- DL manuals
- RAD Data Communications
- Network Router
- SecFlow-4
- Installation and user manual
RAD Data Communications SecFlow-4 Installation and user manual
Summary of SecFlow-4
Page 1
Installation and operation manual 25-284 secflow-4 ver.3.10 cfm configuration flow 25.4 cfm commands hierarchy + root + config terminal + [no] oam + [no] cfm + [no] shutdown + [no] domain-name domain-name - level + [no] ma ma-name - [no] ais-lck - [no] ais-lck-interval {1min
Page 2: Ins
Secflow-4 modular ruggedized scada-aware ethernet switch/router version 3.10 ins tal latio n and u s e r g u id e.
Page 4: Secflow-4
Secflow-4 modular ruggedized scada-aware ethernet switch/ router version 3.10 installation and operation manual notice this manual contains information that is proprietary to rad data communications ltd. ("rad"). No part of this publication may be reproduced in any form whatsoever without prior writ...
Page 5: Limited Warranty
Installation and operation manual ii secflow-4 ver.1.00 limited warranty rad warrants to distributor that the hardware in the secflow-4 to be delivered hereunder shall be free of defects in material and workmanship under normal use and service for a period of twelve (12) months following the date of...
Page 6: Safety Symbols
Installation and operation manual secflow-4 ver.1.00 iii general safety instructions the following instructions serve as a general guide for the safe installation and operation of telecommunications products. Additional instructions, if applicable, are included inside the manual. Safety symbols this...
Page 7
Installation and operation manual iv secflow-4 ver.1.00 handling energized products general safety practices do not touch or tamper with the power supply when the power cord is connected. Line voltages may be present inside certain products even when the power switch (if installed) is in the off pos...
Page 8
Installation and operation manual secflow-4 ver.1.00 v the maximum permissible current capability of the branch distribution circuit that supplies power to the product is 16a (20a for usa and canada). The circuit breaker in the building installation should have high breaking capacity and must operat...
Page 9
Installation and operation manual vi secflow-4 ver.1.00 when using shielded or coaxial cables, verify that there is a good ground connection at both ends. The grounding and bonding of the ground connections should comply with the local codes. The telecommunication wiring in the building may be damag...
Page 10: Fcc-15 User Information
Installation and operation manual secflow-4 ver.1.00 vii fcc-15 user information this equipment has been tested and found to comply with the limits of the class a digital device, pursuant to part 15 of the fcc rules. These limits are designed to provide reasonable protection against harmful interfer...
Page 11: Mise Au Rebut Du Produit
Front matter installation and operation manual viii secflow-4 ver.1.00 f ran çai s mise au rebut du produit afin de faciliter la réutilisation, le recyclage ainsi que d'autres formes de récupération d'équipement mis au rebut dans le cadre de la protection de l'environnement, il est demandé au propri...
Page 12
Installation and operation manual front matter secflow-4 ver.1.00 ix f ran çai s certains produits peuvent être équipés d'une diode laser. Dans de tels cas, une étiquette indiquant la classe laser ainsi que d'autres avertissements, le cas échéant, sera jointe près du transmetteur optique. Le symbole...
Page 13
Front matter installation and operation manual x secflow-4 ver.1.00 f ran çai s connexion au courant du secteur assurez-vous que l'installation électrique est conforme à la réglementation locale. Branchez toujours la fiche de secteur à une prise murale équipée d'une borne protectrice de mise à la te...
Page 14: Secflow-4
Secflow-4 modular ruggedized scada- aware ethernet switch/router initial setup.
Page 15: Package Contents
Initial setup 2-2 secflow-4 thank you for purchasing secflow products. Please observe product installation guide for safety instructions and complete assembly / installation instructions package contents the secflow package includes the following items: • secflow switch with ordered configuration • ...
Page 16: Address
Initial setup secflow-4 4-3 startup and initial configuration upon delivery the device can only be accessed via the console port (“con”) or via outband port (ip). For initial configuration using the serial console interface (rs 232): 1. Connect the dc voltage and power up the unit. 2. Using the supp...
Page 17
Initial setup 4-4 secflow-4 step description command (in cli session via the console port) 4 commit and go back to configuration mode commit ; top; 5 create a new logical in-band ip interface. Router; interface sw0; 6 assign static ip to the interface. "ee" represents the subnet mask (values :8-30)....
Page 18: Secflow-4
Secflow-4 modular ruggedized scada- aware ethernet switch/router installation guide.
Page 19: Chapter 1
Installation guide 1-2 secflow-4 ver.3.10 chapter 1 introduction the secflow service-aware industrial ethernet switches combine a ruggedized ethernet platform with a unique application-aware processing engine. As an industrial ethernet switch the secflow switches provide a strong ethernet and ip fea...
Page 20: Chapter 2
Installation guide secflow-4 ver.3.10 2-3 chapter 2 key features the secflow-4 devices offer the following features: • wire speed, non-blocking layer 2 switching • high-density modular system • advanced ethernet and ip feature-set • application-aware firewall per port • integrated vpn agent • ethern...
Page 21: Chapter 3
Installation guide 3-4 secflow-4 ver.3.10 chapter 3 using this document 3.1 documentation purpose this user guide includes the relevant information for configuring then secflow-4 functionalities. It provides the complete syntax for the commands available in the currently- supported software version ...
Page 22
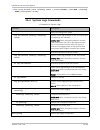
Installation guide secflow-4 ver.3.10 3-5 indicating special information to which the user needs to pay special attention. Indicating special instructions to avoid possible damage to the product. Indicating special instructions to avoid possible injury or death. The table below explains the conventi...
Page 23: Chapter 4
Installation guide 4-6 secflow-4 ver.3.10 chapter 4 safety information danger of electric shock! Avoid any contact with the marked surface while the product is energized or connected to outdoor telecommunication lines. Protective earth: the marked lug or terminal should be connected to the building ...
Page 24
Installation guide secflow-4 ver.3.10 4-7 remove the power cord from a power-supply unit before installing it or remove it from the device. Otherwise, as a result, the power supply or the device could be damaged. (the device can be running while a power supply is being installed or removed, but the ...
Page 25: Chapter 5
Installation guide 5-8 secflow-4 ver.3.10 chapter 5 system description the secflow-4 are modular switches that include power supply modules, main switching unit, several types of interface modules and an application processing module. 5.1 power supply module the secflow-4 comes with up to two power ...
Page 26
Installation guide secflow-4 ver.3.10 5-9 5.4 i/o modules the i/o modules, or media interface modules contain the connectivity for the devices that are to be managed. The i/o modules have both ethernet interfaces as well as serial interfaces providing a flexible infrastructure for connectivity. The ...
Page 27: Chapter 6
Installation guide 6-10 secflow-4 ver.3.10 chapter 6 installing secflow-4 this section includes the relevant information for installing the device. Install this equipment only in a restricted access location per ul 60950-1 clause 1.2.7.3. 6.1 package contents the secflow-4 package includes the follo...
Page 28
Installation guide secflow-4 ver.3.10 6-11 locate on the back of the backplane the din mounting brackets (see figure 1 ). Take the backplane and approach the din rail such that the side with the slots has the numbers facing down. To mount the backplane on the din rail angle the backplane such that t...
Page 29
Installation guide 6-12 secflow-4 ver.3.10 attach the rack mount adapter bracket to the secflow-4 by inserting the backplane into the adapter and securing it with screws. 6.7 inserting the modules the system modules are designed to be plugged into the front side using data connectors per module type...
Page 30
Installation guide secflow-4 ver.3.10 6-13 to install the grounding wire: 1. Prepare a minimum 10 american wire gauge (awg) grounding wire terminated by a crimped two-hole lug with hole diameter and spacing as shown in the below figure. Use a suitable crimping tool to fasten the lug securely to the ...
Page 31: Chapter 7
Installation guide 7-14 secflow-4 ver.3.10 chapter 7 connecting to a power source the secflow-4 switch has two power-supply slots, both supporting 24v and 48v dc power. The device can be installed with either one or two psus. 7.1 power supply leds the following table lists the secflow psu leds shown...
Page 32
Installation guide secflow-4 ver.3.10 7-15 7.2 connecting a dc power source each psu module includes dual power inputs and power input for the 48v dc for power over ethernet (poe). Before connecting the device to a dc power source, make sure that: • the dc supply source is located within the same pr...
Page 33
Installation guide 7-16 secflow-4 ver.3.10 the dc power supply does not have a power on/off button and is automatically turned on when the cabling is completed and the power to the feed line is turned on. Before wiring the dc plug or connecting power to the device, verify that the power to the feed ...
Page 34
Installation guide secflow-4 ver.3.10 7-17 4. For a redundant dc psu, repeat the steps above to connect it. 5. In such scenario, both modules' ps leds are turned on..
Page 35: Chapter 8
Installation guide 8-18 secflow-4 ver.3.10 chapter 8 i/o modules this device has 7 slots, supporting i/o modules. The secflow-4 can be installed with up to 7 i/o modules. The i/o modules are installed in slot numbers 3 and 7 (see figure ). These are indicated by the numbers on the lower part of the ...
Page 36
Installation guide secflow-4 ver.3.10 8-19 table 1: i/o card types: module type p/n notes serial media module if-sl004e 4 ports serial module eth sfp media module if-sp004e 4 ports sfp module eth copper media module if-tp004e future eth fiber media module if-fo004e future the i/o module has led indi...
Page 37: Chapter 9
Installation guide 9-20 secflow-4 ver.3.10 chapter 9 application service module the application service module provides the advanced features of the secflow-4. This module can only be installed in slot 3 (see figure ). The application service module provides: • application aware firewall • serial tu...
Page 38
Installation guide secflow-4 ver.3.10 9-21 the application service module can only be installed in slot #3. Caution.
Page 39: Chapter 10
Installation guide 10-22 secflow-4 ver.3.10 chapter 10 management (cpu) module the secflow-4 is equipped with a management cpu module that provides system management functions and communicates with snmp (snmp agent) and the iems management software. The management cpu module also manages software up...
Page 40
Installation guide secflow-4 ver.3.10 10-23 figure 6: rear view of management cpu module the management cpu module is equipped with leds on the front panel to indicate the status of the device. Thumb screws backplane connector screws guide pin holes guide pin holes.
Page 41
Installation guide 10-24 secflow-4 ver.3.10 table 4: management cpu module led descriptions led indicator color description run red green fault normal maj red major system alarm min yellow minor system alarm rm green (solid) green (blinking) off redundancy manager –ring status ok redundancy manager ...
Page 42: Chapter 11
Installation guide secflow-4 ver.3.10 11-25 chapter 11 switch configuration 11.1 connecting to the console port the console port is a eia232 vt-100 compatible port to enable the definition of the device's basic operational parameters. To connect the device to a pc using the console port: 1. Connect ...
Page 43
Installation guide 11-26 secflow-4 ver.3.10 11.2 boot loader configuration the boot process performs low-level cpu initialization, loads the default operating system software image to the memory, and re-boots the device. At device startup, the loader pauses for 5 seconds enabling access to the loade...
Page 44
Installation guide secflow-4 ver.3.10 11-27 step description command step 3 reload the device reset 11.4 initial configuration the device's initial parameters will need to be defined upon initial access to the device through the console port. These initial parameters are stored in non- volatile memo...
