- DL manuals
- KAPERSKY
- Other
- ANTI-VIRUS 7.0
- User Manual
KAPERSKY ANTI-VIRUS 7.0 User Manual
Summary of ANTI-VIRUS 7.0
Page 1
Kaspersky lab kaspersky anti-virus 7.0 user guide.
Page 2
K a s p e r s k y a n t i - v i r u s 7 . 0 user guide kaspersky lab http://www.Kaspersky.Com revision date: december, 2007.
Page 3
Contents chapter 1. Threats to computer security................................................. 9 1.1. Sources of threats ................................................................................................ 9 1.2. How threats spread ........................................................
Page 4
4 kaspersky anti-virus 7.0 3.2.5. Configuring a virus scan schedule ............................................................... 36 3.2.6. Restricting program access .......................................................................... 37 3.2.7. Application integrity control ...................
Page 5
Contents 5 chapter 7. File anti-virus ................................................................................... 73 7.1. Selecting a file security level ............................................................................... 74 7.2. Configuring file anti-virus .........................
Page 6
6 kaspersky anti-virus 7.0 10.3.2. Creating a registry guard rule ................................................................ 122 chapter 11. Scanning computers for viruses ..................................... 125 11.1. Managing virus scan tasks ...................................................
Page 7
Contents 7 15.2.2. Configuring backup settings .................................................................... 163 15.3. Reports ............................................................................................................ 163 15.3.1. Configuring report settings ....................
Page 8
8 kaspersky anti-virus 7.0 16.11. Viewing help .................................................................................................. 207 16.12. Return codes from the command line interface ........................................... 207 chapter 17. Modifying, repairing, and removing the...
Page 9
Chapter 1.Threats to computer security as information technology has rapidly developed and penetrated many aspects of human existence, so the number and range of crimes aimed at breaching in- formation security has grown. Cyber criminals have shown great interest in the activities of both state stru...
Page 10
10 kaspersky anti-virus 7.0 internal, including the actions of company staff and users of home pcs.Actions taken by this group could be deliberate or accidental. The technological factor. This threat group is connected with technical problems – use of obsolete or poor-quality software and hardware t...
Page 11
Threats to computer security 11 intranet your intranet is your internal network, specially designed for handling information within a company or a home network. An intranet is a unified space for storing, exchanging, and accessing information for all the computers on the network. Therefore, if any o...
Page 12
12 kaspersky anti-virus 7.0 1.3. Types of threats there are a vast number of threats to computer security today. This section will review the threats that are blocked by kaspersky anti-virus. Worms this category of malicious programs spreads itself largely by exploiting vul- nerabilities in computer...
Page 13
Threats to computer security 13 spyware this software collects information about a particular user or organization without their knowledge. Spyware often escapes detection entirely. In gen- eral, the goal of spyware is to: trace user actions on a computer; gather information on the contents of your ...
Page 14
14 kaspersky anti-virus 7.0 word-cracking programs, and other types of programs for cracking network resources or penetrating a system. Kaspersky anti-virus uses two methods for detecting and blocking these threat types: reactive: it is a method designed to search for malicious objects using continu...
Page 15
Threats to computer security 15 it must be noted that these signs can arise from causes other than viruses. For example, in the case of email, infected messages can be sent with your return address but not from your computer. There are also indirect indications that your computer is infected: your c...
Page 16
16 kaspersky anti-virus 7.0 puter to the internet, there is a chance that the virus will send important information to hackers or spread the virus to the addresses in your ad- dress book. That is why if you suspect that your computer has a virus, you should immediately disconnect from the internet. ...
Page 17
Threats to computer security 17 rule no. 2: use caution when copying new data to your computer: scan all removable storage drives, for example floppies, cd/dvds, and flash drives, for viruses before using them (see 5.5 on pg. 51). Treat emails with caution. Do not open any files attached to emails u...
Page 18
Chapter 2.Kaspersky anti- virus 7.0 kaspersky anti-virus 7.0 heralds a new generation of data security products. What really sets kaspersky anti-virus 7.0 apart from other software, even from other kaspersky lab products, is its multi-faceted approach to data security. 2.1. What’s new in kaspersky a...
Page 19
Kaspersky anti-virus 7.0 19 scans using ichecker and iswift. By operating this way, the program rules out scanning files twice. The scan process now runs as a background task, enabling the user to continue using the computer. If there is a competition for system re- sources, the virus scan will paus...
Page 20
20 kaspersky anti-virus 7.0 new program interface features the new kaspersky anti-viru s interface makes the program‟s functions clear and easy to use. You can also change the program‟s appearance by using your own graphics and color schemes. The program regularly provides you with tips as you use i...
Page 21
Kaspersky anti-virus 7.0 21 kaspersky anti-virus includes: real-time protection components (see 2.2.1 on pg. 21) providing real- time protection of all data transfer and input paths through your com- puter. Virus scan tasks (see 2.2.2 on pg. 22) used to scan individual files, folders, drives, or are...
Page 22
22 kaspersky anti-virus 7.0 web anti-virus is specially designed to combat these risks, by intercepting and blocking scripts on web sites if they pose a threat, and by thoroughly monitoring all http traffic. Proactive defense the number of malicious programs grows daily. Such programs become more co...
Page 23
Kaspersky anti-virus 7.0 23 there is also the option to create other virus-scan tasks and create a schedule for them. For example, you can create a scan task for mailboxes once per week, or a virus scan task for the my documents folder. 2.2.3. Update in order to always be ready to delete a virus or ...
Page 24
24 kaspersky anti-virus 7.0 activation when purchasing kaspersky anti-virus, you enter into a licensing agree- ment with kaspersky lab which governs the use of the application as well as your access to application database updates and technical support over a specified period of time. The term of us...
Page 25
Kaspersky anti-virus 7.0 25 128 mb of ram microsoft windows vista, microsoft windows vista x64: intel pentium 800 mhz 32-bit (x86)/ 64-bit (x64) or faster (or compati- ble) 512 mb of ram 2.4. Software packages you can purchase the boxed version of kaspersky anti-virus from our resellers, or download...
Page 26
26 kaspersky anti-virus 7.0 2.5. Support for registered users kaspersky lab provides its registered users with an array of services to make kaspersky anti-virus more effective. When the program has been activated, you become a registered user and will have the following services available until the ...
Page 27
Chapter 3.Installing kaspersky anti-virus 7.0 there are several ways to install kaspersky anti-virus 7.0 to a host: interactively, using the application installation wizard (see 3.1 on pg. 27); this mode requires user input for the install to proceed; non-interactively, this type of install is perfo...
Page 28: Stall Kaspersky Anti-Virus
28 kaspersky anti-virus 7.0 next – accepts an action and moves forward to the next step of installa- tion. Back – goes back to the previous step of installation. Cancel – cancels product installation. Finish – completes the program installation procedure. Le t‟s take a closer look at the steps of th...
Page 29
Installing kaspersky anti-virus 7.0 29 well as configure the installation using a special wizard (see 3.2 on pg. 31). Under the former option, the install will be performed non-interactively, i. E. Sub- sequent steps described in this section will be skipped. In the latter case, you will be required...
Page 30
30 kaspersky anti-virus 7.0 after you have selected the components you want to install, click next. To return the list to the default programs to be installed, click reset. Step 7. Using previously saved installation settings in this step, you are prompted to specify whether you wish to use previous...
