- DL manuals
- M86 Security
- Network Hardware
- M86 Web Filter
- User Manual
M86 Security M86 Web Filter User Manual
Summary of M86 Web Filter
Page 1
M86 web filter user guide for authentication software version: 4.0.10 document version: 06.08.10
Page 2: M86 W
Ii m86 s ecurity u ser g uide m86 w eb f ilter a uthentication u ser g uide © 2010 m86 security all rights reserved. 828 w. Taft ave., orange, ca 92865, usa version 1.01, published june 2010 for software release 4.0.10 printed in the united states of america this document may not, in whole or in par...
Page 3: Ontents
M86 s ecurity u ser g uide iii c ontents c hapter 1: i ntroduction .............................................. 1 about this user guide ................................................................ 1 how to use this user guide ....................................................... 2 convention...
Page 4: 2: N
C ontents iv m86 s ecurity u ser g uide web filter authentication options . ............................................ 25 authentication solution compatibility .............................................. 26 authentication system deployment options ................................... 27 ports fo...
Page 5: 3: Ldap A
C ontents m86 s ecurity u ser g uide v option 3 ........................................................................ 62 common customization ........................................................... 63 enable, disable features ..................................................... 64 authentica...
Page 6: 4: M
C ontents vi m86 s ecurity u ser g uide apply a filtering rule to a profile .............................................. 104 delete a rule ........................................................................... 105 specify a group’s filtering profile priority .....................................
Page 7: 6: T
C ontents m86 s ecurity u ser g uide vii step 8: attempt to access web content . ................................ 149 test net use based authentication settings ................................... 151 activate authentication on the network ............................... 152 activate web-based authe...
Page 8
C ontents viii m86 s ecurity u ser g uide tier 2, tier 3: web-based authentication ...................................... 183 tier 1: single sign-on authentication .................................. 184 net use based authentication process .......................................... 184 re-authentica...
Page 9: B: O
C ontents m86 s ecurity u ser g uide ix novell edirectory servers ........................................................ 208 client workstations . ................................................................ 209 novell clients ......................................................................
Page 10: C: Ldap S
C ontents x m86 s ecurity u ser g uide export a novell ssl certficate .............................................. 255 obtain a sun one ssl certificate ......................................... 257 a ppendix c: ldap s erver c ustomizations ............. 258 openldap server scenario ..................
Page 11: F: G
C ontents m86 s ecurity u ser g uide xi set up pop-up blocking ................................................................. 275 use the internet options dialog box ....................................... 275 use the ie toolbar . .....................................................................
Page 12
C ontents xii m86 s ecurity u ser g uide.
Page 13: Hapter
C hapter 1: i ntroduction a bout this u ser g uide m86 s ecurity u ser g uide 1 c hapter 1: i ntroduction the m86 web filter authentication user guide contains information about setting up authentication on the network. About this user guide this user guide addresses the network administrator desig-...
Page 14: How to Use This User Guide
C hapter 1: i ntroduction h ow to u se this u ser g uide 2 m86 s ecurity u ser g uide izations to make on specified ldap servers; filtering profile file components and setup; tips on how to override pop-up windows with pop-up blocker software installed; a glossary on authentication terms, and an ind...
Page 15: Terminology
C hapter 1: i ntroduction h ow to u se this u ser g uide m86 s ecurity u ser g uide 3 terminology the following terms are used throughout this user guide. Sample images (not to scale) are included for each item. • alert box - a message box that opens in response to an entry you made in a dialog box,...
Page 16
C hapter 1: i ntroduction h ow to u se this u ser g uide 4 m86 s ecurity u ser g uide • frame - a boxed-in area in a dialog box, window, or screen that includes a group of objects such as fields, text boxes, list boxes, buttons, radio buttons, check- boxes, and/or tables. Objects within a frame belo...
Page 17
C hapter 1: i ntroduction h ow to u se this u ser g uide m86 s ecurity u ser g uide 5 • pop-up box or pop-up window - a box or window that opens after you click a button in a dialog box, window, or screen. This box or window may display infor- mation, or may require you to make one or more entries. ...
Page 18
C hapter 1: i ntroduction h ow to u se this u ser g uide 6 m86 s ecurity u ser g uide • sub-topic - a subset of a main topic that displays as a menu item for the topic. The menu of sub-topics opens when a perti- nent topic link in the left panel—the navigation panel—of a screen is clicked. If a sub-...
Page 19
C hapter 1: i ntroduction h ow to u se this u ser g uide m86 s ecurity u ser g uide 7 • tree - a tree displays in the naviga- tion panel of a screen, and is comprised of a hierarchical list of items. An entity associated with a branch of the tree is preceded by a plus (+) sign when the branch is col...
Page 20: Filtering Elements
C hapter 1: i ntroduction f iltering e lements 8 m86 s ecurity u ser g uide filtering elements filtering operations include the following elements: groups, filtering profiles and their components, and rules for filtering. Group types in the policy section of the administrator console, group types ar...
Page 21: Ip Groups
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 9 ip groups the ip group type is represented in the tree by the ip icon . A master ip group is comprised of sub-group members and/or individual ip members . The global administrator adds master ip groups, adds and maintains ov...
Page 22: Ldap Domain Groups
C hapter 1: i ntroduction f iltering e lements 10 m86 s ecurity u ser g uide ldap domain groups an ldap (lightweight directory access protocol) domain on a network server is comprised of ldap groups and their associated members (users), derived from profiles on the network’s authentication server. T...
Page 23: Filtering Profile Types
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 11 filtering profile types a filtering profile is used by all users who are set up to be filtered on the network. This profile consists of rules that dictate whether a user has access to a specified web site or service on the ...
Page 24
C hapter 1: i ntroduction f iltering e lements 12 m86 s ecurity u ser g uide • ldap member filtering profile - used by an ldap group member. • ldap container filtering profile - used by an ldap container in an ldap domain. • ldap time profile - used by an ldap entity at a speci- fied time. Other fil...
Page 25: Static Filtering Profiles
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 13 static filtering profiles static filtering profiles are based on fixed ip addresses and include profiles for master ip groups and their members. Master ip group filtering profile the master ip group filtering profile is cre...
Page 26: Active Filtering Profiles
C hapter 1: i ntroduction f iltering e lements 14 m86 s ecurity u ser g uide active filtering profiles active filtering profiles include the global group profile, ldap authentication profile, override account profile, time profile, and lock profile. Global filtering profile the global filtering prof...
Page 27: Override Account Profile
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 15 override account profile if any user needs access to a specified url that is set up to be blocked, the global administrator or group administrator can create an override account for that user. This account grants the user a...
Page 28: Filtering Profile Components
C hapter 1: i ntroduction f iltering e lements 16 m86 s ecurity u ser g uide filtering profile components filtering profiles are comprised of the following compo- nents: • library categories - used when creating a rule, minimum filtering level, or filtering profile for the global group or any entity...
Page 29: Library Categories
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 17 library categories a library category contains a list of web site addresses and keywords for search engines and urls that have been set up to be blocked or white listed. Library categories are used when creating a rule, the...
Page 30: Service Ports
C hapter 1: i ntroduction f iltering e lements 18 m86 s ecurity u ser g uide service ports service ports are used when setting up filter segments on the network (the range of ip addresses/netmasks to be detected by the web filter), the global (default) filtering profile, and the minimum filtering le...
Page 31: Filter Settings
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 19 note: if the minimum filtering level is not set up, global (default) filtering settings will apply instead. If an override account is established at the ip group level for a member of a master ip group, filtering settings m...
Page 32
C hapter 1: i ntroduction f iltering e lements 20 m86 s ecurity u ser g uide • filter - if a service port is given a filter setting, that port will use filter settings created for library categories (block or open settings) to determine whether users should be denied or allowed access to that port •...
Page 33: Filtering Rules
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 21 filtering rules individual user profiles - a user in an ldap domain can have only one individual profile set up per domain. Filtering levels applied: 1. The global (default) filtering profile applies to any user under the f...
Page 34
C hapter 1: i ntroduction f iltering e lements 22 m86 s ecurity u ser g uide 6. For ldap users, if a user is authenticated, settings for the user’s group or individual profile from the ldap domain are applied and take precedence over any ip profile. A. If the user belongs to more than one group in a...
Page 35
C hapter 1: i ntroduction f iltering e lements m86 s ecurity u ser g uide 23 8. An override account profile takes precedence over a tar lockout profile. This account may override the minimum filtering level—if the override account was set up in the master ip group tree, and the global adminis- trato...
Page 36: Authentication Solutions
C hapter 1: i ntroduction a uthentication s olutions 24 m86 s ecurity u ser g uide authentication solutions ldap authentication protocol the web filter supports the authentication protocol light- weight directory access protocol (ldap). Ldap authentication supports all versions of ldap, such as micr...
Page 37
C hapter 1: i ntroduction a uthentication s olutions m86 s ecurity u ser g uide 25 web filter authentication options depending on the setup of your network, any of the following authentication options can be enabled to ensure the end user is authenticated when logging into his/her workstation: m86 a...
Page 38
C hapter 1: i ntroduction a uthentication s olutions 26 m86 s ecurity u ser g uide authentication solution compatibility below is a chart representing the authentication solution compatibility for a single user: key: • n/a = not applicable • n/r = not recommended tier1 net use tier 2 time based tier...
Page 39
C hapter 1: i ntroduction a uthentication s olutions m86 s ecurity u ser g uide 27 authentication system deployment options below is a chart representing authentication system deploy- ment options on a network: authentication system single sign-on (sso) force authentication sun one openldap communig...
