- DL manuals
- F-SECURE
- Other
- POLICY MANAGER 7.0 -
- Administrator's Manual
F-SECURE POLICY MANAGER 7.0 - Administrator's Manual
Summary of POLICY MANAGER 7.0 -
Page 1
F-secure policy manager 7.0 administrator’s guide.
Page 2
"f-secure" and the triangle symbol are registered trademarks of f-secure corporation and f-secure product names and symbols/logos are either trademarks or registered trademarks of f-secure corporation. All product names referenced herein are trademarks or registered trademarks of their respective co...
Page 3
Iii contents about this guide 9 overview ............................................................................................................................ 10 how this guide is organized ............................................................................................ 11 convent...
Page 4
Iv 3.4 configuring f-secure policy manager server............................................................ 51 3.4.1 changing the communication directory path ................................................ 51 3.4.2 changing the ports where the server listens for requests............................
Page 5
V 6.5.3 local installation and updates with pre-configured packages.................... 129 6.5.4 information delivery...................................................................................... 133 6.6 managing policies ........................................................................
Page 6
Vi chapter 9 f-secure policy manager on linux 171 9.1 overview .................................................................................................................. 172 9.1.1 differences between windows and linux .................................................... 172 9.1.2 supported d...
Page 7
Vii 10.6 web reporting error messages and troubleshooting ............................................. 196 10.6.1 error messages ............................................................................................ 196 10.6.2 troubleshooting......................................................
Page 8
Viii appendix e nsc notation for netmasks 228 e.1 overview ................................................................................................................. 229 technical support 231 overview ...............................................................................................
Page 9
9 a bout t his g uide overview.................................................................................... 10 how this guide is organized..................................................... 11.
Page 10
About this guide 10 overview f-secure policy manager provides tools for administering the following f-secure software products: f-secure client security f-secure internet gatekeeper f-secure vpn+ f-secure anti-virus for workstations firewalls file servers microsoft exchange mimesweeper:.
Page 11
11 how this guide is organized the f-secure policy manager administrator’s guide is divided into the following chapters. Chapter 1. Introduction . Describes the architecture and components of the policy-based management. Chapter 2. System requirements . Defines the software and hardware requirement ...
Page 12
About this guide 12 chapter 12. Troubleshooting . Contains troubleshooting information and frequently asked questions. Appendix a. Snmp support . Contains information about snmp support. Appendix b. Ilaunchr error codes . Contains a list of ilaunchr error codes. Appendix c. Fsii remote installation ...
Page 13
13 conventions used in f-secure guides this section describes the symbols, fonts, and terminology used in this manual. Symbols ⇒ an arrow indicates a one-step procedure. Fonts arial bold (blue) is used to refer to menu names and commands, to buttons and other items in a dialog box. Arial italics (bl...
Page 14
14 courier new bold is used for information that you must type. Small caps ( black ) is used for a key or key combination on your keyboard. Arial underlined (blue) is used for user interface links. Arial italics is used for window and dialog box names. Pdf document this manual is provided in pdf (po...
Page 15
15 1 i ntroduction overview..................................................................................... 16 installation order ........................................................................ 18 features ...................................................................................
Page 16
Chapter 1 16 introduction 1.1 overview f-secure policy manager provides a scalable way to manage the security of numerous applications on multiple operating systems, from one central location. It can be used to keep security software up-to-date, manage configurations, oversee enterprise compliance, ...
Page 17
17 f-secure policy manager server is the repository for policies and software packages distributed by the administrator, and status information and alerts sent by the managed hosts. It provides scalability by working as an extension to the apache web server. Communication between f-secure policy man...
Page 18
Chapter 1 18 introduction the local workstations and provides a common interface for all f-secure applications, and operates within the policy-based management infrastructure. Vpn+ certificate wizard is an application for creating certificates for f-secure vpn+. 1.2 i nstallation order to install f-...
Page 19
19 1.3 f eatures software distribution first-time installation on windows domains with f-secure push installation. Updating of executable files and data files, including virus definition databases. Support for policy-based updates. Policies force the f-secure management agent to perform updates on a...
Page 20
Chapter 1 20 introduction p erformance management statistics and performance data handling and reporting. T ask management management of virus scanning tasks and other operations. 1.4 p olicy-based management a security policy is a set of well-defined rules that regulate how sensitive information an...
Page 21
21 default policy files the default policy file contains the default values (the factory settings) for a single product that are installed by the setup. Default policies are used only on the host. If neither the base policy file nor the incremental policy file contains an entry for a variable, then ...
Page 22
Chapter 1 22 introduction 1.4.1 m anagement information base the management information base (mib) is a hierarchical management data structure used in the simple network management protocol (snmp). In f-secure policy manager, the mib structure is used for defining the contents of the policy files. E...
Page 23
23 traps traps are the messages (including alerts and events) that are sent to the local console, log file, remote administration process, etc. The following types of traps are sent by most of the f-secure products: info. Normal operating information from a host. Warning. A warning from the host. Er...
Page 24
24 2 s ystem r equirements f-secure policy manager server ............................................... 25 f-secure policy manager console............................................. 27.
Page 25
25 2.1 f-secure policy manager server in order to install f-secure policy manager server, your system must meet the following minimum requirements: operating system: microsoft windows: microsoft windows 2000 server (sp 3or higher); windows 2000 advanced server (sp 3or higher); windows server 2003, s...
Page 26
Chapter 2 26 system requirements memory: 256 mb ram when web reporting is enabled, 512 mb ram. Disk space: disk space: 200 mb of free hard disk space; 500 mb or more is recommended. The disk space requirements depend on the size of the installation. In addition to this it is recommended to allocate ...
Page 27
27 2.2 f-secure policy manager console in order to install f-secure policy manager console, your system must meet the following minimum requirements: operating system: microsoft windows: microsoft windows 2000 professional (sp3 or higher) windows 2000 server (sp3 or higher) windows 2000 advanced ser...
Page 28
Chapter 2 28 system requirements disk space: 100 mb of free hard disk space. Display: minimum 256-color display with resolution of 1024x768 (32-bit color with 1280x960 or higher resolution recommended). Network: ethernet network interface or equivalent. 10 mbit network between console and server is ...
Page 29
29 3 i nstalling f-s ecure p olicy m anager s erver overview..................................................................................... 30 security issues ........................................................................... 31 installation steps ........................................
Page 30
Chapter 3 30 installing f-secure policy manager server 3.1 overview f-secure policy manager server is the link between f-secure policy manager console and the managed hosts and acts as the repository for policies and software packages distributed by the administrator, as well as status information a...
Page 31
31 the information stored by f-secure policy manager server includes the following files: policy domain structure. Policy data, which is the actual policy information attached to each policy domain or host. Base policy files generated from the policy data. Status information, including incremental p...