Page 31
Installing kaspersky anti-virus 7.0 31 step 9. Finishing program installation in this stage, the program will ask you to finish installing the program on your computer. We do not recommend deselecting the enable self-defense before installa- tion when initially installing kaspersky internet security...
Page 32
32 kaspersky anti-virus 7.0 you can skip this initial settings stage when installing the program by closing the wizard window. In the future, you can run it again from the program interface if you restore the default settings for kaspersky anti-virus (see 15.9.4 on pg. 189). 3.2.1. Using objects sav...
Page 33
Installing kaspersky anti-virus 7.0 33 apply existing key. Activate the application using the key file for kaspersky anti-virus 7.0. Activate later. If you choose this option, you will skip the activation stage. Kaspersky anti-virus 7.0 will be installed on your computer and you will have access to ...
Page 34
34 kaspersky anti-virus 7.0 3.2.2.3. User registration this step of the activation wizard requires you to provide your contact informa- tion: email address, city and country of residence. This information is required for kaspersky lab technical support to identify you as a registered user. After the...
Page 35
Installing kaspersky anti-virus 7.0 35 3.2.2.6. Completing program activation the setup wizard will inform you that the program has been successfully acti- vated. It will also display information on the license key installed: owner name, key code, key type (commercial, for beta testing, trial, etc.)...
Page 36
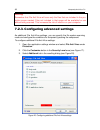
36 kaspersky anti-virus 7.0 3.2.4. Configuring update settings your computer‟s security depends directly on updating databases and program modules on a regular basis. In this window, the setup wizard asks you to select a mode for program updates, and to configure a schedule. Automatically. Kaspersky...
Page 37
Installing kaspersky anti-virus 7.0 37 full computer scan for a full virus scan of your computer to run automatically, check the appro- priate box. You can configure the schedule by clicking change. The default setting, for scheduled running of this task, is disabled. However, we recommend running a...
Page 38
38 kaspersky anti-virus 7.0 in the future, kaspersky anti-virus will use information obtained while analyzing application structure to prevent malicious code from being imbedded in applica- tion modules. Analyzing the applications installed on your computer may take some time. 3.2.8. Finishing the s...
Page 39
Chapter 4.Program interface kaspersky anti-virus has a straightforward, user-friendly interface. This chapter will discuss its basic features: icon in the taskbar notification area (see 4.1 on pg. 39) context menu (see 4.2 on pg. 40) main window (see 4.3 on pg. 41) program settings window (see 4.4 o...
Page 40
40 kaspersky anti-virus 7.0 emails are being scanned. Scripts are being scanned. A file that you or some program is opening, saving, or running is being scanned. Kaspersky anti-virus databases and program modules are being up- dated. Computer needs to reboot to apply updates. An error has occurred i...
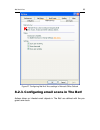
Page 41
Program interface 41 activate – activate the program. You must activate your version of kas- persky anti-virus to obtain registered user status which provides access to the full functionality of the application and technical support. This menu item is only available if the program is not activated. ...
Page 42
42 kaspersky anti-virus 7.0 computer is properly protected while yellow and red are indications of various problems in kaspersky anti-virus configuration or operation. To obtain detailed troubleshooting information and speedy problem res- olution, use the security wizard which opens when the securit...
Page 43
Program interface 43 main window section purpose the primary purpose of the protection section is to provide access to your com- puter‟s basic real-time protection compo- nents. To view the status of a protection compo- nent or its modules, to configure its settings or open a relevant report, select...
Page 44
44 kaspersky anti-virus 7.0 the update section contains information on application updates: database publica- tion date and virus signature record count. Appropriate links may be used to start an update, view a detailed report, configure updates, and roll an update back to a pre- vious version. Repo...
Page 45
Program interface 45 the lower left-hand side of the window houses two buttons: help, which provides access to the kaspersky anti-virus help system, and settings, which opens the application settings window. 4.4. Program settings window you can open the kaspersky anti-virus settings window from the ...
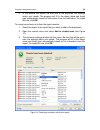
Page 46
46 kaspersky anti-virus 7.0 figure 3. Kaspersky anti-virus settings window.
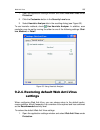
Page 47
Chapter 5.Getting started one of kaspersky lab‟s main goals in creating kaspersky anti-virus was to pro- vide optimum configuration for each of the program‟s options. This makes it possible for a user with any level of computer literacy to quickly protect their computer straight after installation. ...
Page 48
48 kaspersky anti-virus 7.0 the following color codes are used to show protection status: application main window is green. This status is an indication that your computer is properly protected. Which means that the databases have been updated in a timely man- ner, all protection components are acti...
Page 49
Getting started 49 postpone threat elimination. If for any reason you cannot immediately eliminate the threat, you can postpone that action and come back to it later. To do so, use the postpone link. Note that this option is not available for serious threats. Such threats in- clude, for example, mal...
Page 50
50 kaspersky anti-virus 7.0 your own, save the component report to a file using action → save as and contact kaspersky lab technical support. Component status may be followed by information on settings being used by the component (such as, security level, action to be applied to dangerous objects). ...
Page 51
Getting started 51 5.4. How to scan critical areas of the computer there are areas on your computer that are critical from a security perspective. These are the targets of malicious programs aimed at damaging your operating system, processor, memory, etc. It is extremely important to protect these c...
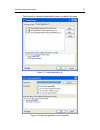
Page 52
52 kaspersky anti-virus 7.0 figure 4. Scanning an object selected using a standard microsoft windows context-sensitive menu a scan of the selected object will then begin, and the details will be shown in a special window. When you click the close button, the window with information about installatio...
Page 53
Getting started 53 as a result, kaspersky anti-virus will begin the update process, and display the details of the process in a special window. 5.7. What to do if protection is not running if problems or errors arise in the performance of any protection component, be sure to check its status. If the...
Page 54
Chapter 6.Protection management system this section provides information on configuring common application settings used by all real-time protection components and tasks as well as information on creating protection scopes and lists of threats to be handled by the application and a list of trusted o...
Page 55
Protection management system 55 note that in this case protection is discussed in the context of the protection components. Disabling or pausing protection components does not affect the performance of virus scan tasks or program updates. 6.1.1. Pausing protection pausing real-time protection means ...
Page 56
56 kaspersky anti-virus 7.0 figure 5. Pause protection window 6.1.2. Stopping protection stopping protection means fully disabling your real-time protection components. Virus scans and updates continue to work in this mode. If protection is stopped, it can be only be resumed by the user: protection ...
Page 57
Protection management system 57 6.1.3. Pausing / stopping individual protection components there are several ways to stop a protection component. Before doing so, you are strongly advised to establish why you need to stop it. It is likely that the problem can be solved in another way, for example, b...
Page 58
58 kaspersky anti-virus 7.0 from the context menu. To do so, select resume protection. From the program’s main window. Select the protection section in the left-hand side of the main window and click enable protection. The protection status immediately changes to running . The program‟s icon in the ...
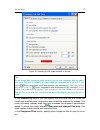
Page 59
Protection management system 59 tection, and check disable scheduled scans while running on battery power under additional (see figure 6). 6.4. Runtime computer performance to limit cpu and storage subsystem loads, virus scan tasks may be postponed. Scanning for viruses increases cpu and storage sub...
