- DL manuals
- Raritan
- Server
- Dominion SX II
- Administrator's Manual
Raritan Dominion SX II Administrator's Manual
Summary of Dominion SX II
Page 1
Copyright © 2015 raritan, inc. Dsx2-v2.0.0.-0a-e august 2015 255-60-0005-00 dominion sx ii administrators guide 2.0.0
Page 2
This document contains proprietary information that is protected by copyright. All rights reserved. No part of this document may be photocopied, reproduced, or translated into another language without express prior written consent of raritan, inc. © copyright 2015 raritan, inc. All third-party softw...
Page 3
Iii contents cs03 certification - dsx2-16 and dsx2-48 vii chapter 1 features and benefits 1 package contents .......................................................................................................................... 8 sx ii models ........................................................
Page 4
Contents iv chapter 4 access targets 35 port action menu options - connect, disconnect, power on, power off and power cycle targets ......................................................................................................................................... 35 connect to a target ..........
Page 5
Contents v configure snmp traps from the remote console ......................................................... 126 configure event management - destinations .................................................................. 130 enable smtp notifications from the remote console ......................
Page 6
Contents vi chapter 7 connect a rack pdu to sx ii and configure power control options 234 connecting the sx ii to the px2 serial port .............................................................................. 234 connecting the sx ii to the px2 feature port .........................................
Page 7: Dsx2-48
Vii to avoid potentially fatal shock hazard and possible damage to raritan equipment: • do not use a 2-wire power cord in any product configuration. • test ac outlets at your computer and monitor for proper polarity and grounding. • use only with grounded outlets at both the computer and monitor. • ...
Page 8
1 next-generation console server raritan's next-generation serial console server the dominion sx ii is raritan's next-generation serial console server (also known as terminal server) that provides it and network administrators secure ip access and control of serial devices, anytime, anywhere. The ne...
Page 9
Chapter 1: features and benefits 2 powerful hardware platform powerful new hardware platform powerful new hardware platform with 1ghz cpu engine, with an 8-fold increase in ram. Increased flash memory, up to 8 gb, for storage and logging. Front panel led's show port connection status. Wide variety o...
Page 10
Chapter 1: features and benefits 3 productive serial-over-ip access widest variety of serial-over-ip access the dominion sx ii supports the widest variety of serial-over-ip connections via ssh/telnet clients, web-browser, commandcenter, telephony modem, cellular modem and at-the- rack access. This i...
Page 11
Chapter 1: features and benefits 4 productive serial-over-ip access automatic serial device logoff once a user is timed out for inactivity, a user defined "logoff" command can be sent to the target. Improved security of user sessions results as serial sessions are automatically closed upon time out ...
Page 12
Chapter 1: features and benefits 5 strong 256 bit aes encryption the sx ii utilizes the advanced encryption standard (aes) encryption for added security. 128- and 256-bit aes encryption is available. Aes is a u.S. Government-approved cryptographic algorithm that is recommended by the national instit...
Page 13
Chapter 1: features and benefits 6 security - networking dual stack ip networking – ipv4 and ipv6 the dominion sx ii provides dual-stack ip networking with simultaneous support of ipv4 and ipv6. Iptables firewall support fully configurable "iptables" firewall support. User selectable and customizabl...
Page 14
Chapter 1: features and benefits 7 easy to install and manage full cli-based configuration and management the sx ii offers complete cli administration and management via ssh, telnet and web-based user interface. Two script-based automatic configuration methods are available for a fast installation a...
Page 15
Chapter 1: features and benefits 8 raritan commandcenter® management and scalability raritan’s commandcenter centralized management like the rest of the dominion series, dominion sx ii features complete commandcenter secure gateway integration, allowing users to consolidate all dominion sx ii and ot...
Page 16
Chapter 1: features and benefits 9 sx ii models the following sx ii models are available. Models with an m include an internal modem in addition to the standard features that are provided on all sx ii models. For a list of standard features, see introduction (see " features and benefits " on page 1)...
Page 17
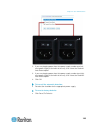
Chapter 1: features and benefits 10 appliance diagram key j usb port k led port indicators l power status (note sx ii 48 port models have their power status located above the front-panel usb port.) supported serial devices • routers • lan switches • rack pdus • wireless modems • telecom modems • win...
Page 18
Chapter 1: features and benefits 11 sx ii access clients raritan serial console (rsc) (rsc) access rsc by connecting from the remote console or use standalone rsc to access targets directly. See raritan serial console (rsc) help (on page 47) direct port access direct port access allows users to bypa...
Page 19
12 sx ii can be configured from the remote console or command line interface (cli). In this chapter default login information ........................................................................ 12 initial sx ii configuration using command line interface (optional) ..... 12 default login informa...
Page 20
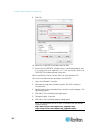
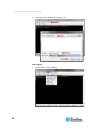
Chapter 2: configure sx ii for the first time 13 connect a keyboard tray or kvm console to the dvi-d and usb ports. connect a laptop to the miniusb admin port. 2. The emulator interface opens once you are connected to sx ii. Press the enter key on your keyboard. 3. When the login prompt appears,...
Page 21
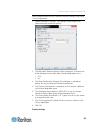
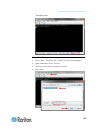
Chapter 2: configure sx ii for the first time 14 10. Enter top to return to the top level prompt. 11. Next, enter config and then enter ports at the next prompt. You can now configure each server port that has a target device connected to it. 12. Enter config port then hit ? To see the port paramete...
Page 22
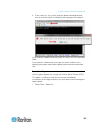
Chapter 2: configure sx ii for the first time 15 set the cli escape sequence the escape key sequence is user-configurable and can be configured per port. The escape sequence is programmable per port because different target operating systems and host applications may trap different escape key sequen...
Page 23: Features
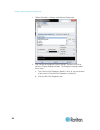
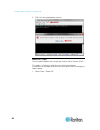
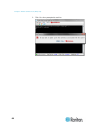
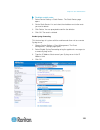
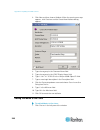
16 the remote console is a browser-based interface accessed when you log in to sx ii via a network connection. Administrator functions in the remote console administrators perform sx ii configuration and maintenance functions from the remote console, such as configuring network access, adding and ma...
Page 24
Chapter 3: access and use remote console features 17 allow pop-ups regardless of the browser you are using, you must allow pop-ups in order to launch the sx ii remote console. Security warnings and validation messages when logging in to sx ii, security warnings and application validation message may...
Page 25
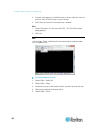
Chapter 3: access and use remote console features 18 java validation and access warning when logging in to sx ii, java ™ prompts you to validate sx ii, and to allow access to the application. Raritan recommends installing an ssl certificate in each sx ii device in order to reduce java warnings, and ...
Page 26
Chapter 3: access and use remote console features 19 additional security warnings even after an ssl certificate is installed in the sx ii, depending on your browser and security settings, additional security warnings may be displayed when you log in to sx ii. It is necessary to accept these warnings...
Page 27
Chapter 3: access and use remote console features 20 use a standard cat5 cable to connect your target device to an available port on the back of sx ii. Note: check the pin definition of the rj45 port on the target. It should match the pin definition on sx ii. Or if needed, connect a raritan nulling ...
Page 28
Chapter 3: access and use remote console features 21 installing a certificate you may be prompted by the browser to accept and validate the sx ii's ssl certificate. Depending on your browser and security settings, additional security warnings may be displayed when you log in to sx ii. It is necessar...
Page 29
Chapter 3: access and use remote console features 22 note: if you are not prompted by the browser, manually select tools > internet options to open the internet options dialog. 1. Click the content tab. 2. Click certificates. The certificate import wizard opens and walks you through each step. fil...
Page 30
Chapter 3: access and use remote console features 23 example 2: add the sx ii to trusted sites and import the certificate in this example, the sx ii's url is added as a trusted site, and the self signed certificate is added as part of the process. 1. Open an ie browser, then select tools > internet ...
Page 31
Chapter 3: access and use remote console features 24 next, import the certificate. 1. Open an ie browser, then log in to sx ii. 2. Click more information on the first java ™ security warning. 3. Click view certificate details on the more information dialog. You are prompted to install the certificat...
Page 32
Chapter 3: access and use remote console features 25 converting a binary certificate to a base64-encoded der certificate (optional) sx ii requires an ssl certificate in either base64-encoded der format or pem format. If you are using an ssl certificate in binary format, you cannot install it. Howeve...