Page 32
Chapter 3 32 installing f-secure policy manager server a document containing advice on how to secure an installation of the apache web server is available at http://www.Apache.Org/docs/misc/ security_tips.Html. And a list of vulnerabilities at http://www.Apacheweek.Com/features/security-13 . 3.2.1 i...
Page 33
33 allowed full administrative rights. Multiple users can keep a read-only session open simultaneously, monitoring the system status without affecting other administrators or managed hosts in any way. 2. To enable easy migration to new management keys, it is possible to re-sign the policy domain str...
Page 34
Chapter 3 34 installing f-secure policy manager server 2. Access to f-secure policy manager server will be limited only to the separately defined ip addresses by editing the httpd.Conf file. Below is an example of edited httpd.Conf file section: #fsmsa listen listen 8080 localhost only #fsmsa port o...
Page 35
35 as an alternative, f-secure policy manager console and f-secure policy manager server can be installed on the same machine, and access limited to the localhost. Remote administrator access to the f-secure policy manager console can be arranged by using a secure remote desktop product. Installing ...
Page 36
Chapter 3 36 installing f-secure policy manager server below is an example of edited httpd.Conf file section, in which access is allowed from the localhost and from one separately defined ip address: #web reporting listen listen 8081 # web reporting port: jkmount /* ajp13 errordocument 500 "policy m...
Page 37
37 3.3 installation steps to install f-secure policy manager server, you need physical access to the server machine. Step 1. 1. Insert the f-secure cd in your cd-rom drive. 2. Select corporate use . Click next to continue. 3. Go to the install or update managed software menu and select f-secure poli...
Page 38
Chapter 3 38 installing f-secure policy manager server step 3. Read the license agreement information. If you agree, select i accept this agreement . Click next to continue..
Page 39
39 step 4. Select the type of installation: typical - setup installs the product with default options: f-secure policy manager server, f-secure policy manager console, f-secure policy manager update server & agent are installed on the same computer. The default ports are used for f-secure policy man...
Page 40
Chapter 3 40 installing f-secure policy manager server step 5. If you are installing on a clean computer, select the following components: f-secure policy manager server, f-secure policy manager update server & agent - automate virus definition database updates, f-secure installation packages - sele...
Page 41
41 step 6. Choose the destination folder. Click next. It is recommended to use the default installation directory. If you want to install f-secure policy manager server in a different directory, you can use the browse feature. Warning: if you have f-secure management agent installed in the same mach...
Page 42
Chapter 3 42 installing f-secure policy manager server step 7. Setup requests confirmation if a previous installation of f-secure policy manager exists. 1. If yes , select i have existing f-secure policy manager installation . Enter the communication directory path of the installed f-secure policy m...
Page 43
43 step 8. Select whether you want to keep the existing settings or change them. By default the setup keeps the existing settings. Select this option if you have manually updated the f-secure policy manager server configuration file ( httpd.Conf ). This option automatically keeps the existing admini...
Page 44
Chapter 3 44 installing f-secure policy manager server step 9. Select the f-secure policy manager server modules to enable: host module is used for communication with the hosts. The default port is 80. Administration module is used for communication with f-secure policy manager console. The default ...
Page 45
45 click next to continue..
Page 46
Chapter 3 46 installing f-secure policy manager server step 10. Select to add product installation package(s) from the list of available packages (if you selected f-secure installation packages in step 4 on page 17). Click next..
Page 47
47 step 11. Setup displays the components that will be installed. Click next..
Page 48
Chapter 3 48 installing f-secure policy manager server step 12. When the setup is completed, the setup shows whether all components were installed successfully..
Page 49
49 step 13. F-secure policy manager server is now installed. Restart the computer if you are prompted to do so. Click finish to complete the installation..
Page 50
Chapter 3 50 installing f-secure policy manager server step 14. To determine if your installation was successful, open a web browser in the machine where f-secure policy manager server was installed, enter http://localhost:80 (if you used the default port number during the installation) and press en...
Page 51
51 3.4 configuring f-secure policy manager server under the conf\ directory in the policy manager server installation directory, you will find a file named httpd.Conf, which contains the configuration information for f-secure policy manager server. 3.4.1 changing the communication directory path if ...
Page 52
Chapter 3 52 installing f-secure policy manager server 5. Start the f-secure policy manager server service. 6. Check that everything still works. 7. Delete the old commdir files. 3.4.2 changing the ports where the server listens for requests there are two directives that define the ports for both of...
Page 53
53 the directive, which is associated with f-secure policy manager server admin module. Here is that directive’s default configuration: #fsmsa port sethandler fsmsa-handler to associate it with the newly selected port, change the statement to: #new fsmsa port sethandler fsmsa-handler 3.4.3 f-secure ...
Page 54
Chapter 3 54 installing f-secure policy manager server timeout: this directive defines the period of time that the server will wait before closing a connection, when there is no outbound or inbound traffic in the network connection. Loadmodule: this directive defines the symbolic name of the module ...
Page 55
55 policy manager server; for example, has two virtual hosts, one running in port 80 (f-secure policy manager server host module) and another one running in port 8080 (fsmsa or admin module). Here is the default configuration for f-secure policy manager server: # fsmsh port sethandler fsmsh-handler ...
Page 57
57 'x' = connection aborted before the response completed. '+' = connection may be kept alive after the response is sent. '-' = connection will be closed after the response is sent. 5. F-secure policy manager server admin module error code (0 for success). 6. Bytes transferred to the server (“-” for...
Page 58
Chapter 3 58 installing f-secure policy manager server for more information on the settings you can read the httpd.Sample file that is located in the same directory as the configuration file of f-secure policy manager server (\conf). Mod_gzip_on yes: this setting is one of the several compression se...
Page 59
59 3. The f-secure uninstall dialog box appears. Click start to begin uninstallation. 4. When the uninstallation is complete, click close . 5. Click ok to exit add/remove programs . 6. Reboot your computer for changes to take effect..
Page 60
60 4 c omm d ir m igration introduction................................................................................. 61 instructions ................................................................................. 61.
Page 61
61 4.1 introduction in f-secure policy managerrelease 6.0 and onwards the use of communication directory (commdir) instead of f-secure policy manager server is not supported. Therefore you must upgrade the commdir based installations to f-secure policy manager server installations. This chapter cont...
Page 62
Chapter 4 62 commdir migration 3. After you have located the backup, a confirmation dialog is displayed. Click ok to proceed. Step 3. Connect policy manager console to the new policy manager server 1. Connect the f-secure policy manager console to the new f-secure policy manager server. 2. Configure...
Page 63
63 step 4. Configure connections to old commdir 1. Connect f-secure policy manager console to the old commdir. 2. Configure the correct f-secure policy manager server address to use: select the settings tab and open the centralized management page. Enter the address of f-secure policy manager server...
