- DL manuals
- F-SECURE
- Server
- INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61 -
- Administrator's Manual
F-SECURE INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61 - Administrator's Manual
Summary of INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61 -
Page 1
F-secure internet gatekeeper windows 2000/2003 server administrator’s guide.
Page 2
"f-secure" and the triangle symbol are registered trademarks of f-secure corporation and f-secure product names and symbols/logos are either trademarks or registered trademarks of f-secure corporation. All product names referenced herein are trademarks or registered trademarks of their respective co...
Page 3
3 contents about this guide 10 how this guide is organized ............................................................................................ 11 conventions used in f-secure guides .............................................................................. 13 symbols ......................
Page 4
4 3.1.2 web browser software requirements ........................................................... 46 3.2 centrally administered or stand-alone installation? .................................................. 47 3.2.1 installation overview for centrally administered installation.....................
Page 5
5 5.3.5 access control ............................................................................................. 123 5.4 monitoring logs........................................................................................................ 127 5.4.1 error log.......................................
Page 6
6 6.5 viewing statistics ..................................................................................................... 199 6.5.1 viewing statistics with f-secure internet gatekeeper web console........... 199 6.5.2 viewing statistics with f-secure policy manager.................................
Page 7
7 10.2 configuring quarantine options............................................................................... 260 10.3 searching the quarantined content......................................................................... 260 10.4 query results page ..........................................
Page 8
8 13.1.3 checking that f-secure content scanner server is up and running.......... 293 13.1.4 checking that the network connection to the original mail server is working.. 293 13.2 starting and stopping f-secure internet gatekeeper components ........................ 294 13.3 frequently asked questi...
Page 9
9 f.2.1 examples...................................................................................................... 322 f.2.2 transparent proxy with linux and unix based systems.............................. 327 f.2.3 transparent proxy with cisco, nortel and lucent ..................................
Page 10
10 a bout t his g uide how this guide is organized..................................................... 11 conventions used in f-secure guides ..................................... 13.
Page 11
About this guide 11 how this guide is organized f-secure internet gatekeeper administrator's guide is divided into the following chapters and appendixes. Chapter 1. Introduction . General information about f-secure internet gatekeeper and other f-secure anti-virus for mail server and gateway product...
Page 12
12 chapter 9. Administering f-secure management agent . Instructions on how to configure f-secure management agent. Chapter 10. Quarantine management . Instructions on how to manage and search quarantined content. Chapter 11. Security and performance . Instructions on how to optimize security and pe...
Page 13
13 conventions used in f-secure guides this section describes the symbols, fonts, and terminology used in this manual. Symbols ⇒ an arrow indicates a one-step procedure. Fonts arial bold (blue) is used to refer to menu names and commands, to buttons and other items in a dialog box. Arial italics (bl...
Page 14
14 courier new bold is used for information that you must type. Small caps ( black ) is used for a key or key combination on your keyboard. Arial underlined (blue) is used for user interface links. Arial italics is used for window and dialog box names. Pdf document this manual is provided in pdf (po...
Page 15
15 1 i ntroduction overview..................................................................................... 16 how the product works.............................................................. 17 features ..................................................................................... 21...
Page 16
16 1.1 overview malicious code, such as computer viruses, is one of the main threats for companies today. When users began to use office applications with macro capabilities to write documents and distribute them via mail and groupware servers, macro viruses started spreading rapidly. After the mill...
Page 17
Chapter 1 17 introduction 1.2 how the product works f-secure internet gatekeeper is a suite of real-time services to protect the corporate network against computer viruses and malicious code coming in web (http and ftp-over-http) and e-mail (smtp) traffic. F-secure internet gatekeeper is comprised o...
Page 18
18 figure 1-1 web traffic flow after f-secure anti-virus for internet gateways has been installed f-secure anti-virus for internet gateways provides comprehensive virus protection and content filtering. It can be configured to do any of the following: deny access to specified web sites, block files ...
Page 19
Chapter 1 19 introduction f-secure anti-virus for internet gateways can be deployed transparently to end-users. Since all http and ftp-over-http requests and downloads pass through the proxy server, f-secure anti-virus for internet gateways provides effective access control and protection against vi...
Page 20
20 figure 1-2 mail traffic flow after f-secure anti-virus for internet mail has been installed if f-secure anti-virus for internet mail finds an infected attachment or other malicious content, it can do any of the following: block the whole e-mail message, strip the infected attachment, send a custo...
Page 21
Chapter 1 21 introduction 1.2.3 f-secure content scanner server f-secure content scanner server is the back-end component that provides anti-virus and spam scanning services for f-secure anti-virus for internet gateways and f-secure anti-virus for internet mail. F-secure content scanner server recei...
Page 22
22 easy to administer f-secure internet gatekeeper can be centrally managed with f-secure policy manager. You can configure f-secure internet gatekeeper settings with f-secure policy manager any time you want. In stand-alone mode, the f-secure internet gatekeeper web console can be used to administe...
Page 23
Chapter 1 23 introduction transparency and scalability viruses are intercepted before they enter the network and spread to workstations and servers. Real-time scanning of internal, inbound and outbound mail messages. The company network can be configured so that users cannot bypass the system, which...
Page 24
24 1.4 f-secure anti-virus mail server and gateway products the f-secure anti-virus product line consists of workstation, file server, mail server and gateway products. F-secure internet gatekeeper is a high performance, totally automated web (http and ftp-over-http) and e-mail (smtp) virus scanning...
Page 25
Chapter 1 25 introduction automatically from f-secure, keeping the virus protection always up to date. A powerful and easy-to-use management console simplifies the installation and configuration of the product. F-secure messaging security gateway™ delivers the industry’s most complete and effective ...
Page 26
26 2 d eployment overview..................................................................................... 27 deployment scenarios ............................................................... 29.
Page 27
Chapter 2 27 deployment 2.1 overview depending on the corporate network structure, you might consider various scenarios of deploying f-secure internet gatekeeper. This chapter describes some possible deployment scenarios of f-secure internet gatekeeper in the corporate network - use the one that bes...
Page 28
28 2.2 network requirements this network configuration is valid for all scenarios described in this chapter. Make sure that the following network traffic can travel: service process inbound ports outbound ports f-secure anti-virus for internet gateways %programfiles%\f-secure\ anti-virus for interne...
Page 29
Chapter 2 29 deployment 2.3 deployment scenarios this section describes the f-secure anti-virus for internet gateways and f-secure anti-virus for internet mail deployment scenarios. 2.3.1 f-secure anti-virus for internet gateways there are four different deployment scenarios for f-secure anti-virus ...
Page 30
30 f-secure anti-virus for internet gateways configuration add end-user workstations to the list of hosts which are allowed to connect to f-secure anti-virus for internet gateways. For more information, see “ connections to f-secure anti-virus for internet gateways ”, 123 firewall configuration allo...
Page 31
Chapter 2 31 deployment f-secure anti-virus for internet gateways configuration add end-user workstations to the list of hosts which are allowed to connect to f-secure anti-virus for internet gateways. For more information, see “ connections to f-secure anti-virus for internet gateways ”, 123 define...
Page 32
32 scenario 3: as an upstream proxy figure 2-3 f-secure anti-virus for internet gateways deployed as an upstream proxy advantages end-users do not have to change the proxy settings of their web browsers. Disadvantages if virus definition databases are not up-to-date, there is a risk of malicious cod...
Page 33
Chapter 2 33 deployment http proxy or cache server configuration configure http proxy or cache server to forward all http requests to f-secure anti-virus for internet gateways. Firewall configuration allow http and https requests only from f-secure anti-virus for internet gateways. Dns configuration...
Page 34
34 configuration on end-user workstations web browsers do not have to be configured to use the proxy, http requests are sent directly. Adjust the routing table to forward requests to a firewall or router if necessary. F-secure anti-virus for internet gateways configuration add the internal firewall ...
Page 35
Chapter 2 35 deployment scenario 1: on a dedicated machine figure 2-5 f-secure anti-virus for internet mail deployed on a dedicated machine advantages the mail server may run on any operating system using any hardware. All inbound, outbound and internal mails are scanned. The overall performance is ...
Page 36
36 configuration on end-user workstations if the mail server for outgoing mails is specified as a dns name (for example, smtp.Example.Com), e-mail client configurations do not have to be changed. Otherwise, e-mail clients should be configured to send e-mails to f-secure anti-virus for internet mail....
Page 37
Chapter 2 37 deployment scenario 2: with a mail server on the same machine figure 2-6 f-secure anti-virus for internet mail deployed with a mail server on the same machine advantages f-secure anti-virus for internet mail does not require an additional server. E-mail clients, dns and firewall configu...
Page 38
38 mail server configuration change the port number that the mail server listens to something other than 25 (e.G. 26). Configure the mail server to accept incoming smtp connections only from f-secure anti-virus for internet mail (i.E. From localhost, or 127.0.0.1). F-secure anti-virus for internet m...
Page 39
Chapter 2 39 deployment advantages e-mail clients can send mails using other protocol(s) than smtp. The internal mail server may run on any operating system using any hardware. Disadvantages internal mails are not scanned. Dns and firewall configuration no changes are required in firewall configurat...
Page 40
40 scenario 4: multiple f-secure internet gatekeeper installations with centralized quarantine management figure 2-8 two installation of f-secure anti-virus for internet mail deployed with centralized quarantine management sql server used for the centralized quarantine database there is a common sql...
Page 41
Chapter 2 41 deployment f-secure anti-virus for internet mail configuration when installing the product, configure each instance of the product to use the same sql server and database. Make sure that the sql server, the database name, user name and password are identical in the quarantine configurat...
Page 42
42 3 i nstallation recommended system requirements....................................... 43 centrally administered or stand-alone installation?................... 47 installation instructions............................................................... 50 after the installation......................
Page 43
Chapter 3 43 installation 3.1 recommended system requirements operating system: windows 2000 server family: microsoft® windows 2000 server with the latest service pack microsoft® windows 2000 advanced server with the latest service pack windows 2003 server family: microsoft® windows server 2003, sta...
Page 44
44 if you plan to install the product on microsoft windows 2000 platform, then the latest microsoft data access components (mdac, version 2.8 or newer) needs to be installed to the system before the product installation. The latest version of mdac can be downloaded from this page: http://msdn.Micros...
Page 45
Chapter 3 45 installation 3.1.1 which sql server to use for the quarantine database? As a minimum requirement, the quarantine database should have the capacity to store information about all inbound and outbound mail to and from your organization that would normally be sent during 2-3 days. Take int...
Page 46
46 microsoft sql server 2000 if your organization sends a large amount of e-mails, it is recommended to use microsoft sql server 2000. It is recommended to use microsoft sql server 2000 if you are planning to use centralized quarantine management with multiple f-secure internet gatekeeper installati...
Page 47
Chapter 3 47 installation 3.2 centrally administered or stand-alone installation? F-secure internet gatekeeper can be managed either locally with f-secure internet gatekeeper web console or centrally with f-secure policy manager console. You can select the management method when you install the prod...
Page 48
48 the general installation plan is as follows: 1. Install f- secure policy manager server and f-secure installation packages from f- secure policy manager setup. For installation instructions, see the chapter installing f-secure policy manager server in f-secure policy manager administrator’s guide...
Page 49
Chapter 3 49 installation 3.2.2 installation overview for stand-alone installation the general installation plan is as follows: 1. Install f- secure internet gatekeeper. See the installation instructions in “ installation instructions ”, 50. Note that when f- secure internet gatekeeper is installed ...
Page 50: Step 1.
50 3.3 installation instructions the installation instructions in this section are valid for both centrally managed and stand-alone installations, but the options to select are determined by the administration mode you are going to use. The administration modes are explained in “ centrally administe...
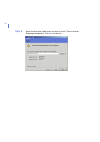
Page 51: Step 3.
Chapter 3 51 installation step 3. Read the license agreement. If you accept the agreement, select the i accept this agreement check box and click next to continue..
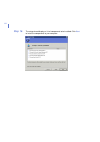
Page 52: Step 4.
52 step 4. Enter the product keycode and click next to continue. If you are installing the evaluation version, this screen is not displayed..