Page 40
C hapter 1: i ntroduction a uthentication s olutions 28 m86 s ecurity u ser g uide ports for authentication system access the following ports should be used for authentication system access: type no. Function tcp 8081 used between the web filter’s transmitting interface and the ssl block page for ti...
Page 41: Configuration Procedures
C hapter 1: i ntroduction a uthentication s olutions m86 s ecurity u ser g uide 29 configuring web filter for authentication configuration procedures when configuring the web filter for authentication, settings must be made in system and policy windows in the admin- istrator console. Notes: if the n...
Page 42
C hapter 1: i ntroduction a uthentication s olutions 30 m86 s ecurity u ser g uide the entries made in this window will vary depending on whether you are using the invisible mode, or the router or firewall mode. The lan1 and lan2 ip addresses usually should be in a different subnet. • if using the i...
Page 43
C hapter 1: i ntroduction a uthentication s olutions m86 s ecurity u ser g uide 31 4. Select “authentication” from the navigation panel, and then select “authentication settings” from the pop-up menu. In the settings frame, enter general configuration settings for the web filter such as ip address e...
Page 44: Policy Section
C hapter 1: i ntroduction a uthentication s olutions 32 m86 s ecurity u ser g uide group administrators will later be assigned to manage entities (nodes) in the ldap branch of the policy tree. Policy section in the policy section of the administrator console, choose ldap, and then do the following: ...
Page 45: Hapter
C hapter 2: n etwork s etup e nvironment r equirements m86 s ecurity u ser g uide 33 c hapter 2: n etwork s etup environment requirements workstation requirements administrator system requirements for the administrator include the following: • windows xp, vista, or 7 operating system running: • inte...
Page 46: End User
C hapter 2: n etwork s etup e nvironment r equirements 34 m86 s ecurity u ser g uide end user system requirements for the end user include the following: • windows xp, vista, or 7 operating system running: • internet explorer (ie) 7.0 or 8.0 • firefox 3.5 • macintosh os x version 10.5 or 10.6 runnin...
Page 47
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 35 set up the network for authentication the first settings for authentication must be made in the system section of the console in the following windows: operation mode, lan settings, enable/disable auth...
Page 48: Specify The Operation Mode
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 36 m86 s ecurity u ser g uide specify the operation mode click mode and select operation mode from the pop-up menu to display the operation mode window: fig. 2-1 operation mode window the entries made in this window will vary depen...
Page 49
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 37 3. In the block page device frame: • if using the invisible mode, select “lan2”. • if using the router or firewall mode, select “lan1”. If using the invisible mode, the block page delivery method frame...
Page 50: Invisible Mode
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 38 m86 s ecurity u ser g uide specify the subnet mask, ip address(es) click network and select lan settings from the pop-up menu to display the lan settings window: fig. 2-2 lan settings window the entries made in this window will ...
Page 51: Router Or Firewall Mode
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 39 router or firewall mode 1. Enter the following information: • in the lan1 ip field of the ip/mask setting frame, enter the ip address and specify the corresponding subnet of the “lan1” network interfac...
Page 52
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 40 m86 s ecurity u ser g uide enable authentication, specify criteria 1. Click authentication and select enable/disable authenti- cation from the pop-up menu to display the enable/ disable authentication window: 2. Click enable to ...
Page 53
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 41 4. Enable any of the following authentication options, as pertinent to your environment: • if using ldap authentication and workstation profiles, click “on” in the map workstation name across all domai...
Page 54: Net Use Based Authentication
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 42 m86 s ecurity u ser g uide feature, turn “on” the ad agent, and then specify settings for administrator computers authorized to configure the ad agent via the active directory agent console. Download and install the ad agent (dc...
Page 55: Web-Based Authentication
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 43 web-based authentication choose either tier 2 or tier 3 if web-based authentication will be used. Note: if selecting either tier 2 or tier 3, please be informed that in an organization with more than 5...
Page 56
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 44 m86 s ecurity u ser g uide tier 3: use persistent logins via a java applet – choose this option if using ldap authentication, and you want the user to maintain a persistent network connection. This option opens a profile window ...
Page 57
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 45 3. To ensure that end-users are using the most current version of jre, choose the method for distributing the current version to their workstations: “m86 automatically distributes jre during user login...
Page 58
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 46 m86 s ecurity u ser g uide enter network settings for authentication 1. Click authentication and select authentication settings from the pop-up menu to display the authentication settings window: fig. 2-6 authentication settings...
Page 59
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 47 warning: if the ip address entered here is not in the same subnet as this web filter, the net use connection will fail. 4. From the nic device to use for authentication pull- down menu: • if using the ...
Page 60: Create An Ssl Certificate
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 48 m86 s ecurity u ser g uide create an ssl certificate authentication ssl certificate should be used if web-based authentication will be deployed on the web filter. Using this feature, a secured sockets layer (ssl) self-signed cer...
Page 61
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 49 create, download a self-signed certificate 1. On the self signed certificate tab, click create self signed certificate to generate the ssl certificate. 2. Click the download/view/delete certificate tab...
Page 62
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 50 m86 s ecurity u ser g uide once the certificate is saved to your workstation, it can be distributed to client workstations for users who need to be authenticated. Tip: click delete certificate to remove the certificate from the ...
Page 63
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 51 fig. 2-10 create csr pop-up window the common name (host name) field should automat- ically be populated with the host name. This field can be edited, if necessary. 3. Enter your email address. 4. Ente...
Page 64
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 52 m86 s ecurity u ser g uide upload a third party certificate 1. In the third party certificate tab, click upload certifi- cate to open the upload signed ssl certificate for web filter pop-up window: fig. 2-11 upload signed ssl ce...
Page 65
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 53 3. Select the file to be uploaded. 4. Click upload file to upload this file to the web filter. 5. Click ok in the message dialog box to confirm the upload and to close the dialog box. Download a third ...
Page 66: Specify Block Page Settings
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 54 m86 s ecurity u ser g uide specify block page settings click control and select block page authentication from the pop-up menu to display the block page authentication window: fig. 2-13 block page authentication window block pag...
Page 67
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 55 • override account - select this option if any user has an override account, allowing him/her to access urls set up to be blocked at the global or ip group level. Tip: multiple options can be selected ...
Page 68: Block Page
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 56 m86 s ecurity u ser g uide block page when a user attempts to access internet content set up to be blocked, the block page displays on the user’s screen: fig. 2-14 block page notes: see block page customization for information o...
Page 69: User/machine Frame
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 57 user/machine frame by default, the following data displays in the user/machine frame: • user/machine field - the username displays for the ldap user. This field is blank for the ip group user. • ip fie...
Page 70: Optional Links
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 58 m86 s ecurity u ser g uide optional links by default, these links are included in the block page under the following conditions: • for further options, click here. - this phrase and link is included if any option was selected at...
Page 71: Options Page
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 59 options page the options page displays when the user clicks the following link in the block page: for further options, click here. Fig. 2-15 options page the following items previously described for th...
Page 72: Option 1
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 60 m86 s ecurity u ser g uide option 1 option 1 is included in the options page if “web-based authentication” was selected at the re-authentication options field in the block page authentication window. The following phrase/link di...
Page 73: Option 2
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 61 option 2 the following phrase/link displays, based on options selected at the re-authentication options field in the block page authentication window: • re-start your system and re-login - this phrase ...
Page 74: Option 3
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 62 m86 s ecurity u ser g uide option 3 option 3 is included in the options page, if “override account” was selected at the re-authentication options field in the block page authentication window. This option is used by any user who...
Page 75: Common Customization
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 63 common customization common customization lets you specify elements to be included in block pages and/or the authentication request form end users will see. Click customization and then select common c...
Page 76: Enable, Disable Features
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 64 m86 s ecurity u ser g uide enable, disable features 1. Click “on” or “off” to enable or disable the following elements in the html pages, and make entries in fields to display customized text, if necessary: • username display - ...
Page 77
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 65 • help link url - by default, http:// www.M86security.Com/support/r3000/accessde- nied.Asp displays as the help link url. Enter the url to be used when the end user clicks the help link text (specified...
Page 78
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 66 m86 s ecurity u ser g uide authentication form customization to customize the authentication request form, click customization and select authentication form from the pop-up menu: fig. 2-19 authentication form customization wind...
Page 79
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 67 1. Make an entry in any of the following fields: • in the header field, enter a static header to be displayed at the top of the authentication request form. • in the description field, enter a static t...
Page 80
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 68 m86 s ecurity u ser g uide preview sample authentication request form 1. Click preview to launch a separate browser window containing a sample authentication request form, based on entries saved in this window and in the common ...
Page 81
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 69 by default, the following standard links are included in the authentication request form: • help - clicking this link takes the user to m86’s tech- nical support page that explains why access to the si...
Page 82: Block Page Customization
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 70 m86 s ecurity u ser g uide block page customization to customize the block page, click customization and select block page from the pop-up menu: fig. 2-21 block page customization window note: see appendix b: create a custom blo...
Page 83
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 71 1. Make an entry in any of the following fields: • in the header field, enter a static header to be displayed at the top of the block page. • in the description field, enter a static text message to be...
Page 84: Preview Sample Block Page
C hapter 2: n etwork s etup s et up the n etwork for a uthentication 72 m86 s ecurity u ser g uide preview sample block page 1. Click preview to launch a separate browser window containing a sample customized block page, based on entries saved in this window and in the common customization window: f...
Page 85
C hapter 2: n etwork s etup s et up the n etwork for a uthentication m86 s ecurity u ser g uide 73 by default, the following standard links are included in the block page: • help - clicking this link takes the user to m86’s tech- nical support page that explains why access to the site or service may...
