- DL manuals
- D-Link
- Extender
- DUA-2000
- User Manual
D-Link DUA-2000 User Manual
Summary of DUA-2000
Page 1
Policy manager user manual dua-2000 ver. 1.0 business wireless solution building networks for people.
Page 2
D-link dua-2000 policy manager user manual ii information in this document is subject to change without notice. © 2016 d-link corporation. All rights reserved. Reproduction in any manner whatsoever without the written permission of d-link corporation is strictly forbidden. Trademarks used in this te...
Page 3: Table Of Contents
D-link dua-2000 policy manager user manual iii table of contents table of contents ................................................................................................................................................................. Iii 1. Introduction ......................................
Page 4
D-link dua-2000 policy manager user manual iv radius ...................................................................................................................................................................... 28 9. Policy & object .............................................................
Page 5
D-link dua-2000 policy manager user manual v backup system ........................................................................................................................................................ 78 restore system .........................................................................
Page 6: Introduction
D-link dua-2000 policy manager user manual 1 1. Introduction the manual is organized by the menu layout on the policy manager. Audience this reference manual is intended for network administrators and other it networking professionals responsible for managing the policy manager using the web user in...
Page 7: Notes, Notices, and Cautions
D-link dua-2000 policy manager user manual 2 notes, notices, and cautions below are examples of the three types of indicators used in this manual. When administering the policy manager using the information in this document, you should pay special attention to these indicators. Each example below pr...
Page 8: Product Introduction
D-link dua-2000 policy manager user manual 3 2. Product introduction the trend of bring your own device (byod) is a new challenge for network administrators and managers. Many companies that allow employees to use their own devices expect to see improvements in performance and productivity, however ...
Page 9: Hardware Installation
D-link dua-2000 policy manager user manual 4 3. Hardware installation this chapter provides unpacking and installation information for the dua-2000 policy manager. Step 1: unpacking open the shipping carton and carefully unpack its contents. Please consult the list below to make sure all items are p...
Page 10: Configuring The Network
D-link dua-2000 policy manager user manual 5 connecting to the device there are several methods of connecting to the policy manager, including the web user interface (web ui), snmp and command-line access (telnet / ssh / console). Here we will document the most common method of access, the web user ...
Page 11
D-link dua-2000 policy manager user manual 6 figure 4-1 – device dashboard changing the default ip address the default ip address of the policy manager will need to be changed to match your network topology. It is recommended that this is completed before the device is connected to the production ne...
Page 12: System Overview
D-link dua-2000 policy manager user manual 7 4. System overview the policy manager works by authenticating clients and devices using either a username and password combination or a mac address. Depending on the policy type, users will either be authenticated using their username and password (if the...
Page 13
D-link dua-2000 policy manager user manual 8 figure 5-1 – logical system overview.
Page 14: Network Requirements
D-link dua-2000 policy manager user manual 9 5. Network configuration example the d-link dua-2000 policy manager is a highly integrated solution which requires access to multiple services, such as wireless controllers, unified access points (aps) and layer 2 and 3 switches. This high level of integr...
Page 15: Network Topology
D-link dua-2000 policy manager user manual 10 network topology this is an example of how the network can be configured to support wireless client access control using a captive portal and an external radius server. The network topology is as follows: figure 6-1 – example network topology the vlans c...
Page 16: Network Configuration
D-link dua-2000 policy manager user manual 11 network configuration use the following steps to configure the wireless controller and network devices for use with the policy manager captive portal. Wireless controller these steps can be used to configure the wireless controller for use with the capti...
Page 17: Network Environment
D-link dua-2000 policy manager user manual 12 network environment a dynamic host configuration protocol (dhcp) server and multiple vlans are required for captive portal. A guest vlan for unauthenticated guests is required, along with an employee vlan for authenticated corporate clients and a persona...
Page 18: Status & Monitor
D-link dua-2000 policy manager user manual 13 6. Status & monitor dashboard dashboard this provides a system overview of the cpu status, ram status, network status, hard drive status, association status and number of active users. It is the default page that is displayed when logging-in to the polic...
