchronization configuration configuration procedure n prior to performing the following configuration, be sure you have completed mpls vpn-related configurations and make sure of the reachability bet...
Page 2075
Ntp configuration examples 2075 [ce3] display ntp-service status clock status: synchronized clock stratum: 2 reference clock id: 10.1.1.1 nominal frequency: 63.9100 hz actual frequency: 63.9100 hz clock precision: 2^7 clock offset: 0.0000 ms root delay: 47.00 ms root dispersion: 0.18 ms peer dispers...
Page 2076
2076 c hapter 111: ntp c onfiguration reference time: 02:44:01.200 utc jan 1 2001(bdfa6d71.33333333) [pe2] display ntp-service sessions source reference stra reach poll now offset delay disper ************************************************************************** [12345]10.1.1.2 locl 1 1 64 29 -...
Page 2077: 112
112 rmon c onfiguration when configuring rmon, go to these sections for information you are interested in: ■ “rmon overview” on page 2077 ■ “configuring rmon” on page 2079 ■ “displaying and maintaining rmon” on page 2081 ■ “rmon configuration example” on page 2081 rmon overview this section covers t...
Page 2078
2078 c hapter 112: rmon c onfiguration information but four groups of information, alarm, event, history, and statistics, in most cases. The device adopts the second way. By using rmon agents on network monitors, an nms can obtain information about traffic size, error statistics, and performance sta...
Page 2079
Configuring rmon 2079 n if the count result overpasses the same threshold multiple times, only the first one can cause an alarm event. That is, the rising alarm and falling alarm are alternate. History group the history group controls the periodic statistical sampling of data, such as bandwidth util...
Page 2080
2080 c hapter 112: rmon c onfiguration n ■ two entries with the same configuration cannot be created. If the parameters of a newly created entry are identical to the corresponding parameters of an existing entry, the system considers their configurations the same and the creation fails. Refer to tab...
Page 2081
Displaying and maintaining rmon 2081 displaying and maintaining rmon n if the alarm entry corresponding the configuration command is invalid (that is, the entry in the display rmon event command is invalid), the configuration command is not displayed in the configuration file, that is, the configura...
Page 2082
2082 c hapter 112: rmon c onfiguration network diagram figure 623 network diagram for rmon configuration procedure # configure the snmp agent, keeping its write/read communities and version consistent with those configured on the nms. System-view [sysname] snmp-agent [sysname] snmp-agent community r...
Page 2083
Rmon configuration example 2083 # display statistics for interface ethernet 1/0. Display rmon statistics ethernet 1/0 statistics entry 1 owned by user1-rmon is valid. Interface : ethernet1/0 etherstatsoctets : 57329 , etherstatspkts : 455 etherstatsbroadcastpkts : 53 , etherstatsmulticastpkts : 353 ...
Page 2084
2084 c hapter 112: rmon c onfiguration.
Page 2085: 113
113 snmp c onfiguration when configuring snmp, go to these sections for information you are interested in: ■ “snmp overview” on page 2085 ■ “snmp configuration” on page 2085 ■ “trap configuration” on page 2088 ■ “displaying and maintaining snmp” on page 2090 ■ “snmp configuration example” on page 20...
Page 2086
2086 c hapter 113: snmp c onfiguration ■ get operation: nms gets the value of a certain variable of agent through this operation. ■ set operation: nms can reconfigure certain values in the agent mib (management information base) to make the agent perform certain tasks by means of this operation. ■ t...
Page 2087
Snmp configuration 2087 follow these steps to configure snmpv1 and snmpv2c: to do... Use the command... Remarks enter system view system-view - enable snmp agent snmp-agent optional disabled by default you can enable snmp agent through this command or any commands that begin with “snmp-agent”. Confi...
Page 2088
2088 c hapter 113: snmp c onfiguration c caution: the validity of a usm user depends on the switch fabric id of the snmp agent. If the switch fabric id used for usm user creation is not identical to the current switch fabric id, the usm user is invalid. Trap configuration snmp agent sends trap messa...
Page 2089
Trap configuration 2089 c caution: to enable an interface to send snmp trap packets when its state changes, you need to enable the link up/down trap packet transmission function on an interface and globally. Use the enable snmp trap updown command to enable this function on an interface, and use the...
Page 2090
2090 c hapter 113: snmp c onfiguration displaying and maintaining snmp snmp configuration example network requirements ■ the nms connects to the agent, a router, through an ethernet. ■ the ip address of the nms is 1.1.1.2/24. ■ the ip address of ethernet interface on the router is 1.1.1.1/24. ■ the ...
Page 2091
Configuration example for snmp logging 2091 # configure the system information of the router. [sysname] snmp-agent sys-info version all [sysname] snmp-agent sys-info contact ;mr.Wang-tel:3306 [sysname] snmp-agent sys-info location telephone-closet,3rd-floor # configure the ip address for the port et...
Page 2092
2092 c hapter 113: snmp c onfiguration configuration procedure n the configurations for nms and agent are omitted. # enable logging display on the terminal (optional, enabled by default). Terminal monitor terminal logging # enable the information center to output the system information with the seve...
Page 2093
Configuration example for snmp logging 2093 snmp log to be output to other directions, refer to “information center configuration” on page 2137 ..
Page 2094
2094 c hapter 113: snmp c onfiguration.
Page 2095: 114
114 f ile s ystem m anagement c onfiguration n ■ a file name cannot be longer than 64 characters (including drive letter and a string terminator. If the drive letter is “cf: /”, the file name can be at most [ 64-1-4 ] = 59 characters in length; or, errors will occur in file operation. Typically, the...
Page 2096
2096 c hapter 114: f ile s ystem m anagement c onfiguration n ■ the directory to be removed must be empty, meaning before you remove a directory, you must delete all the files and the subdirectory under this directory. For file deletion, refer to the delete command and for subdirectory deletion, ref...
Page 2097
File system management 2097 n you can create a file by copying or downloading or using the save command. C caution: ■ empty the recycle bin timely with the reset recycle-bin command to save memory space. ■ as the delete /unreserved file-url command deletes a file permanently and the action cannot be...
Page 2098
2098 c hapter 114: f ile s ystem m anagement c onfiguration c caution: ■ do not remove the storage device or swap the board when mounting or unmounting the device, or when you are processing files on the storage device. Otherwise, the file system could be damaged. ■ when a storage device is connecte...
Page 2099
Configuration file management 2099 dir directory of flash:/test/ 0 drw- - feb 16 2006 15:28:14 mytest 2540 kb total (2519 kb free) # return to the upper directory. Cd .. # display the current working directory. Pwd configuration file management the device provides the configuration file management f...
Page 2100
2100 c hapter 114: f ile s ystem m anagement c onfiguration main/backup attribute of the configuration file a main configuration file and a backup configuration file can exist simultaneously if the device supports main/backup configuration file attribute. As such, when the main configuration file is...
Page 2101
Configuration file management 2101 original configuration file if the device reboots or the power fails during the process. ■ safe mode. This is the mode when you use the save command with the safely keyword. The mode saves the file slower but can retain the original configuration file in the device...
Page 2102
2102 c hapter 114: f ile s ystem m anagement c onfiguration ■ if you use the save file-name command, even if the configuration file saving synchronization for the amb and smb (standby main board) function is enabled, the smb does not automatically save the current configuration to its own configurat...
Page 2103
Configuration file management 2103 assigning backup attribute to the startup configuration file for next startup ■ if you save the current configuration to the backup configuration file, the system will automatically set the file as the backup startup configuration file. ■ you can also use the start...
Page 2104
2104 c hapter 114: f ile s ystem m anagement c onfiguration n ■ before restoring a configuration file, you should ensure that the server is reachable, the server is enabled with tftp service, and the client has permission to read and write. ■ after the command is successfully executed, you can use t...
Page 2105: 115
115 ftp c onfiguration when configuring ftp, go to these sections for information you are interested in: ■ “ftp overview” on page 2105 ■ “file system management configuration” on page 2095 ■ “configuring the ftp server” on page 2110 ■ “displaying and maintaining ftp” on page 2112 ftp overview introd...
Page 2106
2106 c hapter 115: ftp c onfiguration c caution: ■ a route must exist between the ftp server and client for the ftp function to take effect. ■ when the device serving as the ftp server logs in to the router through ie, some of the functions are not supported because multiple user connections are est...
Page 2107
Configuring the ftp client 2107 n ■ if no primary ip address is configured on the source interface, the ftp connection fails. ■ if you use the ftp client source command to first configure the source interface and then the source ip address of the transmitted packets, the new source ip address will o...
Page 2108
2108 c hapter 115: ftp c onfiguration n ■ ftp uses two modes for file transfer: ascii mode and binary mode. ■ the is command can only display the file/directory name, while the dir command can display more information, such as the size and date of creation of files or directories. Ftp client configu...
Page 2109
Configuring the ftp client 2109 network diagram figure 628 network diagram for ftping an image file from an ftp server configuration procedure # check files on your device. Remove those redundant to ensure adequate space for the startup file to be downloaded. Dir directory of flash:/ 0 drw- - dec 07...
Page 2110
2110 c hapter 115: ftp c onfiguration c caution: startup files for next startup must be saved under the root directory. For the details of this command, refer to “device management” on page 2005 . Configuring the ftp server configuring ftp server operating parameters the ftp server uses two modes to...
Page 2111
Configuring the ftp server 2111 n if ftp server performs authentication, authorization and accounting (aaa) policy on ftp client, aaa related parameters should be configured on the ftp server. For more information about the local-user, password, service-type, ftp and work-directory commands and the ...
Page 2112
2112 c hapter 115: ftp c onfiguration [sysname] ftp server enable [sysname] quit # check files on your device. Remove those redundant to ensure adequate space for the startup file to be uploaded. Dir directory of cf:/ 0 drw- - dec 07 2005 10:00:57 filename 1 drw- - jan 02 2006 14:27:51 logfile 2 -rw...
Page 2113
Displaying and maintaining ftp 2113 display detailed information about logged-in ftp users display ftp-user available in any view to do... Use the command... Remarks.
Page 2114
2114 c hapter 115: ftp c onfiguration.
Page 2115: 116
116 tftp c onfiguration when configuring tftp, go to these sections for information you are interested in: ■ “tftp overview” on page 2115 ■ “configuring the tftp client” on page 2116 ■ “displaying and maintaining the tftp client” on page 2117 ■ “tftp client configuration example” on page 2117 tftp o...
Page 2116
2116 c hapter 116: tftp c onfiguration before using tftp, the administrator needs to configure ip addresses for the tftp client and server, and make sure that there is a route between the tftp client and server. Configuring the tftp client when a device acts as a tftp client, you can upload files on...
Page 2117
Displaying and maintaining the tftp client 2117 n ■ if no primary ip address is configured on the source interface, tftp connection fails. ■ if you use the ftp client source command to first configure the source interface and then the source ip address of the packets of the tftp client, the new sour...
Page 2118
2118 c hapter 116: tftp c onfiguration configuration procedure 1 configure pc (tftp server), the configuration procedure omitted. ■ on the pc, enable tftp server ■ configure a tftp working directory. 2 configure the device (tftp client) c caution: if the free memory space of the device is not big en...
Page 2119: 117
117 s ystem m aintaining and d ebugging when maintaining and debugging the system, go to these sections for information you are interested in: ■ “system maintaining and debugging overview” on page 2119 ■ “system maintaining and debugging” on page 2121 ■ “system maintaining example” on page 2122 syst...
Page 2120
2120 c hapter 117: s ystem m aintaining and d ebugging the tracert command by using the tracert command, you can trace the routers involved in delivering a packet from source to destination. This is useful for identification of failed node(s) in the event of network failure. The tracert command invo...
