- DL manuals
- D-Link
- Firewall
- CP310 - DFL - Security Appliance
- User Manual
D-Link CP310 - DFL - Security Appliance User Manual
Summary of CP310 - DFL - Security Appliance
Page 1
D-link netdefend firewall security vpn firewall netdefend secured by check point user guide version 1.0 revised: 01/17/2006.
Page 2
Copyright & trademarks copyright © 2005 sofaware, all rights reserved. No part of this document may be reproduced in any form or by any means without written permission from sofaware. Information in this document is subject to change without notice and does not represent a commitment on part of sofa...
Page 3
Running for such interactive use in the most ordinary way, to print or display an announcement including an appropriate copyright notice and a notice that there is no warranty (or else, saying that you provide a warranty) and that users may redistribute the program under these conditions, and tellin...
Page 4
Countries not thus excluded. In such case, this license incorporates the limitation as if written in the body of this license. 9. The free software foundation may publish revised and/or new versions of the general public license from time to time. Such new versions will be similar in spirit to the p...
Page 5: Contents
Contents contents about this guide .................................................................................................................................Xi introduction............................................................................................................................
Page 6
Contents wall mounting the appliance ...........................................................................................................30 securing the appliance against theft ...............................................................................................32 network installati...
Page 7
Contents using a dialup connection ...........................................................................................................75 using no connection....................................................................................................................77 setting up a dial...
Page 8
Contents modifying port assignments ......................................................................................................147 modifying link configurations ..................................................................................................149 resetting ports to default...
Page 9
Contents viewing computers ........................................................................................................................194 viewing connections ......................................................................................................................197 viewing...
Page 10
Contents updating vstream antivirus...........................................................................................................279 using subscription services .............................................................................................................281 connecting to...
Page 11
Contents enabling/disabling a vpn site.......................................................................................................340 logging on to a remote access vpn site......................................................................................341 logging on through the netd...
Page 12
Contents using the serial console.............................................................................................................388 configuring https ........................................................................................................................390 configuring ...
Page 13
Contents other problems ...............................................................................................................................443 specifications .....................................................................................................................................
Page 15: About This Guide
About your d-link netdefend firewall about this guide to make finding information in this manual easier, some types of information are marked with special symbols or formatting. Boldface type is used for command and button names. Note: notes are denoted by indented text and preceded by the note icon...
Page 17: Chapter 1
About your d-link netdefend firewall chapter 1 this chapter introduces the d-link netdefend firewall and this guide. Introduction this chapter includes the following topics: about your d-link netdefend firewall ......................................................1 netdefend secured by check point ...
Page 18: Connectivity
Netdefend secured by check point product family netdefend secured by check point product family the netdefend series includes the following hardware models: • dfl-cp310 security vpn firewall • dfl-cpg310 wireless security vpn firewall you can upgrade your netdefend firewall to include additional fea...
Page 19: Firewall
Netdefend features and compatibility • static nat • static routes and source routes • ethernet cable type recognition • backup internet connection • dead internet connection detection (dcd) • traffic monitoring • traffic shaping • vlan support (requires power pack) • dynamic routing (requires power ...
Page 20: Vpn
Netdefend features and compatibility • p2p file sharing blocking/monitoring vpn the netdefend series includes the following features: • remote access vpn server with officemode and radius support • remote access vpn client • site to site vpn gateway • ipsec vpn pass-through • algorithms: aes/3des/de...
Page 21: Optional Security Services
Netdefend features and compatibility optional security services the following subscription security services are available to netdefend owners by connecting to a service center: • firewall security and software updates • web filtering • email antivirus and antispam protection • vstream embedded anti...
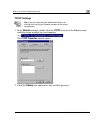
Page 22: Package Contents
Netdefend features and compatibility feature dfl-cp310/cpg310 dfl-cp310/cpg310 with power pack vlan (port/tag-based) — vpn throughput 20 mbps 30 mbps site-to-site vpn 2 tunnels 15 tunnels site-to-site vpn (managed) * 10 tunnels 100 tunnels included vpn-1 securemote client licenses 5 users 25 users *...
Page 23: Network Requirements
Netdefend features and compatibility the dfl-cpg310 also includes: • two antennas • wall mounting kit, including two plastic conical anchors and two cross- head screws • usb extension cable network requirements • a broadband internet connection via cable or dsl modem with ethernet interface (rj-45) ...
Page 24: Rear Panel
Getting to know your netdefend firewall getting to know your netdefend firewall rear panel all physical connections (network and power) to the netdefend firewall are made via the rear panel of your netdefend firewall. Figure 1: netdefend firewall rear panel items figure 2: netdefend firewall rear pa...
Page 25
Getting to know your netdefend firewall label description reset a button used for rebooting the netdefend firewall or resetting the netdefend firewall to its factory defaults. You need to use a pointed object to press this button. • short press. Reboots the netdefend firewall • long press (7 seconds...
Page 26: Front Panel
Getting to know your netdefend firewall front panel the netdefend firewall includes several status leds that enable you to monitor the appliance’s operation. Figure 3: netdefend firewall front panel for an explanation of the netdefend firewall’s status leds, see the table below. Table 2: netdefend f...
Page 27: Ear Panel
Getting to know your netdefend firewall led state explanation link/act on, 100 on 100 mbps link established for the corresponding port lnk/act flashing data is being transmitted/received vpn flashing (green) vpn port in use serial flashing (green) serial port in use getting to know your netdefend fi...
Page 28
Getting to know your netdefend firewall label description reset a button used for rebooting the netdefend firewall or resetting the netdefend firewall to its factory defaults. You need to use a pointed object to press this button. • short press. Reboots the netdefend firewall • long press (7 seconds...
Page 29: Front Panel
Getting to know your netdefend firewall front panel the netdefend firewall appliance includes several status leds that enable you to monitor the appliance’s operation. Figure 5: netdefend firewall front panel for an explanation of the netdefend firewall appliance’s status leds, see the table below. ...
Page 30: Contacting Technical Support
Contacting technical support led state explanation link/act on, 100 on 100 mbps link established for the corresponding port lnk/act flashing data is being transmitted/received vpn flashing (green) vpn port in use serial flashing (green) serial port in use usb flashing (green) usb port in use wlan fl...
Page 31: Chapter 2
Before you install the netdefend firewall chapter 2 this chapter describes how to properly set up and install your netdefend firewall in your networking environment. Installing and setting up the netdefend firewall this chapter includes the following topics: before you install the netdefend firewall...
Page 32: Windows 2000/xp
Before you install the netdefend firewall windows 2000/xp note: while windows xp has an "internet connection firewall" option, it is recommended to disable it if you are using a netdefend firewall, since the netdefend firewall offers better protection. Checking the tcp/ip installation 1. Click start...
Page 33
Before you install the netdefend firewall the network and dial-up connections window appears. 3. Right-click the icon and select properties from the pop-up menu that opens. Chapter 2: installing and setting up the netdefend firewall 17.
Page 34
Before you install the netdefend firewall the local area connection properties window appears. 4. N the components list and if it is properly configured with the ethernet card, installed on your computer. If ou must install it as described in in the above window, check if tcp/ip appears i tcp/ip doe...
Page 35
Before you install the netdefend firewall installing tcp/ip protocol 1. In the local area connection properties window click install…. The select network component type window appears. 2. Choose protocol and click add. The select network protocol window appears. 3. Choose internet protocol (tcp/ip) ...
Page 36
Before you install the netdefend firewall tcp/ip settings 1. In the local area connection properties window double-click the internet ct it and click properties. Window opens. Protocol (tcp/ip) component, or sele the internet protocol (tcp/ip) properties 2. Click the obtain an ip address automatical...
Page 37: Win
Before you install the netdefend firewall win checking the tcp/ip installation 1. Click start > settings > control panel. The control panel window appears. Dows 98/millennium 2. Double-click the icon. Chapter 2: installing and setting up the netdefend firewall 21.
Page 38
Before you install the netdefend firewall the network window appears. 3. In the network window, check if tcp/ip and if it is already configured with th appears in the network components list e ethernet card, installed on your computer. Installing tcp/ip protocol note: if tcp/ip is already installed ...
Page 39
Before you install the netdefend firewall the select network component type window appears. 2. Choose protocol and click add. The select network protocol window appears. 3. In manufacturers list choose microsoft, and in the network protocols list choose tcp/ip. 4. Click ok. If windows asks for origi...
Page 40
Before you install the netdefend firewall tcp/ip settings note: if you are connecting your netdefend firewall to an existing lan, consult your network manager for the correct configurations. 1. In the network window, double-click the tcp/ip service for the ethernet card, which has been installed on ...
Page 41
Before you install the netdefend firewall 3. Click the dns configuration tab, and click the disable dns radio button. Chapter 2: installing and setting up the netdefend firewall 25.
Page 42: Ac Os
Before you install the netdefend firewall 4. Click the ip address button. Tab, and click the obtain an ip address automatically radio note: normally, it is not recommended to assign a static ip address to your pc but rather to obtain an ip address automatically. If for some reason you need to assign...
Page 43
Before you install the netdefend firewall 1. Choose apple menus -> control panels -> tcp/ip. The tcp/ip window appears. 2. Click the connect via drop-down list, and select ethernet. 3. Click the configure drop-down list, and select using dhcp server. 4. Close the window and save the setup. Chapter 2...
Page 44: Mac Os-X
Before you install the netdefend firewall mac os-x use the following procedure for setting up the tcp/ip protocol. 1. Choose apple -> system preferences. The system preferences window appears. 2. Click network. The network window appears. 28 d-link netdefend firewall user guide.
Page 45
Before you install the netdefend firewall 3. Click configure. Chapter 2: installing and setting up the netdefend firewall 29.
Page 46: Wall M
Wall mounting the appliance tcp/ip configuration fields appear. 4. Click the configure ipv4 drop-down list, and select using dhcp. Click 5. Wall m apply now. Ounting the appliance if desired, you can mount your netdefend firewall on the wall. To mount the netdefend firewall on the wall 1. Decide whe...
Page 47
Wall mounting the appliance note: mounting the appliance facing downwards is not recommended, as dust might accumulate in unused ports. Ark two drill holes on the wall, in accordance with the following sk 3. M etch: 4. Drill two 3.5 mm diameter holes, approximately 25 mm deep. 5. Insert two plastic ...
Page 48: Securing The Applia
Securing the appliance against theft 7. Align the holes on the netdefend firewall' wall, then push your netdefend firewall is wall mounted. You can now connect it to your computer. See network installation on page 35. Securing the applia s underside with the screws on the the appliance in and down. ...
Page 49
Securing the appliance against theft while these parts may differ between devices, all looped security cables include a bolt with knobs, as shown in the diagram below: figure 7: looped security cable bolt the bolt has two states, open and closed, and is used to connect the looped security cable to t...
Page 50
Securing the appliance against theft 4. Insert the bolt into the netdefend firewall's security slot, and then slide the bolt to the closed position until the bolt holes are aligned. 5. Thread the anti-theft device's pin through the bolt’s holes, and insert the pin into the main body of the anti-thef...
Page 51: Network Installation
Network installation network installation 1. Verify that you have the correct cable type. For information, see network requirements. D of the ethernet cable to one of the lan ports at the back s. 3 back of the • connect the other end of the cable to a cable modem, xdsl modem or pwr, at the back of t...
Page 52: S Tting
Setting up the netdefend firewall 6. Netdefend firewall for a wireless connection: a. Connect the antennas that came with your netdefend firewall to the ant1 and ant2 antenna connectors in the appliance's rear panel. B. Bend the antennas at the hinges, so that they point upwards. 7. In models with a...
Page 53
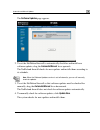
Setting up the netdefend firewall logging on to the netdefend portal and setting up your password initial login to the netdefend portal on page 39 configuring an internet connection using the internet wizard on page 54 setting the time on your netdefend firewall setting the time on the appliance on ...
Page 54
Setting up the netdefend firewall to access the setup wizard ab. The firmware page appears. 1. Click setup in the main menu, and click the firmware t 2. Click end setup wizard. Netdef the netdefend setup wizard opens with the welcome page displayed. 38 d-link netdefend firewall user guide.
Page 55: Chapter 3
Initial login to the netdefend portal chapter 3 this chapter contains all the information you need in order to get started using your netdefend firewall. This chapter includes the following topics: initial login to the netdefend portal .........................................................39 logg...
Page 56
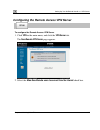
Initial login to the netdefend portal the initial login page appears. Type a password both in the password and the confirm password fields. 2. Note: the password must be five to 25 characters (letters or numbers). Note: you can change your password at any time. For further information, see changing ...
Page 57
Initial login to the netdefend portal th welcome page displayed. E netdefend setup wizard opens, with the 4. Configure y • internet e inte ou through using the , see using the internet wizard on page 54. Netdefend firewall. • internet setup internet setup offers advanced setup options, such as confi...
Page 58
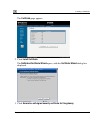
Logging on to the netdefend portal logging on to the netdefend portal note: by default, http and https access to the netdefend portal is not allowed from the wlan, unless you do one of the following: firewall rule to allow access from the wlan. See using rules on page 209. O • enable https access fr...
Page 59
Logging on to the netdefend portal the login page appears. 2. Type your username and password. 3. Click ok. Chapter 3: getting started 43.
Page 60: G The
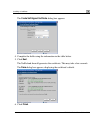
Accessing the tnetdefendt portal remotely using https the welcome page appears. G the accessin https netdefendportal remotely using you can access the netdefend portal remotely (from the internet) through https. Https is a protocol for accessing a secure web server. It is used to transfer confidenti...
Page 61
Accessing the tnetdefendt portal remotely using https note: your browser must support 128-bit cipher strength. To check your browser's cipher strength, open internet explorer and click help > about internet explorer. Cess the netdefend portal from your internal network • browse to (note that the url...
Page 62: Sing The Netdefend Portal
Using the netdefend portal the security alert dialog box reappears. The netdefend portal appears. U u to configure the netdefend firewall operation and options. Hree major elements. T ents elem h. Click yes. Sing the netdefend portal the netdefend portal is a web-based management interface, which en...
Page 63: Main Menu
Using the netdefend portal figure 9: netdefend portal main menu includes the following submenus. T this s the main menu able 6: main menu submenus does this… ubmenu… welcome displays general welcome information. R , active computers, and established connections. Securit y computer in antivirus servi...
Page 64: Ain Frame
Using the netdefend portal this subm does this… enu… network and internet connections. Allows you to manage and configure your network settings setup provides a set of tools for managing your netdefend firewall. Allows you to upgrade your license and firmware and to configure https access to your ne...
Page 65
Using the netdefend portal tabl this field… displays this… e 7: status bar fields internet your internet connection status. The connection status may be one of the following: • connected. The netdefend firewall is connected to the internet. • connected – probing ok. Connection probing is enabled and...
