- DL manuals
- IBM
- Storage
- DS8000 - ADDITIONAL INFORMATION
- User Manual
IBM DS8000 - ADDITIONAL INFORMATION User Manual
Summary of DS8000 - ADDITIONAL INFORMATION
Page 1
Ibm system storage ds8000 user’s guide version 1 release 4 sc26-7915-02.
Page 3
Ibm system storage ds8000 user’s guide version 1 release 4 sc26-7915-02.
Page 4
Note: before using this information and the product it supports, read the information under safety and environmental notices and notices . This edition replaces sc26-7915-01 and all previous versions of sc26-7623. © copyright international business machines corporation 2004, 2008. All rights reserve...
Page 5: Contents
Contents figures . . . . . . . . . . . . . . Vii tables . . . . . . . . . . . . . . . Ix about this guide . . . . . . . . . . . Xi notices and publication information xiii safety notices . . . . . . . . . . . . . Xiii environmental notices . . . . . . . . . . Xiii product recycling and disposal . . ...
Page 6
Starting the ds storage manager on a windows operating system . . . . . . . . . . . 81 starting the ds8000 storage manager on a linux operating system . . . . . . . . . . . 82 getting started with the ds storage manager . . . 82 activating licensed functions . . . . . . . 83 chapter 5. Ibm system st...
Page 7
Industry canada compliance statement . . . . 181 european union emc directive conformance statement . . . . . . . . . . . . . . 181 japanese voluntary control council for interference (vcci) class a statement . . . . 182 korean ministry of information and communication (mic) statement . . . . . . 18...
Page 8
Vi ds8000 user’s guide.
Page 9: Figures
Figures 1. A base model (with front cover off) and its main components . . . . . . . . . . . 2 2. An expansion model (with front cover off) and its main components . . . . . . . . . . 3 3. Maximum configuration for model 921 or model 931 . . . . . . . . . . . . . 4 4. Configuration for model 922, 93...
Page 10
Viii ds8000 user’s guide.
Page 11: Tables
Tables 1. Ds8000 model comparison chart . . . . . . 6 2. Comparison of licensed functions . . . . . 29 3. User group capabilities . . . . . . . . 92 4. Failover and failback implementation 155 5. Remote mirror and copy return codes 160 6. Copy services suspension reason codes 163 © copyright ibm cor...
Page 12
X ds8000 user’s guide.
Page 13: About
About this guide ibm system storage ™ ds8000 is a high-performance, high-capacity series of disk storage that is designed to support continuous operations. This publication provides information that allows you to effectively use the ds8000 storage unit. Included among this information are procedures...
Page 14
Xii ds8000 user’s guide.
Page 15: Notices
Notices and publication information this section contains information about safety notices that are used in this guide, environmental notices for this product, publication information, and information about sending your comments to ibm. Safety notices complete this task to find information about saf...
Page 16
Notice: this mark applies only to countries within the european union (eu) and norway. Appliances are labeled in accordance with european directive 2002/96/ec concerning waste electrical and electronic equipment (weee). The directive determines the framework for the return and recycling of used appl...
Page 17
For taiwan: please recycle batteries. Conventions used in this guide the following typefaces are used to show emphasis: boldface text in boldface represents menu items and lowercase or mixed-case command names. Italics text in italics is used to emphasize a word. In command syntax, it is used for va...
Page 18
Related information this section provides information about locating and ordering ds8000 ™ publications. The tables in this section list and describe the following publications: v the publications that make up the ibm ® system storage ™ ds8000 series library v other ibm publications that relate to t...
Page 19
Title description order number ibm system storage ds8000 messages reference this publication provides explanations of error, information, and warning messages that are issued from the ds8000 user interfaces. Gc26-7914 other ibm publications other ibm publications contain additional information that ...
Page 20
Title description order number ibm system storage ds8000 series: copy services in open environments this publication, from the ibm international technical support organization, describes the copy services feature, which can provide immediate copies of data and make the data available to other applic...
Page 21
Title description order number z/os advanced copy services this publication helps you understand and use ibm advanced copy services functions. It describes three dynamic copy functions and several point-in-time copy functions. These functions provide backup and recovery of data if a disaster occurs ...
Page 22
Title description order number using ibm 3390 direct access storage in a vm environment this publication provides device-specific information for the various models of the 3390 and describes methods you can use to manage storage efficiently using the vm operating system. It provides guidance on mana...
Page 23
Title description order number ibm totalstorage ds8000 series: implementation this publication, from the ibm international technical support organization, helps you plan, install, and configure the ibm system storage ds8000 series. It can help you plan, design, and implement a new installation or mi...
Page 24
Title description order number ibm system storage productivity center software installation and user’s guide this publication describes how to install and use the ibm system storage productivity center software. Sc23-8823 ordering ibm publications you can order copies of ibm publications using the i...
Page 25
Type of storage information web site ibm storage products http://www.Storage.Ibm.Com/ ibm system storage ds8000 series http://www-1.Ibm.Com/servers/storage/disk/ds8000 ibm version of the java ™ (jre) that is often required for ibm products http://www-106.Ibm.Com/developerworks/java/jdk/ multiple dev...
Page 26
Xxiv ds8000 user’s guide.
Page 27: Summary
Summary of changes for sc26-7915-02 ibm system storage ds8000 user’s guide this document contains terminology, maintenance, and editorial changes. Technical changes or additions to the text and illustrations are indicated by a vertical line to the left of the change. This summary of changes describe...
Page 28
V the ibm totalstorage productivity center for replication manager. See “ibm totalstorage productivity center for replication” on page 14 for more information. V the metro/global mirror function for copy services. See “metro/global mirror” on page 118 v chapter one was updated to include the followi...
Page 29: Chapter
Chapter 1. Introduction to ibm system storage ds8000 series ibm system storage ds8000 series is a high-performance, high-capacity series of disk storage that is designed to support continuous operations. Ds8000 series models (machine type 2107/242x) use the ibm power5 ™ server technology that is int...
Page 30
Figure 1 provides a high-level view of the components of a base model (models 921, 922, 931, 932, 9a2, 9b2). The following notes provide additional information about the labeled components on figure 1: 1. The rack power area of the base models provides redundant power supplies (two primary power sup...
Page 31
Figure 2 provides a high-level view of the components of an expansion model (models 92e, 9ae). The following notes provide additional information about the labeled components on figure 2: 1. The rack power area of each expansion model provides redundant power supplies (two primary power supplies) an...
Page 32
Ds8100 (model 921 and model 931) the ibm system storage ds8100, which is model 921 and model 931, offers many features. The ds8100 provides the following features: v dual 2-way processor complex v up to 128 disk drives, for a maximum capacity of 64 tb v up to 128 gb of processor memory (cache) v up ...
Page 33
Ds8300 (models 922, 932, 9a2, and 9b2) ibm system storage ds8300 models (models 922, 932, 9a2, and 9b2) offer higher performance and capacity than the ds8100. Models 9a2 and 9b2 also enable you to create two storage system lpars (images) within the same storage unit. All ds8300 models offer the foll...
Page 34
Model comparison ds8000 models vary on the processor types that they use, their disk capacity, and other supported features. Table 1 compares the various supported features that are available on different ds8000 model configurations. Table 1. Ds8000 model comparison chart base model images (logical ...
