- DL manuals
- M86 Security
- Server
- 300
- Installation Manual
M86 Security 300 Installation Manual
Summary of 300
Page 1
M86 security reporter installation guide models: 300, 500, 700, 705, 730, 735 software version: 3.0.00 document version: 10.30.10
Page 2: M86 S
Ii m86 s ecurity i nstallation g uide m86 s ecurity r eporter i nstallation g uide for 300, 500, 700, 705, 730, 735 m odels © 2010 m86 security all rights reserved. Printed in the united states of america this document may not, in whole or in part, be copied, photocopied, reproduced, trans- lated, o...
Page 3: Ontents
M86 s ecurity i nstallation g uide iii c ontents m86 sr a ppliance i ntroduction ................................................................1 about this document...................................................................................................... 2 security reporter models 705 ...
Page 4
C ontents iv m86 s ecurity i nstallation g uide step 1: setup procedures. ........................................................................................... 21 quick start setup requirements ............................................................................................21 lcd p...
Page 5
C ontents m86 s ecurity i nstallation g uide v access the sr via its lan 1 ip address ................................................................................41 accept the security certificate in firefox ...............................................................................42 tempor...
Page 6
C ontents vi m86 s ecurity i nstallation g uide step c: export the report view in the pdf output format ................................................77 iii. Save and schedule a report exercise ................................................................................78 step a. Save a report...
Page 7
C ontents m86 s ecurity i nstallation g uide vii evaluation mode pop-up............................................................................................ 113 report manager server information panel. .............................................................. 114 led i ndicators and b ut...
Page 8
C ontents viii m86 s ecurity i nstallation g uide a ppendix b: o ptional e thernet t ap i nstallation ...............................127 preliminary setup procedures................................................................................... 127 unpack the ethernet tap unit from the box ........
Page 9: M86 Sr A
M86 sr a ppliance i ntroduction m86 s ecurity i nstallation g uide 1 m86 sr a ppliance i ntroduction thank you for choosing to install and evaluate the m86 security reporter appli- ance. The security reporter (sr) from m86 security consists of the best in breed of m86 professional edition reporting ...
Page 10: About This Document
M86 sr a ppliance i ntroduction a bout this d ocument 2 m86 s ecurity i nstallation g uide about this document this document is divided into the following sections: • introduction - this section is comprised of an overview of the sr product and how to use this document • service information - this s...
Page 11
M86 sr a ppliance i ntroduction s ecurity r eporter m odels 705 and 735 m86 s ecurity i nstallation g uide 3 security reporter models 705 and 735 please refer to the appropriate ibm documentation when installing security reporter models 705 and 735; these units use ibm system x3620 m3 hardware. Syst...
Page 12
M86 sr a ppliance i ntroduction c onventions u sed in this d ocument 4 m86 s ecurity i nstallation g uide conventions used in this document the following icons are used throughout this document to call attention to impor- tant information pertaining to handling, operation, and maintenance of the ser...
Page 13: Ervice
S ervice i nformation m86 t echnical s upport c all p rocedures m86 s ecurity i nstallation g uide 5 s ervice i nformation the user should not attempt any maintenance or service on the unit beyond the procedures outlined in this document. Any initial hardware setup problem that cannot be resolved at...
Page 14: Reliminary
P reliminary s etup p rocedures u npack the u nit from the c arton 6 m86 s ecurity i nstallation g uide p reliminary s etup p rocedures unpack the unit from the carton inspect the packaging container for evidence of mishandling during transit. If the packaging container is damaged, photograph it for...
Page 15: Select A Site For The Server
P reliminary s etup p rocedures s elect a s ite for the s erver m86 s ecurity i nstallation g uide 7 select a site for the server the server operates reliably within normal office environmental limits. Select a site that meets the following criteria: • clean and relatively free of excess dust. • wel...
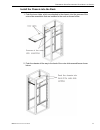
Page 16: Rack Mount The Server
P reliminary s etup p rocedures r ack m ount the s erver 8 m86 s ecurity i nstallation g uide rack mount the server rack setup precautions warning: before rack mounting the server, the physical environment should be set up to safely accommodate the server. Be sure that: • the weight of all units in ...
Page 17
P reliminary s etup p rocedures r ack m ount the s erver m86 s ecurity i nstallation g uide 9 rack mount instructions for 500 model servers rack setup suggestions • determine the placement of each component in the rack before you install the rails. • install the heaviest server components on the bot...
Page 18
P reliminary s etup p rocedures r ack m ount the s erver 10 m86 s ecurity i nstallation g uide install the slide assemblies to the rack 1. After you have installed the short and long brackets to the outer slides, you are ready to install the whole slide assemblies (outer slides with short and long b...
