- DL manuals
- SMC Networks
- Network Router
- 6752AL2 - annexe 1
- Management Manual
SMC Networks 6752AL2 - annexe 1 Management Manual
TigerSwitch 10/100
48-Port 10/100Mbps
Fast Ethernet Managed Switch
◆ 48 auto-MDI/MDI-X 10BASE-T/100BASE-TX ports
◆ 2 Gigabit RJ-45 ports shared with 2 SFP transceiver slots
◆ 2 Gigabit RJ-45 ports
◆ 17.8 Gbps of aggregate bandwidth
◆ Non-blocking switching architecture
◆ Spanning Tree Protocol and Rapid STP
◆ Up to four LACP or static 4-port trunks
◆ Layer 2/3/4 CoS support through four priority queues
◆ Full support for VLANs with GVRP
◆ IGMP multicast filtering and snooping
◆ Support for jumbo frames up to 9 KB
◆ Manageable via console, Web, SNMP, RMON
Management Guide
SMC6752AL2
Summary of 6752AL2 - annexe 1
Page 1
Tigerswitch 10/100 48-port 10/100mbps fast ethernet managed switch ◆ 48 auto-mdi/mdi-x 10base-t/100base-tx ports ◆ 2 gigabit rj-45 ports shared with 2 sfp transceiver slots ◆ 2 gigabit rj-45 ports ◆ 17.8 gbps of aggregate bandwidth ◆ non-blocking switching architecture ◆ spanning tree protocol and r...
Page 3: Tigerswitch 10/100
38 tesla irvine, ca 92618 phone: (949) 679-8000 tigerswitch 10/100 management guide from smc’s tiger line of feature-rich workgroup lan solutions november 2004 pub. # 149100005200h.
Page 4
Information furnished by smc networks, inc. (smc) is believed to be accu- rate and reliable. However, no responsibility is assumed by smc for its use, nor for any infringements of patents or other rights of third parties which may result from its use. No license is granted by implication or otherwis...
Page 5
I l imited w arranty limited warranty statement: smc networks, inc. (“smc”) warrants its products to be free from defects in workmanship and materials, under normal use and service, for the applicable warranty term. All smc products carry a standard 90-day limited warranty from the date of purchase ...
Page 6
L imited w arranty ii warranties exclusive: if an smc product does not operate as warranted above, customer’s sole remedy shall be repair or replacement of the product in question, at smc’s option. The foregoing warranties and remedies are exclusive and are in lieu of all other warranties or conditi...
Page 7
Iii c ontents 1 introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1-1 key features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1 description of software features . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Page 8
C ontents iv using dhcp/bootp . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-19 managing firmware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-21 downloading system software from a server . . . . . . . . . . 3-22 saving or restoring configuration settings . . . . . ...
Page 9
C ontents v configuring a standard ip acl . . . . . . . . . . . . . . . . . . . . . 3-80 configuring an extended ip acl . . . . . . . . . . . . . . . . . . . 3-82 configuring a mac acl . . . . . . . . . . . . . . . . . . . . . . . . . . 3-84 binding a port to an access control list . . . . . . . . ....
Page 10
C ontents vi configuring vlan behavior for interfaces . . . . . . . . . . 3-156 private vlans . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-159 displaying current private vlans . . . . . . . . . . . . . . . . . 3-160 configuring private vlans . . . . . . . . . . . . . ....
Page 11
C ontents vii getting help on commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5 showing commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6 partial keyword lookup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7 negating the effect o...
Page 12
C ontents viii user access commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-34 username . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-35 enable password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-36 ip filter commands...
Page 13
C ontents ix logging sendmail level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-69 logging sendmail source-email . . . . . . . . . . . . . . . . . . . . . . 4-70 logging sendmail destination-email . . . . . . . . . . . . . . . . . . 4-70 logging sendmail . . . . . . . . . . . . . . ....
Page 14
C ontents x show radius-server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-101 tacacs+ client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-102 tacacs-server host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-102 tacacs-server port . . . ...
Page 15
C ontents xi show map access-list mac . . . . . . . . . . . . . . . . . . . . . . . . . 4-134 acl information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-135 show access-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-135 show access-group . . . ....
Page 16
C ontents xii lacp port-priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-171 show lacp . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-172 address table commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Page 17
C ontents xiii displaying vlan information . . . . . . . . . . . . . . . . . . . . . . . . 4-207 show vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-207 configuring private vlans . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-208 private-vlan . . . . . . ...
Page 18: Glossary
C ontents xiv multicast filtering commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-236 igmp snooping commands . . . . . . . . . . . . . . . . . . . . . . . . . 4-236 ip igmp snooping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-237 ip igmp snooping vlan stati...
Page 19
Xv t ables table 1-1 key features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1 table 1-2 system defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7 table 3-1 configuration options . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4 ta...
Page 20
T ables xvi table 4-21 smtp alert commands . . . . . . . . . . . . . . . . . . . . . . . . . 4-68 table 4-22 time commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-72 table 4-23 system status commands . . . . . . . . . . . . . . . . . . . . . . . . 4-78 table 4-24 frame size c...
Page 21
T ables xvii table 4-58 priority commands (layer 2) . . . . . . . . . . . . . . . . . . . . 4-221 table 4-59 default cos priority levels . . . . . . . . . . . . . . . . . . . . . . 4-225 table 4-60 priority commands (layer 3 and 4) . . . . . . . . . . . . . . . 4-228 table 4-61 mapping ip precedence...
Page 22
T ables xviii.
Page 23
F igures xix f igures figure 3-1 home page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3 figure 3-2 panel display . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4 figure 3-3 system information . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Page 24
F igures xx figure 3-37 acl configuration - extended ip . . . . . . . . . . . . . . . . . 3-83 figure 3-38 acl configuration - mac . . . . . . . . . . . . . . . . . . . . . . . 3-85 figure 3-39 binding a port to an acl . . . . . . . . . . . . . . . . . . . . . . . . 3-86 figure 3-40 displaying port/...
Page 25
F igures xxi figure 3-74 queue mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-172 figure 3-75 configuring queue scheduling . . . . . . . . . . . . . . . . . . . 3-173 figure 3-76 ip precedence/dscp priority status . . . . . . . . . . . . . . 3-175 figure 3-77 mapping ip pre...
Page 26
F igures xxii.
Page 27: Key Features
1-1 c hapter 1 i ntroduction this switch provides a broad range of features for layer 2 switching. It includes a management agent that allows you to configure the features listed in this manual. The default configuration can be used for most of the features provided by this switch. However, there ar...
Page 28
I ntroduction 1-2 description of software features the switch provides a wide range of advanced performance enhancing features. Flow control eliminates the loss of packets due to bottlenecks caused by port saturation. Broadcast storm suppression prevents broadcast traffic storms from engulfing the n...
Page 29
D escription of s oftware f eatures 1-3 configuration backup and restore – you can save the current configuration settings to a file on a tftp server, and later download this file to restore the switch configuration settings. Authentication – this switch authenticates management access via the conso...
Page 30
I ntroduction 1-4 rate limiting – this feature controls the maximum rate for traffic transmitted or received on an interface. Rate limiting is configured on interfaces at the edge of a network to limit traffic into or out of the network. Traffic that falls within the rate limit is transmitted, while...
Page 31
D escription of s oftware f eatures 1-5 store-and-forward switching – the switch copies each frame into its memory before forwarding them to another port. This ensures that all frames are a standard ethernet size and have been verified for accuracy with the cyclic redundancy check (crc). This preven...
Page 32
I ntroduction 1-6 switch to restrict traffic to the vlan groups to which a user has been assigned. By segmenting your network into vlans, you can: • eliminate broadcast storms which severely degrade performance in a flat network. • simplify network management for node changes/moves by remotely confi...
Page 33: System Defaults
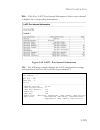
S ystem d efaults 1-7 system defaults the switch’s system defaults are provided in the configuration file “factory_default_config.Cfg.” to reset the switch defaults, this file should be set as the startup configuration file (page 3-23). The following table lists some of the basic system defaults. Ta...
Page 34
I ntroduction 1-8 web management http server enabled http port number 80 http secure server enabled http secure port number 443 snmp community strings “public” (read only) “private” (read/write) traps authentication traps: enabled link-up-down events: enabled port configuration admin status enabled ...
Page 35
S ystem d efaults 1-9 virtual lans default vlan 1 pvid 1 acceptable frame type all ingress filtering disabled switchport mode (egress mode) hybrid: tagged/untagged frames gvrp (global) disabled gvrp (port interface) disabled traffic prioritization ingress port priority 0 weighted round robin queue: ...
Page 36
I ntroduction 1-10
Page 37: Connecting to The Switch
2-1 c hapter 2 i nitial c onfiguration connecting to the switch configuration options the switch includes a built-in network management agent. The agent offers a variety of management options, including snmp, rmon (groups 1, 2, 3, 9) and a web-based interface. A pc may also be connected directly to ...
Page 38: Required Connections
I nitial c onfiguration 2-2 the switch’s web interface, cli configuration program, and snmp agent allow you to perform the following management functions: • set user names and passwords for up to 16 users • set an ip interface for a management vlan • configure snmp parameters • enable/disable any po...
Page 39
C onnecting to the s witch 2-3 attach a vt100-compatible terminal, or a pc running a terminal emulation program to the switch. You can use the console cable provided with this package, or use a null-modem cable that complies with the wiring assignments shown in the installation guide. To connect a t...
Page 40: Remote Connections
I nitial c onfiguration 2-4 for a description of how to use the cli, see “using the command line interface” on page 4-1. For a list of all the cli commands and detailed information on using the cli, refer to “command groups” on page 4-12. Remote connections prior to accessing the switch’s onboard ag...
Page 41: Basic Configuration
B asic c onfiguration 2-5 basic configuration console connection the cli program provides two different command levels — normal access level (normal exec) and privileged access level (privileged exec). The commands available at the normal exec level are a limited subset of those available at the pri...
Page 42: Setting An Ip Address
I nitial c onfiguration 2-6 2. Type “configure” and press . 3. Type “username guest password 0 password,” for the normal exec level, where password is your new password. Press . 4. Type “username admin password 0 password,” for the privileged exec level, where password is your new password. Press . ...
Page 43: Manual Configuration
B asic c onfiguration 2-7 manual configuration you can manually assign an ip address to the switch. You may also need to specify a default gateway that resides between this device and management stations that exist on another network segment. Valid ip addresses consist of four decimal numbers, 0 to ...
Page 44: Dynamic Configuration
I nitial c onfiguration 2-8 dynamic configuration if you select the “bootp” or “dhcp” option, ip will be enabled but will not function until a bootp or dhcp reply has been received. You therefore need to use the “ip dhcp restart” command to start broadcasting service requests. Requests will be sent ...
Page 45: Community Strings
B asic c onfiguration 2-9 6. Then save your configuration changes by typing “copy running-config startup-config.” enter the startup file name and press . Enabling snmp management access the switch can be configured to accept management commands from simple network management protocol (snmp) applicat...
Page 46: Trap Receivers
I nitial c onfiguration 2-10 the default strings are: • public - with read-only access. Authorized management stations are only able to retrieve mib objects. • private - with read-write access. Authorized management stations are able to both retrieve and modify mib objects. Note: if you do not inten...
Page 47
B asic c onfiguration 2-11 “community-string” is the string associated with that host. Press . 2. In order to configure the switch to send snmp notifications, you must enter at least one snmp-server enable traps command. Type “snmp-server enable traps type,” where “type” is either authentication or ...
Page 48: Managing System Files
I nitial c onfiguration 2-12 managing system files the switch’s flash memory supports three types of system files that can be managed by the cli program, web interface, or snmp. The switch’s file system allows files to be uploaded and downloaded, copied, deleted, and set as a start-up file. The thre...
Page 49: Using The Web Interface
3-1 c hapter 3 c onfiguring the s witch using the web interface this switch provides an embedded http web agent. Using a web browser you can configure the switch and view statistics to monitor network activity. The web agent can be accessed by any computer on the network using a standard web browser...
Page 50
C onfiguring the s witch 3-2 notes: 1. You are allowed three attempts to enter the correct password; on the third failed attempt the current connection is terminated. 2. If you log into the web interface as guest (normal exec level), you can view the configuration settings or change the guest passwo...
Page 51: Home Page
N avigating the w eb b rowser i nterface 3-3 navigating the web browser interface to access the web-browser interface you must first enter a user name and password. The administrator has read/write access to all configuration parameters and statistics. The default user name and password for the admi...
Page 52: Configuration Options
C onfiguring the s witch 3-4 configuration options configurable parameters have a dialog box or a drop-down list. Once a configuration change has been made on a page, be sure to click on the apply button to confirm the new setting. The following table summarizes the web page configuration buttons. N...
Page 53: Main Menu
M ain m enu 3-5 main menu using the onboard web agent, you can define system parameters, manage and control the switch, and all its ports, or monitor network conditions. The following table briefly describes the selections available from this program. Table 3-2 main menu menu description page system...
Page 54
C onfiguring the s witch 3-6 sntp 3-42 configuration configures sntp client settings, including broadcast mode or a specified list of servers 3-42 clock time zone sets the local time zone for the system clock 3-44 snmp 3-45 configuration configures community strings and related trap functions 3-45 s...
Page 55
M ain m enu 3-7 ip filter sets ip addresses of clients allowed management access via the web, snmp, and telnet 3-76 port 3-87 port information displays port connection status 3-87 trunk information displays trunk connection status 3-87 port configuration configures port connection settings 3-90 trun...
Page 56
C onfiguring the s witch 3-8 output port configuration sets the output rate limit for each port 3-113 output trunk configuration sets the output rate limit for each trunk 3-113 port statistics lists ethernet and rmon port statistics 3-114 address table 3-121 static addresses displays entries for int...
Page 57
M ain m enu 3-9 static membership by port configures membership type for interfaces, including tagged, untagged or forbidden 3-153 port configuration specifies default pvid and vlan attributes 3-155 trunk configuration specifies default trunk vid and vlan attributes 3-155 private vlan 3-158 informat...
Page 58
C onfiguring the s witch 3-10 queue scheduling configures weighted round robin queueing 3-173 ip precedence/ dscp priority status globally selects ip precedence or dscp priority, or disables both. 3-175 ip precedence priority sets ip type of service priority, mapping the precedence tag to a class-of...
Page 59: Basic Configuration
B asic c onfiguration 3-11 basic configuration displaying system information you can easily identify the system by displaying the device name, location and contact information. Field attributes • system name – name assigned to the switch system. • object id – mib ii object id for switch’s network ma...
Page 60
C onfiguring the s witch 3-12 web – click system, system information. Specify the system name, location, and contact information for the system administrator, then click apply. (this page also includes a telnet button that allows access to the command line interface via telnet.) figure 3-3 system in...
Page 61: Field Attributes
B asic c onfiguration 3-13 cli – specify the hostname, location and contact information. Displaying switch hardware/software versions use the switch information page to display hardware/firmware version numbers for the main board and management software, as well as the power status of the system. Fi...
Page 62
C onfiguring the s witch 3-14 management software • loader version – version number of loader code. • boot-rom version – version of power-on self-test (post) and boot code. • operation code version – version number of runtime code. • role – shows that this switch is operating as master or slave. Exp...
Page 63: Field Attributes
B asic c onfiguration 3-15 cli – use the following command to display version information. Displaying bridge extension capabilities the bridge mib includes extensions for managed devices that support multicast filtering, traffic classes, and virtual lans. You can access these extensions to display d...
