- DL manuals
- D-Link
- Gateway
- DSA-3600
- User Manual
D-Link DSA-3600 User Manual
Summary of DSA-3600
Page 1
Dsa-3600 user guide version dsa-3600-3.00 december, 2007.
Page 2
Copyright © 2007 d-link corporation all rights reserved. Printed in taiwan. D-link corporation reserves the right to change, modify, and revise this publication without notice. Trademarks copyright 2007 d-link corporation. All rights reserved. D-link, the d-link logo, and dsa-3600 are trademarks of ...
Page 3: Table of Contents
Table of contents chapter 1. Before you start .............................................................................................................................................1 1.1 audience .....................................................................................................
Page 4
4.3 access points ........................................................................................................................................................76 4.3.1 list .......................................................................................................................
Page 5
Appendix g. Network configuration on pc ...............................................................................................................173 appendix h. Local vpn ..............................................................................................................................
Page 7: 1.1 Audience
Chapter 1. Before you start 1 chapter 1. Before you start 1.1 audience this manual is intended for use by system integrators, field engineers and network administrators to help them set up dsa-3600 multi-service business gateway in their network environments. It contains step by step procedures and ...
Page 8: Chapter 2. Overview
Chapter 2. Overview 2 chapter 2. Overview 2.1 introduction of dsa-3600 dsa-3600 is a multi-service business gateway specially designed for small and medium business, and branch office operational environments. The major functional areas include user management, access control, ap management, securit...
Page 9
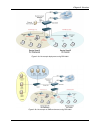
Chapter 2. Overview 3 figure-2.2a: an example deployment using dsa-3600 figure-2.2b: an example of smb environment using dsa-3600
Page 10
Chapter 3. Hardware installation 4 chapter 3. Hardware installation 3.1 panel function descriptions the dsa-3600 is implemented on an embedded platform with mini-desktop form factor. On the front panel of the product, there are eight leds that are used to indicate the system power, system status, an...
Page 11
Chapter 3. Hardware installation 5 rear panel 1 power socket: the power adapter is attached here. 2 reset button: press and hold the reset button about five seconds, status led on front panel starts to blink before restarting the dsa-3600. Press and hold the reset button for more than ten seconds; s...
Page 12: 3.2 Package
Chapter 3. Hardware installation 6 3.2 package contents the standard package of the dsa-3600 includes: y dsa-3600 x 1 y quick install guide x 1 y cd-rom x 1 y console cable x 1 y straight-through ethernet cable x 1 y power cord x 1 y power adapter x 1 3.3 system requirement y standard 10/100baset in...
Page 13
Chapter 4. Web interface configuration 7 chapter 4. Web interface configuration this chapter provides further detailed information on setting up the dsa-3600. The following table shows all the functions of dsa-3600. In the web management interface, there are three main interface areas: tools menu, m...
Page 14
Chapter 4. Web interface configuration 8 option function nat privilege monitor ip walled garden proxy server ddns client mobility network vpn system interface routing table online users user logs status e-mail & syslog setup wizard password change backup & restore system upgrade restart utilities to...
Page 15
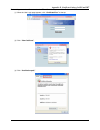
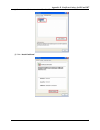
Chapter 4. Web interface configuration 9 web management interface the dsa-3600 provides a web management interface for configuration. After completing the hardware installation, the administrator can configure the dsa-3600 via web browsers with javascript enabled such as internet explorer version 6....
Page 16
Chapter 4. Web interface configuration 10 2. After successfully logging into the dsa-3600, the system overview page of the web management interface will appear. To logout, simply click the logout icon on the upper right corner of the interface to return to the administrator login page..
Page 17: 4.1 System
Chapter 4.1 system 11 4.1 system this section provides information on the following functions: general, wan1, wan2, wan traffic, lan port mapping and service zones. It displays the information such as system time, up time and firmware version..
Page 18
Chapter 4. Web interface configuration 12 4.1.1 general the system and network related parameters such as system name, homepage redirect url, management ip address list, and https protected login can be configured from the menu shown as below. Y system name: set the name of the system or use the def...
Page 19
Chapter 4.1 system 13 management ip address list: set the ip addresses within a range which the administrator can use to connect to the web management interface of dsa-3600 via its wan and/or lan ports. The administrator can grant the access of the web management interface by specifying a list speci...
Page 20
Chapter 4. Web interface configuration 14 4.1.2 wan1 there are four connection types supported on the wan1 port: static, dynamic, pppoe, and pptp. Y static (use the following ip settings): select static to specify a static ip address for wan1 port manually when a static ip address is available for d...
Page 21
Chapter 4.1 system 15 y pppoe: select the option when pppoe is the connection protocol provided by the network service providers. When dial on demand is enabled, there is a maximum idle time available. The system will disconnect itself from the internet automatically when the maximum idle time is re...
Page 22
Chapter 4. Web interface configuration 16.
Page 23
Chapter 4.1 system 17 4.1.3 wan2 wan2 can be disabled when selecting none. When wan2 port is enabled, it supports 3 connection types: static, dynamic and pppoe. Y none: the wan2 port is disabled. Y static: select the option to specify a static ip address for wan2 interface manually when a static ip ...
Page 24
Chapter 4. Web interface configuration 18.
Page 25
Chapter 4.1 system 19 4.1.4 wan traffic dsa-3600 supports uplink/downlink bandwidth management and wan failover features, including wan failover, load balancing and connection detection features. Available bandwidth on wan interface: y uplink: it defines the maximum uplink bandwidth allowed to share...
Page 26
Chapter 4. Web interface configuration 20 y enable wan failover: the purpose of wan failover is to have a backup link for wan1 when wan2 is available. Check the check box of enable wan failover to active the wan failover function of the dsa-3600. Normally a service zone uses wan1 as it primary gatew...
Page 27
Chapter 4.1 system 21 4.1.5 lan port mapping dsa-3600 supports multiple service zones in either of the two vlan modes, port-based or tag-based, but not concurrently. In the wireless environment, a service zone of the dsa-3600 is mapped to the vlan with an associated ssid. When the dsa-3600 is set fo...
Page 28
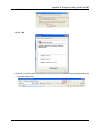
Chapter 4. Web interface configuration 22 ¾ tag-based service zones configuration example – enabling two service zones log in to the web management interface and enter “admin” for both the default username and password in the username and password fields of the administrator login page. After loggin...