Page 45: Chapter 12
Installation guide 12-28 secflow-4 ver.3.10 chapter 12 using the command line interface (cli) the cli is a network management application operated through an ascii terminal. Using the cli commands, users can configure the device parameters and maintain them, receiving text output on the terminal mon...
Page 46
Installation guide secflow-4 ver.3.10 12-29 • initiating the configuration mode configuration mode the configuration mode is the mode in which users can change the device configuration. To enter this mode from operational mode, use the config terminal command. Device-name#config terminal entering co...
Page 47
Installation guide 12-30 secflow-4 ver.3.10 • arguments specify the command’s configuration parameters • the cli commands are not case sensitive. The general cli syntax is represented by the following format: device-name[(config- ...)]#keyword(s) [ argument(s) ] ... [keyword(s)] [ argument(s) ] in t...
Page 48
Installation guide secflow-4 ver.3.10 12-31 command purpose abbreviated-command to display a command’s possible completions, type the partial command followed immediately by or . If the partially typed command uniquely identifies a command, the full command name is displayed. Otherwise, the cli disp...
Page 49: Chapter 13
Installation guide 13-32 secflow-4 ver.3.10 chapter 13 setup and maintenance 13.1 cli over secure shell (ssh) and telnet after the initial device ip configuration, the device can be managed remotely via ssh or telnet. Ssh to access the device via ssh protocol, install one of the below supported ssh ...
Page 50
Installation guide secflow-4 ver.3.10 13-33 13.3 software download the device's executable software-image is stored in an erasable flash memory. New versions of the software image are available from time to time. Use tftp/ftp to download new software-image files. The device remains operational durin...
Page 51
Installation guide 13-34 secflow-4 ver.3.10 step description command via ftp name:password> is the ftp server username and password is the ftp server ip address name> is the software-image file name file cp os-image ftp:// @ / step 4 activate the new image file activate-os-image software- image file...
Page 52: Secflow-4
Secflow-4 modular ruggedized scada-aware ethernet switch/router user guide.
Page 53: Chapter 1
Installation and operation manual 1-2 secflow-4 ver.3.10 chapter 1 introduction the secflow service-aware industrial ethernet switches, combine a ruggedized ethernet platform with a unique application-aware processing engine. As an industrial ethernet switch the secflow switches provide a strong eth...
Page 54
Installation and operation manual secflow-4 ver.3.10 1-3 1.2 using this document documentation purpose this user guide includes the relevant information for configuring then secflow-4 functionalities. It provides the complete syntax for the commands available in the currently- supported software ver...
Page 55
Installation and operation manual 1-4 secflow-4 ver.3.10 conventions used the conventions below are used to inform important information: indicating special information to which the user needs to pay special attention. Indicating special instructions to avoid possible damage to the product. Indicati...
Page 56: Chapter 2
Installation and operation manual secflow-4 ver.3.10 2-5 chapter 2 device administration 2.1 using the command line interface (cli) the cli is a network management application operated through an ascii terminal. Using the cli commands, users can configure the device parameters and maintain them, rec...
Page 57
Installation and operation manual 2-6 secflow-4 ver.3.10 • viewing the system status • controlling the cli environment • monitoring and troubleshooting network connectivity • initiating the configuration mode configuration mode the configuration mode is the mode in which users can change the device ...
Page 58
Installation and operation manual secflow-4 ver.3.10 2-7 example device-name(config)#router ospf interface 200.1.1.1 device-name(config-interface- 200.1.1.1 )#commit aborted: 'router ospf interface 200.1.1.1 area-id' is not configured device-name(config-interface- 200.1.1.1 )# using the cli command ...
Page 59
Installation and operation manual 2-8 secflow-4 ver.3.10 minimum abbreviation the cli accepts a minimum number of characters that uniquely identify a command. Therefore you can abbreviate commands and parameters as long as they contain enough letters to differentiate them from any other available co...
Page 61
Installation and operation manual 2-10 secflow-4 ver.3.10 command purpose ? Lists all commands available in the current command mode. Example device-name(config-service)#? Possible completions: customer sdp vpls vpws --- commit commit current set of changes exit exit from current mode help provide h...
Page 63
Installation and operation manual 2-12 secflow-4 ver.3.10 you can also use the show history command to display a list of executed commands. Device-name#show history 05:46:29 -- router ospf 05:46:32 -- router-id 1.1.1.1 05:46:37 -- area 0 05:46:44 -- exit 05:46:46 -- area 1 05:46:49 -- exit 05:47:02 ...
Page 64
Installation and operation manual secflow-4 ver.3.10 2-13 key function ctrl+c interrupts the current input and moves to the next command line ctrl+t transposes characters esc+m enters multi-line mode (>): [entering multiline mode, exit with ctrl-d.] ctrl+z returns to operational mode general operati...
Page 66
Installation and operation manual secflow-4 ver.3.10 2-15 command description history size> specifies the number of commands kept in the history list: • size: in the range of default: 10 no history restores to default id displays the user’s identity information (such as username and user groups) ign...
Page 67
Installation and operation manual 2-16 secflow-4 ver.3.10 show commands + root - show - show routes - show bfd-session - show bist - show ethernet - show port - show snmp - show snmp-server - show snmp-system - show syslog - show active-boot parameters - show cli - show clock - show history - show i...
Page 68
Installation and operation manual secflow-4 ver.3.10 2-17 command description show cli displays the cli configuration: • autowizard • complete-on-space • display-level • history • idle-timeout • ignore-leading-space • output- • paginate • screen-width • service prompt config • show-defaults • termin...
Page 69
Installation and operation manual 2-18 secflow-4 ver.3.10 general configuration mode commands + root + config terminal - abort - clear - commit [comment comment-description ] - commit label label-description - commit persist-id id > - commit abort [persist-id id >] - commit and-quit [comment comment...
Page 71
Installation and operation manual 2-20 secflow-4 ver.3.10 top command returns you to the configuration mode from any other mode, and executes the selected command in the configuration mode validate validates the current configuration 2.2 router license configuration license configuration commands hi...
Page 72
Installation and operation manual secflow-4 ver.3.10 2-21 cli over secure shell (ssh) the operating system offers both an ssh server and an ssh client. You can connect to your device's ssh server from an ssh client, or you can connect your device's ssh client to another device that has an ssh server...
Page 73
Installation and operation manual 2-22 secflow-4 ver.3.10 config system telnet-server no shutdown port 2000 access source-ip 172.17.203.150/32 !Subnet must be 32 access source-ip 172.18.212.100/32 !Subnet must be 32 access source-ip 192.168.0.1/32 !Subnet must be 32 ! ! Managing the device via snmp ...
Page 74: Chapter 3
Installation and operation manual secflow-4 ver.3.10 3-23 chapter 3 association of ports 3.1 addressing depending on the harware variant ordered your switch will hold phisycal ethernet and serial ports. General addressing for ports uu/ss/pp [unit/slot/port] 3.2 3080 • serial, rj 45 ports, are rs-232...
Page 75
Installation and operation manual 3-24 secflow-4 ver.3.10 serial io cards require the use of the application card to be installed on slot 3. When the application card is used, it must be placed on slot 3. Its physical sfp port is addressed as 1/3/4 and is a standard ethernet port supporting all the ...
Page 76: Chapter 4
Installation and operation manual secflow-4 ver.3.10 4-25 chapter 4 mac-address table (fdb) 4.1 overview the mac (media access control) address is the unique hardware number that identifies the computer on a local area network (lan) or other network. Mac addresses are 12-digit hexadecimal numbers (4...
Page 77
Installation and operation manual 4-26 secflow-4 ver.3.10 • filtered entries —a filtered entry can be created in two ways. One way is to configure filter entry statically for blocking the traffic from and to specific mac address on the device. The second way is to use the port security or the port l...
Page 78
Installation and operation manual secflow-4 ver.3.10 4-27 mac-address table commands mac-address table commands command description config terminal enters the configuration mode port uu/ss/pp enters the specific port’s configuration mode no port [uu/ss/pp] removes the port configurations learn-new-m...
Page 79
Installation and operation manual 4-28 secflow-4 ver.3.10 4.2 mac learning security policies the port security and port limit policies control how many addresses the device can learn for a particular port. Port security: mac addresses are entered in the mac address table with a secure status. Secure...
Page 80
Installation and operation manual secflow-4 ver.3.10 4-29 command descriptions command description config terminal enters configuration mode ethernet enters ethernet configuration mode mac-learning learning-profile name mandatory defines a specific mac-learning profile and enters the mac-learning co...
Page 81
Installation and operation manual 4-30 secflow-4 ver.3.10 no port [uu/ss/pp] removes port configurations mac-learning-profile name assigns a mac-learning profile to a port: name: profile name no mac-learning-profile [ name ] removes the assigned mac-learning profile: name: (optional) profile name tx...
Page 82
Installation and operation manual secflow-4 ver.3.10 4-31 command description file activate-os-image file-name sets boot statements to load the selected software image on startup: file-name: the file name file backup binary-running- config flash creates a backup file in the local flash system: defau...
Page 83
Installation and operation manual 4-32 secflow-4 ver.3.10 command description file cp protocol[user[:password]@]ipv4[: port]/file-name1 file-name2 copies a file from a tftp/ftp server to the local flash system: protocol: the protocol type (tftp://a.B.C.D or ftp://user:pass@a.B.C.D). For the tftp ser...
Page 84
Installation and operation manual secflow-4 ver.3.10 4-33 command description file cp running-configuration file-name copies the running-configuration file to the local flash system: file-name: the file name file ls [os-image] lists the content of the local flash system, used, and free memory space:...
Page 85
Installation and operation manual 4-34 secflow-4 ver.3.10 configurations of application features (as serial, security and gre) are saved in a file called rf_db.Tar.Gz.1. This file can be backuped by copying it locally or by uploading it to a server . Activation is by deleting older file, downloading...
Page 86
Installation and operation manual secflow-4 ver.3.10 4-35 secflow_1#file backup binary-running-config ftp://ftp:ftp@172.18.212.200/save_1 2. Restore from the server. Secflow_1#file restore binary-running-config ftp://ftp:ftp@172.18.212.200/save_1 restore of backup configuration file will reload the ...
Page 87
Installation and operation manual 4-36 secflow-4 ver.3.10 accessing safe mode to enter safe mode, you need to first connect to the device directly through the devices’ serial console port. To access safe mode: power on or reload the device. During the device’s initialization, press the s key within ...
Page 88
Installation and operation manual secflow-4 ver.3.10 4-37 summer time (daylight saving time) you can configure your device to observe the daylight saving time (dst). The dst is followed by the u.S. Standards. You can have the device advance the clock one hour at 2:00 a.M. On the first sunday in apri...
Page 89
Installation and operation manual 4-38 secflow-4 ver.3.10 example – manual setup of time and date using cli secflow _3700#config entering configuration mode terminal secflow _3700#(config)#system secflow _3700#(config-system)#time secflow _3700#(config-time)#date 2011-06-27t12:33:00 secflow _3700#(c...
Page 90
Installation and operation manual secflow-4 ver.3.10 4-39 command description no system removes the system configurations (system time and date configurations, snmp, periodic monitoring configurations, and etc.) time enters the time server configuration mode no time removes the system time configura...
Page 91
Installation and operation manual 4-40 secflow-4 ver.3.10 command description no authentication key-id removes the md5 authentication key refresh-interval interval> defines the number of minutes to synchronize the device’s system time to the ntp server: interval: in the range of minutes (the upper l...