Page 64
64 5 i nstalling f-s ecure p olicy m anager c onsole overview..................................................................................... 65 installation steps ........................................................................ 65 uninstalling f-secure policy manager console .............
Page 65
65 5.1 overview f-secure policy manager console can operate in two modes: administrator mode - you can use f-secure policy manager console to its full extent. Read-only mode - you can view f-secure policy manager console information but cannot perform any administrative tasks (this mode is useful fo...
Page 66
Chapter 5 66 installing f-secure policy manager console step 2. View the welcome screen, and follow the setup instructions. Select the installation language from the drop-down menu. Click next to continue..
Page 67
67 step 3. Read the license agreement information. If you agree, select i accept this agreement . Click next to continue..
Page 68
Chapter 5 68 installing f-secure policy manager console step 4. Select the type of installation: typical - setup installs the product with default options: f-secure policy manager server, f-secure policy manager console, f-secure policy manager update server & agent are installed on the same compute...
Page 69
69 step 5. Select the following components to be installed: f-secure policy manager console f-secure vpn+ certificate wizard (optional, required only for f-secure vpn+ management) click next to continue..
Page 70
Chapter 5 70 installing f-secure policy manager console step 6. Choose the destination folder. Click next . It is recommended to use the default installation directory. Use the browse feature to install f-secure policy manager console in a different directory..
Page 71
71 step 7. Specify f-secure policy manager server address, and administration port number. Click next to continue..
Page 72
Chapter 5 72 installing f-secure policy manager console step 8. Review the changes that setup is about to make. Click next to continue..
Page 73
73 step 9. By default the setup will run the f-secure policy manager console for the first time immediately after the cd setup has been run. It is important to run the console after the setup, because some connection properties will be collected during the initial console startup. Click finish to la...
Page 74
Chapter 5 74 installing f-secure policy manager console step 10. If you did not choose to launch f-secure policy manager console immediately after the setup has finished, you can find the shortcut from start > programs > f-secure policy manager console > f-secure policy manager console . When f-secu...
Page 75
75 step 11. Select your user mode according to your needs: administrator mode - enables all administrator features. Read-only mode - allows you to view administrator data, but no changes can be made. If you select read-only mode , you will not be able to administer hosts. To change to administrator ...
Page 76
Chapter 5 76 installing f-secure policy manager console step 12. Enter the address of the f-secure policy manager server that is used for communicating with the managed hosts..
Page 77
77 step 13. Enter the path where the administrator’s public key and private key files will be stored. By default, key files are stored in the f-secure policy manager console installation directory: program files\f-secure\administrator . Click next to continue. If the key-pair does not pre-exist, it ...
Page 78
Chapter 5 78 installing f-secure policy manager console step 14. Move your mouse cursor around in the window to initialize the random seed used by the management key-pair generator. Using the path of the mouse movement ensures that the seed number for the key-pair generation algorithm has enough ran...
Page 79
79 step 15. Enter a passphrase, which will secure your private management key. Re-enter your passphrase in the confirm passphrase field. Click next ..
Page 80
Chapter 5 80 installing f-secure policy manager console step 16. Click finish to complete the setup process. F-secure policy manager console will generate the management key-pair..
Page 81
81 after the key-pair is generated, f-secure policy manager console will start..
Page 82
Chapter 5 82 installing f-secure policy manager console f-secure policy manager console starts in anti-virus mode, which is a optimized user interface for managing f-secure client security and f-secure anti-virus for workstations. If you are going to use f-secure policy manager console for managing ...
Page 83
83 certain directories and files should be protected by setting their permissions to allow access only by administrators. To achieve this, do the following: 1. Remove all unnecessary access rights to the \ fsa subdirectory. Only the administrator who is running f-secure policy manager console should...
Page 84
84 6 u sing f-s ecure p olicy m anager c onsole overview..................................................................................... 85 f-secure policy manager console basics ................................. 86 f-secure client security management..................................... 104 ma...
Page 85
85 6.1 overview f-secure policy manager console is a remote management console for the most commonly used f-secure security products, designed to provide a common platform for all of the security management functions required in a corporate network. An administrator can create different security pol...
Page 86
Chapter 6 86 using f-secure policy manager console the administrator has access to the administration private key. This private key is stored as a file, which may be shared among users with management rights. The administrator uses f-secure policy manager console to define policies for different dom...
Page 87
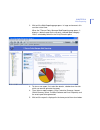
87 6.2.1 logging in when you start f-secure policy manager console, the following dialog box will open (click options to expand the dialog box to include more options) figure 6-1 f-secure policy manager console login dialog the dialog box can be used to select defined connections. Each connection ha...
Page 88
Chapter 6 88 using f-secure policy manager console connection properties the link to the data repository is defined as the http url of the f-secure policy manager server. Figure 6-2 connection properties dialog the name field specifies what the connection will be called in the connection: field in t...
Page 89
89 icon in the domain tree and they will appear in the disconnected hosts list in the domain status view. The domain tree notification icons can be switched off from advanced options . Note that it is possible to define an interval that is shorter than one day by simply typing in a floating point nu...
Page 90
Chapter 6 90 using f-secure policy manager console disable. Disable all polling disables all of the polling items. Whether or not automatic polling is disabled, manual refresh operations can be used to refresh the selected view. Figure 6-4 polling periods dialog see “ preferences ” , 149 for more in...
Page 91
91 figure 6-5 f-secure policy manager console user interface 6.2.3 policy domain pane in the policy domain pane, you can do the following: add a new policy domain (click the icon, which is located on the toolbar). A new policy domain can be created only when a parent domain is selected. Add a new ho...
Page 92
Chapter 6 92 using f-secure policy manager console after selecting a domain or host, you can access the above options from the edit menu. The domains referred to in the commands are not windows nt or dns domains. Policy domains are groups of hosts or subdomains that have a similar security policy. 6...
Page 93
93 6.2.5 product view pane the function of the product view pane changes according to which tab of the properties pane is open: policy tab - in the product view pane, you can set the value of a policy variable. All modifications affect the selected policy domain or host. There is a predefined editor...
Page 94
Chapter 6 94 using f-secure policy manager console using help in most cases the product view fields offer the same help texts as the mib tree nodes. In addition, each tab has it's own help text. The help texts follow mouse clicks (all tabs and policy and status editors) and field focus (only availab...
Page 95
95 figure 6-6 product view pane using the context menu for policy settings most editor fields in the product view include a context menu (activated by right-clicking your mouse). The context menu contains the following options: go to, clear value, force value and show domain values . Figure 6-7 cont...
Page 96
Chapter 6 96 using f-secure policy manager console shortcut to the mib tree node sometimes it is convenient to see what setting of the mib tree is actually changed when modifying some specific product view item. Select the go to menu item to display the corresponding mib tree node in the properties ...
