- DL manuals
- IBM
- Software
- Network Access Control Solution
- User Manual
IBM Network Access Control Solution User Manual
ibm.com/redbooks
Building a Network
Access Control Solution
with IBM Tivoli and Cisco Systems
Axel Buecker
Richard Abdullah
Markus Belkin
Mike Dougherty
Wlodzimierz Dymaczewski
Vahid Mehr
Frank Yeh
Covering Cisco Network Admission
Control Framework and Appliance
Automated remediation of
noncompliant workstations
Advanced security
compliance notification
Front cover
Summary of Network Access Control Solution
Page 1
Ibm.Com/redbooks building a network access control solution with ibm tivoli and cisco systems axel buecker richard abdullah markus belkin mike dougherty wlodzimierz dymaczewski vahid mehr frank yeh covering cisco network admission control framework and appliance automated remediation of noncompliant...
Page 3
Building a network access control solution with ibm tivoli and cisco systems january 2007 international technical support organization sg24-6678-01.
Page 4
© copyright international business machines corporation 2005, 2007. All rights reserved. Note to u.S. Government users restricted rights -- use, duplication or disclosure restricted by gsa adp schedule contract with ibm corp. Second edition (january 2007) this edition applies to tivoli security comp...
Page 5: Contents
© copyright ibm corp. 2005, 2007. All rights reserved. Iii contents notices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Vii trademarks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ....
Page 6
Iv building a network access control solution with ibm tivoli and cisco systems 3.1.1 network admission control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41 3.1.2 compliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46 3.1.3 remedia...
Page 7
Contents v 6.2.1 posture collectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153 6.2.2 policy collector . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154 6.2.3 installation of posture collectors . . . . . . . . . . . . . . . . . . ...
Page 8
Vi building a network access control solution with ibm tivoli and cisco systems fault isolation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 448 security compliance manager server and client . . . . . . . . . . . . . . . . . . . . . . 450 communic...
Page 9: Notices
© copyright ibm corp. 2005, 2007. All rights reserved. Vii notices this information was developed for products and services offered in the u.S.A. Ibm may not offer the products, services, or features discussed in this document in other countries. Consult your local ibm representative for information...
Page 10: Trademarks
Viii building a network access control solution with ibm tivoli and cisco systems trademarks the following terms are trademarks of the international business machines corporation in the united states, other countries, or both: redbooks (logo) ™ developerworks® ibm.Com® access360® aix® db2 universal ...
Page 11: Preface
© copyright ibm corp. 2005, 2007. All rights reserved. Ix preface in february of 2004, ibm® announced that it would be joining cisco’s network admission control (nac) program. In december of 2004, ibm released its first offering for the cisco nac program in the form of the ibm tivoli® compliance and...
Page 12
X building a network access control solution with ibm tivoli and cisco systems the team that wrote this redbook this redbook was produced by a team of specialists from around the world working for the international technical support organization, austin center. The project was executed at the cisco ...
Page 13
Preface xi richard abdullah is a consulting engineer with cisco systems strategic alliances. Prior to joining cisco systems in 2001, he worked in technical capacities within various service providers. He has spent 19 years in the it industry focusing on networking and most recently on network securi...
Page 14: Become A Published Author
Xii building a network access control solution with ibm tivoli and cisco systems thanks to the following people for their contributions to this project: cheryl gera, erica wazewski, lorinda schwarz, julie czubik international technical support organization, poughkeepsie center wing leung, alex rodri...
Page 15: Comments Welcome
Preface xiii find out more about the residency program, browse the residency index, and apply online at: ibm.Com/redbooks/residencies.Html comments welcome your comments are important to us! We want our redbooks™ to be as helpful as possible. Send us your comments about this or other redbooks in one...
Page 16
Xiv building a network access control solution with ibm tivoli and cisco systems.
Page 17: Summary of Changes
© copyright ibm corp. 2005, 2007. All rights reserved. Xv summary of changes this section describes the technical changes made in this edition of the book and in previous editions. This edition may also include minor corrections and editorial changes that are not identified. Summary of changes for s...
Page 18
Xvi building a network access control solution with ibm tivoli and cisco systems.
Page 19: Architecture
© copyright ibm corp. 2005, 2007. All rights reserved. 1 part 1 architecture and design in this part we discuss the overall business context of the ibm integrated security solution for cisco networks. We then describe how to technically architect the overall solution into an existing environment, an...
Page 20
2 building a network access control solution with ibm tivoli and cisco systems.
Page 21: Business Context
© copyright ibm corp. 2005, 2007. All rights reserved. 3 chapter 1. Business context information technology (it) security is a vital component of business success and is very important in e-business security and security for on demand services. As the internet increasingly becomes an effective means...
Page 22
4 building a network access control solution with ibm tivoli and cisco systems personal computer workstations are used in the office, at home, or at a remote client location. Telecommuters must use mobile pc workstations to meet customer expectations and provide quicker response to queries, quotes, ...
Page 23: 1.2 Why We Need This
Chapter 1. Business context 5 concept that can protect all networks in this era. This ibm and cisco integration, depicted in an overview in figure 1-1, is a true enabler for the on demand self-defending and security compliance strategy. Figure 1-1 ibm and cisco integration strategy ibm security comp...
Page 24
6 building a network access control solution with ibm tivoli and cisco systems it has become mandatory for businesses to comply with regulatory guidelines such as the gramm-leach-bliley act (glba; also known as the financial services modernization act ), sarbanes-oxley act (sox), and health insuranc...
Page 25
Chapter 1. Business context 7 the ibm integrated security solution for cisco networks checks every client’s workstation when it attempts to connect to the corporate local area network (lan) using predefined policies. For example, it can examine whether the workstation has the latest antivirus signat...
Page 26
8 building a network access control solution with ibm tivoli and cisco systems standard reports that can be generated from the ibm integrated security solution for cisco networks can be valuable to corporate auditors. These can be used as artifacts, thereby reducing the effort in checking individual...
Page 27
Chapter 1. Business context 9 enable an automated remediation process that eases the process of regaining compliancy for all authorized users on the corporate network. Provide partners and visitors access to the internet but not the corporate intranet. 1.6 achievable benefits for being compliant how...
Page 28: 1.7 Conclusion
10 building a network access control solution with ibm tivoli and cisco systems figure 1-2 depicts the relevant tasks in a life-cycle overview for endpoint protection. All of the topics discussed in this chapter are represented at some point in this life cycle. Figure 1-2 integrated endpoint protect...
Page 29
Chapter 1. Business context 11 those mentioned in 1.2, “why we need this” on page 5, mandate every organization to comply with regulatory acts. Keys to greater productivity include identifying authorized users and providing them easier access to network and system resources while keeping them compli...
Page 30
12 building a network access control solution with ibm tivoli and cisco systems.
Page 31: Architecting The Solution
© copyright ibm corp. 2005, 2007. All rights reserved. 13 chapter 2. Architecting the solution in this chapter we discuss the solution architecture of the ibm integrated security solution for cisco networks with its compliance-based network admission control system. We provide an overview of the key...
Page 32
14 building a network access control solution with ibm tivoli and cisco systems 2.1 solution architectures, design, and methodologies our objective for this chapter is not to discuss any general approach for architecting a security solution; however, we follow the ibm method for architecting secure ...
Page 33
Chapter 2. Architecting the solution 15 in general, the ibm integrated security solution for cisco networks consists of three subsystems or logical components, as shown in figure 2-1 on page 14: network admission control (nac) subsystem based on cisco technology compliance subsystem based on ibm tiv...
Page 34
16 building a network access control solution with ibm tivoli and cisco systems devices seeking to access network computing resources, thereby limiting damage from viruses and worms. Using nac, organizations can provide network access to endpoint devices such as pcs, pdas, and servers that are verif...
Page 35
Chapter 2. Architecting the solution 17 security compliance manager ibm tivoli security compliance manager performs the functions of managing security compliance policies and monitoring compliance of clients to these policies. It plays a vital role in deploying predefined policies and providing a re...
Page 36
18 building a network access control solution with ibm tivoli and cisco systems port details and communication flows between security compliance manager server and client can be found in “security compliance manager server and client” on page 450. Details of the activities performed by server and cl...
Page 37
Chapter 2. Architecting the solution 19 tivoli configuration manager ibm tivoli configuration manager automates the manual provisioning and deployment process. Tivoli configuration manager provides an automated software and patch distribution solution that can also run pre-built scripts on a client,...
Page 38
20 building a network access control solution with ibm tivoli and cisco systems tables that contain data gathered by the collectors. In a generic security compliance manager deployment, the compliance queries are evaluated on the server, but with nac-enabled clients using new posture collectors they...
Page 39
Chapter 2. Architecting the solution 21 if the client is not security compliance manager policy–enabled, it is denied access to the corporate network and may be allowed only restricted access to the internet or may be denied access to all networks. When a client is quarantined, the user is given a c...
Page 40
22 building a network access control solution with ibm tivoli and cisco systems access, this is an acceptable solution. Users are authenticated and placed into a default network based on their identity. It is not until the user attempted access across a nac-enabled router that the integrity check wa...
Page 41
Chapter 2. Architecting the solution 23 the ieee 802.1x standard addresses the need to authenticate the user or client trying to connect to the particular network. Point-to-point protocol (ppp) can be used in a basic dial-up scenario, but it limits the authentication process to checking only user an...
Page 42
24 building a network access control solution with ibm tivoli and cisco systems in the cisco nac solution, the eap header is extended with posture data and the admission process is based on policies governing the network admission decision. Those policies consider all of the attributes provided by t...
Page 43
Chapter 2. Architecting the solution 25 this requirement can be fulfilled by providing each user with a unique identity and verifying it even before the posture condition of a client is checked. This process was standarized with the ieee 802.1x protocol, and ibm provides the solution to facilitate i...
Page 44
26 building a network access control solution with ibm tivoli and cisco systems 2.2 definition of a network admission control project objectives of a network admission control solution must be carefully planned because the result of having a large number of workstations quarantined may be more disru...
Page 45
Chapter 2. Architecting the solution 27 figure 2-5 illustrates a possible nac deployment scenario. Figure 2-5 nac deployment scenario typical candidates for nac protection are networks (both wireless and wired) used by the mobile users to connect to the intranet while visiting the office [1], as wel...
Page 46: 2.3 Design Process
28 building a network access control solution with ibm tivoli and cisco systems 2.3 design process the mass methodology that we follow in this book includes the following steps of the design process: 1. Model business process. 2. Establish security design objectives. 3. Select and enumerate subsyste...
Page 47
Chapter 2. Architecting the solution 29 2. Check control settings and compare to security policy. The audit team periodically checks the systems to be sure their settings are in compliance with the policy. The audit team creates a report listing all controlled systems and the violated controls. Peri...
Page 48
30 building a network access control solution with ibm tivoli and cisco systems the security compliance process for desktops and mobile clients can be simplified to look like this: 1. Apply security policy. The first step in setting up a health check process is to make sure the required security con...
Page 49
Chapter 2. Architecting the solution 31 reason a policy cannot be complied with due to a particular business need, the situation has to be accepted as a security risk for a well-defined period of time and signed off by the project sponsor. A policy that is created but is not enforced is no better th...
Page 50: 2.3.3 Solution Objectives
32 building a network access control solution with ibm tivoli and cisco systems this means that for each desired change in the configuration settings, there must be an appropriate configuration change process in place to perform the changes on the afflicted systems. For example, if there is a securi...
Page 51
Chapter 2. Architecting the solution 33 2.3.4 network design discussion in this section we discuss the following network design factors for the ibm integrated security solution for cisco networks: network segmentation via vlans and downloadable ip acls performance adding new components that may not ...
Page 52
34 building a network access control solution with ibm tivoli and cisco systems in the reference architecture described later in this book, there are several untrusted networks that are the default networks to which users are assigned based on their identity-based authentication. When clients are in...
Page 53: 2.4 Implementation Flow
Chapter 2. Architecting the solution 35 revalidation process takes place too often, this pop-up window may become annoying and significantly lower the user’s productivity. The recommended value is 14400 seconds (4 hours) or more. The router or the network access device (nad) periodically queries the...
Page 54
36 building a network access control solution with ibm tivoli and cisco systems particular security compliance concept is aimed at validating client access to the corporate network, so it is mandatory that the system is available at all times. As mentioned in chapter 1, “business context” on page 3,...
Page 55: 2.6 Conclusion
Chapter 2. Architecting the solution 37 part 2, “customer environment” on page 75, details a comprehensive deployment scenario. 2.6 conclusion in this chapter, we discussed the architecture and design principles for the ibm integrated security solution using cisco networks. The overall architecture ...
Page 56
38 building a network access control solution with ibm tivoli and cisco systems.
Page 57: Component Structure
© copyright ibm corp. 2005, 2007. All rights reserved. 39 chapter 3. Component structure this chapter introduces the logical and physical components of the ibm integrated security solution for cisco networks. The final section of this chapter talks about the logical data flow among the various compo...
Page 58: 3.1 Logical Components
40 building a network access control solution with ibm tivoli and cisco systems 3.1 logical components the ibm integrated security solution for cisco networks detects the state of network clients and compares it with a set of centrally defined and managed policies to establish client postures. It th...
Page 59
Chapter 3. Component structure 41 the logical components are: network admission control compliance remediation the following sections provide function and architecture details for each component. 3.1.1 network admission control network admission control (nac) is the cisco component of the solution t...
Page 60
42 building a network access control solution with ibm tivoli and cisco systems for network devices and other services. The various components that constitute the acs and a brief description of their functions are discussed here. The acs architecture consists of seven services bundled within acs. Fi...
Page 61
Chapter 3. Component structure 43 policy enforcement device clients access enterprise resources via the network which makes it an effective point to validate system posture prior to allowing access to such resources. In the nac solution, policy enforcement is accomplished using a network access devi...
Page 62
44 building a network access control solution with ibm tivoli and cisco systems figure 3-3 shows the cisco trust agent architecture, followed by a brief explanation of the components that make up the cisco trust agent. Figure 3-3 cisco trust agent architecture cisco trust agent service responds to n...
Page 63
Chapter 3. Component structure 45 eap methods provide a mechanism to authenticate the application or device requesting the host credentials, and encrypts or decrypts that information. Network admission control appliance the network admission control appliance consists of the following subcomponents:...
Page 64: 3.1.2 Compliance
46 building a network access control solution with ibm tivoli and cisco systems clean access policy updates these are regular updates of pre-packaged policies/rules that can be used to check the up-to-date status of operating systems, antivirus (av), antispyware (as), and other client software. 3.1....
Page 65
Chapter 3. Component structure 47 figure 3-4 depicts security compliance manager’s high-level component architecture, followed by a brief explanation. Figure 3-4 ibm tivoli security compliance manager logical component architecture figure 3-4 shows: administration components consist of a graphical u...
Page 66
48 building a network access control solution with ibm tivoli and cisco systems compliance evaluation consisting of security compliance manager snapshots and policies, these components centrally verify security compliance. Compliance client the client consists of modules that run on the endpoint to ...
Page 67
Chapter 3. Component structure 49 the compliance client component (figure 3-5) consists of the following modules: policy collector posture collector posture cache posture plug-in default remediation handler figure 3-5 compliance client logical component posture collector a collector is a java langua...
Page 68
50 building a network access control solution with ibm tivoli and cisco systems in the ibm integrated security solution for cisco networks, the collector is called a posture collector . A posture collector consists of posture data collection and posture status determination. The posture data collect...