Page 64
C onfiguring the s witch 3-16 • configurable pvid tagging – this switch allows you to override the default port vlan id (pvid used in frame tags) and egress status (vlan-tagged or untagged) on each port. (refer to “vlan configuration” on page 3-141.) • local vlan capable – this switch does not suppo...
Page 65: Command Attributes
B asic c onfiguration 3-17 cli – enter the following command. Setting the switch’s ip address this section describes how to configure an ip interface for management access over the network. The ip address for this switch is obtained via dhcp by default. To manually configure an address, you need to ...
Page 66: Manual Configuration
C onfiguring the s witch 3-18 requests will be broadcast periodically by the switch for an ip address. (dhcp/bootp values can include the ip address, subnet mask, and default gateway.) • ip address – address of the vlan interface that is allowed management access. Valid ip addresses consist of four ...
Page 67: Using Dhcp/bootp
B asic c onfiguration 3-19 cli – specify the management interface, ip address and default gateway. Using dhcp/bootp if your network provides dhcp/bootp services, you can configure the switch to be dynamically configured by these services. Web – click system, ip configuration. Specify the vlan to whi...
Page 68
C onfiguring the s witch 3-20 cli – specify the management interface, and set the ip address mode to dhcp or bootp, and then enter the “ip dhcp restart” command. Renewing dchp – dhcp may lease addresses to clients indefinitely or for a specific period of time. If the address expires or the switch is...
Page 69: Managing Firmware
B asic c onfiguration 3-21 managing firmware you can upload/download firmware to or from a tftp server, or copy files to and from switch units in a stack. By saving runtime code to a file on a tftp server, that file can later be downloaded to the switch to restore operation. You can also set the swi...
Page 70
C onfiguring the s witch 3-22 downloading system software from a server when downloading runtime code, you can specify the destination file name to replace the current image, or first download the file using a different name from the current runtime code file, and then set the new file as the startu...
Page 71
B asic c onfiguration 3-23 if you download to a new destination file, go to the system/file/set start-up menu, mark the operation code file used at startup, and click apply. To start the new firmware, reboot the system via the system/reset menu. Figure 3-9 select start-up operation file to delete a ...
Page 72: Command Attributes
C onfiguring the s witch 3-24 cli – to download new firmware form a tftp server, enter the ip address of the tftp server, select “opcode” as the file type, then enter the source and destination file names. When the file has finished downloading, set the new file to start up the system, and then rest...
Page 73
B asic c onfiguration 3-25 - running-config to tftp– copies the running configuration to a tftp server. - startup-config to file– copies the startup configuration to a file on the switch. - startup-config to running-config– copies the startup config to the running config. - startup-config to tftp– c...
Page 74
C onfiguring the s witch 3-26 downloading configuration settings from a server you can download the configuration file under a new file name and then set it as the startup file, or you can specify the current startup configuration file as the destination file to directly replace it. Note that the fi...
Page 75
B asic c onfiguration 3-27 if you download to a new file name using “tftp to startup-config” or “tftp to file,” the file is automatically set as the start-up configuration file. To use the new settings, reboot the system via the system/reset menu. Note that you can also select any configuration file...
Page 76: Console Port Settings
C onfiguring the s witch 3-28 console port settings you can access the onboard configuration program by attaching a vt100 compatible device to the switch’s serial console port. Management access through the console port is controlled by various parameters, including a password, timeouts, and basic c...
Page 77
B asic c onfiguration 3-29 • speed – sets the terminal line’s baud rate for transmit (to terminal) and receive (from terminal). Set the speed to match the baud rate of the device connected to the serial port. (range: 9600, 19200, 38400, 57600, or 115200 baud; default: 9600 bps) • stop bits – sets th...
Page 78: Telnet Settings
C onfiguring the s witch 3-30 cli – enter line configuration mode for the console, then specify the connection parameters as required. To display the current console port settings, use the show line command from the normal exec level. Telnet settings you can access the onboard configuration program ...
Page 79
B asic c onfiguration 3-31 • login timeout – sets the interval that the system waits for a user to log into the cli. If a login attempt is not detected within the timeout interval, the connection is terminated for the session. (range: 0-300 seconds; default: 300 seconds) • exec timeout – sets the in...
Page 80
C onfiguring the s witch 3-32 web – click system, line, telnet. Specify the connection parameters for telnet access, then click apply. Figure 3-14 enabling telnet cli – enter line configuration mode for a virtual terminal, then specify the connection parameters as required. To display the current vi...
Page 81: Configuring Event Logging
B asic c onfiguration 3-33 configuring event logging the switch allows you to control the logging of error messages, including the type of events that are recorded in switch memory, logging to a remote system log (syslog) server, and displays a list of recent event messages. System log configuration...
Page 82
C onfiguring the s witch 3-34 • ram level – limits log messages saved to the switch’s temporary ram memory for all levels up to the specified level. For example, if level 7 is specified, all messages from level 0 to level 7 will be logged to ram. (range: 0-7, default: 6) note: the flash level must b...
Page 83: Remote Log Configuration
B asic c onfiguration 3-35 web – click system, log, system logs. Specify system log status, set the level of event messages to be logged to ram and flash memory, then click apply. Figure 3-15 system logs cli – enable system logging and then specify the level of messages to be logged to ram and flash...
Page 84: Command Attributes
C onfiguring the s witch 3-36 command attributes • remote log status – enables/disables the logging of debug or error messages to the remote logging process. (default: enabled) • logging facility – sets the facility type for remote logging of syslog messages. There are eight facility types specified...
Page 85
B asic c onfiguration 3-37 web – click system, log, remote logs. To add an ip address to the host ip list, type the new ip address in the host ip address box, and then click add. To delete an ip address, click the entry in the host ip list, and then click remove. Figure 3-16 remote logs cli – enter ...
Page 86: Displaying Log Messages
C onfiguring the s witch 3-38 displaying log messages the logs page allows you to scroll through the logged system and event messages. The switch can store up to 2048 log entries in temporary random access memory (ram; i.E., memory flushed on power reset) and up to 4096 entries in permanent flash me...
Page 87: Command Attributes
B asic c onfiguration 3-39 sending simple mail transfer protocol alerts to alert system administrators of problems, the switch can use smtp (simple mail transfer protocol) to send email messages when triggered by logging events of a specified level. The messages are sent to specified smtp servers on...
Page 88
C onfiguring the s witch 3-40 web – click system, log, smtp. Enable smtp, specify a source email address, and select the minimum severity level. To add an ip address to the smtp server list, type the new ip address in the smtp server field and click add. To delete an ip address, click the entry in t...
Page 89: Resetting The System
B asic c onfiguration 3-41 cli – enter the ip address of at least one smtp server, set the syslog severity level to trigger an email message, and specify the switch (source) and up to five recipient (destination) email addresses. Enable smtp with the logging sendmail command to complete the configur...
Page 90: Setting The System Clock
C onfiguring the s witch 3-42 cli – use the reload command to restart the switch. When prompted, confirm that you want to reset the switch. Note: when restarting the system, it will always run the power-on self-test. Setting the system clock simple network time protocol (sntp) allows the switch to s...
Page 91
B asic c onfiguration 3-43 • sntp server –sets the ip address for up to three time servers. The switch attempts to update the time from the first server, if this fails it attempts an update from the next server in the sequence. Web – select sntp, configuration. Modify any of the required parameters,...
Page 92: Setting The Time Zone
C onfiguring the s witch 3-44 setting the time zone sntp uses coordinated universal time (or utc, formerly greenwich mean time, or gmt) based on the time at the earth’s prime meridian, zero degrees longitude. To display a time corresponding to your local time, you must indicate the number of hours a...
Page 93: Command Attributes
S imple n etwork m anagement p rotocol 3-45 simple network management protocol simple network management protocol (snmp) is a communication protocol designed specifically for managing devices on a network. Equipment commonly managed with snmp includes switches, routers and host computers. Snmp is ty...
Page 94
C onfiguring the s witch 3-46 • access mode - read-only – specifies read-only access. Authorized management stations are only able to retrieve mib objects. - read/write – specifies read-write access. Authorized management stations are able to both retrieve and modify mib objects. Web – click snmp, c...
Page 95: Command Attributes
S imple n etwork m anagement p rotocol 3-47 command attributes • trap manager capability – this switch supports up to five trap managers. • current – displays a list of the trap managers currently configured. • trap manager ip address – ip address of the host (the targeted recipient). • trap manager...
Page 96: User Authentication
C onfiguring the s witch 3-48 cli – this example adds a trap manager and enables both authentication and link-up, link-down traps. User authentication you can restrict management access to this switch using the following options: • user accounts – manually configure access rights on the switch for s...
Page 97: Command Attributes
U ser a uthentication 3-49 command attributes • account list – displays the current list of user accounts and associated access levels. (defaults: admin, and guest) • new account – displays configuration settings for a new account. - user name – the name of the user. (maximum length: 8 characters; m...
Page 98
C onfiguring the s witch 3-50 cli – assign a user name to access-level 15 (i.E., administrator), then specify the password. Configuring local/remote logon authentication use the authentication settings menu to restrict management access based on specified user names and passwords. You can manually c...
Page 99: Command Usage
U ser a uthentication 3-51 command usage • by default, management access is always checked against the authentication database stored on the local switch. If a remote authentication server is used, you must specify the authentication sequence and the corresponding parameters for the remote authentic...
Page 100
C onfiguring the s witch 3-52 • radius settings - global – provides globally applicable radius settings. - serverindex – specifies one of five radius servers that may be configured. The switch attempts authentication using the listed sequence of servers. The process ends when a server either approve...
Page 101
U ser a uthentication 3-53 web – click security, authentication settings. To configure local or remote authentication preferences, specify the authentication sequence (i.E., one to three methods), fill in the parameters for radius or tacacs+ authentication if selected, and click apply. Figure 3-25 a...
Page 102: Configuring Https
C onfiguring the s witch 3-54 cli – specify all the required parameters to enable logon authentication. Configuring https you can configure the switch to enable the secure hypertext transfer protocol (https) over the secure socket layer (ssl), providing secure access (i.E., an encrypted connection) ...
Page 103: Command Attributes
U ser a uthentication 3-55 • if you enable https, you must indicate this in the url that you specify in your browser: https://device[:port_number] • when you start https, the connection is established in this way: - the client authenticates the server using the server’s digital certificate. - the cl...
Page 104
C onfiguring the s witch 3-56 web – click security, https settings. Enable https and specify the port number, then click apply. Figure 3-26 https settings cli – this example enables the http secure server and modifies the port number. Replacing the default secure-site certificate when you log onto t...
Page 105
U ser a uthentication 3-57 when you have obtained these, place them on your tftp server, and use the following command at the switch's command-line interface to replace the default (unrecognized) certificate with an authorized one: note: the switch must be reset for the new certificate to be activat...
Page 106: Command Usage
C onfiguring the s witch 3-58 command usage the ssh server on this switch supports both password and public key authentication. If password authentication is specified by the ssh client, then the password can be authenticated either locally or via a radius or tacacs+ remote authentication server, as...
Page 107
U ser a uthentication 3-59 3. Import client’s public key to the switch – use the copy tftp public-key command (page 4-87) to copy a file containing the public key for all the ssh client’s granted management access to the switch. (note that these clients must be configured locally on the switch via t...
Page 108: Field Attributes
C onfiguring the s witch 3-60 e. The switch compares the decrypted bytes to the original bytes it sent. If the two sets match, this means that the client's private key corresponds to an authorized public key, and the client is authenticated. Notes: 1. To use ssh with only password authentication, th...
Page 109
U ser a uthentication 3-61 • host-key type – the key type used to generate the host key pair (i.E., public and private keys). (range: rsa (version 1), dsa (version 2), both; default: rsa) the ssh server uses rsa or dsa for key exchange when the client first establishes a connection with the switch, ...
Page 110
C onfiguring the s witch 3-62 web – click security, ssh, host-key settings. Select the host-key type from the drop-down box, select the option to save the host key from memory to flash (if required) prior to generating the key, and then click generate. Figure 3-27 ssh host-key settings.
Page 111: Configuring The Ssh Server
U ser a uthentication 3-63 cli – this example generates a host-key pair using both the rsa and dsa algorithms, stores the keys to flash memory, and then displays the host’s public keys. Configuring the ssh server the ssh server includes basic settings for authentication. Field attributes • ssh serve...
Page 112
C onfiguring the s witch 3-64 • ssh authentication retries – specifies the number of authentication attempts that a client is allowed before authentication fails and the client has to restart the authentication process. (range: 1-5 times; default: 3) • ssh server-key size – specifies the ssh server ...
Page 113: Configuring Port Security
U ser a uthentication 3-65 cli – this example enables ssh, sets the authentication parameters, and displays the current configuration. It shows that the administrator has made a connection via shh, and then disables this connection. Configuring port security port security is a feature that allows yo...
Page 114: Command Usage
C onfiguring the s witch 3-66 already in the address table will be retained and will not age out. Any other device that attempts to use the port will be prevented from accessing the switch. Command usage • a secure port has the following restrictions: - it cannot use port monitoring. - it cannot be ...
Page 115
U ser a uthentication 3-67 web – click security, port security. Set the action to take when an invalid address is detected on a port, mark the checkbox in the status column to enable security for a port, set the maximum number of mac addresses allowed on a port, and click apply. Figure 3-29 configur...
Page 116
C onfiguring the s witch 3-68 this switch uses the extensible authentication protocol over lans (eapol) to exchange authentication protocol messages with the client, and a remote radius authentication server to verify user identity and access rights. When a client (i.E., supplicant) connects to a sw...
Page 117: Command Attributes
U ser a uthentication 3-69 • the radius server and 802.1x client support eap. (the switch only supports eapol in order to pass the eap packets from the server to the client.) • the radius server and client also have to support the same eap authentication type – md5. (some clients have native support...
Page 118: Command Attributes
C onfiguring the s witch 3-70 cli – this example shows the default global setting for 802.1x. Configuring 802.1x global settings the 802.1x protocol includes port authentication. The 802.1x protocol must be enabled globally for the switch system before port settings are active. Command attributes • ...
Page 119: Command Attributes
U ser a uthentication 3-71 configuring port settings for 802.1x when 802.1x is enabled, you need to configure the parameters for the authentication process that runs between the client and the switch (i.E., authenticator), as well as the client identity lookup process that runs between the switch an...
Page 120
C onfiguring the s witch 3-72 • quiet period – sets the time that a switch port waits after the max request count has been exceeded before attempting to acquire a new client. (range: 1-65535 seconds; default: 60) • re-authen period – sets the time period after which a connected client must be re-aut...
Page 121
U ser a uthentication 3-73 cli – this example sets the 802.1x parameters on port 2. For a description of the additional fields displayed in this example, see “show dot1x” on page 4-114. Console(config)#interface ethernet 1/2 4-145 console(config-if)#dot1x port-control auto 4-109 console(config-if)#d...
Page 122
C onfiguring the s witch 3-74 displaying 802.1x statistics this switch can display statistics for dot1x protocol exchanges for any port. Table 3-5 802.1x statistics parameter description rx eapol start the number of eapol start frames that have been received by this authenticator. Rx eapol logoff th...
Page 123
U ser a uthentication 3-75 web – select security, 802.1x, statistics. Select the required port and then click query. Click refresh to update the statistics. Figure 3-33 displaying 802.1x port statistics cli – this example displays the 802.1x statistics for port 4. Console#show dot1x statistics inter...