Page 29
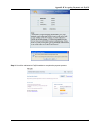
Chapter 4.1 system 23 scroll down to near bottom of page and in the wireless settings area enter the ssid (e.G. Ssid-staff) for connecting to this service zone. Scroll up to the middle of the page where the authentication settings is, and check the enabled box for the authentication required for the...
Page 30
Chapter 4. Web interface configuration 24 remember to enable authentication requirement for this service zone and enable the on-demand users authentication options only. Click apply to activate the changes for the second service zone. Now is the time to restart the system. After the restart, the sys...
Page 31
Chapter 4.1 system 25 figure-4.1.5a: an example using tag-based service zones y port-based: for port-based service zone, each lan port can be assigned to a service zone since a lan port can be mapped to a vlan tag. The mapping between the ports and the service zones are many-to-one. With factory def...
Page 32
Chapter 4. Web interface configuration 26 assume lan1, lan2, lan3 will be used by default service zone for internal staff while lan4 is to be assigned to another service zone for external users only. In the above mentioned page, click lan4’s drop-down menu to select the desired second zone such as ‘...
Page 33
Chapter 4.1 system 27 for single zone deployment, use the default service zone with port-based mode. Figure-4.1.5b: an example using port-based service zones.
Page 34
Chapter 4. Web interface configuration 28 4.1.6 service zones a service zone is a logical network area to cover certain wired and wireless networks in an organization such as smb or branch offices. By associating a unique vlan tag and ssid with a service zone, administrators can separate wired netwo...
Page 35
Chapter 4.1 system 29 ¾ default authentication option: default authentication database/server that is used within the service zone. ¾ status: each service zone can be enabled or disabled. ¾ details: configurable, detailed settings for each service zone. Click the button of configure to configure eac...
Page 36
Chapter 4. Web interface configuration 30 the service zone runs in nat mode. When router mode is chosen this service zone runs in router mode. O ip address: the ip address of this service zone. O subnet mask: the subnet mask of this service zone. ¾ dhcp server: the system supports three types of dhc...
Page 37
Chapter 4.1 system 31 authentication settings the system supports several authentication databases that are local, pop3, radius, ldap, and nt domain and provides up to four authentication options server1~4, one on-demand users authentication option and one sip authentication. The administrator needs...
Page 38
Chapter 4. Web interface configuration 32 ¾ default policy in this service zone: multiple sets of policy are provided by the system. Each policy consists of firewall profile, specific route profile, schedule profile, qos profile, and privilege profile . Policies can be defined in the policy tab. The...
Page 39
Chapter 4.1 system 33 an example of template login page:.
Page 40
Chapter 4. Web interface configuration 34 y login page Æ uploaded page choose uploaded page and upload a login page. The user-defined login page must include the following html codes to provide the necessary fields for username and password. If the user-defined login page includes an image file, the...
Page 41
Chapter 4.1 system 35 choose the external page selection and get the login page from the specific website. In the external page setting, enter the url of the external login page and then click apply. After applying the setting, the new login page can be previewed by clicking preview button at the bo...
Page 42
Chapter 4. Web interface configuration 36 please note: while this process is similar to that of the login page, the html code for the user-defined logout interface however is different. The following html code must be added in order for the user to enter the username and password. After the upload i...
Page 43
Chapter 4.1 system 37 y login success page Æ uploaded page choose uploaded page to upload the login success page. Click the browse button to select the file for the login success page upload. Next, click submit to complete the upload process. After the upload process is completed and applied, the ne...
Page 44
Chapter 4. Web interface configuration 38 4) login success page for on-demand user the users can apply their own login success page for on-demand users in the menu. As the process is similar to that of the login page, please refer to the instructions on login page for more details. Y login success p...
Page 45
Chapter 4.1 system 39 choose uploaded page and get the login success page for on-demand user by uploading. Click the browse button to select the login success page file for instant upload. Then click submit to complete the upload process..
Page 46
Chapter 4. Web interface configuration 40 y login success page for on-demand user Æ external page choose the external page selection to get the login success page for on-demand user from the specific website. In the external page setting, enter the url of the external login success page and then cli...
Page 47
Chapter 4.1 system 41 y logout success page Æ uploaded page choose uploaded page to get the logout success page for upload. Click the browse button to select the file for the logout success page upload. Next, click submit to complete the upload process. After the upload process is completed and appl...
Page 48
Chapter 4. Web interface configuration 42 wireless settings ¾ ssid: each service zone must setup its own ssid. Each ssid as unique name could not be repeated. ¾ security: each service zone can setup its own authentication and encryption support for ap security setting. Authentication support: wpa, w...
Page 49: 4.2 Users
Chapter 4.2 users 43 4.2 users this section provides information on the following functions: authentication, black list, policy and additional control . It displays the information of the user, such as the number of total online users and the number of on-demand users..
Page 50
Chapter 4. Web interface configuration 44 4.2.1 authentication this section is for administrators to pre-configure authentication options for the entire system's service zones. For a particular service zone, administrators can enable all the authentication options which will be used and also specify...
Page 51
Chapter 4.2 users 45 y name: set a name for the authentication option by using numbers (0~9), alphabets (a~z or a ~z), dash (-), underline (_), space and dot (.) only. The length of this field is up to 40 characters. This name is used for the administrator to identify the authentication options easi...
Page 52
Chapter 4. Web interface configuration 46 y add user: click this button to enter into the adding user(s) to the list interface. Fill in the necessary information such as “username”, “password”, “mac” and “remark”. Select a desired policy and choose whether to enable local vpn. Only “username” and “p...
Page 53
Chapter 4.2 users 47 y download user: use this function to create a .Txt file with all built-in user account information and then save it on disk. Y search: enter a keyword of a username to be searched in the text filed and click this button to perform the search. All usernames matching the keyword ...
Page 54
Chapter 4. Web interface configuration 48 y edit user: if editing the content of individual user account is needed, click the username of the desired user account to enter the editing existing user data interface for that particular user, and then modify or add any desired information such as “usern...
Page 55
Chapter 4.2 users 49 ¾ account roaming out: the system’s local user database can also be an external radius database to another system. When account roaming out is enabled, local users can login from other domains with their original local user accounts. The authentication database with their origin...
