- DL manuals
- D-Link
- Firewall
- DFL-500
- User Manual
D-Link DFL-500 User Manual
Summary of DFL-500
Page 1
Dfl-500 v2.27 user manual d-link systems, inc. Dfl-500 user manual 1.
Page 2
© copyright 2002 d-link systems, inc. All rights reserved. No part of this publication including text, examples, diagrams or illustrations may be reproduced, transmitted, or translated in any form or by any means, electronic, mechanical, manual, optical or otherwise, for any purpose, without prior w...
Page 3: Table of Contents
Table of contents introduction ................................................................................................... 9 antivirus protection ......................................................................................................................................... 9 web co...
Page 4
Using the setup wizard.................................................................................................................................. 25 connecting to the web-based manager.................................................................................................... 25 chang...
Page 5
Adding ip/mac binding addresses........................................................................................................... 46 enabling ip/mac binding.......................................................................................................................... 46 traffic s...
Page 6
Configuring a windows 2000 client for pptp.......................................................................................... 78 configuring a windows xp client for pptp ............................................................................................. 78 pptp pass through............
Page 7
Restoring the banned word list ................................................................................................................. 98 block access to internet sites ....................................................................................................................... 9...
Page 8
Setting system date and time ................................................................................................................. 121 changing web-based manager options.................................................................................................. 122 adding and editi...
Page 9: Introduction
Introduction the dfl-500 network protection gateway (npg) supports network-based deployment of application-level services--including virus protection and full-scan content filtering. Dfl-500 npgs improve network security, reduce network misuse and abuse, and help you use communications resources mor...
Page 10: Web Content Filtering
Dfl-500 virus and worm prevention is transparent to the end user. Client and server programs require no special configuration, and dfl-500 high-performance hardware and software ensure there are no noticeable download delays. Web content filtering dfl-500 web content filtering can be configured to s...
Page 11: Vpn
Addresses on the protected internal networks. Route mode policies route allowed connections between firewall interfaces without performing network address translation. Transparent mode transparent mode is used to provide firewall protection to a pre-existing network with public addresses. The intern...
Page 12
Secure installation, configuration, and management installation is quick and simple. When you initially power the dfl-500 up, it is already configured with default ip addresses and security policies. All that is required for the dfl-500 to start protecting your network is to connect to the web-based...
Page 13: About This Document
· report network services used · report traffic permitted by firewall policies · report traffic that was denied by firewall policies · report events such as configuration changes and other management events, ipsec tunnel negotiation, virus detection, attacks, and web page blocking logs can be sent t...
Page 14
Customer service and technical support for firmware, attack database, and antivirus database updates, updated product documentation, technical support information, and other resources, please visit our web site at http://www.D-link.Com and follow the link to the support page. The d-link automatic up...
Page 15: Getting Started
Getting started this chapter describes unpacking, setting up, and powering on your dfl-500. Once you have completed the procedures in this chapter, you can proceed to one of the following: · if you are going to run your dfl-500 in nat/route mode, go to nat/route mode installation · if you are going ...
Page 16: Powering On
Weight · 1.5 lb. (0.68 kg) power requirements · dc input voltage: 5 v · dc input current: 3 a environmental specifications · operating temperature: 32 to 104 °f (0 to 40 °c) · storage temperature: -13 to 158 °f (-25 to 70 °c) · humidity: 5 to 95% non-condensing powering on to power on the dfl-500: ·...
Page 17: Next Steps
Front and back view of the dfl-500 next steps now that your dfl-500 is up and running, you can proceed to configure it for operation: · if you are going to run your dfl-500 in nat/route mode, go to nat/route mode installation · if you are going to run your dfl-500 in transparent mode, go to transpar...
Page 18: Nat/route Mode Installation
Nat/route mode installation this chapter describes how to install your dfl-500 in nat/route mode. If you want to install the dfl-500 in transparent mode, see transparent mode installation . This chapter includes: · preparing to configure nat/route mode · using the setup wizard · using the command li...
Page 19
Default gateway: _____._____._____._____ primary dns server: _____._____._____._____ secondary dns server: _____._____._____._____ web server: _____._____._____._____ smtp: _____._____._____._____ mail server: pop3: _____._____._____._____ ftp server: _____._____._____._____ internal server settings...