Page 60
60 kaspersky anti-virus 7.0 caution! If the application is installed on a computer running microsoft windows vista or microsoft windows vista x64, resolution of compatibility issued for other applica- tions‟ built-in tamper-proof mechanisms is not supported. 6.6. Running virus scans and updates as a...
Page 61
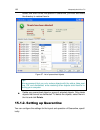
Protection management system 61 figure 8. Configuring an update task from another profile 6.7. Configuring scheduled tasks and notifications scheduling configuration is the same for virus scan tasks, application updates, and kaspersky anti-virus runtime messages. By default, the virus scan tasks cre...
Page 62
62 kaspersky anti-virus 7.0 figure 9. Creating task execution schedule days. Tasks will be started or notifications sent every few days. Specify the interval length in the schedule settings: select every n days and specify n, if you wish to keep an interval of a certain number of days. Select every ...
Page 63
Protection management system 63 6.8. Types of malware to monitor kaspersky anti-virus protects you from various types of malicious programs. Regardless of your settings, the program always protects your computer from the most dangerous types of malware such as viruses, trojans, and hack tools. These...
Page 64
64 kaspersky anti-virus 7.0 figure 10. Selecting threats to monitor 6.9. Creating a trusted zone a trusted zone is a list of objects created by the user, that kaspersky anti-virus does not monitor. In other words, it is a set of programs excluded from protec- tion. The user creates a trusted zone ba...
Page 65
Protection management system 65 figure 11. Creating a trusted zone 6.9.1. Exclusion rules exclusion rules are sets of conditions that kaspersky anti-virus uses to deter- mine not to scan an object. You can exclude files of certain formats from the scan, use a file mask, or ex- clude a certain area, ...
Page 66
66 kaspersky anti-virus 7.0 kaspersky anti-virus, see the virus encyclopedia at www.Viruslist.Com ). After the scan, these programs may be blocked. Since several of them are very common, you have the option of excluding them from the scan. To do so, you must add threat name or mask to the trusted zo...
Page 67
Protection management system 67 figure 12. Creating an exclusion rule 3. Assign values to the selected exclusion types. To do so, left-click in the rule description section on the specify link located next to the exclu- sion type: for the object type, enter its name in the window that opens (this ca...
Page 68
68 kaspersky anti-virus 7.0 o launchinginternetbrowser. For this threat, you can list browser open settings as additional exclusion settings. For example, you blocked browsers from opening with certain settings in the proactive defense application activity analysis. However, you want to allow the br...
Page 69
Protection management system 69 2. In the window that opens, be sure that all the exclusion rule settings match your needs. The program will fill in the object name and threat type automatically, based on information from the notification. To create the rule, click ok. To create an exclusion rule fr...
Page 70
70 kaspersky anti-virus 7.0 6.9.2. Trusted applications kaspersky anti-virus provides the capability to create a list of trusted applica- tions whose activity, suspicious or otherwise, or file, network, and system registry access, is not monitored. For example, you feel that objects and processes us...
Page 71
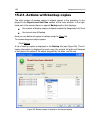
Protection management system 71 the file path is inserted automatically when you select its name. Figure 15. Trusted application list figure 16. Adding an application to the trusted list.
Page 72
72 kaspersky anti-virus 7.0 3. Specify which actions performed by this process will not be monitored: do not scan opened files – excludes from the scan all files that the trusted application process. Do not restrict application activity – excludes from proactive de- fense monitoring any activity, su...
Page 73
Chapter 7.File anti-virus the kaspersky anti-virus component that protect your computer files against infection is called file anti-virus. It loads when you start your operating system, runs in your computer‟s ram, and scans all files opened, saved, or executed. The component‟s activity is indicated...
Page 74
74 kaspersky anti-virus 7.0 7.1. Selecting a file security level file anti-virus protects files that you are using at one of the following levels (see figure 17): maximum protection – the level with the most comprehensive monitor- ing of files opened, saved, or run. Recommended –kaspersky lab recomm...
Page 75
File anti-virus 75 example: the work you do on your computer uses a large number of file types, and some the files may be fairly large. You would not want to run the risk of skipping any files in the scan because of the size or extension, even if this would somewhat affect the productivity of your c...
Page 76
76 kaspersky anti-virus 7.0 7.2.1. Defining the file types to be scanned when you select file types to be scanned, you establish what file formats, sizes, and what drives will be scanned for viruses when opened, executed, or saved. To make configuration easier, all files are divided into two groups:...
Page 77
File anti-virus 77 figure 18. Selecting the file types scanned for viruses tip: do not forget that someone could send a virus to your computer with an exten- sion (e.G. .Txt) that is actually an executable file renamed as a .Txt file. If you select scan programs and documents (by extension), the sca...
Page 78
78 kaspersky anti-virus 7.0 scan archives – scans .Zip, .Cab, .Rar, and .Arj archives. Scan installation packages – scans self-extracting archives for viruses. Scan embedded ole objects – scans objects imbedded in files (for exam- ple, microsoft office excel spreadsheets or macros imbedded in a micr...
Page 79
File anti-virus 79 3. Combine methods one and two – create a protection scope that ex- cludes a number of objects. Figure 19. Creating a protected zone you can use masks when you add objects for scanning. Note that you can only enter masks will absolute paths to objects: c:\dir\*.* or c:\dir\* or c:...
Page 80
80 kaspersky anti-virus 7.0 warning! Remember that file anti-virus will scan only the files that are included in the pro- tection scope created. Files not included in that scope will be available for use without being scanned. This increases the risk of infection on your computer. 7.2.3. Configuring...
Page 81
File anti-virus 81 the file scanning mode determines the file anti-virus processing conditions. You have following options: smart mode. This mode is aimed at speeding up file processing and return them to the user. When it is selected, a decision to scan is made based on analyzing the operations per...
Page 82
82 kaspersky anti-virus 7.0 you can temporarily disable the pause on file anti-virus when using a specific application. To do so, uncheck the name of the application. You do not have to delete it from the list. Figure 22. Creating an application list 7.2.4. Using heuristic analysis heuristic methods...
Page 83
File anti-virus 83 delete the object skip (if you are positive that the object cannot be malicious). To use the heuristic method, select use heuristic analyzer. You can addi- tionally select the level of detail of the scan. To do so, move the slider to one of these positions: shallow, medium, or det...
Page 84
84 kaspersky anti-virus 7.0 the heuristic analyzer tab(see figure 23) may be used to disable / enable file anti-virus heuristic analysis for unknown threats. This requires that the following steps be performed: 1. Open the application settings window and select file anti-virus under protection. 2. C...
Page 85
File anti-virus 85 to edit an action for an object: open the application settings window and select file anti-virus under pro- tection. All potential actions are displayed in the appropriate sections (see figure 24). Figure 24. Possible file anti-virus actions with dangerous objects if the action se...
Page 86
86 kaspersky anti-virus 7.0 if the action selected was when it detects a dangerous object delete will delete it. When disinfecting or deleting an object, kaspersky anti-virus creates a backup copy before it attempts to treat the object or delete it, in case the object needs to be restored or an oppo...
Page 87
Chapter 8.Mail anti-virus mail anti-virus is kaspersky anti- virus‟s component to prevent incoming and outgoing email from transferring dangerous objects. It starts running when the operating system boots up, stays active in your system memory, and scans all email on protocols pop3, smtp, imap, mapi...