Page 19: Network
D-link dua-2000 policy manager user manual 14 network interface utilization the displays the network interface utilization of the 4 ports on the policy manager. The ports are listed from port 1 to 4 and refresh automatically. To get to the following page, browse to: status & monitor >> network >> in...
Page 20: Logs
D-link dua-2000 policy manager user manual 15 figure 7-3 – device status the following fields are available: field description system name the hostname of the policy manager. System time the system date and time, in the format: hh:mm:ss mm/dd/yyyy. System location the location of the policy manager....
Page 21
D-link dua-2000 policy manager user manual 16 figure 7-4 – logs the following search fields are available: field description type choose the log type to search. Date the beginning and end date of the log selection. Table 7-3 – search logs click get log to display logs of the chosen type. The followi...
Page 22: Network
D-link dua-2000 policy manager user manual 17 7. Network device ip interface ip interface this page is used to set the ip address settings of the dua-2000. There is one default entry of ‘system’, which is used to manage the device. Edit this or create a new interface to connect the dua-2000 to multi...
Page 23
D-link dua-2000 policy manager user manual 18 click add to add an ip interface. Click edit to edit existing interface settings. Click delete to delete an interface. Click save to save the changes made. Click cancel to revert the settings to their previous state. Add ip interface click the add or edi...
Page 24
D-link dua-2000 policy manager user manual 19 metric the metric for the interface in the routing table on the dua-2000. This decides the preference of the interface for outgoing traffic. Default is 0. The range is: 0 - 999. Dns assign dns servers for the interface. Port trunk configure the ports as ...
Page 25: Radius Client
D-link dua-2000 policy manager user manual 20 layer 3 and 4, ip address and tcp/udp port number. Table 8-3 – port trunk advance setting click save to save the changes made. Click cancel to revert the settings to their previous state. Radius client this page is used to enter the radius client informa...
Page 26
D-link dua-2000 policy manager user manual 21 click cancel to revert the settings to their previous state. Add radius server client click the add or edit buttons to view the following window: figure 8-5 – add radius server client the following fields can be configured: field description name name th...
Page 27: Identity Domain
D-link dua-2000 policy manager user manual 22 identity domain identity domain this is used to set the authentication sources for wireless clients. It is based on the external servers configured on the external server page. To get to the following page, browse to: network >> identity domain >> identi...
Page 28
D-link dua-2000 policy manager user manual 23 description the description of the identity domain. Table 8-7 – identity domain 2 click edit to edit existing identity domain. Click delete to delete an identity domain. Please note that the local identity domain cannot be deleted. Click save to save the...
Page 29: External Server
D-link dua-2000 policy manager user manual 24 external server ldap lightweight directory authentication protocol (ldap) is used for authenticating users and devices over an ip network. To get to the following page, browse to: network >> external server >> ldap : figure 8-8 – ldap server setting the ...
Page 30
D-link dua-2000 policy manager user manual 25 secondary ip address the ip address of the secondary ldap server. Port the port to connect to on the ldap server. Default is 389. The range is: 1 – 65535. Ldap base dn the ldap search base for the container that contains the users or devices to be authen...
Page 31
D-link dua-2000 policy manager user manual 26 figure 8-9 – ad server setting the following fields are available: field description server check click this button to test the ad server configuration. Server group name create a server group name. This is referenced by the identity / domain and is used...
Page 32: Pop3
D-link dua-2000 policy manager user manual 27 ad server and authenticate the client. Ssl enabled click to enable or disable ssl for ad authentication. The options are enabled or disabled . Third ip address the ip address of the third ad server. Port the port to connect to on the ad server. Default i...
Page 33: Radius
D-link dua-2000 policy manager user manual 28 server check click this button to test the pop3 server configuration. Server group name create a server group name. This is referenced by the identity / domain and is used to group the pop3 servers defined on this page. Up to 3 server groups can be defin...