Page 92
Installation and operation manual secflow-4 ver.3.10 4-41 privilege description administrators full read/write privileges (with no restrictions) for layer 2 and layer 3. Network-admins read/write privileges for layer 2 and layer 3, without access to security (usernames and passwords), debug commands...
Page 94
Installation and operation manual secflow-4 ver.3.10 4-43 command description privilege-profile privilege- profile-name mandatory defines a new privilege profile and enters the profile configuration mode: • privilege-profile-name: a string of characters default: administrators, net-admins, technicia...
Page 95
Installation and operation manual 4-44 secflow-4 ver.3.10 example – manual setup of user assignment of user "cto" with password "cto" and membership to "admin" secflow_3700#config entering configuration mode terminal secflow_3700(config)#system secflow_3700(config-system)#security secflow_3700(confi...
Page 96
Installation and operation manual secflow-4 ver.3.10 4-45 device-name(config)#system device-name(config-system)#security privilege-profile telco device-name(config-privilege-profile-telco)#commit commit complete. Device-name(config-privilege-profile-telco)#command-access-rule 1 device-name(config-co...
Page 97
Installation and operation manual 4-46 secflow-4 ver.3.10 radius negotiation procedure the below figure demonstrates a typical radius negotiation procedure. In this example: 1. The user sends a telnet request to connect to a 3080 device (the nas). 2. The device sends an access request packet to the ...
Page 99
Installation and operation manual 4-48 secflow-4 ver.3.10 command description deadtime defines the number of minutes the device waits for an authentication response before declaring the radius server unavailability and skips to the next radius server: minutes: in the range of minutes default: 3 minu...
Page 100
Installation and operation manual secflow-4 ver.3.10 4-49 configuration example 1. Select the radius server and define the shared secret key: device-name#config terminal device-name(config)#system device-name(config-system)#security device-name(config-security)#radius-server host 10.2.42.137 device-...
Page 101
Installation and operation manual 4-50 secflow-4 ver.3.10 the request is forward to the radius server for verification. If the authentication server (radius server) determines the credentials are valid, the supplicant is allowed to access resources located on the protected side of the network. The a...
Page 102
Installation and operation manual secflow-4 ver.3.10 4-51 802.1x configuration commands command description config terminal enters the configuration mode ethernet enters the system configuration mode [no] dot1x shutdown enters the security configuration mode [no] dot1x port uu/ss/pp select port for ...
Page 103
Installation and operation manual 4-52 secflow-4 ver.3.10 tacacs+ negotiation procedure a user’s attempt to connect to the device triggers the following procedure: 1. The nas mediates between the user and the tacacs+ server requesting and obtaining a username prompt. 2. When the user types a usernam...
Page 104
Installation and operation manual secflow-4 ver.3.10 4-53 multiprotocol support does not support some protocols, such as: • appletalk remote access (ara) • netbios frame protocol control • novell asynchronous services interface (nasi) • x.25 pad connection offers multiprotocol support tacacs+ config...
Page 105
Installation and operation manual 4-54 secflow-4 ver.3.10 tacacs+ configuration commands command description config terminal enters the configuration mode system enters the system configuration mode security enters the security configuration mode tacplus host a.B.C.D mandatory selects tacacs+ server...
Page 106
Installation and operation manual secflow-4 ver.3.10 4-55 ------------------------------------------------- tac_plus.Conf ------------------------------------------------- key = " tacacsplus " user = admin { login = cleartext "adminpass" pap = cleartext "adminpass" service = secflow { group = "admin...
Page 107
Installation and operation manual 4-56 secflow-4 ver.3.10 username: richy password: username: 2. When accessing the device using local username admin and password adminpass , the tacacs+ server sends an accept reply, authenticating the user: username: admin password: adminpass device-name#.
Page 108: Chapter 5
Installation and operation manual secflow-4 ver.3.10 5-57 chapter 5 vty (virtual terminal) virtual terminal interface (vty) is used solely to control inbound connections. They are a function of software - there is no hardware associated with them. 5.1 vty session commands vty session commands hierar...
Page 109: Chapter 6
Installation and operation manual 6-58 secflow-4 ver.3.10 chapter 6 physical ports and logical interfaces 6.1 fast and giga ethernet ports the secflow devices allow service providers to deliver multiple services on separate user ports. Multiple application flows are supported over a single customer ...
Page 112
Installation and operation manual secflow-4 ver.3.10 6-61 command description shutdown disables the interface no shutdown enables the interface command description show port name uu/ss/pp displays the status and configuration of the selected port: uu/ss/pp: unit/slot/port show port statistics displa...
Page 113
Installation and operation manual 6-62 secflow-4 ver.3.10 lags are numbered from 1 to 14. Each lag can consist of up to eight compatibly configured ports. There are two lag types: • static lags, which consist of individual gigabit ethernet links bundled into a single logical link, treat multiple dev...
Page 114
Installation and operation manual secflow-4 ver.3.10 6-63 link aggregation control protocol (lacp) the link aggregation protocol (lacp) is the protocol used by a lag. Lacp, defined in ieee 802.3ad, dynamically groups similarly configured ports into a single logical link (aggregate port) to increase ...
Page 116
Installation and operation manual secflow-4 ver.3.10 6-65 command description no lacp enable restores to default lacp administrative-key defines the lacp administrative key, determining the ability of the port to aggregate with other ports: number: in the range of default: 1 if a single lag is confi...
Page 118
Installation and operation manual secflow-4 ver.3.10 6-67 configuring device 1 in the following example ports 1/1/1, 1/1/2, 1/1/3 , and 1/1/4 are added respectively to lag ag1 and ag2 on which lacp is enabled. 1. Create static lags ag1 and ag2. Add relevant ports to both lags: device-name(config)#et...
Page 119
Installation and operation manual 6-68 secflow-4 ver.3.10 device-name#show ethernet lag lag-id ag1 details interface name ag1 mode: network distribution type: l2 operational status: up lacp: enabled lacp mode: active system id: 005043b5aa9c system priority: 32768 administrative key: 1 marker: disabl...
Page 120
Installation and operation manual secflow-4 ver.3.10 6-69 device-name#show ethernet lag lag-id ag1 details interface name ag1 mode: network distribution type: l2 operational status: up lacp: enabled lacp mode: active system id: 005043b5aa66 system priority: 32768 administrative key: 1 marker: disabl...
Page 121
Installation and operation manual 6-70 secflow-4 ver.3.10 6.5 resilient links resilient links protect critical links and prevent network downtime. A resilient link consists of a main link and a standby (backup) link that together form a resilient- link pair. Under normal network conditions, the main...
Page 123: Chapter 7
Installation and operation manual 7-72 secflow-4 ver.3.10 chapter 7 virtual lan (vlan)—ieee 802.1q 7.1 overview vlan tagging is a standard designed for grouping hosts with common requirements, allowing them to communicate as if they were on the same lan regardless of their physical location. This al...
Page 124
Installation and operation manual secflow-4 ver.3.10 7-73 a port can be a member of one or more vlans. However, only one of these vlans can be the port’s default vlan. Initially all the device ports are members of a vlan named default (vlan id 1). Ports assigned to different vlans can communicate on...
Page 125
Installation and operation manual 7-74 secflow-4 ver.3.10 vlan tagging and egress traffic in addition to the vlans a port is assigned to, the system administrator defines whether the port is a tagged or an untagged member of a specified vlan. This affects the outgoing (egress) traffic process: • if ...
Page 126
Installation and operation manual secflow-4 ver.3.10 7-75 • ssh to the device • snmp management • pinging the device • tftp download or upload receiving outgoing syslog messages by default, management access to the device is disabled on all vlans. When configuring a particular vlan (in vlan configur...
Page 127
Installation and operation manual 7-76 secflow-4 ver.3.10 7.3 vlans commands hierarchy + root + config terminal + [no] vlan vlan-name - [no] tagged uu/ss/pp - [no] untagged uu/ss/pp - [no] management - [no] routing-interface swn - show vlan 7.4 vlans configuration commands command description config...
Page 128
Installation and operation manual secflow-4 ver.3.10 7-77 command description routing-interface swn attaches an ip interface to the specified vlan. The sw0 ip interface is attached only to the default vlan (vlan id 1). Swn: an ip interface number in the range of no routing-interface detaches the ip ...
Page 130: Chapter 8
Installation and operation manual secflow-4 ver.3.10 8-79 chapter 8 igmp snooping 8.1 overview internet group multicast protocol (igmp) snooping constrains the flooding of multicast traffic by dynamically configuring ports so that multicast traffic is forwarded to only those ports where the attached...
Page 131
Installation and operation manual 8-80 secflow-4 ver.3.10 initial igmp join message a multicast router (mrouter) is a router that runs a multicast routing protocol and participates in the multicast tree. On the edge of the network, a multicast router is connected to an igmp snooping device. The igmp...
Page 132
Installation and operation manual secflow-4 ver.3.10 8-81 fast-leave processing the igmp snooping fast-leave processing removes a port that receives a leave group message from the multicast forwarding table immediately . Fast-leave processing ensures optimal bandwidth management for all hosts on a s...
Page 133
Installation and operation manual 8-82 secflow-4 ver.3.10 - [no] ip-igmp-snooping router-alert-check - [no] ip-igmp-snooping router-timers last-member-query- interval - [no] ip-igmp-snooping router-timers query-interval - [no] ip-igmp-snooping router-timers robustness - [no] ip-igmp-snooping router-...
Page 134
Installation and operation manual secflow-4 ver.3.10 8-83 command description vlan vlan-name mandatory creates a vlan with the specified name and id (vlan tag) and enters the vlan configuration mode: vlan-id: in the range of vlan-name: a string of characters no vlan vlan-name removes the existing vl...
Page 135
Installation and operation manual 8-84 secflow-4 ver.3.10 command description ip-igmp-snooping router- timers router-query-interval interval> defines the time that the multicast router waits to receive a response to an igmp general query: interval: in the range of seconds default: 10 seconds no ip-i...
Page 136
Installation and operation manual secflow-4 ver.3.10 8-85 command description no untagged uu/ss/pp igmp- snooping mrouter-block restores to default tagged uu/ss/pp igmp-snooping enables igmp snooping on a specified port: uu/ss/pp: 1/1/1-1/1/4, 1/2/1-1/2/8 default: disabled no tagged uu/ss/pp igmp-sn...
Page 137
Installation and operation manual 8-86 secflow-4 ver.3.10 command description ip a.B.C.D defines the ip address of the multicast group: a.B.C.D: in the range of no ip a.B.C.D removes the defined multicast ip address: a.B.C.D: in the range of ip-source a.B.C.D a1.B1.C1.D1 defines a source-specific mu...
Page 139
Installation and operation manual 8-88 secflow-4 ver.3.10 device-name#show igmp-snooping vlan 100 mrouters ============================================================================= vlan id 100 - igmp snooping mrouters ============================================================================= ...
Page 140: Chapter 9
Installation and operation manual secflow-4 ver.3.10 9-89 chapter 9 spanning tree (rstp/mstp) 9.1 overview spanning tree protocol (stp) is a layer 2 link management protocol that provides path redundancy while preventing undesirable loops in the network. An ethernet network will function properly if...
Page 141
Installation and operation manual 9-90 secflow-4 ver.3.10 8 bytes bridge id (bid) 1 2 3 4 5 6 7 bridge priority 6-byte mac address 9.3 election of the root bridge the switches in the network exchange data messages called bridge protocol data units (bpdus) for information gathering about other switch...