Page 19
P reliminary s etup p rocedures r ack m ount the s erver m86 s ecurity i nstallation g uide 11 install the chassis into the rack 1. Push the inner slides, which are attached to the chassis, into the grooves of the outer slide assemblies that are installed in the rack as shown below: 2. Push the chas...
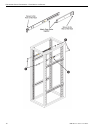
Page 20
P reliminary s etup p rocedures r ack m ount the s erver 12 m86 s ecurity i nstallation g uide rack mount instructions for 700 and 730 model servers rack setup suggestions • determine the placement of each component in the rack before you install the rails. • install the heaviest server components o...
Page 21
P reliminary s etup p rocedures r ack m ount the s erver m86 s ecurity i nstallation g uide 13 install the inner rails 1. Place the inner rack extensions on the side of the chassis aligning the hooks of the chassis with the rail extension holes. Make sure the extension faces "outward" just like the ...
Page 22
P reliminary s etup p rocedures r ack m ount the s erver 14 m86 s ecurity i nstallation g uide.
Page 23
P reliminary s etup p rocedures r ack m ount the s erver m86 s ecurity i nstallation g uide 15 install the server into the rack 1. Confirm that chassis includes the inner rails (a) and rail extensions (b). Also, confirm that the outer rails (c) are installed on the rack. 2. Line chassis rails (a and...
Page 24
P reliminary s etup p rocedures r ack m ount the s erver 16 m86 s ecurity i nstallation g uide install the server into a telco rack if you are installing the server into a telco type rack, follow the directions given on the previous pages for rack installation. The only difference in the installatio...
Page 25
P reliminary s etup p rocedures r ack m ount the s erver m86 s ecurity i nstallation g uide 17 install the bezel on the 500, 700, and 730 model chassis after rack mounting a 500, 700, or 730 model server, the bezel should be installed on the front end of the chassis. Note: this portion of the instal...
Page 26: Check The Power Supply
P reliminary s etup p rocedures c heck the p ower s upply 18 m86 s ecurity i nstallation g uide check the power supply the server is equipped with a universal power supply that handles 100-240 v, 50/ 60 hz. A standard power cord interface (iec 950) facilitates power plugs that are suitable for most ...
Page 27
P reliminary s etup p rocedures g eneral s afety i nformation m86 s ecurity i nstallation g uide 19 • to ensure proper cooling, always operate the server with its covers in place. Do not block any openings on the chassis. Do not place the server near a heater. • always exit the software application ...
Page 28
P reliminary s etup p rocedures g eneral s afety i nformation 20 m86 s ecurity i nstallation g uide motherboard battery precautions caution: the battery on the motherboard should not be replaced without following instruc- tions provided by the manufacturer. Only qualified service personnel should re...
Page 29: Nstall
I nstall the s erver s tep 1: s etup p rocedures m86 s ecurity i nstallation g uide 21 i nstall the s erver step 1: setup procedures this step requires you to set up parameters for the sr to function on the network. If using a 300, 500, 700, or 730 server, you have the option of using the text-based...
Page 30
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures 22 m86 s ecurity i nstallation g uide step 1a: quick start setup procedures storage device setup (for attached storage units) if you have a nas (fibre channel connected storage device or “san”) that will be used with the sr, you will ne...
Page 31: Power On The Sr
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures m86 s ecurity i nstallation g uide 23 fig. 4 - rear of 705 / 735 model chassis, serial port circled in red b. Power on the laptop. C. Proceed to the next set of instructions: power on the sr. Power on the sr power up a 300 model a. Make...
Page 32
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures 24 m86 s ecurity i nstallation g uide power up a 500, 700, or 730 model a. Make sure the power cord(s) is/are plugged into the back of the chassis. B. Plug the power cord(s) into a power source with an appropriate rating. Warning: it is...
Page 33
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures m86 s ecurity i nstallation g uide 25 hyperterminal setup procedures if using a serial console, follow these procedures on a windows xp machine to create a hyperterminal session. Note: hyperterminal is no longer included with windows as...
Page 34
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures 26 m86 s ecurity i nstallation g uide c. At the connect using field, select the com port assigned to the serial port on the laptop (probably “com1”), and then click ok to open the properties dialog box, displaying the port settings tab:...
Page 35
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures m86 s ecurity i nstallation g uide 27 f. In the hyperterminal session window, go to file > properties to open the prop- erties dialog box, displaying the connect to and settings tabs: g. Click the settings tab, and at the emulation menu...
