- DL manuals
- F-SECURE
- Other
- INTERNET GATEKEEPER FOR LINUX 4.01 -
- Administrator's Manual
F-SECURE INTERNET GATEKEEPER FOR LINUX 4.01 - Administrator's Manual
Summary of INTERNET GATEKEEPER FOR LINUX 4.01 -
Page 1
F-secure internet gatekeeper for linux ― a comprehensive internet and anti-virus solution ― version 4 Rev. 20100125 administrator’s guide.
Page 2
F-secure internet gatekeeper for linux/administrator’s guide 2 about this guide this guide describes the installation and uninstallation, usage, and settings for f-secure internet gatekeeper for linux. Please note that “f-secure internet gatekeeper for linux” is also referred to as “the product” and...
Page 3
F-secure internet gatekeeper for linux/administrator’s guide 3 contents 1. Introduction .............................................................................................. 6 2. Features .................................................................................................. 8 2....
Page 4
F-secure internet gatekeeper for linux/administrator’s guide 4 7.1 web console settings .............................................................................................................. 28 7.1.1 proxy settings ................................................................................
Page 5
F-secure internet gatekeeper for linux/administrator’s guide 5 10.3.3 changing the ip address ....................................................................................... 121 10.3.4 changing ip addresses with iptables .................................................................... 12...
Page 6
F-secure internet gatekeeper for linux/administrator’s guide 6 1. Introduction f-secure internet gatekeeper for linux is an internet gatekeeper solution designed to protect corporate networks, internet service provider networks, and home networks against malware. Computer viruses are one of the most...
Page 7
F-secure internet gatekeeper for linux/administrator’s guide 7 internet mail server pc pc pc pc mail server web server f-secure internet gatekeeper.
Page 8
F-secure internet gatekeeper for linux/administrator’s guide 8 2. Features 2.1 overview f-secure internet gatekeeper for linux: • protects a range of different networks against viruses: - internal company networks - isp networks - home networks • uses a single computer to monitor the network access ...
Page 9
F-secure internet gatekeeper for linux/administrator’s guide 9 simple installation • runs in almost all linux environments • combines all functions in a single computer • can be installed as an rpm or deb package. The rpm package complies with linux standard base, which is used in red hat linux and ...
Page 10
F-secure internet gatekeeper for linux/administrator’s guide 10 anti-virus • uses the award-winning and proven f-secure engine • can handle practically all existing viruses • can handle viruses for windows, dos, microsoft office, vbs, linux, and other environments • combined use of multiple engines ...
Page 11
F-secure internet gatekeeper for linux/administrator’s guide 11 3. System requirements f-secure internet gatekeeper for linux has the following system requirements. 3.1 hardware requirements minimum hardware requirements cpu intel pentium compatible cpu memory 512 mb ram or more disk 5 gb or more fr...
Page 12
F-secure internet gatekeeper for linux/administrator’s guide 12 3.2 software requirements required components • linux kernel 2.4/2.6 • glibc 2.3.2 or later • perl 5.8 or later supported distributions 32-bit: • asianux server 3 • asianux 2.0 (miracle linux 4.0) • asianux 1.0 (miracle linux 3.0) • cen...
Page 13
F-secure internet gatekeeper for linux/administrator’s guide 13 4. Installing f-secure internet gatekeeper for linux use either the rpm package, deb package or tar.Gz package to install f-secure internet gatekeeper for linux. ■ use the rpm package for installation if possible. ■ you can install upda...
Page 14
F-secure internet gatekeeper for linux/administrator’s guide 14 4.2 installing a deb package this section explains how to install f-secure internet gatekeeper for linux on a server, which runs one of the debian or ubuntu based linux distributions. In a debian or ubuntu distribution, you can easily i...
Page 15
F-secure internet gatekeeper for linux/administrator’s guide 15 4.3 installing a tar.Gz package if you cannot use the rpm or deb package to install f-secure internet gatekeeper for linux, you can install it by using a tar.Gz package. Execute the following command with root privileges: # tar -zxvf fs...
Page 16
F-secure internet gatekeeper for linux/administrator’s guide 16 command examples to install the whole product, use this command: # make install to install multiple copies of the software, use this command: # make prefix=/opt/f-secure/fsigk2 suffix=2 adminport=10012 install 4.5 uninstalling f-secure ...
Page 17
F-secure internet gatekeeper for linux/administrator’s guide 17 5. Typical configurations once the installation has completed, locate the appropriate internet gatekeeper server and modify the settings as required. The next step is to configure client computers. 5.1 configuration overview the followi...
Page 18
F-secure internet gatekeeper for linux/administrator’s guide 18 5.1.2 smtp connection • without virus scanning the e-mail client sends e-mail to mail servers on the internet through an smtp server for outbound e-mail. • with virus scanning when virus scanning is used, internet gatekeeper stands betw...
Page 19
F-secure internet gatekeeper for linux/administrator’s guide 19 5.1.3 pop connection • without virus scanning to retrieve e-mail, the e-mail client connects to the mail server directly by using the pop protocol. • with virus scanning when virus scanning is used, internet gatekeeper stands between th...
Page 20
F-secure internet gatekeeper for linux/administrator’s guide 20 5.1.4 ftp connection • without virus scanning to send and receive files, the ftp client connects to an ftp server directly by using the ftp protocol. • with virus scanning when virus scanning is used, internet gatekeeper stands between ...
Page 21
F-secure internet gatekeeper for linux/administrator’s guide 21 5.2 network configuration examples f-secure internet gatekeeper for linux operates as a proxy server, which is located between the client and the web and mail servers. The scenarios described here assume that internet gatekeeper is inst...
Page 22
F-secure internet gatekeeper for linux/administrator’s guide 22 5.3 internet gatekeeper server settings to use f-secure internet gatekeeper for linux for virus scanning, configure the internet gatekeeper server in which the product is installed as follows. Always specify the following settings: ■ se...
