- DL manuals
- D-Link
- Other
- DFL-M510
- User Manual
D-Link DFL-M510 User Manual
Summary of DFL-M510
Page 1
Network security solution http://www.Dlink.Com dfl-m510 security security information security gateway(isg) user manual.
Page 3
I before you begin before you begin using this manual, take a look at the copyright, trademark, and safety information in this section. Copyright this publication, including all photographs, illustrations and software, is protected under international copyright laws, with all rights reserved. Neithe...
Page 4
Ii gnutella ( ) is a registered trademark of osmb, llc kazza ( ) is a registered trademark of sharman networks bittorrent ( ) is a registered trademark of bittorrent, inc. Directconnect ( ) is a registered trademark of neo modus inc. Pp365 ( ) is a registered trademark of pp365.Com inc. Winmx ( ) is...
Page 5
Iii shielded interconnect cables and a shielded ac power cable must be employed with this equipment to ensure compliance with the pertinent rf emission limits governing this device. Changes or modifications not expressly approved by the system's manufacturer could void the user's authority to operat...
Page 6
Iv.
Page 7
Table of contents chapter 1: getting started with the dfl-m510 ------------------------------------------------- 1 identifying components .......................................................................................... 1 front view .............................................................
Page 8
Vi chapter 5: objects ------------------------------------------------------------------------------------------63 the objects screen ........................................................................................................... 63 the setup hosts tab ......................................
Page 9
Vii history command ................................................................................................. 121 exit command ...................................................................................................... 122 reboot command ..............................................
Page 10
1 chapter 1: getting started with the dfl-m510 the dfl-m5 10 is a transparent network device. To ensure there is no disruption to your network, it can be installed in in-line mode with a hardware bypass function enabled. The hardware bypass ensures that if the dfl-m510 crashes, or experiences a powe...
Page 11
2 status leds the following table describes the status leds on the front of the dfl-m510. Function naming color status led description off power off power power green on power off power off (system not ready) system system green on system ready and running ok off hardware bypass is not enabled bypas...
Page 12
3 detailed information on the lcm can be found in the appendix. See “appendix a: the command line interface” on page 107. Configuring the dfl-m510 before managing the dfl-m510, it must be initialized. This procedure is accomplished through the dfl-m510 command line interface. Access to the command l...
Page 13
4 data bits 8 parity none stop bits 1 flow control nine 2. To open a connection in windows 95/98/nt/2000/xp go to, program files accessory → communications → super terminal. 3. Once you access the command line interface (cli) with a terminal connection, press any key. The following prompt appears: 4...
Page 14
5 5. Use the get system command to get information on the dfl-m510. 6. Use the set system ip command to set the ip address..
Page 15
6 7. After the system reboots, use set system gateway to set the default gateway. 8. After setting the ip address, mask and gateway, use the get system command to get correct information. Use the web-based interface to configure other parameters. See “configuration through a web-based interface” on ...
Page 16
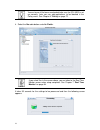
7 configuration through a web-based interface the dfl-m510 gui is a web-based application that allows you to manage the dfl-m510. The gui is a java ™ applet application. Before accessing the gui from any pc, you must install java run time environment (j2re v1.4.2 or above). Then you can log on to th...
Page 17
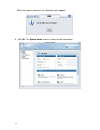
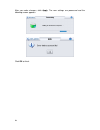
8 3. Click run to start the installation. Follow the onscreen prompts to complete the installation. The following security warning appears. 4. Click always to continue and prevent this screen appearing again. The login screen appears. The ip address shown below is only an example. Instead use the ip...
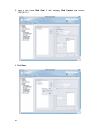
Page 18
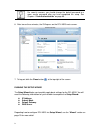
9 for security reasons, you should change the default password to a more secure password after you have completed the setup. See chapter 4 “user authentication” on page 60. 6. After two or three minutes, the gui opens on the dfl-m510 main screen. 7. To log out click the close button at the top-right...
Page 19
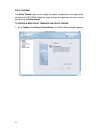
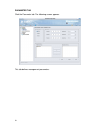
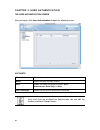
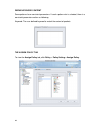
10 the first time you log on to the dfl-m510, the setup wizard starts automatically. Toolbar the toolbar provides many handy and frequent-use functions for you. These functions are mainly divided into three categories: wizard, tools and status, illustrated as below. The wizard, including setup wizar...