Page 142
Installation and operation manual secflow-4 ver.3.10 9-91 uses this information to elect the root switch and root port for the switched network and the root port and designated port for each switched segment. The bpdu contains information regarding: root bridge id - which device is the root bridge d...
Page 143
Installation and operation manual 9-92 secflow-4 ver.3.10 spanning tree port states when the switch is powered-up and stp is enabled, every port in the switch goes through the blocking state and the transitory states of listening and learning. Spanning tree stabilizes each port at the forwarding or ...
Page 144
Installation and operation manual secflow-4 ver.3.10 9-93 a port in the blocking state performs as follows: • discards frames received on the port • discards frames switched from another port for forwarding • does not learn addresses • receives bpdus. 9.8 listening state the listening state is the f...
Page 145
Installation and operation manual 9-94 secflow-4 ver.3.10 9.10 disabled state a port in the disabled state does not participate in frame forwarding or stp. A port in the disabled state is non-operational. A disabled port performs as follows: • discards frames received on the port • discards frames s...
Page 146
Installation and operation manual secflow-4 ver.3.10 9-95 9.13 rstp/mstp commands command description config terminal ethernet enters the ethernet configuration mode spanning-tree enters the rtsp/mstp configuration mode no spanning-tree disables spanning tree forward-delay defined the time a port wa...
Page 147
Installation and operation manual 9-96 secflow-4 ver.3.10 9.14 port mirroring (port monitoring) overview port mirroring is a method for monitoring network traffic. Port mirroring forwards all the data transmitted and received by a port to a different location where it can be examined. The port monit...
Page 149
Installation and operation manual 9-98 secflow-4 ver.3.10 1. Set the destination port (sniffer port) for both rx and tx: device-name(config)#system mirror tx destination 1/4/1 device-name(config)#system mirror rx destination 1/4/1 2. Set the source ports (monitored ports): device-name(config)#system...
Page 150: Chapter 10
Installation and operation manual secflow-4 ver.3.10 10-99 chapter 10 access control lists (acls) access control lists (acls) are sets of numbered rules that process packets going through the device and provide the ability to control network traffic. Using acls, system administrators can filter pack...
Page 151
Installation and operation manual 10-100 secflow-4 ver.3.10 • ingress acls process incoming packets, manipulating permitted packets and forwarding them according to matched acl conditions. Packets that do not match any of the acls are discarded, reducing the load on the outbound interface. • vlan : ...
Page 152
Installation and operation manual secflow-4 ver.3.10 10-101 • once created, users can add new rules to the end of the acl • the device tests the packets only until it finds the first match, defining whether to permit or deny the packets • if the packets do not match any of the acls: in case of ingre...
Page 153
Installation and operation manual 10-102 secflow-4 ver.3.10 • the excess burst size (ebs) determines how large traffic bursts can be before all traffic exceeds the rate limit the traffic is then marked as follows: • traffic within cir always conforms and is marked green • traffic that falls above ci...
Page 154
Installation and operation manual secflow-4 ver.3.10 10-103 traffic redirection systems administrators can redirect traffic to separate servers, based on the packet header parameters (such as, ip address, ip protocol, and application). They can select to redirect traffic to a specified interface or ...
Page 158
Installation and operation manual secflow-4 ver.3.10 10-107 command description source_ip a.B.C.D/mask mandatory defines the packet’s source-address: a.B.C.D/mask: source ip-address/source mask. Use keyword any when source ip-address/source-mask is 0.0.0.0/255.255.255.255 (any host) untagged the acl...
Page 160
Installation and operation manual secflow-4 ver.3.10 10-109 command description icmp-code (optional, valid for icmp protocol only) matches icmp packets by the icmp message code: value: in the range of or a valid literal icmp message code no icmp-code removes the icmp message code icmp-type (optional...
Page 161
Installation and operation manual 10-110 secflow-4 ver.3.10 command description tos value> the acl rule matches packets by the service level type: value: in the range of or a valid literal tos value no tos removes the valid literal tos value untagged the acl rule matches untagged packets only defaul...
Page 163
Installation and operation manual 10-112 secflow-4 ver.3.10 command description cir (only for single rate) defines the committed information rate (cir): value: in the range of kbps color-aware enables the color-aware mode default: color blind pbs (only for dual rate) defines the peak burst size (pbs...
Page 165
Installation and operation manual 10-114 secflow-4 ver.3.10 command description no redirect [uu/ss/pp] removes the traffic redirection from the specified port: uu/ss/pp: (optional) 1/1/1–1/1/16, 1/2/1–1/2/8, 1/3/1, 1/3/2, 1/4/1 and 1/4/2 vlan vlan-id> redirects matching traffic to the specified vlan...
Page 166
Installation and operation manual secflow-4 ver.3.10 10-115 command description redirect uu/ss/pp redirects matching traffic to the specified sap port: uu/ss/pp: 1/1/1–1/1/16, 1/2/1–1/2/8, 1/3/1, 1/3/2, 1/4/1 and 1/4/2 no redirect [uu/ss/pp] removes the traffic redirection from the specified sap por...
Page 170
Installation and operation manual secflow-4 ver.3.10 10-119 command description inner-vpt priority> defines the packet’s filtering by the vlan priority tag (vpt) in the inner-vlan tag header: priority: in the range of no inner-vpt [priority>] removes the selected vpt: priority: (optional) in the ran...
Page 171
Installation and operation manual 10-120 secflow-4 ver.3.10 command description access-groups-rule-sequence mandatory sequence number : 1-100. Will determine the order of execution of the acls on the port. Each acl assigned to a port must be precede with a sequence number determining its place in th...
Page 174
Installation and operation manual secflow-4 ver.3.10 10-123 command description pir (only for dual rate) defines the peak information rate (pir): value: in the range of kbps redirect uu/ss/pp redirects matching traffic to the specified port: uu/ss/pp: 1/1/1–1/1/16, 1/2/1–1/2/8, 1/3/1, 1/3/2, 1/4/1 a...
Page 176
Installation and operation manual secflow-4 ver.3.10 10-125 command description precedence type the acl rule matches packets by the literal precedence values: no precedence removes the precedence value tos value> the acl rule matches packets by the service level type: value: in the range of or a val...
Page 178
Installation and operation manual secflow-4 ver.3.10 10-127 command description pbs (only for dual rate) defines the peak burst size (pbs): value: in the range of kbps pir (only for dual rate) defines the peak information rate (pir): value: in the range of kbps redirect uu/ss/pp redirects matching t...
Page 181
Installation and operation manual 10-130 secflow-4 ver.3.10 device-name(config)# port 1/1/5 access-groups-rule-sequence 1 ip-access-group-extended _acl-103 vlan add-vlan 200 access-groups-rule-sequence 2 ip-access-group-extended _acl-105 in redirect 1/3/2 access-groups-rule-sequence 3 ip-access-grou...
Page 182
Installation and operation manual secflow-4 ver.3.10 10-131 mac access-list robot rule 1 action permit !Specifically allow traffic from plc source_mac 00:00:00:00:00:10 ! Mac of the plc destination_mac 00:00:00:00:00:20 ! Mac of the robot ! Rule 2 !Specifically deny all other traffic action deny sou...
Page 183: Chapter 11
Installation and operation manual 11-132 secflow-4 ver.3.10 chapter 11 quality of service (qos) today’s networks transmit data streams for various applications using many different protocols. Different types of traffic sharing a data path through the network can interact in ways that affect their ap...
Page 184
Installation and operation manual secflow-4 ver.3.10 11-133 • strict priority (sp) queuing sets the eight queues in a rigid order, and always transmits packets from the highest-priority queue that has packets waiting • weighted round-robin (wrr) queuing lets the user assigns a relative weight to eac...
Page 185
Installation and operation manual 11-134 secflow-4 ver.3.10 browser client). An exception to this pattern may be created by some java™ - based applications. • web-based applications are generally tolerant of latency, jitter, and some packet loss, but small packet-loss may have a large impact on perc...
Page 186
Installation and operation manual secflow-4 ver.3.10 11-135 features, packets accumulating at a port are queued until the port is free to transmit them; they are then scheduled for transmission according to their assigned priority and the queuing mechanism configured for the port. The router determi...
Page 187
Installation and operation manual 11-136 secflow-4 ver.3.10 note that if a packet length exceeds the queue allowed bandwidth, the packet is still transmitted during its time slot, but its quota is overdrawn so that on the next time slot it receives a smaller allotment. This mechanism guarantees a mi...
Page 188
Installation and operation manual secflow-4 ver.3.10 11-137 when sending again the queue, less data is dequeued to compensate the excess of data previously sent. As a result, the average amount of data dequeued per queue is close to the configured value. Two variables define each drr/mdrr queue: • q...
Page 189
Installation and operation manual 11-138 secflow-4 ver.3.10 11.7 egress traffic shaping when congestion occurs, the packets are transmitted on the outgoing port and the assigned queues. Traffic shaping allows the user to shape output traffic (egress traffic) on a per- port basis and also per queue o...
Page 190
Installation and operation manual secflow-4 ver.3.10 11-139 the device supports several types of policies (described in detail in the following subsections). Each policy type includes parameters related to a different set of qos features. In addition, some of the features are configured using profil...
Page 191
Installation and operation manual 11-140 secflow-4 ver.3.10 • scheduling profiles: 8 (including sp default profile) 11.11 maximum number of policies • port ingress policies: 64 (including one default policy) • port egress policies: 64 (including one default policy) 11.12 order of configuration defin...
Page 192
Installation and operation manual secflow-4 ver.3.10 11-141 feature default value traffic shaping disabled port policies profiles configuration mapping profile default configuration mapping profile default configuration port policies profiles default configuration.
Page 193
Installation and operation manual 11-142 secflow-4 ver.3.10 qos classification and policing diagram changing fc of ingress traffic – untrusted packets comments: • the untrusted mode is given to the physical port without distinguishing between the traffic over it. • creating additional mapping profil...
Page 194
Installation and operation manual secflow-4 ver.3.10 11-143 changing fc of ingress traffic – trusted packets comments: • the trusted mode is given to the physical port . • fc will be assigned to a packet in accordance to the mapping profile activated by the ingress policy on the portschanging fc of ...
Page 195
Installation and operation manual 11-144 secflow-4 ver.3.10 • no mapping profile is needed. • no ingress policy is needed • not relevant if the traffic is considered trusted or untrusted 11.14 changing vpt/dscp for egress packets comments: vpt /dscp will be changed for the packets meeting the acl ru...
Page 196
Installation and operation manual secflow-4 ver.3.10 11-145 11.15 qos configuration flow the following flow chart shows the process of configuring the qos parameters. 11.16 qos commands hierarchy qos profile configuration commands + config terminal + qos + [no] mapping-profile profile-name - [no] an...
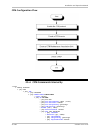
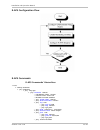
Page 200
Installation and operation manual secflow-4 ver.3.10 11-149 command description no set-to-fc restores to default vpt-to-fc enters the vpt-to-fc mode for the specified vpt marking for configuring the mapping of the ingress traffic bearing that marking to a particular color and forwarding class: : spe...