Page 124: Command Usage
C onfiguring the s witch 3-76 filtering addresses for management access you create a list of up to 16 ip addresses or ip address groups that are allowed management access to the switch through the web interface, snmp, or telnet. Command usage • the management interfaces are open to all ip addresses ...
Page 125
U ser a uthentication 3-77 • end ip address – the end address of a range. • add/remove filtering entry – adds/removes an ip address from the list. Web – click security, ip filter. Enter the ip addresses or range of addresses that are allowed management access to an interface, and click add ip filter...
Page 126: Access Control Lists
C onfiguring the s witch 3-78 cli – this example allows snmp access for a specific client. Access control lists access control lists (acl) provide packet filtering for ip frames (based on address, protocol, layer 4 protocol port number or tcp control code) or any frames (based on mac address or ethe...
Page 127: Command Usage
A ccess c ontrol l ists 3-79 command usage the following restrictions apply to acls: • each acl can have up to 32 rules. • the maximum number of acls is 88. • however, due to resource restrictions, the average number of rules bound to the ports should not exceed 20. • this switch supports acls for i...
Page 128: Command Attributes
C onfiguring the s witch 3-80 - mac: mac acl mode that filters packets based on the source or destination mac address and the ethernet frame type (rfc 1060). Web – click security, acl, configuration. Enter an acl name in the name field, select the list type (ip standard, ip extended, or mac), and cl...
Page 129
A ccess c ontrol l ists 3-81 • subnet mask – a subnet mask containing four integers from 0 to 255, each separated by a period. The mask uses 1 bits to indicate “match” and 0 bits to indicate “ignore.” the mask is bitwise anded with the specified source ip address, and compared with the address for e...
Page 130: Command Attributes
C onfiguring the s witch 3-82 configuring an extended ip acl command attributes • action – an acl can contain any combination of permit or deny rules. • source/destination address type – specifies the source or destination ip address. Use “any” to include all possible addresses, “host” to specify a ...
Page 131
A ccess c ontrol l ists 3-83 - 4 (rst) – reset - 8 (psh) – push - 16 (ack) – acknowledgement - 32 (urg) – urgent pointer for example, use the code value and mask below to catch packets with the following flags set: - syn flag valid, use control-code 2, control bitmask 2 - both syn and ack valid, use...
Page 132: Configuring A Mac Acl
C onfiguring the s witch 3-84 cli – this example adds two rules: 1. Accept any incoming packets if the source address is in subnet 10.7.1.X. For example, if the rule is matched; i.E., the rule (10.7.1.0 & 255.255.255.0) equals the masked address (10.7.1.2 & 255.255.255.0), the packet passes through....
Page 133
A ccess c ontrol l ists 3-85 • ethernet type – this option can only be used to filter ethernet ii formatted packets. (range: 0-65535) a detailed listing of ethernet protocol types can be found in rfc 1060. A few of the more common types include 0800 (ip), 0806 (arp), 8137 (ipx). Web – specify the ac...
Page 134: Command Usage
C onfiguring the s witch 3-86 binding a port to an access control list after configuring access control lists (acl), you should bind them to the ports that need to filter traffic. You can assign one ip access list to any port, but you can only assign one mac access list to all the ports on the switc...
Page 135: Port Configuration
P ort c onfiguration 3-87 cli – this example assigns an ip and mac access list to port 1, and an ip access list to port 3. Port configuration displaying connection status you can use the port information or trunk information pages to display the current connection status, including link state, speed...
Page 136: Field Attributes (Cli)
C onfiguring the s witch 3-88 web – click port, port information or trunk information. Figure 3-40 displaying port/trunk information field attributes (cli) basic information: • port type – indicates the port type. (100base-tx, 1000base-t, or sfp) • mac address – the physical layer address for this p...
Page 137
P ort c onfiguration 3-89 • capabilities – specifies the capabilities to be advertised for a port during auto-negotiation. (to access this item on the web, see “configuring interface connections” on page 3-48.) the following capabilities are supported. - 10half - supports 10 mbps half-duplex operati...
Page 138: Command Attributes
C onfiguring the s witch 3-90 cli – this example shows the connection status for port 5. Configuring interface connections you can use the port configuration or trunk configuration page to enable/disable an interface, set auto-negotiation and the interface capabilities to advertise, or manually fix ...
Page 139
P ort c onfiguration 3-91 • autonegotiation (port capabilities)– allows auto-negotiation to be enabled/disabled. When auto-negotiation is enabled, you need to specify the capabilities to be advertised. When auto-negotiation is disabled, you can force the settings for speed, mode, and flow control.Th...
Page 140: Creating Trunk Groups
C onfiguring the s witch 3-92 web – click port, port configuration or trunk configuration. Modify the required interface settings, and click apply. Figure 3-41 port/trunk configuration cli – select the interface, and then enter the required settings. Creating trunk groups you can create multiple lin...
Page 141: Command Usage
P ort c onfiguration 3-93 automatically negotiate a trunked link with lacp-configured ports on another device. You can configure any number of ports on the switch as lacp, as long as they are not already configured as part of a static trunk. If ports on another device are also configured as lacp, th...
Page 142: Command Usage
C onfiguring the s witch 3-94 statically configuring a trunk command usage • when configuring static trunks, you may not be able to link switches of different types, depending on the manufacturer’s implementation. However, note that the static trunks on this switch are cisco etherchannel compatible....
Page 143
P ort c onfiguration 3-95 web – click port, trunk membership. Enter a trunk id of 1-4 in the trunk field, select any of the switch ports from the scroll-down port list, and click add. After you have completed adding ports to the member list, click apply. Figure 3-42 static trunk configuration.
Page 144: Command Usage
C onfiguring the s witch 3-96 cli – this example creates trunk 2 with ports 1 and 2. Just connect these ports to two static trunk ports on another switch to form a trunk. Enabling lacp on selected ports command usage • to avoid creating a loop in the network, be sure you enable lacp before connectin...
Page 145: Command Attributes
P ort c onfiguration 3-97 • a trunk formed with another switch using lacp will automatically be assigned the next available trunk id. • if more than four ports attached to the same target switch have lacp enabled, the additional ports will be placed in standby mode, and will only be enabled if one o...
Page 146: Configuring Lacp Parameters
C onfiguring the s witch 3-98 cli – the following example enables lacp for ports 1 to 6. Just connect these ports to lacp-enabled trunk ports on another switch to form a trunk. Configuring lacp parameters dynamically creating a port channel – ports assigned to a common port channel must meet the fol...
Page 147: Command Attributes
P ort c onfiguration 3-99 note: if the port channel admin key (lacp admin key, page 4-171) is not set (through the cli) when a channel group is formed (i.E., it has a null value of 0), this key is set to the same value as the port admin key used by the interfaces that joined the group (lacp admin ke...
Page 148
C onfiguring the s witch 3-100 web – click port, lacp, aggregation port. Set the system priority, admin key, and port priority for the port actor. You can optionally configure these settings for the port partner. (be aware that these settings only affect the administrative state of the partner, and ...
Page 149
P ort c onfiguration 3-101 cli – the following example configures lacp parameters for ports 1-4. Ports 1-4 are used as active members of the lag. Console(config)#interface ethernet 1/1 4-145 console(config-if)#lacp actor system-priority 3 4-169 console(config-if)#lacp actor admin-key 120 4-170 conso...
Page 150
C onfiguring the s witch 3-102 displaying lacp port counters you can display statistics for lacp protocol messages. Web – click port, lacp, port counters information. Select a member port to display the corresponding information. Figure 3-45 lacp - port counters information table 3-6 lacp port count...
Page 151
P ort c onfiguration 3-103 cli – the following example displays lacp counters. Displaying lacp settings and status for the local side you can display configuration settings and the operational state for the local side of an link aggregation. Console#show lacp counters 4-173 port channel : 1 --------...
Page 152
C onfiguring the s witch 3-104 lacp port priority lacp port priority assigned to this interface within the channel group. Admin state, oper state administrative or operational values of the actor’s state parameters: • expired – the actor’s receive machine is in the expired state; • defaulted – the a...
Page 153
P ort c onfiguration 3-105 web – click port, lacp, port internal information. Select a port channel to display the corresponding information. Figure 3-46 lacp - port internal information cli – the following example displays the lacp configuration settings and operational state for the local side of ...
Page 154
C onfiguring the s witch 3-106 displaying lacp settings and status for the remote side you can display configuration settings and the operational state for the remote side of an link aggregation. Table 3-8 lacp neighbor configuration information field description partner admin system id lag partner’...
Page 155
P ort c onfiguration 3-107 web – click port, lacp, port neighbors information. Select a port channel to display the corresponding information. Figure 3-47 lacp - port neighbors information cli – the following example displays the lacp configuration settings and operational state for the remote side ...
Page 156: Command Usage
C onfiguring the s witch 3-108 setting broadcast storm thresholds broadcast storms may occur when a device on your network is malfunctioning, or if application programs are not well designed or properly configured. If there is too much broadcast traffic on your network, performance can be severely d...
Page 157
P ort c onfiguration 3-109 web – click port, port/trunk broadcast control. Set the threshold, mark the enabled field for the desired interface and click apply. Figure 3-48 port broadcast control.
Page 158: Configuring Port Mirroring
C onfiguring the s witch 3-110 cli – specify any interface, and then enter the threshold. The following disables broadcast storm control for port 1, and then sets broadcast suppression at 600 octets per second for port 2 (which applies to all ports). Configuring port mirroring you can mirror traffic...
Page 159: Command Attributes
P ort c onfiguration 3-111 command attributes • mirror sessions – displays a list of current mirror sessions. • source unit –the unit whose port traffic will be monitored. • source port – the port whose traffic will be monitored. • type – allows you to select which traffic to mirror to the target po...
Page 160: Configuring Rate Limits
C onfiguring the s witch 3-112 configuring rate limits this function allows the network manager to control the maximum rate for traffic transmitted or received on a port. Rate limiting is configured on ports at the edge of a network to limit traffic coming into or out of the network. Traffic that fa...
Page 161: Rate Limit Configuration
P ort c onfiguration 3-113 cli - this example sets and displays fast ethernet and gigabit ethernet granularity. Rate limit configuration use the rate limit configuration pages to apply rate limiting. Command usage • input and output rate limit can be enabled or disabled for individual interfaces. Co...
Page 162: Showing Port Statistics
C onfiguring the s witch 3-114 web – click port, rate limit, input/output port/trunk configuration. Enable the rate limit status for the required interfaces, set the rate limit level, and click apply. Figure 3-51 output rate limit port configuration cli - this example sets the rate limit level for i...
Page 163
P ort c onfiguration 3-115 note: rmon groups 2, 3 and 9 can only be accessed using snmp management software such as smc eliteview. Table 3-9 port statistics parameter description interface statistics received octets the total number of octets received on the interface, including framing characters. ...
Page 164
C onfiguring the s witch 3-116 transmit multicast packets the total number of packets that higher-level protocols requested be transmitted, and which were addressed to a multicast address at this sub-layer, including those that were discarded or not sent. Transmit broadcast packets the total number ...
Page 165
P ort c onfiguration 3-117 multiple collision frames a count of successfully transmitted frames for which transmission is inhibited by more than one collision. Carrier sense errors the number of times that the carrier sense condition was lost or never asserted when attempting to transmit a frame. Sq...
Page 166
C onfiguring the s witch 3-118 multicast frames the total number of good frames received that were directed to this multicast address. Crc/alignment errors the number of crc/alignment errors (fcs or alignment errors). Undersize frames the total number of frames received that were less than 64 octets...
Page 167
P ort c onfiguration 3-119 web – click port, port statistics. Select the required interface, and click query. You can also use the refresh button at the bottom of the page to update the screen. Figure 3-52 port statistics.
Page 168
C onfiguring the s witch 3-120 cli – this example shows statistics for port 13. Console#show interfaces counters ethernet 1/13 4-154 ethernet 1/13 iftable stats: octets input: 868453, octets output: 3492122 unicast input: 7315, unitcast output: 6658 discard input: 0, discard output: 0 error input: 0...
Page 169: Address Table Settings
A ddress t able s ettings 3-121 address table settings switches store the addresses for all known devices. This information is used to pass traffic directly between the inbound and outbound ports. All the addresses learned by monitoring traffic are stored in the dynamic address table. You can also m...
Page 170: Displaying The Address Table
C onfiguring the s witch 3-122 web – click address table, static addresses. Specify the interface, the mac address and vlan, then click add static address. Figure 3-53 configuring a static address table cli – this example adds an address to the static address table, but sets it to be deleted when th...
Page 171
A ddress t able s ettings 3-123 • vlan – id of configured vlan (1-4094). • address table sort key – you can sort the information displayed based on mac address, vlan or interface (port or trunk). • dynamic address counts – the number of addresses dynamically learned. • current dynamic address table ...
Page 172: Changing The Aging Time
C onfiguring the s witch 3-124 changing the aging time you can set the aging time for entries in the dynamic address table. Command attributes • aging status – enables/disables the function. • aging time – the time after which a learned entry is discarded. (range: 10-30000 seconds; default: 300) web...
Page 173
S panning t ree a lgorithm c onfiguration 3-125 the spanning tree algorithms supported by this switch include these versions: • stp – spanning tree protocol (ieee 802.1d) • rstp – rapid spanning tree protocol (ieee 802.1w) sta uses a distributed algorithm to select a bridging device (sta-compliant s...
Page 174: Displaying Global Settings
C onfiguring the s witch 3-126 that can be used when a node or port fails, and retaining the forwarding database for ports insensitive to changes in the tree structure when reconfiguration occurs. Displaying global settings you can display a summary of the current bridge sta information that applies...
Page 175
S panning t ree a lgorithm c onfiguration 3-127 • designated root – the priority and mac address of the device in the spanning tree that this switch has accepted as the root device. - root port – the number of the port on this switch that is closest to the root. This switch communicates with the roo...
Page 176
C onfiguring the s witch 3-128 • root forward delay – the maximum time (in seconds) this device will wait before changing states (i.E., discarding to learning to forwarding). This delay is required because every device must receive information about topology changes before it starts to forward frame...
Page 177
S panning t ree a lgorithm c onfiguration 3-129 cli – this command displays global sta settings, followed by settings for each port. Note: the current root port and current root cost display as zero when this device is not connected to the network. Console#show spanning-tree 4-196 spanning-tree info...
Page 178: Configuring Global Settings
C onfiguring the s witch 3-130 configuring global settings global settings apply to the entire switch. Command usage • spanning tree protocol 10 uses rstp for the internal state machine, but sends only 802.1d bpdus. • rapid spanning tree protocol 10 rstp supports connections to either stp or rstp no...
Page 179
S panning t ree a lgorithm c onfiguration 3-131 • priority – bridge priority is used in selecting the root device, root port, and designated port. The device with the highest priority becomes the sta root device. However, if all devices have the same priority, the device with the lowest mac address ...
Page 180
C onfiguring the s witch 3-132 • forward delay – the maximum time (in seconds) this device will wait before changing states (i.E., discarding to learning to forwarding). This delay is required because every device must receive information about topology changes before it starts to forward frames. In...
Page 181
S panning t ree a lgorithm c onfiguration 3-133 web – click spanning tree, sta, configuration. Modify the required attributes, and click apply. Figure 3-57 sta configuration cli – this example enables spanning tree protocol, sets the mode to rstp, and then configures the sta and rstp parameters. Con...
Page 182: Field Attributes
C onfiguring the s witch 3-134 displaying interface settings the sta port information and sta trunk information pages display the current status of ports and trunks in the spanning tree. Field attributes • spanning tree – shows if sta has been enabled on this interface. • sta status – displays curre...
