- DL manuals
- D-Link
- Firewall
- DFL-1100 - Security Appliance
- User Manual
D-Link DFL-1100 - Security Appliance User Manual - Administrative Access
Administration Settings
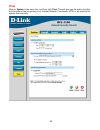
Administrative Access
Ping – If enabled, specifies who can ping the interface IP of the N
ET
D
EFEND
DFL-1100.
The default setting allows anyone to ping the interface IP.
Admin – If enabled allows all users with admin access to connect to the DFL-1100 and
change the configuration, which can be HTTPS or HTTP and HTTPS.
Read-Only – If enabled allows all users with read-only access to connect to the DFL-1100
and look at the configuration, which can be HTTPS or HTTP and HTTPS.
Summary of DFL-1100 - Security Appliance
Page 1
D-link dfl-1100 network security firewall manual october 7, 2004 building networks for people.
Page 2: Contents
2 contents introduction .................................................................................... 6 features and benefits .......................................................................... 6 introduction to firewalls ...................................................................
Page 3
Cluster heartbeats.......................................................................................25 the synchronization interface .....................................................................25 setting up a high availability cluster ......................................................
Page 4
4 services ............................................................................................. 49 adding tcp, udp or tcp/udp service......................................................49 adding ip protocol .....................................................................................
Page 5
Backup............................................................................................... 68 exporting the dfl-1100’s configuration .....................................................68 restoring the dfl-1100’s configuration.....................................................68 restar...
Page 6: Features and Benefits
6 introduction the n et d efend dfl-1100 provides four 10/100mb ethernet network interface ports: internal/lan, external/wan, a dmz port and a port that can be configured as a high availability sync port or as an eth4 port. It also provides an easily operated web interface that allows users to set s...
Page 7
Introduction to local area networking local area networking (lan) is the term used when connecting several computers together over a small area such as a building or group of buildings. Lans can be connected over large areas. A collection of lans connected over a large area is called a wide area net...
Page 8
8 leds & hardware connections wan, lan, dmz & eth4/sync: ethernet link port indicators, green. The act led flickers when the ports are sending or receiving data. Power: a solid light indicates a proper connection to the power supply. Status: system status indicators, flashes to indicate an active sy...
Page 9: Package Contents
Package contents contents of package: • d-link n et d efend dfl-1100 firewall • manual and cd • power cord • installation guide – mini manual • cat5 - straight-through • cat5 - crossover if any of the above items are missing, please contact your reseller. System requirements • computer with a window...
Page 10
10 important note about managing the d-link n et d efend dfl-1100 when a change is made to the configuration, a new icon named activate changes will appear. When all changes have been made, click activate changes on the activate configuration changes page. The dfl-1100 will save the configuration, r...
Page 11: Administrative Access
Administration settings administrative access ping – if enabled, specifies who can ping the interface ip of the n et d efend dfl-1100. The default setting allows anyone to ping the interface ip. Admin – if enabled allows all users with admin access to connect to the dfl-1100 and change the configura...
Page 12
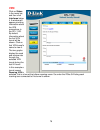
12 snmp – specifies if snmp should be allowed or not on the interface, the dfl-1100 supports read-only access. Add ping access to an interface follow these steps to add ping access to an interface. Step 1. Click on the interface to which you would like to add ping access. Step 2. Enable the ping che...
Page 13
Add read-only access to an interface note that if you have read-only access enabled on an interface, all users will get read-only access, even if they are administrators. Follow these steps to add read-only access to an interface. Step 1. Click on the interface. Step 2. Enable the read-only checkbox...
Page 14: Interfaces
14 system interfaces click on system in the menu bar, and then click interfaces below it. Change the ip of the lan, dmz or eth4 interface follow these steps to change the ip of the lan or dmz interface. Step 1. Choose which interface to view or change under the available interfaces list. Step 2. Fil...
Page 15
Wan interface settings – using static ip if you are using static ip you must fill in the ip address information provided to you by your isp. All fields are required except the secondary dns server. The numbers displayed in these fields are used only as examples. • ip address – the ip address of the ...
Page 16
16 wan interface settings – using pppoe use the following procedure to configure the n et d efend dfl-1100 external interface to use pppoe (point-to-point protocol over ethernet). This configuration is required if your isp uses pppoe to assign the ip address of the external interface. Please enter t...
Page 17
Wan interface settings – using pptp pptp over ethernet connections are used in some dsl and cable modem networks. You will need your account details, and you may also need the ip configuration parameters of the actual physical interface of the pptp tunnel. Your isp will supply you with this informat...
