- DL manuals
- Raritan
- Switch
- Dominion KX II-101-V2
- User Manual
Raritan Dominion KX II-101-V2 User Manual
Summary of Dominion KX II-101-V2
Page 1
Copyright © 2014 raritan, inc. Kx2101v2-v3.6.0-d-e may 2014 255-62-3059-00 dominion kx ii-101-v2 user guide release 3.6.0
Page 2
This document contains proprietary information that is protected by copyright. All rights reserved. No part of this document may be photocopied, reproduced, or translated into another language without express prior written consent of raritan, inc. © copyright 2014 raritan, inc. All third-party softw...
Page 3: Contents
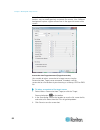
Iii contents chapter 1 introduction 1 kx ii-101-v2 overview .................................................................................................................. 2 package contents .............................................................................................................
Page 4
Contents iv toolbar buttons and status bar icons ............................................................................... 39 power controlling a target server .................................................................................... 41 disconnecting kvm target servers ................
Page 5
Contents v view users by port ............................................................................................................ 80 disconnecting users from ports ........................................................................................ 80 logging users off the kx ii-101-v2 ...
Page 6
Contents vi analog kvm switch ................................................................................................................... 123 resetting the kx ii-101-v2 using the reset button .................................................................. 124 changing the default gui lang...
Page 7
Contents vii logging in .................................................................................................................................. 164 navigation of the cli ................................................................................................................. 164 c...
Page 8
Contents viii setting the registry to permit write operations to the schema ............................................... 185 creating a new attribute ............................................................................................................ 185 adding attributes to the class ......
Page 9: Chapter 1 Introduction
1 in this chapter kx ii-101-v2 overview .............................................................................. 2 package contents ..................................................................................... 3 kx ii-101-v2 help ...........................................................
Page 10
Chapter 1: introduction 2 kx ii-101-v2 overview thank you for purchasing the dominion kx ii-101-v2. The kx ii-101-v2 provides a single keyboard, video, and mouse (kvm) port for connection to a target server, and a single ip port for connection to an ip network. Within the kx ii-101-v2 device, kvm si...
Page 11
Chapter 1: introduction 3 diagram key kx ii-101-v2 lan windows ® , linux ® and sun ™ servers tcp/ip lan remote (network) access mobile access via iphone ® and ipad ® using cc-sg package contents each kx ii-101-v2 device ships with: 1 - kx ii-101-v2 kvm over ip 1 - kvm cable 1 - power adapter (ac/dc ...
Page 12
Chapter 1: introduction 4 kx ii-101-v2 help kx ii-101-v2 online help is considered your primary help resource. Pdf versions of help are a secondary resource. See the kx ii-101-v2 release notes for important information on the current release before you begin using the kx ii-101-v2. Kvm client help i...
Page 13
Chapter 1: introduction 5 product features interfaces integrated ps/2 kvm connection usb connection for control and virtual media serial admin port for initial device configuration and diagnostics, as well as use with an external modem access and raritan power strip control local port for monitor co...
Page 14
Chapter 1: introduction 6 administration features web-based management ldap, active directory ® , radius, or internal authentication and authorization dhcp or fixed ip addressing integration with raritan's commandcenter secure gateway (cc- sg) management unit mobile access from ipad ® and iphone ® t...
Page 15
Chapter 1: introduction 7 mounting rack mounting bracket.
Page 16
8 in this chapter overview .................................................................................................... 8 default login information .......................................................................... 8 getting started ......................................................
Page 17
Chapter 2: installation and configuration 9 getting started kx ii-101-v2 users with microsoft ® internet explorer ® version 6 or windows 2000 ® must upgrade to service pack 4 (sp4) or higher. The kx ii-101-v2 ships with a static default ip address. On a network without a dhcp server, you must config...
Page 18
Chapter 2: installation and configuration 10 mouse modes the kx ii-101-v2 operates in several mouse modes: absolute mouse synchronization ™ , intelligent mouse mode and standard mouse mode. Note: do not use an animated mouse while using intelligent mouse mode. Mouse parameters do not have to be alte...
Page 19
Chapter 2: installation and configuration 11 windows xp, windows 2003, windows 2008 mouse settings configure these mouse settings in windows xp ® , windows 2003 ® and windows 2008 ® : configure the motion settings: set the mouse motion speed setting to exactly the middle speed disable the "enhance p...
Page 20
Chapter 2: installation and configuration 12 sun solaris mouse settings configure these sun ® solaris ™ mouse settings: set the mouse acceleration value to exactly 1 and the threshold to exactly 1 ensure that your video card is set to a supported resolution and that its output is vga, not composite ...
Page 21
Chapter 2: installation and configuration 13 step 3: connect the equipment power the kx ii-101-v2 is powered by a 100-240v ac input and 5vdc output power adaptor that is included with the device. For standard ac power, plug the included ac power adaptor into the power port and plug the other end int...
Page 22
Chapter 2: installation and configuration 14 target server use either the ps/2 or usb to connect to the target. Before connecting, configure your target server's video to a supported resolution. Use the usb connection if you are using virtual media or absolute mouse mode. The following items are in ...
Page 23
Chapter 2: installation and configuration 15 2. Connect the usb connector of the kvm cable to the kx ii-101-v2 and to a usb port on the target server. 3. Connect a monitor to the kx ii-101-v2 local user port if you need to use the local video. Optional 4. Connect the usb keyboard and mouse directly ...
Page 24
Chapter 2: installation and configuration 16 admin port use the admin port to do the following: configure and manage the device with a terminal emulation such as hyperterminal program on your pc. Configure and manage a power strip (requires an adapter, not included). Connect an external modem to dia...
Page 25
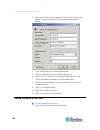
Chapter 2: installation and configuration 17 step 4: configure the kx ii-101-v2 note: you must use a crossover cable between the kx ii-101-v2 and client if you are configuring the kx ii-101-v2 through a web browser. For the following steps, you must change the default password and assign the kx ii-1...
Page 26
Chapter 2: installation and configuration 18 configure the ipv4 settings 1. In the ipv4 section, enter or select the appropriate ipv4-specific network settings: a. Enter the ip address if needed. The default ip address is 192.168.0.192. B. Enter the subnet mask. The default subnet mask is 255.255.25...
Page 27
Chapter 2: installation and configuration 19 d. Enter the gateway ip address. E. Link-local ip address. This address is automatically assigned to the device, and is used for neighbor discovery or when no routers are present. Read-only f. Zone id. Identifies the device the address is associated with....