Page 35
Table 1. Ds8000 model comparison chart (continued) base model images (logical partitions) expansion models processor type disk drives processor memory host adapters model 922/932 1 image none 4-way up to 128 disks (maximum capacity of 64 tb) up to 256 gb up to 16 host adapters with 1 expansion model...
Page 36
Note: ibm service representatives can perform the conversion in the field when you order one of the following model conversions: v model 921 to 922 v model 921 to 9a2 (will be first converted to a 922, and then to a 9a2) v model 931 to 932 v model 931 to 9b2 (will be first converted to a 932, and th...
Page 37
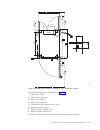
The following dimensions are labeled on figure 5: 1. Front cover width 2. Front service clearance 3. Back cover widths 4. Back service clearance 5. Clearance to allow front cover to open 6. Distance between casters 7. Depth of frame without covers 8. Depth of frame with covers 9. Minimum dimension b...
Page 38
Ds8000 series performance features the ds8000 series is designed to provide you with high-performance, connectivity, and reliability allowing your workload to be easily consolidated into a single storage subsystem. The following list provides an overview of some of the features that are associated w...
Page 39
Benefits that are offered by higher performance 4 gb san-based solutions, while maintaining compatibility with existing 2 gb infrastructures. Host attachments the ds8100 offers up to 16 host adapters (64 fcp/ficon ports) and the ds8300 offers up to 32 host adapters (128 fcp/ficon ports), further inc...
Page 40
Features when your storage unit is attached to the network. This component provides you with real-time (online) configuration support. Copy services this component allows you to process copy services functions. You can install the simulated ds storage manager using the gui (graphical mode) or using ...
Page 41
Ds open application programming interface the ibm system storage ds open application programming interface (api) is a nonproprietary storage management client application that supports routine lun management activities, such as lun creation, mapping and masking, and the creation or deletion of raid ...
Page 42
Volume controller, and other storage subsystems that support the smi-s block service performance subprofile. The performance functions start with the data collection task, which captures performance statistics for the devices and stores the data in the database. You can set thresholds for certain pe...
Page 43
Ds8000 hardware specifics the ds8000 models offer a high degree of availability and performance through the use of redundant components that can be replaced while the system is operating. You can use the ds8000 models with a mix of different operating systems and clustered and nonclustered variants ...
Page 44
Host attachment overview the ds8000 storage unit provides a variety of host attachments so that you can consolidate storage capacity and workloads for open-systems hosts and system z or s/390 hosts. The ds8000 provides extensive connectivity using fibre-channel or escon adapters across a broad range...
Page 45
Interconnects them. The network consists of elements like switches, bridges, and repeaters that are used to interconnect the fibre-channel ports. Fibre-channel overview for the ds8000 series each storage unit fibre-channel adapter has four ports, and each port has a unique worldwide port name (wwpn)...
Page 46
V linux v transaction processing facility (tpf) v virtual storage extended/enterprise storage architecture (vse/esa ™ ) v z/os v z/vm ® v z/vse ™ for the most current information on supported hosts, operating systems, adapters and switches, see the ds8000 interoperability matrix at http://www.Ibm.Co...
Page 47
Servers/storage/disk/ds8000/ or the system storage interoperation center (ssic) at http://www.Ibm.Com/systems/support/storage/config/ssic/. Processor memory the ds8100 models 921 and 931 offer up to 128 gb of processor memory. The ds8300 models 922, 932, 9a2, and 9b2 offer up to 256 gb of processor ...
Page 48
Requirements: if you choose the remote zseries power control options, you must have the remote zseries power control feature. There are no requirements for the other options. – remote management console, manual : your use of the ds storage manager power on/off page controls when the unit powers on a...
Page 49
Rack operator panel the rack operator panel contains 3 light-emitting diodes (leds) and the unit emergency power off (uepo) switch. The leds reflect various conditions of operation depending on the function they represent. When you observe that their standard reflection is different, it can mean tha...
Page 50
Redundant array of independent disks (raid) is a method of configuring multiple disk drives in a storage subsystem for high availability and high performance. The collection of two or more disk drives presents the image of a single disk drive to the system. In the event of a single device failure, d...
Page 51
Manage parity. However, with half of the ddms in the group used for data and the other half used to mirror that data, raid 10 disk groups have less capacity than raid 5 disk groups. Arrays across loops the arrays across loops helps prevent data loss. The storage unit provides arrays across loops. Ra...
Page 52
The following ibm system storage resiliency family functions are available as optional features: v point-in-time copy, which includes ibm system storage flashcopy and space-efficient flashcopy the flashcopy function enables you to make point-in-time, full volume copies of data, so that the copies ar...
Page 53
Flashcopy is an optional function. To use it, you must purchase one of the point-in-time 2244/239x function authorization features. The flashcopy function creates a copy of a source volume on the target volume. This copy is called a point-in-time copy. When you initiate a flashcopy operation, a flas...
Page 54
Persistent flashcopy allows the flashcopy relationship to remain even after the flashcopy operation completes. You must explicitly delete the relationship. Refresh target volume provides the ability to refresh a flashcopy relationship, without recopying all tracks from the source volume to the targe...
Page 55
Between two storage units that can be located up to 300 km from each other. With metro mirror copying, the source and target volumes can be on the same storage unit or on separate storage units. You can locate the storage unit at another site, some distance away. Metro mirror is a synchronous copy f...
Page 56
Same data. When you establish volume pairs and elect not to copy a volume, a relationship is established between the volumes but no data is sent from the source volume to the target volume. In this case, it is assumed that the volumes contain exactly the same data and are consistent, so copying the ...
Page 57
Z/os global mirror in the event of workload peaks, which might temporarily overload the bandwidth of the global mirror configuration, the enhanced z/os global mirror function initiates a global mirror suspension that preserves primary site application performance. If you are installing new high-perf...
Page 58
Table 2. Comparison of licensed functions (continued) licensed function description advantages considerations global mirror asynchronous copy nearly unlimited distance, scalable, and low rpo. The rpo is the time needed to recover from a disaster; that is, the total system downtime. Rpo might grow wh...
Page 59
Maximum supported sizes. Ds8000 and z/os limit ckd extended address volumes sizes. A 3390 model a volume has the capacity of 1 - 262668 cylinders (approximately 223.2 gb maximum). Z/vm and z/os software are required to use extended address volumes. Volume creation and volume expansion is limited to ...
Page 60
Http://www.Ibm.Com/servers/storage/disk/ds8000/ planning data migration the planning and methods of data migration for the ds8000 vary by environment. The ds8000 supports over 90 operating systems. You can migrate data to a storage unit from these host and operating system environments. When you pla...
Page 61
After you create ranks, your physical storage can be considered virtualized. Virtualization dissociates your physical storage configuration from your logical configuration, so that volume sizes are no longer constrained by the physical size of your arrays. The available space on each rank is divided...
Page 62
The storage management software can be used in real-time or simulated modes. When you are connected to storage devices over your network, you can use the real-time manager to manage your hardware or configure your storage. When you want to work offline, you can use the simulated manager to create or...
