- DL manuals
- Range Master
- Antenna
- WiFi King
- User manual
Range Master WiFi King User manual
Summary of WiFi King
Page 1
Version: 2.0 iii 802.11n long-range usb wifi antenna user manual version: 2.0
Page 2: Table Of Contents
Version: 2.0 iii table of contents overview ..........................................................1 u npacking i nformation ................................................................................................ . 1 i ntroduction to the wifi king w ireless usb a dapter ....................
Page 3: Unpacking Information
Version: 2.0 1 overview thank you for purchasing this product. Read this chapter to learn about your range master wifi king 802.11n wireless usb adapter. Unpacking information before getting started, please verify that your package includes the following items: 1. Wifi king wireless usb adapter. 2. ...
Page 4: Key Features
Version: 2.0 2 key features y complies with ieee 802.11n wireless standards y supports wireless data encryption with 64/128-bit wep, wpa, wpa2, tkip, aes y 2.4ghz frequency band, mimo y supports qos: wmm, wmm-ps y complies with usb 2.0 y supports multiple bssid y high speed transfer data rate up to ...
Page 5
Version: 2.0 3 3. Select if you are going to install the driver and wireless utility; or install the driver only. 4. Select if you are going to configure your wireless network with this device or with microsoft zero configuration tool. Note: this can be changed after installing this software..
Page 6
Version: 2.0 4 5. Click the install button to start installing. 6. Click the finish button to complete installation..
Page 7
Version: 2.0 5 ….. Management guide read this chapter to understand the management interface of the device and how to manage the device. Making a basic network connection select a configuration tool in the following instructions for making a network connection, we use the utility we provide to confi...
Page 8
Version: 2.0 6 the tool shows the available wireless networks. Select the network you want to connect to. To connect to a wireless network with more security settings, please click change advanced settings and configure to be compatible with your wireless network security settings..
Page 9
Version: 2.0 7 to connect with 802.11n wireless lan utility we provide this utility for users to connect to a wireless network easily. It provides more information and configuration for this adapter. As default, the utility is started automatically upon starting your computer and connects to a conne...
Page 10
Version: 2.0 8 introduction to the 802.11n wireless lan utility note: the utility in linux and mac are different from the following. Interfaces this utility basically consists of three parts: 1 2 3 1. Function buttons: on top of the window. You can click each button to access each configuration wind...
Page 11
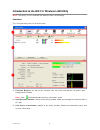
Version: 2.0 9 link status information a c d b a. Network information: items information status show the connecting status. Also shows the ssid while connecting to a valid network. Extra info display link status in use. Channel display current channel in use. Authentication authentication mode in us...
Page 12
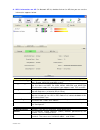
Version: 2.0 10 profile the profile page allows users to save different wireless settings, which helps users to get access to wireless networks at home, office or other wireless network environments quickly. A c b a. Profile list: the list shows all the profiles you have added before. B. Buttons: yo...
Page 13
Version: 2.0 11 to add a new profile: 1. Click the add button. The add profile window pops up. Note: you could also add a new profile quickly by selecting an available network in the network function then click the add to profile button. ← click on these tabs 2. There are three tabs on the window: s...
Page 14
3. In section, fill in information for this profile: items information profile name choose a name for this profile, or use default name defined by system. Ssid fill in the intended ssid name or use the drop list to select from available aps. Network type there are two types, infrastructure and 802.1...
Page 15
Version: 2.0 13 authentication available encryption selection open none, wep shared wep leap (no selection) wpa/wpa2/wpa-psk wpa2-psk/wpa-none tkip, aes authentication available encryption selection open none, wep shared wep wpa/ wpa-psk/ wpa2-psk tkip, aes wpa2 tkip, aes, tkip(mfp), aes(mfp) cckm w...
Page 16
Version: 2.0 14 use 802.1x this checkbox appears while the environment is set to an open authentication with wep encryption. Mark the checkbox to make the section available. The section is also available in wpa and wpa2 authentication types. Preshared key this is the shared secret between ap and sta...