Page 23
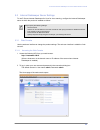
F-secure internet gatekeeper for linux/administrator’s guide 23 if you cannot connect to the web console, view the error log (/opt/f-secure/fsigk/log/admin/error.Log) from the command line. 5.3.1.2 web console layout the web console consists of a menu on the left of the screen and a work area on the...
Page 24
F-secure internet gatekeeper for linux/administrator’s guide 24 5.3.2 typical settings in a typical product setup, the following settings are specified in the web console. Proxy settings after editing the settings, click the save and restart button. The enabled services are started and the changed s...
Page 25
F-secure internet gatekeeper for linux/administrator’s guide 25 5.4 client settings to use f-secure internet gatekeeper for linux for virus scanning, you need to change the proxy server setting in your web browser and the mail server setting in your e-mail client. Web browser settings proxy server h...
Page 26
F-secure internet gatekeeper for linux/administrator’s guide 26 6. Checking the proxy setup after configuring the settings, follow the steps below to confirm that the software is working correctly. If the software is not working correctly, use one of the following methods to view the error log. ■ fr...
Page 27
F-secure internet gatekeeper for linux/administrator’s guide 27 6.3 checking the pop proxy do the following and confirm that the virus is detected: 1 start your web browser and download the test virus (eicar) from the following location: http://www.Eicar.Org/anti_virus_test_file.Htm clear the proxy ...
Page 28
F-secure internet gatekeeper for linux/administrator’s guide 28 7. Advanced settings 7.1 web console settings you can use the web console to change the settings as required. The settings are described below. For information on the web console, see “ web console ”, 20. 7.1.1 proxy settings the name i...
Page 29
F-secure internet gatekeeper for linux/administrator’s guide 29 iptables on your system. Parent server parent server (self_proxy / parent_server_host / parent_server_port) all connections are forwarded to the specified server. If you use more than one level of proxies, specify the parent proxy. If t...
Page 30
F-secure internet gatekeeper for linux/administrator’s guide 30 following file is updated: /opt/f-secure/fsigk/conf/template_http.Html. Http proxy authentication proxy authentication (proxyauth_pam_auth) authenticates the proxy by using pams (pluggable authentication modules). You can change the aut...
Page 31
F-secure internet gatekeeper for linux/administrator’s guide 31 user-agent: (pass_user_agent, pass_user_agent_list) skips virus scanning for connections from clients with the specified user-agent. Usually, all data is saved and transmitted to the client only after the virus scanning is completed. If...
Page 32
F-secure internet gatekeeper for linux/administrator’s guide 32 skips virus scanning for file data beyond the specified size. Usually, all data is saved and transmitted to the client only after the virus scanning has completed. This setting specifies that the data beyond the specified length in a fi...
Page 33
F-secure internet gatekeeper for linux/administrator’s guide 33 enables riskware scanning. This detects riskware as well as known viruses. For more information about riskware, see “ riskware ”, 119. Skip these targets skip scanning for riskware: (pass_riskware) excludes the specified riskware from d...
Page 34
F-secure internet gatekeeper for linux/administrator’s guide 34 • use the iptables command from the command line to specify the setting as follows. (the example shows the port number being set to 9800.) # iptables -t nat -a prerouting -i eth1 -p tcp --dport 80 ¥ -j redirect --to-port 9080 for more i...
Page 35
F-secure internet gatekeeper for linux/administrator’s guide 35 7.1.1.2 smtp proxy smtp proxy smtp proxy (smtp_service) click the on and off buttons to start or stop the smtp proxy service. Proxy port proxy port (svcport) specifies the port number used by the proxy service. The standard port number ...
Page 36
F-secure internet gatekeeper for linux/administrator’s guide 36 the standard port number is 25. This setting is ignored in transparent mode. What to do when a virus is detected action on viruses (action) pass pass (action=pass) allows e-mail to pass even if a virus is detected. In this case, the det...
Page 37
F-secure internet gatekeeper for linux/administrator’s guide 37 quarantine quarantine(keep) (quarantine) quarantines viruses. The viruses are quarantined in the directory that you can set in quarantine directory under “common settings”. The viruses are stored in mailbox format. Specify this setting ...
Page 38
F-secure internet gatekeeper for linux/administrator’s guide 38 notify the administrator by e-mail notify admin (spam_notify_admin) sends a notification to the administrator by e-mail. Specify the e-mail address, mail server, and detection message in settings to notify the administrator under “commo...
Page 39
F-secure internet gatekeeper for linux/administrator’s guide 39 authenticated through the pop proxy are permitted to use the smtp proxy for a fixed time period. If you use smtp authentication simultaneously on the internet gatekeeper and mail server, e-mail can be sent if either smtp authentication ...
Page 40
F-secure internet gatekeeper for linux/administrator’s guide 40 554 infected by [virus name] delete delete (action=blackhole) deletes infected e-mails. Does not send a detection message. Delete and notify recipients delete and send to receiver (action=delete) deletes the virus and sends a virus dete...
Page 41
F-secure internet gatekeeper for linux/administrator’s guide 41 ■ if you edit the detection message setting by using the web console, the following file is updated: /opt/f-secure/fsigk/conf/template_smtp_lan.Txt. Maximum number of simultaneous connections maximum connections (pre_spawn) specifies th...
Page 42
F-secure internet gatekeeper for linux/administrator’s guide 42 the detection name is "fsigk/policy_block_activex". When activex content is detected, it is handled in the same way as viruses. For more information, see the what to do when a virus is detected setting. If you disabe virus scanning, act...
Page 43
F-secure internet gatekeeper for linux/administrator’s guide 43 separate each name with a comma (",") by using backward matching (a file is skipped if the trailing characters of the file name match the specified file name or extension). The setting is not case sensitive. The setting does not apply t...