Page 28
Chapter 2: installation and configuration 20 connect to a switch once kx ii-101-v2 is network accessible, remove the crossover cable and connect the kx ii-101-v2 to the switch using a cat5 cable. Configure date/time settings (optional) optionally, configure the date and time settings. The date and t...
Page 29
Chapter 2: installation and configuration 21 configure the kx ii-101-v2 using a terminal emulation program (optional) you can use the admin serial console with a terminal emulation program like hyperterminal to set the following configuration parameters for the kx ii-101-v2: ip address subnet mask a...
Page 31
Chapter 2: installation and configuration 23 command argument options interface mode based on the network. 10hdx - 10 mb/s, half duplex. 10fdx - 10 mb/s, full duplex 100hdx - 100 mb/s, half duplex 100fdx - 100 mb/s, full duplex when you have successfully changed a setting, you see a confirma...
Page 32
Chapter 2: installation and configuration 24 java validation and access warning when logging in to kx ii-101-v2, jave ™ 1.7 prompts you to validate kx ii-101-v2, and to allow access to the application. Raritan recommends installing an ssl certificate in each kx ii-101-v2 device in order to reduce ja...
Page 33
Chapter 2: installation and configuration 25 example 1: import the certificate into the browser in this example, you import the certificate into the browser. Steps open an ie browser, then log in to kx ii-101-v2. Click more information on the first java ™ security warning. Click view certificate det...
Page 34
Chapter 2: installation and configuration 26 steps click the content tab. Click certificates. The certificate import wizard opens and walks you through each step. file to import - browse to locate the certificate certificate store - select the location to store the certificate click finish on th...
Page 35
Chapter 2: installation and configuration 27 example 2: add the kx ii-101-v2 to trusted sites and import the certificate in this example, the kx ii-101-v2's url is added as a trusted site, and the self signed certificate is added as part of the process. Steps open an ie browser, then select tools > ...
Page 36
Chapter 2: installation and configuration 28 steps click ok on the internet options dialog to apply the changes, then close and reopen the browser. Next, import the certificate. Steps open an ie browser, then log in to kx ii-101-v2. Click more information on the first java ™ security warning. Click ...
Page 37
29 in this chapter interfaces ................................................................................................. 29 virtual kvm client (vkc) ......................................................................... 38 interfaces kx ii-101-v2 remote console interface the kx ii-101-v2 r...
Page 38
Chapter 3: working with target servers 30 3. Select the enable direct port access via url checkbox. 4. Click save. To define a direct port access url: define a url with the ip address, user name, password, and if necessary, port number of the kx ii-101-v2. The format for a direct port access url is:...
Page 39
Chapter 3: working with target servers 31 information description when displayed? State the current state of the application, either idle or active. If idle, the application tracks and displays the time the session has been idle. Always your ip the ip address used to access the kx ii-101-v2. Always ...
Page 40
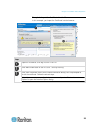
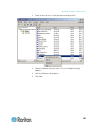
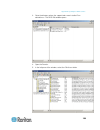
Chapter 3: working with target servers 32 click on the blue, left-facing arrow located approximately halfway down the left side of the panel. Once the panel is collapsed, click the blue arrow again to expand it. Port access page after successfully logging in to the kx ii-101-v2 remote console, the p...
Page 41
Chapter 3: working with target servers 33 2. Click the port name of the target server you want to access. The port action menu appears. See port action menu (on page 33) for details on available menu options. 3. Choose the desired menu command from the port action menu. Port action menu when you cli...
Page 42
Chapter 3: working with target servers 34 managing favorites a favorites feature is provided so you can organize and quickly access the devices you use frequently. The favorite devices section is located in the lower left side (sidebar) of the port access page and provides the ability to: create and...
Page 43
Chapter 3: working with target servers 35 enable favorites click enable in the favorite devices section of the left panel of the kx ii-101-v2 interface. Once enabled, the enable button becomes a disable button..
Page 44
Chapter 3: working with target servers 36 access and display favorites to access a favorite kx ii-101-v2 device: click the device name (listed beneath favorite devices). A new browser opens to that device. To display favorites by name: click display by name. To display favorites by ip address: click...
Page 45
Chapter 3: working with target servers 37 to use a different discovery port: a. Deselect the use default port 5000 checkbox. B. Type the port number in the discover on port field. C. Click save. 3. Click refresh. The list of devices on the local subnet is refreshed. To add devices to your favorite...
Page 46
Chapter 3: working with target servers 38 logging out to quit the kx ii-101-v2: click logout in the upper right-hand corner of the page. Note: logging out also closes any open virtual kvm client and serial client sessions. Multi-platform client (mpc) raritan multi-platform client (mpc) is a graphica...
Page 47
Chapter 3: working with target servers 39 connect to a target server once you have logged on to the kx ii-101-v2 remote console, access target servers via the virtual kvm client (kvc). Note: the kx ii-101-v2 only supports a connection to one target at a time. To connect to a target server: 1. On the...
Page 48
Chapter 3: working with target servers 40 button button name description video settings opens the video settings dialog, allowing you to manually adjust video conversion parameters. Color calibration adjusts color settings to reduce excess color noise. Same as choosing video > color calibrate. Note:...
Page 49
Chapter 3: working with target servers 41 button button name description single cursor mode starts single cursor mode in which the local mouse pointer no longer appears onscreen. Press ctrl+alt+o to exit this mode. Full screen mode maximizes the screen real estate to view the target server desktop. ...
Page 50
Chapter 3: working with target servers 42 disconnecting kvm target servers to disconnect a target server: on the port access page, click the port name of the target you want to disconnect from, then click disconnect on port action menu when it appears. Tip: you can also close the virtual kvm client ...
Page 51
Chapter 3: working with target servers 43 128 kb (dual isdn) 56 kb (isp modem) 33 kb (fast modem) 24 kb (slow modem) note that these settings are an optimization for specific conditions rather than an exact speed. The client and server always attempt to deliver video as quickly as possible o...
Page 52
Chapter 3: working with target servers 44 connection information to obtain information about your virtual kvm client connection: choose connection > info... The connection info window opens. The following information is displayed about the current connection: device name - the name of the device. Ip...
Page 53
Chapter 3: working with target servers 45 import/export keyboard macros macros exported from active kvm client (akc) cannot be imported into multi-platform client (mpc) or virtual kvm client (vkc). Macros exported from mpc or vkc cannot be imported into akc. To import macros: 1. Choose keyboard > im...