Page 20
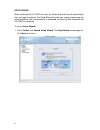
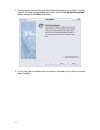
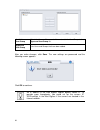
11 setup wizard when initializing the dfl-m510 first time, the setup wizard will launch automatically after you logon the device. The setup wizard will guide you step-by-step through the entire procedure. After the procedure is completed, the basic system information for dfl-m510 is configured. To r...
Page 21
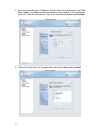
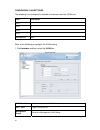
12 2. You need to provide your ip address, subnet mask, default gateway, and dns server address to enable the device to connect to your network. If the network was set by cli, check the settings here. Type in the required information and click next. 3. Select the check boxes for the applications you...
Page 22
13 you can leave all the boxes unchecked to be sure the dfl-m510 is set up correctly. Later you can add applications to be blocked in the policy menu. See chapter 6 “policy ” on page 72. 4. Select the no radio button and click finish. If you select yes in the screen above, you are taken to the real ...
Page 23
14 when the setup is successful, the following screen appears: 5. Click ok. The system status screen is shown for your information..
Page 24
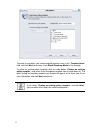
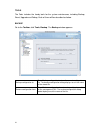
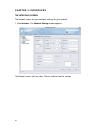
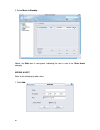
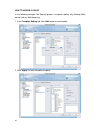
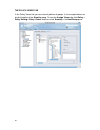
15 policy wizard the policy wizard helps you to simplify the policy configurations and apply policy settings for the dfl-m510. Follow the steps as below to experience the easy use and convenience of policy wizard: to create a new policy template via policy wizard 1. Go to toolbar, click wizard, poli...
Page 25
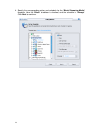
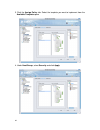
16 2. You can choose to manually setup host/group information here or latter in the tree view list. To setup the host/group information, click the “set up host/group now” button, otherwise, click next to continue. 3. In this step, you can choose either to create a new policy or to select an existing...
Page 26
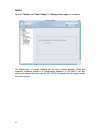
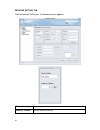
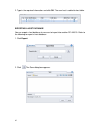
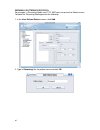
17 to create a new policy, you need to provide a policy name in the “template name” field, and click next to continue. Here block streaming media is the example. To utilize an existing policy template, click the radio button “choose an existing policy template”, and select an existing policy templat...
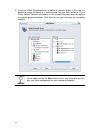
Page 27
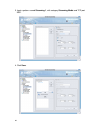
18 4. Specify the corresponding action and schedule for the “block streaming media” template. Here the “block” checkbox is checked, and the schedule is “always”. Click next to continue..
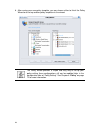
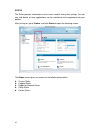
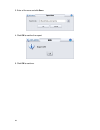
Page 28
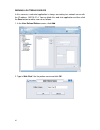
19 5. Assign the “block streaming media” template to a specific group. In this step, it is optional to assign the policy to a specific group. You can latter configure it in the “policy setting” tab when you require. In this example, the policy does not apply to any specific group immediately. Click ...
Page 29
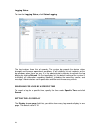
20 6. After saving your new policy template, you can choose either to finish the policy wizard or to set up another policy template via the wizard. The policy wizard provides a simple and easy way to set up your policy setting, these configurations still can be modified latter in the configuration t...
Page 30
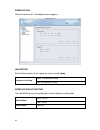
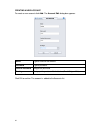
21 tools the tools includes the handy tools for the system maintenance, including backup, reset, upgrade and debug. Each of them will be described as below. Backup go to the toolbar, click tools, backup. The backup window appears. Backup configuration to press backup configuration to store the curre...
Page 31
22 restoring a configuration backup 1. Click browse. 2. Locate the dfl-m510.Cbk file and click open. 3. Click restore to send the file to the device. 4. When the update completes, click reboot to reboot the device. The configuration file includes the user-defined policy. Reset go to the toolbar, cli...