Page 86
C hapter 2: n etwork s etup s et up g roup a dministrator a ccounts 74 m86 s ecurity u ser g uide set up group administrator accounts the global administrator creates group administrator (sub admin) accounts so that these group administrators can be assigned to manage specific ldap entities (nodes) ...
Page 87
C hapter 2: n etwork s etup s et up g roup a dministrator a ccounts m86 s ecurity u ser g uide 75 add a group administrator account to add an ldap group administrator (sub admin) account: 1. In the account details frame, enter the username in the username field. 2. In the password field, enter eight...
Page 88
C hapter 2: n etwork s etup s et up g roup a dministrator a ccounts 76 m86 s ecurity u ser g uide delete a group administrator account to delete an administrator account: 1. Select the username from the current user list box. 2. Click delete to remove the account. Note: if a group administrator assi...
Page 89: View Log Results
C hapter 2: n etwork s etup v iew l og r esults m86 s ecurity u ser g uide 77 view log results use the view log file window if you need to troubleshoot any problems with the authentication setup process. 1. Click diagnostics and select view log file from the pop- up menu to display the view log file...
Page 90
C hapter 2: n etwork s etup v iew l og r esults 78 m86 s ecurity u ser g uide • “admin gui server log (adminguiserver.Log)” - used for viewing information on entries made by the admin- istrator in the console. • “edirectory agent debug log (ediragent.Log)” - used for viewing the debug log, if using ...
Page 91: Hapter
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 79 c hapter 3: ldap a uthentication s etup create an ldap domain in the policy section of the console, add an ldap domain that contains entities to be authenticated. Add the ldap domain 1. Click ldap in the na...
Page 92: Refresh The Ldap Branch
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 80 m86 s ecurity u ser g uide refresh the ldap branch click ldap in the navigation panel to open the pop-up menu, and select refresh whenever changes have been made in this branch of the tree. View, modify, enter ldap domain details dou...
Page 93: Ldap Server Type
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 81 warning: the instructions in this user guide have been docu- mented based on standard default settings in ldap for microsoft active directory services. The suggested entries and examples may not be applicab...
Page 94: Group Objects
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 82 m86 s ecurity u ser g uide warning: the contents of the tabs for user and group do not normally need to be changed. The settings on these tabs are made automatically when you select the server type at the begin- ning of the setup pro...
Page 95
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 83 1. Generally, no action needs to be performed on this tab. However, under special circumstances, the following actions can be performed: • a group object can be added or excluded by making an entry in the a...
Page 96: User Objects
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 84 m86 s ecurity u ser g uide 3. If any modifications were made on this tab, click save. 4. Next to go to the user tab. User objects the user tab is used for including or excluding user objects in the ldap domain. Fig. 3-4 domain detail...
Page 97: Workstation Objects
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 85 • a user object can be removed by selecting the user object and then clicking remove. • if the user dn cannot be auto-detected during the profile setup process, click “use case-sensitive comparison” to perf...
Page 98: Address Info
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 86 m86 s ecurity u ser g uide • a workstation object can be added or excluded by making an entry in the appropriate field, and then clicking the include or exclude button. • a workstation object name can be edited by selecting the works...
Page 99
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 87 requirements for ldap authentication. Please ensure the correct dns settings are set. 1. This tab includes the following fields, some pre-popu- lated by default, and some that you may wish to edit: • the se...
Page 100: Account Info
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 88 m86 s ecurity u ser g uide • by default, the ldap query base displays the root of the ldap database to query using the ldap syntax, e.G. Dc=domain,dc=com, or o=server-org. The entry in this field is case sensitive and should be edite...
Page 101
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 89 • if your ldap database does not require a username to be provided in order to bind to the ldap database, click the “use anonymous bind” checkbox to grey out the fields—and find distinguished name button, i...
Page 102: Ssl Settings
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 90 m86 s ecurity u ser g uide click find distinguished name to perform the search for the ldap distinguished name. If the adminis- trator’s user name and password are successfully retrieved, the pop-up box closes and the fields on this ...
Page 103
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 91 1. If applicable, click in the “enable secure ldap over ssl” checkbox. This action activates the upload buttons in the manually upload ssl certificate for ldaps frame and the automatically upload ssl certif...
Page 104: Alias List
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 92 m86 s ecurity u ser g uide warning: if using a novell server, be sure the name on the ssl certificate (to be uploaded to the server) matches the server dns name entered in the address info tab. 3. Click save. 4. Click next to go to t...
Page 105
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 93 after the search is completed, the search in progress box closes, and the list displays the alias name and the corre- sponding ldap container name. Note: if the alias list does not display, double-check the...
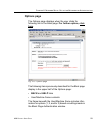
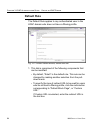
Page 106: Default Rule
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 94 m86 s ecurity u ser g uide default rule the default rule applies to any authenticated user in the ldap domain who does not have a filtering profile. Fig. 3-13 domain details window, default rule tab 1. This tab is comprised of the fo...
Page 107
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 95 • click the checkbox(es) corresponding to the option(s) to be applied to the filtering profile: “x strikes blocking”, “google/bing/yahoo!/youtube/ask/aol safe search enforcement”, “search engine keyword fil...
Page 108: Configure A Backup Server
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 96 m86 s ecurity u ser g uide ldap backup server configuration configure a backup server to add a backup server’s settings: 1. Click add to open the backup server configuration wizard pop-up window: fig. 3-14 backup server configuration...
Page 109
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 97 • dns domain name - dns name of the ldap domain, such as logo.Local notes: if your ldap server’s name is not a resolvable, fully qualified dns name, you may be able to enter the domain name. Be sure the dns...
Page 110
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 98 m86 s ecurity u ser g uide note: the distinguished name auto discovery frame only displays if the type of ldap server is microsoft active directory. 5. Enter, edit, or verify the following criteria: • “use anonymous bind” - click thi...
Page 111
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 99 search for the ldap distinguished name. If the administrator’s user name and password are successfully retrieved, the pop-up box closes and the fields on this tab become populated with appropriate data. Not...
Page 112
C hapter 3: ldap a uthentication s etup c reate an ldap d omain 100 m86 s ecurity u ser g uide b. To automatically upload an ssl certificate, go to the automatically upload ssl certificate for ldaps frame and do the following: • in the wait __ seconds for certificate field, by default 3 displays. En...
Page 113: Delete A Domain
C hapter 3: ldap a uthentication s etup c reate an ldap d omain m86 s ecurity u ser g uide 101 delete a backup server’s configuration on the default rule tab, click delete to remove the backup server’s configuration. Delete a domain to delete a domain profile, choose delete from the ldap domain menu...
Page 114: Set Up Ldap Domain Nodes
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes 102 m86 s ecurity u ser g uide set up ldap domain nodes in the navigation panel, the ldap domain branch of the tree menu includes options for setting up entities (nodes) in the domain so that filtering profiles can later be created....
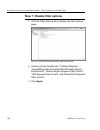
Page 115: Perform A Basic Search
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes m86 s ecurity u ser g uide 103 notes: if the “use dynamic group” option was specified in the group tab of domain details, “dynamic group enabled” displays towards the bottom left of this window. If the “use nested group” option was ...
Page 116: Options For Search Results
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes 104 m86 s ecurity u ser g uide options for search results the following actions can be performed on search results: • to narrow the number of records returned by your initial query, click the “within results” checkbox, modify your s...
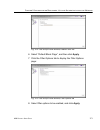
Page 117: Delete A Rule
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes m86 s ecurity u ser g uide 105 when the ldap branch of the tree is refreshed, all nodes with rules applied to them appear in the tree. Delete a rule to delete a rule from a profile, the entity must currently display in the grid and ...
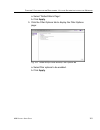
Page 118
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes 106 m86 s ecurity u ser g uide specify a group’s filtering profile priority 1. Select the ldap domain, and choose set group priority from the pop-up menu to display the set group priority window: fig. 3-18 set group priority window ...
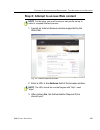
Page 119
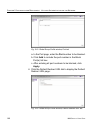
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes m86 s ecurity u ser g uide 107 manually add a workstation name to the tree 1. Select the ldap domain, and choose manually add workstation from the pop-up menu to open the manually add workstation dialog box: fig. 3-19 manually add w...
Page 120
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes 108 m86 s ecurity u ser g uide manually add a user’s name to the tree 1. Select the ldap domain, and choose manually add member from the pop-up menu to open the manually add member dialog box: fig. 3-20 manually add member box this ...
Page 121
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes m86 s ecurity u ser g uide 109 manually add a group’s name to the tree 1. Select the ldap domain, and choose manually add group from the pop-up menu to open the manually add group dialog box: fig. 3-21 manually add group box this di...
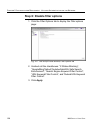
Page 122
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes 110 m86 s ecurity u ser g uide upload a file of filtering profiles to the tree 1. Select the ldap domain, and choose upload profile from the pop-up menu to open the upload user/group profile window: fig. 3-22 upload user/group profi...
Page 123
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes m86 s ecurity u ser g uide 111 note: leave the refresh page open until the file containing the profile has been uploaded. 3. Click browse... To open the choose file window. 4. Select the file to be uploaded. Warning: any file upload...
Page 124
C hapter 3: ldap a uthentication s etup s et up ldap d omain n odes 112 m86 s ecurity u ser g uide warning: when uploading a list of profiles to the tree, the user will be blocked from internet access if the minimum filtering level has not been defined via the minimum filtering level window. If you ...