Page 69: 3.1.3 Remediation
Chapter 3. Component structure 51 posture cache this component provides the caching area where posture collectors store the results of posture determination in a temporary file. The policy collector refers to the information captured in the posture cache for determining the violation count. Posture ...
Page 70: 3.2 Physical Components
52 building a network access control solution with ibm tivoli and cisco systems and any client components that would normally be installed on a tivoli configuration manager client are embedded within the security compliance manager compliance policy. For the ibm integrated security solution for cisc...
Page 71
Chapter 3. Component structure 53 cisco trust agent the cisco trust agent is cisco client software that is required to pass posture credentials and validation results between the cisco nac solution and the ibm security compliance manager client. Security compliance manager client the security compli...
Page 72
54 building a network access control solution with ibm tivoli and cisco systems 3.2.2 network access infrastructure all users connect to enterprise resources via network access devices. The topology varies depending on the size of the organization, but most networks can be classified into lan (local...
Page 73
Chapter 3. Component structure 55 be deployed to the clients. The server is also used for administration and for providing reports about client compliance to deployed policies. Tivoli configuration manager servers there are two tivoli configuration manager servers used for remediation. Tivoli config...
Page 74
56 building a network access control solution with ibm tivoli and cisco systems the flow consists of these process groups, depicted in figure 3-6: 1. Policy creation and deployment 2. Posture collection 3. Posture validation and policy enforcement 4. Remediation figure 3-6 solution data and communic...
Page 75
Chapter 3. Component structure 57 remediation object should also be provided. Details of the policy creation and deployment process are discussed here: remediation object creation and publishing (1a) a remediation object that can remediate violations must be provided. The naming and creation of thes...
Page 76
58 building a network access control solution with ibm tivoli and cisco systems cisco secure acs policy creation (1d) an acs policy consists of rules that must match required posture criteria. Depending on the matched criteria, a token is assigned to the network client that requires validation. The ...
Page 77
Chapter 3. Component structure 59 posture validation and policy enforcement (flow 3) this section contains details about how a client in a live environment connects to the network and how its posture is validated by the acs. After validation the client is provided access based on client posture. Cli...
Page 78
60 building a network access control solution with ibm tivoli and cisco systems – quarantine – infected – unknown posture notification (3f) after the acs has determined the posture token it performs these actions: a. Cisco secure acs sends the system posture token to the network client. B. The cisco...
Page 79
Chapter 3. Component structure 61 remediation (flow 4) two cases should be considered for the remediation process: one where the organization has a tivoli configuration manager server with an automatic remediation implementation, and the other where the organization will use manual methods for remed...
Page 80: 3.3.1 Secure Communication
62 building a network access control solution with ibm tivoli and cisco systems 3.3.1 secure communication the components are designed to provide a high level of security between the various elements in the solution. We provide a description of how the various components securely communicate, and fi...
Page 81: 3.4 Component Placement
Chapter 3. Component structure 63 nac communication during communication of the cisco trust agent client with the cisco secure acs, a secure peap session is established with the network client and requests the network client security posture credentials. Cisco trust agent uses certificates to establ...
Page 82
64 building a network access control solution with ibm tivoli and cisco systems figure 3-8 shows the security zones and their classifications. Organizations could have different topologies and have their own architecture and naming of zones depending on their security policy. Figure 3-8 security zon...
Page 83
Chapter 3. Component structure 65 corporate network through what are considered external networks , such as the dmz and intranet zones. Details of resources that are generally deployed in the various security zones, the possible access methods by which network clients access these enterprise resourc...
Page 84
66 building a network access control solution with ibm tivoli and cisco systems remote offices and branch offices can use the internet as a primary method of access or for backup if the primary access method fails. Organizations can provide partners access over the internet and exchange data over vp...
Page 85
Chapter 3. Component structure 67 3.4.2 policy enforcement points the ibm integrated security solution for cisco networks employs the cisco nac solution to restrict access to users depending on the compliance level of the client. The nac solution requires network access devices (nad) to be deployed ...
Page 86
68 building a network access control solution with ibm tivoli and cisco systems advantages of this kind of deployment are: policy enforcement load distribution across the various routers protection against virus infection between branch offices if the network has a mesh topology factors that must be...
Page 87
Chapter 3. Component structure 69 figure 3-11 campus ingress enforcement site-to-site vpn users internet aaa aaa branch office compliance (campus ingress enforcement) corporate headquarters data center posture enforcement points router aaa aaa server vpn.
Page 88
70 building a network access control solution with ibm tivoli and cisco systems small office home office compliance policy enforcement can be used to protect corporate networks from noncompliant and potentially infected small office and home office (soho) users, as shown in figure 3-12. This will al...
Page 89
Chapter 3. Component structure 71 extranet compliance organizations could have wan connections to share information with partners. This would require partner systems connecting to the parent organization to comply with the policies laid down by the parent organization. The policy enforcement device ...
Page 90
72 building a network access control solution with ibm tivoli and cisco systems lab compliance organizations prefer having lab networks to test systems before deployment of new solutions or equipment. Traffic from this zone to the primary network is restricted so that operations in the lab setup do ...
Page 91
Chapter 3. Component structure 73 data center protection the data center is the site where organizations host business-critical systems that require maximum protection. Compliance can be checked for client systems before they are provided connections to the resources at the data center (figure 3-15)...
Page 92: 3.5 Conclusion
74 building a network access control solution with ibm tivoli and cisco systems remote access protection remote access users use dial-up or vpn to connect to corporate resources. To enforce these users to comply to the corporate policies, a policy enforcement device may be deployed at the remote acc...
Page 93: Customer
© copyright ibm corp. 2005, 2007. All rights reserved. 75 part 2 customer environment part 2 discusses how the ibm integrated security solution for cisco networks might be used in customer situations. We use a well-know customer scenario, the armando banking brothers corp. In our last encounter in t...
Page 94
76 building a network access control solution with ibm tivoli and cisco systems.
Page 95: Armando Banking Brothers
© copyright ibm corp. 2005, 2007. All rights reserved. 77 chapter 4. Armando banking brothers corporation this chapter provides an introduction to the overall structure of the armando banking brothers corporation (abbc). This introduction includes a description of abbc’s business profile, their curr...
Page 96: 4.1 Company Profile
78 building a network access control solution with ibm tivoli and cisco systems 4.1 company profile armando brothers banking corporation (abbc) is a fictional financial institution that traces its roots back to the early days of industrialization. During a time of radical change and growing financin...
Page 97
Chapter 4. Armando banking brothers corporation 79 4.2 current it architecture this section provides background information about the existing armando banking brothers company it architecture, including the network infrastructure, security infrastructure, and the middleware/application infrastructur...
Page 98
80 building a network access control solution with ibm tivoli and cisco systems uncontrolled zone - internet the internet has become a pivotal component in the banking industry with its immense flexibility and business opportunities. But it has also become one of the preferred methods for spreading ...
Page 99
Chapter 4. Armando banking brothers corporation 81 figure 4-2 is representative of the itso lab environment used for l2dot1x nac deployment. Vlan-11 healthy sales vlan in the core network. This vlan hosts those users that have been authenticated by ieee 802.1x as members of the sales group and have ...
Page 100
82 building a network access control solution with ibm tivoli and cisco systems his credentials, the cisco secure acs checks its local user database and assigns the user to the respective group. The user is then mapped to the healthy or quarantine vlan of that group, depending on the state of postur...
Page 101
Chapter 4. Armando banking brothers corporation 83 figure 4-3 on page 84 is representative of the itso lab environment used for nac appliance deployment. Vlan 20 this is the access vlan for a healthy user. All dhcp addresses are provided from vlan 20, regardless of whether a user is compliant or non...
Page 102
84 building a network access control solution with ibm tivoli and cisco systems figure 4-3 armando banking brothers network environment for nac appliance when a user connects to the network controlled by nac appliance, the cam is advised of a linkup notification sent by the user’s switch. The cam ch...
Page 103
Chapter 4. Armando banking brothers corporation 85 4.2.3 application security infrastructure general management and the it department are aware of the need for a solid basis to implement their future goals. The current environment with multiple systems is complex; the introduction of ibm tivoli acce...
Page 104
86 building a network access control solution with ibm tivoli and cisco systems the diagram in figure 4-4 provides a high-level graphical overview of the existing abbc security infrastructure. We see that abbc is using the ibm tivoli access manager best-practice deployment methodology by incorporati...
Page 105
Chapter 4. Armando banking brothers corporation 87 cluster of ibm http servers and websphere® application servers providing internet banking and other services to external users. Similarly, the internal application server block represents multiple servers providing application support for internal u...
Page 106
88 building a network access control solution with ibm tivoli and cisco systems in the practice of it security, it is possible to design an extremely secure, hardened system. However, this apex of maximum security will likely incur a cost of reduced system usability. Likewise it is possible to creat...
Page 107
Chapter 4. Armando banking brothers corporation 89 configure security compliance manager posture policy. Ample thought time must always be provided for determining proper policy for the business. In a true deployment, the proper forethought, establishment of process, and policy are major keys to suc...
Page 108
90 building a network access control solution with ibm tivoli and cisco systems installing the clean access agent highlights the steps for installing the clean access agent 7.2.1, “installing cca agent” on page 304 configuring a cca oob vg server highlights all the steps to configure the cam and cas...
Page 109: 4.4 Conclusion
Chapter 4. Armando banking brothers corporation 91 4.4 conclusion armando banking brothers corporation (abbc) is a company with a long history of leading-edge technology adoption. Abbc is well aware of the rising threats of computer viruses, worms, and the exploitation of known system vulnerabilitie...
Page 110
92 building a network access control solution with ibm tivoli and cisco systems.
Page 111: Solution Design
© copyright ibm corp. 2005, 2007. All rights reserved. 93 chapter 5. Solution design in this chapter we describe the business objectives that drive the functional requirements of the technical solution. As a best practice, it is typical in a production environment to deploy a new technology, such as...
Page 112
94 building a network access control solution with ibm tivoli and cisco systems implementation of part two is described inchapter 7, “network enforcement subsystem implementation” on page 213. Part 3, “appendixes” on page 439, builds on this infrastructure and adds automatic remediation functionalit...
Page 113: 5.1 Business Requirements
Chapter 5. Solution design 95 5.1 business requirements as described in chapter 4, “armando banking brothers corporation” on page 77, armando banking brothers corporation (abbc) is well vested in the ibm tivoli identity, access, and compliance management solutions. With the emergence of the network ...
Page 114
96 building a network access control solution with ibm tivoli and cisco systems 5.2 functional requirements in this section, the business requirements are further examined in order to extract the functional requirements. In subsequent sections of this book, the functional requirements are further di...
Page 115
Chapter 5. Solution design 97 5.2.3 remediation requirements examining the operational maintenance related requirements we found that the following pain points are the requirement drivers: desktop security requirements became so complex that most of the non-technical end users cannot track the polic...
Page 116
98 building a network access control solution with ibm tivoli and cisco systems allows us to warn users if any noncompliance is found and explain the current desktop security policy requirement. This helps to keep users aware of the current security policy requirements and allow reporting on the com...
Page 117
Chapter 5. Solution design 99 abbc will institute posture-based network admission. Systems deemed in noncompliance will be quarantined and allowed to access only the remediation network. Figure 5-1 shows a conceptualized view of the functional requirements. Figure 5-1 nac solution conceptual functio...
Page 118
100 building a network access control solution with ibm tivoli and cisco systems 4. The security compliance manager client is armed with a remediation handler . The remediation handler provides a method of displaying the compliance posture data to the end user. In addition to informing the user of t...
Page 119
Chapter 5. Solution design 101 recommend that a process be in place for the normal notification and distribution of required workstation updates and corporate policies; for all but the most extreme cases, the life cycle management process includes a grace period. The deployment of the nac, along wit...
Page 120: 5.3.1 Logical Components
102 building a network access control solution with ibm tivoli and cisco systems integrated solution include the security compliance manager client/server componentry and the tivoli configuration manager remediation client/server code. In this section we see how these components map to the implement...
Page 121
Chapter 5. Solution design 103 with the web gateway component to allow for automated remediation at the workstation level without need of having tivoli framework endpoint installed. Again referencing figure 5-3 on page 102, note that the total solution is comprised of three major subsystems: the com...
Page 122
104 building a network access control solution with ibm tivoli and cisco systems establishing the policy collector parameters at this point, we have to establish the posture policy version because this has a direct bearing on how the network access control permissions will be set. Figure 5-4 shows a...
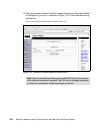
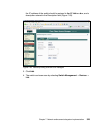
Page 123
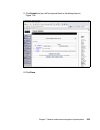
Chapter 5. Solution design 105 although the policy collector appears to be at a peer level with the posture collectors in figure 5-5, it is actually a hierarchical relationship, as shown in figure 5-4 on page 104. Figure 5-5 security compliance manager policy collector - edit collector parameters th...
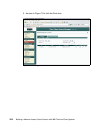
Page 124
106 building a network access control solution with ibm tivoli and cisco systems there are several parameters of interest: the policy_version parameter (figure 5-6) establishes the version level of the policy. This field is simply a string value. The company version control process is strictly a man...
Page 125
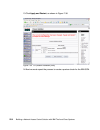
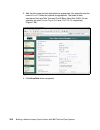
Chapter 5. Solution design 107 for abbc we set the parameter to 60 seconds. Effectively this forces the posture status to refresh itself at every challenge. Figure 5-8 shows the conceptual control flow for this parameter. Figure 5-8 max_data_age_secs conceptual flow c lie n t c h a lle n g e is s u ...
Page 126
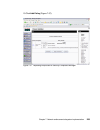
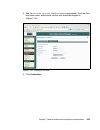
108 building a network access control solution with ibm tivoli and cisco systems the handler_attributes parameter (figure 5-9) establishes the url where the remediation handler will send the remediation request, as well as more attributes for the remediation handler. This field has to have a form of...
Page 127
Chapter 5. Solution design 109 the remediator_jar parameter (figure 5-10 on page 108) tells the class loader where the jar file is located for the remediation java class specified in the remediation_class attribute. This field is a simple string and should have the value of: collectors/com.Ibm.Scm.N...
Page 128
110 building a network access control solution with ibm tivoli and cisco systems focus on how our posture policy, as established by the tivoli security compliance manager, interrelates with the cisco secure access control server and how its associated polices form an interlocked security solution (f...
Page 129
Chapter 5. Solution design 111 in the posture validation policies, we check that a client has the correct minimum supported version of cta installed and is running the correct version of the security compliance manager policy (figure 5-13). Figure 5-13 posture validation policies for detailed inform...
Page 130
112 building a network access control solution with ibm tivoli and cisco systems those users that are in breach of these requirements, and how to remediate them back to a compliant state. Terms that are used include: network access profile a network access profile is a means to classify access reque...
Page 131
Chapter 5. Solution design 113 quarantine system posture token for a policy violation, he will be mapped to the quarantine_engineering_rac (vlan14). This allows for scalability and granularity. Figure 5-14 shared radius authorization components in our scenario, we list the cisco trust agent (cisco:p...
Page 132
114 building a network access control solution with ibm tivoli and cisco systems the cisco secure acs evaluates each of the authorization rules in order from top to bottom. The first match assigns the client the listed posture token. If no match is found, the default rule assigns the listed token. A...