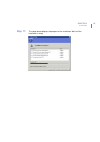
Page 53: Step 5.
Chapter 3 53 installation step 5. Installable components are displayed. The options available may vary depending on the keycode you entered in the previous step. Select the components to install and click next to continue. If you are installing only f-secure anti-virus for internet gateways or f-sec...
Page 54: Step 6.
54 step 6. Select the destination folder where you want to install f-secure internet gatekeeper components. Click next to continue..
Page 55: Step 7.
Chapter 3 55 installation step 7. Select the administration method you want to use to manage your f-secure internet gatekeeper: select centralized administration through network to use f-secure policy manager console to remotely manage all f-secure internet gatekeeper components. For more informatio...
Page 56: Step 8.
56 step 8. Enter the path or click browse to locate the management key. This is the key that you created during the f-secure policy manager console setup. Click next to continue..
Page 57: Step 9.
Chapter 3 57 installation step 9. Select the network communication method. If you are using f-secure policy manager to manage f-secure internet gatekeeper, select f-secure policy manager server. Click next to continue..
Page 58: Step 10.
58 step 10. Enter the ip address of the f-secure policy manager server. Click next to continue..
Page 59: Step 11.
Chapter 3 59 installation step 11. Specify the ip address or the dns address and the administration tcp port number (by default 8080) of f-secure policy manager server. The administration port is used because the setup program needs to upload new mib files to f-secure policy manager server. Click ne...
Page 60: Step 12.
60 step 12. Select the quarantine management mode: if you have only one f-secure internet gatekeeper installation, or you do not want to manage quarantined e-mails centrally, select the default option, local quarantine management. If you have multiple installations and you want to manage quarantined...
Page 61: Step 13.
Chapter 3 61 installation step 13. Specify where the sql server database for storing quarantined content should be created. For small environments select the default option, install and use microsoft sql server desktop engine (msde). This option installs the quarantine database on the same server wi...
Page 62: Step 14.
62 step 14. A) specify msde installation directory specify where the msde program and data files will be installed. Then enter a password for the database server administrator account. Do not leave the password empty. Re-enter the password in the confirm password field. F-secure internet gatekeeper ...
Page 63: Step 15.
Chapter 3 63 installation b) specify sql server and database details enter the computer name of the sql server, or click browse to locate the server. Then enter the database server administrator account and password. The setup will use them to connect the sql server where the quarantine database wil...
Page 64: Step 16.
64 step 16. The setup wizard displays a list of components to be installed. Click start to install the components to your computer..
Page 65: Step 17.
Chapter 3 65 installation step 17. The setup wizard displays the progress of the installation. Wait until the installation is ready..
Page 66: Step 18.
66 step 18. The setup wizard displays the installation result for each component after the installation is completed. Click next to continue..
Page 67: Step 19.
Chapter 3 67 installation step 19. Click finish to complete the installation. If you were doing an upgrade installation and are prompted to restart your computer, select restart now. The new software version will be operational after the restart..
Page 68: Step 20.
68 step 20. After the installation, the product updates virus definition databases automatically. If the product is installed in centralized administration mode, it downloads the new databases from the f-secure policy manager server. If the product is installed in stand-alone mode, the databases are...
Page 69
Chapter 3 69 installation 3.4 after the installation this section describes what you have to do after the installation to take f-secure internet gatekeeper into use. 3.4.1 importing product mib files to f-secure policy manager console if you are using the product in centrally managed mode, there are...
Page 70
70 3.4.2 configuring the product by default, f-secure internet gatekeeper has very strict access control settings for security reasons. You have to configure f-secure internet gatekeeper before you can use it properly. Follow these instructions before you start using f-secure internet gatekeeper: f-...
Page 71
Chapter 3 71 installation 3. Configure the virus scanning and access control settings to specify the type of traffic you want to scan and sites where you want to deny the access. For http and ftp-over-http scanning, see “ configuring web traffic scanning ”, 107. Make sure that you specify which host...
Page 72
72 3.5 upgrading f-secure internet gatekeeper this section describes the needed configuration changes, if any, when upgrading f-secure internet gatekeeper. 3.5.1 upgrade instructions if you are using f-secure internet gatekeeper 6.4x or 6.50, you can upgrade it to f-secure internet gatekeeper 6.61 w...
Page 73
Chapter 3 73 installation figure 3-1 inbound mail routing table displayed during f-secure internet gatekeeper upgrade important: if this, or any other setting defined during the installation needs to be changed later on, the setting must be defined as final in the f-secure policy manager console bef...
Page 74
74 4. Specify how the outbound mail routing is to be handled. The table displays the domain, ip address and port number information read from the previous version’s configuration (see the example in the figure below). You can also add the information for a new outbound mail server. Figure 3-2 outbou...
Page 75: Step 2.
Chapter 3 75 installation 5. Specify the ip addresses and port numbers of primary f-secure content scanner servers where f-secure anti-virus for internet mail sends files to be scanned. Figure 3-3 primary f-secure content scanner servers list displayed during f-secure internet gatekeeper upgrade 6. ...
Page 76: Step 3.
76 step 3. Update the virus definition databases update the virus definition databases. Normally this is done automatically. For more information on updating the virus definition databases, see “ updating virus and spam definition databases ”, 280. Step 4. Enable the mail delivery enable mail delive...
Page 77
Chapter 3 77 installation tnbutil.Exe /keycode: where is the keycode you received. Tnbutil can be found under %programfiles%\f-secure\tnb directory. 3.6 uninstallation to uninstall f-secure internet gatekeeper, select add/remove programs from the windows control panel. To uninstall f-secure internet...
Page 78
78 4 b asics of u sing f-s ecure i nternet g atekeeper introduction................................................................................. 79 using f-secure policy manager................................................. 79 using f-secure internet gatekeeper web console ......................
Page 79
Chapter 4 79 basics of using f-secure internet gatekeeper 4.1 introduction this chapter contains a brief introduction into using f-secure policy manager for administering f-secure internet gatekeeper in centrally managed installations. In addition, it describes how to monitor the status of f-secure ...
Page 80
80 after a policy is created, it must be distributed to hosts by choosing distribute from the file menu. The status tab of the properties pane shows statistics and the settings that were configured during the installation of f-secure internet gatekeeper. Statistics are updated periodically and can b...
Page 81
Chapter 4 81 basics of using f-secure internet gatekeeper for detailed descriptions of f-secure content scanner server settings, see “ configuring f-secure content scanner server ”, 211. 4.2.4 f-secure management agent settings use the variables under the f-secure management agent / settings / branc...
Page 82
82 4.3 using f-secure internet gatekeeper web console in centrally managed installations of f-secure internet gatekeeper, the f-secure internet gatekeeper web console can be used for monitoring the system status and statistics. It can also be used for viewing the settings currently in use and execut...
Page 83
Chapter 4 83 basics of using f-secure internet gatekeeper when you log in for the first time, your browser will display a security alert dialog window about the security certificate for f-secure internet gatekeeper web console. You can create a security certificate for f-secure internet gatekeeper w...
Page 84
84 if you are using internet explorer 7, click continue and then certificate error . 3. Click view certificate to view the certificate information. 4. The certificate window opens. Click install certificate to proceed to the certificate import wizard. 5. Follow the instructions in the certificate im...
Page 85
Chapter 4 85 basics of using f-secure internet gatekeeper 7. When the login page opens, enter the user name and the password. Note that you must have administrator rights to the host. Then click log in . Figure 4-1 f-secure internet gatekeeper web console login page 8. You will be forwarded to the h...
Page 86
86 figure 4-2 f-secure internet gatekeeper home page 4.3.2 checking the product status you can check the overall product status on the home page. The home page displays a summary of the component statuses and most important statistics. From the home page you can also open the product logs and procee...
Page 87
Chapter 4 87 basics of using f-secure internet gatekeeper f-secure anti-virus for internet mail the home page displays the status the f-secure anti-virus for internet mail as well as a summary of the f-secure anti-virus for internet mail statistics. Click configure to configure f-secure anti-virus f...
Page 88
88 f-secure content scanner server the home page displays the status the f-secure content scanner server as well as a summary of the f-secure content scanner server statistics. Click configure to configure f-secure content scanner server. For more information, see “ configuring f-secure content scan...
Page 89
Chapter 4 89 basics of using f-secure internet gatekeeper f-secure automatic update agent click configure to configure f-secure automatic update agent. For more information, see “ automatic updates ”, 281. F-secure management agent click configure to configure the f-secure management agent. For more...
Page 90
90 click export settings to open a list of all f-secure internet gatekeeper settings in a new internet browser window. You can then save the file for later use by selecting file > save as.... Click export statistics to open a list of all f-secure internet gatekeeper statistics in a new internet brow...
Page 91
Chapter 4 91 basics of using f-secure internet gatekeeper to add a new host in the list, click add to add new a new line in the table and then enter the ip address of the host..
Page 92
92 5 a dministering f-s ecure a nti -v irus for i nternet g ateways overview - http scanning........................................................ 93 configuring f-secure anti-virus for internet gateways ............. 94 configuring web traffic scanning............................................ ...
Page 93
Chapter 5 93 administering f-secure anti-virus for internet gateways 5.1 overview - http scanning f-secure anti-virus for internet gateways takes care of http traffic scanning. This chapter describes how to configure and administer f-secure anti-virus for internet gateways. F-secure anti-virus for i...
Page 94
94 5.2 configuring f-secure anti-virus for internet gateways change the f-secure anti-virus for internet gateways settings to set up the working directory, connection, logging and advanced settings. For information on how to change http scanning settings, see “ content control ”, 107. The f-secure c...
Page 95
Chapter 5 95 administering f-secure anti-virus for internet gateways figure 5-1 network configuration / binding settings listen specify the port that f-secure anti-virus for internet gateways should listen to for incoming http requests. Users must have this port configured in the web browser proxy s...
Page 96
96 connection you can configure the timeout and persistent connections settings from f-secure anti-virus for internet gateways / settings / network configuration / connection. Figure 5-2 network configuration / connection settings usually the proxy connect method is used when a web browser requests ...
Page 97
Chapter 5 97 administering f-secure anti-virus for internet gateways timeout specify how long (in seconds) f-secure anti-virus for internet gateways waits for response from the web server before it timeouts. The connection can timeout while: requesting web page contents (sending an http get request)...
Page 98
98 proxy chaining if you use an existing upstream proxy server in your corporate network, you can set up proxy chaining. F-secure anti-virus for internet gateways can forward all requests to the existing proxy server. You can configure these settings from f-secure anti-virus for internet gateways / ...
Page 99
Chapter 5 99 administering f-secure anti-virus for internet gateways figure 5-3 network configuration / proxy chaining settings remote proxy server specify the address and port number of the proxy server where f-secure anti-virus for internet gateways forwards all requests. Specify the address in fo...
Page 100
100 proxy max forwards specify the maximum number of proxies through which a single request may pass. Setting a maximum number of proxy forwards prevents infinite proxy loops and denial of service attacks. By default, the value is 10. Proxy via specify how http/1.1 via headers should be handled. Via...
Page 101
Chapter 5 101 administering f-secure anti-virus for internet gateways data trickling if you enable data trickling, data is sent to requesting clients little by little while it is being downloaded to f-secure anti-virus for internet gateways. Once the whole file has been downloaded, it will be scanne...
Page 102
102 trickle packet size set the size of the packets to send through when the trickle interval is reached. Trickled data is not scanned before it has been downloaded to f-secure gatekeeper completely. It may be unsafe to keep the packet size large, as potential malware may trickle through byte by byt...
Page 103
Chapter 5 103 administering f-secure anti-virus for internet gateways content scanner server you can configure the content scanner server settings from f-secure anti-virus for internet gateways / settings / network configuration / content scanner server. Figure 5-5 network configuration / content sc...
Page 104
104 logging you can configure the logging settings from f-secure anti-virus for internet gateways / settings / logging. Figure 5-6 network configuration / logging settings for more information about logging, see “ monitoring logs ”, 127. Log directory specify the logging directory. Enter the complet...