Page 66
Using the netdefend portal this field… displays this… service center displays your subscription services status. Your service center may offer various subscription services. These include the firewall service and optional services such as web filtering and email antivirus. Your subscription services...
Page 67: Logging Off
Logging off logging off logging off terminates your administration session. Any subsequent attempt to pa to l logout page appears. Connect to the netdefend portal will require re-entering of the administration ssword. Log off of the netdefend porta • do one of the following: • if you are connected t...
Page 69: Chapter 4
Overview chapter 4 this chapter describes how to configure and work with an internet connection. This chapter includes the following topics: overview ....................................................................................................53 using the internet wizard ........................
Page 70: The Inte
Using the internet wizard for information on traffic shaper, see using traffic shaper on page 151. Configure a dialup internet connection. Config nnection, you must first set up the modem. For ation, see on page 84. The inte • before uring the co inform setting up a dialup modem using rnet wizard th...
Page 71
Using the internet wizard the internet wizard opens with the welcome page displayed. 3. Click next. The internet connection method dialog box appears. 4. Select the internet connection method you want to use for connecting to the internet. Chapter 4: configuring the internet connection 55.
Page 72
Using the internet wizard note: if you selected pptp or connect to the internet. Pppoe dialer, do not use your dial-up software to 5. Click next. U no further settings are required for a direct lan (local area network) connection. Sing a direct lan connection the confirmation screen appears. 1. Clic...
Page 73
Using the internet wizard at the end of the connection process the connected screen appears. 2. Click finish. Chapter 4: configuring the internet connection 57.
Page 74
Using the internet wizard using a cable modem connection if you selected the cable modem connection method, the identification dialog box appears. 1. S do not fic hostname. 2. A mac address is a 12-digit identifier assigned to every network device. If your isp restricts connections to specific, reco...
Page 75
Using the internet wizard 3. Click next. The confirmation screen appears. 4. Click next. The system attempts to connect to the internet. The connecting… screen appears. At the end of the connection process the connected screen appears. 5. Click finish. Using a pptp or pppoe dialer connection if you ...
Page 76: Using Pppoe
Using the internet wizard using pppoe if you selected the pppoe connection method, the dsl configuration dialog box appears. Complete 1. The fields using the information in the table below. 2. The confirmation screen appears. 4. Click finish. Click next. 3. Click next. The system attempts to connect...
Page 77: Using Pptp
Using the internet wizard table 8: pppoe connection fields in this field… do this… username type your user name. Password type your password. Confirm password type your password again. Service type your service name. This field can be left blank. Using pptp if you selected the pptp connection method...
Page 78
Using the internet wizard 3. Click next. The system attempts to connect to the internet via the dsl connection. The at the end of the connection process the connected screen appears. 4. Click finish. Table 9: pptp connection fields in this field… do this… connecting… screen appears. Username type yo...
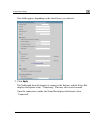
Page 79: Using Internet Setup
Using internet setup using internet setup internet setup allows you to manually configure your internet connection. Igure the using internet setup 1. Click network in the main menu, and click the internet tab. To conf internet connection 2. Next to the desired internet connection, click edit. Chapte...
Page 80
Using internet setup the internet setup page appears. 3. From the con pe you are using/intend to use. C ing steps should be performed in accordance with the connection type nection type drop-down list, select the internet connection ty the display the follow you have chosen. Hanges according to the ...
Page 81: Using A Lan Connection
Using internet setup using a lan connection 1. Complete the fields using the relevant information in internet setup fields on page 77. Chapter 4: configuring the internet connection 65.
Page 82
Using internet setup new fields appear, depending on the check boxes you selected. 2. Click apply. The netdefen ar displays the internet status “connecting”. This may take several seconds. Once the connection is made, the status bar displays the internet status “connected”. D firewall attempts to co...
Page 83
Using internet setup using a cable modem connection 1. Complete the fields using the relevant information in internet setup fields on page 77. Chapter 4: configuring the internet connection 67.
Page 84
Using internet setup new fields appear, depending on the check boxes you selected. 2. Click apply. The netdefend firewall attempts to connect to the internet, and the status bar displays the internet status “connecting”. This may take several seconds. Once the connection is made, the status bar disp...
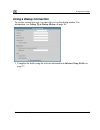
Page 85: Using A Pppoe Connection
Using internet setup using a pppoe connection 1. Complete the e on page 77. Fi lds using the relevant information in internet setup fields chapter 4: configuring the internet connection 69.
Page 86
Using internet setup new fields appear, depending on the check boxes you selected. 2. T, and the status bar s “connecting”. This may take several seconds. Once the connection is made, the status bar displays the internet status “connected”. Click apply. The netdefend firewall attempts to connect to ...
Page 87: Using A Pptp Connection
Using internet setup using a pptp connection 1. Comp the relevant information in internet setup fields lete the fields using page 77. On chapter 4: configuring the internet connection 71.
Page 88
Using internet setup new fields appear, depending on the check boxes you selected. 2. Click apply. The netdefend firewall attempts to connect to the internet, and the status bar displays the internet status “connecting”. This may take several seconds. 72 d-link netdefend firewall user guide.
Page 89: G A Tels
Using internet setup once the connection is made, the status bar displays the internet status g a tels ) connection this internet re subscribed to telstra® bigpond™ internet. Telstra bigpond is a trademark of telstra corporation limited. “connected”. Usin tra (bpa use connection type only if you a 1...
Page 90
Using internet setup new fields appear, depending on the check boxes you selected. 2. Click apply. The netdefend firewall attempts to connect to the internet, and the status bar displays the internet status “connecting”. This may take several seconds. Once the connection is made, the status bar disp...
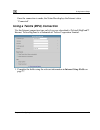
Page 91: Using A Dialup Connection
Using internet setup using a dialup connection information, see setting up a dialup modem on page 84. To use this connection type, you must first set up the dialup modem. For 1. Complete the fields using the relevant information in internet setup fields on page 77. Chapter 4: configuring the interne...
Page 92
Using internet setup new fields appear, depending on the check boxes you selected. 2. Click apply. The netdefend firewall attempts to connect to the internet, and the status bar ay take several seconds. On ternet status “connected”. Displays the internet status “connecting”. This m ce the connection...
Page 93: Using No Connection
Using internet setup using no connection if you do not have an internet connection, set the connection type to none. • click apply. Table 10 in : internet setup fields this field… do this… username type your user name. Pass c servi if your isp has not provided you with a service name, leave this fie...
Page 94
Using internet setup in this field… do this… connect on demand select this option if you do not want the dialup modem to be constantly connected to the internet. The modem will dial a connection only under certain conditions. This option is useful when configuring a dialup backup connection. For inf...
Page 95
Using internet setup in this field… do this… default gateway type the ip address of your isp’s default gateway. Name servers o n auto address automatically using dhcp, but not to automatically configure obt ser auto an ip configure the primary dns type the primary dns server ip address. Server wins ...
Page 96
Using internet setup in this field… do this… shape downs eam: link r select this option to enable traffic shaper for incoming traffic. Then type a rate (in kilobits/second) slightly lower than your internet connection's s the best results. By y if page 151. Tr ate maximum measured downstream speed i...
Page 97
Using internet setup in this field… do this… mac cloning a mac address is a 12-digit identifier assigned to every network device. If your isp restricts connections to specific, recognized mac addresses, you ection, the dmz/wan2 port must be configured as wan2; otherwise this field is disabled. For i...
Page 98
Using internet setup in this field… do this… p select this option to automatically detect loss of connectivity to the default n, this is done by sending arp requests to the f you selected pptp, pppoe, or dialup, this is done by lt gateway does not respond, the internet mined that the internet connec...
Page 99
Using internet setup in this field… do this… connection probing method while the probe next hop option checks the availability of the next hop router, which is usually at your isp, connectivity to the next hop router are more than one hop away. , by selecting one • none. Do not perform internet conn...
Page 100: Setting Up A Dialup Modem
Setting up a dialup modem in this field… do this… 1, 2, 3 if you chose the ping addresses connection probing method, type the ip addresses or dns names of the desired servers. If you chose the probe vpn gateway (rdp) connection probing method, type the ip addresses or dns names of the desired vpn ga...
Page 101
Setting up a dialup modem the ports page appears. 3. 4. Ly. 5. Next to the rs232 drop-down list, click setup. In the rs232 drop-down list, select dialup. Click app chapter 4: configuring the internet connection 85.
Page 102
Setting up a dialup modem the dialup page appears. 6. Complete the fields using the information in the table below. 7. Click 8. To check that that the values you entered are correct, click test. A message indicating whether the test succeeded. Using internet t in apply. The dialup page displays 9. C...
Page 103
Viewing internet connection information in this field… do this… dial mode select the dial mode the modem uses. Port speed select the modem's port speed (in bits per second). Viewing internet connection information you can view information on your internet connection(s) in terms of status, duration, ...
Page 104: Enabling/disa
Enabling/disabling the internet connection table 12: internet page fields de ription field sc status indicates the connection’s status. Duration indicates the connection duration, if active. The duration is given in the form hh= mm ss=seconds you enabled indi ed. For further info ternet co received ...
Page 105
Enabling/disabling the internet connection to enable/disable an internet connection 1. Click network in the main menu, and click the internet tab. Ernet pag 2. Next to the internet connection, do one of the following: • to enable the the int e appears. Connection, click . The button changes to and t...
Page 106
Using quick internet connection/disconnection 90 d-link netdefend firewall user guide using quick internet connection/disconnection ng the connect or disconnect button (depending on the connection status) by clicki on the in et connection using the inate the n. The internet connection retains its co...
Page 107
Configuring a backup internet connection setting up a lan or broadband backup connection using the netdefend firewall's wan port to set up a lan or broadband backup internet connection 1. Connect a hub or switch to the wan port on your appliance's rear panel. 2. Conne 3. Configure two internet conne...
Page 108
Configuring a backup internet connection setting up a dialup backup connection if desired, you can use a dialup modem as the secondary internet connection method. The netdefend firewall automatically dials the modem if the primary m on page 84. 2. G internet setup on page 63. Internet connection fai...
Page 109: Chapter 5
Configuring network settings chapter 5 configure your network connection and set c ....................................................................93 c ..................................................................119 .................................139 145 co this chapter describes how to ...
Page 110: Configuring A Dhcp Server
Configuring network settings configuring a dhcp server by default, the netdefend firewall operates as a dhcp (dynamic host au vices on your network with their network configuration protocol) server. This allows the netdefend firewall to tomatically configure all the de configuration details. Note: t...
Page 111
Configuring network settings dhcp server enabling/disabling the netdefend you can enable and disable the netdefend dhcp server for internal networks. Note: e network. Nabling and disabling the dhcp server is not available for the officemode to enable/disable the netdefend dhcp server menu, and click...
Page 112
Configuring network settings the edit network settings page appears. 3. From the dhcp server list, select enabled or disabled. 4. Click apply. A warning message appears. 6. If you enabled the dhcp server, your computer obtains an ip address in the dhcp address range. 5. Click ok. A success message a...
Page 113
Configuring network settings hcp address range configuring the d by default, the netdefend dhcp server automatically sets the dhcp address range. The dhcp address range is the range of ip addresses that the dhcp server can assign to network devices. Ip addresses outside of the dhcp address range are...
Page 114
Configuring network settings the dhcp ip range fields appear. B. In the dhcp ip range fields type the desired dhcp range. 4. To allow the dhcp server to set the ip address range, select the automatic dhcp range check box. 5. Click apply. A warning message appears. 6. Click ok. A success message appe...
Page 115
Configuring network settings configuring dhcp relay you can configure dhcp relay for internal networks. Note: dhcp relay will not work if the appliance is located behind a nat device. Note: configuring dhcp options are not available for the officemode network. Cp relay 1. Nu, and click the my networ...
Page 116
Configuring network settings the automatic dhcp range check box is disabled, and the relay to ip field appears. 4. In the relay to ip field, type the ip address of the desired dhcp server. 5. 6. 7. Puter is configured to obtain its ip address automatically (using dhcp ther dhcp server is enabled, re...
Page 117
Configuring network settings co ptions nfiguring dhcp server o if desired, you can configure the following custom dhcp options for an internal • • • network: domain suffix • dns servers • wins servers ntp servers voip call managers • tftp server and boot filename note: configuring dhcp options are n...
Page 118
Configuring network settings the dhcp server options page appears. 4. Levant information in the table below. Complete the fields using the re 102 d-link netdefend firewall user guide.
Page 119
Configuring network settings new fields appear, depending on the check boxes you selected. Click apply. If your computer is configured to obtain its ip address automa 5. 6. Tically (using ddress in the dhcp address range. Tabl s in th dhcp), restart your computer. Your computer obtains an ip a e 13:...
Page 120
Configuring network settings in this field… do this… name servers automatically dns server (recommend d a m wins ed the nfiguration (in the internet setup page). W o k. Time server 1, 2 to use network time protocol (ntp) servers to synchronize the time on the dhcp clients, type the ip address of the...
Page 121: Changing Ip Addresses
Configuring network settings in this field… do this… t booting diskless a tftp server to the dhcp clients, type the ip address of ftp server trivial file transfer protocol (tftp) enables computers over the network. To assign the tftp server. Tftp . Boot file type the boot file to use for booting dhc...
Page 122
Configuring network settings note: the internal network range is defined both by the netdefend fire ip address and by the subnet mask. Wall’s internal for example, if the netdefend firewall’s internal ip address is 192.168.100.7, and you set the subnet mask to 255.255.255.0, the network’s ip address...
Page 123: Enabling/disabling Hide Nat
Configuring network settings enabling/disabling hide nat hide network address translation (hide nat) enables you to share a single public internet ip address among several computers, by “hiding” the private ip ad et ip dresses of the internal computers behind the netdefend firewall’s single intern a...
Page 124: Configuring A Dmz Network
Configuring network settings configuring a dmz network in addition to the lan network, you can define a second internal network called a dmz (demilitarized zone) network. For information on default security policy rules controlling traffic to and from the z, see default s figure a dmz network 1. Con...
Page 125
Configuring network settings 3. In the dmz drop-down list, select dmz. 4. Click apply. 5. Click network in the main menu, and click the my network tab. The edit network settings page appears. 7. In the drop-down list, select enabled. The fields are enabled. Enable or disa at. /disabling 107. 9. If d...
Page 126
Configuring network settings configuring the officemode network by default, vpn clients connect to th locally assigned by an isp. This may lead to the following problem e vpn server using an internet ip address s: • th ea pn server. This is because their ip ad refore attempt to secure • offic autom ...
Page 127: Nfiguring Vlans
Configuring network settings 4. In default gateway. The ip address field, type the ip address to use as the officemode network's note: the of ficemode network must not overlap other networks. The officemode internal network range. 6. Se page 107. 7. If 8. Cl 9. Cl co 5. In the subnet mask text box, ...
Page 128
Configuring network settings you can easily transfer a member of one division to another division without rewiring your network, by simply reassigning them to the desired vlan. The netdefend firewall supports the following vlan types: ce to a vlan-aware switch. Each vlan behind the trunk is assigned...