Page 63: Chapter
Chapter 2. Installing the simulated ds8000 storage manager interface the simulated ds8000 storage manager is installed using a graphical or unattended (silent) mode for the windows and linux operating systems. It can be accessed using a web browser from any location that has network access. This ins...
Page 64
Have occurred during the upgrade. You can check online support for error definitions. Additional information can be found in the logs of the local directories. Firewall installation alert note: during the installation process, it is possible to receive several alerts for java processes that are tryi...
Page 65
To install the ds storage manager on the windows operating system using graphical mode, perform the following steps: 1. Log on as a user with administrator authority. 2. Insert the ibm system storage ds storage manager cd into the cd-rom drive. The ibm system storage ds storage manager program start...
Page 66
The welcome window of the ibm system storage ds storage manager installation program displays if no problems are discovered during the initial system check. If an error is discovered (for example, the operating system does not match the prerequisite), an error message is displayed and the installati...
Page 67
Physical network node on the server. When multiple network cards exist in the server, the host name or ip address must resolve to one of the network cards. The value that you specify for the host name is used as the value of the hostname property in websphere application server configuration files. ...
Page 68
A. Designate whether you want to generate a new ssl certificate by selecting generate the self-signed certificates during installation . This is the most likely selection when you are installing ds storage manager for the first time. You can also select use existing ssl certificates . This choice is...
Page 69
Country or region the two-character designator that identifies the country where your company is located. Use the pull-down menu to make this selection. Validity period (days) specifies the lifetime of the certificate in days. The information that you provide is used to build a profile for the certi...
Page 70
Note: you can click cancel (not recommended) during the components installation process. The installation process stops immediately when the cancel button is clicked. A window with a confirmation message is displayed. For a new installation, when you confirm that you want to stop the process, all of...
Page 71
Installing the ibm system storage ds storage manager on the windows operating system using unattended (silent) mode complete this task to install the simulated ibm system storage ds storage manager in your windows environment using the unattended (silent) mode. When you are installing on a ds8000 st...
Page 72
The parameter default value to the value that you want for that option. You must enclose all values in double quotation marks ( ″″). V verify that all paths generated or modified in the response file are correct. There are some cases when the generated file displays an incorrect string representing ...
Page 73
Administrative tools , and then services . Both servers must show a ″started″ status. You cannot start the ds storage manager until both of the servers are started. 10. Check the install log file for any possible error messages. This file is located in the xxx\logs\install.Log directory, where xxx i...
Page 74
################################################################################ # # user input field - hostname # # the fully-qualified host name of the machine where the ds storage manager # server will be installed. # ### -w wasexpressconfig.Hostname="" ###########################################...
Page 75
################################################################################ # # user input field - certificateoption # # ssl certificates files select one of the following options concerning the ssl # certificates. Legal values are: "generate" (the default value) - generate the # self-signed ce...
Page 76
################################################################################ # # user input field - confirmedtruststorepassword # # the password confirmation of the truststore file. On silent mode the password # confirmation is not necessary. # ### -w wassslconfiguration.Confirmedtruststorepassw...
Page 77
################################################################################ # # user input field - organizationname # # the name of your organization. # ### -w certificateparams.Organizationname="" ################################################################################ # # user input f...
Page 78
Removing the ds storage manager from a windows operating system complete this task to remove the ibm system storage ds storage manager from your windows operating system by using the windows add/remove programs facility. 1. Log on to your windows operating system with administrator authority. 2. Nav...
Page 79
9. Restart your system, if required (now or later), to complete the removal process. If you want to remove all configuration settings before you reinstall the ds storage manager, you must delete the dsniserver and the smserver subdirectories from the program files\ibm directory. Removing the ds stor...
Page 80
A. Type launchpad at the command prompt and press enter . The launchpad window opens. B. Locate and double-click the launchpad.Bat reference in windows explorer. Note: if you are viewing the folder with windows explorer with the option that hides the extensions for unknown file types, use the launch...
Page 81
6. Read the license agreement and click your acceptance or nonacceptance of the agreement. If you accept, the next button is highlighted. Click next to continue or click cancel to exit the upgrade process. When you click next , the product version check window opens. 7. Observe the information that ...
Page 82
13. Complete each of the input fields with the required information. Use the following as a guide to provide the needed information: keystore alias this is the alias for the self-signed certificate. It uniquely identifies the certificate within the keystore file. It is a good practice to use a uniqu...
Page 83
B. If one or both of the servers are not installed or have to be upgraded on your system, they are installed or upgraded in the following order (the progress of the installation is indicated on the associated progress window): 1) ds storage manager server installation progress window 2) ds network i...
Page 84
V if the error is due to a system problem, correct it and reinstall the ds8000 storage manager using either the interactive or unattended (silent) mode of installation. V if the error is due to a wrong installation parameter value, restart the installation using the steps that are described in this ...
Page 85: Chapter
Chapter 3. Installing the simulated ibm system storage ds8000 storage manager on the linux operating system this section provides and overview of the installation, upgrade, and uninstall processes and instructions associated with the simulated ibm system storage ds8000 storage manager on the linux o...
Page 86
6. Run the wizard launcher, launchpad_linux, by typing the following command: # ./launchpad_linux . The installation in graphical mode begins with a launchpad facility to launch the installation program wizard. The launchpad facility provides links for you to view various text files, such as: ds8000...
Page 87
10. Read the license agreement and click your acceptance or nonacceptance of the agreement. If you accept, the next button is highlighted. Click next to continue or click cancel to exit the installation. When you click next , the destination directory window is displayed. 11. Choose the directory on...
Page 88
V the fully qualified domain name servers (dns) host name string; for example, xmachine.Manhattan.Ibm.Com. V the default short dns host name string; for example, xmachine. V the numeric ip address; for example, 9.127.255.3. V the generic name localhost or its equivalent ip address; for example, 127....
Page 89
And trust file are identified by an extension of .Jks. Also, provide a password for each file. The password must be a minimum of six characters and cannot contain any blanks. Allowable characters are letters a-z and a-z, digits 1-9, and special characters - and _ (hyphen and underscore). 16. Click n...
Page 90
18. Click next . The installation confirmation window is displayed. This window displays both the location where the product will be installed and the total size that is needed for the installation 19. Click the install button on the installation confirmation window to begin the installation process...
Page 91
If a system logoff is required, the installer finish window is displayed, which asks you to log off from the system. Click next on the finish window. The installer logoff window is displayed. Click finish on the logout window. 20. Click finish to exit the installation process. When the installation ...
Page 92
B. Type the following command at the command prompt: # mount -o ro /dev/cdrom /mnt/cdrom 4. Choose the destination paths for the ds8000 storage manager components and be sure you have enough available space on the chosen destination. The installation program (installer) provides a default installati...
Page 93
Designates the path where the response file was created before designates the relative name of the response file that you created and modified before 10. Wait for the ds8000 storage manager installation program to install the product. This can take 5 - 10 minutes. Note: during this processing, the i...
Page 94
################################################################################ # # ibm system storage ds8000 storage manager install location # # the install location of the product. Specify a valid directory into which the # product should be installed. If the directory contains spaces, enclose i...
Page 95
################################################################################ # # user input field - soapport # # the address for the simple object access protocol (soap) connector in the # application server. This value must not conflict with existing port # assignments on the system. # -w wasex...