Page 183
S panning t ree a lgorithm c onfiguration 3-135 • designated bridge – the bridge priority and mac address of the device through which this port must communicate to reach the root of the spanning tree. • designated port – the port priority and number of the port on the designated bridging device thro...
Page 184
C onfiguring the s witch 3-136 • trunk member – indicates if a port is a member of a trunk. (sta port information only) these additional parameters are only displayed for the cli: • admin status – shows if this interface is enabled. • path cost – this parameter is used by the sta to determine the be...
Page 185
S panning t ree a lgorithm c onfiguration 3-137 • admin edge port – you can enable this option if an interface is attached to a lan segment that is at the end of a bridged lan or to an end node. Since end nodes cannot cause forwarding loops, they can pass directly through to the spanning tree forwar...
Page 186: Command Attributes
C onfiguring the s witch 3-138 cli – this example shows the sta attributes for port 5. Configuring interface settings you can configure rstp attributes for specific interfaces, including port priority, path cost, link type, and edge port. You may use a different priority or path cost for ports of th...
Page 187
S panning t ree a lgorithm c onfiguration 3-139 - learning - port has transmitted configuration messages for an interval set by the forward delay parameter without receiving contradictory information. Port address table is cleared, and the port begins learning addresses. - forwarding - port forwards...
Page 188
C onfiguring the s witch 3-140 -default: - ethernet – half duplex: 2,000,000; full duplex: 1,000,000; trunk: 500,000 - fast ethernet – half duplex: 200,000; full duplex: 100,000; trunk: 50,000 - gigabit ethernet – full duplex: 10,000; trunk: 5,000 • admin link type – the link type attached to this i...
Page 189: Vlan Configuration
Vlan c onfiguration 3-141 web – click spanning tree, sta, port configuration or trunk configuration. Modify the required attributes, then click apply. Figure 3-59 sta port configuration cli – this example sets sta attributes for port 7. Vlan configuration ieee 802.1q vlans in large networks, routers...
Page 190: Assigning Ports To Vlans
C onfiguring the s witch 3-142 vlans help to simplify network management by allowing you to move devices to a new vlan without having to change any physical connections. Vlans can be easily organized to reflect departmental groups (such as marketing or r&d), usage groups (such as e-mail), or multica...
Page 191
Vlan c onfiguration 3-143 note: vlan-tagged frames can pass through vlan-aware or vlan-unaware network interconnection devices, but the vlan tags should be stripped off before passing it on to any end-node host that does not support vlan tagging. Vlan classification – when the switch receives a fram...
Page 192
C onfiguring the s witch 3-144 automatic vlan registration – gvrp (garp vlan registration protocol) defines a system whereby the switch can automatically learn the vlans to which each end station should be assigned. If an end station (or its network adapter) supports the ieee 802.1q vlan protocol, i...
Page 193
Vlan c onfiguration 3-145 forwarding tagged/untagged frames if you want to create a small port-based vlan for devices attached directly to a single switch, you can assign ports to the same untagged vlan. However, to participate in a vlan group that crosses several switches, you should create a vlan ...
Page 194: Field Attributes
C onfiguring the s witch 3-146 enabling or disabling gvrp (global setting) garp vlan registration protocol (gvrp) defines a way for switches to exchange vlan information in order to register vlan members on ports across the network. Vlans are dynamically configured based on join messages issued by h...
Page 195: Displaying Current Vlans
Vlan c onfiguration 3-147 web – click vlan, 802.1q vlan, basic information. Figure 3-61 vlan basic information cli – enter the following command. Displaying current vlans the vlan current table shows the current port members of each vlan and whether or not the port supports vlan tagging. Ports assig...
Page 196: Command Attributes (Cli)
C onfiguring the s witch 3-148 • egress ports – shows all the vlan port members. • untagged ports – shows the untagged vlan port members. Web – click vlan, 802.1q vlan, current table. Select any id from the scroll-down list. Figure 3-62 displaying current vlans command attributes (cli) • vlan – id o...
Page 197: Creating Vlans
Vlan c onfiguration 3-149 cli – current vlan information can be displayed with the following command. Creating vlans use the vlan static list to create or remove vlan groups. To propagate information about vlan groups used on this switch to external network devices, you must specify a vlan id for ea...
Page 198
C onfiguring the s witch 3-150 • state (cli) – enables or disables the specified vlan. - active: vlan is operational. - suspend: vlan is suspended; i.E., does not pass packets. • add – adds a new vlan group to the current list. • remove – removes a vlan group from the current list. If any port is as...
Page 199
Vlan c onfiguration 3-151 cli – this example creates a new vlan. Adding static members to vlans (vlan index) use the vlan static table to configure port members for the selected vlan index. Assign ports as tagged if they are connected to 802.1q vlan compliant devices, or untagged they are not connec...
Page 200: Command Attributes
C onfiguring the s witch 3-152 command attributes • vlan – id of configured vlan (1-4094). • name – name of the vlan (1 to 32 characters). • status – enables or disables the specified vlan. - enable: vlan is operational. - disable: vlan is suspended; i.E., does not pass packets. • port – port identi...
Page 201: Command Attributes
Vlan c onfiguration 3-153 web – click vlan, 802.1q vlan, static table. Select a vlan id from the scroll-down list. Modify the vlan name and status if required. Select the membership type by marking the appropriate radio button in the list of ports or trunks. Click apply. Figure 3-64 configuring a vl...
Page 202
C onfiguring the s witch 3-154 • non-member – vlans for which the selected interface is not a tagged member. Web – open vlan, 802.1q vlan, static membership by port. Select an interface from the scroll-down box (port or trunk). Click query to display membership information for the interface. Select ...
Page 203: Command Usage
Vlan c onfiguration 3-155 configuring vlan behavior for interfaces you can configure vlan behavior for specific interfaces, including the default vlan identifier (pvid), accepted frame types, ingress filtering, gvrp status, and garp timers. Command usage • gvrp – garp vlan registration protocol defi...
Page 204
C onfiguring the s witch 3-156 - if ingress filtering is disabled and a port receives frames tagged for vlans for which it is not a member, these frames will be flooded to all other ports (except for those vlans explicitly forbidden on this port). - if ingress filtering is enabled and a port receive...
Page 205
Vlan c onfiguration 3-157 • mode – indicates vlan membership mode for an interface. (default: hybrid) - 1q trunk – specifies a port as an end-point for a vlan trunk. A trunk is a direct link between two switches, so the port transmits tagged frames that identify the source vlan. Note that frames bel...
Page 206: Private Vlans
C onfiguring the s witch 3-158 cli – this example sets port 3 to accept only tagged frames, assigns pvid 3 as the native vlan id, enables gvrp, sets the garp timers, and then sets the switchport mode to hybrid. Private vlans private vlans provide port-based security and isolation between ports withi...
Page 207: Command Attributes
Vlan c onfiguration 3-159 to configure private vlans, follow these steps: 1. Use the private vlan configuration menu (page 3-161) to designate one or more isolated or community vlans, and the primary vlan that will channel traffic outside of the vlan groups. 2. Use the private vlan association menu ...
Page 208
C onfiguring the s witch 3-160 web – click vlan, private vlan, information. Select the desired port from the vlan id drop-down menu. Figure 3-67 private vlan information cli – this example shows the switch configured with primary vlan 5 and secondary vlan 6. Port 3 has been configured as a promiscuo...
Page 209: Configuring Private Vlans
Vlan c onfiguration 3-161 configuring private vlans the private vlan configuration page is used to create/remove primary or community vlans. Command attributes • vlan id – id of configured vlan (1-4094). • type – there are three types of vlans within a private vlan: - primary vlans – conveys traffic...
Page 210: Associating Vlans
C onfiguring the s witch 3-162 cli – this example configures vlan 5 as a primary vlan, and vlan 6 as a community vlan and vlan 7 as an isolated vlan. Associating vlans each community or isolated vlan must be associated with a primary vlan. Command attributes • primary vlan id – id of primary vlan (1...
Page 211: Command Attributes
Vlan c onfiguration 3-163 cli – this example associates community vlans 6 and 7 with primary vlan 5. Displaying private vlan interface information use the private vlan port information and private vlan trunk information menus to display the interfaces associated with private vlans. Command attribute...
Page 212
C onfiguring the s witch 3-164 • isolated vlan – conveys traffic only between the vlan’s isolated ports and promiscuous ports. Traffic between isolated ports within the vlan is blocked. • trunk – the trunk identifier. (port information only) web – click vlan, private vlan, port information or trunk ...
Page 213: Command Attributes
Vlan c onfiguration 3-165 cli – this example shows the switch configured with primary vlan 5 and community vlan 6. Port 3 has been configured as a promiscuous port and mapped to vlan 5, while ports 4 and 5 have been configured as host ports and associated with vlan 6. This means that traffic for por...
Page 214
C onfiguring the s witch 3-166 specify the associated primary vlan. For “host” type, the primary vlan displayed is the one to which the selected secondary vlan has been associated. • community vlan – a community vlan conveys traffic between community ports, and from community ports to their designat...
Page 215: Layer 2 Queue Settings
C lass of s ervice c onfiguration 3-167 cli – this example shows the switch configured with primary vlan 5 and secondary vlan 6. Port 3 has been configured as a promiscuous port and mapped to vlan 5, while ports 4 and 5 have been configured as a host ports and associated with vlan 6. This means that...
Page 216: Command Usage
C onfiguring the s witch 3-168 command usage • this switch provides four priority queues for each port. It uses weighted round robin to prevent head-of-queue blockage. • the default priority applies for an untagged frame received on a port set to accept all frame types (i.E, receives both untagged a...
Page 217
C lass of s ervice c onfiguration 3-169 cli – this example assigns a default priority of 5 to port 3. Mapping cos values to egress queues this switch processes class of service (cos) priority tagged traffic by using four priority queues for each port, with service schedules based on strict or weight...
Page 218: Command Attributes
C onfiguring the s witch 3-170 the priority levels recommended in the ieee 802.1p standard for various network applications are shown in the following table. However, you can map the priority levels to the switch’s output queues in any way that benefits application traffic for your own network. Comm...
Page 219
C lass of s ervice c onfiguration 3-171 web – click priority, traffic classes. Assign priorities to the traffic classes (i.E., output queues), then click apply. Figure 3-73 traffic classes cli – the following example shows how to change the cos assignments. Note: mapping specific values for cos prio...
Page 220: Selecting The Queue Mode
C onfiguring the s witch 3-172 selecting the queue mode you can set the switch to service the queues based on a strict rule that requires all traffic in a higher priority queue to be processed before lower priority queues are serviced, or use weighted round-robin (wrr) queuing that specifies a relat...
Page 221: Command Attributes
C lass of s ervice c onfiguration 3-173 setting the service weight for traffic classes this switch uses the weighted round robin (wrr) algorithm to determine the frequency at which it services each priority queue. As described in “mapping cos values to egress queues” on page 3-169, the traffic class...
Page 222: Layer 3/4 Priority Settings
C onfiguring the s witch 3-174 cli – the following example shows how to assign wrr weights to each of the priority queues. Layer 3/4 priority settings mapping layer 3/4 priorities to cos values this switch supports several common methods of prioritizing layer 3/4 traffic to meet application requirem...
Page 223: Command Attributes
C lass of s ervice c onfiguration 3-175 selecting ip precedence/dscp priority the switch allows you to choose between using ip precedence or dscp priority. Select one of the methods or disable this feature. Command attributes • disabled – disables both priority services. (this is the default setting...
Page 224: Command Attributes
C onfiguring the s witch 3-176 command attributes • ip precedence priority table –shows the ip precedence to cos map. • class of service value –maps a cos value to the selected ip precedence value. Note that “0” represents low priority and “7” represent high priority. Web – click priority, ip preced...
Page 225: Mapping Dscp Priority
C lass of s ervice c onfiguration 3-177 cli – the following example globally enables ip precedence service on the switch, maps ip precedence value 1 to cos value 0 (on port 1), and then displays the ip precedence settings. Note: mapping specific values for ip precedence is implemented as an interfac...
Page 226: Command Attributes
C onfiguring the s witch 3-178 command attributes • dscp priority table – shows the dscp priority to cos map. • class of service value – maps a cos value to the selected dscp priority value. Note that “0” represents low priority and “7” represent high priority. Web – click priority, ip dscp priority...
Page 227: Mapping Ip Port Priority
C lass of s ervice c onfiguration 3-179 cli – the following example globally enables dscp priority service on the switch, maps dscp value 0 to cos value 1 (on port 1), and then displays the dscp priority settings. Note: mapping specific values for ip dscp is implemented as an interface configuration...
Page 228
C onfiguring the s witch 3-180 web – click priority, ip port priority status. Set ip port priority status to enabled. Figure 3-79 ip port priority status click priority, ip port priority. Enter the port number for a network application in the ip port number box and the new cos value in the class of ...
Page 229: Mapping Cos Values to Acls
C lass of s ervice c onfiguration 3-181 cli – the following example globally enables ip port priority service on the switch, maps http traffic on port 5 to cos value 0, and then displays all the ip port priority settings for that port. Note: mapping specific values for ip port priority is implemente...
Page 230
C onfiguring the s witch 3-182 • cos priority – cos value used for packets matching an ip acl rule. (range: 0-7) • acl cos priority mapping – displays the configured information. Web – click priority, acl cos priority. Enable mapping for any port, select an acl from the scroll-down list, then click ...
Page 231: Multicast Filtering
M ulticast f iltering 3-183 multicast filtering multicasting is used to support real-time applications such as videoconferencing or streaming audio. A multicast server does not have to establish a separate connection with each client. It merely broadcasts its service to the network, and any hosts th...
Page 232: Command Usage
C onfiguring the s witch 3-184 layer 2 igmp (snooping and query) igmp snooping and query – if multicast routing is not supported on other switches in your network, you can use igmp snooping and query (page 3-184) to monitor igmp service requests passing between multicast clients and servers, and dyn...
Page 233: Command Attributes
M ulticast f iltering 3-185 • igmp querier – a router, or multicast-enabled switch, can periodically ask their hosts if they want to receive multicast traffic. If there is more than one router/switch on the lan performing ip multicasting, one of these devices is elected “querier” and assumes the rol...
Page 234
C onfiguring the s witch 3-186 • igmp version — sets the protocol version for compatibility with other devices on the network. (range: 1-2; default: 2) notes: 1. All systems on the subnet must support the same version. 2. Some attributes are only enabled for igmpv2, including igmp report delay and i...
Page 235: Command Attributes
M ulticast f iltering 3-187 cli – this example modifies the settings for multicast filtering, and then displays the current status. Displaying interfaces attached to a multicast router multicast routers that are attached to ports on the switch use information obtained from igmp, along with a multica...
Page 236: Command Attributes
C onfiguring the s witch 3-188 web – click igmp snooping, multicast router port information. Select the required vlan id from the scroll-down list to display the associated multicast routers. Figure 3-83 multicast router port information cli – this example shows that port 11 has been statically conf...
Page 237: Command Attributes
M ulticast f iltering 3-189 • vlan id – selects the vlan to propagate all multicast traffic coming from the attached multicast router. • port or trunk – specifies the interface attached to a multicast router. Web – click igmp snooping, static multicast router port configuration. Specify the interfac...
Page 238
C onfiguring the s witch 3-190 • multicast group port list – shows the interfaces that have already been assigned to the selected vlan to propagate a specific multicast service. Web – click igmp snooping, ip multicast registration table. Select a vlan id and the ip address for a multicast service fr...
