- DL manuals
- Ralink
- Adapter
- 150N wireless adapter
- User Manual
Ralink 150N wireless adapter User Manual
Summary of 150N wireless adapter
Page 1
150n wireless lan usb adapter user manual version: 1.0 (june, 2009).
Page 2: Copyright
Copyright copyright ©2009/2010 by this company. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, ch...
Page 3: Interference Statement
Federal communication commission interference statement this equipment has been tested and found to comply with the limits for a class b digital device, pursuant to part 15 of fcc rules. These limits are designed to provide reasonable protection against harmful interference in a residential installa...
Page 4
Federal communication commission (fcc) radiation exposure statement this eut is compliance with sar for general population/uncontrolled exposure limits in ansi/ieee c95.1-1999 and had been tested in accordance with the measurement methods and procedures specified in oet bulletin 65 supplement c. The...
Page 5: R&tte Compliance Statement
R&tte compliance statement this equipment complies with all the requirements of directive 1999/5/ec of the european parliament and the council of march 9, 1999 on radio equipment and telecommunication terminal equipment and the mutual recognition of their conformity (r&tte) the r&tte directive repea...
Page 6: C A T A L O G
C a t a l o g chapter i: product information ............................................................. 1 1-1 introduction and safety information ................................................................ 1 1-2 safety information ................................................................
Page 7
Chapter iv: appendix ............................................................................ 72 4-1 specification .................................................................................................. 72 4-2 troubleshooting ..............................................................
Page 8
1 chapter i: product information 1-1 introduction and safety information thank you for purchasing this high-speed wireless network card! Excepting common wireless standards 802.11b/g, this wireless network card is also able to access 802.11n wireless networks - data transfer rate is 150mbps, and tha...
Page 9
2 1-2 safety information in order to keep the safety of users and your properties, please follow the following safety instructions: 1. This usb wireless network card is designed for indoor use only. Do not expose this network card to direct sun light, rain, or snow. 2. Do not put this network card a...
Page 10
3 1-3 system requirements an empty usb 2.0 port (may not be able work with usb 1.1 port, and performance will be greatly reduced) windows 2000, xp, or vista operating system cd-rom drive at least 100mb of available disk space.
Page 11
4 1-4 package contents before you starting to use this wireless network card, please check if there’s anything missing in the package, and contact your dealer of purchase to claim for missing items: □ usb wireless network card (1 pcs) …………………………… 1 □ protection cap (1 pcs) ……………………………………..…… 2 □ qui...
Page 12
5 1-5 familiar with your new wireless network card 1. Usb connector 2. Connector cap (to protect usb connector when not in use) 3. Link/activity led 4. Wps button led name light status description radio off off wireless lan function is disabled. Radio on (no link) off no link to wireless ap or route...
Page 13
6 chapter ii: driver installation and configuration 2-1 network card installation please follow the following instructions to install your new wireless network card: 1. Insert the usb wireless network card into an empty usb 2.0 port of your computer when computer is switched on. Never use force to i...
Page 14
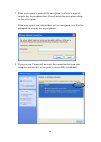
7 2. The following message will appear on your computer, click ‘cancel’. 3. Insert device driver cdrom into the cd/dvd rom drive of your computer, and execute ‘setup.Exe’ program. Please read the end user license agreement and click ‘i accept the terms of the license agreement’ then click ‘next’ but...
Page 15
8 4. It is recommend installing driver and utility if the network card is installing the first time. If you want to update the driver only, choose ’install driver only’. Click ‘next’ to continue. 5. You can choose the configuration tool used to configure the wireless network card here. It’s recommen...
Page 16: Please Ignore It and Wait.
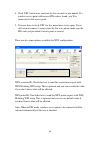
9 6. Now you’ll see the following message, please click ‘install’ to start utility installation. If you see ‘found new hardware’ message again, please ignore it and wait..
Page 17
10 7. Please wait while the install procedure is running. When you see this message, please click ‘finish’ to complete the driver installation process..
Page 18: Here!
11 8. After installation is complete, wireless configuration utility will be shown in the desktop of your computer automatically. You will also see an icon at the lower-right corner of your windows system. If you put the mouse cursor on the icon, the status of wireless card will be displayed as a po...