Page 125: Hapter
C hapter 4: m anage n odes m86 s ecurity u ser g uide 113 c hapter 4: m anage n odes once ldap domains are set up in the policy tree, the global administrator assigns sub admin group administrators the following entities (nodes) to manage: domain, group(s), workstations, members, and/or containers. ...
Page 126
C hapter 4: m anage n odes a ssign s ub a dmin to an ldap n ode 114 m86 s ecurity u ser g uide assign sub admin to an ldap node a group administrator assigned to an ldap node (domain, group, workstation, member, or container) has the privileges to add, edit, or delete entities to/from that node to w...
Page 127
C hapter 4: m anage n odes a ssign s ub a dmin to an ldap n ode m86 s ecurity u ser g uide 115 fig. 4-2 assign access view window 4. Click the policy, library, and help tabs to view the menu topics, sub-topics, and tree nodes currently available to that sub admin. 5. Click the “x” in the upper right...
Page 128
C hapter 4: m anage n odes a ssign s ub a dmin to an ldap n ode 116 m86 s ecurity u ser g uide fig. 4-3 assign access window with node assigned 7. Click the “x” in the upper right corner of the assign access pop-up window to close it. Tip: to unassign the sub admin from that node, click the unas- si...
Page 129
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 117 create and maintain filtering profiles if a sub admin group administrator is assigned to an ldap domain, he/she can add groups and members to that domain. A sub admin group administrator assigned to ...
Page 130
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 118 m86 s ecurity u ser g uide add a group member to the tree list from the domain, select the group and choose group member details from the pop-up menu to display the group/ member details window: fig. 4-4 group member details w...
Page 131: View Container Details
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 119 view container details from the policy tree, select the domain and choose container details from the pop-up menu to display the container details window: fig. 4-5 container details window this view o...
Page 132
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 120 m86 s ecurity u ser g uide add or maintain a node’s profile from the domain, select the node and choose profile from the pop-up menu to display the default category tab of the profile window: fig. 4-6 group profile window, cat...
Page 133: Category Profile
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 121 category profile category profile is used for creating the categories portion of the filtering profile for the entity. Note: in order to use this tab, filtering rules should already have been set up ...
Page 134
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 122 m86 s ecurity u ser g uide note: if a category group does not display any filter setting (i.E. The check mark does not display in any column for the category group), one or more library categories within that group has a setti...
Page 135
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 123 • in the quota column, enter the number of minutes the user will be able to access the library group/category. The minimum number of minutes is “1” and the maximum is “1439” (one day minus one minute...
Page 136: Redirect Url
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 124 m86 s ecurity u ser g uide redirect url click the redirect url tab to display the redirect url page of the profile window: fig. 4-7 group profile window, redirect url tab , ldap group redirect url is used for specifying the ur...
Page 137: Filter Options
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 125 filter options click the filter options tab to display the filter options page of the profile window: fig. 4-8 group profile window, filter options tab, ldap group filter options is used for specifyi...
Page 138
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 126 m86 s ecurity u ser g uide add an exception url to the profile from the domain, select the node and choose exception url from the pop-up menu to display the exception url window: fig. 4-9 exception url window, ldap group this ...
Page 139: Valid Url Entries
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 127 valid url entries the following types of url entries are accepted in this window: • formats such as: http://www.Coors.Com, www.Coors.Com, or coors.Com • ip address - e.G. "209.247.228.221" in http://...
Page 140
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 128 m86 s ecurity u ser g uide add urls to block url or bypass url frame to block or bypass specified urls, in the block url or the bypass url frame: 1. Type the url to be blocked in the block urls field, or the url to be bypassed...
Page 141
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 129 the message “url can be added, but conflicting urls will be removed” applies to any url that the query found included in the opposite frame of the exception url window. When this scenario occurs, for...
Page 142: Url Frame
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 130 m86 s ecurity u ser g uide remove urls from block url or bypass url frame to remove urls from the block url or the bypass url frame: 1. Select a url to be removed from the block url / bypass url list box; your selection popula...
Page 143: Apply Settings
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 131 tip: click cancel to close this pop-up window without making any selections. 3. Click remove selected to close the pop-up window and to remove your selection(s) from the appropriate url list box. App...
Page 144: Add A Time Profile
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 132 m86 s ecurity u ser g uide add a time profile to create a time profile: 1. Click add to open the adding time profile pop-up box: fig. 4-14 adding time profile 2. Type in three to 20 alphanumeric characters—the under- score ( _...
Page 145
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 133 a. Select from a list of time slots incremented by 15 minutes: “12:00” to “11:45”. By default, the start field displays the closest 15-minute future time, and the end field displays a time that is on...
Page 146
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 134 m86 s ecurity u ser g uide • weekly - if this selection is made, enter the interval for the weeks this time profile will be used, and specify the day(s) of the week (“sunday” - “saturday”). By default, “1” displays and today’s...
Page 147
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles m86 s ecurity u ser g uide 135 next, choose from one of two options to specify the day of the month for the interval: • the first option lets you choose a specific month (“january” - “december”) and day (“1” - “31”). By default th...
Page 148
C hapter 4: m anage n odes c reate and m aintain f iltering p rofiles 136 m86 s ecurity u ser g uide 9. Click close to close the adding time profile pop-up window and to return to the time profile window. In this window, the current time profiles list box now shows the name and description of the ti...
Page 149
C hapter 4: m anage n odes v erify that an ldap p rofile is a ctive m86 s ecurity u ser g uide 137 verify that an ldap profile is active the active profile lookup window is a useful tool for the global administrator to use to find out whether or not an ldap profile is active. 1. In the system sectio...
Page 150
C hapter 4: m anage n odes v erify that an ldap p rofile is a ctive 138 m86 s ecurity u ser g uide if an ldap filtering profile is active, a pop-up box opens containing the result frame that displays profile settings applied to the profile: fig. 4-17 active profile lookup results the default login s...
Page 151
C hapter 4: m anage n odes v erify that an ldap p rofile is a ctive m86 s ecurity u ser g uide 139 tip: in the category groups tree, double-click the group enve- lope to open that segment of the tree and to view library catego- ries belonging to that group. A check mark inside a green circle display...
Page 152
C hapter 4: m anage n odes v erify that an ldap p rofile is a ctive 140 m86 s ecurity u ser g uide at the bottom of the rule details frame, uncategorized sitesare set to “pass”, “warn”, or “block”, indicating that the selected setting applies to any non-classified url. If the overall quotafield is e...
Page 153: Hapter
C hapter 5: a uthentication d eployment t est a uthentication s ettings m86 s ecurity u ser g uide 141 c hapter 5: a uthentication d eployment this final step of the authentication setup process includes testing authentication settings and activating authentication on the network. Test authenticatio...
Page 154
C hapter 5: a uthentication d eployment t est a uthentication s ettings 142 m86 s ecurity u ser g uide note: in order to complete the test process, you should be sure you have your own filtering profile set up. To verify that authentication is working, do either of the following, based on the tier y...
Page 155
C hapter 5: a uthentication d eployment t est a uthentication s ettings m86 s ecurity u ser g uide 143 test web-based authentication settings to verify that authentication is working properly, make the following settings in the policy section of the console: step 1: create an ip group, “test” 1. Cli...
Page 156
C hapter 5: a uthentication d eployment t est a uthentication s ettings 144 m86 s ecurity u ser g uide 3. Enter workstation as the group name. 4. Click ok to add the sub-group to the ip group. Step 3: set up “test” with a 32-bit net mask 1. Select the ip group named “test” from the tree. 2. Click me...
Page 157
C hapter 5: a uthentication d eployment t est a uthentication s ettings m86 s ecurity u ser g uide 145 step 4: give “workstation” a 32-bit net mask 1. Select the ip sub-group “workstation” from the tree. 2. Click members in the pop-up menu to display the members window: fig. 5-5 sub group members wi...
Page 158
C hapter 5: a uthentication d eployment t est a uthentication s ettings 146 m86 s ecurity u ser g uide step 5: block everything for the sub-group 1. Select the ip sub-group “workstation” from the tree. 2. Click sub group profile in the pop-up menu to display the sub group profile window: fig. 5-6 su...
Page 159: Redirect Url
C hapter 5: a uthentication d eployment t est a uthentication s ettings m86 s ecurity u ser g uide 147 step 6: use authentication request page for redirect url 1. Click the redirect url tab to display the redirect url page: fig. 5-7 sub group profile window, redirect url tab 2. Select “authenticatio...
Page 160
C hapter 5: a uthentication d eployment t est a uthentication s ettings 148 m86 s ecurity u ser g uide step 7: disable filter options 1. Click the filter options tab to display the filter options page: fig. 5-8 sub group profile window, filter options tab 2. Uncheck all the checkboxes: “x strikes bl...
Page 161
C hapter 5: a uthentication d eployment t est a uthentication s ettings m86 s ecurity u ser g uide 149 step 8: attempt to access web content note: for this step, you must have your own profile set up in order to complete the test process. 1. Launch an internet browser window supported by the web fil...
Page 162
C hapter 5: a uthentication d eployment t est a uthentication s ettings 150 m86 s ecurity u ser g uide fig. 5-10 authentication request form 4. Enter the following information: • username • password if the domain and alias fields display, select the following information: • domain you are using • al...
Page 163
C hapter 5: a uthentication d eployment t est a uthentication s ettings m86 s ecurity u ser g uide 151 test net use based authentication settings 1. From the test workstation, go to the net use command line and enter the net use command using the following format: net use \\virtualip\r3000$ for exam...
Page 164
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 152 m86 s ecurity u ser g uide activate authentication on the network after successfully testing authentication settings, you are now ready to activate authentication on the network. To verify that authentication is re...