Page 239: Command Usage
M ulticast f iltering 3-191 assigning ports to multicast services multicast filtering can be dynamically configured using igmp snooping and igmp query messages as described in “configuring igmp snooping and query parameters” on page 3-133. For certain applications that require tighter control, you m...
Page 240
C onfiguring the s witch 3-192 web – click igmp snooping, igmp member port table. Specify the interface attached to a multicast service (via an igmp-enabled switch or multicast router), indicate the vlan that will propagate the multicast service, specify the multicast ip address, and click add. Afte...
Page 241: Accessing The Cli
4-1 c hapter 4 c ommand l ine i nterface this chapter describes how to use the command line interface (cli). Using the command line interface accessing the cli when accessing the management interface for the switch over a direct connection to the server’s console port, or via a telnet connection, th...
Page 242: Telnet Connection
C ommand l ine i nterface 4-2 after connecting to the system through the console port, the login screen displays: telnet connection telnet operates over the ip transport protocol. In this environment, your management station and any network device you want to manage over the network must have a vali...
Page 243
U sing the c ommand l ine i nterface 4-3 2. At the prompt, enter the user name and system password. The cli will display the “vty-n#” prompt for the administrator to show that you are using privileged access mode (i.E., privileged exec), or “vty-n>” for the guest to show that you are using normal ac...
Page 244: Entering Commands
C ommand l ine i nterface 4-4 entering commands this section describes how to enter cli commands. Keywords and arguments a cli command is a series of keywords and arguments. Keywords identify a command, and arguments specify configuration parameters. For example, in the command “show interfaces stat...
Page 245: Command Completion
E ntering c ommands 4-5 command completion if you terminate input with a tab key, the cli will print the remaining characters of a partial keyword up to the point of ambiguity. In the “logging history” example, typing log followed by a tab will result in printing the command up to “logging.” getting...
Page 246: Showing Commands
C ommand l ine i nterface 4-6 showing commands if you enter a “?” at the command prompt, the system will display the first level of keywords for the current command class (normal exec or privileged exec) or configuration class (global, acl, interface, line or vlan database). You can also display a l...
Page 247: Partial Keyword Lookup
E ntering c ommands 4-7 the command “show interfaces ?” will display the following information: partial keyword lookup if you terminate a partial keyword with a question mark, alternatives that match the initial letters are provided. (remember not to leave a space between the command and question ma...
Page 248: Understanding Command Modes
C ommand l ine i nterface 4-8 understanding command modes the command set is divided into exec and configuration classes. Exec commands generally display information on system status or clear statistical counters. Configuration commands, on the other hand, modify interface parameters or enable certa...
Page 249: Configuration Commands
E ntering c ommands 4-9 to enter privileged exec mode, enter the following user names and passwords: configuration commands configuration commands are privileged level commands used to modify switch settings. These commands modify the running configuration only and are not saved when the switch is r...
Page 250
C ommand l ine i nterface 4-10 • vlan configuration - includes the command to create vlan groups. To enter the global configuration mode, enter the command configure in privileged exec mode. The system prompt will change to “console(config)#” which gives you access privilege to all global configurat...
Page 251: Command Line Processing
E ntering c ommands 4-11 command line processing commands are not case sensitive. You can abbreviate commands and parameters as long as they contain enough letters to differentiate them from any other currently available commands or parameters. You can use the tab key to complete partial commands, o...
Page 252: Command Groups
C ommand l ine i nterface 4-12 command groups the system commands can be broken down into the functional groups shown below . Table 4-4 command groups command group description page line sets communication parameters for the serial port and telnet, including baud rate and console time-out 4-14 gener...
Page 253
C ommand g roups 4-13 the access mode shown in the following tables is indicated by these abbreviations: ne (normal exec) pe (privileged exec) gc (global configuration) acl (access control list configuration) ic (interface configuration) lc (line configuration) vc (vlan database configuration) addre...
Page 254: Line Commands
C ommand l ine i nterface 4-14 line commands you can access the onboard configuration program by attaching a vt100 compatible device to the server’s serial port. These commands are used to set communication parameters for the serial port or telnet (i.E., a virtual terminal). Table 4-5 line commands ...
Page 256: Login
C ommand l ine i nterface 4-16 login this command enables password checking at login. Use the no form to disable password checking and allow connections without a password. Syntax login [local] no login local - selects local password checking. Authentication is based on the user name specified with ...
Page 258: Timeout Login Response
C ommand l ine i nterface 4-18 configuration file from a tftp server. There is no need for you to manually configure encrypted passwords. Example related commands login (4-16) password-thresh (4-20) timeout login response this command sets the interval that the system waits for a user to log into th...
Page 259: Exec-Timeout
L ine c ommands 4-19 example to set the timeout to two minutes, enter this command: related commands silent-time (4-21) exec-timeout (4-14) exec-timeout this command sets the interval that the system waits until user input is detected. Use the no form to restore the default. Syntax exec-timeout [sec...
Page 260: Password-Thresh
C ommand l ine i nterface 4-20 example to set the timeout to two minutes, enter this command: related commands silent-time (4-21) timeout login response (4-13) password-thresh this command sets the password intrusion threshold which limits the number of failed logon attempts. Use the no form to remo...
Page 261: Silent-Time
L ine c ommands 4-21 example to set the password threshold to five attempts, enter this command: related commands silent-time (4-21) timeout login response (4-13) silent-time this command sets the amount of time the management console is inaccessible after the number of unsuccessful logon attempts e...
Page 264: Stopbits
C ommand l ine i nterface 4-24 default setting 9600 command mode line configuration command usage set the speed to match the baud rate of the device connected to the serial port. Some baud rates available on devices connected to the port might not be supported. The system indicates if the speed you ...
Page 265: Disconnect
L ine c ommands 4-25 disconnect this command terminates an ssh, telnet, or console connection. Syntax disconnect session-id session-id – the session identifier for an ssh, telnet or console connection. (range: 0-4) command mode privileged exec command usage specifying session identifier “0” will dis...
Page 266: General Commands
C ommand l ine i nterface 4-26 example to show all lines, enter this command: general commands console#show line console configuration: password threshold: 3 times interactive timeout: disabled login timeout: disabled silent time: disabled baudrate: 9600 databits: 8 parity: none stopbits: 1 vty conf...
Page 267: Enable
G eneral c ommands 4-27 enable this command activates privileged exec mode. In privileged mode, additional commands are available, and certain commands display additional information. See “understanding command modes” on page 4-8. Syntax enable [level] level - privilege level to log into the device....
Page 268: Disable
C ommand l ine i nterface 4-28 disable this command returns to normal exec mode from privileged mode. In normal access mode, you can only display basic information on the switch's configuration or ethernet statistics. To gain access to all commands, you must use the privileged mode. See “understandi...
Page 269: Show History
G eneral c ommands 4-29 example related commands end (4-30) show history this command shows the contents of the command history buffer. Default setting none command mode normal exec, privileged exec command usage the history buffer size is fixed at 10 execution commands and 10 configuration commands...
Page 270: Reload
C ommand l ine i nterface 4-30 the ! Command repeats commands from the execution command history buffer when you are in normal exec or privileged exec mode, and commands from the configuration command history buffer when you are in any of the configuration modes. In this example, the !2 command repe...
Page 271: Exit
G eneral c ommands 4-31 command mode global configuration, interface configuration, line configuration, and vlan database configuration. Example this example shows how to return to the privileged exec mode from the interface configuration mode: exit this command returns to the previous configuration...
Page 272: System Management Commands
C ommand l ine i nterface 4-32 command mode normal exec, privileged exec command usage the quit and exit commands can both exit the configuration program. Example this example shows how to quit a cli session: system management commands these commands are used to control system logs, passwords, user ...
Page 273: Device Designation Commands
S ystem m anagement c ommands 4-33 device designation commands prompt this command customizes the cli prompt. Use the no form to restore the default prompt. Syntax prompt string no prompt string - any alphanumeric string to use for the cli prompt. (maximum length: 255 characters) default setting con...
Page 274: Hostname
C ommand l ine i nterface 4-34 hostname this command specifies or modifies the host name for this device. Use the no form to restore the default host name. Syntax hostname name no hostname name - the name of this host. (maximum length: 255 characters) default setting none command mode global configu...
Page 275: Username
S ystem m anagement c ommands 4-35 username this command adds named users, requires authentication at login, specifies or changes a user's password (or specify that no password is required), or specifies or changes a user's access level. Use the no form to remove a user name. Syntax username name {a...
Page 276: Enable Password
C ommand l ine i nterface 4-36 command usage the encrypted password is required for compatibility with legacy password settings (i.E., plain text or encrypted) when reading the configuration file during system bootup or when downloading the configuration file from a tftp server. There is no need for...
Page 277: Ip Filter Commands
S ystem m anagement c ommands 4-37 command usage • you cannot set a null password. You will have to enter a password to change the command mode from normal exec to privileged exec with the enable command (page 4-27). • the encrypted password is required for compatibility with legacy password setting...
Page 279: Show Management
S ystem m anagement c ommands 4-39 • you can delete an address range just by specifying the start address, or by specifying both the start address and end address. Example this example restricts management access to the indicated addresses. Show management this command displays the client ip address...
Page 280: Web Server Commands
C ommand l ine i nterface 4-40 example web server commands console#show management all-client management ip filter http-client: start ip address end ip address ----------------------------------------------- 1. 192.168.1.19 192.168.1.19 2. 192.168.1.25 192.168.1.30 snmp-client: start ip address end ...
Page 281: Ip Http Port
S ystem m anagement c ommands 4-41 ip http port this command specifies the tcp port number used by the web browser interface. Use the no form to use the default port. Syntax ip http port port-number no ip http port port-number - the tcp port to be used by the browser interface. (range: 1-65535) defa...
Page 282: Ip Http Secure-Server
C ommand l ine i nterface 4-42 example related commands ip http port (4-41) ip http secure-server this command enables the secure hypertext transfer protocol (https) over the secure socket layer (ssl), providing secure access (i.E., an encrypted connection) to the switch’s web interface. Use the no ...
Page 283: Ip Http Secure-Port
S ystem m anagement c ommands 4-43 • a padlock icon should appear in the status bar for internet explorer 5.X and netscape navigator 6.2 or later versions. • the following web browsers and operating systems currently support https: • to specify a secure-site certificate, see “replacing the default s...
Page 284: Telnet Server Commands
C ommand l ine i nterface 4-44 command mode global configuration command usage • you cannot configure the http and https servers to use the same port. • if you change the https port number, clients attempting to connect to the https server must specify the port number in the url, in this format: htt...
Page 285: Ip Telnet Server
S ystem m anagement c ommands 4-45 default setting 23 command mode global configuration example related commands ip telnet server (4-45) ip telnet server this command allows this device to be monitored or configured from telnet. Use the no form to disable this function. Syntax [no] ip telnet server ...
Page 286: Secure Shell Commands
C ommand l ine i nterface 4-46 secure shell commands the berkley-standard includes remote access tools originally designed for unix systems. Some of these tools have also been implemented for microsoft windows and other environments. These tools, including commands such as rlogin (remote login), rsh...
Page 287
S ystem m anagement c ommands 4-47 the ssh server on this switch supports both password and public key authentication. If password authentication is specified by the ssh client, then the password can be authenticated either locally or via a radius or tacacs+ remote authentication server, as specifie...
Page 288
C ommand l ine i nterface 4-48 2. Provide host public key to clients – many ssh client programs automatically import the host public key during the initial connection setup with the switch. Otherwise, you need to manually create a known hosts file on the management station and place the host public ...
Page 289: Ip Ssh Server
S ystem m anagement c ommands 4-49 a. The client sends its public key to the switch. B. The switch compares the client's public key to those stored in memory. C. If a match is found, the switch uses the public key to encrypt a random sequence of bytes, and sends this string to the client. D. The cli...
Page 290: Ip Ssh Timeout
C ommand l ine i nterface 4-50 • you must generate the host key before enabling the ssh server. Example related commands ip ssh crypto host-key generate (4-53) show ssh (4-55) ip ssh timeout this command configures the timeout for the ssh server. Use the no form to restore the default setting. Synta...
Page 291: Ip Ssh Server-Key Size
S ystem m anagement c ommands 4-51 related commands exec-timeout (4-19) show ip ssh (4-55) ip ssh authentication-retries this command configures the number of times the ssh server attempts to reauthenticate a user. Use the no form to restore the default setting. Syntax ip ssh authentication-retries ...
Page 292: Delete Public-Key
C ommand l ine i nterface 4-52 default setting 768 bits command mode global configuration command usage • the server key is a private key that is never shared outside the switch. • the host key is shared with the ssh client, and is fixed at 1024 bits. Example delete public-key this command deletes t...
Page 295: Show Ip Ssh
S ystem m anagement c ommands 4-55 default setting saves both the dsa and rsa key. Command mode privileged exec example related commands ip ssh crypto host-key generate (4-53) show ip ssh this command displays the connection settings used when authenticating client access to the ssh server. Command ...
Page 296
C ommand l ine i nterface 4-56 table 4-16 show ssh - display description field description session the session number. (range: 0-3) version the secure shell version number. State the authentication negotiation state. (values: negotiation-started, authentication-started, session-started) username the...
Page 298
C ommand l ine i nterface 4-58 example console#show public-key host host: rsa: 1024 35 1568499540186766925933394677505461732531367489083654725415020245593 1998685443583616519999233297817660658309586108259132128902337654680 1726272571413428762941301196195566782595664104869574278881462065194 174677298...
Page 299: Event Logging Commands
S ystem m anagement c ommands 4-59 event logging commands logging on this command controls logging of error messages, sending debug or error messages to switch memory. The no form disables the logging process. Syntax [no] logging on default setting none command mode global configuration command usag...
Page 301: Logging Host
S ystem m anagement c ommands 4-61 default setting flash: errors (level 3 - 0) ram: warnings (level 6 - 0) command mode global configuration command usage the message level specified for flash memory must be a higher priority (i.E., numerically lower) than that specified for ram. Example logging hos...
Page 302: Logging Facility
C ommand l ine i nterface 4-62 command usage • by using this command more than once you can build up a list of host ip addresses. • the maximum number of host ip addresses allowed is five. Example logging facility this command sets the facility type for remote logging of syslog messages. Use the no ...
Page 303: Logging Trap
S ystem m anagement c ommands 4-63 logging trap this command enables the logging of system messages to a remote server, or limits the syslog messages saved to a remote server based on severity. Use this command without a specified level to enable remote logging. Use the no form to disable remote log...
Page 305
S ystem m anagement c ommands 4-65 default setting none command mode privileged exec example the following example shows that system logging is enabled, the message level for flash memory is “errors” (i.E., default level 3 - 0), the message level for ram is “informational” (i.E., default level 6 - 0...
Page 306
C ommand l ine i nterface 4-66 the following example displays settings for the trap function. Related commands show logging sendmail (4-71) console#show logging trap syslog logging: enabled remotelog status: enabled remotelog facility type: local use 7 remotelog level type: informational messages on...
Page 308: Smtp Alert Commands
C ommand l ine i nterface 4-68 smtp alert commands these commands configure smtp event handling, and forwarding of alert messages to the specified smtp servers and email recipients. Logging sendmail host this command specifies smtp servers that will be sent alert messages. Use the no form to remove ...
Page 309: Logging Sendmail Level
S ystem m anagement c ommands 4-69 • to send email alerts, the switch first opens a connection, sends all the email alerts waiting in the queue one by one, and finally closes the connection. • to open a connection, the switch first selects the server that successfully sent mail during the last conne...
