- DL manuals
- KAPERSKY
- Firewall
- ANTI-VIRUS 5.5 - FOR CHECK POINT FIREWALL-1
- Administrator's Manual
KAPERSKY ANTI-VIRUS 5.5 - FOR CHECK POINT FIREWALL-1 Administrator's Manual
Summary of ANTI-VIRUS 5.5 - FOR CHECK POINT FIREWALL-1
Page 1
Kaspersky lab kaspersky anti-virus ® 5.5 for check point tm firewall-1 ® administrator's guide.
Page 2
K a s p e r s k y a n t i - v i r u s ® 5 . 5 f o r c h e c k p o i n t t m f i r e w a l l - 1 ® administrator's guide © kaspersky lab ltd http://www.Kaspersky.Com revision date: november, 2006.
Page 3
Table of contents chapter 1. Introduction ...................................................................................... 6 1.1. Computer viruses and malicious software............................................................ 6 1.2. Purpose, main functions and structure of kaspersky anti-v...
Page 4
4 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 5.7. Protection without additional configuration ......................................................... 47 5.8. Verifying the application performance ................................................................ 48 5.8.1. Test “virus” ...
Page 5
Table of contents 5 10.1. Configuring the diagnostics level ...................................................................... 99 10.2. Configuring log files settings ........................................................................... 101 chapter 11. License keys............................
Page 6
Chapter 1.Introduction the main source of viruses today is the global internet. Most virus infections happen via e-mail. The facts that almost every computer has e-mail client applications installed and that malicious programs are able to take a full advantage of software address books in order to f...
Page 7
Introduction 7 • viruses –programs that infect other programs by adding their code to the infected program's code in order to gain control when infected files are run. This simple definition helps determine that the major action a virus performs is infecting computer programs. Viruses spread somewha...
Page 8
8 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • automatic dialers (pornware) - programs that establish modem connection with various pay-per-visit internet (as a rule, pornographic) websites. • hacking tools - tools used by hackers to obtain access to the user's computer. This type of s...
Page 9
Introduction 9 • creates list of objects that will not be scanned for viruses. • saves backup copies of objects to a special storage before disinfecting, deleting or blocking the object for the consequent restoring which pre- vents the loss of data. Configurable filters allow to easily locate the or...
Page 10
10 kaspersky anti-virus 5.5 for check point tm firewall-1 ® agement module is implemented as the extension of the microsoft man- agement console (mmc). 1.3. What's new in version 5.5? Kaspersky anti-virus 5.5 for check point tm firewall-1 ® has the following distinctions from the previous version: •...
Page 11
Introduction 11 log and in the application's logs. An ability to configure the degree of in- formation completeness and the extent of detail has been added. Logs can be viewed using the microsoft windows events viewer tool and standard text editors, such as notepad. • an ability to create regular ex...
Page 12
12 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • microsoft windows server 2003 enterprise edition or higher. Management console: • hardware requirements: • processor intel pentium ii 300 mhz or higher; • 256 mb ram; • 10 mb free disk space. • software requirements: • microsoft windows 2...
Page 13
Introduction 13 1.5.1. License agreement license agreement is a legal contract between you and kaspersky lab ltd., which contains the terms and conditions, on which you may use the anti-virus product you have purchased. Read the license agreement carefully! If you do not agree with the terms of the ...
Page 14
14 kaspersky anti-virus 5.5 for check point tm firewall-1 ® format feature meaning/usage bold font titles of menus, menu items, windows, dialog boxes and their elements, etc. Note additional information, notes attention! Information requiring special attention in order to perform, step 1. … descript...
Page 15
Chapter 2.Operation of kaspersky anti-virus kaspersky anti-virus 5.5 for check point tm firewall-1 ® acts as a filter: processes data, transferred over http, ftp and smtp protocols, identifies monitored objects, analyzes them for the presence of malicious code and blocks attempts of infected files a...
Page 16
16 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 1. Install the security server component on the computer that has a tcp/ip connection to the computer where the check point tm firewall-1 ® application is installed. The installation is performed from the installation cd. If there are sever...
Page 17
Operation of kaspersky anti-virus 17 • fine-tune the anti-virus database update settings (see chapter 6, page 51). • verify the correctness of the settings and of the anti-virus operation using a test "virus" eicar (see section 5.8, page 48). • configure the event logs and reports settings (see chap...
