- DL manuals
- ABB
- Inverter
- GMS600
- Manual
ABB GMS600 Manual
Summary of GMS600
Page 1
— relion® 650 series gms600 version 1.3 cyber security deployment guideline.
Page 3
Document id: 1mrk 511 454-uen issued: november 2017 revision: a product version: 1.3 © copyright 2017 abb. All rights reserved.
Page 4
Copyright this document and parts thereof must not be reproduced or copied without written permission from abb, and the contents thereof must not be imparted to a third party, nor used for any unauthorized purpose. The software and hardware described in this document is furnished under a license and...
Page 5
Disclaimer the data, examples and diagrams in this manual are included solely for the concept or product description and are not to be deemed as a statement of guaranteed properties. All persons responsible for applying the equipment addressed in this manual must satisfy themselves that each intende...
Page 6
Conformity this product complies with the directive of the council of the european communities on the approximation of the laws of the member states relating to electromagnetic compatibility (emc directive 2004/108/ec) and concerning electrical equipment for use within specified voltage limits (low-...
Page 7
Table of contents section 1 introduction.......................................................................3 this manual........................................................................................ 3 document revision history...............................................................
Page 8
Event types.......................................................................................33 section 6 local hmi use................................................................ 37 logging on........................................................................................37 logging...
Page 9
Section 1 introduction guid-f68e2f07-fb9f-4a24-92e2-5ed05f4a8162 v2 1.1 this manual guid-9ff63f88-086d-41d9-8980-43573ee42430 v2 cyber security deployment guidelines describes password procedures and levels of access in the system. 1.2 document revision history guid-52a4699c-f83b-48f8-bf4e-d853043ab...
Page 10
4.
Page 11
Section 2 security in substation automation 2.1 general security in substation automation guid-d156d1ea-15ef-4700-b6e2-8a316a7c3288 v1 the electric power grid has evolved significantly over the past decade thanks to many technological advancements and breakthroughs. As a result, the emerging “smart ...
Page 12
Iec12000189-2-en.Vsd iec12000189 v2 en-us figure 1: system architecture for substation automation system section 2 1mrk 511 454-uen a security in substation automation 6 gms600 1.3 cyber security deployment guideline.
Page 13
Section 3 secure system setup 3.1 physical interfaces guid-da029f79-3173-4d17-a7b9-aa213fac8f68 v1 to reduce exposure for cyber-attacks and thus comply with cyber security requirements, it must be possible to prevent services in the ied from operating on other physical interfaces than the ones speci...
Page 14
Port protocol default state front rear service comment 2102 tcp open on on pcm access (ied configuration protocol) ied configuration protocol 20 000 tcp closed off on dnp3 dnp3.0 dnp communication 20 000 udp closed off on dnp3 dnp3.0 dnp communication 1) when the ied is configured as a sntp client i...
Page 15
Ip routing is not possible via any of the physical interfaces. Some ip ports are not possible to use in all physical interfaces. Aj:3 - - ' · - · . ...... . ... . ,,..,.,,oc,, -- · 1u,,- _ ... ,.,...., ;::;,.,.--- ., _ , . U - a d = = m d gms600 = iec12000172 v2.1.1 en-us figure 2: ethernet port u...
Page 16
The automatic negotiation mode acts on configured port number 21 and server features, it tries to negotiate with explicit tls via auth tls. If the specified port is any other, it tries to negotiate in a similar way. Using ftp without tls encryption gives the ftp client reduced capabilities. This mod...
Page 17
3.6 certificate handling guid-c9f2cfbf-1a4a-4237-a37f-50064a6e1e65 v1.1.1 a self-signed certificate is signed by the ied itself. Certificates use encryption to provide secure communication over the network. The certificate is always trusted during communication between the ied and pcm600. If windows...
Page 18
12.
Page 19
Section 4 managing user roles and user accounts 4.1 authorization guid-981a881d-9229-45e8-9ee5-d6df2ca457e5 v1.1.1 the user roles with different user rights are predefined in the ied. The ied users can be created, deleted and edited only with pcm600. One user can belong to one or several user roles....