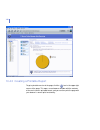
Page 97
97 figure 6-8 show domain values dialog viewing status open the status tab and select the product from the properties pane. F-secure policy manager console will render a product view to the product view pane, where you can view the more important local settings and statistics. For the policy domains...
Page 98
Chapter 6 98 using f-secure policy manager console disconnected. If the reason is clear, for example, if the host's f-secure software has been uninstalled, the host can be deleted normally. After investigating one disconnected host, the most convenient way to get back to the previously selected doma...
Page 99
99 figure 6-11 the status of a component displayed in the product view pane 6.2.6 messages pane f-secure policy manager console logs messages in the message pane about different events. Unlike the alerts and reports panes, message pane events are generated only by f-secure policy manager console. Th...
Page 100
Chapter 6 100 using f-secure policy manager console 6.2.7 the toolbar the toolbar contains buttons for the most common f-secure policy manager console tasks. Saves the policy data distributes the policy go to the previous domain or host in the domain tree selection history. Go to the next domain or ...
Page 101
101 starts push installation to windows hosts. Imports autoregistered hosts to the currently selected domain. Green signifies that the host has sent an autoregistration request. Displays available installation packages. Updates the virus definition database. Displays all alerts. The icon is highligh...
Page 102
Chapter 6 102 using f-secure policy manager console 6.2.8 menu commands menu command action file new creates a new policy data instance with the management information base (mib) defaults. This command is rarely needed because existing policy data will usually be modified and saved using the save as...
Page 103
103 status bar displays the status bar. Tooltips displays on-screen descriptions of buttons when the mouse pointer rests on them. Embedded restriction editors toggles between the embedded restriction editor and the restrictions dialog box. Messages shows/hides the messages pane at bottom of screen. ...
Page 104
Chapter 6 104 using f-secure policy manager console 6.3 f-secure client security management in f-secure policy manager 5.50 and later there is a new separate graphical user interface for managing f-secure client security and f-secure anti-virus for workstations. The new user interface is optimized f...
Page 105
105 if you have designed the policy domain structure beforehand, you can import the hosts directly to that structure. If you want to get started quickly, you can also import all hosts to the root domain first, and create the domain structure later, when the need for that arises. The hosts can then b...
Page 106
Chapter 6 106 using f-secure policy manager console a third possibility is to group the hosts into subdomains based on the installed f-secure client security version. You could, for example, group hosts that have f-secure client security 6.X installed into one sub-domain, and hosts that have f-secur...
Page 107
107 6.4.2 adding hosts the main methods of adding hosts to your policy domain, depending on your operating system, are as follows: import hosts directly from your windows domain. Import hosts through autoregistration (requires that f-secure management agent be installed on the imported hosts). You c...
Page 108
Chapter 6 108 using f-secure policy manager console figure 6-16 import autoregistered hosts dialog > autoregistered hosts tab the autoregistration view offers a tabular view to the data which the host sends in the autoregistration message. This includes the possible custom autoregistration propertie...
Page 109
109 autoregistration import rules figure 6-17 import autoregistered hosts dialog > import rules tab you can define the import rules for the autoregistered hosts on the import rules tab in the import autoregistered hosts window. You can use the following as import criteria in the rules: wins name, dn...
Page 110
Chapter 6 110 using f-secure policy manager console 192.1.2.3 ) and ip sub-domain matching (for example: 10.15.0.0/16 ). You can hide and display columns in the table by using the right-click menu that opens when you right-click any column heading in the import rules window. Only the values in the c...
Page 111
111 if you want to create several rules for a domain, you can use the clone option. Start by creating one rule for the domain. Then select the row and click clone . Now you can edit the criteria on the new duplicated row. When you want to start the import operation, select the autoregistered hosts t...
Page 112
Chapter 6 112 using f-secure policy manager console figure 6-18 an example of a domain with hosts and servers in their own sub-domains 6.4.3 host properties host names for the network can be ip addresses, domain names, or wins names. To view host properties, right-click on the appropriate host and f...
Page 113
113 the network name for the host is the name that the host uses internally in the network to access policies. Figure 6-19 host properties dialog in the platform tab, you can add the operating system of the host to the properties. Platform name is the name of the operating system. The operating syst...
Page 114
Chapter 6 114 using f-secure policy manager console the vpn+ tab is used only if you have f-secure vpn+ software. The vpn+ tab contains information about the host's vpn+ identity (used with ipsec connections). Automatic initialization of vpn+ identities vpn+ identities support automatic property upd...
Page 115
115 automatic initialization is useful when the original host properties do not contain information about vpn+ identities. For example, this can happen in the following scenario: the host is imported from a windows domain. (the f-secure management agent is installed remotely.) because vpn+ is not in...
Page 116
Chapter 6 116 using f-secure policy manager console installations, push installation features can be used to update or repair installations whenever the policy-based installations are not suitable. Policy-based installations - f-secure policy manager can initiate installation and update operations w...
Page 117
117 6.5.1 f-secure push installations the only difference between the autodiscover windows hosts and the push install to windows hosts features is how the target hosts are selected: autodiscover browses the windows domains and user can select the target hosts from a list of hosts, push install to wi...
Page 118
Chapter 6 118 using f-secure policy manager console 1. Select the policy domain for the hosts to which you will install f-secure management agent. 2. Open the edit menu and select autodiscover windows hosts (alternatively, click the button). 3. From the nt domains list, select one of the domains and...
Page 119
119 resolve hosts with all details (slower) with this selection, all details about the hosts are shown, such as the versions of the operating system and f-secure management agent. Resolve host names and comments only (quicker) if all hosts are not shown in the detailed view or it takes too much time...
Page 120
Chapter 6 120 using f-secure policy manager console push install to windows hosts to install: 1. Select the policy domain for the hosts to which you will install f-secure management agent. 2. Open the edit menu and select push install to windows hosts (alternatively, click the button). 3. Enter the ...
Page 121
121 1. Select the installation package, and click next to continue. 2. Select the products to install. You can choose to force reinstallation if applications with the same version number already exist. Click next to continue. 3. Choose to accept the default policy, or specify which host or domain po...
Page 122
Chapter 6 122 using f-secure policy manager console select either this account (the current account) or another account . This account — when you select “this account”, you will use the security rights of the account currently logged on. Use this option in the following cases: a. You are already log...
Page 123
123 when using a local administrator account, use format account. (do not enter the host name as part of the account, otherwise the account is accepted only by the host in question.) 5. Review the installation summary. To start the remote installation wizard, click start . The remote installation wi...
Page 124
Chapter 6 124 using f-secure policy manager console 6.5.2 policy-based installation base policy files are used to start installations on hosts that have f-secure management agent installed. F-secure policy manager console creates an operation-specific installation package, which it stores on the f-s...
Page 125
125 figure 6-21 installation editor the installation editor contains the following information about the products that are installed on your target policy domain or host: product name name of the product, which is either installed on a host or domain, or which can be installed with an available inst...