Page 19
12.
Page 20
13 2-2 connect to wireless access point after the driver is correctly installed, it will try to connect to any unencrypted wireless access point automatically. If you want to connect to a specific wireless access point, or the access point you wish to connect uses encryption, you have to configure t...
Page 21
14 2-2-1 using ralink utility please follow the following instructions to use ralink configuration utility to connect to wireless access point. 1. Right-click the ralink configuration utility icon located at lower-right corner of computer desktop and then clicks ‘launch config utility’. 2. Ralink se...
Page 22
15 you can click ‘more / less’ button again, and setup utility window will resume to its original size. Tip: if a setup item requires more information to complete the setup procedure, the setup utility window will expand automatically..
Page 23
16 2-2-1-1 scan for other wireless devices there are two kinds of wireless connection mode: infrastructure and ad-hoc. Infrastructure mode is used by wireless access points, which is able to establish wireless connection for you and other wireless / wired network clients. Ad-hoc mode is also know as...
Page 24
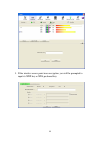
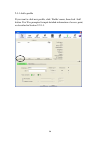
17 scan results will be displayed here, please check if the wireless device (access point or another computer) with the ssid you wish to connect is shown here. Scan result includes 6 types of information, they are: a the ssid (service set identifier) of wireless device. If nothing is displayed here,...
Page 25
18 c the wireless standard supported by this access point is displayed here. ‘n’ for 802.11n , ‘g; for 802.11g , and ‘b’ for 802.11b . Wps icon will appear when the access point supports wps. If the access point uses encryption, a key icon will appear. Note: when the access point supports wps and wp...
Page 26
19 there are 4 types of technical information: general: displays basic information about this access point, such as ssid, mac address, authentication / encryption type, channel etc. Wps: if this access point supports wps (wi-fi protected setup), related information will be displayed here. Ccx: if th...
Page 27
20 and here are descriptions of every setup item in setup area: item name description sorted by >> you can decide how to sort all listed access point by ‘ssid’, ‘channel’, or ‘signal’ (signal strength). Show dbm check this box to show the signal strength of access point, instead of percentage. Resca...
Page 28
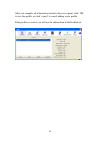
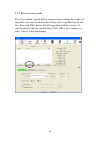
21 2-2-1-2 connect to an access point if the wireless access point you wish to connect is found, you can establish connection with it by clicking ‘connect’ button. Instructions will be given as follow: 1. Click the wireless access point or network device you wish to connect, it will be highlighted, ...
Page 29
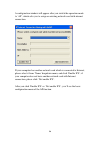
22 3. If the wireless access point uses encryption, you will be prompted to input its wep key or wpa preshared key..
Page 30
23 4. Please ask the owner of the wireless access point you want to connect, and input the correct key here and then click ‘ok’. By checking ‘show password’ box, the encryption key you inputted here will be displayed. If the value you inputted here is wrong, you will not be able to connect to this w...
Page 31
24 you can also click more / less button ( ) to see detailed information of connected access point:.
Page 32
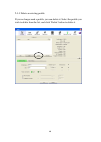
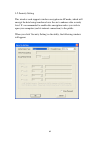
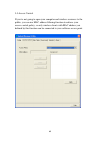
25 2-2-1-3 add an access point to profile if you will connect to some specific wireless access point frequently, you can add their information to the profile. Just like the telephone directory, the profile saves all information of access points, and you can recall them anytime you wish to establish ...
Page 33
26 the setup utility will expand: here are descriptions of every setup item: item name description profile name you can give this profile a name. Every profile needs a unique name. Ssid please input the ssid of this access point. If you selected an access point from the list, and its ssid is not hid...
Page 34
27 decide the best output power for you. Preamble select the preamble for ad hoc mode here. Available options are ‘auto’ and ‘long’. It’s suggested to select ‘auto’ to let setup utility decide the preamble for you. Channel you can select the radio channel number for adhoc mode here. Power save mode ...
Page 35
28 to set authentication / encryption information for the access point. Please click ‘auth. \ encry.’ tab: here are descriptions of every setup item: item name description authentication select the authentication type of the wireless access point or wireless device you wish to connect. When you’re a...