Page 20
After three consecutive failed login attempts the user will be locked out for ten minutes before a new attempt to log in can be performed. This time is settable 10 minutes to 60 minutes. The pcm600 tool caches the login credentials after successful login for 15 minutes. During that time no more logi...
Page 21
Table 5: access rights explanation access rights explanation config – basic configuration – basic is intended for engineers that only adapt an existing configuration e.G. The i/o-configuration using smt config – advanced configuration – advanced is intended for engineers that do the whole applicatio...
Page 22
In order to allow the ied to communicate with pcm600 when users are defined via the ied users tool, the access rights “useradministration” and “filetransfer — limited” must be applied to at least one user. Do not use access rights “fileloading”, “filedumping”, “file transfer (super)”, and “db access...
Page 23
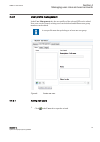
Iec13000027-1-en.Vsd iec13000027 v1 en-us figure 6: change password policies dialog box in ied users tool in pcm600 4.4 ied user management guid-b3a1a9f3-7f76-413c-a9a1-e090b90a8b3a v2 the ied users tool in pcm600 is used for editing user profiles and role assignments. In the ied users tool, the dat...
Page 24
4.4.1 starting ied user management guid-58114bac-2e0b-49dd-a2ab-a50384369b38 v1 • connect the pc to the ied • start pcm600 • select an ied in the object tree • select tools/ied users or, • right-click an ied in the object tree and select ied users the ied user dialog box appears. 4.4.2 general setti...
Page 25
4.4.3 user profile management guid-74eebf57-309e-4c97-a5a0-5731e21b9cbe v2 in the user management tab, the user profiles of the selected ied can be edited. New users can be created, existing users can be deleted and different user group members can be edited. A user profile must always belong to at ...
Page 26
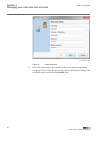
Iec12000200-1-en.Vsd iec12000200 v1 en-us figure 9: create new user 2. Follow the instructions in the wizard to define a user name, password and user group. Select at least one user group where the defined user belongs. The user profile can be seen in the user details field. Section 4 1mrk 511 454-u...
Page 27
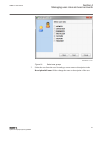
Iec12000201-1-en.Vsd iec12000201 v1 en-us figure 10: select user groups 3. Select the user from the user list and type a new name or description in the description/full name field to change the name or description of the user. 1mrk 511 454-uen a section 4 managing user roles and user accounts gms600...
Page 28
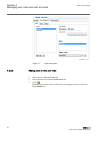
Iec12000202-1-en.Vsd iec12000202 v1 en-us figure 11: enter description 4.4.3.2 adding users to new user roles guid-f335590a-eac7-42e2-ac6b-c0051fd21d05 v2.1.1 1. Select the user from the users list. 2. Select the new role from the select a role list. 3. Click . Information about the roles to which t...
Page 29
Iec12000203-1-en.Vsd iec12000203 v1 en-us figure 12: adding user 4.4.3.3 deleting existing users guid-472bf39b-ddac-4d88-9b74-e6c49d054524 v2.1.1 1. Select the user from the users list. 1mrk 511 454-uen a section 4 managing user roles and user accounts gms600 1.3 23 cyber security deployment guideli...
Page 30
Iec12000204-1-en.Vsd iec12000204 v1 en-us figure 13: select user to be deleted 2. Click . Iec12000205-1-en.Vsd iec12000205 v1 en-us figure 14: delete existing user section 4 1mrk 511 454-uen a managing user roles and user accounts 24 gms600 1.3 cyber security deployment guideline.
Page 31
4.4.3.4 changing password guid-6180d722-cc49-445b-b520-bad8904a60af v2.1.1 1. Select the user from the users list. Iec12000206-1-en.Vsd iec12000206 v1 en-us figure 15: select user 2. Click . 3. Type the old password once and the new password twice in the required fields. The passwords can be saved i...