Page 54
Chapter 3: working with target servers 46 the macros are then imported. If a macro is imported that contains a hot key that already exists, the hot key for the imported macro is discarded. To export macros: 1. Choose tools > export macros to open the select keyboard macros to export dialog. 2. Selec...
Page 55
Chapter 3: working with target servers 47 building a keyboard macro to build a macro: 1. Click keyboard > keyboard macros. The keyboard macros dialog appears. 2. Click add. The add keyboard macro dialog appears. 3. Type a name for the macro in the keyboard macro name field. This name appears in the ...
Page 56
Chapter 3: working with target servers 48 9. Select the new macro on the menu to run it or use the keystrokes you assigned to the macro. To use the send text to target function for the macro: 1. Click the keyboard > send text to target. The send text to target dialog appears. 2. Enter the text you w...
Page 57
Chapter 3: working with target servers 49 modifying and removing keyboard macros to modify a macro: 1. Choose keyboard > keyboard macros. The keyboard macros dialog appears. 2. Choose the macro from among those listed. 3. Click modify. The add/edit macro dialog appears. 4. Make your changes. 5. Clic...
Page 58
Chapter 3: working with target servers 50 auto-sense video settings the auto-sense video settings command forces a re-sensing of the video settings (resolution, refresh rate) and redraws the video screen. To automatically detect the video settings, do the following: choose video > auto-sense video s...
Page 59
Chapter 3: working with target servers 51 warning: exercise caution when changing the clock and phase settings. Doing so may result in lost or distorted video and you may not be able to return to the previous state. Contact raritan technical support before making any changes. I. Horizontal offset - ...
Page 60
Chapter 3: working with target servers 52 note: some sun background screens, such as screens with very dark borders, may not center precisely on certain sun servers. Use a different background or place a lighter colored icon in the upper left corner of the screen. Screenshot from target command (tar...
Page 61
Chapter 3: working with target servers 53 changing the maximum refresh rate if the video card you are using on the target uses custom software, and you are accessing the target through the virtual kvm client (vkc) or multi-platform client (mpc), you may need to change the maximum refresh rate of the...
Page 62
Chapter 3: working with target servers 54 mouse pointer synchronization when remotely viewing a target server that uses a mouse, two mouse cursors are displayed: one belonging to your remote client workstation and the other belonging to the target server. When the mouse pointer lies within the virtu...
Page 63
Chapter 3: working with target servers 55 additional notes for intelligent mouse mode be sure that there are no icons or applications in the upper left section of the screen since that is where the synchronization routine takes place. Do not use an animated mouse. Disable active desktop on kvm targe...
Page 64
Chapter 3: working with target servers 56 intelligent mouse mode in intelligent mouse mode, the device can detect the target mouse settings and synchronize the mouse cursors accordingly, allowing mouse acceleration on the target. Intelligent mouse mode is the default for non- vm targets. During sync...
Page 65
Chapter 3: working with target servers 57 please note that mouse configurations will vary on different target operating systems. Consult your os guidelines for further details. Also note that intelligent mouse synchronization does not work with unix targets. Absolute mouse mode in this mode, absolut...
Page 66
Chapter 3: working with target servers 58 swedish (sweden) german (switzerland) hungarian (hungary) spanish (spain) italian (italy) slovenian translation: french - us translation: french - us international in akc, the keyboard type defaults to the local client, so this option does no...
Page 67
Chapter 3: working with target servers 59 keyboard limitations turkish keyboards if using a turkish keyboard, you must connect to a target server through the active kvm client (akc). It is not supported by other raritan clients. Slovenian keyboards the limitation. Language configuration on linux bec...
Page 68
Chapter 3: working with target servers 60 client launch settings configuring client launch settings allows you to define the screen settings for a kvm session. Note: lx devices support this feature in mpc. Lx does not support client launch setting in vkc and akc. To configure client launch settings:...
Page 69
Chapter 3: working with target servers 61 configure scan settings in vkc and akc the kx ii and lx provide the port scanning feature to search for selected targets, and display them in a slide show view, allowing you to monitor up to 32 targets at one time. You can connect to targets or focus on a sp...
Page 70
Chapter 3: working with target servers 62 view status bar by default, the status bar is displayed at the bottom of the target window. To hide the status bar: click view > status bar to deselect it. To restore the status bar: click view > status bar to select it. Scaling scaling your target window al...
Page 71
Chapter 3: working with target servers 63 full screen mode when you enter full screen mode, the target's full screen is displayed and acquires the same resolution as the target server. The hot key used for exiting this mode is specified in the options dialog, see tool options (on page 57). While in ...
Page 72: Chapter 4 Virtual Media
64 in this chapter overview .................................................................................................. 64 prerequisites for using virtual media ...................................................... 65 mounting local drives .......................................................
Page 73
Chapter 4: virtual media 65 prerequisites for using virtual media kx ii-101-v2 virtual media prerequisites for users requiring access to virtual media, the kx ii-101-v2 permissions must be set to allow access to the relevant ports, as well as virtual media access (vm access port permission) for thos...
Page 74
Chapter 4: virtual media 66 notes on mounting local drives kvm target servers running the windows xp ® operating system may not accept new mass storage connections after an ntfs-formatted partition (for example, the local c drive) has been redirected to them. If this occurs, close the remote console...
Page 75
Chapter 4: virtual media 67 number of supported virtual media drives with the virtual media feature, you can mount up to two drives (of different types) that are supported by the usb profile currently applied to the target. These drives are accessible for the duration of the kvm session. For example...
Page 76
Chapter 4: virtual media 68 when checked, you will be able to read or write to the connected usb disk. Warning: enabling read/write access can be dangerous! Simultaneous access to the same drive from more than one entity can result in data corruption. If you do not require write access, leave this o...
Page 77
Chapter 4: virtual media 69 c. File server username - user name required for access to the file server. The name can include the domain name such as mydomain/username. D. File server password - password required for access to the file server (field is masked as you type). E. Click connect. The media...
Page 78
Chapter 4: virtual media 70 virtual media in a linux environment active system partitions you cannot mount active system partitions from a linux client. Linux ext3/4 drive partitions need to be unmounted via umount /dev/ prior to a making a virtual media connection. Drive partitions the following dr...
Page 79
Chapter 4: virtual media 71 virtual media file server setup (file server iso images only) this feature is only required when using virtual media to access file server iso images. Iso9660 format is the standard supported by raritan. However, other cd-rom extensions may also work. Note: smb/cifs suppo...