Page 2121
System maintaining and debugging 2121 figure 632 the relationship between the protocol and screen debugging switch n outputting debugging information to a terminal is most commonly used. You can also configure to output debugging information to other directions, refer to “information center configur...
Page 2122
2122 c hapter 117: s ystem m aintaining and d ebugging system debugging n ■ the debugging commands are usually used by administrators in diagnosing network failure. ■ output of the debugging information may reduce system efficiency, especially during execution of the debugging all command. ■ after c...
Page 2123
System maintaining example 2123 the above output shows that nine routers are involved from the source to the destination device..
Page 2124
2124 c hapter 117: s ystem m aintaining and d ebugging.
Page 2125: 118
118 b asic c onfigurations while performing basic configurations of the system, go to these sections for information you are interested in: ■ “basic configurations” on page 2125 ■ “cli features” on page 2133 basic configurations this section covers the following topics: ■ “entering/exiting system vi...
Page 2126
2126 c hapter 118: b asic c onfigurations display the system clock the system clock is displayed by system time stamp, which is the same as that displayed by the display clock command. The system clock is decided by the commands clock datetime, clock timezone and clock summer-time. If these three co...
Page 2127
Basic configurations 2127 3 if the original system clock is not in the summer time range, the original system clock is displayed. Configure: clock summer-time ss one-off 1:00 2006/1/1 1:00 2006/8/8 2 display: 01:00:00 utc sat 01/01/2005 if the original system clock is in the summer time range, the o...
Page 2128
2128 c hapter 118: b asic c onfigurations 2 and 3 or 3 and 2 if the value of the original system clock ± “zone-offset” is not in the summer-time range, the original system clock ± “zone-offset” is displayed. Configure: clock timezone zone-time add 1 and clock summer-time ss one-off 1:00 2007/1/1 1:0...
Page 2129
Basic configurations 2129 configuring a banner introduction to banners banners are prompt information displayed by the system when users are connected to the device, perform login authentication, and start interactive configuration. The administrator can set corresponding banners as needed. At prese...
Page 2130
2130 c hapter 118: b asic c onfigurations configuring cli hotkeys n by default, the , and hotkeys are configured with command line and the and commands are null. ■ corresponds to the display current-configuration command. ■ corresponds to the display ip routing-table command. ■ corresponds to the un...
Page 2131
Basic configurations 2131 n these hotkeys are defined by the device. When you interact with the device from terminal software, these keys may be defined to perform other operations. If so, the definition of the terminal software will dominate. Configuring user levels and command levels all the comma...
Page 2132
2132 c hapter 118: b asic c onfigurations c caution: ■ when you configure the password for switching user level with the super password command, the user level is defaulted to 3 if no user level is specified. ■ you can switch to a lower user level unconditionally. To switch to a higher user level, h...
Page 2133
Cli features 2133 during daily maintenance or when the system is operating abnormally, you need to view each module’s running status to find the problem. Therefore, you are required to execute the corresponding display commands one by one. To collect more information one time, you can execute the di...
Page 2134
2134 c hapter 118: b asic c onfigurations to obtain the desired help information, you can: 1 enter > in any view to access all the commands in this view and brief description about them as well. ? User view commands: backup backup next startup-configuration file to tftp server boot-loader set boot l...
Page 2135
Cli features 2135 display features cli offers the following feature: when the information displayed exceeds one screen, you can pause using one of the methods shown in table 64 . History command the cli can automatically save the commands that have been used. You can invoke and repeatedly execute th...
Page 2136
2136 c hapter 118: b asic c onfigurations edit features the cli provides the basic command edit functions and supports multi-line editing. The maximum length of each command is 256 characters. Table 67 lists these functions. Too many parameters too many parameters % wrong parameter found at ’^’ posi...
Page 2137: 119
119 i nformation c enter c onfiguration when configuring information center, go to these sections for information you are interested in: ■ “information center overview” on page 2137 ■ “configuring information center” on page 2142 ■ “displaying and maintaining information center” on page 2148 ■ “info...
Page 2138
2138 c hapter 119: i nformation c enter c onfiguration information filtering by severity works this way: information with the severity value greater than the configured threshold is not output during the filtering. ■ if the threshold is set to 0, only information with the severity being emergencies ...
Page 2139
Information center overview 2139 outputting system information by source module the system is composed of a variety of protocol modules, board drivers, and configuration modules. The system information can be classified, filtered, and output by source module. Some source module names and description...
Page 2140
2140 c hapter 119: i nformation c enter c onfiguration lagg link aggregation module ldp label distribution protocol module line line module linkagg link agg module lqos lan switch qos module ls local server module lspagent label switched path agent module lspm label switch path management module mix...
Page 2141
Information center overview 2141 to sum up, the major task of the information center is to output the three types of information of the modules onto the ten channels in terms of the eight severity levels and according to the user’s settings, and then redirect the ten information channels to the seve...
Page 2142
2142 c hapter 119: i nformation c enter c onfiguration refer to table 70 for module name and description. Between “module” and “level” is a “/”. Level (severity) system information can be divided into eight levels based on its severity, from 0 to 7. Refer to table 68 for definition and description o...
Page 2143
Configuring information center 2143 enabling the display of system information on the console after setting to output system information to the console, you need to enable the associated display function to display the output information on the console. Follow these steps in user view to enable the ...
Page 2144
2144 c hapter 119: i nformation c enter c onfiguration setting to output system information to a monitor terminal system information can also be output to a monitor terminal, which is a user terminal that has login connections through the aux, vty, or tty user interface. Setting to output system inf...
Page 2145
Configuring information center 2145 setting to output system information to a log host setting to output system information to the trap buffer to do... Use the command... Remarks enter system view system-view - enable information center info-center enable optional enabled by default name the channel...
Page 2147
Configuring information center 2147 n to ensure that system information can be output to the snmp nms, you need to make the necessary configurations on the snmp agent and the nms. For detailed information on snmp, refer to “snmp configuration” on page 2085 . Setting to save system information to a l...
Page 2148
2148 c hapter 119: i nformation c enter c onfiguration ■ use the info-center logfile switch-directory command to manually configure the directory to which a log file can be saved. The configuration will be invalid after system reboots or the primary/backup switchover. Configuring synchronous informa...
Page 2149
Information center configuration example 2149 information center configuration example outputting log information to a unix log host network requirements ■ send log information to a unix log host with an ip address of 1.2.0.1/16; ■ log information with severity higher than informational will be outp...
Page 2150
2150 c hapter 119: i nformation c enter c onfiguration 2 configuring the log host the following configurations were performed on sunos 4.0 which has similar configurations to the unix operating systems implemented by other vendors. Step 1: issue the following commands as a root user. # mkdir /var/lo...
Page 2151
Information center configuration example 2151 configuration procedure 1 configuring the device # enable information center. System-view [sysname] info-center enable # specify the channel to output log information to the log host (optional, loghost by default). [sysname] info-center loghost 1.2.0.1 c...
Page 2152
2152 c hapter 119: i nformation c enter c onfiguration step three: after the log file information has been created and the /etc/syslog.Conf file has been modified, issue the following commands to display the process id of syslogd, terminate a syslogd process, and to restart syslogd using the r optio...
Page 2153
Information center configuration example 2153 [sysname] info-center source arp channel console log level informational [sysname] quit # enable the display of log information on a monitor terminal. Terminal monitor % current terminal monitor is on terminal logging % current terminal logging is on aft...
Page 2154
2154 c hapter 119: i nformation c enter c onfiguration.
Page 2155: 120
120 u ser i nterface c onfiguration when configuring user interface, go to these sections for information you are interested in: ■ “user interface overview” on page 2155 ■ “configuring asynchronous serial interface attributes” on page 2157 ■ “configuring terminal attributes” on page 2157 ■ “configur...
Page 2156
2156 c hapter 120: u ser i nterface c onfiguration ■ console port: a view which you log in from the console port. Console port is a line device port. The device has only one console port, with the port type as eia/tia-232 dce. ■ aux port: a view which you log in from the aux port. Aux port is also a...
Page 2157
Configuring asynchronous serial interface attributes 2157 configuring asynchronous serial interface attributes follow these steps to configure asynchronous attributes of a serial interface: configuring terminal attributes “configuring the auto-execute command” on page 2159 optional “configuring user...
Page 2158
2158 c hapter 120: u ser i nterface c onfiguration n the system supports two types of terminal display: ansi and vt100. If the terminal display of the device and the client (for example, hyper terminal or telnet terminal) is inconsistent or is set to ansi, and if the total number of the characters o...
Page 2159
Configuring the auto-execute command 2159 n the above configuration takes effect only for the aux port or other asynchronous serial interfaces working in flow mode. For details about asynchronous interface, refer to “asynchronous serial interface” on page 99 . Configuring the auto-execute command wi...
Page 2160
2160 c hapter 120: u ser i nterface c onfiguration level. For the detailed description of the local-user and level commands, refer to “aaa/radius/hwtacacs configuration” on page 1751 . Follow these steps to configure the user privilege level under a user interface: configuring access restriction on ...
Page 2161
Configuring redirection function on asynchronous serial interface(s) 2161 c caution: ■ if ssh is configured, you must set the authentication mode to scheme using the authentication-mode scheme command to guarantee a successful login. The protocol inbound ssh command fails if the authentication mode ...
Page 2162
2162 c hapter 120: u ser i nterface c onfiguration n ■ execute the other redirect commands after using the redirect enable command to enable redirection on the user interface. ■ you must set the same stop bits for the user interfaces corresponding to the device that redirects telnet connection and t...
Page 2163
Configuring authentication mode at login 2163 follow these steps to configure authentication mode at login as scheme: n for the detailed description of the local-user, password and service-type commands, refer to “aaa/radius/hwtacacs configuration” on page 1751 . C caution: if you configure to adopt...
Page 2164
2164 c hapter 120: u ser i nterface c onfiguration defining shortcut keys for starting terminal sessions/aborting tasks n the activation-key command is not supported on the vty user interface. Sending messages to the specified user interface(s) releasing the connection established on the user interf...
Page 2165: 121
121 mac a ddress t able m anagement c onfiguration n ■ interfaces that mac address table management involves can only be layer 2 ethernet interfaces. ■ this manual covers only static, dynamic and blackhole mac address table management. For the management of multicast mac address table management, re...
Page 2166
2166 c hapter 121: mac a ddress t able m anagement c onfiguration ■ unicast mode: if an entry is available for the destination mac address, the device forwards the frame directly from the hardware. ■ broadcast mode: if the device receives a frame with the destination address being all fs, or no entr...
Page 2167
Configuring mac address table management 2167 disabling global mac address learning disables the learning function on all ports. This can result in removal of learned mac addresses. Follow these steps to disable mac address learning: disabling mac address learning on an ethernet port or aggregation ...
Page 2168
2168 c hapter 121: mac a ddress t able m anagement c onfiguration n the mac address aging timer takes effect globally on dynamic mac address entries (learned or administratively configured) only. Configuring maximum number of mac addresses an ethernet port or aggregation port group can learn to prev...
Page 2169
Mac address table management configuration example 2169 mac address table management configuration example network requirements log onto your device from the console port to configure mac address table management as follows: ■ set the aging timer to 500 seconds for dynamic mac address entries. ■ add...
Page 2170
2170 c hapter 121: mac a ddress t able m anagement c onfiguration.
Page 2171: 122
122 a utomatic c onfiguration introduction to automatic configuration automatic configuration enables a device to automatically obtain and execute the configuration files when it starts up without loading the configuration files. Automatic configuration simplifies network configuration, facilitating...
Page 2172
2172 c hapter 122: a utomatic c onfiguration device to obtain the configuration files (for example, configuration file name, domain name and ip address of the tftp server and dns server). 2 if the device successfully obtains the ip addresses and the configuration file name from the dhcp server, it i...