Page 32
23 rebooting or resetting the device closes the gui. Log back on as you normally do. Upgrade go to the toolbar, click tools, upgrade. The firmware upgrade window appears, see below. File path type the file path to the update file. Browse press browse to locate the update file. Then press upload to s...
Page 33
24 debug go to the toolbar, click tools, debug. The debug window appears, see below. The debug tool is a trouble shooting tool for your hardware provider. When you encounter hardware problems or configuration problems of dfl-m510, you can retrieve the debug information from the dfl-m510, and provide...
Page 34
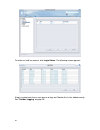
25 status the status provides information on the current network and system settings. You can also find details of what applications can be monitored and incorporated into your policies. After you log on, go to toolbar, and click status to open the following screen: the status screen gives you acces...
Page 35
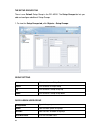
26 system status the system tab information is updated every minute. You can also click the refresh button to update the information. To view the system status, click status/system. Ip address shows the ip address (the default is 192.168.1.1) subnet mask shows the subnet mask (the default is 255.255...
Page 36
27 last time updated shows last time the firmware was updated pattern version shows the pattern version last time updated shows the last time the pattern was updated pattern number shows the pattern number boot time/up time shows the last time the device was booted up device time shows the system de...
Page 37
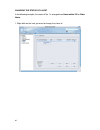
28 logging status to view the logging status, click status/logging. The log involves three lists of records. The system log records the device status changes and firmware operational conditions. It will statically list out incidents on the log windows when there are any. It is the administrator’s de...
Page 38
29 navigating logs use the navigation arrows > to jump to the first or last page. Use prev/next, to go to the previous or next page. Go to a specific page by selecting it from the page drop-down arrow. The report for network status to view the report for network status, click status /report. In the ...
Page 39
30 interactive report after you click generate, the report window opens. The above screen is described in the real time monitor chapter. See “monitoring real time traffic”. Click print to print the report. Click save as to save the report to the local computer. Click close to close the report window...
Page 40
31 viewing a saved report reports are saved in html format and can be viewed in a web browser. 1. Click save as. 2. Type a name for the report and click save as. 3. Open the file you saved in your web browser. 4. Scroll down to view the details of the report..
Page 41
32 policy status to view the policy status, click status/policy status. Application status click application to select the application category which you want to know. It will display the current version in the right field. The following are the currently supported applications and version of the df...
Page 42
33 grokstar v2.6 directconnect 2.2.0 beedo 2.0 pp365 2004 softether 2.0 vnc 3.37 realplayer 10.5 windows media player 10.0 h.323 rtsp itunes 4.8 winamp 5.09 radio365 1.1.11 streaming media quicktime 6.5.2 general ftp applications getright : 5.2d file transfer flashget : 1.71 msn : 7.5(build 7.5.031)...
Page 43
34 request new application support if there is a new application that the dfl-m510 can not support, you can use this function to request support. 1. Click user request. The following screen appears. 2. Complete all information of the new application, and click send. You will be contacted by the d-li...
Page 44
35 pattern status to view the pattern status, click status/pattern status. Pattern information this page will display the pattern information last update shows the last time the pattern was updated version of current pattern shows the pattern version number of pattern shows the pattern number patter...
Page 45
36 chapter 2: system the system menu is where you carry out the basic setup of the dfl-m510 such as integration with your network. The system menu also lets you set local time settings and carry out maintenance. The system screen after you log on, click system to open the following screen: the syste...
Page 46
37 the date and time screen use date and time to adjust the time for your location. 1. Click system > date and time. The date and time window appears. 2. Click to the right of current date and time..
Page 47
38 3. Select the current date and click to return to the date and time screen. 4. In the current date and time field, type in the current time and then choose the time zone for your location from the drop-down list. 5. Click apply to confirm your settings. The following screen appears: 6. Click ok t...
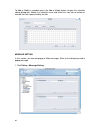
Page 48
39 the remote management screen use remote management to allow management remotely. The following screen appears. The dfl-m510 can be remotely managed via http or ssh. The remote access tab lets you control access rights. Http/ssh the descriptions for the http and ssh fields are the same. Server acc...
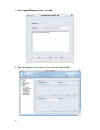
Page 49
40 configuring server access for ssh for specific ip addresses 1. Select wan in the server access field. 2. Click the selected ip address radio button and click add. 3. Type in the ip address and subnet mask for the pc that will access the dfl-m510 and click ok. The ip address is added to the select...