Page 18
Chapter 3.Installing and removing the application before the installation of kaspersky anti-virus, make sure that the software and hardware of the computers used meet the installation requirements. The minimum allowable configuration is described in section 1.4, page 2. For installation of kaspersky...
Page 19: System
Installing and removing the application 19 3.1.1. First-time installation in order to install kaspersky anti-virus, run the executable file from the installation cd. The installation process will be facilitated by the setup wizard. Setup wizard will offer you to configure the installation settings a...
Page 20
20 kaspersky anti-virus 5.5 for check point tm firewall-1 ® step 4. Selecting application components to be installed if you selected the custom installation option, specify application components to be installed on your computer. You can also change the default folder into which they will be install...
Page 21
Installing and removing the application 21 note that databases used by the application are created only once, during the installation of the security server. If you decide change the application data folder, then in order to ensure the correct data transfer into the new folder, the entire content of...
Page 22
22 kaspersky anti-virus 5.5 for check point tm firewall-1 ® if, at the time of the installation, you still do not have the license key (for example you ordered it from kaspersky lab via internet but have not received it yet), you can install it later when you run the application for the first time u...
Page 23
Chapter 4.Integration of kaspersky anti-virus with check point tm firewall-1 ® the process of integration of kaspersky anti-virus with check point tm firewall- 1 ® is a standard procedure for opsec tm applications and involves two steps: 1. Registration of the security server with check point tm fir...
Page 24
24 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 1. Creating a security server network object 2. When creating a new object, that is an opsec tm application (opsec tm application/new) in the general tab of the opsec tm application properties settings configuration window (see figur...
Page 25
Integration of kaspersky anti-virus with check point tm 25 • in the server entities and client entities sections, select cvp, amon and ela as protocols supported by the application. Configuring the protocols settings is not required. Kaspersky anti-virus uses the default check point tm firewall-1 ® ...
Page 26
26 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 3. Setup a secure connection of the security server to check point tm firewall-1 ® (secure internal communications). The following will be created as the result: • key to obtain a security server certificate; • a security server certificate...
Page 27
Integration of kaspersky anti-virus with check point tm 27 figure 3. Creating a uri-resource. The cvp tab • to create an ftp resource check the get and the put boxes in the methods section on the match tab (see figure 4);.
Page 28
28 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 4. Creating an ftp resource. The match tab • to create a uri resource, select the enforce uri capabilities option in the use this resource to section on the general tab (see figure 5)..
Page 29
Integration of kaspersky anti-virus with check point tm 29 figure 5. Creating a uri resource. The general tab in order to increase the efficiency of the anti-virus scan, specify the following settings values on the cvp tab (see figure 3): • check the cvp server is allowed to modify content box for u...
Page 30
30 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • select the return data before content is approved option in the reply order section for uri, smtp and ftp resource. This parameter determines the possibility of early data transfer to the user before this data is scanned (see section 7.4,...
Page 31
Integration of kaspersky anti-virus with check point tm 31 figure 6. Configuring the smtp resource settings. The action2 tab.
Page 32
32 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 7. Configuring the settings of check point tm firewall-1 ® . Restricting the message size 4.2. Obtaining a security server certificate obtaining the certificate is a standard procedure for applications integrated with check point tm ...
Page 33
Integration of kaspersky anti-virus with check point tm 33 the settings will be assigned values set during the registration of the security server with check point tm firewall-1 ® (see section 4.1, page 23). In order to obtain the security server certificate: run executable file opsec_pull_cert.Exe ...
Page 34
Chapter 5.Starting using the application 5.1. Starting the application the server part of the application, the security server, is launched automatically at the startup of the operating system on the computer on which the security system is installed. If the settings used for the interaction of the ...
Page 35
Starting using the application 35 figure 8. Main application window the kaspersky anti-virus 5.5 for check point tm firewall-1 ® namespace contains the list of monitored servers (that is, computers that are monitored by kaspersky anti-virus via this console) in the form of nodes. Immediately after t...
Page 36
36 kaspersky anti-virus 5.5 for check point tm firewall-1 ® if the connection to the monitored server was established, the node will include nested folders; each of these folders will be used for managing a particular function of the application. • backup storage - for working with the backup storag...