Page 96
################################################################################ # # user input field - truststorefilename # # the absolute path of the truststore file. # -w wassslconfiguration.Truststorefilename="/opt/ibm/ smserver/keys/smservertrustfile.Jks" #######################################...
Page 97
################################################################################ # # user input field - keysize # # the key size. That must be between 512 and 1024 and must be multiple of # 64b.The only two allowed values are 512 or 1024. If you enter other values it # takes the default value 1024. ...
Page 98
Removing the ibm system storage ds storage manager from a linux operating system you can remove the ibm system storage ds storage manager by following the steps in this procedure. 1. Log on as root to the system where the ds8000 storage manager is installed. 2. Type: # dest_path>/_uninst/uninstall t...
Page 99
3. Click next to continue or click cancel to exit the removal process. When you click next , the confirmation window is displayed showing the directory from which the ibm system storage ds storage manager gui program is removed. 4. Click remove to continue or cancel to stop the removal and exit the ...
Page 100
Known as /dev/cdrom at mount point /mnt/cdrom. When the time comes for you to mount the cd in this drive, perform the following steps: a. Insert the cd in the cd-rom drive. B. Type the following command at the command prompt: # mount -o ro /dev/cdrom /mnt/cdrom 4. Choose the destination paths for th...
Page 101
Started. The launchpad returns to the foreground when the upgrade is complete. You can click exit to close the launchpad. There might be a slight delay while the software loads on your system. After the software loads, a command prompt window opens to display the following message: initializing inst...
Page 102
C. If you are creating new certificates, create a password for each file. The password must be a minimum of six characters and it cannot contain any blanks. Allowable characters are letters a - z and a - z, digits 1 - 9, and special characters - and _ (hyphen and underscore). Supply the existing pas...
Page 103
19. Click the install button on the installation confirmation window to begin the upgrade process. There are several progress windows that are displayed. There is no required interaction on your part for each of the progress windows that are displayed. However, you can choose to cancel (not recommen...
Page 104
Postinstallation tasks. If the upgrade failed, you must exit the upgrade process and check the install log for error messages. 21. If the finish window indicates that the upgrade has failed, check the install log for error messages. The install log is located in xxx/logs/install.Log, where xxx is th...
Page 105
5. Read the readme.Txt file that is located on the ds8000 storage manager cd to check for information that might supersede the information in these upgrade instructions. 6. Type ./setup.Linux -silent in the same command prompt window in which you changed the current directory to the root of the cd, ...
Page 106
78 ds8000 user’s guide.
Page 107: Chapter
Chapter 4. Ds storage manager postinstallation instructions you have just installed the ds storage manager and its two supporting servers. The servers are automatically started when you start your computer and remain on until you stop them manually or there is a system outage. The following instruct...
Page 108
– use http 1.1. – use http 1.1 through proxy connections. 4. Click apply . 5. Close and then reopen the browser. 6. You will now be able to access the ibm totalstorage productivity center gui. Stop and start the ds storage manager servers the ibm system storage ds storage manager server and ibm syst...
Page 109
5. Type /etc/init.D/dsnisrv stop to stop the ds network interface server. 6. Type /etc/init.D/dsnisrv start to start the ds network interface server. Starting the ds storage manager program the topics in this section describe how to start the ds storage manager program. The ds storage manager progra...
Page 110
V is case-sensitive. V four unique new passwords must be issued before an old password can be reused. Starting the ds8000 storage manager on a linux operating system you can start the ds8000 storage manager on a linux operating system by issuing a command from the command prompt window. Within this ...
Page 111
Log in you can log in to the ds8000 storage manager by providing your user name and password. This function is generally administered through your system administrator and by your company policies. Note: the default password that you use the first time (generally the password is admin ) expires imme...
Page 112
The initial enablement of any optional ds8000 licensed function is a concurrent activity (assuming the appropriate level of microcode is installed on the machine for the given function). Note: the following activating activities are disruptive and require a machine iml (models 921, 922, 931, and 932...
Page 113
Activating activities are disruptive and require a machine iml (models 921, 922, 931, and 932) or reboot of the affected image (models 9a2 and 9b2): v removal of a ds8000 licensed function to deactivate the function. Contact your ibm service representative to perform this operation. V a lateral chan...
Page 114
1. Before you begin this task, you must resolve any current ds8000 problems. Contact ibm support for assistance in resolving these problems. 2. Before you configure, disable or provide paths through any firewalls, because they might interfere with ds8000 communication. Perform the following steps to...
Page 115: Chapter
Chapter 5. Ibm system storage management console the ibm system storage management console is the focal point for configuration, copy services management, and maintenance activities. The management console is a dedicated workstation that is physically located (installed) inside your ds8100 and ds830...
Page 116
Logging off the management console the management console must always be left operational. However, you might consider the following actions when you leave the management console unattended or when you must logoff your management console session. 1. In the main menu, click console → exit . At this p...
Page 117
4. Click browser . The web browser is started with no address bar and a web page titled welcome to the ds8000management console is displayed. 5. Click the link ″ibm system storage ds storage manager ″ to access the ds storage manager. Dual hardware management consoles an external management console ...
Page 118
Link-local address assigned on a given subnet, only one is one required. The first 10 bits of link local addresses are limited to b‘1111 1110 10’ (for example, fe80::1) global uni-cast address used for cross subnet identification. Any prefix other than 1s is reserved for a link-local address. Mult-c...
Page 119: Chapter
Chapter 6. Administering user accounts the topics in this section provide information related to administering your ds8000 user accounts. If you have administrator level privileges, you can add a new user account, delete an existing user account, or modify the user name, password, and group for a us...
Page 120
Monitor (only) must be the only assigned group. This group has access to all read-only, nonsecurity service functions and all ds8000 resources. No access (only) the default selection. Must be the only assigned group. This group has no access to any service functions or ds8000 resources. This is the ...
Page 121
Table 3. User group capabilities (continued) capability administrator physical operator logical operator copy services operator monitor no access manage copy services (flashcopy, remote mirror and copy, global mirror) x x x set copy services timeout values x x x update user account password x x x x ...
Page 122
V four unique new passwords must be issued before an old password can be reused. 4. Retype the password in the confirm password box. This entry must match the password entry above. Characters in this field appear as asterisks. 5. Assign a group role to the user account by selecting the appropriate g...
Page 123
2. Select delete in the select action drop-down box. A confirmation message is displayed. 3. Click ok . The user id is removed immediately. Unlocking a user account there might be times when users forget the password that they use to access the ds storage manager. Beyond the set number of allowable ...
Page 124
5. Select service utilities from the tasks list, and then highlight the storage facility. 6. Navigate to selected → get hmcs , and then highlight the hmc. 7. Navigate to selected → start/stop essni , and then select reset under the security recovery options . 8. Click apply . 96 ds8000 user’s guide.
Page 125: Chapter
Chapter 7. Storage system logical partition overview a storage system logical partition (lpar) allows the division of a single server into two completely independent virtual storage systems. A logical partition uses hardware and firmware to logically allocate the resources between partitions. The st...
Page 126
Each storage image has access to the following components: v 50 percent of the processors is the default. With variable lpar implementation on ds8300 model 9b2, the split can be 25/75 percent or 75/25 percent. V 50 percent of the processor memory is the default. With variable lpar implementation on ...