Page 20: Using The Setup Wizard
Using the setup wizard use the procedures in this section to connect to the web-based manager and the setup wizard to create the initial configuration of your dfl-500. Connecting to the web-based manager you require: · a computer with an ethernet connection · internet explorer version 4.0 or higher ...
Page 21
Reconnecting to the web-based manager if you changed the ip address of the internal interface while using the setup wizard, you must reconnect to the web-based manager using a new ip address. Browse to https:// followed by the new ip address of the internal interface. Otherwise, you can reconnect to...
Page 22: Connecting To Your Network
Configuring nat/route mode ip addresses · login to the cli if you are not already logged in. · set the ip address and netmask of the internal interface to the internal ip address and netmask that you recorded in nat/route mode settings . Enter: set system interface internal ip example set system int...
Page 23: Completing The Configuration
Dfl-500 network connections configuring your internal network if you are running the dfl-500 in nat/route mode, your internal network must be configured to route all internet traffic to the address of the internal interface of the dfl-500. This means changing the default gateway address of all compu...
Page 24
Transparent mode installation this chapter describes how to install your dfl-500 in transparent mode. If you want to install the dfl-500 in nat/route mode, see nat/route mode installation . This chapter includes: · preparing to configure transparent mode · using the setup wizard · using the command ...
Page 25: Using The Setup Wizard
Using the setup wizard use the procedures in this section to connect to the web-based manager and the setup wizard to create the initial configuration of your dfl-500. Connecting to the web-based manager you require: · a computer with an ethernet connection · internet explorer version 4.0 or higher ...
Page 26
Starting the setup wizard to start the setup wizard: · select the wizard button at the upper right of the web-based manager. · use the information that you gathered in transparent mode settings to fill in the wizard fields. Select the next button to step through the wizard pages. · confirm your conf...
Page 27
· type admin and press enter. The following prompt appears: type ? For a list of commands. Configuring the dfl-500 to run in transparent mode use the information that you gathered in transparent mode settings to complete the following procedures. Changing to transparent mode · login to the cli if yo...
Page 28: Setting The Date And Time
Setting the date and time for effective scheduling and logging, the dfl-500 date and time should be accurate. You can either manually set the time or you can configure the dfl-500 to automatically keep its time correct by synchronizing with a network time protocol (ntp) server. To set the dfl-500 da...
Page 29: Firewall Configuration
Firewall configuration by default the users on your internal network can connect through the dfl-500 to the internet. The dfl-500 blocks all other connections.The dfl-500 is configured with a default firewall security policy that matches any connection request received from the internal network and ...
Page 30
In nat/route mode you can also create route mode policies between interfaces. Route mode policies accept or deny connections between networks without performing address translation. Transparent mode select transparent mode to provide firewall protection to a network with public addresses. There are ...
Page 31: Adding Policies
Note: changing policy modes between interfaces resets firewall policies and addresses and ipsec vpn policies. To change the policy mode between the internal and external interface using the web-based manager: · go to firewall > mode . · select the mode for connections between the internal and extern...
Page 32
Service a service that matches the service (or port number) of the packet. You can select from a wide range of predefined services, or add custom services and service groups. See services . Action select how the firewall should respond when the policy matches a connection attempt. You can configure ...
Page 33
You can also select insert policy before on a policy in the list to add the new policy above a specific policy. · configure the policy. Sample ext to int nat mode policy source an address that matches the source address of the packet. This can be a single ip address or an address range. Before you c...
Page 34
Editing policies to edit a policy: · go to firewall > policy . · select the tab for the policy list containing the policy to edit. · choose the policy to edit and select edit . · edit the policy settings as required. You can change any of the policy settings. · select ok to save your changes. Orderi...
Page 35: Adding Addresses
Adding addresses all policies require source and destination addresses. To be able to add an address to a policy between two interfaces, you must first add addresses to the address list for each interface. These addresses must be valid addresses for the network connected to that interface. By defaul...
Page 36: Adding Virtual Ips
Editing addresses edit an address to change it's ip address and netmask. You cannot edit the address name. If you need to change an address name, you must delete the address and then re-add it with a new name. Using the web-based manager: · go to firewall > address . · select the interface with the ...
Page 37: Services
For example, if the virtual ip is for a web server the ip address must be a static ip address obtained from your isp for your web server and must not be the same as the external address of the dfl-500. However, your isp must route this address to the external interface of the dfl-500. · in the map t...