Page 36: Login Screen
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures 28 m86 s ecurity i nstallation g uide login screen the login screen displays after powering on the sr unit using a monitor and keyboard, or after creating a hyperterminal session. Notes: if using a hyperterminal session, the login scree...
Page 37: Quick Start Setup
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures m86 s ecurity i nstallation g uide 29 quick start setup a. At the press the number of your selection prompt, press 2 to select the “quick start setup” process. The quick start setup process takes you to the following configuration scree...
Page 38
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures 30 m86 s ecurity i nstallation g uide configure network interface lan1 a. From the quick start menu, press 3 to go to the configure network interface screen for lan1. B. At the enter interface lan1 ip address prompt, type in the lan1 ip...
Page 39
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures m86 s ecurity i nstallation g uide 31 time zone regional setting a. From the quick start menu, press 8 to go to the time zone regional configura- tion screen. B. Select a region using up-arrow and down-arrow keys. Press y when you have ...
Page 40
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures 32 m86 s ecurity i nstallation g uide non-quick start procedures or settings the options described below do not pertain to the quick start setup process. Reboot system a. From the quick start menu, press b to go to the reboot confirmati...
Page 41: System Status Screen
I nstall the s erver s tep 1a: q uick s tart s etup p rocedures m86 s ecurity i nstallation g uide 33 system status screen the system status screen contains the following information: • lan1 ip address and netmask specified in screen 3, and current status (“active” or “inactive”) • lan2 ip address a...
Page 42: Lcd Panel
I nstall the s erver s tep 1b: lcd p anel s etup p rocedures 34 m86 s ecurity i nstallation g uide step 1b: lcd panel setup procedures storage device setup (for attached storage units) if you have a nas (fibre channel connected storage device or “san”) that will be used with the sr, you will need to...
Page 43: M86 Menu
I nstall the s erver s tep 1b: lcd p anel s etup p rocedures m86 s ecurity i nstallation g uide 35 lcd menu the lcd menu tree includes the following two main menu selections: • lcd options - this choice includes options for viewing the lcd display and monitoring the sr once it is configured and runn...
Page 44
I nstall the s erver s tep 1b: lcd p anel s etup p rocedures 36 m86 s ecurity i nstallation g uide ip / lan1 and 2 when the ip / lan 1 (2) option is selected, the ip / lan 1 (2) screen displays with the following menu items: • configure lan 1 (2) ip • change lan1 (2) netmask a. Choose configure lan ...
Page 45
I nstall the s erver s tep 1b: lcd p anel s etup p rocedures m86 s ecurity i nstallation g uide 37 host name when the host name option is selected, the host name screen displays with the configure hostname menu item. A. Choose configure hostname and press the checkmark key to go to the configure hos...
Page 46
I nstall the s erver s tep 1b: lcd p anel s etup p rocedures 38 m86 s ecurity i nstallation g uide non-quick start procedures or settings the options described below do not pertain to the quick start setup process. Sr patch level when the sr patch level option is selected, “security reporter” and th...
Page 47: Lcd Options Menu
I nstall the s erver s tep 1b: lcd p anel s etup p rocedures m86 s ecurity i nstallation g uide 39 lcd options menu when “lcd options >” is selected, the following menu items display on the screen: heartbeat, backlight, lcd controls >. Make a selection from the menu, and press the checkmark / enter ...
Page 48: Bandwidth Management
I nstall the s erver s tep 2: p hysically c onnect the u nit to the n etwork 40 m86 s ecurity i nstallation g uide step 2: physically connect the unit to the network now that your sr network parameters are set, you can physically connect the unit to your network. This step requires a standard cat-5e...
Page 49
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline m86 s ecurity i nstallation g uide 41 step 3: access the sr and its applications online next you will access the sr and its applications online. For this step you will need your network administrator to provide you the follow...
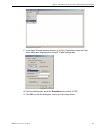
Page 50
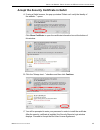
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline 42 m86 s ecurity i nstallation g uide accept the security certificate in firefox a. If using a firefox browser, in the page “this connection is untrusted,” click the option i understand the risks: b. In the next set of instru...
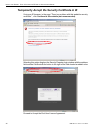
Page 51
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline m86 s ecurity i nstallation g uide 43 c. In the add security exception window, click get certificate and wait a few seconds until the security certificate is obtained by the server. D. With the checkbox permanently store this...
Page 52
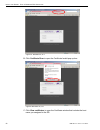
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline 44 m86 s ecurity i nstallation g uide temporarily accept the security certificate in ie if using an ie browser, in the page “there is a problem with this website's security certificate.”, click continue to this website (not r...