Page 44
F-secure internet gatekeeper for linux/administrator’s guide 44 transparent proxy transparent proxy mode (transparent) enables transparent proxy mode. A nat redirection setting is required when the proxy operates as a transparent proxy. Use one of the following methods to specify the nat redirection...
Page 45
F-secure internet gatekeeper for linux/administrator’s guide 45 7.1.1.3 pop proxy pop proxy pop proxy (pop_service) click the on and off buttons to start or stop the pop proxy service. Proxy port proxy port (svcport) specifies the port number that the proxy service uses. The standard port number is ...
Page 46
F-secure internet gatekeeper for linux/administrator’s guide 46 delete (action={pass,delete}) deletes viruses. The e-mail that contains the virus is replaced with the information specified in the virus detection message. The detection event is recorded in the log, a notification is sent to the admin...
Page 47
F-secure internet gatekeeper for linux/administrator’s guide 47 allows the spam to pass. "x-spam-status:" is added to the header of e-mail that is classified as spam. You can use the sorting function on the client to classify e-mail in which the value of "x-spam-status:" starts with "yes" as spam. T...
Page 48
F-secure internet gatekeeper for linux/administrator’s guide 48 maximum number of simultaneous connections maximum connections (pre_spawn) specifies the maximum number of simultaneous connections from clients. The specified number of processes listen for connections from clients. You can check the n...
Page 49
F-secure internet gatekeeper for linux/administrator’s guide 49 when activex content is detected, it is handled in the same way as viruses. For more information, see the what to do when a virus is detected setting. If you disable virus scanning, activex content scanning is also disabled. Scripts scr...
Page 50
F-secure internet gatekeeper for linux/administrator’s guide 50 separate each name with a comma (",") by using backward matching (a file is skipped if the trailing characters of the file name match the specified file name or extension). The setting is not case sensitive. The setting does not apply t...
Page 51
F-secure internet gatekeeper for linux/administrator’s guide 51 • use the " edit nat (iptables) redirect settings". To do this, click edit nat (iptables) redirect settings . • use the iptables command from the command line to specify the setting as follows. (the example shows the port number being s...
Page 52
F-secure internet gatekeeper for linux/administrator’s guide 52 7.1.1.4 ftp proxy ftp proxy ftp proxy (ftp_service) click the on and off buttons to start or stop the ftp proxy service. Proxy port proxy port (svcport) specifies the port number which the proxy service uses. The standard port number is...
Page 53
F-secure internet gatekeeper for linux/administrator’s guide 53 quarantine quarantine(keep) (quarantine) quarantines viruses. The viruses are quarantined in the directory that you can set in quarantine directory under “common settings”. Specify this setting only if sufficient disk space is available...
Page 54
F-secure internet gatekeeper for linux/administrator’s guide 54 to: (acl_to) only accepts connections to the designated list of hosts. For examples, see “ access control ”, 65. If you edit the to these hosts setting by using the web console, the ftp to field is updated in /opt/f-secure/fsigk/conf/ho...
Page 55
F-secure internet gatekeeper for linux/administrator’s guide 55 if scanning takes a long time, this setting terminates scanning after the specified time. Note, however, that if you set a shorter scanning time, it limits the extent to which archived and other large files can be scanned. Riskware scan...
Page 56
F-secure internet gatekeeper for linux/administrator’s guide 56 7.1.1.5 common settings common settings common settings admin notification settings admin notification settings e-mail address e-mail address (admin_mailaddr) specifies the administrator’s e-mail address. If you have enabled the notify ...
Page 57
F-secure internet gatekeeper for linux/administrator’s guide 57 spam filtering method spam detection method specifies the spam filtering method. The line "x-spam-status: yes() with []" is added to the e-mail header if the mail is classified as spam. If an e-mail matches multiple conditions, scanning...
Page 58
F-secure internet gatekeeper for linux/administrator’s guide 58 • always always treat as spam or not spam. Search string scanning searches for the specified character string in the part specified by the field name. You can specify multiple character strings to scan for, separated by commas (","). Yo...
Page 59
F-secure internet gatekeeper for linux/administrator’s guide 59 in the text body, this checks whether the character string matches the leading characters of each line. Prefix search cannot be used for the html body. Backward search compare whether the trailing characters of the specified field match...
Page 60
F-secure internet gatekeeper for linux/administrator’s guide 60 • database updating proxy settings is also used for the spam detection engine proxy. • the spam detection engine connects to the following server: o host: ct-cache%d.F-secure.Com (%d can be digit from 1 to 9) o port: tcp/80 o protocol: ...
Page 61
F-secure internet gatekeeper for linux/administrator’s guide 61 rbl server name : name of the rbl server in which the address was found rbl reply address : reply address from the rbl server when spam is detected surbl querying is performed by looking up the name in the dns. The dns server to query i...
Page 62
F-secure internet gatekeeper for linux/administrator’s guide 62 7.1.2 virus definition database virus definition update virus definition update manual update manual update updates virus definition files to the latest version. Updating may take some time as the virus definition databases are download...
Page 63
F-secure internet gatekeeper for linux/administrator’s guide 63 if the virus definition databases fail to download, check if the files can be downloaded from the following url: http://fsbwserver.F-secure.Com/ in addition, check the log file (/opt/f-secure/fsigk/log/dbupdate.Log, /opt/f-secure/fsigk/...
Page 64
F-secure internet gatekeeper for linux/administrator’s guide 64 7.1.4 top menu admin password admin password changes the password that you need to log into the web console. If you edit the “admin password” setting by using the web console, the following file is updated: /opt/f-secure/fsigk/conf/fsig...