Page 38
Https ssl service for secure communications with web servers. Tcp 1-65535 443 imap imap email protocol for reading email from an imap server. Tcp 1-65535 143 irc internet relay chat for connecting to chat groups. Tcp 1-65535 6660-6669 111 tcp 1-65535 2049 111 nfs network file services for sharing fi...
Page 39
The name can contain numbers (0-9) and upper and lower case letters (a-z, a-z), and the special characters - and _. Other special characters and spaces are not allowed. · select the protocol (either tcp or udp) used by the service. · specify a port number range for the service by typing in the low a...
Page 40: Schedules
Adding a service group · to add services to the service group, select a service from the available services list and select the right arrow to copy it to the members list. · to remove services from the service group, select a service from the members list and select the left arrow to remove it from ...
Page 41
· set the start date and time for the schedule. Set start and stop times to 00 for the schedule to cover the entire day. · set the stop date and time for the schedule. Note: one-time schedules use the 24-hour clock. · select ok to add the one-time schedule. Sample one-time schedule creating recurrin...
Page 42: Users and Authentication
Sample recurring schedule adding a schedule to a policy once you have created schedules, you can add them to policies to schedule when the policies are active. You can add the new schedules to policies when you create the policy or you can edit existing policies and add a new schedule to them. To ad...
Page 43
Matched by a policy requiring authentication, the user requesting the connection must enter a valid user name and password to be allowed to connect through the firewall. Note: authentication is not supported in transparent mode. This section describes: · adding user names and passwords · setting aut...
Page 44: Port Forwarding
· select the tab corresponding to the type of policy to which to add authentication. · select new to add a policy or select edit to edit a policy to add authentication. · configure the policy as required. · set action to auth. · set service to http, ftp, or telnet. · select ok to save the policy · a...
Page 45: Ip/mac Binding
· set the forwarded ip to the ip address of the server to which to send the packets. · in the forwarded service port list, select the service used by the packets when they are forwarded to the server. Usually you would select the same service as you selected in the external service port list, but yo...
Page 46: Traffic Shaping
Adding ip/mac binding addresses · go to firewall > ip/mac binding > ip mac . · select new to add an ip address/mac address pair. · add the ip address and the mac address. · select enable to enable ip/mac binding for this address pair. · select ok to save the ip/mac binding pair. Enabling ip/mac bind...
Page 47
Priorities of different types of traffic. For example, a policy for connecting to a secure web-server needed to support e-commerce traffic should be assigned a high traffic priority. Less important services should be assigned a low priority. The firewall provides bandwidth to low priority connection...
Page 48: Example Policies
Example policies · nat mode policy for public access to a server · route mode policy for public access to a server · transparent mode policy for public access to a server · denying connections from the internet · denying connections to the internet · adding policies that accept connections · requiri...
Page 49
· select new to add a new policy. · configure the policy. Source external_all destination the address added in step add an address for the server to the internal address list. Schedule always service select a service to match the internet server for a web server, select http action select accept · s...
Page 50
Using a schedule to deny access the following example procedure to periodically deny access to a public web server to allow for regular maintenance is similar to any procedure to deny a connection that would otherwise be accepted by an existing policy. In this example, the dfl-500 is running in nat/...
Page 51
· select insert policy before to add a new policy above the default policy. · configure the policy to match the default policy with the following exceptions: · set service to pop3 · set action to deny · select ok to save the policy. You must add the deny policy above the default policy in the policy...
Page 52
· select ok to save the policy. If you are using accept policies to restrict access, you must remove all general access policies, such as the default policy, that could be matched by a connection that you do not want. For more information, see policy matching in detail and ordering policies in polic...
Page 53: Ipsec Vpns
Ipsec vpns using ipsec virtual private networking (vpn), you can join two or more widely separated private networks together through the internet. For example, a company that has two offices in different cities, each with its own private network, can use vpn to create a secure tunnel between the off...
Page 54
Autokey ipsec vpn between two networks use the following procedures to configure a vpn that provides a direct communication link between users and computers on two different networks. Example vpn between two internal networks shows an example vpn between the main office and a branch office of a comp...
Page 55
Creating the vpn tunnel a vpn tunnel consists of a name for the tunnel, the ip address of the vpn gateway at the opposite end of the tunnel, the keylife for the tunnel, and the authentication key to be used to start the tunnel. You must create complementary vpn tunnels on each of the vpn gateways. O...