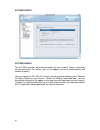
Page 50
41 when the settings are processed, the following screen appears: 5. Click ok to finish..
Page 51
42 chapter 3: interfaces the interface screen the network screen lets you configure settings for your network. 1. Click interface. The network setting window appears. The network screen has four tabs. Click on a tab to view the settings..
Page 52
43 network setting tab click the network setting tab. The following screen appears. Device name type a name for the device. Inactivity timeout set the inactivity time out..
Page 53
44 when more than one dfl-m510 is installed in your location, assign device names to help identify different units. Device setting these fields display the ip address and related network information of the device. Ip address device ip address subnet mask device subnet mask dns server device dns serv...
Page 54
45 admin email to enable the network administrator to receive emails from the dfl-m510, the following fields must be completed. Email address type the administrator’s email address smtp server type the ip of the smtp server id type an id if sender authentication is required password type a password ...
Page 55
46 snmp configuration to set up snmp (simple network management protocol), the snmp communities have to be set and access control to the snmp server has to be enabled set community type the snmp community that allows the snmp set command. You can use snmp software to configure the device such as sys...
Page 56
47 configuring server access for lan and wan for specific ip addresses 1. Select all in the server access field. Note: this setting has no remote access restrictions; any ip address will have access to the dfl-m510. 2. Click the selected ip address radio button and click add. 3. Type in the ip addre...
Page 57
48 when the settings are processed, the following screen appears: 5. Click ok to finish..
Page 58
49 interface tab click the interface tab. The following screen appears. Link setting set the ethernet ports for the speed you want and click apply. Wan - 10/100/half/full/auto interface link setup lan -10/100/half/full/auto interface stealth setting the lan/wan ports can be configured in stealth mod...
Page 59
50 after you make changes, click apply. The new settings are processed and the following screen appears: click ok to finish..
Page 60
51 parameter tab click the parameter tab. The following screen appears. This tab defines management parameters..
Page 61
52 operation mode in-line in in-line mode, the dfl-m510 works as a transparent gateway in your network. All traffic is inspected as it passes through the dfl-m510. The dfl-m510 responds to illegal activities based on policy rules. When attacks are detected, the dfl-m510 can take the following action...
Page 62
53 dmz bypass in order to speed up traffic from the intranet to dmz, hosts within the given dmz subnet addresses are not checked and all packets from or to those hosts pass unhindered. Ip address type in the ip address subnet mask type in the subnet mask the ip addresses of the hosts in a subnet mus...
Page 63
54 setting up the dmz bypass function in the following example, a mail server with the ip address 10.10.10.250 is added to dmz bypass. 1. Type in the ip address and the subnet mask of the mail server. 2. Click save. Host/groups bypass hosts within the intranet which do not need to be monitored are a...
Page 64
55 available user/group select the user or group and click >> to add the user/group to the bypassed user/group list. Bypassed user/group lists users and groups that have been added. After you make changes, click save. The new settings are processed and the following screen appears: click ok to conti...
Page 65
56 vlan tab click the vlan tab. The following screen appears. A vlan (virtual lan) is a group of devices on one or more lans that are configured (using management software) so that they can communicate as if they were attached to the same wire, when in fact they are located on a number of different ...
Page 66
57 configuring vlan settings the following is an example of a network environment with four vlan sets. Item description vid1 1 vid2 3 vid3 5 vid4 7 management vid2 refer to the following to configure the vlan setting. 1. Click interface and then select the vlan tab. Vlan enabled enables or disables ...
Page 67
58 2. Click the vlan enabled checkbox to enable vlan. 3. Type in each vid in the vid1 to vid7 boxes. The dfl-m510 supports up to seven vlans. The management vid must be either pvid, or vid1 to vid7. Configurations depend on your environment. 4. Click apply. The screen updates as follows..
Page 68
59 vlan status management ip shows the device ip address management vlan shows the management vlan group id vid1 - vid7 shows the id of each vlan.
Page 69
60 chapter 4: user authentication the user authentication screen after you log on, click user authentication to open the following screen. Accounts no. Shows the current number of accounts name shows the name for each account role shows the shows the level of the user ’ s policy: administrator; read...
Page 70
61 creating a new account to create a new account click add. The account edit dialog box appears. Name type a name for the account. Password type a password. Confirm password retype the password. Privilege assign privilege status: administrator; read only; or write. Click ok to confirm. The account ...