Page 88
88 kaspersky anti-virus 7.0 if no malicious code is discovered in the email, it is immediately made available again to the user. A special plug-in (see 8.2.2 on pg. 92) is provided for microsoft office outlook that can configure email scans more exactly. If you use the bat!, kaspersky anti-virus can...
Page 89
Mail anti-virus 89 you can raise or lower the email security level by selecting the level you want, or editing the settings for the current level. To change the security level: adjust the sliders. By altering the security level, you define the ratio of scan speed to the total number of objects scann...
Page 90
90 kaspersky anti-virus 7.0 settings defining the use of heuristic methods(see 8.2.4 on pg. 95) email scan settings for microsoft office outlook (see 8.2.2 on pg. 92) and the bat! (see 8.2.3 on pg. 93) settings that define actions for dangerous email objects (see 8.2.4 on pg. 95) the following secti...
Page 91
Mail anti-virus 91 figure 26. Mail anti-virus settings you can configure the filtration conditions for objects connected to an email in the attachment filter section: disable filtering – do not use additional filtration for attachments. Rename selected attachment types – filter out a certain attachm...
Page 92
92 kaspersky anti-virus 7.0 8.2.2. Configuring email processing in microsoft office outlook if you use microsoft office outlook as your email client, you can set up custom configurations for virus scans. A special plug-in is installed in microsoft office outlook when you install kas- persky anti-vir...
Page 93
Mail anti-virus 93 figure 27. Configuring mail anti-virus settings in microsoft office outlook 8.2.3. Configuring email scans in the bat! Actions taken on infected email objects in the bat! Are defined with the pro- gram's own tools..
Page 94
94 kaspersky anti-virus 7.0 warning! The mail anti-virus settings that determine whether incoming and outgoing email is scanned, as well as actions on dangerous email objects and exclu- sions, are ignored. The only settings that the bat! Takes into account relate to scanning archived attachments and...
Page 95
Mail anti-virus 95 the actions taken by the email client when dangerous objects are de- tected in emails. For example, you could select: try to cure infected parts – tries to treat the infected email object, and if the object cannot be disinfected, it stays in the email. Kaspersky anti-virus will al...
Page 96
96 kaspersky anti-virus 7.0 figure 29. Using heuristic analysis heuristic methods of detecting new threats may be enabled / disabled for the mail anti-virus component using the heuristic analyzer tab. This requires that the following steps be performed: 1. Open the application settings window and se...
Page 97
Mail anti-virus 97 to restore the default mail anti-virus settings: 1. Open the application settings window and select mail anti-virus under protection. 2. Click the default button under security level (see figure 25). 8.2.6. Selecting actions for dangerous email objects if a scan shows that an emai...
Page 98
98 kaspersky anti-virus 7.0 if the action selected was when a dangerous object is detected prompt for action mail anti-virus will issue a warning mes- sage containing information about what malicious program has infected (potentially infected) the file and gives you the choice of one of the followin...
Page 99
Chapter 9.Web anti-virus whenever you use the internet, information stored on your computer is open to the risk of infection by dangerous programs, which can penetrate your computer when you read an article on the internet. Web anti-virus is kaspersky anti- virus‟s component for guarding your comput...
Page 100
100 kaspersky anti-virus 7.0 web anti-virus guards http traffic as follows: 1. Each web page or file that can be accessed by the user or by a certain application via http is intercepted and analyzed by web anti-virus for malicious code. Malicious objects are detected using both the databas- es inclu...
Page 101
Web anti-virus 101 but limits the caching time for file fragments, thus accelerating the scan and returning objects to the user sooner. High speed – the security level with settings that let you comfortably use resource-intensive applications, since the scope of objects scanned is reduced by using a...
Page 102
102 kaspersky anti-virus 7.0 through http traffic, because there is no centralized web protection and due to the use of dial-up to connect to the internet. It is recommended that you use maximum protection as your starting point, with the following changes: you are advised to limit the caching time ...
Page 103
Web anti-virus 103 pying and processing large objects because of the connection with the http client timing out. We suggest limiting the caching time for web object fragments downloaded from the internet to solve this problem. When this time limit expires, the user will re- ceive the downloaded part...
Page 104
104 kaspersky anti-virus 7.0 9.2.2. Creating a trusted address list you have the option of creating a list of trusted addresses whose contents you fully trust. Web anti-virus will not analyze data from those addresses for danger- ous objects. This option can be used in cases where web anti-virus rep...
Page 105
Web anti-virus 105 1. Open the application settings window and select web anti-virus under protection. 2. Click the customize button in the security level area. 3. Select heuristic analyzer tab in the resulting dialog (see figure 33). To use heuristic methods, check use heuristic analyzer. In additi...
Page 106
106 kaspersky anti-virus 7.0 2. Click the default button under security level (see figure 31). 9.2.5. Selecting responses to dangerous objects if analyzing an http object shows that it contains malicious code, the web anti- virus response depends on the actions you select. To configure web anti-viru...
Page 107
Web anti-virus 107 web anti-virus always blocks dangerous scripts, and issues popup messages that inform the user of the action taken. You cannot change the response to a dangerous script, other than by disabling the script scanning module..
Page 108
Chapter 10.Proactive defense warning! There is no application integrity control component in this version of the ap- plication for computers running microsoft windows xp professional x64 edition, microsoft windows vista or microsoft windows vista x64. Kaspersky anti-virus protects you both from know...
Page 109
Proactive defense 109 proactive defense tracks and blocks all dangerous operations by using the set of rules together with a list of excluded applications. In operation, proactive defense uses a set of rules included with the program, as well as rules created by the user while using the program. A r...
Page 110
110 kaspersky anti-virus 7.0 base of dangerous activity types comes with kaspersky anti-virus and is updated with the application databases). Integrity of the program modules of the programs installed on your computer, which helps avoid application modules being substituted for malicious code embedd...
Page 111
Proactive defense 111 ules, and of the application itself. You can create rules (see 10.2 on pg. 115) for monitoring the integrity of modules from any application. To do so, add that application to the list of monitored applications. Figure 35. Proactive defense settings this proactive defense compo...
Page 112
112 kaspersky anti-virus 7.0 10.1. Activity monitoring rules note that configuring application control under microsoft windows xp profes- sional x64 edition, microsoft windows vista or microsoft windows vista x64 dif- fers from the configuration process on other operating systems. Information about ...
Page 113
Proactive defense 113 suspicious values in registry. The system registry is a database for stor- ing system and user settings that control the operation of microsoft windows, as well as any utilities established on the computer. Malicious programs, attempting to mask their presence in the system, co...
Page 114
114 kaspersky anti-virus 7.0 figure 36. Configuring application activity control to edit a dangerous activity monitoring rule, select it from the list and assign the rule settings in the lower part of the tab: assign the proactive defense response to the dangerous activity. You can assign any of the...
Page 115
Proactive defense 115 suspicious activities basing on the list of rules, created by kaspersky lab spe- cialists. If you want kaspersky anti-virus to monitor the activity of system processes in addition to user processes, select the watch system user accounts check- box (see figure 37). This option i...
Page 116
116 kaspersky anti-virus 7.0 proactive defense monitors critical applications and analyzes their activity, inte- grity of the modules of those applications, and observes other processes which they spawn. Kaspersky anti-virus comes with a list of critical applications, each of which has its own monit...
Page 117
Proactive defense 117 proactive defense analyzes the following operations involving critical applica- tions: their launch, changing the makeup of application modules, and starting an application as a child process. You can select the proactive defense response to each of the operations listed (allow...