Page 129
Configuring network settings • port-based port-based vlan allows assigning the appliance's lan ports to vlans, effectively transforming the appliance's four-port switch into up to four firewall- isolated security zones. You can assign multiple ports to the same vlan, or each port to a separate vlan....
Page 130
Configuring network settings adding and editing port-based vlans to 1. Enu, and click the my network tab. The my network page appears. 2. Do one of the following: • to add a vlan site, click add vlan. • to edit a vlan site, click edit in the desired vlan’s row. The edit network settings page for vla...
Page 131
Configuring network settings 5. Default gateway. In the ip address field, type the ip address of the vlan network's note: the vlan network must not overlap other networks. 6. In the subnet mask field, type the vlan's internal network range. 7. If desired, enable or disable hide nat. See enabling/dis...
Page 132
Configuring network settings adding and editing tag-based vlans to add or edit a tag-based vlan 1. Click network in the main menu, and click the my network tab. The my network page appears. 2. Do one of the following: • to add a vlan site, click add vlan. • to edit a vlan site, click edit in the des...
Page 133
Configuring network settings 10 a warning message appears. 12 z/wan2 drop-down list, select vlan trunk. 14 vlan trunk (802.1q) port on the vlan-aware switch, 16. Connect the netdefend firewall's dmz/wan2 port to the vlan-aware switch's vlan trunk port. . Click apply. 11. Click ok. A success message ...
Page 134
Configuring network settings deleting vlans to delete a vlan 1. If the vlan is port-based, do the following: network he ports pag b. Remove all port assignm orks in th c. Click apply. 2. Click network in menu, and click the my network tab. Ork desired vlan’s row, click the erase a. Click t in the ma...
Page 135
Configuring high availability configuring high availability you can create a high availability (ha) cluster consisting of two or more alls your cting ay through which all raffic is routed, and one acting as the “backup”. If the master fails, the backup automatical oles of the master. This ensures th...
Page 136
Configuring high availability user-specified amount, if its inte gateway's priority drops below a rnet connection goes down. If the active nother gateway's priority, then the other gateway becomes the active gateway. Note: you can force a fail-over to a passive netdefend firewall. You may want to do...
Page 137
Configuring high availability • • the appliances must have identical firmware versions and firewall rules. • the appliances' internal networks must be the same. • the appliances must have different real internal ip addresses, but share the same virtual ip address. • the appliances' synchronization i...
Page 138
Configuring high availability configuring high availability on a gateway the following procedure explains how to configure ha on a single gateway. You must perform this procedure on each netdefend firewall that you want to include in the ha cluster. To configure ha on a netdefend firewall 1. Set the...
Page 139
Configuring high availability the fields are enabled. 4. Next to each network for which you want to enable ha, select the ha check 5. In virtual ip field, type the default gateway ip address. , and must be the same for all 6. Click the synchronization radio button next to the network you want to use...
Page 140
Configuring high availability note: the s always be connected and enabled on all gateways. Otherwise, m ynchronization interface must be the same for all gateways, and must ultiple appliances e below. 8. Essage appears. 9. An ha for both the primary and secondary internet this setting should be the ...
Page 141
Configuring high availability in this field… do this… internet - secondary type the amount to reduce the gateway's priority if the secondary internet connection goes down. This must be an integer between 0 and 255. Note: this value is only relevant if you configured a backup connection. For informat...
Page 142
Configuring high availability sample implementation on two gateways the following procedure illustrates how to configure ha for the following tw netdefend gateways, gateway a and gateway b: able 15: gateway details o t gateway a gateway b in dmz ternal networks lan, dmz lan, intern y and secondary p...
Page 143
Configuring high availability 2. 3. Co 4. 5. Do a. . B. Igh availability page appears. C. Availability area is enabled. The lan and dmz networks d. Next to lan, select the ha check box. , type the default gateway ip address 192.168.100.3. F. Next to mz, select the ha check box. Next to dmz. 0". Eans...
Page 144
Configuring high availability gateway a will reduce its prio goes down l. Click rity by 30, if its secondary internet connection apply. A success m o the follow te and network range to the values specified in the table above. See chang b. Click setup in the main menu, and click the high availability...
Page 145
Configuring high availability gateway a's priority is 100, and gateway b' gateway a's internet connections is up, gate s priority is 60. So long as one of way a is the active gateway, because its priority is higher than that of gateway b. If both of gateway a's internet connections are down, it dedu...
Page 146: Ng And E
Configuring high availability ss to a mac address istently assigns the same ip address to a specific computer. However, if the netdefend dhcp server runs out of ip addresses and the computer is down, then the dhcp server may reassign the ip constant, you can reserve the ip address for use by the com...
Page 147
Configuring high availability the network objects page appears with a list of network objects. 2. Do one of the following: network object, click new. • to add a • to edit an existing network object, click edit next to the desired computer in the list. Chapter 5: managing your network 131.
Page 148
Configuring high availability the netdefend network object wizard opens, with the step 1: network obje type dialog box displayed. Ct do one of the following: 3. R or 4. • to specify that the network object should represent a single compute device, click single computer. • to specify that the network...
Page 149
Configuring high availability the step 2: computer details dialog bo the dialog box includes the perform st x appears. If you chose single computer, atic nat option. If you chose network, the dialog box does not include this option. 5. Comp 6. Click lete the fields using the information in the table...
Page 150
Configuring high availability the step 3: save dialog box appears. 7. Type a name for the network object in the field. 8. Click finish. Rts in the main menu, and click the active computers tab. To add or edit a network object via the active computers page 1. Click repo 134 d-link netdefend firewall ...
Page 151
Configuring high availability the active computers page appears. If a computer has not yet been added as a network object, the add button appears next to it. If a computer has already been added as a network object, the edit button appears next to it. 2. Do one of the following: • to add a network o...
Page 152
Configuring high availability • to specify that the network object should represent a network, click network. 4. Click next. Er's ip address and mac address are automatically filled in. 5. Elow. 6. Click next. The step 3: save dialog box appears with the network object's name. If you are adding a ne...
Page 153
Configuring high availability table 16: network object fields for a single computer in this field… do this… ip address type the ip address of the local computer, or click this computer to specify your computer. Reserve a fixed ip address for this computer select this option to assign the network obj...
Page 154: Viewing And
Configuring high availability ork ds for a network table 17: netw object fiel in this field… do this… ip range rk. Type the range of local computer ip addresses in the netwo perform static nat (network address translation) dress range to a range of external ip range exclude this network from hotspot...
Page 155: Using Stati
Using static routes using stati s c route a static route is ng in a certain subnet and/or destined for a certain subnet. Packets with a source and destination that fault gateway. To modify the default gateway, see using a lan connection on page 65. A static route ca the source ip addres source routi...
Page 156
Using static routes the static routes page appears, with a list of existing static routes. 2. Do one of the following: • to add a static route, click new route. • to edit an existing st list. Atic route, click edit next to the desired route in the 140 d-link netdefend firewall user guide.
Page 157
Using static routes the static route wizard opens displaying the step 1: source and destination dialog box. 3. To select a specific source network (source routing), do the following: rce drop-down list, select specified network. A) in the sou new fields appear. He network field, type the ip address ...
Page 158
Using static routes c) in the netmask drop-down list, select the subnet mask. 4. To select a specific destination network, do the following: a) in the destination drop-down list, select specified network. New fields appear. B) in the network field, type the ip address of the destination network. C) ...
Page 159
Using static routes the step 2: next hop and metric dialog box appears. 6. In the next hop ip field, type the ip address of the gateway (next hop router) to ou 7. In the metric the gateway destination and has the lowest metric. The default v 8. Click next. Which to r te the packets destined for this...
Page 160
Using static routes the new static route is saved. Viewing and deleting static routes note: the “default” route can to delete a static route the static routes page appears, with a list of existing static routes. 2. In the desired not be deleted. 1. Click network in the main menu, and click the route...
Page 161: Man G
Managing ports chapter 5: managing your network 145 man g a ing ports the netdefend firewall enables you to quickly and easily assign its ports to different uses, as shown in the table below. Furthermore, you can restrict each port table 18: ports and assignments you can assign this port... To these...
Page 162: Viewing Port Statuses
Managing ports viewing port statuses you can view the status of the netdefend firewall's ports on the ports page, including each ethernet connection's duplex state. This is useful if you need to the to view port statuses 1. Click network in the main menu, and click the ports tab. The ports page appe...
Page 163: G P
Managing ports • assign to. The port's current assignment. For example, if the uration. The configured link speed (10 mbps or 100 mbps) and half duplex) configured for the port. E port is configured to automatically x. Detect anything connected to the d indicates that the port is disabled. For examp...
Page 164
Managing ports to assign a port to... See... Wan2 e 91 setting up a lan or broadband backup connection on pag dmz c console modem onfiguring a dmz network using a console on page 388 setting up a dialup modem on page 84 to modify a port as 1. Click networ n the ports page in the assign sired port as...
Page 165
Managing ports modifying link configurations by default, the net duplex. If desired, you can m a specific link speed. To modify a por 1. Click networ the ports page appears. Link c of the following: • select the • select au ally detect the link speed and duplex. This is the d 3. Click apply. Rt use ...
Page 166
Managing ports resetting ports to defaults you can reset the ne ("automatic de e below). Table 20: default por port defaul tdefend firewall's ports to their default link configurations tection") and default assignments (shown in the tabl t assignments t assignment 1-4 lan dmz / wan2 dmz wan rs232 mo...
Page 167: Chapter 6
Overview chapter 6 this chapter describes how to use traffic shaper to control the flow of . R i following topics: overview ..................................................................................................151 affic shaper.................................................................
Page 168
Overview bandwidth, and the ftp connection will receive 25% (10/40) of the leftover bandwidth. If the web connection closes, the ftp connection will receive 100% of lass has a it, which is the maximum amount of bandwidth that connections belonging to that class may use together. Once a class has rea...
Page 169: Setting Up Traffic Shaper
Setting up traffic shaper setting up traffic shaper to set up traffic 1. Enable traff ion, using the procedure using internet setu you can ena • when enabling traffic shaper for outgoing traffic: specify a connectio • when enabli specify a t et connection' it is recommended to try different rates in...
Page 170: Predefined
Predefined qos classes for example, if traffic shaper is enabled for outgoing traffic, and you create an allow rule associating all outgoing vpn traffic with the urgent qos class, then r the see adding and editing rules on page 213. Traffic shaper will handl policy fo e outgoing vpn traffic as speci...
Page 171: Adding and Editing Classes
Adding and editing classes class weight delay sensitivity useful for important 20 medium normal traffic (normal traffic) l (bulk traffic) s not sensitive to long delays. For example, smtp traffic (outgoing email). Ow priority 5 low traffic that i adding and editing classes in simplified traffic shap...
Page 172
Adding and editing classes the netdefend qos class editor wizard opens, with the step 1 of 3: quality of service parameters dialog box displayed. 3. Le below. 4. Click th complete the fields using the relevant information in the tab next. E step 2 of 3: advanced options dialog box appears. Lete the ...
Page 173
Adding and editing classes incoming traffic as accurately as for outgoing traffic. This is because traffic shaper cannot control the number or type of packets it receives from the internet; it can note: traffic shaper may not enforce guaranteed rates and relative weights for only affect the rate of ...
Page 174
Adding and editing classes t in this field… do this… able 22: qos class fields relative weight type a value indicating the class's importance relative to the other defined classes. For example, if you assign one class a weight of 100, and you assign another class a weight of 50, the first class will...
Page 175: Deleting Classes
Deleting classes in this field… do this… in limit maximum rate (in kilobits/second) in the field coming traffic: rate to select this option to limit the rate of incoming traffic belonging to this class. Then type the provided. Diffserv cod p with a diffserv code point (dscp), which is an integer bet...
Page 176
Restoring traffic shaper defaults restoring traffic shaper defaults if desired, you can reset the traffic shaper bandwidth policy to use the four s and their defaults, see predefined qos classes on page 154. Predefined classes, and restore these classes to their default settings. For information on ...
Page 177: Chapter 7
Overview chapter 7 this chapter describes how to set up a wireless internal network. This chapter o a w ....................................................................163 165 t ting wireless connectivity ...................................................183 ov s internal ne l-cpg310. For inf o...
Page 178: Firewall
About the wireless hardware in your netdefend firewall a firewall o tly int is at bo -cpg310 als of up to 108mbps with super g compatible stations. For more information on the super g th 2.4ghz range, using dual diversity antennas to increase the range. In add range (x access point. Xr dramatically ...
Page 179: Ireless Security Protocols
Wireless security protocols w table 23: w security protocol ireless security protocols the netdefend wireless security appliance supports the following security protocols: ireless security protocols description none no security method is used. This option is not recommended, because it allows unauth...
Page 180
Wireless security protocols security protocol description wpa: radius authentication, encryption the wpa (wi-fi protected access) security method uses mic (message integrity check) to ensure the integrity of messages, and tkip (temporal key integrity protocol) to enhance data encryption. Furthermore...
Page 181: Manually Configuring A Wlan
Manually configuring a wlan not curity, it is recommended to enable the netdefend internal vp connecting from your internal networks, and to install securemote on each computer in the wlan. Th from the wlan to the lan are encrypted and au internal vpn server on page 302 and setting u vpn server on p...
Page 182
Manually configuring a wlan the edit network settings page appears. 5. In he the fields are enabled. 6. If desired, enable or disable hide nat. See enabling/disabling hide nat on page 107. 7. If desired, configure a dhcp server. See configuring a dhcp server on page 94. T mode drop-down list, select...
Page 183
Manually configuring a wlan 8. Complete the fields using the information in basic wlan settings fields on and complete the advanced wlan settings fields on page 172. New fields appear. Page 168. 9. To configure advanced settings, click show advanced settings fields using the information in 10 . A s,...
Page 184
Manually configuring a wlan 11. Click ok. 12. Prepare the wireless stations. See preparing the wireless stations on page 182. T in a success message appears. Able 24: wlan settings fields this field… do this… ip her networks. Address type the ip address of the wlan network's default gateway. Note: t...
Page 185
Manually configuring a wlan in this field… do this… operation mode select an operation mode: • 802.11b (11mbps). Operates in the 2.4 ghz range and offers a maximum theoretical rate of 11 mbps. When using this mode, only 802.11b stations will be able to connect. • 802.11g (54 mbps). Operates in the 2...
Page 186
Manually configuring a wlan in this field… do this… chann select the radio frequency to use for the wireless connection: nels is dependent on the selected country and operation mode. Reless network in th o networks ould t are at least 25 mhz (5 channels) apart. Rnatively, you can reduce the transmis...
Page 187
Manually configuring a wlan in this field… do this… require wpa2 (802.11i) specify whether you want to require wireless stations to connect using wpa2, by selecting one of the following: a or wpa2 can access the wlan network. This is the default. • enable. Only wireless stations using wpa2 can acces...