Page 105
Chapter 5 105 administering f-secure anti-virus for internet gateways error log level specify the level of messages that are recorded to the error log file. All error messages of the specified level and above are recorded. Specify one of the following levels: emergency - emergencies, the system is u...
Page 106
106 click add to add a new row in the table. Then select the cell you want to edit in the table, and click edit . Enter the data for the new format: nickname - specify the name for the log format, which you can see and select from the logging page. Format - specify the string for the access log form...
Page 107
Chapter 5 107 administering f-secure anti-virus for internet gateways 5.3 configuring web traffic scanning change the f-secure anti-virus for internet gateways scanning settings to view scanning statistics and to select which files and web pages downloaded via http and ftp-over-http should be scanne...
Page 108
108 scan for viruses specify which content types should be scanned for viruses. Disabled - disables the virus scan. All content types - scans all content that passes through f-secure anti-virus for internet gateways. Only included content types - scan all specified content types. All except excluded...
Page 109
Chapter 5 109 administering f-secure anti-virus for internet gateways f-secure anti-virus for internet gateways supports the scanning of ftp-over-http traffic, if f-secure anti-virus for internet gateways has been defined as the http and ftp proxy server in the browsers. Otherwise the scanning will ...
Page 110
110 to delete a content type permanently, select the corresponding row, and then click clear row . Click clear all to clear the whole table. Click defaults to restore default log formats to the table. Restoring the default list deletes all other entries from the table. The default list of scanned co...
Page 111
Chapter 5 111 administering f-secure anti-virus for internet gateways drop - drop all files that f-secure anti-virus for internet gateways cannot scan. Pass - let all files that f-secure anti-virus for internet gateways cannot scan pass through to the requesting client. Using this option is not reco...
Page 112
112 blocking you can select which files f-secure anti-virus for internet gateways should block without scanning them. You can configure these settings from f-secure anti-virus for internet gateways / settings / content control / blocking. Figure 5-8 content control / blocking settings block content ...
Page 113
Chapter 5 113 administering f-secure anti-virus for internet gateways http only - disallowed content in http traffic will be blocked according to content blocking rules and ftp-over-http downloads will pass through without processing. Ftp-over-http only - disallowed content in ftp-over-http traffic ...
Page 114
114 file type recognition trojans and other malicious code can disguise themselves with content types and filename extensions which are usually considered safe to use. With the file type recognition, you can configure f-secure anti-virus for internet gateways to recognize the real file type and use ...
Page 115
Chapter 5 115 administering f-secure anti-virus for internet gateways note that other scanning settings have an effect on the use of file type recognition. Even if the file type recognition is turned on, it is used only when the file would not be scanned because of its content type. For example, if ...
Page 116
116 f-secure anti-virus for internet gateways can show virus warning messages to users when it finds malicious code in the downloaded content or blocks the access to a disallowed content. It also keeps log of all virus scans it performs. You can edit virus and blocking alerts and specify how often a...
Page 117
Chapter 5 117 administering f-secure anti-virus for internet gateways always - send the virus warning message every time f-secure anti-virus for internet gateways finds malicious code in the downloaded content. Send block alerts to administrator specify whether f-secure anti-virus for internet gatew...
Page 118
118 an example of a scan summary: from: f-secure anti-virus for internet gateways sent: thursday, march 25, 2007 10:51 am to: administrator@example.Com subject: alert! Date: 2007-03-25 10:50:52+04:00 host: hostname (127.0.0.1) computer name: hostname user account: hostname\system product: f-secure a...
Page 119
Chapter 5 119 administering f-secure anti-virus for internet gateways 5.3.3 performance use scan result cache to process frequently accessed web pages faster. F-secure internet gatekeeper does not cache scanned files, it just stores a unique identifier for each file. The content is verified with a c...
Page 120
120 scan result cache specify whether f-secure anti-virus for internet gateways should use the recent transaction results cache to process identical files without scanning them again for viruses. Scan result cache size specify how many transaction results f-secure anti-virus for internet gateways sh...
Page 121
Chapter 5 121 administering f-secure anti-virus for internet gateways the scan result cache is automatically reset when any f-secure anti-virus for internet gateways or f-secure content scanner server settings are changed or when virus definition databases are updated. F-secure anti-virus for intern...
Page 122
122 5.3.4 administration f-secure anti-virus for internet gateways scans http content which is smaller than 1 mb in memory, and buffers and scans content that is larger than 1 mb in the working directory. You can change the working directory settings from f-secure anti-virus for internet gateways / ...
Page 123
Chapter 5 123 administering f-secure anti-virus for internet gateways 5.3.5 access control with access control, you can specify which hosts can connect to f-secure anti-virus for internet gateways. Furthermore, you can specify hosts and sites which are never scanned for viruses and sites which the u...
Page 124
124 figure 5-13 access control settings the figure below shows which hosts are allowed and denied connections when the different access policies are in use. Access policy specify whether you want to allow specific hosts to connect to f-secure anti-virus for internet gateways and deny all other conne...
Page 125
Chapter 5 125 administering f-secure anti-virus for internet gateways figure 5-14 access policies and the allowed and denied hosts allowed hosts specify hosts and subnets that are allowed to connect to f-secure anti-virus for internet gateways. For more information, see “ specifying hosts ”, 300. De...
Page 126
126 trusted hosts files which come from trusted hosts are never scanned for viruses and downloads are never blocked. Click add to add a new host in the table. To modify an existing host, select the corresponding row and click edit . For more information, see “ specifying hosts ”, 300. Trusted sites ...
Page 127
Chapter 5 127 administering f-secure anti-virus for internet gateways banned sites connections to banned sites are blocked. The content from banned sites is always blocked, regardless of trusted hosts. Click add to add a new banned site in the table. To modify an existing site, select the correspond...
Page 128
128 5.4.1 error log f-secure anti-virus for internet gateways saves all informational and error messages and saves them to the logging directory. For more information, see “ logging ”, 104. You can specify the level of messages that are recorded to the error log file by changing the error log level ...
Page 129
Chapter 5 129 administering f-secure anti-virus for internet gateways 5.4.2 access log f-secure anti-virus for internet gateways logs all requests in the access log. You can specify the string format in the access log by changing the access log format setting. The default access log format: %t \"%r\...
Page 130
130 5.5 viewing statistics you can view http and total scanning statistics with f-secure policy manager console or with f-secure internet gatekeeper web console. F-secure internet gatekeeper web console can be used for viewing statistics also when the product is installed in centralized administrati...
Page 131
Chapter 5 131 administering f-secure anti-virus for internet gateways summary the summary page of f-secure anti-virus for internet gateways displays the http traffic scanning statistics: the number of scanned files, the last virus found and the last time a virus was found. Figure 5-15 http scanning ...
Page 132
132 statistics click start / stop to start or stop the f-secure anti-virus for internet gateways. Click reset statistics to reset all http scanning statistics. Processed files displays the total number of files that have passed through and have been scanned. Size of processed files displays the tota...
Page 133
Chapter 5 133 administering f-secure anti-virus for internet gateways content control the content control page of f-secure anti-virus for internet gateways displays more in-depth statistics, displaying the amount of files and kilobytes processed and the number of blocked, infected and disinfected fi...
Page 134
134 blocked files displays the total number of files that have been blocked before they have been delivered to the requesting client. Disinfected files displays the total number of infected files that have been disinfected. Last time infection found displays the date and time the last virus was foun...
Page 135
Chapter 5 135 administering f-secure anti-virus for internet gateways 5.5.2 viewing statistics with f-secure policy manager console to view the f-secure anti-virus for internet gateways statistics in f-secure policy manager console, select the status tab in the properties pane, and then select the f...
Page 136
136 5.6 examples of http notifications you can set f-secure anti-virus for internet gateways to show virus warning messages to users when it finds malicious code in downloaded content or when it blocks access to a file. You can edit virus and blocking warning messages in the notifications page. For ...
Page 137
Chapter 5 137 administering f-secure anti-virus for internet gateways 5.6.1 virus warning message the virus warning message is displayed to users when they try to download a file that contains malicious code. Figure 5-18 an example of a virus warning message.
Page 138
138 5.6.2 block warning message the block warning message is displayed to users when they try to download a file that has been blocked. Figure 5-19 an example of a block warning message.
Page 139
Chapter 5 139 administering f-secure anti-virus for internet gateways 5.6.3 banned site warning message the banned site warning message is displayed to users when they try to access a site which they are not allowed to access. Figure 5-20 an example of a banned site warning message.
Page 140
140 6 a dministering f-s ecure a nti -v irus for i nternet m ail overview - smtp scanning ..................................................... 141 configuring f-secure anti-virus for internet mail..................... 142 configuring smtp traffic scanning ......................................... 1...
Page 141
Chapter 6 141 administering f-secure anti-virus for internet mail 6.1 overview - smtp scanning f-secure anti-virus for internet mail takes care of smtp traffic scanning. This chapter describes how to configure and administer f-secure anti-virus for internet mail. F-secure anti-virus for internet mai...
Page 142
142 6.2 configuring f-secure anti-virus for internet mail set up the common settings to configure common smtp scanning settings. For more information on how to specify inbound and outbound e-mail scanning settings, see “ configuring smtp traffic scanning ”, 166. The f-secure content scanner settings...
Page 143
Chapter 6 143 administering f-secure anti-virus for internet mail 6.2.1 smtp settings you can change the general smtp settings from f-secure anti-virus for internet mail / settings / common / smtp settings. Figure 6-1 common / smtp settings settings ip addresses specify the ip addresses that f-secur...
Page 144
144 if you are using dns load balancing between mail servers, you need to disable dns lookup caching. For more information, see the following microsoft knowledgebase articles: windows 2000 server: http://support.Microsoft.Com/ default.Aspx?Scid=kb;en-us;245437 windows server 2003: http://support.Mic...
Page 145
Chapter 6 145 administering f-secure anti-virus for internet mail since all mail servers are not able to resolve the host name, use legal address (for example username@example.Com). If you do not specify the domain, the name of the host running the agent is automatically appended to the end. Agent s...
Page 146
146 6.2.2 smtp connections you can change the general connections settings from f-secure anti-virus for internet mail / settings / common / smtp connections. If the value is specified as zero (0), there can be an unlimited number of received: fields. Bounced mail sender address specify the e-mail se...
Page 147
Chapter 6 147 administering f-secure anti-virus for internet mail figure 6-2 common / smtp connections settings max connections specify the maximum number of simultaneous connections that are accepted. The excess connections are temporarily rejected. Using a very high value might increase the risk o...
Page 148
148 allowed hosts specify the ip addresses of hosts that are allowed to connect to f-secure anti-virus for internet mail. Denied hosts specify the ip addresses of hosts that are not allowed to connect to f-secure anti-virus for internet mail. An ip address range can be defined as a network/netmask p...
Page 149
Chapter 6 149 administering f-secure anti-virus for internet mail 6.2.3 content scanner servers you can specify how f-secure anti-virus for internet mail should connect to f-secure content scanner server from f-secure anti-virus for internet mail / settings / common / content scanner servers. Figure...
Page 150
150 click add to add a new entry to the table and clear to remove the selected entry. Click edit to edit the selected entry. Important: this setting must be defined as final with the restriction editor before the policies are distributed. Otherwise the setting will not be changed in the product. Bac...
Page 151
Chapter 6 151 administering f-secure anti-virus for internet mail 6.2.4 quarantine quarantine in f-secure internet gatekeeper is handled through a sql database. The product is able to quarantine e-mails and attachments which contain malicious or otherwise unwanted content, such as spam messages. The...
Page 152
152 in stand-alone installations, quarantine-related settings are configured and the quarantined files managed through the f-secure internet gatekeeper web console. Figure 6-4 the quarantine query page in web console is used for searching the quarantined content when the product places content to th...
Page 153
Chapter 6 153 administering f-secure anti-virus for internet mail for information on how to manage and search quarantined content, see “ quarantine management ”, 258. Figure 6-5 common / quarantine settings that are used for configuring the quarantining in centrally managed environments.
Page 154
154 figure 6-6 quarantine / options settings in the web console that are used for configuring the quarantining in stand-alone installations.