Page 118
118 kaspersky anti-virus 7.0 define the proactive defense response to attempts to execute the critical application, change its makeup, or start it as a child process. You can use any of these actions as a response: allow, prompt for action, or block. Left-click on the action link until it reaches th...
Page 119
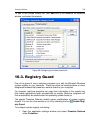
Proactive defense 119 to add to the trusted module list, click add and in the standard file selection window, and select the module. Figure 39. Configuring the trusted module list 10.3. Registry guard one of the goals of many malicious programs is to edit the microsoft windows system registry on you...
Page 120
120 kaspersky anti-virus 7.0 2. Click the settings button in the registry guard section (see figure 35). Kaspersky lab has created a list of rules that control registry file operations, and have included it in the program. Operations with registry files are categorized into logical groups such as sy...
Page 121
Proactive defense 121 take these steps in the window that opens: 1. Enter the name of the new file group for monitoring system registry keys in the group name field. 2. Select the keys tab, and create a list of registry files that will be in- cluded in the monitored group (see 10.3.1 on pg. 121) for...
Page 122
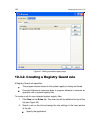
122 kaspersky anti-virus 7.0 figure 41. Adding controlled registry keys 10.3.2. Creating a registry guard rule a registry guard rule specifies: the program whose access to the system registry is being monitored proactive defense‟s response when a program attempts to execute an operation with a syste...
Page 123
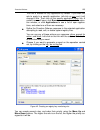
Proactive defense 123 the rule is created for any application by default. If you want the rule to apply to a specific application, left-click on any and it will change to this. Then click on the specify application name link. A context menu will open: click browse to see the standard file selec- tio...
Page 124
124 kaspersky anti-virus 7.0 you can also create an allow rule (i.E. All actions are allowed) for a system regi- stry object from a notification window stating that a program is trying to execute an operation with an object. To do so, click create allow rule in the notification and specify the syste...
Page 125
Chapter 11.Scanning computers for viruses one of the important aspects of protecting your computer is scanning user- defined areas for viruses. Kaspersky anti-virus can scan individual items – files, folders, disks, removable devices – or the entire computer. Scanning for viruses stops malicious cod...
Page 126
126 kaspersky anti-virus 7.0 with the standard tools of the microsoft windows operating system (for example, in the explorer program window or on your desktop). You can view a complete list of virus scan tasks for your computer by clicking on scan in the left-hand pane of the main application window...
Page 127
Scanning computers for viruses 127 figure 43. List of objects to scan object scan lists are already made for default tasks created when you install the program. When you create your own tasks or select an object for a virus scan task, you can create a list of objects. You can add to or edit an objec...
Page 128
128 kaspersky anti-virus 7.0 figure 44. Scanning objects from the microsoft windows context menu 11.3. Creating virus scan tasks to scan objects on your computer for viruses, you can use built-in scan tasks included with the program and create your own tasks. New scan tasks are created using existin...
Page 129
Scanning computers for viruses 129 to rename an existing task: select the task under scan in the application main window and click re- name. Enter the new name for the task in the window that opens and click ok. The task name will also be changed in the scan section. To delete an existing task: sele...
Page 130
130 kaspersky anti-virus 7.0 in addition, you can configure global settings (see 11.4.8 on pg. 139) for running all tasks. The following sections examine the task settings listed above in detail. 11.4.1. Selecting a security level each virus scan task can be assigned a security level (see figure 45)...
Page 131
Scanning computers for viruses 131 2. Click on customize under security level (see figure 45). 3. Edit file protection parameters in the resulting window and click ok. 11.4.2. Specifying the types of objects to scan by specifying the types of objects to scan, you establish which file formats, files ...
Page 132
132 kaspersky anti-virus 7.0 figure 46. Configuring scan settings in the productivity section, you can specify that only new files and those that have been modified since the previous scan or new files should be scanned for viruses. This mode noticeably reduces scan time and increases the program‟s ...
Page 133
Scanning computers for viruses 133 warning! Kaspersky anti-virus does not delete compressed file formats that it does not support (for example, .Ha, .Uue, .Tar) automatically, even if you select the option of automatically curing or deleting if the objects cannot be cured. To delete such compressed ...
Page 134
134 kaspersky anti-virus 7.0 the application databases, the date the object was last scanned, and modifi- cations to scan settings. Figure 47. Advanced scan settings for example, you have an archived file that the program scanned and as- signed the status of not infected. The next time, the program ...
Page 135
Scanning computers for viruses 135 dow (see para. 15.3.2 on pg. 166). If this box is unchecked, dangerous ob- ject data will not be recorded in the report; therefore, these objects will be impossible to process. Concede resources to other applications – pause that virus scan task if the processor is...
Page 136
136 kaspersky anti-virus 7.0 figure 48. Configuring rootkit scans and heuristic methods 11.4.5. Using heuristic methods heuristic methods are utilized by several real-time protection components and virus scan tasks (see 7.2.4 at p. 82 for more detail). The heuristic analyzer tab(see figure 48) may b...
Page 137
Scanning computers for viruses 137 11.4.6. Restoring default scan settings when configuring scan task settings, you can always return to the recommended settings. Kaspersky lab considers them to be optimal and has combined them in the recommended security level. To restore the default virus scan set...
Page 138
138 kaspersky anti-virus 7.0 if the action selected was when it detects a malicious or potential- ly infected object prompt for action when the scan is complete the program does not process the objects until the end of the scan. When the scan is complete, the statistics window will pop up with a lis...
Page 139
Scanning computers for viruses 139 when disinfecting or deleting an object, kaspersky anti-virus creates a backup copy of it, and sends it to backup (see 15.2 on pg. 161) in case the object needs to be restored or an opportunity arises later to treat it. 11.4.8. Setting up global scan settings for a...
Page 140
Chapter 12.Testing kaspersky anti-virus features after installing and configuring kaspersky anti-virus, we recommend that you verify that settings and program operation are correct using a test virus and vari- ations of it. 12.1. The eicar test virus and its variations the test virus was specially d...
Page 141
Testing kaspersky anti-virus features 141 prefix test virus status corresponding action when the application processes the ob- ject corr – corrupted. The application could access the object but could not scan it, since the object is corrupted (for exam- ple, the file structure is breached, or it is ...
Page 142
142 kaspersky anti-virus 7.0 the status and reaction of kaspersky anti-virus to various types of test virus. The third column contains information on objects with the same status that the appli- cation has processed. Values in the anti-virus scan settings determine the action taken on each of the ob...
Page 143
Testing kaspersky anti-virus features 143 when you select different options for dealing with detected objects, you can test file anti-virus's reaction to detecting various object types. You can view details on file anti-virus performance in the report on the compo- nent. 12.3. Testing virus scan tas...
Page 144
144 kaspersky anti-virus 7.0 figure 51. Dangerous object detected this way, by selecting different options for actions, you can test kaspersky anti- virus reactions to detecting various object types. You can view details on virus scan task performance in the report on the compo- nent..
Page 145
Chapter 13.Program updates keeping your anti-virus software up-to- date is an investment in your computer‟s security. Because new viruses, trojans, and malicious software emerge daily, it is important to regularly update the application to keep your information constant- ly protected. Updating the a...