Page 133
Chapter 5. Solution design 115 svis. Each shared radius authorization component had a corresponding acl defined on the nad. The example below shows the configuration used for the healthy engineering vlan and the quarantine sales vlan. Access-list 120 remark **healthy engineering vlan acls** access-l...
Page 134: 5.3.2 Physical Components
116 building a network access control solution with ibm tivoli and cisco systems see 8.4, “building the remediation workflows” on page 417, for information about the creation of the workflows for the ibm integrated security solution for cisco networks. Remediation handler html pages the remediation ...
Page 135
Chapter 5. Solution design 117 compliance subsystem the compliance subsystem has two major components: the ibm security compliance manager server the ibm security compliance manager client ibm security compliance manager server the required ibm security compliance manager server software is version ...
Page 136
118 building a network access control solution with ibm tivoli and cisco systems the system used by abbc for the security compliance manager server is: windows 2003 server enterprise edition with sp1 installed pentium® iv @ 3.0ghz cpu 512 mb of system memory 3 gb of free disk space ibm tivoli securi...
Page 137
Chapter 5. Solution design 119 operating system requirements for acs v4.0 are: windows 2000 server windows 2000 advanced server with the following conditions: – service pack 4 installed – without any feature specific to windows 2000 advanced server enabled or without microsoft clustering service ena...
Page 138
120 building a network access control solution with ibm tivoli and cisco systems nac-enabled network device the following layer 2 and layer 3 network devices are supported for a network admission control implementation. Layer 2 devices table 5-2 shows the supported layer 2 devices. Table 5-2 layer 2...
Page 139
Chapter 5. Solution design 121 cisco 2600xm series router cisco 2691 multiservice platform cisco 2800 series router cisco 3640 multiservice platform cisco 3660-ent series router cisco 3725 and 3745 multiservice access routers cisco 3800 series router cisco 7200 series router for the most up-to-date ...
Page 140
122 building a network access control solution with ibm tivoli and cisco systems remediation subsystem the remediation subsystem has three components: ibm tivoli configuration manager server software package web server remediation handler ibm tivoli configuration manager server the tivoli configurat...
Page 141: 5.4 Conclusion
Chapter 5. Solution design 123 ear file. This application must be installed on the same websphere application server as the web gateway component. Remediation handler in the current release of the solution, the remediation handler is delivered in the form of the security compliance manger collector ...
Page 142
124 building a network access control solution with ibm tivoli and cisco systems.
Page 143: Compliance Subsystem
© copyright ibm corp. 2005, 2007. All rights reserved. 125 chapter 6. Compliance subsystem implementation this chapter describes the ibm tivoli security compliance manager part of the network admission control (nac) solution, where the main concern is the establishment of security policy. We describ...
Page 144
126 building a network access control solution with ibm tivoli and cisco systems 6.1 tivoli security compliance manager setup tivoli security compliance manager server is an important component of the solution providing the policy management service to the client workstations. In the section below w...
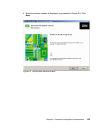
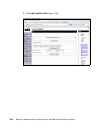
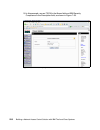
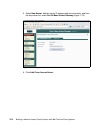
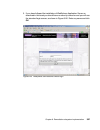
Page 145
Chapter 6. Compliance subsystem implementation 127 2. After a little while you are presented with the welcome window, as shown in figure 6-1. Click the install product selection on the left. Figure 6-1 db2 installation welcome window.
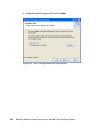
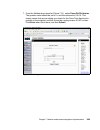
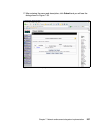
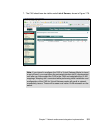
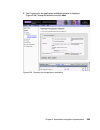
Page 146
128 building a network access control solution with ibm tivoli and cisco systems 3. The db2 version selection is presented similar to the one shown in figure 6-2. Depending on the media installation you use there may be more than one option presented. Select db2 udb enterprise server edition and cli...
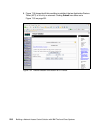
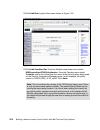
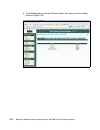
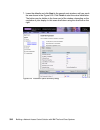
Page 147
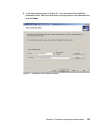
Chapter 6. Compliance subsystem implementation 129 4. Next the welcome window is displayed, as presented in figure 6-3. Click next. Figure 6-3 setup wizard welcome window.
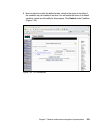
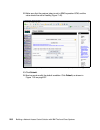
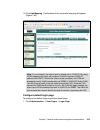
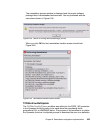
Page 148
130 building a network access control solution with ibm tivoli and cisco systems 5. On the next dialog you are presented with the standard license agreement (figure 6-4). Accept the license and click next. Figure 6-4 license agreement window.
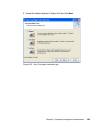
Page 149
Chapter 6. Compliance subsystem implementation 131 6. In the installation type selection window (figure 6-5) leave all of the default values (which is typical installation) and click next. Figure 6-5 installation type selection window.
Page 150
132 building a network access control solution with ibm tivoli and cisco systems 7. On the next dialog, shown in figure 6-6, you are presented with the installation action selection, where there are two options: install the product which is selected by default save your settings which will save your...
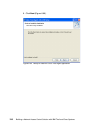
Page 151
Chapter 6. Compliance subsystem implementation 133 8. In the next window, shown in figure 6-7, you must select the installation destination folder. Make sure that there is enough space on the selected drive and click next. Figure 6-7 installation folder selection window.
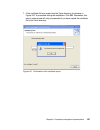
Page 152
134 building a network access control solution with ibm tivoli and cisco systems 9. In the next dialog, shown in figure 6-8, you must provide user information. We strongly recommend leaving the default user name db2admin. In the next two fields provide the password for this user. Make sure that you ...
Page 153
Chapter 6. Compliance subsystem implementation 135 10.In the next dialog, depicted in figure 6-9, you are presented with the administration contact configuration options, where you may specify names of the users who should be notified by the database if something goes wrong. If you leave the default...
Page 154
136 building a network access control solution with ibm tivoli and cisco systems 11.In the next window, shown in figure 6-10, you can modify the db2 instance configuration options. You can explore the protocols settings and change the startup options. The default instance name on windows is db2, the...
Page 155
Chapter 6. Compliance subsystem implementation 137 12.As we do not need to use any db2 tools on the next dialog, shown in figure 6-11, click next. Figure 6-11 db2 tools selection dialog.
Page 156
138 building a network access control solution with ibm tivoli and cisco systems 13.In the next window, presented in figure 6-12, you can provide the contact information for a user to receive the database health notifications. Select the option to defer this task until after installation is complete...
Page 157
Chapter 6. Compliance subsystem implementation 139 14.In the next window, shown in figure 6-13, you are given a last chance to review your selected options. If everything is as you want, click install. Figure 6-13 installation options summary.
Page 158
140 building a network access control solution with ibm tivoli and cisco systems 15.The installation may take a few minutes depending on the configuration of your server. When it is complete you are presented with the final window, shown in figure 6-14. When you click finish there may be additional ...
Page 159
Chapter 6. Compliance subsystem implementation 141 2. The usual language selection box is presented, as shown on figure 6-15. Accept english and click next. Figure 6-15 language selection dialog 3. Click next on the tivoli security compliance manager welcome window, which is presented next. There wi...
Page 160
142 building a network access control solution with ibm tivoli and cisco systems 4. In the next window, shown in figure 6-17, specify the destination directory for the tivoli security compliance manager installation. Accept the default, which is c:\program files\ibm\scm, and click next. Figure 6-17 ...
Page 161
Chapter 6. Compliance subsystem implementation 143 tivoli security compliance manager server installation. This is a recommended option in large scale deployments. For this installation we must have all three components installed, so select the second option server, as presented on figure 6-18, and ...
Page 162
144 building a network access control solution with ibm tivoli and cisco systems 6. You are presented the e-mail server configuration dialog, as shown in figure 6-19. The tivoli security compliance manager server uses e-mails to notify the administrators of the violations found, as well as for distr...
Page 163
Chapter 6. Compliance subsystem implementation 145 7. In the next window, shown on figure 6-20, the installation wizard asks for the communication ports the server uses to communicate with the clients. We strongly recommend leaving the defaults. Click next. Figure 6-20 server communication configura...
Page 164
146 building a network access control solution with ibm tivoli and cisco systems 8. The server security configuration window is displayed, as shown in figure 6-21. In the system name certificate field you must provide the system name that will be used to generate the self-signed certificate for the ...
Page 165
Chapter 6. Compliance subsystem implementation 147 9. In the next window, presented in figure 6-22, select the location for your database. If you installed db2 as described in 6.1.1, “installation of db2 database server” on page 126, select the database is on the local system option and click next. ...
Page 166
148 building a network access control solution with ibm tivoli and cisco systems 10.In the next dialog, provide the database configuration information, as shown in figure 6-23. Enter the username and password for the db2 administrator you have provided in step 9 on page 134. Leave the other fields w...
Page 167
Chapter 6. Compliance subsystem implementation 149 11.In the next dialog, shown in figure 6-24, you are asked whether the database should be created during this installation. Make sure that the check box is marked and click next. Figure 6-24 database creation choice window.
Page 168
150 building a network access control solution with ibm tivoli and cisco systems 12.The next dialog allows you to specify an administrator user id and password for tivoli security compliance manager server, as shown in figure 6-25. Use the name admin and enter a password of your choice. This user id...
Page 169
Chapter 6. Compliance subsystem implementation 151 13.Finally you are presented with the installation selection summary, as shown in figure 6-26. Click next to start the actual installation. Figure 6-26 installation options summary window.
Page 170
152 building a network access control solution with ibm tivoli and cisco systems 14.The installation itself is very fast, but the database creation process may take a while. You may see the black command line window popping up listing the db2 command execution results. Do not close this window. When...
Page 171: 6.2.1 Posture Collectors
Chapter 6. Compliance subsystem implementation 153 the user password settings on the client workstation have to be following the policy, which means that the password must be at least eight characters in length and it must be renewed at least every 90 days. The appropriate operating system service p...
Page 172: 6.2.2 Policy Collector
154 building a network access control solution with ibm tivoli and cisco systems the status of a posture element can be one of the following: pass the data collection was successful, and the security posture of the selected item matches the required value. Fail the data collection was successful, bu...
Page 173
Chapter 6. Compliance subsystem implementation 155 remediation subsystem, such as a tivoli configuration manager. After the remediation has been performed, the remediation subsystem communicates to the policy collector to obtain updated status and, if necessary, perform additional remediation. 6.2.3...
Page 174
156 building a network access control solution with ibm tivoli and cisco systems 3. When the gui pops up, as shown on figure 6-28, log in with the credentials you specified during the installation, as described in step 12 on page 150 in the installation of tivoli security compliance manager server p...
Page 175
Chapter 6. Compliance subsystem implementation 157 5. You are presented with the default message of the day window, which by default contains only the information about the tivoli security compliance manager version. Click ok. On the main administrative console window, as shown on figure 6-30, switc...
Page 176
158 building a network access control solution with ibm tivoli and cisco systems 7. Navigate to the sample_polices directory created in step 1 and select the tcmcli.Pol file, as shown in figure 6-32. Click import. Figure 6-32 import file selection dialog 8. In the next dialog, presented in figure 6-...
Page 177
Chapter 6. Compliance subsystem implementation 159 9. In the next step the import wizard performs a validation of the signatures of the collectors included with the policy. When it is completed, as shown in figure 6-34, click next. Figure 6-34 collectors signature validation.
Page 178
160 building a network access control solution with ibm tivoli and cisco systems 10.Now the actual policy installation is performed. Depending on the collectors you have already installed in your environment you may be asked if the existing collectors should be overwritten with the new ones included...
Page 179
Chapter 6. Compliance subsystem implementation 161 11.After the wizard is closed you will see the imported policy in the administrative console, as shown in figure 6-36. Figure 6-36 compliance policy view to import the additional two sample policies named iisscn_tcm_v2.00_winxp.Pol and iisscn_tcm_v2...
Page 180
162 building a network access control solution with ibm tivoli and cisco systems must be evaluated on each client workstation. This is the reason why the appropriate values must be supplied as parameters for the nac collectors rather then in the sql query in the compliance object definition. 1. To s...
Page 181
Chapter 6. Compliance subsystem implementation 163 2. In the right pane click the collectors tab and select the symantec antivirus collector, as shown on figure 6-38. Figure 6-38 collectors configuration view 3. The collector responsible for the symantec antivirus policy check is named nac.Win.Any.N...
Page 182
164 building a network access control solution with ibm tivoli and cisco systems the different conditions are: – version of the symantec antivirus software – last scan date – age of the latest virus definition file there are nine parameters regulating the behavior of the collector, as described in t...
Page 183
Chapter 6. Compliance subsystem implementation 165 to adjust the parameters to your need modify the operational parameters, selecting the appropriate tabs. To add additional values to the parameter click the plus (+) sign. To remove a value click the minus (-) sign. Do not change the default names o...
Page 184
166 building a network access control solution with ibm tivoli and cisco systems there are six parameters regulating the behavior of the collector, which are described in table 6-2. Table 6-2 parameter information for nac.Win.Any.Netaccounts.Posturenetaccountsv2 for the purpose of the book we requir...
Page 185
Chapter 6. Compliance subsystem implementation 167 when you are done editing click save. 5. The next policy we customize is the one that checks for the appropriate operating system service pack level installed on the client workstation. Back at the list of the collectors right-click the windows serv...
Page 186
168 building a network access control solution with ibm tivoli and cisco systems 6. The parameters for the collector nac.Win.Any.Oslevel.Postureoslevelv2 are displayed, as shown in figure 6-42. Figure 6-42 parameters for windows service pack collector as you can see, this is a generic collector for ...
Page 187
Chapter 6. Compliance subsystem implementation 169 the operational parameters listed above accept multiple values, so edit the appropriate parameters by selecting the proper tabs and adding all the versions accepted in your environment. To add additional values to the parameter click the plus (+) si...
Page 188
170 building a network access control solution with ibm tivoli and cisco systems back at the list of the collectors right-click the windows hotfixes collector. Then click edit collector parameters. The parameters for collector nac.Win.Any.Hotfix.Posturehotfixv2 are displayed as shown in figure 6-43....
Page 189
Chapter 6. Compliance subsystem implementation 171 8. The next policy we configure checks whether the personal firewall is installed and running. Since we are using the generic posture collectors, this policy was implemented as two separate policies, one for checking the registry if the firewall is ...
Page 190
172 building a network access control solution with ibm tivoli and cisco systems no_key_rule operational used to determine the status of the registry key existence check if the registry key specified in key is not found. No more than one parameter value should be provided. If more than one parameter...
Page 191
Chapter 6. Compliance subsystem implementation 173 the way this collector works depends on the data you have provided as parameters. It first checks for the key existence if one is specified. Then it checks if the value is specified. Finally, if both are found, it verifies the rules specified in val...
Page 192
174 building a network access control solution with ibm tivoli and cisco systems rules rules are used to evaluate the detected registry value and determine the status of the registry value data element. All rules conform to simple rule grammar, and are composed of the following: a rule operator a ru...
Page 193
Chapter 6. Compliance subsystem implementation 175 there are some limitations on numeric context evaluations. The collector initially receives all values from the underlying utilities as strings. For example, even though the registry type might be reg_dword and the value is set to 0x00000630, the co...