Page 37
Starting using the application 37 additional shortcut menu commands are also provided for report templates and for the backup storage: • using the create a report command you can create a report based on the selected template and save it as a file; • using the view report command you can display the...
Page 38
38 kaspersky anti-virus 5.5 for check point tm firewall-1 ® in order to establish connection between the management console and the security server when adding the server, check the con- nect now box (details see section 5.4. Page 38). The security server component must be installed on the se- lecte...
Page 39
Starting using the application 39 component installed on the monitored server. The application will then receive information from the server and display it as the console tree. In order to connect to the security server select the node that corresponds to the server you need in the console tree, ope...
Page 40
40 kaspersky anti-virus 5.5 for check point tm firewall-1 ® connecting applications using a secured protocol is recommended by check point tm company. By default, kaspersky anti-virus uses a secured connection protocol and the default check point tm firewall-1 ® settings. The interaction between the...
Page 41
Starting using the application 41 • the port number on the security server that will be used to receive requests for connection from check point tm firewall-1 ® . By default, these are port 18181 for cvp protocol and port 18193 for amon protocol. • the type of authentication used for connection. Sel...
Page 42
42 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • ela server: netbios name or the full domain name (fqdn) or the ip address of the computer, on which check point tm firewall-1 ® is installed, • ela sic-server name. The internal sic name of check point tm firewall-1 ® to which the securit...
Page 43
Starting using the application 43 figure 10. Configuring opsec tm settings the connection tab in order to specify settings required to configure connection between kaspersky anti-virus and check point tm firewall-1 ® that are not included in the connection tab, press the advanced button. This will o...
Page 44
44 kaspersky anti-virus 5.5 for check point tm firewall-1 ® for detailed information about secure connection types and default values for various versions of check point tm firewall- 1 ® visit the check point tm corporate website at: http://www.Opsec.Com/developer/gw_comm_mode.Html figure 11. Config...
Page 45
Starting using the application 45 do not notify option if you do not want notifications to be issued. O specify the frequency for the security server to attempt to restore the connection with check point tm firewall-1 ® if the connection fails, in the try to connection every field. Information about...
Page 46
46 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 12. Opsec tm setting configuration. The parameters tab 4. After you are done with the settings, press the apply or the ok button. You can restore the default settings by pressing the restore the default settings button. 5.6. Minimum ...
Page 47
Starting using the application 47 5.7. Protection without additional configuration the anti-virus protection will start operating immediately after the parameters for the interaction between kaspersky anti-virus and check point tm fiewall-1 are configured. The default operation mode of the anti-viru...
Page 48
48 kaspersky anti-virus 5.5 for check point tm firewall-1 ® the message sent by you contains an infected object . The message has been blocked. Suspicious, protected and corrupted objects will be delivered to the user intact. • the anti-virus database is updated hourly via internet from the kaspersk...
Page 49
Starting using the application 49 x5o!P%@ap[4\pzx54(p^)7cc)7}$eicar-standard-antivirus- test-file!$h+h* the file downloaded from the eicar website or created as described above contains the body of a standard test “virus”. Kaspersky anti-virus will detect it, assign it the infected category and appl...
Page 50
50 kaspersky anti-virus 5.5 for check point tm firewall-1 ® kaspersky anti-virus will detect this object, identify it as infected and will perform an action specified in the smtp traffic scan settings as the default action for this type of objects (see section 5.7, page 47): • all attached objects w...
Page 51
Chapter 6.Updating the anti-virus database users of kaspersky lab's products can update the anti-virus database used by kaspersky anti-virus to detect malware and to disinfect infected objects. Kaspersky lab's anti-virus database contains the description of the following objects categories: a. All c...
Page 52
52 kaspersky anti-virus 5.5 for check point tm firewall-1 ® categories of objects that will be detected by the anti-virus in the traffic passing through the firewall will be determined by the selected level of the anti-virus protection (see section 7.2, page 63). As new malicious programs are create...
Page 53
Updating the anti-virus database 53 figure 13. Anti-virus database updates settings window. Configuring internet updates downloading 3. For automatic updates, create an updates downloading schedule (details see section 6.3, page 56). If updates are required immediately, press the update now button (...