Page 146
146 kaspersky anti-virus 7.0 if you do not have access to kaspersky lab‟s update servers (for example, your computer is not connected to the internet), you can call the kaspersky lab main office at +7 (495) 797-87-00, +7 (495) 645-79-39, +7 (495) 956-00-00 to request contact information for kaspersk...
Page 147
Program updates 147 to start the updater from the shortcut menu: 1. Right click the application icon in the taskbar notification area to open the shortcut menu. 2. Select update. To start the updater from the main program window: 1. Open application main window and select the update component. 2. Cl...
Page 148
148 kaspersky anti-virus 7.0 which user will the update run as (see 6.6 on pg. 60) whether downloaded updates are to be copied to a local directory (see 13.3.3 on pg. 152) what actions are to be performed after updating is complete (see 13.3.3 on pg. 152) the following sections examine these aspects...
Page 149
Program updates 149 figure 52. Selecting an update source to download updates from another ftp or http site: 1. Click add. 2. In the select update source dialog box, select the target ftp or http site or specify the ip address, character name, or url address of this site in the source field. When se...
Page 150
150 kaspersky anti-virus 7.0 kaspersky anti-virus adds new update sources at the top of the list, and auto- matically enables the source, by checking the box beside the source name. If several resources are selected as update sources, the application tries to con- nect to them one after another, sta...
Page 151
Program updates 151 if you want to download and install updates for program modules: open application settings window, select update, and check update ap- plication modules. If there is an application module update on the update source, the applica- tion will download the required updates and apply ...
Page 152
152 kaspersky anti-virus 7.0 13.3.3. Update distribution if your home computers are connected through a home network, you do not need to download and installed updates on each of them separately, since this would consume more network bandwidth. You can use the update distribution feature, which help...
Page 153
Program updates 153 figure 55. Copy updates tool settings note that kaspersky anti-virus 7.0 only retrieves update packages for v. 7.0 ap- plications from the kaspersky lab update servers. If you want other computers on the network to update from the folder that con- tains updates copied from the in...
Page 154
154 kaspersky anti-virus 7.0 why these objects should be scanned? The quarantine area contains objects that have been flagged by the program as suspicious or possibly infected (see 15.1 on pg. 158). Using the latest version of the databases, kaspersky anti-virus may be able to identify the threat an...
Page 155
Chapter 14.Managing keys kaspersky anti-virus needs a key file to operate. You are provided with a key when you buy the program. It gives you the right to use the program from the day you install the key. Without a key, unless a trial version of the application has been activated, kas- persky anti-v...
Page 156
156 kaspersky anti-virus 7.0 figure 56. Key management kaspersky lab regularly has special pricing offers on license extensions for our products. Check for specials on the kaspersky lab website in the prod- ucts sales and special offers area..
Page 157
Chapter 15.Advanced options kaspersky anti-virus has other features that expand its functionality. The program places some objects in special storage areas, in order to ensure maximum protection of data with minimum losses. Backup contains copies of objects that kaspersky anti-virus has changed or d...
Page 158
158 kaspersky anti-virus 7.0 the program also provides detailed reports (see 15.3 on pg. 163) on the opera- tion of all protection components, virus scan tasks, and updates. Monitored ports can regulate which kaspersky anti-virus modules control data transferred on select ports (see 15.4 on pg. 171)...
Page 159
Advanced options 159 a potentially infected object can be detected and placed in quarantine by file anti-virus, mail anti-virus, proactive defense or in the course of a virus scan. You can place an object in quarantine by clicking quarantine in the notification that pops up when a potentially infect...
Page 160
160 kaspersky anti-virus 7.0 bases, and email format files placed in quarantine, you must also select the directory to restore them to. Figure 57. List of quarantined objects tip: we recommend that you only restore objects with the status false posi- tive, ok, and disinfected, since restoring other ...
Page 161
Advanced options 161 set up automatic scans for objects in quarantine after each application database update (for more details, see 13.3.3 on pg. 152). Warning! The program will not be able to scan quarantined objects immediately after updating the databases if you are accessing the quarantine area....
Page 162
162 kaspersky anti-virus 7.0 15.2.1. Actions with backup copies the total number of backup copies of objects placed in the repository is dis- played in the reports and data files section of the main window. In the right- hand part of the screen there is a special backup section that displays: the nu...
Page 163
Advanced options 163 you can restore selected copies using the restore button. The object is restored from backup with the same name that it had prior to disinfection. If there is an object in the original location with that name (this is possible if a copy was made of the object being restored prio...
Page 164
164 kaspersky anti-virus 7.0 the reports tab (see figure 60) lists the latest reports on all components and virus scan and update tasks run during the current session of kaspersky anti- virus. The status is listed beside each component or task, for example, running, paused, or complete. If you want ...
Page 165
Advanced options 165 the settings tab displays settings used by protection components, vi- rus scans, or application database updates. The registry tabs are only in the proactive defense report and contain information about all attempts to modify the operating system registry. You can export the ent...
Page 166
166 kaspersky anti-virus 7.0 process all the objects on the list). After each object is processed, a message will appear on screen. Here you will have to decide what to do with them next. If you check apply to all in the notification window, the action selected will be applied to all objects with th...
Page 167
Advanced options 167 if you want the list to contain both dangerous objects and successfully neutra- lized objects, check show neutralized objects. Figure 62. List of detected dangerous objects dangerous objects detected by kaspersky anti-virus are processed using the disinfect button (for one objec...
Page 168
168 kaspersky anti-virus 7.0 important events are events that must be investigated, since they reflect important situations in the operation of the program. For example, stopped. Informative messages are reference-type messages which generally do not contain important information. For example, ok, n...
Page 169
Advanced options 169 how many objects were scanned for dangerous traits in this session of a component, or after a task is completed. The number of scanned arc- hives, compressed files, and password protected and corrupted objects is displayed. How many dangerous objects were detected, not disinfect...
Page 170
170 kaspersky anti-virus 7.0 figure 65. Component settings set the computer‟s mode of operation for after a virus scan is complete. You can configure the computer to shut down, restart, or go into stand- by or sleep mode. To select an option, left-click on the hyperlink until it displays the option ...
Page 171
Advanced options 171 figure 66. Read and modify system registry events the tab lists the full name of the key, its value, the data type, and information about the operation that has taken place: what action was attempted, at what time, and whether it was allowed. 15.4. Rescue disk kaspersky anti-vir...
Page 172
172 kaspersky anti-virus 7.0 you can only create a rescue disk under microsoft windows xp or microsoft windows vista. The rescue disk feature is not available under other supported operating systems, including microsoft windows xp professional x64 edition and microsoft windows vista x64. 15.4.1. Cre...
Page 173
Advanced options 173 step 2. Creating an .Iso file after pe builder has completed creating the rescue disk files, a create .Iso file window will open. The .Iso file is a cd image of the disk, saved as an archive. The majority of cd burning programs correctly recognize .Iso files (nero, for example)....
Page 174
174 kaspersky anti-virus 7.0 3. Bart pe has built-in network support for using your lan. When the pro- gram starts, it will ask you if you want to enable it. You should enable network support if you plan to update application databases from the lan before scanning your computer. If you do not need t...
Page 175
Advanced options 175 to edit the monitored port list, take the following steps: 1. Open the application settings window and select traffic monitoring. 2. Click port settings. 3. Update the list of monitored ports in the port settings dialog (see figure 67). Figure 67. List of monitored ports this wi...