Page 2173
Introduction to automatic configuration 2173 command, refer to “dns configuration” on page 609 ) removal of the temporary configuration is to execute the undo ip host command to remove the temporary configuration. ■ for the detailed introduction to dhcp, refer to “dhcp overview” on page 565 . Obtain...
Page 2174
2174 c hapter 122: a utomatic c onfiguration executing the configuration files if the device successfully obtains the configuration files, it removes the temporary configurations and executes the obtained configuration files; otherwise, it removes the temporary configurations and starts up without l...
Page 2175: 123
123 p o e c onfiguration when configuring poe, go to these sections for information you are interested in: ■ “poe overview” on page 2175 ■ “configuring the pse” on page 2176 ■ “configuring poe power management” on page 2179 ■ “configuring the poe monitoring function” on page 2181 ■ “upgrading pse pr...
Page 2176
2176 c hapter 123: p o e c onfiguration the whole poe system is powered by the poe power, which includes external poe power and internal poe power. N the support for the poe power type varies with devices. ■ pse pse is a card or subcard. Pse manages its own poe interfaces independently. Pse examines...
Page 2177
Configuring the poe interface 2177 n ■ pse-id indicates number of the slot where a poe interface locates. ■ when the remaining power of the poe system is lower than the maximum power of the pse, poe is disabled for the pse. ■ the maximum power of the pse must be greater than or equal to the sum of m...
Page 2178
2178 c hapter 123: p o e c onfiguration configuring poe interfaces through a poe configuration file a poe configuration file is used to configure at the same time multiple poe interfaces with the same attributes to simplify operations. This configuration method is a supplement to the common command ...
Page 2179
Configuring poe power management 2179 ■ if you have configured a poe interface through the command line, you cannot configure it through a poe configuration file again. If you want to reconfigure the interface through a poe configuration file, you must first remove the command line configuration on ...
Page 2180
2180 c hapter 123: p o e c onfiguration configuring pd power management the power priority of a pd depends on the priority of the poe interface. The priority levels of poe interfaces include critical, high and low in descending order. Power supply to a pd is subject to pd power management policies. ...
Page 2181
Configuring the poe monitoring function 2181 configuring the poe monitoring function the poe monitoring function involves monitoring of poe power, pse and pd. ■ monitoring poe power means monitoring the voltage of the poe power. ■ when the current power utilization of the pse is above or below the a...
Page 2182
2182 c hapter 123: p o e c onfiguration online pse processing software upgrade may be unexpectedly interrupted (for example, an error results in device reboot). If you fail to upgrade the pse processing software in full mode after reboot, you can power off the device and restart it before upgrading ...
Page 2183
Displaying and maintaining poe 2183 the support for the display poe pse pse pse-id interface and display poe pse pse-id interface power commands varies with devices. Displaying and maintaining poe poe configuration example network requirements ■ the device is equipped with two poe-supporting cards, ...
Page 2184
2184 c hapter 123: p o e c onfiguration network diagram figure 638 network diagram for poe configuration procedure # enable poe for the pse. System-view [sysname] poe enable pse 4 [sysname] poe enable pse 6 # set the maximum power of pse 4 to 400 watts. You do not need to configure the power for the...
Page 2185
Troubleshooting poe 2185 [sysname-gigabitethernet5/1] quit after the configuration takes effect, the ip phone and ar device are powered and can work normally. Troubleshooting poe symptom 1: setting the priority of a poe interface to critical fails. Analysis: ■ the guaranteed remaining power of the p...
Page 2186
2186 c hapter 123: p o e c onfiguration.
Page 2187: 124
124 oap m odule c onfiguration n note: in some regions, the oap modules are sold as “osm” modules. They are identical in function. When configuring an oap module, go to these sections for information you are interested in: ■ “oap module overview” on page 2187 ■ “switch of the interface on an oap mod...
Page 2188
2188 c hapter 124: oap m odule c onfiguration resetting an oap module when the linux operating system is operating abnormally or under other anomalies, you can reset an oap module by performing the following operation, which equals to resetting the oap module by pressing the reset button on the oap ...
Page 2189: 125
125 acfp c onfiguration when configuring acfp, go to these sections for information you are interested in: ■ “introduction to acfp” on page 2189 ■ “configuring acfp” on page 2194 ■ “displaying and maintaining acfp” on page 2195 ■ “acfp configuration example” on page 2195 introduction to acfp basic d...
Page 2190
2190 c hapter 125: acfp c onfiguration as shown in figure 639 , the acfp architecture consists of: ■ routing/switching component: as the main part of routers and switches, it performs complete router/switcher functions and is also the core of user management control. ■ independent service component:...
Page 2191
Introduction to acfp 2191 an acfp server supports multiple acfp clients. Therefore, acfp client information, acfp cooperation policy, and acfp cooperation rule are organized in the forms of tables. Acfp server information is generated by the acfp server itself. Acfp client information, acfp cooperat...
Page 2192
2192 c hapter 125: acfp c onfiguration ■ clientid: acfp client identifier. It can be assigned by the acfp server through a cooperation protocol or specified by the network administrator. It ensures that each acfp client has a unique client id to the acfp server. ■ description: acfp client descriptio...
Page 2193
Introduction to acfp 2193 rule information is described as follows: ■ clientid: acfp client identifier. ■ policy-index: policy index. ■ rule-index: rule identifier ■ status: it indicates whether the rule is applied successfully. ■ action: it can be mirror, redirect, deny, or permit. ■ match all pack...
Page 2194
2194 c hapter 125: acfp c onfiguration you can use the cooperation policy to manage the cooperation rules that belong to it. Using acfp ■ after acfp is enabled, some vlan ids must not be used by any other modules; otherwise, part of the data packets may be forwarded incorrectly. The range of vlan id...
Page 2195
Displaying and maintaining acfp 2195 displaying and maintaining acfp acfp configuration example network requirements ■ different departments are interconnected on the intranet through the device (acfp server). ■ the acfp client is connected to the device to control the traffic on the device (acfp se...
Page 2196
2196 c hapter 125: acfp c onfiguration network diagram figure 641 network diagram for acfp configuration configuration procedure ■ configure the device. # enable acfp. System-view [device] acfp enable ■ configure the collaboration policy and monitoring rules for the acfp client through mib. # config...
Page 2197
Acfp configuration example 2197 configure the acfp policy through mib browser to send information to device, where the client index is 1, policy index is 2, the policy inbound interface is ethernet 1/2 (by setting the node h3cacfppolicyinifindex), and the other parameters adopt the default values. #...
Page 2198
2198 c hapter 125: acfp c onfiguration.
Page 2199: 126
126 acsei c onfiguration this chapter involves the following contents: ■ “introduction to acsei” on page 2199 ■ “acsei server configuration” on page 2200 ■ “acsei client configuration” on page 2201 introduction to acsei as a private protocol, acsei provides a method for exchanging information betwee...
Page 2200
2200 c hapter 126: acsei c onfiguration ■ control of the acsei clients from an acsei server. For example, you can close acsei client, or restart acsei client from the acsei server. An acsei server can register multiple acsei clients. The maximum number of acsei clients an acsei server allows to regi...
Page 2201
Acsei client configuration 2201 configuring the clock synchronization timer configuring the monitoring timer close acsei client restart acsei client displaying and maintaining acsei server acsei client configuration multiple kinds of acsei clients have been developed at present. Refer to the manuals...
Page 2202
2202 c hapter 126: acsei c onfiguration acsei clients. The following contents introduce the acsei client configuration on an oap module: ■ “installing acsei client” on page 2202 ■ “configuring the default startup settings for acsei client” on page 2202 ■ “controlling acsei client” on page 2204 ■ “di...
Page 2203
Acsei client configuration 2203 n for description on the oap connect slot command, refer to “oap module configuration” on page 2187 modifying the default startup settings through gui 1 execute the oap connect slot slot-number command in user view to enter the linux system of the oap module. 2 execut...
Page 2204
2204 c hapter 126: acsei c onfiguration figure 643 service interface for acsei client default startup 4 move the cursor to acseid, and use the space key to choose: ■ [ * ] specifies that when started up, the system automatically startup acsei client. ■ [ ] specifies that when started up, the system ...
Page 2205
Acsei client configuration 2205 n for description on the oap connect slot command, refer to “oap module configuration” on page 2187 . C caution: ■ conditional restart means that if the acsei client process is running, the command stops the process and then restarts it, and if the acsei client proces...
Page 2206
2206 c hapter 126: acsei c onfiguration.
Page 2207: 127
127 t rack c onfiguration track overview figure 644 collaboration through the track module the track module is used to implement collaboration of different modules by establishing collaboration objects. The collaboration here involves three parts: the application modules, the track module, and the d...
Page 2208
2208 c hapter 127: t rack c onfiguration ■ static routing ■ policy routing. ■ backup center configuring track-nqa collaboration through the following configuration, you can establish the collaboration between the track module and the nqa, which probes the reaction entry and informs the track module ...
Page 2209
Configuring collaboration between the track module and application modules 2209 n ■ do not perform track object monitoring on the ip address owner. ■ when the status of the monitored track object turns from negative to positive, the corresponding router restores its priority automatically. ■ refer t...
Page 2210
2210 c hapter 127: t rack c onfiguration ■ if a static route needs route recursion, the associated track object must monitor the next hop of the recursive route instead of that of the static route; otherwise, a valid route may be considered invalid. ■ for details of static route configuration, refer...
Page 2211
Displaying and maintaining track object(s) 2211 n ■ the track object to be associated with the policy routing can be a nonexistent one. After you use the track command to create the track object, the association takes effect. ■ for details of policy routing configuration, refer to “configuring ip un...
Page 2212
2212 c hapter 127: t rack c onfiguration track configuration example vrrp-track-nqa collaboration configuration example network requirements ■ host a needs to access host b on the internet. The default gateway of host a is 10.1.1.10/24. ■ router a and router b belong to vrrp standby group 1, whose v...
Page 2213
Track configuration example 2213 [routera-nqa-admin-test-icmp-echo] frequency 100 # configure reaction 1, and set that five consecutive probe failures trigger the track-nqa collaboration. [routera-nqa-admin-test-icmp-echo] reaction 1 checked-element probe- fail threshold-type consecutive 5 action-ty...
Page 2214
2214 c hapter 127: t rack c onfiguration # set the authentication mode of standby group 1 to simple, and the authentication key to hello. [routerb-ethernet1/0] vrrp vrid 1 authentication-mode simple hello # configure the master router to send vrrp packets at an interval of five seconds. [routerb-eth...
Page 2215
Track configuration example 2215 when there is a fault on the link between router a and router c, you can still successfully ping host b on host a. Use the display vrrp command to view information about standby group 1. # display detailed information about standby group 1 on router a when there is a...
Page 2216
2216 c hapter 127: t rack c onfiguration.
Page 2217: 128
128 ipx c onfiguration when configuring ipx, go to these sections for information you are interested in: ■ “ipx protocol overview” on page 2217 ■ “configuring ipx basic functions” on page 2219 ■ “configuring ipx routing” on page 2219 ■ “configuring ipx sap” on page 2221 ■ “configuring the ipx forwar...
Page 2218
2218 c hapter 128: ipx c onfiguration via rip, an ipx router exchanges routing information with neighbors and maintains an inter-network routing information database (usually called routing table) according to network changes. When the router receives a packet, it finds a next hop from the routing t...
Page 2219
Configuring ipx basic functions 2219 novell is to set the packet type contained in the ipx header to 20, indicating that the ipx packet is a netbios packet. A device must forward such packets according to certain rules to ensure that netbios packets are transmitted in the ipx network. Protocol and s...
Page 2220
2220 c hapter 128: ipx c onfiguration configuring an ipx static route follow these steps to configure an ipx static route: n the specified interface-type interface-number can only be a ppp interface currently. Configuring ipx route number limitation in ipx, the maximum number of static and dynamic r...