Page 54
54 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 6.1. Downloading updates from the internet in order to ensure that kaspersky anti-virus receives the anti-virus da- tabase updates from the internet, 1. Select the node corresponding to the required server in the console tree and follow the...
Page 55
Updating the anti-virus database 55 • if you connect to the internet using a proxy server, check the use proxy server box and specify the connection settings: address and number of the port used for connection. If you use a password in order to access the proxy server, specify the proxy user's authe...
Page 56
56 kaspersky anti-virus 5.5 for check point tm firewall-1 ® updates source and enter the path to the required folder in the corresponding field manually or using the browse button. 3. After you are done with the settings, press the apply or the ok button. You can restore the default settings by pres...
Page 57
Updating the anti-virus database 57 3. After you are done with the settings, press the apply or the ok button. You can restore the default settings by pressing the restore the default settings button. As a result, the application will be automatically updating the anti-virus database at the specifie...
Page 58
Chapter 7.Anti-virus protection the main task of kaspersky anti-virus is scanning mail traffic passing through check point tm firewall-1 ® and disinfecting or blocking e-mail messages using the information contained in the current (latest) version of the anti-virus database. Depending on the anti-vi...
Page 59
Anti-virus protection 59 kaspersky anti-virus allows the user to configure notifications about the results of the anti-virus scan of objects (see chapter 12 on page 110). When scanning e-mail messages transferred via smtp protocol the program scans the body of the message and all attached files of a...
Page 60
60 kaspersky anti-virus 5.5 for check point tm firewall-1 ® object is not infected, the rest of the information will be transferred to the user. Otherwise, the application will break the connection with the source and display a message informing the user that the information can not be downloaded. T...
Page 61
Anti-virus protection 61 you can configure notifications about the detection of infected, suspicious, protected and corrupted objects (see chapter 12 on page 110). No notification is made about objects that are not infected. Before the processing, a copy of the object can be saved in the backup stor...
Page 62
62 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 7.1.2. Actions performed with objects transferred via ftp protocol the following actions can be performed to disinfect infected objects detected during the scan of data transferred via ftp protocol. • disinfect – disinfect and pass the obje...
Page 63
Anti-virus protection 63 the selected action will be applied to the entire message irrespective of whether an infected, suspicious, protected or corrupted object is detected in the message body or in one of the attached files. Copies of clean and skipped objects can also be saved in the backup stora...
Page 64
64 kaspersky anti-virus 5.5 for check point tm firewall-1 ® in order to enable or disable the anti-virus protection or to change its level, 1. Select the node corresponding to the required server in the console tree and follow the anti-virus protection link in the results pane. 2. Select one of the ...
Page 65
Anti-virus protection 65 figure 16. Enabling anti-virus protection 7.4. Scanning http traffic in order to configure the settings for scanning data transferred via http protocol: 1. Select the node corresponding to the required server in the console tree and follow the http traffic settings link in t...
Page 66
66 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • transfer of information, downloaded from the source in parts, to the user. • transfer of data that does not include service information to the user. Figure 17. Http traffic scan settings the settings tab • in order to minimize the number ...
Page 67
Anti-virus protection 67 sending interval field. The value of this setting is set based on the parameters of the client program and shall not exceed the time period after which the client displays a message about the failed attempt to connect to the specified address. The suggested default value is ...
Page 68
68 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 18. Http traffic scan settings. The actions tab 3. Specify which actions will be performed upon detection of infected, suspicious, protected and corrupted objects on the actions tab (see figure 18). Determine the order of processing ...
Page 69
Anti-virus protection 69 when the save copies of clean and passed objects check box is selected, the disinfect, save a copy action will be applied to all in- fected objects instead of the disinfect action. The original copies of disinfected objects and the objects that cannot be disinfected will als...
Page 70
70 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 20. Http traffic scan settings the exclusions tab 5. In order to apply the changes, press the apply or the ok button. You can restore the default settings by pressing the restore the default settings button. In order to disable scann...
Page 71
Anti-virus protection 71 this will open the ftp scan settings window(see figure 21). Configure the anti-virus operation settings for scanning ftp traffic on the tabs of this window. The settings are configured similarly to the settings used for http traffic. (see section 7.4, page 65). Figure 21. Ft...