Page 56
About p1 and p2 proposals ipsec vpns use a two-phase process for creating a vpn tunnel. During the first phase (p1) the vpn gateways at each end of the tunnel negotiate to select a common algorithm for encryption and another one for authentication. When you select a p1 proposal, you are selecting th...
Page 57
Example main office autokey ike vpn tunnel adding source and destination addresses the next step in configuring the vpn is to add the addresses of the networks that are to be connected using the vpn tunnel. These address will be added to the vpn policy. On each vpn gateway, you must add two addresse...
Page 58
Netmask end of the vpn tunnel. 255.255.255.0 255.255.255.0 complete the following procedures on both vpn gateways to add the source and destination addresses. Adding a source address to add the source address to the internal address list: · go to firewall > address > internal . · select new to add a...
Page 59
Tunnel configuration ). Incoming nat select incoming nat if you require network address translation for vpn packets. Select select complete the following procedure on both vpn gateways to add the vpn policy: · go to vpn > ipsec > policy . · select new to add a new ipsec vpn policy. · select a source...
Page 60
Example vpn between an internal network and remote clients use the following procedures to configure an ipsec autokey ike vpn that allows vpn clients to connect to an internal network: · configuring the network end of the vpn tunnel · adding source and destination addresses · adding an ipsec vpn pol...
Page 61
Select the authentication algorithms to propose for phase 1 of the ipsec vpn connection. Md5 specify the keylife for phase 1. The keylife is the amount of time in seconds before the phase 1 encryption key expires. When the key expires, a new key is generated without interrupting service. 600 select ...
Page 62
Name can contain numbers (0-9) and upper and lower case letters (a-z, a-z), and the special characters - and _. Other special characters and spaces are not allowed. Ip address 192.168.1.0 netmask the ip address and netmask of the source address that the vpn client can connect to. 255.255.255.0 desti...
Page 63: Dial-Up Vpn
· select a destination address. · select the vpn tunnel. · select ok to save the vpn policy. Configuring the ipsec vpn client the vpn client pc must be running industry standard ipsec autokey ike vpn client software. D-link recommends the safenet/soft-pk client from ire, inc. Configure the client as...
Page 64
Example dial-up vpn configuration use the following procedures to create a dial-up vpn configuration: · adding a dial-up vpn tunnel · configuring remote ipsec vpn clients · configuring remote ipsec vpn gateways adding a dial-up vpn tunnel dial-up vpn tunnel configuration shows the information requir...
Page 65
Select enable perfect forward secrecy (pfs) to improve the security of phase 2 keys. See about perfect forward secrecy (pfs) . Select specify the keylife for phase 2. The keylife is the amount of time in seconds before the phase 2 encryption key expires. When the key expires, a new key is generated ...
Page 66: Viewing Vpn Tunnel Status
Dial-up vpn gateway. Remote gateway the external ip address of the dial-up vpn gateway. 1.1.1.1 authentication key the client authentication key should match the dial-up vpn gateway tunnel authentication key. Ddchh01887d vpn policies and addresses add as required to configure the remote gateway to c...
Page 67
Dial-up monitor manual key ipsec vpn between two networks dfl-500 ipsec vpns can be configured to use autokey ike or manual key exchange. In most cases autokey key exchange is preferred because it is easier to configure and maintain. However, manual key exchange may be necessary in some cases for co...
Page 68
For md5 encryption algorithms, enter two hexadecimal numbers of 16 digits each. Use the same authentication key at both ends of the tunnel. For sha1 encryption algorithms, enter two hexadecimal numbers one of 16 digits and one of 20 digits. Use the same authentication key at both ends of the tunnel....
Page 69: Testing A Vpn
Configuring the vpn tunnel you can either create multiple vpn tunnels, one for each vpn client, or you can create one vpn tunnel with a remote gateway address set to 0.0.0.0. This vpn tunnel accepts connections from any internet address. You must create complementary vpn tunnels on the vpn gateway a...
Page 70
· a subnet on your internal network, protected by an ipsec vpn gateway, can connect through your dfl- 500 to an ipsec vpn gateway on the internet other than enabling ipsec pass through, no special configuration is required for the dfl-500 that will be passed through. The vpn tunnel configuration of ...