Page 33
Chapter 3: access and use remote console features 26 3. Click "copy to file...". 4. The certificate export wizard opens. Click next to start the wizard. 5. Select "base-64 encoded x.509" in the second wizard dialog. 6. Click next to save the file as a base-64 encoded x.509. You can now install the c...
Page 34
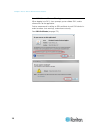
Chapter 3: access and use remote console features 27 log in to sx ii 1. Launch a supported web browser. 2. Enter the sx ii http, https or dns address provided to you by your administrator. Note: you are always redirected to the ip address from http to https. 3. Enter your username and password, then...
Page 35
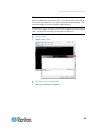
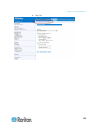
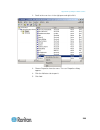
Chapter 3: access and use remote console features 28 sx ii port access page after a successful login, the port access page opens listing all ports along with their status and availability..
Page 36
Chapter 3: access and use remote console features 29 ports are numbered from 1 up to the total number of ports available for the sx ii. For example, port_1 - port_64, port_1 - port_32. "serialport"_"port #" are what make up the default name the physical port until a name is configured for the port. ...
Page 37
Chapter 3: access and use remote console features 30 information description displayed when? State the current state of the application, either idle or active. If idle, the application tracks and displays the amount time the session has been idle. Always your ip the ip address used to access sx ii. ...
Page 38
Chapter 3: access and use remote console features 31 collapse the left panel and then expand it again by clicking on the blue arrow located along the right edge of the panel..
Page 39
Chapter 3: access and use remote console features 32 enable favorites enable the favorites feature and display a list of favorite, frequently accessed sx ii devices by clicking enable in the favorite devices section of the left panel of the sx ii interface. Accept security warnings if they are displ...
Page 40
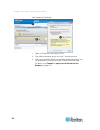
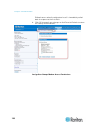
Chapter 3: access and use remote console features 33 • by ip address • by host name (if applicable) discover devices product subnet this option discovers sx ii devices on the device subnet. This is the subnet of the sx ii device's ip address. You can access these devices directly from the subnet pag...
Page 41
Chapter 3: access and use remote console features 34 to add devices to your favorites list: 1. Select the checkbox next to the device name/ip address. 2. Click add. To access a discovered device: • click the device name or ip address for that device. A new browser opens to that device..
Page 42
35 target devices can be accessed from the remote console's port access page using raritan serial console (rsc) (rsc), and at-the-rack via command line interface (cli). Targets can also be accessed via direct port access, in which case you are connected directly to the target via sx ii and no interm...
Page 43
Chapter 4: access targets 36 power on a target (see " power on a target or power strip " on page 39) power off a target (see " power off a target or power strip " on page 40) power cycle a target (see " power cycle a target or power strip " on page 41) you can then connect via raritan serial console...
Page 44
Chapter 4: access targets 37 connect to a target creates a new connection to the target device. From the sx ii remote console, raritan serial console (rsc) opens in a new window and you manage the target from there. If you are connected to the target from the local console port, you access the targe...
Page 45
Chapter 4: access targets 38 disconnect from a target or power strip once connected to a target or power strip, and the port status is up, the disconnect menu option is available in the port action menu. Clicking on the disconnect option disconnects from a target or power strip, and closes the rarit...
Page 46
Chapter 4: access targets 39 power on a target or power strip power on the target from the remote console through the associated outlet. This option is visible only when there are one or more power associations to the target, and when you have permission to manage the target's power. You can also pe...
Page 47
Chapter 4: access targets 40 power off a target or power strip power off the target or power strip through the associated outlet. This option is visible only when - • there are one or more power associations to the target or power strip • you have permission to manage the power you can also perform ...
Page 48
Chapter 4: access targets 41 power cycle a target or power strip power cycling allows you to turn a target or power strip off and then back on through the outlet it is plugged into. This option is visible only when - • there are one or more power associations to the target or power strip • you have ...
Page 49
Chapter 4: access targets 42 connect a keyboard tray or kvm console to the dvi-d and usb ports. connect a laptop to the mini-usb admin port..
Page 50
Chapter 4: access targets 43 note that connecting to the sx ii local console via the local port is an independent access path to each connected target device. Video resolution the default, local console port video resolution is 1024x768@60. By default, monitors are typically set to the highest resol...
Page 51
Chapter 4: access targets 44 send a break to the connected target. Admin > [portname] > sendbreak lock write access to this port. Admin > [portname] > writelock unlock write access to this port. Admin > [portname] > writeunlock query power status of this port. Admin > [portname] > powerstatus toggle...
Page 52
Chapter 4: access targets 45 command line interface partial searches enter the first few characters of command and press the tab key on your keyboard in order to locate a specific command. The command line interface (cli) completes the entry if the characters form an exact match. For example enterin...
Page 53
Chapter 4: access targets 46 command line interface high-level commands the cli is menu based. Some commands move to a menu with a different command set. The following common commands can be used at all levels of the command line interface (cli): • top - return to the top level of the cli hierarchy,...
Page 54
47 use raritan serial console (rsc) to connect to serial targets from the sx ii remote console. Alternatively, install rsc as a standalone-client. The rsc stand-alone client uses the sx ii ip address and the target's port number to connect directly to the target, so you do not have to connect to the...
Page 55
Chapter 5: raritan serial console (rsc) help 48 standalone raritan serial console requirements the following requirements must be met to support the raritan serial console (rsc): • minimum 1 ghz pc with 512 mb ram. • java ™ see sx ii release notes for the required version. If you do not have a compa...
Page 56
Chapter 5: raritan serial console (rsc) help 49 3. In the system variables section, click new. 4. Write down the installed java path. 5. In the variable value block field of the new system variable dialog, add java_home to the variable name block and the java path you wrote down earlier. 6. Click ok...
Page 57
Chapter 5: raritan serial console (rsc) help 50 9. Click ok. 10. Select the classpath variable and click edit. 11. Ensure the classpath variable value is configured properly; that is, its value must have a period (.) in it. If, for any reason, there is no classpath variable defined, create one. Next...
Page 58
Chapter 5: raritan serial console (rsc) help 51 7. Click next. The windows shortcut page opens. 8. Select the program group for the shortcut. 9. Click next. The installation finished page opens. 10. Click done. Set linux os variables and install standalone raritan serial console (rsc) for linux to s...
Page 59
Chapter 5: raritan serial console (rsc) help 52 setting unix os variables to check the latest jre ™ version on sun solaris ™ : 1. Launch a terminal window on the sun solaris desktop. 2. Type java-version in the command line and press enter. The currently-installed version of java ™ runtime environme...
Page 60
Chapter 5: raritan serial console (rsc) help 53 launching rsc on windows systems 1. Double-click the shortcut or use start programs to launch the standalone raritan serial console (rsc). The rsc login connection properties dialog appears. 2. Enter the dominion sx ii ip address, account information, ...
Page 61
Chapter 5: raritan serial console (rsc) help 54 change the default idle timeout setting and then launch the rsc. See login limitations (on page 163) for details on changing the idle timeout setting. Access emulator options 1. Select the emulator drop-down menu to display a list of options. Settings.
Page 62
Chapter 5: raritan serial console (rsc) help 55 note: an administrator can set terminal emulation settings using setup > port configuration. 1. Choose emulator > settings. The settings screen displays the general tab with the default settings. 2. The main menu shortcut default is none; accept this, ...
Page 63
Chapter 5: raritan serial console (rsc) help 56 1. Choose emulator > settings and click the display tab. 2. Click default to accept the default settings, and then click ok to close the display settings window. To change the settings, follow these steps: a. The terminal font properties default is ari...
Page 64
Chapter 5: raritan serial console (rsc) help 57 c. The default font property is monospace, or you can choose a font from the gui font properties scrolling list. Note: for simplified chinese characters, rsc supports euc-cn encoding system. 3. Choose the following from their respective drop-down menus...
Page 65
Chapter 5: raritan serial console (rsc) help 58 korean chinese bulgarian 6. Click ok to close the display settings window. If you changed the language setting, the rsc changes to that language when the display settings window is closed. Note: in case of unrecognized characters or blurry screen...
Page 66
Chapter 5: raritan serial console (rsc) help 59 get write lock write lock prevents other users from taking the write access while you are using it. 1. To get write lock, choose emulator > get write lock. 2. If get write lock is not available, a request rejected message appears. Write unlock to get w...