Page 18
18 wan interface settings – using bigpond the isp telstra bigpond uses bigpond for authentication; the ip is assigned with dhcp. • username – the login or username supplied to you by your isp. • password – the password supplied to you by your isp. Traffic shaping when traffic shaping is enabled, and...
Page 19
Mtu configuration to improve the performance of your internet connection, you can adjust the maximum transmission unit (mtu) of the packets that the n et d efend dfl-1100 transmits from its external interface. Ideally, you want this mtu to be the same as the smallest mtu of all the networks between ...
Page 20: Vlan
20 vlan click on system in the menu bar, and then click vlan below it, this will give a list of all configured vlans, it will look something like this: add a new vlan follow these steps to add a new vlan. Step 1. Go to system and vlan. Step 2. Click on add new in the bottom of the routing table. Ste...
Page 21: Routing
Routing click on system in the menu bar, and then click routing, this will give a list of all configured routes, it will look something like this: the routing configuration section shows the firewall’s routing table. Dfl-1100 has an easy to use interface. Interface – specifies the interface through ...
Page 22
22 add a new static route follow these steps to add a new route. Step 1. Go to system and routing. Step 2. Click on add new in the bottom of the routing table. Step 3. Choose the interface that the route should be sent through from the dropdown menu. Step 4. Specify the network and subnet mask. Step...
Page 23: High Availability
High availability d-link high availability works by adding a back-up firewall to your existing firewall. The back- up firewall has the same configuration as the primary firewall. It will stay inactive, monitoring the primary firewall, until it deems that the primary firewall is no longer functioning...
Page 24
24 ip addresses explained for each cluster interface, there are three ip addresses: • two "real" ip addresses; one for each firewall. These addresses are used to communicate with the firewalls themselves, i.E., for remote control and monitoring. They should not be associated in any way with traffic ...
Page 25
Cluster heartbeats a firewall detects that its peer is no longer operational when it can no longer hear "cluster heartbeats" from its peer. Currently, a firewall will send five cluster heartbeats per second. When a firewall has "missed" three heartbeats, i.E., after 0.6 seconds, it will be declared ...
Page 26
26 setting up a high availability cluster first of all, the two dfl-1100s need to be setup so that you can manage them over the web interface. In this example the two units are configured as follows, the master dfl-1100 will be configured with 192.168.1.2 on its internal interface, and the slave dfl...
Page 27
When this is done click apply. Now login to the slave firewall and go to system > ha; in this screen you will click on receive configuration from first unit. This will show the screen below; here you will fill in the cluster id configured on the first unit. When you click apply the unit should trans...
Page 28: Logging
28 logging click on system in the menu bar, and then click logging below it. Logging, the ability to audit decisions made by the firewall, is a vital part in all network security products. The d-link n et d efend dfl-1100 provides several options for logging its activity. The d-link dfl-1100 logs it...
Page 29
Configured to generate log entries. It’s also possible to have e-mail alerting for ids/idp events to up to three email addresses. Enable logging follow these steps to enable logging. Step 1. Enable syslog by checking the syslog box. Step 2. Fill in your first syslog server as syslog server 1, if you...
Page 30: Time
30 time click on system in the menu bar, and then click time. This will give you the option to either set the system time by syncing to an internet network time server (ntp) or by entering the system time manually..
Page 31
Changing the time zone follow these steps to change the time zone. Step 1. Choose the correct time zone in the dropdown menu. Step 2. Specify your daylight time or choose no daylight saving time by checking the correct box. Click apply to apply the setting, or click cancel to discard the changes. Us...
Page 32: Policy
32 firewall policy the firewall policy configuration section is very important. These policies are the primary filters that are configured to allow or disallow certain types of network traffic through the firewall. The policies also regulate how bandwidth management (traffic shaping) is applied to t...
Page 33
Source users/groups – specifies if an authenticated username is needed for this policy to match. Either make a list of usernames, separated by a comma, or write any for any authenticated user. If it’s left blank there is no need for authentication for the policy. Destination nets – specifies the spa...
Page 34
34 (if configured) and pass on the traffic. If prevention is used, the traffic will be dropped and logged, and if configured, an email alert will be sent. Traffic shaping the simplest way to obtain quality of service in a network, seen from a security as well as a functionality perspective, is to ha...