Page 56
Chapter 4. Web interface configuration 50 supports end-users’ devices under windows 2000 and windows xp sp1, sp2. Y server: the ip address of the external pop3 server. Y port: the authentication port of the external pop3 server. Y ssl setting: the system supports pop3. Check the check box of the ssl...
Page 57
Chapter 4.2 users 51 subnet mask, and shared secret key of the authorized devices. An example would be those downstream access points with 802.1x option turned on and shared secret key set accordingly. Click the hyperlink roaming out & 802.1x client device settings to enter the roaming out & 802.1x ...
Page 58
Chapter 4. Web interface configuration 52 4.2.1.4 authentication database – ldap the system supports authentication by an external ldap authentication database. There are two sets of ldap server provided by the system, primary and secondary, which are for fault tolerance. Click the hyperlink configu...
Page 59
Chapter 4.2 users 53 4.2.1.5 authentication database – nt domain the system supports authentication by an external nt domain authentication database. Y server: the ip address of the external nt domain server. Y transparent login: transparent loginmeans windows nt domain single sign on. When transpar...
Page 60
Chapter 4. Web interface configuration 54 4.2.1.6 authentication database – ondemand there are some deployment scenarios (for example, at venues such as coffee shops, hotels, restaurants, etc.) where retail customers or casual visitors want to get wireless internet access. To offer the wi-fi access ...
Page 61
Chapter 4.2 users 55 ticket printer which is connected to the serial port. 2) ticket customization on-demand account ticket can be customized here and previewed on the screen. Y receipt header 1/2: the entered content will be printed on the header area. These headers are optional. Y receipt footer: ...
Page 62
Chapter 4. Web interface configuration 56 uploaded image: click on edit button to upload the picture in the popup y preview: click preview button to see the ticket with the items that are customized above. Please note: a dimension of 460x480 image is recommended..
Page 63
Chapter 4.2 users 57 3) billing plans with the billing plans configured and enabled, administrators are able to control and charge the network usage of on-demand users. Y plan: the number of the specific plan. Y type: this is the type (time, volume, or cut-off) of the plan, based on which it defines...
Page 64
Chapter 4. Web interface configuration 58 without paying additional fee. Y price: the unit price of each plan. Y enable: click the check box to activate the plan. Y function: click the edit button to add or edit the specific billing plan. 4) external payment gateway this section is for merchants to ...
Page 65
Chapter 4.2 users 59 ¾ paypal payment page configuration business account: this is the “login id” (email address) that is associated with the paypal business account. Payment gateway url: this is the default website address to post all transaction data. Identity token: this is the key used by paypal...
Page 66
Chapter 4. Web interface configuration 60 can be further enabled or disabled here, as needed. Enable/disable: choose to enable or cancel the plan. Quota: the usagetime or condition of each plan. Price: the price charged for this plan. ¾ client’s purchasing record starting invoice number: an invoice ...
Page 67
Chapter 4.2 users 61 note: in order to printout the ticket with the background picture, the web browser should configure as show below: • first: open the internet explorer and select “tools” for the drop down menu then click on “internet options” • second: inside the “internet option” menu click on ...
Page 68
Chapter 4. Web interface configuration 62 • last: printout the ticket and it will show the ticket together with the background. 6) on-demand account list all created on-demand accounts are listed and related information on is also provided. Y search: a keyword can be used to search for the matching ...
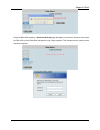
Page 69
Chapter 4.2 users 63 y delete: this will delete the account individually. 4.2.1.7 authentication database – sip the system provides sip proxy functionality, which allows sip clients to pass through nat. When enabled, all sip traffic can pass through nat via a fixed wan interface. Administrators are ...
Page 70
Chapter 4. Web interface configuration 64 4.2.2 black list the administrator can add or delete users in the black list for user access control. There are 5 sets of black lists provided by the system. A user account listed in the black list is not allowed to log into the system, the client's access w...
Page 71
Chapter 4.2 users 65 4.2.3 policy there are twelve sets of policy provided by the system and one global policy. Global is the system’s universal policy including firewall profile, specific routes profile and privilege profile. Each policy consists of firewall profile, specific route profile, schedul...
Page 72
Chapter 4. Web interface configuration 66 4.2.3.1 global policy global is the system’s universal policy including firewall rules, specific routes and privilege which will be applied to all users unless the user has been regulated and applied to another policy. ¾ select policy: select global to set t...
Page 73
Chapter 4.2 users 67 b. Firewall rules: click the number of filter rule no. To edit individual rules and click apply to save the settings. The rule status will show on the list. Check “active” box and click apply to enable that rule. This link leads to the firewall rules page. Rule no.1 has the high...
Page 74
Chapter 4. Web interface configuration 68 ¾ action for matched packets: there are two options, block and pass. Block is to prevent packets from passing and pass is to permit packets passing. B. Specific route profile: click the button of setting for specific route profile, the specific route profile...
Page 75
Chapter 4.2 users 69 ¾ select policy: select a desired individual policy for configuration. ¾ firewall profile: global policy and each policy have a firewall service list and a set of firewall profile which is composed of firewall rules. ¾ specific route profile: the default gateway of wan1, wan2, o...
Page 76
Chapter 4. Web interface configuration 70 a. Firewall profile: click the button of settingfor firewall profile, the firewall configuration will appear. Click predefined and custom service protocols to edit the protocol list. Click firewall rules to edit the rules. Please refer to global policy secti...
Page 77
Chapter 4.2 users 71 ¾ rule number: this is therule selected “1”. Rule no. 1 has the highest priority; rule no. 2 has the second priority, and so on. ¾ rule name: the rule name can be changed here. ¾ source/destination – interface/zone: there are choices of all, wan1, wan2, default, and the named se...
Page 78
Chapter 4. Web interface configuration 72 ¾ default gateway: select the default gateway as wan1, wan2 or an assigned ip address. Ip address (destination): the destination ip address of the host or the network. ¾ subnet netmask: select a destination subnet netmask of the host or the network. ¾ ip add...
Page 79
Chapter 4.2 users 73 within the same policy. ¾ individual maximum uplink: the individual maximum uplink defines the maximum bandwidth allowed for an individual client; the individual maximum uplink can not exceed the value of total uplink. ¾ individual request uplink: the individual request uplink b...