Page 32
Iec12000207-1-en.Vsd iec12000207 v1 en-us figure 16: change password 4.4.4 user role management guid-213fbf87-3268-42e6-88b0-8ee260127b08 v2 in the roles tab, the user roles can be modified. The user's memberships to specific roles can be modified with a list of available user roles and users. Iec12...
Page 33
4.4.4.1 adding new users to user roles guid-c53b644a-6c5c-43fc-96d7-e2ca152bd84a v1 1. Select the required role from the roles list. The role profile can be seen under the role details field. 2. Select the new user from the select a user list. 3. Click . The new user is shown in the users assigned l...
Page 34
The user account data is exported to a file with user defined filename and location. Import ied user rights to an ied 1. Click import ied account data. 2. Open the previously exported file. Only users who have the right to change the user account data in pcm600 are allowed to export and import. Iec1...
Page 35
4.4.6 reading user management settings from the ied guid-26732b3e-d422-4a39-82ba-74fca1c6dd0e v1 • click the read user management settings from ied button on the toolbar. 4.4.7 saving user management settings guid-ae198606-6e71-4c77-a4e1-02b79e4270b4 v2 • select file/save from the menu. • click the ...
Page 36
30
Page 37
Section 5 user activity logging 5.1 activity logging activlog guid-bed7c3d6-6be3-4dac-84b3-92239e819cc0 v1 activlog contains all settings for activity logging. There can be 6 external log servers to send syslog events to. Each server can be configured with ip address; ip port number and protocol for...
Page 38
Name values (range) unit step default description extlogsrv5ip 0 - 18 ip address 1 127.0.0.1 external log server 5 ip-address extlogsrv6type off syslog udp/ip syslog tcp/ip cef tcp/ip - - off external log server 6 type extlogsrv6port 1 - 65535 - 1 514 external log server 6 port number extlogsrv6ip 0...
Page 39
Pid-3430-outputsignals v1 table 8: secalarm output signals name type description eventid integer eventid of the generated security event seqnumber integer sequence number of the generated security event 5.4 about security events guid-6d781865-211f-4009-aab1-c00c3a919e49 v1 relevant user operations a...
Page 40
Event number acronyms gsal mapping english 2170 user_role_removed_ok user role assignment removed successfully 2210 user_pw_change_ok gsal.Svcviol user password changed successfully 2220 user_pw_change_fail gsal.Svcviol change of user password failed 5110 manual_reset gsal.Ina manual reset 5120 rese...
Page 41
Event number acronyms gsal mapping english 13500 read_firmw_ok firmware files read/exported from the device successfully 13520 transfer_certs_ok certificates transferred to the device successfully 13580 read_certs_ok exported/read certificates from device successfully 14200 transfer_config_fail fail...
Page 42
36.
Page 43
Section 6 local hmi use guid-9d51f5a5-b05a-4bec-9e71-8bd0beb87764 v2 at delivery, logging on is not required and the user has full access until users and passwords are created with pcm600 and written into the ied. The lhmi is logged on as superuser by default until other users are defined. Commands,...
Page 44
Upper and lower case letters are also found by scrolling the 255 characters with and . Iec12000157-3-en.Vsd iec12000157 v3 en-us figure 23: entering the password passwords are case sensitive. Only characters a - z, a - z and 0 - 9 shall be used in user names. User names are not case sensitive. For p...
Page 45
6.2 logging off guid-0fddb51b-d1c2-4442-aae5-865bc39ae253 v1 the user is automatically logged off after the display timeout. The ied returns to a state where only reading is enabled. Manual logoff is also possible. 1. Press . 2. To confirm logoff, select yes and press . Iec12000159-3-en.Vsd iec12000...
Page 46
6.4 recovering password guid-51505ce4-c9ff-40e9-b903-2b0ad4a2dab0 v2 in case of password loss or any other file system error that prevents the ied from working properly, the whole file system can be restored to ied default state. All the default settings and configuration files stored in the ied at ...
Page 47
Iec12000170-4-en.Vsdx iec12000170 v4 en-us figure 29: turn off authority 6. Select ok to turn off the authority and press . Iec12000169-4-en.Vsdx iec12000169 v4 en-us figure 30: confirm selection 7. Press to continue the startup sequence, (now the authority is temporarily disabled until next reboot ...