Page 65
F-secure internet gatekeeper for linux/administrator’s guide 65 7.2 access control you can use the proxy and other settings to control access based on the host and network. Specify the settings as described below. Access control uses tcpwrapper. For more information about tcpwrapper, run "man 5 host...
Page 66
F-secure internet gatekeeper for linux/administrator’s guide 66 what to do if a line contains more than 2047 bytes the access control setting file (/opt/f-secure/fsigk/conf/hosts.Allow) permits a maximum of 2047 bytes per line. Use the following methods if you want to specify lines longer than 2047 ...
Page 67
F-secure internet gatekeeper for linux/administrator’s guide 67 7.3 detection notification templates you can specify a header in the top line of the detection notification template. When sending a notification e-mail to the sender or administrator from the smtp service, you can specify "from: name@d...
Page 68
F-secure internet gatekeeper for linux/administrator’s guide 68 access time in text format (example: 'tue may 7 16:16:17 2002') ${header} content of the header ${text} content of the text message ${mailfrom} smtp sender address (the address passed to the "mail from:" command) ${rcptto} smtp recipien...
Page 69
F-secure internet gatekeeper for linux/administrator’s guide 69 7.4 expert options reference information for expert options usually, you do not need to specify any other settings than those available through the web console and described in this manual. However, a number of expert options are availa...
Page 70
F-secure internet gatekeeper for linux/administrator’s guide 70 8. Command-line tools you do not need to use command-line operations daily. Please refer to this chapter if command-line operations are required. The proxy function of internet gatekeeper is automatically started when changes are made t...
Page 71
F-secure internet gatekeeper for linux/administrator’s guide 71 8.2 proxy execution overview of operations: executes a proxy according to the set options or with a configuration file. Usually, you need to specify /opt/f-secure/fsigk/conf/fsigk.Ini as the configuration file. Command names: cd /opt/f-...
Page 72
F-secure internet gatekeeper for linux/administrator’s guide 72 8.3 virus definition updates overview of operations: updates virus definition files. Updating may take some time because virus definition files are downloaded from the internet. You can specify proxy settings in conf/dbupdate.Conf. Upda...
Page 74
F-secure internet gatekeeper for linux/administrator’s guide 74 command examples: restart all services that are enabled. # cd /opt/f-secure/fsigk; make restart 8.5 creating diagnostic information overview of operations: creates a diagnostic information file (diag.Tar.Gz) in the /opt/f-secure/fsigk d...
Page 75
F-secure internet gatekeeper for linux/administrator’s guide 75 9. Logs f-secure internet gatekeeper for linux records access status, virus detection status, and error occurrences to log files. The log files are saved in /opt/f-secure/fsigk/log/ and a directory is created for each service. 9.1 log f...
Page 76
F-secure internet gatekeeper for linux/administrator’s guide 76 when pop is used, the url is “pop://pop user name@pop server name:port number”. When smtp is used, the url is “mail:destination”. • user name displays the user name when proxy authentication is used. “-“ is recorded if authentication is...
Page 77
F-secure internet gatekeeper for linux/administrator’s guide 77 generated) detection time the time (milliseconds) spent on virus checks executed in one connection (the time applies to the time elapsed since the last time an access log was generated) detection details displays the detection details w...
Page 78
F-secure internet gatekeeper for linux/administrator’s guide 78 ” ( 151) appears. Smtp ・ server/error reply(mail): buf=[xxx] error response when the "mail from" command to the smtp server is sent ・ server/error reply(rcpt): buf=[xxx] error response when the " rcpt to " command to the smtp server is ...
Page 79
F-secure internet gatekeeper for linux/administrator’s guide 79 9.1.3 error logs logs are recorded when an error occurs. Refer to the error logs if the program is not working properly. Error logs are formatted in the following manner. The format and text of the messages may change in the future if n...
Page 80
F-secure internet gatekeeper for linux/administrator’s guide 80 message ###error### maximum connections: warning: client connections reached maximum connections(maximum connections). More request will be blocked/rejected. If there is many warnings, please increase 'maximum connections' settings(pre_...
Page 81
F-secure internet gatekeeper for linux/administrator’s guide 81 -http 200 -smtp 50 -pop 50 -ftp 10 if you increase the maximum number of connections, more connections are allowed, but it requires more memory. Approximately 500 kb of memory is used for each connection. Message ###error### notify_admi...
Page 82
F-secure internet gatekeeper for linux/administrator’s guide 82 message ###error### semget failure. Childnum(pre_spawn=[maximum connections]) may be large. If needed, maximum semaphore number(semmni) can increase by adding like 'kernel.Sem=250 128000 32 512' on '/etc/sysctl.Conf' and running 'sysctl...
Page 83
F-secure internet gatekeeper for linux/administrator’s guide 83 message ###error### get_response_header: too large header description is displayed when a http response header is too large (over 10 kb). The service is working without any problems. Solution check if the problem occurs for a specific u...
Page 84
F-secure internet gatekeeper for linux/administrator’s guide 84 message ###error### smtp_data_cmd_itr:auth buf=[response line] /strerror(xxx)=xxx description is displayed when a response code during smtp authentication with the smtp server returns an irregular code (besides 334, 5xx, 235). The [resp...
Page 85
F-secure internet gatekeeper for linux/administrator’s guide 85 1. Add the following line to sysctl.Conf (the maximum number of file handles is changed to 65535): fs.File-max = 65535 2. Run the following command to apply the changes: sysctl -p message ###error### xxx cannot open [/var/tmp/fsigk/prox...
Page 86
F-secure internet gatekeeper for linux/administrator’s guide 86 message ###error### vsd_start() error description virus definition files or the scanning engine library could not be loaded. Solution if virus definition files or files used by scanning engines are deleted, overwrite the installation wi...
Page 87
F-secure internet gatekeeper for linux/administrator’s guide 87 message ###error### main/accept_loop/accept(s=x):/strerror(104)=connection reset by peer description this message can appear if you use kernel 2.2 and if you disconnect immediately after the connection is established. The product can wo...