Page 202
Installation and operation manual secflow-4 ver.3.10 11-151 command description no cbs restores to default cir cir > specifies the committed information rate (cir)for the shaper profile, in kilobits per second: cir: the valid range is kbps no cir restores to default description description assigns a...
Page 204
Installation and operation manual secflow-4 ver.3.10 11-153 command description shaper-profile profile-id > assigns a shaper profile to the configured policy. The profile is selected from the available shaper profiles. Profile-id: id of the assigned profile no shaper-profile removes the shaper sched...
Page 205
Installation and operation manual 11-154 secflow-4 ver.3.10 command description queue queue-id> assigns queue to the configured policy and enters queue configuration mode for that queue: queue-id: id of the assigned queue, the valid range is no queue queue-id> removes the specified queue from the co...
Page 206
Installation and operation manual secflow-4 ver.3.10 11-155 command description no port uu/ss/pp removes the port from the configuration: uu/ss/pp: 1/1/1-1/1/4, 1/2/1- 1/2/8 qos-egress-policy policy-name specifies port egress policy to apply to the configured port. The policy is selected from the av...
Page 207
Installation and operation manual 11-156 secflow-4 ver.3.10 - show running-config qos port-ingress-policy [policy-name] - show running-config qos shaper-profile - show running-config qos shaper-profile port [] - show running-config qos shaper-profile service [] - show running-config qos scheduling-p...
Page 208
Installation and operation manual secflow-4 ver.3.10 11-157 3080(config-qos)#scheduling-profile 2 3080(config-scheduling-profile-2)#scheduling-type sp 3080(config-scheduling-profile-2)# sp is the default scheduler of the default egress policy of the system (on all ports). Hence aerating scheduling-p...
Page 209
Installation and operation manual 11-158 secflow-4 ver.3.10 • iec 104 traffic will be managed as follows: traffic directed to or from the scada stations will be assigned to queue 5 (fc to h2) using ingress layer 3 acls on designated ports. Traffic between the 104 servers will be assigned to queue 4 ...
Page 210
Installation and operation manual secflow-4 ver.3.10 11-159 switch_e(config)#vlan iec_104 10 switch_e(config-vlan-10)#untagged 1/1/1 switch_e(config-untagged-1/1/1)#tagged 1/1/8 switch_e(config-tagged-1/1/8)#top switch_e(config)#port 1/1/1 switch_e(config-port-1/1/1)#default-vlan 10 switch_e(config-...
Page 211
Installation and operation manual 11-160 secflow-4 ver.3.10 switch_e(233)(config)#ip access-list extended 110 switch_e(233)(config-extended-110)#rule 1 switch_e(233)(config-rule-1)#action permit switch_e(233)(config-rule-1)#source_ip any switch_e(233)(config-rule-1)#destination_ip any switch_e(233)(...
Page 212
Installation and operation manual secflow-4 ver.3.10 11-161 switch_e(233)(config)#port 1/1/8 switch_e(233)(config-port-1/1/8)#access-groups-rule-sequence 10 switch_e(233)(config-access-groups-rule-sequence-10)#ip-access-group-extended 101 out vpt 4 switch_e(233)(config-port-1/1/8)#access-groups-rule...
Page 213
Installation and operation manual 11-162 secflow-4 ver.3.10 switch_e(233)(config-qos)#mapping-profile scada_1 switch_e(233)(config-mapping-profile-scada_1)#vpt-to-fc 4 set-to-fc ef color green switch_e(233)(config-vpt-to-fc-4)#top switch_e(233)(config-qos)#port-ingress-policy scada_1 switch_e(233)(c...
Page 214: Chapter 12
Installation and operation manual secflow-4 ver.3.10 12-163 chapter 12 traffic storm control the traffic storm-control feature prevents lan ports from being disrupted by a broadcast, multicast, and/or unicast traffic storm. This mechanism regulates the rate at which devices forward the traffic. Traf...
Page 215
Installation and operation manual 12-164 secflow-4 ver.3.10 command description traffic-type broadcast [ratethreshold ] defines the upper threshold rate for broadcast traffic. The storm control action occurs when traffic utilization reaches this rate. Rate: the valid range is packets per second (pps...
Page 216
Installation and operation manual secflow-4 ver.3.10 12-165 12.3 supported standards, mibs, and rfcs.
Page 217: Chapter 13
Installation and operation manual 13-166 secflow-4 ver.3.10 chapter 13 ip routing 13.1 creating an ip interface the routing software and hardware directs ip traffic between router ip interfaces. A router ip interface is simply a vlan that has an ip address assigned to it. As vlans with ip addresses ...
Page 218
Installation and operation manual secflow-4 ver.3.10 13-167 device-name(config)#router device-name (config-router)#interface sw0 device-name (config-interface-sw0)#address 172.17.212.200/24 device-name (config-interface-sw0)#exit device-name (config-router)#interface sw1 device-name (config-interfac...
Page 220
Installation and operation manual secflow-4 ver.3.10 13-169 device-name(config)#vlan nni 100 device-name (config-vlan-nni/100)#tagged 1/3/1 device-name (config-tagged-1/3/1)#tagged 1/5/1 device-name (config-tagged-1/5/1)#tagged commit device-name (config-tagged-1/5/1)#end device-name# create an ip i...
Page 221
Installation and operation manual 13-170 secflow-4 ver.3.10 • an update for the network is not received for a period of time that is determined by the routing protocol (i.E., the dynamic route is aged out of the table) • a neighbor sends a command to delete the dynamic routes advertised by the routi...
Page 222
Installation and operation manual secflow-4 ver.3.10 13-171 ip unicast routing default configuration ip unicast routing default configuration parameter default value default ip address for sw0 ip interface not defined ip interface multicast flag set the default administrative distances of the dynami...
Page 223
Installation and operation manual 13-172 secflow-4 ver.3.10 command description no router static-route [a.B.C.D/m a1.B1.C1.D1 distance-value>] removes a specific static route or all configured static routes • a.B.C.D/m: (optional) the destination ip address and mask in dotted-decimal format • a1.B1....
Page 224
Installation and operation manual secflow-4 ver.3.10 13-173 area types ospf requires dividing the network into a logical star of areas. The topology within an area is hidden from the rest of the as. Hiding this information significantly reduces lsa traffic and the calculations needed to maintain the...
Page 225
Installation and operation manual 13-174 secflow-4 ver.3.10 • on broadcast or point-to-point segments, the routers dynamically discover neighbors through the ospf multicast, 224.0.0.5, using the ospf hello protocol. • on non-broadcast multiple access (nbma) networks the system administrators have to...
Page 226
Installation and operation manual secflow-4 ver.3.10 13-175 point-to-multipoint the point-to-multipoint network type runs on nbma networks, such as frame relay and atm. Routers are addressed out of a common ip subnet on wan ip interfaces. However, this network type does not require a full mesh, sinc...
Page 227
Installation and operation manual 13-176 secflow-4 ver.3.10 - [no] auto-cost-refbandwidth - [no] compatible-rfc1583 {false,true} - [no] default-info-originate {false,true} - [no] default-metric - [no] external-distance - [no] intra-area-distance - [no] inter-area-distance - [no] abr-type [alternativ...
Page 229
Installation and operation manual 13-178 secflow-4 ver.3.10 command description ospf enables ospf and enters the ospf router configuration mode default: enabled router-id a.B.C.D defines the ospf fixed-router id: a.B.C.D: fixed-router id in a dotted-decimal format default: no ospf routing process is...
Page 230
Installation and operation manual secflow-4 ver.3.10 13-179 command description inter-area-distance inter-area- distance> defines the inter-area route distance. Inter-area routes are routes to other areas: inter-area-distance: in the range of default: 110 no inter-area-distance restores to default a...
Page 232
Installation and operation manual secflow-4 ver.3.10 13-181 no route-map restores to default ospf neighbor configuration commands command description config terminal enters the configuration mode router enters the router configuration mode ospf enables ospf and enters the ospf router configuration m...
Page 234
Installation and operation manual secflow-4 ver.3.10 13-183 command description area a.B.C.D mandatory defines an ospf area: a.B.C.D: ospf area’s ip address default: not defined no area [a.B.C.D] deletes the specified area: a.B.C.D: (optional) ospf area’s ip address export-list string defines a filt...
Page 236
Installation and operation manual secflow-4 ver.3.10 13-185 command description interface a.B.C.D mandatory defines an ospf interface: a.B.C.D: ospf interface’s ip address default: not activated no interface [a.B.C.D] deletes the ospf interface configuration: a.B.C.D: ospf interface’s ip address are...
Page 237
Installation and operation manual 13-186 secflow-4 ver.3.10 command description no priority restores to default dead-interval dead-interval value> defines the number of seconds that a device must wait before it declares a neighbor ospf router down: dead-interval value: in the range of seconds defaul...
Page 238
Installation and operation manual secflow-4 ver.3.10 13-187 command description ospf enables ospf and enters the ospf router configuration mode default: enabled ext-lsdb-limit ext-lsdb-limit- value> assigns the upper limit to the number of lsas allowed in the router link-state database (lsdb): ext-l...
Page 240
Installation and operation manual secflow-4 ver.3.10 13-189 configuration scripts switch 1 1. Remove network ports from default vlan 1 config vlan 1 no untagged 1/1/1 no untagged 1/1/2 no routing-interface sw0 top commit 2. Assign interfaces and vlans to network ports.
Page 241
Installation and operation manual 13-190 secflow-4 ver.3.10 router interface sw101 address 10.169.15.149/30 no shutdown top vlan 101 name net_101 routing-interface sw101 tagged 1/1/2 top router interface sw104 address 10.169.15.162/30 no shutdown top vlan 104 name net_104 routing-interface sw104 tag...
Page 242
Installation and operation manual secflow-4 ver.3.10 13-191 router interface sw10 !Ip interface for rtu gateway address 10.169.15.1/29 no shutdown top port 1/1/8 !Rtu connected at port 1/1/8 as untagged default-vlan 10 top vlan 10 name user routing-interface sw10 untagged 1/1/8 top commit 3. Assign ...
Page 243: Chapter 14
Installation and operation manual 14-192 secflow-4 ver.3.10 chapter 14 dhcp relay 14.1 overview dhcp relay agent is a bootstrap protocol (bootp) relay agent that relays dynamic host configuration protocol (dhcp) messages between dhcp clients and dhcp servers on different ip networks. The dhcp relay ...
Page 244
Installation and operation manual secflow-4 ver.3.10 14-193 agent circuit id (text) the contents of option 82 can also be defined by the user as a string of characters, for example: circuit1 . The dhcp server will identify the circuit id by its name - “ circuit1 ”. In such cases option 82 is referre...
Page 245
Installation and operation manual 14-194 secflow-4 ver.3.10 14.4 dhcp relay configuration example in the following setup the dhcp client and the dhcp server are designated to be on different subnets. The 3080 is hence acting as a router for the dhcp traffic. 1. Ip interfaces configuration: 3080#conf...
Page 246
Installation and operation manual secflow-4 ver.3.10 14-195 3080(config-dhcp-relay)#relay-interface sw20 3080(config-relay-interface-sw20)#no shutdown 3080(config-relay-interface-sw20)# 6. Configure the dhcp server ip address 3080(config-relay-interface-sw20)#dhcp-server 172.18.212.100 3080(config-d...
Page 247: Chapter 15
Installation and operation manual 15-196 secflow-4 ver.3.10 chapter 15 simple network management protocol (snmp) 15.1 overview snmp is an application layer protocol that facilitates the exchange of management information between network devices. An snmp-managed network consists of three key componen...