Page 35
Add a new policy follow these steps to add a new outgoing policy. Step 1. Choose the lan > wan policy list from the available policy lists. Step 2. Click on the add new link. Step 3. Fill in the following values: name: specifies a symbolic name for the rule. This name is used mainly as a rule refere...
Page 36
36 change order of policy follow these steps to change the order of a policy. Step 1. Choose the policy list. Step 2. Click on the edit link on the rule you want to change. Step 3. Change the number in the position to the new position. After the apply button is clicked the policy will be moved to th...
Page 37
Configure intrusion prevention follow these steps to configure idp on a policy. Step 1. Choose the policy. Step 2. Click on edit. Step 3. Enable the intrusion detection / prevention checkbox. Step 4. Choose prevention from the mode drop down list. Step 5. Enable the alerting checkbox for email alert...
Page 38
38 port mapping / virtual servers the port mapping / virtual servers configuration section is where you can configure virtual servers, like web servers. It’s also possible to regulate how bandwidth management, traffic shaping, is applied to traffic flowing through the wan interface of the firewall. ...
Page 39
Delete mapping follow these steps to delete a mapping. Step 1. Choose the mapping list (wan, lan or dmz) step 2. Click on edit. Step 3. Enable the delete mapping checkbox. Click apply to apply the change, or click cancel to discard the changes..
Page 40: Administrative Users
40 administrative users click on firewall in the menu bar, and then click users below it. This will show all the users. The first section is the administrative users. The first column shows the access levels, administrator and read-only. An administrator user can add, edit and remove rules, change s...
Page 41
Change administrative user access level to change the access level of a user, click on the user name and you will see the following screen. From here you can change the access level by choosing the appropriate level from the drop-down menu. Access levels • administrator – the user can add, edit and ...
Page 42
42 delete administrative user to delete a user, click on the user name, and you will see the following screen. Follow these steps to delete an administrative user. Step 1. Click on the user. Step 2. Enable the delete user checkbox. Click apply to apply the setting, or click cancel to discard changes...
Page 43: Users
Users user authentication allows an administrator to grant or reject access to specific users from specific ip addresses, based on their user credentials. Before any traffic is allowed to pass through any policies configured with username or groups, the users must first be authenticated. The dfl-110...
Page 44
44 enable user authentication via http / https follow these steps to enable user authentication. Step 1. Enable the checkbox for user authentication. Step 2. Specify if http and https or only https should be used for the login. Step 3. Specify the idle-timeout, the time a user can be idle before bei...
Page 45
Add user follow these steps to add a new user. Step 1. Click on add after the type of user you would like to add, admin or read-only. Step 2. Fill in the user name; make sure you are not trying to add one that already exists. Step 3. Specify what groups the user should be a member of. Step 3. Specif...
Page 46
46 delete user to delete a user click on the user name and you will see the following screen. Follow these steps to delete a user. Step 1. Click on the user. Step 2. Enable the delete user checkbox. Click apply to apply the setting, or click cancel to discard the changes. Note: deleting a user is ir...
Page 47: Schedules
Schedules it is possible to configure a schedule for policies to take affect. By creating a schedule, the dfl-1100 is allowing the firewall policies to be used at those designated times only. Any activities outside of the scheduled time slot will not follow the policies and will therefore likely not...
Page 48
48 add new one-time schedule follow these steps to add new one-time schedule. Step 1. Go to firewall>schedules, and choose add new. Step 2. Choose the starting and ending date, and the hour when the schedule should be active. Step 3. Use the checkboxes to set the times this schedule should be active...
Page 49: Services
Services a service is basically a definition of a specific ip protocol with corresponding parameters. The service http, for instance, is defined as the use of tcp protocol with a destination port 80. Services are simplistic, in that they cannot carry out any action in the firewall on their own. Thus...
Page 50
50 adding other ip protocols when the desired type of service is ip protocol, an ip protocol number may be specified in the text field. To have the service match the gre protocol, for example, the ip protocol should be specified as 47. A list of some defined ip protocols can be found in the appendix...
Page 51
Protocol-independent settings allow icmp errors from the destination to the source – icmp error messages are sent in several situations: for example, when an ip packet cannot reach its destination. The purpose of these error control messages is to provide feedback about problems in the communication...
Page 52: Vpn
52 vpn this chapter introduces ipsec, the method, or rather set of methods used to provide vpn functionality. Ipsec, internet protocol security, is a set of protocols defined by the ietf, internet engineering task force, to provide ip security at the network layer. An ipsec based vpn, such as the df...