Page 67
Chapter 5: raritan serial console (rsc) help 60 2. A check mark appears in the write access column after the name of the user who has write access to the console. 3. Click close to close the connected users window. Exit 1. Choose emulator > exit to close the rsc. The exit confirmation dialog appears...
Page 68
Chapter 5: raritan serial console (rsc) help 61 note: the copy-paste limit of text in rsc is 9999 lines. Keyboard shortcuts to highlight, copy, and paste all or partial lines of text: • click and drag your mouse over the text you wish to copy. • use ctrl+c to copy text. • position the cursor where y...
Page 69
Chapter 5: raritan serial console (rsc) help 62 3. Click save after selecting or creating a file. Stop logging • choose tools > stop logging..
Page 70
Chapter 5: raritan serial console (rsc) help 63 the logging stops. Send a text file 1. Select tools > send text file. A send text file screen appears. 2. Open the directory of the text file. 3. Click on or enter the file name of the text file. 4. Click open..
Page 71
Chapter 5: raritan serial console (rsc) help 64 when you click open, raritan serial console (rsc) sends whatever file you selected directly to the port. if there is currently no target connected, nothing is visible on the screen. Note, if you are using a mac ® and/or safari ® , do the following ...
Page 72
Chapter 5: raritan serial console (rsc) help 65 3. If you select yes, the system sends the power command to either turn on or off the outlets associated to the target port of the device. If you receive a hardware error message, this means the pdu command failed. If you receive a software error messa...
Page 73
Chapter 5: raritan serial console (rsc) help 66 2. Click yes when prompted to confirm. Power off a target use this option to power off a target from raritan serial console (rsc). This option is visible only when there are one or more power associations to the target, and when you have permission to ...
Page 74
Chapter 5: raritan serial console (rsc) help 67 2. Click yes when prompted to confirm. Power cycle a target power cycling allows you to turn a target off and then back on through the outlet it is plugged into. This option is visible only when - • there are one or more power associations to the targe...
Page 75
Chapter 5: raritan serial console (rsc) help 68 2. Click yes when prompted to confirm..
Page 76
Chapter 5: raritan serial console (rsc) help 69 chat when using browser access over ssl, an interactive chat feature called chat allows you and other users on the same port to communicate. The maximum length of a chat message is 300 characters. Note: when a chat is initiated, a chat window appears o...
Page 77
Chapter 5: raritan serial console (rsc) help 70 help and about help topics include online assistance for operating the raritan serial console (rsc) and release information about rsc. Help topics • choose help > help topics. Help is displayed in a secondary window. About raritan serial console • choo...
Page 78
71 this help contains information on tasks typically performed by administrators, such as managing user groups and users, managing authentication and security, configuring network settings and so on. Note that the same tasks can be performed from the remote console or command line interface (cli), s...
Page 79
Chapter 6: sx ii administration 72 if no power strips are connected to sx ii, a message stating "no power strips found" is displayed in the powerstrip device section of page. If power strips are down or cannot be reached, the message "cannot communicate with power strip or outlet number not match, p...
Page 80
Chapter 6: sx ii administration 73 the currently selected powerstrip's outlet names, their current state, and their associated ports, if applicable, are displayed below the powerstrip information. Use the on, off and cycle buttons on the page to control each of the powerstrip's outlets. Select anoth...
Page 81
Chapter 6: sx ii administration 74 2. Click ok. The outlet then cycles (note that this may take a few seconds). 3. Once the cycling is complete a dialog will open. Click ok to close the dialog. Specify power cycle duration to specify the duration between powering an outlet off and on when the cycle ...
Page 82
Chapter 6: sx ii administration 75 4. Change the port name, if needed. 5. Click ok. Sx ii attempts to communicate with the power strip. If communication is successful, the port is configured as a power port. Note: if the power strip is in not in support mode, a communication failure occurs. Update t...
Page 83
Chapter 6: sx ii administration 76 2. Associate the active target to the disconnected power port. This will break the disconnected target's power association. 3. Finally, associate the active target to the correct power port. Configure and manage users and groups from the remote console note: these ...
Page 84
Chapter 6: sx ii administration 77 user group users belong to a group and groups have privileges. Organizing the various users of your sx ii into groups saves time by allowing you to manage permissions for all users in a group at once, instead of managing permissions on a user-by-user basis. You m...
Page 85
Chapter 6: sx ii administration 78 any newly created user is automatically put in this group until they are assigned to another group. • individual group an individual group is essentially a "group" of one. That is, the specific user is in its own group and not affiliated with other groups. Use an i...
Page 86
Chapter 6: sx ii administration 79 user profiles serve two purposes: • to provide users with a username and password to log in to sx ii. • to associate the user with a user group. The user group determines which functions and ports the user can access. Sx ii is shipped with one user profile built in...
Page 87
Chapter 6: sx ii administration 80 2. Type a descriptive name for the new user group into the group name field. Set group permissions 3. Select the permissions to assign to the group. device access while under cc-sg management - allows users and user groups with this permission to directly access ...
Page 88
Chapter 6: sx ii administration 81 user authentication is performed based on sx ii authentication settings. Note: the admin user group has this permission by default. device settings - network settings, date/time settings, port configuration, event management (snmp, syslog), and so on. diagnosti...
Page 89
Chapter 6: sx ii administration 82 4. Select the access permissions the group has to server ports and power control. The default is deny. Select each port individually, or use the checkboxes at the bottom of the page to apply permissions to all ports. deny - denied access completely. view - view...
Page 90
Chapter 6: sx ii administration 83 this feature limits a user's access to the sx ii by allowing you to assign them to a group that can only access the device through specific ip addresses. This feature applies only to users belonging to the specific group. This is unlike the ip access control list f...
Page 91
Chapter 6: sx ii administration 84 3. Choose the action from the action drop-down list. 4. Click insert and then click ok. If the rule number you just typed equals an existing rule number, the new rule is placed ahead of the exiting rule and all rules are moved down in the list. To replace a rule: 1...
Page 92
Chapter 6: sx ii administration 85 4. Type a password in the password field, and then type it again in the confirm password field. Required the password is case sensitive. Note: if the strong password feature is enabled, there are other password requirements. See strong passwords for details. 5. A...
Page 93
Chapter 6: sx ii administration 86 add ssh client certificates for users note: this function can also be performed using command line interface. See configure user authorization and authentication services using cli (on page 200). If needed, ssh (secure shell) client authentication keys can be added...
Page 94
Chapter 6: sx ii administration 87 edit or deactivate a user note: this function can also be performed using command line interface. See configure and manage users and user groups using cli (on page 197). 1. Choose user management > user list. The user list page opens. It looks exactly like the new ...
Page 95
Chapter 6: sx ii administration 88 view users by port the user by ports page lists all authenticated local and remote users and ports they are being connected to. • if the same user is logged on from more than one client, their username appears on the page for each connection they have made. For exa...
Page 96
Chapter 6: sx ii administration 89 disconnect a user from a port you can disconnect a user from a specific port without logging them off of sx ii. For example, if a user is connected to serial port 1 via raritan serial console (rsc), you can disconnect them from the port. This is unlike the force us...
Page 97
Chapter 6: sx ii administration 90 log a user off of sx ii (force logoff) if you are an administrator or have user management permissions, you are able to log off any authenticated user who is logged on to sx ii. Users can also be disconnected at the port level. See disconnecting users from ports. 1...
Page 98
Chapter 6: sx ii administration 91 configure user authentication from the remote console sx ii requires users be authenticated to access the appliance. Authentication is the process of verifying that a user is who he says he is. Once a user is authenticated, the user's group is used to determine his...
Page 99
Chapter 6: sx ii administration 92 enable local user authentication users are validated based on their username and password from a local database. Note that if a remote authentication is enabled but the user is not found, sx ii checks the local authentication database as well. 1. Choose user manage...
Page 100
Chapter 6: sx ii administration 93 enable ldap/ldaps authentication note: when configuring the ldap server, the query string format on the server should contain the name of the group configured on sx ii. You can use the lightweight directory access protocol (ldap) to authenticate sx ii users instead...
Page 101
Chapter 6: sx ii administration 94 server configuration 3. In the primary ldap server field, type the ip address or host name of your ldap/ldaps remote authentication server. 4. Optional in the secondary ldap server field, type the ip address or host name of your backup ldap/ldaps server (up to 256 ...