Page 36
29 profile from an existing access point or wireless device, the encryption type will be selected automatically, and please do not modify it. Wpa preshared key input wpa preshared key here. If encryption is not enabled, or you select ‘wep’ as encryption type, this field will be disabled and grayed o...
Page 37
30 to set 802.1x authentication for the access point. Please click ‘802.1x’ tab: here are descriptions of every setup item: item name description eap method select 802.1x eap method from dropdown menu. Please ask the administrator of the access point you wish to connect to select a correct eap metho...
Page 38
31 if you need to use protected authentication credential, check ‘use protected authentication credential’ box, and click ‘import’ to load .Pac credential file; to remove a loaded credential file, click ‘remove’. Session resumption you can enable or disable session resumption here. If you don’t know...
Page 39
32 after you complete all information related to the access point, click ‘ok’ to save the profile, or click ‘cancel’ to cancel adding a new profile. If the profile is created, you will see the information in the profile list..
Page 40: Here!
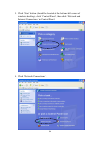
33 2-2-2 using windows zero configuration windows xp and vista has a built-in wireless network configuration utility, called as ‘windows zero configuration’ (wzc). You can also use wzc to configure your wireless network parameter: 1. Right-click ralink configuration utility icon and select ‘use zero...
Page 41
34 3. Click ‘start’ button (should be located at the bottom-left corner of windows desktop), click ‘control panel’, then click ‘network and internet connections’ in control panel. 4. Click ‘network connections’..
Page 42
35 5. Right-click ‘wireless network connection’ (it may have a number as suffix if you have more than one wireless network card, please make sure you right-click the ‘ralink 802.11n wireless lan card), then select ‘view available wireless networks’. 6. All wireless access points in proximity will be...
Page 43
36 7. If the access point is protected by encryption, you have to input its security key or passphrase here. It must match the encryption setting on the access point. If the access point you selected does not use encryption, you’ll not be prompted for security key or passphrase. 8. If you can see ‘c...
Page 44
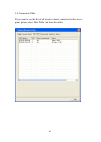
37 2-3 profile management if you need to connect to different wireless access points at different time, like of access point of your home, office, cybercafe, or public wireless service, you can store the connection parameters (encryption, passphrase, security etc, etc.) as a profile for every access...
Page 45
38 2-3-1 add a profile if you want to click new profile, click ‘profile’ menu, then click ‘add’ button. You’ll be prompted to input detailed information of access point, as described in section 2-2-1-3..
Page 46
39 2-3-2 edit an existing profile if you have added a profile before, and you wish to change the content of the profile, you can use this function. Please select a profile from the list first, then click ‘edit’ button. You’ll be provided with the contents of selected profile, and you can edit them. ...
Page 47
40 2-3-3 delete an existing profile if you no longer need a profile, you can delete it. Select the profile you wish to delete from the list, and click ‘delete’ button to delete it..
Page 48
41 2-3-4 activate a profile when you want to connect to a specific wireless device in the profile list, you can select it and click ‘activate’ button, to establish connection with it. When you selected a profile and click ‘activate’ button to activate the profile, a icon will be displayed in front o...
Page 49
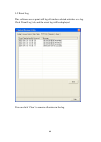
42 2-4 advanced settings this wireless network card provides several advanced settings for experienced wireless users. You can change these settings to increase data transfer performance, or change operation mode. Please follow the following instructions to set advanced wireless settings: 1. Right-c...
Page 50
43 here are descriptions of every setup item: item name description wireless mode display the wireless operation mode of the network card. Enable tx burst check this box to accelerate the data transmit rate. It may not work with all wireless access point and wireless devices. Enable tcp window size ...
Page 51
44 enable radio measurements: when you’re connecting to ccx-compatible access point, check this box to enable radio measurement function to improve wireless connectivity. Non-serving channel measurements limit: when you’re connecting to ccx-compatible access point, check this box to enable measureme...
Page 52
45 2-5 view network statistics the configuration utility provides information about network statistics and link status. If you want to know how your wireless network card works, you can use these functions to get detailed information about the wireless connection you’re using. Please follow the foll...
