KAPERSKY ANTI-VIRUS - FOR FREEBSD-OPENBSD-BSDI FILE SERVER User Manual
Summary of ANTI-VIRUS - FOR FREEBSD-OPENBSD-BSDI FILE SERVER
Page 1
Kaspersky lab kaspersky anti-virus for freebsd, openbsd and bsdi file server user guide.
Page 2
1 11 1 k a s p e r s k y a n t i - v i r u s f o r f r e e b s d , o p e n b s d a n d b s d i f i l e s e r v e r user guide user guide user guide user guide kaspersky lab ltd. Http://www.Kaspersky.Com revision date: june 2002.
Page 3
2 22 2 contents 1. Kaspersky tm anti-virus for freebsd, openbsd and bsdi file server ............................................................................. 8 1.1. Introduction ................................................................................. 8 1.2. Distribution kit...............
Page 4
C o n t e n t s 3 33 3 4.1. Starting scanner....................................................................... 25 4.2. Searching for viruses and deleting them................................. 27 4.2.1. Loading anti-virus scanner ................................................. 27 4.2.2. Handli...
Page 5
C o n t e n t s 4 44 4 6.2. Launching the daemon process .............................................. 60 6.3. Calling up the process from a client program ......................... 63 7. Anti-virus monitor: monitoring the system for viruses ............................................................
Page 6
C o n t e n t s 5 55 5 9.6. The options page..................................................................... 93 9.7. The report page....................................................................... 95 9.8. The actionwith page...................................................................
Page 7
C o n t e n t s 6 66 6 10.8.1. Scanner settings ............................................................... 135 10.8.2. Remote configuration of the scanner program ............... 137 10.8.3. Launching scanner from a remote location.................. 137 10.8.4. Reviewing the log file..............
Page 8
C o n t e n t s 7 77 7 15.1. Files with the program settings .............................................. 163 15.2. Scanner and daemon: the initialization file(avpunix.Ini) ... 163 15.3. Scanner and daemon: the profile(defunix.Prf) .................... 165 15.4. Scanner and daemon: command line sw...
Page 9
8 88 8 attention!!! New viruses arise every day and if you want to keep your anti-virus fresh and capable, we strongly recommend you to update anti-virus databases at least every day (for more details see below). Moreover, make sure to update them right after you install the product on your computer...
Page 10
I n t r o d u c t i o n 9 99 9 allows detection and deletion of all currently known types of viruses and mailware codes including: • polymorphic or self-encoding viruses; • stealth or invisible viruses; • viruses for windows 9x, windows nt, unix, os/2; • new viruses for java applets; • macroviruses ...
Page 11
I n t r o d u c t i o n 10 10 10 10 the package also contains the special configuration program kavtuner (tuner), which allows you to define the virus-scanning settings of the scanner and daemon programs. By using the kavinspector program (inspector) you can check the filesystem. This will allow you...
Page 12
I n t r o d u c t i o n 11 11 11 11 1.2.2. License agreement the license agreement (la) is a legal agreement between you (either an individual or a single entity) and the manufacturer (kaspersky lab ltd.) describing the terms on which you may employ the anti-virus product, which you have purchased. ...
Page 13
I n t r o d u c t i o n 12 12 12 12 if you register and purchase a subscription you will be provided with the following services for the period of your subscription: • daily virus-definition database updates via e-mail; • product upgrades; • phone and e-mail advice on matters related to your softwar...
Page 14
I n t r o d u c t i o n 13 13 13 13 convention meaning bold font menu titles, commands, window titles, dialog elements, etc. !"note. Additional information, notes #" attention! Very important information $" to do this: … 1. Step 1. 2. … actions that must be taken • function of the control—function o...
Page 15
14 14 14 14 2. 2. 2. 2. Installing kaspersky anti installing kaspersky anti installing kaspersky anti installing kaspersky anti---- virus for xbsd file se virus for xbsd file se virus for xbsd file se virus for xbsd file server rver rver rver 2.1. Software and hardware requirements what hardware and...
Page 16
I n s t a l l a t i o n 15 15 15 15 2.2. Backing up your installation diskettes if you purchased the kaspersky anti-virus for xbsd file server package on installation diskettes (but not the cd) before installing the program on your computer, it is recommended that you back up those diskettes. Then, ...
Page 17
I n s t a l l a t i o n 16 16 16 16 the following: pkg_add kav-workstationsuit-4.0.0.0-freebsd-4.X.Tgz 4. Copy the .Key file from the installation cd (installation diskette) to the directory defined in the keyspath line of the file avpunix.Ini. The default .Key file directory is /etc. 5. Run the upd...
Page 18
I n s t a l l a t i o n 17 17 17 17 #" if any component of the kaspersky anti-virus for freebsd software package failed to start, apply the launching procedure described in the corresponding chapter of this book . 2.3.2. … of kaspersky anti-virus for openbsd and bsdi $" to install the kaspersky anti...
Page 19
I n s t a l l a t i o n 18 18 18 18 2.4. Preparing to run how to edit the .Ini file and a path to the directory for temporary files. Customizing the software for various needs. 2.4.1. Editing the .Ini file the initialization file avpunix.Ini contains information that is essential for your program’s ...
Page 20
I n s t a l l a t i o n 19 19 19 19 #" when editing the setfile parameter, be sure to specify only the name of your .Set file. You do not need to define the full path to it! • if you copied the key files to a separate directory, you must specify a new path to these files in the keyspath line of your...
Page 21
I n s t a l l a t i o n 20 20 20 20 3. If necessary, edit the profile (see appendix b). If you specify the –ua=name switch(where name is the user name) in the tuner or the installer command line, the programs will automatically perform the steps described above..
Page 22
21 21 21 21 3. 3. 3. 3. Running kaspersky anti running kaspersky anti running kaspersky anti running kaspersky anti----virus virus virus virus for xbsd file server for xbsd file server for xbsd file server for xbsd file server 3.1. Changing scanning settings how to change scanning settings. Using co...
Page 23
R u n n i n g 22 22 22 22 • first—by means of the configuration program called tuner (see chapter 9) or the remote configuration program called webtuner (see chapter 10). • second—by opening and editing a profile in any text editor (see subchapter 5.2). For various situations, you may define differe...
Page 24
R u n n i n g 23 23 23 23 is defunix.Prf, a sample of which is supplied with kaspersky anti-virus for xbsd file server. If your package doesn’t contain the file, the scanner will use its own default settings. You may also redefine settings by using the switch f=profile_name in the command line. To c...
Page 25
R u n n i n g 24 24 24 24 you may also refer to the site at www.Kaspersky.Com for a complete list of kaspersky lab dealers that can provide you with updates. To efficiently protect your computer from new viruses it's advisable to update your virus-definition databases on a regular basis. Updater tha...
Page 26
25 25 25 25 4. 4. 4. 4. Anti anti anti anti----virus scanner: scanning virus scanner: scanning virus scanner: scanning virus scanner: scanning and disinfecting and disinfecting and disinfecting and disinfecting 4.1. Starting scanner starting the scanner from the command line or from a script file. U...