Page 88
F-secure internet gatekeeper for linux/administrator’s guide 88 message ###error### csdkmain_classifymessage failed: type=3, code=200, desc=can't resolve host ct-cache1.F-secure.Com description the problem is in resolving the address of servers for the spam detection engine (ct-cache%d.F-secure.Com,...
Page 89
F-secure internet gatekeeper for linux/administrator’s guide 89 message (other messages) description an unusual error may have occurred. Solution please send the error log files and diagnostic information to f-secure for inspection. 9.1.4 information logs the information log (info.Log) records any o...
Page 90
F-secure internet gatekeeper for linux/administrator’s guide 90 message main: accept_loop(sock=socket number,pid=process number). Starting to accept connection on each proxy process. Description a message which indicates the start of a proxy process. The message is displayed when a service is starte...
Page 91
F-secure internet gatekeeper for linux/administrator’s guide 91 message is_server_alivesocket: select(s=aaa):ret=bbb,cur_pid=ccc: server closed connection while transaction. There may be timeout on the server because of no traffic. (elasped=tttms) description is displayed when a server closes a conn...
Page 92
F-secure internet gatekeeper for linux/administrator’s guide 92 message from: %s:%d(%s) to: %s:%d(%s) message-id: %s infected: %d virusname: %s description using the smtp service, a mail that contains “from: client address: from client port (sender address)”, “to: server address: to server port (rec...
Page 93
F-secure internet gatekeeper for linux/administrator’s guide 93 message error reply(data) url=[%s] buf=[%s] error reply(dataend): url=[%s] buf=[%s] error reply(mail): buf=[%s] error reply(rcpt): buf=[%s] error reply(auth): buf=[%s] error reply(quit): buf=[%s] error reply(noop): buf=[null], error=......
Page 94
F-secure internet gatekeeper for linux/administrator’s guide 94 9.2 splitting/rotating log files log files are saved as a single file by default and not split into multiple files. To split log files, use the logrotate command. To set up a split rotation for log files by using the sample configuratio...
Page 95
F-secure internet gatekeeper for linux/administrator’s guide 95 9.3 time display conversion tool most logs display the time in seconds elapsed from epoch time. With the logconv tool, the date fields of year, month, date, hour, minute, and second can be added to the beginning of the date line in a lo...
Page 96
F-secure internet gatekeeper for linux/administrator’s guide 96 9.4 log analysis tools the access logs used by the product are compatible with squid format. This makes it possible to use various log analysis tools, such as webalizer. You can perform the daily access analysis with webalizer by runnin...
Page 97
F-secure internet gatekeeper for linux/administrator’s guide 97 9.5 external output of logs logs are saved as files by default. However, they can be output to other formats such as syslog. Use pipes in the external command to redirect the output. To set the external output, specify the configuration...
Page 98
F-secure internet gatekeeper for linux/administrator’s guide 98 10. Other settings this chapter describes additional settings, which you can configure for the product. For most users, the settings described in “ typical configurations ” (15) provide enough security. However, some users may require a...
Page 99
F-secure internet gatekeeper for linux/administrator’s guide 99 proxy access control you can configure access control by using the access control options. To apply restrictions which are based on host names, you must first enable “dns reverse lookup”. For more information, see “ access control ”, 65...
Page 100
F-secure internet gatekeeper for linux/administrator’s guide 100 10.1.2 authentication using virtual networks to set up authentication by using a virtual network, you must first set up a tcp/ip communication path between the client and internet gatekeeper by using a virtual network (ssh/vpn, etc.), ...
Page 101
F-secure internet gatekeeper for linux/administrator’s guide 101 settings 1 install an ssh server to the same server (or a computer on the network) as f-secure linux internet gatekeeper. For certain linux distributions (such as red hat 7 and later versions), openssh is installed by default. 2 instal...
Page 102
F-secure internet gatekeeper for linux/administrator’s guide 102 10.1.3 proxy authentication using internet gatekeeper internet m ail server web server access prohibited access granted user a internet gatekeeper user b f-secure internet gatekeeper for linux can authenticate each user with a password...
Page 103
F-secure internet gatekeeper for linux/administrator’s guide 103 to prevent the files from being overwritten during updates, remove the symbolic links and create copies before editing the configuration files. Proxy settings proxy settings http proxy http proxy authentication: on add or remove users:...
Page 104
F-secure internet gatekeeper for linux/administrator’s guide 104 10.1.4 authentication by mail servers internet mail server access prohibited access granted user a user b anti-virus gateway f-secure internet gatekeeper uses pop and smtp authentication on the server side. The product works as a proxy...
Page 105
F-secure internet gatekeeper for linux/administrator’s guide 105 10.1.5 authentication using pop-before-smtp internet mail server smtp access prohibited smtp access granted pop authentication successful pop authenticati on fails user a user b anti-virus gateway smtp services can be accessed using po...
Page 106
F-secure internet gatekeeper for linux/administrator’s guide 106 because e-mails from the internet are delivered to mail servers through the product, the corresponding mail servers must be allowed to deliver without authentication. The following describes how you can configure this: proxy settings s...
Page 107
F-secure internet gatekeeper for linux/administrator’s guide 107 10.2 transparent proxy f-secure internet gatekeeper for linux can work as a transparent proxy for each service (http, ftp, smtp, pop). In this way, you can perform virus scans for services without having to change settings for each use...
Page 108
F-secure internet gatekeeper for linux/administrator’s guide 108 10.2.1 transparent proxy details normally, clients access web servers and mail servers directly. To use f-secure internet gatekeeper for linux as a transparent proxy, you must install it on the ip routing between clients and servers. T...