Page 34
D-link dua-2000 policy manager user manual 29 figure 8-11 – radius server (client) the following fields are available: field description server check click this button to test the radius server configuration. Server group name create a server group name. This is referenced by the identity / domain a...
Page 35
D-link dua-2000 policy manager user manual 30 third ip address the ip address of the third radius server. Authentication port the tcp port to use for radius authentication. Range: 1 - 65535. The default is: 1812. Accounting port the tcp port to use for radius accounting. Range: 1 - 65535. The defaul...
Page 36: Policy & Object
D-link dua-2000 policy manager user manual 31 8. Policy & object policy rule rule the policy rule links all of the different configuration elements that are used to authenticate a user or device. It is based on the user group, device type, location profile and schedule profile and references the aut...
Page 37
D-link dua-2000 policy manager user manual 32 the following fields are available: field description rule name the name of the policy rule. Authentication database the database to use for authentication. This is defined on the identity domain page. Each database can only be selected once, apart from ...
Page 38
D-link dua-2000 policy manager user manual 33 field description rule name the name of the policy rule. Authentication database the database to use for authentication. This is defined on the identity domain page. Each database can only be selected once, apart from the default local server (sql) datab...
Page 39: Client
D-link dua-2000 policy manager user manual 34 client user database group the user database is a way of managing users and the devices associated with them. If the mac binding feature is enabled, then both the user and device are authenticated. If the mac binding feature is disabled, then only the us...
Page 40
D-link dua-2000 policy manager user manual 35 table 9-4 – group click add to add a user group. Click edit to edit existing user group settings. Click delete to delete a user group. Add user group click the add or edit buttons to view the following window: figure 9-4 – add user group the following fi...
Page 41
D-link dua-2000 policy manager user manual 36 account the account links the username, password, binding device list and group. The binding device list is the devices that a user is permitted to log in from. The group is associated with the policy rule and provides the list of users and devices that ...
Page 42
D-link dua-2000 policy manager user manual 37 click add to add a user group. Click edit to edit existing user group settings. Click detail to get an overview of the user account. Click delete to delete a user group. Add new account click the add or edit buttons to view the following window: figure 9...
Page 43: Device Database
D-link dua-2000 policy manager user manual 38 click apply to apply the settings . Device database property group the device database is a way of managing devices on the system. Devices are assigned to users through the binding device list on the account page. A property group is used to manage devic...
Page 44
D-link dua-2000 policy manager user manual 39 click edit to edit existing property group settings. Click delete to delete a property group. Add property group click the add or edit buttons to view the following window: figure 9-8 – add property group the following fields can be configured: field des...
Page 45
D-link dua-2000 policy manager user manual 40 to get to the following page, browse to: policy & object >> client >> device database and click on the device tab: figure 9-9 – device the following fields are available: field description property group the property group to search for devices. The can ...
Page 46
D-link dua-2000 policy manager user manual 41 click add to add a device. Click import to import a device csv file. Click export to export a device csv file. Click edit to edit existing device settings. Click delete to delete a device. Add device click the add or edit buttons to view the following wi...
Page 47: Endpoint
D-link dua-2000 policy manager user manual 42 endpoint location profile location profile a location profile is a way of grouping endpoints for form a location. A location is a group of switch ports that are used to define where a client can authenticate from. An endpoint can have one port assigned t...
Page 48
D-link dua-2000 policy manager user manual 43 figure 9-12 – add location profile the following fields can be configured: field description profile name the name of the location profile. Description the description of the location profile. Table 9-15 – add location profile click apply to apply the se...
Page 49
D-link dua-2000 policy manager user manual 44 figure 9-13 – endpoint list the following fields are available: field description manual add endpoint add an endpoint to the endpoint list manually. Table 9-16 – endpoint list 1 click add to manually add an endpoint. The following fields are available: f...
Page 50
D-link dua-2000 policy manager user manual 45 the following fields are available: field description endpoint name the name of the endpoint. This can be a switch or wireless ap. Mac address the mac address of the endpoint, in the format: xx:xx:xx:xx:xx:xx. This is the mac address of the switch or wir...