Page 188
Manually configuring a wlan in this field… do this… key 1 box , 2, 3, 4 text type the wep key, or click random to randomly generate a key matching the selected length. The key is composed of hexadecimal characters 0-9 and a-f, and is not case-sensitive. Tabl in th e 25: advanced wlan settings fields...
Page 189
Manually configuring a wlan in this field… do this… mac filteri hether you want to enable mac address filtering, by selecting one wing: dresses that you added as network objects can connect to your network. For information on network objects, see using network objects on page 129. • no. Disable mac ...
Page 190
Manually configuring a wlan in this field… do this… antenna selection multipath distortion is caused by the reflection of radio frequency (rf) signals traveling from the transmitter to the receiver along more than one netdefend firewalls avoid the problems of multipath distortion by using an ystem. ...
Page 191
Manually configuring a wlan in this field… do this… rts threshold t ze for which a station must send an rts (request to send) before sending the ip packet. If ons are in range of the access point, but not in range of each other, they might send data to the access point simultaneously, th nsures that...
Page 192
Using the wireless configuration wizard using the wireless configuration wizard the wireless configuration wizard provides a quick and simple way of setting up your basic wlan parameters for the first time. To configure a wlan using the wireless configuration wizard 1. Prepare the appliance for a wi...
Page 193
Using the wireless configuration wizard the fields are enabled. 6. Complete the fields using the information in basic wlan settings fields on e 168. Next wireless security dialog box appears. Pag 7. Click 8. The . 9. Do • one of click wpa-psk to use the wpa-psk security mode. Nd authenticates encryp...
Page 194: Wpa-Ps
Using the wireless configuration wizard • click no security to use no security to create a public, unsecured access point. Note: you cannot configure wpa and 8 co 02.1x using this wizard. For information on nf odes, see manually configuring a wlan on page 165. 10. Click next. K if you chose wpa-psk,...
Page 195
Using the wireless configuration wizard the wireless security confirmation dialog box appears. 3. Click next. 4. The wireless security complete dialog box appears. 5. Click finish. The wizard closes. 6. Prepare the wireless stations. Chapter 7: configuring a wireless network 179.
Page 196: Wep
Using the wireless configuration wizard see preparing the wireless stations on page 182. Wep if you chose wep, the wireless configuration-wep dialog box appears. Do the following: 1. Choose a wep key length. The possible key lengths are: • 64 bits - the key length is 10 hexadecimal characters. • 128...
Page 197: Security
Using the wireless configuration wizard 3. Click next. The wire nfirmation dialog box appears. 4. Click next. The wireless security no t • less security co complete dialog box appears. 5. Click finish. The wizard closes. 6. Prepare the wireless stations. See preparing the wireless stations on page 1...
Page 198
Preparing the wireless stations preparing the wireless stations after you have configured a wlan, the wireless stations must be prepared nnection to the wlan. For co to 1. Cted the wep security mode, give the wep key to the wireless 2. 3. Stations' administrators should configure the wireless statio...
Page 199
Troubleshooting wireless connectivity troubleshooting wireless connectivity ot conn m a wire should i do? Ck that the ssid configured on the station matches the netdefend firewall's ssid. The ssid is case-sensitive. Check etting mode and keys) m • if mac , verify that the mac address of all stations...
Page 200
Troubleshooting wireless connectivity • check the transmission power parameter in the wlan's advanced settings • sing two access points in close proximity and on the same frequency. For minimum interference, channel separation between nearby access points must be at least 25 mhz (5 channels). Ed ran...
Page 201
Troubleshooting wireless connectivity in addition, try setting the fragmentation threshold parameter in the wlan's configuring a wlan on page 165) to a lower fragment ip packets of a certain size into smaller packets, thereby reducing the likeliness of collisions and increasing network speed. Advanc...
Page 203: Chapter 8
Viewing the event log chapter 8 v this chapter describes the netdefend portal reports. This chapter includes the following topics: viewing the event log.............................................................................187 using the traffic monitor ............................................
Page 204
Viewing the event log an event marked in olor… indicates… this c green traffic accepted by the firewall. By default, accepted traffic is not logged. However, such traffic may be logged if specified by a security policy defined downloaded from your service center, or if specified in user- rules. You ...
Page 205
Viewing the event log to view the lick re vent log tab. The eve l event log 1. C ports in the main menu, and click the e nt og page appears. 2. If an eve our network, you can display the attacker’s details, by clicking on the ip address of the attacking the netdefend firewall queries the internet wh...
Page 206
Viewing the event log a standard file download dialog b. Click save. Box appears. The save as dialog box appears. C. Browse to a destination directory of your choice. R the configuration file and click save. Tory. 5. Nts: a. Click clear. A confirmation message appears. B. Click ok. All events are cl...
Page 207: Using The Traffic Monitor
Using the traffic monitor using the traffic monitor you can view incoming and outgoing traffic for selected network interfaces and qos classes using the traffic monitor. This enables you to identify network traffic trends and anomalies, and to fine-tune traffic shaper qos class assignments. The traf...
Page 208
Using the traffic monitor the traffic monitor page appears. 2. In the traffic monitor report which you want to view a drop-down list, select the network interface for report. C rrently enabled networks. For example, if the dmz network is enabled, it will appear in the list. If traffic shaper is enab...
Page 209
Using the traffic monitor configuring traffic monitor settings you can confi ct traffic data for to configure traffic monitor settings ick repo b. The traffic 2. Click settin the traffic gure the interval at which the netdefend firewall should colle network traffic reports. 1. Cl rts in the main men...
Page 210: Viewing Computers
Viewing computers exporting general traffic reports you can expor networks and a . You can open to export a general traffi 1. Click repo enu, and click the traffic monitor tab. The traffic monitor page appears. Port. Dard . A 4. Browse to a 5. Type a name for the configuration file and click a *.Csv...
Page 211
Viewing computers the active computers page pp a ears. If you configured high availability, both the master and backup appliances are shown. If you configured officemode, the officemode network is shown. If you are using the dfl-cpg310, the wireless stations are shown. For information on viewing sta...
Page 212
Viewing computers • authenticated. The computer i • not authenticated. The computer is not logged on to my hotspot. S logged on to my hotspot. • excluded from hotspot. The computer is in an ip address range excluded from hotspot enforcement. To enforce hotspot, you must edit the on page 130. Network...
Page 213: Viewing Connections
Viewing connections viewing connections this option allows you to view the currently active connections between your network and the external world. To view the active connections 1. Click reports in the main menu, and click the active connections tab. The active connections page appears. The page d...
Page 214
Viewing wireless statistics 4. To view information about a port, click the port. A window opens displaying information about the port. T t able 28: active connections fields his field… displays… protocol the protocol used (tcp, udp, etc.) source - ip address the source ip address source - port the s...
Page 215
Viewing wireless statistics the wireless page appears. The page displays the information in the table below. 2. Tabl t to refresh the display, click refresh. E 29: wlan statistics his field… displays… wireless mode the operation mode used by the wlan, followed by the transmission rate in mbps mac ad...
Page 216
Viewing wireless statistics this field… displays… security the security mode used by the wlan connected stations the number of wireless stations currently connected to the wlan frames ok the total number of frames that were successfully transmitted and received errors the total number of transmitted...
Page 217
Viewing wireless statistics 3. To refresh the display, click refresh. T th able 30: wireless station statistics is field… displays… c t reception and transmission rate in mbps urrent rate the curren f were successfully transmitted and received e umber of transmitted and received frames for which an ...
Page 218
Viewing wireless statistics this field… displays… cipher the security protocol used for the connection with the wireless client. For more information, see wireless security protocols on page 163. 202 d-link netdefend firewall user guide.
Page 219: Chapter 9
Default security policy chapter 9 d w to set up your netdefend firewall security policy. Can enhan d em subscription services this chapter c fault securit g the firewall security lev configuring ser ........................................................................207 using rules ................
Page 220: Firewall Security Level
Setting the firewall security level • access is blocked from the wan (internet) to all internal networks (lan, dmz, wlan, vlans, and officemode). • access is allowed from the internal networks to the wan, according to the firewall security level (low/medium/high). • access is allowed from the lan ne...
Page 221
Setting the firewall security level t this level… does this… further details able 31: firewall security levels low enforces basic control on incoming connections, ile outgo all inbound traffic is blocked to the external netdefend firewall ip address, except for icmp echoes ("pings"). Wh permitting a...
Page 222
Setting the firewall security level note: the definitions of fire netdefend firewall’s default service center may alter this wall security levels provided in this table represent the security policy. Security updates downloaded from a policy and change these definitions. Vel ain menu, and click the ...
Page 223: Configuring Servers
Configuring servers configuring servers note: if ost any public internet servers (web server, mail server etc.) in yo using the netdefend portal, you can selectively allow incoming network ections in ver, mail server or you do not intend to h ur network, you can skip this section. Conn to your netwo...
Page 224
Configuring servers 2. Complete the fields using the information in the table below. . T in this column… do this… 3. Click apply. A success message appears, and the selected computer is allowed to run the desired service or application able 32: servers page fields allow select the desired service or...
Page 225: Using Rules
Using rules using rules the netdefend firewall checks the protocol used, the ports range, and the destination ip address, when deciding whether to allow or block traffic. User-defined rules have priority over the default security policy rules and provide you with greater flexibility in defining and ...
Page 226
Using rules for example, if you want to block all outgoing ftp traffic, except traffic from a create a rule blocking all outgoing ftp traffic and table. Then create a rule allowing ftp traffic from add ove this rule to a higher location in the rules table specific ip address, you can move the rule d...
Page 227
Using rules table 33: firewall rule types rule description al f • forward all such connections to a specific computer in your network. • redirect the specified connections to a specific port. This option is translation (pat). • assign traffic to a qos class. If tra enabled for incoming traffic, then...
Page 228
Using rules rule description al service on the internet. Note: e not • permit incoming access from the internet to a specific service in your internal network. • assign traffic to a qos class. If traffic shaper is enabled for the direction of traffic specified in the rule (incoming or outgoing), the...
Page 229: G Rules
Using rules g rules adding and editin to add or edit 1. Click security s tab. The rules p e a rule in the main menu, and click the rule ag appears. 2. Do one of the following: • to add a new rule, click add rule. To edit an existing rule, click the ed • it icon next to the desired rule. Chapter 9: s...
Page 230
Using rules the displayed. Netdefend firewall rule pens, with the step 1: rule type dialog box wizard o 3. Select the type of r ate. 4. Click next. W rule. Ule you want to cre the p 2: service dialog box appears. The example below shows an allo ste 5. Complete the fields using the relevant informati...
Page 231
Using rules 6. Click next. The step 3: destination & source dialog box appears. 7. Complete the fields using the relevant information in the table below. He step 4: t done dialog box appears. 8. Click finish. The new rule appears in the firewall rules page. Chapter 9: setting your security policy 21...
Page 232
Using rules table 34: firewall rule fields in this field… do this… any service click this option to specify that the rule should apply to any service. Standard s ould apply to a specific standard you must then select the desired service from the drop-down list. Custom service click this option to sp...
Page 233
Using rules in this field… do this… d to specify an ip address range, select specified range and type the desired ip address range in the fields provided. This option is not available in allow e ip address, select this gateway. This option is not available in rward rules. Estination select the desti...
Page 234: Enabling/disabling Rules
Using rules in this field… do this… redir edirect the connections to a specific port. Ect to port select this option to r you must then type the desired port in the field provided. This option is called port address translation (pat), and is only available when defining an allow and forward rule. En...
Page 235: Riority
Using rules riority changing rules' p to change a ru 1. Click secur the rules p 2. Do one of the following: • click le's priority ity in the main menu, and click the rules tab. Age appears. Next to the desired rule, to move the rule up in the table. • click next to the desired rule, to move the rule...
Page 236: Using Sma
Using smartdefense using sma nse rtdefe the netdefend check point a attack safeguar following way • validating c • validating e • limiting application ability to carry malicious data • controlling application-layer operations in addition, sm tp, instant messag haring, file-sharing operations, and fi...
Page 237: Configuring Smartdefense
Using smartdefense configuring smartdefense for convenience, smartdefen represents a category of setting se is organized as a tree, in which each branch s. When a category is expanded, the settings it contains appear as nodes. For information on each category and the nodes it contains, see smartdefe...
Page 238
Using smartdefense to configure a smartdefense node enu, and click the smartdefense tab. D e appears. 1. Click security in the main m the smart efense pag the left pane displays a tree containing smartdefense categories. • to expand a category, click the icon next to it. • to collapse a category, cl...
Page 239
Using smartdefense the right pane displays a description of the node, followed by fields. 3. To modify the node's current settings, do the following: a) complete the fields using the relevant information in smartdefense categories on page 224. B) click apply. 4. To reset the node to its default valu...
Page 240: Ries
Using smartdefense ries categories: • denial of service on page 224 • tcp on pag 2 • port scan o p • peer to peer on page 252 • instant messengers on page 254 de spurious data, to the po nd to legitimate ser cks: • • land on page 226 7 teardrop ack, the attacker sends two ip fragments, the latter en...
Page 241
Using smartdefense you can configure how teardrop attacks should be handled. T in able 35: teardrop fields this field… do this… a ck occurs, by selecting one • block. Block the attack. This is the default. • none. No action. Ction specify what action to take when a teardrop atta of the following: tr...
Page 242
Using smartdefense you can configure how ping of death attacks should be handled. Table 36: ping of dea in this field… do t th fields his… action specify what action to take when a ping of death attack occurs, by selecting one of the following: • block. Block the attack. This is the default. • none....
Page 243
Using smartdefense you can configure how land attacks should be handled. Table 37: land fie field… do lds in this this… action sp ke when a land attack occurs, by selecting one of the ll • this is the default. • ecify what action to ta fo owing: block. Block the attack. None. No action. Track specif...
Page 244
Using smartdefense you can protect against non-tcp flooding attacks by limiting the percentage of state table capacity used for non-tcp connections. T in able 38: non-tcp flooding fields this field… do this… action specify what action to take when the percentage of state table capacity used ons reac...
Page 245
Using smartdefense ip and icmp allows you to enable various ip and icmp protocol tests, and to • packet sanity on page 229 • max ping size on • ip fragments ge 234 pa ity performs several layer 3 and layer 4 sanity checks. These include packet size, udp and tcp header lengths, dropping ip options, a...
Page 246
Using smartdefense table 39: packet sanity fields in this field… do this… action sp one • e default. • ecify what action to take when a packet fails a sanity test, by selecting of the following: block. Block the packet. This is th none. No action. Track sp sel following: • fault. • verification th d...
Page 247
Using smartdefense max ping size ping (icmp echo request) is a program that uses icmp protocol to check whether a remote machine is up. The client sends a request, and the server responds with a reply echoing the client's data. An attacker can echo the client with a large amount of data, causing a b...