Page 2221
Configuring ipx sap 2221 n routing protocols can redistribute routes from one another to share routing information. However, a rip router can only redistribute active static routes rather than inactive static routes and advertise them to directly connected networks. Configuring ipx rip parameters fo...
Page 2222
2222 c hapter 128: ipx c onfiguration configuring ipx sap timers in a large network, ipx sap broadcasts may occupy much bandwidth. Changing ipx sap update interval is an effective way to reduce bandwidth occupation. You can configure ipx sap aging interval as a value multiple times the update interv...
Page 2223
Configuring ipx sap 2223 configuring ipx service information generally, a client only uses the service advertised by netware server and saved by the advising router. In order that the client can always use a specific service, static service information can be manually added to the service informatio...
Page 2224
2224 c hapter 128: ipx c onfiguration configuring the ipx forwarding feature configuration prerequisite you need configure ipx basic functions before this task. Configuring ipx forwarding feature n ■ ipx rip and sap periodically broadcast updating packets. With the triggered updating feature enabled...
Page 2225
Pinging an ipx network 2225 pinging an ipx network configuration prerequisites you need to complete the ipx basic configuration before this task. Configuration procedure follow these steps to ping an ipx network: displaying and maintaining ipx configuration ipx configuration example networking requi...
Page 2226
2226 c hapter 128: ipx c onfiguration network diagram figure 646 network diagram for ipx configuration (on routers) configuration procedure configure router a # enable ipx. System-view [routera] ipx enable # enable ipx on the interface ethernet 1/1, with the network id being 2. [routera] interface e...
Page 2227
Troubleshooting ipx configuration 2227 # set the packet encapsulation format on the ethernet interface to ethernet_snap. [routerb-ethernet1/1] ipx encapsulation snap [routerb-ethernet1/1] quit # enable ipx on the interface ethernet1/0, with the network id being 1001. [routerb] interface ethernet 1/0...
Page 2228
2228 c hapter 128: ipx c onfiguration ■ if ipx packet debugging information displays a packet is discarded, and the prompt is “packet size is greater than interface mtu!”, it indicates the output packet size is greater than the maximum packet size that the interface can transmit. Use the display int...
Page 2229
Troubleshooting ipx configuration 2229 outgoing interface is down. When the route becomes active, it can be advertised as a rip route. ■ if the static route exists in the routing table, check its hops. If hops are more than or equal to 15, the static route can not be advertised. Troubleshooting ipx ...
Page 2230
2230 c hapter 128: ipx c onfiguration solution: ■ use the debugging ipx packet and debugging ipx sap packet verbose commands to check packet contents. All incoming and outgoing packets are displayed in debugging information. If no related packets are displayed, problems in lower layer network connec...
Page 2231
Troubleshooting ipx configuration 2231 ■ if round-robin is configured, verify whether there are multiple equivalent service information items for the service type of the requests. The equivalent service information items must have the same rip ticks, rip hops, sap hops and sap preferences. Ipx routi...
Page 2232
2232 c hapter 128: ipx c onfiguration.
Page 2233: 129
129 v oice o verview introduction to voip voip makes it possible that voice services such as plain old telephone service (pots) can be carried over the ip network. Voip is implemented via voice packets. In voip, the voice gateway segments the voice signal into frames and stores them in voice packets...
Page 2234
2234 c hapter 129: v oice o verview 3 the voip signal processing module generates a dial tone. 4 the user hears the dial tone played by the session application and begins dialing before the dial tone expires. 5 the session application collects the digits dialed by the user. 6 the session application...
Page 2235
Voice function configuration 2235 modulation and demodulation, fax protocol processing, and ip channel maintenance. ■ one-stage dialing and two-stage dialing one-stage dialing and two-stage dialing can well fit in with the situation where there are differences when various pbxs transmit called numbe...
Page 2236
2236 c hapter 129: v oice o verview figure 649 voice function configuration procedure table 73 description of the voice function configuration procedure step operation reference 1 connect the physical devices according to the network diagram. - 2 configure links and routes and ensure that the links ...
Page 2237
Voice function configuration 2237 voice subscriber line voice subscriber line configuration is to implement the functions of the voice subscriber line. Voice subscriber lines, which are connected to telephone network devices such as analog telephone and pbx, implement all physical layer functions be...
Page 2238
2238 c hapter 129: v oice o verview there are two kinds of voice entities: plain old telephone service (pots) entity and voip entity. ■ the pots entity corresponds to the local telephone or pstn. Pots entity configuration is to associate a voice subscriber line on the voip gateway with a local telep...
Page 2239
Voice function configuration 2239 capabilities, and call policies. The registration server sends the registration information to the location server for storage. ■ sip endpoints can use the proxy server to set up calls. Sip endpoints send signaling messages to the proxy server and then the proxy ser...
Page 2240
2240 c hapter 129: v oice o verview the dial plan configuration directly affects the selection of voice entity and the final call connection. The dial plan configuration involves global configuration, voice subscriber line configuration, and voice entity configuration. You can select one or more con...
Page 2241
Voice function configuration 2241 voice view configure global voice parameters [system-voice] key in voice-setup in system view quit. Return to system view voice dial program view configure dial plan [system-voice-di al] key in dial-program in voice view quit. Return to voice view voice subscriber l...
Page 2242
2242 c hapter 129: v oice o verview.
Page 2243: 130
130 v o ip o verview this document is organized as follows: ■ “voip overview” on page 2243 ■ “voice subscriber line configuration” on page 2245 ■ “voice entity configuration” on page 2265 introduction to voip the voice over ip (voip) network is an ip-based packet switched network. After digitization...
Page 2244
2244 c hapter 130: v o ip o verview.
Page 2245: 131
131 v oice s ubscriber l ine c onfiguration when configuring voice subscriber line, go to these sections for information you are interested in: ■ “signal tone” on page 2245 ■ “fxs voice subscriber line” on page 2246 ■ “fxo voice subscriber line” on page 2246 ■ “e&m voice subscriber line” on page 224...
Page 2246
2246 c hapter 131: v oice s ubscriber l ine c onfiguration signal tones support two modes: country mode and custom mode. In addition, the amplitude of signal tones can be customized for the avoidance of signal tone detection failure in special cases. Fxs voice subscriber line fxs interface a foreign...
Page 2247
Fxo voice subscriber line 2247 the calling number is sent to the ip network, and if the function is disabled, the character "p" or "o" is sent. Busy tone detection in practice, there are various switches and these switches use different signaling standards. Alike, the call progress tones played on t...
Page 2248
2248 c hapter 131: v oice s ubscriber l ine c onfiguration 3 use the vi-card busy-tone-detect command in voice view to start the detection. To seize the busy tone signal sent by pbx b, you are recommended to run the above command 2 seconds after on-hook. 4 (the console terminal displays "begin to au...
Page 2249
Configuration task list 2249 ■ delay start. In this mode, the caller first picks up the phone to seize the trunk line, and the called side (such as the peer pbx) also enters the off-hook state in response to the off-hook action of the caller. The called side (pbx) will be in the off-hook state until...
Page 2250
2250 c hapter 131: v oice s ubscriber l ine c onfiguration configuring call progress tones configuration prerequisites the router is equipped with fxs, fxo, e&m, ve1, and vt1 interface cards. Specifying the call progress tones of a country follow these steps to specifying the call progress tones of ...
Page 2251
Configuring basic functions 2251 configuring basic functions configuration prerequisites the router is equipped with fxs, fxo, and e&m interface cards and the router supports the voice interface cards. N the commands in fxs, fxo, or e&m voice subscriber line view are applicable only when the router ...
Page 2252
2252 c hapter 131: v oice s ubscriber l ine c onfiguration n ■ to implement the cid function, besides the voip router is required to support receiving calling number in the on-hook state, the hardware and software of pbx must support this service and the subscriber telephone must support the cid fun...
Page 2253
Configuring fxo voice subscriber line 2253 n ■ to implement the cid function, besides the voip router is required to support receiving calling number in the on-hook state, the hardware and software of pbx must support this service and the subscriber telephone must support the cid function. That is, ...
Page 2254
2254 c hapter 131: v oice s ubscriber l ine c onfiguration n ■ you can increase the number of busy tone periods for detection by using the busytone-t-th command to improve the busy tone detection accuracy. This can avoid wrong on-hooks resulting from incorrect busy tone data to some extent, and mean...
Page 2255
Configuring fxo voice subscriber line 2255 n ■ usually, you are not recommended to use this function because incorrect configuration may lead to wrong on-hooks. ■ you are recommended to test multiple groups of parameters during configuration to find a proper group of parameters that will not only av...
Page 2256
2256 c hapter 131: v oice s ubscriber l ine c onfiguration configuring other functions follow these steps to configure other functions: binding one fxs interface to one fxo interface the one-to-one binding of fxs interfaces to fxo interfaces enhances the reliability of voice solutions. For industry-...
Page 2257
Configuring e&m voice subscriber line 2257 n this feature involves the caller-permit and private-line commands. For details about these two commands, refer to “dial plan configuration” on page 2289 . Configuring e&m voice subscriber line configuration prerequisites the router is equipped with an e&m...
Page 2258
2258 c hapter 131: v oice s ubscriber l ine c onfiguration configuring start mode configure the immediate start mode follow these steps to configure the immediate start mode: configure the delay start mode follow these steps to configure the delay start mode: configure the wink start mode follow the...
Page 2259
Configuring dtmf 2259 configuring output gain of slic chip follow these steps to configure the output gain of the slic chip: configuring dtmf introduction to dtmf dual tone multi frequency (dtmf) involves high frequency and low frequency groups, each of which comprises four frequencies. A high frequ...
Page 2260
2260 c hapter 131: v oice s ubscriber l ine c onfiguration figure 655 key spectrum as seen from figure 655 , 1209hz, 1336hz, 1477hz, and 1633hz form a column frequency group, and 697hz, 770hz, 852hz, and 941hz form a row frequency group. Each dtmf key tone consists of a row frequency and a column fr...
Page 2261
Configuring options related to dial plan 2261 ■ sensitivity detection: if the dtmf detection sensitivity is high, the reliability is low but a detection error may occur. If the detection sensitivity is low, the reliability is high but a dtmf may fail to be detected. Configuration procedure follow th...
Page 2262
2262 c hapter 131: v oice s ubscriber l ine c onfiguration configuring echo adjustment function echo adjustment the voice of a user is repeated and sent back to the handset, resulting in echoes. This is because analog signals leak into the receiving path of the user. The echo adjustment function pro...
Page 2263
Configuring adjustment functions 2263 configuration procedure follow these steps to configure the echo adjustment function: n currently, only digital cards, instead of analog cards support the undo nlp-on command. Configuring gain adjustment function follow these steps to configure the gain adjustme...
Page 2264
2264 c hapter 131: v oice s ubscriber l ine c onfiguration configuring comfort noise function you can use the cng-on command to generate some comfortable background noise to replace the toneless intervals during a conversation. If no comfortable noise is generated, the toneless intervals will make b...
Page 2265: 132
132 v oice e ntity c onfiguration before configuring voice entities, go to these sections for information you are interested: ■ “introduction to voice entities” on page 2265 ■ “configuring pots entity” on page 2266 ■ “configuring voip entity” on page 2271 ■ “configuring voice performance” on page 22...
Page 2266
2266 c hapter 132: v oice e ntity c onfiguration ■ pots entity. This type of voice entity corresponds to the local telephone or pstn side. Pots entity configuration is required to establish connections between physical voice subscriber-lines and local telephone devices. ■ voip entity. This type of e...