Page 53
46 2-6 wmm setting this wireless network card provides wmm (wi-fi multimedia) function, which can improve the performance of certain network applications, like audio/video streaming, network telephony (voip), and others. When you enable the wmm function of this network card, you can define the prior...
Page 54
47 in ‘wmm setup status’ block, current wmm settings will be displayed. And here are descriptions of every setup item: item name description wmm enable check this box to enable wmm function. Please click ‘apply’ button on the right of this check box after you check or uncheck this box, so correspond...
Page 55
48 2-7 wps configuration wi-fi protected setup (wps) is the latest wireless network technology which makes wireless network setup become very simple. If you have wps-enabled wireless access point, and you want to establish a secure connection to it, you don’t have to configure the wireless access po...
Page 56
49 2-7-1 wps setup - pbc (push-button configuration) 1. Right-click the ralink configuration utility icon located at lower-right corner of computer desktop and then click ‘launch config utility’. 2. Click ‘wps’ menu, and the following settings will appear. 3. Set ‘config mode’ to ‘enrollee’, and the...
Page 57
50 4. Before you start to establish the wireless connection by using wps, you can click ‘rescan’ button to search for wps-enabled access points near you again, to make sure the wps function of your access point is activated. All access points with wps function enabled will be displayed here. Please ...
Page 58
51 6. You can click ‘detail’ button to see detailed information of connected access point. If you wish to save this connection as a profile, you can click ‘export profile’ button, and this connection will be saved. You can find this connection in ‘profile’ tab in a later time. 7. Sometime wps may fa...
Page 59
52 2-7-2 wps setup - pin if the wireless access point you wish to connect supports pin, please follow the following instructions to establish connection to it: 1. Right-click the ralink configuration utility icon located at lower-right corner of computer desktop and then click ‘launch config utility...
Page 60
53 4. Click ‘pin’ button now, and wait for few seconds to one minute. If a wireless access point with correct pin code is found, you’ll be connected to that access point. 5. You may have to click ‘pin’ for few more times to try again. If you still can not connect to access point by this way, please ...
Page 61
54 2-8 radio on/off you can switch the wireless radio transceiver on and off by the utility, so if you want to disable wireless network function, you don’t have to remove the network card physically. 1. Right-click the ralink configuration utility icon located at lower-right corner of computer deskt...
Page 62
55 2-9 about the ‘about’ tab provides you the information about version number of the configuration utility, driver, and other important information about your wireless network card. Please follow the following instructions to see these information: 1. Right-click the ralink configuration utility ic...
Page 63
56 2-10 on-line help if you need to know the directions of how to use specific function in the utility, please click ‘help’ button. On-line help documents will be presented in windows help format. Click this button to view on-line help documents..
Page 64
57 chapter iii: soft-ap function excepting become a wireless client of other wireless access points, this wireless card can act as a wireless service provider also! You can switch this wireless card’s operating mode to ‘ap’ mode to simulate the function of a real wireless access point by software, a...
Page 65
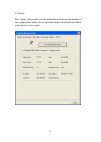
58 a configuration window will appear after you switch the operation mode to ‘ap’, which asks you to assign an existing network card with internet connection. If your computer has another network card which is connected to internet, please select it from ‘name’ dropdown menu, and click ‘enable ics’;...
Page 66
59 here are descriptions of every setup item: item name description ssid please input the ssid (the name used to identify this wireless access point) here. Up to 32 numerical characters can be accepted here, excepting space. Channel please select the wireless channel you wish to use. The number of c...
Page 67: Regulations.
60 wireless card as ssid. A prefix ‘ap’ will be added automatically. Security setting set the security options (wireless data encryption). Please refer to chapter 3-2 ‘security settings’ for details. Country region code please select the country code of the country or region you live. Available opti...
Page 68
61 beacon(ms) you can define the time interval that a beacon signal should be send. Default value is 100. Do not modify this value unless you know what will be affected. Tx power you can select the wireless output power here. Please select a proper output power setting according to your actual needs...
Page 69
62 3-2 security setting this wireless card supports wireless encryption in ap mode, which will encrypt the data being transferred over the air to enhance data security level. It’s recommended to enable data encryption unless you wish to open your computer (and its internet connection) to the public....