Page 53
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline m86 s ecurity i nstallation g uide 45 accept the security certificate in safari a. If using a safari browser, the pop-up window "safari can't verify the identity of the website..." opens: click show certificate to open the ce...
Page 54
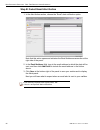
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline 46 m86 s ecurity i nstallation g uide accept the end user license agreement a. In the security reporter login window, enter your username and password, and then click login to proceed: you may be prompted to accept a security...
Page 55
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline m86 s ecurity i nstallation g uide 47 log in to the security reporter wizard a. In the username field of the login window, type in the username specified in the configure setup wizard user screen of the quick start setup proc...
Page 56
I nstall the s erver s tep 3: a ccess the sr and its a pplications o nline 48 m86 s ecurity i nstallation g uide c. Enter the password to be used with that username, and enter the same pass- word again in the confirm password field. Enter bandwidth range a. Enter the bandwidth ip address range the s...
Page 57
I nstall the s erver s tep 4: g enerate ssl c ertificate m86 s ecurity i nstallation g uide 49 step 4: generate ssl certificate generate a self-signed certficate for the sr this step requires you to generate a self-signed certificate so your browser will recognize the sr as an accepted device. A. In...
Page 58
I nstall the s erver s tep 4: g enerate ssl c ertificate 50 m86 s ecurity i nstallation g uide c. Organizational unit name - name of your department, such as administration. D. Locality (city) - name of your organization’s city or principality, such as orange. E. State or province name - full name o...
Page 59
I nstall the s erver s tep 4: g enerate ssl c ertificate m86 s ecurity i nstallation g uide 51 ie security certificate installation procedures accept the security certificate in ie go to the appropriate sub-section if using the following windows operating system and ie browser: • windows xp or vista...
Page 60
I nstall the s erver s tep 4: g enerate ssl c ertificate 52 m86 s ecurity i nstallation g uide figure a2: windows xp, ie 7 b. Click certificate error to open the certificate invalid pop-up box: figure b: windows xp, ie 7 c. Click view certificates to open the certificate window that includes the hos...
Page 61
I nstall the s erver s tep 4: g enerate ssl c ertificate m86 s ecurity i nstallation g uide 53 figure c: windows xp, ie 7 d. Click install certificate... To launch the certificate import wizard: figure d: windows xp, ie 7 e. Click next > to display the certificate store page: figure e: windows xp, i...
Page 62
I nstall the s erver s tep 4: g enerate ssl c ertificate 54 m86 s ecurity i nstallation g uide f. Choose the option “place all certificates in the following store” and then click browse... To open the select certificate store pop-up box: figure f: windows xp, ie 7 g. Choose “trusted root certificati...
Page 63
I nstall the s erver s tep 4: g enerate ssl c ertificate m86 s ecurity i nstallation g uide 55 now that the security certificate is installed, you will need to map the sr’s ip address to its host name. Proceed to map the sr’s ip address to the server’s host name. Windows 7 with ie 8 a. If using an i...
Page 64
I nstall the s erver s tep 4: g enerate ssl c ertificate 56 m86 s ecurity i nstallation g uide now that the security certificate is installed, you will need to map the sr’s ip address to its host name. Proceed to map the sr’s ip address to the server’s host name. Map the sr’s ip address to the serve...
Page 65
I nstall the s erver s tep 4: g enerate ssl c ertificate m86 s ecurity i nstallation g uide 57 c. Enter a line in the hosts file with the sr’s ip address and its host name—the latter entered during the configure host name screen of the quick start setup procedures (step 1a), or the host name screen ...
Page 66: Add A Web Filter Device
I nstall the s erver s tep 5: a dd w eb f ilter , swg to d evice r egistry 58 m86 s ecurity i nstallation g uide step 5: add web filter, swg to device registry before you begin configuring the web filter and/or swg to send logs to the sr, you will need to add the web filter/swg in the sr’s device re...
Page 67: Add An Swg Device
I nstall the s erver s tep 5: a dd w eb f ilter , swg to d evice r egistry m86 s ecurity i nstallation g uide 59 add an swg device a. At the bottom of the device registry panel, click new policy server to open the new policy server pop-up window: the following information displays and cannot be edit...
Page 68: Web Filter Setup
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers 60 m86 s ecurity i nstallation g uide step 6: set up web filter, swg log transfers this step can be performed any time during sr setup, but must be completed in order for the sr to receive logs from the web filter and/or swg. W...