Page 2267
Configuring pots entity 2267 n the router with fxo, fxs, or e&m voice interface cards can generate voice subscriber lines automatically. When configuring a pots entity, use the line line-number command to bind the entity to the corresponding subscriber lines. For configurations of fxs voice subscrib...
Page 2268
2268 c hapter 132: v oice e ntity c onfiguration n ■ two communication parties can communicate normally only if they share some identical codec algorithms. Therefore, when you configure the compression command, make sure that the devices on both sides share identical codec algorithms. Otherwise, the...
Page 2269
Configuring pots entity 2269 configuring dtmf transmission dtmf transmission in conversation, dtmf digits can be transparently transmitted between the originating and terminating gateways in inband or out-of-band mode: ■ inband transmission: dtmf digits are encapsulated in rtp voice packets for tran...
Page 2270
2270 c hapter 132: v oice e ntity c onfiguration transmitted only when an active voice segment is detected. Researches show that vad can save the transmission bandwidth by 50%. Follow these steps to enable vad: configuring options related to dial plan follow these steps to configure options related ...
Page 2271
Configuring voip entity 2271 configuring voip entity configuration task list complete the following tasks to configure a voip entity: configuration prerequisites log in to the router equipped with a voice card (for example, an fxs interface card) and enter user view. Creating voip entity follow thes...
Page 2272
2272 c hapter 132: v oice e ntity c onfiguration configuring dtmf transmission follow these steps to configure the out-of-band dtmf transmission: n for precautions, refer to “configuring dtmf transmission” on page 2269 . Configuring fast connection and tunneling fast connection and tunneling ■ accor...
Page 2273
Configuring voip entity 2273 ■ tunneling means that in fast connection mode, non-standard h.245 messages (e.G., transparent transmission capability of dtmf digit) are encapsulated in an h.225.0 facility message to complete capability negotiation and call forwarding, which makes it unnecessary to est...
Page 2274
2274 c hapter 132: v oice e ntity c onfiguration configuring dtmf transmission in fast connection mode follow these steps to configure a dtmf transmission in the fast connection mode: n in actual configuration, to implement the transparent transmission of dtmf digit, you need to perform configuratio...
Page 2275
Configuring voice performance 2275 configuring options related to dial plan follow these steps to configure options related to dial plan: for details about the above commands, refer to “dial plan configuration” on page 2289 . Configuring voice performance configuration prerequisites you have complet...
Page 2276
2276 c hapter 132: v oice e ntity c onfiguration n in voice view, the vqa dscp media command has global significance, and the dscp media command is valid only for the configured voice entity.. Resetting a voice card when a card is reset, all traffic carried by it will be interrupted and the card wil...
Page 2277
Configuring global default voice parameters 2277 difference between the default command and the undo default command the default command (such as the default entity vad-on command) is used to configure default values for parameters of voice entities globally. The undo default command is used to rest...
Page 2278
2278 c hapter 132: v oice e ntity c onfiguration figure 659 restore the parameter default of the command command to the system fixed value configuration procedure follow these steps to configure global default voice parameters: n for the default entity fax command, refer to “fax over ip configuratio...
Page 2279
Voip configuration example 2279 voip configuration example fxs interface network requirements two voice gateways (router a and router b) communicate with each other through wan. For example, the user of tel. 1 (010-1001) attached to routers a dials 0755-2001, the number of tel. 3 attached to router ...
Page 2280
2280 c hapter 132: v oice e ntity c onfiguration configuration procedure 1 configure router a # configure the voip entity to router b. System-view [routera] voice-setup [routera-voice] dial-program [routera-voice-dial] entity 0755 voip [routera-voice-dial-entity755] match-template 0755.... [routera-...
Page 2281
Voip configuration example 2281 dialing the number 0755-2003 on phone 0755-2001 connects to router b. Since router b works in the private-line mode, it requests connection to the preset remote number 010-1001 at router a side. Network diagram figure 661 network diagram for fxo configuration procedur...
Page 2282
2282 c hapter 132: v oice e ntity c onfiguration one-to-one binding between fxs and fxo network requirements ■ router a and router b are both connected to an ip network and a pstn. Telephone a attached to router a can make calls to telephone b attached to router b over the ip network or the pstn. ■ ...
Page 2283
Voip configuration example 2283 [sysname-voice-dial-entity101001] line 6/24 [sysname-voice-dial-entity101001] quit # configure a backup pots entity for the fxo voice subscriber line, set the match template to ".T", enable the sending of all digits of a called number, and configure a calling number p...
Page 2284
2284 c hapter 132: v oice e ntity c onfiguration # configure the private line auto ring-down (plar) function and the delay off-hook binding. [sysname-voice] subscriber-line 6/0 [sysname-voice-line6/0] private-line 2101002 [sysname-voice-line6/0] hookoff-mode delay bind 6/24 [sysname-voice-line6/0] q...
Page 2285
Troubleshooting voip configuration 2285 [routera-voice-dial-entity755] match-template 0755.... [routera-voice-dial-entity755] address ip 2.2.2.2 # enable fast connection, tunnel function and h.255 out-of-band dtmf transmission for the voip entity. [routera-voice-dial-entity755] fast-connect [routera...
Page 2286
2286 c hapter 132: v oice e ntity c onfiguration solution ■ check that the peer is reachable. You can use the ping command to ping the peer ip address. ■ check that the voice entity configuration is correct. Failed to hang up symptom the fxo voice subscriber line cannot detect busy tone signals from...
Page 2287
Troubleshooting voip configuration 2287 detect busy tone following the steps for the automatic busy tone detection. If failed, it may be that the operation of checking busy tone parameter failed. Repeat above operations until the busy tone parameters are checked..
Page 2288
2288 c hapter 132: v oice e ntity c onfiguration.
Page 2289: 133
133 d ial p lan c onfiguration dial plan overview the wide application of voip has resulted in more and more dialing plans. While service flexibility is enhanced and customer requirements are satisfied, reasonable, operable number management becomes increasingly important. A dial plan can help voice...
Page 2290
2290 c hapter 133: d ial p lan c onfiguration figure 665 dial plan process on the calling side 1 the voice gateway on the calling side substitutes the calling/called number on the subscriber line according to the number substitution rule. 2 the voice gateway performs global number substitution. 3 th...
Page 2291
Dial plan overview 2291 figure 666 dial plan process on the called side 1 after receiving a voice call (the called number), the voice gateway on the called side performs calling/called number substitution globally. 2 the voice gateway on the called side selects a proper voice entity based on the voi...
Page 2292
2292 c hapter 133: d ial p lan c onfiguration n ■ the sub-expression (one digit or digit string) before a control character such as !, +, and % can appear for the corresponding times. For example, (100)+ can match 100, 100100, 100100100, and so on. Once any number of them is matched, the match is co...
Page 2293
Configuration task list 2293 if there exist multiple number substitution rules in a number substitution rule list, only one number substitution rule will be matched. The match process is as follows: 1 the preferred number substitution rule is matched first. If the match succeeds, the gateway substit...
Page 2294
2294 c hapter 133: d ial p lan c onfiguration enabling private line auto ring-down with the private line auto ring-down (plar) function enabled, the voice gateway automatically dials the specified called number (string) as soon as the subscriber picks up the phone. Follow these steps to configure th...
Page 2295
Configuring voice entity selection priority rules 2295 configuring a dial terminator in areas where variable-length numbers are used, you can specify a character as the dial terminator so that the voice gateway can dial out the number before the dialing interval expires. The dial terminator identifi...
Page 2296
2296 c hapter 133: d ial p lan c onfiguration n ■ the voice entity type selection priority rule takes precedence over the voice entity selection priority rule. ■ the priority of a value with a t (for example, 3.T) is higher than that of the same value without a t (for example, 3). Configuring a numb...
Page 2297
Configuring a maximum-call-connection set 2297 n ■ after the number-priority peer enable command is configured, a dialed number will match first against a voice entity match template and then a service feature code. For example, if a service feature code is *40*1234 and the match template *40 is con...
Page 2298
2298 c hapter 133: d ial p lan c onfiguration configuring number substitution a number substitution rule list defines some number substitution methods. It can be used wherever number substitution is necessary. There is no limitation on where and how many times it is used. Therefore, a number substit...
Page 2300
2300 c hapter 133: d ial p lan c onfiguration configuring number substitution for a voice subscriber line follow these steps to configure number substitution for a subscriber line: n whatever number substitution mode configured, the system performs number substitution only once on a given number. Co...
Page 2301
Configuring a dial prefix 2301 configuring a dial prefix configuration prerequisites you have configured the required basic functions of pots and voip entities. Configuration procedure follow these steps to configure a dial prefix: displaying and maintaining dial plan configuration dial plan configu...
Page 2302
2302 c hapter 133: d ial p lan c onfiguration subscribers in one pbx network can make ordinary calls to remote subscribers in the other pbx network over a voip network. There are a financial department, market department, and sales department at both place a (area code 021) and place b (area code 01...
Page 2303
Dial plan configuration examples 2303 [routerb-voice-dial-substitute21101] rule 1 0101688 0001 [routerb-voice-dial-substitute21101] rule 2 0103366 0002 [routerb-voice-dial-substitute21101] rule 3 0102323 0003 # configure a number substitution rule list for calling numbers of outgoing calls. [routerb...
Page 2304
2304 c hapter 133: d ial p lan c onfiguration [routera-voice-dial-entity1010] line 1/0 [routera-voice-dial-entity1010] send-number all # configure a local port line 1/1. [routera-voice-dial-entity1010] quit [routera-voice-dial] entity 2010 pots [routera-voice-dial-entity2010] match-template .... [ro...
Page 2305
Dial plan configuration examples 2305 [routera-voice-dial-entity 2001] match-template 010.... [routera-voice-dial-entity 2001] address ip 1.1.1.3 [routera-voice-dial-entity 2001] quit # configure pots entities. [routera-voice-dial] entity 1000 pots [routera-voice-dial-entity 1000] match-template 100...
Page 2306
2306 c hapter 133: d ial p lan c onfiguration [routerc-voice-dial] entity 1000 pots [routerc-voice-dial-entity 1000] match-template 010.... [routerc-voice-dial-entity 1000] line 1/0 [routerc-voice-dial-entity 1000] send-number all [routerc-voice-dial-entity 1000] quit [routerc-voice-dial] entity 100...
Page 2307
Dial plan configuration examples 2307 # configure pots entities. [routera-voice-dial] entity 1000 pots [routera-voice-dial-entity 1000] match-template 1000 [routera-voice-dial-entity 1000] line 1/0 [routera-voice-dial-entity 1000] quit [routera-voice-dial] entity 1001 pots [routera-voice-dial-entity...
Page 2308
2308 c hapter 133: d ial p lan c onfiguration ■ configuration on router c # configure an ethernet address. System-view [routerc] interface ethernet 2/0 [routerc-ethernet] ip address 1.1.1.3 24 [routerc-ethernet] quit # configure pots entities. [routerc-voice-dial] entity 1000 pots [routerc-voice-dia...
Page 2309: 134
134 e1 and t1 c onfiguration introduction to e1 and t1 this section covers these topics: ■ “overview” on page 2309 ■ “e1/t1 voice functions” on page 2309 ■ “e1/t1 interface” on page 2310 ■ “features of e1/t1” on page 2311 overview plesiochronous digital hierarchy (pdh) system includes two major comm...
Page 2310
2310 c hapter 134: e1 and t1 c onfiguration figure 670 network diagram for an e1/t1 voice system e1/t1 voice allows the router to provide more channels of voice communication, greatly improving router utilization and broadening service range. E1/t1 interface this section covers these topics: ■ “e1 i...
Page 2311
Introduction to e1 and t1 2311 ■ when digital lgs signaling is adopted, the e1 interface functions as a digital fxo or fxs interface. On the interface, timeslot division and functions are the same as those with r2 signaling. N ■ after you create a ts set and configure signaling on a ve1 voice interf...