Page 126
Chapter 6 126 using f-secure policy manager console if a host is selected, the progress field displays one of the following messages: if a domain is selected, the progress field displays one of the following: when all required version numbers are selected, click start . The installation editor launc...
Page 127
127 distribution installation package that is customized for the specific installation operation. The new package is saved on f-secure policy manager server. Because the installation operation uses policy-based triggering, you must distribute new policy files. The policy file will contain an entry t...
Page 128
Chapter 6 128 using f-secure policy manager console remote uninstallation uninstallation can be performed as easily as an update. A distribution package is created that contains only the software needed to uninstall the product. If the product does not support remote uninstallation, the installation...
Page 129
129 6.5.3 local installation and updates with pre-configured packages you can export pre-configured packages in jar or in msi (microsoft installer) format. The msi packages can be distributed, for example, using windows group policy in active directory environment. The procedure for exporting in bot...
Page 130
Chapter 6 130 using f-secure policy manager console 3. Specify the file format, jar or msi , and the location where you want to save the customized installation package. Click export . 4. Specify the file location where you want to save the customized installation jar package. Click save . 5. Select...
Page 131
131 one example of how to utilize custom properties is to create a separate installation package for different organizational units, which should be grouped under unit-specific policy domains. The property name could be unit and the value is different in each installation package. Now hosts from eac...
Page 132
Chapter 6 132 using f-secure policy manager console ilaunchr .Jar where is replaced by the actual name of the jar package being installed. When the installation runs, the user will see a dialog displaying the installation progress. If a restart is required after the installation, the user is prompte...
Page 133
133 4. Add the following line to the login script: setup.Exe\silent /checkfsma if the parameter /checkfsma is not used, the installation will be run every time runsetup.Exe is executed. 6.5.4 information delivery all of the installation information is delivered as files through the f-secure policy m...
Page 134
Chapter 6 134 using f-secure policy manager console 6.6 managing policies this section describes how to configure and distribute policies. 6.6.1 settings to configure settings, browse the policy tree and change the values of the policy variables. There are two types of policy variables: (1) leaf nod...
Page 135
135 6.6.2 restrictions there are two types of restriction: access restrictions and value restrictions. Access restrictions are final and hidden . Final always forces the policy: the policy variable overrides any local host value, and the end user cannot change the value as long as the final restrict...
Page 136
Chapter 6 136 using f-secure policy manager console restrictions can be edited within the embedded product view pane, or in a separate dialog box. To toggle between these two choices, choose embedded restriction editors from the view menu. If embedded editors are switched off, the product view pane ...
Page 137
137 6.6.5 policy inheritance in f-secure policy manager console, each policy domain automatically inherits the settings of its parent domain, allowing for easy and efficient management of large networks. The inherited settings may be overridden for individual hosts or domains. When a domain's inheri...
Page 138
Chapter 6 138 using f-secure policy manager console figure 6-24 show domain values dialog if the subdomain or host values need to be reset to the current domain values, the force value operation can be used to clean the sub-domain and host values. You can also use the reporting tool to create inheri...
Page 139
139 index inheritance in tables when you clear a row in a table using the clear row button, the selected row is emptied. The result depends on the types of default rows defined in the parent domains and in mib as default rows. If a row exists that has the same index values as the cleared row, it wil...
Page 140
Chapter 6 140 using f-secure policy manager console 6.7 managing operations and tasks to launch an operation from f-secure policy manager console: 1. Select one of the actions from the selected product’s operations branch in the policy tab of the properties pane. 2. The following pane appears in the...
Page 141
141 6.8.1 viewing alerts and reports the hosts can send alerts and reports if there has been a problem with a program or an operation. When an alert is received, the button will brighten. To view the alerts, click . The alerts tab in the properties pane will open. All alerts received will be display...
Page 142
Chapter 6 142 using f-secure policy manager console when an alert is selected from the list, the product view pane displays more specific information about the alert. F-secure anti-virus scanning alerts may have an attached report. This report will also be in the product view pane. To view reports, ...
Page 143
143 figure 6-25 f-secure management agent>settings>alert forwarding . The same table can also be found in the f-secure management agent product view in the alert forwarding tab. You can specify where alerts are sent according to severity level. The target can be f-secure policy manager console, the ...
Page 144
Chapter 6 144 using f-secure policy manager console for troubleshooting, but if these alerts are enabled, the number of transmitted alerts will increase substantially. If you have a large domain structure, specifying strict alert-forwarding rules at the root domain level could flood f-secure policy ...
Page 145
145 figure 6-27 reporting tool 6.9.1 policy domain / host selector pane in the policy domain / host selector pane you can select the domains and/or hosts you are interested in from the reporting point of view. The domain selected in the policy domain pane is selected by default in the reporting tool...
Page 146
Chapter 6 146 using f-secure policy manager console 6.9.2 report type selector pane in the report type selector pane you can do the following: select the type of report to be made. Select the filtering by product (only information on selected products is included to the report to be made). The follo...
Page 147
147 6.9.3 report pane in the report pane, you can: select report type dependent configurations for the currently selected report type. With the report type dependent configurations, the user can adjust more filtering to the report to be made. Find description for the currently selected report type. ...
Page 148
Chapter 6 148 using f-secure policy manager console 6.9.4 bottom pane in the bottom pane, you can: reset the defaults to all user interface components. Launch the report exporting process. Launch the report viewing process. Stop the report generating process. Close the reporting tool user interface....
Page 149
149 figure 6-28 saving and exporting a report 6.10 preferences preference settings are either shared or applied to the specific connection..
Page 150
Chapter 6 150 using f-secure policy manager console 6.10.1 connection-specific preferences to edit these, select preferences from the tools menu. Only the current connection object is affected. Tab setting meaning communication polling periods polling periods for different package types. You can sel...
Page 151
151 disable initial status loading you can disable initial status loading if you want to reduce f-secure policy manager console startup time in a large environment (this is an advanced option that should be used with care, since it causes the following functional differences to the normal status han...
Page 152
Chapter 6 152 using f-secure policy manager console background reports loading see background alerts loading. Policy files policy file optimizations indentation defines if separation characters will be added to the file when it is being created, which would make it more human-readable. If you choose...
Page 153
153 6.10.2 shared preferences these apply to all connections defined in a particular installation of f-secure policy manager console. Browsing timeout important only if the hide already managed hosts option is in use. This is the maximum time allowed to access the host registry. Maximum concurrent n...
Page 154
Chapter 6 154 using f-secure policy manager console policy files products allows you to deactivate mibs for products which you do not have installed, and exclude them from the distributed policy files. Deactivating mibs reduces the size of the policy files sent to managed hosts. Warning: do not deac...