Page 248
Installation and operation manual secflow-4 ver.3.10 15-197 an snmp entity is an implementation of the snmp architecture. Each entity consists of an snmp engine and one or more associated applications. An snmp engine provides services for sending and receiving messages, authenticating and encrypting...
Page 249
Installation and operation manual 15-198 secflow-4 ver.3.10 snmp engine id the snmp engine id is a 5 to 32 bytes long, administratively unique identifier of a participant in snmp communication within a single management domain. The snmp manager and snmp agent must be configured by an administrator t...
Page 250
Installation and operation manual secflow-4 ver.3.10 15-199 in the agent successfully sends an inform request to the manager. When the manager receives the inform request, it sends a response back to the agent. Thus, the agent knows that the inform request successfully reached its destination. In th...
Page 251
Installation and operation manual 15-200 secflow-4 ver.3.10 inform request successfully resent to snmp manager the discovery mechanism to protect the user network against message reply, delay and redirection, one of the snmp engines involved in each communication is designated to be the authoritativ...
Page 252
Installation and operation manual secflow-4 ver.3.10 15-201 to reduce a configuration complexity, the application software agent implements an auto discovery procedure for obtaining the snmp engine ids of different inform recipients. When an event occurs, for example linkup , the agent sends an info...
Page 253
Installation and operation manual 15-202 secflow-4 ver.3.10 variable description bases its security on community strings. Snmpv2c snmp version 2c (the c stands for community) is the community-string based administrative framework. Snmpv2c includes the following improvements over snmpv1: • improved p...
Page 254
Installation and operation manual secflow-4 ver.3.10 15-203 security levels available in the snmpv3 security models level authentication encryption explanation noauthnopriv username no all pdus are sent unencrypted and not authenticated in the network. Authnopriv hmac-md5 or hmac-sha no the pdus are...
Page 256
Installation and operation manual secflow-4 ver.3.10 15-205 command description authentication-failure-trap sends authenticationfailure notifications. This command controls the value of mib-ii mib- 2.Snmp.Snmpenableauthtraps default: enabled no authentication-failure-trap disables the sending of aut...
Page 259
Installation and operation manual 15-208 secflow-4 ver.3.10 command description no address restores to default security-name username defines the security name that identifies how snmp messages will be generated using this entry: username: the security user name up to 32 characters no security-name ...
Page 260
Installation and operation manual secflow-4 ver.3.10 15-209 command description show snmp group [displaylevel ] displays the configured groups, their associated views, and the security model. If the security model is usm (v3), the command displays the security level: level: in the range of show snmp...
Page 261
Installation and operation manual 15-210 secflow-4 ver.3.10 argument value description powersupplytest the sending agent senses that one of the power- supply changed its status. The trap should be sent once the bist status of the power supply test changes. Ramfreespaceexceeded the sending agent sens...
Page 262
Installation and operation manual secflow-4 ver.3.10 15-211 device-name(config-snmp)#group public security-model noauthnopriv read all_mib write all_mib notify all_mib device-name(config-snmp)#user tester public v1 4. Enable snmp server: device-name(config-snmp)#no shutdown 5. Commit the configurati...
Page 263
Installation and operation manual 15-212 secflow-4 ver.3.10 =============================================================== number of entries: 0 device-name #show snmp group snmp groups table =============================================================== snmp group name : public security-model : no...
Page 264
Installation and operation manual secflow-4 ver.3.10 15-213 • view parameters: snmp trap in this example, a trap is configured . Target address is set to the ip of the management unit "snmp-mgmt" (user computer) . Destination port on the management unit (computer) is set to 1100. 1. Enable snmp: dev...
Page 265
Installation and operation manual 15-214 secflow-4 ver.3.10 device-name#show running-config system snmp snmp notification targets =============================================================== notification target name : snmp-mgmt security name : tester message model : v1 security level : noauthnopr...
Page 266
Installation and operation manual secflow-4 ver.3.10 15-215 device-name(config-snmp)#view all_included 1.3 included 3. Create a view that excludes the entire mib tree from root: device-name(config-snmp)#view all_excluded 1.3 excluded 4. Create a user named worker that uses snmpv2 and attach it to a ...
Page 267
Installation and operation manual 15-216 secflow-4 ver.3.10 network management protocol (snmp) rfc 3413, simple network management protocol (snmp) applications rfc 3414, user-based security model (usm) for version 3 of the simple network management protocol (snmpv3) rfc 3415, view-based access contr...
Page 268: Chapter 16
Installation and operation manual secflow-4 ver.3.10 16-217 chapter 16 application aware firewall 16.1 overview the secflow 3xxx switches support remote access contain an integrated firewall on each port, providing a network-based distributed security solution equivalent to the use of personal firew...
Page 269
Installation and operation manual 16-218 secflow-4 ver.3.10 application protocol state-machine – check that the application-level session flow follows the expected logic as defined in the standard including verification of the master and slave roles, session setup and closing state-machine and comma...
Page 270
Installation and operation manual secflow-4 ver.3.10 16-219 mapped to separate vlans in the backbone network so that traffic within a service group reaches only the assigned end-devices. After defining a service group the user configures a security matrix with detailed security rules for each pair o...
Page 271: Chapter 17
Installation and operation manual 17-220 secflow-4 ver.3.10 chapter 17 vpn 17.1 overview inter-site layer 2 vpn when a distributed operational network uses public transport links for the inter- site connectivity, the traffic must be encrypted to ensure its confidentiality and its integrity. The secf...
Page 274
Installation and operation manual secflow-4 ver.3.10 17-223 command description policy create configure the policy to determine the type of traffic to encrypt: • src-ip : a.B.C.D form ip address of the packet source. • dst-ip : a.B.C.D form ip address of the packet destination. • src-port : port num...
Page 275
Installation and operation manual 17-224 secflow-4 ver.3.10 3080(config)#router 3080(config-router)#interface sw0 address 172.17.203.100/24 3080(config-interface-sw0)#exit 3080(config-router)#interface sw1 address 172.18.212.100/24 3080(config-interface-sw1)#commit commit complete. 2. Create vlans: ...
Page 276
Installation and operation manual secflow-4 ver.3.10 17-225 3080#application connect secflow application module welcome to secflow industrial cli [/] router interface create address-prefix 172.17.203.220/24 vlan 17 [router/] static router/static> enable router/static# configure terminal router/stati...
Page 277
Installation and operation manual 17-226 secflow-4 ver.3.10 3080#config 3080(config)#router interface sw1 3080(config-interface-sw1)#address 192.168.0.102/24 3080(config-interface-sw1)#commit commit complete. 3080(config-interface-sw1)#top 3080(config)#vlan access 10 3080(config-vlan-access/10)#mana...
Page 278: Chapter 18
Installation and operation manual secflow-4 ver.3.10 18-227 chapter 18 gprs/umts interface 18.1 overview an important benefit of the secflow portfolio is its support of variety of medium interfaces. A gprs/umts modem provides a key solution for connectivity to remote sites. The modem support dual si...
Page 279
Installation and operation manual 18-228 secflow-4 ver.3.10 18.2 hardware hub – a secflow switch 3xxx with application card installed and configured. The hub requires a fixed connection to the internet with a static, public ip address assigned to its application interface. Spoke – a secflow 3180 pro...
Page 280
Installation and operation manual secflow-4 ver.3.10 18-229 18.4 backup and redundancy backup between isp (choice sim cards) a properly configured sim card along with a proper isp service will be indicated by the modem as “ready” state. If connected, the sim card slot will be indicates as “connected...
Page 281
Installation and operation manual 18-230 secflow-4 ver.3.10 • once the connection does not meet the minimum watchdog tests criteria, the second sim interface will be enabled as “alternative” and the system will establish a link with it. • the modem will not switch back form the “alternative” to the ...
Page 282
Installation and operation manual secflow-4 ver.3.10 18-231 backup between interfaces (between gsm or physical interface) a gsm link is by nature an a high cost path and with a significant lower bandwidth then a physical channel. When the gsm link is to be used for backup to a physical link then res...
Page 283
Installation and operation manual 18-232 secflow-4 ver.3.10 18.6 gprs/umts commands command description application connect enter the industrial application menu cellular enter the configuration mode for the cellular application enable: enable application disable: disable application continuous-echo...
Page 284
Installation and operation manual secflow-4 ver.3.10 18-233 command description settings update quality check: define time interval in seconds for internal rssi check of active sim.. 0 – disable rssi check. Backoff1 : minimum time to stay on a sim after any fail over. Backoff2 : minimum time to stay...
Page 285
Installation and operation manual 18-234 secflow-4 ver.3.10 cellular wan update admin-status enable apn-name internetg sim-slot 1 operator-name cellcom user-name guest password guest cellular wan update admin-status enable apn-name internet.Pelephone.Net.Il sim-slot 2 operator-name pelephone user-na...
Page 286
Installation and operation manual secflow-4 ver.3.10 18-235 example cellular watch dog in the following example we will configure a watchdog to cellular modem and see how the sim status is changing due to the failed test of the watch dog. An unreachable address of 10.10.10.10 is configured as the de...
Page 288
Installation and operation manual secflow-4 ver.3.10 18-237 [cellular/continuous-echo/] create name destination_2 dest-ip-address 80.74.102.38 loss-threshold 20 num-of-requests 3 interval 2 request-size 64 in next screenshot we see that although the remote ip 80.74.102.38 is accessible, the echo req...
Page 289
Installation and operation manual 18-238 secflow-4 ver.3.10 2. At the hub side, a static, public address should be assigned to the switch application interface. In the following example the hub is located behind a nat router. The nat, holding a public address 80.74.102.38 should route all traffic de...
Page 290
Installation and operation manual secflow-4 ver.3.10 18-239 3080#config terminal 3080(spoke)(config)#vlan lan 700 3080(spoke)(config-vlan-lan/700)#tagged 1/3/2 3080(spoke)(config-tagged-1/3/2)#untagged 1/1/4 3080(spoke)(config-untagged-1/1/4)#top 3080(spoke)(config)#port 1/1/4 3080(spoke)(config-por...
Page 291
Installation and operation manual 18-240 secflow-4 ver.3.10 3080#application connect []ipsec isakmp update dh-group modp1024 []ipsec isakmp update my-id rtu1.Secflow.Com []ipsec preshared create id hub.Secflow.Com key secretkey []ipsec preshared create id rtu1.Secflow.Com key secretkey []ipsec polic...
Page 292
Installation and operation manual secflow-4 ver.3.10 18-241 3080#application connect []ipsec isakmp update dh-group modp1024 []ipsec isakmp update my-id hub.Secflow.Com []ipsec preshared create id hub.Secflow.Com key secretkey []ipsec preshared create id rtu1.Secflow.Com key secretkey []ipsec policy...
Page 293: Chapter 19
Installation and operation manual 19-242 secflow-4 ver.3.10 chapter 19 serial services 19.1 overview the serial i/o module of the secflow 3xxx switches connects “legacy” serial- based industrial devices to an ethernet network. The serial module has 2xrs-232 interfaces and 2xrs-485 interfaces and an ...
Page 294
Installation and operation manual secflow-4 ver.3.10 19-243 tunnel latency = min (40*bytetime, assemlytimeout)+2*50usec+network latency. Assuming that the serial tunnel packets are handled in high priority in the network, minimal tolerance in the network latency is introducned due to the potential h...