Page 109
F-secure internet gatekeeper for linux/administrator’s guide 109 10.2.2 transparent proxy – router mode to function as a transparent proxy in router mode, you must install internet gatekeeper on a computer, which acts as a router between the clients and the servers. This diagram below illustrates ho...
Page 110
F-secure internet gatekeeper for linux/administrator’s guide 110 overview of operations: the following describes how clients connect to servers when f-secure internet gatekeeper for linux is set up as a transparent proxy: 1 the client starts a connection to a service port (example 110) of a server (...
Page 111
F-secure internet gatekeeper for linux/administrator’s guide 111 2 change the access destination of the client to fsigk:9110 by changing iptables on internet gatekeeper. • configuring the web console: from the web console, select “http”, “smtp”, “pop”, or “ftp” from the “proxy settings” menu. Select...
Page 112
F-secure internet gatekeeper for linux/administrator’s guide 112 3 change the default route of the nat (lower-level) router to fsigk to let all data communication pass through fsigk. If the router is running linux, run the following commands: nat-router# route del -net default nat-router# route add ...
Page 113
F-secure internet gatekeeper for linux/administrator’s guide 113 10.2.3 transparent proxy – bridge mode f-secure internet gatekeeper for linux can also operate as a bridge while acting as a transparent proxy. If you configure the product in bridge mode, virus scanning functions can be provided to cl...
Page 114
F-secure internet gatekeeper for linux/administrator’s guide 114 overview of operations: the following describes how clients connect to servers when f-secure internet gatekeeper for linux is set up as a transparent proxy: 1 the client starts a connection to a service port (example 110) of a server (...
Page 115
F-secure internet gatekeeper for linux/administrator’s guide 115 • required software: [os] linux2.4.21 (or later) (the linux kernel archives: http://www.Kernel.Org/ ) [ebtables + br-netfilter (kernel patch)] ebtables-brnf_vs_2.4.21.Diff.Gz (or later) (ebtables: http://ebtables.Sourceforge.Net/ ) • k...
Page 116
F-secure internet gatekeeper for linux/administrator’s guide 116 5 check that virus scans can be performed when a client accesses a server. When a service accesses a server from internet gatekeeper, the ip address of the product is normally assigned as the ip address of the service source. For this ...
Page 117
F-secure internet gatekeeper for linux/administrator’s guide 117 10.3 coexisting with mail servers f-secure internet gatekeeper for linux can operate in the same computer as the mail server. If the product is implemented in the same computer as a mail server, you must change the ip address or the no...
Page 118
F-secure internet gatekeeper for linux/administrator’s guide 118 10.3.2 changing the port number of the mail server internet gatekeeper server fsigk(smtp) smtp pop m ail box 9025 25 9110 fsigk(pop) lan internet 110 if you specify a different port number for the mail server, it is possible to use the...
Page 120
F-secure internet gatekeeper for linux/administrator’s guide 120 as outbound access is denied by restricting recipient domains, allow access from clients within the lan. The following example enables ip addresses specified in 192.168.1.Xxx and 192.168.2.Xxx. Proxy settings smtp proxy lan access sett...
Page 121
F-secure internet gatekeeper for linux/administrator’s guide 121 10.3.3 changing the ip address internet gatekeeper service fsigk(smtp) smtp pop mail box 192.168.1.1:25 192.168.2.1:25 192.168.1.1:110 fsigk(pop) 192.168.2.1:110 lan (192.168. 2.Xxx) eth0(192.168.1.1) eth1(192.168.2.1) internet if f-se...
Page 122
F-secure internet gatekeeper for linux/administrator’s guide 122 • using ipop3d + xinetd: 1 make the following change in /etc/xinetd.D/ipop3. Bind=192.168.1.1 2 restart xinetd. # /etc/rc.D/init.D/xinetd restart • using qmail+tcpserver: make the following changes in /var/qmail/rc. /usr/local/bin/tcps...
Page 123
F-secure internet gatekeeper for linux/administrator’s guide 123 client settings set the mail server to 192.168.2.1. Make sure that the client can send and receive mails. 10.3.4 changing ip addresses with iptables eth0 f-secure internet gatekeeper server (192.168.1.1, 192.168.2.1) fsigk(smtp) smtp s...
Page 124
F-secure internet gatekeeper for linux/administrator’s guide 124 iptables setting for the gateway server follow these instructions to redirect the access to ports 25 and 110 of eth1 (192.168.2.1) to 9025 and 9110. • iptables – commands: # iptables -t nat -a prerouting -d 192.168.2.1 -p tcp --dport 2...
Page 125
F-secure internet gatekeeper for linux/administrator’s guide 125 10.4 scanning viruses before saving mail to the mail server by default, virus scans are performed on all inbound e-mails that are sent to the mail server by using the specified pop protocol. For this reason, you do not need to make any...
Page 126
F-secure internet gatekeeper for linux/administrator’s guide 126 settings 1 set up f-secure internet gatekeeper for linux under a temporary host name (virus-gw) and apply the following proxy settings: proxy settings smtp proxy: on proxy port: 25 global settings parent server: host name: port number:...
Page 127
F-secure internet gatekeeper for linux/administrator’s guide 127 • using postfix: ① add the following line to /etc/postfix/main.Cf: mynetworks= address of virus-gw (example: 192.168.0.99)>, within lan (example: 192.168.1.0/24.)> ② restart postfix. # postfix reload 3 check that e-mails can be sent fr...
Page 128
F-secure internet gatekeeper for linux/administrator’s guide 128 10.5 reverse proxy settings f-secure internet gatekeeper for linux can be set up as a reverse proxy to scan connections from a client to a specific web server. It is also possible to implement the product as a transparent proxy, which ...
Page 129
F-secure internet gatekeeper for linux/administrator’s guide 129 10.5.2 coexisting with web servers f-secure internet gatekeeper for linux can operate in the same computer as a web server. By specifying a different port number for the web server, it is possible to use the product and a web server in...