Page 102
Chapter 6: sx ii administration 95 type the name of the active directory domain if you selected microsoft active directory. For example, acme.Com. Consult your active directive administrator for a specific domain name. Optional 6. In the user search dn field, enter the distinguished name of where ...
Page 103
Chapter 6: sx ii administration 96 10. The default secure ldap port is 636. Either use the default port or specify another port. This field is only used when the enable secure ldap checkbox is selected. 11. Select the "enable ldaps server certificate validation" checkbox to use the previously upload...
Page 104
Chapter 6: sx ii administration 97 the sx ii then tests the ldap configuration from the authentication settings page. This is helpful due to the complexity sometimes encountered when configuring the ldap server and sx ii for remote authentication. Once the test is completed, a message is displayed t...
Page 105
Chapter 6: sx ii administration 98 10. Choose the global authentication type from among the options in the drop-down list: pap - with pap, passwords are sent as plain text. Pap is not interactive. The user name and password are sent as one data package once a connection is established, rather than...
Page 106
Chapter 6: sx ii administration 99 create a radiu ias policy this section describes the steps to create a policy to allow radius users to access sx ii. The example in this section requires two conditions: the client source ip address of sx ii and that the userid is a member of sx ii user group: • na...
Page 107
Chapter 6: sx ii administration 100 the value can be raritan:g{admin}:d{1234567890} if you are using the dial back feature, where 1234567890 is the phone number for dial back. the value raritan:g{admin} must match with the local group on the sx ii. the sx ii comes from the factory with the def...
Page 108
Chapter 6: sx ii administration 101 2. Click add/remove windows components. 3. Highlight networking services then click the details... Button. 4. Select the internet authentication service checkbox and then click ok. 5. Click next> and continue with the wizard steps. Ias active directory access if u...
Page 109
Chapter 6: sx ii administration 102 cisco acs 5.X for radius authentication the cisco access control server (acs) is another authentication solution supported by the sx ii. For the sx ii to support radius, both the sx ii and the user information must be added into the radius configuration. If you ar...
Page 110
Chapter 6: sx ii administration 103 attribute data nas-ip-address (4) the ip address for the sx ii. User-name (1) the user name entered at the login screen. Acct-session-id (44) session id for accounting. User-password(2) the encrypted password. Accounting-request(4) acct-status (40) start(1) - star...
Page 111
Chapter 6: sx ii administration 104 2. Click the tacacs+ radio button to enable the tacacs+ section of the page. The section expands. If it does not, click the section header to expand it. 3. Under primary tacacs+, type the ip address of the tacacs+ server and the port on which it is listening (defa...
Page 112
Chapter 6: sx ii administration 105 9. Click ok. Tacacs+ authentication is enabled. Returning user group information from active directory server the sx ii supports user authentication to active directory ® (ad) without requiring that users be defined locally on the sx ii. This allows active directo...
Page 113
Chapter 6: sx ii administration 106 information about updating the ad ldap/ldaps schema. To enable your ad server on sx ii: 1. In sx ii, create special groups and assign proper permissions and privileges to these groups. For example, create groups such as ad_admin and ad_operator. 2. On your active ...
Page 114
Chapter 6: sx ii administration 107 configure sx ii network settings from the remote console the configuration settings described in initial sx ii configuration from the remote console (on page 19) are the same that apply when making any changes. Reset network settings to factory defaults 1. Select ...
Page 115
Chapter 6: sx ii administration 108 enable auto script from the remote console for use with tftp or a usb stick use this feature to copy the same settings to each of your sx iis. To do this, a configuration script file with the sx ii's settings is created. Example script config localport config enab...
Page 116
Chapter 6: sx ii administration 109 • save the file to usb stick. The file can then be brought to each appliance and used to configure it. 1. Access and configure the sx ii you want to create a configuration file from. 2. Select device settings > auto configuration. 3. The name of the script is list...
Page 117
Chapter 6: sx ii administration 110 3. Click ok to create the script. A success message is displayed on the page. Enable automatic script configuration via tftp server: 1. Select the "enable automatic script configuration via tftp stick" checkbox. 2. The tftp auto script settings section is enabled....
Page 118
Chapter 6: sx ii administration 111 retrieve tftp ip address via dhcp - note that to do this, ip auto configuration must set to dhcp and enabled on the sx ii. See disable or enable dhcp in sx ii. set tftp ip address manually - enter the ip address in the field provided. 5. Click ok. Prepare a us...
Page 119
Chapter 6: sx ii administration 112 4. Create a script file named _.Autoscript containing all of the scripts that need to be executed on the appliance to configure it. 5. Copy all above files to the top directory of the usb stick. 6. Remove any file named __result.Txt . 7. Following are examples of ...
Page 120
Chapter 6: sx ii administration 113 configure device settings from the remote console enable ssh access (optional) ssh is enabled by default. For information on required open ports and port protocols, see port access protocol requirements (on page 238). Note that ssh can be disabled or enabled via r...
Page 121
Chapter 6: sx ii administration 114 enable telnet (optional) due to the lack of security, the username, password and all traffic is in clear-text on the wire. Telnet must be enabled before it can be used; is disabled by default. Note that telnet can be disabled or enabled via remote console or comma...
Page 122
Chapter 6: sx ii administration 115 change http and https port settings if needed, change http and/or https ports used by sx ii. For example, if you are using the default http port 80 for another purpose, changing the port ensures the appliance does not attempt to use it. For information on required...
Page 123
Chapter 6: sx ii administration 116 change the tcp discovery port sx ii discovery occurs over a single, configurable tcp port. The default is port 5000, but you can change it to use any tcp port except 80 and 443. To access sx ii from beyond a firewall, your firewall settings must enable two-way com...
Page 124
Chapter 6: sx ii administration 117 enable direct port access direct port access allows users to bypass having to use the sx ii's login dialog and port access page. There are three methods to access ports directly. Note that direct port access can be configured via remote console or command line int...
Page 125
Chapter 6: sx ii administration 118 3. Locate the port in the table below the checkboxes, then enter the ip address you want to assign to the port. 4. Click ok to apply the settings. Enable direct port access via username for ssh/telnet this feature provides the ability to access dpa through a usern...
Page 126
Chapter 6: sx ii administration 119 ip forwarding and static routes enable ip forwarding, or create static routes if sx ii has two lan ports or is configured for modem access. To enable ip forwarding: 1. Select device settings > static routes. The static routes page opens. 2. Go to the ip forwarding...
Page 127
Chapter 6: sx ii administration 120 the route fields are displayed. 3. Select the one you want to configure from the drop-down menu in the interface field. lan1 = eth0 lan2 = eth1 4. Type the ip address, subnet mask, and gateway of the destination host in the destination, mask, and gateway field...
Page 128
Chapter 6: sx ii administration 121 to delete a static route: 1. Select device settings > static routes. The static routes page opens. 2. Go the static routes list and select the checkbox next to the route you want to delete. 3. Click delete. You are prompted to confirm the deletion. 4. Click ok. Th...
Page 129
Chapter 6: sx ii administration 122 note: ipv6 addresses cannot exceed 80 characters in length for the host name. • click reset to defaults at the bottom of the page to remove the setting. Configure date and time settings from the remote console use the date/time settings page to specify the date an...
Page 130
Chapter 6: sx ii administration 123 6. Click ok..
Page 131
Chapter 6: sx ii administration 124 configure snmp agents from the remote console snmp-compliant devices, called agents, store data about themselves in management information bases (mibs) and return this data to the snmp managers. See viewing the sx ii mib (on page 130) for information on viewing th...
Page 132
Chapter 6: sx ii administration 125 community - the appliance's community string community type - grant either read-only or read-write access to the community users note: an snmp community is the group to which appliances and management stations running snmp belong. It helps define where informa...
Page 133
Chapter 6: sx ii administration 126 configure snmp traps from the remote console simple network management protocol (snmp) is a protocol governing network management and the monitoring of network devices and their functions. Snmp provides the ability to send traps, or notifications, over a network t...
Page 134
Chapter 6: sx ii administration 127 trap description networkfailure an ethernet interface of the product can no longer communicate over the network. Networkparameterchanged a change has been made to the network parameters. Networkparameterchangedv2 a change has been made to network parameters when w...
Page 135
Chapter 6: sx ii administration 128 trap description userconnectionlost a user with an active session has experienced an abnormal session termination. Userdeleted a user account has been deleted. Userforcedlogout a user was forcibly logged out by admin userlogin a user has successfully logged into t...
