- DL manuals
- Pakedge Device & Software
- Switch
- SK24
- User Manual
Pakedge Device & Software SK24 User Manual
Summary of SK24
Page 1
Pakedgedevice&software inc. Sk series sk24, sk24f.
Page 2
1 fcc declaration of conformity pakedge device & software, inc., 2847 breakwater avenue, hayward, ca, declares under sole responsibility that the sk series switches complies with 47 cfr parts 2 and 15 of the fcc rules as a class b digital device. These devices comply with part 15 of fcc rules. Opera...
Page 3
2 use notes 1. Use the provided accessories, such as the cable, mounting kit, etc; 2. Ensure the basic supply voltage standard must be met; 3. Keep the power plug clean and dry in case of electric shock or other dangers; 4. Keep your hands dry while plugging cables; 5. Shutdown the device and power ...
Page 4
3 contents introduction .................................................................................................................................................. 5 customer service and technical support ...........................................................................................
Page 5
4 configuration ...................................................................................................................................... 31 traffic .............................................................................................................................................
Page 6
5 introduction the sk series 24 port smart gigabit switches provide 24 10/100/100. Mbps rj45 ports, 2 independent 1000mbps fiber ports and one console port. These switches support vlans, qos, dhcp relay, igmp snooping, acl, stp, rstp, port mirroring, link aggregation and other features. This switch ...
Page 7
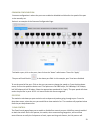
6 getting to know your product package contents: • sk series switch • power cord • rack mount set the front panel of the sk switches has several blue leds. See table1 below for more information. Table 1: front panel led explanation from left to right. Led status operation power blue the switch is po...
Page 8
7 led status operation reset n/a press and hold for about 10 seconds to factory reset the switch sys blue switch is booting up flashing blue switch is turned on off switch is powered off console blue switch is booting up flashing blue activitys through console port off no activity through port sfp p...
Page 9
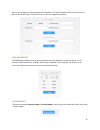
8 4. Enter the switch's default ip address 192.168.1.205 into the address bar and press . 5. A page will appear, prompting you for a username and password. Enter admin as the username and leave the password field blank. Click ok to log in to the web administration portal. Note: it is recommended tha...
Page 10
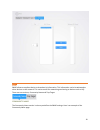
9 dashboard the dashboard provides frequently used quick links to help with more efficient setup..
Page 11
10 menu the menu provides access to all of the configurable options on the switch. An example of the menu is shown below. These options are described in detail in this manual. System the system section contains the four sub sections systems settings, ip setting, acl, snmp system settings there are f...
Page 12
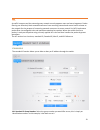
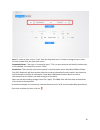
11 further down, is the serial information, this is the information that you will need to console into the switch. The following three parameters can be changed on this page. • name – give the switch a unique name. • location –allows you to enter the location of the switch. Depending on your network...
Page 13
12 you can also change the telnet password at the bottom. The telnet password will be used if you ever need to access the switch via terminal, such as putty or hypertext terminal. Safe mangement safe management determines by which methods users are allowed to access the switch. In this example http ...
Page 14
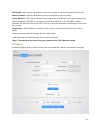
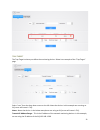
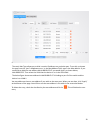
13 acl as traffic increases and the network grows, network security appears more and more important. Packet filtering can effectively block unauthorized users from accessing network and control traffic volume on the network for the purpose of conserving network resources. An access control list (acl...
Page 15
14 ace number - ace controls and monitors access to the object. In the above example this is set to 1. Source ip address – specify the ip address that you would like to permit or deny. Source wildcard – this is used to determine the range of the ip addresses. In the above example, the source ip addr...
Page 16
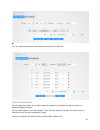
15 acl extended group num – select the group number you would like to use, this is simply an identification number. In this example, it has been set to 10. Ace number - ace controls and monitors access to the object. In the above example this is set to 0. Source ip – specify source ip of packets for...
Page 17
16 *note - to enable this rule on particular ports, please see the “acl reference section” mac ip acl mac ip group num - select the group number you would like to use, this is simply an identification number. In this example, it has been set to 20. Ace num – ace controls and monitors access to the o...
Page 18
17 *note - to enable this rule to particular ports, please see the “acl reference section” acl reference the acl reference page allows you to apply your rules to ports on the switch..
Page 19
18 port - select the port that you would like to apply or view the rule. All acl groups- from this column, select the rule that you would like to use for the port number you selected. Then click the add button, the rule will move over to the right hand column. Reference acl groups- this is where you...