Page 194
176 building a network access control solution with ibm tivoli and cisco systems value equal to installdirectory. No_key_rule equal to fail. No_value_rule equal to fail. Since you do not care about the actual value, but only of its existence, the value_data_rules must be set to: *;pass if any of the...
Page 195
Chapter 6. Compliance subsystem implementation 177 when you are done with editing the parameters for the nac.Win.Any.Regkey.Postureregkeyv2 collector click save. 1. The second part of the firewall policy is meant to check whether the firewall service is running. This policy is checked using the gene...
Page 196
178 building a network access control solution with ibm tivoli and cisco systems to configure the policy with the right service name check it in the services window on the client workstation and then enter the exact value on the req_service tab. In our lab we will check for truevector internet monit...
Page 197
Chapter 6. Compliance subsystem implementation 179 – service_running_wf equal to tcrzlsoftwarerunning – req_disabled not set – service_disabled_wf not set when you are done editing click save. 2. According to our security policy outlined in “security compliance criteria” on page 100 we must add one ...
Page 198
180 building a network access control solution with ibm tivoli and cisco systems the new dialog is presented, as shown in figure 6-47. Select the destination policy for the copy process of the compliance query. Select iisscn_tcm_v2.00_winxp, which is also the source for this compliance query, and cl...
Page 199
Chapter 6. Compliance subsystem implementation 181 there cannot be two compliance queries with the same name in one policy, so the copy of the compliance query is automatically renamed. It received an added _0 suffix. We must rename our new compliance query. Right-click the new zonealarm firewall ac...
Page 200
182 building a network access control solution with ibm tivoli and cisco systems in the following dialog modify the name value to messenger service disabled and click ok. Then, in the right pane, modify the description of the compliance query, as shown on figure 6-49, and click the save button on th...
Page 201
Chapter 6. Compliance subsystem implementation 183 next select the compliance sql tab on the right pane and modify the violation message generated by the compliance check, as shown in figure 6-50. There is no need to change the sql compliance query itself, as it does not refer to any values other th...
Page 202
184 building a network access control solution with ibm tivoli and cisco systems collector as well. Right-click the zonealarm firewall active name under messenger service disabled and click stop sharing collector item from the pop-up menu, as shown in figure 6-51. Figure 6-51 disabling collector sha...
Page 203
Chapter 6. Compliance subsystem implementation 185 now we must change the parameters for the new collector instance. Right-click the messenger service disabled collector instance and click edit collector parameters from the pop-up menu. The parameters were described in table 6-7 on page 177. Provide...
Page 204
186 building a network access control solution with ibm tivoli and cisco systems you are presented with a warning that the changes will affect all of the clients that have this policy assigned, as shown in figure 6-54. Figure 6-54 save policy collectors warning click yes to have your changes saved. ...
Page 205
Chapter 6. Compliance subsystem implementation 187 the steps are: 1. When logged into the tivoli security compliance manager administration console with administrative privileges select the clients tab and click the actions → group → create group menu item, as shown in figure 6-55. Figure 6-55 creat...
Page 206
188 building a network access control solution with ibm tivoli and cisco systems 3. Assign the policy to this new group. Select the group in the navigation tree in the left pane and click actions → policy → add policy, as shown in figure 6-57. Figure 6-57 add policy menu selection 4. The select a po...
Page 207
Chapter 6. Compliance subsystem implementation 189 5. An informational dialog is displayed, as shown in figure 6-59, showing the successful completion. To close it click ok. Figure 6-59 operation complete dialog 6. Repeat steps 3 to 5 to select the tcmcli policy this time. When you have your group s...
Page 208: 6.3.1 Cisco Trust Agent
190 building a network access control solution with ibm tivoli and cisco systems book we cover only the installation of the client on windows. For other platforms and more detailed system prerequisites see tivoli security compliance manager: installation guide: client component, gc32-1593. A prerequ...
Page 209
Chapter 6. Compliance subsystem implementation 191 the installation of the certificate that is required for secure communication with the cisco secure acs can be performed during the installation of the cisco trust agent or later using the ctacert.Exe utility. To have the certificate installed durin...
Page 210
192 building a network access control solution with ibm tivoli and cisco systems installation of cisco trust agent on windows the cisco trust agent installation uses the microsoft windows installer (msi) and requires administrator privileges. 1. Start the installation process by double-clicking the ...
Page 211
Chapter 6. Compliance subsystem implementation 193 3. The license agreement is presented, as shown in figure 6-63. Select i accept the license agreement and click next. Figure 6-63 license agreement for cisco trust agent.
Page 212
194 building a network access control solution with ibm tivoli and cisco systems 4. Accept the defaults (figure 6-64) and click next. Figure 6-64 cisco trust agent destination folder selection.
Page 213
Chapter 6. Compliance subsystem implementation 195 5. Accept the default depicted in figure 6-65 and click next. Figure 6-65 cisco trust agent installation type.
Page 214
196 building a network access control solution with ibm tivoli and cisco systems 6. Click next (figure 6-66). Figure 6-66 ready to install the cisco trust agent application.
Page 215
Chapter 6. Compliance subsystem implementation 197 7. If the certificate file was copied into the certs directory, the window in figure 6-67 is presented during the installation. Click ok. Remember, this step is optional and will only be presented if you have copied the certificate file to the certs...
Page 216
198 building a network access control solution with ibm tivoli and cisco systems 8. Click finish to close the installation, as shown in figure 6-68. Figure 6-68 successful completion of cisco trust agent installation 9. If you have not created a certs directory before the installation as described i...
Page 217
Chapter 6. Compliance subsystem implementation 199 if the certificate has been successfully imported, the window shown in figure 6-69 is displayed. Figure 6-69 successful certificate import the last element required by the cisco trust agent to perform its role is the posture plug-in. In our scenario...
Page 218
200 building a network access control solution with ibm tivoli and cisco systems the security compliance manager client installation requires the following media: security compliance manager 5.1.0.30 client base installation image. Installation of the security compliance manager client the procedure...
Page 219
Chapter 6. Compliance subsystem implementation 201 2. The security compliance manager welcome screen appears momentarily (figure 6-71). Figure 6-71 the welcome window.
Page 220
202 building a network access control solution with ibm tivoli and cisco systems 3. The client installation utility window appears, as depicted in figure 6-72. After carefully reading all of the required information, click next. Figure 6-72 client installation utility window.
Page 221
Chapter 6. Compliance subsystem implementation 203 4. The license agreement window is displayed (figure 6-73). Select i accept the terms in the license agreement and click next. Figure 6-73 license agreement for ibm tivoli security compliance manager.
Page 222
204 building a network access control solution with ibm tivoli and cisco systems 5. Accept the default destination folder, shown in figure 6-74, and click next. Figure 6-74 directory selection window.
Page 223
Chapter 6. Compliance subsystem implementation 205 6. Accept the default client installation (figure 6-75) and click next. Figure 6-75 setup type window.
Page 224
206 building a network access control solution with ibm tivoli and cisco systems 7. In the ibm security solution for cisco networks window (figure 6-76), ensure that the box select the checkbox to install ibm integrated security solution for cisco networks is checked, then click next figure 6-76 the...
Page 225
Chapter 6. Compliance subsystem implementation 207 figure 6-77 client connection window.
Page 226
208 building a network access control solution with ibm tivoli and cisco systems 9. The server communication configuration window, shown in figure 6-78, is used to provide the client with the location information of the server. In the server host name field insert the fully qualified name of the sec...
Page 227
Chapter 6. Compliance subsystem implementation 209 10.If you selected the dhcp option in the previous step, you will see the client dhcp configuration dialogue, as in figure 6-79. In the dhcp client alias field, provide the alias name for the client. This name will be shown on the security complianc...
Page 228
210 building a network access control solution with ibm tivoli and cisco systems 11.Finally, the installation summary window is displayed (figure 6-80). Click next. Figure 6-80 security compliance manager client installation summary window.
Page 229
Chapter 6. Compliance subsystem implementation 211 12.The security compliance manager client is successfully installed. Click finish to close the window shown in figure 6-81 to complete this step of the process. Figure 6-81 successful completion window.
Page 230: 6.4 Conclusion
212 building a network access control solution with ibm tivoli and cisco systems 13.If you want to verify that the security compliance manager posture plug-in was registered successfully with the cisco trust agent, check the c:\program files\common files\postureagent\plugins directory. The ibmnac6.D...
Page 231: Network Enforcement
© copyright ibm corp. 2005, 2007. All rights reserved. 213 chapter 7. Network enforcement subsystem implementation this chapter contains detailed descriptions for the installation and configuration of the following network enforcement subsystem components: configuring nac framework components – conf...
Page 232
214 building a network access control solution with ibm tivoli and cisco systems 7.1 configuring nac framework components this section focuses on the deployment of nac framework. Nac framework can be deployed as nac l3 ip, nac l2 ip, or nac l2 802.1x. Configure the cisco secure acs for nac l2 802.1x...
Page 233
Chapter 7. Network enforcement subsystem implementation 215 installing cisco secure acs to install cisco secure acs version 4.0 software on a machine running a supported operating system, run the setup.Exe program provided with the cisco secure acs installation software. When you install cisco secur...
Page 234
216 building a network access control solution with ibm tivoli and cisco systems configuring the administrative interface to cisco secure acs by default, not all features and options of the cisco secure acs administrator interface are enabled. The advanced features required by the ibm integrated sec...
Page 235
Chapter 7. Network enforcement subsystem implementation 217 – network access filtering this option enables the appearance of the network access filtering option under the shared profile components window. This allows a network to have different enforcement policies downloaded for applications to a c...
Page 236
218 building a network access control solution with ibm tivoli and cisco systems allowing administrator access via http (optional) if you want to configure acs from a remote client using the web interface, you must configure at least one administrator user name and password: 1. Click administration ...
Page 237
Chapter 7. Network enforcement subsystem implementation 219 2. Fill in the user name and password fields, and click grant all to give all configuration rights to the administrator. If desired, an administrator’s privileges can be limited to individual groups and components in order to have separate ...
Page 238
220 building a network access control solution with ibm tivoli and cisco systems cisco secure acs uses the certificate store that is built into the windows operating system. The server certificate may be installed in several ways. If you have an external public/private ca, you can add the ca to the ...
Page 239
Chapter 7. Network enforcement subsystem implementation 221 to use a self-signed certificate, perform the following steps: 1. Click generate self-signed certificate in the cisco secure acs certificate setup window (figure 7-6). Figure 7-6 generating self-signed certificate 2. Fill in the blanks with...
Page 240
222 building a network access control solution with ibm tivoli and cisco systems 4. Restart the cisco secure acs (figure 7-7). Figure 7-7 restart cisco secure acs.
Page 241
Chapter 7. Network enforcement subsystem implementation 223 5. After completing the certificate setup process and installation, verify that the certificate has been installed by clicking install acs certificate from the acs certificate setup screen (figure 7-8). Figure 7-8 self-signed certificate in...
Page 242
224 building a network access control solution with ibm tivoli and cisco systems to import security compliance manager attributes, perform the following steps: 1. Copy the security compliance manager attributes definition file to a directory accessible to the cisco secure acs. Example 7-1 shows the ...
Page 243
Chapter 7. Network enforcement subsystem implementation 225 filename is the name of the file in which you want csutil.Exe to write all attribute definitions. Example 7-2 shows the execution of this command. Example 7-2 import security compliance manager attribute c:\program files\ciscosecure acs v4....
Page 244
226 building a network access control solution with ibm tivoli and cisco systems filename is the file that the attributes will be written to. The security compliance manager attributes should be viewable in this file. Configuring logging logging configuration is crucial for monitoring, reporting, an...
Page 245
Chapter 7. Network enforcement subsystem implementation 227 that you wish to include in the log file. Scroll down and change the file management settings if desired. We recommend that you include the following fields in logged attribute: – network access profile name – shared rac – application postu...
Page 246
228 building a network access control solution with ibm tivoli and cisco systems 6. Click the log to csv failed attempts report under enable logging. Repeat step 4 on page 226, selecting the items you wish to log. A selection is shown in figure 7-11. Figure 7-11 failed attempts logging 7. Click syst...
Page 247
Chapter 7. Network enforcement subsystem implementation 229 8. In the window in under services log file configuration (figure 7-12) change level of detail to full, and increase the file size from 2048 kb as necessary. Click restart to apply the new configuration. Figure 7-12 log file management conf...
Page 248
230 building a network access control solution with ibm tivoli and cisco systems it is possible to group the nads into network device groups (ndgs) for location or service-based filtering. To do this, the use of ndgs must first be enabled: 1. Click interface configuration from the main menu (figure ...
Page 249
Chapter 7. Network enforcement subsystem implementation 231 2. Select advanced options (figure 7-13 on page 230). Ensure that network device groups is checked (figure 7-14). Figure 7-14 network device group check box.
Page 250
232 building a network access control solution with ibm tivoli and cisco systems 3. Select network configuration in the main menu. The screen in figure 7-15 is shown. Figure 7-15 network configuration 4. (optional) select add entry under network device groups (figure 7-15). 5. (optional) add the nam...
Page 251
Chapter 7. Network enforcement subsystem implementation 233 6. From the network configuration screen, select the hyperlink under network device groups. If you did not assign a name in step 5, you will see not assigned as the name (figure 7-15 on page 232). By clicking this link, you will see the aaa...
Page 252
234 building a network access control solution with ibm tivoli and cisco systems 7. Click add entry under aaa clients to add any aaa clients to this particular ndg. You can configure all nads as a single aaa client by using ip address wild cards (*.*.*.*). In figure 7-17 we have done this and used t...
Page 253
Chapter 7. Network enforcement subsystem implementation 235 8. You should now see the newly defined aaa clients (figure 7-18). Figure 7-18 aaa clients.
Page 254
236 building a network access control solution with ibm tivoli and cisco systems configuring radius attributes the radius attributes required for nac must be globally enabled on the cisco secure acs. 1. Select interface configuration from the main menu (figure 7-13 on page 230), then select radius (...
Page 255
Chapter 7. Network enforcement subsystem implementation 237 2. From the interface configuration menu, select radius (cisco ios/pix 6.0) (figure 7-20). Figure 7-20 cisco ios/pix 6.0 radius attributes for l2dot1x nac, you must select [026/009/001] cisco-av-pair. 3. After selecting this item, click sub...
Page 256
238 building a network access control solution with ibm tivoli and cisco systems active directory, for example. To configure groups and vendor-specific attributes, complete these steps: 1. Click group setup on the cisco secure acs main menu. 2. Choose any unused groups, and rename each group as appl...
Page 257
Chapter 7. Network enforcement subsystem implementation 239 configuring users now that the groups have been defined, we can create our users and then add them to their relevant group. 1. From the main menu select user setup, as shown in figure 7-22. Figure 7-22 user setup 2. In the user field, type ...
Page 258
240 building a network access control solution with ibm tivoli and cisco systems 3. You will be prompted for the user’s real name and description under supplementary user info, followed by user setup details , as shown in figure 7-23. The password authentication, in this example, is set to acs inter...
Page 259
Chapter 7. Network enforcement subsystem implementation 241 global authentication setup the cisco secure acs supports many types of protocols for securely transferring credentials from the host to the cisco secure acs for authentication and authorization. 1. Click system configuration from the main ...