Page 80
Chapter 4: virtual media 72 disconnecting virtual media to disconnect the virtual media drives: for local drives, choose virtual media > disconnect drive. For cd-rom, dvd-rom, and iso images, choose virtual media > disconnect cd-rom/iso image. Note: in addition to disconnecting the virtual media usi...
Page 81
73 in this chapter user groups ............................................................................................ 73 users ....................................................................................................... 79 authentication settings .......................................
Page 82
Chapter 5: user management 74 user group list user groups are used with local and remote authentication (via radius or ldap/ldaps). It is a good idea to define user groups before creating individual users since, when you add a user, you must assign that user to an existing user group. The user group...
Page 83
Chapter 5: user management 75 2. Type a descriptive name for the new user group into the group name field (up to 64 characters). 3. Select the checkboxes next to the permissions you want to assign to all of the users belonging to this group. See setting permissions (on page 77). Setting port permiss...
Page 84
Chapter 5: user management 76 control. It is possible to be locked out of your kx ii-101-v2 if your ip address is within a range that has been denied access. This feature limits access to the kx ii-101-v2 device by users in the selected group to specific ip addresses. This feature applies only to us...
Page 85
Chapter 5: user management 77 to replace a rule: 1. Specify the rule number you want to replace. 2. Type the starting ip and ending ip fields. 3. Choose the action from the drop-down list. 4. Click replace. Your new rule replaces the original rule with the same rule number. To delete a rule: 1. Spec...
Page 86
Chapter 5: user management 78 permission description note: the admin user group has this permission by default. Device settings network settings, date/time settings, port configuration (channel names, power associations), event management (snmp, syslog), virtual media file server setup diagnostics n...
Page 87
Chapter 5: user management 79 2. Set the permissions for the group. Select the checkboxes before the permissions you want to assign to all of the users belonging to this group. See setting permissions (on page 77). 3. Set the port permissions. Specify the server ports that can be accessed by users b...
Page 88
Chapter 5: user management 80 view users by port the user by ports page lists all authenticated local and remote users and ports they are being connected to. Only permanent connections to ports are listed. If the same user is logged on from more than one client, their username appears on the page fo...
Page 89
Chapter 5: user management 81 logging users off the kx ii-101-v2 (force logoff) if you are an administrator, you are able to log off any authenticated user who is logged on to the kx ii-101-v2. Users can also be disconnected at the port level. See disconnecting users from ports (on page 80). To log ...
Page 90
Chapter 5: user management 82 modifying an existing user to modify an existing user: 1. Open the user list page by choosing user management > user list. 2. Locate the user from among those listed on the user list page. 3. Click the user name. The user page opens. 4. On the user page, change the appr...
Page 91
Chapter 5: user management 83 authentication settings authentication is the process of verifying that a user is who he says he is. Once a user is authenticated, the user's group is used to determine his system and port permissions. The user's assigned privileges determine what type of access is allo...
Page 92
Chapter 5: user management 84 implementing ldap/ldaps remote authentication lightweight directory access protocol (ldap/ldaps) is a networking protocol for querying and modifying directory services running over tcp/ip. A client starts an ldap session by connecting to an ldap/ldaps server (the defaul...
Page 93
Chapter 5: user management 85 9. In the user search dn field, enter the distinguished name of where in the ldap database you want to begin searching for user information. Up to 64 characters can be used. An example base search value might be: cn=users,dc=raritan,dc=com. Consult your authentication s...
Page 94
Chapter 5: user management 86 11. If you entered a distinguished name for the administrative user, you must enter the password that will be used to authenticate the administrative user's dn against the remote authentication server. Enter the password in the secret phrase field and again in the confi...
Page 95
Chapter 5: user management 87 14. The default secure ldap port is 636. Either use the default port or specify another port. This field is only used when the enable secure ldap checkbox is selected. 15. Select the enable ldaps server certificate validation checkbox to use the previously uploaded root...
Page 96
Chapter 5: user management 88 17. The kx ii-101-v2 provides you with the ability to test the ldap configuration from the authentication settings page due to the complexity sometimes encountered with successfully configuring the ldap server and kx ii-101-v2 for remote authentication. To test the ldap...
Page 97
Chapter 5: user management 89 2. On your active directory server, create new groups with the same group names as in the previous step. 3. On your ad server, assign the kx ii-101-v2 users to the groups created in step 2. 4. From the kx ii-101-v2, enable and configure your ad server properly. See impl...
Page 98
Chapter 5: user management 90 the timeout is the length of time the kx ii-101-v2 waits for a response from the radius server before sending another authentication request. 9. The default number of retries is 3 retries. This is the number of times the kx ii-101-v2 will send an authentication request ...
Page 99
Chapter 5: user management 91 chap - with chap, authentication can be requested by the server at any time. Chap provides more security than pap. Returning user group information via radius when a radius authentication attempt succeeds, the kx ii-101-v2 determines the permissions for a given user b...
Page 100
Chapter 5: user management 92 radius communication exchange specifications the kx ii-101-v2 sends the following radius attributes to your radius server: attribute data log in access-request (1) nas-port-type (61) virtual (5) for network connections. Nas-ip-address (4) the ip address for the kx ii-10...
Page 101
Chapter 5: user management 93 user authentication process when the device is configured to authenticate and authorize local users, the order in which the user credentials are validated follows the following process:.
Page 102
Chapter 5: user management 94 remote authentication follows the process specified in the flowchart below:.
Page 103
Chapter 5: user management 95 changing a password to change your kx ii-101-v2 password: 1. Choose user management > change password. The change password page opens. 2. Type your current password in the old password field. 3. Type a new password in the new password field. Retype the new password in t...
Page 104
96 in this chapter network settings ..................................................................................... 96 device services ..................................................................................... 100 keyboard/mouse setup ...................................................
Page 105
Chapter 6: device management 97 network basic settings these procedures describe how to assign an ip address on the network settings page. For complete information about all of the fields and the operation of this page, see network settings (on page 96). Assign the kx ii-101-v2 an ip address to assi...
Page 106
Chapter 6: device management 98 with this option, network parameters are assigned by the dhcp server. If dhcp is used, enter the preferred host name (dhcp only). Up to 63 characters. 2. Next, configure ipv6 and/or dns settings. Configure the ipv6 settings 1. If using ipv6, enter or select the approp...
Page 107
Chapter 6: device management 99 configure the dns settings 1. Select obtain dns server address automatically if dhcp is selected and obtain dns server address is enabled. When obtain dns server address automatically, the dns information provided by the dhcp server will be used. 2. If use the followi...