Page 155
155 7 m aintaining f-s ecure p olicy m anager s erver overview .......................................................................... 156 backing up & restoring f-secure policy manager console data ................................................................................. 156 replicating ...
Page 156
Chapter 7 156 maintaining f-secure policy manager server 7.1 overview f-secure policy manager server can be maintained by routinely backing up and restoring the console data in the server. 7.2 backing up & restoring f-secure policy manager console data it is highly recommended that you back up the m...
Page 157
157 to back up the management key-pair, copy the admin.Prv file and the admin.Pub file from the root of the local f-secure policy manager console installation directory. Keep the admin.Prv file stored in a secure place. It is very important to save a backup copy of the admin.Prv key file. If you wan...
Page 158
Chapter 7 158 maintaining f-secure policy manager server 5. Back up the lib\administrator.Properties file from the local f-secure policy manager console installation directory. 6. Restart f-secure policy manager server service. 7. Reopen the f-secure policy manager console management sessions. 8. Di...
Page 159
159 10. If you backed up only the policy domain structure (policy data and domain structure backup), restore it as follows: 11. Close all f-secure policy manager console management sessions and stop f-secure policy manager server service. 12. Delete the contents of the \fsa\domains directory. 13. Co...
Page 160
Chapter 7 160 maintaining f-secure policy manager server 4. Create the disk image file. 5. The utility program resets the unique id in the f-secure anti-virus installation. A new unique id is created automatically when the system is restarted. This will happen individually on each machine where the ...
Page 161
161 8 u pdating f-s ecure v irus d efinition d atabases automatic updates with f-secure automatic update agent. 162 using the automatic update agent....................................... 164 forcing the update agent to check for new updates immediately..................................................
Page 162
Chapter 8 162 updating f-secure virus definition databases 8.1 automatic updates with f-secure automatic update agent with f-secure automatic update agent, you are able to receive automatic updates and informational content without interrupting your work to wait for files to download from the web. F...
Page 163
163 in f-secure policy manager 6.0 and onwards, the automatic update agent installed with f-secure products tries to download the automatic updates from the configured update sources in the following order: a. If there are policy manager proxies in use in the company network, the client tries to con...
Page 164
Chapter 8 164 updating f-secure virus definition databases automated updates you don't have to look for the updates and manually download them. With f-secure automatic update agent, you will automatically get the virus definition updates when they have been published by f-secure. 8.2 using the autom...
Page 165
165 examples: http_proxies=http://proxy1:8080/,http://backup_proxy:8880/,http:// domain\username:usernamespassword@ntlmproxy.Domain.Com:80 step 3. Specify the polling interval the poll_interval directive specifies how often the f-secure automatic update agent checks for new updates.The default is 36...
Page 166
Chapter 8 166 updating f-secure virus definition databases [ 3988] thu oct 26 12:40:39 2006(3) : downloaded 'f-secure anti-virus update 2006-10-26_04' - 'dfupdates' version '1161851933' from fsbwserver.F-secure.Com, 12445450 bytes (download size 3853577) a brief explanation of what happened. When an...
Page 167
167 messages in fsaua.Log below are examples of some messages that you can find in the log file. Message meaning update check completed successfully the connection to the update source was successful. Update check completed successfully. No updates are available. The connection to the update source ...
Page 168
Chapter 8 168 updating f-secure virus definition databases what updates are logged in fsaua.Log? Below is a list of updates you can find in the log: 'f-secure anti-virus update 2006-10-24_01' - 'dfupdates' 'f-secure spam control update 2006-10-19_02' - 'scdb3' 'f-secure anti spyware update 2006-10-1...
Page 169
169 8.3 forcing the update agent to check for new updates immediately if you need to force f-secure automatic update agent to check for new updates immediately, you need to stop and restart the fsaua service. To do this, enter the following commands on command line: net stop fsaua net start fsaua th...
Page 170
Chapter 8 170 updating f-secure virus definition databases 8.5 troubleshooting below are some examples of problems that may be logged as error messages in the fsaua.Log file. Problem: there was a dns lookup failure, or connection failed, was lost or refused. Reason: network problems solution: check ...
Page 171
171 9 f-s ecure p olicy m anager on l inux overview................................................................................... 172 installation ................................................................................ 172 configuration ....................................................
Page 172
Chapter 9 172 f-secure policy manager on linux 9.1 overview f-secure policy manager can also be installed on linux. 9.1.1 differences between windows and linux services not available when f-secure policy manager console is running on linux: push installation features windows installer package (msi) ...
Page 173
173 1. F-secure automatic update agent 2. F-secure policy manager server 3. F-secure policy manager console 4. F-secure policy manager web reporting. F-secure policy manager server, f-secure policy manager web reporting and f-secure automatic update agent must all be installed on the same computer. ...
Page 174
Chapter 9 174 f-secure policy manager on linux 6. If you want to specify how often f-secure automatic update agent checks for new updates, enter a new polling interval value when the configuration script asks for it. The default is 3600 seconds, which is 1 hour. Once the configuration script is fini...
Page 175
175 9.2.3 installing f-secure policy manager console 1. Log in as root . 2. Open a terminal. 3. To install type: a new user group called fspmc is created automatically. Users must be added to the fspmc user group before they can run f-secure policy manager console: 4. Check which groups the user bel...
Page 176
Chapter 9 176 f-secure policy manager on linux the first time this command is entered, you will be prompted to answer a few questions to complete the configuration. These questions are the same as for the windows version (see “ installation steps ” , 65 ). 9.2.4 installing f-secure policy manager we...
Page 177
177 9.3 configuration f-secure policy manager components have separate configuration scripts. To configure each component type the corresponding configuration command and answer the questions. 9.4 uninstallation you must uninstall the four components in this order: 1. F-secure policy manager web rep...
Page 178
Chapter 9 178 f-secure policy manager on linux 9.4.2 uninstalling f-secure policy manager console 1. Log in as root . 1. Open a terminal. 2. Type: 9.4.3 uninstalling f-secure policy manager server 1. Log in as root . 2. Open a terminal. 3. Type: debian based distributions rpm based distributions dpk...
Page 179
179 9.4.4 uninstalling f-secure automatic update agent 1. Log in as root . 2. Open a terminal. 3. Type: # /opt/f-secure/fsaua/fsaua-config uninstall 4. Type: 9.5 frequently asked questions q. Why doesn't f-secure policy manager console start? A. Runtime errors and warnings are logged to: /opt/f-secu...
Page 180
Chapter 9 180 f-secure policy manager on linux q. How can i update the virus definition database manually? A. Run the updating tool by typing: sudo -u fspms /opt/f-secure/fspms/bin/fsavupd q. Why does f-secure policy manager server not distribute new virus definition databases? F-secure policy manag...