Page 70
63 here are descriptions of every setup item: item name description authentication type please select a wireless authentication type you wish to use. Available options are ‘open’, ‘shared’, wpa-psk’, ‘wpa2-psk’, and ‘wpa-psk / wpa2-psk’. If you want to disable wireless data encryption, you must sele...
Page 71
64 characters if you select ascii. 128 bits encryption is safer then 64 bits, but the data transfer speed will be slightly reduced. Show password check this box and the wpa pre-shared key or wep key you inputted will be shown, but not replaced by asterisk (*). When you finish with setting and want t...
Page 72
65 3-3 access control if you’re not going to open your computer and wireless resources to the public, you can use mac address filtering function to enforce your access control policy, so only wireless clients with mac address you defined by this function can be connected to your software access poin...
Page 73
66 here are descriptions of every setup item: item name description access policy select the policy type of your access rule. Disable: allow any wireless client with proper authentication settings to connect to this access point. Allow all: only allow wireless clients with mac address listed here to...
Page 74
67 3-4 connection table if you want to see the list of all wireless clients connected to this access point, please select ‘mac table’ tab from the utility..
Page 75
68 here are descriptions of every field: item name description mac address displays the mac address of this wireless client. Aid the serial number of this wireless connection. Power saving mode displays the capability of power-saving function of this wireless client. Status displays additional infor...
Page 76
69 3-5 event log this software access point will log all wireless-related activities as a log. Click ‘event log’ tab, and the event log will be displayed. You can click ‘clear’ to remove all entries in the log..
Page 77
70 3-6 statistics if you want to know detailed information about how your software access point works, click ‘statistics’ tab, and the event log will be displayed. You can click ‘reset counters’ button to reset all counters to zero..
Page 78
71 3-7 about the ‘about’ tab provides you the information about version number of the configuration utility, driver, and other important information about your wireless access point..
Page 79: Chapter Iv: Appendix
72 chapter iv: appendix 4-1 specification standards: ieee 802.11b/g/n (1t1r) interface: usb 2.0 (usb 1.1 compatible) frequency band: 2.4000 ~ 2.4835ghz (industrial scientific medical band) data rate: 11b: 1/2/5.5/11mbps 11g: 6/9/12/24/36/48/54mbps 11n (20mhz): mcs0-7 (up to 72mbps) 11n (40mhz): mcs0...
Page 80
73 4-2 troubleshooting if you encounter any problem when you’re using this wireless network card, don’t panic! Before you call your dealer of purchase for help, please check this troubleshooting table, the solution of your problem could be very simple, and you can solve the problem by yourself! Scen...
Page 81
74 wireless access point connect is hidden (nothing displayed in ‘ssid’ field in ‘site survey’ function), you have to input correct ssid of the access point you wish to connect. Please contact the owner of access point to ask for correct ssid. 3. You have to input correct security key to connect an ...
Page 82: 4. What Is Ad-Hoc?
75 4-3 glossary 1. What is the ieee 802.11g standard? 802.11g is the new ieee standard for high-speed wireless lan communications that provides for up to 54 mbps data rate in the 2.4 ghz band. 802.11g is quickly becoming the next mainstream wireless lan technology for the home, office and public net...
Page 83: 6. What Is Bss Id?
76 5. What is infrastructure? An integrated wireless and wireless and wired lan is called an infrastructure configuration. Infrastructure is applicable to enterprise scale for wireless access to central database, or wireless application for mobile workers. 6. What is bss id? A specific ad hoc lan is...
Page 84: 14. What Is Wmm?
77 12. What is dsss? What is fhss? And what are their differences? Frequency-hopping spread-spectrum (fhss) uses a narrowband carrier that changes frequency in a pattern that is known to both transmitter and receiver. Properly synchronized, the net effect is to maintain a single logical channel. To ...
Page 85
78 15. What is wmm power save? Wmm power save is a set of features for wi-fi networks that increase the efficiency and flexibility of data transmission in order to conserve power. Wmm power save has been optimized for mobile devices running latency-sensitive applications such as voice, audio, or vid...