Page 108
Chapter 6: device management 100 256 kilobit 512 kilobit 2 megabit 5 megabit 10 megabit 100 megabit need new screenshot device services the device services page allows you to configure the following functions: enable ssh access enter the discovery port enable direct port access enable te...
Page 109
Chapter 6: device management 101 2. Select enable ssh access. 3. Enter the ssh port information. The standard ssh tcp port number is 22 but the port number can be changed to provide a higher level of security operations. 4. Click ok. Http and https port settings you are able to configure http and/or...
Page 110
Chapter 6: device management 102 enabling direct port access via url direct port access allows users to bypass having to use the device's login dialog and port access page. This feature also provides the ability to enter a username and password directly to proceed to the target, if the username and ...
Page 111
Chapter 6: device management 103 3. Select either or both enable snmp v1/v2c and enable snmp v3. At least one option must be selected. Required 4. Complete the following fields for snmp v1/v2c (if needed): a. Community - the device's community string b. Community type - grant either read-only or rea...
Page 112
Chapter 6: device management 104 configure snmp traps on the event management - settings page, which can be quickly accessed by clicking the snmp trap configuration link. See configuring snmp traps for information on creating snmp traps and list of kx ii-101-v2 snmp traps for a list of available kx ...
Page 113
Chapter 6: device management 105 keyboard/mouse setup use the keyboard/mouse setup page to configure the keyboard and mouse interface between the kx ii-101-v2 and the host device. 1. Click device settings > keyboard/mouse. 2. Select the host interface. This selection determines if the kx ii-101- v2 ...
Page 114
Chapter 6: device management 106 admin port to configure the admin serial port: 1. Choose device settings > serial port. The serial port settings page appears. 2. Select the admin port radio button. 3. Choose one of these options to connect to the kx ii-101-v2 directly from a client pc and access th...
Page 115
Chapter 6: device management 107 modem server ip address - the address the user types to access the kx ii-101-v2 web interface once connected via modem. modem client ip address - the address assigned to the user once connected via modem. 4. Click ok. See modem access cable connections (on page 1...
Page 116
Chapter 6: device management 108 synchronize with ntp server - use this option to synchronize the date and time with the network time protocol (ntp) server. 5. For the synchronize with ntp server option: a. Enter the ip address of the primary time server. B. Enter the ip address of the secondary t...
Page 117
Chapter 6: device management 109 configuring snmp traps simple network management protocol (snmp) is a protocol governing network management and the monitoring of network devices and their functions. Snmp traps are sent out over a network to gather information. The traps are configured on the event ...
Page 118
Chapter 6: device management 110 note: ipv6 addresses cannot exceed 80 characters in length for the host name. B. Port number - the port number used by the snmp manager c. Security name - the username or service account name of the entity communicating with the snmp agent (up to 32 characters) d. Au...
Page 119
Chapter 6: device management 111 note: if you disable snmp settings at any time, the snmp information is retained so you do not have to reenter if you re-enable the settings. To delete snmp traps: clear all of the snmp trap fields and save. Use the reset to factory defaults feature to remove the snm...
Page 120
Chapter 6: device management 112 trap name description deviceupgradestarted the kx ii-101-v2 has begun update via an rfp file. Factoryreset the device has been reset to factory defaults. Firmwarefilediscarded firmware file was discarded. Firmwareupdatefailed firmware update failed. Firmwarevalidatio...
Page 121
Chapter 6: device management 113 trap name description securitybannerchanged a change has been made to the security banner. Securityviolation security violation. Setdatetime the date and time for the device has been set. Setfipsmode fips mode has been enabled. Startccmanagement the device has been p...
Page 122
Chapter 6: device management 114 viewing the kx ii-101-v2 mib to view the kx ii-101-v2 mib: 1. Choose device settings > event management - settings. The event management - settings page opens. 2. Click the 'click here to view the dominion snmp mib' link. The mib file opens in a browser window. Note:...
Page 123
Chapter 6: device management 115 configuring event management - destinations system events, if enabled, generate snmp notification events (traps), or can be logged to the syslog or audit log. Use the event management - destinations page to select the system events to track and where to send this inf...
Page 124
Chapter 6: device management 116 sorting this page is initially displayed in port number order, but can be sorted on any of the fields by clicking on the column heading. Port name - the name assigned to the port. A port name displayed in black indicates that you cannot change the name and that the p...
Page 125
Chapter 6: device management 117 managing kvm target servers (port page) this port page opens when you select a port from the port configuration page that is connected to a target server. From this page, you can make power associations and change the port name to something more descriptive. A server...
Page 126
Chapter 6: device management 118 valid special characters character description character description ! Exclamation point ; semi-colon " double quote = equal sign # pound sign > greater than sign $ dollar sign ? Question mark % percent sign @ at sign & ampersand [ left bracket ( left parenthesis \ b...
Page 127
Chapter 6: device management 119 connecting the power strip diagram key kx ii-101-v2 raritan power strip. Dkx2-101-v2-pdu (db9-rj45 adapter) connector (not included) from the kx ii-101-v2 to a raritan the power strip. To connect the kx ii-101-v2 to a raritan power strip: 1. Connect the dkx2-101-v2-p...
Page 128
Chapter 6: device management 120 5. Power on the raritan power strip. 6. Click to device settings > serial port to open the serial port page. 7. Select the power strip control radio button and click ok. Once this is done, the power menu is available on the remote console. Naming the power strip (por...
Page 129
Chapter 6: device management 121 to cancel without saving changes: click cancel. Managing power associations to make power associations (associate power strip outlets with the kvm target server): note: when a power strip is associated with the target server (port), the outlet name is replaced by the...
Page 130
Chapter 6: device management 122 2. For that power strip, select the appropriate outlet from the outlet name drop-down list. 3. From the outlet name drop-down list, select none. 4. Click ok. That power strip/outlet association is removed. A confirmation message appears. To show the power port config...
Page 131
Chapter 6: device management 123 analog kvm switch you can configure a raritan analog kvm switch to work with the kx ii- 101-v2. The kx ii-101-v2's compatibility has been verified with the following raritan kvm switches: switchman sw2, sw4 and sw8 master console mx416 and mxu similar products from r...
Page 132
Chapter 6: device management 124 8. Click ok to configure the analog kvm switch. To restore analog kvm switch defaults: click reset to defaults. Resetting the kx ii-101-v2 using the reset button on the top of the device, there is a reset button. It is recessed to prevent accidental resets (you will ...
Page 133
Chapter 6: device management 125 note: if the kx ii-101-v2 is set to restore to the factory defaults upon reset, the ip address, user name, and other options will be set accordingly. Changing the default gui language setting the kx ii-101-v2 gui defaults to english, but also supports the following l...