Page 2312
2312 c hapter 134: e1 and t1 c onfiguration ■ digital e&m signaling, similar to r2 signaling. It transmits e (receive) and m (transmit) call control signals similar to analog e&m signaling in ts16, alignment signals in ts0, and voice signals in other timeslots. In digital e&m signaling, when an e1 t...
Page 2313
Configuring basic parameters for e1 voice interfaces 2313 “features of e1/t1” on page 2311 to get some basic knowledge about different types of signaling. Configuring basic parameters for e1 voice interfaces configuring a tdm clock source introduction to tdm clock source when digital voice e1/t1 int...
Page 2314
2314 c hapter 134: e1 and t1 c onfiguration configuring the framing format and line coding format follow these steps to configure the framing format and line coding format: n for controller e1, frame-format, and code commands, refer to “wan interface configuration” on page 99 . Creating a ts set fol...
Page 2315
Configuring basic parameters for t1 voice interface 2315 configuring basic parameters for t1 voice interface configuring a tdm clock source follow these steps to configure a tdm clock source: configuring the framing format and line coding format follow these steps to configure the framing format and...
Page 2316
2316 c hapter 134: e1 and t1 c onfiguration placed, local tdm calls can still be placed. Therefore, you can configure this command even if no dsp resource is available. Configuring the voice subscriber line for a ts set a ts set is a list of timeslots on an e1/t1 interface which abstractly forms a l...
Page 2317
Configuring the voice subscriber line for a ts set 2317 digits collection, a high probability of detection errors, and a low probability of dtmf failing to be detected. Follow these steps to configure a dtmf detection sensitivity: configuring the volume adjustment function follow these steps to conf...
Page 2318
2318 c hapter 134: e1 and t1 c onfiguration configuring the comfortable noise function follow these steps to configure the comfortable noise function: configuring options related to dial plan follow these steps to configure the options related to dial plan: create a ts set according to the selected ...
Page 2319
Binding logical voice subscriber line to pots entity 2319 for details about the above commands, refer to “dial plan configuration” on page 2289 . Binding logical voice subscriber line to pots entity follow these steps to bind a logical voice subscriber line to a pots entity: configuring r2 signaling...
Page 2320
2320 c hapter 134: e1 and t1 c onfiguration figure 671 r2 signaling elements 1 itu-t digital line signaling digital line signaling is responsible for changing call statuses and conditions of a line. It functions to identify and detect these four states: calling party goes off-hook and seizes the lin...
Page 2321
Configuring r2 signaling 2321 sends back a seizure acknowledgement signal after it recognizes the seizure signal. At this time, the circuits of the both sides are seized, and they start interregister signaling exchange. When the called party picks up the phone, the terminating point sends a backward...
Page 2322
2322 c hapter 134: e1 and t1 c onfiguration figure 674 r2 digital line signaling - terminating point releases the call ■ line released by forced release signal: when the terminating point supports metering signals, the system may send a forced release signal 00 instead of a clear-back signal 11 to r...
Page 2323
Configuring r2 signaling 2323 ■ group a backward signals: control signals used for controlling and acknowledging group i forward signals. ■ group ii forward signals: identify the calling party category. The system looks at the calling party category to decide whether the calling party can perform fo...
Page 2324
2324 c hapter 134: e1 and t1 c onfiguration ■ group b backward signals: identify the state of the called party, and acknowledge group ii signals and control connection. The following figure shows the exchange process requesting calling party information, which is typical of r2 interregister signalin...
Page 2325
Configuring r2 signaling 2325 figure 675 itu-t r2 interregister signaling exchange process configuring basic r2 signaling parameters configuring the country or region mode follow these steps to configure the country or region mode: configuring the trunk direction for r2 signaling follow these steps ...
Page 2326
2326 c hapter 134: e1 and t1 c onfiguration enabling the terminating side to send busy tones to the calling subscriber follow these steps to enable the terminating side to send busy tones to the calling subscriber: enabling the dtmf mode to receive and send r2 signaling follow these steps to enable ...
Page 2327
Configuring r2 signaling 2327 configuring the connection mode for an r2 call there are two connection modes for an r2 call: terminal-to-terminal (terminal) and segment-to-segment (segment) mode. ■ in the terminal-to-terminal (terminal) mode, after all digits of the called number are collected, the r...
Page 2329
Configuring r2 signaling 2329 configuring r2 interregister signaling follow these steps to configure r2 interregister signaling: idle 1001 1001 seize 0001 0001 seizure-ack 1101 1101 release-guard 1001 1001 table 88 default values of signals in r2 digital line signaling signal default rx-bits abcd de...
Page 2330
2330 c hapter 134: e1 and t1 c onfiguration configuring dss1 and q.Sig signaling after you create a pri set with the pri-set command on an e1/t1 interface, a serial interface is automatically created. This interface is named serial number:15 on an e1 interface and serial number:23 on a t1 interface....
Page 2331
Configuring digital e&m signaling 2331 n ■ for the isdn protocol-type and isdn protocol-mode commands, refer to “isdn configuration” on page 421 . ■ the pri-set command is independent of the dsp resource (voice processing module-vpm). When no dsp resource is available, though ip calls cannot be plac...
Page 2332
2332 c hapter 134: e1 and t1 c onfiguration configuring the delay start mode follow these steps to configure the delay start mode: configuring the wink start mode follow these steps to configure the wink start mode: configuring receive and transit signaling follow these steps to configure receive an...
Page 2333
Configuring digital e&m signaling 2333 n ■ the abcd bit pattern of the receive idle signal from the local end must be the same as that of the transmit idle signal from the remote end. Seized signals and idle signals are processed in the same way. ■ after you change the abcd bit pattern of a digital ...
Page 2334
2334 c hapter 134: e1 and t1 c onfiguration querying the trunk circuits of a timeslot or a range of timeslots follow these steps to query the trunk circuits of a timeslot or a range of timeslots: configuring digital lgs signaling configuring the time adjustment function follow these steps to configu...
Page 2335
Displaying and maintaining e1 and t1 voice configuration 2335 displaying and maintaining e1 and t1 voice configuration e1/t1 voice configuration example this section provides two configuration examples: ■ “e1 r2 signaling and digital e&m signaling configuration example” on page 2335 ■ “e1 voice dss1...
Page 2336
2336 c hapter 134: e1 and t1 c onfiguration configuration procedure 1 configure router a in city a # configure the ip address 1.1.1.1/24 for the interface ethernet 2/0. System-view [routera] interface ethernet 2/0 [routera-ethernet0/0] ip address 1.1.1.1 255.255.255.0 [routera-ethernet0/0] quit # cr...
Page 2337
E1/t1 voice configuration example 2337 # associate the pots voice entity with subscriber line 1/1:1. [routera-voice-dial-entity1002] line 1/1:1 [routera-voice-dial-entity1002] send-number all # create a voip voice entity. [routera-voice-dial-entity1002] entity 0755 voip # configure a target match-te...
Page 2338
2338 c hapter 134: e1 and t1 c onfiguration # associate the pots voice entity with subscriber line 1/1:1. [routerb-voice-dial-entity2002] line 1/1:1 [routerb-voice-dial-entity2002] send-number all [routerb-voice-dial-entity2002] quit # create a voip voice entity. [routerb-voice-dial] entity 010 voip...
Page 2339
E1/t1 voice configuration example 2339 [routera-ethernet0/0] ip address 1.1.1.1 255.255.255.0 [routera-ethernet0/0] quit # create an isdn pri set on interface e1 1/1. [routera] system-view [routera] controller e1 1/1 [routera-e1 1/1] pri-set # create a pots voice entity for the fxs interface. [route...
Page 2340
2340 c hapter 134: e1 and t1 c onfiguration [routera-voice-dial] entity 0755 voip # configure a target match-template for the voip voice entity. [routera-voice-dial-entity755] match-template 0755.... # configure the target address of the voip voice entity. [routera-voice-dial-entity755] address ip 2...
Page 2341
Troubleshooting 2341 # create a voip voice entity. [routerb-voice-dial] entity 010 voip # configure a target match-template for the pots voice entity. [routerb-voice-dial-entity10] match-template 010.... # configure the target address of the voip voice entity. [routerb-voice-dial-entity10] address i...
Page 2342
2342 c hapter 134: e1 and t1 c onfiguration.
Page 2343: 135
135 f ax over ip c onfiguration when configuring fax over ip (foip), go to these sections for information you are interested in: ■ “foip overview” on page 2343 ■ “foip configuration” on page 2344 ■ “displaying and maintaining foip configuration” on page 2352 ■ “foip configuration example” on page 23...
Page 2344
2344 c hapter 135: f ax over ip c onfiguration protocol criteria for foip ip real-time fax complies with the itu-t t.30 and t.4 protocols on the pstn side and the h.323 and t.38 protocols on the ip network side. ■ t.30 protocol is about file and fax transmission over pstn. It describes and regulates...
Page 2345
Foip configuration 2345 foip configuration includes: ■ “enabling ecm for fax” on page 2345 ■ “configuring fax capability transmission mode” on page 2346 ■ “configuring maximum fax rate” on page 2346 ■ “configuring fax training mode” on page 2347 ■ “configuring a fax local training threshold” on page...
Page 2346
2346 c hapter 135: f ax over ip c onfiguration configuring fax capability transmission mode in common fax applications, the participating fax terminals negotiate with the standard capability (such as v.17 and v.29 rate) by default. It means that they do not send each other non-standard facilities (n...
Page 2347
Foip configuration 2347 ■ if g.729 is used, the fax rate will be 9600 bps and the corresponding fax protocol is v.29. If the fax rate is set to “disable”, the fax function will be disabled. Configuration prerequisites voip configuration is completed, ip calls can be made successfully, and fax machin...
Page 2348
2348 c hapter 135: f ax over ip c onfiguration n vofr entities only support the ppp training mode. Configuring a fax local training threshold when rate training is carried on between facsimile terminals, the transmitting terminal transmits “zero-filled” tcf data (the filling time per packet is 1.5±1...
Page 2349
Foip configuration 2349 configuration prerequisites voip configuration is completed, ip calls can be made successfully, and fax machines are connected correctly. Configuration procedure follow these steps to configure the transmit energy level of the gateway carrier: configuring fax interworking pro...
Page 2350
2350 c hapter 135: f ax over ip c onfiguration sides can directly communicate over a transparent ip link, and the voice gateways (routers) do not discriminate fax calls from voice calls. After detecting a fax tone in an established voip call, the voice gateway makes sure whether the voice codec prot...
Page 2351
Foip configuration 2351 n because netmeeting does not support t.38 capability description parsing, you must disable the voice gateway in h.323 slow start mode from containing the t.38 capability description in its capability set to interwork with netmeeting. Configuring default values of fax paramet...
Page 2352
2352 c hapter 135: f ax over ip c onfiguration displaying and maintaining foip configuration foip configuration example network requirements the headquarters of a company in city b and its branch in city a transmit and receive faxes over an ip network. Router a in city a and router b in city b use t...
Page 2353
Foip configuration example 2353 network diagram figure 679 network diagram for foip configuration configuration procedure 1 configure router a. System-view [routera] voice-setup [routera-voice] dial-program [routera-voice-dial] entity 0755 voip [routera-voice-dial-entity755] match-template 0755.... ...
Page 2354
2354 c hapter 135: f ax over ip c onfiguration.
Page 2355: 136
136 h.323 c onfiguration when configuring h.323, go to these sections for information you are interested in: ■ “introduction” on page 2355 ■ “h.323 architecture” on page 2357 ■ “h.323 fundamentals” on page 2358 ■ “h.323 gateway configuration” on page 2360 ■ “displaying and maintaining the h.323 gate...