Page 27
S c a n n e r 26 26 26 26 [ switchn] is the optional switch in the scanner command line, [path] is the optional xbsd path that defines the location to be checked [filemasks] are the optional xbsd file masks that define the files to be checked for viruses. By default, the program checks for viruses i...
Page 28
S c a n n e r 27 27 27 27 4.2. Searching for viruses and deleting them actions to be taken regarding infected objects. Recommendations. Messages generated by the anti-virus scanner when it detected objects that are suspicious or infected with a virus, and messages about a virus in your anti-virus pr...
Page 29
S c a n n e r 28 28 28 28 !"if you started the program with no predefined objects to be checked, the following message will appear on your screen: "nothing to scan. You should select files and/or sectors in the *.Prf file." if you see this message, specify the objects to be checked by your scanner. ...
Page 30
S c a n n e r 29 29 29 29 • disinfect—try to disinfect the object; the virus will be deleted and the object will be restored to its virus-free state, close to the original; • delete—delete the object; • cancel—ignore the object and continue with checking; • stop—abort the check. The inquiry string w...
Page 31
S c a n n e r 30 30 30 30 #" the sector check function under your operating system may be not available. If you confirm the action, scanner will right away start disinfecting the sectors and will replace them with a standard ms-dos 6.0 boot sector. If you cancel the action, the scanning will be abor...
Page 32
S c a n n e r 31 31 31 31 if you choose to confirm the action, the program will automatically delete all infected objects that it is not able to disinfect. If you cancel the action, next time when the program finds an infected object it is not able to disinfect, it will again ask whether you want to...
Page 33
S c a n n e r 32 32 32 32 4.3. Reviewing performance statistics how to review virus check reports. Messages about checked objects. Performance statistics. While checking for viruses the program displays current results. On the left side of your screen you may see names of the objects that were check...
Page 34
S c a n n e r 33 33 33 33 !"messages about infected objects and general statistics will be logged, if you preset the program to do so. !"to process and summarize data within the performance reports and to review details of scanning operations use the slogan program (for details refer to chapter 8)..
Page 35
34 34 34 34 5. 5. 5. 5. Anti anti anti anti----virus scanner and virus scanner and virus scanner and virus scanner and daemon proces daemon proces daemon proces daemon process: using s: using s: using s: using switches and profiles switches and profiles switches and profiles switches and profiles 5....
Page 36
D e f i n i n g s e t t i n g s 35 35 35 35 • actions to be taken on infected objects: they may be disinfected or deleted, or copied to another directories. • advanced scanning tools: checking for corrupted and modified viruses, redundant scanning tool, i.E. A full-scan device that checks not just t...
Page 37
D e f i n i n g s e t t i n g s 36 36 36 36 create a set of regular profiles with various settings. This way, when you need your scanner to be set according to some certain profile, define this profile in the program command line. • irregular check. There may be some irregular situations, when you n...
Page 38
D e f i n i n g s e t t i n g s 37 37 37 37 $" to define the location to be checked, in the names line of the [object] section, enter the filesystem directories to be checked for viruses. If you define more then one directory, they must be separated by semicolons. There is one more important thing: ...
Page 39
D e f i n i n g s e t t i n g s 38 38 38 38 5.3.2. Defining objects to be checked 5.3.2.1. Object types now, when you defined the location to be checked (see subchapter 5.3.1) after you defined the location to be scanned, you must define objects that will be checked for viruses. The program can chec...
Page 40
D e f i n i n g s e t t i n g s 39 39 39 39 check mbr. The switch -b disables and the switch -b- enables the scanner to check boot sectors of disks defined in the names line. 5.3.2.3. Files $" to scan files within the selected location: 1. Type yes in the files line of the profile. 2. To be more spe...
Page 41
D e f i n i n g s e t t i n g s 40 40 40 40 character ! Is specified in the switch (i.E. -@!=filename), upon completion of the task the filename file will be deleted. If this character is not in the switch (i.E. -@=filename), this file will be kept. $" to exclude some files from the check: 1. Enter ...
Page 42
D e f i n i n g s e t t i n g s 41 41 41 41 5.3.2.4. Packed executables scanner can check for viruses in packed executable files that are unpacked by the special engine. Packed executable files contain special unpacking modules. When such a file is started, the module unpacks the program to ram and ...
Page 43
D e f i n i n g s e t t i n g s 42 42 42 42 if the unpacking and extracting (see subchapter 5.3.2.5) engines are enabled, kaspersky anti-virus for xbsd file server is able to detect an infected file even though it was enciphered by the cryptcom utility, then packed by pklite and, finally, added to t...
Page 44
D e f i n i n g s e t t i n g s 43 43 43 43 5.3.2.6. Mail databases and plain mail files you can enable your scanner to check for viruses in mail databases and plain mail files. The mail databases and especially plain mail files scanning modes noticeably slow down the scanner scanning rate. Therefor...
Page 45
D e f i n i n g s e t t i n g s 44 44 44 44 $" to check for viruses in plain mail files, type yes in the mailplain line of the profile. Otherwise, type no. !"this parameter corresponds to the command line switch -mp[-]. The switch -mp enables and the switch -mp- disables your anti-virus scanner to c...
Page 46
D e f i n i n g s e t t i n g s 45 45 45 45 • 0 — reports infected, suspicious and corrupted objects. Messages will be displayed and, if preset, logged into the file (see subchapter 5.4.4). The program will not disinfect or delete infected objects. !" 0 in the infectedaction line of the profile corr...
Page 47
D e f i n i n g s e t t i n g s 46 46 46 46 (see subchapter 5.4.4). The program will not delete these objects. !" 0 in the ifdisinfimpossible line corresponds to the command line switch –i2s. • 1 — deletes unrecoverable objects. !" 1 in the ifdisinfimpossible line corresponds to the command line swi...
Page 48
D e f i n i n g s e t t i n g s 47 47 47 47 file server algorithmic legs searching for virus-similar instructions. • redundant scanning tool checks not just the entry points into a file that are used by the system when processing, but the entire contents of the examined files. In most cases a virus ...
Page 49
D e f i n i n g s e t t i n g s 48 48 48 48 • com—the file seems to be infected by a virus that infects .Com files; • exe—the file seems to be infected by a virus that infects .Exe files; • comexe—the file seems to be infected by a virus that infects both .Com and .Exe files; • comtsr, exetsr, systs...
Page 50
D e f i n i n g s e t t i n g s 49 49 49 49 $" to enable the redundant scanning tool, type yes in the redundantscan line of the profile. !"this parameter corresponds to the command line switch -v[-]. The switch -v enables and the switch -v- disables the redundant scanning tool. !"the redundant scann...
Page 51
D e f i n i n g s e t t i n g s 50 50 50 50 • generation of the check report and the performance statistics (see subchapter 5.4.4). 5.4.2. Defining scanning and performance settings: scanner and daemon general parameters for the program performance are located in the [customize] section of a profile...
Page 52
D e f i n i n g s e t t i n g s 51 51 51 51 $" to enable error reporting at the program start, type yes in the othermessages line of the [customize] section of a profile. Otherwise, type no. $" to be asked for confirmation when enabling the redundant scanning tool, type yes in the redundantmessage l...