Page 72
72 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 22. Ftp traffic scan settings. The actions tab 4. On the exclusions tab (see figure 23) provide the list of objects that will not be scanned for the presence of malicious code. In order to do this, check boxes next to the correspondi...
Page 73
Anti-virus protection 73 figure 23. Ftp traffic scan settings. The exclusions tab 5. In order to apply the changes, press the apply or the ok button. You can restore the default settings by pressing the restore the default settings button. In order to disable scanning data transferred via ftp protoc...
Page 74
74 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 2. In order to ensure that traffic will be scanned, check the scan smtp traffic box (see figure 24) on the settings tab. Figure 24 smtp traffic scan settings the settings tab 3. Specify which actions will be performed upon detection of infe...
Page 75
Anti-virus protection 75 figure 25 smtp traffic scan settings the actions tab 4. In order to apply the changes, press the apply or the ok button. You can restore the default settings by pressing the restore the default settings button. In order to disable scanning data transferred via smtp protocol:...
Page 76
76 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 2. Select the performance tab in the anti-virus protection window that will open (see figure 26) and specify the values for the settings displayed on this tab. Figure 26. Kaspersky anti-virus performance settings • number of instances of th...
Page 77
Anti-virus protection 77 o graphic objects less than 2 mb; o all other objects (except applications) less than 256 kb. • the maximum number of objects scanned in ram without saving to the working folder on the hard drive. You can set this value in the range between 1 to 1000. The suggested default v...
Page 78
78 kaspersky anti-virus 5.5 for check point tm firewall-1 ® as archives are a type of containers, the restrictions to scan- ning containers apply to archives as well. If you impose a restriction on scanning containers, the same nesting level restrictions will be applied to archives (if ar- chives ha...
Page 79
Chapter 8.Backup storage kaspersky anti-virus allows saving a backup copy of an infected object before processing. A copy of such object is created in the backup storage. Later such object stored in the backup storage can be restored (see section 8.3, page 84) or deleted (see section 8.4, page 86). ...
Page 80
80 kaspersky anti-virus 5.5 for check point tm firewall-1 ® for convenient viewing, search for information in the backup storage and for structuring the storage the application includes configurable user filters (see section 8.2, page 81). Filters, created for the backup storage, can be viewed in th...
Page 81
Backup storage 81 • to. Ip address of the computer from which the object was requested or e-mail address of the recipient for objects transferred via smtp protocol. • size. Object’s size in bytes. • status. Status assigned to the object as a result of the anti- virus scan: infected, disinfected, sus...
Page 82
82 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 28. Creating a filter 2. Specify a name under which the filter will be saved in the backup storage folder. 3. Specify the parameter values that will be used to perform the search for (filtering of) objects stored in the backup storag...
Page 83
Backup storage 83 • http, ftp address of the source of the subject of the message for objects transferred via smtp protocol; • time interval during which the object was detected. 4. After you are done with the settings press the apply or the ok button. If you wish to cancel creation of the filter, p...
Page 84
84 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 29. Configuring filter 2. Change the values of the filter's parameters as required. 3. In order to apply the changes, press the apply or the ok button. For exit without saving the changes made, press the cancel button. As a result, t...
Page 85
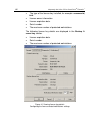
Backup storage 85 as a result of these actions the object will be moved from the backup storage into the specified folder and saved with the specified name. The restored object will have the same format as it had when it first processed by kaspersky anti-virus. After successful restoration of the ob...
Page 86
86 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 31. Restoring an object from the backup storage 8.4. Deleting objects from the backup storage the following objects are automatically deleted from the backup storage: • objects for which the storage period has expired; • "older" obje...
Page 87
Backup storage 87 2. Select the object you wish to delete in the table displaying the content of the backup storage (see figure 27). You can use filters for searching for the object (see section 8.2, page 81). 3. Open the shortcut menu and use the delete command or the analogous command under the ac...
Page 88
88 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 32. Configuring the backup storage settings 4. In order to apply the changes, press the apply or the ok button. For exit without saving the changes made, press the cancel button. You can restore the default settings by pressing the r...