Page 248
Using smartdefense 232 d-link netdefend firewall user guide in this field… do this… max ping size specify the maximum data size for icmp echo response. The default value is 1500. Ip fragmen when an ip packet is too big to be transported by a network link, it is split into ed in fragments. To conceal...
Page 249
Using smartdefense table 41: ip fragments fields in this field… do this… f ragmented packets should be dropped, by selecting this is the default. Under normal circumstances, it is recommended to leave this field set to false. Setting this field to true may disrupt internet connectivity, because it d...
Page 250
Using smartdefense network quota an attacker may try to overload a server in your network by establishing a very large number of connections per second. To protect against denial of service (dos) attacks, network quota enforces a limit upon the number of connections per second that are allowed from ...
Page 251
Using smartdefense in this field… do this… max. Connection from same s/secon source ip nd ddress. Set a lower threshold for stronger protection against dos attacks. S value too low can lead to false alarms. D type the maximum number of network connections allowed per seco from the same source ip a t...
Page 252
Using smartdefense t in th able 43: welchia fields is field… do this… action specify what action to take when the welchia worm is detected, by selecting attack. This is the default. One of the following: • block. Block the • none. No action. Track cify whether to log welchia worm attacks, by selecti...
Page 253
Using smartdefense you can configure how cisco ios dos attacks should be handled. Tab do this… le 44: cisco ios dos in this field… action specify what action to take when a cisco ios dos attack occurs, by selecting one of the following: • block. Block the attack. This is the default. • none. No acti...
Page 254
Using smartdefense in this field… do this… action protection for swipe - protocol 53 / lity - protocol 55 / sun-nd - protocol 77 / pim - protocol 103 specify what action to take when an ip pecific protocol type is received, by selecting one of the following: • the packet. This is the • none. No acti...
Page 255
Using smartdefense in this field… do this… tr g packets, by selecting one of the ack specify whether to log null payload pin following: • log. Log the packets. This is the default. • none. Do not log the packets. Tcp this catego he tcp protocol. It • strict tcp • small pmtu on page 241 strict tcp ou...
Page 256
Using smartdefense yo packets should be handled. U can configure how out-of-state tcp table 46: strict tcp in this field… do this… actio selecting one of the following: n specify what action to take when an out-of-state tcp packet arrives, by • block. Block the packets. • none. No action. This is th...
Page 257
Using smartdefense small pmtu small pmt server into u (p is a bandwidth attack in which the client fools the sendi using small packets. Each packet has a large overhead th you can protect ing a minimum packet size for data sent over the internet. Acket mtu) ng large amounts of data at creates a "bot...
Page 258
Using smartdefense in this field… do this… m si attack, while an overly large value might degrade performance and cause legitimate requests to be dropped. Inimal mtu ze type the minimum value allowed for the mtu field in ip packets sent by a client. An overly small value will not prevent an the defa...
Page 259
Using smartdefense table 48: port scan fields in this field… do this… number of ports accessed smartdefense detects ports scans by measuring the number of ports accessed over a period of time. The number of ports accessed must exceed the number of ports accessed value, within the number of seconds s...
Page 260
Using smartdefense in this field… do this… in a period of [seconds] smartdefense detects ports scans by measuring the number of ports accessed over a period of time. The number of ports accessed must exceed the number of ports accessed value, within the number of seconds specified by the in a period...
Page 261
Using smartdefense ftp this category allows you to configure various protections related to the ftp protocol. It includes the following: • ftp bounce on page 245 • block known ports on page 246 • block port overflow on page 247 • blocked ftp commands on page 248 ftp bounce when connecting to an ftp ...
Page 262
Using smartdefense table 49: ftp bounce fields s field… in thi do this… action specify what action to take when an ftp bounce attack occurs, by selecting one of the following: • block. Block the attack. This is the default. • none. No action. Track specify whether to log ftp bounc y selecting one of...
Page 263
Using smartdefense table 50: block known ports fields in this field… do this… action specify what action to take when the ftp server attempts to connect to a well-known port, by selecting one of the following: • block. Block the connection. • none. No action. This is the default. Block port overflow...
Page 264
Using smartdefense table 51: block port overflow in this field… do this… a ction to take for port commands containing a number • block. Block the port command. This is the default. Ction specify what a greater than 255, by selecting one of the following: • none. No action. Blocked ftp command so ty ...
Page 265
Using smartdefense to disable ftp command blocking • in the action drop-down list, select none. All ftp commands are allowed, including those in the blocked commands box. To block a specific ftp command d. 2. Click block. The ftp command appears in the blocked commands box. 3. Click apply. When ftp ...
Page 266
Using smartdefense you can configure how cifs worms should be handled. Table 52: file print and s r in this field… do this… ha ing fields action specify wh y selecting one of the following: • block. Block the attack. • none. No action. This is the default. At action to take when a cifs worm attack i...
Page 267
Using smartdefense the igmp protocol. Igmp is used by hosts and routers to dynamically register and discover multicast group membership. Attacks on the igmp protocol usually target a vulnerability in the multicast routing so igmp packets. You can configure how igmp this category includes ftware/hard...
Page 268
Using smartdefense in this field… do this… enforce igmp to multicast addresses m according to the igmp specification, igmp packets must be sent to ulticast addresses. Sending igmp packets to a unicast or broadcast address might constitute and attack; therefore the netdefend firewall blocks suc speci...
Page 269
Using smartdefense in each node, you can configure how peer-to-peer connections of the selected type should be handled, using the table below. Tab in t le 54: peer-to-peer fields his field… do this… acti mpted, by selecting • block. Block the connection. On specify what action to take when a connect...
Page 270
Using smartdefense ins smartdefense can block instant messaging applications that use voip protocols, by identifying the messaging application's fingerprints and http headers. This category includes the following nodes: • skype • yahoo • icq tant messengers note: smartdefense can detect instant mess...
Page 271
Using smartdefense table 5 in 5: instant messengers fields do this… this field… actio when a connection is attempted, by selecting o action. This is the default. N specify what action to take one of the following: • block. Block the connection. • none. N track specify whether to log instant messenge...
Page 272: Using Secure Hotspot
Using secure hotspot using secure hotspot you can enable your netdefend firewall as a public internet access hotspot for specific networks. When users on those networks attempt to access the internet, they are automatically re-directed to the my hotspot page http://my.Hotspot. On this page, they mus...
Page 273: P S
Using secure hotspot you can choose to exclude specific network objects from hotspot enforcement. Page 129. For information, see using network objects on important: securemote vpn software users who are authenticated by the internal vpn server are automatically exempt from hotspot enforcement. This ...
Page 274: Enabling/dis
Using secure hotspot enabling/dis ecure hotspot abling s to enable/disable secur 1. Click security in the main menu, and click the my hotspot tab. The my hotspot page appears. E hotspot 2. In the hotspot networks area, do one of the following: • to enable secure hotspot for a specific network, selec...
Page 275: Customizing Secure Hotspot
Using secure hotspot customizing secure hotspot to customize secure hotspot 1. Click security in the main menu, and click the my hotspot tab. The my hotspot page appears. G the information in the table below. 2. Complete the fields usin additional fields may appear. 3. To preview the my hotspot page...
Page 276
Using secure hotspot 4. Click apply. Your changes are saved. T ot fields in th able 56: my hotsp is field… do this… my hotspot title type the title that should appear on the my hotspot page. The default title is "welcome to my hotspot". My hotspot terms type the terms to which the user must agree be...
Page 277: Defining An Exposed Host
Defining an exposed host defining an exposed host the netdefend firewall allows you to define an exposed host, which is a computer that is not protected by the firewall. This is useful for setting up a public server. It allows unlimited incoming and outgoing connections between the internet and the ...
Page 278
Defining an exposed host 2. In the computer you wish to define as an exposed host. Alternatively, you can click this computer to define your computer as the exposed host. 3. Click apply. The selected computer is now defined as an exposed host. The exposed host page appears. 2. Click 3. Cl the expose...
Page 279: Chapter 10
Overview chapter 10 using vstream antivirus this chapter explains how to use the vstream antivirus engine to block security threats before they reach your network. This chapter includes the following topics: overview ......................................................................................
Page 280
Overview t if a virus if found in this protocol... Vstream antivirus does this... The protocol is detected on this port... Able 57: vstream antivirus actions p • terminates the only port 80 htt connection all ports on which vstream is enabled by the policy, not pop3 infected email from the server nd...
Page 281
Enabling/disabling vstream antivirus if you are subscribed to the vstream antivirus subscription service, vstream antivirus virus signatures are automatically updated, so that security is always up- to-date, and your network is always protected. Note: vstream antivirus differs from the email antivir...
Page 282
Viewing vstream signature database information the vstream antivirus page appears. 2. Drag the on/off lever upwards or downwards. Vstream antivirus is enabled/disabled for all internal network computers. Viewing vstream signature database information vstream antivirus maintains two databases: a dail...
Page 283
Configuring vstream antivirus t this field… displays… able 58: account page fields main database the date and time at which the main database was last updated, he version number. Followed by t daily database the date and time at which the daily database was last updated, followed by the version numb...
Page 284
Configuring vstream antivirus for example, if you want to scan all outgoing smtp traffic, except traffic from a ng all outgoing smtp traffic and mo le passing smtp traffi ation in the antiv is rule numb specific ip address, you can create a rule scanni ve the rule down in the antivirus policy table....
Page 285
Configuring vstream antivirus rule description scan this rule type enables you to specify that vstream antivirus should scan traffic matching the rule. If a virus is found, it is blocked and logged. Adding and editing rules to add or edit a rule 1. Click antivirus in the main menu, and click the pol...
Page 286
Configuring vstream antivirus the vstream policy rule wizard opens, with the step 1: rule type dialog box displayed. 3. Select the type of rule you want to create. 4. Click next. The step 2: service dialog box appears. The example below shows a scan rule. 5. Complete the fields using the relevant in...
Page 287
Configuring vstream antivirus 6. Click next. The step 3: destination & source dialog box appears. 7. Complete the fields using the relevant information in the table below. The step 4: done dialog box appears. 8. Click finish. The new rule appears in the firewall rules page. Chapter 10: using vstream...
Page 288
Configuring vstream antivirus table 60: vstream rule fields in this field… do this… any serv ny service. Ice click this option to specify that the rule should apply to a standard service cific tandard op-d wn list. Custo lds are enabled. You must fill them in. Proto ld apply. Ou do not enter a port ...
Page 289
Configuring vstream antivirus in this field… do this… and the destination is select the destination of the connections you want to allow or block. To specify an ip address, select specified ip and type the desired ip address type the desired ip address range in the fields provided. This option is no...
Page 290
Configuring vstream antivirus 2. Next to the desired rule, do one of the following: • to enable the rule, click . The button changes to and the rule is enabled. • to disable the rule, click . The button changes to and the rule is disabled. Changing rules' priority to change a rule's priority 1. Menu...
Page 291
Configuring vstream antivirus 3. Click ok. The rule is deleted. Configuring vstream advanced settings to vanced settings 1. Configure vstream antivirus ad click antivirus in the main menu, and click the advanced tab. The advanced antivirus settings page appears. 2. Complete the fields using the tabl...
Page 292
Configuring vstream antivirus the vstream antivirus settings are reset to their defaults. For information on the default values, refer to the table below. Table 61: advanced antivirus settings fields in this field… do this… file types block potentially unsafe file types in email messages select this...
Page 293
Configuring vstream antivirus in this field… do this… pass safe file types without scanning select this option to accept common file types that are known to be safe, without scanning them. Safe files types are: • mpeg streams • riff ogg stream • mp3 • pdf • postscript • wma/wmv/asf • realmedia • jpe...
Page 294
Configuring vstream antivirus in this field… do this… maximum compression ratio 1:x fill in the field to complete the maximum compression ratio of files that vstream antivirus should scan. For example, to specify a 1:150 maximum compression ratio, type 150. Setting a higher number allows the scannin...
Page 295: Updating Vstream Antivirus
Updating vstream antivirus updating vstream antivirus when you are subscribed to the vstream antivirus updates service, vstream antivirus virus signatures are automatically updated, keeping security up-to-date with no need for user intervention. However, you can still check for updates manually, if ...
Page 297: Chapter 11
Connecting to a service center chapter 11 th w to use software updates, web filtering, and email filtering services. Is chapter explains how to start subscription services, and ho note: check with your reseller regarding availability of subscription services, or surf to www.Sofaware.Com/servic ecent...
Page 298
Connecting to a service center the account page appears. 2. In the service account area, click connect. 282 d-link netdefend firewall user guide.
Page 299
Connecting to a service center the netdefend services wizard opens, with the service center dialog box displayed. 3. 4. Ware service center, choose usercenter.Sofaware.Com. Specified ip and then in the specified ter’s ip address, as given to you by ste rator. 5. Click . Connect make sure the connect...
Page 300
Connecting to a service center • if the service center re dialog quires authentication, the service center login box appears. Enter your gateway id and registration key in the appropriate fields, as given to you by • the conne • the confir log box appears with a list of services to which you are sub...
Page 301
Connecting to a service center 6. Click the done next. Screen appears with a success message. 7. Click fin the ish. Following n: • if a new fi downloadi l minutes. Once the download is plete, the netdef • the welcome page appears. Things happe rmware is available, the netdefend firewall may start ng...
Page 302
Connecting to a service center • the services to which you are subscribed are now available on your nd listed as such on the account page. See viewing on page 287 for further information. Netdefend firewall a services information • the services submenu includes the services to which you are subscrib...
Page 303: Viewing Services Information
Viewing services information viewing services information th t t page fields this e account page displays the following information about your subscription. Able 62: accoun field… displays… service center name the name of the service center to which you are connected (if known). Gateway id your gate...
Page 304: Configuring Your Account
Refreshing your service center connection this field… displays… information the mode to which each service is set. If you are subscribed to dynamic dns, this field displays your gateway's domain name. For further information, see web filtering on page 290, virus scanning on page error! Bookmark not ...
Page 305
Disconnecting from your service center to configure your account 1. The account page appears. 2. In the service account area, click configure. Click services in the main menu, and click the account tab. Note: if no additional settings are available from your service center, this button will not appe...
Page 306: Web Filtering
Web filtering • the services to which you were subscribed are no longer available on your netdefend firewall. Web filtering when the web filtering serv accord ries specified under allow categories. Authorized users will be strictions, only after they have provided the administrator password via the ...
Page 307: Selec
Web filtering the web filtering page appears. 2. Drag the on/off lever upwards or downwards. E selec w b filtering is enabled/disabled. Ting categories for blocking you c r your family o s marked with an define which types of web sites should be considered appropriate fo r office members, by selecti...
Page 308
Web filtering to • allow/block a category in the allow categories area, click or next to the desired category. Temporarily disabling web filtering if to temporarily disable web filtering 1. Click services in the main menu, and click the web filtering tab. The web filtering page appears. 2. Click sno...
Page 309
Web filtering • the snooze button changes to resume. • the web filtering off popup window opens. 3. He we page. • rnal network computers. G page, the button changes to snooze. To re-enable the service, click resume, either in the popup window, or on t b filtering the service is re-enabled for all in...