Page 51
D-link dua-2000 policy manager user manual 46 field description endpoint name the name of the endpoint. This can be a switch or wireless ap. Mac address the mac address of the endpoint, in the format: xx:xx:xx:xx:xx:xx. This is the mac address of the switch or wireless ap. Port list the ports on the...
Page 52: Authorization
D-link dua-2000 policy manager user manual 47 field description location profile the location profile to associate the endpoint with. This is taken from the location profile page. Table 9-21 – endpoint to location profile 1 click create new location profile to be taken to the location profile page. ...
Page 53
D-link dua-2000 policy manager user manual 48 figure 9-16 – authorization profile the following fields are available: field description profile name the name of the authorization profile. Vlan id the vlan id or number that the authorization profile applies to. Ingress bandwidth the ingress or downlo...
Page 54
D-link dua-2000 policy manager user manual 49 figure 9-17 – add authorization profile the following fields can be configured: field description profile name the name of the authorization profile. Vlan id the vlan id or number that the authorization profile applies to. Range: 1 - 4094. Ingress bandwi...
Page 55
D-link dua-2000 policy manager user manual 50 to get to the following page, browse to: policy & object >> authorization >> authorization profile and click on the acl profile tab: figure 9-18 – acl profile the following fields are available: field description acl profile name the name of the acl prof...
Page 56
D-link dua-2000 policy manager user manual 51 figure 9-19 – add acl profile the following fields can be configured: field description profile name the name of the acl profile. Acl rule this is an acl rule created on the acl rule page. The rules are numbered from 1 to 10, with 1 being matched first a...
Page 57
D-link dua-2000 policy manager user manual 52 figure 9-20 – acl rule the following fields are available: field description rule name the name of the acl rule. Destination mac the destination mac address that the rule matches. Destination ip the destination ip address that the rule matches. Tcp port ...
Page 58
D-link dua-2000 policy manager user manual 53 figure 9-21 – add acl rule the following fields can be configured: field description rule name the name of the acl rule. Network layer the network layer that the rule applies to. Select l2 (layer 2) or l3 (layer 3). Destination mac the destination mac ad...
Page 59: Schedule
D-link dua-2000 policy manager user manual 54 schedule schedule profile a schedule profile is applied to the policy rule and is a way of defining when a policy rule is active. If a policy rule is not active then it is not available to authenticate clients and client users and devices are denied acce...
Page 60
D-link dua-2000 policy manager user manual 55 click delete to delete a schedule profile. Add schedule profile click the add or edit buttons to view the following window: figure 9-23 – add schedule profile the following fields can be configured: field description name the name of the schedule profile...
Page 61
D-link dua-2000 policy manager user manual 56 table 9-30 – add schedule profile click apply to apply the settings ..
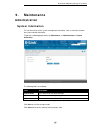
Page 62: Maintenance
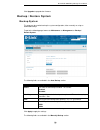
D-link dua-2000 policy manager user manual 57 9. Maintenance administration system information this can be used to set the system management information, such as hostname, location and system contact information. To get to the following page, browse to: maintenance >> administration >> system inform...
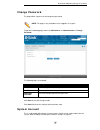
Page 63: Change Password
D-link dua-2000 policy manager user manual 58 change password this page allows a guest user to change their password. Note: this page is only available to users logged-in as a guest. To get to the following page, browse to: maintenance >> administration >> change password : figure 10-2 – change pass...
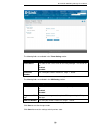
Page 64
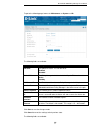
D-link dua-2000 policy manager user manual 59 to get to the following page, browse to: maintenance >> administration >> system account : figure 10-3 – system account the following fields are available: field description account this is the username of the system account. This is local to the policy ...
Page 65: Date And Time
D-link dua-2000 policy manager user manual 60 figure 10-4 – add system account the following fields can be configured: field description account this is the username of the system account. This is local to the policy manager only and is not integrated with any external authentication sources. Permis...