Page 181
181 locations of some files of special interest: q. How do i change the ports at which f-secure policy manager server listens for requests? A. See “ access to f-secure policy manager server will be limited only to the separately defined ip addresses by editing the httpd.Conf file. ” , 34 . Q. How ca...
Page 182
Chapter 9 182 f-secure policy manager on linux q. How can i configure f-secure automatic update agent to use f-secure policy manager proxy a. To use f-secure policy manager proxy: a. Open the file /opt/f-secure/fsaua/etc/fsaua_config with a text editor b. Add the line update_proxies=host:port to the...
Page 183
183 q. How can i restart f-secure automatic update agent after changing the configuration file? A. To restart f-secure automatic update agent, type: /etc/init.D/fsaua restart.
Page 184
184 10 w eb r eporting overview................................................................................... 185 introduction............................................................................... 185 web reporting client system requirements ........................... 186 generating a...
Page 185
185 10.1 overview this chapter contains an introduction to f-secure policy manager web reporting and its features instructions how to generate and view web reports instructions how to configure and maintain the f-secure policy manager web reporting application; for example, how to restrict or give a...
Page 186
Chapter 10 186 web reporting incremental policy files ( .Ipf ). You can configure how long the data is stored in the web reporting database and in this way also optimize the database performance. 10.3 web reporting client system requirements in order to view the reports generated by f-secure policy ...
Page 187
187 compare the page in the cache to the page on the network every time i view the page. Select this if you want netscape to compare a web page to the cache every time you view it. When the page is out of date. Select this if you want netscape to compare a web page to the cache when the page is dete...
Page 188
Chapter 10 188 web reporting 2. Wait until the web reporting page opens. In large environments this can take a lot of time. When the f-secure policy manager web reporting page opens, it displays a default report for the currently selected report category. Root is selected by default in the policy do...
Page 189
189 10.4.3 creating a printable report to get a printable version of the page, click the icon in the upper right corner of the page. This opens a new browser window with the contents of the main frame in printable format, and you can then print the page with your browser’s normal print functionality...
Page 190
Chapter 10 190 web reporting you can also save the report for later use with your browser’s save as or save page as options. You should make sure that the save option used saves the complete web page, including images: if you are using microsoft internet explorer 6, first select save as from the fil...
Page 191
191 10.5.1 disabling web reporting you can disable f-secure policy manager web reporting by using the service control panel as follows: 1. Open the service control panel from the windows start menu. 2. Select f-secure policy manager web reporting from the list of services. 3. Open the action menu an...
Page 192
Chapter 10 192 web reporting 10.5.3 restricting or allowing wider access to web reports under the conf\ directory in the f-secure policy manager server installation directory, you will find a file named httpd.Conf , which contains the configuration information for f-secure policy manager server and ...
Page 193
193 specify a list of hosts that can access web reporting access to f-secure policy manager web reporting can also be allowed only from certain separately defined ip addresses. Below is an example of the edited httpd.Conf file section: #web reporting listen listen 8081 # web reporting port: jkmount ...
Page 194
Chapter 10 194 web reporting 1. Stop f-secure policy manager server. 2. Edit the web reporting port ( listen ) and virtualhost parameters in the httpd.Conf file so that they contain the new port number. 3. Start f-secure policy manager server. If there is a port conflict, f-secure policy manager ser...
Page 195
195 1. Stop the f-secure policy manager web reporting service. 2. Copy and decompress the fspmwr.Fdb file from the backup media to the following directory: 3. C:\program files\f-secure\management server 5\web reporting\firebird\data 4. Restart the f-secure policy manager web reporting service. 10.5....
Page 196
Chapter 10 196 web reporting the new setting will be taken into use immediately. For example, if you shortened the maximum time that data will be stored in the database, all the data that is older than the new time limit will be deleted. 10.6 web reporting error messages and troubleshooting this sec...
Page 197
197 error message: "web reporting lost its connection to the f-secure policy manager server at . Report data may be outdated, therefore reports cannot be viewed.” if web reporting cannot contact f-secure policy manager server it may mean that the f-secure policy manager server was extremely overload...
Page 198
Chapter 10 198 web reporting resetting the web reporting database normally the web reporting server erases automatically any obsolete data from the database, based on the currently configured maximum time the data is to be stored. However, if the database is really broken, you can also copy an empty...
Page 199
199 11 f-s ecure p olicy m anager p roxy overview................................................................................... 200 main differences between anti-virus proxy and policy manager proxy ........................................................................................ 200
Page 200
Chapter 11 200 f-secure policy manager proxy 11.1 overview f-secure policy manager proxy offers a solution to bandwidth problems in distributed installations of f-secure client security by significantly reducing load on networks with slow connections. It caches virus definition database updates retr...
Page 201
201 both types of proxies can exist on the same network but they cannot provide updates for the product for which they are not designed for. For example, f-secure anti-virus proxy cannot be used to deliver updates to f-secure client security 6.X and later. F-secure anti-virus proxy acts as a standal...
Page 202
202 12 t roubleshooting overview................................................................................... 203 f-secure policy manager server and console ........................ 203 f-secure policy manager web reporting................................ 208 policy distribution..................
Page 203
203 12.1 overview this chapter contains troubleshooting information and frequently asked questions about f-secure policy manager server and f-secure policy manager console. For information on how to configure f-secure policy manager server, and how to change the ports the server listen for requests,...
Page 204
Chapter 12 204 troubleshooting user manually, and set the access rights to full control . Propagate the access rights to the management server 5 directory (by default c:\program files\f-secure\management server 5 ) and all its subdirectories. After these changes, restart the f-secure policy manager ...
Page 205
205 q. How can the server role change stop f-secure policy manager server from working? A. Domain controller server and member/standalone server use different types of accounts: domain accounts on domain controller and local accounts on member server. Because f-secure policy manager server uses its ...
Page 206
Chapter 12 206 troubleshooting q. How can windows security hardening stop f-secure policy manager server from working? A. Access rights restrictions, especially restrictions under %systemroot% directory ( c:\windows or c:\winnt ) can stop f-secure policy manager server from starting, as its own acco...
Page 207
207 q. Why does f-secure policy manager console lose the connection to f-secure policy manager server? A. If f-secure policy manager console is run on a separate computer from f-secure policy manager server, then the connection may be affected by network problems. There have been numerous reports wh...
Page 208
Chapter 12 208 troubleshooting useful windows networking settings are: hklm\system\currentcontrolset\services\tcpip\parameters\ maxuserport (maximum number of network ports, default = 5000) hklm\system \currentcontrolset\services\tcpip\parameters\ tcptimedwaitdelay (time to wait before closing inact...
Page 209
209 12.4 policy distribution q. When distributing a policy, f-secure policy manager console shows an error message about an invalid policy value. What should i do? A. See below for information on error messages you may see during policy distribution, and for the reasons and solutions. Error messages...