Page 69
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers m86 s ecurity i nstallation g uide 61 web filter log transfer verification you can see if log files have transferred by following these steps in the sr: a. Access the system configuration administrator console. B. Go to the dat...
Page 70
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers 62 m86 s ecurity i nstallation g uide set self-monitoring a. In the sr report manager navigation toolbar, select administration > system configuration to display the server status panel screen of the system config- uration admi...
Page 71: Swg Setup
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers m86 s ecurity i nstallation g uide 63 swg setup setup instructions differ depending on the swg software version to be used with the sr (10.0 or 9.2.5). Important: if this sr being configured will be receiving logs from multiple...
Page 72
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers 64 m86 s ecurity i nstallation g uide • password: type in the password you entered for the swg in the device registry. Note: be sure “extended format” is selected for archive format, and the log archive scheduling frame specifi...
Page 73
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers m86 s ecurity i nstallation g uide 65 swg configuration for software version 9.2.5 configure swg to send logs to the sr a. Access the swg user interface. B. Navigate to administration > system settings > m86 devices. C. In the ...
Page 74
I nstall the s erver s tep 6: s et up w eb f ilter , swg l og t ransfers 66 m86 s ecurity i nstallation g uide policy settings a. Navigate to policies > default policy settings and verify if the settings in the enable emergency policy frame and default policy values frame are the ones you wish to us...
Page 75: Single Sign-On Access
I nstall the s erver s ingle s ign -o n a ccess , d efault u sername /p assword m86 s ecurity i nstallation g uide 67 single sign-on access, default username/password single sign-on access if using a web filter, the single sign-on (sso) access feature is available for the global administrator accoun...
Page 76: Onclusion
C onclusion s ingle s ign -o n a ccess , d efault u sername /p assword 68 m86 s ecurity i nstallation g uide c onclusion congratulations; you have completed the sr installation procedures. Now that the sr server is set up on your network you will need to be sure the web-access logging device you are...
Page 77: Est
B est r eporting p ractices m86 s ecurity i nstallation g uide 69 b est r eporting p ractices this best reporting practices section is provided to help you get started using the report manager user interface. The main areas of focus in this section are creating basic reports, real time reporting, an...
Page 78
B est r eporting p ractices r eport m anager u sage s cenarios 70 m86 s ecurity i nstallation g uide report manager usage scenarios this collection of reporting scenarios is designed to help you use the report manager to create typical snapshots of end user internet activity. Each scenario is follow...
Page 79
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 71 this report shows the top 20 categories that were most frequently visited by users yesterday. Review the list of categories in this canned report. In a later step you will need to select the category...
Page 80
B est r eporting p ractices r eport m anager u sage s cenarios 72 m86 s ecurity i nstallation g uide note that this drill down report view has been generated for today’s activity by default. To continue this investigation using data from yesterday’s summary report, you must create a new report from ...
Page 81
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 73 in the security reporter user guide index, see: • how to: create a new report from the current report view step d: create a double-break report with two sets of criteria 1. To continue this exercise,...
Page 82
B est r eporting p ractices r eport m anager u sage s cenarios 74 m86 s ecurity i nstallation g uide for the last step of this exercise, you will select a user from the current summary drill down report view and then drill down further to see which urls that user visited, thereby creating a detail d...
Page 83
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 75 ii. Double-break report and export report exercise in this exercise you will learn how to display only the top 10 records of a summary drill down double-break report view, export that report view in ...
Page 84
B est r eporting p ractices r eport m anager u sage s cenarios 76 m86 s ecurity i nstallation g uide note that urls/ip addresses of sites users visited in the category now display in the first column of the modified report view, instead of category names. In the security reporter user guide index, s...
Page 85
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 77 step c: export the report view in the pdf output format 1. To export the current report view in the pdf format, at the bottom of the report view click export to open the export pop-up window: by defa...
Page 86
B est r eporting p ractices r eport m anager u sage s cenarios 78 m86 s ecurity i nstallation g uide 3. Print or save the pdf file using available tools or icons in the pdf file window, or close the pdf file. In the security reporter user guide index, see: • how to: export a summary drill down repor...
Page 87
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 79 3. Choose the save and schedule option from the “save” options at the bottom of the window. The three “save” options are as follows: • save and schedule - this option lets you save criteria from the ...
Page 88
B est r eporting p ractices r eport m anager u sage s cenarios 80 m86 s ecurity i nstallation g uide in the security reporter user guide index, see: • how to: schedule a report to run you have now learned how to save a report and schedule a recurring event for running this report. Reports created fo...