Page 176
176 kaspersky anti-virus 7.0 when any of its components starts, kaspersky anti-virus opens port 1110 as a listening port for all incoming connections. If that port is busy at the time, it se- lects 1111, 1112, etc. As a listening port. If you use kaspersky anti-virus and anot her company‟s firewall ...
Page 177
Advanced options 177 figure 68. Notification on ssl connection detection to scan encrypted connections, kaspersky anti-virus replaces the security certif- icate requested with a self-signed one. In some cases, programs that are estab- lishing connections will not accept this certificate, resulting i...
Page 178
178 kaspersky anti-virus 7.0 do not check encrypted connections – do not scan traffic incoming on ssl protocol for viruses. Figure 69. Configuring secure connection scans 15.7. Configuring proxy-server connection to a proxy server may be configured using the proxy server section (see figure 70) of t...
Page 179
Advanced options 179 figure 70. Configuring proxy-server specify whether the proxy server uses authentication. Authentication is a procedure to verify user account information for the purposes of access control. If authentication is required to connect to the proxy server, check use authentication a...
Page 180
180 kaspersky anti-virus 7.0 by default, the update server connection timeout is 1 minute. If connection fails, an attempt will be made to connect to the next update server once this timeout expires. This enumeration continues until a connection is successfully estab- lished or until all available u...
Page 181
Advanced options 181 in the right-hand part of the settings window, you can configure: user defined graphical components and color scheme in the application interface. By the default the graphical user interface uses system colors and styles. These can be replaced by unchecking use system colors and...
Page 182
182 kaspersky anti-virus 7.0 protected from all threat types. If you do not want to use the protection indicator, uncheck show icon above microsoft windows login window. Note that modifications of kaspersky anti-virus interface settings are not saved when default settings are restored or if the appl...
Page 183
Advanced options 183 figure 72. Configuring advanced options 15.9.1. Kaspersky anti-virus event notifications different kinds of events occur in kaspersky anti-virus. They can be of an infor- mative nature or contain important information. For example, an event can inform you that the program has up...
Page 184
184 kaspersky anti-virus 7.0 2. Define the event types from kaspersky anti-virus for which you want notifications, and the notification delivery method (see 15.9.1.1 on pg. 184). 3. Configure email notification delivery settings, if that is the notification method that is being used (see 15.9.1.2 on...
Page 185
Advanced options 185 email notification to use this type of notice, check the e-mail columnacross from the event about which you want to be informed, and configure settings for sending notices (see 15.9.1.2 on pg. 185). Logging events to record information in the log about events that occur, check i...
Page 186
186 kaspersky anti-virus 7.0 3. Use the events notification settings window (see figure 73) to check events that should trigger email notification in the e-mail column. 4. In the window (see figure 74) that opens when you click email set- tings, configure the following settings for sending e-mail no...
Page 187
Advanced options 187 2. Click advanced under events notification. Use the events notification settings window to select the option of logging information for an event and click the log settings button. Kaspersky anti-virus has the option of recording information about events that arise while the pro...
Page 188
188 kaspersky anti-virus 7.0 trusted applications list, and the setting do not monitor application activity should be enabled (see 6.9.2 on pg. 70). If any of the actions listed are attempted, a message will appear over the application icon in the taskbar notification area (unless the notification s...
Page 189
Advanced options 189 15.9.3. Importing and exporting kaspersky anti-virus settings kaspersky anti-virus allows you to import and export application settings. This feature is useful when, for example, the program is installed both on your home computer and in your office. You can configure the progra...
Page 190
190 kaspersky anti-virus 7.0 examples of special settings would be trusted address lists used by web anti- virus; exclusion rules created for program components, and application rules for proactive defense. These lists are populated gradually by using the program, based on individual tasks and secur...
Page 191
Advanced options 191 user registration is performed using the activation wizard (see 3.2.2 on pg. 32), if the application is being activated using an activation code. A client id will be assigned at the end of the registration process which may be viewed under sup- port (see figure 76) of the main w...
Page 192
192 kaspersky anti-virus 7.0 figure 76. Technical support information for urgent assistance, use the contact numbers provided in the help system (see b.2 on pg. 228). Telephone support is provided 24/7 in russian, english, french, german, and spanish. Use the online course link to obtain further inf...
Page 193
Advanced options 193 please note that any downloads underway at the time the connections are bro- ken will be interrupted unless a download manager is being used. The download will have to be restarted for you to get the file. You can prevent the connections from being broken by clicking no in the n...
Page 194
Chapter 16.Working with the program from the command line you can use kaspersky anti-virus from the command line. You can execute the following operations: starting, stopping, pausing and resuming the activity of application components starting, stopping, pausing and resuming virus scans obtaining i...
Page 195
Working with the program from the command line 195 resume resumes a component or a task stop stops a component or a task (command can only be ex- ecuted if the password assigned through the program interface is entered) status displays the current component or task status on screen statistics displa...
Page 196
196 kaspersky anti-virus 7.0 addkey /password= parameter description: program activation code provided when you pur- chased it. Name of the key file with the extension .Key. Password for accessing kaspersky anti-virus as- signed in the application interface. Note that you cannot execute the addkey c...
Page 197
Working with the program from the command line 197 or task. Status - display the current status of the real-time protection component or task. Statistics – outputs statistics to the screen on real- time protection component or task operation. Note that you cannot execute the commands pause and stop ...
Page 198
198 kaspersky anti-virus 7.0 avp.Com start , with the value for the specific protection component entered for file>. For example, avp.Com start fm. Fm file anti-virus em mail anti-virus wm web anti-virus values for web anti-virus subcomponents: httpscan – scans http traffic sc – scans scripts bm pro...
Page 199
Working with the program from the command line 199 to view the current status of proactive defense on your computer, type the fol- lowing text at the command prompt: avp.Com status bm to stop a my computer scan task from the command prompt, enter: avp.Com stop scan_my_computer /password= 16.3. Anti-...
Page 200
200 kaspersky anti-virus 7.0 /remdrives all removable media drives /fixdrives all internal drives /netdrives all network drives /quarantine quarantined objects /all complete scan /@: path to a file containing a list of objects and folders to be included in the scan. The file should be in a text form...
Page 201
Working with the program from the command line 201 - this parameter defines the file types that will be subject to the anti- virus scan. If this parameter is not defined, the default value is /fi. /fe scan only potentially infected files by extension /fi scan only potentially infected files by conte...
Page 202
202 kaspersky anti-virus 7.0 - this parameter determines the format of the report on scan results. You can use an absolute or relative path to the file. If the parameter is not de- fined, the scan results are displayed on screen, and all events are displayed. /r: only log important events in this fi...
Page 203
Working with the program from the command line 203 16.4. Program updates the syntax for updating kaspersky anti-virus databases and modules from the command prompt is as follows: avp.Com update [] [/r[a]:] [/c:] [/app=] parameter description: [] http or ftp server or network folder for download- ing...
Page 204
204 kaspersky anti-virus 7.0 update the kaspersky anti-virus program modules by using the settings in the configuration file updateapp.Ini: avp.Com update /app=on/c:updateapp.Ini sample configuration file: "ftp://my_server/kav updates" /ra:avbases_upd.Txt /app=on 16.5. Rollback settings command synt...
Page 205
Working with the program from the command line 205 path to the file to which the kaspersky anti-virus settings are exported. You can use an absolute or relative path. The configuration file is saved in binary format (.Dat), and it can be used later to import application settings on other computers. ...