Page 80
Chapter 4. Web interface configuration 74 4.2.4 additional control in this section, additional settings are provided for the administrator to the following for user management. Y user session control: functions under this section applies for all general users. Idle timeout: define the time that the ...
Page 81
Chapter 4.2 users 75 y customization: the system supports upload customized certificate to system. Y remaining time reminder: there is a remaining time reminder supported by the system to remind users that their accounts are about to cut-off within the set time. When remaining time reminder is enabl...
Page 82: 4.3 Access Points
Chapter 4. Web interface configuration 76 4.3 access points this section provides information on the following functions: list, discovery, adding, templates, firmware and upgrade . It displays the information of the access points, such as the number of total managed ap, the number of down ap and the...
Page 83
Chapter 4.3 access points 77 4.3.1 list all of the supported managed aps (such as dwl-2100ap f/w version v2.2, v2.3) under management of the system will be shown in the list. The list is empty during first setup. The administrator can add supported aps from discovery or the adding tabs. After the ap...
Page 84
Chapter 4. Web interface configuration 78 (5) lost/unknown: after dsa-3600’s rebooting and before it tries to probe the ap and determine the exact status, the status will be displayed as lost or unknown temporarily. Enter the hyperlink of ap name: ¾ general setting: click setting to enter the genera...
Page 85
Chapter 4.3 access points 79 properties: y ssid broadcast: select this option to enable the ssid to broadcast in your network. When configuring the network, it is suggested to enable this function but disable it when the configuration is complete. With this enabled, someone could easily obtain the s...
Page 86
Chapter 4. Web interface configuration 80 y dtim interval: delivery traffic indication message. Enter a value between 1 and 255. Y preamble: select long only or short and long. A short preamble is recommended for high-traffic networks. Y transmit power: select either full, half(-3db), quarter(-6db),...
Page 87
Chapter 4.3 access points 81 y last reporting time: the time when this summary is last updated. ¾ lan interface status: the table shows the information about ip address, subnet mask and gateway. ¾ wireless lan status: the table shows all of the related wireless information. ¾ access control status: ...
Page 88
Chapter 4. Web interface configuration 82 4.3.2 discovery use this function to detect and manage all the supported aps in the network segment. Y discovery settings when the administrator tries to discover a new ap, select the ap type and select the interface (service zone) first. If the system is se...
Page 89
Chapter 4.3 access points 83 the aps. ¾ ip addresses of aps after discovery : it is the start ip address that will be assigned to the discovered aps and it must be in the same segment of the selected aln interface (service zone). ¾ scan now: click the scan now button and the aps that match the given...
Page 90
Chapter 4. Web interface configuration 84 ¾ new ip address assignment : service zone is the service zone where aps are connected to. Start ip address is the start ip address that will be assigned to the discovered aps and it must be in the same segment of the selected lan interface. ¾ admin settings...
Page 91
Chapter 4.3 access points 85 4.3.3 adding the administrator can add supported aps into the list table manually here. Enter the related information of the ap and select a template applied. Click add and then the ap will be added to the list. Similar to the ap added after discovery, a manually added a...
Page 92
Chapter 4. Web interface configuration 86 4.3.4 templates a template is a model that can be copied to every ap without having to configure the each ap individually. The administrator can configure the setting together in the template instead of logging the ap management interface to set the configur...
Page 93
Chapter 4.3 access points 87 i. Dwl-2100ap dwl-2100ap includes all standards 802.11b/g only. The connection could be select to enable 802.11b/g or disable. The dwl-2100ap is fully compatible with the ieee 802.11b and 802.11g standards. Subnet mask: the default is 255.255.255.0. All devices in the ne...
Page 94
Chapter 4. Web interface configuration 88 the server. The embedded memory can only have up to 300 logs. Properties ¾ ssid broadcast: select this option to enable the ssid to broadcast in your network. When configuring the network, it is suggested to enable this function but disable it when the confi...
Page 95
Chapter 4.3 access points 89 ii. Dwl-3200ap v2.2 dwl-3200ap version 2.2 templates settings allow users to configure general, wireless properties, access control and wireless 802.11b/g mode settings. Compatible with the 802.11b standard to provide a wireless data rate up to 11 mbps, users can migrate...
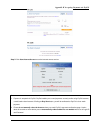
Page 96
Chapter 4. Web interface configuration 90 ¾ sntp/ntp server ip: enter the ip address of a sntp/ntp server. ¾ daylight saving time: check the box to enable daylight saving time. Snmp ¾ public community: when enabled, change the public community name here. ¾ private community: when enabled, change the...
Page 97
Chapter 4.3 access points 91 receive packets. O right antenna: ap won’t switch antenna and the radio will use the right antenna to transmit and receive packets. ¾ wmm: wmm stands for wi-fi multimedia, by enabling this feature. It will improve the user experience for audio and video applications over...
Page 98
Chapter 4. Web interface configuration 92 iii. Dwl-3200ap v2.3+ dwl-3200ap version 2.3 templates settings allow users to configure wireless 802.11b/g mode settings. Compared with dwl-3200 v2.2, dwl-3200ap 2.3+ enables users to configure snmp of general settings and adding the properties of load bala...
Page 99
Chapter 4.3 access points 93 snmp ¾ public community: when enabled, change the public community name here. ¾ private community: when enabled, change the private community name here. Syslog ¾ system activity: select “enable” to allow the logging of system actions, such as logging a firmware upgrade. ...
Page 100
Chapter 4. Web interface configuration 94 receive packets. O right antenna: ap won’t switch antenna and the radio will use the right antenna to transmit and receive packets. ¾ wmm: wmm stands for wi-fi multimedia, by enabling this feature. It will improve the user experience for audio and video appl...
Page 101
Chapter 4.3 access points 95 iv dwl-8200ap dwl-8200ap templates settings allows users to configure 802.11a and 802.11b and g mode settings. The connection could be select to enable 802.11a, 802.11b/g, or disable. Compatible with 802.11a, 802.11b and 802.11g devices that is fully compatible with the ...
Page 102
Chapter 4. Web interface configuration 96 ¾ time zone: select your time zone from the drop-down menu. ¾ sntp/ntp server ip: enter the ip address of a sntp/ntp server. ¾ daylight saving time: check the box to enable daylight saving time. Snmp ¾ public community: when enabled, change the public commun...