Page 2356
2356 c hapter 136: h.323 c onfiguration diagnosis as well. These two protocols work together to ensure real-time voice transmission. The following figure illustrations the h.323 stack: figure 680 h.323 stack itu-t ras is implemented in compliant with the h.323v2 protocol for communication between ga...
Page 2357
H.323 architecture 2357 h.323 architecture an h.323 network consists of terminals, voice gateways, an optional gatekeeper, and multipoint control units (mcus). If a gatekeeper is present in an h.323 network, the terminals, gateways, and mcus registered with the gatekeeper form a zone. In this zone, ...
Page 2358
2358 c hapter 136: h.323 c onfiguration figure 681 h.323 network h.323 fundamentals gatekeeper discovery when an endpoint wants to establish a call with another endpoint, it first looks for a gatekeeper with which it can register for services. This process is called gatekeeper discovery. An ras sign...
Page 2359
H.323 fundamentals 2359 figure 682 direct call signaling between endpoints figure 683 gatekeeper-routed call signaling call setup after receiving the acf message from the gatekeeper, the calling endpoint sends call signaling to set up a call. In a direct call signaling for example, the calling endpo...
Page 2360
2360 c hapter 136: h.323 c onfiguration opening/closing logical channel(s) the two endpoints open one or more logical channels between them for transporting media streams. (the logical channels are specified by ip address plus port number.) these channels are closed when the communication is over. C...
Page 2361
H.323 gateway configuration 2361 configuration procedure follow these steps to configure basic h.323 gateway functions: n ■ for more information about pots and voip entities, refer to “configuring pots entity” on page 2266 and “configuring voip entity” on page 2271 . ■ before you can configure a sec...
Page 2362
2362 c hapter 136: h.323 c onfiguration configuration prerequisites complete the required basic h.323 gateway configurations except for the ras-on command. (the ras-on command is used for initiating registration requests to the gatekeeper after all configurations are completed.) configuration proced...
Page 2363
H.323 gateway configuration example 2363 h.323 gateway configuration example network requirements telephones in city a and city b can communicate with each other through routers with the voice function across an ip network where a gatekeeper is used for dynamic telephone number to ip address transla...
Page 2364
2364 c hapter 136: h.323 c onfiguration [routera-voice-dial] entity 1001 pots [routera-voice-dial-entity1001] match-template 0101001 [routera-voice-dial-entity1001] line 1/1 # specify a loopback interface as the h.323 gateway interface. [routera-voice-dial-entity1001] return system-view [routera] in...
Page 2365
Troubleshooting 2365 [sysname[routerb-voice-dial-entity2001] quit [sysname[routerb-voice-dial] quit [sysname[routerb-voice] gk-client # configure the gateway alias, and the name and ip address of the gatekeeper. [routerb-voice-gk] gw-address 2.2.2.2 [routerb-voice-gk] gw-id cityb-gw [routerb-voice-g...
Page 2366
2366 c hapter 136: h.323 c onfiguration.
Page 2367: 137
137 sip o verview when configuring sip, go to these sections for information you are interested in: ■ “introduction to sip” on page 2367 ■ “sip ua configuration” on page 2373 ■ “displaying and maintaining sip uas” on page 2379 ■ “sip ua configuration examples” on page 2379 ■ “troubleshooting” on pag...
Page 2368
2368 c hapter 137: sip o verview terms multimedia session according to rfc2327, “a multimedia session is a set of multimedia senders and receivers and the data streams flowing from senders to receivers. A multimedia conference is an example of a multimedia session.” a session is identified by a set ...
Page 2369
Introduction to sip 2369 registrar a registrar records the location information of uas for proxy servers to retrieve. In some simple applications, the registrar and the associated proxy server are usually co-located. Functionality and features of sip functions sip supports five facets of establishin...
Page 2370
2370 c hapter 137: sip o verview ■ easy to install and maintain. Even unprofessional individuals can install and maintain sip systems. Sip messages sip messages, falling into sip request messages and sip response messages, are encoded in text mode. Sip request messages include invite, ack, options, ...
Page 2371
Introduction to sip 2371 figure 686 message exchange for a ua to register with a registrar call setup sip operates in client/server model and sets up calls through ua-proxy server communication. N a sip endpoint is called ua when it acts as both uac and uas. Normally, a sip endpoint plays both roles...
Page 2372
2372 c hapter 137: sip o verview figure 688 illustrates the complete call setup procedures. Figure 688 call setup procedures involving a proxy server this is a simplified scenario where only one proxy server is involved and no registrar is present. A complex scenario, however, may involve multiple p...
Page 2373
Sip configuration task list 2373 figure 689 call redirection procedure for uas this is a common application. Fundamentally, a redirect server can respond with the address of a proxy server as well. The subsequent call procedures are the same as the call procedures involving proxy servers. Sip config...
Page 2374
2374 c hapter 137: sip o verview a ua registers with the registrar by sending a register request containing such information as address, route, and number. Thus, when it is called by some other ua through a proxy server, the proxy server can consult the registrar for its registration information. Th...
Page 2375
Sip ua configuration 2375 configure sip authentication information in voice entity view follow these steps to configure sip authentication information in pots entity view: configuring registrar information on sip ua configuration prerequisites the configuration on the sip server is completed. Config...
Page 2376
2376 c hapter 137: sip o verview configuring fuzzy telephone number registration the fuzzy telephone number registration refers to the use of a wildcard (including the dot . And the character t), rather than a standard e.164 number in the match template of a pots entity. After enabling fuzzy telepho...
Page 2377
Sip ua configuration 2377 configuring out-of-band sip dtmf code transmission mode during the communication between caller and callee, dual tone multi-frequency (dtmf) codes can be transmitted transparently between them in two ways: in-band and out-of-band. In the in-band approach, dtmf is encoded in...
Page 2378
2378 c hapter 137: sip o verview configuration prerequisites none configuration procedure follow these steps to configure a domain name of the sip ua: configuring sip compatibility for interoperability with the devices of other vendors, you need to configure the sip compatibility option. Configurati...
Page 2379
Displaying and maintaining sip uas 2379 displaying and maintaining sip uas sip ua configuration examples this section provides two configuration examples: ■ “configuring direct calling for sip uas” on page 2379 ■ “configuring proxy server involved calling for sip uas” on page 2380 configuring direct...
Page 2380
2380 c hapter 137: sip o verview system-view [routera] interface ethernet 1/0 [routera-ethernet1/0] ip address 192.168.2.1 255.255.255.0 # configure voice entities [routera-ethernet1/0] quit [routera] voice-setup [routera-voice] dial-program [routera-voice-dial] entity 2222 voip [routera-voice-dial-...
Page 2381
Sip ua configuration examples 2381 configuration procedure n ■ routing-related configurations are beyond the scope of this example. This example assumes that router a, router b, and the sip server are reachable to each other. ■ the configuration of sip server is not dealt with in this example becaus...
Page 2382
2382 c hapter 137: sip o verview # configure voice entities [routerb-voice] dial-program [routerb-voice-dial] entity 2222 pots [routerb-voice-dial-entity2222] line 1/0 [routerb-voice-dial-entity2222] match-template 2222 [routerb-voice-dial-entity2222] quit [routerb-voice-dial]entity 1111 voip [route...
Page 2383
Troubleshooting 2383 failed to set up point-to-point calls symptom the ua could not set up point-to-point calls. Solution check that the ip address and the port number of the remote voice gateway are correctly configured. Failed to send register requests symptom the ua does not send register message...
Page 2384
2384 c hapter 137: sip o verview.
Page 2385: 138
138 v o fr c onfiguration overview voice over frame relay (vofr) enables a router to transmit voice and voice-band data (for example, fax data and analog data from a modem) over a frame relay network. When voice traffic is sent over frame relay, it is segmented and encapsulated for transmission acro...
Page 2386
2386 c hapter 138: v o fr c onfiguration and voice by using frf.11. Figure 693 shows the protocols and standards that vofr complies with. Figure 693 protocols and standards that vofr complies with call flow in dynamic mode the following shows the call flow in the dynamic mode: 1 the calling party pi...
Page 2387
Configuration task lists 2387 no signaling exchange is involved in frf.11 trunk mode. The following shows the call flow in the frf.11 trunk mode, with the first four steps being the same as those in the dynamic mode: 1 the calling party picks up the phone. The voice interface card detects the off-ho...
Page 2388
2388 c hapter 138: v o fr c onfiguration configuring basic functions follow these steps to configure the basic functions of the vofr entity: configuring dtmf transmission follow these steps to configure the dtmf transmission for the vofr entity: to do... Use the command... Remarks enter system view ...
Page 2389
Configuring vofr voice bandwidth 2389 n ■ in the dynamic mode, the dtmf transmission mode is determined by the configuration of the vofr entity on the originating side. ■ in the frf.11 trunk mode, the dtmf transmission mode is determined by the configurations of the vofr entities on the originating ...
Page 2390
2390 c hapter 138: v o fr c onfiguration follow these steps to configure vofr voice bandwidth: n for frame relay class operation, refer to “frame relay qos configuration” on page 1709 and “frame relay configuration” on page 235 . The bandwidth occupied by a call is related to the codec. Table 91 lis...
Page 2391
Configuring dynamic mode 2391 configuring dynamic mode configuring huawei-compatible mode configuration prerequisites before configuring huawei-compatible vofr, complete the following tasks: ■ configure pots entities ■ configure vofr entities configure a call mode follow these steps to configure a c...
Page 2392
2392 c hapter 138: v o fr c onfiguration configure vofr packets to carry a timestamp follow these steps to configure vofr packets to carry a timestamp: configuring nonstandard-compatibl e mode configuration prerequisites before configuring nonstandard compatible vofr, complete the following tasks: ■...
Page 2393
Configuring frf.11 trunk mode 2393 configure cid selection mode refer to “configure a cid selection mode” on page 2391 . Configure vofr packets to carry a sequence number the terminating voice gateway can determine whether any voice packet loss, duplicate voice packet, or out-of-sequence occurs acco...
Page 2394
2394 c hapter 138: v o fr c onfiguration configuring pstn-dialed number follow these steps to configure a pstn-dialed number: configuring call control protocol follow these steps to configure a call control protocol: n ■ in the frf.11 trunk mode, if the vofr call control protocol is huawei-compatibl...
Page 2395
Displaying and maintaining vofr 2395 number or signaling sub-channel number. In the frf.11 trunk mode, the motorola-compatible protocol is not supported. ■ in the frf.11 trunk mode, two voice entities (one vofr entity and one voice entity of any type) must be configured at each end of the trunk. The...
Page 2396
2396 c hapter 138: v o fr c onfiguration serves as data circuit-terminating equipment (dce) and router b serves as data terminal equipment (dte). Network diagram figure 694 network diagram for huawei-compatible vofr configuration procedure 1 configure router a. # create a new frame relay class “vofr...
Page 2397
Vofr configuration example 2397 2 configure router b. # create a new frame relay class “vofr” and set the maximum amount of voice bandwidth. System-view [routerb] fr class vofr [routerb-fr-class-vofr] voice bandwidth 32000 reserved [routerb-fr-class-vofr] quit # enter interface serial 1/0 view and c...
Page 2398
2398 c hapter 138: v o fr c onfiguration network diagram figure 695 network diagram for nonstandard-compatible vofr configuration procedure 1 configure router a. # create a new frame relay class “vofr” and set the maximum amount of voice bandwidth. System-view [routera] fr class vofr [routera-fr-cla...
Page 2399
Vofr configuration example 2399 # configure the pots entity (0101001). [routera-voice-dial-entity755] entity 1001 pots [routera-voice-dial-entity1001] match-template 0101001 [routera-voice-dial-entity1001] line 3/0 2 configure router b. Router b is an industry-leading router and is configured accord...