Page 53
D e f i n i n g s e t t i n g s 52 52 52 52 type no in the scanremovable line of the [options] section of a profile. Otherwise, type yes. $" to scan subdirectories in the last place (after all the other objects have been scanned), type yes in the scansubdiratend line of the [options] section of a pr...
Page 54
D e f i n i n g s e t t i n g s 53 53 53 53 2. Define the maximum number of simultaneously scanned files in the limitforprocesses line. $" to implement the loop-scanning for viruses: 1. Type yes in the endlesslyscan line. Otherwise, type no. 2. Define the interval between two loops (in seconds) in t...
Page 55
D e f i n i n g s e t t i n g s 54 54 54 54 5.4.3. Defining actions on infected and suspicious objects the following three sections allow you to define actions to be taken by the program when it detects infected, suspicious or corrupted objects: • [actionwithinfected] section parameters define how t...
Page 56
D e f i n i n g s e t t i n g s 55 55 55 55 $" to copy infected, suspicious and corrupted objects together with their paths, type yes in the copywithpaths lines of the above sections. Otherwise, type no. #" it’s recommended to enable the above option since you may have files with similar names on yo...
Page 57
D e f i n i n g s e t t i n g s 56 56 56 56 5.4.4. Defining the reporting parameters to review results of the check performed by the program you must define its reporting parameters located in the [report] section of a profile. This section also allows you to enable/disable additional information in...
Page 58
D e f i n i n g s e t t i n g s 57 57 57 57 some text editors it will be difficult to review these files, since the program shows everything written on a single line. If you feel this way with your text editor, type yes for the above parameterand the program will use both separators (carriage return...
Page 59
D e f i n i n g s e t t i n g s 58 58 58 58 $" use the below parameters to define optional information that will be added to the report: • writetime – reports the date and the time when the program messages were displayed. Type yes to enable these messages in the report , or no to disable them. • wr...
Page 60
59 59 59 59 6. 6. 6. 6. Daemon process: integrating daemon process: integrating daemon process: integrating daemon process: integrating anti anti anti anti----virus protection in clients virus protection in clients virus protection in clients virus protection in clients 6.1. Features of the daemon p...
Page 61
D a e m o n 60 60 60 60 daemon has all the features of anti-virus programs designed for other platforms, and allows checking for viruses in all file types (including archives, packed and plain mail files), application of the heuristic detection and redundant checking tools. The process can perform f...
Page 62
D a e m o n 61 61 61 61 [path] is the optional xbsd path that defines the location to be checked. !"the meaning of path in the daemon command line differs from that of the scanner program. For the scanner this setting defines the location to be checked for viruses, but for daemon it assigns the path...
Page 63
D a e m o n 62 62 62 62 in this version when you launch the daemon process, it automatically initiates the following two processes: the primary process handles calls from the client programs, the secondary process reports performance of the first. It is possible to disable the second process . -dl —...
Page 64
D a e m o n 63 63 63 63 6.3. Calling up the process from a client program how to call up the process from a client program. The example. $" to call up the existing daemon process from the client program, follow these steps: 1. Create a socket. 2. Link the socket to the daemon program. 3. Type the co...
Page 65
D a e m o n 64 64 64 64 • 3—the command param substring transfers parameters of the shared memory, where the examined object was preplaced. The mode is used if the objects are checked without being intermediately saved onto the disk. In this case the general format of the string is: date_and_time: w...
Page 66
65 65 65 65 7. 7. 7. 7. Anti anti anti anti----virus monitor: monitoring virus monitor: monitoring virus monitor: monitoring virus monitor: monitoring the system for viruses the system for viruses the system for viruses the system for viruses 7.1. Features and functions function and features of the ...
Page 67
M o n i t o r 66 66 66 66 !"monitor is a client program of the daemon process. Therefore, in order to run monitor you must also install and customize daemon. 7.2. Assembling and configuring assembling the freebsd kernel anti-virus module and the anti-virus monitor. Editing the monitor configuration ...
Page 68
M o n i t o r 67 67 67 67 monitor. The monitor processes the file and transfers its name to the daemon process, which checks for viruses in the file. If the file is not infected, the daemon returns the appropriate code to the monitor, which informs the anti-virus module that a permission to work wit...
Page 69
M o n i t o r 68 68 68 68 required start level. For example: insmod monitor-2.2.18.о 4. Go to the directory with the monitor source codes using the command cd. For example, cd /usr/local/share/avp/monitor 5. Assemble monitor using the command make. 7.2.2. Configuring monitor you may configure the mo...
Page 70
M o n i t o r 69 69 69 69 check only slows down the system performance. Therefore, it is advisable to exclude these files from the monitoring. $" to exclude some files from the objects to be checked when they are opened, saved or executed, in the options section of the configuration file define valu...
Page 71
M o n i t o r 70 70 70 70 $" to define the quantity of files to be scanned for viruses only once, when they are opened the first time, enter the required number in the cachesize line of the options section. For example: cachesize 2500 !"this value depends on the computer capacity and its functions w...
Page 72
M o n i t o r 71 71 71 71 daemon settings. For example, if a directory is not included in the location to be checked by the daemon program, it will be ignored although it may be not excluded from the location to be checked by monitor. 7.3. Launching monitor how to launch the program. $" to launch mo...
Page 73
M o n i t o r 72 72 72 72 7.4. Reviewing the performance results how to review the performance results. While checking for viruses in the files to be opened, saved or executed the monitor program (if preset) logs its performance results into the log file. The log file name and the reporting mode are...
Page 74
M o n i t o r 73 73 73 73 $" if when launching the monitor you see the following message on your screen: error: could not open kavmonitor peer file: permission denied, this means that you are not authorized to launch monitor. Only the root user has the rights to launch the monitor program. $" if all...
Page 75
M o n i t o r 74 74 74 74 2. Enter the command lsmod in the command line to check whether the kernel anti-virus module is loaded. 3. Try to launch the monitor program with a path to the configuration file in the command line..
Page 76
75 75 75 75 8. 8. 8. 8. Slogan: processing and slogan: processing and slogan: processing and slogan: processing and summarizing summarizing summarizing summarizing the perform the perform the perform the performance ance ance ance reports reports reports reports 8.1. Features and functions function ...
Page 77
S l o g a n 76 76 76 76 8.2. Launching slogan starting the program from the command line. To launch slogan, the log processing and summarizing program, enter its name and the required switches in the command line: ./slogan [switch1] [switch2] […] [switchn] where [switchn] is the slogan optional comm...
Page 78
S l o g a n 77 77 77 77 figure 2. The example of a summary report produced by slogan -ds dd.Mm.Yyyy the program will summarize the reports generated starting from the date defined by this switch. -de dd.Mm.Yyyy the program will summarize the reports generated before and on the date defined by this s...
Page 79
S l o g a n 78 78 78 78 8.3. Slogan in the real-time monitoring mode performance of the program in the monitoring mode. The real time monitoring mode allows you to track changes in the predefined log file and study them. The general format of the command line for slogan in the monitoring mode is: ./...
Page 80
S l o g a n 79 79 79 79 -r this switch redisplays the log file, if it became unavailable at some point of time . The screen (see figure 3) displayed by slogan in the real-time monitoring mode is divided into the following two panes : • general statistics displays the following total amounts: • reque...