Page 71
62 to review or audit an account, click login status. The following screen appears: a log is created each time a user logs on or logs out. Monitor this list for added security. See “toolbar, logging” on page 28..
Page 72
63 chapter 5: objects in dfl-m510, the term “objects” mainly refers to hosts and groups. A host is a client computer with a network interface. A group is a set of hosts. The dfl-m510 learns host information from packets passing through the device. Host information includes the mac address, ip addres...
Page 73
64 the setup hosts tab the setup hosts tab lets you add new hosts and manage current hosts. 1. To view the setup hosts tab, click objects > setup hosts. No. Shows the current number of hosts state shows the status for each host (refer to color legend at the bottom of the screen) host/ip address show...
Page 74
65 changing the status of a host in the following example, the status of no. 1 is changed from hosts within 150 to other hosts. 1. Right-click on the host you want to change the status of..
Page 75
66 2. Select move to standby. Notice, the state icon is now green, indicating the host is now in the other hosts category. Adding a host refer to the following to add a host. 1. Click add..
Page 76
67 2. Type in the required information and click ok. The new host is added to host table. Exporting a host database you can export a host database to reuse or to import into another dfl-m5 10. Refer to the following to export a host database. 1. Click export. 2. Click . The save dialog box appears..
Page 77
68 3. Enter a file name and click save. 4. Click ok to confirm the export. 5. Click ok to continue..
Page 78
69 the setup groups tab there is one default setup group in the dfl-m510. The setup groups tab lets you add and configure additional setup groups. 1. To view the setup groups tab, click objects > setup groups. Group setting add click to add a new setup group delete click to delete a setup group up c...
Page 79
70 hosts in selected group lists the hosts in the selected group add subnet click to add a sequential ip address range to a group. Assigning hosts to groups you can assign a host to a group by checking the button crossing the host and the group. Refer to the following to add a host to a group. 1. Cl...
Page 80
71 3. Select the host and click to add it to the hosts in selected group window. 4. Click apply. 5. Click ok to finish. The new group is added to the group setting list..
Page 81
72 chapter 6: policy policy is the most important information in the dfl-m510 management system. A policy can consist of thousands of patterns. Each pattern defines how to detect an application, how to respond when an application is detected, what to block, and when to block. You can view and modify...
Page 82
73 manually or via the template wizard. Once a template is defined, it can be assigned to a host or a group and it becomes a complete policy. The policy setting screen after you log on, click policy/policy setting to open the following screen: every template, including the global template created by...
Page 83
74 video communication icq chat icq5 file transfer login audio communication video communication aim chat 5.9.3759 file transfer login audio communication video communication ichat chat 2.1 file transfer login audio communication video communication yahoo file transfer 6.0.0.1921 messenger login cha...
Page 84
75 file transfer web web web page keyword -- control application url keyword upload web post download java applet cookie mail smtp mail attached file -- connect b. The p2p/remote access application that can be allowed/blocked by the dfl-m510 item protocol software version internet file ezpeer ezpeer...
Page 85
76 bittorrent bittornado 0.3.12 bitcomet 0.59 bittorrent experimental 3.2.1 beta 2 shareaza 2.1.2.0 beta bittorrent 4.1.2 beta mldonkey 2.5.X directconnect peerweb dc++ 0.205 dc++ 0.674 directconnect 2.205 pigo pigo v 3.0 pp365 pp365 v2004 winmx winmx 3.53 pc anywhere pc anywhere 11 vnc vnc ver. 3.3...
Page 86
77 the dfl-m510 manages p2p downloads by using p2p protocol. In this architecture, no matter what version of client is used, the dfl-m510 can manage it. The dfl-m510 only supports http download via getright. The policy setting screen has the following three tabs: • “the template setting tab” on page...
Page 87
78 when you select a template from this list, its patterns are listed in the center pane. You can add, delete, and duplicate templates. To quickly make a new template, find an existing template that has a similar pattern and duplicate it. Then modify the new template as desired. Each time only one c...
Page 88
79 alert by email an email with details of the attack to the administrator defined in email management parameter. Win popup message send a windows popup message to the user. Web message send a message to the user and cut the web connection and replace it with a web page. When you turn off messenger ...
Page 89
80 define keyword content some patterns have constraint parameters. If such a pattern rule is selected, there is a constraint parameter section as following. Keyword: the user defined keyword to match the content of packets. The assign policy tab to view the assign policy tab, click policy > policy ...