Page 310: Automatic and Manual Updates
Automatic and manual updates • if you clicked resume in the web filtering off popup window, the popup window closes. Automatic and manual updates are the software updates service enables you to check for new security and softw updates. Note: so and su ftware updates are only available if you are con...
Page 311
Automatic and manual updates the software updates page appears. 2. Click update now. The system checks for new updates and installs them. Checking for software updates when locally managed if your netdefend firewall is locally managed, you can set it to automatically check for software updates, or y...
Page 312
Automatic and manual updates the software updates page appears. 2. To set the ne atically check for and install new the netdefend firewall checks for new updates and installs them according to . Tdefend firewall to autom software updates, drag the automatic/manual lever upwards. Its schedule note: w...
Page 313: Chapter 12
Overview chapter 12 this chapter des ccess ient, serv this chapter includes the following topics: overview ........... .... Setting up your net adding and editi deleting a vpn site .................................................................................340 .....................................
Page 314: Site-to-Site Vp
Overview check point securemote vpn client, provided for free with your • internal vpn s remote can also be used from your internal networks, allowing you to secure your wired or wireless network with ong encryp on and authentication. Vp gateway in a permanent, bi-directional relationship. • remote ...
Page 315
Overview networks function as a single network. You can use this type of vpn to mesh office branches into one corporate network. Figure 12: site-to-site vpn chapter 12: working with vpns 299.
Page 316
Overview to create a site-to-site vpn with 1. On the first vpn site’s netd two vpn sites efend firewall, do the following: a. Define the second vpn site as a site-to-site vpn gateway, or create a pppoe tunnel to the second vpn site, using the procedure adding and editing vpn sites on page 308. Dure ...
Page 317: Remote Access Vpns
Overview remote access vpns a remote access vpn consists of one rem ite vpn gateway, and one or m type of vpn to make an office network remotely available to authorized users, su o the office remote access vpn pn clients. Ote access vpn server or site-to-s ore remote access vpn clients. You can use ...
Page 318: Internal Vpn Server
Overview to create a remote access vpn with two vpn sites 1. On the remote user vpn site's firewall, add the office remote access vpn server as a remote access vpn site. See adding and editing vpn sites the remote user's firewall appliance will act as a remote access vpn client. 2. On the office vpn...
Page 319
Setting up your netdefend firewall as a vpn server using the internal vpn server, along with a strict security policy for non-vpn users, can enhance security both for wired networks and for wireless networks, which are particularly vulnerable to security breaches. The internal vpn server can be used...
Page 320
Setting up your netdefend firewall as a vpn server to set up your netdefend firewall as a vpn server 1. Configure the vpn server in one or more of the following ways: ote access vpn server on page 305. • s from your internal networks. Er on page 306. Install securemote on the desired page 307. 3. Se...
Page 321
Setting up your netdefend firewall as a vpn server configuring the remote access vpn server to er 1. Tab. Page appears. Configure the remote access vpn serv click vpn in the main menu, and click the vpn server the securemote vpn server 2. Select the llow securemote users to connect from the internet...
Page 322
Setting up your netdefend firewall as a vpn server new check boxes appear. 3. To allow authenticated users connecting from the internet to bypass nat when nat check box. 4. To allow authenticated users connecting from the internet to bypass the firewall bypass the 5. Click apply. Configuring the int...
Page 323: Ins
Setting up your netdefend firewall as a vpn server 2. Tworks check box. New check boxes appear. Select the allow securemote users to connect from my internal ne 3. Nnecting from internal networks to bypass the on, select the bypass d for the internal vpn server, and cannot be 4. Is enabled for the s...
Page 324: Adding and Editing Vpn Sites
Adding and editing vpn sites to install securemote 1. Click vpn in enu, and click the vpn server tab. The securemote vpn server page appears. 2. Click the download securemote vpn client n-1 se pens in a new window. To complete installation. Ati securemote pn client icon in the taskbar, select settin...
Page 325
Adding and editing vpn sites the vpn sites page appears with a list of vpn sites. 2. Vpn site, click new site. Do one of the following: • to add a • to edit a vpn site, click edit in the desired vpn site’s row. Chapter 12: working with vpns 309.
Page 326
Adding and editing vpn sites the netdefend vpn site wizard opens, with the welcome to the vpn site wizard dialog box displayed. 3. Do one of the following: • select remote access vpn to establish remote access from your remote access vpn client to a remote access vpn server. • el ano vpn gateway. 4....
Page 327
Adding and editing vpn sites configuring a remote access vpn site if you selected remote access vpn, the vpn gateway address dialog box appears. 1. Enter want to . 2. 3. The ip address of the remote access vpn server to which you connect, as given to you by the network administrator to allow the vpn...
Page 328
Adding and editing vpn sites the vpn network configuration dialog box appears. 4. Specify how you want to obtain the vpn network configuration. Refer to vpn the following things happen in the order below: • if you chose specify configuration, a second vpn network configuration g bo network configura...
Page 329
Adding and editing vpn sites complete the fields using the information in vpn network configuration fields on page 320 and click next. The auth • entication method dialog box appears. 6. Complete the fields using the information in authentication methods fields on page 322. 7. Click next. Chapter 12...
Page 330
Adding and editing vpn sites username and password authentication method ox appears. If you selected username and password, the vpn login dialog b e the fields using the information in vpn login fields o 1. Complet n page 322. 2. Click next. Rs. • if you selected automatic login, the connect dialog ...
Page 331
Adding and editing vpn sites do the following: chapter 12: working with vpns 315 pn server, select the try nect to the vpn gateway check box. This allows you to test the vpn connection. 1) to try to connect to the remote access v to con warning: if you try to connect to the vpn site before c existin...
Page 332
Adding and editing vpn sites the vpn site created screen appears. 5. Click finish. The vpn sites page reappears. If you added a vpn site, the new site appears in the vpn sites list. If you edited a vpn site, the modifications are reflected in the vpn sites list. Certificate authentication method if ...
Page 333
Adding and editing vpn sites 1. To try to connect to the remote access vpn server, select the try to connect to the vpn ox. This allows you to test the vpn connection. Gateway check b warning: if you try to connect to the vpn site befo existing tunnels will be terminated. 2. Click next. Ateway, the ...
Page 334
Adding and editing vpn sites the vpn site created screen appears. 5. Click finish. The vpn sites ears in the vp eflected in the t. Rsa securid authentication method if you selected rsa securid, the site name dialog box appears. Page reappears. If you added a vpn site, the new site app n sites list. ...
Page 335
Adding and editing vpn sites 1. Site. You may choose any name. The vpn site created screen appears. Enter a name for the vpn 2. Click next. 3. Pears in the vpn sites list. If you edited a vpn site, the modifications are reflected in the click finish. The vpn sites page reappears. If you added a vpn ...
Page 336
Adding and editing vpn sites tabl in this field… do this… e 63: vpn network configuration fields download configuration click this option to obtain the network configuration by downloading it from the vpn site . This option will automatically configure your vpn settings, by downloading the network t...
Page 337
Adding and editing vpn sites in this field… do this… route based vpn cl th r re dynamic or static routing schemes. This improves network and vpn management efficiency for large ne works, it is recommended to use a route-based vpn combined with ospf dynamic routing. This enables you to make fre es to...
Page 338
Adding and editing vpn sites table 64: au in this fi thentica eld… do this… tion methods fields username and password s vpn authentication. In the next step, you can specify whether you want to log on to the vpn si elect this option to use a user name and password for te automatically or manually. C...
Page 339
Adding and editing vpn sites t in th able 65: vpn login fields is field… do this… m s option to configure the site for manual login. To the vpn site, and only when the appropriate user name and password login, see, logging on to a vpn site on page 341. Anual login click thi manual login connects onl...
Page 340
Adding and editing vpn sites configuring a site-to-site vpn gateway address dialog box appears. If you selected site-to-site vpn, the vpn gateway 1. Complete the fields using the information in vpn gateway address field page 335. S on 2. Click next. G box appears. The vpn network configuration dialo...
Page 341
Adding and editing vpn sites 3. Specify how you want to obtain the vpn network configuration. Refer to vpn network configuration fields on page 320. 4. Click next. • if you chose specify configuration, a second vpn network configuration dialog box appears. Complete the fields using the information i...
Page 342
Adding and editing vpn sites • if you chose route based vpn, the route based vpn dialog box appears. Complete the fields using the information in route based vpn fields on 6, an authent page 33 • the d then click next. Ication method dialog box appears. 5. Complete the fi fields on page 337. 6. Clic...
Page 343
Adding and editing vpn sites shared secret authentication method cted ret, the authentication dialog box appears. If you sele shared sec if you chose download configuration, the dialog box contains additional fields. 1. Complete the fields using the information in vpn authentication fields on page 3...
Page 344
Adding and editing vpn sites the security methods dialog box appears. 2. To configure advanced security settings, click show advanced settings. New fields appear. 3. Complete the fields using the information in security methods fields on page 337 and click next. 328 d-link netdefend firewall user gu...
Page 345
Adding and editing vpn sites the connect dialog box appears. 4. To try to connect to the remote access vpn server, select the try to connect to the vpn gateway check box. This allows you to test the vpn connection. Warning: if you try to connect to the vpn site b leting the wizard, all existing tunn...
Page 346
Adding and editing vpn sites • th dialog pe e site name box ap ars. 6. Enter e vpn site. You m e. 7. To keep the tunnel to the vpn site alive even if there is no network traffic between the netdefend firewall and the vpn site, select keep this site alive. . Click next. A name for th ay choose any na...
Page 347
Adding and editing vpn sites • if you selected keep this site alive, and previously you chose download conf "k ep alive" configuration dialog box appears. Iguration, the e do the following: 1) type up to three ip addresses which the netdefend firewall should the vpn sites page reappears. If you adde...
Page 348
Adding and editing vpn sites • if you chose download configuration, the authentication dialog box appears. Complete the fields using the information in vpn authentication fields on page 337 and click next. • the security methods dialog box appears. 1. To configure advanced security settings, click s...
Page 349
Adding and editing vpn sites new fields appear. 2. Complete the fields using the info 337 and click next. Rmation in security methods fields on page the connect dialog box appears. 3. To try to connect to the r the vpn gateway check b emote access vpn server, select the try to connect to ox. This al...
Page 350
Adding and editing vpn sites warning: if you try to connect to the vp n site before completing the wizard, all existing tunnels will be terminated. Nect to the vpn gateway, the following things n appears. E dialog box appears. 4. Click next. • if you selected try to con happen: the connecting… scree...
Page 351
Adding and editing vpn sites • if you selected keep this site alive, and previously you chose download og box appears. Configuration, the "keep alive" configuration dial do the following: 1) type up to three ip addresses which the netdefend firewall should e tunnel to the vpn site alive. • the vpn s...
Page 352
Adding and editing vpn sites tabl ateway address fields in this field… do this… e 66: vpn g gateway address type the ip address of the site-to-site vpn gateway to which you want to connect, as given to you by the network administrator. Bypass nat select this option to allow the vpn site to bypass na...
Page 353
Adding and editing vpn sites tabl in this field… do this… e 68: authentication methods fields shared secret select this option to use a shared secret for vpn authentication. A shared secret is a string used to identify vpn sites to each other. Certificate select this option to use a certificate for ...
Page 354
Adding and editing vpn sites table 70: security methods fields in this field… do this… phase 1 security methods select the encryption and integrity algorithm to use for ike negotiations: • automatic. The netdefend firewall automatically selects the best security methods supported by the site. This i...
Page 355
Adding and editing vpn sites in this field… do this… p secrec bled. The diffie-hellman group field is enerate a new diffie-hellman key during ike phase 2 e key for each key exchange. Enable pfs only in situations where extreme security is required. Erfect forward y specify whether to enable perfect ...
Page 356: Deleting A Vpn Site
Deleting a vpn site deleting a vpn site to delete a vpn site 1. Click vpn in the main menu, and click the vpn sites tab. The vpn sites page appears, with a list of vpn sites. 2. In the desired vpn site’s row, click the erase icon. A confirmation m sage appears. 3. Click ok. Es the vpn site is delete...
Page 357
Logging on to a remote access vpn site 3. To disable a vpn site, do the following: note: disab l and erases the network topology. Ck the ling a vpn site eliminates the tunne a. Cli icon in the desired vpn site’s row. A confirmat b. Click ok. Ion message appears. The icon changes to , and the vpn sit...
Page 358
Logging on to a remote access vpn site logging on through the netdefend portal note: you can only login to sites that are configured for manual login. To manually log on to a vpn site through the netdefend portal 1. Click vpn in the main menu, and click the vpn login tab. The vpn login page appears....
Page 359: Log
Logging on to a remote access vpn site chapter 12: working with vpns 343 • if the netdefend firewall is configured to automatically download the network configuration, the netdefend firewall downloads the network specified a network configuration, the irewall has finished connecting, the vpn login ”...
Page 360
Logging on to a remote access vpn site the vpn login screen appears. 2. In the site name list, select the site to which you want to log on. 3. Enter your user name and password in the appropriate fields. 4. Click login. • if the netdefend firewall is configured to automatically download the network ...
Page 361: Ing A Certificate
Logging off a remote access vpn site chapter 12: working with vpns 345 logging off a remote access vpn site you need to manually log off a vpn site, if it is a remote access vpn site to log off a • ogin status box, click logout. E configured for manual login. Vpn site in the vpn l all open tunnels f...
Page 362
Installing a certificate the netdefend firewall sup information exchange synt ports certificates encoded in the pkcs#12 (personal ax standard) format, and enables you to install such certificates in the following ways: • by generating a self-signed certificate. 12" file extension. If you do not have...
Page 363
Installing a certificate the certificate page appears. 2. Click install certificate. The netdefend certificate wizard opens, with the certificate wizard dialog box displayed. 3. Click generate a self-signed security certificate for this gateway. Chapter 12: working with vpns 347.
Page 364
Installing a certificate the create self-signed certificate dialog box appears. 4. 5. The netdefend firewall generates the certificate. This may take a few seconds. Complete the fields using the information in the table below. Click next. The done dialog box appears, displaying the certificate's det...
Page 365
Installing a certificate the netdefend firewall installs the certificate. If a certificate is already installed, it is overwritten. The certificate wizard closes. The certificates page displays the following information: • the gateway's certificate • the gateway's name • the gateway certificate's fi...
Page 366: Importing A Certificate
Installing a certificate table 71: certificate fields in this field… do this… country select your country from the drop-down list. Organization type the name of your organization. Organizational unit type the name of your division. Gateway name type the gateway's name. This name will appear on the c...
Page 367
Installing a certificate the import certificate dialog box appears. 4. Click browse to open a file browser from which to locate and select the file. Th 5. The import-certificate passphrase dialog box appears. This may take a few mo e filename that you selected is displayed. Click next. Ments. 6. Typ...