Page 81
80 80 80 80 9. 9. 9. 9. Tuner: customizing scanner tuner: customizing scanner tuner: customizing scanner tuner: customizing scanner and daemon and daemon and daemon and daemon 9.1. Features and functions function and features of the program. Tuner, the customization program, allows you to create and...
Page 82
T u n e r 81 81 81 81 9.2. Launching tuner starting the program from the command line. Available command line switches. The general format of the tuner command line is: ./kavtuner [switch1] […] [switchn], where [switch1] is the optional command line switch (see below). When starting tuner you can us...
Page 83
T u n e r 82 82 82 82 9.3. Interface discussing the interface. The page functions. When you start the program its main window appears on your screen. The main window is divided into the following two panes: menu bar and working area. At the top of the window you may see the menu bar containing three...
Page 84
T u n e r 83 83 83 83 use the following keys when selecting options within a page: • ome >—move the cursor to the beginning of the text field; • nd >—move the cursor to the end of the text field; • pace >—check/uncheck the check-box or select/deselect the option; • ab >—go to the next item; • —go to...
Page 85
T u n e r 84 84 84 84 !"to cancel saving of the settings press the cancel button. $" to edit a profile, follow these steps: 1. Start your tuner. The main window will appear on your screen. !"when started the program loads the default profile (its name is specified in the .Ini file) or the file defin...
Page 86
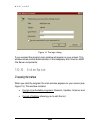
T u n e r 85 85 85 85 9.5. The location page defining the location to be checked. The settings defined for a separate directory to be checked for viruses. 9.5.1. Defining the location to be scanned for viruses in the location page (see figure 4) you can define the list of directories to be scanned f...
Page 87
T u n e r 86 86 86 86 !"this is a general list of directories to be checked. The directories that should be checked are prefixed with " +", and the directories that should be skipped are prefixed with " -". $" to edit an item within the list, you must press the s pace key or double-click it with you...
Page 88
T u n e r 87 87 87 87 9.5.2. Defining scanning settings for a separate directory 9.5.2.1. The directory property window: selecting the required directory $" the tuner program allows to define scanning settings for a separate directory. To do this, follow these steps: 1. Select the required directory...
Page 89
T u n e r 88 88 88 88 when you press the button the add folder window will appear on your screen. Use the window to add the required directory to the list of directories on the location page (for instructions about how to add a directory to the location to be checked see subchapter 9.5.1). The direc...
Page 90
T u n e r 89 89 89 89 #" the sector check function under your operating system may be not available. Files — check this box to scan for viruses in files. If you checked this box, you must select the file types to be checked. For details of how to do this see below. Packed files — check this box to s...
Page 91
T u n e r 90 90 90 90 that are capable of containing a virus-code. Programs — scans all the files with extensions: .Bat, .Bin, .Cla, .Cmd, .Com, .Cpl, .Dll, .Doc, .Dot, .Dpl, .Drv, .Dwg, .Eml, .Exe, .Fpm, .Hlp, .Hta, .Htm, .Htt, .Ini, .Js, .Jse, .Lnk, .Mbx, .Md*, .Msg, .Msi, .Ocx, .Otm, .Ov*, .Php, ...
Page 92
T u n e r 91 91 91 91 display disinfect dialog — displays the inquiry about how to handle the infected object. The program will suggest to disinfect the object (for recoverable objects) or to delete it (for unrecoverable objects). Disinfect automatically — disinfects infected objects without asking ...
Page 93
T u n e r 92 92 92 92 9.5.2.4. The directory property window: defining the advanced scanning tools used. The options page options on the property window options page (see figure 7) allow you enable/disable the following advanced scanning tools. $" you can use the following advanced scanning tools: w...
Page 94
T u n e r 93 93 93 93 subdirectories of the selected directory. Cross filesystems — check this box to enable the program to cross filesystem borders. This check box is useful if there are other filesystems mounted under yours, and you want to scan files in all the available filesystems. 9.6. The opt...
Page 95
T u n e r 94 94 94 94 $" define the following settings: scan subdir at end — check this box to scan subdirectories in the last place (after all the other predefined objects have been scanned). Scan removable — check this box to scan for viruses on the removable disks. #" the following option is not ...
Page 96
T u n e r 95 95 95 95 parameter is used only if you checked endlessly scan check box. #" if the scan delay value is equal to 0, there will be no interval between the loops! 9.7. 9.7. 9.7. 9.7. The report page options located on the report page. Options on the report page of the tuner main window (se...
Page 97
T u n e r 96 96 96 96 !"the checked use syslog box automatically suppresses the following parameters: reportfilename, append, reportfilelimit reportfilesize and repcreateflag. Append — check this box to append new reports to the contents of the log file. Extended report — check this box to add more ...
Page 98
T u n e r 97 97 97 97 check the showing button to display the corresponding dialog window (see figure 10) that is divided into the following two parts: • the working area with the list of check boxes defining optional messages to be included in the performance report. By default all the check boxes ...
Page 99
T u n e r 98 98 98 98 show warning in the log — check this box to be reported about the objects suspected as infected with the modification of a known virus. Show corrupted in the log — check this box to be reported about the examined corrupted objects. Show unknown in the log — check this box to be...
Page 100
T u n e r 99 99 99 99 figure 11. The actionwith page !"we recommend that you enter an absolute path to suspicious and infected folders, but not relative. #" be careful when handling infected and suspicious objects or their copies! If an executable file is infected, do not start it. Copy with path — ...
Page 101
T u n e r 100 100 100 100 9.9. The customize page options located on the customize page. Options on the customize page of the tuner main window (see figure 12) allow you to define the program performance settings. !"the customize page corresponds to the [customize] section of a profile. Figure 12. T...
Page 102
T u n e r 101 101 101 101 confirmation when enabling the redundant scanning tool. !"this setting will be used only for the directory to be checked with enabled redundant scanning tool(see subchapter 9.5.2.4). "delete all…" message — check this box to be asked for confirmation when deleting an infect...
Page 103
102 102 102 102 10. 10. 10. 10. Webtuner: remote webtuner: remote webtuner: remote webtuner: remote administration program administration program administration program administration program 10.1. Functions and features discussing the program features. Webtuner is developed to administrate kaspersk...
Page 104
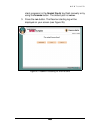
W e b t u n e r 103 103 103 103 10.2. General concept of the program performance features and the operation sequence of the program performance. Webtuner is developed to remotely administrate kaspersky anti-virus for xbsd file server. You can call up this program via any web browser. The browser com...
Page 105
W e b t u n e r 104 104 104 104 figure 13. Calling up kaspersky anti-virus for xbsd file server from webtuner the sequence of steps to be performed to call up kaspersky anti-virus for xbsd file server: 1. Refer to the web server using your web browser. Communication between the web server and the we...
Page 106
W e b t u n e r 105 105 105 105 4. While working with webtuner you can administrate (change settings and start) kaspersky anti-virus for xbsd file server. 10.3. Installing webtuner. Access rights step-by-step installation. Defining access rights to the programs. 10.3.1. The webtuner components right...