Page 127
V device adapter slots. V storage enclosure slots. V rio-g bus bandwidth required hardware components to build a storage image when you build a storage image, you need to consider your i/o resources, the processor and memory allocations, and the rio-g interconnect separation. The hardware management...
Page 128
Mirrored across the two physical disk drives for each lpar. For the ds8300 model 9a2/9b2, there are four drives in one physical processor complex. Processor and memory allocation in the ds8300 model 9a2/9b2 each processor complex has four processors and up to 128 gb memory capacity. There is also a ...
Page 129: Chapter
Chapter 8. Optional feature codes for the ds8000 the ds8000 is designed to meet or exceed the storage requirements of a broad range of operating environments. There are many features that are enabled to meet your data management requirements. The following two areas are particularly useful for data ...
Page 130
Parallel access volumes parallel access volumes (pavs) allow your system to access volumes in parallel when you use a system z or s/390 host. A pav capability represents a significant performance improvement by the storage unit over traditional i/o processing. With pavs, your system can access a sin...
Page 131
The configuration might only have a subset of these addresses, and the subset might not be contiguous. You need to know what cu images you created before you can update the i/o configuration. Your host system uses the updated i/o information in order to know what cu images are on the ds8000. Overvie...
Page 132
********************************************************************* * * * define escon chpids * * * ********************************************************************* chpid path=(70),partition=(host1),switch=50,type=cnc chpid path=(71),partition=(host1),switch=50,type=cnc chpid path=(72),partit...
Page 133
* define 2107-9a2 logical control unit 4 * * * ********************************************************************** cntlunit cunumbr=7004,path=(74,75,fc,fd),unitadd=((00,256)), * link=(24,2d,34,3d),cuadd=4,unit=2107 ********************************************************************* * define 339...
Page 134
V only define the actual base and alias devices to iocp or hcd to avoid unnecessary definition of processor subchannels. V only define the unit address range to iocp or hcd as necessary for the installed devices in an lcu (64, 128, or 256). Defining the unit address range enables you to put more lcu...
Page 135
Attention: ensure that there is sufficient memory in the hardware storage area to store the new configuration. 5. Add new 3390 volumes to the lcu. 6. Assign new pavs. Ibm ds8000 copy services functions the ds8000 supports copy services functions that contribute to the protection of data. These produ...
Page 136
– failover and failback – copy services functions across a 2105 and 2107 – copy services functions with i5/os v in addition, the following example copy services tasks are included at the end of the chapter: – creating remote flashcopy transactions (known as inband flashcopy on the ess 2105) – adding...
Page 137
Fast reverse reverses the flashcopy relationship without waiting for the finish of the background copy of the previous flashcopy. This option applies to the global mirror mode. Inhibit writes to target ensures that write operations are inhibited on the target volume until a refresh flashcopy operati...
Page 138
Flashcopy to metro mirror source volumes you can use an existing metro mirror source volume as a flashcopy target volume. This process allows you to create a point-in-time copy and then make a copy of that data at a remote site. Previously, you could create a flashcopy relationship between two volum...
Page 139
Multiple relationship flashcopy the multiple relationship flashcopy function allows a source volume to have multiple targets simultaneously. When a flashcopy operation copies data from a source volume to a target volume, that source volume can be involved in more than one flashcopy relationship at t...
Page 140
The use of the persistent flashcopy function requires that the flashcopy relationship is explicitly withdrawn before another flashcopy operation can be performed. While this restriction does not guarantee that a point-in-time copy cannot be overwritten by mistake, it does provide an extra measure of...
Page 141
Storage servers that are located at some distance from each other. Second, and more significantly, remote mirror and copy does not capture the state of the source volume at some point in time, but rather reflects all changes that were made on the source volume to the target volume. Metro mirror metr...
Page 142
Global copy is a nonsynchronous mirroring function and is an alternative mirroring approach to metro mirror operations. Host updates to the source volume are not delayed by waiting for the update to be confirmed by a storage unit at your recovery site. The source volume sends a periodic, incremental...
Page 143
Global mirror processing is most often associated with disaster recovery or preparing for disaster recovery. However, it can also be used for everyday processing and data migration. The global mirror function is designed to mirror data between volume pairs of a storage unit over greater distances wi...
Page 144
Session a session is a collection of volumes across multiple storage units that are managed together to create consistent copies of data. The session is identified with an id that is unique across the enterprise. The id identifies volumes that will participate in the global mirror consistency group....
Page 145
Volumes across multiple storage units that are managed together when creating consistent copies of data. The formation of these consistency groups is coordinated by the master storage unit, which sends commands over remote mirror and copy links to its subordinate storage units. With global mirror fu...
Page 146
A copy services session is a collection of volumes across multiple storage units that are managed together to create consistent copies of data. Sessions are managed for global mirror relationships. The global mirror mode supports data consistency across multiple volumes, logical subsystems (lsss), a...
Page 147
The metro/global mirror function provides this combination of synchronous and asynchronous mirroring. Metro/global mirror is an extension of global mirror, which is based on existing global copy (formerly known as pprc xd) and flashcopy functions. Global mirror running at the intermediate site, usin...
Page 148
For global mirror processing, one storage unit at the intermediate site is designated as the master storage unit. The master storage unit sends commands over fibre channel protocol (fcp) links and coordinates the consistency group formation process. These links are required for the global mirror mas...
Page 149
A metro/global mirror environment is configured using a minimum of three storage units, one each at the local, intermediate, and remote sites. Data from the a volumes at the local site is synchronously replicated to b volumes at the intermediate site using metro mirror. Data from the b volumes at th...
Page 150
A three-site metro/global mirror configuration provides the following recovery options at the alternate sites if a failure occurs: v if an outage occurs at the local site, recovery operations can begin at the intermediate site. Global mirror continues to mirror updates between the intermediate and r...
Page 151
The process of forming consistency groups using global mirror involves the following steps: 1. The consistency group is created. 2. Data in the consistency group is sent to the remote site. 3. Data in the consistency group is saved as a group. In a metro/global mirror configuration, metro mirror and...
Page 152
After the master storage unit has coordinated a consistent point across the source volumes of the global mirror pairs (the b volumes in a metro/global mirror configuration), the master storage unit monitors the progress of the transfer of the consistency group to the remote site. When the consistenc...
Page 153
Each consistency group. The default is zero seconds, which means that global mirror will continuously form consistency groups as fast as the environment will allow. In most situations, it is recommended that you leave the default value of zero to allow global mirror to form consistency groups as fas...
Page 154
You can also customize tasks for other user-defined actions, such as planned site switches in which the workload is switched from one site to another. For further information about gdps, see gdps/pprc v3r2 installation and customization guide (or gdps/pprc hyperswap manager v3r2 installation and cus...
Page 155
Mirror configuration. The volumes are continually updated to maintain a record of tracks that have changed data that has not been secured at the remote site. If the intermediate site fails, the change recording bitmaps and out-of-synchronization bitmaps on the primary metro mirror volumes contain th...
Page 156
Periodically, the incremental resynchronization function performs queries from each of the a volumes at the local site to each of the b volumes at the intermediate site to determine when data has been secured on the c volumes at the remote site. The queries generate a report that allows you to view ...
