Conceptronic 300N Wireless LAN Broadband Router User Manual
Summary of 300N Wireless LAN Broadband Router
Page 1
Conceptronic 150 n wireless lan broadband router user’s manual version: 3.0
Page 2: Contents
Contents chapter i: introduction 1-1. Product features 1-2. Safety information 1-3. Package contents 1-4. Familiar with your new wireless broadband router 1-4-1. Front panel 1-4-2. Back panel chapter ii: system and network setup 2-1. Build network connection 2-2. Connecting to wireless broadband rou...
Page 3
Chapter iv: configuration – wireless 4-1. Wireless - basic 4-2. Wireless - security 4-2-1. Wep 4-2-2. Wpa-psk (personal) 4-2-3. Wpa2-psk (personal) 4-2-4. Mixed wpa-psk / wpa2-psk (personal) 4-2-5. Wpa (enterprise) 4-2-6. Wpa2 (enterprise) 4-2-7. Mixed wpa / wpa2 (enterprise) 4-2-8. 802.1x 4-3. Wire...
Page 4
Chapter vi: configuration – tools 6-1. Tools - admin 6-2. Tools - time settings 6-3. Tools - backup / restore 6-4. Tools - upgrade 6-5. Tools - restore to factory 6-6. Tools - reboot chapter vii: configuration – status 7-1. Status - dhcp client 7-2. Status - wireless client 7-3. Status - traffic sta...
Page 5: Chapter I: Introduction
1 chapter i: introduction thank you for purchasing the conceptronic c150brs4 wireless broadband router! The conceptronic c150brs4 utilizes advanced mimo technology and increases over 8 times transmission range of ordinary 802.11g products. Compatible with ieee802.11n (draft 4.0) and ieee802.11g/b st...
Page 6
2 1-1. Product features includes router, wireless access point, four-port switch and firewall in one provides up to 150mbps uploading and downloading speed supports two wps (wi-fi protected setup) encryption methods: pbc and pin compliant to ieee802.11n, ieee802.11g, ieee802.11b, ieee802.3 and ieee8...
Page 7
3 1-2. Safety information in order to keep the safety of users and your properties, please follow the following safety instructions: this router is designed for indoor use only; do not place this router outdoor. Do not put this router at or near hot or humid places, like kitchen or bathroom. Also, d...
Page 8
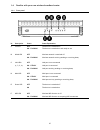
4 1-4. Familiar with your new wireless broadband router 1-4-1. Front panel nr description status status explanation a sys led off the device is switched off on – flashing the device is switched on and ready to use b wlan led off wireless network is switched off on - flashing wireless network activit...
Page 9
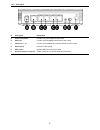
5 1-4-2. Back panel nr description explanation a power connection connect the power supply to the router b wan port connect your broadband connection to the router c lan ports (1 – 4) connect your computer(s)/network device(s) to the router d reset button perform a reset (hold) e wps button activate...
Page 10
6 chapter ii: system and network setup 2-1. Build network connection please follow the following instruction to build the network connection between your new wireless router and your computers, network devices: a. Connect your xdsl / cable modem to the wan port of router by ethernet cable. B. Connec...
Page 11
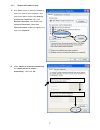
7 2-2-1. Windows xp ip address setup: a. Click „start‟ button (it should be located at lower-left corner of your computer), then click control panel. Double-click network and internet connections icon, click network connections, then double-click local area connection, local area connection status w...
Page 12
8 2-2-2. Windows vista ip address setup: a. Click „start‟ button (it should be located at lower-left corner of your computer), then click control panel. Click view network status and tasks, and then click manage network connections. Right-click local area network, then select ‘properties’. Local are...
Page 13
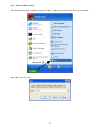
9 2-2-3. Router ip address lookup after the ip address setup is complete, please click „start‟ -> „run‟ at the bottom-lower corner of your desktop: input „cmd‟, then click „ok‟.
Page 14
10 input „ipconfig‟, then press „enter‟ key. Please check the ip address followed by „default gateway‟ (in this example, the ip address of router is 192.168.0.1, please note that this value may be different.) note: if the ip address of gateway is not displayed, or the address followed by „ip address...
Page 15
11 when the user name and password are correct the wireless router will show the main page with the status of the wireless router: on the main page, you can see the status of the internet connection, the system status, firmware version and activated services. Note: by default, the wireless router is...