Page 20
19 snmp snmp allows a compliant device to broadcast its information. This information can be broadcasted to other devices on the network. This can be useful for networking monitoring on devices such as ihiji. There are two sections, community name and trap target. Community name the community name s...
Page 21
20 item- to create an item, click on “new” from the drop down menu. To edit or change an item, select the item number from the drop down menu. Community name - then type a “community name.” this is a name that you can identify the device by. In this example, the community name is “sk24.” permissions...
Page 22
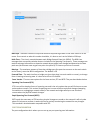
21 trap target the trap target is where you define the monitoring device. Below is an example of the “trap target” page. Select “new” from the drop down menu on the left. Name the device. In this example we are using an ihiji so we will name it “ihiji. Name - name the device. In the below example we...
Page 23
22 snmp version – there are two versions available on the sk-24 switch, v1 and v2c. Version 1 will broadcast the necessary information but there will be no acknowledgement of the reception of the message. Version v2c, will send acknowledgment that a message has been received. When not sure which one...
Page 24
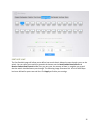
23 common configuration common configuration is where the ports are enabled or disabled and allow for the speed of the port to be manually set. Below is an example of the common configuration page. To disable a port, click on the port, then click on the “down” radio button. Then click “apply” the po...
Page 25
24 temporarily stop sending packets to the switch, thus avoiding packets drop and ensuring a reliable network. Meanwhile, if a certain port receives a pause frame, it will also stop sending packets out. By default, the flow control feature is disabled. To enable flow control, click on the port you w...
Page 26
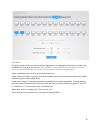
25 port rate limit the port ratelimit page will allow you to define how much data is allowed to pass through a port on the switch. You can select ports and then towards the bottom set the send packets rate control and receive packets rate control to on. Then you can enter the amount of data, in mega...
Page 27
26 ag group the ag group tab is where you can set up link aggregation. Link aggregation allow you to combine the bandwidth of 2 to 8 ports. On a device. Note: the device must have more than one ethernet port on it and must support this feature for it to work. Only 8 port per switch can be aggregated...
Page 28
27 mirror port mirroring allows you to watch traffic using wireshark or another tool, without disturbing the original port. We want to monitor traffic on port 10. We will mirror port 4. Port 4 will be monitoring the traffic on port 10. We will connect a laptop to port 4 with wireshark installed to m...
Page 29
28 mac control mac control allows you to block or allow access or deny access to a device via mac address. Binding configuration binding allows you to bind a mac address on the port. Under the mac type drop down menu, there are 3 options. All, dynamic, static and drop. We will focus on all, dynamic ...
Page 30
29 static the static mac type allows you to bind a certain ip address to a particular port. To set this up choose the port from the “port” dropdown menu. In the mac address field, type in the mac address. If you would like to bind the mac address aa:aa:bb:bb:cc:cc you would type it as shown below, a...
Page 31
30 all the “all” option shows you all mac addresses both dynamic and static. Filter configuration filter configuration allows you to define what mac addresses are allowed through the switch are blocked through the switch. Type the mac address in the “mac address” field. The mac address be typed in t...
Page 32
31 click on “apply” when finished. Vlan the vlan section allows you to set up vlans. Vlans are subnetworks that help to segregate network traffic. The below section describes how to configure vlans. Configuration configuration allows you to set up vlan and assign ports to them. Note: the vlans will ...
Page 33
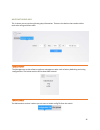
32 below is an example of what the vlan page looks like. First step is to add a vlan under “manage vlans.” click the “add” button as shown below. You will then see the below screen..
Page 34
33 in the “vlan id” field you will type the vlan number that you would like to add. Then name the vlan (optional). Note: the vlan id’s must be set up in the router to work on the switch. In this example, we are adding vlan 6 and naming it “guest.” then click on the “apply” you will now see the new v...
Page 35
34 then click on the ports that you would like to add to the vlan. In this example, we are adding ports 5,7,9,11. When ports are selected they will look like this the ports will then populate next to the vlan as shown below. When you are finished hit apply. The ports on the page will then look like ...
Page 36
35 when you are down click on “apply” at the bottom of the page. The ports will then show the vlan below the port. As seen below. Adding a hybrid port to add a hybrid port, click on the next to the “hybrid” column. The staggered line field will appear as seen below. Click in the untagged field(u)..
Page 37
36 then click on the vlan that you would like to add. This should be your primary vlan or the vlan that you want the physical device to be on. In this example we are adding vlan 1. Vlan 1 is the after clicking on vlan 1, it will populate below. Then click on the tagged (t) field. Click the vlans tha...