Page 53
Ipsec vpn between two networks in the following example users on the main office internal network can connect to the branch office internal network or vice versa. Communication between the two networks takes place in an encrypted vpn tunnel that connects the two dfl-1100 network security firewalls a...
Page 54
54 ipsec vpn between client and an internal network in the following example, users can connect to the main office internal network from anywhere on the internet. Communication between the client and the internal network takes place in an encrypted vpn tunnel that connects the dfl-1100 and the roami...
Page 55: Vpn – Advanced Settings
Vpn – advanced settings advanced settings for a vpn tunnel are used when one needs to change some characteristics of the tunnel when, for example, trying to connect to a third party vpn gateway. The different settings to set per tunnel are the following: limit mtu with this setting it’s possible to ...
Page 56
56 proposal lists to agree on the vpn connection parameters, a negotiation process is performed. As the result of the negotiations, the ike and ipsec security associations (sas) are established. As the name implies, a proposal is the starting point for the negotiation. A proposal defines encryption ...
Page 57: Certificates
Certificates a certificate is a digital proof of identity. It links an identity to a public key in a trustworthy manner. Certificates can be used to authenticate individual users or other entities. These types of certificates are commonly called end-entity certificates. Before a vpn tunnel with cert...
Page 58
58 upload the certificate file. This certificate can be selected in the certificates field on the vpn page. Note: if the uploaded certificate is a ca certificate, it will automatically be placed in the certificate authorities list, even if add new was clicked in the remote peers list. Similiarly, a ...
Page 59: Content Filtering
Content filtering dfl-1100 http content filtering can be configured to scan all http content protocol streams for urls or for web page content. If a requested url is on the url block list, the dfl-1100 will block that web page. You can configure url blacklist to block all or just some of the pages o...
Page 60
60 edit the url global blacklist follow these steps to add or remove a url. Step 1. Go to firewall and content filtering and choose edit global url blacklist step 2. Add/edit or remove the url that should be checked with the content filtering. Click the apply button below to apply the change or clic...
Page 61
Active content handling active content handling can be enabled or disabled by checking the checkbox before each type you would like to strip. For example, to strip activex and flash, enable the checkbox named strip activex objects. It’s possible to strip activex, flash, java, javascript and vbscript...
Page 62: Dhcp Server
62 servers dhcp server settings the dfl-1100 contains a dhcp server; dhcp (dynamic host configuration protocol) is a protocol that lets network administrators automatically assign ip numbers to computers on a network. The dfl-1100 dhcp server helps to minimize the work necessary to administer a netw...
Page 63
Enable dhcp server to enable the dhcp server on an interface, click on servers in the menu bar, and then click dhcp server below it. Follow these steps to enable the dhcp server on the lan interface. Step 1. Choose the lan interface from the available interfaces list. Step 2. Enable by checking the ...
Page 64: Dns Relayer Settings
64 dns relayer settings click on servers in the menu bar, and then click dns relay below it. The dfl-1100 contains a dns relayer that can be configured to relay dns queries from the internal lan to the dns servers used by the firewall itself. Enable dns relayer follow these steps to enable the dns r...
Page 65
Disable dns relayer follow these steps to disable the dns relayer. Step 1. Disable by un-checking the enable dns relayer box. Click the apply button below to apply the setting or click cancel to discard changes..
Page 66: Ping
66 tools ping click on tools in the menu bar, and then click ping below it. This tool is used to send a specified number of icmp echo request packets to a given destination. All packets are sent in immediate succession rather than one per second. This behavior is the best one suited for diagnosing c...
Page 67: Dynamic Dns
Dynamic dns the dynamic dns (requires dynamic dns service) allows you to alias a dynamic ip address to a static hostname, allowing your device to be more easily accessed by specific name. When this function is enabled, the ip address in dynamic dns server will be automatically updated with the new i...
Page 68: Backup
68 backup click on tools in the menu bar, and then click backup below it. Here a administrator can backup and restore the configuration. The configuration file stores system settings, ip addresses of firewall’s network interfaces, address table, service table, ipsec settings, port mapping and polici...
Page 69: Restart/reset
Restart/reset restarting the dfl-1100 follow these steps to restart the dfl-1100. Step 1. Choose if you want to do a quick or full restart. Step 2. Click restart unit and the unit will restart. Restoring system settings to factory defaults use the following procedure to restore system settings to th...