Page 155
Chapter 6 155 administering f-secure anti-virus for internet mail quarantine storage specify the location of the quarantine storage where quarantined e-mails and attachments are placed. Warning: during the setup, access rights are adjusted so that only the operating system, the product itself and th...
Page 156
156 active -enable or disable the selected entry in the table. Quarantine category - select a category the retention period or cleanup interval of which you want to modify. The categories are: infected disallowed suspicious spam scan failure unsafe retention period - specify an exception to the defa...
Page 157
Chapter 6 157 administering f-secure anti-virus for internet mail e-mail messages and infected, suspicious and disallowed attachments are stored and counted as separate items in the quarantine storage. For example, if a message has three attachments and only one of them has been found infected, two ...
Page 158
158 6.2.5 spooling with the spooling settings you can change where e-mails should be placed before they are processed and how often the spool should be flushed. The spooling settings are located in the f-secure anti-virus for internet mail / settings / common / spooling branch. Max attempts to proce...
Page 159
Chapter 6 159 administering f-secure anti-virus for internet mail figure 6-7 common / spooling settings spool directory specify the location of the spool directory where e-mail messages are spooled before they are processed. Make sure that the spool directory is on a local hard disk to ensure the be...
Page 160
160 to scan and send all currently spooled messages, select f-secure anti-virus for internet mail / operations / flush spool directory and click start . Important: this setting must be defined as final with the restriction editor before the policies are distributed. Otherwise the setting will not be...
Page 161
Chapter 6 161 administering f-secure anti-virus for internet mail continue accepting mail - the product sends a low spool error alert to the administrator and accepts incoming mail as usual. Reject mail temporarily - the product sends a low spool error alert to the administrator and rejects incoming...
Page 162
162 6.2.6 logging you can set f-secure anti-virus for internet mail to keep log of all the e-mails that pass through it. The logging settings are located under the f-secure anti-virus for internet mail / settings / common / logging branch. For more information on the content of the mail log, see “ m...
Page 163
Chapter 6 163 administering f-secure anti-virus for internet mail mail logging specify whether all e-mails should be logged. Logged events include accepting e-mail for delivery, scanning e-mail, and sending e-mail to the mail server. Logging directory specify the location of the logging directory wh...
Page 164
164 6.2.7 intranet hosts you can define the internal network addresses of your company with the intranet hosts settings. Add all intranet host addresses to the list to use inbound and outbound mail settings properly. Outbound e-mails e-mail messages that come from intranet hosts are sent by the user...
Page 165
Chapter 6 165 administering f-secure anti-virus for internet mail figure 6-9 common / intranet hosts settings click add to add a new entry to the intranet hosts list and edit to edit a previously made entry. Click remove to remove the selected entry from the intranet hosts list. An ip address range ...
Page 166
166 6.3 configuring smtp traffic scanning change the scanning settings to specify which e-mails should be scanned and blocked, and what to do with the infected content. In a centrally managed environment you can configure these settings for inbound mail in f-secure anti-virus for internet mail / set...
Page 167
Chapter 6 167 administering f-secure anti-virus for internet mail figure 6-10 inbound mail / receiving settings accept mail specify whether e-mail messages are accepted or rejected. Reject permanently - reject all messages. F-secure anti-virus for internet mail sends the smtp reply code 521, which i...
Page 168
168 accept always - accept all messages. If the mail server is unreachable, f-secure anti-virus for internet mail spools all messages and sends them when the connection is restored. Max message size specify the maximum size (in kilobytes) of the e-mail message that the product accepts. Set the value...
Page 169
Chapter 6 169 administering f-secure anti-virus for internet mail verify recipients select whether the recipient addresses should be verified. Allowed recipients specify recipients who are allowed to receive e-mail messages. Usually, allowed recipients should include all internal addresses. Denied r...
Page 170
170 max number of recipients per message specify the maximum number of recipients for inbound mail that will be accepted in one smtp session. The product will accept messages only to the number of recipients specified. The sending smtp server is then expected to retransmit the message to the remaini...
Page 171
Chapter 6 171 administering f-secure anti-virus for internet mail editing recipient lists use the username@example.Com format to specify recipient addresses. You can use wildcards in adresses: '?' to match one character and '*' to match any number of characters. Click add to add a new entry to the r...
Page 172
172 when importing the csv file, select the setting you want to import to, and click import... In the restriction editor. When the import table content from csv dialog opens, you can change the delimiter character by clicking the options... Button. 6.3.3 spam control for information on configuring s...
Page 173
Chapter 6 173 administering f-secure anti-virus for internet mail strip attachments specify whether attachments are stripped from the e-mails. Disabled - attachments are not stripped. All files - all attachments are stripped from e-mail messages. All disallowed attachments - specified attachments ar...
Page 174
174 scan stripped attachments if you want statistics about viruses found in stripped attachments, you can specify whether the product should scan stripped attachments before taking the corresponding action (block, drop and/or quarantine) on them. Enabling this setting might cause extra load on the s...
Page 175
Chapter 6 175 administering f-secure anti-virus for internet mail you can also use wildcards: '?' matches exactly one character, '*' matches any number of characters, including zero (0) characters. For example: '*.Mp3, *.Txt.Exe'. Block partial messages specify whether multipart messages (with 'mess...
Page 176
176 send notification message to recipient specify whether a notification message is sent to the mail recipient when a disallowed attachment has been dropped. The notification message text is added to the original e-mail message. If the whole message is stopped, no notification is sent. Recipient no...
Page 177
Chapter 6 177 administering f-secure anti-virus for internet mail 6.3.5 virus scanning you can change the virus scanning and virus notification settings from f-secure anti-virus for internet mail / settings / inbound mail / virus scanning. Figure 6-12 inbound mail / virus scanning settings sender no...
Page 178
178 scan for viruses select whether f-secure anti-virus for internet mail should scan messages and attachments for viruses. Mail message body is always scanned unless this setting is set to 'do not scan inbound messages'. Do not scan inbound messages - inbound messages are not scanned. All attachmen...
Page 179
Chapter 6 179 administering f-secure anti-virus for internet mail files with these extensions are checked for viruses when the scan for viruses setting is set to all attachments with included extensions. Excluded extensions specify a space-separated list of the file extensions that are excluded from...
Page 180
180 enabled - if this setting is enabled and if the action on infected messages setting is set to drop attachment or disinfect attachment, the product will only quarantine attachments that are found infected or suspicious and that cannot be disinfected. If this setting is enabled and the action on i...
Page 181
Chapter 6 181 administering f-secure anti-virus for internet mail sender virus notification subject specify the subject of the notification message that is sent to the sender when a virus or other malicious code has been found. Sender virus notification message specify the body of the notification m...
Page 182
182 6.3.6 virus outbreak response the product can notify about virus outbreaks when the number of virus threats found during the specified period of time exceeds the specified limit. When proactive virus threat detection is enabled, the product analyzes inbound e-mail messages for possible security ...
Page 183
Chapter 6 183 administering f-secure anti-virus for internet mail 6.3.7 file type recognition trojans and other malicious code can be disguised under spoofed filename extensions. The intelligent file type recognition recognizes the legitimate file type and detects "unsafe" content coming with "safe"...
Page 184
184 file type recognition does not check files that are inside archives, as this would seriously degrade the system performance. Intelligent file type recognition select whether intelligent file type recognition is enabled or disabled. Enabled - the product attempts to determine the real file type o...
Page 185
Chapter 6 185 administering f-secure anti-virus for internet mail 6.3.8 disclaimer you can change the disclaimer settings from f-secure anti-virus for internet mail / settings / inbound mail / notifications. Figure 6-14 inbound mail / disclaimer settings add disclaimer to message select whether a di...
Page 186
186 disclaimer text specify the disclaimer text. It is recommended to use the disclaimer text only as a business e-mail signature that states, for example, that the message is confidential. An example disclaimer text: this e-mail and any files transmitted with it are confidential and intended solely...
Page 187
Chapter 6 187 administering f-secure anti-virus for internet mail 6.3.9 mail delivery you can set where scanned e-mails should be sent from f-secure anti-virus for internet mail / settings / inbound mail / delivery. Figure 6-15 inbound mail / delivery settings mail routing table specify how the traf...
Page 188
188 important: the settings in the mail routing table must be defined as final with the restriction editor before the policies are distributed. Otherwise the settings will not be changed in the product. Fields for a mail routing entry: order specify an ordinal number for the entry. The entries in th...
Page 189
Chapter 6 189 administering f-secure anti-virus for internet mail - the port number. If the port number is not specified, the default smtp port (25) is used. For example, the following entries are valid: 'smtp.Example.Com:25', '192.168.100.42:26'. Comment use this field for comments for the entry. U...
Page 190
190 restore connection interval specify the time that f-secure anti-virus for internet mail waits before attempting to connect to the mail server if the previous attempt failed or the connection was lost. Give up time specify how long f-secure anti-virus for internet mail attempts to deliver inbound...
Page 191
Chapter 6 191 administering f-secure anti-virus for internet mail 6.3.10 security options you can configure the security options from f-secure anti-virus for internet mail / settings / inbound mail / security options. Figure 6-16 inbound mail / security options settings action on malformed mails spe...
Page 192
192 pass through and report - the product does not scan malformed content and lets the e-mail message pass through unless malicious code is found in the rest of the message. The administrator receives an alert about the malformed content found in the message. Max levels of nested messages specify ho...
Page 193
Chapter 6 193 administering f-secure anti-virus for internet mail examples of malformed messages malformed mail headers can include, for example: multiple content-type, content-disposition and/or content-transfer encoding headers, multiple “name” parameters in content-type headers, or multiple “file...
Page 194
194 in this example, there are multiple "content-disposition" headers and they refer to different attachments (name): this is a multi-part message in mime format. ------=_nextpart_000_007b_01c19931.61582b60 content-type: application/octet-stream content-transfer-encoding: base64 content-disposition:...
Page 195
Chapter 6 195 administering f-secure anti-virus for internet mail 6.4 monitoring logs f-secure anti-virus for internet mail maintains extensive logs. All the e-mails that pass through f-secure anti-virus for internet mail are logged in mail log. F-secure management agent maintains logfile.Log that c...
Page 196
196 an example of a received entry: 2007-06-01 11:58:45; [received]; job: smtp40bc454400; msg-id: ; host: 127.0.0.1; from: ; to: ; size: 696; direction: inbound; scanned entry the scanned entry is added to the log when all parts of the mail have been successfully scanned. The scanned entry includes ...
Page 197
Chapter 6 197 administering f-secure anti-virus for internet mail an example of a sent entry: 2007-06-01 11:59:26; [sent]; job: smtp40bc454400; msg-id: ; type: non-delivery-notice; from: ; to: ; msize: 2524; trashed entry the trashed entry is added to the log when f-secure anti-virus for internet ma...
Page 198
198 the failure entry includes the time of failure, the job name (the name of the spool file), the message id and the reason for failure. 2007-06-01 14:42:07; [failure]; job: smtp40bc454400; msg-id: ; reason: temporary error when sending mail to '(can't establish connection with host '10.1.1.1' due ...
Page 199
Chapter 6 199 administering f-secure anti-virus for internet mail 6.5 viewing statistics you can view smtp and total scanning statistics with f-secure policy manager console or f-secure internet gatekeeper web console. For instructions on how to log in the f-secure internet gatekeeper web console, s...
Page 200
200 figure 6-17 summary of smtp scanning statistics in f-secure internet gatekeeper web console.
Page 201
Chapter 6 201 administering f-secure anti-virus for internet mail status displays whether f-secure anti-virus for internet mail is currently running or not. Start time displays the date and time when f-secure anti-virus for internet mail was started. Messages accepted for delivery shows the total nu...
Page 202
202 click start to start f-secure anti-virus for internet mail and stop to stop it. Click reset statistics to reset the statistics. Inbound mail and outbound mail statistics the inbound mail / statistics page displays the inbound smtp traffic scanning statistics. The outbound mail / statistics page ...
Page 203
Chapter 6 203 administering f-secure anti-virus for internet mail figure 6-18 inbound mail statistics in f-secure internet gatekeeper web console.
Page 204
204 the statistics items displayed are the following: messages accepted for delivery displays the amount of messages that have been accepted. Messages successfully delivered displays the amount of messages that have been successfully delivered to the mail server. Processed messages displays the amou...