Page 136
Chapter 6: sx ii administration 129 4. Complete the following fields for snmp v1/v2c (as needed): destination ip/hostname - the ip or hostname of the snmp destination. Up to five (5) snmp trap destinations can be created. Note: ipv6 addresses cannot exceed 80 characters in length for the host name...
Page 137
Chapter 6: sx ii administration 130 next, configure where the snmp trap events are sent and logged. Destinations are configured on the event management - destination page. See configuring event management - destinations. Sx ii supports snmp logging for snmp v1/v2c and/or v3. Snmp v1/v2c defines mess...
Page 138
Chapter 6: sx ii administration 131 tip: enable or disable entire categories by checking or clearing the category checkboxes, respectively. 3. Click ok. To reset to factory defaults: • click reset to defaults. Warning: when using snmp traps over udp, it is possible for the sx ii and the router that ...
Page 139
Chapter 6: sx ii administration 132 2. Go to the smtp settings panel and select the enable smtp server checkbox. 3. Type the email address of the smtp subscriber in the new email subscriber address field and then click add. 4. Click ok. Configure and test smtp server settings enter the information r...
Page 140
Chapter 6: sx ii administration 133 4. Click apply. Configu it is important that the smtp server information be accurate so that the sx ii appliance can send messages using that smtp server. This test sends an email using the settings displayed on the page in the smtp settings pane. Sx ii saves the ...
Page 141
Chapter 6: sx ii administration 134 configure modem settings from the remote console configure modem settings for sx ii models with internal, analog modems on the modem settings page. You can also configure modem settings via command line interface. See configure a modem using cli (on page 204). Not...
Page 142
Chapter 6: sx ii administration 135 note: the enable broadband modem feature is specific to use of an external, wireless modem. See connect and enable global access to an external modem (see " connect and enable global access to an external broadband modem " on page 137). 2. Select enable modem. 3. ...
Page 143
Chapter 6: sx ii administration 136 dialback occurs when the originator of a call is immediately called back in response to the first dial-in. 6. Click ok to commit your changes or click reset to defaults to return the settings to their defaults. Assign user groups modem access permissions.
Page 144
Chapter 6: sx ii administration 137 • if needed, assign users to a group with modem access permissions. Modem access permission is assigned to a user group on the group page, and the user is then assigned to the group on the user page. For more information, see configure and manage users and groups ...
Page 145
Chapter 6: sx ii administration 138 gx440 must have at least aleos software version 4.4.1.014 raritan has tested this configuration with the verizon wireless mc7750 radio module using firmware version 3.05.10.13. Connect the external, wireless modem usb connection use either a micro a or micro b to ...
Page 146
Chapter 6: sx ii administration 139 for security reasons, raritan recommends you change the default admin account username to a new name before using the gx440.. Assign user groups modem access permissions following are settings applied in sx ii. • modem access permission is assigned to a user group...
Page 147
Chapter 6: sx ii administration 140 use this feature to enable or disable access to an external gx440 modem. Broadband is disabled by default. Since this is a global-level feature, it is disabled for all users. Once it is enabled, only users who belong to a user group with modem access permissions c...
Page 148
Chapter 6: sx ii administration 141 the connection event is logged in the sx ii audit log. Once the devices are on and the connection is active, the gateway ip address is displayed in the remote console in the left panel under the network section. Additionally, the gateway ip address is displayed on...
Page 149
Chapter 6: sx ii administration 142 power supply setup sx ii provides dual power supplies, and can automatically detect and provide notification regarding the status of these power supplies. When both power supplies are used, sx ii automatically detects them and notifies you of their status. Additio...
Page 150
Chapter 6: sx ii administration 143 2. If you are plugging power input into power supply number one (left- most power supply at the back of the unit), then select the powerln1 auto detect option. 3. If you are plugging power input into power supply number two (right- most power supply at the back of...
Page 151
Chapter 6: sx ii administration 144 configure local port settings from the remote console configure local console port settings on this page. Some changes you make to the settings on the local port settings page restart the local terminals. If a local terminal restart occurs when a setting is change...
Page 152
Chapter 6: sx ii administration 145 us portuguese (portugal) us/international norwegian (norway) united kingdom swedish (sweden) french (france) danish (denmark) german (germany) belgian (belgium) german (switzerland) hungarian simplified chinese spanish traditional chi...
Page 153
Chapter 6: sx ii administration 146 changing the default gui language setting from the remote console the sx ii web-based interface defaults to english, but also supports the following localized languages. These languages are not applied to the local console. • japanese • simplified chinese • tradit...
Page 154
Chapter 6: sx ii administration 147 if needed, make changes to the default timestamp interval and/or the logging update frequency. Timestamp represents the interval between two timestamp messages. Enter a time in seconds between 0 – 99999. Note that entering 0 disables timestamps for port logging. T...
Page 155
Chapter 6: sx ii administration 148 enable the port log local file to capture data for each port locally on sx ii. Log files are stored on sx ii's internal flash drive. For 8 and 16 port models, there is 2gb internal flash drive. All other models have 8gb flash drive. If needed, enter a maximum file...
Page 156
Chapter 6: sx ii administration 149 this feature sends event log messages to a remote syslog server. The messages from the sx ii appliance are sent to the local0 channel of the syslog server for more efficient parsing. Since all messages are sent from the local0 channel on the syslog server, all por...
Page 157
Chapter 6: sx ii administration 150 you must also enable port logging. For more information on port logging, see enable port logging. Note: the nfs server must have the exported directory with write permission for the port logging to work. 1. Select the enable nfs checkbox to enable nfs logging. 2. ...
Page 158
Chapter 6: sx ii administration 151 if the re-mount succeeds, logging continues; otherwise, further logging events are inhibited. Manage port logging - local files from the remote console to delete log files: 1. Select checkbox for log files. 2. Click "delete log file"..
Page 159
Chapter 6: sx ii administration 152 to retrieve a log file: • click the download link for a log file's "outputfile" or "inputfile". Note that power string data is not saved in port log files. For information on configuring local log files for ports, see configure port logging - settings (see " confi...
Page 160
Chapter 6: sx ii administration 153 configure powerstrips 1. If you selected power strip, change the power strip name and click ok. If a power strip is detected, you are returned to the port configuration page. 2. Select the port again to edit it and its outlet names, if desired. Outlet names defaul...
Page 161
Chapter 6: sx ii administration 154 a port can have up to four associated outlets, and you can associate a different rack pdu (power strip) with each. From this page, you can define those associations so that you can power on, power off, and power cycle the server from the port access page. To use t...
Page 162
Chapter 6: sx ii administration 155 5. To allow direct port access to the target's port, enter the port's ip address, and the ssh port and telnet port. Configure port settings configure the remaining port settings, as needed or required. 1. Select the terminal emulation type from the drop-down menu ...
Page 163
Chapter 6: sx ii administration 156 2. Set encoding if you want raritan serial console (rsc) to always use a specific character encoding for this port. Encoding overrides the global rsc setting for the port to whatever value you set. The choices are: default,us-ascii,iso8859-1, iso8859-15,utf- 8, sh...
Page 164
Chapter 6: sx ii administration 157 12. Alternatively, deselect this and all messages such as "authentication successful." these messages are displayed to users when they connect via direct port access. The default is deselected. The default is none. 13. Select the escape mode. The escape sequence a...
Page 165
Chapter 6: sx ii administration 158 17. Click ok. Apply settings to other ports.
Page 166
Chapter 6: sx ii administration 159 once finished, you can apply the same port settings to other ports. 1. Select the ports from the apply serial port settings to other ports" section of the page by selecting them individually or using the selection buttons at the bottom of the page. 2. Click ok to ...
Page 167
Chapter 6: sx ii administration 160 port keyword list port keywords work as a filter. You can create port keywords and associate them with - • events • local/remote syslog messages • snmp traps if a keyword is detected - • a corresponding message is logged in a local/nfs port log. • a corresponding ...
Page 168
Chapter 6: sx ii administration 161 the serial alert event is selected from the event management - destinations page. 1. Choose device settings > port keywords. The port keyword list page opens..
Page 169
Chapter 6: sx ii administration 162 2. Click add at the bottom of list on the page. The keyword page opens. 3. Type a keyword in the keyword field. 4. Select the port(s) you want to associate with that keyword. 5. Click add to add them to the selected box. 6. Click ok..
Page 170
Chapter 6: sx ii administration 163 configure security settings from the remote console login limitations using login limitations, you can specify restrictions for single login, password aging, and the logging out idle users. Login limitations are configured on the security settings page. • select s...