Page 89
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 81 in the security reporter user guide index, see: • how to: add a custom category group step b: run a report for a specified custom category group 1. To create a report for a custom category group, cho...
Page 90
B est r eporting p ractices r eport m anager u sage s cenarios 82 m86 s ecurity i nstallation g uide v. Create a custom user group and generate reports in addition to running reports for various custom category groups, you might want to create one or more custom user groups and run reports for these...
Page 91
B est r eporting p ractices r eport m anager u sage s cenarios m86 s ecurity i nstallation g uide 83 3. Type in the group name and check the box(es) corresponding to “patterns”, “ip ranges”, and/or “single users/exclude” to activate the frames in the section below. For this example, select “ip range...
Page 92
B est r eporting p ractices r eal t ime r eports u sage s cenarios 84 m86 s ecurity i nstallation g uide real time reports usage scenarios this collection of setup and usage scenarios is designed to help you understand and use basic tools in the console for enforcing your internet usage policy. Each...
Page 93
B est r eporting p ractices r eal t ime r eports u sage s cenarios m86 s ecurity i nstallation g uide 85 • overall ranking - view details about current gauge activity for all end users affecting gauges • lockouts - prevent the end user from accessing specified urls, the internet, or the entire netwo...
Page 94
B est r eporting p ractices r eal t ime r eports u sage s cenarios 86 m86 s ecurity i nstallation g uide note: the gauge ranking panel is also accessible by right-clicking a dashboard gauge and then selecting view gauge ranking from the pop-up menu. 2. Find the library category with the highest scor...
Page 95
B est r eporting p ractices r eal t ime r eports u sage s cenarios m86 s ecurity i nstallation g uide 87 step b: investigate a user’s activity in a specified gauge 1. To find out which urls the top end user visited in the high-scoring library cate- gory, select the category with the highest score an...
Page 96
B est r eporting p ractices r eal t ime r eports u sage s cenarios 88 m86 s ecurity i nstallation g uide step c: investigate the user’s internet activity in other gauges 1. To find out which other gauges the same user is currently affecting, return to the gauge ranking table by going to the lower le...
Page 97: III. Create A Gauge Exercise
B est r eporting p ractices r eal t ime r eports u sage s cenarios m86 s ecurity i nstallation g uide 89 4. To find out which urls the user is viewing in a particular library category, choose the category from the list, and then click the url in the urls list. In the security reporter user guide ind...
Page 98
B est r eporting p ractices r eal t ime r eports u sage s cenarios 90 m86 s ecurity i nstallation g uide in the security reporter user guide index, see: • how to: access the add/edit gauges panel step b: add a url gauge 1. Click new gauge at the bottom left of the panel to open the url gauge panel: ...
Page 99
B est r eporting p ractices r eal t ime r eports u sage s cenarios m86 s ecurity i nstallation g uide 91 5. From the available user groups list, select the user group to highlight it. 6. Click add > to move the user group to the assigned user groups list box. 7. After adding users, click save at the...
Page 100
B est r eporting p ractices r eal t ime r eports u sage s cenarios 92 m86 s ecurity i nstallation g uide now that you know the basics of creating a gauge, you will soon be able to create and use gauges to monitor various groups of users who frequent urls in library categories you wish to restrict, a...
Page 101
B est r eporting p ractices r eal t ime r eports u sage s cenarios m86 s ecurity i nstallation g uide 93 4. Type in the alert name to be used for the alert that will be delivered to the group administrator. 5. Specify the user threshold ceiling of gauge activity that will trigger the alert. The defa...
Page 102
B est r eporting p ractices r eal t ime r eports u sage s cenarios 94 m86 s ecurity i nstallation g uide step b: select email alert action 1. In the alert action section, choose the “email” alert notification option. Note that this action opens and activates the email addresses accordion at the righ...
Page 103
B est r eporting p ractices r eal t ime r eports u sage s cenarios m86 s ecurity i nstallation g uide 95 step c: receiving an email alert when an end user’s activity in a gauge reaches the threshold limit established for an alert, it triggers an alert notification. If the email alert option was sele...
Page 104
B est r eporting p ractices s ecurity r eports u sage s cenarios 96 m86 s ecurity i nstallation g uide security reports usage scenarios this collection of reporting scenarios is tailored towards familiarizing you with tools for generating, exporting, saving, and scheduling security reports. Each sce...
Page 105
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 97 step b: navigate to the security policy violations report click the security policy violations tab to display the the security policy viola- tions report view: this report provides information on e...
Page 106
B est r eporting p ractices s ecurity r eports u sage s cenarios 98 m86 s ecurity i nstallation g uide step d: navigate to the rule transactions report click the rule transactions tab to display the rule transactions report view: this report includes each instance in which an end user triggered a th...