Page 165: Ip Group
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 153 activate web-based authentication for an ip group ip group authentication is the preferred selection for web- based authentication—over the global group profile authentication option—as i...
Page 166
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 154 m86 s ecurity u ser g uide step 2: set “webauth” to cover users in range 1. Select the ip group “webauth” from the tree. 2. Click members in the pop-up menu to display the members window: fig. 5-12 members window 3...
Page 167
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 155 step 3: create an ip sub-group 1. Select the ip group “webauth” from the tree. 2. Click add sub group in the pop-up menu to open the create sub group dialog box: fig. 5-13 create sub grou...
Page 168
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 156 m86 s ecurity u ser g uide 8. In the member ip fields, enter the ip address range for members of the sub-group, and specify the subnet mask. 9. Click modify. Step 4: block everything for the sub-group 1. Select the...
Page 169: Redirect Url
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 157 step 5: use authentication request page for redirect url 1. Click the redirect url tab to display the redirect url page: fig. 5-16 sub group profile window, redirect url tab 2. Select “au...
Page 170
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 158 m86 s ecurity u ser g uide step 6: disable filter options 1. Click the filter options tab to display the filter options page: fig. 5-17 sub group profile window, filter options tab 2. Uncheck all the checkboxes: “x...
Page 171: Traffic
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 159 step 7: set global group to filter unknown traffic 1. Click global group in the tree to open the pop-up menu. 2. Select global group profile to display the category tab of the profile win...
Page 172
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 160 m86 s ecurity u ser g uide fig. 5-19 global group profile window, port tab a. In the port page, enter the port number to be blocked. B. Click add to include the port number in the block port(s) list box. C. After e...
Page 173
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 161 a. Select “default block page”. B. Click apply. 5. Click the filter options tab to display the filter options page: fig. 5-21 global group profile window, filter options tab a. Select fil...
Page 174
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 162 m86 s ecurity u ser g uide as a result of these entries, the standard block page will display—instead of the authentication request form— when any user in this sub-group is blocked from accessing internet content. ...
Page 175: Global Group
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 163 activate web-based authentication for the global group this selection of web-based authentication creates more of a load on the web filter than the ip group selection, and should only be ...
Page 176: Range to Detect
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 164 m86 s ecurity u ser g uide step 1a: block web access, logging via range to detect note: segments of network traffic should not be defined if using the firewall mode. Range to detect settings 1. Click global group i...
Page 177
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 165 fig. 5-24 range to detect settings window, main window 4. Click start the setup wizard to display step 1 of the range to detect setup wizard: range to detect setup wizard fig. 5-25 range ...
Page 178
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 166 m86 s ecurity u ser g uide 2. Click next to go to step 2 of the wizard: fig. 5-26 range to detect setup wizard, step 2 3. An entry for this step of the wizard is optional. If there are destination ip address(es) to...
Page 179
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 167 5. An entry for this step of the wizard is optional. If there are source ip address(es) to be ignored, enter the ip address and specify the netmask, or enter the indi- vidual ip address. ...
Page 180
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 168 m86 s ecurity u ser g uide f ig. 5-29 range to detect setup wizard, step 5 9. An entry for this step of the wizard is optional. If there are ports to be excluded from filtering, enter each port number in the indivi...
Page 181
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 169 as a result of these entries, the ip address(es) specified to be excluded will not be logged or filtered on the network. Bypass step 1b and go on to step 2 to complete this process..
Page 182: Profile
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 170 m86 s ecurity u ser g uide step 1b: block web access via ip sub-group profile note: this step assumes that the ip group and sub-group have already been created. 1. Select the ip sub-group from the tree. 2. Click su...
Page 183
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 171 fig. 5-32 sub group profile window, redirect url tab 6. Select “default block page”, and then click apply. 7. Click the filter options tab to display the filter options page: fig. 5-33 su...
Page 184
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 172 m86 s ecurity u ser g uide as a result of these entries, the machine will not be served the authentication request form, and will use the default block page instead. Go on to step 2 to complete this process. Step 2...
Page 185
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 173 3. Click the port tab to display the port page: fig. 5-35 global group profile window, port tab a. Enter the port number to be blocked, and then click add to include the port number in th...
Page 186
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 174 m86 s ecurity u ser g uide 4. Click the default redirect url tab to display the default redirect url page: fig. 5-36 global group profile window, redirect url tab a. Select “authentication request form”. Note: sinc...
Page 187
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 175 5. Click the filter options tab to display the filter options page: fig. 5-37 global group profile window, filter options tab a. Select filter options to be enabled. B. Click apply. As a ...
Page 188
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 176 m86 s ecurity u ser g uide add net use command to login scripts after testing the net use command, the next step is to add the net use command to users’ login scripts. We recom- mend that you add the 3-try login sc...
Page 189
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork m86 s ecurity u ser g uide 177 if errorlevel 0 echo code 0: success goto :end :try3 echo running net use... Net use \\192.168.0.20\r3000$ if errorlevel 1 goto :error if errorlevel 0 echo code 0: success goto :end :erro...
Page 190
C hapter 5: a uthentication d eployment a ctivate a uthentication on the n etwork 178 m86 s ecurity u ser g uide 1. Click global group in the tree to open the pop-up menu. 2. Select global group profile to display the category tab of the profile window. 3. In the category profile page, select catego...
Page 191: Hapter
C hapter 6: t echnical s upport h ours m86 s ecurity u ser g uide 179 c hapter 6: t echnical s upport for technical support, visit m86 security’s technical support web page at http://www.M86security.Com/ support/ or contact us by phone, by e-mail, or in writing. For troubleshooting tips, visit http:...
Page 192: Contact Information
C hapter 6: t echnical s upport c ontact i nformation 180 m86 s ecurity u ser g uide contact information domestic (united states) 1. Call 1-888-786-7999 2. Select option 3 international 1. Call +1-714-282-6111 2. Select option 3 e-mail for non-emergency assistance, e-mail us at support@m86security.C...
Page 193: M86 Taiwan
C hapter 6: t echnical s upport c ontact i nformation m86 s ecurity u ser g uide 181 office locations and phone numbers m86 corporate headquarters (usa) 828 west taft avenue orange, ca 92865-4232 usa local : 714.282.6111 fax : 714.282.6116 domestic us : 1.888.786.7999 international : +1.714.282.6111...
Page 194: Support Procedures
C hapter 6: t echnical s upport s upport p rocedures 182 m86 s ecurity u ser g uide support procedures when you contact our technical support department: • you will be greeted by a technical professional who will request the details of the problem and attempt to resolve the issue directly. • if your...
Page 195: Ppendix
A ppendix a: a uthentication o perations a uthentication t ier s elections m86 s ecurity u ser g uide 183 a ppendix a: a uthentication o perations when enabling authentication in the interface, there are three tiers from which to select based on the type of server(s) used on the network, and various...
Page 196
A ppendix a: a uthentication o perations t ier 1: s ingle s ign -o n a uthentication 184 m86 s ecurity u ser g uide tier 1: single sign-on authentication net use based authentication process the following diagram and steps describe the operations of the net use based user authentication process: fig...
Page 197: Re-Authentication Process
A ppendix a: a uthentication o perations t ier 1: s ingle s ign -o n a uthentication m86 s ecurity u ser g uide 185 4. Upon creating the ipc share, the software in the web filter queries the network authentication server with the user's login name and password sent by the workstation. 5. Once the us...
Page 198: Tier 1 Authentication Method
A ppendix a: a uthentication o perations t ier 1: s ingle s ign -o n a uthentication 186 m86 s ecurity u ser g uide tier 1 authentication method tier 1 supports the ldap authentication method. Ldap is a directory service protocol that stores entries (distinguished names) in a domain’s directory usin...
Page 199: Login Scripts
A ppendix a: a uthentication o perations t ier 1: s ingle s ign -o n a uthentication m86 s ecurity u ser g uide 187 must have a valid dns entry or the ip address must be added to the web filter hosts file. Configuring the authentication server when configuring authentication, you must first go to th...
Page 200
A ppendix a: a uthentication o perations t ier 1: s ingle s ign -o n a uthentication 188 m86 s ecurity u ser g uide example: net use \\192.168.0.20\r3000$/ user:logo\jsmith xyz579 • the command to disconnect a session is: net use \\virtualip\r3000$ /delete view login script on the server console the...
Page 201: Ldap Server Setup Rules
A ppendix a: a uthentication o perations t ier 1: s ingle s ign -o n a uthentication m86 s ecurity u ser g uide 189 ldap server setup rules warning: the instructions in this user guide have been docu- mented based on standard default settings in ldap for microsoft active directory services. The use ...
Page 202
A ppendix a: a uthentication o perations t ier 2: t ime - based , w eb a uthentication 190 m86 s ecurity u ser g uide tier 2: time-based, web authentication the following diagram and steps describe the operations of the time-based authentication process: fig. A-2 web-based authentication module diag...
Page 203
A ppendix a: a uthentication o perations t ier 2: t ime - based , w eb a uthentication m86 s ecurity u ser g uide 191 tier 2 implementation in an environment in an environment where tier 2 time-based profiles have been implemented, end users receive filtering profiles after correctly entering their ...
Page 204: Tier 2 Script
A ppendix a: a uthentication o perations t ier 2: t ime - based , w eb a uthentication 192 m86 s ecurity u ser g uide tier 2 script if using tier 2 only, this script should be inserted into the network’s login script. If the network also uses a logoff script, m86’s script should be inserted there as...