Page 90
81 how to assign a policy in the following example, the security group is assigned a policy only allowing web control such as web browsing. 1. In the template setting tab, click add to add a new template. 2. Click “apply” to save the policy template..
Page 91
82 3. Click the assign policy tab. Select the template you want to implement from the available templates pane 4. Under host/group, select security and click apply..
Page 92
83 the policy viewer tab in the policy viewer tab, you can view all policies of groups. In the example below, we check the policy of the security group. To view the assign viewer tab, click policy > policy setting > policy viewer and then select security in the host/group pane..
Page 93
84 user defined pattern the pattern database is made by a team of professional signature researchers. They are familiar with protocols, system vulnerability, and application patterns. After a new application pattern is detected, the pattern is put into the pattern database and published. Before publ...
Page 94
85 defining a pattern by protocol for example, a streaming media sees tcp 3001 ports to connect to media servers. To block this streaming media game do the following. 1. In the user defined pattern screen, click add. 2. Type in streaming1 for the pattern name and click ok..
Page 95
86 3. Input a pattern named streaming 1, with category streaming media and tcp port 3001. 4. Click save..
Page 96
87 defining a pattern by server in this scenario, a web chat application is always connecting to a network server with the ip address 140.126.21.4. You can block this web chat application and then click the save button to add a new rule as follows. 1. In the user defined pattern screen, click add. 2...
Page 97
88 3. Input a rule name web chat 1, with category web control and servers, 140.126.21.4. 4. Click save..
Page 98
89 the dfl-m510 supports 1500 sets of user-defined patterns by protocol and 1500 sets of user-defined patterns by application server. The schedule screen it is possible to define the active time range of a policy. The time range can be defined by the schedule. Each schedule has a name, and a time ra...
Page 99
90 to add or modify a schedule press the add or modify button to open the schedule editing dialog box. Modify the schedule name and check the hour tab to include or exclude the hour represented by the tab. Message setting in this section, you can edit popup or web messages. Refer to the following to...
Page 100
91 2. Under popup message to user, click add. 3. Type a description and the content of the message and click ok..
Page 101
92 when you turn off messenger service or enable personal firewall, the win popup message function works correctly. Keyword filter the dfl-m510 provides the following keyword functions: • web page keyword • url keyword • msn keyword these keyword functions are used to describe applications of msn an...
Page 102
93 pattern update pattern update the dfl-m510 provides up-to-date protection for your network. Pattern information can be reviewed in this section such as last update, version of current pattern and number of pattern. You can register the dfl-m510 in d-link's security portal by clicking on the "regi...
Page 103
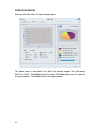
94 chapter 7: real time monitor the real time monitor provides real-time tracking of network usage in the form of text and graphs. System administrators can monitor significant application pattern events, quickly understand network status, and take imperative action. The real time monitor screen aft...
Page 104
95 monitoring real time traffic to monitor real time traffic check the real time traffic radio button. All the number of bytes of all packets received all m510 the total amount of traffic the dfl-m510 can manage drop the number of bytes of packets that are identified as an application patter and dis...
Page 105
96 administrators can accumulate and analyze detected application patterns by information revealed from their packets. These are explained in the top n analysis section. Refresh time the system provides the new traffic status every thirty seconds. Traffic lines one line in the traffic chart means on...
Page 106
97 the real time application page shows management information classified by pre-defined types and hosts. The left of this screen displays the current application information; the right of this screen displays the accumulated application information for top n analyzing. The right part is the same as...
Page 107
98 health checking the health checking table is a layer seven table. Instead of classifying the application pattern, several packets that come from attacking tools can damage the host. Some of the packets are assembled and stored in the file system and are detectable by anti-virus software. Some pac...
Page 108
99 eim the eim table provides layer seven monitoring. A packet is classified by its application pattern and summarized into six categories: im, p2p, web application, file transfer, e-mail, and media. If a host is connecting to the internet and identified as a category application, the table shows a ...
Page 109
100 two levels top n analysis administrators can review detected application patterns by information revealed from its packets. All triggered incidents are categorized on the principle of sequence, health, time of occurrence, name of pattern, source address, destination address, counts, and responsi...
Page 110
101 the lower list shows details of each category. When the im category is chosen, the second level chart covers the first chart as follows: it would be understood that the msn is the most frequent application within the im category. If you press reset, all data is erased. Click back to go to the pr...