Page 134
126 in this chapter overview ................................................................................................ 127 usb connection settings ...................................................................... 127 advanced usb connection settings .........................................
Page 135
Chapter 7: managing usb connections 127 overview to broaden the kx ii-101-v2's compatibility with different kvm target servers, raritan provides a user defined real-time selection of usb configuration profile options for a wide range of operating system and bios-level server implementations. The def...
Page 136
Chapter 7: managing usb connections 128 2. Click usb connection settings to expand the usb connection settings section. 3. Select the usb connection settings you will be using: enable absolute mouse - applies only if usb is active keyboard/mouse interface use full speed - useful for bios that ca...
Page 137
Chapter 7: managing usb connections 129 3. Click the user defined kx ii-101 usb profile configuration table link to access the recommended configurations to apply to the advanced usb connection settings section. 4. Configure the following as needed: a. Virtual media interface #1 type b. Check the re...
Page 138
130 in this chapter security settings .................................................................................... 130 configuring ip access control .............................................................. 139 ssl certificates ..............................................................
Page 139
Chapter 8: security management 131 limitation description this field is enabled and required when the enable password aging checkbox is selected. Enter the number of days after which a password change is required. The default is 60 days. Log out idle users, after (1-365 minutes) select the "log off ...
Page 140
Chapter 8: security management 132 strong passwords strong passwords provide more secure local authentication for the system. Using strong passwords, you can specify the format of valid kx ii-101-v2 local passwords such as minimum and maximum length, required characters, and password history retenti...
Page 141
Chapter 8: security management 133 user blocking the user blocking options specify the criteria by which users are blocked from accessing the system after the specified number of unsuccessful login attempts. The three options are mutually exclusive: option description disabled the default option. Us...
Page 142
Chapter 8: security management 134 option description timer lockout users are denied access to the system for the specified amount of time after exceeding the specified number of unsuccessful login attempts. When selected, the following fields are enabled: attempts - the number of unsuccessful log...
Page 143
Chapter 8: security management 135 encryption & share using the encryption & share settings you can specify the type of encryption used, pc and vm share modes, and the type of reset performed when the kx ii-101-v2 reset button is pressed. Warning: if you select an encryption mode that is not support...
Page 144
Chapter 8: security management 136 encryption mode description browser supports it, otherwise you will not be able to connect. See checking your browser for aes encryption (on page 137) for more information. Aes-256 the advanced encryption standard (aes) is a national institute of standards and tech...
Page 145
Chapter 8: security management 137 6. If needed, select local device reset mode. This option specifies which actions are taken when the hardware reset button (at the back of the device) is depressed. For more information, see resetting the kx ii-101-v2 using the reset button (on page 124). Choose on...
Page 146
Chapter 8: security management 138 enabling fips 140-2 for government and other high security environments, enabling fips 140-2 mode may be required. The kx ii-101-v2 uses an embedded fips 140-2-validated cryptographic module running on a linux ® platform per fips 140-2 implementation guidance secti...
Page 147
Chapter 8: security management 139 fips 140-2 support requirements the kx ii-101-v2 supports the use of fips 140-2 approved encryption algorithms. This allows an ssl server and client to successfully negotiate the cipher suite used for the encrypted session when a client is configured for fips 140-2...
Page 148
Chapter 8: security management 140 to use ip access control: 1. Open the ip access control page by selecting security > ip access control. The ip access control page opens. 2. Select the enable ip access control checkbox to enable ip access control and the remaining fields on the page. 3. Choose the...
Page 149
Chapter 8: security management 141 3. Choose the policy from the drop-down list. 4. Click replace. Your new rule replaces the original rule with the same rule number. To delete a rule: 1. Specify the rule number you want to delete. 2. Click delete. 3. You are prompted to confirm the deletion. Click ...
Page 150
Chapter 8: security management 142 ssl certificates the kx ii-101-v2 uses the secure socket layer (ssl) protocol for any encrypted network traffic between itself and a connected client. When establishing a connection, the kx ii-101-v2 has to identify itself to a client using a cryptographic certific...
Page 151
Chapter 8: security management 143 f. Country (iso code) - the country where the organization is located. This is the two-letter iso code, e.G. De for germany, or us for the u.S. G. Challenge password - some certification authorities require a challenge password to authorize later changes on the cer...
Page 152
Chapter 8: security management 144 b. A message containing all of the information you entered appears. C. The csr and the file containing the private key used when generating it can be downloaded by clicking download csr. D. Send the saved csr to a ca for certification. You will get the new certific...
Page 153
Chapter 8: security management 145 security banner kx ii-101-v2 provides you with the ability to add a security banner to the kx ii-101-v2 login process. This feature requires users to either accept or decline a security agreement before they can access the kx ii-101- v2. The information provided in...
Page 154: Chapter 9 Maintenance
146 in this chapter audit log................................................................................................ 146 device information ................................................................................. 147 backup and restore .................................................
Page 155
Chapter 9: maintenance 147 device information the device information page provides detailed information about your kx ii-101-v2 device. This information is helpful should you need to contact raritan technical support. To view information about your kx ii-101-v2: choose maintenance > device informati...
Page 156
Chapter 9: maintenance 148 backup and restore from the backup/restore page, you can backup and restore the settings and configuration for your kx ii-101-v2. In addition to using backup and restore for business continuity purposes, you can use this feature as a time-saving mechanism. For instance, yo...
Page 157
Chapter 9: maintenance 149 in ie 7 (and later), ie is used as the default application to open files, so you are prompted to open the file versus save the file. To avoid this, you must change the default application that is used to open files to wordpad ® . 2. To do this: a. Save the backup file. The...
Page 158
Chapter 9: maintenance 150 upgrading firmware use the firmware upgrade page to upgrade the firmware for your kx ii- 101-v2. Important: do not turn off your kx ii-101-v2 device while the upgrade is in progress - doing so will likely result in damage to the device. To upgrade your kx ii-101-v2 device:...
Page 159
Chapter 9: maintenance 151 5. Click upgrade. Wait for the upgrade to complete. Status information and progress bars are displayed during the upgrade. Upon completion of the upgrade, the device reboots. 6. As prompted, close the browser and wait approximately 5 minutes before logging into the kx ii-1...
Page 160
Chapter 9: maintenance 152 full factory reset - removes the entire configuration and resets the device completely to the factory defaults. Note that any management associations with commandcenter will be broken. Because of the complete nature of this reset, you will be prompted to confirm the fact...