Page 16
12 chapter iii: configuration - home 3-1. Home - wizard you can setup the wireless router through the built-in wizard. This wizard will help you configuring the basic settings of the wireless router step by step. Note: before starting the wizard, make sure you have all information about your interne...
Page 17
13 e. For system management purpose, a correct time setting is critical to have accurate time stamps on the system logs. Set an appropriate time zone in this step. When completed, click“next”. F. Select the internet connection method which corresponds with your provider settings. If you don‟t know w...
Page 18
14 h. When your provider requires a dynamic ip connection, select the “dynamic ip” option. Some providers require a specific hostname for their connections. If your provider requires a specific hostname, enter the host name in the field. Some providers only allow 1 specific mac address to connect to...
Page 19
15 j. When your provider requires a pptp connection, select the “pptp” option. Enter the requested information: server ip pptp account pptp password retype password when completed, click “next”. Connection - pptp k. When your provider requires a l2tp connection, select the “l2tp” option. Enter the r...
Page 20
16 you can secure your wireless connection with encryption. By default, the wireless router is secured with wpa-psk/wpa2-psk mixed mode encryption. The predefined encryption key can be found on the bottom of the router. Note: all security options of the setup wizard are explained, but it is advised ...
Page 21
17 p. When all wireless settings are made, click “next” to continue. Q. The setup wizard is now complete. If you want to apply your settings, click “save & take effect”. If you want to change any setting, click “back” to return to the previous screen. If you want to close the setup wizard without an...
Page 22
18 3-2. Home - wan in this screen, select one mode of your internet connection you use. If you are not clear, press the “detect” button or contact your internet service provider, and click “next”. 3-2-1. Adsl virtual dial-up (via pppoe) enter the account and password provided by your isp, and click ...
Page 23
19 3-2-2. Dynamic ip (via dhcp) if your connection mode is dynamic ip, it means your ip address keeps changing every time you connect. You do not need to enter the information like other modes. Click “next” and “save” to finish the settings. 3-2-3. Static ip in this screen, fill the network address ...
Page 24
20 3-2-4. L2tp l2tp server ip : enter the server ip provided by your isp. User name : enter l2tp username. Password : enter l2tp password. Mtu : maximum transmission unit, you may need to change it for optimal performance with your specific isp. 1400 is the default mtu. Address mode : select “static...
Page 25
21 3-2-5. Pptp pptp server ip : enter the server ip provided by your isp. User name : enter pptp username provided by your isp. Password : enter pptp password provided by your isp. Address mode : select “static” if your isp supplies you with the ip address, subnet mask, and gateway. In most cases, s...
Page 26
22 3-3. Home - wan advanced in the “wan advanced” page, you will find 3 sections: wan medium wan mac address clone wan connection mode.
Page 27
23 3-3-1. Wan medium in most cases, isp provides wired wan access (adsl modem, cable modem, etc.) and you only need to insert the line into the router‟s wan port. Sometime, wireless wan access type, more flexible and convenient, is also provided by some isp. Wired wan : in this type, wan port should...
Page 28
24 3-3-3. Wan connection mode after you have selected the isp connection type in “wan” and you want to modify the related settings, here you can modify and configure the settings in details. 3-3-3-1. Virtual dial-up (pppoe) connection mode : show your current connection mode. Account : enter them pr...
Page 29
25 3-4. Home - lan lan settings are for the basic tcp/ip parameters of lan ports. Mac address : the router‟s physical mac address as seen on your local network, which is unchangeable. Ip address : the router‟s lan ip addresses (not your pc‟s ip address). 192.168.0.1 is the default value. Subnet mask...
Page 30
26 3-5. Home - dns settings dns is short for domain name system (or service), an internet service that translate domain names into ip addresses which are provided by your internet service provider. Please consult your internet service provider for details if you do not have them. Dns : click the che...
Page 31
27 3-6. Home - dhcp server a dhcp (dynamic host control protocol) is to assign an ip address to the computers on the lan/private network. When you enable the dhcp server, the dhcp server will allocate automatically an unused ip address from the ip address pool to the requesting computer in premise o...
Page 32
28 chapter iv: configuration - wireless 4-1. Wireless - basic enable wireless : check to enable the router‟s wireless features; uncheck to disable it. Network mode : select one mode from the following. The default is 11b/g/n mode. 11b mode : allow the wireless client to connect with the device in 11...