Page 107
W e b t u n e r 10 10 10 106 66 6 10.3.2. Setting up the web server and webtuner web server and webtuner, the remote administration program, are installed on your computer by the installer program (for details refer to chapter 2). Right after the installation is completed you must follow the steps d...
Page 108
W e b t u n e r 107 107 107 107 • ch_root—yes in this line enables the program to perform the function chroot() when the server is started. No disables the feature. • docroot—path to the web server root directory. For example, docroot=/usr/local/share/avp/httpd/html #" make sure that the log_file an...
Page 109
W e b t u n e r 108 108 108 108 with the distributive. These are the files providing the communication privacy. To do this, open the open ssl project programs and follow these steps: create the key and the certificate request: openssl req -new >; cert.Csr delete the password from the key: openssl rs...
Page 110
W e b t u n e r 109 109 109 109 2. Edit the server settings to define the file index.Html as the default file for this directory. If it is not possible, rename the file into the one defined as the default for your server. 3. Enable execution of cgi scripts for the subdirectory html/cgi-bin. 4. Edit ...
Page 111
W e b t u n e r 110 110 110 110 • read and write within the directory containing the kaspersky anti-virus for xbsd file server initialization file (avpunix.Ini); • read, write and execute files within the directory for temporary files of webtuner ( html/tmp); • read, write and execute files within t...
Page 112
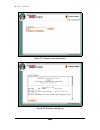
W e b t u n e r 111 111 111 111 10.4. Launching webtuner discussing how to start the webtuner program. As it was mentioned above, webtuner is installed under the web server enabling remote administration of kaspersky anti-virus for xbsd file server. In this connection, you are able to call up webtun...
Page 113
W e b t u n e r 112 112 112 112 figure 14. The login dialog if you succeed the program main window will appear on your screen. This window allows remote administration of the kaspersky anti-virus for xbsd file server components. 10.5. Interface discussing the interface. When you start the program th...
Page 114
W e b t u n e r 113 113 113 113 figure 15. The webtuner main window $" to select a program from the list, 1. Highlight it with your left mouse button. 2. Press the select button, if your browser does not support java script or the java script support is disabled. For web browsers supporting java scr...
Page 115
W e b t u n e r 114 114 114 114 !"be careful when pressing the hide button. If you will do it without an item selected in the list, the list will be cleared. $" if you again want to see all the controllable programs in the list, press the show all button. !"this is useful if you want to restore the ...
Page 116
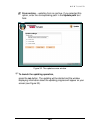
W e b t u n e r 115 115 115 115 figure 16. The webtuner main window with webtuner selected in the list the webtuner configure window (see figure 17) will appear on your screen. The window contains hyperlinks allowing you to display the following pages: • the main page items allow you to define the c...
Page 117
W e b t u n e r 116 116 116 116 10.6.2. The main page: webtuner performance settings for your webtuner to operate correctly, you must define its main performance settings located on the main page (see figure 17) of the webtuner configure window. Figure 17. The main page $" to insure correct performa...
Page 118
W e b t u n e r 117 117 117 117 2. Enter the full path to the kaspersky anti-virus for xbsd file server directory in the kaspersky anti-virus directory text field. You can do this manually or by using the browse button. The default path is: /usr/local/share/avp/ 3. Enter the name of the kaspersky an...
Page 119
W e b t u n e r 118 118 118 118 figure 18. The modules page !"before you use the properties or the delete button make sure to select a module from the list with your left mouse button! $" to add an item to the list, follow these steps: 1. Press the add button. 2. Enter the new module name in the nam...
Page 120
W e b t u n e r 119 119 119 119 $" to define the properties of a module, follow these steps: 1. Select the required module from the list with your left mouse button. 2. Press the properties button. 3. In the module: name window on your screen (see figure 19), define the following settings: • main cg...
Page 121
W e b t u n e r 120 120 120 120 !"for details on the macroinstructions that are used in the above text field values refer to subchapter 15.13 of appendix b. #" by omitting any of the above values and leaving the corresponding text field blank, you remove the corresponding hyperlink from the webtuner...
Page 122
W e b t u n e r 121 121 121 121 10.7. Webtuner: administering daemon webtuner for the daemon process. Editing the profile, launching the program and reviewing the log. 10.7.1. Daemon settings webtuner allows you to remotely administrate the daemon program, i.E. To edit the program profile, to launch...
Page 123
W e b t u n e r 122 122 122 122 figure 20. The webtuner main window: daemon is selected $" to edit another profile, follow these steps: 1. Click the config hyperlink. 2. Select the required profile from the drop down list in the window on your screen and press the open button. 3. Edit the daemon set...
Page 124
W e b t u n e r 123 123 123 123 10.7.2. Remote configuration of the daemon program 10.7.2.1. The profile tuning window webtuner allows you to edit profiles of the daemon program. The settings defined from webtuner can be saved to the default profile as well as to any other profile that can be assign...
Page 125
W e b t u n e r 124 124 124 124 figure 21. The objects page 10.7.2.2. The objects page: location to be scanned on the objects page (see figure 21) you can define the list of directories to be scanned for viruses and scanning settings for a separate directory. $" to define scanning settings for the s...
Page 126
W e b t u n e r 125 125 125 125 • the actions page allows you to define the way infected and suspicious objects must be processed. Options on this page are similar to those described in subchapter 9.5.2.3. • the options page allows you to define the advanced scanning tools to be used. Options on thi...
Page 127
W e b t u n e r 126 126 126 126 pressing the select button (for browsers not supporting java script). 3. Check the exclude path check box if you want the directory to be excluded from the location to be checked (prefixed with "–"). 4. Press the add button to add the directory to the list on the obje...
Page 128
W e b t u n e r 127 127 127 127 in fact, the actions page includes two subpages containing: 1. Options for infected and suspicious objects detected. The page options and their functions are similar to those described in subchapter 9.8. 2. Options for corrupted and suspicious objects detected (see fi...
Page 129
W e b t u n e r 128 128 128 128 included in the report is defined on the second sub-page of the report page. To move between the subpages use the arrow buttons and , located in the upper right corner of the page. 10.7.2.6. The customs page: advanced scanning settings the customs page items allow you...
Page 130
W e b t u n e r 129 129 129 129 client programs) in the socket file dir text field manually or by using the browse button. The default path is /var/run. 3. Press the run button. The daemon starting log will be displayed on your screen (see figure 25). Figure 23. Daemon is starting for the first time.
Page 131
W e b t u n e r 130 130 130 130 figure 24. Daemon start parameters figure 25. Daemon starting log.
Page 132
W e b t u n e r 131 131 131 131 starting the daemon process for the second (third, fourth…) time in this case the daemon starter window (see figure 26) on your screen contains information about the existing daemon process: • pid – the daemon process identification number. • socket directory name – p...
Page 133
W e b t u n e r 132 132 132 132 #" the existing process must be killed to avoid conflicts that may arise between two or more simultaneously existing processes. In this case, if a client program calls up a daemon process, it will be impossible to identify the target process correctly among the existi...