Page 205
Chapter 6 205 administering f-secure anti-virus for internet mail size of spam messages displays the total size of spam messages received. Last infection found displays the name of the last infection in inbound mail. Last infection found on displays the date and time of the last infection..
Page 206
206 6.5.2 viewing statistics with f-secure policy manager total smtp scanning statistics in f-secure policy manager console you can see the f-secure anti-virus for internet mail statistics on the status tab under the f-secure anti-virus for internet mail / statistics / total branch. For explanations...
Page 207
Chapter 6 207 administering f-secure anti-virus for internet mail inbound mail and outbound mail statistics in f-secure policy manager console you can see the f-secure anti-virus for internet mail inbound mail statistics on the status tab under the f-secure anti-virus for internet mail / statistics ...
Page 208
208 6.6 notifications f-secure anti-virus for internet mail can send notification messages to users when it finds malicious code in the scanned e-mail, or when it strips attachments from messages. It can also be configured to add a disclaimer in the end of clean messages. Smtp notifications f-secure...
Page 209
209 7 a dministering f-s ecure c ontent s canner s erver overview................................................................................... 210 configuring f-secure content scanner server........................ 211 configuring scanning settings ................................................
Page 210
210 7.1 overview f-secure content scanner server handles the actual virus and spam scanning tasks for f-secure anti-virus for internet mail and f-secure anti-virus for internet gateways. F-secure content scanner server scans files, e-mail message bodies and attachments for malicious code. You can ch...
Page 211
Chapter 7 211 administering f-secure content scanner server 7.2 configuring f-secure content scanner server this section explains how you can configure the 7.2.1 service connections you can specify how f-secure content scanner server should interact with f-secure for internet gateways and f-secure f...
Page 212
212 ip address specify the ip address that f-secure content scanner server listens to. If you do not assign any ip address (0.0.0.0), f-secure content scanner server responds to all connections. Tcp port specify the port number that f-secure content scanner server listens to for incoming connections...
Page 213
Chapter 7 213 administering f-secure content scanner server database updates f-secure content scanner server can notify the administrator if it detects that virus definition databases are outdated. You can change the notification settings in f-secure content scanner server / settings / database upda...
Page 214
214 figure 7-2 database update settings poll automatically specify whether f-secure content scanner server should poll automatically for the virus definition database updates. The polling interval is determined by f-secure management agent/settings/ communications/protocols//incoming packages pollin...
Page 215
Chapter 7 215 administering f-secure content scanner server notify when databases become old select whether an alert should be sent to the administrator when the virus definitions databases become older than the specified time limit. The options available are: disabled, send informational alert, sen...
Page 216
216 7.3 configuring scanning settings with the scanning settings you can specify, for example, how different types of archives are scanned, and configure security related settings such as how password protected archives are handled. 7.3.1 virus scanning go to f-secure content scanner server / settin...
Page 217
Chapter 7 217 administering f-secure content scanner server click reset statistics to reset the statistics for the scan engines. Version displays the version of the scan engine. Custom settings displays the custom settings for the scan engine. Excluded extensions specify a space-separated list of fi...
Page 218
218 suspect max nested archives specify what f-secure content scanner server should do with archive files the nesting level of which exceeds the value specified in max levels in nested archives. Treat as safe - archives are scanned to the specified level and allowed to pass through if no infections ...
Page 219
Chapter 7 219 administering f-secure content scanner server there is a security risk associated with password protected archives because their content cannot be inspected without a password that is known only to the sender and (in most of the cases) the recipient. If the recipients do not have any v...
Page 220
220 7.3.2 spam filtering the number of spam scanner instances can be configured in f-secure content scanner server / settings / spam filtering. Figure 7-4 spam filtering settings number of spam scanner instances specify the number of spam scanner instances to be created and used for spam analysis. A...
Page 221
Chapter 7 221 administering f-secure content scanner server you might need to modify this setting if you enable realtime blackhole lists (dnsbl/ rbl) for spam filtering. For more information, see “ enabling realtime blackhole lists ”, 248 and “ optimizing f-secure spam control performance ”, 250. Th...
Page 222
222 7.3.3 threat detection the virus outbreak and spam threat detection can be configured in f-secure content scanner server / settings / threat detection engine. Vod cache size specify the maximum number of patterns to cache for the virus outbreak detection service. By default, the cache size is 10...
Page 223
Chapter 7 223 administering f-secure content scanner server proxy configuration specify proxy server parameters that content scanner server uses when it connects to the threat detection center. Heuristic scanning - f-secure content scanner server checks the message using spam heuristics. Trusted net...
Page 224
224 7.3.4 advanced the advanced f-secure content scanner settings can be configured in f-secure content scanner server / settings / advanced. Figure 7-5 advanced settings working directory specify the path to the working directory where the product will create temporary files. Important: this settin...
Page 225
Chapter 7 225 administering f-secure content scanner server working directory clean interval temporary files are usually deleted automatically during processing. However, in some instances (for example, when a transaction is dropped, or a file transfer is cancelled by a user) temporary files can be ...
Page 226
226 7.4 configuring and viewing statistics this section describes how to configure and view the virus and spam statistics. 7.4.1 configuring virus statistics f-secure internet gatekeeper can display a summary list of the viruses that have been found most often in the scanned traffic. Under the f-sec...
Page 227
Chapter 7 227 administering f-secure content scanner server 7.4.2 viewing virus and spam statistics with f-secure internet gatekeeper web console you can view virus and spam statistics with f-secure policy manager console or f-secure internet gatekeeper web console. For instructions on how to log in...
Page 228
228 figure 7-7 a summary of scanning statistics in f-secure internet gatekeeper web console status status displays whether f-secure content scanner server is currently running or not. Start time displays the start date and time of f-secure content scanner server. Scanned files shows the number of fi...
Page 229
Chapter 7 229 administering f-secure content scanner server click start to start f-secure content scanner server and stop to stop f-secure content scanner server. Click reset statistics to reset the statistics displayed on this page. Database update version displays the version of the virus definiti...
Page 230
230 virus statistics you can see the list of most active viruses on the summary > virus statistics pagein f-secure internet gatekeeper web console. Figure 7-8 virus statistics in f-secure internet gatekeeper web console most active viruses (top 10) displays a top 10 listing of the viruses that have ...
Page 231
Chapter 7 231 administering f-secure content scanner server for information on how to configure the virus statistics list, see “ configuring virus statistics ”, 226. Spam scanner statistics on the summary > spam scanner statistics pagein f-secure internet gatekeeper web console you can see the spam ...
Page 232
232 scan engines you can see the status of all scan engines on the scan engines > properties page of f-secure internet gatekeeper web console. Figure 7-10 scan engine statuses and statistics in f-secure internet gatekeeper web console.
Page 233
Chapter 7 233 administering f-secure content scanner server status displays the status of the scan engine. The possible statuses are: unknown - this status might be displayed right after installation when the product statistics are not yet updated, or in centrally managed environments when f-secure ...
Page 234
234 click disable engine to stop a scan engine. Click enable engine to start a scan engine that is currently not running. Click reset statistics to reset the statistics of the currently selected scan engine. Disinfected files displays the number of infected files the selected scan engine has success...
Page 235
Chapter 7 235 administering f-secure content scanner server 7.4.3 viewing virus and spam statistics with f-secure policy manager console total scanning statistics in f-secure policy manager you can see a summary of the scanning statistics under f-secure content scanner server / statistics / server b...
Page 236
236 virus statistics in f-secure policy manager console you can see the list of most active viruses under the f-secure content scanner server / statistics / virus statistics / most active viruses branch. Figure 7-12 virus statistics in f-secure policy manager console for explanations for these stati...
Page 237
Chapter 7 237 administering f-secure content scanner server spam control statistics in f-secure policy manager console you can see the spam statistics under the f-secure content scanner server / statistics / spam control branch. Figure 7-13 spam control statistics in f-secure policy manager console ...
Page 238
238 scan engines in f-secure policy manager console you can see the status of the scan engines under the f-secure content scanner server / statistics / scan engines branch. Figure 7-14 scan engine statuses and statistics in f-secure policy manager console for explanations for these statistics, see “...
Page 239
Chapter 7 239 administering f-secure content scanner server 7.5 monitoring logs this section explains how you can monitor the logs generated by f-secure content scanner server. 7.5.1 logfile.Log f-secure content scanner server does not have a separate log of its own. Instead, it logs all events in l...
Page 240
240 8 a dministering f-s ecure s pam c ontrol introduction............................................................................... 241 spam control settings.............................................................. 242 realtime blackhole list configuration....................................
Page 241
Chapter 8 241 administering f-secure spam control 8.1 introduction when f-secure spam control is enabled, incoming messages that are considered spam are marked automatically by adding an x-header with the spam flag or predefined text in the message header. The end users can then create filtering rul...
Page 242
242 8.2 spam control settings change the settings in f-secure anti-virus for internet mail / settings / inbound mail / spam control to configure howf-secure anti-virus for internet mail scans incoming mail for spam. These settings are used only if f-secure spam control is installed with the product....
Page 243
Chapter 8 243 administering f-secure spam control when the heuristic spam analysis is enabled, all messages that the threat detection engine does not classify as spam are further analyzed for spam. When the heuristic spam analysis is disabled, only the threat detection engine scans inbound mails for...
Page 244
244 action on spam messages specify the action to take with e-mail messages considered spam. Pass through - e-mail messages considered spam are marked as specified by the add-x header and modify spam message subject settings and delivered to designated recipient(s). Quarantine - e-mail messages cons...
Page 245
Chapter 8 245 administering f-secure spam control add x-header with spam flag specifies if the spam flag will be added to the mail as a x-spam-flag header in the following format: x-spam-flag: crlf where is either "yes" or "no". Yes - the mail is considered spam. No - the mail is not considered spam...
Page 246
246 forward spam messages to e-mail address specifies the e-mail address where e-mail messages considered spam will be forwarded to if the action on spam messages setting is set to forward. The address should be specified in "local-part@domain" format, e.G. Abuse@example.Com. Max message size specif...
Page 247
Chapter 8 247 administering f-secure spam control blocked recipients specify the list of e-mail recipients whose incoming messages are always treated as spam. When specifying sender and recipient addresses, use the username@example.Com format. You can use wildcards. The match is not case sensitive. ...
Page 248
248 8.3 realtime blackhole list configuration this section describes how to enable and disable realtime blackhole lists, how to optimize f-secure spam control performance. 8.3.1 enabling realtime blackhole lists the product supports dns blackhole list (dnsbl), also known as realtime blackhole list (...
Page 249
Chapter 8 249 administering f-secure spam control 5. Find the sample configuration file fssc_example.Cfg in f-secure spam control installation directory: \spam control\fssc_example.Cfg 6. Copy the file to the same directory with the name fssc.Cfg 7. Open fssc.Cfg in a text editor (like windows notep...
Page 250
250 to force f-secure spam control to use a specific dns server, do the following: 1. Right-click the my computer icon and select properties. 2. Select advanced and click the environment variables.. Button. 3. In the system variables panel click new.. . 4. In the new system variable dialog specify t...
Page 251
251 9 a dministering f-s ecure m anagement a gent f-secure management agent settings .................................... 252 configuring alert forwarding.................................................... 254.
Page 252
252 9.1 f-secure management agent settings f-secure management agent enforces the security policies set by the administrator. It handles all management functions on the local workstations and provides a common interface for all f-secure applications. And operates within the policy-based management i...
Page 253
Chapter 9 253 administering f-secure management agent file sharing http communication directory path the path to the communication directory hierarchy. This must be specified as a unc path (for example, \\server\commdir). Do not use mapped drive letters (for example, s:\commdir). Incoming packages p...
Page 254
254 9.2 configuring alert forwarding in f-secure policy manager you can configure alert forwarding by editing the alert forwarding table, which is located under f-secure management agent / settings / alerting. Figure 9-1 alert forwarding table in f-secure policy manager console incoming packages pol...