Page 103
Chapter 4.3 access points 97 ¾ rts length: enter a value between 256 and 2346. When wireless clients would like to send a packet which is larger than this value, it transmits an rts and waits for reply. ¾ beacon interval (ms): enter a value between 20 and 1000 msec. The default value is 100 millisec...
Page 104
Chapter 4. Web interface configuration 98 status column and enter the desired clients’ mac addresses in the mac address list. When this function is enabled, please make sure the mac address list is not empty..
Page 105
Chapter 4.3 access points 99 4.3.5 firmware this is where ap’s firmware can be uploaded. The current firmware can also be downloaded to the local storage if required. The system supports the firmware management of aps to upload new firmware, delete the existing firmware, and download the firmware to...
Page 106
Chapter 4. Web interface configuration 100 4.3.6 upgrade the administrator can upgrade the firmware of selected aps individually or at the same time by checking the check box of the aps in selection column. Note that both the version before upgrade and the next version must be ones that have been in...
Page 107: 4.4 Network
Chapter 4.4 network 101 4.4 network this section provides information on nat, privilege, monitor ip, walled garden, proxy server, ddns, client mobility and vpn. It displays the information of the interfaces. For wan1 and wan2, it will show the ip address and the connection status. For lan ports, it ...
Page 108
Chapter 4. Web interface configuration 102 4.4.1 nat there are three functions that need to be set here: dmz (demilitarized zone), public accessible server and port and redirect . Dmz (demilitarized zone) the administrator can define mandatory external to internal ip mapping using this function, so ...
Page 109
Chapter 4.4 network 103 port and ip redirect when users attempt to connect to the port of a destination ip address listed here, the connection packet will be converted and redirected to the port of the translated to destination ip address. Enter the ip address and port of destination, and the ip add...
Page 110
Chapter 4. Web interface configuration 104 4.4.2 privilege the dsa-3600 provides two privilege lists, ip address list and mac address list. The administrator can add desired ip addresses and mac addresses in these lists using the privilege list function. The ip addresses and mac addresses in these l...
Page 111
Chapter 4.4 network 105 warning: permitting specific mac addresses to have network access rights without going through standard authentication process may result in security problems..
Page 112
Chapter 4. Web interface configuration 106 4.4.3 monitor ip the dsa-3600 will send out a packet periodically to monitor the connection status of the ip addresses on the list. If the monitored ip address does not respond, the system will send an e-mail to notify the administrator that such destinatio...
Page 113
Chapter 4.4 network 107 when the monitor now button is clicked, monitor ip results page will appear. If the entered ip address is unreachable, a red dot under result field will appear. A green dot indicates that the ip address is reachable and alive..
Page 114
Chapter 4. Web interface configuration 108 4.4.4 walled garden this function allows clients of specified addresses or domain names to access the internet before login and authentication. Users without network access right in this list can make use of the actual network service free of charge. Enter ...
Page 115
Chapter 4.4 network 109 4.4.5 proxy server the system provides a build-in proxy server and external proxy server function. Under its security management, the system will match the proxy setting of external proxy servers list to the clients' proxy setting in their browsers. If no matching, the client...
Page 116
Chapter 4. Web interface configuration 110 4.4.6 ddns the system provides a convenient dynamic dns function to translate the ip address of wan port to a domain name that helps the administrator memorize and connect to wan1 port. When the ddns is enabled, the system will update the newest ip address ...
Page 117
Chapter 4.4 network 111 4.4.7 client mobility the dsa-3600 supports ip pnp function. When enabled, this function allows clients with fixed or assigned ip address to authenticate through the dsa-3600 to access the network. By enabling ip pnp, a pc with a static ip address will be able to access the n...
Page 118
Chapter 4. Web interface configuration 112 4.4.8 vpn v irtual private network (vpn) is designed to increase the security of information transferred over the internet. Vpn can work with wired or wireless networks and dial-up connections over pops. It can create a private encrypted tunnel from the end...
Page 119
Chapter 4.4 network 113 sip transparent proxy will help the sip traffic of authenticated remote vpn users when the sip service is enabled in the last service zone. Remote users can use sip when sip configuration here is enabled. Site-to-site vpn when the setting is enabled, the system will enable th...
Page 120
Chapter 4. Web interface configuration 114 click add a local site to enter the local site information page for further configuration. Click add a new host to enter the screen of remote vpn gateway..
Page 121
Chapter 4.4 network 115.
Page 122: 4.5 Status
Chapter 4. Web interface configuration 116 4.5 status this section covers the description of system status information and online user status, which include system, interface , online users, user logs, and e-mail & syslog. An overview of the system is also provided here for the administrator's refer...
Page 123
Chapter 4.5 status 117 4.5.1 system this section provides an overview of the system administration..
Page 124
Chapter 4. Web interface configuration 118 the following information in the table describes all the items found in the system setting overview menu: item description firmware version the present firmware version of dsa-3600 build the build version of firmware system name the system name. The default...
Page 125
Chapter 4.5 status 119 4.5.2 interface this section provides an overview of the all interfaces for the administrator such as wan1, wan2, service zone - default, service zone - default dhcp server. Each service zone represents a virtual system. Therefore, the information of the system’s network inter...
Page 126
Chapter 4. Web interface configuration 120 the description of the table is as follows: item description mac address the mac address of wan1 port. Ip address the ip address of the wan1 port. Wan1 subnet mask the subnet mask of the wan1 port. Mac address the mac address of wan2 port. Ip address the ip...
Page 127
Chapter 4.5 status 121 4.5.3 routing table all the policy route rules and global policy route rules will be listed here. Also it will show the system route rules specified by each interface. Y policy 1~8: shows the information of the individual policy from 1 to 8. Y global policy: shows the informat...
Page 128
Chapter 4. Web interface configuration 122 ¾ destination: the destination ip address of the device. ¾ subnet mask: the subnet mask ip address of the port. ¾ gateway: the gateway ip address of the port. ¾ interface: thechoice of interface network, including wan1, wan2, default, or the named service z...
Page 129
Chapter 4.5 status 123 4.5.4 online users each online user’s information can be obtained using this function. These include username, ip address, mac address , pkts in, bytes in, pkts out, bytes out, idle, access from and kick out. All online users will be listed here. Theadministrator can use this ...
Page 130
Chapter 4. Web interface configuration 124 4.5.5 user logs this function is used to check the history of dsa-3600. There are several types of log provided by the system. The log will be saved separately by day in the dram and the system supports up to 3 days. These logs are stored in volatile memory...