Page 107
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 99 • click this icon to re-display the top six graphs and table of records (the default view) • click this icon to display the table of records only: in the security reporter user guide index, see: • ...
Page 108
B est r eporting p ractices s ecurity r eports u sage s cenarios 100 m86 s ecurity i nstallation g uide ii. Create a customized security report once you become familiar with the basic four security reports, you may want to create your own customized reports. This exercise will show you two different...
Page 109
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 101 for a traffic analysis or rule transactions report, you can narrow your search result by including filters: a. Click >> filters at the bottom right of the panel to display the filter results panel...
Page 110
B est r eporting p ractices s ecurity r eports u sage s cenarios 102 m86 s ecurity i nstallation g uide exercise b: use the report wizard to run a custom report 1. Navigate to reports > security reports > report wizard to display the secu- rity report wizard panel where you will need to specify crit...
Page 111
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 103 iii. Export a security report in this exercise you will learn how to export the current security report view in the pdf format by selecting one of two export options. Step a: specify records to in...
Page 112
B est r eporting p ractices s ecurity r eports u sage s cenarios 104 m86 s ecurity i nstallation g uide 2. Specify the delivery method for the email address: “to” (default), “bcc”, or “cc”. 3. Enter the subject for the email message. 4. If you wish, enter text to be included in the body of the messa...
Page 113: IV. Save A Security Report
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 105 in the security reporter user guide index, see: • how to: export a security report iv. Save a security report a security report can be saved only by using the “report settings” save option. Step a...
Page 114
B est r eporting p ractices s ecurity r eports u sage s cenarios 106 m86 s ecurity i nstallation g uide step b: specify criteria in the report details frame 1. In the report details frame, type in the report name. 2. Specify the report time span by choosing one of two options: • predefined ranges - ...
Page 115
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 107 step d: populate the email settings frame 1. In the email settings frame, enter at least one email address and then click add to include the email address in the list box below. 2. Specify the del...
Page 116
B est r eporting p ractices s ecurity r eports u sage s cenarios 108 m86 s ecurity i nstallation g uide 2. In the report details frame, type in the report name. 3. Specify the report time span by choosing one of two options: • predefined ranges - if choosing this option, make a selection from the pu...
Page 117
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 109 a. Click >> filters at the bottom right of the panel to display the filter results panel. B. Choose a filter type from an available accordion (policies, rules, action, content type) and indicate c...
Page 118
B est r eporting p ractices s ecurity r eports u sage s cenarios 110 m86 s ecurity i nstallation g uide exercise b: use the wizard to create and schedule reports 1. Navigate to reports > security reports > report wizard to open the security report wizard panel: 2. In the report details frame, type i...
Page 119
B est r eporting p ractices s ecurity r eports u sage s cenarios m86 s ecurity i nstallation g uide 111 access the report schedule panel to access the report schedule panel that includes all productivity and security reports scheduled to run, navigate to reports > report schedule: reports scheduled ...
Page 120
B est r eporting p ractices s ecurity r eports u sage s cenarios 112 m86 s ecurity i nstallation g uide the following information displays in this frame: name assigned to the scheduled event; selected report to run; interval when to run the report; day of the week the report will run if the report i...
Page 121: Mportant
I mportant i nformation about using the sr in the e valuation m ode e valuation m ode p op -u p m86 s ecurity i nstallation g uide 113 i mportant i nformation about using the sr in the e valuation m ode evaluation mode pop-up when evaluating the sr in the evaluation mode, the sr status pop-up box op...
Page 122
I mportant i nformation about using the sr in the e valuation m ode r eport m anager s erver i nformation p anel 114 m86 s ecurity i nstallation g uide report manager server information panel in the server information window, the mode section displays “evaluation - max data storage ‘x’ weeks”. The e...
Page 123: Led I
Led i ndicators and b uttons f ront c ontrol p anels on 500, 700 and 730 m odels m86 s ecurity i nstallation g uide 115 led i ndicators and b uttons front control panels on 500, 700 and 730 models control panel buttons, icons, and led indicators display on the right side of a 500, 700 and 730 model’...
Page 124
Led i ndicators and b uttons r ear p anel on the 700 and 730 m odel 116 m86 s ecurity i nstallation g uide rear panel on the 700 and 730 model power supplies (led indicators) – the power supplies are located at the right on the rear of the chassis. An led indicator is located above each of the power...