Page 310
C ommand l ine i nterface 4-70 logging sendmail source-email this command sets the email address used for the “from” field in alert messages. Use the no form to delete the source email address. Syntax [no] logging sendmail source-email email-address email-address - the source email address used in a...
Page 311: Logging Sendmail
S ystem m anagement c ommands 4-71 command mode global configuration command usage you can specify up to five recipients for alert messages. However, you must enter a separate command to specify each recipient. Example logging sendmail this command enables smtp event handling. Use the no form to dis...
Page 312: Time Commands
C ommand l ine i nterface 4-72 example time commands the system clock can be dynamically set by polling a set of specified time servers (ntp or sntp). Maintaining an accurate time on the switch enables the system log to record meaningful dates and times for event entries. If the clock is not set, th...
Page 313: Sntp Client
S ystem m anagement c ommands 4-73 sntp client this command enables sntp client requests for time synchronization from ntp or sntp time servers specified with the sntp servers command. Use the no form to disable sntp client requests. Syntax [no] sntp client default setting disabled command mode glob...
Page 314: Sntp Server
C ommand l ine i nterface 4-74 sntp server this command sets the ip address of the servers to which sntp time requests are issued. Use the this command with no arguments to clear all time servers from the current list. Syntax sntp server [ip1 [ip2 [ip3]]] ip - ip address of a time server (ntp or snt...
Page 315: Sntp Poll
S ystem m anagement c ommands 4-75 sntp poll this command sets the interval between sending time requests when the switch is set to sntp client mode. Use the no form to restore to the default. Syntax sntp poll seconds no sntp poll seconds - interval between time requests. (range: 16-16384 seconds) d...
Page 317: Calendar Set
S ystem m anagement c ommands 4-77 example related commands show sntp (4-75) calendar set this command sets the system clock. It may be used if there is no time server on your network, or if you have not configured the switch to receive signals from a time server. Syntax calendar set hour min sec {d...
Page 318: Show Calendar
C ommand l ine i nterface 4-78 show calendar this command displays the system clock. Default setting none command mode normal exec, privileged exec example system status commands console#show calendar 15:12:45 april 1 2004 console# table 4-23 system status commands command function mode page show st...
Page 319: Show Startup-Config
S ystem m anagement c ommands 4-79 show startup-config this command displays the configuration file stored in non-volatile memory that is used to start up the system. Default setting none command mode privileged exec command usage • use this command in conjunction with the show running-config comman...
Page 320
C ommand l ine i nterface 4-80 example related commands show running-config (4-81) console#show startup-config building startup-config, please wait..... ! ! Username admin access-level 15 username admin password 0 admin ! Username guest access-level 0 username guest password 0 guest ! Enable passwor...
Page 321: Show Running-Config
S ystem m anagement c ommands 4-81 show running-config this command displays the configuration information currently in use. Default setting none command mode privileged exec command usage • use this command in conjunction with the show startup-config command to compare the information in running me...
Page 322
C ommand l ine i nterface 4-82 example related commands show startup-config (4-79) console#show running-config building running-config, please wait..... ! Phymap 00-30-f1-d3-26-00 ! Sntp server 0.0.0.0 0.0.0.0 0.0.0.0 ! Clock timezone hours 0 minute 0 after-utc ! Snmp-server community private rw snm...
Page 323: Show System
S ystem m anagement c ommands 4-83 show system this command displays system information. Default setting none command mode normal exec, privileged exec command usage • for a description of the items shown by this command, refer to “displaying system information” on page -11. • the post results shoul...
Page 324: Show Users
C ommand l ine i nterface 4-84 show users shows all active console and telnet sessions, including user name, idle time, and ip address of telnet client. Default setting none command mode normal exec, privileged exec command usage the session used to execute this command is indicated by a “*” symbol ...
Page 325: Frame Size Commands
S ystem m anagement c ommands 4-85 command mode normal exec, privileged exec command usage see “displaying switch hardware/software versions” on page 3-13 for detailed information on the items displayed by this command. Example frame size commands jumbo frame this command enables support for jumbo f...
Page 326: Flash/file Commands
C ommand l ine i nterface 4-86 command mode global configuration command usage • this switch provides more efficient throughput for large sequential data transfers by supporting jumbo frames up to 9216 bytes. Compared to standard ethernet frames that run only up to 1.5 kb, using jumbo frames signifi...
Page 327: Copy
F lash /f ile c ommands 4-87 copy this command moves (upload/download) a code image or configuration file between the switch’s flash memory and a tftp server. When you save the system code or configuration settings to a file on a tftp server, that file can later be downloaded to the switch to restor...
Page 328
C ommand l ine i nterface 4-88 command mode privileged exec command usage • the system prompts for data required to complete the copy command. • the destination file name should not contain slashes (\ or /), the leading letter of the file name should not be a period (.), and the maximum length for f...
Page 329
F lash /f ile c ommands 4-89 example the following example shows how to upload the configuration settings to a file on the tftp server: the following example shows how to copy the running configuration to a startup file. The following example shows how to download a configuration file: this example ...
Page 330: Delete
C ommand l ine i nterface 4-90 this example shows how to copy a public-key used by ssh from an tftp server. Note that public key authentication via ssh is only supported for users configured locally on the switch: delete this command deletes a file or image. Syntax delete [unit:] filename filename -...
Page 332: Whichboot
C ommand l ine i nterface 4-92 • file information is shown below: example the following example shows how to display all file information: whichboot this command displays which files were booted when the system powered up. Syntax whichboot default setting none command mode privileged exec table 4-26...
Page 333: Boot System
F lash /f ile c ommands 4-93 example this example shows the information displayed by the whichboot command. See the table under the dir command for a description of the file information displayed by this command. Boot system this command specifies the image used to start up the system. Syntax boot s...
Page 334: Authentication Commands
C ommand l ine i nterface 4-94 example related commands dir (4-91) whichboot (4-92) authentication commands you can configure this switch to authenticate users logging into the system for management access using local or radius authentication methods. You can also enable port-based authentication fo...
Page 335: Authentication Login
A uthentication c ommands 4-95 authentication login this command defines the login authentication method and precedence. Use the no form to restore the default. Syntax authentication login {[local] [radius] [tacacs]} no authentication login • local - use local password. • radius - use radius server ...
Page 336: Authentication Enable
C ommand l ine i nterface 4-96 example related commands username - for setting the local user names and passwords (4-35) authentication enable this command defines the authentication method and precedence to use when changing from exec command mode to privileged exec command mode with the enable com...
Page 337: Radius Client
A uthentication c ommands 4-97 • you can specify three authentication methods in a single command to indicate the authentication sequence. For example, if you enter “authentication enable radius tacacs local,” the user name and password on the radius server is verified first. If the radius server is...
Page 339: Radius-Server Port
A uthentication c ommands 4-99 radius-server port this command sets the radius server network port. Use the no form to restore the default. Syntax radius-server port port_number no radius-server port port_number - radius server udp port used for authentication messages. (range: 1-65535) default sett...
Page 340: Radius-Server Retransmit
C ommand l ine i nterface 4-100 example radius-server retransmit this command sets the number of retries. Use the no form to restore the default. Syntax radius-server retransmit number_of_retries no radius-server retransmit number_of_retries - number of times the switch will try to authenticate logo...
Page 341: Show Radius-Server
A uthentication c ommands 4-101 command mode global configuration example show radius-server this command displays the current settings for the radius server. Default setting none command mode privileged exec example console(config)#radius-server timeout 10 console(config)# console#show radius-serve...
Page 342: Tacacs+ Client
C ommand l ine i nterface 4-102 tacacs+ client terminal access controller access control system (tacacs+) is a logon authentication protocol that uses software running on a central server to control access to tacacs-aware devices on the network. An authentication server contains a database of multip...
Page 343: Tacacs-Server Port
A uthentication c ommands 4-103 tacacs-server port this command specifies the tacacs+ server network port. Use the no form to restore the default. Syntax tacacs-server port port_number no tacacs-server port port_number - tacacs+ server tcp port used for authentication messages. (range: 1-65535) defa...
Page 344: Show Tacacs-Server
C ommand l ine i nterface 4-104 example show tacacs-server this command displays the current settings for the tacacs+ server. Default setting none command mode privileged exec example port security commands these commands can be used to enable port security on a port. When using port security, the s...
Page 345: Port Security
A uthentication c ommands 4-105 port security this command enables or configures port security. Use the no form without any keywords to disable port security. Use the no form with the appropriate keyword to restore the default settings for a response to security violation or for the maximum number o...
Page 346
C ommand l ine i nterface 4-106 command usage • if you enable port security, the switch stops learning new mac addresses on the specified port when it has reached a configured maximum number. Only incoming traffic with source addresses already stored in the dynamic or static address table will be ac...
Page 347: 802.1X Port Authentication
A uthentication c ommands 4-107 802.1x port authentication the switch supports ieee 802.1x (dot1x) port-based access control that prevents unauthorized access to the network by requiring users to first submit credentials for authentication. Client authentication is controlled centrally by a radius s...
Page 348: Dot1X System-Auth-Control
C ommand l ine i nterface 4-108 dot1x system-auth-control this command enables 802.1x port authentication globally on the switch. Use the no form to restore the default. Syntax [no] system-auth-control default setting disabled command mode global configuration example dot1x default this command sets...
Page 349: Dot1X Max-Req
A uthentication c ommands 4-109 dot1x max-req this command sets the maximum number of times the switch port will retransmit an eap request/identity packet to the client before it times out the authentication session. Use the no form to restore the default. Syntax dot1x max-req count no dot1x max-req...
Page 350: Dot1X Operation-Mode
C ommand l ine i nterface 4-110 default force-authorized command mode interface configuration example dot1x operation-mode this command allows single or multiple hosts (clients) to connect to an 802.1x-authorized port. Use the no form with no keywords to restore the default to single host. Use the n...
Page 351: Dot1X Re-Authenticate
A uthentication c ommands 4-111 • in “multi-host” mode, only one host connected to a port needs to pass authentication for all other hosts to be granted network access. Similarly, a port can become unauthorized for all hosts if one attached host fails re-authentication or sends an eapol logoff messa...
Page 352: Dot1X Timeout Quiet-Period
C ommand l ine i nterface 4-112 example dot1x timeout quiet-period this command sets the time that a switch port waits after the max request count has been exceeded before attempting to acquire a new client. Use the no form to reset the default. Syntax dot1x timeout quiet-period seconds no dot1x tim...
Page 353: Dot1X Timeout Tx-Period
A uthentication c ommands 4-113 command mode interface configuration example dot1x timeout tx-period this command sets the time that an interface on the switch waits during an authentication session before re-transmitting an eap packet. Use the no form to reset to the default value. Syntax dot1x tim...
Page 354: Show Dot1X
C ommand l ine i nterface 4-114 show dot1x this command shows general port authentication related settings on the switch or a specific interface. Syntax show dot1x [statistics] [interface interface] • statistics - displays dot1x status for each port. • interface • ethernet unit/port -unit - stack un...
Page 355
A uthentication c ommands 4-115 - tx-period – time a port waits during authentication session before re-transmitting eap packet (page 4-113). - supplicant-timeout – supplicant timeout. - server-timeout – server timeout. - reauth-max – maximum number of reauthentication attempts. - max-req – maximum ...
Page 356
C ommand l ine i nterface 4-116 from the authentication server. • reauthentication state machine - state – current state (including initialize, reauthenticate). Example console#show dot1x global 802.1x parameters system-auth-control: enable 802.1x port summary port name status operation mode mode au...
Page 357: Access Control List Commands
A ccess c ontrol l ist c ommands 4-117 access control list commands access control lists (acl) provide packet filtering for ip frames (based on address, protocol, layer 4 protocol port number or tcp control code) or any frames (based on mac address or ethernet type). To filter packets, first create ...
Page 358: Ip Acls
C ommand l ine i nterface 4-118 • this switch supports acls for ingress filtering only. You can only bind one ip acl to any port and one mac acl globally for ingress filtering. In other words, only two acls can be bound to an interface - ingress ip acl and ingress mac acl. The order in which active ...
Page 360
C ommand l ine i nterface 4-120 command usage • when you create a new acl or enter configuration mode for an existing acl, use the permit or deny command to add new rules to the bottom of the list. To create an acl, you must add at least one rule to the list. • to remove a rule, use the no permit or...
Page 361
A ccess c ontrol l ist c ommands 4-121 command usage • new rules are appended to the end of the list. • address bitmasks are similar to a subnet mask, containing four integers from 0 to 255, each separated by a period. The binary mask uses 1 bits to indicate “match” and 0 bits to indicate “ignore.” ...
Page 362
C ommand l ine i nterface 4-122 permit, deny (extended acl) this command adds a rule to an extended ip acl. The rule sets a filter condition for packets with specific source or destination ip addresses, protocol types, source or destination protocol ports, or tcp control codes. Use the no form to re...
Page 363
A ccess c ontrol l ist c ommands 4-123 default setting none command mode extended acl command usage • all new rules are appended to the end of the list. • address bitmasks are similar to a subnet mask, containing four integers from 0 to 255, each separated by a period. The binary mask uses 1 bits to...
Page 364: Show Ip Access-List
C ommand l ine i nterface 4-124 example this example accepts any incoming packets if the source address is within subnet 10.7.1.X. For example, if the rule is matched; i.E., the rule (10.7.1.0 & 255.255.255.0) equals the masked address (10.7.1.2 & 255.255.255.0), the packet passes through. This allo...
Page 365: Ip Access-Group
A ccess c ontrol l ist c ommands 4-125 example related commands permit, deny 4-120 ip access-group (4-125) ip access-group this command binds a port to an ip acl. Use the no form to remove the port. Syntax [no] ip access-group acl_name in • acl_name – name of the acl. (maximum length: 16 characters)...
Page 366: Show Ip Access-Group
C ommand l ine i nterface 4-126 example related commands show ip access-list (4-124) show ip access-group this command shows the ports assigned to ip acls. Command mode privileged exec example related commands ip access-group (4-125) map access-list ip this command sets the output queue for packets ...
Page 367: Show Map Access-List Ip
A ccess c ontrol l ist c ommands 4-127 command mode interface configuration (ethernet) command usage a packet matching a rule within the specified acl is mapped to one of the output queues as shown in the following table. For information on mapping the cos values to output queues, see queue cos-map ...
Page 368: Mac Acls
C ommand l ine i nterface 4-128 example related commands map access-list ip (4-126) mac acls access-list mac this command adds a mac access list and enters mac acl configuration mode. Use the no form to remove the specified acl. Syntax [no] access-list mac acl_name acl_name – name of the acl. (maxim...
Page 369
A ccess c ontrol l ist c ommands 4-129 default setting none command mode global configuration command usage • when you create a new acl or enter configuration mode for an existing acl, use the permit or deny command to add new rules to the bottom of the list. To create an acl, you must add at least ...
Page 371: Show Mac Access-List
A ccess c ontrol l ist c ommands 4-131 • a detailed listing of ethernet protocol types can be found in rfc 1060. A few of the more common types include the following: • 0800 - ip • 0806 - arp • 8137 - ipx example this rule permits packets from any source mac address to the destination address 00-e0-...
Page 372: Mac Access-Group
C ommand l ine i nterface 4-132 mac access-group this command binds a port to a mac acl. Use the no form to remove the port. Syntax mac access-group acl_name in • acl_name – name of the acl. (maximum length: 16 characters) • in – indicates that this list applies to ingress packets. Default setting n...