Page 71
Ipsec client connecting to a vpn on the internet using vpn pass through configure the ipsec vpn client · configure the ipsec vpn client to connect to the ipsec vpn gateway as if the client computer is connected directly to the internet. · set the default gateway of the ipsec vpn client computer to 1...
Page 72
When the ipsec client connects to the ipsec vpn gateway, the dfl-500 accepts ipsec vpn connections from the internal network and performs network address translation on them. The vpn packets are forwarded to the destination ipsec vpn gateway with a source address of the external interface of the dfl...
Page 73
Configure the internet ipsec vpn gateway the administrator of the remote ipsec vpn gateway creates a standard vpn gateway configuration. The destination address of the vpn policy is set to the address of the internal network behind the internal ipsec vpn gateway. Using the example in ipsec network t...
Page 74
No special vpn configuration is required. When a computer on the internal ipsec vpn network connects to the internal network behind the internet ipsec vpn gateway, the dfl-500 accepts ipsec vpn connections from the internal network and performs network address translation on them. The vpn packets ar...
Page 75: Pptp And L2Tp Vpns
Pptp and l2tp vpns using dfl-500 pptp and l2tp virtual private networking (vpn), you can create a secure connection between a client computer running windows and your internal network. Pptp is a microsoft windows vpn standard. You can use pptp to connect computers running microsoft windows to a dfl-...
Page 76
Pptp vpn between a windows client and the dfl-500 configuring the dfl-500 as a pptp gateway use the following procedure to configure the dfl-500 to be a pptp gateway: · go to vpn > pptp > pptp user . · select new to add a pptp user name and password. · enter a user name and password. The user name c...
Page 77
Sample pptp range configuration configuring a windows 98 client for pptp use the following procedure to configure a client machine running windows 98 so that it can connect to a dfl-500 pptp vpn. To configure the windows 98 client, you must install and configure windows dial-up networking and virtua...
Page 78
· select ok twice. Connecting to the pptp vpn · start the dial-up connection that you configured in the previous procedure. · enter your pptp vpn user name and password. · select connect. Configuring a windows 2000 client for pptp use the following procedure to configure a client machine running win...
Page 79: Pptp Pass Through
· in the vpn server selection dialog, enter the external ip address or hostname of the dfl-500 to connect to and select next. · select finish. Configure the vpn connection · right-click the icon that you have created. · select properties > security . · select typical to configure typical settings. ·...
Page 80
Pptp pass through is only supported in nat mode. Pptp client to network pass through in the configuration shown in pptp client connecting to a vpn on the internet using pptp pass through , the dfl-500 is configured for pptp pass through. The pptp vpn client on your internal network runs pptp vpn cli...
Page 81: L2Tp Vpn Configuration
No special vpn configuration is required. When the pptp client connects to the destination pptp vpn gateway, the dfl-500 accepts pptp packets from the internal network. The dfl-500 performs network address translation to change the source address of these packets to the ip address of the external in...
Page 82
The password must be at least 6 characters long and can contain numbers (0-9), and upper and lower case letters (a-z, a-z), and the special characters - and _. Other special characters and spaces are not allowed. A client can connect to the l2tp vpn with this user name and password. · select ok. · r...
Page 83
· select the security tab. · make sure require data encryption is checked. · select the networking tab. · set vpn server type to layer-2 tunneling protocol (l2tp). · save your changes and continue with the following procedure. Disabling ipsec · select the networking tab. · select internet protocol (...
Page 84
· select create a connection to the network of your workplace and select next. · select virtual private network connection and select next. · name the connection and select next. · if the public network dialog box appears, choose the appropriate initial connection and select next. · in the vpn serve...
Page 85
You must add the prohibitipsec registry value to each windows xp-based endpoint computer of an l2tp or ipsec connection to prevent the automatic filter for l2tp and ipsec traffic from being created. When the prohibitipsec registry value is set to 1, your windows xp-based computer does not create the...
Page 86
Example radius configuration turning on radius authentication for pptp radius authentication can be turned on separately for pptp and l2tp. To turn on radius authentication for pptp users: · go to vpn > pptp > pptp range . · check enable radius. · select apply. Turning on radius authentication for l...
Page 87: Nids Features
Network intrusion detection system (nids) the dfl-500 nids is a real-time network intrusion detection sensor that can identify a wide variety of suspicious network traffic including direct attacks, and take action as required. The nids uses attack signatures, stored in the attack database, to identi...