Page 260
242 building a network access control solution with ibm tivoli and cisco systems 4. Click eap-fast configuration from the global authentication setup (figure 7-24 on page 241). Figure 7-25 eap-fast configuration screen 5. The eap-fast configuration, as shown in figure 7-25, requires you to enter a l...
Page 261
Chapter 7. Network enforcement subsystem implementation 243 6. Click submit + restart. Require client certificate for provisioning checked allow machine authentication checked machine pac ttl one week allow stateless session resume checked authorization pac ttl one hour allow inner methods eap-gtc c...
Page 262
244 building a network access control solution with ibm tivoli and cisco systems configuring posture validation to do this: 1. Select posture validation from the main menu (figure 7-26). Figure 7-26 posture validation.
Page 263
Chapter 7. Network enforcement subsystem implementation 245 2. Select internal posture validation. The screen show in figure 7-27 will be displayed. 3. Click add policy (figure 7-27). Figure 7-27 posture validation policies.
Page 264
246 building a network access control solution with ibm tivoli and cisco systems 4. In this example, we have entered the name of the first policy as cta with the description cisco trust agent. Then click submit (figure 7-28). Figure 7-28 cta posture validation policy.
Page 265
Chapter 7. Network enforcement subsystem implementation 247 5. Click add rule (figure 7-29). Figure 7-29 posture validation for cta.
Page 266
248 building a network access control solution with ibm tivoli and cisco systems 6. Click add condition set (figure 7-30). Figure 7-30 condition sets for cta policy.
Page 267
Chapter 7. Network enforcement subsystem implementation 249 7. From the attribute drop-down list (figure 7-31), select cisco:pa:pa-version. The operator value should be set to >= and the value set to 2.0.0.0. This simply means that we are setting up a check for the cisco trust agent to be present on...
Page 268
250 building a network access control solution with ibm tivoli and cisco systems 8. Figure 7-32 shows that if this condition is satisfied, that an application posture token (apt) of healthy is returned. Clicking submit here takes us to figure 7-33 on page 251. Figure 7-32 posture validation rule cre...
Page 269
Chapter 7. Network enforcement subsystem implementation 251 9. Next we need to modify the default action, which is the action to be taken if the condition we just created is not met. You will notice that there is a default condition, which we will modify for this purpose. Click default under conditi...
Page 270
252 building a network access control solution with ibm tivoli and cisco systems 10.The posture token remains cisco:pa, however the posture token value should be changed to quarantine , as shown in figure 7-34. In the notification string, add the line: http://tcmweb/softwarepackageserverweb/spservle...
Page 271
Chapter 7. Network enforcement subsystem implementation 253 11.Click submit and you will find yourself back in the dialog shown in figure 7-35. Figure 7-35 completed posture validation for cta 12.Click done..
Page 272
254 building a network access control solution with ibm tivoli and cisco systems 13.Click apply and restart, as shown in figure 7-36. Figure 7-36 cta posture validation policy 14.Next we must repeat the process to create a posture check for the ibm:scm..
Page 273
Chapter 7. Network enforcement subsystem implementation 255 15.Click add policy (figure 7-37). Figure 7-37 repeating the process for security compliance manager.
Page 274
256 building a network access control solution with ibm tivoli and cisco systems 16.In this example, we use tscm in the name field and ibm security compliance in the description field, as shown in figure 7-38. Figure 7-38 ibm tscm policy creation.
Page 275
Chapter 7. Network enforcement subsystem implementation 257 17.After entering the name and description, click submit and you will see the dialog shown in figure 7-39. Figure 7-39 ibm tscm policy creation.
Page 276
258 building a network access control solution with ibm tivoli and cisco systems 18.Click add rule to get to the screen shown in figure 7-40. Figure 7-40 condition set creation for tscm 19.Click add condition set. From the attribute drop-down menu, select ibmcorporation:scm:policyversion. From the o...
Page 277
Chapter 7. Network enforcement subsystem implementation 259 20.From the attribute drop-down menu, select ibmcorporation:scm:policyviolation. From the operator menu select = , and for the value enter 0 . Then click enter (figure 7-41). Figure 7-41 tscm policy components 21.Click submit..
Page 278
260 building a network access control solution with ibm tivoli and cisco systems 22.Make sure that the posture token is set to ibmcorporation:scm, and the value should be set to healthy (figure 7-42). Figure 7-42 completed posture validation check for security compliance manager 23.Click submit. 24....
Page 279
Chapter 7. Network enforcement subsystem implementation 261 25.The posture token should be set to ibmcorporation:scm (figure 7-43) and the value should be set to quarantine . The notification string should be the same as we discussed in step 10 on page 252 of this section: http://tcmweb/softwarepack...
Page 280
262 building a network access control solution with ibm tivoli and cisco systems 27.Click done (figure 7-44). Figure 7-44 completed security compliance manager posture validation.
Page 281
Chapter 7. Network enforcement subsystem implementation 263 28.Click apply and restart (figure 7-45). Figure 7-45 completed posture validation rules.
Page 282
264 building a network access control solution with ibm tivoli and cisco systems configuring radius authorization components in this section we configure radius authorization components (ras), a new concept introduced with cisco secure acs 4.0. 1. Click shared profile components from the main menu. ...
Page 283
Chapter 7. Network enforcement subsystem implementation 265 3. Click add. 4. To create the healthy sales rac, in the name field type healthy_sales_rac . 5. In the add new attribute section, we are using the drop-down menus to add the required values, which are described in table 7-2. Table 7-2 healt...
Page 284
266 building a network access control solution with ibm tivoli and cisco systems 6. Click add next to cisco ios/pix6.0, which brings you to figure 7-47. Figure 7-47 ios rac attribute 7. In the value field, enter status-query-timeout=30 . 8. Click submit. 9. Repeat this procedure, clicking add next t...
Page 285
Chapter 7. Network enforcement subsystem implementation 267 10.Repeat the same procedure for the ietf attributes, first selecting the relevant field from the drop-down menu, then clicking add (figure 7-48). Use the values in table 7-2 on page 265. Figure 7-48 ietf drop-down menu.
Page 286
268 building a network access control solution with ibm tivoli and cisco systems 11.When completed, your healthy sales rac should look like figure 7-49. Figure 7-49 healthy sales rac 12.Click submit. 13.Repeat steps 3 through to 12 for each of the racs to be configured. Using our example, there are ...
Page 287
Chapter 7. Network enforcement subsystem implementation 269 table 7-4 quarantine sales rac attributes table 7-5 quarantine engineering rac attributes table 7-6 default quarantine rac attributes ietf tunnel-private-group-id (81) [t1] 12 vendor attribute value cisco ios/pix 6.0 cisco-av-pair (1) statu...
Page 288
270 building a network access control solution with ibm tivoli and cisco systems ietf termination-action (29) radius-request(1) ietf tunnel-type (64) [t1] vlan (13) ietf tunnel-medium-type (65) [t1] 802 (6) ietf tunnel-private-group-id (81) [t1] 15 note: the dot1x reauthentication timer is controlle...
Page 289
Chapter 7. Network enforcement subsystem implementation 271 configuring network access profiles we have now configured all of the individual components to be in a position to bring them together and create the network access profiles, which determine what to check and what action to take based on th...
Page 290
272 building a network access control solution with ibm tivoli and cisco systems 4. The newly created nap is shown (figure 7-51) with the three policies that comprise the nap — authentication , posture validation, and authorization . Each of these will have to be configured in turn, after clicking a...
Page 291
Chapter 7. Network enforcement subsystem implementation 273 5. Click authentication. Click the tab populate from global and ensure that posture validation - required is set. Selected databases should contain acs internal database (figure 7-52). Figure 7-52 authentication configuration for rac 6. Cli...
Page 292
274 building a network access control solution with ibm tivoli and cisco systems 8. From the screen shown in figure 7-53, click add rule. Figure 7-53 posture validation rule creation 9. Add a name in the name field. In our example we used nac_iisscn_posture_profile..
Page 293
Chapter 7. Network enforcement subsystem implementation 275 10.Under condition → required credential types, there is a list of available credentials. Select ibmcorporation:scm, then click the arrow ( → )to move this to the column for selected credentials, as shown in figure 7-54. Repeat this process...
Page 294
276 building a network access control solution with ibm tivoli and cisco systems 11.Scrolling down the page to action → selected internal posture validation policies, cta and tscm should already be present. The only action required here is to check them both under select (figure 7-55). Figure 7-55 s...
Page 295
Chapter 7. Network enforcement subsystem implementation 277 an example of the cta healthy pop-up is shown in figure 7-56. Figure 7-56 example of cta healthy pop-up 13.(optional) under system posture token configuration , add the following syntax in the quarantine pa message (this process is depicted...
Page 296
278 building a network access control solution with ibm tivoli and cisco systems figure 7-58 cta pop-up configuration 14.Click submit. Note: steps 12 and 13 are optional because they are simply embedding some color in the cta pop-ups on the end user’s workstation. You can tailor this so that you can...
Page 297
Chapter 7. Network enforcement subsystem implementation 279 figure 7-59 completed posture validation for nac_iisscn 15.Click done. This will take you back to the screen shown in figure 7-50 on page 271. Click apply and restart..
Page 298
280 building a network access control solution with ibm tivoli and cisco systems 16.From the screen shown in figure 7-51 on page 272, click authorization. This takes you to the dialog depicted in figure 7-60. Figure 7-60 authorization rule creation 17.Click add rule. 18.For this example, from the dr...
Page 299
Chapter 7. Network enforcement subsystem implementation 281 21.Click submit (figure 7-61). Figure 7-61 healthy sales spt creation 22.Repeat this process to create additional authorization rules using the information provided in table 7-7. Table 7-7 authorization rules note: remember that this scenar...
Page 300
282 building a network access control solution with ibm tivoli and cisco systems 23.Your screen should look similar to that in figure 7-62. Figure 7-62 completed authorization rac configuration 24.Click submit. 25.This will take you back to the screen in figure 7-51 on page 272. Click apply and rest...
Page 301
Chapter 7. Network enforcement subsystem implementation 283 external user database one of the most common methods of deploying an acs is to use an external user database, such as active directory, or using a token server, for user and machine authentication. We did not use this method in the writing...
Page 302
284 building a network access control solution with ibm tivoli and cisco systems downloadable access control lists nac l2/l3 ip uses eapoudp (eou), which allows for acls to be downloaded from the acs to the nad. In our example, the nad will be a cisco 3750 switch. The acls are downloaded on a per-us...
Page 303
Chapter 7. Network enforcement subsystem implementation 285 5. Add a name and description in the name and description fields as appropriate (figure 7-64). After this has been done, click add. Figure 7-64 naming of acl.
Page 304
286 building a network access control solution with ibm tivoli and cisco systems 6. Enter the name of the acl and the acl definition (figure 7-65). Figure 7-65 quarantine acl definitions 7. Click submit..
Page 305
Chapter 7. Network enforcement subsystem implementation 287 8. Note that there is an option of binding the acl just created to a network access filter (figure 7-66). This allows for different acls to be applied to different items. We are not using network filtering, so we leave the default (all-aaa-...
Page 306
288 building a network access control solution with ibm tivoli and cisco systems 3. Repeat step 3 on page 265 to step 12 on page 268, using the values listed in table 7-8 and table 7-9. We used the names healthy_l2ip_rac and quarantine_l2ip_rac. Table 7-8 l2 ip healthy rac values table 7-9 l2 ip qua...
Page 307
Chapter 7. Network enforcement subsystem implementation 289 configuring network access profiles we have now configured all the individual components to be in a position to bring them together and create the network access profiles, which determine what to check and what action to take based on the r...
Page 308
290 building a network access control solution with ibm tivoli and cisco systems 6. From the downloadable acl drop-down list, select healthy_acl (figure 7-68). Figure 7-68 l2ip healthy authorization rule 7. Click add rule. 8. From user group, select any. 9. From system posture token, select quaranti...
Page 309
Chapter 7. Network enforcement subsystem implementation 291 12.For this scenario, we selected the quarantine_l2ip_rac and quarantine_acl as the shared rac and downloadable acl to be applied in case a condition is not defined or there is no matched condition (figure 7-69). Figure 7-69 completed l2ip ...
Page 310
292 building a network access control solution with ibm tivoli and cisco systems configuring cisco 3750 switch for nac l2 802.1x new for nac phase 2 is the ability of a cisco switch to act as a nac policy enforcement device. For the purposes of this book, we used a cisco 3750 switch, running the adv...
Page 311
Chapter 7. Network enforcement subsystem implementation 293 ! ! Interface fastethernet1/0/5 description **connected to care-system workstation** switchport mode access dot1x pae authenticator dot1x port-control auto dot1x timeout reauth-period server dot1x reauthentication dot1x guest-vlan 15 spanni...
Page 312
294 building a network access control solution with ibm tivoli and cisco systems access-list 140 deny ip any 192.168.11.0 0.0.0.255 access-list 140 deny ip any 192.168.12.0 0.0.0.255 access-list 140 deny ip any 192.168.13.0 0.0.0.255 access-list 140 deny ip any 192.168.15.0 0.0.0.255 access-list 140...
Page 313
Chapter 7. Network enforcement subsystem implementation 295 allow web access and dns access in case of manual remediation requirements or access to the intranet web pages for help. On the 3750 switch, enter the following verification command: show dot1x interface fa1/0/5 detail nac3750sa#sho dot1x i...
Page 314
296 building a network access control solution with ibm tivoli and cisco systems this section describes how to configure a cisco 3750 switch acting as the nad: aaa new-model aaa authentication login local_only line aaa authentication eou default group radius aaa authorization network default group r...
Page 315
Chapter 7. Network enforcement subsystem implementation 297 permit tcp any any eq domain deny ip any any ip access-list extended initial-acl permit udp any any eq domain permit udp any any eq bootpc permit udp any any eq bootps permit icmp any any permit udp any any eq 21862 ! Radius-server attribut...
Page 316
298 building a network access control solution with ibm tivoli and cisco systems audit session id : 000000005222bff40000001bc0a80b33 posturetoken : quarantine age(min) : 0 url redirect : no url redirect url redirect acl : quarantine_acl acl name : #acsacl#-ip-quarantine_acl-4514163a user name : care...
Page 317
Chapter 7. Network enforcement subsystem implementation 299 2. Configuring admission control eou 3. Configuring an exception list configuration for clientless hosts 4. Configuring clientless user policy 5. Configuring eap over udp timers 6. Configuring the interfaces and intercept acl 7. Configuring...
Page 318
300 building a network access control solution with ibm tivoli and cisco systems this example causes traffic with a destination port 53 (domain) or port 21862 (default eap-over-udp) to be exempt from the admission control process: router(config)# access-list 102 deny udp any host 10.10.30.10 eq 2186...
Page 319
Chapter 7. Network enforcement subsystem implementation 301 the cisco secure acs then issues a token according to the group in which a user with the clientless user name is placed. This configuration is useful for pcs and workstations that receive their ip addresses through dhcp and do not have the ...
Page 320
302 building a network access control solution with ibm tivoli and cisco systems 7. Enabling the http server is necessary for url redirection. When url redirection is configured in the group configuration section, these url redirections are sent to the cisco ios software nad. Router(config)# ip http...
Page 321
Chapter 7. Network enforcement subsystem implementation 303 10.3.3.30 fastethernet0/0 eap healthy 13 10.3.3.31 fastethernet0/0 eap quarantine 2 router# 7.2 configuring nac appliance components there are various components that make up the nac appliance solution. They are: clean access manager (cam) ...