Page 134
W e b t u n e r 133 133 133 133 $" to review the log of the existing daemon process, press the view log button in the webtuner main window with the daemon item selected in the list (see figure 20). The daemon log window will appear on your screen (see figure 28). The window will contain the followin...
Page 135
W e b t u n e r 134 134 134 134 figure 28. The daemon process performance results $" to review the log of a previous process, 1. Press the report button. 2. In the window on your screen, select the required log file from the appropriate drop-down list with your right mouse button and by pressing the...
Page 136
W e b t u n e r 135 135 135 135 webtuner distributive. Reports in text format are generated on the basis of web_template.Tm, and reports in html are generated on the basis of web_new_template.Tm. 10.8. Webtuner: administering scanner webtuner for the anti-virus scanner. Editing the profile, launchin...
Page 137
W e b t u n e r 136 136 136 136 figure 29. The webtuner main window: scanner is selected $" to edit another profile, follow these steps: 1. Click the config hyperlink. 2. Select the required profile from the drop-down list in the window on your screen. Edit the scanner settings using appropriate pag...
Page 138
W e b t u n e r 137 137 137 137 10.8.2. Remote configuration of the scanner program webtuner allows you to edit the profiles of the scanner program. Scanner parameters are similar to those described for the daemon process (see subchapter 10.7.2). The difference is the report page (see figure 9), whe...
Page 139
W e b t u n e r 138 138 138 138 • view log – displays the scanner performance report. • exit – allows you to exit the scanner start parameters window. $" to scan a location different from that defined in the profile, 1. Define the location in the scan path text field; 2. Select the scan input path o...
Page 140
W e b t u n e r 139 139 139 139 10.8.4. Reviewing the log file webtuner allows to review reports about the current scanning operation and about the operations performed previously. $" to review the required scanning report, follow these steps: 1. Click the run hyperlink in the webtuner main window w...
Page 141
W e b t u n e r 140 140 140 140 • run – launches the updating utility. • view log – displays the updater performance report. • exit – allows you to exit the updater window. Figure 31. The webtuner main window: updater is selected the virus-definition databases may be updated: • via the internet; • f...
Page 142
W e b t u n e r 141 141 141 141 from archive – updating from an archive. If you selected this option, enter the corresponding path in the update path text field. Figure 32. The update source window $" to launch the updating operation, press the run button. The updating will be started and the window...
Page 143
W e b t u n e r 142 142 142 142 figure 33. The updating operation is in progress $" to review the status of the last updating operation, press the view log button. The program will display a window with information about the last updating operation (see figure 33). If the updating operation is in pr...
Page 144
143 143 143 143 11. 11. 11. 11. Updater: updating virus updater: updating virus updater: updating virus updater: updating virus---- definition databases definition databases definition databases definition databases 11.1. Function and features updater updates virus-definition databases, which are us...
Page 145
U p d a t e r 144 144 144 144 ./kavupdater update_switch [switch1] [switch2]... Where update_switch is a mandatory switch reflecting the way the update will be performed (see subchapter 11.3); [switchn] is an optional command line switch. For a list of switches and their functions see appendix b. By...
Page 146
U p d a t e r 145 145 145 145 11.3. How to update virus- definition databases updating via the internet. Updating from a network directory. Updating from an archive. Examples. 11.3.1. Updating via the internet $" to retrieve new virus-definition databases from an ftp or a web server, launch the prog...
Page 147
U p d a t e r 146 146 146 146 11.3.2. Updating from a network directory if you need to update virus-definition databases and upgrade programs on several computers, it’s more convenient to download updates/upgrades via the internet to your network directory and then perform updating/upgrading from th...
Page 148
U p d a t e r 147 147 147 147 11.4. Saving the report to a file saving the report to a file. Example. $" to save report data to a file, use the command line switch –w: ./kavupdater -uik=server_and_path -w[t][a][-][+][=filename] where: • -wt or -wt+ is the switch creating a new log file; • -wa or -wa...
Page 149
148 148 148 148 12. 12. 12. 12. Inspector: monitoring inspector: monitoring inspector: monitoring inspector: monitoring filesystem integrity filesystem integrity filesystem integrity filesystem integrity 12.1. Function and features the inspector program is an integrity checker running under the xbsd...
Page 150
I n s p e c t o r 149 149 149 149 restore the originals). For details about handling new or modified files see subchapter 12.2.3. If inspector fails to disinfect infected files, they are transferred to the daemon program. 12.2. Running inspector 12.2.1. The program command line inspector must be sta...
Page 151
I n s p e c t o r 150 150 150 150 by comparing newly collected data against the database master copy the program identifies new and modified files and checks for viruses in them. !"you can create separate inspector databases for every location to be checked. If a database master copy for the locatio...
Page 152
I n s p e c t o r 151 151 151 151 $" to set inspector to load the location to be checked from a text file, follow these steps: 1. Create a list of directories to be checked and save it to a text file. Every directory with its full path must be located in a separate line in the text file list. For ex...
Page 153
I n s p e c t o r 152 152 152 152 by default, inspector is preset to check for viruses in the subdirectories of the defined directories to be checked. To exclude all the subdirectories from the check use the switch – r in the inspector command line. Let's review the following example for training pu...
Page 154
I n s p e c t o r 153 153 153 153 $" to set the program to display a report about the modified and new files detected, use the switch –da0 in the inspector command line. $" to set the program to automatically handle all the modified and new files detected, use the switch –da2 in the inspector comman...
Page 155
I n s p e c t o r 154 154 154 154 %" solution: to do this, enter the following strings in the inspector start-up command line: ./kavinspector –g[=base_documents] /documents –r– –da2d –dc –a[=var/run] –s[=base_documents] 12.2.4. Saving the performance report inspector can save the performance report ...
Page 156
155 155 155 155 13. 13. 13. 13. Control centre: scheduling control centre: scheduling control centre: scheduling control centre: scheduling the kaspersky anti the kaspersky anti the kaspersky anti the kaspersky anti----virus for virus for virus for virus for xbsd file server performance xbsd file se...
Page 157
C o n t r o l c e n t r e 156 156 156 156 where: switchn – is the optional command line switch of control centre. !"you can use more than one switch in the control centre command line. For the complete list of available command line switches refer to subchapter 15.8 appendix b. 13.3. Scheduling perf...
Page 158
C o n t r o l c e n t r e 157 157 157 157 #" program performance parameters must be separated by colons . –u=username is the user name under which the prgname program will be started ; -e=hour:min is the prgname program performance time. When the time is over, the program shuts down. Let's review th...
Page 159
C o n t r o l c e n t r e 158 158 158 158 where: prgname is the name of the prgname program executable file; –a:arg[:arg1[…]]is the prgname performance parameters; #" program performance parameters must be separated by colons . –u=username is the user name under which the prgname program will be sta...
Page 161
C o n t r o l c e n t r e 160 160 160 160 ???? Example : you want to schedule the updater to update virus- definition databases from the archive kavbases.Zip on every monday at 7.00 p.M. And to log the performance results in the file report.Txt. The lifetime for this task is from 01.01.02 to 31.12.0...
Page 162
C o n t r o l c e n t r e 161 161 161 161 if the character a is defined in the switch, the report will be appended to the contents of filename, the character t overwrites the report with a new one. If the character + is defined, extra information will be included in the report heading. The character...