Page 373: Map Access-List Mac
A ccess c ontrol l ist c ommands 4-133 related commands mac access-group (4-132) map access-list mac this command sets the output queue for packets matching an acl rule. The specified cos value is only used to map the matching packet to an output queue; it is not written to the packet itself. Use th...
Page 374: Show Map Access-List Mac
C ommand l ine i nterface 4-134 related commands queue cos-map (4-226) show map access-list mac (4-134) show map access-list mac this command shows the cos value mapped to a mac acl for the current interface. (the cos value determines the output queue for packets matching an acl rule.) syntax show m...
Page 375: Acl Information
A ccess c ontrol l ist c ommands 4-135 acl information show access-list this command shows all acls and associated rules, as well as all the user-defined masks. Command mode privileged exec command usage once the acl is bound to an interface (i.E., the acl is active), the order in which the rules ar...
Page 376: Show Access-Group
C ommand l ine i nterface 4-136 show access-group this command shows the port assignments of acls. Command mode privileged executive example snmp commands controls access to this switch from management stations using the simple network management protocol (snmp), as well as the error types sent to t...
Page 378: Snmp-Server Contact
C ommand l ine i nterface 4-138 snmp-server contact this command sets the system contact string. Use the no form to remove the system contact information. Syntax snmp-server contact string no snmp-server contact string - string that describes the system contact information. (maximum length: 255 char...
Page 379: Snmp-Server Host
Snmp c ommands 4-139 command mode global configuration example related commands snmp-server contact (4-138) snmp-server host this command specifies the recipient of a simple network management protocol notification operation. Use the no form to remove the specified host. Syntax snmp-server host host...
Page 380
C ommand l ine i nterface 4-140 command usage • if you do not enter an snmp-server host command, no notifications are sent. In order to configure the switch to send snmp notifications, you must enter at least one snmp-server host command. In order to enable multiple hosts, you must issue a separate ...
Page 382: Show Snmp
C ommand l ine i nterface 4-142 show snmp this command checks the status of snmp communications. Default setting none command mode normal exec, privileged exec command usage this command provides information on the community access strings, counter information for snmp input and output protocol data...
Page 383
Snmp c ommands 4-143 example console#show snmp snmp traps: authentication: enabled link-up-down: enabled snmp communities: 1. Alpha, and the privilege is read-write 2. Private, and the privilege is read-write 3. Public, and the privilege is read-only 0 snmp packets input 0 bad snmp version errors 0 ...
Page 384: Interface Commands
C ommand l ine i nterface 4-144 interface commands these commands are used to display or set communication parameters for an ethernet port, aggregated link, or vlan. Table 4-40 interface commands command function mode page interface configures an interface type and enters interface configuration mod...
Page 385: Interface
I nterface c ommands 4-145 interface this command configures an interface type and enter interface configuration mode. Use the no form to remove a trunk. Syntax interface interface no interfaceport-channel channel-id interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port ...
Page 386: Speed-Duplex
C ommand l ine i nterface 4-146 default setting none command mode interface configuration (ethernet, port channel) example the following example adds a description to port 24. Speed-duplex this command configures the speed and duplex mode of a given interface when autonegotiation is disabled. Use th...
Page 387: Negotiation
I nterface c ommands 4-147 • when using the negotiation command to enable auto-negotiation, the optimal settings will be determined by the capabilities command. To set the speed/duplex mode under auto-negotiation, the required mode must be specified in the capabilities list for an interface. Example...
Page 388: Capabilities
C ommand l ine i nterface 4-148 example the following example configures port 11 to use autonegotiation. Related commands capabilities (4-148) speed-duplex (4-146) capabilities this command advertises the port capabilities of a given interface during autonegotiation. Use the no form with parameters ...
Page 389: Flowcontrol
I nterface c ommands 4-149 command usage when auto-negotiation is enabled with the negotiation command, the switch will negotiate the best settings for a link based on the capabilites command. When auto-negotiation is disabled, you must manually specify the link attributes with the speed-duplex and ...
Page 390: Shutdown
C ommand l ine i nterface 4-150 • to force flow control on or off (with the flowcontrol or no flowcontrol command), use the no negotiation command to disable auto-negotiation on the selected interface. • when using the negotiation command to enable auto-negotiation, the optimal settings will be dete...
Page 391
I nterface c ommands 4-151 command usage this command allows you to disable a port due to abnormal behavior (e.G., excessive collisions), and then reenable it after the problem has been resolved. You may also want to disable a port for security reasons. Example the following example disables port 5....
Page 392: Clear Counters
C ommand l ine i nterface 4-152 example the following shows how to configure broadcast storm control at 600 packets per second: clear counters this command clears statistics on an interface. Syntax clear counters interface interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port -...
Page 393: Show Interfaces Status
I nterface c ommands 4-153 show interfaces status this command displays the status for an interface. Syntax show interfaces status [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-52) • port-channel channel-id (range: 1-4) • vlan vlan-i...
Page 394: Show Interfaces Counters
C ommand l ine i nterface 4-154 example show interfaces counters this command displays interface statistics. Syntax show interfaces counters [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-52) • port-channel channel-id (range: 1-4) def...
Page 395
I nterface c ommands 4-155 command usage if no interface is specified, information on all interfaces is displayed. For a description of the items displayed by this command, see “showing port statistics” on page 3-114. Example console#show interfaces counters ethernet 1/7 ethernet 1/7 iftable stats: ...
Page 396: Show Interfaces Switchport
C ommand l ine i nterface 4-156 show interfaces switchport this command displays the administrative and operational status of the specified interfaces. Syntax show interfaces switchport [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-5...
Page 397
I nterface c ommands 4-157 table 4-41 interfaces switchport statistics field description broadcast threshold shows if broadcast storm suppression is enabled or disabled; if enabled it also shows the threshold level (page 4-151). Lacp status shows if link aggregation control protocol has been enabled...
Page 399: Show Port Monitor
M irror p ort c ommands 4-159 • the mirror port and monitor port speeds should match, otherwise traffic may be dropped from the monitor port. • you can only create a single mirror session. Example the following example configures the switch to mirror received packets from port 6 to 11: show port mon...
Page 400: Rate Limit Commands
C ommand l ine i nterface 4-160 example the following shows mirroring configured from port 6 to port 11: rate limit commands this function allows the network manager to control the maximum rate for traffic transmitted or received on an interface. Rate limiting is configured on interfaces at the edge...
Page 403: Show Rate-Limit
R ate l imit c ommands 4-163 show rate-limit use this command to display the rate limit granularity. Default setting fast ethernet interface – 3.3 mbps gigabit ethernet interface – 33.3 mbps command mode privileged exec command usage • for fast ethernet interfaces, the rate limit granularity is 512 ...
Page 404: Link Aggregation Commands
C ommand l ine i nterface 4-164 link aggregation commands ports can be statically grouped into an aggregate link (i.E., trunk) to increase the bandwidth of a network connection or to ensure fault recovery. Or you can use the link aggregation control protocol (lacp) to automatically negotiate a trunk...
Page 405
L ink a ggregation c ommands 4-165 guidelines for creating trunks general guidelines – • finish configuring port trunks before you connect the corresponding network cables between switches to avoid creating a loop. • a trunk can have up to eight ports. • the ports at both ends of a connection must b...
Page 406: Channel-Group
C ommand l ine i nterface 4-166 channel-group this command adds a port to a trunk. Use the no form to remove a port from a trunk. Syntax channel-group channel-id no channel-group channel-id - trunk index (range: 1-4) default setting the current port will be added to this trunk. Command mode interfac...
Page 407
L ink a ggregation c ommands 4-167 command mode interface configuration (ethernet) command usage • the ports on both ends of an lacp trunk must be configured for full duplex, either by forced mode or auto-negotiation. • a trunk formed with another switch using lacp will automatically be assigned the...
Page 408
C ommand l ine i nterface 4-168 example the following shows lacp enabled on ports 11-13. Because lacp has also been enabled on the ports at the other end of the links, the show interfaces status port-channel 1 command shows that trunk 1 has been established. Console(config)#interface ethernet 1/11 c...
Page 414
C ommand l ine i nterface 4-174 example console#show lacp 1 counters port channel : 1 ------------------------------------------------------------------- eth 1/ 1 ------------------------------------------------------------------- lacpdus sent : 21 lacpdus received : 21 marker sent : 0 marker receiv...
Page 415
L ink a ggregation c ommands 4-175 console#show lacp 1 internal port channel : 1 ------------------------------------------------------------------- oper key : 4 admin key : 0 eth 1/1 ------------------------------------------------------------------- lacpdus internal : 30 sec lacp system priority :...
Page 416
C ommand l ine i nterface 4-176 admin state, oper state administrative or operational values of the actor’s state parameters: • expired – the actor’s receive machine is in the expired state; • defaulted – the actor’s receive machine is using defaulted operational partner information, administrativel...
Page 417
L ink a ggregation c ommands 4-177 console#show lacp 1 neighbors port channel 1 neighbors ------------------------------------------------------------------- eth 1/1 ------------------------------------------------------------------- partner admin system id : 32768, 00-00-00-00-00-00 partner oper sy...
Page 418: Address Table Commands
C ommand l ine i nterface 4-178 address table commands these commands are used to configure the address table for filtering specified addresses, displaying current entries, clearing the table, or setting the aging time. Console#show lacp sysid port channel system priority system mac address --------...
Page 419: Mac-Address-Table Static
A ddress t able c ommands 4-179 mac-address-table static this command maps a static address to a destination port in a vlan. Use the no form to remove an address. Syntax mac-address-table static mac-address interface interface vlan vlan-id [action] no mac-address-table static mac-address vlan vlan-i...
Page 420: Show Mac-Address-Table
C ommand l ine i nterface 4-180 • a static address cannot be learned on another port until the address is removed with the no form of this command. Example clear mac-address-table dynamic this command removes any learned entries from the forwarding database and clears the transmit and receive counts...
Page 421: Mac-Address-Table Aging-Time
A ddress t able c ommands 4-181 default setting none command mode privileged exec command usage • the mac address table contains the mac addresses associated with each interface. Note that the type field may include the following types: - learned - dynamic address entries - permanent - static entry ...
Page 422
C ommand l ine i nterface 4-182 default setting 300 seconds command mode global configuration command usage the aging time is used to age out dynamically learned forwarding information. Example show mac-address-table aging-time this command shows the aging time for entries in the address table. Defa...
Page 423: Spanning Tree Commands
S panning t ree c ommands 4-183 spanning tree commands this section includes commands that configure the spanning tree algorithm (sta) globally for the switch, and commands that configure sta for the selected interface. Table 4-50 spanning tree commands command function mode page spanning-tree enabl...
Page 424: Spanning-Tree
C ommand l ine i nterface 4-184 spanning-tree this command enables the spanning tree algorithm globally for the switch. Use the no form to disable it. Syntax [no] spanning-tree default setting spanning tree is enabled. Command mode global configuration command usage the spanning tree algorithm (sta)...
Page 426: Spanning-Tree Forward-Time
C ommand l ine i nterface 4-186 spanning-tree forward-time this command configures the spanning tree bridge forward time globally for this switch. Use the no form to restore the default. Syntax spanning-tree forward-time seconds no spanning-tree forward-time seconds - time in seconds. (range: 4 - 30...
Page 427: Spanning-Tree Max-Age
S panning t ree c ommands 4-187 default setting 2 seconds command mode global configuration command usage this command sets the time interval (in seconds) at which the root device transmits a configuration message. Example spanning-tree max-age this command configures the spanning tree bridge maximu...
Page 428: Spanning-Tree Priority
C ommand l ine i nterface 4-188 becomes the designated port for the attached lan. If it is a root port, a new root port is selected from among the device ports attached to the network. Example spanning-tree priority this command configures the spanning tree priority globally for this switch. Use the...
Page 430
C ommand l ine i nterface 4-190 command mode global configuration command usage this command limits the maximum transmission rate for bpdus. Example spanning-tree spanning-disabled this command disables the spanning tree algorithm for the specified interface. Use the no form to reenable the spanning...
Page 431: Spanning-Tree Cost
S panning t ree c ommands 4-191 spanning-tree cost this command configures the spanning tree path cost for the specified interface. Use the no form to restore the default. Syntax spanning-tree cost cost no spanning-tree cost cost - the path cost for the port. (range: 1-200,000,000)) the recommended ...
Page 432: Spanning-Tree Port-Priority
C ommand l ine i nterface 4-192 spanning-tree port-priority this command configures the priority for the specified interface. Use the no form to restore the default. Syntax spanning-tree port-priority priority no spanning-tree port-priority priority - the priority for a port. (range: 0-240, in steps...
Page 433: Spanning-Tree Portfast
S panning t ree c ommands 4-193 default setting disabled command mode interface configuration (ethernet, port channel) command usage • you can enable this option if an interface is attached to a lan segment that is at the end of a bridged lan or to an end node. Since end nodes cannot cause forwardin...
Page 434: Spanning-Tree Link-Type
C ommand l ine i nterface 4-194 command mode interface configuration (ethernet, port channel) command usage • this command is used to enable/disable the fast spanning-tree mode for the selected port. In this mode, ports skip the discarding and learning states, and proceed straight to forwarding. • s...
Page 435
S panning t ree c ommands 4-195 default setting auto command mode interface configuration (ethernet, port channel) command usage • specify a point-to-point link if the interface can only be connected to exactly one other bridge, or a shared link if it can be connected to two or more bridges. • when ...
Page 436: Show Spanning-Tree
C ommand l ine i nterface 4-196 command usage if at any time the switch detects stp bpdus, including configuration or topology change notification bpdus, it will automatically set the selected interface to forced stp-compatible mode. However, you can also use the spanning-tree protocol-migration com...
Page 437
S panning t ree c ommands 4-197 • for a description of the items displayed under “spanning-tree information,” see “configuring global settings” on page 3 -130. For a description of the items displayed for specific interfaces, see “displaying interface settings” on page 3 -134. Example console#show s...
Page 438: Vlan Commands
C ommand l ine i nterface 4-198 vlan commands a vlan is a group of ports that can be located anywhere in the network, but communicate as though they belong to the same physical segment. This section describes commands used to create vlan groups, add port members, specify how vlan tagging is used, an...
Page 439: Vlan
Vlan c ommands 4-199 command mode global configuration command usage • use the vlan database command mode to add, change, and delete vlans. After finishing configuration changes, you can display the vlan settings by entering the show vlan command. • use the interface vlan command mode to define the ...
Page 440
C ommand l ine i nterface 4-200 default setting by default only vlan 1 exists and is active. Command mode vlan database configuration command usage • no vlan vlan-id deletes the vlan. • no vlan vlan-id name removes the vlan name. • no vlan vlan-id state returns the vlan to the default state (i.E., a...
Page 441: Configuring Vlan Interfaces
Vlan c ommands 4-201 configuring vlan interfaces interface vlan this command enters interface configuration mode for vlans, which is used to configure vlan parameters for a physical interface. Syntax interface vlan vlan-id vlan-id - id of the configured vlan. (range: 1-4094, no leading zeroes) defau...
Page 442: Switchport Mode
C ommand l ine i nterface 4-202 example the following example shows how to set the interface configuration mode to vlan 1, and then assign an ip address to the vlan: related commands shutdown (4-150) switchport mode this command configures the vlan membership mode for a port. Use the no form to rest...
Page 443
Vlan c ommands 4-203 example the following shows how to set the configuration mode to port 1, and then set the switchport mode to hybrid: related commands switchport acceptable-frame-types (4-203) switchport acceptable-frame-types this command configures the acceptable frame types for a port. Use th...