Page 88: Configuring Nids Detection
· buffer overflows including smtp vrfy and smtp expn · account scans · os identification exploits exploits are attempts to take advantage of features or bugs to gain unauthorized access to a computer or network. The dfl-500 nids protects against the following common exploits: · brute force attack · ...
Page 89: Viewing The Attack List
Nids detection configuration viewing the attack list use the following procedure to display the attacks in the current attack database: · to display the virus list, go to nids > detection > attack list . · scroll through the virus list to view the names of all of the viruses in the list. Configuring...
Page 90
Summary record a brief summary message stating the name of the attack and the source and destination addresses. Full record a more detailed message about the attack with details about the attack and the nids response. · for address obfuscation, check source address, destination address, or both. Whe...
Page 91: Virus Protection
Virus protection dfl-500 antivirus protection screens the information found in web (http protocol) and email content (smtp, pop3, and imap protocols) as it passes through the dfl-500. The content can be contained in normal network traffic that is allowed to pass between dfl-500 interfaces as well as...
Page 92
· select the connection type to configure for that protocol for each connection type you can select to protect: · firewall traffic · ipsec vpn traffic for each protocol and connection type you can turn on virus scanning or turn on and configure file blocking. This section describes: · antivirus conn...
Page 93: Worm Protection
Them for viruses: executable files (exe, bat, and com) visual basic files (vbs) compressed files (zip, gzip, tar, hta, and rar) screen saver files (scr) dynamic link libraries (dll) ms office files containing macros if the virus scanner finds a virus, the file is deleted from the data stream and rep...
Page 94: Customize Antivirus Messages
Customize antivirus messages use the following procedures to customize the message that appears when dfl-500 antivirus protection removes a file from a content protocol stream. · customizing messages added to email · customizing messages added to web pages customizing messages added to email to conf...
Page 95
· select ok to save your changes. · under http, select infected message to customize the message that appears when antivirus scanning detects a virus in a file that a user has attempted to download from a web page. You can change the message as required. The messages can be in plain text or include ...
Page 96: Web Content Filtering
Web content filtering use dfl-500 web content filtering to: · block web pages that contain unwanted content · block access to internet sites · remove scripts from web pages block web pages that contain unwanted content block web pages that contain unwanted content by enabling content blocking and th...
Page 97
· select new to add a word or phrase to the banned word list. · choose a language or character set for the banned word or phrase. You can choose western, simplified chinese, traditional chinese, japanese, or korean. Your computer and web browser must be configured to enter characters in the characte...
Page 98
All unchecked items in the banned word list are not blocked by the dfl-500. Clearing the banned word list use the following procedure to remove all of the entries from the banned word list. · go to web filter > content block . · select delete to remove all of the words in the banned word list. Backi...
Page 99
Enabling the url block list to turn on url blocking by enabling the url block list: · go to web filter > url block . · select enable url block to turn on url blocking. The dfl-500 now blocks web pages added to the url block list. Changing the url block message to customize the message that users rec...
Page 100
You can add urls to the url block list by entering them into a text file and then uploading the text file to the dfl- 500. See uploading a url block list . Sample url block list. Temporarily disabling the url block list · go to web filter > url block . · uncheck enable url block to disable url block...
Page 101
Uploading a url block list you can create a url block list in a text editor and then upload the text file to the dfl-500. Add one url to each line of the text file. You can follow the url with a space and then a 1 to enable or a zero (0) to disable the url. If you do not add this information to the ...
Page 102
Dfl-500 user manual 102.
Page 103: Logging And Reporting
Logging and reporting you can configure the dfl-500 to record 3 types of logs: · traffic logs record all traffic that attempts to connect through the dfl-500 · event logs record changes to the system configuration · attack logs record attacks intercepted by the nids this chapter describes: · configu...
Page 104: Log Message Formats
Example log settings selecting what to log use the following procedure to configure the type of information recorded in dfl-500 logs. When running in transparent mode, the dfl-500 only supports log all events. · go to log&report > log setting . · select log all internal traffic to firewall to record...
Page 105
Traffic log example messages 2002 jun 19 15:35:09 src=192.168.2.1 dst=216.21.132.114 proto=80 msg="tcp, sport=3125, syn, accept" 2002 jun 19 16:35:09 src=192.1.1.2 dst=2.3.4.5 proto=25 msg="udp, sport=udp, sport=5214, accept" event log message format event logs record management events and activity ...