Page 125: Egulatory
R egulatory s pecifications and d isclaimers d eclaration of the m anufacturer or i mporter m86 s ecurity i nstallation g uide 117 r egulatory s pecifications and d isclaimers the information in this section pertains to sr models 500, 700, and 730. Declaration of the manufacturer or importer safety ...
Page 126: Ec Declaration of Conformity
R egulatory s pecifications and d isclaimers d eclaration of the m anufacturer or i mporter 118 m86 s ecurity i nstallation g uide ec declaration of conformity european community directives requirement (ce) declaration of conformity manufacturer’s name: m86 security 828 w. Taft avenue orange, ca 928...
Page 127: Ppendix
A ppendix a: f ibre c hannel c onnected s torage d evice p reliminary s etup p rocedures m86 s ecurity i nstallation g uide 119 a ppendix a: f ibre c hannel c onnected s torage d evice this appendix pertains to the installation of the optional nas (fibre channel connected storage device or “san”) un...
Page 128: Rack Mount The Server
A ppendix a: f ibre c hannel c onnected s torage d evice p reliminary s etup p rocedures 120 m86 s ecurity i nstallation g uide rack mount the server rack mount components the following items are needed to install rails for rack mounting: • 1 slide kit and mounting hardware • 1 pair accuride slide r...
Page 129
A ppendix a: f ibre c hannel c onnected s torage d evice p reliminary s etup p rocedures m86 s ecurity i nstallation g uide 121 step 1 remove inner slide rail as shown. Press down on latch to release. Step 2 attach inner slide rail to chassis using 3 screws as shown. Note: when attaching the extende...
Page 130
A ppendix a: f ibre c hannel c onnected s torage d evice p reliminary s etup p rocedures 122 m86 s ecurity i nstallation g uide step 4 attach left and right front (short) extended brackets to the outer rail using 2 screws, 2 washers, and 2 nuts for each bracket. Note: make sure the flange is on the ...
Page 131: Install The Unit
A ppendix a: f ibre c hannel c onnected s torage d evice i nstall the u nit m86 s ecurity i nstallation g uide 123 install the unit link the sr unit with the fibre channel connected device this step is a continuation from the storage device setup (for attached storage units) portion of step 1a or 1b...
Page 132
A ppendix a: f ibre c hannel c onnected s torage d evice i nstall the u nit 124 m86 s ecurity i nstallation g uide f. Plug the loose ends of the ac power cords into a power source with an appropriate rating. It is strongly suggested you use an uninterruptible power supply. Warning: be sure all drive...
Page 133: Physical Components
A ppendix a: f ibre c hannel c onnected s torage d evice p hysical c omponents m86 s ecurity i nstallation g uide 125 physical components.
Page 134: Led Display
A ppendix a: f ibre c hannel c onnected s torage d evice p hysical c omponents 126 m86 s ecurity i nstallation g uide led display temperature and ventilation status when the led is green, the blowers are operating at an acceptable rpm, and the internal temperature sensors are within accept- able lim...
Page 135: Ppendix
A ppendix b: o ptional e thernet t ap i nstallation p reliminary s etup p rocedures m86 s ecurity i nstallation g uide 127 a ppendix b: o ptional e thernet t ap i nstallation this appendix pertains to the optional installation of the ethernet tap unit for band- width monitoring. Note: in order to mo...
Page 136
A ppendix b: o ptional e thernet t ap i nstallation i nstall the e thernet t ap u nit 128 m86 s ecurity i nstallation g uide diagram showing ethernet tap installation on the network if the designated web filter/swg has not yet been installed, disregard this sub- step and proceed to sub-step c. C. Us...
Page 137: Ndex
M86 s ecurity i nstallation g uide 129 i ndex a access the report schedule panel 111 add to report schedule 79 b boot up 300 series server 116 500, 700 series server 115 c change quick start password 32 configure setup wizard user 37 create a customized security report 100 create a gauge 89 create a...
Page 138
I ndex 130 m86 s ecurity i nstallation g uide lvd 117 m modify report 76 n nas 22 , 34 , 119 p ping the sr 41 power supply precautions 18 q quick start menu 28 r rack setup precautions 8 , 120 raid 126 reboot 32 , 38 , 124 300 series server 116 500, 700 series server 115 report for a custom user gro...
Page 139
I ndex m86 s ecurity i nstallation g uide 131 wizard installation procedures 67.
Page 140
I ndex 132 m86 s ecurity i nstallation g uide.
Page 142
M86 security corporate headquarters (usa): 828 west taft avenue orange, ca 92865-4232 • tel: 714.282.6111 or 888.786.7999 fax: 714.282.6116 (sales/technical support) • 714.282.6117 (general office).