Page 66
D-link dua-2000 policy manager user manual 61 figure 10-5 – date and time the following fields are available: field description current device time the current system time, in the format: hh:mm:ss mm/dd/yyyy. Time zone the system time zone. Sntp the simple network time protocol (sntp) status. This c...
Page 67: Session
D-link dua-2000 policy manager user manual 62 disabled . Do not follow dst. Table 10-5 – date and time click save to save the changes made. Click cancel to revert the settings to their previous state. Session view the session information, showing all accounts logged-in to the system. To get to the f...
Page 68: Management
D-link dua-2000 policy manager user manual 63 management snmp snmp v3 user simple network management protocol (snmp) v3 is a protocol for administering devices on an ip network. Management applications can be used to set and view system properties on devices which support snmp. To get to the followi...
Page 69
D-link dua-2000 policy manager user manual 64 encryption the encryption algorithm used to ensure privacy of the snmp data. It can be set to: des aes table 10-7 – snmp v3 user click edit to edit existing snmp user settings. Click save to save the changes made. Click cancel to revert the settings to t...
Page 70
D-link dua-2000 policy manager user manual 65 md5 sha password the password of the user, if no-auth or auth no-priv have been selected in the security level. Privacy algorithm the encryption algorithm used to ensure privacy of the snmp data. It can be set to: des aes table 10-8 – edit snmp v3 user c...
Page 71
D-link dua-2000 policy manager user manual 66 used if a link changes state and can be set to: enabled disabled coldstart traps this is used to enable or disable snmp coldstart traps. These are used if the system was powered-off before being powered-on and can be set to: enabled disabled warmstart tr...
Page 72
D-link dua-2000 policy manager user manual 67 port the tcp port to use for snmp traps. Community the community string to use for snmp traps. Snmp version the snmp protocol version to use for snmp traps. Table 10-10 – snmp host list click add to add a snmp host. Click save to save the changes made. C...
Page 73
D-link dua-2000 policy manager user manual 68 v3 table 10-11 – add snmp host click apply to apply the settings . Access control list this is a way to control which devices on the network have snmp access to the policy manager. To get to the following page, browse to: maintenance >> management >> snm...
Page 74
D-link dua-2000 policy manager user manual 69 click the add or edit buttons to view the following window: figure 10-13 – add access control list the following fields can be configured: field description ip address the ip address of the network host. Mask the netmask of the network host. Table 10-13 ...
Page 75
D-link dua-2000 policy manager user manual 70 figure 10-14 – snmp community the following fields are available: field description community name the snmp community string. This is used to authenticate client devices connecting to the policy manager using snmp. Access right the access rights of the c...
Page 76: Telnet / Ssh
D-link dua-2000 policy manager user manual 71 figure 10-15 – add snmp community the following fields can be configured: field description community name the snmp community string. This is used to authenticate client devices connecting to the policy manager using snmp. Access right the access rights ...
Page 77
D-link dua-2000 policy manager user manual 72 figure 10-16 – telnet / ssh the following fields are available in the telnet setting section: field description telnet status the status of the telnet server on the policy manager. This can be set to: enabled disabled telnet port number the telnet port n...
Page 78: Web Server Configuration
D-link dua-2000 policy manager user manual 73 web server configuration this is used to enable or disable https on the policy manager web ui. It allows a self- signed certificated to be generated, or for a signed certificate to be imported. This allows connections to the policy manager web ui to be e...
Page 79: Ddp
D-link dua-2000 policy manager user manual 74 ddp d-link discovery protocol (ddp) is a protocol for automatic discovery of ip devices. It can be used to identify network devices to each other and manage the network using software such as d-link network assistant (dna). To get to the following page, ...
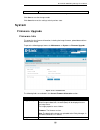
Page 80: System
D-link dua-2000 policy manager user manual 75 disabled table 10-20 – ddp per port setting click save to save the changes made. Click cancel to revert the settings to their previous state. System firmware upgrade firmware info this page lists the firmware information, including the image firmware, up...