Page 106
Example content filtering messages: 2002 jun 19 23:35:09 src=25.155.34.2 dst=192.168.100.105 proto=http msg="type=web-filter status=banwordblock url=www.Filtered.Com/index.Htm" 2002 jun 12 15:35:02 src=23.11.34.2 dst=192.168.100.105 proto=http msg="type=web-filter status=urlblock url=www.Filtered.Co...
Page 107: Administration
Administration this chapter describes how to use the dfl-500 web-based manager to administer and maintain the dfl-500. It contains the following sections: · logging into the web-based manager · system status · upgrading the dfl-500 firmware · manual antivirus database updates · manual attack databas...
Page 108: System Status
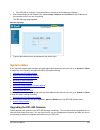
· if the dfl-500 is running in transparent mode, connect to the management interface · start internet explorer and browse to the address https://address where address is the ip address of the interface to which you are connecting. The dfl-500 login page appears. Dfl-500 login page · type an administ...
Page 109
· upgrading the firmware using the web-based manager · upgrading the firmware from a tftp server using the cli upgrading the firmware using the web-based manager using the web-based manager: · go to system > status . · select firmware upgrade . · enter the path and filename of the firmware update fi...
Page 110
· select the following port settings and select ok: · bits per second: 9600 · data bits: 8 · parity: none · stop bits: 1 · flow control: none · press enter to connect to the cli. The following prompt appears: d-link login: · type a valid administrator name and press enter. · type the password for th...
Page 111
· type the address of the internal interface of the dfl-500 and press enter. The following message appears: enter file name [image.Out]: · enter the firmware image file name and press enter. The tftp server uploads the firmware image file to the dfl-500 and messages similar to the following appear: ...
Page 112
To configure the dfl-500 for automatic attack database updates, see automatic antivirus and attack database updates .You can also manually update your attack database by going to system > update and selecting update now. · download the latest attack database from the d-link update website at http://...
Page 113
Restoring system settings to factory defaults use the following procedure to restore system settings to the values set at the factory. This procedure does not change the dfl-500 firmware version or the antivirus database. This procedure deletes all of the changes that you have made to the dfl-500 co...
Page 114
System status monitor at the top of the display, the system status monitor shows: cpu usage the current cpu usage statistics of the dfl-500. Memory usage the percentage of available memory being used by the dfl-500. Up time the number of days, hours, and minutes since the dfl-500 was last started. E...
Page 115: Network Configuration
· select periodic update to turn on the automatic database updates. · select whether to check for and download updates: daily once a day. You can specify the time of day to check for updates. Weekly once a week. You can specify the day of the week and the time of day to check for updates. · select v...
Page 116
· for the internal interface, select modify . · change the ip address and netmask as required. · select the management access methods for the internal interface. Https to allow secure https connections to the web-based manager through the internal interface. Ping if you want the internal interface t...
Page 117
Configuring the external interface for dhcp use the following procedure to configure the dfl-500 external interface to use dhcp. This configuration is required if your isp uses dhcp to assign the ip address of the dfl-500 external interface. To configure the external interface to use dhcp: · go to s...
Page 118
Controlling management access to the external interface use the following procedure to control management access to the dfl-500 through the external interface. You can configure the dfl-500 so that you can access the web-based manager and cli by connecting to the external interface. You can also con...
Page 119
Configuring the management interface (transparent mode) you can configure the management interface for management access to the dfl-500 in transparent mode. To connect to the management interface you must connect to the dfl-500 internal port. To configure the management interface using the web-based...
Page 120
To enable rip server support: · go to system > network > routing . · select internal interface to enable rip server support from the internal interface. · select external interface to enable rip server support from the external interface. Providing dhcp services to your internal network if it is ope...
Page 121: System Configuration
Sample dhcp settings system configuration go to system > config to make any of the following changes to the dfl-500 system configuration: · setting system date and time · changing web-based manager options · adding and editing administrator accounts · configuring snmp · automatic antivirus and attac...
Page 122
· specify how often the dfl-500 should synchronize its time with the ntp server. A typical syn interval would be 1440 minutes for the dfl-500 to synchronize its time once a day. · select apply. Example date and time setting changing web-based manager options you can change the web-based manager idle...