Page 295: Chapter 20
Installation and operation manual 20-244 secflow-4 ver.3.10 chapter 20 transparent tunneling serial tunneling commands hierarchy + application connect + serial + port - clear counters - create { slot } { port } [ baudrate ] [ parity ] [ stopbits ] [mode-of-operation ] - remove [ slot ] [ port ] - up...
Page 296
Installation and operation manual secflow-4 ver.3.10 20-245 command description mode of operation : transparent, transparent9bit, bitstream remove slot : physical slot number; 3700 = [3-9]; 3080 = [1]. Port : physical port number. 3700 = [1-4]; 3080 = [12]. Show local-end-point create slot : physica...
Page 297
Installation and operation manual 20-246 secflow-4 ver.3.10 command description application : serial-tunnel (default) terminal-server iec101-gw modbus-gw tg800-gw show remote-end-point create remote-address : ip address aa:bb:cc:dd service id : numeric value of serial service. Position: n/a - point ...
Page 298
Installation and operation manual secflow-4 ver.3.10 20-247 485 and 3,4 for rs 232) is done within the application cli. The central switch identifies the different serial io cards as they are physically assembled on different slots but each card is mapped as one port, always numbered as '2'. The fol...
Page 299
Installation and operation manual 20-248 secflow-4 ver.3.10 config vlan serial 4092 //the name "serial" is an example only the value 4092 is mandatory. Untagged 1/5/2 //the serial io card which is physically assembled on slot 5 of the bacplane is assigned to vlan 4092 as untagged member. The value '...
Page 300
Installation and operation manual secflow-4 ver.3.10 20-249 serial port at the switch db-9 female conector for end device pinout for crossed cable ("cbl-rj45/db9/null") : cable switch port [3xxx] female db-9 (dce) male rj-45 female rj-45 2 6 6 tx 3 5 5 rx 5 4 4 gnd pinout for straight cable ("cbl-rj...
Page 301
Installation and operation manual 20-250 secflow-4 ver.3.10 service. In the following example see vlan 850 used . 6. Establish ip communication between the switches based on application routing interface . Check with ping from within the application 7. Create vlan for the serial ports. Must be numbe...
Page 302
Installation and operation manual secflow-4 ver.3.10 20-251 both switches vlan configuration +root config vlan default 1 no untagged 1/5/4 no untagged 1/6/2 exit vlan serial 4092 tag 1/3/1 untagged 1/6/2 vlan service1 850 tagged 1/3/1 tagged 1/5/4 exit vlan service2 851 tagged 1/3/1 tagged 1/5/4 exi...
Page 303
Installation and operation manual 20-252 secflow-4 ver.3.10 switch a application connect router interface create address-prefix 10.10.10.100/24 vlan 850 serial port create slot 6 port 3 port create slot 6 port 4 local-end-point create slot 6 port 3 service-id 1 position master local-end-point create...
Page 304: Chapter 21
Installation and operation manual secflow-4 ver.3.10 21-253 chapter 21 protocol gateway iec 101 to iec 104 the secflow switch, using its application module implements the gateway for iec101 serial devices to the iec104 ip protocol. The iec101 and iec104 protocols are fully integrated in the applicat...
Page 305
Installation and operation manual 21-254 secflow-4 ver.3.10 • unbalanced mode – up to 32 asdu addresses behind each iec101 server device 21.2 iec101/104 gateway properties iec 101 • system role : controlling station definition (master) • network configuration : point-to-point multiple point-to-point...
Page 306
Installation and operation manual secflow-4 ver.3.10 21-255 balanced transmission unbalanced transmission address field of the link not present (balanced transmission only) one octet two octets structured values translation unstructured • application layer common address of asdu one octet two octets...
Page 307
Installation and operation manual 21-256 secflow-4 ver.3.10 := integrated totals with time tag := event of protection equipment with time tag := packed start events of protection equipment with time tag := packed output circuit transmission of protection equipment with time tag := packed single-poin...
Page 308
Installation and operation manual secflow-4 ver.3.10 21-257 := parameter of measured value, scaled value := parameter of measured value, short floating point value := parameter activation := file ready := section ready := call directory, select file, call file, call section := last section, last seg...
Page 310
Installation and operation manual secflow-4 ver.3.10 21-259 21.5 gateway 101/104 commands command description iec101-gw configuration mode of 101/104 gateway operation start : activate the gateway stop : stop the gateway *takes effect on all iec 101 nodes connected to the switch config gw update mod...
Page 311
Installation and operation manual 21-260 secflow-4 ver.3.10 command description orig_addr_participate : yes/no to indicate if the 101 slave uses the originator address field. Should be identical to the configuration at the 101 slave. The cause of transmission (cot) will be influenced by this configu...
Page 312: Chapter 22
Installation and operation manual secflow-4 ver.3.10 22-261 chapter 22 protocol gateway tg800 to iec 104 the secflow switch, using its application module implements protocol translation for tg800 serial devices to the iec104 ip protocol. The serial tg800 slave devices are connected at the switch ser...
Page 313
Installation and operation manual 22-262 secflow-4 ver.3.10 mapping of the source 104 message to a destination serial slave is done by associating the 104 asdus with a corresponding serial service-ids which defines the slaves. An iec104 message received at the gateway will hold a target asdu address...
Page 316
Installation and operation manual secflow-4 ver.3.10 22-265 command description service id : numeric value of serial service. Position: n/a - point to point master – point to multipoint slave – point to multipoint show tg800-gw configuration mode of tg800 gateway admin-status disable : disables the ...
Page 317
Installation and operation manual 22-266 secflow-4 ver.3.10 command description this is a 1 byte size field representing the tg800 address over the serial link. This value should be identical to the address configured at the tg800 slave. Allowed values : decimal 0-254 tg800-slave-stn – station numbe...
Page 318: Chapter 23
Installation and operation manual secflow-4 ver.3.10 23-267 chapter 23 terminal server 23.1 terminal server service secflow switches allows a special service fortext-based console ports of remote devices to be reached via terminal server service using telnet from any pc with ethernet link. In the fo...
Page 319
Installation and operation manual 23-268 secflow-4 ver.3.10 - create slot port baudrate parity stopbits mode-of-operation - remove slot port - update slot port baudrate parity stopbits mode-of-operation - show + local-end-point - create slot port service-id position protocol application server> - re...
Page 320
Installation and operation manual secflow-4 ver.3.10 23-269 command description remove slot : physical slot number; 3700 = [3-9]; 3080 = [1]. Port : physical port number. 3700 = [1-4]; 3080 = [12]. Show local-end-point create slot : physical slot number; 3700 = [3-9]; 3080 = [1]. Port : physical por...
Page 321
Installation and operation manual 23-270 secflow-4 ver.3.10 command description serial-tunnel configuration options to be used at the switch where the serial port is connected at. These fields will determine the remote side to where to draw the serial service to (the remote side is the switch at whi...
Page 322
Installation and operation manual secflow-4 ver.3.10 23-271 the pc has no serial interface and requires to telnet the device over ip. A telnet session will be etablished pc – switch . A serial transparent tunneling will be established between the switch and the oscillograph over the serial link. 1. ...
Page 323
Installation and operation manual 23-272 secflow-4 ver.3.10 [/] serial [serial/] port create slot 5 port 2 mode-of-operation transparent [serial/] local-end-point create slot 5 port 2 service-id 1 application terminal-server [serial/] port show slot port bus mode baudrate data parity stop allowed-la...
Page 324
Installation and operation manual secflow-4 ver.3.10 23-273 device-name#application connect entering character mode escape character is '^]'. Secflow application module welcome to secflow industrial cli [/] router interface create address-prefix 172.18.212.231/24 vlan 10 completed ok [/] router show...
Page 325: Chapter 24
Installation and operation manual 24-274 secflow-4 ver.3.10 chapter 24 discrete io tunneling 24.1 discrete channel interfaces discrete signals are very common in industrial application to monitor alarams and indications from the field side. The secflow 3x00 switch allows the most effective feature o...
Page 326
Installation and operation manual secflow-4 ver.3.10 24-275 at each switch, when declaring the use of a service, the direction of operation must be determined, as input or output thus associating the the relevant physical hardware to the service id. Service service id 1 direction hardware terminals ...
Page 327
Installation and operation manual 24-276 secflow-4 ver.3.10 dc: max 220v, 30 watt. Above mentioned power limitations should not be exceeded . Maximum current allowed at the contacts is 1a. 24.3 discrete io tunneling commands hierarchy + root + application connect + discrete + service - create servic...
Page 328
Installation and operation manual secflow-4 ver.3.10 24-277 6. At each switch assign the service id direction as either input or output. 7. Wire input connection point. 8. Wire output load. Configuration example in this example, digital input channel 1 at switch a will be tuuneled to switch b at dig...
Page 329: Chapter 25
Installation and operation manual 25-278 secflow-4 ver.3.10 chapter 25 operations, administration, and maintenance (oam) 25.1 overview ieee 802.1ag connectivity fault management (cfm) refers to the ability of a network to monitor the health of an end-to-end service delivered to customers (as oppose ...
Page 330
Installation and operation manual secflow-4 ver.3.10 25-279 cfm provides capabilities for detecting, verifying, and isolating connectivity failures in such networks, where multiple organizations are involved in providing and using the ethernet service (such as customers, service providers, and opera...
Page 331
Installation and operation manual 25-280 secflow-4 ver.3.10 ccms are periodic hello messages multicast by a mep within the ma at a defined rate. The receiving meps build a mep database that catalogs a list of the various mas, including their meps and mips (indicating each entity's mac address) as fu...
Page 332
Installation and operation manual secflow-4 ver.3.10 25-281 cfm also provides an alarm suppression mechanism in cases where a network fault affects more than one vlan and to avoid a situation where different meps generate an alarm notifying of the same common fault. 25.3 fault verification (loopback...
Page 333
Installation and operation manual 25-282 secflow-4 ver.3.10 link trace operation in case of ethernet, fault isolation is more challenging due to mac addresses aging out, erasing the information needed for locating the fault. The possible ways to address this issue are: • carrying out the linktrace w...
Page 334
Installation and operation manual secflow-4 ver.3.10 25-283 in the order of their priority the defects are: • defrdiccm—the last ccm received by this mep from a remote mep contained the rdi bit • defmacstatus—the last ccm received by this mep from a remote mep indicated that the transmitting mep’s a...
Page 337
Installation and operation manual 25-286 secflow-4 ver.3.10 command description cfm enters the cfm protocol configuration mode shutdown disables cfm no shutdown mandatory enables cfm domain-name domain-name mandatory creates a maintenance domain (md) and enters a specific maintenance domain mode: do...
Page 338
Installation and operation manual secflow-4 ver.3.10 25-287 command description no ais-lck-level removes the configured ais-lck level ais-lck-priority priority> defines a priority used for ais and lck sent packets: priority: in the range of default: 6 no ais-lck-priority restores to default ccm-prio...
Page 339
Installation and operation manual 25-288 secflow-4 ver.3.10 command description mep mep-id sapstring mandatory adds a sap port (part of the service where ma was created on) as mep to a specific ma: • mep-id: in the range of • sapstring: in uu/ss/pp:: format • uu/ss/pp: the corresponding port • vlan-...