Page 255
Chapter 9 255 administering f-secure management agent you can specify where an alert is sent according to its severity level. You can send an alert to any of the following: f-secure policy manager console nt event viewer e-mail snmp. If you choose to forward alerts to smtp, you will need to specify ...
Page 256
256 configuring alert forwarding with f-secure management agent you can configure alert forwarding in stand-alone mode using f-secure management agent. To open f-secure management agent, double-click the f-secure settings and statistics icon in the windows system tray. Select f-secure management age...
Page 257
Chapter 9 257 administering f-secure management agent if you choose to forward alerts to an e-mail address (smtp), you have to specify the e-mail address of the recipient and the mail server you want to use. Select e-mail (smtp) and click properties to specify smtp settings. Figure 9-4 e-mail recipi...
Page 258
258 10 q uarantine m anagement introduction............................................................................... 259 configuring quarantine options............................................... 260 searching the quarantined content......................................... 260 query result...
Page 259
Chapter 10 259 quarantine management 10.1 introduction you can manage and search quarantined mails with the f-secure internet gatekeeper web console. You can search for quarantined content by using different search criteria, including the quarantine id, recipient and sender address, the time period ...
Page 260
260 for more information on the sql servers recommended for different environments, see “ which sql server to use for the quarantine database? ”, 45. Quarantine storage the quarantine storage where the quarantined messages are stored is located on the server where f-secure internet gatekeeper is ins...
Page 261
Chapter 10 261 quarantine management figure 10-1 quarantine query page.
Page 262
262 you can use the following search criteria: quarantine id enter the quarantine id of a quarantined message. The quarantine id is displayed in the notification sent to the user about the quarantined message. Reason select the quarantining reason from the drop-down menu. The following options are a...
Page 263
Chapter 10 263 quarantine management you can use the sql wildcards in searches in the reason details, sender, recipients, subject, message id and host/ip address fields. For more information, see “ using wildcards ”, 264. Sender enter the e-mail sender address. You can only search for one address at...
Page 264
264 click query to start the search. The quarantine query results page is displayed once the query is completed. If you want to clear all the fields on the query page, click reset . Using wildcards you can use the following sql wildcards in the quarantine queries: e-mails to be reprocessed and relea...
Page 265
Chapter 10 265 quarantine management 10.4 query results page figure 10-2 quarantine query results page the quarantine query results page displays a list of e-mails that were found in the query. To view detailed information about a quarantined e-mail, click the view... Link in the details column. For...
Page 266
266 you can select an operation to perform on the messages that were found in the query: click reprocess to scan the currently selected e-mail again, or click reprocess all to scan all e-mail messages that were found. For more information, see “ reprocessing the quarantined content ”, 268. Click rel...
Page 267
Chapter 10 267 quarantine management 10.5 viewing details of a quarantined message to view the details of a quarantined message, do the following: 1. On the query search results page, click the view... Link in the details column. 2. The quarantined content details page opens. Figure 10-3 quarantined...
Page 268
268 it displays the following information about the quarantined message: quarantine id (qid) submit date - the date and time when the item was placed in the quarantine. Processing server - the f-secure anti-virus for internet mail server that processed the message. Envelope sender - the address of t...
Page 269
Chapter 10 269 quarantine management 1. Select the f-secure anti-virus for internet mail tab and the quarantine page. 2. Select the start and end dates and times of the quarantining period from the start time: and end time: drop-down menus. 3. If you want to specify how the search results are sorted...
Page 270
270 1. Select the f-secure anti-virus for internet mail tab and the quarantine page. 2. Enter the quarantine id of the message in the quarantine id field. 3. Click query . 4. When the query is finished, the query results page is displayed. Click the release button to release the displayed quarantine...
Page 271
Chapter 10 271 quarantine management 10.8 removing the quarantined content quarantined messages are removed from the quarantine based on the currently configured quarantine retention and cleanup settings. For an example on how to configure those settings, see “ deleting old quarantined content autom...
Page 272
272 3. Select the category for which you want to specify the exception, for example infected, from the quarantine category drop-down menu. 4. Specify a retention period that is shorter than the default value, for example 1 day, in the retention period column. 5. Specify a cleanup interval that is sh...
Page 273
Chapter 10 273 quarantine management 10.10 quarantine database settings you can specify the database where information about quarantined e-mails is stored and from which it is retrieved. For more information refer to the product support pages at http://support.F-secure.Com/enu/corporate/ 10.11 quara...
Page 274
274 figure 10-4 quarantine > statistics page e-mail messages and infected, suspicious and disallowed attachments are stored and counted as separate items in the quarantine storage. For example, if a message has three attachments and only one of them has been found infected, two items will be created...
Page 275
275 11 s ecurity and p erformance introduction............................................................................... 276 optimizing security................................................................... 276 optimizing performance............................................................
Page 276
276 11.1 introduction after you have configured basic settings and you are sure that f-secure internet gatekeeper is running properly, you can modify settings to optimize security and performance. 11.2 optimizing security for maximum security, you should remove all unnecessary system services, file ...
Page 277
Chapter 11 277 security and performance 11.2.2 access control f-secure anti-virus for internet gateways should allow outbound connections only from the intranet hosts. To specify which hosts are allowed to connect to f-secure anti-virus for internet gateways, see “ connections to f-secure anti-virus...
Page 278
278 keep the connection alive if the network has only a few clients and the server load is small, you can increase keep alive timeout and maximum keep alive requests values to optimize the performance. If f-secure internet gatekeeper has many clients, the server load increases and keep alive timeout...
Page 279
Chapter 11 279 security and performance concurrent transactions you can optimize the performance on a multiprocessor system by increasing the number of concurrent transactions. For more information, see “ service connections ”, 211. Number of ports in use if necessary, you can enhance the performanc...
Page 280
280 12 u pdating v irus and s pam d efinition d atabases overview................................................................................... 281 automatic updates ................................................................... 281 configuring automatic updates...............................
Page 281
Chapter 12 281 updating virus and spam definition databases 12.1 overview it is of the utmost importance that virus definition databases are kept up-to-date. F-secure internet gatekeeper takes care of this task automatically. If database update fails, it is strongly recommended to update the databas...
Page 282
282 12.3 configuring automatic updates f-secure automatic update agent user interface provides information about downloaded virus and spam definition updates. To access the f-secure automatic update agent user interface, open the f-secure internet gatekeeper web console, and select the automatic upd...
Page 283
Chapter 12 283 updating virus and spam definition databases 12.3.1 summary figure 12-1 automatic update agent summary in f-secure internet gatekeeper web console.
Page 284
284 the status page displays information on the latest update. Status displays the current status of f-secure automatic update agent. Version displays the version number of f-secure automatic update agent. Channel name the channel from where the updates are downloaded. Channel address the address of...
Page 285
Chapter 12 285 updating virus and spam definition databases downloads figure 12-2 automatic update agent downloads in f-secure internet gatekeeper web console the downloads page displays downloaded and installed update packages..
Page 286
286 12.3.2 automatic updates figure 12-3 automatic update settings in f-secure internet gatekeeper web console specify the how the product connects to f-secure update server..
Page 287
Chapter 12 287 updating virus and spam definition databases edit general settings to select whether you want to use automatic updates and how often the product checks for new updates. Automatic updates enable and disable the automatic virus definition updates. By default, automatic updates are enabl...
Page 288
288 server failover time define (in hours) the failover time to connect to f-secure policy manager server or f-secure policy manager proxy. If the product cannot connect to any user-specified update server during the failover time, it retrieves the latest virus definition updates from f-secure updat...
Page 289
Chapter 12 289 updating virus and spam definition databases 12.3.3 policy manager proxies figure 12-4 policy manager proxy settings in f-secure internet gatekeeper web console edit the list of virus definition database update sources and f-secure policy manager proxies. If no update servers are conf...
Page 290
290 1. Click add to add the new entry to the list. 2. Enter the url of the update source in the proxy address field. 3. Edit the priority of the update source. The priority numbers are used to define the order in which the host tries to connect servers. Virus definition updates are downloaded from t...
Page 291
291 13 t roubleshooting testing the connections ....................................................... 292 starting and stopping f-secure internet gatekeeper components......................................................................... 294 frequently asked questions .............................
Page 292
292 13.1 testing the connections if you have a problem that is not covered here, see “ technical support ”, 409, for instructions on how to get more information. 13.1.1 checking that f-secure anti-virus for internet gateways is up and running you can test that the product is running by opening http:...
Page 293
Chapter 13 293 troubleshooting 13.1.3 checking that f-secure content scanner server is up and running you can test if the product is running by opening a telnet connection to the f-secure content scanner server machine to the port 18971 (if you have specified a different fnp/scip port, use that port...
Page 294
294 13.2 starting and stopping f-secure internet gatekeeper components to start or stop f-secure anti-virus for internet gateways: open the f-secure internet gatekeeper web console and select the anti-virus for internet gateways tab. Click stop to stop f-secure anti-virus for internet gateways and c...
Page 295
Chapter 13 295 troubleshooting 13.3 frequently asked questions all support issues, frequently asked questions and hotfixes can be found under the support pages at http://support.F-secure.Com/ . For more information, see “ technical support ”, 409..
Page 296
296 a appendix: warning messages http warning messages ........................................................ 297 smtp warning messages........................................................ 298.
Page 297
Appendix a 297 warning messages a.1 http warning messages the following table lists variables that can be included in the warning message that is shown to users when they try to download a file that contains malicious code or a file that is blocked. These variables are dynamically replaced by their ...
Page 298
298 a.2 smtp warning messages the following table lists variables that can be included in the warning message sent by f-secure internet gatekeeper if an infection is found or an attachment is stripped from a scanned message. These variables are dynamically replaced by their actual names. If an actua...
Page 299
Appendix a 299 warning messages the following table lists variables that can be included in the scan report, in other words the variables that can be used in the warning message between $report-begin and $report-end. A.3 virus outbreak notification messages the following table lists variables that c...
Page 300
300 b appendix: specifying hosts introduction............................................................................... 301 domain ..................................................................................... 301 subnet ......................................................................
Page 301
Appendix b 301 specifying hosts b.1 introduction you can specify a host or group of hosts in f-secure anti-virus for internet gateways with a domain, subnet, ip address or hostname. B.2 domain a domain is a partially qualified dns domain name, preceded by a period. It represents a list of hosts whic...
Page 302
302 examples: the subnet 192.168.0.0 with an implied netmask of 16 valid bits (sometimes used in the netmask form 255.255.0.0) 192.168 the subnet 192.168.112.0/21 with a netmask of 21 valid bits (also used in the netmask form 255.255.248.0) 192.168.112.0/21 a subnet with 32 valid bits is the equival...
Page 303
Appendix b 303 specifying hosts hostname comparisons are case insensitive, and hostnames are always assumed to be anchored in the root of the dns tree. Therefore, hosts “www.Example.Com” and “www.Example.Com.” (note the trailing period) are considered to be equal. Usually it is more effective to spe...
Page 304
304 c appendix: access log variables list of access log variables..................................................... 305.
Page 305
Appendix c 305 access log variables c.1 list of access log variables you can use the following variables in the access log: format string description %a the remote ip address. %a the local ip address. %b bytes sent, excluding http headers. When no bytes are sent, the value is ‘0’. %b bytes sent in c...
Page 306
306 %{example}o the contents of ‘example’: header line(s) in the reply. %p the canonical port of the server serving the request. %p the process id of the child that serviced the request. %q the query string. If the query string exists, a ‘?’ is added to the beginning, otherwise an empty string is us...
Page 307
Appendix c 307 access log variables the following notes can be used in the %....N format, for example: %{fsfilter::action}n : note description {fsfilter::scanresult} the value is the result of the file scan infected - the file contained malicious code. Clean - the file was clean. Suspicious - the fi...
Page 308
308 trusted - the client or the site was trusted. Error - there was an error while processing the request. See the error log for more information. Abort - the client closed the connection unexpectedly. {fsfilter::infection} the value is the name of the infection if the file is infected. If the file ...
Page 309
309 d appendix: mail log variables list of mail log variables.......................................................... 310
Page 310
310 d.1 list of mail log variables you can use the following macros to specify what kind of information is collected from different events in the f-secure anti-virus for internet mail mail log. Macro for which events description $datetime all the date and time when the event occurred $event all even...