Page 17
Version: 2.0 15 5. Specify the 802.1x information if you are using the 802.1x certification method. Users that do not use this function or connect to an open-wireless network please skip this part. A b c a. Eap method: for windows 2000 user: there are total 5 modes: peap, tls/smart card, ttls, eap-f...
Page 18
Version: 2.0 16 b. Tunnel authentication: the tunnel authentication will differ from the eap method you have chosen, the result is shown below: for windows 2000 user: eap method tunnel authentication peap eap-mschap v2 , eap-tls/smart card, generic token card tls/smart card (no selection) ttls chp, ...
Page 19
Version: 2.0 17 id \ password items information authentication id / password the identity, password and domain name for server. Only "eap-fast" and "leap" authentication can be keyed in domain name. Blank space can be keyed in domain name. Tunnel id / password identity and password for server. Passw...
Page 20
Version: 2.0 18 server certificate items information use certificate chain mark the checkbox to enable using certification chain. Allow intimidate certificates mark to allow intimidates certification. Server name enter an authentication sever root. Eap fast items information allow unauthenticated pr...
Page 21
Version: 2.0 19 network this network lists the available wireless networks. The utility connects to a wireless network with the best signal strength automatically. You can change the connecting network by clicking on the network name and click the connect button. To see detail information of each ne...
Page 22
Version: 2.0 20 advanced this page provides advanced configurations to this adapter. Please refer to the following chart for definitions of each item. Items information wireless mode select wireless mode. 2.4g/5.8g is supported. Enable tx burst select to enable connecting to a tx burst supported dev...
Page 23
Version: 2.0 21 statistics statistics page displays the detail counter information based on 802.11 mib counters. This page translates the mib counters into a format easier for user to understand. Items information frames transmitted successfully frames successfully sent. Frames retransmitted success...
Page 24
Version: 2.0 22 wmm this page allows users to activate the wmm function for this device. Please note that this function only works while connecting to a wmm compatible device. Items information wmm enable enable wi-fi multi-media. Wmm - power save enable enable wmm power save. Please enable wmm befo...
Page 25
Version: 2.0 23 steps to enable direct link setup function: 1. Click the "direct link setup enable" checkbox. 2. Change to "network" function. Add an ap that supports dls features to the profile. 3. Fill in the blanks of direct link with mac address of sta. The sta must conform to these two conditio...
Page 26
Version: 2.0 24 wps the primary goal of wi-fi protected setup (wi-fi simple configuration) is to simplify the security setup and management of wi-fi networks. This adapter supports the configuration setup using pin configuration method or pbc configuration method through an internal or external regi...
Page 27
Version: 2.0 25 the following description divides into four parts: a. Wps information on ap b. Example of adding to registrar using pin method c. Example of adding to registrar using pin method d. Example of configuring a network/ap using pin or pbc method.
Page 28
Version: 2.0 26 a. Wps information on ap: on network ap list, double click on the ap then you can see the information appears below. Items information authentication type there are three authentication modes supported by this utility. They are open, shared, wpa-psk and wpa system. Encryption type fo...
Page 29
Version: 2.0 27 b. Example of adding to registrar using pin method the user obtains a device password (pin code) from the sta and enters the password into the registrar. Both the enrollee and the registrar use pin config method for the configuration setup. Please follow the step below. 1. Select "en...
Page 30
Version: 2.0 28 4. Click "pin" to enter the pin. 5. Enter the pin code of the sta into the registrar when prompted by the registrar. Note: y allow of an exchange between step 4 and step 5. Y if you use microsoft window connection now as an external registrar, you must start pin connection at sta fir...
Page 31
Version: 2.0 29 7. Configure one or more credentials. Then connect successfully. 8. Click "detail." you can see the figure below. C. Example of adding to the registrar using the pbc method the pbc method requires the user to press a pbc button on both the enrollee and the registrar within a two-minu...