Page 205: Tier 1 and Tier 2 Script
A ppendix a: a uthentication o perations t ier 2: t ime - based , w eb a uthentication m86 s ecurity u ser g uide 193 tier 1 and tier 2 script in an environment in which both tier 1 and tier 2 are used, this version of m86’s script should be inserted into the network’s login script. M86’s script att...
Page 206
A ppendix a: a uthentication o perations t ier 2: t ime - based , w eb a uthentication 194 m86 s ecurity u ser g uide :try1 net use \\10.10.10.10\r3000$ if errorlevel 1 goto :try2 if errorlevel 0 echo code 0: success goto :end :try2 net use \\10.10.10.10\r3000$ if errorlevel 1 goto :try3 if errorlev...
Page 207
A ppendix a: a uthentication o perations t ier 3: s ession - based , w eb a uthentication m86 s ecurity u ser g uide 195 tier 3: session-based, web authentication the diagram on the previous page (fig. A-2) and steps below describe the operations of the session-based authen- tication process: 1. The...
Page 208: M86 Authenticator
A ppendix a: a uthentication o perations m86 a uthenticator 196 m86 s ecurity u ser g uide m86 authenticator the m86 authenticator ensures the end user is authenti- cated on his/her workstation, via an executable file that launches during the login process. To use this option, the m86 authenticator ...
Page 209: Environment Requirements
A ppendix a: a uthentication o perations m86 a uthenticator m86 s ecurity u ser g uide 197 environment requirements windows minimum system requirements the following minimum server components are required when using netware edirectory server 6.5: • server-class pc with a pentium ii or amd k7 process...
Page 210: Workstation Requirements
A ppendix a: a uthentication o perations m86 a uthenticator 198 m86 s ecurity u ser g uide • bootable cd drive that supports the el torito specifica- tion • usb or ps/2* mouse macintosh minimum system requirements the following minimum server components are required when using a macintosh: • os x 10...
Page 211: Work Flow In Environments
A ppendix a: a uthentication o perations m86 a uthenticator m86 s ecurity u ser g uide 199 work flow in environments windows environment 1. The administrator stores the m86 authenticator client (authenticat.Exe) in a network-shared location that a login script can access. 2. Using a windows machine,...
Page 212: Macintosh Environment
A ppendix a: a uthentication o perations m86 a uthenticator 200 m86 s ecurity u ser g uide macintosh environment 1. The administrator installs a launchagent on the client machine. 2. Using a macintosh machine, an end user logs on the domain and launches the launchagent. 3. The end user’s launchd pro...
Page 213: Windows
A ppendix a: a uthentication o perations m86 a uthenticator m86 s ecurity u ser g uide 201 m86 authenticator configuration priority the source and order in which parameters are received and override one another are described below. Notes: the ra[] parameter for the web filter ip address is the only ...
Page 214: Macintosh
A ppendix a: a uthentication o perations m86 a uthenticator 202 m86 s ecurity u ser g uide macintosh 1. Compiled defaults: given no parameters at all, the client will try to execute using the default compilation. 2. Configuration file (optional): the default configuration file name is “8e6authentica...
Page 215: Sample Configuration File
A ppendix a: a uthentication o perations m86 a uthenticator m86 s ecurity u ser g uide 203 m86 authenticator configuration syntax all configuration parameters, regardless of their source, will use the following format/syntax: waa[b]w{c}w {parameter ‘aa’ with data ‘b’, and comment ‘c’ ignored.} w;dd[...
Page 216
A ppendix a: a uthentication o perations m86 a uthenticator 204 m86 s ecurity u ser g uide sample configuration update packet ‘pcfg’ after decryption, with protocol headers removed: rh[30000]rc[1000]le[1] you only need to change the options you do not wish to remain as default. Often the ip address ...
Page 217: Table of Parameters
A ppendix a: a uthentication o perations m86 a uthenticator m86 s ecurity u ser g uide 205 table of parameters the following table contains the different parameters, their meanings, and possible values. Param id parameter meaning values dbg default release default ut+ user’s logon environment 1-256 ...
Page 218
A ppendix a: a uthentication o perations m86 a uthenticator 206 m86 s ecurity u ser g uide + if ut[0] is set, then the novell environment will be ignored, if present, and only the windows environment information will be retrieved and sent to the web filter. If ut[1] is set and the novell environment...
Page 219
A ppendix a: a uthentication o perations m86 a uthenticator m86 s ecurity u ser g uide 207 rp[] affects port-less addresses specified in the rv[] command as well. • for ra[], each ip address is separated by a semi-colon ‘;’ and the first ip address will be tried for each new connection attempt. When...
Page 220: Novell Edirectory Agent
A ppendix a: a uthentication o perations n ovell e d irectory a gent 208 m86 s ecurity u ser g uide novell edirectory agent novell edirectory agent provides single sign-on (sso) authentication for an web filter set up in a novell edirectory environment. Using novell edirectory agent, the web filter ...
Page 221: Client Workstations
A ppendix a: a uthentication o perations n ovell e d irectory a gent m86 s ecurity u ser g uide 209 client workstations to use this option, all end users must log in the network. The following os have been tested: • windows 2000 professional • windows xp • macintosh novell clients the following nove...
Page 222
A ppendix a: a uthentication o perations n ovell e d irectory a gent 210 m86 s ecurity u ser g uide web filter setup and event logs when using a novell edirectory server and choosing to use the novell edirectory agent option in the web filter: • enable novell edirectory agent in the enable/disable a...
Page 223: Active Directory Agent
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 211 active directory agent active directory agent is a windows service that provides transparent user identification for windows active directory- based networks. The active directory agent (also called “ad...
Page 224: Windows Server Requirements
A ppendix a: a uthentication o perations a ctive d irectory a gent 212 m86 s ecurity u ser g uide windows server requirements • windows 2000 or windows 2003 server running on a 32- bit platform • latest microsoft patches/service packs applied • at least 512 mb ram • 100 mb disk space • special domai...
Page 225: Set Up Ad Agent
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 213 set up ad agent step 1: ad agent settings on the web filter to set up active directory agent on the web filter, go to system > authentication > enable/disable authentication window in the web filter use...
Page 226
A ppendix a: a uthentication o perations a ctive d irectory a gent 214 m86 s ecurity u ser g uide fig. A-4 ad agent settings pop-up window 3. In the computer name field, enter the name of the primary ad agent machine. 4. Enter from seven to 20 alphanumeric characters in the passphrase field, and ent...
Page 227
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 215 step 2: configure the domain, service account 1. Create a new group on the domain named dcagent_services. 2. Create a new domain user account named dcagent_service and make it a member of the dcagent_se...
Page 228
A ppendix a: a uthentication o perations a ctive d irectory a gent 216 m86 s ecurity u ser g uide d. Add the dcagent_services and domain admins groups to the list of permitted users. If installing the ad agent on a domain controller only: • double-click the “allow logon locally” setting. • add the d...
Page 229
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 217 note: if prompted, install microsoft .Net framework 2.0. Framework may require updating other windows components before installing the ad agent. 2. Click run to open the end user license agreement (eula...
Page 230
A ppendix a: a uthentication o perations a ctive d irectory a gent 218 m86 s ecurity u ser g uide 4. After specifying the destination folder for installing the ad agent, click next to begin the installation setup process: fig. A-8 ad agent installation 5. When the ad agent installation setup process...
Page 231
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 219 step 3c: run ad agent configuration wizard the ad agent configuration wizard should be run when setting up ad agent for the first time, and if the role of the ad agent on the current machine changes (fr...
Page 232
A ppendix a: a uthentication o perations a ctive d irectory a gent 220 m86 s ecurity u ser g uide fig. A-11 account and password information 2. By default, the account field is populated with the path of the dcagent_service account. A. Enter the password for this account, specified during step 2. B....
Page 233
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 221 fig. A-12 specify role of ad agent on current machine 3. By default, the role of the ad agent on the current machine being configured is “primary”—indicating that this is either the only machine running...
Page 234
A ppendix a: a uthentication o perations a ctive d irectory a gent 222 m86 s ecurity u ser g uide b. Enter the primary agent computer name that will delegate to this machine the areas of the network to scan for end user logon/logoff events. This satellite machine running the ad agent will send its l...
Page 235
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 223 d. Appliance passphrase - enter the passphrase that was entered in the passphrase field in the ad agent settings pop-up window (accessible via the enable/ disable authentication window). E. (repeat pass...
Page 236: Activity Tab
A ppendix a: a uthentication o perations a ctive d irectory a gent 224 m86 s ecurity u ser g uide note: information about how to view and use the activity log is explained in the activity tab section of use the active directory agent console. Use the active directory agent console the active directo...
Page 237
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 225 in this tab the activity log displays, comprised of rows of records for the most recent activity on the current machine running the ad agent. The most recent activity displays at the bottom of the log. ...
Page 238
A ppendix a: a uthentication o perations a ctive d irectory a gent 226 m86 s ecurity u ser g uide the following actions can be performed via the activity tab: • view/download the activity log in the text file format - click the view as text button to launch a notepad file containing the contents of ...
Page 239: Sessions Tab
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 227 sessions tab sessions displays by default when the active directory agent console is launched on a machine running the ad agent in the primary role, or whenever the sessions tab is clicked in the consol...
Page 240
A ppendix a: a uthentication o perations a ctive d irectory a gent 228 m86 s ecurity u ser g uide • login - date and time the end user last logged in (using the mm/yy hh:mm military time format). If 01/01 00:00 displays, the end user has not logged on at that worksta- tion since the ad agent service...