Page 38
37 the finished product is shown below. This example shows port 1 as the default vlan with vlan 2-6 tagged on port 21 and 22. In the port image, the hybrid ports will show in a broken line box as shown below. Adding a trunk in port to add a trunk port, click on the next to the “trunk” column. The st...
Page 39
38 select the vlans you would like to tag. They will then show up in the (t) field as shown below. Then click on the “assigned port” select the following ports you want the trunk setting to be on. In this example we are using ports 8, 10, and 12. Once finished, it will look something like this. In t...
Page 40
39 when finish click on “apply.” traffic the traffic section is where you can configure qos, stp and igmp. Qos quality of service (qos) allows you to prioritize the traffic on your network. There are two tabs in this section, schedule and apply. We will focus on the apply section. Apply you will see...
Page 41
40 first click on the ports that you would like to prioritize. In this example 5, 7 and 9 are selected. Select cos-based from the drop down menu under “qos” type. Then assign the priority from the drop down meu. In this example we chose 7, which is the highest priority. When you are finished hit app...
Page 42
41 stp spanning tree protocol (stp) prevents loops that might be caused in a network. Loops are caused when there are multiple “paths” in a network between a device on the network and a device such as a router or a switch. The loop can then cause broadcast storms. Broadcast storms occur when broadca...
Page 43
42 max hops - maximum number of hops that would be required to get back to the main switch or to the router. If not certain to what this number should be, it is best to use it at the default of 20 hops. Hello time – the time in seconds between each bridge protocol data unit (bpdu). The bpdu are mess...
Page 44
43 to enable spanning tree on a particular port, click on the port that you would like to configure spanning tree on. Status – this is where you enable or disable spanning tree on a port. In this example we are enabling it on port 3. Priority – this is the port priority, by default this should be se...
Page 45
44 igmp snooping igmp snooping is the process of listening to internet group management protocol (igmp) network traffic. Igmp snooping, as implied by the name, is a feature that allows a network switch to listen to on the igmp conversation between hosts and routers. By listening to the conversations...
Page 46
45 multicast group info this is where you set up the multicast group information. These are the devices that need to talk to each other using multicast traffic. Management the management section allows to perform management tasks such as factory defaulting and saving configurations. The below sectio...
Page 47
46 configuration file the configuration file page is shown below. The text shown in the below figure, is the plain text of the configuration. Here you can save or delete your configuration of the switch. To save the configuration, click on the “download” button. File upload the file upload tab allow...
Page 48
47 to upload a file, click on the” browse” button, and navigate to the file you want to upload. You will see the file next to the “browse” button. If it is a configuration file (.Cfg) click on “import” if it is a firmware file (.Iso) click upgrade, like in the below example.
Page 49
48 log this section is used for pakedge use when to determine issues on the switch when troubleshooting steps have been exhausted. Lldp lldp (link layer discovery protocol) is a layer 2 protocol that is used for network devices to advertise their own device information periodically to neighbors on t...
Page 50
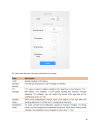
49 the table below describes the options displayed on this page..
Page 51
50 port setup select the port setup select allows you to configure the lldp port properties. By selecting a port, you will be able to make the following changes from the below dropdown menu. • disable – disable the lldp functions on the selected port. • tx – transmit lldp packets only. • rx – receiv...
Page 52
51 port statistics the port statistics page will display lldp statistics on each port..
Page 53
52.
Page 54
53 appendix a – technical support please visit our website for up-to-date support information: website: www.Pakedge.Com email: support@pakedge.Com contact information: pakedge device & software inc. 3847 breakwater avenue hayward, ca 94545-3606.
Page 55
54 appendix b- specifications feature description specifications powered by poe no port orientation available as rear and front facing management 1. Telnet configuration 2. Console interface configuration 3. Snmp (simple network management protocol) pakedge zone support basic zones port density tota...
Page 56
55 dram 128mbits power input voltage 100-240ac, 50/60hz physical specification dimensions 17.36 x 10 x 1.73 in (44.09 x 25.4 x 4.39 cm) weight 6.7 lbs (3.04 kg) operation temperature -0°c-40°c (32°f-104°f) storage temperature -40 ~ 70° (-40°~158°f) operating humidity 10% - 90% non-condensing certifi...
Page 57
56 appendix c- limited warranty sk series congratulations on your purchase of a pakedge device & software product! Pakedge designs and manufactures the finest home networking products. With proper installation, setup, and care, you should enjoy many years of unparalleled performance. Please read thi...
Page 58
57 installtion and setup work be performed only by an authorized pakedge dealer to protect your rights under this warranty. This will also ensure that you enjoy the fine performance your pakedge product is capable of providing. Rights, limits, and exclusions pakedge limits its obligation under any i...