Page 312
312 e appendix: configuring mail servers configuring the network........................................................... 313 configuring mail servers .......................................................... 314.
Page 313
Appendix e 313 configuring mail servers e.1 configuring the network inbound, outbound and internal e-mail should be routed to f-secure internet gatekeeper where they are scanned and sent back to the original mail server. The original mail server delivers e-mail onwards. Dns configuration if the orig...
Page 314
314 f-secure anti-virus for internet mail configuration specify the hosts that belong to your organization. For more information, see “ intranet hosts ”, 164. Configure f-secure anti-virus for internet mail to connect to the new ip address or host name of the original mail server. For more informati...
Page 315
Appendix e 315 configuring mail servers to change the smtp port number in lotus domino r4: 1. Open the notes.Ini used by the lotus domino server (by default c:\winntotes.Ini). 2. Change the setting smtpmta_ipport to a port other than 25 (for example 26). If the smtpmta_ipport setting does not exis...
Page 316
316 to change the smtp port number in ms exchange 2000: 1. Start the exchange system manager from the start menu. 2. Open the servers / {current server} / protocols / smtp branch..
Page 317
Appendix e 317 configuring mail servers 3. Open the properties window of default smtp virtual server. 4. Click advanced . 5. Select the line that has smtp port number 25 and click edit ..
Page 318
318 6. Change the tcp port to some other unused port, for example 26. 7. Click ok for all the windows and reboot the server..
Page 319
319 f appendix: advanced deployment options introduction....................................................................... 320 transparent proxy ............................................................ 320 http load balancing ....................................................... 329 load ...
Page 320
320 f.1 introduction if you want to provide a reliable and easy http scanning service in your network with f-secure internet gatekeeper, you should use a transparent proxy. For information about different methods that you can use when setting up a transparent proxy, see transparent proxy . Below. If...
Page 321
Appendix f 321 advanced deployment options want to configure a transparent proxy if you want all clients to use the proxy server without any changes in web browser configurations and if you want to make sure that all clients use the proxy server. One method that you can use to configure a transparen...
Page 322
322 f.2.1 examples the following examples provide very basic steps to enable http transparent proxy. When you make changes in firewall configurations, make sure that you do not compromise the system security. It is recommended to test the transparent proxy on a test system before it is taken into pr...
Page 323
Appendix f 323 advanced deployment options 4. Click ok . Step 2. 1. Open the isa management console. 2. Open servers and arrays > extensions > application filters. 3. Right-click http redirector filter and select properties. 4. Select options and make sure that redirect to local web proxy service is...
Page 324
324 5. Click ok . Step 3. 1. Open the isa management console. 2. Open servers and arrays > network configuration > routing. 3. Right-click default rule and select action. 4. Enable routing them to a specified upstream server..
Page 325
Appendix f 325 advanced deployment options 5. For the primary route, set the ip address and the port number that f-secure internet gatekeeper is configured to listen for incoming connections. For the backup route, select the one which is the most appropriate for you..
Page 326
326 6. Click ok . Transparent proxy with microsoft isa server 2004 example: 1. Open the isa management console 2. Open arrays > [servername] > configuration > networks. 3. Select the web chaining tab. 4. Right-click the last default rule and select properties . 5. Select the action tab. Enable the r...
Page 327
Appendix f 327 advanced deployment options 6. Select settings . 7. Specify the server ip address and the port number where f-secure internet gatekeeper is configured to listen for incoming connections. Make sure the automatically poll upstream server for the configuration setting is deselected. 8. C...
Page 328
328 benefits does not require expensive software or hardware components. Open source. The system may run on any hardware. Drawbacks may be difficult to configure. No graphical user interface. Examples an example using "ipchains" (linux 2.2) # /sbin/ipchains -a input -d 0/0 80 -p tcp -j redirect 3128...
Page 329
Appendix f 329 advanced deployment options http://www.Freebsd.Org/doc/en_us.Iso8859-1/books/handbook/ firewalls.Html f.2.3 transparent proxy with cisco, nortel and lucent benefits professional transparent proxy support. Easy to integrate. Drawbacks requires additional software and hardware. Requires...
Page 330
330 f.3.1 round-robin dns based load balancing figure f-2 f-secure anti-virus for internet gateways deployed with round-robin dns based load balancing clients have to configure web browsers to use a http proxy. A domain name server (dns) server resolves the name of the proxy server to its ip address...
Page 331
Appendix f 331 advanced deployment options drawbacks the dns server does not know if one of the proxy servers has degraded performance or if it is completely unavailable. If one server fails, the dns round robin continues to send traffic to the failed server and as a result, clients can receive "ser...
Page 332
332 example of java script auto-configuration file can be found here: http://wp.Netscape.Com/eng/mozilla/2.0/relnotes/demo/proxy-live.Html you can find more information about hash-based proxy auto-configuration scripts from the sharp super proxy script page. With hash-based proxy auto-configuration ...
Page 333
Appendix f 333 advanced deployment options f.3.3 load balancing with proxy or firewall figure f-4 f-secure anti-virus for internet gateways deployed with http proxy clients have to configure web browsers to use a http proxy. If the upstream proxy is transparent, clients do not require any configurat...
Page 334
334 microsoft isa server (formerly ms proxy) http://www.Microsoft.Com/isaserver/ http://www.Microsoft.Com/isaserver/techinfo/ planning/isa2000caching.Doc netscape proxy server http://wp.Netscape.Com/proxy/v3.5/ http://wp.Netscape.Com/proxy/v3.5/ evalguide/advantages.Html check point firewall-1 and c...
Page 335
Appendix f 335 advanced deployment options f.3.4 hardware and software load-balancing solutions network address translation (nat) figure f-5 f-secure anti-virus for internet gateways deployed with network address translation (nat) direct-path routing figure f-6 f-secure anti-virus for internet gatew...
Page 336
336 benefits supports several load-balancing models (for example round-robin, least connections, weighted round-robin) proxying on the tcp/ip level. Capable of performing osi layer 2 to 7 load balancing. Can be implemented transparently with a non-transparent proxy, so no configuration changes need ...
Page 337
Appendix f 337 advanced deployment options f.3.5 load balancing and high availability with clustering figure f-7 f-secure anti-virus for internet gateways deployed with clustering clients access a cluster, a virtual server. Nodes in a cluster communicate among themselves and provide high-availabilit...
Page 338
338 benefits provides true dynamic load balancing across the cluster to optimize the use of all available resources. Users are protected during the scheduled shut-downs, when individual servers are taken off-line for maintenance or upgrades. The product is installed on a node. Drawbacks requires som...
Page 339
Appendix f 339 advanced deployment options f.4 load balancing with windows network load balancing service load balancing between multiple instances of f-secure internet gatekeeper can be implemented with a network load balancing service, which is included in windows server 2003. The network load bal...
Page 340
340 f.4.2 setting up network load balancing services the network load balancing service is included in all windows 2003 server versions, but is has to be installed and configured before it can be used. Configuring tcp/ip and network load balancing settings all settings should be identical for all se...
Page 341
Appendix f 341 advanced deployment options in this example, we use the following values: ip address:192.168.0.231 netmask:255.255.255.0 gateway:192.168.0.1 dns server:192.168.0.10 all other computers connected to the local area network connect to the cluster with address 192.168.0.233. In networks t...
Page 342
342 4. Add the cluster address as the second ip address in the advanced options. (in our case 192.168.0.233) 5. Use the following settings in network load balancing:.
Page 343
Appendix f 343 advanced deployment options use the multicast communication mode. 6. The remote control is not necessary and it can be disabled. 7. Use an individual ip address for each different server. Each server should have a different host identifier number (priority)..
Page 344
344 8. Change the affinity to none. Otherwise the default settings are fine. 9. You can use different settings, just make sure that all settings are identical on all servers. 10. After you have configured tcp/ip and network load balancing settings, check that the cluster is working..
Page 345
Appendix f 345 advanced deployment options checking the status of the cluster 1. Open the network load balancing manager from the administrative tools to administer the cluster and individual nodes. 2. Select cluster > connect to existing to connect to the cluster..
Page 346
346 3. Enter the address of the cluster and click connect . 4. Make sure that the log window at the bottom of the window does not contain any error messages and all servers have green icons without exclamation marks. 5. The status should be converged. 6. After you have made sure that the cluster wor...
Page 347
Appendix f 347 advanced deployment options 3. Edit each file in each server so that you know which server in the cluster sent the page to the browser. For example: change files on other servers in the same way but use a different ip address. Checking the status of the cluster after you have installe...
Page 348
348 1. Set the ip address of the cluster as the proxy address of the web browser n 2. Enter http://192.168.0.233:3128 in the web browser and open the page. 3. Refresh the page several times and if everything is working properly, you can see that each server in the cluster returns the correct page..
Page 349
Appendix f 349 advanced deployment options f.5 deployment scenarios for environments with multiple sub-domains f.5.1 scenario 1: f-secure anti-virus for internet mail as an upstream mail transfer agent figure f-8 f-secure anti-virus for internet mail deployed as an upstream mail transfer agent.
Page 350
350 environment: f-secure anti-virus for internet mail is installed on the host smtp.My.Intranet instead of the original mail transfer agent. No changes are needed in dns. The dns mx records point my.Sub1.Domain and my.Sub2.Domain to the smtp.My.Intranet host (or to the host running the firewall). A...
Page 351
Appendix f 351 advanced deployment options inbound mail delivery options are configured as follows: the use dns mx records setting in f-secure anti-virus for internet mail / settings / inbound mail / delivery is disabled. The mail routing table contains the following entries: outbound mail delivery ...
Page 352
352 f.5.2 scenario 2: f-secure anti-virus for internet mail as interim mail transfer agent figure f-9 f-secure anti-virus for internet mail deployed as an interim mail transfer agent.
Page 353
Appendix f 353 advanced deployment options environment: f-secure anti-virus for internet mail is installed on a host named smtp.My.Intranet. The original mail transfer agent remains on the original computer, but the host name is changed to something else, for example mx.My.Intranet. The configuratio...
Page 354
354 inbound mail delivery options are configured as follows: the use dns mx records setting in f-secure anti-virus for internet mail / settings / inbound mail / delivery is disabled. The mail routing table contains the following entries: outbound mail delivery options are configured as follows: the ...
Page 355
Appendix f 355 advanced deployment options drawbacks: firewall configuration needs to be changed. A separate host is required for installing f-secure anti-virus for internet mail. The configuration of the original/upstream mail transfer agent needs to be changed. Internal e-mail inside sub-domains i...
Page 356
356 f.5.3 scenario 3: f-secure anti-virus for internet mail for each sub-domain figure f-10 f-secure anti-virus for internet mail installed on a separate computer for each sub-domain.
Page 357
Appendix f 357 advanced deployment options a note about deploying quarantine management in this type of environment you need to decide whether f-secure anti-virus for internet mail installed in each sub-domain uses its own quarantine database, or if all f-secure anti-virus for internet mail installa...
Page 358
358 f-secure anti-virus for internet mail configuration: • f-secure anti-virus for internet mail is configured to accept incoming connections on port 25 from smtp.My.Intranet host and the end-user workstations belonging to my.Sub1.Domain only. • add end-user workstations that belong to my.Sub1.Domai...
Page 359
Appendix f 359 advanced deployment options drawbacks: you need to do multiple installations of f-secure anti-virus for internet mail to be made and administered. (to facilitate administration, deploy f-secure policy manager and manage f-secure anti-virus for internet mail instances via fspm console....
Page 360
360 g appendix: services and processes list of services and processes ................................................ 361.
Page 361
Appendix g 361 services and processes g.1 list of services and processes the followings tables list the services and processes that are running on the system after the installation. F-secure anti-virus for internet gateways f-secure anti-virus for internet mail service process description f-secure a...
Page 362
362 f-secure content scanner server f-secure quarantine manager f-secure internet gatekeeper web console service process description f-secure content scanner server daemon fsavsd.Exe the back-end component that provides anti-virus scanning and spam filtering services for simple content inspection pr...