Page 131
Chapter 4.5 status 125 y on-demand user log the on-demand user log provides the login and logout activities of on-demand users such as date, system name, ip address, mac address, packets in, packets out, bytes in, bytes out, 1 st login expiration time, and account valid through. ¾ system name: the s...
Page 132
Chapter 4. Web interface configuration 126 y roaming in user log the roaming in user log provides the login and logout activities of roaming in users. ¾ type: the authentication and accounting type of the external radius server. There is a type called accept for authentication. There are three types...
Page 133
Chapter 4.5 status 127 ¾ username: username of the local user account. ¾ connection time usage: the total time used by the user. ¾ pkts in / pkts out: the total number of packets received and sent by the user. ¾ bytes in / bytes out: the total number of bytes received and sent by the user..
Page 134
Chapter 4. Web interface configuration 128 4.5.6 e-mail & syslog the system supports sending notification e-mails of monitor ip report, users log, on-demand users log, session log and ap status change up to 3 email accounts automatically. The notification of ap status change is triggered by event wh...
Page 135
Chapter 4.6 tools 129 o plain and cram-md5 are standardized authentication mechanisms while login and ntlmv1 are microsoft proprietary mechanisms. Only plain and login can use the unix login password. Netscape uses plain. Outlook and outlook express uses login as default, although they can be set to...
Page 136: 4.6 Tools
Chapter 4. Web interface configuration 130 4.6 tools this section provides information on utilities used for customizing and maintaining the system, including setup wizard , password change, backup & restore, system upgrade, restart, utilities, and quick links..
Page 137
Chapter 4.6 tools 131 4.6.1 setup wizard the administrator can configure the dsa-3600 via its web management interface as specified. In order to connect to the internet, the tcp/ip related information such as ip address, subnet mask, and gateway address, must first be obtained from the isp. The conf...
Page 138
Chapter 4. Web interface configuration 132 step 1: general change password enter the administrator’s new password in the new password field and retype it again in the verify password field. (note: the maximum length of the password is twenty-character and no space is allowed.) to secure the system, ...
Page 139
Chapter 4.6 tools 133 static ip address: set wan1 port’s static ip address enter the ip address, subnet mask and default gateway provided by the isp. Click next to continue. Pppoe: set pppoe client’s information enter theusername and password provided by the isp. Click next to continue..
Page 140
Chapter 4. Web interface configuration 134 step 3: local user account (optional) local user - add user new local accounts can be added into the local user database. Enter the username (e.G. Testuser) and password (e.G. Testuser) of the desired new account to add a new local account into the system. ...
Page 141
Chapter 4.6 tools 135 during the dsa-3600 restarting, a confirm and restart page will appear on the screen. Please do not interrupt the dsa-3600 until the dsa-3600 administrator login page reappears. This indicates that the restart process has been completed..
Page 142
Chapter 4. Web interface configuration 136 back and exit: during every step of the wizard, if you wish to go back to modify the settings, please click the back button to go back to the previous step. Click exit to leave the wizard. Please note: login to the web management interface again by using us...
Page 143
Chapter 4.6 tools 137 figure-4.6.1a: an example using tag-based service zones.
Page 144
Chapter 4. Web interface configuration 138 4.6.2 password change dsa-3600 supports three accounts with different access privileges. Choose to log in as admin, manager or operator . The default password and access privilege for each account are as follow: admin: the administrator can access all confi...
Page 145
Chapter 4.6 tools 139 4.6.3 backup & restore this function is used to backup/restore the dsa-3600 settings. The dsa-3600 can also be restored to the factory default settings using this function. Y backup system setting: click backup button to save the current system configurations to a backup file o...
Page 146
Chapter 4. Web interface configuration 140 caution: due to the limitation on database compatibility, the backup database file from a major release of previous firmware version cannot be restored to a later major release of current firmware - for example, a backup of v2.00 cannot be restored to v3.00...
Page 147
Chapter 4.6 tools 141 4.6.4 system upgrade to upgrade the system firmware, click the browse button to choose the new firmware file and then click apply to execute the process. There will be a prompt confirmation message appearing to notify the administrator to restart the system upon successful firm...
Page 148
Chapter 4. Web interface configuration 142 4.6.5 restart this function allows the administrator to safely restart the dsa-3600. The process should take about three minutes. Click yes to restart the dsa-3600; click no to go back to the previous screen. Ifturning off the power is necessary, restart th...
Page 149
Chapter 4.6 tools 143 4.6.6 utilities the utilities allows the administrators to manage functions including wake-on-lan, ping, trace route, and showing arp table by entering ip or domain name. Y wake-on-lan: it supports to boot up a power-down computer with wake-on-lan feature connected on the lan s...
Page 150
Chapter 4. Web interface configuration 144 4.6.7 quick links the quick links provide the shortcut to eight links for administrators to directly access frequently used functions of the web management interface. The eight functional links are: system status, local user management, policy management , ...
Page 151
Chapter 4.6 tools 145 link 1. System status the system status quick link provides at a glance, the system setting overview, a shortcut to 4.5.1 system in status section. It provides a summary of system information to the administrator in a single page. Please refer to the section on system for detai...
Page 152
Chapter 4. Web interface configuration 146 link 4. On-demand account management on-demand account management provides information from the on-demand account configuration, a shortcut to 4.2.1 authentication in users sections and 4.1.6 service zone Æ on-demand user. It lets the customers use wireless...
Page 153
Chapter 4.6 tools 147 link 6. Authentication configuration authentication configuration provides information from the authentication settings, a shortcut to 4.2.1 authentication in users sections and 4.1.6 service zone: authentication settings . It lets the administrator configure a list of authenti...
Page 154: 4.7 Help
Chapter 4. Web interface configuration 148 4.7 help the help button is at the upper right corner of the dsa-3600 display screen. Click help for the online help window, then click the hyperlink of the relevant information required..
Page 155
Appendix a. External network access 149 appendix a. An example of user login normally, users will be authenticated before they get network access through dsa-3600. This section presents the basic authentication flow for end users. Please make sure that the dsa-3600 is configured properly and network...
Page 156
Appendix a. An example of user login 150 note: when on-demand accounts are used (for example, we use v8ch@ondemand here), the system will display additional information and function. (1) remaining usage/expiration time: the remaining quota of this on-demand account that the user can surf the interne...