Page 89
Chapter 9.Reports kaspersky anti-virus allows receiving reports about the results of the anti-virus traffic scan. Reports contain information registered during a certain period of time and provide information about: • general scan results • the total number of scanned objects: • the total size of al...
Page 90
90 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 33. The report templates folder apart from the template name the table contains the following information for each template: • status: status of the report created based on the template. • expected: date and time of creation of the n...
Page 91
Reports 91 9.1. Creating reports in order to create an anti-virus scan report: 1. Create a report template (see section 9.2, page 92) or select an existing template. 2. Check the create report box on the general tab of the report template configuration window (see figure 35). As a result, a new repo...
Page 92
92 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 2. Open the shortcut menu and use the properties command or the analogous command under the action menu. 3. In the properties: report templates window that will open (see figure 34): figure 34. Configuring the reports settings • check the s...
Page 93
Reports 93 2. Open the shortcut menu and use the create a report template or the analogous command under the action menu. 3. As a result, a report template settings window template> will open (see figure 35); this window consists of the following tabs: general and parameters. Specify the required va...
Page 94
94 kaspersky anti-virus 5.5 for check point tm firewall-1 ® specify the reporting period and the report creation schedule set- tings in the settings tab (see figure 36). • the following options are available when specifying the reporting period: o specify the time interval. In this case, the report ...
Page 95
Reports 95 figure 36. Report template. The settings tab 9.3. Viewing reports in order to view a report using the file system: 1. Enter the folder where the logs are stored. By default, it is the reports folder located on the server in the application's data folder. 2. Select and open an html file wi...
Page 96
96 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 37. Viewing reports general scan results the left frame of the report contains the list of the report’s sections (table of contents); the heading and the content of the selected section are displayed in the right frame. In order to v...
Page 97
Reports 97 3. Open the shortcut menu and use the view report or the analogous command under the action menu. 4. As the result the last report created based on the selected template will be displayed. Reports are viewed using the default system browser. 5. If no reports were created based on the sele...
Page 98
Chapter 10.Application event log kaspersky anti-virus allows the user to perform full diagnostic of its operation and to register events in the microsoft windows application log in the kaspersky anti-virus application's log. The degree of the completeness of the information entered into the logs dep...
Page 99
Application event log 99 new records entered into kaspersky anti-virus logs are appended to the end of the newest file. The log size is not restricted. Kaspersky anti-virus logs can be viewed by using the file system. By default, logs are stored in the logs folder. This folder is created in the appl...
Page 100
100 kaspersky anti-virus 5.5 for check point tm firewall-1 ® figure 39. The diagnostics tab 3. The diagnostics level for system components section located in the tab contains a table. The left part of the table contains the list of all components included into the structure of the program. The right...
Page 101
Application event log 101 4. After you are done with the settings, press the apply or the ok button. You can restore the default settings by pressing the restore the default settings button. 10.2. Configuring log files settings in order to configure logs files settings, 1. Select the node correspond...
Page 102
Chapter 11.License keys when you purchase kaspersky anti-virus, you enter into a license agreement with kaspersky lab ltd. Based on this agreement you are entitled to use this software during the specified period of time to protect the mail traffic received and requested from the number of workstati...
Page 103
License keys 103 about the expiration date of the currently installed license key. Notification period can be changed (see section 11.3 on page 107). Kaspersky anti-virus settings also provide for a possibility to configure notifications of the forthcoming expiration of the license and restrictions ...
Page 104
104 kaspersky anti-virus 5.5 for check point tm firewall-1 ® 11.1. License information in order to view the license: 1. Select the node corresponding to the required server in the console tree and follow the general settings link in the results pane. 2. Go to the general tab in the general parameter...
Page 105
License keys 105 • license expiry date: • the status of the current license key. • application functionality available based on the current license key: o all functions. The application operates as provided for in the license agreement. O updating function is not available. The anti-virus data- base...
Page 106
106 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • the type of the license key installed, for example: commercial, trial. • license owner information • license expiration date. • serial number. • the maximum number of protected workstations. The following license key details are displaye...
Page 107
License keys 107 11.3. License-related notifications the application verifies the compliance with the terms and conditions of the license agreement on a regular basis and each time the anti-virus database is updated. If the following is the case based on the verification results: • the current licen...