Page 130
F-secure internet gatekeeper for linux/administrator’s guide 130 10.5.3 implementing a https (ssl) server f-secure internet gatekeeper for linux cannot scan https (ssl) data because they are encrypted. To scan a connection from a specific http (ssl) server, decrypt the data with a ssl proxy or ssl a...
Page 131
F-secure internet gatekeeper for linux/administrator’s guide 131 internet gatekeeper settings at the web console, configure the proxy port to 9080 and the parent server port to 80. Proxy settings http proxy: on proxy port: 9080 parent server: host name: localhost port number: 80 web server settings ...
Page 132
F-secure internet gatekeeper for linux/administrator’s guide 132 11. Product specifications 11.1 product specifications the following describes the specifications for f-secure internet gatekeeper for linux. Web console - supported languages english/japanese web console - authentication timeout 300 s...
Page 133
F-secure internet gatekeeper for linux/administrator’s guide 133 scanned pop commands that can be used user/pass/apop/uidl/top/stat/list/retr/dele/noop/rset/qui t/ auth, and other similar response commands * apop cannot be used if “defining parent server by user” is enabled and the product is runnin...
Page 134
F-secure internet gatekeeper for linux/administrator’s guide 134 11.2 http proxy process this section describes how common protocols are processed with the http proxy. Proxy mode, get method client internet gatekeeper (0.0.0.1) http server (httpserver,0.0.0.2) tcp connect(to: 0.0.0.1:9080) ---------...
Page 135
F-secure internet gatekeeper for linux/administrator’s guide 135 transparent proxy mode (router or bridge), get method client internet gatekeeper (0.0.0.1) http server (httpserver,0.0.0.2) tcp connect(to: 0.0.0.2:80) -----------------------------> get /index.Html http/1.0... ------------------------...
Page 136
F-secure internet gatekeeper for linux/administrator’s guide 136 11.3 smtp proxy process this section describes how common protocols are processed with the smtp proxy. Proxy mode client internet gatekeeper (fsigk, 0.0.0.1) smtp server (smtpserver, 0.0.0.2) tcp connect(to: 0.0.0.1:9025) -------------...
Page 137
F-secure internet gatekeeper for linux/administrator’s guide 137 transparent proxy mode (router or bridge) client internet gatekeeper (fsigk, 0.0.0.1) smtp server (smtpserver, 0.0.0.2) tcp connect(to: 0.0.0.2:25) -----------------------------> tcp connect(to: 0.0.0.2:25) ----------------------------...
Page 138
F-secure internet gatekeeper for linux/administrator’s guide 138 11.4 pop proxy process this section describes how common protocols are processed with the pop proxy. Proxy mode client internet gatekeeper (fsigk,0.0.0.1) pop server (popserver, 0.0.0.2) tcp connect(to: 0.0.0.1:9110) ------------------...
Page 139
F-secure internet gatekeeper for linux/administrator’s guide 139 transparent mode (router or bridge) client internet gatekeeper (fsigk,0.0.0.1) pop server (popserver, 0.0.0.2) tcp connect(to: 0.0.0.2:110) -----------------------------> tcp connect(to: 0.0.0.2:110) -----------------------------> +ok ...
Page 140
F-secure internet gatekeeper for linux/administrator’s guide 140 11.5 ftp proxy process the ftp service relays both the control session and data session. This section describes how common protocols are processed with the ftp proxy. Proxy mode, passive ftp client internet gatekeeper (fsigk, 0.0.0.1) ...
Page 141
F-secure internet gatekeeper for linux/administrator’s guide 141 221 goodbye. Proxy mode, active ftp client (0.0.0.3) internet gatekeeper (fsigk,0.0.0.1) ftp server (ftpserver, 0.0.0.2) tcp connect(to: 0.0.0.1:9021) -----------------------------> 220 fsigk at fsigk user user@ftpserver --------------...
Page 142
F-secure internet gatekeeper for linux/administrator’s guide 142 transparent mode (router or bridge), passive ftp client internet gatekeeper (0.0.0.1) ftp server (ftpserver, 0.0.0.2) tcp connect(to: 0.0.0.2:21) -----------------------------> tcp connect(to: 0.0.0.2:21) ----------------------------->...
Page 143
F-secure internet gatekeeper for linux/administrator’s guide 143 transparent mode (router or bridge), active ftp client (0.0.0.3) internet gatekeeper (fsigk,0.0.0.1) ftp server (ftpserver, 0.0.0.2) tcp connect(to: 0.0.0.2:21) -----------------------------> tcp connect(to: 0.0.0.2:21) ---------------...
Page 144
F-secure internet gatekeeper for linux/administrator’s guide 144 11.6 http error responses the section describes errors that occur during the http access. You can change the messages which are shown to the clients. You can do this by editing the error message template file (/opt/f-secure/fsigk/conf/...
Page 145
F-secure internet gatekeeper for linux/administrator’s guide 145 description the http version of the request exceeds the limit (98 bytes) response code 400 reason bad request message too long request version request version error description the request http version specified is a version other than...
Page 146
F-secure internet gatekeeper for linux/administrator’s guide 146 11.7 http request and response headers http request and response headers are not changed for the most part but the following headers are changed by the product. Request header: • request line if the request version is “http/1.1”, it is...
Page 147
F-secure internet gatekeeper for linux/administrator’s guide 147 response header: • response line if the response header version is “http/1.1”, it is changed to “http/1.0” • connection the current connection header is removed if the connection is keep-alive, the following is added. Connection: keep-...
Page 148
F-secure internet gatekeeper for linux/administrator’s guide 148 11.8 smtp command responses usually, server responses are relayed to clients during smtp connections. However, sometimes they can be generated by f-secure internet gatekeeper for linux. The product generates the following messages: [re...