Page 322
304 building a network access control solution with ibm tivoli and cisco systems 7.2.1 installing cca agent at the time of writing this book, the latest version of the cca agent available from cisco was 4.0.2.0. The version that we used for this book is a special version 4.0.1.1. 1. Click ccaagent_s...
Page 323
Chapter 7. Network enforcement subsystem implementation 305 2. Accept the default installation folder and click next, as shown in figure 7-72. Figure 7-72 default install directory 3. Click install to begin the installation (figure 7-73). Figure 7-73 beginning the installation.
Page 324
306 building a network access control solution with ibm tivoli and cisco systems 4. Click finish to complete the installation (figure 7-74). Figure 7-74 completed installation 7.2.2 configuring a cca oob vg server the cam uses java remote method invocation (rmi) for parts of its communication with t...
Page 325
Chapter 7. Network enforcement subsystem implementation 307 the steps are: 1. Open a web browser and enter the ip address of the cam. There is no specific port required. 2. Enter the administrator name and password, then click login (figure 7-75). Figure 7-75 cam login page.
Page 326
308 building a network access control solution with ibm tivoli and cisco systems 3. The clean access summary window will be displayed (figure 7-76). Figure 7-76 cam summary window.
Page 327
Chapter 7. Network enforcement subsystem implementation 309 4. From the main menu, select device management → cca servers (figure 7-77). Figure 7-77 device management.
Page 328
310 building a network access control solution with ibm tivoli and cisco systems 5. Select new server. Add the server ip address and server location, and from the drop-down list, select out-of-band virtual gateway (figure 7-78). Figure 7-78 adding a new cas 6. Click add clean access server..
Page 329
Chapter 7. Network enforcement subsystem implementation 311 7. The cas should now be visible under list of servers, shown in figure 7-79. Figure 7-79 successful cas addition note: if you intend to configure the cas in virtual gateway mode (in-band or out-of-band), you must leave the untrusted interf...
Page 330
312 building a network access control solution with ibm tivoli and cisco systems 8. Click the manage icon for the cas just added. This takes you to the dialog shown in figure 7-80. Figure 7-80 cas status screen.
Page 331
Chapter 7. Network enforcement subsystem implementation 313 9. Select device management → cca servers → network. Check that your screen resembles figure 7-81. Figure 7-81 network ip screen 10.Select device management → cca servers → advanced → managed subnet. 11.Enter ip addresses from the trusted a...
Page 332
314 building a network access control solution with ibm tivoli and cisco systems and non-trusted networks. The main subnet is added by default. For each managed network include the ip address and subnet mask vlan id , as shown in figure 7-82. Click add managed subnet. Figure 7-82 managed subnets 12....
Page 333
Chapter 7. Network enforcement subsystem implementation 315 14.Click add mapping. Confirmation of the successful mapping will appear (figure 7-83). Figure 7-83 vlan mapping example configure default login page to configure the default login page follow these steps: 1. Click administration → user pag...
Page 334
316 building a network access control solution with ibm tivoli and cisco systems 2. Click add. The vlan id should be an asterisk (*), the subnet information should be ‘*’/’*’ and the operating system should be set to all . This will allow web login and clean access agent users to authenticate (figur...
Page 335
Chapter 7. Network enforcement subsystem implementation 317 2. Enter the group name and description (figure 7-85). Figure 7-85 switch group creation 3. Click add..
Page 336
318 building a network access control solution with ibm tivoli and cisco systems 4. Verify your new switch group (figure 7-86). Figure 7-86 switch group verification.
Page 337
Chapter 7. Network enforcement subsystem implementation 319 configuring a switch profile to configure a switch profile follow these steps: 1. From switch management in the main menu, select profiles → switch → new (figure 7-87). Figure 7-87 new switch profile 2. Fill in the fields as appropriate. In...
Page 338
320 building a network access control solution with ibm tivoli and cisco systems 3. Click add. A confirmation of the new profile will appear, as shown in figure 7-88. Figure 7-88 switch profile configuring port profile there are three types of port profiles for switch ports: uncontrolled, controlled...
Page 339
Chapter 7. Network enforcement subsystem implementation 321 when a client connects to a controlled port, the port is assigned to the authentication vlan. After the client has been successfully authenticated, the port is assigned to the access vlan specified in the port profile or the role settings. ...
Page 340
322 building a network access control solution with ibm tivoli and cisco systems 4. Under options: device disconnect, checkthe box remove out-of-band online user when snmp link-down is received (figure 7-90). Figure 7-90 managed profile creation.
Page 341
Chapter 7. Network enforcement subsystem implementation 323 5. Click add. The configured switch profiles will be displayed (figure 7-91). Figure 7-91 configured switch profiles configuring snmp receiver snmp receiver setup provides settings for the snmp receiver running on the cam, which receives th...
Page 342
324 building a network access control solution with ibm tivoli and cisco systems 2. Complete as necessary, depending on the version of snmp being used and the snmp community strings in the environment (figure 7-92). Figure 7-92 snmp configuration 3. Click add. Adding a managed switch this allows the...
Page 343
Chapter 7. Network enforcement subsystem implementation 325 the ip address of the switch should be entered in the ip address box, and a description entered in the description field (figure 7-93). Figure 7-93 manually adding a switch to be managed 3. Click add. 4. The switch can been seen by selectin...
Page 344
326 building a network access control solution with ibm tivoli and cisco systems 5. As seen in figure 7-94, click the ports icon. Figure 7-94 managed switch.
Page 345
Chapter 7. Network enforcement subsystem implementation 327 6. Under profile, use the drop-down list to configure the ports as appropriate. Our client was installed on port fa1/0/12, (figure 7-95) so the profile was set to control_20. Figure 7-95 applying profiles to ports. Note port fa1/0/12 defini...
Page 346
328 building a network access control solution with ibm tivoli and cisco systems 2. Add the role name and role description as appropriate. Our example uses the name allowall . Select the options as appropriate. The fields of main importance here are role type and out-of-band user role vlan. For our ...
Page 347
Chapter 7. Network enforcement subsystem implementation 329 4. The new role should be visible under list of roles , depicted in figure 7-97. Figure 7-97 list of roles creating traffic policies for new installations of cisco nac appliance, the default allows all traffic from the trusted network to th...
Page 348
330 building a network access control solution with ibm tivoli and cisco systems 2. From the first drop-down menu, select the role you have created. In our example that is allowall . In the second drop-down menu, select trusted → untrusted. Click select (figure 7-98). Figure 7-98 rules for trusted t...
Page 349
Chapter 7. Network enforcement subsystem implementation 331 5. The action should be allow and the protocol should be all (figure 7-99). Figure 7-99 rules for untrusted to trusted 6. Select the group you created ( allowall ) from the first drop-down menu. Select untrusted → trusted from the second dr...
Page 350
332 building a network access control solution with ibm tivoli and cisco systems the completed ruleset should look like figure 7-100. Figure 7-100 untrusted → trusted rule creation 11.Repeat steps 6 through 10 for the quarantine role and temporary role . Users in this scenario, utilizing cca, are pl...
Page 351
Chapter 7. Network enforcement subsystem implementation 333 2. Add the user name , password , and description as appropriate. From the role drop-down menu, select which role this user should be mapped to (figure 7-101). Figure 7-101 creating a new user 3. Click create user..
Page 352
334 building a network access control solution with ibm tivoli and cisco systems 4. The user just created should be seen under list of local users , as shown in figure 7-102. Figure 7-102 list of local users configure clean access agent this section identifies rules and checks that will be applied t...
Page 353
Chapter 7. Network enforcement subsystem implementation 335 2. Select the following options (figure 7-103): – from the check category drop-down menu, select service check. The screen will refresh and the check type should be set to service status. – check name should be set to scm_service. – service...
Page 354
336 building a network access control solution with ibm tivoli and cisco systems – value name should be set to version. – value data type should be set to string. – operator should be set to equals. – value data should be set to 4.0.1.1 – check description should be set to cca_compliance. – operatin...
Page 355
Chapter 7. Network enforcement subsystem implementation 337 6. These two checks should now be displayed (figure 7-105). Figure 7-105 rules check list check.
Page 356
338 building a network access control solution with ibm tivoli and cisco systems 7. Click new rule (figure 7-106). Figure 7-106 new rule 8. Enter the following information: rule name scm_service rule description tivoli scm service operating system windows xp checked rule expression® scm_service 9. C...
Page 357
Chapter 7. Network enforcement subsystem implementation 339 10.Repeat steps 7 and 8, entering the following information (figure 7-107): rule name cca_compliance rule description cisco clean access agent version operating system windows xp rule expression cca_compliance figure 7-107 cca compliance ru...
Page 358
340 building a network access control solution with ibm tivoli and cisco systems 12.The newly defined rules will be displayed (figure 7-108). Figure 7-108 new rules 13.Note that both the rules have a blue tick under validity ..
Page 359
Chapter 7. Network enforcement subsystem implementation 341 14.Click requirements → new requirements (figure 7-109). Figure 7-109 requirements 15.Enter the following information: – from the requirement type drop-down menu, select ibm tivoli scm. – set the priority to 1. – for requirement name, enter...
Page 360
342 building a network access control solution with ibm tivoli and cisco systems 17.Repeat steps 14 and 15, entering the following information (figure 7-110): – from the requirement type drop-down menu, select ibm tivoli scm. – set the priority to 2. – for requirement name, enter cca_compliance . – ...
Page 361
Chapter 7. Network enforcement subsystem implementation 343 19.The requirement list window should appear similar to figure 7-111. Figure 7-111 requirements list 20.Click requirement rules. 21.Enter the following information: – from requirement name, select scm_service. – from operating system, selec...
Page 362
344 building a network access control solution with ibm tivoli and cisco systems 22.Repeat steps 20 and 21, entering the following information (figure 7-112): – from requirement name, select cca_compliance. – from operating system, select windows xp. – from rules for selected operating system, check...
Page 363
Chapter 7. Network enforcement subsystem implementation 345 25.From “select requirements to associate with the role,” select both scm_service and cca_compliance (figure 7-113). Figure 7-113 role requirements 26.Click update..
Page 364
346 building a network access control solution with ibm tivoli and cisco systems discovered clients to check that the clean access solution is working properly, select view online users → out-of-band (figure 7-114). Figure 7-114 viewing online users.
Page 365
Chapter 7. Network enforcement subsystem implementation 347 logging on as a client to log on as a client follow these steps. 1. Once the cca agent software has been installed on the client machine, the user will be prompted for their user name and password (figure 7-115). Figure 7-115 client log-in ...
Page 366
348 building a network access control solution with ibm tivoli and cisco systems 4. Click ok. 5. If a client fails the compliance check, a web page will pop-up notifying the user that he is noncompliant (figure 7-117). Figure 7-117 web page pop-up informing user about non-compliance 6. Click continu...
Page 367
Chapter 7. Network enforcement subsystem implementation 349 8. The user is advised of their temporary access (figure 7-118), and clicks continue. Figure 7-118 temporary access notification 9. User clicks update (figure 7-119). Figure 7-119 required software notification screen.
Page 368
350 building a network access control solution with ibm tivoli and cisco systems 10.The security compliance manager compliance report window pops up (figure 7-120). In this example we can see that there is a policy violation with the user password settings. Figure 7-120 security compliance manager c...
Page 369
Chapter 7. Network enforcement subsystem implementation 351 13.The user clicks close on the security compliance manager compliance report window, which shows all items in a state of green tick compliance (figure 7-122). Figure 7-122 security compliance manager compliance report window - all complian...
Page 370
352 building a network access control solution with ibm tivoli and cisco systems 15.The end user is advised of successful login to the network (figure 7-123). Figure 7-123 successful login this concludes the basic configuration requirements for the carex on the cam. 7.2.3 deployment of the network i...
Page 371
Chapter 7. Network enforcement subsystem implementation 353 example of interface configuration for cam interface: interface fastethernet1/0/18 description **cam interface** switchport access vlan 9 switchport mode access spanning-tree portfast ! Example of interface configuration for untrusted cas i...
Page 372: 7.3 Conclusion
354 building a network access control solution with ibm tivoli and cisco systems example of snmp configuration: snmp-server community public rw snmp-server community c3750_read ro snmp-server location matanzas snmp-server contact admin snmp-server enable traps snmp linkdown linkup snmp-server enable...
Page 373: Remediation Subsystem
© copyright ibm corp. 2005, 2007. All rights reserved. 355 chapter 8. Remediation subsystem implementation this chapter describes the ibm tivoli configuration manager part of the network admission control (nac) solution, where the main concern is the remediation of the noncompliant clients. The reme...
Page 374
356 building a network access control solution with ibm tivoli and cisco systems – installation of the software package utilities – creating remediation workflows that matches security compliance manager policies with the suitable remediation workflow names and parameters.
Page 375
Chapter 8. Remediation subsystem implementation 357 8.1 automated remediation enablement to enable automated remediation, the remediation handler that is automatically installed on the client with the policy collector has to be properly configured. As opposed to the first release of the remediation ...
Page 376: 8.2.1 Prerequisites
358 building a network access control solution with ibm tivoli and cisco systems for tivoli configuration manager package at the ibm tivoli security compliance manager 5.1 utilities page at the following link: http://www.Ibm.Com/support/docview.Wss?Uid=swg24007082 2. The com.Ibm.Scm.Nac.Posture.Poli...
Page 377
Chapter 8. Remediation subsystem implementation 359 for software package web server component: the iisscn enablement pack2 for tivoli configuration manager package available on the ibm tivoli security compliance manager 5.1 utilities web site: http://www.Ibm.Com/support/docview.Wss?Uid=swg24007082 t...
Page 378
360 building a network access control solution with ibm tivoli and cisco systems preparing for the installation tivoli configuration manager web gateway requires several prerequisites to be successfully installed. The following steps must be accomplished before attempting tivoli configuration manage...
Page 379
Chapter 8. Remediation subsystem implementation 361 the steps to install the minimal required version of web infrastructure are: 1. To start the installation go the directory where you have your installation media for websphere application server 5.1 to the \win subdirectory and run the file launchp...
Page 380
362 building a network access control solution with ibm tivoli and cisco systems 3. The websphere application server installation wizard is displayed, as shown in figure 8-2. Click next. Figure 8-2 websphere installation wizard window.
Page 381
Chapter 8. Remediation subsystem implementation 363 4. In the next window, the standard license agreement is presented, as shown in figure 8-3. Accept the license and click next. Figure 8-3 software license agreement window.
Page 382
364 building a network access control solution with ibm tivoli and cisco systems 5. In the next window shown in figure 8-4 you must select the installation type. For the lab environment we decided to select custom installation to prevent the installation of unnecessary components in order to limit m...
Page 383
Chapter 8. Remediation subsystem implementation 365 this is shown in figure 8-5. Click next. Figure 8-5 component selection dialog important: if you have the internet information server installed on the machine where you are performing websphere installation there may be a port conflict on port 80. ...
Page 384
366 building a network access control solution with ibm tivoli and cisco systems 7. In the next window, shown in figure 8-6, you may specify the directories where the software components will be installed. Leave the default values and click next. Figure 8-6 destination folder selection window.
Page 385
Chapter 8. Remediation subsystem implementation 367 8. In the next window you must specify the node name and host name for the application server to use. Both fields will be filled in with your server host name by default, as shown in figure 8-7. We recommend that you leave the defaults and click ne...