Page 33
29 mbssid ap isolation : one access control feature based on wireless mac address. When this feature is enabled, wireless clients connected with the same ssid can not communicate with each other. For example, configure main ssid as ap1, minor ssid as ap2. Pc1 and pc2 connect to ap1 via wireless adap...
Page 34
30 4-2. Wireless - security it is used to configure the ap network‟s security setting. Here presents the encryption methods, including wep, wpa-personal, wpa-enterprise, wpa2-personal, wpa2- enterprise, etc. 4-2-1. Wep wep (wired equivalent privacy), a basic encryption method, usually encrypts wirel...
Page 35
31 4-2-2. Wpa-psk (personal) wpa (wi-fi protected access), a wi-fi standard, is a more recent wireless encryption scheme, designed to improve the security features of wep. It applies more powerful encryption types (such as tkip [temporal key integrity protocol], aes [advanced encryption standard]) o...
Page 36
32 4-2-3. Wpa2-psk (personal) wpa2 (wi-fi protected access version 2) provides higher security than wep (wireless equivalent privacy) and wpa (wi-fi protected access). Ssid choice : select the ssid (main ssid or minor ssid) to configure security setting from the drop-down menu. Security mode : from ...
Page 37
33 4-2-4. Mixed wpa-psk / wpa2-psk (personal) mixed wpa-psk / wpa2-psk (personal) combines the wpa-personal and wpa-2 personal security levels. Clients which support wpa2-psk (personal) will use wpa2-psk (personal), while older clients without this support can use wpa-psk (personal). Ssid choice : s...
Page 38
34 4-2-5. Wpa (enterprise) this security mode is used when a radius server is connected to the device. Ssid choice : select the ssid (main ssid or minor ssid) to configure security setting from the drop-down menu. Security mode : from the drop-down menu select the corresponding security encryption m...
Page 39
35 4-2-6. Wpa2 (enterprise) this security mode is based on radius authentication server and wpa2 encryption method. Wpa2 is used when a radius server is connected to the device. Ssid choice : select the ssid (main ssid or minor ssid) to configure security setting from the drop-down menu. Security mo...
Page 40
36 4-2-7. Mixed wpa / wpa2 (enterprise) this security mode combines wpa and wpa2 (enterprise) and is used when a radius server is connected to the device. When the client supports wpa2 (enterprise), wpa2 (enterprise) will be used. Older clients will use wpa (enterprise). Ssid choice : select the ssi...
Page 41
37 4-2-8. 802.1x this security mode is used when a radius server is connected to the device. 802.1x, a kind of port-based authentication protocol, is an authentication type and strategy for users. The port can be either a physic port or logic port (such as vlan). For wireless lan users, a port is ju...
Page 42
38 4-3. Wireless - advanced this section is to configure the advanced wireless setting of the router, including the radio preamble, 802.11g/n rate, fragmentation threshold, rts threshold, etc. Bg protection mode : auto by default. It is for 11b/g wireless client to connect 11n wireless network smoot...
Page 43
39 4-4. Wireless - wps wps (wi-fi protected setting) can be easy and quick to establish the connection between the wireless network clients and the device through encrypted contents. The users only enter pin code or press wps button on the panel to configure it without selecting encryption method an...
Page 44
40 wps encrypt type : the encryption type used by wps, generally aes/tkip. Wps key : the effective key generated by ap automatically. Ap pin(key) : the pin code used by default. Reset oob : when this button is pressed, the wps client will be idle state, and wps indicator will be turned off. Ap will ...
Page 45
41 4-6. Wireless - access control to secure your wireless lan, the wireless access control is actually based on the mac address management to allow or block the specific clients to access the wireless network. Mac address filter : enable/disable mac address filter. Select “close” to malfunction mac ...
Page 46
42 chapter v: configuration - advanced 5-1. Advanced - single port forwarding note: in the picture above, you will see an example of some port forwarding rules. The router can be configured as a virtual server on behalf of local services behind the lan port. The given remote requests will be re-dire...
Page 47
43 delete/enable : click to check it for corresponding operation. Well-known service port : select the well-known services as dns, ftp from the drop-down menu to add to the configured one above. Note: if you set the virtual server of the service port as 80, you must set the web management port on re...
Page 48
44 5-2. Advanced - port range forwarding note: in the picture above, you will see an example of some port forwarding rules. This section deals with the port range forwarding mainly. The port range forwarding allows you to set up a range of public services such as web servers, ftp, e-mail and other s...