Page 171
Chapter 6: sx ii administration 164 the idle timeout field is used to set the amount of time (in minutes) after which an idle user will be logged out. This field is enabled when the log out idle users option is selected. Up to 365 minutes can be entered as the field value • anonymous port access whe...
Page 172
Chapter 6: sx ii administration 165 lockout time - the amount of time for which the user will be locked out. The valid range is 1 - 1440 minutes and the default is 5 minutes. Note: users in the role of administrator are exempt from the timer lockout settings. • deactivate user-id when selected, th...
Page 173
Chapter 6: sx ii administration 166 to enforce this use of a special character, select "enforce at least one printable special character". "number of restricted passwords based on history" enforces the number of prior passwords that cannot be repeated. The range is 1-12 and the default is 5. Configu...
Page 174
Chapter 6: sx ii administration 167 rc4 - secures user names, passwords and data using the rsa rc4 encryption method. This is a 128 - bit secure sockets layer (ssl) protocol that provides a private communications channel between the sx ii device and the remote pc during initial connection authenti...
Page 175
Chapter 6: sx ii administration 168 enable local admin password reset - resets the local administrator password only. The password is reset to raritan. disable all local resets - no reset action is taken. Resets the local administrator password only. The password is reset to raritan. 5. Click ok...
Page 176
Chapter 6: sx ii administration 169 fips 140-2 support requirements the sx ii supports the use of fips 140-2 approved encryption algorithms. This allows an ssl server and client to successfully negotiate the cipher suite used for the encrypted session when a client is configured for fips 140-2 only ...
Page 177
Chapter 6: sx ii administration 170 enable fips 140-2 for government and other high security environments, enabling fips 140-2 mode may be required. The sx ii uses an embedded fips 140-2-validated cryptographic module running on a linux ® platform per fips 140-2 implementation guidance section g.5 g...
Page 178
Chapter 6: sx ii administration 171 firewall the sx ii has a firewall function to provide protection for the ip network and to control access between the internal router and lan 1, lan 2, and the modem interfaces. 1. Choose security > firewall. The firewall page opens, displaying the existing iptabl...
Page 179
Chapter 6: sx ii administration 172 4. Enter a rule in the iptables rule field the click apply. Add as many rules as are needed. 5. Click save. The rule is displayed on the screen. 6. You can delete some or all of the default rules if you choose to. Ssl certificates sx ii uses the secure socket laye...
Page 180
Chapter 6: sx ii administration 173 a. Common name - the network name of the sx ii once it is installed on your network (usually the fully qualified domain name). The common name is identical to the name used to access the sx ii with a web browser, but without the prefix “http://”. In case the name ...
Page 181
Chapter 6: sx ii administration 174 d. A confirmation dialog is displayed. Click ok to close it. E. Reboot the sx ii to activate the self-signed certificate. to generate a csr to send to the ca for certification: a. Click create. B. A message containing all of the information you entered appears. ...
Page 182
Chapter 6: sx ii administration 175 back! In case you deleted it by mistake, you have to repeat the three steps as described above. To avoid this, use the download function so you will have a copy of the csr and its private key. Converting a binary certificate to a base64-encoded der certificate (op...
Page 183
Chapter 6: sx ii administration 176 3. Click "copy to file...". 4. The certificate export wizard opens. Click next to start the wizard. 5. Select "base-64 encoded x.509" in the second wizard dialog. 6. Click next to save the file as a base-64 encoded x.509. You can now install the certificate on you...
Page 184
Chapter 6: sx ii administration 177 security banner sx ii provides you with the ability to add a security banner to the sx ii login process. This feature requires users to either accept or decline a security agreement before they can access the sx ii. The information provided in a security banner wi...
Page 185
Chapter 6: sx ii administration 178 b. Upload the information from .Txt file by selecting the restricted services banner file radio button and using the browse feature to locate and upload the file. Click ok. Once the file is uploaded, the text from the file will appear in the restricted services ba...
Page 186
Chapter 6: sx ii administration 179 configure maintenance settings from the remote console audit log a log is created of sx ii system events. The audit log can contain up to approximately 2000 lines worth of data before it starts overwriting the oldest entries. To avoid losing audit log data, export...
Page 187
Chapter 6: sx ii administration 180 5. To page through the audit log, use the [older] and [newer] links..
Page 188
Chapter 6: sx ii administration 181 device information selection maintenance > device information to view information specific to your sx ii. This is useful for support. Backup and restore from the backup/restore page, you can backup and restore the settings and configuration for your sx ii. In addi...
Page 189
Chapter 6: sx ii administration 182 2. Click backup. A file download dialog appears that contains an open button. Do not click open. In ie 7 (and later), ie is used as the default application to open files, so you are prompted to open the file versus save the file. To avoid this, you must change the...
Page 190
Chapter 6: sx ii administration 183 full restore - a complete restore of the entire system. Generally used for traditional backup and restore purposes. protected restore - everything is restored except appliance- specific information such as ip address, name, and so forth. With this option, you ...
Page 191
Chapter 6: sx ii administration 184 1. Choose maintenance > firmware upgrade. The firmware upgrade page opens. 2. Click the show latest firmware link to locate the appropriate raritan firmware distribution file (*.Rfp) on the raritan website on the firmware upgrades web page. 3. Unzip the file. Plea...
Page 192
Chapter 6: sx ii administration 185 upgrade history the sx ii provides information about upgrades performed on the sx ii and attached devices. • choose maintenance > upgrade history to view the upgrade history. Information is provided about the sx ii upgrade(s) that have been run, the final status o...
Page 193
Chapter 6: sx ii administration 186 to reboot your sx ii: 1. Choose maintenance > reboot. The reboot page opens. 2. Click reboot. You are prompted to confirm the action. Click yes to proceed with the reboot..
Page 194
Chapter 6: sx ii administration 187 reset the sx ii using the reset button on the appliance on the back panel of the appliance, there is a reset button. It is recessed to prevent accidental resets, so you need a pointed object to press this button. The actions that are performed when the reset butto...
Page 195
Chapter 6: sx ii administration 188 4. While continuing to hold the reset button, power the sx ii device back on. Continue holding the reset button until you hear a beep that is about one second long. Once the device is successfully reset, two (2) beeps are emitted from the appliance. Configure diag...
Page 196
Chapter 6: sx ii administration 189 4. Select the interface in the network interface drop-down box to ping on a specified interface. Optional trace route to host page trace route is a network tool used to determine the route taken to the provided hostname or ip address. To trace the route to the hos...
Page 197
Chapter 6: sx ii administration 190 5. Select the interface in the network interface drop-down box to trace route on a specified interface. Optional.
Page 198
Chapter 6: sx ii administration 191 execute a diagnostics script and create a diagnostics file note: this page is for use by raritan field engineers or when you are directed by raritan technical support. Use this feature to download diagnostic information from the sx ii to the client machine. Two op...
Page 199
Chapter 6: sx ii administration 192 4. To create a diagnostics file to send to raritan technical support, click save to file and save the file locally from the save as dialog. 5. Email this file as directed by raritan technical support..
Page 200
Chapter 6: sx ii administration 193 network interface page the sx ii provides information about the status of your network interface. To view information about your network interface: • choose diagnostics > network interface. The network interface page opens. The following information is displayed: ...
Page 201
Chapter 6: sx ii administration 194 statistics - produces a page similar to the one displayed here. interfaces - produces a page similar to the one displayed here..
Page 202
Chapter 6: sx ii administration 195 route - produces a page similar to the one displayed here. Administering sx ii using command line interface this section is specific to tasks performed using command line interface. For information on performing tasks in the sx ii remote console, see administeri...
Page 203
Chapter 6: sx ii administration 196 command description parameters password create a new password, if needed. new password configure power strips using cli note: these functions can also be managed from the remote console. See configure power strips from the remote console (on page 71). The follow...
Page 204
Chapter 6: sx ii administration 197 command description parameters unassociate remove a power outlet association from a sx ii port. - sx port number to unassociate - name of power strip to access - outlet number on power strip to unassociate unsetpowerpor t configure an sx ii port to remove a ...
Page 205
Chapter 6: sx ii administration 198 command description parameters pcshare pc-share access - indicate whether users in the group are allowed to access a port that already has users connected to it if the port access mode is set to share. Permitted (true), denied (false). viewonly settings false>...