Page 70
70 follow these steps to reset the dfl-1100 to factory default. Step 1. Under the tools menu and the reset section, click on the reset to factory defaults button. Step 2. Click ok in the dialog to reset the unit to factory default, or press cancel to cancel. You can restore your system settings by u...
Page 71: Upgrade
Upgrade the dfl-1100’s software, ids signatures and system parameters are all stored on a flash memory card. The flash memory card is re-writable and re-readable. Upgrade firmware to upgrade the firmware first download the correct firmware from d-link. After having the newest version of software, pl...
Page 72: System
72 status in this section, the dfl-1100 displays the status information about the firewall. The administrator may use status to check the system status, interface statistics, vpn, connections and dhcp servers. System click on status in the menu bar, and then click system below it. A window will appe...
Page 73: Interfaces
Interfaces click on status in the menu bar, and then click interfaces below it. A window will appear providing information about the interfaces in the dfl-1100. By default information about the lan interface will be show, to see another one click on that interface (wan or dmz). Interface – name of t...
Page 74
74 ha click on status in the menu bar, and then click ha below it. A window will appear providing information about the ha cluster configured in the dfl-1100. Status - status of the cluster, will show if the unit is active or inactive. Cluster peer - status of the other unit in the cluster. Cluster ...
Page 75: Vlan
Vlan click on status in the menu bar, and then click vlan below it. A window will appear providing information about the virtual interfaces configured in the dfl-1100. Vlan interface – name of the virtual interface shown. Vlan id – id assigned to the vlan. Ip address – ip address of the virtual inte...
Page 76: Vpn
76 vpn click on status in the menu bar, and then click interfaces below it. A window will appear providing information about the vpn connections in the dfl-1100. By default, information about the first vpn tunnel will be shown. Click on that vpn tunnel’s name to view it. The two graphs display the s...
Page 77: Connections
Connections click on status in the menu bar, and then click connections below it. A window will appear providing information about the content of the state table. Shown are the last 100 connections opened through the firewall. Connections are created when traffic is permitted to pass via the policie...
Page 78: Dhcp Server
78 dhcp server click on status in the menu bar, and then click dhcp server below it. A window will appear providing information about the configured dhcp servers. By default, information about the lan interface will be shown. To view another one, click on that interface. Interface – name of the inte...
Page 79: Usage Events
How to read the logs although the exact format of each log entry depends on how your syslog recipient works, most are very much alike. The way in which logs are read is also dependent on how your syslog recipient works. Syslog daemons on unix servers usually log to text files, line by line. Most sys...
Page 80
80 oct 20 2003 09:47:56 gateway efw: conn: prio=1 rule=rule_8 conn=open connipproto=tcp connrecvif=lan connsrcip=192.168.0.10 connsrcport=3179 conndestif=wan conndestip=64.7.210.132 conndestport=80 in this line, traffic from 192.168.0.10 on the lan interface is connecting to 64.7.210.132 on port 80 ...
Page 81
Appendixes appendix a: icmp types and codes the internet control message protocol (icmp) has many messages that are identified by a “type” field; many of these icmp types have a "code" field. Here we list the types with their assigned code fields. Type name code description reference 0 echo reply 0 ...
Page 82
82 1 redirect datagram for the host rfc792 2 redirect datagram for the type of service and network rfc792 3 redirect datagram for the type of service and host rfc792 8 echo 0 no code rfc792 9 router advertisement 0 normal router advertisement rfc1256 16 does not route common traffic rfc2002 10 route...
Page 83
Appendix b: common ip protocol numbers these are some of the more common ip protocols, for all follow the link after the table. Decimal keyword description reference 1 icmp internet control message rfc792 2 igmp internet group management rfc1112 3 ggp gateway-to-gateway rfc823 4 ip ip in ip (encapsu...
Page 84
84 limited warranty subject to the terms and conditions set forth herein, d-link systems, inc. (“d-link”) provides this limited warranty for its product only to the person or entity that originally purchased the product from: • d-link or its authorized reseller or distributor and • products purchase...
Page 85
Sellers, or the liquidators expressly disclaim their warranty obligation pertaining to the product and in that case, the product is being sold "as-is" without any warranty whatsoever including, without limitation, the limited warranty as described herein, notwithstanding anything stated herein to th...
Page 86
86 limitation of liability: to the maximum extent permitted by law, d-link is not liable under any contract, negligence, strict liability or other legal or equitable theory for any loss of use of the product, inconvenience or damages of any character, whether direct, special, incidental or consequen...