Page 157
Note: when incremental resynchronization is started, there is a short period of time where a full volume copy is required. This occurs because incremental resynchronization has not fully initialized. Overriding incremental resynchronization function checking you can override (or bypass) system verif...
Page 158
With fcp, a single fibre-channel link between two ports enables bi-directional remote mirror and copy operations. This means that it is possible to send and receive data in both directions simultaneously. For example, one link can have a path that is established in one direction and then have anothe...
Page 159
You can create paths from a source lss to a target lss that have the consistency group option enabled. All volume pairs in remote mirror and copy relationships from this source to target lss (sharing the same paths) belong to the consistency group. Other volumes pairs are not affected. With the cons...
Page 160
Failover and failback operations the failover operation is the process of switching production to a backup facility (normally your recovery site). A failback operation is the process of returning production to its original location after a disaster or a scheduled maintenance period. There are times,...
Page 161
Copy services functions across a 2105 and 2107/242x copy services functions that are performed using either the ds storage manager or ds cli are designed to interact with both the 2107/242x and the ibm totalstorage enterprise storage servers (ess) models 750 and 800. Most copy services functions tha...
Page 162
There are two types of lun protection: protected and unprotected. In reality, both volume protection types have the same ds8000 internal raid protection. If you define a lun as protected, it is protected by the hardware (the ds8000) rather than by i5/os host-based mirroring. If you define a lun as u...
Page 163
The objects they are protecting. The system asp and all the user asps together are called traditional asps. An independent auxiliary storage pool is an independent disk pool. It is a method of configuring multiple disk units into one group. (disk pool, iasp, and database are sometimes used interchan...
Page 164
Must be the same on the 2107/242x and 2105. This allows the user to access the 2105 server from the ds storage manager, without having to authenticate on the 2105. Perform the following steps to configure the 2105 copy services domain and add it to the list of storage complexes. 1. Determine the add...
Page 165
Before you begin, ensure that you meet the following requirements: v the license for the remote mirror and copy feature must be activated. V to create a metro mirror volume pair between machine types 2107/242x and a 2105, you must have added the add 2105 copy services domain option from the select a...
Page 166
9. On the select source volumes page, select the volumes that you want to include for the metro mirror relationships and click next . If the resource type is an lss, specify which from lss to select source volumes. Optionally, you can click the create paths button to create a new path. You are linke...
Page 167
Note: you can perform all steps from the ds cli. Perform the following steps to create a remote flashcopy operation: 1. Create paths between the source lss and the target lss. For example, ibm.2107-1300861 and ibm.2107-1300871. You need to know which volumes are available for use before you can issu...
Page 168
140 ds8000 user’s guide.
Page 169: Chapter
Chapter 9. Migrating data to a storage unit the ds8000 supports over 90 operating systems. You can migrate data to a storage unit from these host and operating system environments. The planning and methods of data migration vary by environment. When you replace existing storage, you can partition th...
Page 170
V management software provides simple robust methods that you can generally use during production without disturbing users. V the aix logical volume manager (lvm) provides methods that you can use at any time without disrupting user access to the data. You might notice a small performance degradatio...
Page 171
Extra bytes. The storage unit lic uses the sequence number and lrc. The storage unit does not transfer them to the host system. Most fixed-block disk architectures use a fixed-byte sector of 512-bytes. This includes most unix systems, including aix. When used in a storage unit, the format of a ddm h...
Page 172
In the second example, the cplv command copies data from existing logical volume oldlv to existing logical volume existinglv (-e) . When you use the -e option, it overwrites the existing target-logical volume with the data from the source-logical volume. When you use the -e option, it maintains the ...
Page 173
Using the migratepv command use the following information as a guide for how to use the logical volume manager (lvm) migratepv command to migrate data that is associated with physical volumes. You can use the lvm migratepv command to migrate data that is associated with physical volumes. The followi...
Page 174
Next, find a disk or disks that have the available space. In this case, hdisk1 has 515 free physical partitions, which is more than the required space of 399 physical partitions. The only situation that is specific to rootvg is if the desired disk contains the boot image. Generally, this is the logi...
Page 175
V unmount both file systems and mount the new file system over the original mount point directory when the migration is complete. You will probably be unable to use the volume management methods if the database uses volume serial numbers in its licensing code or validity checking. If the database us...
Page 176
Fibre-channel adapter are supported by the ds8000. If the multipathing option (only available on i5/os v5r3 and above) is selected, then a maximum of 16 luns per adapter is recommended. Because the system i host does not support 7133 drawers, you have no existing 7133 drawers to reformat. If you hav...
Page 177
Environment or operating system data migration method z/os operating system v dfsmsdss (simplest method) v dfsmshsm v idcams export/import (vsam) v idcams repro (vsam, sam, bdam) v iebcopy (partitioned data set (pds), including load module libraries, and pdse) v icegener (sam), part of dfsort v iebg...
Page 178
Migrating data to a ds8000 storage unit using volume management methods the unix volume manager method for migrating data is very similar to the method that is used by aix systems. It involves the use of commands or a combination of commands that copy and move the data. The following methods are ava...
Page 179
Migrating data using the direct copy method use the following information as a guide for determining when to use the direct copy method to migrate data for a unix operating system. This method suffers from the same drawback as using the cplv and splitlvcopy commands on logical volumes. You can use t...
Page 180
3. Convert the pairs to ibm system storage metro mirror after the bulk copy is complete if you use global copy. 4. Ensure that all remote mirror and copy volumes are in duplex state. 5. Quiesce the applications before you switch to the new volumes. 6. End all remote mirror and copy pairs across all ...
Page 181: Chapter
Chapter 10. Disaster recovery using copy services one of the main reasons for using copy services functions is to prepare for a possible disaster by backing up, copying, and mirroring your data both at the local (production) and remote sites. Having a disaster recovery plan can ensure that critical ...
Page 182
Storage units) internally manages data consistency using consistency groups within a global mirror configuration. Consistency groups can be created many times per hour to increase the currency of data that is captured in the consistency groups at the remote site. Note: a consistency group is a colle...
Page 183
V applications continue to update the source volumes that are located at site a. V paths are established from site a to site b. V volume pairs are in duplex state. The following steps summarize the actions that you must take to move production to site b after you initiate a planned outage at site a....
Page 184
Table 4. Failover and failback implementation (continued) step operation mc connectivity required to format of source volume and target volume format of source and target volume pair result: site a result: site b disaster at site a failover site b volume b, volume a volume b1 : volume a1 volume a1 -...
Page 185
For this scenario, assume that site a is operational and that connectivity from site b to site a is available. Use this procedure to restart your production environment using the volumes from site b. After the failover operation processes, the volumes at site b are available to be mounted and used b...
Page 186
Moving production to site b after unplanned outages (failover) for this scenario, assume that an unexpected failure occurs at site a. The failure at site a causes the volumes to be suspended or causes a mix of suspended and full duplex volume pairs because the input might have been written to those ...
Page 187: Appendix.
Appendix. Troubleshooting and analyzing problems the topics in this appendix provide information on troubleshooting and analyzing problems. Troubleshooting the topics in this section provide troubleshooting information related to your ds8000. Topics covered include analyzing, verifying, understandin...