Page 111
102 top 10 applications / top 10 users in these charts, the first level shows the top 10 applications. When an application is chosen, the second level shows the top 10 users in the chosen application. The following means that the top application is msn..
Page 112
103 top 10 groups/top 10 applications in these charts, the first level shows the top 10 groups. When a group is chosen, the second level shows the top 10 applications. The following means that the top group is the default group..
Page 113
104 top 10 users/top 10 applications in these charts, the first level shows the top 10 users. When a user is chosen, the second level shows the top 10 applications in the chosen user. The following means that the top user is jeffrey..
Page 114
105 top n health concerns/top n users in these charts, the first level shows the top 3 health concerns. When a health concern is chosen, the second level shows the top 10 users in the chosen health concern. The following means that the top health concern is the illegal agent..
Page 115
106 top n user with health concerns/top n health concerns in these charts, the first level shows the top 10 users with health concerns. When a user is chosen, the second level shows the top 3 health concerns in the chosen user. The following means that the top user with health concern is cjho..
Page 116
107 appendix a: the command line interface this section covers the following topics: z terminal/ssh (secure shell) connection z cli command list z help command z get command z set command z exit command z reboot command z reset command z ping command terminal/ssh (secure shell) connection the dfl-m5...
Page 117
108 getting started once you have accessed the command line interface (cli) with a terminal connection, press any key and the following prompt will appear. Enter the user name and password: the default user name is admin, the default password is admin. Welcome to d-link dfl-m510 console environment ...
Page 118
109 help command help is used for getting information of other command’s usage and argument configuration. Main command sub command example command description get help get display all information of “get” command. Set help set display all information of “set” command. History help history display a...
Page 119
110 (d) help exit >> help exit exit - log out (e) help reboot >> help reboot reboot - reboot system (f) help reset >> help reset reset - reset system configurations to manufacturing defaults (g) help set >> help ping ping - ping utility.
Page 120
111 get command this command will display all kinds of configuration information of the dfl-m510. Main command sub command example command description system get system display system configurations, including ip, password and etc. Time get time display device clock setting state get state display d...
Page 121
112 (c) get state >> get state operation mode: in-line (d) get interface >> get interface interface: wan: auto. Lan: auto. Set command use this command to set the system’s parameter. Main command sub command command description system set system configurations, including ip, password and etc. Time s...
Page 122
113 vlan set system vlan set the vlan environment related parameters name set system name set device’s name prefix command 2 nd command 3 rd command postfix comman d example command description tcptimeout 20 -2592000 set system detect tcptimeout 6000 set tcp connection timeout on set system detect p...
Page 123
114 prefix 2 nd command 3 rd command example command description on set system vlan on turn on vlan function off set system vlan off turn off vlan function set system vlan vid 1 - 4094 set system vlan 1 set vlan id example (a) set system ip >> set system ip 192.168.1..245 do you want to apply this s...
Page 124
115 (f) set system detect policy wan on >> set system detect policy wan on apply policy check for wan interface ok. (g) set system detect policy wan off >> set system detect policy wan off remove policy check for wan interface ok. (h) set system detect policy lan on >> set system detect policy lan o...
Page 125
116 (n) set system detect tcpcoldstart 250 >> set system detect tcpcoldstart 250 change tcp cold start duration time ok. (o) set system vlan on >>set system vlan on turn on vlan function. (p) set system vlan off >>set system vlan off turn off vlan function. (q) set system vlan vid 1 >>set system vla...
Page 126
117 change time successfully ! Current time : (gmt + 0) mon apr 18 10:57:43 2005 dst time : (gmt + 0) mon apr 18 10:57:43 2005 system duration: 0 days 1:9:1 “set state” command prefix 2 nd command example command description inline set state inline set isg to execute normally based on its configured...
Page 127
118 “set remote” command prefix command 2nd command 3rd command postfix command command description wan enable remote access using browser from wan port lan enable remote access using browser from lan port all enable remote access using browser from wan and lan port access disable disable remote acc...
Page 128
119 example (a) set remote http access wan >> set remote http access wan do you want to apply this setting immediately? Your current ssh/http connection will be cut off. (y/n) (b) set remote http access lan >> set remote http access lan do you want to apply this setting immediately? Your current ssh...