Page 206
Chapter 6: sx ii administration 199 command description parameters showgroup shows the details of existing user groups. If there is no group specified, the command displays all groups in the system. - group to display. Deletegroup deletes an existing user group. - group to delete. Adduser add an...
Page 207
Chapter 6: sx ii administration 200 command description parameters edituser update information for a specified user. see addgroup parameters. Deleteuser delete a specified user. user - user to delete showuser displays the details for an existing user. user - user to display insertgroupacl inse...
Page 208
Chapter 6: sx ii administration 201 command description parameters authmode set the authentication mode. mode ldap configuration theldap configuration menu offers commands to set up ldap and ldaps. Enter admin > config > authentication > ldap to access the menu. Command description parameters ldap...
Page 209
Chapter 6: sx ii administration 202 the radius menu provides access to commands used to configure access to a radius server. The dictionary file must be created at the following location. /user/share/freeradius/ # -*- text -*- # # dictionary.Raritan # # version: $id$ # vendor raritan 8267 # # standa...
Page 210
Chapter 6: sx ii administration 203 command description parameters primaryradius access to configure the primary radius settings. ip - ip address secret - radius authentication secret authport - radius authentication port acctport - radius accounting port timeout - radius timeout (in secon...
Page 211
Chapter 6: sx ii administration 204 command description parameters secondarytacac s used to configure the secondary tacacs+ settings. ip - ip address secret - tacacs+ authentication secret port - tacacs+ port timeout - tacacs+ timeout (in seconds) retries - tacacs+ retries configure a mode...
Page 212
Chapter 6: sx ii administration 205 if needed, assign users to a group with modem access permissions. Modem access permission is assigned to a user group on the group page, and the user is then assigned to the group on the user page. For more information, see configure and manage users and user grou...
Page 213
Chapter 6: sx ii administration 206 command description parameters provided by dhcp or manually set tftp address - tftp server address autoconfigusb set/get automatic script via usb configuration. enable - enable (true), disable (false) enter admin > to access the menu. Command description param...
Page 214
Chapter 6: sx ii administration 207 command description parameters ethernetfailover used to enable and disable the ability to failover from one lan to another. enable - ethernet failover enable (true), disable (false) interface configure network settings for dual-lan failover. By default, dual lan...
Page 215
Chapter 6: sx ii administration 208 command description parameters staticrouteadd add a static route. dest - destination if - interface (lan1/lan2) prefix - ipv6 prefix length mask - ipv4 mask gateway - gateway mtu - mtu (64..65536) flags - flags (host/net) staticrouteshow show a list ...
Page 216
Chapter 6: sx ii administration 209 command description parameters telnet enable or disable telnet access. Due to the lack of security, the username, password and all traffic is in clear-text on the wire. Telnet must be enabled before it can be used; it is disabled by default. By default, the telnet...
Page 217
Chapter 6: sx ii administration 210 you can establish an anonymous direct port access connection via telnet by typing anonymous, or pressing enter at the username prompt. The anonymous connection is established without prompting for a password. When establishing a direct port access connection via s...
Page 218
Chapter 6: sx ii administration 211 command description parameters addv3 add trap recipients. A recipient is an ip address with an optional space- separated port number. Traps may be sent to multiple ports with the same ip address. dest - destination ip/hostname port - destination port name - ...
Page 219
Chapter 6: sx ii administration 212 command description parameters snmpv3agent configure an snmpv3 agent. enable - snmp v3 agent, enable (true), disable (false) name - security name authproto - snmp auth protocol authpass - snmp auth passphrase privproto - snmp privacy protocol privpass ...
Page 220
Chapter 6: sx ii administration 213 command description parameters timezonelist used to find the number code that corresponds to your time zone. Na ntp use this command if you are synchronizing sx ii with an ntp server. enable - enable or disable the use of ntp, enable (true), disable (false) pr...
Page 221
Chapter 6: sx ii administration 214 configure smtp events and notifications using cli note: this setting can also be configured from the remote console. See enable smtp notifications from the remote console (on page 131). Use the log > smtp menu to access to the options that can be used to configure...
Page 222
Chapter 6: sx ii administration 215 configure port logging settings using cli note: these settings can also be configured from the remote console. See configure port logging settings from the remote console (on page 146). As part of its security capabilities, sx ii logs data and to provide alerts ba...
Page 223
Chapter 6: sx ii administration 216 command description parameters eventdest event configuration. event - event index, use 'eventlist' to see index and current configurations audit - audit logging, enable (true), disable (false) snmp - snmp logging, enable (true), disable (false) syslog - sy...
Page 224
Chapter 6: sx ii administration 217 command description parameters nfsportlog configure the logging of port data. enable - logging of port data to remote nfs server, enable (true), disable (false) primaryip - primary portlog syslog server secondaryip - secondary portlog syslog server primary...
Page 225
Chapter 6: sx ii administration 218 command description parameters enable (true), disable (false) serialportlogdel delete serial port log file. port - ports to delete log of serialportlogview view serial port log file. port - ports to modify decrypt encrypted log on linux-based nfs server to dec...
Page 226
Chapter 6: sx ii administration 219 command description parameters keywordadd add a keyword to the port. port - single port or range of ports (1-n or 1,3,4 or * for all ports) keyword - when keyword is detected on target, notification is sent. Keyworddelete delete an existing keyword from the po...
Page 227
Chapter 6: sx ii administration 220 command description parameters example, config port 1 exitstring logout (execute logout on exit) config port 1 exitstring #0 (disable exit string for the port). The delay is the amount of time to wait after writing the command to the target. Number in seconds up t...
Page 228
Chapter 6: sx ii administration 221 command description parameters escapechar - escape character encoding - 8859-1/iso-8859-15/utf-8/shift-jis/euc- jp/euc-cn/euc-kr> - target encoding type telnet - tcp port assigned for dpa via telnet (1..65535) multiwrite - port set in multiple writer mode ...
Page 229
Chapter 6: sx ii administration 222 in both cases above, port 1 will have an ip assigned as 10.0.13.200, while port 2 will have 10.0.13.201, port 3 10.0.13.203, and so on. The following example configures dpa port settings for ssh and telnet by tcp port. Admin > config > port > config port 1 ssh 700...
Page 230
Chapter 6: sx ii administration 223 command description parameters (true), disable (false) auth - local user authentication: common-(local/ldap/radius/tacacs+); none- (no authentication) (common/none) ignorecc - ignore cc managed mode on local port, enable (true), disable (false) kbd - keyboar...
Page 231
Chapter 6: sx ii administration 224 command description parameters statement can be configured using the above command maintained on an external ftp site. (default 21) path - path to banner file to retrieve user - ftp username password - ftp password (prompted if missing) pcshare simultaneous ...
Page 232
Chapter 6: sx ii administration 225 command description parameters and examples iptables-save save ip tables (v4 and v6) to make firewall rules persistent. Na enter admin > security > loginsettings to access the menu and menu options. Command description parameters idletimeout specify the amount of ...
Page 233
Chapter 6: sx ii administration 226 command description parameters userblocking configure user lockout parameters. Mode - > set user blocking mode (disabled/timer_lockout/deactivate_userid) timerattempts - timer lockout attempts lockouttime - timer lockout time deactivateattempts - deactivate userid...
Page 234
Chapter 6: sx ii administration 227 command description parameters generatecsr generate certificate signing request. Bits - bit strength of certificate key name - common name (cn) country - 2 character iso country code (c) state - state/province (st) locality - locality/city (l) org - organization (...
Page 235
Chapter 6: sx ii administration 228 command description parameters viewcsrkey view the certificate signing request key. Na deletecsr delete the current certificate signing request. Na addressing security issues consider doing the following in order to enhance security for console servers. Sx ii supp...
Page 236
Chapter 6: sx ii administration 229 command description parameters deviceinfo provides information about the sx ii appliance such as build and so on. Na userlist displays a list of all users who are logged in, as well as their source ip addresses and any ports to which they are connected. Also found...
Page 237
Chapter 6: sx ii administration 230 command description parameters auditlogftp get the audit log and store on ftp server. address - address of ftp server port - port of ftp server (1..65535) path - ftp server path for audit log file. file - optional destination file name. Default: audit.Log ...
Page 238
Chapter 6: sx ii administration 231 command description parameters logoff log a user off sx ii (terminate their session). user - close all sessions for the specified user by name. session - close the session by identifier number or all sessions (id/all) port - close sessions on the specified p...