Page 149
F-secure internet gatekeeper for linux/administrator’s guide 149 other command responses message 500 too long line reason the length of the command line exceeds 9999 bytes. Responses from commands other than helo, ehlo, auth, quit, rset message 500 authentication required" reason the authentication ...
Page 150
F-secure internet gatekeeper for linux/administrator’s guide 150 reason authentication failed. Is displayed only when smtp authentication is performed by f-secure internet gatekeeper for linux. If authentication is done on the smtp server side, the smtp server response is relayed. Message 500 discon...
Page 151
F-secure internet gatekeeper for linux/administrator’s guide 151 11.9 smtp commands – operations during smtp connections, commands executed from clients are operated in the following way. The [product name] is by default "f-secure/fsigk_smtp/version/host name". You can change the product name by edi...
Page 152
F-secure internet gatekeeper for linux/administrator’s guide 152 ehlo command 1 the following is sent to the server: ehlo [host name] 2 receives a response from the server. 3 the following option lines are deleted from the response information. Chunking , binarymime, pipelining,starttls 4 set the re...
Page 153
F-secure internet gatekeeper for linux/administrator’s guide 153 data command 1 the following is sent to the client: 354 enter mail ([product name]) 2 mail data is received. 3 mail data is scanned for viruses or spam. 4 if a virus or spam is detected: ① virus logs are recorded. ② a notification is s...
Page 154
F-secure internet gatekeeper for linux/administrator’s guide 154 a) the following is sent to the server: to: [recipient address of the e-mail received] b) the following is sent to the server: cc: [cc address of the e-mail received] 9) if the from field is not included in the infected e-mail notifica...
Page 155
F-secure internet gatekeeper for linux/administrator’s guide 155 1 the following is sent to the server: 500 unknown command: "[command received]" ([product name]) 11.10 pop commands – operations during pop connections, commands executed from clients are operated in the following way. The [product na...
Page 156
F-secure internet gatekeeper for linux/administrator’s guide 156 ④ if the connection fails: 1) the following is sent to the client: -err can't connect to (server host: server port) errmsg=[connection error message] for connection error messages, see “ connection error messages ”, 162. ⑤ the followin...
Page 157
F-secure internet gatekeeper for linux/administrator’s guide 157 6 if (5) above does not apply: ① if a virus or spam is detected: 1) the following is sent to the client: received: from fsigk: current time(rfc822 format) ② if spam is detected: 1) the following is sent to the client: x-spam-status: ye...
Page 158
F-secure internet gatekeeper for linux/administrator’s guide 158 2 if (1) above does not apply: ① if user authentication is enabled: 1) if the user is not added: a) the following is sent to the client: 500 invalid account auth. ② if the user name contains “@” or “#”: 1) the server specified by the l...
Page 159
F-secure internet gatekeeper for linux/administrator’s guide 159 ④ if the connection fails: 1) the following is sent to the client: -500 can't connect to (server host: server port) errmsg=[connection error message] for connection error messages, see “ connection error messages ”, 162. ⑤ the followin...
Page 160
F-secure internet gatekeeper for linux/administrator’s guide 160 3 if the mode is active: ① receives a response from the server. ② if the response code is other than 1xx: 1) the command terminates. ③ connects to the client with the data session. ④ if the client connection fails: 1) information of th...
Page 161
F-secure internet gatekeeper for linux/administrator’s guide 161 host name lookup failure : failed to look up the specified host. (occurs, for example, when a response from the dns server could not be reached. If there is no problem on the dns server, check if you can look up the host name from the ...
Page 162
F-secure internet gatekeeper for linux/administrator’s guide 162 11.13 service process list f-secure linux internet gatekeeper uses the following processes to provide its services. Tomcat(java) web application server used for the web console of the product. Tomcat uses java. It uses a single process...
Page 163
F-secure internet gatekeeper for linux/administrator’s guide 163 fsavd handles the scanning engine process. The number of processes it uses varies depending on the usage. The process uses a minimum of 2 processes for each service (http, smtp, pop, ftp), and the maximum number of processes it can use...
Page 164
F-secure internet gatekeeper for linux/administrator’s guide 164 11.14 detection names if f-secure internet gatekeeper for linux detects a virus, the virus name is recorded in a log. Detailed information on viruses can be found on the following web page: http://www.F-secure.Com/v-descs/ if you speci...
Page 165
F-secure internet gatekeeper for linux/administrator’s guide 165 fsigk/spam_list/uce/([condition number])/(header field)) spam detected by a database (unsolicited advertisements). The condition number indicates the number of lines detected in the database file. Fsigk/spam_list/advertisement/(conditi...
Page 166
F-secure internet gatekeeper for linux/administrator’s guide 166 11.15 riskware riskware is not malware. Riskware is not designed specifically to harm the computer, but it has security-critical functions that may harm the computer if misused. These programs perform some useful but potentially danger...
Page 167
F-secure internet gatekeeper for linux/administrator’s guide 167 riskware platforms: apropos bat casino clearsearch dos drweb dudu esafe html java js linux lop macro maxifiles nai navipromo newdotnet palm perl php searcher solomon symantec trendmicro unix vba vbs win16 win32 wintol zenosearch.
Page 168
F-secure internet gatekeeper for linux/administrator’s guide 168 12. Copyright information copyright (c) 1993-2004 f secure corporation. All rights reserved. Portions copyright (c) 1991-2004 kaspersky labs, ltd. Copyright (c) 2003 commtouch(r) software ltd this product may be covered by one or more ...
Page 169
F-secure internet gatekeeper for linux/administrator’s guide 169 apache myfaces(myfaces core / myfaces tomahawk) original package: http://myfaces.Apache.Org/ gnu wget original package: http://www.Gnu.Org/software/wget/ location: “tool/wget” on installation directory license: gpl.