Page 123
There are three administration account access levels: admin has all permissions. Can view, add, edit, and delete administrator accounts. Can view and change the dfl- 500 configuration. There is only one admin level user. Read & write can view and change the dfl-500 configuration. Can view but cannot...
Page 124
· optionally type a trusted host ip address and wildcard mask for the location from which the administrator can log into the web-based manager. If you want the administrator to be able to access the dfl-500 from any address, set the trusted host to 0.0.0.0 and the wildcard mask to 255.255.255.255. T...
Page 125
Dfl-500 traps the dfl-500 agent can send traps to up to 3 snmp trap receivers on your network that are configured to receive traps from the dfl-500. The dfl-500 agent sends traps in response to the events listed in . Snmp traps snmp traps event description system startup the dfl-500 starts or restar...
Page 126
Sample snmp configuration system name type in a name for this dfl-500.The system name can be up to 31 characters long and can contain, numbers (0-9), upper and lower case letters (a-z, a-z), and the special characters - and _. Spaces and the \ [ ] ` $ % & characters are not allowed. System location ...
Page 127
Configuring alert email · go to system >config > alert mail . · in the smtp server field, enter the name of the smtp server to which the dfl-500 should send email. The smtp server can be located on any network connected to the dfl-500. · in the smtp user field, enter a valid email address (for examp...
Page 128: Glossary
Glossary connection : a link between machines, applications, processes, and so on that can be logical, physical, or both. Dns, domain name service : a service that converts symbolic node names to ip addresses. Ethernet : a local-area network (lan) architecture that uses a bus or star topology and su...
Page 129
Netmask : also called subnet mask. A set of rules for omitting parts of a complete ip address to reach a target destination without using a broadcast message. It can indicate a subnetwork portion of a larger network in tcp/ip. Sometimes referred to as an address mask. Ntp , network time protocol : u...
Page 130
Vpn, virtual private network : a network that links private networks over the internet. Vpns use encryption and other security mechanisms to ensure that only authorized users can access the network and that data cannot be intercepted. Virus : a computer program that attaches itself to other programs...
Page 131: Troubleshooting Faqs
Troubleshooting faqs · general administration · network configuration · firewall policies · schedules · vpn · virus protection · web content filtering · logging general administration q: i am trying to set up some of the firewall options, but it keeps asking me for a password while i work. Increase ...
Page 132: Schedules
Use the setup wizard to make sure that the external address and external gateway of the firewall have been properly set to your internet service provider's (isp) specifications. If there is no discrepancy, it would be a good idea to double check with your isp that they have provided you with the cor...
Page 133: Web Content Filtering
Set virus protection to block. See configuring antivirus protection . Next contact d-link and obtain an antivirus database update which includes protection against the new virus. To install the new database, see automatic antivirus and attack database updates . Web content filtering q: my employees ...
Page 134: Technical Support
Technical support offices australia d-link australia unit 16, 390 eastern valley way, roseville, nsw 2069, australia tel: 61-2-9417-7100 fax: 61-2-9417-1077 toll free: 1800-177-100 (australia), 0800-900900 (new zealand) e-mail: support@dlink.Com.Au, info@dlink.Com.Au url: www.Dlink.Com.Au benelux d-...
Page 135
Registration card print, type or use block letters. Your name: mr./ms _____________________________________________________________________________ organization: ________________________________________________ dept. ____________________________ your title at organization: __________________________...
Page 136
Dfl-500 user manual 136.
Page 137: Limited Warranty
Limited warranty d-link systems, inc. (“d-link”) provides this 1-year warranty for its product only to the person or entity who originally purchased the product from: · d-link or its authorized reseller or distributor. · products purchased and delivered with the fifty united states, the district of ...
Page 138
Submitting a claim. Any claim under this limited warranty must be submitted in writing before the end of the warranty period to an authorized d-link service office. · the customer must submit as part of the claim a written description of the hardware defect or software nonconformance in sufficient d...
Page 139
Governing law: this 1-year warranty shall be governed by the laws of the state of california. Some states do not allow exclusion or limitation of incidental or consequential damages, or limitations on how long an implied warranty lasts, so the foregoing limitations and exclusions may not apply. This...
Page 140: Registration
Registration register the d-link dfl-500 office firewall online at http://www.Dlink.Com/sales/reg dfl-500 user manual 140