Page 239
Chapter 6: sx ii administration 232 command description parameters netif network interface info na netstat get network statistics type - stats interfaces route ping ping a remote system to ensure it is reachable. ip - ip address/hostname to ping if - network interface (default: auto) tracerout...
Page 240
Chapter 6: sx ii administration 233 command description parameters vflag - verbose flag (timestamp/module/thread/fileline) verbose - verbose control (on/off) viewstats view module status module - module name.
Page 241
234 sx ii provides the following options when connecting a px2 to a sx ii: • connect sx ii to the px2 serial port. In this configuration, access to the px2 is done through the px2 command line interface (cli). • connect the sx ii to the feature port on the px2. In this configuration, the px2 is mana...
Page 242
Chapter 7: connect a rack pdu to sx ii and configure power control options 235 3. Power on the px2 (if it is not already). The command line interface (cli) interface appears. Px appliance sx ii connecting the sx ii to the px2 feature port in this configuration, the px is managed from the sx ii inter...
Page 243
Chapter 7: connect a rack pdu to sx ii and configure power control options 236 you can now add the px as a managed power strip to the sx ii. See configure power strips from the remote console (on page 71) or configure power strips using cli (on page 196). Px appliance sx ii.
Page 244
237 in this chapter sx ii dimensions and physical specifications ...................................... 237 supported remote connections ........................................................... 237 supported number of ports and remote users per sx ii model .......... 238 maximum number of users s...
Page 245
Appendix a: specifications 238 • tcp/ip • http • https • radius • ldap/ldaps • ssh • telnet • tacacs+ • udp • sntp supported number of ports and remote users per sx ii model model number of ports sx2-04 and sx2-04m 4 sx2-08 and sx2-08m 8 sx2-16 and sx2-16m 16 sx2-32 and sx2-32m 32 sx2-48 and sx2-48m...
Page 246
Appendix a: specifications 239 protocol port communication direction http ports 80, 443 and 5000 must be open in the firewall for the appliance to operate. Port 80 this port can be configured as needed. See http and https port settings. By default, all requests received by the sx ii via http (port 8...
Page 247
Appendix a: specifications 240 protocol port communication direction radius port 1812 if sx ii is configured to remotely authenticate user logins via the radius protocol, port 1812 is used and must be open. However, but the system can also be configured to use any port of your designation. Optional ...
Page 248
Appendix a: specifications 241 you may have to open additional ports when nfs logging, using ldap servers, and so forth. These ports may vary from installation-to-installation depending on network topologies, virtual local area networks (vlans), and firewall configurations. Contact your network admi...
Page 249
Appendix a: specifications 242 dce mode on serve port pin 2 dsr input pin 3 rxd input pin 4 ground pin 5 ground pin 6 txd output pin 7 dtr output pin 8 rts output sx2 port ranges the port range for internal port configuration - csc, http, https, ssh, telnet, dpa ssh , dpa telnet - is 1 to 64510. The...
Page 250
Appendix a: specifications 243 sx ii network speed setting 10/full sx ii: 10/half switch: 10/full no communica tion no communica tion no communicat ion 10/full sx ii: 10/half switch: 10/full 10/half 10/half no communica tion no communica tion no communicat ion sx ii: 10/full switch: 10/half 10/half ...
Page 251
Appendix a: specifications 244 sx ii supported local port dvi resolutions following are the resolutions supported when connecting to a dvi monitor from the sx ii local port. • 1920x1080@60hz • 1280x720@60hz • 1024x768@60hz (default) • 1024x768@75hz • 1280x1024@60hz • 1280x1024@75hz • 1600x1200@60hz ...
Page 252
Appendix a: specifications 245 note: the target must be powered on in order for the sx ii port channel led to turn on and the sx ii to detect the target. • when you physically disconnect a target from a port on an sx ii, the port channel's led turns off. • when you log in to sx ii and connect to a t...
Page 253
246 in this chapter returning user group information ........................................................ 246 setting the registry to permit write operations to the schema ........... 247 creating a new attribute ....................................................................... 247 adding ...
Page 254
Appendix b: updating the ldap schema 247 setting the registry to permit write operations to the schema to allow a domain controller to write to the schema, you must set a registry entry that permits schema updates. To permit write operations to the schema: 1. Right-click the active directory ® schem...
Page 255
Appendix b: updating the ldap schema 248 3. Click new and then choose attribute. When the warning message appears, click continue and the create new attribute dialog appears. 4. Type rciusergroup in the common name field. 5. Type rciusergroup in the ldap display name field. 6. Type 1.3.6.1.4.1.13742...
Page 256
Appendix b: updating the ldap schema 249 2. Scroll to the user class in the right pane and right-click it. 3. Choose properties from the menu. The user properties dialog appears. 4. Click the attributes tab to open it. 5. Click add..
Page 257
Appendix b: updating the ldap schema 250 6. Choose rciusergroup from the select schema object list. 7. Click ok in the select schema object dialog. 8. Click ok in the user properties dialog. Updating the schema cache to update the schema cache: 1. Right-click active directory ® schema in the left pa...
Page 258
Appendix b: updating the ldap schema 251 3. Go to the directory where the support tools were installed. Run adsiedit.Msc. The adsi edit window opens. 4. Open the domain. 5. In the left pane of the window, select the cn=users folder..
Page 259
Appendix b: updating the ldap schema 252 6. Locate the user name whose properties you want to adjust in the right pane. Right-click the user name and select properties. 7. Click the attribute editor tab if it is not already open. Choose rciusergroup from the attributes list. 8. Click edit. The strin...
Page 260: Appendix C Faqs
253 dominion sx ii overview appendix c faqs.
Page 261
Appendix c: faqs 254 dominion sx ii overview what is the dominion sx ii? The dominion sx ii is raritan's next-generation serial console server that provides ip access and control of serial devices, anytime, anywhere. The new sx ii is the most powerful, secure, reliable, easy-to-use and manageable se...
Page 262
Appendix c: faqs 255 dominion sx ii overview continue software support for the current sx for two years from the end-of-sales announcement date; after that there will be no more firmware releases for the current sx. Commandcenter support will likely continue past the end-of- support date. Existing h...
Page 263
Appendix c: faqs 256 dominion sx ii hardware platform what are some of the hardware improvements? There are many: more powerful cpu, memory and flash space, dual power supplies (ac & dc), dual gigabit lan ports, port status led's, 4 usb ports, autosensing dte/dce ports, usb laptop access, dvi/usb ac...
Page 264
Appendix c: faqs 257 serial-over-ip sessions and access what types of serial access are available? The sx ii has the widest variety of serial access. This includes: ssh, telnet and web browser serial connections. Web browser access is available via the raritan serial client and through raritan comma...
Page 265
Appendix c: faqs 258 serial-over-ip sessions and access multiple sx ii's to another sx ii with straight cat5 cables. Second you can connect the dvi/usb local ports of the sx ii's to a kvm switch like the dominion kx iii. This can give you access to multiple sx ii's in and around the data center. Wha...
Page 266
Appendix c: faqs 259 connecting to serial devices what type of devices can the sx ii connect to? The sx ii can connect to a wide variety of serial devices including network routers, ethernet switches, firewalls, unix/linux servers, windows servers, virtual hosts, rack pdu's, ups systems and telecom/...
Page 267
Appendix c: faqs 260 installation, management & configuration.
Page 268
Appendix c: faqs 261 installation, management & configuration how do i initially configure the sx ii? Initial configuration can be done manually from the sx ii local console or automatically via usb stick or tftp server. Manual configuration can be done via cli by connecting your laptop via (1) usb ...
Page 269
Appendix c: faqs 262 security is the dominion sx ii secure? Yes, the dominion sx ii has rock-solid security with military grade security features such as 256 bit aes encryption with a fips 140-2 mode and encryption module. The sx ii has a long list of security features and each release is tested wit...
Page 270
Appendix c: faqs 263 user interface & documentation what type of web-based user interface does the dominion sx ii have? The dominion sx ii graphical user interface is similar to the other dominion products, providing a common look-and-feel across the dominion sx ii, kx, ksx and kx2-101-v2. In additi...
Page 271
264 in addition to raritan technical support and customer support, the following resources are available. In this chapter sx ii release notes and help ............................................................... 264 contact the documentation team with feedback ................................ 265...
Page 272
Appendix d: sx ii support 265 contact the documentation team with feedback contact the documentation directly with any questions or feedback related to the online help or user guides . Email us at documentation@raritan.Com, or directly from online help by doing one of the following - use the "send f...