Page 386
368 building a network access control solution with ibm tivoli and cisco systems 9. The next dialog (figure 8-8) allows you to select whether you want your web components to run as a service. To accept the default selection, which is yes for both components, enter a user name and password for the us...
Page 387
Chapter 8. Remediation subsystem implementation 369 10.The next window presented to you contains the installation options summary, as shown in figure 8-9. To proceed with the installation click next. Figure 8-9 installation options summary 11.The installation progress is shown in another dialog. The...
Page 388
370 building a network access control solution with ibm tivoli and cisco systems it may take a few minutes to complete the installation. Then you are presented with the online registration window, as shown in figure 8-10. Uncheck “register this product now” and click next. Figure 8-10 online registr...
Page 389
Chapter 8. Remediation subsystem implementation 371 12.Finally, there remain two open windows. One of them is the first steps dialog you can just exit. The second one, shown in figure 8-11, presents the installation status summary. To close the wizard click finish. Figure 8-11 installation status su...
Page 390
372 building a network access control solution with ibm tivoli and cisco systems 3. Make sure that the ibm http server is not running (look for the apache.Exe or httpd processes). If it is running it can be stopped using the services panel or with the following commands: net stop “ibm http administr...
Page 391
Chapter 8. Remediation subsystem implementation 373 b. The install fix packs option is selected, as shown in figure 8-13. Figure 8-13 installation option selection.
Page 392
374 building a network access control solution with ibm tivoli and cisco systems c. The directory location provided for the fix packs is the fix packs subdirectory under your temporary directory you have created in step 1 (figure 8-14). Figure 8-14 fix packs directory location 7. As fix pack 1 is th...
Page 393
Chapter 8. Remediation subsystem implementation 375 now you can continue with the tivoli configuration manager web gateway installation. Installation of tivoli configuration manager web gateway in this section we detail the steps for tivoli configuration manager web gateway. To install this componen...
Page 394
376 building a network access control solution with ibm tivoli and cisco systems 3. The welcome window is presented (figure 8-16). Click next. Figure 8-16 welcome window.
Page 395
Chapter 8. Remediation subsystem implementation 377 4. In the next window (figure 8-17), the standard license agreement is shown. Accept the license and click next. Figure 8-17 license agreement window.
Page 396
378 building a network access control solution with ibm tivoli and cisco systems 5. The component selection is displayed, as shown in figure 8-18. Make sure that all three options are selected and click next. Figure 8-18 component selection.
Page 397
Chapter 8. Remediation subsystem implementation 379 6. The installation directory selection window is displayed (figure 8-19). Accept the default path but make sure that the drive has at least 510 mb of free space and click next. Figure 8-19 installation directory selection window.
Page 398
380 building a network access control solution with ibm tivoli and cisco systems 7. In the next dialog (figure 8-20) most of the fields are already filled in. Provide the passwords for the db2 administration user and the dmsadmin user you have created according to the procedure described in “creatin...
Page 399
Chapter 8. Remediation subsystem implementation 381 8. The web infrastructure configuration window is displayed (figure 8-21). Check whether the right paths are entered (usually these are the defaults for the selected platform) and click next. Figure 8-21 web infrastructure configuration window 9. I...
Page 400
382 building a network access control solution with ibm tivoli and cisco systems if your tivoli configuration manager is a single node installation this would be localhost, as shown in the figure 8-22. Then click next. Figure 8-22 endpoint configuration window.
Page 401
Chapter 8. Remediation subsystem implementation 383 10.The secure access configuration window is presented, as shown in figure 8-23. Since we are not using tivoli access manager in our environment accept the default ( enable security is false ) and click next. Figure 8-23 secure access configuration.
Page 402
384 building a network access control solution with ibm tivoli and cisco systems 11.The summary of the selected installation options is presented, as shown in figure 8-24. Click next to proceed with the installation. Figure 8-24 summary of installation options.
Page 403
Chapter 8. Remediation subsystem implementation 385 12.The installation can take a while depending on the configuration of your system. You can follow the progress of the installation in the dialog window. Figure 8-25 shows the final status. To finish the web gateway installation click finish. Figur...
Page 404
386 building a network access control solution with ibm tivoli and cisco systems handler located on the workstation attempting to connect to the network and the tivoli configuration manager web gateway. The software package web server code is located in the iisscn extension pack2 for tivoli configur...
Page 405
Chapter 8. Remediation subsystem implementation 387 3. If you have followed the installation of websphere application server as described in this book you should have no security turned on and you will see the standard login screen, as shown in figure 8-26. Enter any name and click ok. Figure 8-26 w...
Page 406
388 building a network access control solution with ibm tivoli and cisco systems 4. On the next page expand the applications menu item in the left pane and click the install new application option. The new content should be displayed in the right pane, as shown in figure 8-27. Figure 8-27 install ne...
Page 407
Chapter 8. Remediation subsystem implementation 389 6. The preparing for the application installation window is displayed (figure 8-28). Accept the defaults and click next. Figure 8-28 preparing for the application installation.
Page 408
390 building a network access control solution with ibm tivoli and cisco systems 7. Leave the defaults and click next in the several next windows until you reach the one shown in the figure 8-29. Click finish to start the actual installation. The button may be hidden in the lower part of the window,...
Page 409
Chapter 8. Remediation subsystem implementation 391 8. The installation may take a few seconds or few minutes depending on your server configuration. In the window that displays the installation results, find and click the save to master configuration link. Figure 8-30 installation status window.
Page 410
392 building a network access control solution with ibm tivoli and cisco systems 9. In the next window, shown in figure 8-31, select save to save the configuration changes to the master configuration file. Figure 8-31 saving the configuration changes.
Page 411
Chapter 8. Remediation subsystem implementation 393 10.When you click the enterprise application link under applications in the left pane you should see a window similar to the one presented in figure 8-32. Figure 8-32 enterprise applications window configuration of the software package web server t...
Page 412
394 building a network access control solution with ibm tivoli and cisco systems open the file using a text editor, and find the value of the web_server_doc_root key in the file. In our lab this is: c:\program files\ibmhttpserver\htdocs\en_us 3. Open the softwarepackageserverconfig.Properties file l...
Page 413
Chapter 8. Remediation subsystem implementation 395 this file contains the mapping between the remediation workflows and the posture collector parameters used in the compliance policies defined on the tivoli security compliance manager server. 4. Edit the workflowposturecollectormapping.Properties f...
Page 414
396 building a network access control solution with ibm tivoli and cisco systems 5. You must initialize the package creation utility environment. Issue the following commands: cd %bindir% cd tcmremed\cfg sputil_initial_setup.Bat this creates the necessary objects on the tivoli configuration manager,...
Page 415
Chapter 8. Remediation subsystem implementation 397 in example 8-2 and example 8-3 we present the final content required for the files that must be changed or added. Example 8-2 nac.Win.Any.Services.Postureservices_service_running_wf.Defa ultconfig.Properties file content # sputil default config fil...
Page 416: 8.3.1 Locating Html
398 building a network access control solution with ibm tivoli and cisco systems access to corporate intranet resources). To avoid serious business disruptions, necessary means should be taken to minimize this effect, including: setting up a grace period for non-critical noncompliance situations usi...
Page 417
Chapter 8. Remediation subsystem implementation 399 the checks defined by the particular compliance objects within the policy relate to the data gathered by one posture collector. This means that the individual violations are collector-related, and this determines the way the html pages are organize...
Page 418
400 building a network access control solution with ibm tivoli and cisco systems pages would be in a subdirectory named pl_pl . The default language and local is en_us . This document will use the variables listed in table 8-1 to describe the dynamic parts of the paths to html pages. Table 8-1 varia...
Page 419
Chapter 8. Remediation subsystem implementation 401 if none of these locations contain a valid page, the user interface falls back to the method used to locate the base html page. Html pages example assume that a policy wants to ensure that the zonealarm and remote desktop services are running, and ...
Page 420
402 building a network access control solution with ibm tivoli and cisco systems posture element html each posture element has a unique name and status. The user interface will first attempt to find pages that are specific to the item's name and status before moving to more general instance-level pa...
Page 421
Chapter 8. Remediation subsystem implementation 403 the wfattribute tag the simplest variables are workflow attributes. When a posture collector performs a check that fails, it will often associate a workflow object with the element. The workflow object may contain one or more named lists of attribu...
Page 422
404 building a network access control solution with ibm tivoli and cisco systems table 8-5 presents the field names that may be used when a posture item is selected. Table 8-5 the field tag usage on posture item level table 8-6 presents the field names that may be used when a posture element is sele...
Page 423
Chapter 8. Remediation subsystem implementation 405 the attributes that are generated by the security compliance manager client are always present, and are known as innate attributes. These attributes, presented in table 8-7, cannot be overridden by user settings. Table 8-7 innate remattribute tag u...
Page 424: 8.3.3 Debug Attributes
406 building a network access control solution with ibm tivoli and cisco systems information. For example, to enable the user interface to display the fix now button even if a remediation url has not been sent, the following entry could be made in either the handler_attributes or handlers.Properties...
Page 425
Chapter 8. Remediation subsystem implementation 407 the attributes will be listed each time a posture element is selected (they are not logged when a posture item is selected). For example: attribute: os.Arch -> x86 attribute: client.Dhcp -> false attribute: client.Fingerprint -> 63:9a:42:ac:de:13:4...
Page 427
Chapter 8. Remediation subsystem implementation 409 8.3.4 creating html pages for abbc policy figure 8-34 summarizes the directory structure for the html remediation pages used in our example. Figure 8-34 sample directory structure for abbc the following three steps build meaningful html examples fo...
Page 428
410 building a network access control solution with ibm tivoli and cisco systems first we create the default.Html page describing these basic requirements and save it in the nac.Win.Any.Netaccounts.Posturenetaccountsv2\en_us\ directory, as shown in figure 8-34 on page 409. Figure 8-35 shows the samp...
Page 429
Chapter 8. Remediation subsystem implementation 411 tivoli network access control.
Page 430
412 building a network access control solution with ibm tivoli and cisco systems background: #fff url("file:///c:/progra~1/ibm/scm/client/scripts/com.Ibm.Scm.Nac.Posture.Pol icycollector/logo.Gif") no-repeat top left; height: 70px; } #sectiontitle { margin:10px 0px 10px 0px; padding:10px 10px 10px 1...
Page 431
Chapter 8. Remediation subsystem implementation 413 to prepare separate descriptions for each of these conditions we create two subdirectories named after the checks. In the minimum password length subdirectory we create an html page named warn.Html, shown in figure 8-36. Figure 8-36 minimum passwor...
Page 432
414 building a network access control solution with ibm tivoli and cisco systems tivoli network access control.
Page 433
Chapter 8. Remediation subsystem implementation 415 3. Understanding the tags described in the previous step, we now build a more sophisticated html page for maximum password age check named fail.Html. This page will be used when the compliance check generates the fail status. Figure 8-37 shows the ...
Page 434
416 building a network access control solution with ibm tivoli and cisco systems tivoli network access control.
Page 435
Chapter 8. Remediation subsystem implementation 417 you can build similar pages for all of the compliance checks described in your policy. In the next section we provide the detailed steps to build the remediation workflows called when the user clicks the fix now button on the remediation user inter...
Page 436
418 building a network access control solution with ibm tivoli and cisco systems while editing our policy in 6.2, “configuration of the compliance policies” on page 152, we have defined the following workflow names to be used for automated remediation: tcrnavscan tcrnavvirusdefupdate tcrnavsoftwarei...
Page 437
Chapter 8. Remediation subsystem implementation 419 2. In the next step we create the windows script that will perform the actual job. We can reuse the one provided with the samples in the sample_tcrnavscan directory named navscanmessage_en.Wsf (windows script file format) or create a new one using ...
Page 438
420 building a network access control solution with ibm tivoli and cisco systems 3. Next we create the configuration file for the sputil.Sh utility containing the instructions how to build the package. Copy the sample.Properties file from sample_tcrnavscan directory to the tcrnavscan directory and e...
Page 439
Chapter 8. Remediation subsystem implementation 421 as a result you should see the output presented below: region disp flags port ipaddr hostname(s) 1406765930 1 ct- 94 192.168.230.140 tcmweb 5. Run the sputil.Sh command to create the software package block and publish it on the web gateway. To achi...
Page 440
422 building a network access control solution with ibm tivoli and cisco systems two additional files are created in the $bindir/tcmremed/work directory. These are: tcrnavscan.Spd software package definition file. This is a text meta file containing all of the package configuration information. Tcrn...
Page 441
Chapter 8. Remediation subsystem implementation 423 the remediation process window is displayed and the proper software package block is downloaded and executed. You are presented with the instructions shown in figure 8-39. Figure 8-39 result of running navscanmessage_en.Wsf when you click ok the fi...
Page 442
424 building a network access control solution with ibm tivoli and cisco systems file. The live update process is initiated with the vpdn_lu.Exe executable located in the symantec antivirus home directory. When run with a /s flag the process runs silently in the background. Based on this knowledge w...
Page 443
Chapter 8. Remediation subsystem implementation 425 3. Run the sputil.Sh command to create the software package block and publish it on the web gateway. To achieve this run the following commands: cd $bindir/tcmremed/download cd tcrnavvirusdefupdate $bindir/tcmremed/bin/sputil.Sh -p sample.Propertie...
Page 444
426 building a network access control solution with ibm tivoli and cisco systems 3. Create the configuration file for sputil.Sh utility containing the instructions on how to build the package. Copy the sample.Properties file from the sample_tcrnavsoftwareinstalled directory to the tcrnavsoftwareinst...
Page 445
Chapter 8. Remediation subsystem implementation 427 the missing hotfixes. As this policy checks for multiple hotfixes in parallel, the missing ones must be passed back to the remediation workflow as a parameter. You must build the remediation package separately for each hotfix you have specified in ...
Page 446
428 building a network access control solution with ibm tivoli and cisco systems hotfixid=kb896423 tmfwebuiendpoint=tcmweb 4. This configuration file is a little different from the others created before. The first difference is the additional parameter close to the end named hotfixid . The value of ...
Page 447
Chapter 8. Remediation subsystem implementation 429 if the package was created the result will look like below (the number in the middle of the resulting string will be different in your environment as it is meant to be unique and is associated with tivoli management region number): tcrmspatchesinst...
Page 448
430 building a network access control solution with ibm tivoli and cisco systems there is a small catch with this collector, as it is able to check for any windows version service pack level including windows nt, windows xp, windows 2000, and windows 2003, but there is a possibility to specify only ...
Page 449
Chapter 8. Remediation subsystem implementation 431 addregistryvaluebeforeexecdata.Arraylength=2 addregistryvaluebeforeexecparentkey[0]=hkey_local_machine\\software\\polici es\\microsoft\\windowsfirewall addregistryvaluebeforeexeckey[0]=domainprofile addregistryvaluebeforeexecname[0]=enablefirewall ...
Page 450
432 building a network access control solution with ibm tivoli and cisco systems tcrzlsoftwareinstalled the tcrzlsoftwareinstalled workflow is also very similar to the ones described above, as all it does is install software that is missing. The tcrzlsoftwareinstalled workflow was defined in the key...
Page 451
Chapter 8. Remediation subsystem implementation 433 3. Create the configuration file for the sputil.Sh utility containing the instructions on how to build the package. Copy the sample.Properties file from the sample_tcrzlsoftwareinstalled directory to the tcrzlsoftwareinstalled directory and edit it...