Page 129
120 (h) set remote ssh access lan >> set remote ssh access lan do you want to apply this setting immediately? Your current ssh/http connection will be cut off. (y/n) (i) set remote ssh access all >> set remote ssh access all do you want to apply this setting immediately? Your current ssh/http connec...
Page 130
121 “set interface” command main command sub command command description set interface set interface link mode example (a) set interface >> set interface interface. Wan: auto lan: auto setup wan port configuration : specify auto mode or speed [auto / 10 / 100] : specify stealth mode [on / off] : set...
Page 131
122 exit command use this command to exit command shell. Main command sub command example command description exit none exit exit command shell example (a) exit >> exit logout welcome to d-link dfl-m510 console environment copyright (c) 2005 d-link corp. Dfl-m510 login: reboot command use this comma...
Page 132
123 reset command use this command to reset system configuration to default settings. Main command sub command example command description reset none reset reset system configuration to default settings, type "y" to load default setting. Example (a) reset >> reset this will set the system configurat...
Page 133
124 appendix b: glossary bandwidth the transmission capacity of a given device or network bit a binary digit (either a one or a zero); a single digit number in base-2. A bit is the smallest unit of computerized data. Bridge a device that connects two different kinds of local networks, such as a wire...
Page 134
125 fcc (federal communications commission) the fcc (federal communications commission) is in charge of allocating the electromagnetic spectrum and thus the bandwidth of various communication systems. Firewall a hardware or software "wall" that restricts access in and out of a network. Firewalls are...
Page 135
126 irc (internet relay chat) it is a way for multiple users on a system to “chat” over the network. Isp (internet service providers) provide connections into the internet for home users and businesses. There are local, regional, national, and global isps. You can think of local isps as the gatekeep...
Page 136
127 router a device that connects two networks together. Routers monitor, direct and filter information that passes between these networks. Rs-232 rs-232 is an eia standard which is the most common way of linking data devices together. Server a computer, or a software package, that provides a specif...
Page 137
128 url (uniform resource locator) url is an object on the internet or an intranet that resides on a host system. Objects include directories and an assortment of file types, including text files, graphics, video and audio. A url is the address of an object that is normally typed in the address fiel...
Page 138
129 appendix c: features and specifications hardware specification ethernet 2 x 10/100 m auto-sensing auto-crossing with frog light other port rs232(9 pin) lcd module blue background with white light lcd panel power ac line 100-240v ac 50-60hz 0.8a max dimension (l*d*h, mm) 440mm * 250mm * 44mm feat...
Page 139
130 11. Morpheus 12. Bearshare 13. Wimmx web browser (http/html) 1. Web mail 2. Web uploading 3. Web download 4. Web posting 5. Web im 6. Web url filter 7. Web content 1. Login 2. Post/put 3. Upload 4. Download 5. Url 6. Keyword 7. Cookie retrieval 3. Web application control java applet /activex app...
Page 140
131 helper identification hosts 2. Trojan affected hosts 3. Spyware/adware affected hosts 4. Intruded hosts generated by victim lcm module main menu sub-menu description firmware ver policy ver policy number current date current time dev. Up time cpu load memory usage system info. Current session wa...
Page 141
132 wan link mode wan stealth reset reset confirm reboot reboot confirm other specifications performance: 30-40 mbps (all function enabled), wires peed for l3 switching concurrent users: 150 concurrent tcp sessions: 4,000
Page 142
133 mechanic & id design front led indicators function naming color status led description off power off power power green on power on off power off (system not ready) system system green on system ready and running ok off system bypass not enable bypass bypass red on system bypass or failed off eth...
Page 143
134 physical environment power ~ 25w open frame switching power supply, input ac range 100 ~ 240v 50/60hz. Operation temperature 0 – 60 storage temperature -20 – 70 humidity operation: 10%~90% rh storage: 5%~90% rh.
Page 144
135 index a active schedule, template 64 administrator, email notification 25 application block, new 102 application blocking, supported 100 assign policy tab 66 b bypass zone, dmz 33 bypass, hosts/groups 35 c command line interface 105 common network protocol 82 configuring, command line interface ...
Page 145
136 n network analysis 84 network screen 23 network setting tab 23 network, status 98 o operation mode, inline, bypass, monitor 32 p parameter tab 32 pattern, user defined 68 policy rule, by server 71 policy rule, defining 69 policy screen 55 policy setting screen 58 policy status tab 100 policy vie...