Page 163
162 162 162 162 14. 14. 14. 14. Appendix a. Appendix a. Appendix a. Appendix a. Principal files principal files principal files principal files files that are principal for kaspersky anti-virus for xbsd file server and their functions. The following files are vital for the kaspersky anti-virus for x...
Page 164
163 163 163 163 15. 15. 15. 15. Appendix b. Appendix b. Appendix b. Appendix b. Supplementary details of supplementary details of supplementary details of supplementary details of kaspersky anti kaspersky anti kaspersky anti kaspersky anti----virus for xbsd virus for xbsd virus for xbsd virus for xb...
Page 165
A p p e n d i x b 164 164 164 164 [avp32] " defaultprofile=defunix.Prf [configuration] keyfile=avplinux.Key keyspath=. Setfile=avp.Set basepath=. You may edit any section of the file ( [avp32] and [configuration]). The [avp32] section contains the parameter: defaultprofile – the profile to be loaded...
Page 166
A p p e n d i x b 165 165 165 165 example, if you move your scanner to a separate directory, avpunix.Ini must be copied to the same directory or the personal directory of a user authorized to access the scanner. In this case make sure to edit the parameter values within the initialization file the a...
Page 167
A p p e n d i x b 166 166 166 166 repforeachdisk=no writetime=1 writetimeinfo=1 longstrings=no userreport=no userreportname=userreport. Log showok=yes showpack=yes showpassworded=yes showsuspision=yes showwarning=yes showcorrupted=yes showunknown=yes [actionwithinfected] infectedcopy=no infectedfold...
Page 168
A p p e n d i x b 167 167 167 167 the [object] section contains parameters defining the location and the objects to be checked. If you are not authorized to access the defined directories and/or files, they will be ignored during the check. Names – this parameter defines the location to be checked, ...
Page 169
A p p e n d i x b 168 168 168 168 .Ov*, .Php, .Pht, .Pif, .Plg, .Pp*, .Prg, .Rtf, .Scr, .Shs, .Sys, .Tsp, .Vbe, .Vbs, .Vxd, .Xl*. 2 – scans every file of every type (this value is equal to the mask "*.*"). 3 – scans file types defined by the user for the usermask parameter. If you define more then o...
Page 170
A p p e n d i x b 169 169 169 169 in mail databases. No disables this feature. Mailplain – yes in this line enables the program to check for viruses in plain mail files. No disables this feature. Embedded – yes in this line enables the program to check for viruses in ole objects embedded in the exam...
Page 171
A p p e n d i x b 170 170 170 170 viruses on the removable disks. No disables this feature. Scansubdiratend – yes in this line enables the program to scan subdirectories in the last place (after all the other objects have been scanned) . No disables this feature. Symlinks – here you must define one ...
Page 172
A p p e n d i x b 171 171 171 171 !"the positive value ( yes) in the usesyslog line automatically suppresses the following parameters: reportfilename, append, reportfilelimit, reportfilesize and repcreateflag. Reportfilename – the name of your log file (valid only if report=yes and usesyslog=no). Th...
Page 173
A p p e n d i x b 172 172 172 172 #" the following two parameters are used only if you call up the daemon process from a script file and want to display the performance report. Userreport – yes in this line enables the program to add current check results to the user-defined log file (see the userre...
Page 174
A p p e n d i x b 173 173 173 173 copywithpaths – yes in this line enables the program to copy infected objects to a separate folder together with their paths. No disables this feature. Changeext – yes in this line enables the program to change extensions of infected files. No disables this feature....
Page 175
A p p e n d i x b 174 174 174 174 the [actionwithcorrupted] section parameters define the actions to be taken by the program when it detects corrupted objects. Corruptedcopy – yes in this line enables the program to copy corrupted files to a separate folder that must be defined in the corruptedfolde...
Page 176
A p p e n d i x b 175 175 175 175 the [customize] section parameters define the advanced program performance settings. Updatecheck – yes in this line enables the program to remind you about the need to update your virus-definition databases. No disables this feature. Updateinterval – the interval (i...
Page 177
A p p e n d i x b 176 176 176 176 15.4. Scanner and daemon: command line switches a list of scanner command line switches and their functions. The difference between command line switches for the scanner and the daemon process. The general format of the scanner command line is: ./kavscanner [switch1...
Page 178
A p p e n d i x b 177 177 177 177 -h[-] disables the heuristic checking tool . -u[-] disables unpacking engine. -a[-] disables unpacking engine. -v[-] enables the redundant scanning tool . -r[-] skips the scanning into subdirectories. If you define this switch, the scanner will check only files of t...
Page 179
A p p e n d i x b 178 178 178 178 -lh checks only the files and directories available via the symbolic links predefined in the command line and ignores other symbolic links. -ll checks the files and directories available via symbolic links. -lp skips the files and directories available via symbolic ...
Page 180
A p p e n d i x b 179 179 179 179 -i1 prompts for disinfecting infected objects. -- or -i2 disinfects infected objects automatically if possible. When running in this mode the program checks for viruses and tries to recover infected files and boot sectors to exactly (if possible) or mostly match the...
Page 181
A p p e n d i x b 180 180 180 180 -vl[=filename] logs the list of viruses into filename. If the file is not defined, the list of viruses will be screened. -h or -? Displays the list of command line switches. -t=path the path to the temporary files directory. -e defines english as the default languag...
Page 182
A p p e n d i x b 181 181 181 181 -k kills the parent daemon process. -ka kills all daemon processes running. -v displays the version number. -f=directory creates and stores the files avpctl and avppid in the defined directory. If you do not start daemon from under the root user, the program may be ...
Page 183
A p p e n d i x b 182 182 182 182 ok – no virus or virus-like instructions were detected in the file or sector. This message will be displayed only if you preset the scanner to report virus-free objects. #" the sector check function under your operating system may be not available. Infected: – the d...
Page 184
A p p e n d i x b 183 183 183 183 15.6. Scanner and daemon: exit codes the list of exit codes that can be returned by the program. Example of using these codes in a script file. If you start scanner or daemon from a script file, you may analyze its exit code. After the task is finished, the program ...
Page 185
A p p e n d i x b 184 184 184 184 hi=$[$exitcode/16] case $lo in ;; 7) echo 7 - file kavscanner is corrupted ... ;; 0) echo 0 - no viruses were found ;; *) echo error! Esac case $hi in 0) echo internal error: integrity failed ;; 4) echo internal error: bases not found ;; esac exit 0 15.7. Slogan: re...
Page 186
A p p e n d i x b 185 185 185 185 • template.Tm2 – detail report template for the console display; • template.Htm – detail report template in html for the console display; • web_template.Tm – report template for webtuner; • web_new_template.Tm – report template in html for webtuner. By editing these...
Page 187
A p p e n d i x b 186 186 186 186 the list of modified and corrupted viruses detected: %w virus name: $virus total found: $count %% each of the cycles mentioned above may include the following macros: $virus – name of the virus detected. $count – total number of the virus pieces detected. For exampl...