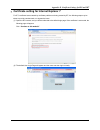
Page 157
Appendix b. Console interface configuration 151 appendix b. Console interface configuration upon completing this process, the console interface configuration will be accessible via the console port to handle problems and situations occurring during operation. 1. To connect to the console port of the...
Page 158
Appendix b. Console interface configuration 152 (1) utilities for network debugging the console interface provides several utilities to assist the administrator to check the system conditions and perform debugging. The utilities are described as following: ping host (ip): by sending icmp echo reques...
Page 159
Appendix b. Console interface configuration 153 (2) change admin password the username and the default password is “admin” by default, which is similar to the web management interface. The administrator’s password can be changed. If the password cannot be remembered and the management interface cann...
Page 160: Using Internet Proxy Server
Appendix c. Proxy configuration 154 appendix c. Proxy configuration basically, a proxy server can help clients access the network resources more quickly. This section presents basic examples for configuring the proxy server settings of the dsa-3600. Using internet proxy server the first scenario is ...
Page 161
Appendix c. Proxy configuration 155 follow the following steps to complete the proxy configuration: step 1. Log into the dsa-3600 by using the admin account. Step 2. Network Æ proxy server Æ external proxy servers page. Add the ip address (leaving it blank means any ip address) and port number of th...
Page 162
Appendix c. Proxy configuration 156 setting..
Page 163: Using Extranet Proxy Server
Appendix c. Proxy configuration 157 using extranet proxy server the second scenario is that a proxy server is placed in the extranet (such as dmz), which all users from the intranet or the internet are able to access. For example, the following diagram shows that a proxy server of an organization in...
Page 164
Appendix d. Certificate settings for ie6 and ie7 158 follow the following steps to complete the proxy configuration: step 1. Log in the dsa-3600 by using the admin account. Step 2. Network Æ proxy server Æ external proxy servers page. Add the ip address and port number of the proxy server into exter...
Page 165: Background Information
Appendix d. Certificate settings for ie6 and ie7 159 appendix d. Certificate settings for ie6 and ie7 certificate setting for the company with certificate authority ¾ background information any website or high-value web applications will require a client to access their websites via secure sockets l...
Page 166
Appendix d. Certificate settings for ie6 and ie7 160 certificate setting for internet explorer 7 for ie7, certificate issues caused by certificate publisher not being trusted by ie7, the following steps may be taken to provide a workaround or to bypass the issue. (1) open the ie7 browser, and you wi...
Page 167
Appendix d. Certificate settings for ie6 and ie7 161 for installing a trusted certificate to solve the ie7 certificate issue, please follow the instructions stated below. (1) when the user login page appears, click “certificate error” at the top. (2) click “view certificate”. (3) click “certificatio...
Page 168
Appendix d. Certificate settings for ie6 and ie7 162 (4) select root certification, then click “view certificate”. (5) click “install certificate”..
Page 169
Appendix d. Certificate settings for ie6 and ie7 163 (6) click “next”. (7) select “automatically select the certificate store based on the type of certificate”, then click “next”. (8) click “finish”..
Page 170
Appendix d. Certificate settings for ie6 and ie7 164 (9) click “yes”. (10) click “ok”. (11) launch a new ie7 browser. The certificate is now trusted via ie7 according to the key symbol shown at top next to the address field..
Page 171
Appendix d. Certificate settings for ie6 and ie7 165 certificate setting for internet explorer 6 for issues relating to ie6 certificate error, the following information provides the step to take when the certificate publisher is not trusted by ie6. (1) open an ie6 browser, the security alert message...
Page 172
Appendix e. Service zones − deployment examples 166 appendix e. Service zones – deployment examples typical application scenario: employees vs. Guests typical service zone settings will separate users groups into employee and guests for the purpose of different authentication level. ¾ application ...
Page 173
Appendix e. Service zones − deployment examples 167 ¾ requirements for the application scenario : 1. Regardless of the location in the office, all users should be divided into two groups (employee and guest ) for the purpose of authentication differences. 2. Each service zone must setup its own ssid...
Page 174
Appendix e. Service zones − deployment examples 168 step 3: configure the “service zone“ accordingly ¾ configure the ssid ¾ choose the authentication option and configure the login page ¾ choose the appropriate policy for this “service zone“.
Page 175
Appendix e. Service zones – deployment examples 169 finished configuration – service zone settings: once the settings of two service zones are completed, the configured result will be displayed on screen in the service zone settings . The name of the service zone and the enabled status should appear...
Page 176
Appendix f. Deploying dsa-3600 using dwl-2100ap 170 appendix f. Deploying dsa-3600 using dwl-2100ap wireless features of dwl-2100ap wireless security can be addressed using the dwl-2100ap access point with wpa (wi-fi protected access) and 802.1x authentication to provide a higher level of security...
Page 177
Appendix f. Deploying dsa-3600 using dwl-2100ap 171 ¾ single set of wep keys: all ssids which belong to the same dwl-2100ap share the same set of wep keys (key1 ~ key4): caution: if two or more ssids belong to the same dwl-2100ap and the wireless security of the associated service zones is set in th...
Page 178
Appendix f. Deploying dsa-3600 using dwl-2100ap 172 ¾ availability of 802.1x authentication : when an ssid (primary type) of the dwl-2100ap is set in the mode of “open system“, “shared key”, or “open system or shared key“, it will not support 802.1x authentication. Caution: 802.1x authentication sho...
Page 179
Appendix g. Network configuration on pc 173 appendix g. Network configuration on pc after the dsa-3600 is installed, the following configurations must be set up on the pc: internet connection setup and tcp/ip network setup. Internet connection setup if the internet connection of this client pc has b...
Page 180
Appendix g. Network configuration on pc 174 3. Click next when welcome to the new connection wizard screen appears. 4. Choose “connect to the internet” and then click next. 5. Choose “set up my connection manually” and then click next..
Page 181
Appendix g. Network configuration on pc 175 6. Choose “connect using a broadband connection that is always on” and then click next . 7. Finally, click finish to exit the connection wizard . Now, you have completed the setup. Tcp/ip network setup in the default configuration, the dsa-3600 will assign...