Page 210
Chapter 12 210 troubleshooting 1. Group the hosts into subdomains based on the installed product version. For example, group hosts that have f-secure client security 6.X installed into one sub-domain, and hosts that have f-secure client security 7.X installed into another domain 2. Set most of the s...
Page 211
211 a snmp support overview................................................................................... 212 installing f-secure management agent with snmp support... 213 configuring the snmp master agent ...................................... 214 management information base .....................
Page 212
Appendix a 212 snmp support a.1 overview this section covers the following topics about snmp support: f-secure management agent with snmp agent installing f-secure management agent with snmp support f-secure management agent management information base (mib) snmp traps sent by f-secure management ag...
Page 213
213 are loaded, thus enabling the f-secure snmp management extension to monitor f-secure management agent activities independently of other f-secure management agent modules. A.2 installing f-secure management agent with snmp support a.2.1 f-secure snmp management extension installation snmp support...
Page 214
Appendix a 214 snmp support a.3 configuring the snmp master agent the snmp service is installed from the windows control panel network options window. The snmp service option is in the tcp/ip installation options window. After the snmp service software is installed on your computer, you must configu...
Page 215
215 a.4 management information base a management information base (mib) describes a set of managed objects on an snmp agent. A management system can manipulate the objects if the snmp agent has associated an extension agent dll with that mib. The snmp mib files are automatically installed under f-se...
Page 216
216 b ilaunchr error codes overview................................................................................... 217 error codes .............................................................................. 218.
Page 217
217 b.1 overview when ilaunchr.Exe is completed silently, it reports installation results with the standard exit codes. With the login script, you can test for the cause of the problem. Here is one example, which you can insert into your login script: start /wait ilaunchr.Exe \\server\share\mysuite....
Page 218
Appendix b 218 ilaunchr error codes b.2 error codes 0 installation ok. 1 fsma already installed. 2 user has no administrative rights. 3 jar not found. 4 jar corrupted. 6 error occurred when unpacking an installation package. 7 target disk has insufficient free space for installation. 8 file package....
Page 219
219 101 update is disabled. (setup attempted to update the installation.) 102 setup was unable to read the product.Ini file. 103 invalid data is encountered in prodsett.Ini . 104 management agent canceled the installation or conflicting software was found. Installation aborted. 105 the cd-key was en...
Page 220
Appendix b 220 ilaunchr error codes 151 setup was unable to load installation support dll. 152 setup was unable to load wrapper dll. 160 setup was unable to initialize a cabinet file. 170 management agent setup plug-in returned error. 171 plug-in returned an unexpected code. 172 plug-in returned a w...
Page 221
221 c fsii remote installation error codes overview................................................................................... 222 windows error codes............................................................... 222 error messages ..............................................................
Page 222
Appendix c 222 fsii remote installation error codes c.1 overview this appendix describes the most common error codes and messages that can occur during the autodiscover windows hosts operation. C.2 windows error codes error code description 1057 the user account name is invalid or does not exist. 5 ...
Page 223
223 c.3 error messages q. The required privilege is not granted for the current account and should be added manually. A. By default even the administrator does not have a required “act as part of operating system” privilege on the f-secure policy manager console machine. Without this privilege, wind...
Page 224
Appendix c 224 fsii remote installation error codes q. Management agent installation failed to fatal fsmainst error, see host log files for details. A. Fatal installation error occurred during f-secure management agent installation. It is recommended that management agent be installed manually to th...
Page 225
225 d remote installation support for windows 98/me enabling remote administration .............................................. 226.
Page 226
Appendix d 226 remote installation support for windows 98/me d.1 enabling remote administration there are some requirements for windows 98/me workstations to allow fsii to work with them. Complete the following steps to enable remote administration. 1. From control panel network, enable file sharing...
Page 227
227 user group names that are not compatible with the english version of windows nt server. You must verify that the administrators list contains the administrator group name in pure english ( domain admins )..
Page 228
228 e nsc notation for netmasks overview................................................................................... 229.
Page 229
229 e.1 overview nsc notation is a standard shorthand notation, which combines a network address with its associated netmask. Nsc notation defines the number of contiguous one-bits in the netmask with a slash and a number following the network address. Here is a simple example: nsc notation is not c...
Page 230
Appendix e 230 nsc notation for netmasks netmask bits netmask bits 255.255.128.0 17 255.255.255.128 25 255.255.192.0 18 255.255.255.192 26 255.255.224.0 19 255.255.255.224 27 255.255.240.0 20 255.255.255.240 28 255.255.248.0 21 255.255.255.248 29 255.255.252.0 22 255.255.255.252 30 255.255.254.0 23 ...
Page 231
231 t echnical s upport overview................................................................................... 232 web club.................................................................................. 232 advanced technical support.................................................... 232 f-...
Page 232
Technical support 232 overview f-secure technical support is available by e-mail and from the f-secure web site. You can access our web site from within your f-secure application or from your web browser. Web club the f-secure web club provides assistance to users of f-secure products. To enter, cho...
Page 233
233 1. Name and version number of your f-secure software program (including the build number). 2. Name and version number of your operating system (including the build number). 3. A detailed description of the problem, including any error messages displayed by the program, and any other details, whi...
Page 234
Technical support 234 the courses take place in modern and well-equipped classrooms. All of our courses consist of theory and hands-on parts. At the end of each course there is a certification exam. Contact your local f-secure office or f-secure certified training partner to get information about th...
Page 235
235 g lossary.
Page 236
Glossary 236 authentication the act of proving one’s identity. Authorization the right to perform an action on an object. Also the act of proving this right. Bit the smallest unit of memory size, sets of which make up bytes, arranged in a sequential pattern to express text, numbers, or other detaile...
Page 237
237 ftp (file transfer protocol) a very common method of moving files between two internet sites. Host any computer on a network that is a repository for services available to other computers on the network. Http the hyper text transfer protocol is the protocol used between a web browser and a serve...
Page 238
Glossary 238 kernel mode the part of the windows operating system, through which, among other things, user-mode applications and services use an api to interact with the computer's hardware. The kernel mode also contains an interface to user-mode, and a facility for synchronizing it's own services a...
Page 239
239 policy the set of conditions under which users of a system can access the system’s resources. Policy-based management controlling the actions and configurations of a system using policy statements. Private key the part of the key in a public key system which is kept secret and is used only by it...
Page 240
Glossary 240 snmp simple network management protocol. A standard tcp/ip protocol used for monitoring and setting network parameters and counters of lan- and wan-connected repeaters, bridges, routers, and other devices. Tcp/ip (transmission control protocol/internet protocol) this is the suite of pro...
Page 241
About f-secure corporation f-secure corporation is the fastest growing publicly listed company in the antivirus and intrusion prevention industry with more than 50% revenue growth in 2004. Founded in 1988, f-secure has been listed on the helsinki stock exchange since 1999. We have our headquarters i...