Page 49
45 5-3. Advanced - alg service in the context of computer networking, an alg or application layer gateway consists of a security component that augments a firewall or nat employed in a computer network. It allows customized nat traversal filters to be plugged into the gateway to support address and ...
Page 50
46 5-4. Advanced - dmz the dmz function is to allow one computer in lan to be exposed to the internet for a special-purpose service as internet gaming or videoconferencing. Dmz host ip address : the ip address of the computer you want to expose. Enable : click the checkbox to enable the dmz host. Im...
Page 51
47 5-5. Advanced - upnp it supports latest universal plug and play. This function goes into effect on windows xp or windows me or this function would go into effect if you have installed software that supports upnp. With the upnp function, host in lan can request the router to process some special p...
Page 52
48 5-6. Advanced - mac filters in order to manage the computers in lan better, you could control the computer‟s access to internet by mac address filter. Mac address filter : check to enable mac address filter. Access policy : select one number from the drop-down menu. Enable : check to enable the a...
Page 53
49 5-7. Advanced - url filters in order to control the computer to have access to websites, you can use url filtering to allow the computer to have access to certain websites at fixed time and forbids it having access to certain websites at fixed time. Url filter : check to enable url filter. Access...
Page 54
50 5-8. Advanced - client filters to benefit your further management to the computers in the lan, you can control some ports access to internet by data packet filter function. Client filter : check to enable client filter. Access policy : select one number from the drop-down menu. Enable : check to ...
Page 55
51 5-9. Advanced - ddns the ddns (dynamic domain name system) is supported in this router. It is to assign a fixed host and domain name to a dynamic internet ip address, which is used to monitor hosting website, ftp server and so on behind the router. If you want to activate this function, please se...
Page 56
52 5-10. Advanced - prevent network attack this section is to protect the internal network from exotic attack such as syn flooding attack, smurf attack, land attack, etc. Once detecting the unknown attack, the router will restrict its bandwidth automatically. The attacker‟s ip address can be found f...
Page 57
53 5-12. Advanced - traffic control traffic control is used to limit communication speed in the lan and wan. Up to 20 entries can be supported with the capability for at most 254 pcs' speed control, including for ip address range configuration. Enable traffic control : to enable or disable the inter...
Page 58
54 5-13. Advanced - url monitor this feature is used to record user‟s internet activity, so in terms of this feature, the administrator can check out and control what they can do and have done. Enable url monitor : after checking this feature, the router will record lan computer‟s url information, i...
Page 59
55 5-14. Advanced - static routing this page is used to configure the router‟s static routing. Destination lan ip : the address of the remote host with which you want to construct a static route. Subnet mask : the network portion of the destination lan ip. Gateway : the gateway of the next hop, usua...
Page 60
56 chapter vi: configuration - tools 6-1. Tools - admin the “admin” page exists of 3 sections: administrator password section local web management section remote web management section administrator password section: this section is to set a new user name and password to better secure your router an...
Page 61
57 local web management section: local web management, the alternative to remote web management, is to allow the network administrator to manage the router in lan. Any pc in the lan can access the web management utility by default. So you can enter the specific mac address of the lan computer to fun...
Page 62
58 6-2. Tools - time settings this section is to select the time zone for your location. If you turn off the router, the settings for time disappear. However, the router will automatically obtain the gmt time again once it has access to the internet. Time zone : select your time zone from the drop-d...
Page 63
59 6-3. Tools - backup / restore the device provides backup/restore settings, so you need set a directory to keep these parameters. Backup setting: click “backup” button to back up the router‟s settings and select the path for save. Click “save” to save the configuration files. Restore setting: clic...
Page 64
60 6-5. Tools - restore to factory this button is to reset all settings to the default values. It means the router will lose all the settings you have set. So please note down the related settings if necessary. Restore : click this button to restore to default settings. Factory default settings: use...
Page 65
61 chapter vii: configuration - status 7-1. Status - dhcp client the static ip assignment is to add a specifically static ip address to the assigned mac address. You can view the related information in the dhcp server list. Ip address : enter the ip address which needs to be bound. Mac address : ent...
Page 66
62 7-2. Status - wireless client this page shows wireless client‟s connection status, including mac address, channel bandwidth, etc. Mac address : shows current mac addresses of the hosts connecting to the router. Bandwidth : shows current bandwidth of the hosts (wireless client). 7-3. Status - traf...