Page 2400
2400 c hapter 138: v o fr c onfiguration [routera-serial2/0] fr dlci 100 [routera-fr-dlci-serial2/0-100] fr-class vofr # specify the call control protocol to be used by dlci 100 as huawei-compatible (dce). [routera-fr-dlci-serial2/0-100] vofr huawei-compatible dce [routera-fr-dlci-serial2/0-100] qui...
Page 2401
Vofr configuration example 2401 [routerb-voice-dial] entity 8 vofr [routerb-voice-dial-entity8] match-template 8 [routerb-voice-dial-entity8] call-mode static [routerb-voice-dial-entity8] address vofr-static serial 1/0 100 6 [routerb-voice-dial-entity8] trunk-id 07552001 [routerb-voice-dial-entity8]...
Page 2402
2402 c hapter 138: v o fr c onfiguration # configure the fragment size of data packets in the case that the voice function is enabled. [routera-fr-class-vofr] fragment 100 voice-level [routera-fr-class-vofr] quit # enter interface serial 1/0 view and configure the encapsulation format and the ip add...
Page 2403
Vofr configuration example 2403 [routerb-fr-class-vofr] fragment 200 data-level # configure the fragment size of data packets in the case that the voice function is enabled. [routerb-fr-class-vofr] fragment 100 voice-level [routerb-fr-class-vofr] quit # enter interface serial 1/0 view and configure ...
Page 2404
2404 c hapter 138: v o fr c onfiguration troubleshooting vofr call failure in huawei-compatible mode symptom calls cannot be connected in huawei-compatible mode analysis in the huawei-compatible mode, calls can be connected only when the frame relay is normal, voice entities are configured correctly...
Page 2405: 139
139 v oice radius c onfiguration overview fundamentals introduction to voice radius remote access dial in user service (radius) is a protocol standard developed for implementing authentication, authorization and accounting (aaa) for access users, who can be ppp users or voice users. The voice radius...
Page 2406
2406 c hapter 139: v oice radius c onfiguration as shown in figure 698 , the entire call setup process is as follows: 1 the calling party (1000) who originates a call from pstn dials the called number 1001. The originating gateway receives the called number and determines that the called party is no...
Page 2407
Overview 2407 message exchange in the entire process is quite complicated, access procedures differ, aaa fails, calls are exceptionally terminated, or the called party hangs up. Obviously, radius cannot operate normally without the radius server. Aaa messages exchanged between the voice gateway and ...
Page 2408
2408 c hapter 139: v oice radius c onfiguration ■ card number/password process: the calling party first dials an access number. The voice gateway plays a prompt tone. The calling party enters a card number and password as prompted, and then dials a called number. The voice gateway originates a call ...
Page 2409
Voice radius configuration task list 2409 voice radius configuration task list n for specific configurations of the radius server, refer to “configuring radius” on page 1769 . When configuring voice radius, pay attention to the sequence and the applicable scope of configuration tasks. ■ the authenti...
Page 2410
2410 c hapter 139: v oice radius c onfiguration ■ configure the accounting method ■ configure a rule for saving cdrs the configuration tasks for the one-stage dialing process include: ■ enter voice aaa client view ■ enable the authentication function for one-stage dialing users ■ enable the authoriz...
Page 2411
Configuring voice radius 2411 configuring voice radius configuring accounting method the radius client (voice gateway) processes radius accounting requests and responses in multiple ways. The radius client sends accounting messages to the radius server in different ways at different accounting time....
Page 2412
2412 c hapter 139: v oice radius c onfiguration n ■ for direct inward dialing (did), it is unnecessary to dial an access number before a called number, relative to two-stage dialing. ■ if you want to prohibit users from making calls when their account balance in the radius server which is a composit...
Page 2413
Configuring voice radius 2413 configuration prerequisites a voice interface card (for example, an fxs interface card) is inserted in the router. The authentication function is enabled for one-stage dialing users. Authentication is a prerequisite for authorization. The authentication function must be...
Page 2414
2414 c hapter 139: v oice radius c onfiguration n at most 500 cdrs can be saved in a voice gateway. That is to say, the number of cdrs saved in the voice gateway cannot exceed 500 even if none of the saved cdrs has reached the lifetime. In the case that bursty traffic is generated during a period of...
Page 2415
Configuring voice radius 2415 configuration prerequisites you have configured an access number. Configuration procedure follow these steps to configure a two-stage dialing process: enabling accounting function for two-stage dialing users after configuring access numbers, you can enable the radius ac...
Page 2416
2416 c hapter 139: v oice radius c onfiguration configuration prerequisites you have configured an access number. Configuration procedure follow these steps to enable the authentication function for two-stage dialing users: n the authentication function for two-stage dialing users is enabled for a s...
Page 2417
Configuring voice radius 2417 n the authorization function for two-stage dialing users is enabled for a specific access number, while the authorization function for one-stage dialing users is enabled in voice aaa client view configuring method of collecting digits of called number you can use the ca...
Page 2418
2418 c hapter 139: v oice radius c onfiguration configuration procedure follow these steps to configure the number of digits in a card number and that in a password: n ■ the card-digit and password-digit commands apply only to the card number/password process. They are unavailable in the case of the...
Page 2419
Configuring voice radius 2419 n pay attention to the following points when configuring the number of redial attempts ■ for the card number/password process, the number of redial attempts applies to each dial step, including selecting a language option, and dialing a card number, password, or called ...
Page 2420
2420 c hapter 139: v oice radius c onfiguration displaying and maintaining voice radius voice radius configuration example card number/password process configuration network requirements local telephone users are connected to voice subscriber lines of routers directly or via pbxs. The routers are co...
Page 2421
Voice radius configuration example 2421 network diagram figure 699 network diagram for card number/password process configuration configuration procedure 1 configure the voice gateway router a. # create a radius scheme. System-view [routera] radius scheme sch1 # configure an access password for acce...
Page 2422
2422 c hapter 139: v oice radius c onfiguration # configure the access number and set the dialing process to the card number/password process. [routera-voice] dial-program [routera-voice-dial] gw-access-number 12345 [routera-voice-dial-anum12345] process-config cardnumber # configure the number of d...
Page 2423
Troubleshooting voice radius 2423 [routerb-radius-sch1] server-type extended # configure the radius scheme in the default domain. [routerb] domain system [routerb-isp-system] authentication voip radius-scheme sch1 [routerb-isp-system] authorization voip radius-scheme sch1 [routerb-isp-system] accoun...
Page 2424
2424 c hapter 139: v oice radius c onfiguration follow the steps below to remove the fault: 1 use the display voice access-number command to check that the current settings are correct. 2 check that the radius server (cams) works normally. For example, check that an ip service module is installed on...
Page 2425: 140
140 c all s ervices c onfiguration introduction to call services more and more voip-based services are demanded as voice application environments expand. On basis of basic calls, new features are implemented to meet different application requirements of voip users. So far, the new features include: ...
Page 2426
2426 c hapter 140: c all s ervices c onfiguration currently, the system supports four different types of call forwarding. ■ call forwarding unconditional: with this feature enabled on a voice subscriber line, incoming calls will be forwarded to the predetermined destination, no matter whether the vo...
Page 2427
Call services configuration task list 2427 call services configuration task list for the service features of call waiting, call forwarding, incoming call barring, and outgoing call barring, the system supports two configuration methods. ■ one is that the system administrator performs configurations ...
Page 2428
2428 c hapter 140: c all s ervices c onfiguration n currently, the device supports the call waiting configuration for the fxs voice subscriber line on telephone terminals. After you enable call waiting on a telephone, you can view the corresponding operation result by using the display this command ...
Page 2429
Configuring call hold 2429 system-view [sysname]voice-setup [sysname-voice]subscriber-line 1/0 [sysname-voice-line1/0]call-waiting enable configuring call hold configuration prerequisites the router is equipped with an fxs voice interface card. Configuring call hold using command lines follow these ...
Page 2430
2430 c hapter 140: c all s ervices c onfiguration system-view [sysname]voice-setup [sysname-voice]subscriber-line 1/0 [sysname-voice-line1/0]call-hold enable configuring call forwarding the device supports four different types of call forwarding, which basically cover all scenarios. The device suppo...
Page 2431
Configuring call forwarding 2431 enabling call forwarding no reply follow these steps to enable call forwarding no reply: enabling call forwarding busy follow these steps to enable call forwarding busy: enabling call forwarding unavailable configuring call forwarding priority level follow these step...
Page 2432
2432 c hapter 140: c all s ervices c onfiguration n ■ currently, a priority level applies to only the features of call waiting, call forwarding, and hunt group. ■ by default, the priority levels for hunt group, call forwarding, and call waiting are 1, 2, and 3 respectively. The smaller the value is,...
Page 2433
Configuring call transfer 2433 [sysname-voice-line2/0] call-forwarding unavailable enable forward-n umber 3000 configuring call transfer configuration prerequisites ■ the router is equipped with an fxs voice interface card. ■ the call hold feature is enabled for the voice subscriber line of the call...
Page 2434
2434 c hapter 140: c all s ervices c onfiguration enabling hunt group follow these steps to enable hunt group: configuring hunt group priority level follow these steps to configure a hunt group priority level: n ■ currently, a priority level applies to only the features of call waiting, call forward...
Page 2435
Configuring outgoing call barring 2435 ■ users perform configurations by using keys on a telephone terminal. ■ the system administrator performs configurations by using command lines on the device. Configuration prerequisites the router is equipped with an fxs voice interface card. Enabling/disablin...
Page 2436
2436 c hapter 140: c all s ervices c onfiguration ■ the system administrator performs configurations by using command lines on the device. Configuration prerequisites the router is equipped with an fxs voice interface card. Enabling/disabling outgoing call barring using keys use the following keys t...
Page 2437
Configuring feature service 2437 symbol “*”. After the setting is completed, you will hear the system playing tones indicating the setting succeeds or fails. Configuration prerequisites the router is equipped with an fxs voice interface card. Enabling/disabling feature service setting using keys use...
Page 2438
2438 c hapter 140: c all s ervices c onfiguration configuring feature service using command lines follow these steps to configure the feature service: configuration example 3com voice systems are connected with a 3com server. Telephone a wants to implement the 3com feature service. # enter voice sub...
Page 2439
Call services configuration example 2439 call services configuration example call forwarding busy network requirements telephone a calls telephone b. Router b forwards the call to telephone c when telephone b is too busy to answer the call. Finally, telephone a and telephone c start a conversation. ...
Page 2440
2440 c hapter 140: c all s ervices c onfiguration system-view [routerb] voice-setup [routerb-voice] subscriber-line 1/0 [routerb-voice-line1/0] call-forwarding on-busy enable forward-numbe r 3000 3 configure router c. System-view [routerc] voice-setup [routerc-voice] dial-program [routerc-voice-dial...
Page 2441
Call services configuration example 2441 [routera-voice-dial-entity3000] quit [routera-voice-dial] entity 1000 pots [routera-voice-dial-entity1000] line 1/0 [routera-voice-dial-entity1000] match-template 1000 # enable call hold and call transfer. System-view [routera] voice-setup [routera-voice] sub...
Page 2442
2442 c hapter 140: c all s ervices c onfiguration network diagram figure 702 network diagram for hunt group configuration procedure 1 configure router a. # configure the voice entity with a higher priority. System-view [routera] voice-setup [routera-voice] dial-program [routera-voice-dial] entity 10...
Page 2443
Call services configuration example 2443 [routerb-voice-dial] entity 1000 voip [routerb-voice-dial-entity1000] address sip ip 10.1.1.1 [routerb-voice-dial-entity1000] match-template 1000 [routerb-voice-dial-entity1000] quit [routerb-voice-dial] entity 2000 pots [routerb-voice-dial-entity2000] line 1...