Page 241: Session Table Spreadsheet
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 229 • view/modify primary ad agent configuration, stop/start ad agent service - click the configuration button to open a pop-up window containing ad agent configura- tion tools and configured settings (see ...
Page 242: Session Properties Window
A ppendix a: a uthentication o perations a ctive d irectory a gent 230 m86 s ecurity u ser g uide session properties window 1. To view detailed information about a record in the session table, do one of the following: • double-click the record in the session table to open the session properties pop-...
Page 243
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 231 last error (an error code displays if the probe failed to successfully identify the end user); last updated (shows the time data last changed for the end user’s workstation, using the m/d/yyyy h:m:ss am...
Page 244
A ppendix a: a uthentication o perations a ctive d irectory a gent 232 m86 s ecurity u ser g uide 2. Click either of the probe buttons to activate the probe search on demand: • nwksta probe - this is the default probe used for iden- tifying workstations. This probe requires the user’s domain account...
Page 245
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 233 active directory agent configuration window the active directory agent configuration window lets you modify settings for the ad agent team, if there are changes to the ad agent setup or to the web filte...
Page 246
A ppendix a: a uthentication o perations a ctive d irectory a gent 234 m86 s ecurity u ser g uide • agent hosts - used for specifying the role (primary or satellite) the ad agent will play on the current machine being configured. • options - used for specifying configuration options for the primary ...
Page 247: Service Page
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 235 service page 1. Click service to display the service page: fig. A-20 primary host configuration, service the server status displays to indicate the status of ad agent on the current machine: running, st...
Page 248: Appliance Page
A ppendix a: a uthentication o perations a ctive d irectory a gent 236 m86 s ecurity u ser g uide • reset team state - this button is activated if the ad agent service is running on the primary host. Clicking this button flushes all accumulated session data for the entire team (primary and satellite...
Page 249: Agent Hosts Page
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 237 agent hosts page 1. Click agent hosts to display the agent hosts page: fig. A-22 primary host configuration, agent hosts by default, the fields in this page are populated with entries made during the co...
Page 250: Add A Satellite
A ppendix a: a uthentication o perations a ctive d irectory a gent 238 m86 s ecurity u ser g uide • configuration - on a primary host server, selecting a satellite in the ad agent servers list box and clicking this activated button opens a dialog box in which servers and/or workstations to be scanne...
Page 251: Configure A Satellite
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 239 configure a satellite on a primary host server: 1. Select the satellite machine in the ad agent servers list box. 2. Click configuration to open the satellite agent configu- ration dialog box: fig. A-24...
Page 252
A ppendix a: a uthentication o perations a ctive d irectory a gent 240 m86 s ecurity u ser g uide if the satellite will not be manually assigned any machines on the network to scan, click ok to close the dialog box and to display any entries (if made) in the assigned servers field of the satellite a...
Page 253
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 241 a. Enter the lowest ip address in the range. B. Enter the highest ip address in the range. C. Click ok to close the dialog box and to display your entries in the ip address filters list box of the satel...
Page 254
A ppendix a: a uthentication o perations a ctive d irectory a gent 242 m86 s ecurity u ser g uide • period end - the time period (using the hh:mm military time format) of each 10-minute interval in which servers/machines were scanned. The most recent 10- minute interval displays as the first record ...
Page 255: Options Page
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 243 options page on a primary host server: 1. Click options to display the options page: fig. A-28 primary host configuration, options 2. Modify entries or make selections in this page as perti- nent to you...
Page 256
A ppendix a: a uthentication o perations a ctive d irectory a gent 244 m86 s ecurity u ser g uide • “enable netwkstauserenum workstation probes”: by default, this probe process is selected to run. • minimum probe interval: by default, 5 minutes displays as the interval of time in which the selected ...
Page 257: Notifications Page
A ppendix a: a uthentication o perations a ctive d irectory a gent m86 s ecurity u ser g uide 245 notifications page on a primary host server: 1. Click notifications to display the notifications page: fig. A-29 primary host configuration, notifications 2. If using an smtp server, enter the following...
Page 258
A ppendix a: a uthentication o perations a ctive d irectory a gent 246 m86 s ecurity u ser g uide 3. Click send test message to test the email setup connec- tion. Make any necessary modifications to your entries if the sending mail connection fails. Note: the primary ad agent sends an alert email me...
Page 259: Ppendix
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate m86 s ecurity u ser g uide 247 a ppendix b: o btain , e xport an ssl c ertificate when using web-based authentication, the ldap server’s ssl certificate needs to be exported and saved to the hard drive,...
Page 260: Locate Certificates Folder
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate 248 m86 s ecurity u ser g uide 2. Verify that the certificate authority has been installed on this server and is up and running—indicated by a green check mark on the server icon (see circled item in fi...
Page 261
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate m86 s ecurity u ser g uide 249 3. From the toolbar, click console to open the pop-up menu. Select add/remove snap-in to open the add/ remove snap-in dialog box: fig. B-4 add/remove snap-in 4. Click add ...
Page 262
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate 250 m86 s ecurity u ser g uide fig. B-6 certificates snap-in dialog box 6. Choose “computer account”, and click next to go to the select computer wizard page: fig. B-7 select computer dialog box 7. Choo...
Page 263
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate m86 s ecurity u ser g uide 251 notice that the snap-in has now been added to the console root folder: fig. B-8 console root with snap-in export the master certificate for the domain 1. Go to the right p...
Page 264
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate 252 m86 s ecurity u ser g uide this action launches the certificate export wizard: fig. B-10 certificate export wizard 3. Click next to go to the export private key page of the wizard: fig. B-11 export ...
Page 265
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate m86 s ecurity u ser g uide 253 fig. B-12 export file format 5. Select “base-64 encoded x.509 (.Cer)” and click next to go to the file to export page of the wizard: fig. B-13 file to export 6. Enter the ...
Page 266
A ppendix b: o btain , e xport an ssl c ertificate e xport an a ctive d irectory ssl c ertificate 254 m86 s ecurity u ser g uide fig. B-14 settings 7. Notice that the specified settings display in the list box, indicating the certificate has been successfully copied from the console to your disk. Cl...
Page 267
A ppendix b: o btain , e xport an ssl c ertificate e xport a n ovell ssl c ertficate m86 s ecurity u ser g uide 255 export a novell ssl certficate 1. From the console of the ldap server, go to the tree in the left panel and open the security folder to display the contents in the console view (right ...
Page 268
A ppendix b: o btain , e xport an ssl c ertificate e xport a n ovell ssl c ertficate 256 m86 s ecurity u ser g uide 3. Click the certificates tab to go to the self signed certifi- cate page. 4. Click export to open the export a certificate pop-up window: fig. B-17 export a certificate pop-up window ...
Page 269
A ppendix b: o btain , e xport an ssl c ertificate o btain a s un o ne ssl c ertificate m86 s ecurity u ser g uide 257 obtain a sun one ssl certificate unlike microsoft or novell, the sun one ldap directory does not have a tool for exporting an ssl certificate once it has been imported to the ldap s...
Page 270: Ppendix
A ppendix c: ldap s erver c ustomizations o pen ldap s erver s cenario 258 m86 s ecurity u ser g uide a ppendix c: ldap s erver c ustomizations the web filter has been tested on common types of stan- dard ldap servers with default settings. However, due to the number of ldap servers available, and t...
Page 271: Ppendix
A ppendix d: p rofile f ormat and r ules o pen ldap s erver s cenario m86 s ecurity u ser g uide 259 a ppendix d: p rofile f ormat and r ules the file with filtering profiles you upload to the server must be set up in a specified format, with one complete profile per line. This format will differ de...
Page 272: Username Formats
A ppendix d: p rofile f ormat and r ules u sername f ormats 260 m86 s ecurity u ser g uide username formats note: for examples of valid username entries, see file format: rules and examples in this appendix, or go to http:// www.M86security.Com/software/8e6/hlp/r3000/files/ 2group_textfile_user.Html...
Page 273
A ppendix d: p rofile f ormat and r ules r ule c riteria m86 s ecurity u ser g uide 261 • category command codes: category command codes must be entered in the following order: j, r, m, i. “passed” should either be entered after j, r, or m, or after a string of category codes following j, r, or m. J...
Page 274
A ppendix d: p rofile f ormat and r ules r ule c riteria 262 m86 s ecurity u ser g uide • filter option codes: • 0x1 = exception url query (always enabled) • 0x2 = x strikes blocking • 0x4 = google/bing/yahoo!/youtube/ask/aol safe search enforcement • 0x100 = search engine keyword • 0x200 = url keyw...
Page 275
A ppendix d: p rofile f ormat and r ules f ile f ormat : r ules and e xamples m86 s ecurity u ser g uide 263 file format: rules and examples when setting up the file to upload to the server, the following items must be considered: •each profile must be entered on a separate line in the file. • categ...
Page 276
A ppendix d: p rofile f ormat and r ules f ile f ormat : r ules and e xamples 264 m86 s ecurity u ser g uide ldap profile list format and rules when setting up the “ldapwrkstnprofile.Conf” file, “ldapuser- profile.Conf” file, “ldapgroupprofile.Conf” file, or “ldapcontain- erprofile.Conf” file, each ...
Page 277: User Profile List Format
A ppendix d: p rofile f ormat and r ules f ile f ormat : r ules and e xamples m86 s ecurity u ser g uide 265 pornography and pornography/adult content, warn on uncategorized urls, and pass all other categories, use filter mode 1, use redirect url http://www.Cnn.Com in place of the standard block pag...