Page 67
63 7-4. Status - routing table the main duty for a router is to look for a best path for every data frame, and transfer this data frame to a destination. So, it‟s essential for the router to choose the best path, i.E. Routing arithmetic. In order to finish this function, many transferring paths, i.E...
Page 68: Chapter Viii: Appendix
64 chapter viii: appendix 8-1. Troubleshooting if you found the router is working improperly or stop responding to you, don‟t panic! Before you contact your dealer of purchase for help, please read this troubleshooting first. Some problems can be solved by you within very short time! Scenario soluti...
Page 69
65 i can‟t locate my router by my wireless client a. „broadcast essid‟ set to off? B. All two antennas are properly secured. C. Are you too far from your router? Try to get closer. D. Please remember that you have to input essid on your wireless client manually, if essid broadcast is disabled. File ...
Page 70
66 8-2. Glossary default gateway (router): every non-router ip device needs to configure a default gateway‟s ip address. When the device sends out an ip packet, if the destination is not on the same network, the device has to send the packet to its default gateway, which will then send it out toward...
Page 71
67 port: network clients (lan pc) uses port numbers to distinguish one network application/protocol over another. Below you will find a list of some common used ports and their corresponding application: port application port application 20 ftp data (ftp server) 80 http (web server) 21 ftp data (ftp...
Page 72
68 8-3. License agreement licensing information this conceptronic product c150brs4 includes copyrighted third-party software licensed under the terms of the gnu general public license. Please see the gnu general public license for the exact terms and conditions of this license. All used software pac...
Page 73
69 gnu general public license version 2, june 1991 copyright (c) 1989, 1991 free software foundation, inc. Temple place, suite 330, boston, ma 02111-1307 usa everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. Preamble the licenses f...
Page 74
70 gnu general public license terms and conditions for copying, distribution and modification 0. This license applies to any program or other work which contains a notice placed by the copyright holder saying it may be distributed under the terms of this general public license. The "program", below,...
Page 75
71 these requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the program, and can be reasonably considered independent and separate works in themselves, then this license, and its terms, do not apply to those sections when you distribute the...
Page 76
72 4. You may not copy, modify, sublicense, or distribute the program except as expressly provided under this license. Any attempt otherwise to copy, modify, sublicense or distribute the program is void, and will automatically terminate your rights under this license. However, parties who have recei...
Page 77
73 9. The free software foundation may publish revised and/or new versions of the general public license from time to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns. Each version is given a distinguishing version...
Page 78
74 how to apply these terms to your new programs if you develop a new program, and you want it to be of the greatest possible use to the public, the best way to achieve this is to make it free software which everyone can redistribute and change under these terms. To do so, attach the following notic...
Page 79
75 gnu lesser general public license version 2.1, february 1999 copyright (c) 1991, 1999 free software foundation, inc. 51 franklin street, fifth floor, boston, ma 02110-1301 usa everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed. [t...
Page 80
76 to protect each distributor, we want to make it very clear that there is no warranty for the free library. Also, if the library is modified by someone else and passed on, the recipients should know that what they have is not the original version, so that the original author's reputation will not ...
Page 81
77 gnu lesser general public license terms and conditions for copying, distribution and modification 0. This license agreement applies to any software library or other program which contains a notice placed by the copyright holder or other authorized party saying it may be distributed under the term...
Page 82
78 c) you must cause the whole of the work to be licensed at no charge to all third parties under the terms of this license. D) if a facility in the modified library refers to a function or a table of data to be supplied by an application program that uses the facility, other than as an argument pas...
Page 83
79 4. You may copy and distribute the library (or a portion or derivative of it, under section 2) in object code or executable form under the terms of sections 1 and 2 above provided that you accompany it with the complete corresponding machine-readable source code, which must be distributed under t...
Page 84
80 a) accompany the work with the complete corresponding machine-readable source code for the library including whatever changes were used in the work (which must be distributed under sections 1 and 2 above); and, if the work is an executable linked with the library, with the complete machine-readab...
Page 85
81 a) accompany the combined library with a copy of the same work based on the library, uncombined with any other library facilities. This must be distributed under the terms of the sections above. B) give prominent notice with the combined library of the fact that part of it is a work based on the ...
Page 86
82 12. If the distribution and/or use of the library is restricted in certain countries either by patents or by copyrighted interfaces, the original copyright holder who places the library under this license may add an explicit geographical distribution limitation excluding those countries, so that ...
Page 87
83 bsd license redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * redistributio...