Page 182
Appendix g. Network configuration on pc 176 ¾ check the tcp/ip setup of window xp 1. Select start Æ control panel Æ network connection . 2. Click the right button of the mouse on the “local area connection” icon and select “properties” 3. Select “general” label and choose “internet protocol (tcp/ip)...
Page 183
Appendix g. Network configuration on pc 177 4. Using dhcp: to use dhcp, choose “obtain an ip address automatically” and click ok. This is the default setting of windows. Reboot the pc to make sure an ip address is obtained from the dsa-3600. 5. Using specific ip address: to use specific ip address, ...
Page 184: Appendix H. Local Vpn
Appendix h. Ipsec vpn 178 appendix h. Local vpn the dsa-3600 is equipped with ipsec vpn feature starting from release v1.00. To utilize ipsec vpn supported by microsoft windows xp sp2 (with patch) and windows 2000 operating systems, the dsa-3600 implements ipsec vpn tunneling technology between clie...
Page 185
Appendix h. Ipsec vpn 179 during the first login to the dsa-3600, internet explorer will ask user to download the activex component of ipsec vpn. This activex component once downloaded will be running parallel with the “login success” page. The activex component helps to setup the ipsec vpn tunnel b...
Page 186
Appendix h. Ipsec vpn 180 3. Internet connection firewall in windows xp and windows xp sp1, the internet connection firewall is not compatible with ipsec. Internet connection firewall will drop packets from tunneling of ipsec vpn. Suggestion: please turn off internet connection firewall feature or u...
Page 187
Appendix h. Ipsec vpn 181 5. The termination of activex the activex component for ipsec vpn is running parallel with the “login success” web page. Unless user decides to close the session and to disconnect with dsa-3600, the following conditions or behaviors of user’s browser can be avoided in order...
Page 188
Appendix h. Ipsec vpn 182 c. There are some cases of windows messages by which dsa-3600 will hint current user to: (1) close the windows internet explorer, (2) click “logout” button on “login success” page, (3) click “back” or “refresh” of the same internet explorer, (4) enter new url in the same in...
Page 189
Appendix h. Ipsec vpn 183 7. Faq a. How to clean ipsec client? Ans: open a command prompt window and type the commands as follows. C:\> cd %windir%\system32 c:\> clean_ipsec.Bat or c:\> cd %windir%\system32 c:\> ipsec2k.Exe stop b. How to remove activex component in client’s computer? Ans: (1) unins...
Page 190: Appendix I. Dhcp Relay
Appendix k. Accepting payment via paypal 184 appendix i. Dhcp relay the dsa-3600 supports dhcp relay defined according to rfc 3046. For scaling reasons, it is advantageous to set up an external dhcp server apart from using the internal dhcp server implemented in the dsa-3600 for assigning ip. When c...
Page 191
Appendix i. Dhcp relay 185 here is an example of configuration file of the dhcp server: based on the above example, the client that connects to the dsa-3600 sends out a dhcp request. The dhcp relay function being enabled in the dsa-3600 sends a circuit id 00:90:0b:07:60:91_192.168.1.254 to the exter...
Page 192
Appendix j. Session limit and session log 186 appendix j. Session limit and session log session limit to prevent ill-behaved clients or malicious software from using up system’s connection resources, administrators will have to restrict the number of concurrent sessions that a user can establish. ¾ ...
Page 193
Appendix j. Session limit and session log 187 ¾ the following table shows an example of the session log data. Jul 20 12:35:05 2007 [new]user1@local tcp mac=00:09:6b:cd:83:8c sip=10.1.1.37 sport=1626 dip=203.125.164.132 dport=80 jul 20 12:35:05 2007 [new]user1@local tcp mac=00:09:6b:cd:83:8c sip=10.1...
Page 194
Appendix j. Session limit and session log 188 appendix k. Accepting payments via paypal this section is to show independent hotspot owners how to configure related settings in order to accept payments via paypal, making the hotspot an e-commerce environment for end users to pay for and obtain intern...
Page 195
Appendix k. Accepting payments via paypal 189 1. Setting up as follows are the basic steps to open and configure a “business account” on paypal. 1.1 open an account step 1: sign up for a paypal business account and login. Here is a link: https://www.Paypal.Com/cgi-bin/webscr?Cmd=_registration-run st...
Page 196
Appendix k. Accepting payments via paypal 190 settings screenshots auto return (on) return url (redirect webpage) type http://www.Www.Com or other url. Payment data transfer (on) block non-encrypted website payment (off) paypal account optional (off) contact telephone number (off) click save..
Page 197
Appendix k. Accepting payments via paypal 191 1.2 configure dsa-3600 with a paypal business account please log in dsa-3600: users Æ authentication Æ click the option on-demand user Æ external payment gateway Æclick configure Æ external payment gateway Æ select paypal.
Page 198
Appendix k. Accepting payments via paypal 192 three fields are required: setting description business account id this is the “login id” (email address) that is associated with the paypal business account. Payment gateway url https://www.Paypal.Com/cgi-bin/webscr (default url for paypal) identity tok...
Page 199
Appendix k. Accepting payments via paypal 193 2. Basic maintenance in order to maintain the operation, the merchant owner will have to manage the accounts and payment transactions on paypal website as well as dsa-3600. 2.1 refund a completed payment and remove the on-demand account generated on dsa-...
Page 200
Appendix k. Accepting payments via paypal 194 note: as stated by paypal, you can issue a full or partial refund for any reason and for 60 days after the original payment was sent. To find the on-demand account name for a specific payment, click details of the payment listing in the activity history ...
Page 201
Appendix k. Accepting payments via paypal 195 3. Reporting during normal operation, the following steps will be necessary to generate transaction reports. 3.1 transaction activity during a period please log in paypal Æ click history Æ choose activity type from the show field as the search criteria Æ...
Page 202
Appendix k. Accepting payments via paypal 196 4. An example of making payments via paypal step 1: click the link below the login window to pay for the service via paypal. Step 2: choose i agree to accept the terms of use and click next. Step 3: please fill out the form andclick buy now to send out t...
Page 203
Appendix k. Accepting payments via paypal 197 step 4: you will be redirected to paypal website to complete the payment process..
Page 204
Appendix k. Accepting payments via paypal 198 step 5: click start internet access to use the internet access service. Note: 1. Payment is accepted via paypal. Paypal enables you to send payments securely online using paypal account, a credit card or bank account. Clicking on buy now button, you will...