Page 368: Uninstalling A Certificate
Uninstalling a certificate 7. Click next. The done dialog box appears, displaying the certificate's details. 8. Click finish. The netdefend firewall installs the certificate. If a certificate is already installed, it is overwritten. The certificate wizard closes. The certificates page displays the f...
Page 369: Viewing Vpn Tunnels
Viewing vpn tunnels to uninstall a certificate 1. Click vpn in th lick the certificate tab. The certificate page appears with the name of the currently installed certificate. 2. Click uninstall. Tion 3. Click ok. He certificate a success message appears. 4. Click ok. E main menu, and c a confirma me...
Page 370
Viewing vpn tunnels to view vpn tunnels 1. Click reports in the main menu, and click the vpn tunnels tab. The vpn tunnels page appears with a table of open tunnels to vpn sites. The vpn tunnels page includes the information described in the table below. 2. To refresh the table, click refresh. Table ...
Page 371
Viewing vpn tunnels this field… displays… destination the ip address or address range of the entity to which the tunnel is connected. Entity's type is indicated by an icon. See vpn tunnel icons on page the 355. Secu yption used to secure the connection, and the type of the integrity of the note: all...
Page 372
Viewing ike traces for vpn connections this icon… represents… a network for which an ike phase-2 tunnel was negotiated a remote access vpn server a site-to-site vpn gateway a remote access vpn user viewing ike traces for vpn connections if you (inter use the free ike view tool to view the file. The ...
Page 373
Viewing ike traces for vpn connections to view the ike trace for a conne 1. Establish a vpn tunnel to t ction he vpn site with which you are experiencing connection problems. For information on when and how vpn tunnels are established, see viewing 4. Click save. Box appears. 6. File and click save. ...
Page 375: Chapter 13
Changing your password chapter 13 this chapter desc ne multiple users, set the this chapter includes the following topics: your passwo adding and editing .361 adding quick guest viewing and delet setting up remote vpn ac ss for users...............................................367 using radius aut...
Page 376
Changing your password the internal users page appears. 2. Your username, click edit. Rd opens displaying the set user details dialog box. In the row of the account wiza 3. Edit the password and confirm password fields. 360 d-link netdefend firewall user guide.
Page 377: Adding and Editing Users
Adding and editing users note: u se 5 to 25 characters (letters or numbers) for the new password. Xt. 4. Click ne the set user permissions dialog box appears. 5. Cl your changes are saved. Adding and editing users ick finish. This procedure explains how to add and edit users. For information on quic...
Page 378
Adding and editing users 2. Do one of the following: • to create a new user, click new user. Existing user, click edit next to the desire user. Th unt wizard opens d x. • to edit an e acco isplaying the set user details dialog bo 3. Complete the fields using the information in set user details field...
Page 379
Adding and editing users the set user permissions dialog box appears. The options that appear on the page are dependant on the software and services r permissions fields on page 364. 6. Click finish. E user is saved. T in this field… do this… you are using. 5. Complete the fields using the informati...
Page 380
Adding and editing users in this field… do this… e specify an expiration time for the user, select this option and specify xpiration date and time in the fields provided. When the user account expires, it is locked, and the user can no longer log on to the netdefend firewall. Xpires on to the e if y...
Page 381
Adding quick guest hotspot users w override select this option to allow the user to override web filtering. This option onl this option cannot be changed for the “admin” user. Hotspot access select this option to allow the user to log on to the my hotspot page. For information on secure hotspot, see...
Page 382
Adding quick guest hotspot users 366 d-link netdefend firewall user guide to quickly 1. Click in , a d click the internal users tab. Users page appears. 2. Click . Unt wizard opens displaying the save quick guest dialog box. Create a guest user users the main menu n the internal quick guest acco the...
Page 383: Nd Deleting Users
Viewing and deleting users v nd deleting users iewing a note : the “admin” user cannot be deleted. Ck users in the main menu, and click the internal users tab. Rnal users page appears with a list of all users and their permissions. R, do the following: a) in t to view or delete users 1. Cli the inte...
Page 384: Sing Radius Authentication
Using radius authentication remote access vpn clients (a check point secureclient, check point , or another embedded ngx appliance). Server, using the procedure setting up your netdefend firewall as a vpn server on page 303. You must select the vpn remote access option. U securemote to set up remote...
Page 385
Using radius authentication server for a specific user, the gateway will use the default permission set for this to the page appears. User. Use radius authentication 1. Click users in the main menu, and click the radius tab. Radius 2. Complete the fields using the table below. Apply. 3. Click 4. To ...
Page 386
Using radius authentication a confirmation message appears. ) click ok. B the radius settings are reset to their defaults. For information on the default values, refer to the table below. 5. To use the radius vsa to assign permissions to users, configure the vsa. See configuring the radius vendor-sp...
Page 387
Using radius authentication in this field… do this… realm es radius realms, type the realm to append to radius requests. The realm will be appended to the username as follows: @ you set the realm to “myrealm”, and the user "johns" log on to the netdefend portal, the netdefend firewall will adius ser...
Page 388
Configuring the radius vendor-specific attribute in this field… do this… web over this option only appears if the web filtering service is defined. Filtering ride select this option to allow all users authenticated by the radius server to override web filtering. Hotspot access this option only appea...
Page 389
Configuring the radius vendor-specific attribute table 77: vsa syntax permission description attribute number attribute format attribute values notes a cess the readonly. The user can log on to the netdefend portal, odify system settings. Readwrite. The user fy system settings. Dmin indicates the ad...
Page 390
Configuring the radius vendor-specific attribute permission description attribute attribute attribute number format values notes hotspot indicates whether the user can log on via the my hotspot page. 3 string true. The user can access the internet via my hotspot. False. The user hotspot. This permis...
Page 391: Chapter 14
Viewing firmware status chapter 14 maintenance this chapter describes the tasks required for maintenance and diagnosis of your n viewing firmware status .........................................................................375 upgrading your software product .........................................
Page 392
Viewing firmware status to view the firmware status • click setup in the main menu, and click the firmware tab. The firmware page appears. The firmware page displays the following information: tabl t xample… e 78: firmware status fields his field… displays… for e wan mac address the mac address used...
Page 393: Updating The Firmware
Updating the firmware this field… displays… for example… uptim the moment the unit was e the time that elapsed from 01:21:15 turned on hardware type the type of the current netdefend firewall sbox-500 h nd hardware ardware version the current hardware 1.0 version of the netdefe firewall updating the...
Page 394
Updating the firmware the firmware update page appears. 3. Click browse. 4. Select the image file and click open. The firmware update page reappears. The path to the firmware update image file appears in the browse text box. 5. Click upload. Your netdefend firewall firmware is updated. Updating may ...
Page 395
Upgrading your software product upgrading your software product yo wall by adding the dfl-cp310 power pack. After purchasing the power pack, you will receive a new product key that enables you to use the power pack on the same netdefend firewall you have today. There is no need to replace your hardw...
Page 396
Upgrading your software product the netdefend licensing wizard opens, with the install product key dialog box displayed. Enter a d 3. Click ent product key. Iffer product key field, enter the new product key. 4. In the 5. Click next. The installe dialog box appears. D new product key 6. Click next. ...
Page 397
Upgrading your software product the first registration dialog box appears. 7. Do one of the following: • to register your netdefend firewall later on, clear the i want to register my product check box and then click next. • to register your netdefend firewall now, do the following: 1) click next. Ch...
Page 398
Upgrading your software product a second registration dialog box appears. 2) enter your contact information in the appropriate fields. 3) to receive email notifications regarding new firmware versions ears. The third registration dialog box appears. And services, select the check box. 4) click next....
Page 399
Registering your netdefend firewall 8. Your netdefend firewall is restarted and the welcome page appears. Registering your netdefend firewall click finish. If you want to activate your warranty and optionally receive notifications of new firmware versions and services, you must register your netdefe...
Page 400: Configuring Syslog Logging
Configuring syslog logging 9. Click next. The third registration dialog box appears. 10. Click finish. Your netdefend firewall is restarted and the welcome page appears. Configuring syslog logging the registration… screen appears. You can configure the netdefend firewall to send event logs to a sysl...
Page 401
Configuring syslog logging the logging page appears. 2. Complete the fields using the information in the table below. 3. Click apply. Table 79: logging page fields in this field… do this… syslog serv type the ip address of the computer that will run the syslog service twork computers), or click this...
Page 402: Using The Netdefend Portal
Controlling the appliance via the command line controlling the appliance via the command line depending on your netdefend model, you can control your appliance via the co • using the netdefend portal's command line interface. See using the netdefend portal on page 386. • using a console connected to...
Page 403
Controlling the appliance via the command line the tools page appears. 2. Click command. The command line page appears. 3. In the upper field, type a command. Chapter 14: maintenance 387.
Page 404: Using The Serial Console
Controlling the appliance via the command line you can view a list of supported commands using the command help. For information on all commands, refer to the netdefend cli reference guide. 4. Click go. The command is implemented. Using the serial console u can connect a console to the netdefend fir...
Page 405
Controlling the appliance via the command line the ports page appears. 3. In the rs232 drop-down list, select console. 4. Click apply. You can now control the netdefend firewall from the serial console. For information on all supported commands, refer to the netdefend cli reference guide. Chapter 14...
Page 406: Configuring Https
Configuring https configuring https you can enable netdefend firewall users to access the netdefend portal fr ernet. To do so, you must first configure https. Om the int 1. To configure https click setup in the main menu, and click the management tab. The management page appears. 2. Specify from whe...
Page 407
Configuring https note: you can use https to access the netdefend portal from your internal network, by surfing to https ://my.Firewall. If you selected ip address range, additional fields appear. 3. If you selected ip address range, enter the desired ip address range in the fields provided. 4. Clic...
Page 408: Configuring Ssh
Configuring ssh select this to allow access from… option… internal network and vpn the internal network and your vpn. Ip address range a particular range of ip addresses. L fields appear, in which you can enter the desired ip address a d additiona range. Ny any ip address. Isabled nowhere. This comp...
Page 409
Configuring ssh see access options on page 391 for information. Warning: if remote s remotely, so it is especially important to sh is enabled, your netdefend firewall settings can be changed make sure all netdefend firewall users’ passwords are difficult to guess. If you selected ip address range, a...
Page 410: Configuring Snmp
Configuring snmp configuring snmp the netdefend firewall users can monitor the netdefend firewall, using tools that support snmp (simple network management protocol). You can enable users can do so via the internet, by configuring remote snmp access. The netdefend firewall supports the following snm...
Page 411
Configuring snmp the community field and the advanced link are enabled. 3. If you selected ip address range, enter the desired ip address range in the fields ed. 4. In the community field, type the name of the snmp community string. Snmp clients uses the snmp community string as a password, when con...
Page 412
Configuring snmp the snmp configuration page appears. 6. Complete the fields using the table below. Pply. The snmp configuration is saved. Ith the snmp community string. Ed sn in this field... Do this… 7. Click a 8. Configure the snmp clients w table 81: advanc mp settings system location ty e a des...
Page 413
Setting the time on the appliance in this field... Do this… snmp port type the port to use for snmp. The default port is 161. Setting the time on the appliance you set the time displayed in the netdefend portal during initial appliance setup. If desired, you can change the date and time using the pr...
Page 414
Setting the time on the appliance 3. Complete the fields using the information in set time wizard fields on page 400. 4. The following things happen in the order below: • if you selected specify date and time, the specify date and time dialog rs. Click next. Box appea set the date, time, and time zo...
Page 415
Setting the time on the appliance • if you selected use a time server, the time servers dialog box appears. Complete the fields using the information in time servers fields on page 0, then click next. • the date and time updated screen appears. 40 5. Click f inish. Chapter 14: maintenance 399.
Page 416
Setting the time on the appliance table 82: set time wizard fields select this option… to do the following… your computer's clock set the appliance time to your computer’s system time. Your computer’s system time is displayed to the right of this option. Keep the current time do not change the appli...
Page 417: Using Diagnostic Tools
Using diagnostic tools using diagnostic tools the netdefend firewall is equipped with a set of diagnostic tools that are useful for troubleshooting internet connectivity. Table 84: diagnostic tools u to se this ol… to do this… for information, see... Ping check that a specific ip address or dns name...
Page 418: Using Ip Tools
Using diagnostic tools using ip tools to use an ip tool 1. Click setup in the main menu, and click the tools tab. The tools page appears. 2. In the ip tools drop-down list, select the desired tool. 3. In the address field, type the ip address or dns name for which to run the tool. 4. Click go. • if ...
Page 419
Using diagnostic tools the ip tools window opens and displays a list connection. Of routers used to make the • if you selected whois, the following thi the netdefend firewall queries the inte tit or dns tact info ngs happen: rnet whois server. Y to which the ip address rmation. A window displays the...
Page 420: Using Packet Sniffer
Using diagnostic tools using packet sniffer the netdefend firewall includes the capture packets from an packet s to y internal network or n for oubleshooting network problems and for collecting data about network behavior. The netdefend firewall saves the captured packets to a file on your computer....
Page 421
Using diagnostic tools the packet sniffer window disp packets collected, and the percenta appliance for storing the p lays the name of the interface, the number of ge of storage space remaining on the ackets. 5. Click stop to stop collecting packets. Box appears. The save as dialog box appears. 7. B...
Page 422
Using diagnostic tools table 85: packet sniffer fields in this field… do this… interface select the interface from which to the list includes the primary intern tworks. Collect packets. Et connection, the netdefend firewall ports, and all defined ne fi o use for filte atch the filter condi for a lis...
Page 423: Ilter String Syntax
Using diagnostic tools f st of basic filter s dst on page 408 dst port on page 408 • ether proto on page 409 • host on page 410 • not on page 410 • or on page 411 • port on page 411 • src on page 412 • src port on page 412 • tcp on page 413 • udp on page 414 for detailed information on filter syntax...
Page 424
Using diagnostic tools p arameters element s e xample the following filter string saves packets th 192.168.10.1 and are destined for por src 192.168.10.1 and dst port 8 tring. A filter strin at b t 80: 0 g element. Oth originate from ip address is with a specific destination. Arameters ip address or...
Page 425
Using diagnostic tools note: this element can be pre page 413 and udp on page 414. P arameters pended by tc dp. For information, see tcp on r. The port t packet is sent. Xample at are destined for port 80: p or u port intege e o which the the following filter string saves packets th dst port 80 to c...
Page 426
Using diagnostic tools host p urpose the host element captures all incoming and outgoing packets for a specific computer. S yntax host host p arameters host ip address or string. The computer to/from which the packet is sent. This can be the following: • an ip address • a host name e xample the foll...
Page 427
Using diagnostic tools e xample the following filter string saves packets that are not destined for port 80 not dst port 80 : p pose e element is used to alternate between str e of the filter string elem ent...] ent...] element string. A filter string element. T ilter string saves packets that ei om...
Page 428
Using diagnostic tools p arameters integer. The port from/to which the packet is sent. E g saves all packets tha ated from port 80, or port 80 port xample the following filter strin are destined for port 80: t either origin s p ets with a sp source ip address or string. T which the packet is sent. T...