Page 161
Chapter 9: maintenance 153 2. Click reboot. You are prompted to confirm the action. Click yes to proceed with the reboot. Stopping cc-sg management while the kx ii-101-v2 is under cc-sg management, if you try to access the device directly, you are notified that it the device is under cc- sg manageme...
Page 162
Chapter 9: maintenance 154 2. Click yes to begin the processing of removing the device from cc- sg management. A confirmation message will then displayed asking you to confirm that you want the remove the device from cc-sg management. 3. Click yes to remove the device cc-sg management. Once cc-sg ma...
Page 163: Chapter 10 Diagnostics
155 the diagnostics pages are used for troubleshooting and are intended primarily for the administrator of the kx ii-101-v2 device. All of the diagnostics pages (except device diagnostics) run standard networking commands and the information that is displayed is the output of those commands. The dia...
Page 164
Chapter 10: diagnostics 156 statistics - produces a page similar to the one displayed here. interfaces - produces a page similar to the one displayed here..
Page 165
Chapter 10: diagnostics 157 route - produces a page similar to the one displayed here. 3. Click refresh. The relevant information is displayed in the result field..
Page 166
Chapter 10: diagnostics 158 ping host page ping is a network tool used to test whether a particular host or ip address is reachable across an ip network. Using the ping host page, you can determine if a target server or another kx ii-101-v2 is accessible. To ping the host: 1. Choose diagnostics > pi...
Page 167
Chapter 10: diagnostics 159 3. Choose the maximum hops from the drop-down list (5 to 50 in increments of 5). 4. Click trace route. The trace route command is executed for the given hostname or ip address and the maximum hops. The output of trace route is displayed in the result field..
Page 168
Chapter 10: diagnostics 160 device diagnostics note: this page is for use by raritan field engineers or when you are directed by raritan technical support. The device diagnostics page downloads diagnostics information from the kx ii-101-v2 to the client machine. A device diagnostics log can be gener...
Page 169
Chapter 10: diagnostics 161 a. Click save to file. The file download dialog appears. B. Click save. The save as dialog appears. C. Navigate to the desired directory and click save. 4. Email this file as directed by raritan technical support..
Page 170
162 in this chapter overview ................................................................................................ 162 accessing the kx ii-101-v2 using the cli ............................................ 163 ssh connection to the kx ii-101-v2 ................................................
Page 171
Chapter 11: command line interface (cli) 163 accessing the kx ii-101-v2 using the cli access the kx ii-101-v2 using one of the following methods: telnet via ip connection ssh (secure shell) via ip connection multi-function admin serial port via rs-232 serial interface with provided cable and a termi...
Page 172
Chapter 11: command line interface (cli) 164 ssh access from a unix/linux workstation to open an ssh session from a unix ® /linux ® workstation and log in as the user admin, enter the following command: ssh -l admin 192.168.30.222 the password prompt appears. Logging in to log in: 1. Login: admin 2....
Page 173
Chapter 11: command line interface (cli) 165 completion of commands the cli supports the completion of partially-entered commands. After entering the first few characters of an entry, press the tab key. If the characters form a unique match, the cli will complete the entry. If no match is found, the...
Page 174
Chapter 11: command line interface (cli) 166 command description help display an overview of the cli syntax. Quit places the user back one level. Logout logs out the user session. Cli commands the table below lists and describes all available cli commands. Command description config switch to the co...
Page 175
Chapter 11: command line interface (cli) 167 diagnostics the diagnostics menu enables you to set the logging options for different modules of the kx ii-101-v2. You should set logging options only when instructed by a raritan technical support engineer. These logging options enable a support engineer...
Page 177
Chapter 11: command line interface (cli) 169 command option description ipauto static or dynamic ip address ip ipaddress ip address of the kx ii-101-v2 assigned for access from the ip network mask subnetmask subnet mask obtained from the ip administrator gw ipaddress gateway ip address obtained from...
Page 178
Chapter 11: command line interface (cli) 170 listports command the listports command lists the number of active users, user names, port, and status. Listports command example admin port > listports port port port port port no. Name type status availability 1 - dominion_kxii-101_v2_port kvm up idle u...
Page 179
171 in this chapter overview ................................................................................................ 171 removing a kx ii-101-v2 from cc-sg management ........................... 172 using cc-sg in proxy mode ................................................................. ...
Page 180
Chapter 12: cc-sg management 172 removing a kx ii-101-v2 from cc-sg management unless the kx ii-101-v2 is released from cc-sg control, you cannot access the device directly. However, if the kx ii-101-v2 does not receive heartbeat messages from commandcenter (for example, commandcenter is not on the ...
Page 181
Chapter 12: cc-sg management 173 2. Click yes. A message appears, confirming that the device is no longer under cc management. 3. Click ok. The kx ii-101-v2 login page opens. Using cc-sg in proxy mode virtual kvm client version not known from cc-sg proxy mode when the virtual kvm client is launched ...
Page 182
174 in this chapter physical specifications .......................................................................... 174 supported operating systems (clients) ................................................ 175 supported browsers ......................................................................
Page 183
Appendix a: specifications 175 kx ii-101-v2... Description remote connection: network protocols 1 ethernet (rj45) port with activity status indicator tcp/ip, telnet, ssh, http, https, secure ldap, radius, ldap, snmp v2 and v3, dhcp and sntp, dual- stack: ipv4 and ipv6 warranty two years with advance...
Page 184
Appendix a: specifications 176 linux ® the jre ™ plug-in is available for the windows ® 32-bit and 64-bit operating systems. Mpc and vkc can be launched only from a 32-bit browser, or 64-bit browser. Following are the java ™ 32-bit and 64-bit windows operating system requirements. Mode operating sys...
Page 185
Appendix a: specifications 177 supported browsers kx ii-101-v2 supports the following browsers: internet explorer ® 7 through 11 firefox ® 4 (or later) safari ® 3 (or later) mac ® os x mountain lion ® 10.7.5 using safari 6.0.5 running jre ™ 1.7.0_51 mac os x mountain lion 10.8.5 * using safari 6...
Page 186
Appendix a: specifications 178 supported video resolutions ensure each target server's video resolution and refresh rate are supported by the kx ii-101-v2, and that the signal is noninterlaced. Video resolution and cable length are important factors in the ability to obtain mouse synchronization. Th...
Page 187
Appendix a: specifications 179 resolutions 1024x768@72 1920x1080@60hz note: composite sync and sync-on-green video require an additional adapter. Note: some resolutions may not be available by default. If you do not see a resolution, plug in the monitor first, remove the monitor and then plug in the...