Page 81
D-link dua-2000 policy manager user manual 76 default image to boot from, the word (boot) will be displayed next to the image name. The image properties are as follows: firmware : the firmware version. Date : the date that the image was uploaded to the policy manager, in hh:mm:ss mm/dd/yyyy format. ...
Page 82
D-link dua-2000 policy manager user manual 77 can be the name of the image file or a path to the image file on the tftp server. Upgrade to the image to upgrade. This can be set to: image1 image2 table 10-22 – firmware upgrade from tftp click upgrade to upgrade the firmware. The following fields are ...
Page 83: Backup / Restore System
D-link dua-2000 policy manager user manual 78 click upgrade to upgrade the firmware. Backup / restore system backup system this page can be used to back up the system configuration, either manually or using an automated backup. To get to the following page, browse to: maintenance >> management >> ba...
Page 84
D-link dua-2000 policy manager user manual 79 field description folder name the folder on the usb device to save the backup file to. Table 10-27 – manually backup click save to usb port 1 to save the configuration to usb port 1 . Click disconnect usb port 1 to un-mount the usb device in usb port 1. ...
Page 85: Reboot
D-link dua-2000 policy manager user manual 80 field description usb device status the usb device status of usb port 2. This can be: connected disconnected select folder the folder on the usb drive where the backup files are located. Table 10-29 – restore from usb port 2 click restore to restore the ...
Page 86
D-link dua-2000 policy manager user manual 81 to get to the following page, browse to: maintenance >> system >> ha : figure 10-24 – ha the following fields are available: field description ha state the global ha status. This can be set to: enabled disabled default role the policy manager’s default r...
Page 87: Logs
D-link dua-2000 policy manager user manual 82 field description current ha status the current ha status. Current device status the current device status in the ha pair. Table 10-31 – ha click to activate to make the current policy manager the active server in the ha pair. Click stop to stop the ha s...
Page 88: System Logs
D-link dua-2000 policy manager user manual 83 syslog server. Severity . The severity of the logging sent to the syslog server. Syslog server 2 the status of syslog server 2. This can be set to: disabled . Disable syslog logging. Enabled . Enable syslog logging. The following fields are available: fq...
Page 89: Alert
D-link dua-2000 policy manager user manual 84 the following fields are available: field description port link up/down enable or disable port link up/down logs. This can be set to: enabled disabled port trunk enable or disable port trunk logs. This can be set to: enabled disabled user authentication ...
Page 90
D-link dua-2000 policy manager user manual 85 figure 10-27 – email alert the following fields are available: field description e-mail subject the subject of the email that will be sent from the policy manager. E-mail status the status of the email alert. This can be set to: disabled . Disable system...
Page 91
D-link dua-2000 policy manager user manual 86 alert type this page is used to configure the alert type to be included in the email alerts. To get to the following page, browse to: maintenance >> logs >> alert and click on the alert type tab: figure 10-28 – alert type the following fields are availab...
Page 92: Utilities
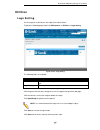
D-link dua-2000 policy manager user manual 87 utilities logo setting use this page to set the banner at the top of the web interface. To get to the following page, browse to: maintenance >> utilities >> logo setting : figure 10-29 – logo setting the following fields are available: field description ...
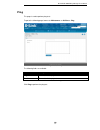
Page 93: Ping
D-link dua-2000 policy manager user manual 88 ping this page is used to perform ping tests. To get to the following page, browse to: maintenance >> utilities>> ping : figure 10-30 – ping the following fields are available: field description ping address the ip address to ping. Result the results of ...
Page 94: 10.
D-link dua-2000 policy manager user manual 89 10. Appendix a - technical specifications capacity • new session/second: o 100 • user database: o 10,000 hardware specification processor and system memory • processor and system memory o processor mips based 1000mhz 64-bit multi-core processor o flash e...
Page 95: 11.
D-link dua-2000 policy manager user manual 90 11. Appendix b – rack mount instructions the following or similar rack-mount instructions are included with the installation instructions: a) elevated operating ambient - if installed in a closed or multi-unit rack assembly, the operating ambient tempera...