Page 108
108 kaspersky anti-virus 5.5 for check point tm firewall-1 ® if the current license key is found in the “black list”, the backup key will not be activated. In this case you have to replace the current license key. You can manually install the backup license key as the current key. There is a provisi...
Page 109
License keys 109 1. Select the node corresponding to the required server in the console tree and follow the general settings link in the results pane. 2. Go to the license keys tab in the general settings window that will open (see figure 41). 3. On the license keys tab: • if you are removing the ba...
Page 110
Chapter 12.Notifications notifications about events registered in the operation of the kaspersky anti-virus application can be configured by the use of the in-built notification feature of check point tm firewall-1 ® . For this the following features must be configured: • settings of interaction of ...
Page 111
Notifications 111 the application functionality at the expiration of the license, restoration of the functionality after the license is renewed. In order to configure notifications made via kaspersky anti-virus: 1. Select the node corresponding to the required server in the console tree and follow t...
Page 112
112 kaspersky anti-virus 5.5 for check point tm firewall-1 ® an example of a program to be launched is a script file alert.Js included in the application distribution package. After the installation of the security server file alert.Js issaved into the component installation folder in the service fo...
Page 113
Notifications 113 events has its own set of variables, the complete list of variables is provided in appendix a on page 118..
Page 114
Chapter 13.Frequently asked questions this chapter is devoted to questions most frequently asked by users regarding the installation, setup, and operation of kaspersky anti-virus. We will try to answer them here in detail. Question: can kaspersky anti-virus be used with other vendors’ anti- virus so...
Page 115
Frequently asked questions 115 only work either for two weeks or for a month. When this period expires, the key will be blocked. Question: what happens when my kaspersky anti-virus license ex- pires? After the expiration of the license, kaspersky anti-virus will continue operating, but anti-virus da...
Page 116
116 kaspersky anti-virus 5.5 for check point tm firewall-1 ® and can only help you if they fully understand it and have been able to reproduce it. 5. Forward to the technical support service the following data packed in one archive: • the current application events logs produced with the debug diagn...
Page 117
Frequently asked questions 117 question: i use a proxy server and cannot perform updates. What should i do? Failure to receive updates via a proxy server can be attributed to the fol- lowing: • incorrect network settings. When configuring the update service you can specify the net- work settings usi...
Page 118
Appendix a.Notification settings this section contains description of settings passed to the application launched in order to issue notification about a kaspersky anti-virus event (see chapter 12 on page 110). Settings are passed using microsoft windows environment variables. Provided below is the l...
Page 119
Appendix a 119 event description settings passed kav4cpf1_to = (for smtp only) kav4cpf1_virus = or kav4cpf1_error = ror_description> or object anti-virus scan notifications queue overflow kav4cpf1_event = "overflow" kav4cpf1_number = ber_of_missed_notifications> kav4cpf1_time = anti-virus database u...
Page 120
120 kaspersky anti-virus 5.5 for check point tm firewall-1 ® event description settings passed report creation report created successfully. Kav4cpf1_event = "report" kav4cpf1_title = (specified in the report set- tings) kav4cpf1_path = kav4cpf1_error = kav4cpf1_time = error creating report. Report h...
Page 121
Appendix a 121 event description settings passed is restored as the result of the license renewal. Only management functionality is available. The event occurs in case of a violation of the license agreement, trial key expiration or anti- virus database corruption. Kav4cpf1_event = "status" kav4cpf1...
Page 122
Appendix b.Glossary the product's documentation contains terms and concepts specific to the field of anti-virus protection. This glossary contains definitions of such concepts. For your convenience, the terms are arranged in the alphabetic order. А administrator’s workstation– a computer on which th...
Page 123
Appendix b 123 black list – a database that contains information about license keys whose owners infringed the terms of the license agreement and about keys that have been created but, for any reason, have not been sold. The content of the black list is updated on a daily basis. C container object –...
Page 124
124 kaspersky anti-virus 5.5 for check point tm firewall-1 ® license period– a period of time for which you are granted the right to use all features of kaspersky anti-virus. The license period is determined by the license key; a standard license period is one year after the license key is installed...
Page 125
Appendix b 125 t traffic scan – anti-virus scan of e-mail messages received by the server in the real-time mode using the current (latest) version of the anti-virus da- tabase. V virus outbreak counter – a template used to create and issue notifications about a virus outbreak threat. The virus outbr...