Page 188
A p p e n d i x b 187 187 187 187 list of all found suspicion virus: ------------------------------------------------ %s virus name: $virus total found: $count %% ------------------------------------------------- list of all warnings: ------------------------------------------------- %w virus name: ...
Page 189
A p p e n d i x b 188 188 188 188 –g[=database_name] loads details of the location to be checked from the defined database file. –s[=database_name] saves details of the location to be checked to the defined database file. #" if you do not specify any database name in the above command line switches,...
Page 190
A p p e n d i x b 1 11 189 89 89 89 -lh checks only the files and directories available via the symbolic links predefined in the command line and ignores other symbolic links. -ll checks the files and directories available via symbolic links. -lp skips the files and directories available via symboli...
Page 191
A p p e n d i x b 190 190 190 190 a[=socket_directory] defines the full path to the directory containing the daemon socket file. -w[t][a][-][+][=filname] logs the performance report into the defined file (the default file is report.Txt). If the character a is defined in the switch, the report will b...
Page 192
A p p e n d i x b 191 191 191 191 where: [switchn] is the optional command line switch of control centre; [instructionn[="task_parameters"]] is the optional instruction of the program. You can use more than one switch and more than one command in the control centre command line . The following comma...
Page 193
A p p e n d i x b 192 192 192 192 -w[t][a][-][+][=filename] logs the performance report into the defined file (the default file is report.Txt). If the character a is defined in the switch, the report will be appended to the contents of filename, the character t overwrites the report with a new one. ...
Page 194
A p p e n d i x b 193 193 193 193 #" if you do not enter values for the parameters -fs=day.Month.Year and - st=hour:min, they will be automatically defined as the task creation date and time. -ls=day.Month.Year is the date when the task must be started for the last time ; -re=delay is the interval b...
Page 195
A p p e n d i x b 194 194 194 194 -cd=idn deletes the task with the defined id . 15.10. Monitor: configuration file (monitor.Conf) parameters in the monitor configuration file. Let's review an example of monitor.Conf: #report file section# logfile /tmp/kasperskymonitor.Log append no #options section...
Page 196
A p p e n d i x b 195 195 195 195 options section defines the program performance settings: cachesize – the quantity of files to be scanned for viruses only once, when they are opened for the first time. The value 500 through 5000 is recommended. !"some files on a computer are opened quite often and...
Page 197
A p p e n d i x b 196 196 196 196 • none – ignores the object. Maxconcurrentchecks – the maximum number of simultaneously scanned files. The value 5 through 15 is recommended depending on the capacity of your computer. 15.11. Updater: command line switches the list of command line switches available...
Page 198
A p p e n d i x b 197 197 197 197 -a=path before performing the updating operation saves the old virus-definition databases to the defined location. #" the switch –a=path cannot be used together with the switch –kb! -p[=num] defines the maximum number of simultaneously downloaded files. The default ...
Page 199
A p p e n d i x b 198 198 198 198 -s[=filename] enables the program to use the defined file as a .Set file (the default file is defined in the setfile line in avpunix.Ini). For example, ./kavupdater -s=avp.Set. -t[=directory] enables the program to use the defined directory for intermediate operatio...
Page 200
A p p e n d i x b 199 199 199 199 one. If the character + is defined, extra information will be included in the report heading. The character - disables the extra information in the report heading. -ws[-] logsperformance results in the system log. -e defines english as the default language for repor...
Page 201
A p p e n d i x b 200 200 200 200 -da uninstalls all kaspersky anti-virus software products from this computer. -e defines english as the default language for reports and messages. 15.13. Webtuner: the configuration file (loader.Cfg) let's review an example of loader.Cfg, the webtuner configuration ...
Page 202
A p p e n d i x b 201 201 201 201 maincgi=updater.Cgi configure=updater.Cgi?Avp_d=%avp_dir%&e_upd=%exec % hide=no [scanner] exec=kavscanner maincgi=scanner_prf.Cgi configure=./scanner_prf.Cgi?Avp_d=%avp_dir%&avp_p rf=%avp_prf%&start_dir=%avp_dir% configuredefault=./scanner_prf.Cgi?Avp_d=%avp_dir %&a...
Page 203
A p p e n d i x b 202 202 202 202 heading must contain a name of the kaspersky anti-virus for xbsd file server software package component to be administrated. Exec – the name of the component executable file. Maincgi – the name of the component file with the .Cgi extension. This file insures availab...
Page 204
A p p e n d i x b 203 203 203 203 !"the run parameter insures availability of the run hyperlink on the webtuner main window with the package component selected in the programs list. Report – defines viewing of the package component performance results from a remote location by using webtuner. !"the ...
Page 205
204 204 204 204 16. 16. 16. 16. Appendix c. Appendix c. Appendix c. Appendix c. Classifying computer viruses classifying computer viruses classifying computer viruses classifying computer viruses discussing various virus types. The computer virus is a computer program(that is, executable code and/or...
Page 206
A p p e n d i x c 205 205 205 205 we can differentiate viruses by the operating system they infect. Every file or network virus is able to infect files of one or more operating systems: dos, windows, win95/nt, os/2 etc. Macro viruses infect file formats used by word, excel, and office97. Boot viruse...
Page 207
A p p e n d i x c 206 206 206 206 self-encoding and polymorphic features are used by almost all virus types to make it difficult to detect them. Polymorphic viruses are difficult to detect because they contain no constant code blocks. Generally speaking, two samples of the same polymorph won’t have ...
Page 208
17. Appendix d. Kaspersky labs ltd. About kaspersky labs kaspersky labs is a privately-owned, international, anti-virus software- development group of companies headquartered in moscow (russia), and representative offices in the united kingdom, united states of america, china, france and poland. Fou...
Page 209
A p p e n d i x d 60,000 known viruses and all other types of malicious code. The product is also powered by a unique heuristic technology combating even future threats: the built-in heuristic code analyzer, which is able to detect up to 92% of unknown viruses and the world's only behavior blocker f...
Page 210
A p p e n d i x d • anti-virus scanner provides a comprehensive check of all local and network drive contents on demand; • anti-virus monitor automatically checks in real-time all used files; • mail filter automatically checks in the background for viruses in all incoming and outgoing messages; • co...
Page 211
A p p e n d i x d kaspersky® security for pda kaspersky® security for pda provides reliable virus protection for the data stored on pda running palm os or windows ce, as well as for any information transferred from a pc or extension card, rom files and databases. Software contains a combination of t...
Page 212
A p p e n d i x d data-protection system that is fully appropriate and compatible for your network configurations. Kaspersky® corporate suite includes full-scale anti-virus protection of: • workstations running windows 95/98/me, windows nt/2000 workstation, windows xp, linux, os/2; • file and applic...
Page 213
A p p e n d i x d 17.2. Contact information if you have any questions, comments or suggestions please refer them to our distributors or directly to kaspersky labs. We will be glad to advise you on any matters related to our product by phone or e-mail and all your recommendations and suggestions will...
Page 214
18. Index advanced checking tool ........46, 47, 92, 170 advanced scanning tools........................... 92 daemon ................................................. 9, 59 extracting engine....................................... 42 heuristic analyzer......................35, 178, 183 initializatio...