Page 188
The sequence number); nnnnn is the problem number; sfaessbc is the logical partition name; ssssssssss is the system reference code (src); and frunloc is the location code of fru n, where n is 1, 2, and 3. Specific trap 100 - remote mirror and copy links degraded this trap displays when an establishe...
Page 189
Table 5. Remote mirror and copy return codes (continued) return code return code explanation x’07’ there is a secondary lss subsystem identifier (ssid) mismatch, or failure of the i/o that collects the secondary information for validation. X’08’ the escon link is offline. This is caused by the lack ...
Page 190
Sec: xxx tttt-ooo pp-zzzzz ll path: type pp plink sp slink rc 1: aaaaa bbbb cccccc dddd eeeeee gg . . . W: aaaaa bbbb cccccc dddd eeeeee gg where yyyy/mm/dd hh:mm:ss tzn is the time that the alert was sent (year, month, day, hour, minute, second, and time zone); -error_description- is the event desc...
Page 191
Specific trap 200 - lss pair consistency group remote mirror and copy pair error this trap displays when the first remote mirror and copy pair that is associated with the consistency group enters the suspended state because of an error. This trap is managed by automation code. Reporting for this tra...
Page 192
Table 6. Copy services suspension reason codes (continued) suspension reason code (src) src explanation x’07’ copy operations between the remote mirror and copy volume pair were suspended when the secondary storage unit notified the primary storage unit of a state change transition to simplex state....
Page 193
The suspension reason codes explain the cause of the error that suspended the primary remote mirror and copy devices. Table 6 on page 163 explains the suspension reason codes. Specific trap 210 - global mirror initial consistency group successfully formed this trap displays when the first consistenc...
Page 194
Specific trap 213 - global mirror consistency group successful recovery this trap displays when a consistency group forms successfully after it had previously failed. The following information is shown for specific trap 213: sseventdescr=yyyy/mm/dd hh:mm:ss tzn -error_description- unit: mnf type-mod...
Page 195
Sseventdescr=yyyy/mm/dd hh:mm:ss tzn -error_description- unit: mnf type-mod serialnm master: xxx tttt-ooo pp-zzzzz slave: xxx tttt-ooo pp-zzzzz session id: qqqq where yyyy/mm/dd hh:mm:ss tzn is the time that the alert was sent (year, month, day, hour, minute, second, and time zone); -error_descripti...
Page 196
Where yyyy/mm/dd hh:mm:ss tzn is the time that the alert was sent (year, month, day, hour, minute, second, and time zone); -error_description- is the event description; xxx is the manufacturer; tttt-ooo is the machine type and model number; pp-zzzzz is the serial number (a combination of the plant o...
Page 197
Sim message types the following sim message types are generated by the storage unit. Direct access storage device (dasd) sim tracks ddm failures and problems. Media sim tracks data check problems on the media. Storage unit sim tracks storage unit, power control, and other hardware problems. Sim seve...
Page 198
Presenting time the time and date of the most recent problem report. Description the description of the error condition for the problem id. User action the recommended actions that you need to take to resolve this error condition. Product-specific alert traps 1 and 2 product-specific alert traps con...
Page 199
Data migration ibm provides a service through global services to help you with your data migration needs. Contact your ibm representative for more details. Command line interface (cli) ibm provides a service through global services to help you with using the ds8000 cli in your system environment. Co...
Page 200
Storage unit location the installer enters the storage unit location during the initial installation of the product. Product machine type and model number assigned by ibm at time of manufacturing. Product serial number assigned by ibm at time of manufacturing. Customer voice phone number the phone n...
Page 201
Probable cause information for the service provider. Failure cause information for the service provider. The following fields are the most useful to you in identifying ddm failures: v description v reporting resource v last occurrence appendix. Troubleshooting and analyzing problems 173.
Page 202
174 ds8000 user’s guide.
Page 203: Accessibility
Accessibility accessibility features provide users who have disabilities with the ability to successfully access information and use technology. Accessibility features help a user who has a physical disability, such as restricted mobility or limited vision, to use software products successfully. Fea...
Page 204
176 ds8000 user’s guide.
Page 205: Notices
Notices this information was developed for products and services offered in the u.S.A. Ibm may not offer the products, services, or features discussed in this document in other countries. Consult your local ibm representative for information on the products and services currently available in your a...
Page 206
Estimated through extrapolation. Actual results may vary. Users of this document should verify the applicable data for their specific environment. Information concerning non-ibm products was obtained from the suppliers of those products, their published announcements or other publicly available sour...
Page 207
Trademarks this topic lists ibm trademarks. The following terms are trademarks of the international business machines corporation in the united states, other countries, or both: v aix v as/400 v db2 v developerworks v dfsms/mvs v dfsms/vm v ds4000 v ds6000 v ds8000 v e (logo) v eserver v enterprise ...
Page 208
V system x v system z v system z9 v system z10 v system storage v system storage ds v tivoli v totalstorage v versatile storage server v virtualization engine v vm/esa v vse/esa v xseries v z/architecture v z/os v z/vm v zseries adobe, the adobe logo, postscript, and the postscript logo are either r...
Page 209
In a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, might cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause...
Page 210
Dieses produkt entspricht den schutzanforderungen der eu-richtlinie 89/336/ewg zur angleichung der rechtsvorschriften über die elektromagnetische verträglichkeit in den eu-mitgliedsstaaten und hält die grenzwerte der en 55022 klasse a ein. Um dieses sicherzustellen, sind die geräte wie in den handbü...
Page 211
Korean ministry of information and communication (mic) statement please note that this device has been certified for business use with regard to electromagnetic interference. If you find this is not suitable for your use, you may exchange it for one of residential use. Taiwan class a compliance stat...
Page 212
184 ds8000 user’s guide.
Page 213: Glossary
Glossary this glossary includes terms for the ibm system storage and other resiliency family products. This glossary includes selected terms and definitions from: v the american national standard dictionary for information systems, ansi x3.172–1990, copyright 1990 by the american national standards ...
Page 214
Warranty period for the licensed functions and they include the following machine types: 2396 (one-year warranty), 2397 (two-year warranty), 2398 (3-year warranty), and 2399 (four-year warranty). Each 239x function authorization machine type corresponds to the 242x hardware machine type that represe...
Page 215
Application programming interface an interface that allows an application program that is written in a high-level language to use specific data or functions of the operating system or another program. Arbitrated loop a fibre-channel topology that enables the interconnection of a set of nodes. See al...
Page 216
With access to the machine, service personnel can perform service tasks, such as viewing error logs and problem logs or initiating trace and dump retrievals. (gc) see also heartbeat and remote technical assistance information network. Cascading 1) connecting network controllers to each other in a su...
Page 217
Available for subsequent processing. The data in the backup copy is frozen at the point in time that the server responds to the request. Concurrent installation of licensed internal code process of installing licensed internal code on a ds8000 series while applications continue to run. Concurrent ma...
Page 218
Coordinated universal time (utc) the international standard of time that is kept by atomic clocks around the world. Copy services a collection of optional software features, with a web-browser interface, that is used for configuring, managing, and monitoring data-copy functions. Count field the firs...