Page 126
Appendix c.Kaspersky lab founded in 1997, kaspersky lab has become a recognized leader in information security technologies. It produces a wide range of data security software and delivers high-performance, comprehensive solutions to protect computers and networks against all types of malicious prog...
Page 127
Appendix c 127 c.1. Other kaspersky lab products kaspersky anti-virus ® personal kaspersky anti-virus ® personal has been designed to provide anti-virus protection to personal computers running microsoft windows 98/me or microsoft windows 2000/nt/xp against all known viruses, including potentially d...
Page 128
128 kaspersky anti-virus 5.5 for check point tm firewall-1 ® unique second-generation heuristic analyzer efficiently detects unknown viruses. A simple and convenient interface allows users to configure the program quickly making work with it easier than ever. Kaspersky anti-virus ® personal pro has ...
Page 129
Appendix c 129 kaspersky ® personal security suite kaspersky ® personal security suite is a software suite designed for organizing comprehensive protection of personal computers running microsoft windows. The suite prevents malicious and potentially dangerous programs from penetrating through any po...
Page 130
130 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • save a report on the scanning results in txt or html formats. Kaspersky ® online scanner pro this program is a subscription service available to visitors of the corporate website allowing to perform efficient anti-virus scan of your comp...
Page 131
Appendix c 131 • system restoration after malicious spyware influence accomplished due to recording of all changes in the registry and computer file system and an opportunity to perform their roll-back at user's discretion. Kaspersky ® internet security 6.0 kaspersky ® internet security 6.0 is an in...
Page 132
132 kaspersky anti-virus 5.5 for check point tm firewall-1 ® • verification against black and white lists of recipients (including addresses of phishing sites). • inspection of phrases in message body. • analysis of message text using a self-learning algorithm. • recognition of spam sent in image fi...
Page 133
Appendix c 133 you are free to choose from any of these anti-virus applications, according to the operating systems and applications you use. Kaspersky ® corporate suite this package provides corporate networks of any size and complexity with comprehensive, scalable anti-virus protection. The packag...
Page 134
134 kaspersky anti-virus 5.5 for check point tm firewall-1 ® installed at the entrance to a network, where it monitors incoming e-mail traffic streams for spam, kaspersky ® anti-spam acts as a barrier to unsolicited e-mail. The product is compatible with any mail system and can be installed on eithe...
Page 135
Appendix c 135 any matters related to our product by phone or via email. All of your recommendations and suggestions will be thoroughly reviewed and considered. Technical support please find the technical support information at http://www.Kaspersky.Com/supportinter.Html general information www: http...
Page 136
Appendix d.License agreement end user license agreement notice to all users: carefully read the following le- gal agreement ("agreement") for the license of speci- fied software ("software") produced by kaspersky lab ("kaspersky lab"). If you have purchased this software via the internet by clicking...
Page 137
Appendix d 137 this case, kaspersky lab will not be held by the part- ner's clauses. The right to return and refund extends only to the original purchaser. All references to "software" herein shall be deemed to include the software activation key ("key identification file") with which you will be pr...
Page 138
138 kaspersky anti-virus 5.5 for check point tm firewall-1 ® steps to achieve interoperability, provided that you only reverse engineer or decompile the software to the extent permitted by law. 1.1.4 you shall not make error corrections to, or otherwise modify, adapt, or translate the software, nor ...
Page 139
Appendix d 139 described herein. Upon any termination or expiration of this agreement, you must immediately destroy all copies of the software and the documentation. You may terminate this agreement at any point by destroying all copies of the software and the documentation. 3. Support. (i) kaspersk...
Page 140
140 kaspersky anti-virus 5.5 for check point tm firewall-1 ® you shall implement reasonable security measures to protect such confidential information, but without limitation to the foregoing shall use best endeavours to maintain the security of the key identification file. 6. Limited warranty. (i) ...
Page 141
Appendix d 141 (whether such losses or damage were foreseen, foreseeable, known or otherwise): (a) loss of revenue; (b) loss of actual or anticipated profits (including for loss of profits on contracts); (c) loss of the use of money; (d) loss of anticipated savings; (e) loss of business; (f) loss of...