Page 32
Version: 2.0 30 1. Select "enrollee" from the config mode drop-down list. 2. Click pbc to start the pbc connection. 3. Push the pbc on ap. Note: allow time for an exchange between step 2 and step 3..
Page 33
Version: 2.0 31 4. The progress bar as shown in the figure below indicates that scanning progress. 5. When one ap is found, join it..
Page 34
Version: 2.0 32 6. Check wps information on the available wps aps. 7. Configure and receive one or more credential(s).Then connect successfully. The result will be displayed as it is in the figure below..
Page 35
Version: 2.0 33 d. Example of configuring a network/ap using pin or pbc method 1. Select "registrar" from the config mode drop-down list. 2. Enter the details of the credential and change configurations (ssid, authentication, encryption and key) manually if needed. 3. If the pin configuration is set...
Page 36
Version: 2.0 34 5. If your ap enrollee has been configured before the wps process, the credential you set in advance will be updated to the ap itself. Otherwise, after a successful registration, the ap enrollee will be re-configured with the new parameters, and the sta registrar will connect to the ...
Page 37
Version: 2.0 35 ccx this page is available for vista user only. It provides ccx configurations to this adapter. Please refer to the following chart for definitions of each item. Items information enable ccx (cisco compatible extensions) select to enable ccx. This function can only be applied when co...
Page 38
Version: 2.0 36 ap mode management guide for windows 2000/xp/vista if you wish to share the internet access with the wireless stations in your environment, you can configure this wireless adapter as a software access point (soft ap). In this mode, this wireless adapter becomes the wireless access po...
Page 39
Software access point (soft ap) application version: 2.0 37.
Page 40
Version: 2.0 38 config this page provides overall configuration to this adapter. Please find the following items for identification to each field. 1 7 2 8 9 3 10 11 12 4 5 6 13 14 15 1. Ssid: ap name of user type. User also can select [use mac address] to display it. 2. Wireless mode: select wireles...
Page 41
Version: 2.0 39 3. Country region code: eight countries to choose. Country channel list: classification range 0: fcc (canada) ch1 ~ ch11 1: etsi ch1 ~ ch13 2: spain ch10 ~ ch11 3: france ch10 ~ ch13 4: mkk ch14 ~ ch14 5: mkki (telec) ch1 ~ ch14 6: israel ch3 ~ ch9 7: israel ch5 ~ ch13 note: country ...
Page 42
Version: 2.0 40 security setting this page pops up after clicking the security setting button. Please follow the instructions below: 1 2 3 4 5 1. Authentication type: select to be open, shared, wpa-psk, wpa2-psk, or wpa psk/wpa2-psk system. 2. Encryption type: select an encryption type from the drop...
Page 43
Version: 2.0 41 access control this function filters users to use this device by designating mac address. Please refer to the following chart for introduction. 1 2 3 4 5 6 1. Access policy: choose a method to process access control from the drop list to determine the mac addresses that you designate...
Page 44
Version: 2.0 42 mac table this page displays the station detail information of current connection. Items information mac address the station mac address of current connection. Aid raise value by current connection. Power saving mode check if the connected station supports power saving. Status the co...
Page 45
Version: 2.0 43 event log record soft ap all event time and message. Items information event time (yy/mm/dd-hh:mm:ss) record event time. Message all event messages..
Page 46
I statistics statistics page displays the detail counter information based on 802.11 mib counters. 1 2 3 1. Transmit statistics items information frames transmitted successfully frames that successfully sent. Frames fail to receive ack after all retries frames that failed to transmit after hitting r...
Page 47: Fcc Certifications
I fcc certifications federal communication commission interference statement this equipment has been tested and found to comply with the limits for a class b digital device, pursuant to part 15 of the fcc rules. These limits are designed to provide reasonable protection against harmful interference ...
Page 48: Ce Mark Warning
Version: 2.0 ii ce mark warning this equipment complies with the requirements relating to electromagnetic compatibility, en 55022 class b for ite, the essential protection requirement of council directive 89/336/eec on the approximation of the laws of the member states relating to electromagnetic co...