Page 429
Using diagnostic tools page 4 note: this element can be prepended by tcp or udp. F rmation, see tcp on 13 and udp on page 414. P s integer. The port to acket is sent. E t ilter string saves packets that or info arameter port which the p xample he following f originated from port 80: src port 80 tc p...
Page 430
Using diagnostic tools e t t xample 1 he following filter string captures all tcp packets: cp e t r string captures all tcp pac tined for port 80: tcp dst port 80 xample 2 he following filte kets des p t ment captures all udp packets. Lement can be prepended to port- rela udp urpose he udp ele ted e...
Page 431
Backing up the netdefend firewall configuration udp e xample 2 t g filter string captures all udp pac d for port 80: udp dst port 80 he followin kets destine backing up the netdefend firewall configuration you can export the netdefend firewall configuration to a *.Cf file to backup and restore netde...
Page 432
Backing up the netdefend firewall configuration 5 the configuration file an configuration file is created and saved to the specified directory. Importing the netdefend firewall configuration . Type a name for d click save. The *.Cfg in order to restore your netdefend firewall’s co m a configuration ...
Page 433
Backing up the netdefend firewall configuration or • click browse, and browse to the configur n message appears. 5. Click settings page displays the config ontent and the result ation file. 4. Click upload. A confirmatio ok. The netdefend firewall settings are imported. The import of implementing ea...
Page 434
Resetting the netdefend firewall to defaults resetting the netdefend firewall to defaults you can reset the netdefend firewall to its default settings. When you reset your netdefend firewall, it reverts to the state it was originally in when you purchased it. You can choose to keep the current firmw...
Page 435
Resetting the netdefend firewall to defaults a confirmation message appears. 3. To revert to the firmware version that shipped with the appliance, select the check box. 4. Click ok. • the please wait screen appears. • the netdefend firewall returns to its factory defaults. • the netdefend firewall i...
Page 436
Resetting the netdefend firewall to defaults 420 d-link netdefend firewall user guide to reset the netdefend firewall to factory defaults using the reset button 1. Make sure the netdefend firewall is powered on. 2. Using a pointed object, press the reset button on the back of the netdefend firewall ...
Page 437: Running Diagnostics
Running diagnostics chapter 14: maintenance 421 running diagnostics you can view technical information about your netdefend firewall’s hardware, firmware, license, network status, and service center. This information is useful for troubleshooting. You can export it to an *.Html file and send it to t...
Page 438
Rebooting the netdefend firewall 422 d-link netdefend firewall user guide rebooting the netdefend firewall if your netdefend firewall is not functioning properly, rebooting it may solve the problem. To reboot the netdefend firewall 1. Click setup in the main menu, and click the firmware tab. The fir...
Page 439: Chapter 15
Overview chapter 15: using network printers 423 chapter 15 this chapter describes how to set up and use network printers. This chapter includes the following topics: h overview h ..................................................................................................423 h setting up networ...
Page 440: Setting Up Network Printers
Setting up network printers 424 d-link netdefend firewall user guide setting up network printers to set up a network printer 1. Connect the network printer to the netdefend firewall. See t network installation t on page 35. 2. Turn the printer on. 3. In the netdefend portal, click setup in the main ...
Page 441: Windows 2000/xp
Configuring computers to use network printers chapter 15: using network printers 425 the port number appears in the printer server tcp port field. You will need this number later, when configuring computers to use the network printer. 6. To change the port number, do the following: a. Type the desir...
Page 442
Configuring computers to use network printers 426 d-link netdefend firewall user guide 2. Click start > settings > control panel. The control panel window opens. 3. Click printers and faxes. The printers and faxes window opens. 4. Right-click in the window, and click add printer in the popup menu. T...
Page 443
Configuring computers to use network printers chapter 15: using network printers 427 note: do not select the automatically detect and install my plug and play printer check box. 7. Click next. The select a printer port dialog box appears. 8. Click create a new port. 9. In the type of port drop-down ...
Page 444
Configuring computers to use network printers 428 d-link netdefend firewall user guide the add port dialog box appears. 12. In the printer name or ip address field, type the netdefend firewall's lan ip address, or "my.Firewall". You can find the lan ip address in the netdefend portal, under network ...
Page 445
Configuring computers to use network printers chapter 15: using network printers 429 the configure standard tcp/ip port monitor dialog box opens. 16. In the port number field, type the printer's port number, as shown in the printers page. 17. In the protocol area, make sure that raw is selected. 18....
Page 446
Configuring computers to use network printers 430 d-link netdefend firewall user guide the add printer wizard reappears, with the install printer software dialog box displayed. 21. Do one of the following: • use the lists to select the printer's manufacturer and model. • if your printer does not app...
Page 447: Mac Os-X
Configuring computers to use network printers chapter 15: using network printers 431 the port's name is ip_. 26. Click ok. Mac os-x this procedure is relevant for computers with the latest version of the mac os-x operating system. Note: this procedure may not apply to earlier mac os-x versions. To c...
Page 448
Configuring computers to use network printers 432 d-link netdefend firewall user guide the system preferences window appears. 3. Click show all to display all categories. 4. In the hardware area, click print & fax. The print & fax window appears. 5. In the printing tab, click set up printers..
Page 449
Configuring computers to use network printers chapter 15: using network printers 433 the printer list window appears. 6. Click add. New fields appear. 7. In the first drop-down list, select ip printing. 8. In the printer type drop-down list, select socket/hp jet direct. 9. In the printer address fie...
Page 450
Configuring computers to use network printers 434 d-link netdefend firewall user guide 11. In the printer model list, select the desired printer type. A list of models appears. 12. In the model name list, select the desired model. 13. Click add. The new printer appears in the printer list window. 14...
Page 451: Viewing Network Printers
Viewing network printers chapter 15: using network printers 435 viewing network printers to view network printers 1. Click setup in the main menu, and click the printers tab. The printers page appears, displaying a list of connected printers. For each printer, the model, serial number, port, and sta...
Page 452: Resetting Network Printers
Resetting network printers 436 d-link netdefend firewall user guide computers. To do this, you must change the replacement printer's port number to the malfunctioning printer's port number, as described below. Note: each printer port number must be different, and must be a high port. To change a pri...
Page 453: Chapter 16
Resetting network printers chapter 16: troubleshooting 437 chapter 16 this chapter provides solutions to common problems you may encounter while using the netdefend firewall. Note: for information on troubleshooting wireless connectivity, see t troubleshooting wireless connectivity t on page 183. Th...
Page 454: Connectivity
Connectivity 438 d-link netdefend firewall user guide connectivity i cannot access the internet. What should i do? • check if the pwr/sec led is green. If not, check the power connection to the netdefend firewall. • check if the wan link/act led is green. If not, check the network cable to the modem...
Page 455
Connectivity chapter 16: troubleshooting 439 • if you connect to your isp using a pppoe or pptp dialer defined in your operating system, your equipment is most likely configured as a dsl bridge. Configure a pppoe or pptp type dsl connection. • if you were not instructed to configure a dialer in your...
Page 456
Connectivity 440 d-link netdefend firewall user guide • check your tcp/ip configuration according to t installing and setting up the netdefend firewall t on page 15. • restart your netdefend firewall and your broadband modem by disconnecting the power and reconnecting after 5 seconds. • if your web ...
Page 457
Connectivity chapter 16: troubleshooting 441 • consider whether you really need the router. The netdefend firewall can be used as a replacement for your router, unless you need it for some additional functionality that it provides, such as wireless access. • if possible, disable nat in the router. R...
Page 458: Service Center and Upgrades
Service center and upgrades 442 d-link netdefend firewall user guide service center and upgrades i purchased an advanced netdefend model, but i only have the functionality of a simpler netdefend model. What should i do? Your have not installed your product key. For further information, see t upgradi...
Page 459: Other Problems
Other problems chapter 16: troubleshooting 443 other problems i have forgotten my password. What should i do? Reset your netdefend firewall to factory defaults using the reset button as detailed in t resetting the netdefend firewall to defaults t on page 418. Why are the date and time displayed inco...
Page 461: Chapter 17
Technical specifications chapter 17: specifications 445 chapter 17 this chapter includes the following topics: h technical specifications h .......................................................................... 445 h ce declaration of conformity h ...................................................
Page 462
Technical specifications 446 d-link netdefend firewall user guide attribute dfl-cp310 dfl-cpg310 max. Power consumption 8w (1.6a) 8w (1.6a w/o external usb devices) 13w (2.6a w usb devices) retail box dimensions (width x height x depth) 29 x 25 x 7.6 cm (11.4 x 9.8 x 3 inches)) 29 x 25 x 7.6 cm (11....
Page 463
Technical specifications chapter 17: specifications 447 attribute dfl-cp310 dfl-cpg310 quality iso9001:2000 tl9000-hw r3.0 iso14001 ohsas18001: 1999 iso9001:2000 tl9000-hw r3.0 iso14001 ohsas18001: 1999 mean time between failures (mtbf) 68,000 hours at 30 ºc 68,000 hours at 30 ºc.
Page 464
Technical specifications 448 d-link netdefend firewall user guide table 87: netdefend wireless attributes attribute dfl-cpg310 series operation frequency 2.412-2.484 mhz transmission power 79.4 mw modulation ofdm, dsss, 64qam, 16qam, qpsk, bpsk, cck, dqpsk, dbpsk wpa authentication modes eap-tls, ea...
Page 465: Ce Declaration of Conformity
Ce declaration of conformity chapter 17: specifications 449 ce declaration of conformity sofaware technologies ltd., 3 hilazon st., ramat-gan israel, hereby declares that this equipment is in conformity with the essential requirements specified in article 3.1 (a) and 3.1 (b) of: • directive 89/336/e...
Page 466
Ce declaration of conformity 450 d-link netdefend firewall user guide attribute dfl-cp310 dfl-cpg310 en 61000-4-8:1993 en 61000-4-11:1994 env50204:1995 en 61000-4-2:1995 en 61000-4-3:1996/a2:2001 en 61000-4-4:1995 en 61000-4-5:1995 en 61000-4-6:1996 en 61000-4-7:1993 en 61000-4-8:1993 en 61000-4-9:1...
Page 467
Federal communications commission radio frequency interference statement chapter 17: specifications 451 federal communications commission radio frequency interference statement this equipment complies with the limits for a class b digital device, pursuant to part 15 of the fcc rules. These limits ar...
Page 469: Glossary of Terms
Glossary of terms glossary of terms 453 a adsl modem a device connecting a computer to the internet via an existing phone line. Adsl (asymmetric digital subscriber line) modems offer a high-speed 'always-on' connection. C ca the certificate authority (ca) issues certificates to entities such as gate...
Page 470
Glossary of terms 454 d-link netdefend firewall user guide anyone knowing about it. Sometimes, tiny programs are 'planted' on the computer that are designed to watch out for, seize and then transmit to another computer, specific types of data. D dhcp any machine requires a unique ip address to conne...
Page 471
Glossary of terms glossary of terms 455 other ways intentionally breaches computer security. The end result is that whatever resides on the computer can be viewed and sensitive data can be stolen without anyone knowing about it. Sometimes, tiny programs are 'planted' on the computer that are designe...
Page 472
Glossary of terms 456 d-link netdefend firewall user guide ipsec ipsec is the leading virtual private networking (vpn) standard. Ipsec enables individuals or offices to establish secure communication channels ('tunnels') over the internet. Isp an isp (internet service provider) is a company that pro...
Page 473
Glossary of terms glossary of terms 457 netbios netbios is the networking protocol used by dos and windows machines. P packet a packet is the basic unit of data that flows from one source on the internet to another destination on the internet. When any file (e-mail message, html file, gif file etc.)...
Page 474
Glossary of terms 458 d-link netdefend firewall user guide level of security by examining every layer within a packet, unlike other systems of inspection. Stateful inspection extracts information required for security decisions from all application layers and retains this information in dynamic stat...
Page 475
Glossary of terms glossary of terms 459 tcp, however, udp does not provide the service of dividing a message into packets (datagrams) and reassembling it at the other end. Udp is often used for applications such as streaming data. Url a url (uniform resource locator) is the address of a file (resour...
Page 477: Index
Index index 461 8 802.1x • 161, 163 a account, configuring • 288 active computers, viewing • 194 active connections, viewing • 197 allow and forward rules, explained • 213 allow rules, explained • 213 automatic login • 341 b backup connection configuring • 90 dialup • 92 lan or broadband • 91 block ...
Page 478
Index 462 d-link netdefend firewall user guide diagnostics • 421 dialup connection • 75, 92 modem • 84 dialup modem, setting up • 84 dmz configuring • 108 configuring high availability for • 119 explained • 108, 454 dns • 90, 401, 454 dynamic dns • 5, 287 e event log, viewing • 187 exposed host defi...
Page 479
Index index 463 installation cable type • 35 network • 35 instant messengers • 254 internal vpn server configuring • 306 explained • 302 internet connection configuring • 53 configuring backup • 90 enabling/disabling • 88 establishing quick • 88 terminating • 90 troubleshooting • 438 viewing informa...
Page 480
Index 464 d-link netdefend firewall user guide configuring high availability • 119 configuring the officemode network • 110 enabling dhcp server on • 94 enabling hide nat • 107 installation on • 35 managing • 93 objects • 129 network objects adding and editing • 130 using • 129 viewing and deleting ...
Page 481
Index index 465 q qos classes • 151 explained • 151 qos classes adding and editing • 155 assigning services to • 209 built-in • 154, 160 deleting • 159 explained • 151 restoring defaults • 160 r radius configuring vsa • 372 explained • 368 using • 368 rebooting • 422 registering • 383 remote access ...
Page 482
Index 466 d-link netdefend firewall user guide smartdefense • 220 security policy default • 203 setting up • 203 security rules adding and editing • 213 changing priority • 219 deleting • 219 enabling/disabling • 218 types • 213 using • 209 serial console • 11 controlling appliance via • 388 using •...
Page 483
Index index 467 viewing and deleting • 144 strict tcp • 239 subnet masks, explained • 458 subscription services explained • 281 starting • 281 viewing information • 287 sweep scan • 242 syslog logging configuring • 384 explained • 384 t tag-based vlan about • 111 adding and editing • 116 tcp, explai...
Page 484
Index 468 d-link netdefend firewall user guide about • 368 configuring • 267 vlan adding and editing • 114, 116 deleting • 118 port-based • 111, 114 tag-based • 111, 116 vpn explained • 297, 459 remote access • 301, 308 sites • 297, 340, 341 site-to-site • 298, 308 tunnnels • 297, 341, 353 viewing i...
Page 485
Index index 469 wireless stations preparing • 182 viewing • 198 wlan configuring • 161 defined • 459 preparing stations for • 182 troubleshooting connectivity • 183 viewing statistics for • 198 wpa • 161, 163 wpa2 • 163 wpa-psk • 161, 163.