Page 452
434 building a network access control solution with ibm tivoli and cisco systems workflows installing or uninstalling software should use silent mode whenever possible. Tcrzlsoftwarerunning the tcrzlsoftwarerunning workflow was defined in the service_running_wf parameter in the zonealarm software ac...
Page 453
Chapter 8. Remediation subsystem implementation 435 4. Run the sputil.Sh command to create the software package block and publish it on the web gateway. To achieve this run the following commands: cd $bindir/tcmremed/download cd tcrzlsoftwarerunning $bindir/tcmremed/bin/sputil.Sh -p sample.Propertie...
Page 454
436 building a network access control solution with ibm tivoli and cisco systems tcrzlsoftwaredisabled directory and edit it with the text editor to match the content specified in example 8-16. Example 8-16 sample.Properties file for tcrmessengerdisabled workflow workflowname=tcrmessengerdisabled co...
Page 455: 8.5 Conclusion
Chapter 8. Remediation subsystem implementation 437 in order to remove the package for the tcrmessengerdisabled remediation workflow: 1. Open a command prompt, import the environment variables for the tivoli framework, and start bash. Then go the directory for the tcrmessengerdisabled workflow. To d...
Page 456
438 building a network access control solution with ibm tivoli and cisco systems.
Page 457: Appendixes
© copyright ibm corp. 2005, 2007. All rights reserved. 439 part 3 appendixes in the following two appendixes we take a closer look at these topics: general hints and tips for everything around the ibm integrated security solution for cisco networks a generic introduction to the cisco network admissi...
Page 458
440 building a network access control solution with ibm tivoli and cisco systems.
Page 459: Hints and Tips
© copyright ibm corp. 2005, 2007. All rights reserved. 441 appendix a. Hints and tips this appendix contains hints, tips, and other useful information that can help the implementer to have a better understanding of the ibm integrated security solution for cisco networks. It also describes the nac ap...
Page 460: Deployment Overview
442 building a network access control solution with ibm tivoli and cisco systems deployment overview the solution deployment starts with the registration of a set of attributes for the ibm integrated security solution for cisco networks on the cisco secure acs server, as shown in figure a-1 on page ...
Page 461
Appendix a. Hints and tips 443 figure a-1 trc-specific objects and relationship acs se rver e xter nal u ser da ta ba se vi ol ati on c ou nt tok e n m anda tory crede ntia l type l ocal p oli cy ru le s po lic y ver sio n act ion po lic y ve rs io n viol at io n count token act io n poli cy versi o...
Page 462: Top-Level Sequence of Events
444 building a network access control solution with ibm tivoli and cisco systems top-level sequence of events the nac process starts when the client tries to access a protected network. When the network access device (typically a switch or router) recognizes that a client is attempting access, it is...
Page 463
Appendix a. Hints and tips 445 figure a-2 isscn top-level sequence diagram re medi a tion obj ec ts () p o st ure q uer y( ) sc m p o lic y c o lle ct o r quar an tine p ost ur enot ifi ca tio n () po st ur e () re m edi at io n co m m and s( ) tc m w e b g a te w ay r emed iat ion hand le r re m e ...
Page 464: Subsystem
446 building a network access control solution with ibm tivoli and cisco systems security compliance manager and nac compliance subsystem figure a-3 shows the compliance subsystem and data flow between the subcomponents that can help during problem determination and also provides insight to better u...
Page 465: Cisco Nac Sequence of Events
Appendix a. Hints and tips 447 cisco nac sequence of events the nac process is initiated by the network. Whenever access to a protected network is detected, the network access device queries the endpoint for its posture. In addition, there are two polling cycles that control what requests are sent t...
Page 466: Fault Isolation
448 building a network access control solution with ibm tivoli and cisco systems attempts by the client to access a protected resource will also trigger a posturequery from the network. This statusquery cycle is typically configured to a low value so that any changes that occur on the client after i...
Page 467
Appendix a. Hints and tips 449 then to determine the actual problem based on the expected behavior of the solution. Assuming that all of the software has been installed and is running, when the client first tries to connect to a protected network, it should receive a pop-up message from the cisco tr...
Page 468
450 building a network access control solution with ibm tivoli and cisco systems collectors, at which time any state changes affected by the remediation process will be discovered. The next time the network polls for statuschange, it will receive a true response and will request the new posture data...
Page 469: Communication Port Usage
Appendix a. Hints and tips 451 communication port usage tivoli security compliance manager server and client communicate only with temporary connections. A persistent connection is not required because the security compliance manager/nac concept can function without the security compliance manager s...
Page 470
452 building a network access control solution with ibm tivoli and cisco systems cisco ios software router on a cisco router running cisco ios software, these commands are useful for debugging: show eou shows eou (eapoverudp) settings including polling cycle timeouts. Show eou all shows current eou ...
Page 471
Appendix a. Hints and tips 453 timetonextreauth = 48 authentication method = dot1x posture = healthy authorized by = authentication server vlan policy = 10 cisco secure acs server on a cisco secure acs server web gui, go to the reports section and look at the passed authentications and failed attemp...
Page 472
454 building a network access control solution with ibm tivoli and cisco systems security compliance manager client when the security compliance manager client is started, the security compliance manager policy collector should listen for tcp connections on port 40500 . If a netstat -an command is r...
Page 473: Nac Appliance Details
Appendix a. Hints and tips 455 client logging can be turned on by setting the debug property to true in the %scm_home%\client\client.Pref file. When turned on, a file called client.Log is created and updated in the %scm_home/client directory. This file displays any notification received from the net...
Page 474
456 building a network access control solution with ibm tivoli and cisco systems assessment). It can also be deployed in layer-2 mode (users are l2-adjacent to cas) or layer-3 (users are multiple l3 hops away from the cas) mode. Clean access agent (caa) this ia a read-only agent that resides on wind...
Page 475: Nac Appliance Integration
Appendix a. Hints and tips 457 meantime, the clean access manager provides port-level or role-level control by assigning ports to specific vlans, assigning users to specific roles that map to specific vlans, and providing a time-based session time out per role. Cisco clean access out-of-band is most...
Page 476
458 building a network access control solution with ibm tivoli and cisco systems interested parties can use this design and the prototypes of these components to perform this integration in labs, for demos, and training purposes. Integration design the fundamental premise of this integration is for ...
Page 477
Appendix a. Hints and tips 459 a high-level overview of this design is depicted in figure 8-42. Figure 8-42 high-level overview integration components the following components are to be considered prototypes for use in labs, demos, training classes, and similar purposes. They are implemented in an i...
Page 478
460 building a network access control solution with ibm tivoli and cisco systems tscmagent.Bat this script creates the compliance semaphore file in and intermediate state that indicates that the client is in the admission process. It then starts the tsecurity compliance manager client service. These...
Page 479
Appendix a. Hints and tips 461 scheduler a platform-specific task scheduler (eg windows task scheduler or cron on unix) is configured to run the security compliance manager client’s statuscheck.Exe on a periodic basis. This is required to create a post-admission polling cycle that monitors the clien...
Page 480
462 building a network access control solution with ibm tivoli and cisco systems using the example html form provided. It should be noted that default security settings on most browsers will prevent active content or ask the user whether to allow it, meaning that the user will still have to manually...
Page 481
Appendix a. Hints and tips 463 the old one. This will indicate that the special functionality of this prototype collector will be lost when the production version is installed. When this collector is included in a compliance policy, it must be configured in the same fashion as a normal policy collec...
Page 482
464 building a network access control solution with ibm tivoli and cisco systems nac appliance manager a policy on the nac appliance manager must be created to check for the following two requirements: the security compliance manager client is running as a service. The c:\program files\ibm\scm\clien...
Page 483
Appendix a. Hints and tips 465 state mapping and scenarios one way for the solution to approach a design is to consider all of the possible states that can occur with regards to the client, its compliance state, and its network admission state. Table 8-8 presents the possible states that should be c...
Page 484
466 building a network access control solution with ibm tivoli and cisco systems – security compliance manager client: i. Runs compliance validation. In this case, violations are found and semaphore does not equal 1, so leave semaphore unchanged. Ii. Since violations are found, client runs remediati...
Page 485
Appendix a. Hints and tips 467 – security compliance manager client: • runs compliance validation. In this case, no violations are found, so set semaphore to 1. • no violations are found so return. – user clicks next button. – nac appliance now finds security compliance manager client running and se...
Page 486
468 building a network access control solution with ibm tivoli and cisco systems – remediation handler: • since semaphore is -1, popup remediation interface. • user can click fix now for autoremediation. • runs compliance scan. In this case no violations are found, so set semaphore to 1. – user clic...
Page 487
Appendix a. Hints and tips 469 since scenarios 5 and 6 are the most complex, the sequence of events for these scenarios is depicted in figure 8-43. Figure 8-43 sequence of events for scenarios #5 and #6 scenario 7 - pre-admission, security compliance manager running, compliant client – nac appliance...
Page 488: Conclusion
470 building a network access control solution with ibm tivoli and cisco systems – statuscheck.Exe: • requests rescan from security compliance manager client – security compliance manager client: • runs compliance validation. In this case, no violations are found. • since violations are not found, e...
Page 489: Network Admission Control
© copyright ibm corp. 2005, 2007. All rights reserved. 471 appendix b. Network admission control in this appendix we discuss the network admission control initiative from cisco systems. This appendix contains a cisco white paper that is publicly available at the following address: http://www.Cisco.C...
Page 490: Executive Summary
472 building a network access control solution with ibm tivoli and cisco systems executive summary emerging network security threats, such as viruses, worms, and spyware, continue to plague customers and drain organizations of money, productivity, and opportunity. Meanwhile, the pervasiveness of mob...
Page 491
Appendix b. Network admission control 473 dramatically improve network security while most organizations use identity management and authentication, authorization, and accounting (aaa) to authenticate users and authorize network privileges, there has been virtually no way to authenticate the securit...
Page 492: Nac Implementation Options
474 building a network access control solution with ibm tivoli and cisco systems some of the security policy compliance checks that nac can perform include: determining whether the device is running an authorized version of an operating system. Checking to see if the os has been properly patched or ...
Page 493: The Nac Appliance
Appendix b. Network admission control 475 support for a complex security implementation involving a number of security vendors, combined with a corporate desktop management solution. The nac appliance, available as cisco clean access, provides rapid deployment with self-contained endpoint assessment...
Page 494: Nac Framework Solution
476 building a network access control solution with ibm tivoli and cisco systems network access by unmanaged computers (such as guests, contractors, or students) a heterogeneous (multivendor) network infrastructure nac framework solution nac is also available as an architecture-based framework solut...
Page 495: Solution
Appendix b. Network admission control 477 organizations have evolving needs, cisco clean access product components that are installed now can be used to support a later nac framework implementation. Regardless of which approach you decide is appropriate for your environment, cisco nac technologies a...
Page 496: The Next Steps
478 building a network access control solution with ibm tivoli and cisco systems the next steps let us take a look at the next steps: 1. Deploy cisco clean access now. Cisco clean access allows you to immediately receive the benefits of an admission control solution. 2. Determine whether you will ne...
Page 497: Nac Framework Components
Appendix b. Network admission control 479 nac framework components the nac framework provides the following technology support: broad network device support for campus lans, wans, vpns, and wireless access points ties to third-party host assessment tools for unmanned, agentless , and other nonrespon...
Page 498
480 building a network access control solution with ibm tivoli and cisco systems recommended components: – cisco security agent – cisco security monitoring, analysis, and response system (mars) – ciscoworks security and information management solution (sims) for more information visit: http://www.Ci...
Page 499: Additional Material
© copyright ibm corp. 2005, 2007. All rights reserved. 481 appendix c. Additional material this redbook refers to additional material that can be downloaded from the internet as described below. Locating the web material the web material associated with this redbook is available in softcopy on the i...
Page 500: Using The Web Material
482 building a network access control solution with ibm tivoli and cisco systems using the web material the additional web material that accompanies this redbook includes the following files: file name description ibm tivoli - cca agent.Zip contains the cisco clean access agent version 4.0.1.1 used ...
Page 501: Related Publications
© copyright ibm corp. 2005, 2007. All rights reserved. 483 related publications the publications listed in this section are considered particularly suitable for a more detailed discussion of the topics covered in this redbook. Ibm redbooks for information about ordering these publications, see “how ...
Page 502: Online Resources
484 building a network access control solution with ibm tivoli and cisco systems online resources these web sites and urls are also relevant as further information sources: gramm-leach-bliley act (glba) http://banking.Senate.Gov/conf/ sarbanes-oxley act (sox) http://www.Sarbanes-oxley.Com health ins...
Page 503: Help From Ibm
Related publications 485 help from ibm ibm support and downloads ibm.Com/support ibm global services ibm.Com/services.
Page 504
486 building a network access control solution with ibm tivoli and cisco systems.
Page 505: Index
© copyright ibm corp. 2005, 2007. All rights reserved. 487 index numerics 802.1x 16, 22, 26, 68, 81, 95, 265 credentials 112 a access control list 34 configuration 293 dynamic 216 access control server 18, 23, 25, 36, 41, 54, 101 action parameter 58 administrative interface 216 authorization rule co...
Page 506
488 building a network access control solution with ibm tivoli and cisco systems physical components 121 pop-up notification 277 posture plug-in 44, 51 posture status reply 59 scm client communication 48 secure communication 63 service 44 troubleshooting 453 violation count 58 clean access agent 45,...
Page 507
Index 489 service pack level collector 167 service running collector 177 software package utilities 394 software package web server 386 switch configuration for nac appliance 352 tivoli configuration manager 358 tivoli configuration manager web gateway 359 configuration change process 32 controlled ...
Page 508
490 building a network access control solution with ibm tivoli and cisco systems ibm tivoli security compliance manager see security compliance manager identity ... Based networking services 95 identity manager access control server provisioning 25 ieee 802.1x 16, 22, 26, 68, 81, 95, 265 credentials...
Page 509
Index 491 configuration in acs 229 network policy enforcement 60 placement 67 polling of posture status 61 posture validation 59 posturequery 444 session initiation 59 network admission control 15, 78, 87 appliance 17, 45 authentication server 214 clientless user 283 deployment scenario 27 external ...
Page 510
492 building a network access control solution with ibm tivoli and cisco systems timers 301 posturenotification 447 posturequery 444, 447 ppp see point-to-point protocol pquery 454 printer ip-connected 300 process 444 productivity loss of ... 95 project plan 88 scope 27 protected extensible authenti...
Page 511
Index 493 s sarbanes-oxley act 6 scalability 35, 357 scope of the project 27 secure access control server see access control server secure communication 62 secure peap session 191 security compliance concept 4 criteria 100 data 18, 46 exception 29 management business process 28 officers involvement ...
Page 512
494 building a network access control solution with ibm tivoli and cisco systems tcrmessengerdisabled workflow 435 tcrmspatchesinstallwinxp workflow 426 tcrmsservicepackinstallwinxpsp2 workflow 429 tcrnavscan workflow 418 tcrnavsoftwareinstalled workflow 425 tcrnavvirusdefupdate workflow 423 tcrzlso...
Page 513
Building a network access c ontrol solution with ibm tivoli and cisco systems.
Page 516: International
® sg24-6678-01 isbn 0738489883 international technical support organization building technical information based on practical experience ibm redbooks are developed by the ibm international technical support organization. Experts from ibm, customers and partners from around the world create timely te...