Page 341
Installation and operation manual 25-290 secflow-4 ver.3.10 command description frame-loss-warning threshold> defines the two-way frame-loss warning monitoring threshold: warning–threshold: in the range of %. If you define a value greater than the frame-loss-error value, the frame-loss-warning is di...
Page 342
Installation and operation manual secflow-4 ver.3.10 25-291 command description round-trip-latency-warning defines the two-way latency warning monitoring threshold: warning–value: in the range of milliseconds default: 1600 milliseconds no round-trip-latency-warning restores to default round-trip-lat...
Page 343
Installation and operation manual 25-292 secflow-4 ver.3.10 command description test domain-namema- name [repeat-interval number] tests the connectivity: • test-id: in the range of • domain-name: a string of characters • ma-name: a string of characters • threshold-profile id: in the range of • numbe...
Page 344
Installation and operation manual secflow-4 ver.3.10 25-293 capabilities facilitate network operation and troubleshooting for both the provider and the customer networks. Basic 802.3 packets convey oam data between two ends of a physical link. The 802.3ah (clause 57) provides the single-link oam cap...
Page 345
Installation and operation manual 25-294 secflow-4 ver.3.10 • oampdu configuration—including the maximum size of oampdus delivered (this information, in combination with a limited rate of ten frames per second, is used to limit the bandwidth allocated to oam traffic) • platform identity—the platform...
Page 346
Installation and operation manual secflow-4 ver.3.10 25-295 rules for active mode the active mode dte: • initiates the oam discovery process • sends information pdus • can send event notification pdus • can send variable request/response pdus • can send loopback control pdus • can respond to variabl...
Page 347
Installation and operation manual 25-296 secflow-4 ver.3.10 allows an oam entity to send failure conditions to its peer. The failure conditions are defined as follows: • link fault—the link fault condition is detected when the receiver loses the signal. This condition is sent once per second in the ...
Page 348
Installation and operation manual secflow-4 ver.3.10 25-297 25.8 efm-oam commands efm-oam commands hierarchy + root + config terminal + [no] oam + [no] efm + [no] shutdown - [no] event-config uu/ss/pp - [no] critical-event-enable - [no] dying-gasp-enable - [no] error-frame-event-notification-enable ...
Page 349
Installation and operation manual 25-298 secflow-4 ver.3.10 command description event-config accesses event configuration mode for the specified interface for configuring thresholds and managing event notifications: uu/ss/pp: 1/1/1-1/1/4, 1/2/1-1/2/8 no event-config removes the configured thresholds...
Page 350
Installation and operation manual secflow-4 ver.3.10 25-299 command description window. Once the threshold is reached, a notification is triggered if the error-symbol-period-event- notification-enable option has been configured. Period–threshold: the valid range is default : 256 no error-symbol-peri...
Page 351
Installation and operation manual 25-300 secflow-4 ver.3.10 command description no log-events disables sending threshold notification messages to the local system log multiple-pdu-count pdu-count> configures number of identical pdus to send when local event occurs: pdu-count: the valid range is defa...
Page 352
Installation and operation manual secflow-4 ver.3.10 25-301 command description efm event-forward-status uu/ss/pp from a target port to its efm peer whenever the source port’s link status changes: uu/ss/pp: target port; the valid range is 1/1/1-1/1/4, 1/2/1-1/2/8 no efm event-forward-status disable ...
Page 353
Installation and operation manual 25-302 secflow-4 ver.3.10 command description no efm role restores to default efm shutdown disables the efm-oam protocol for the configured interface. Though disabled, the interface’s efm-oam configuration is preserved and can be restored with the no efm shutdown co...
Page 354
Installation and operation manual secflow-4 ver.3.10 25-303.
Page 355
Installation and operation manual 25-304 secflow-4 ver.3.10 25.9 itu-t g.8032v2 ring automatic protection switching (r-aps) g.8032, ring automatic protection switching (r-aps, creates a fault tolerant ring topology by configuring a primary and secondary path for each vlan. Upon failure of the primar...
Page 356
Installation and operation manual secflow-4 ver.3.10 25-305 to each main r-aps instance, you can connect up to 10 sub-ring instances. Each sub-ring instance inherits the control and monitored vlans, and the cfm level from the main r-aps instance. The sub-ring instance has only one port. To minimize ...
Page 357
Installation and operation manual 25-306 secflow-4 ver.3.10 when the rpl owner receives an aps signal-fail message, it sends aswitchover command to all the devices in the ring and enables the rpl. Traffic is now sent viathe secondary path. Behavior of the system following recovery of the primary pat...
Page 358
Installation and operation manual secflow-4 ver.3.10 25-307 the logical topology has all nodes connected without a loop and each link is monitored by its two adjacent nodes using eth cc oam messages. Link failure a link/node failure is detected by the nodes adjacent to the failure. In that case the ...
Page 360
Installation and operation manual secflow-4 ver.3.10 25-309 shared link may act as the rpl for only one of the rings that share the link. A signal failure on a non-shared link (when the ring is in idle state) should only trigger protection switching within the ring where the link failed, the other i...
Page 361
Installation and operation manual 25-310 secflow-4 ver.3.10 without r-aps virtual channel • in the first option, r-aps messages are encapsulated and transmitted over an r-aps virtual channel configured on the major ring. • in the second option, r-aps messages are terminated at the interconnection no...
Page 362
Installation and operation manual secflow-4 ver.3.10 25-311 r-aps configuration flow r-aps commands r-aps commands’ hierarchies + root + config-terminal + [no] ethernet + [no] ring-aps + [no] instance value> - cfm-domain-level value> - control-vlan vlan-id> - disable-virtual-channel - [no] guard-tim...
Page 364
Installation and operation manual secflow-4 ver.3.10 25-313 command description control-vlan configures a control vlan used for the ccm traffic. You should not direct any other traffic through this vlan. Vlan-id: in the range of disable-virtual-channel defines a virtual channel for r-aps ring. Raps ...
Page 366
Installation and operation manual secflow-4 ver.3.10 25-315 command description no revertive-mode configure a non-revertive r-aps ring-id id > defines the ring’s id, used to separate rings. The ring id is reflected in the multicast destination mac, used for sending r-aps packets (01-19-a7-00- 00-[ri...
Page 367
Installation and operation manual 25-316 secflow-4 ver.3.10 command description increments default: 0 msec no hold-off-timer restores to default propagate-topology-changes propagates flushing to the main ring when a topology change notification happens in the subring no propagate-topology-changes di...
Page 368
Installation and operation manual secflow-4 ver.3.10 25-317 command description rpl-port configures the selected lag as ring protection link (rpl). Valid only for the rpl owner or rpl neighbor. You can designate only one lag as rpl no rpl-port removes the rpl role from the lag subring-port uu/ss/pp ...
Page 369
Installation and operation manual 25-318 secflow-4 ver.3.10 command description value: in the range of mins default : 5 minutes no-wait-to-restore-timer [] restores to default ethernet ring-aps instance value> clear triggers a revertive behavior, in case revertive mode is not used or in case the wai...
Page 370
Installation and operation manual secflow-4 ver.3.10 25-319 command description by the clear command.) value: in the range of id: in the range of ethernet ring-aps instance value> subring id> forced-switch enables the forced switch option for r-aps subring. In the absence of a failure, you must bloc...
Page 371
Installation and operation manual 25-320 secflow-4 ver.3.10 switch 1 config vlan 1 no management no routing-interface sw0 no untagged 1/1/1 no untagged 1/1/2 no untagged 1/1/3 ! Commit vlan 100 name erp_1_ctrl ! Cfm vlan to be used for control at the erp instance 1 tagged 1/1/1 ! Tagged 1/1/2 ! Tagg...
Page 372
Installation and operation manual secflow-4 ver.3.10 25-321 monitor-vlan 200 !The instance will create the vlan and tag the erp ports in it cfm-domain-level 4 port 0 port-id 1/1/1 !Mapping erp port 0 to a physical ring port mep 211 !Mapping erp port 0 to a remote cfm port rpl-port ! Port 1 port-id 1...
Page 373
Installation and operation manual 25-322 secflow-4 ver.3.10 switch 2 config vlan 1 no management no routing-interface sw0 no untagged 1/1/1 no untagged 1/1/2 no untagged 1/1/3 ! Commit vlan 100 name erp_1_ctrl ! Cfm vlan to be used for control at the erp instance 1 tagged 1/1/1 ! Tagged 1/1/2 ! Tagg...
Page 374
Installation and operation manual secflow-4 ver.3.10 25-323 monitor-vlan 200 !The instance will create the vlan and tag the erp ports in it cfm-domain-level 4 port 0 port-id 1/1/1 !Mapping erp port 0 to a physical ring port mep 121 !Mapping erp port 0 to a remote cfm port rpl-port !Rpl port (because...
Page 375
Installation and operation manual 25-324 secflow-4 ver.3.10 cfm !Cfm configuration for creating control vlan to the erp instance domain ring_1 level 4 sender-id-content all ma erp_1_ctrl vlan 100 mep 313 bind-to 1/1/3 direction down no shutdown ccm-enabled exit ! Mep 322 bind-to 1/1/2 direction down...
Page 376
Installation and operation manual secflow-4 ver.3.10 25-325 vlan 200 !This is the user vlan to be monitored. Created automatically by the instance management routing-interface sw0 untagged 1/1/8 !Tagging user ports must take place only after the vlan creation by the instance. ! ! Port 1/1/8 default-...
Page 377: Chapter 26
Installation and operation manual 26-326 secflow-4 ver.3.10 chapter 26 system log the application software provides system log messages that are useful to the system administrator for troubleshooting problems in the network: • the console log routes system messages to a local or remote console, or t...
Page 378
Installation and operation manual secflow-4 ver.3.10 26-327 example jan 1 01:02:48 info ospf interface 192.168.1.1 join allspfrouters multicast group. 26.2 settings and values severity levels trap level for logging should be configured per receiver (buffer, cli console, ssh console, and syslog serve...
Page 379
Installation and operation manual 26-328 secflow-4 ver.3.10 audit log audit auth security/authorization messages clock clock daemon cron messages generated internally by syslog daemon system daemons ftp ftp daemon local0 local use 0 (local0) local1 local use 1 (local1) local2 local use 2 (local5) lo...
Page 382: Appendix A
Installation and operation manual secflow-4 ver.3.10 27-331 appendix a acronyms glossary acronym meaning aaa authentication, authorization and accounting acg access control group acl access control list ais alarm indication signal arp address resolution protocol as autonomous system asbr autonomous ...
Page 383
Installation and operation manual 27-332 secflow-4 ver.3.10 acronym meaning lbm loopback message lbr loopback reply ler label edge router lsp label switched path ltm linktrace message ltr linktrace reply ma maintenance association mac media access control ma id maintenance association identifier mc ...
Page 384
Installation and operation manual secflow-4 ver.3.10 27-333 acronym meaning sdp service distribution path sf signal failure sfp small form-factor pluggable snmp simple network management protocol ssh secure shell tacacs+ terminal access controller access control system plus tc topology change tcp tr...
Page 385
Installation and operation manual 27-334 secflow-4 ver.3.10
Page 387
Publication no. 614-200-06/13 order this publication by catalog no. 805057 international headquarters 24 raoul wallenberg street tel aviv 69719, israel tel. 972-3-6458181 fax 972-3-6498250, 6474436 e-mail market@rad.Com north america headquarters 900 corporate drive mahwah, nj 07430, usa tel. 201-52...