Page 206
206 kaspersky anti-virus 7.0 16.9. Stopping the program command syntax: exit /password= kaspersky anti-virus password assigned in the pro- gram interface. Note that you cannot execute this command without entering the password. 16.10. Creating a trace file you might need to create a trace file if yo...
Page 208
Chapter 17.Modifying, repairing, and removing the program you can uninstall the application in the following ways: using the application's setup wizard (see 17.2 on pg. 210) from the command prompt (see 17.2 on pg. 210) 17.1. Modifying, repairing, and removing the program using install wizard you ma...
Page 209
Modifying, repairing, and removing the program 209 remove the entire program. To execute the operation you need, click the appro- priate button. The program‟s response depends on the operation you select. Modifying the program is like custom program installation where you can specify which component...
Page 210
210 kaspersky anti-virus 7.0 step 2. Completing program modification, repair, or remov- al the modification, repair, or removal process will be displayed on screen, after which you will be informed of its completion. Removing the program generally requires you to restart your computer, since this is...
Page 211
Chapter 18.Frequently asked questions this chapter is devoted to the most frequently asked questions from users per- taining to installation, setup and operation of the kaspersky anti-virus; here we shall try to answer them here in detail. Question: is it possible to use kaspersky anti-virus 7.0 wit...
Page 212
212 kaspersky anti-virus 7.0 3. Open kaspersky anti-virus. 4. Open the application settings window and select service. 5. Uncheck launch application at startup and click ok. 6. Reboot the operating system in regular mode. Send a request to kaspersky lab technical support. Open the application main w...
Page 213
Appendix a.Reference information this appendix contains reference materials on the file formats and extension masks used in kaspersky anti-virus settings. A.1. List of files scanned by extension if the scan programs and documents (by extension) is selected as the file antivirus scan option or virus ...
Page 214
214 kaspersky anti-virus 7.0 cla – java class vbs – visual basic script vbe – bios video extension js, jse – javascript source text htm – hypertext document htt – microsoft windows hypertext header hta – hypertext program for microsoft internet explorer asp – active server pages script chm – compile...
Page 215
Appendix a 215 emf – enhanced metafile format next generation of microsoft windows os metafiles. Emf files are not supported by 16-bit microsoft windows ico – icon file ov? – microsoft doc executable files xl* - microsoft office excel documents and files, such as: xla – microsoft of- fice excel add-...
Page 216
216 kaspersky anti-virus 7.0 c:\dir\*.* or c:\dir\* or c:\dir\ – all files in folder c:\dir\ c:\dir\*.Exe – all files with extension .Exe in folder c:\dir\ c:\dir\*.Ex? – all files with extension .Ex? In folder c:\dir\, where ? Can represent any one character c:\dir\test – only the file c:\dir\test ...
Page 217
Appendix a 217 threat name by mask. For example: not-a-virus* – excludes potential dangerous programs from the scan, as well as joke programs. *riskware.* – excludes riskware from the scan. *remoteadmin.* – excludes all remote administration programs from the scan..
Page 218
Appendix b.Kaspersky lab founded in 1997, kaspersky lab has become a recognized leader in information security technologies. It produces a wide range of data security software and delivers high-performance, comprehensive solutions to protect computers and networks against all types of malicious prog...
Page 219
Appendix b 219 b.1. Other kaspersky lab products kaspersky lab news agent the news agent is intended for timely delivery of news published by kaspersky lab, notifications about the current status of virus activity, and fresh news. The program reads the list of available news feeds and their content ...
Page 220
220 kaspersky anti-virus 7.0 select standard/extended databases for scanning save a report on the scanning results in .Txt or .Html formats kaspersky ® internet security 7.0 kaspersky ® internet security 7.0 is an integrated solution for protection of per- sonal computers against the major informati...
Page 221
Appendix b 221 the program employs an all-inclusive approach to anti-spam filtering of incoming e-mail messages: verification against black and white lists of recipients (including ad- dresses of phishing sites) inspection of phrases in message body analysis of message text using a learning algorith...
Page 222
222 kaspersky anti-virus 7.0 use of optimization technologies when scanning objects in the server file system; system rollback after virus attacks; scalability of the software package within the scope of system re- sources available; monitoring of the system load balance; creating a list of trusted ...
Page 223
Appendix b 223 proactive defense from new malicious programs whose signatures are not yet added to the database; personal firewall with intrusion detection system and network at- tack warnings; rollback for malicious system modifications; protection from phishing attacks and junk mail; dynamic resou...
Page 224
224 kaspersky anti-virus 7.0 iswift technology to avoid rescanning files within the network; distribution of load among server processors; quarantining suspicious objects from workstations; rollback for malicious system modifications; scalability of the software package within the scope of system re...
Page 225
Appendix b 225 remote administration of the software package, including centra- lized installation, configuration, and administration; support for cisco ® nac (network admission control); proactive defense for workstations from new malicious programs whose signatures are not yet added to the databas...
Page 226
226 kaspersky anti-virus 7.0 centralized reporting on protection status; remote administration of the software package, including centra- lized installation, configuration, and administration; support for cisco® nac (network admission control); support for hardware proxy servers; filters internet tr...
Page 227
Appendix b 227 junk mail filtering; scans incoming and outgoing e-mails and attachments; scans all e-mails on microsoft exchange server for viruses, including shared folders; processes e-mails, databases, and other objects for lotus notes/domino servers; filters e-mails by attachment type; quarantin...
Page 228
228 kaspersky anti-virus 7.0 support for hardware proxy servers; scalability of the software package within the scope of system re- sources available ; automatic database updates. Kaspersky ® anti-spam kaspersky ® anti-spam is a cutting-edge software suite designed to help organi- zations with small...
Page 229
Appendix b 229 general information www: http://www.Kaspersky.Com http://www.Viruslist.Com e-mail: info@kaspersky.Com.
Page 230
Appendix c.License agreement standard end user license agreement notice to all users: carefully read the following legal agreement (“agreement”), for the license of kaspersky anti- virus (“software”) produced by kaspersky lab (“kaspersky lab”). If you have purchased this software via the internet by...
Page 231
Appendix c 231 all references to “software” herein shall be deemed to include the software acti- vation code with which you will be provided by kaspersky lab as part of the kaspersky anti-virus 7.0. 1. License grant. Subject to the payment of the applicable license fees, and sub- ject to the terms a...
Page 232
232 kaspersky anti-virus 7.0 1.1.7 you shall not provide the activation code or license key file to third parties or allow third parties access to the activation code or license key. The activation code and license key are confidential data. 1.1.8 kaspersky lab may ask user to install the latest ver...
Page 233
Appendix c 233 (c) technical support via internet and hot phone-line provided by ven- dor and/or reseller; (d) virus detection and disinfection updates in 24-hours period (v) support services are provided only if and when you have the latest ver- sion of the software (including maintenance packs) as...
Page 234
234 kaspersky anti-virus 7.0 be reasonably necessary to assist the supplier in resolving the defective item. (v) the warranty in (i) shall not apply if you (a) make or cause to be made any modifications to this software without the consent of kaspersky lab, (b) use the software in a manner for which...
Page 235
Appendix c 235 (iii) subject to paragraph (i), the liability of kaspersky lab (whether in con- tract, tort, restitution or otherwise) arising out of or in connection with the supply of the software shall in no circumstances exceed a sum equal to the amount equally paid by you for the software. 7. Th...