Page 219
Data field the optional third field of a count key data (ckd) record. The count field specifies the length of the data field. The data field contains data that the program writes. Data record the basic unit of system z storage on a ds8000, also known as a count-key-data (ckd) record. Data records ar...
Page 220
Disk drive standard term for a disk-based nonvolatile storage medium. The ds8000 series use hard disk drives as the primary nonvolatile storage media to store host data. Disk drive module (ddm) a field replaceable unit that consists of a single disk drive and its associated packaging. Disk drive mod...
Page 221
Electrostatic discharge (esd) an undesirable discharge of static electricity that can damage equipment and degrade electrical circuitry. Emergency power off (epo) a means of turning off power during an emergency, usually a switch. Emif see escon multiple image facility. Enclosure a unit that houses ...
Page 222
F fabric in fibre channel technology, a routing structure, such as a switch, receives addressed information and routes to the appropriate destination. A fabric can consist of more than one switch. When multiple fibre-channel switches are interconnected, they are said to be cascaded. Failback pertain...
Page 223
Fibre channel switched fabric (fc-sf) an implementation of the fibre channel standard that connects the storage unit to one or more open systems hosts through a fabric switch or connects one or more s/390 hosts that run linux on an fibre channel protocol s/390 channel. Ficon see fibre-channel connec...
Page 224
Gigabyte (gb) a gigabyte of storage is 10 9 bytes. A gigabyte of memory is 2 30 bytes. Global copy an optional capability of the ds8000 remote mirror and copy feature that maintains a fuzzy copy of a logical volume on the same ds8000 storage unit or on another ds8000 storage unit. In other words, al...
Page 225
Hop interswitch connection. A hop count is the number of connections that a particular block of data traverses between source and destination. For example, data traveling from one hub over a wire to another hub traverses one hop. Host see host system. Host adapter a physical subunit of a storage ser...
Page 226
Including the ds storage manager and the ds8000 copy services. Ibm system storage multipath subsystem device driver (sdd) ibm software that provides multipath configuration support for a host system that is attached to storage devices. Sdd provides enhanced data availability, dynamic input/output lo...
Page 227
I/o configuration program (iocp) a program that defines to a system all the available i/o devices and channel paths. I/o device an addressable read and write unit, such as a disk drive device, magnetic tape device, or printer. I/o interface an interface that enables a host to perform read and write ...
Page 228
Link-level facility the escon hardware and logical functions of a control unit or channel subsystem that allow communication over an escon write interface and an escon read interface. Local area network (lan) a computer network located on a user’s premises within a limited geographic area. Local e-m...
Page 229
Logical volume the storage medium that is associated with a logical disk drive. A logical volume typically resides on one or more storage devices. The ds8000 administrator defines this unit of storage. The logical volume, when residing on a raid-formatted array, is spread over the drives in the arra...
Page 230
Maximum coordination time the value in milliseconds that indicates the maximum time that is allowed for host i/o to be delayed during the coordination of the primary volumes of an global mirror session. The default is 50 milliseconds if this value is set to zero. Mb see megabyte. Mc see ibm system s...
Page 231
Most see mobile solutions terminal. Mrpd see machine reported product data. Msa see multiport serial adapter. Mtbf see mean time between failures. Multipath subsystem device driver see ibm system storage ds8000 multipath subsystem device driver. Multiple allegiance a ds8000 hardware function that is...
Page 232
Throughout the industry and that therefore can be connected to other systems complying with the same standards. Applied to the ds8000, such systems are those hosts that connect to the ds8000 through scsi or fcp protocols. See also small computer system interface and fibre channel protocol. Organizat...
Page 233
Planar the main printed circuit board (pcb) that other pcbs or assemblies plug into. The planar distributes both power and signals and therefore creates a common communications path to whichever device that plugs into it. Point-in-time copy a flashcopy option that creates an instantaneous view of or...
Page 234
Hewlett-packard that provides for multiple paths to a volume, as well as static load balancing. R r0 see track-descriptor record. Rack see enclosure. Raid see redundant array of independent disks. Raid is also commonly expanded to redundant array of inexpensive disks. See also array. Raid 5 a type o...
Page 235
Paths that are associated with the allegiance; access is for one or more channel programs until the allegiance ends. Retain see remote technical assistance information network. S s/390 ibm enterprise servers based on enterprise systems architecture/390 (esa/390). S/390 is the currently accepted shor...
Page 236
Service clearance the area that is required to open the service covers and to pull out components for servicing. Service information message (sim) a message sent by a storage server to service personnel through a system z operating system. Service personnel a generalization referring to individuals ...
Page 237
Not require modifications to the host software in order to continue to provide an existing function. Source device one of the devices in a dual-copy or remote-copy volume pair. All channel commands to the logical volume are directed to the source device. The data on the source device is duplicated o...
Page 238
Byte, multibyte, record, or block increments across multiple disk drives. Subagent an extension to an snmp agent that permits a user to dynamically add, or in some cases replace, additional management variables in the local mib, thereby providing a means of extending the range of information that ne...
Page 239
A system z control unit. See also small computer system interface. Target device one of the devices in a dual-copy or remote-copy volume pair that contains a duplicate of the data that is on the source device. Unlike the source device, the target device might only accept a limited subset of data. Se...
Page 240
Unit address for system z, the address associated with a device on a given control unit. On escon interfaces, the unit address is the same as the device address. On oemi interfaces, the unit address specifies a control unit and device pair on the interface. Unprotected volume an as/400 term that ind...
Page 241
Zoning in fibre-channel environments, the grouping of multiple ports to form a virtual, private, storage network. Ports that are members of a zone can communicate with each other, but are isolated from ports in other zones. Z/os an operating system for the system z family of products. Z/os global mi...
Page 242
214 ds8000 user’s guide.
Page 243: Index
Index numerics 3390 model a 30 524-byte sector, disk formatting 142 a accessibility 175 account setup adding user accounts 93 administering user accounts 91 unlocking a user account 95 unlocking an administrative password 95 activating licenses 83 adding users 93 api, ds open 13 arrays across loops ...
Page 244
F failback and failover 132 failover site switch 154, 156 failover and fallback 153 fast reverse 116 feature activation (dsfa), ibm disk storage 84 fibre-channel open-systems hosts 16 overview 17 san connections 16 find commands 146 flashcopy changing direction of 109 incremental 108 multiple relati...
Page 245
P panel rack operator 21 parallel access volume (pav) understanding static and dynamic 102 parallel access volumes requirements 102 passwords changing the management console password 88 use criteria 93 path connections 129 pav (parallel access volumes) 102 pavs defining an lcu 105 increasing the for...
Page 246
218 ds8000 user’s guide.
Page 247: Readers’
Readers’ comments — we would like to hear from you ibm system storage ds8000 user’s guide version 1 release 4 publication no. Sc26-7915-02 we appreciate your comments about this publication. Please comment on specific errors or omissions, accuracy, organization, subject matter, or completeness of th...
Page 248: Business
Readers’ comments — we’d like to hear from you sc26-7915-02 sc26-7915-02 cut or fold along line cut or fold along line fold and tape please do not staple fold and tape fold and tape please do not staple fold and tape no postage necessary if mailed in the united states business reply mail first-class...
Page 250
Printed in usa sc26-7915-02.