Page 188
Appendix a: specifications 180 language regions keyboard layout swedish sweden swedish hungarian hungary hungarian slovenian slovenia slovenian italian italy italian spanish spain and most spanish speaking countries spanish portuguese portugal portuguese tcp and udp ports used port description http,...
Page 189
Appendix a: specifications 181 port description configurable ports 389 or 636 via the ldap/ldaps protocol, ports 389 or 636 will be used, but the system can also be configured to use any port of your designation. Optional radius on configurable port 1812 if the kx ii-101-v2 is configured to remotely...
Page 190
Appendix a: specifications 182 kx ii-101-v2 network speed setting 10/full kx ii-101- v2: 10/half switch: 10/full no communica tion no communicat ion 10/full kx ii-101- v2: 10/half switch: 10/full 10/half 10/half no communica tion no communicat ion kx ii-101- v2: 10/full switch: 10/half 10/half legen...
Page 191
Appendix a: specifications 183 pin definition 5 gnd 6 dtr (out) 7 cts (in) 8 rts (out) 9 ri (in).
Page 192
184 note: the procedures in this chapter should be attempted only by experienced users. In this chapter returning user group information ........................................................ 184 setting the registry to permit write operations to the schema ........... 185 creating a new attribute...
Page 193
Appendix b: updating the ldap schema 185 setting the registry to permit write operations to the schema to allow a domain controller to write to the schema, you must set a registry entry that permits schema updates. To permit write operations to the schema: 1. Right-click the active directory ® schem...
Page 194
Appendix b: updating the ldap schema 186 3. Click new and then choose attribute. When the warning message appears, click continue and the create new attribute dialog appears. 4. Type rciusergroup in the common name field. 5. Type rciusergroup in the ldap display name field. 6. Type 1.3.6.1.4.1.13742...
Page 195
Appendix b: updating the ldap schema 187 2. Scroll to the user class in the right pane and right-click it. 3. Choose properties from the menu. The user properties dialog appears. 4. Click the attributes tab to open it. 5. Click add..
Page 196
Appendix b: updating the ldap schema 188 6. Choose rciusergroup from the select schema object list. 7. Click ok in the select schema object dialog. 8. Click ok in the user properties dialog. Updating the schema cache to update the schema cache: 1. Right-click active directory ® schema in the left pa...
Page 197
Appendix b: updating the ldap schema 189 3. Go to the directory where the support tools were installed. Run adsiedit.Msc. The adsi edit window opens. 4. Open the domain. 5. In the left pane of the window, select the cn=users folder..
Page 198
Appendix b: updating the ldap schema 190 6. Locate the user name whose properties you want to adjust in the right pane. Right-click the user name and select properties. 7. Click the attribute editor tab if it is not already open. Choose rciusergroup from the attributes list. 8. Click edit. The strin...
Page 199: Appendix C Rack Mount
191 the kx ii-101-v2 device can be mounted vertically or horizontally, facing the front or the rear, on either side of a server rack. Use the brackets and screws included with the kx ii-101-v2 kit. In this chapter attach the l bracket to the kx ii-101-v2 for a horizontal mount .......... 191 attach ...
Page 200
Appendix c: rack mount 192 diagram key screws.
Page 201
193 in this chapter java runtime environment (jre) ......................................................... 193 ipv6 support notes ............................................................................... 194 keyboard, video and mouse notes .......................................................
Page 202
Appendix d: informational notes 194 ipv6 support notes operating system ipv6 support notes java java ™ 1.6 (and later) supports ipv6 for the following: solaris ™ 10 (and later) linux ® kernel 2.1.2 (and later)/redhat 6.1 (and later) the following ipv6 configurations are not supported by java: j2se d...
Page 203
Appendix d: informational notes 195 bios access limitation from a local keyboard a usb connection is required when using absolute mouse synchronization. However, the keyboards in this section do not support a usb connection to the local keyboard. To access the local keyboard via bios or virtual medi...
Page 204
Appendix d: informational notes 196 compaq alpha and ibm p server mouse mode limitation when connecting to either compaq ® alpha servers or ibm ® p servers through the kx ii-101-v2, you must use single mouse mode. See working with target servers (on page 29). Windows 2000 and windows 2003 server key...
Page 205: Appendix E Faqs
197 in this chapter general faqs ........................................................................................ 197 ipv6 networking .................................................................................... 198 general faqs question answer what is the difference between the domin...
Page 206
Appendix e: faqs 198 question answer what new features are available in the latest release? With release 3.5 (and above), the following features are now available: 1920x1080 video resolution ipad/iphone access (requires cc-sg) dual stack ipv6 fips 140-2 encryption module logoff user and disconnect p...
Page 207
Appendix e: faqs 199 question answer why does kx ii-101-v2 support ipv6 networking? U.S. Government agencies and the department of defense are now mandated to purchase ipv6-compatible products. In addition, many enterprises and foreign countries, such as china, will be transitioning to ipv6 over the...
Page 209: Index
201 9 9 pin pinout • 182 a absolute mouse mod e • 57 access a virtual media drive on a client computer • 67 access and display favorites • 36 accessing the kx ii-101- v2 using the cli • 163 active system partition • 70 active system partitions • 70 adding a new user • 81, 82 adding a new user group ...
Page 210
Index 202 device management • 96 device services • 100, 163 diagnostics • 155, 166, 167 disconnect from virtu al media drives • 69 disconnecting kvm target servers • 42 disconnecting users from ports • 80, 81 disconnecting virtual media • 72 discovering devices on the kx ii-101-v2 subnet • 37 discov...
Page 211
Index 203 managing favorites • 32, 34 managing kvm target servers (port page) • 117, 118 managing power associations • 121 managing usb co nnections • 126 modem • 106 modem access cable connections • 107 modifying an existing user • 82 modifying an existing user group • 78 modifying and removing key...
Page 212
Index 204 step 1 configure the target server • 9 step 2 configure network firewall settings • 12 step 3 connect the equipment • 13 step 4 configure the kx ii-101- v2 • 17 stopping cc- sg management • 153 strong passwords • 95, 130, 132 sun blade video, keyboard, and mouse support limitation • 194 su...
Page 213
U.S./canada/latin america monday - friday 8 a.M. - 6 p.M. Et phone: 800-724-8090 or 732-764-8886 for commandcenter noc: press 6, then press 1 for commandcenter secure gateway: press 6, then press 2 fax: 732-764-8887 email for commandcenter noc: tech-ccnoc@raritan.Com email for all other products: te...