Page 278: Group Profile List Format
A ppendix d: p rofile f ormat and r ules f ile f ormat : r ules and e xamples 266 m86 s ecurity u ser g uide • profile for a user with username “public\, joe q.”, organi- zational units “users” and “sales”, domain “qc”, dns suffix “.Local”: block all ports, use minimum filtering level, use filter mo...
Page 279: Ldap Quota Format and Rules
A ppendix d: p rofile f ormat and r ules f ile f ormat : r ules and e xamples m86 s ecurity u ser g uide 267 ldap quota format and rules when setting up the “quota.Conf” file, each entry must consist of the distinguished name (dn), a tab space, and quota criteria. A zero (0) should be used if no ove...
Page 280: Ppendix
A ppendix e: o verride p op - up b lockers f ile f ormat : r ules and e xamples 268 m86 s ecurity u ser g uide a ppendix e: o verride p op - up b lockers an override account user with pop-up blocking software installed on his/her workstation will need to temporarily disable pop-up blocking in order ...
Page 281
A ppendix e: o verride p op - up b lockers y ahoo ! T oolbar p op - up b locker m86 s ecurity u ser g uide 269 yahoo! Toolbar pop-up blocker if pop-up blocking is enabled 1. In the options page (see fig. E-1), enter your username and password. 2. Press and hold the ctrl key on your keyboard while si...
Page 282
A ppendix e: o verride p op - up b lockers y ahoo ! T oolbar p op - up b locker 270 m86 s ecurity u ser g uide fig. E-3 allow pop-ups from source 3. Select the source from the sources of recently blocked pop-ups list box to activate the allow button. 4. Click allow to move the selected source to the...
Page 283
A ppendix e: o verride p op - up b lockers g oogle t oolbar p op - up b locker m86 s ecurity u ser g uide 271 google toolbar pop-up blocker if pop-up blocking is enabled 1. In the options page (see fig. E-1), enter your username and password. 2. Press and hold the ctrl key on your keyboard while sim...
Page 284: Adwaresafe Pop-Up Blocker
A ppendix e: o verride p op - up b lockers a dware s afe p op - up b locker 272 m86 s ecurity u ser g uide adwaresafe pop-up blocker if pop-up blocking is enabled 1. In the options page (see fig. E-1), enter your username and password. 2. Press and hold the ctrl key on your keyboard while simultaneo...
Page 285
A ppendix e: o verride p op - up b lockers m ozilla f irefox p op - up b locker m86 s ecurity u ser g uide 273 mozilla firefox pop-up blocker add override account to the white list 1. From the firefox browser, go to the toolbar and select tools > options to open the options dialog box. 2. Click the ...
Page 286
A ppendix e: o verride p op - up b lockers m ozilla f irefox p op - up b locker 274 m86 s ecurity u ser g uide fig. E-7 mozilla firefox pop-up window exceptions 4. Enter the address of the web site to let the override account window pass. 5. Click allow to add the url to the list box section below. ...
Page 287: Set Up Pop-Up Blocking
A ppendix e: o verride p op - up b lockers w indows xp sp2 p op - up b locker m86 s ecurity u ser g uide 275 windows xp sp2 pop-up blocker set up pop-up blocking there are two ways to enable the pop-up blocking feature in the ie browser. Use the internet options dialog box 1. From the ie browser, go...
Page 288: Use The Ie Toolbar
A ppendix e: o verride p op - up b lockers w indows xp sp2 p op - up b locker 276 m86 s ecurity u ser g uide use the ie toolbar in the ie browser, go to the toolbar and select tools > pop- up blocker > turn on pop-up blocker: fig. E-9 toolbar setup when you click turn on pop-up blocker, this menu se...
Page 289: Use The Ie Toolbar
A ppendix e: o verride p op - up b lockers w indows xp sp2 p op - up b locker m86 s ecurity u ser g uide 277 add override account to the white list there are two ways to disable pop-up blocking for the over- ride account and to add the override account to your white list. Use the ie toolbar 1. With ...
Page 290: Use The Information Bar
A ppendix e: o verride p op - up b lockers w indows xp sp2 p op - up b locker 278 m86 s ecurity u ser g uide use the information bar with pop-up blocking enabled, the information bar can be set up and used for viewing information about blocked pop- ups or allowing pop-ups from a specified site. Set ...
Page 291
A ppendix e: o verride p op - up b lockers w indows xp sp2 p op - up b locker m86 s ecurity u ser g uide 279 3. Click the information bar for settings options: fig. E-12 information bar menu options 4. Select always allow pop-ups from this site—this action opens the allow pop-ups from this site? Dia...
Page 292: Ppendix
A ppendix f: g lossary d efinitions 280 m86 s ecurity u ser g uide a ppendix f: g lossary definitions this glossary includes definitions for terminology used in this user guide. Ads - active directory services is a windows 2000 direc- tory service that acts as the central authority for network secur...
Page 293
A ppendix f: g lossary d efinitions m86 s ecurity u ser g uide 281 directory service - uses a directory on a server to auto- mate administrative tasks for storing and managing objects on a network (such as users, passwords, and network resources users can access). Ads, dns, and nds (novell directory...
Page 294
A ppendix f: g lossary d efinitions 282 m86 s ecurity u ser g uide filter setting - a setting made for a service port. A service port with a filter setting uses filter settings created for library categories (block, open, or always allow settings) to deter- mine whether users should be denied or all...
Page 295
A ppendix f: g lossary d efinitions m86 s ecurity u ser g uide 283 ldap host - the ldap domain name and dns suffix. For example: “yahoo.Com” or “server.Local”. Login (or logon) script - consists of syntax that is used for re-authenticating a user if the network connection between the user’s machine ...
Page 296
A ppendix f: g lossary d efinitions 284 m86 s ecurity u ser g uide netbios name lookup - an authentication method used for validating a client (machine) by its machine name. Network address translation (nat) - allows a single real ip address to be used by multiple pcs or servers. This is accomplishe...
Page 297
A ppendix f: g lossary d efinitions m86 s ecurity u ser g uide 285 quota - the number of minutes configured for a passed library category in an end user’s profile that lets him/her access urls for a specified time before being blocked from further access to that category. Router mode - a web filter ...
Page 298
A ppendix f: g lossary d efinitions 286 m86 s ecurity u ser g uide time profile - a customized filtering profile set up to be effective at a specified time period for designated users. Tiers - levels of authentication methods. Tier 1 uses net use based authentication for ldap. Tier 2 uses time-based...
Page 299: Ndex
M86 s ecurity u ser g uide 287 i ndex numerics 3-try login script 176 a account tab 88 active directory agent 25 , 211 active filtering profiles 14 address tab 86 administrator window 74 ads, definition 280 alert box, terminology 3 alias list tab 92 alias name 93 always allowed 19 anonymous bind 89 ...
Page 300
I ndex 288 m86 s ecurity u ser g uide login scripts 187 authentication settings window 46 authentication solution single user compatibility chart 26 system deployment options on a network 27 authentication ssl certificate window 48 authmodule.Log 78 b backup domain controller (bdc) 281 backup server...
Page 301
I ndex m86 s ecurity u ser g uide 289 d default rule tab 94 dialog box, terminology 3 directory service, definition 281 directory, definition 280 distinguished name (dn) definition 281 ldap protocol 186 distinguished name auto discovery 89 dns, definition 281 domain definition 281 delete profile 101...
Page 302
I ndex 290 m86 s ecurity u ser g uide profile components 16 profile types 11 rules 21 static profiles 13 user, machine 14 firefox 33 firewall mode 36 , 38 definition 282 frame, terminology 4 g gateway ip address 38 global administrator, definition 282 global filtering profile 14 global group 8 grid,...
Page 303
I ndex m86 s ecurity u ser g uide 291 ipc share 184 j java applet 44 java plug-in 33 java runtime environment 33 , 44 java virtual machine 33 javascript 33 l lan settings window 38 lan1, lan2 38 , 47 ldap active directory service usage 189 authentication protocol 24 definition 282 domain diagram 10 ...
Page 304
I ndex 292 m86 s ecurity u ser g uide examples 187 usage 184 m m86 authenticator 25 , 196 m86 supplied category 17 machine name, definition 283 macintosh 33 manually add group dialog box ldap 109 manually add member dialog box ldap 108 manually add workstation dialog box ldap 107 master ip group 9 f...
Page 305
I ndex m86 s ecurity u ser g uide 293 name lookup, definition 284 netbios domain name 87 , 97 netbios name 46 netscape directory server 81 network address translation (nat), definition 284 network requirements 34 nic device 47 novell 24 , 81 , 92 , 183 , 186 , 199 , 206 , 247 novell edirectory agent...
Page 306
I ndex 294 m86 s ecurity u ser g uide elements 260 profile window 120 protocol definition 284 proxy server definition 284 pull-down menu, terminology 5 q quota 111 definition 285 format 262 r radio button, terminology 5 radius profile 12 re-authentication block page authentication 54 net use based p...
Page 307
I ndex m86 s ecurity u ser g uide 295 set group priority window ldap domain 106 single sign-on novell edirectory authentication 208 tier 1 authentication 184 single sign-on authentication (tier 1) 24 ssl certificate 49 active directory 247 novell 255 obtain, export from ldap server 247 sun one 257 s...
Page 308
I ndex 296 m86 s ecurity u ser g uide session-based, web-based authentication 195 tiers definition 286 web-based authentication 152 time profile add 132 definition 286 profile type 15 time-based authentication (tier 2) 24 time-based profile 43 , 54 topic terminology 6 tree terminology 7 troubleshoot...
Page 309
I ndex m86 s ecurity u ser g uide 297 white list, definition 286 window, terminology 7 wins server 46 workstation objects 85 workstation requirements 33 workstation tab 85.