Page 363
Appendix g 363 services and processes f-secure management agent service process description f-secure management agent fsma32.Exe the service starts and monitors integrated services and applications. F-secure network request broker fnrb32.Exe the service handles the communication with f-secure policy...
Page 364
364 f-secure automatic update agent service process description f-secure automatic update agent fsaua.Exe the service retrieves updates from f-secure policy manager or f-secure update server..
Page 365
365 h appendix: error codes introduction............................................................................... 366 f-secure anti-virus for internet gateways............................... 366 f-secure anti-virus for internet mail ........................................ 374 f-secure content...
Page 366
366 h.1 introduction this appendix describes error codes and messages of f-secure anti-virus for internet gateways (table h.2 on page 366), f-secure anti-virus for internet mail (table h.3 on page 374) and f-secure content scanner server (table h.4 on page 391). H.2 f-secure anti-virus for internet ...
Page 367
Appendix h 367 error codes 101 info module stopping %1 stopping... During product shutdown. The alert contains the name of the module that is stopping. No actions are required. 102 info module started %1 started. During product shutdown. The alert contains the name of the module that has been stoppe...
Page 368
368 110 fatal error unable to register in message broker the registration in f-secure message broker failed due to error: %1. During product startup or restart. Check that f-secure management agent is correctly installed and running. Product restart or system reboot can help to solve this. 111 fatal...
Page 369
Appendix h 369 error codes 120 error unable to open file the file '%1' cannot be opened due to error: %2. If the product cannot open or create the file in question. The alert contains the reason for the failure. Check the reason for the failure and act accordingly. Also, make sure that there is enou...
Page 370
370 130 info settings changed the following settings have been changed: %1. Product settings have been changed from f-secure policy manager console or the web console. The alert contains the list of settings that have been changed. No actions are required. 131 error policy read failed reading policy...
Page 371
Appendix h 371 error codes 141 fatal error invalid magic database the magic database file '%1' is invalid or corrupted. Intelligent file type recognition is disabled. The magic database signature check failed, either the file has been forged or the file has been changed without updating the signatur...
Page 372
372 305 security disallowed content blocked the following file/page has been blocked: request: %1 source: %2 destination: %3 file size: %4 bytes reason: %5 the content was blocked according to current content blocking settings. Check the reason reported in the alert. Consider changing the content bl...
Page 373
Appendix h 373 error codes 405 security evaluation license expires soon the evaluation license will expire in %1 days. Your network remains protected against viruses and other malicious code. The alert is sent every day during the evaluation period until the evaluation license expires or the product...
Page 374
374 h.3 f-secure anti-virus for internet mail id severity trap message when/why solution 1 error unsuccessful file read an error occurred while trying to read the file %1. During product operation. Product cannot read from file. Make sure the file in question exists and the product has sufficient ac...
Page 375
Appendix h 375 error codes 105 error loading module failed module %1 (%2) could not be loaded. %3 the quarantine manager cannot load or initialize the plug-in for f-secure anti-virus for internet mail. Check that the fqmavim.Dll module exists in f-secure anti-virus for internet mail installation dir...
Page 376
376 115 info statistics reset statistics were reset. Product statistics have been reset from f-secure policy manager console or the web console. No actions are required. 120 error read settings failed could not read the settings, using the default or the latest settings. Settings have been changed b...
Page 377
Appendix h 377 error codes 128 error configuration handler unreachable the configuration handler is unreachable. The software cannot receive the updated policy. The product cannot contact f-secure configuration handler, a component of f-secure management agent. Check that f-secure management agent i...
Page 378
378 181 warning quarantine directory near max capacity the volume containing the quarantine directory is near its maximum capacity. Space available on the disk is %1 megabytes. Delete some files to free space. The disk is getting full. Free some disk space or consider moving the quarantine folder to...
Page 379
Appendix h 379 error codes 210 error server unreachable cannot connect to the %1 f-secure content scanner server on %2 due to %3. F-secure anti-virus for internet mail cannot connect to f-secure content scanner server (check the error code). Make sure that f-secure content scanner server is up and r...
Page 380
380 235 error address binding unsuccessful cannot bind to the address to listen for incoming connections on '%1:%2'. Another process is probably using the address. F-secure anti-virus for internet mail could not bind the socket. Check that there are no other programs or services using the same port ...
Page 381
Appendix h 381 error codes 243 fatal error loopback detected the tcp/ip address and port of the mail server is the same as the address and port that the agent is listening on. This means that the agent will send processed messages to itself. Check the settings and make sure the address and/or port n...
Page 382
382 246 warning bounced message trashed sending bounced message was unsuccessful. The bounce message was trashed. Sender: %1 recipient: %2 subject: %3 message id: %4 spool id: %5 reason: %6 message could not be bounced probably because it had a bad sender address. Check that the inbound/ outbound ma...
Page 383
Appendix h 383 error codes 251 error cannot send mail there was an error while trying to send mail to the mta at '%1'. The message was spooled as %2. F-secure anti-virus for internet mail failed to send e-mail. It will continue trying to send the e-mail for a few days (according to settings). Make s...
Page 384
384 263 error scan result not received receiving scan result from the %1 f-secure content scanner server on %2 was unsuccessful while processing spool job '%3', attachment '%4'. Error occurred: %5. F-secure anti-virus for internet mail could not receive the scan result from f-secure content scanner ...
Page 385
Appendix h 385 error codes 277 fatal error disk full volume containing the spool directory '%1' is full. The disk is full. Free more disk space immediately. F-secure anti-virus for internet mail needs a few megabytes in order to process mails and start sending mails from the spool. 280 error disasse...
Page 386
386 310 security virus alert: infected malicious code found in the message: sender: %1 recipient: %2 subject: %3 message id: %4 file name: %5 file size: %6 bytes scan result: %7 action: dropped when a file is found infected on scanning. See below. 311 security virus alert: disinfected malicious code...
Page 387
Appendix h 387 error codes 350 security disallowed attachment disallowed attachment found in the mail: sender: %1 recipient: %2 subject: %3 message id: %4 spool id: %5 attachment name: %6 attachment size: %7 bytes reason: %8 action: %9 quarantined: %10 f-secure anti-virus for internet mail has found...
Page 388
388 400 security evaluation license expired your evaluation license has expired. Inbound and outbound mail traffic are no longer scanned for viruses and other malicious code. To continue using the product after the evaluation period, you will need a new license keycode. If you wish to stop using the...
Page 389
Appendix h 389 error codes 450 error write file error the file '%1' cannot be written to due to %2. The product cannot write data to the file in question. The alert contains the reason for the failure. Check the reason for the failure and act accordingly. 460 error remove file error the file '%1' ca...
Page 390
390 500 error quarantine database unreachable cannot connect to the quarantine database (%1) on %2 due to error: %3. The quarantine manager failed to reprocess, release or delete a quarantined item from the quarantine database, or failed to switch to a new sql server because the sql server is not av...
Page 391
Appendix h 391 error codes h.4 f-secure content scanner server id severity trap message when/why solution 3 error directory access denied the directory %1 could not be accessed. Log, spool, quarantine or installation directory cannot be accessed make sure that the product has sufficient rights to ac...
Page 392
392 110 error quarantine failed could not quarantine due to error %1. File name: %2, file size:%3, scan result: %4, source: %5, destination: %6, protocol: %7, agent: %8 during a quarantine operation. Act according to the reason for the failure. For example, if there is not enough disk space, free so...
Page 393
Appendix h 393 error codes 180 fatal error unable to start f-secure quarantine manager f-secure quarantine manager cannot be started. During startup. Restart the product. 190 fatal error unable to start f-secure anti-virus f-secure anti-virus cannot be started due to error: %1. Alert not used in thi...
Page 394
394 250 warning working directory near max capacity volume containing the working directory is at or near its maximum capacity. You may need to delete some files manually. The disk space is running out on the partition that hosts the working directory. Free some disk space. You might consider deleti...
Page 395
Appendix h 395 error codes 303 warning not enough disk space to update virus definition database file(s) cannot be updated, not enough disk space during database update. Free some disk space. 304 info scanning operation temporarily disabled scanning operation has been temporarily disabled to take ne...
Page 396
396 331 info database update finished the virus database update process has finished. The database update process has finished. If the "database files updated" alert follows this error code, it indicates that the database update operation was completed successfully. Otherwise, the database update wa...
Page 397
Appendix h 397 error codes 400 info database integrity verified successfully the integrity of database update %1 has been successfully verified. The product verifies the integrity of virus definition or spam scanner database updates before taking them into use. The alert is sent if verification is s...
Page 398
398 410 error database verification: module not available database updates cannot be accepted by the product because the database verification module is not available or it has been corrupted. Please reinstall the product or contact technical support to resolve the problem. The product installation ...
Page 399
Appendix h 399 error codes 416 error database verification: no matching manifest file certificate the manifest file does not have a matching certificate: %1. The manifest file has not been signed using the private key whose respective public key is present in the certificate file included in the upd...
Page 400
400 423 security database verification: certificate privilege error the publisher's certificate in the package does not express the right to publish database updates: %1. The database update package includes a publisher's certificate without the authority to publish database updates. See above. 430 ...
Page 401
Appendix h 401 error codes 510 error ungraceful message pump quit quit the message pump with error: %1. Unexpected problem during product operation. Usually this alert can be ignored. If the alert is continuously reported, try to restart the product or reboot the system. 520 fatal error unable to re...
Page 402
402 540 error unable to open file file '%1' cannot be opened due to error: %2. If a component cannot open or create the file in question. The alert contains the reason for the failure. Check the reason for the failure and act accordingly. If you see this alert frequently, increase the directory clea...
Page 403
Appendix h 403 error codes 666 error undefined error undefined error occurred. During product operation. Occurs rarely. Contact f-secure technical support. 777 info debug %1 during product operation. Normally used in debug or special product binaries. 1001 info started listening: authenticated mode ...
Page 404
404 1200 security unauthorized agent a request from an unauthorized ip-address (%1) was received. The request was rejected. When the authorized agents setting is defined. A connection from an unauthorized agent has been attempted and has been rejected. Check the ip address reported in the alert and ...
Page 405
Appendix h 405 error codes 1206 error unable to send response sending response to the agent was unsuccessful. Error: %1. If the content provider cannot send the validation response to the agent. Check that the remote agent is up and running. Make sure the product is not overloaded. If the loading is...
Page 406
406 1211 error no registered processor there are no registered processors for the agent: %1. The request from the agent rejected. If the content processor for the agent in question did not register with the content provider. The problem occurs if the content processor is not installed or fails to st...
Page 407
Appendix h 407 error codes 2002 security virus alert: infected malicious code found in: agent:%8 transaction: %1 protocol: %2 source: %3 destination: %4 file name: %5 file size: %6 bytes scan result: %7 action: dropped when a file is found infected on scanning. See above (id 2001). 2003 security vir...
Page 408
408 2010 error assembling failed assembling of transaction content after processing could not be performed. Agent: %7 transaction: %1 protocol: %2 source: %3 destination: %4 file name: %5 file size: %6 bytes when the product fails to assemble the modified content after processing. The format of the ...
Page 409
409 technical support introduction............................................................................... 410 f-secure online support resources........................................ 410 web club.................................................................................. 412 virus des...
Page 410
410 introduction f-secure technical support is available through f-secure support web pages, e-mail and by phone. Support requests can be submitted through a form on f-secure support web pages directly to f-secure support. F-secure online support resources f-secure support web pages for any f-secure...
Page 411: ›
Technical support 411 1. Log in to the web console. 2. Type https://127.0.0.1:25023/fsdiag/ in the browser’s address field. 3. The f-secure diagnostics tool starts and the dialog window displays the progress of the data collection. 4. When the tool has finished collecting the data, click get report ...
Page 412
412 web club the f-secure web club provides assistance and updated versions of f-secure products. To connect to the web club on our web site, open the web club page of any f-secure internet gatekeeper component, and click web club on the web club tab of the general property page. Alternatively, righ...
Page 413
About f-secure corporation f-secure corporation protects consumers and businesses against computer viruses and other threats from the internet and mobile networks. We want to be the most reliable provider of security services in the market. One way to demonstrate this is the speed of our response. A...
Page 414
414.