Page 48
When revert to ied defaults is selected the ied restores the factory ied default settings and restarts. Restoring can take several minutes. Confirmation of the restored factory ied default settings is shown on the display for a few seconds, after which the ied restarts. Section 6 1mrk 511 454-uen a ...
Page 49
Section 7 webhmi use guid-03f48db5-bea9-42b3-9f4b-1ecb28f934b9 v1 7.1 logging on guid-9334e32e-7a62-44ca-8b31-383e74d48f39 v1.1.1 user can login to webhmi using the url https://. Ip_address is the ip address of the interface used. Since ied uses self-signed certificate, the web page will ask the use...
Page 50
Iec17000151 -1-en.Vsdx iec17000151 v1 en-us 7.2 changing settings guid-7ba265b7-cbba-4248-928b-44453a52d929 v1 to enable change of settings from web, enable the writemode parameter under main menu/configuration/hmi/webserver/webserver:1. To edit the setting, navigate to the function under setting or...
Page 51
Iec17000154-1-en.Vsdx iec17000154 v1 en-us 2. Change the parameter and click on write to ied. Iec17000155-1-en.Vsdx iec17000155 v1 en-us 7.3 logging off guid-08d3e3f3-033a-47d9-9028-d4833f2a5f70 v1 click logout on top right corner of the web page to logout. 1mrk 511 454-uen a section 7 webhmi use gm...
Page 52
46.
Page 53
Section 8 ieee compliance statement guid-716dc304-b1c7-417e-ba01-df9c5ad6660a v1 8.1 ieee1686 compliance guid-009dc366-9abb-430b-a71c-aa4e5fd1b631 v2.1.1 table 10: ieee1686 compliance clause title status comment 5 ied cyber security features acknowledge 5.1 electronic access control acknowledge 5.1....
Page 54
Clause title status comment 5.1.6 d) configuration change comply feature is accessible through individual user accounts. 5.1.6 e) firmware change comply feature is accessible through individual user accounts. 5.1.6 f) id/password or rbac management comply feature is accessible through individual use...
Page 55
Clause title status comment 5.3.3 a) unsuccessful login attempt comply 5.3.3 b) reboot comply a start-up event is created every boot 5.3.3 c) attempted use of unauthorized configuration software exception client certificates are not in use 5.3.3 d) invalid configuration or firmware download comply 5...
Page 56
Clause title status comment 5.4.4 encrypting serial communications comply feature not supported 5.4.5 protocol-specific security features comply 5.5 ied configuration software acknowledge 5.5.1 authentication exception ied can be configured using unauthorized copies of the configuration software. Ho...
Page 57
Section 9 glossary guid-2282ae1e-7e51-4f9f-8066-70614fb38695 v1.1.1 aes advanced encryption standard (aes) is a specification for the encryption of electronic data. The key size used for an aes cipher specifies the number of repetitions of transformation rounds that convert the input, called the pla...
Page 58
En 60255-27 electromagnetic compatibility (emc) - product standard for measuring relays and protection equipment. Esd electrostatic discharge ftp file transfer protocol (ftp) is a standard network protocol used to transfer files from one host or to another host over a tcp-based network, such as the ...
Page 59
2. Ingression protection, according to iec standard ip 20 ingression protection, according to iec standard, level 20 iso 9001 set of standards for quality management. It information technology lan local area network led light-emitting diode lhmi local human machine interface, also local hmi. Microsc...
Page 60
Layer for the transport layer, using asymmetric cryptography for key exchange, symmetric encryption for confidentiality, and message authentication codes for message integrity. Syslog syslog is a standard for computer data logging. Syslog can be used for computer system management and security audit...
Page 61
55.
Page 62
— abb ab grid automation products 721 59 västerås, sweden phone: +46 (0) 21 32 50 00 abb.Com/protection-control © copyright 2017 abb. All rights reserved. Specifications subject to change without notice. 1mrk 511 45 4-uen.