Page 444: Switchport Ingress-Filtering
C ommand l ine i nterface 4-204 related commands switchport mode (4-202) switchport ingress-filtering this command enables ingress filtering for an interface. Use the no form to restore the default. Syntax [no] switchport ingress-filtering default setting disabled command mode interface configuratio...
Page 445: Switchport Native Vlan
Vlan c ommands 4-205 switchport native vlan this command configures the pvid (i.E., default vlan id) for a port. Use the no form to restore the default. Syntax switchport native vlan vlan-id no switchport native vlan vlan-id - default vlan id for a port. (range: 1-4094, no leading zeroes) default se...
Page 447: Switchport Forbidden Vlan
Vlan c ommands 4-207 • if a vlan on the forbidden list for an interface is manually added to that interface, the vlan is automatically removed from the forbidden list for that interface. Example the following example shows how to add vlans 1, 2, 5 and 6 to the allowed list as tagged vlans for port 1...
Page 449: Configuring Private Vlans
Vlan c ommands 4-209 command mode normal exec, privileged exec example the following example shows how to display information for vlan 1: configuring private vlans private vlans provide port-based security and isolation between ports within the assigned vlan. This switch supports three types of priv...
Page 450
C ommand l ine i nterface 4-210 to configure private vlans, follow these steps: 1. Use the private-vlan command to designate one or more isolated or community vlans and the primary vlan that will channel traffic outside the community groups. 2. Use the private-vlan association command to map the com...
Page 454
C ommand l ine i nterface 4-214 switchport private-vlan host-association use this command to associate an interface with a secondary vlan. Use the no form to remove this association. Syntax switchport private-vlan host-association secondary-vlan-id no switchport private-vlan host-association seconda...
Page 455
Vlan c ommands 4-215 command mode interface configuration (ethernet, port channel) command usage all ports assigned to an isolated vlan can pass traffic between group members, but must communicate with resources outside of the group via a promiscuous port. Example switchport private-vlan mapping use...
Page 457: Bridge-Ext Gvrp
Gvrp and b ridge e xtension c ommands 4-217 gvrp and bridge extension commands garp vlan registration protocol defines a way for switches to exchange vlan information in order to automatically register vlan members on interfaces across the network. This section describes how to enable gvrp for indiv...
Page 458: Show Bridge-Ext
C ommand l ine i nterface 4-218 command mode global configuration command usage gvrp defines a way for switches to exchange vlan information in order to register vlan members on ports across the network. This function should be enabled to permit automatic vlan registration, and to support vlans whic...
Page 459: Switchport Gvrp
Gvrp and b ridge e xtension c ommands 4-219 switchport gvrp this command enables gvrp for a port. Use the no form to disable it. Syntax [no] switchport gvrp default setting disabled command mode interface configuration (ethernet, port channel) example show gvrp configuration this command shows if gv...
Page 461: Show Garp Timer
Gvrp and b ridge e xtension c ommands 4-221 example related commands show garp timer (4-221) show garp timer this command shows the garp timers for the selected interface. Syntax show garp timer [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (r...
Page 462: Priority Commands
C ommand l ine i nterface 4-222 priority commands the commands described in this section allow you to specify which data packets have greater precedence when traffic is buffered in the switch due to congestion. This switch supports cos with four priority queues for each port. Data packets in a port’...
Page 464: Switchport Priority Default
C ommand l ine i nterface 4-224 example the following example sets the queue mode to strict priority service mode: switchport priority default this command sets a priority for incoming untagged frames. Use the no form to restore the default value. Syntax switchport priority default default-priority-...
Page 465: Queue Bandwidth
P riority c ommands 4-225 therefore, any inbound frames that do not have priority tags will be placed in queue 0 of the output port. (note that if the output port is an untagged member of the associated vlan, these frames are stripped of all vlan tags prior to transmission.) example the following ex...
Page 466: Queue Cos-Map
C ommand l ine i nterface 4-226 related commands show queue bandwidth (4-227) queue cos-map this command assigns class of service (cos) values to the priority queues (i.E., hardware output queues 0 - 3). Use the no form set the cos map to the default values. Syntax queue cos-map queue_id [cos1 ... C...
Page 467: Show Queue Mode
P riority c ommands 4-227 example the following example shows how to map cos values 0, 1 and 2 to egress queue 0, value 3 to egress queue 1, values 4 and 5 to egress queue 2, and values 6 and 7 to egress queue 3: related commands show queue cos-map (4-228) show queue mode this command shows the curr...
Page 468: Show Queue Cos-Map
C ommand l ine i nterface 4-228 command mode privileged exec example show queue cos-map this command shows the class of service priority map. Syntax show queue cos-map [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-52) • port-channel ...
Page 469
P riority c ommands 4-229 priority commands (layer 3 and 4) map ip port (global configuration) this command enables ip port mapping (i.E., class of service mapping for tcp/udp sockets). Use the no form to disable ip port mapping. Syntax [no] map ip port table 4-60 priority commands (layer 3 and 4) c...
Page 470
C ommand l ine i nterface 4-230 default setting disabled command mode global configuration command usage the precedence for priority mapping is ip port, ip precedence or ip dscp, and default switchport priority. Example the following example shows how to enable tcp/udp port mapping globally: map ip ...
Page 471
P riority c ommands 4-231 example the following example shows how to map http traffic to cos value 0: map ip precedence (global configuration) this command enables ip precedence mapping (i.E., ip type of service). Use the no form to disable ip precedence mapping. Syntax [no] map ip precedence defaul...
Page 472
C ommand l ine i nterface 4-232 map ip precedence (interface configuration) this command sets ip precedence priority (i.E., ip type of service priority). Use the no form to restore the default table. Syntax map ip precedence ip-precedence-value cos cos-value no map ip precedence • precedence-value -...
Page 473
P riority c ommands 4-233 map ip dscp (global configuration) this command enables ip dscp mapping (i.E., differentiated services code point mapping). Use the no form to disable ip dscp mapping. Syntax [no] map ip dscp default setting disabled command mode global configuration command usage • the pre...
Page 474
C ommand l ine i nterface 4-234 default setting the dscp default values are defined in the following table. Note that all the dscp values that are not specified are mapped to cos value 0. Command mode interface configuration (ethernet, port channel) command usage • the precedence for priority mappin...
Page 475: Show Map Ip Port
P riority c ommands 4-235 show map ip port use this command to show the ip port priority map. Syntax show map ip port [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-52) • port-channel channel-id (range: 1-4) default setting none comma...
Page 476: Show Map Ip Precedence
C ommand l ine i nterface 4-236 show map ip precedence this command shows the ip precedence priority map. Syntax show map ip precedence [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-52) • port-channel channel-id (range: 1-4) default ...
Page 477: Show Map Ip Dscp
P riority c ommands 4-237 show map ip dscp this command shows the ip dscp priority map. Syntax show map ip dscp [interface] interface • ethernet unit/port - unit - stack unit. (this is unit 1) - port - port number. (range: 1-52) • port-channel channel-id (range: 1-4) default setting none command mod...
Page 478: Multicast Filtering Commands
C ommand l ine i nterface 4-238 multicast filtering commands this switch uses igmp (internet group management protocol) to query for any attached hosts that want to receive a specific multicast service. It identifies the ports containing hosts requesting a service and sends data out to those ports o...
Page 479: Ip Igmp Snooping
M ulticast f iltering c ommands 4-239 ip igmp snooping this command enables igmp snooping on this switch. Use the no form to disable it. Syntax [no] ip igmp snooping default setting enabled command mode global configuration example the following example enables igmp snooping. Ip igmp snooping vlan s...
Page 480: Ip Igmp Snooping Version
C ommand l ine i nterface 4-240 command mode global configuration example the following shows how to statically configure a multicast group on a port: ip igmp snooping version this command configures the igmp snooping version. Use the no form to restore the default. Syntax ip igmp snooping version {...
Page 481: Show Ip Igmp Snooping
M ulticast f iltering c ommands 4-241 show ip igmp snooping this command shows the igmp snooping configuration. Default setting none command mode privileged exec command usage see configuring igmp snooping and query parameters” on page 3-184 for a description of the displayed items. Example the foll...
Page 482
C ommand l ine i nterface 4-242 command mode privileged exec command usage member types displayed include igmp or user, depending on selected options. Example the following shows the multicast entries learned through igmp snooping for vlan 1: igmp query commands (layer 2) console#show mac-address-ta...
Page 483: Ip Igmp Snooping Querier
M ulticast f iltering c ommands 4-243 ip igmp snooping querier this command enables the switch as an igmp querier. Use the no form to disable it. Syntax [no] ip igmp snooping querier default setting enabled command mode global configuration command usage if enabled, the switch will serve as querier ...
Page 484
C ommand l ine i nterface 4-244 command usage the query count defines how long the querier waits for a response from a multicast client before taking action. If a querier has sent a number of queries defined by this command, but a client has not responded, a countdown timer is started using the time...
Page 485
M ulticast f iltering c ommands 4-245 ip igmp snooping query-max-response-time this command configures the query report delay. Use the no form to restore the default. Syntax ip igmp snooping query-max-response-time seconds no ip igmp snooping query-max-response-time seconds - the report delay advert...
Page 486
C ommand l ine i nterface 4-246 ip igmp snooping router-port-expire-time this command configures the query timeout. Use the no form to restore the default. Syntax ip igmp snooping router-port-expire-time seconds no ip igmp snooping router-port-expire-time seconds - the time the switch waits after th...
Page 487
M ulticast f iltering c ommands 4-247 static multicast routing commands ip igmp snooping vlan mrouter this command statically configures a multicast router port. Use the no form to remove the configuration. Syntax [no] ip igmp snooping vlan vlan-id mrouter interface • vlan-id - vlan id (range: 1-409...
Page 488
C ommand l ine i nterface 4-248 example the following shows how to configure port 11 as a multicast router port within vlan 1: show ip igmp snooping mrouter this command displays information on statically configured and dynamically learned multicast router ports. Syntax show ip igmp snooping mrouter...
Page 489: Ip Interface Commands
Ip i nterface c ommands 4-249 ip interface commands an ip addresses may be used for management access to the switch over your network. The ip address for this switch is obtained via dhcp by default. You can manually configure a specific ip address, or direct the device to obtain an address from a bo...
Page 490
C ommand l ine i nterface 4-250 default setting dhcp command mode interface configuration (vlan) command usage • you must assign an ip address to this device to gain management access over the network. You can manually configure a specific ip address, or direct the device to obtain an address from a...
Page 491: Ip Default-Gateway
Ip i nterface c ommands 4-251 ip default-gateway this command establishes a static route between this switch and devices that exist on another network segment. Use the no form to remove the static route. Syntax ip default-gateway gateway no ip default-gateway gateway - ip address of the default gate...
Page 492: Show Ip Interface
C ommand l ine i nterface 4-252 command usage • this command issues a bootp or dhcp client request for any ip interface that has been set to bootp or dhcp mode via the ip address command. • dhcp requires the server to reassign the client’s last address if available. • if the bootp or dhcp server has...
Page 493: Show Ip Redirects
Ip i nterface c ommands 4-253 show ip redirects this command shows the default gateway configured for this device. Default setting none command mode privileged exec example related commands show ip interface (4-252) ping this command sends icmp echo request packets to another node on the network. Sy...
Page 494
C ommand l ine i nterface 4-254 command usage • use the ping command to see if another site on the network can be reached. • following are some results of the ping command: - normal response - the normal response occurs in one to ten seconds, depending on network traffic. - destination does not resp...
Page 495: Software Features
A-1 a ppendix a s oftware s pecifications software features authentication local, radius, tacacs, port (802.1x), https, ssh, port security access control lists ip, mac (up to 88 lists) dhcp client port configuration 100base-tx: 10/100 mbps, half/full duplex 1000base-t: 10/100 mbps at half/full duple...
Page 496: Management Features
S oftware s pecifications a-2 spanning tree algorithm spanning tree protocol (stp, ieee 802.1d) rapid spanning tree protocol (rstp, ieee 802.1w) vlan support up to 255 groups; port-based or tagged (802.1q), gvrp for automatic vlan learning, private vlans class of service supports four levels of prio...
Page 497: Standards
S oftware s pecifications a-3 rmon groups 1, 2, 3, 9 (statistics, history, alarm, event) standards ieee 802.1d spanning tree protocol and traffic priorities ieee 802.1p priority tags ieee 802.1q vlan ieee 802.1w rapid spanning tree protocol ieee 802.1x port authentication ieee 802.3-2002 ethernet, f...
Page 498: Management Information Bases
S oftware s pecifications a-4 management information bases bridge mib (rfc 1493) entity mib (rfc 2737) ether-like mib (rfc 2665) extended bridge mib (rfc 2674) extensible snmp agents mib (rfc 2742) forwarding table mib (rfc 2096) igmp mib (rfc 2933) interface group mib (rfc 2233) interfaces evolutio...
Page 499
B-1 a ppendix b t roubleshooting problems accessing the management interface table b-1 troubleshooting chart symptom action cannot connect using telnet, web browser, or snmp software • be sure the switch is powered up. • check network cabling between the management station and the switch. • check th...
Page 500
T roubleshooting b-2 cannot connect using secure shell • if you cannot connect using ssh, you may have exceeded the maximum number of concurrent telnet/ssh sessions permitted. Try connecting again at a later time. • be sure the control parameters for the ssh server are properly configured on the swi...
Page 501: Using System Logs
U sing s ystem l ogs b-3 using system logs if a fault does occur, refer to the installation guide to ensure that the problem you encountered is actually caused by the switch. If the problem appears to be caused by the switch, follow these steps: 1. Enable logging. 2. Set the error messages reported ...
Page 502
T roubleshooting b-4.
Page 503
Glossary-1 g lossary access control list (acl) acls can limit network traffic and restrict access to certain users or devices by checking each packet for certain ip or mac (i.E., layer 2) information. Boot protocol (bootp) bootp is used to provide bootup information for network devices, including ip...
Page 504
G lossary glossary-2 dynamic host control protocol (dhcp) provides a framework for passing configuration information to hosts on a tcp/ip network. Dhcp is based on the bootstrap protocol (bootp), adding the capability of automatic allocation of reusable network addresses and additional configuration...
Page 505
G lossary glossary-3 ieee 802.1d specifies a general method for the operation of mac bridges, including the spanning tree protocol. Ieee 802.1q vlan tagging—defines ethernet frame tags which carry vlan information. It allows switches to assign endstations to different virtual lans, and defines a sta...
Page 506
G lossary glossary-4 igmp query on each subnetwork, one igmp-capable device will act as the querier — that is, the device that asks all hosts to report on the ip multicast groups they wish to join or to which they already belong. The elected querier will be the device with the lowest ip address in t...
Page 507
G lossary glossary-5 link aggregation see port trunk. Link aggregation control protocol (lacp) allows ports to automatically negotiate a trunked link with lacp-configured ports on another device. Management information base (mib) an acronym for management information base. It is a set of database ob...
Page 508
G lossary glossary-6 port mirroring a method whereby data on a target port is mirrored to a monitor port for troubleshooting with a logic analyzer or rmon probe. This allows data on the target port to be studied unobstructively. Port trunk defines a network link aggregation and trunking method which...
Page 509
G lossary glossary-7 simple network management protocol (snmp) the application protocol in the internet suite of protocols which offers network management services. Simple network time protocol (sntp) sntp allows a device to set its internal clock based on periodic updates from a network time protoc...
Page 510
G lossary glossary-8 user datagram protocol (udp) udp provides a datagram mode for packet-switched communications. It uses ip as the underlying transport mechanism to provide access to ip-like services. Udp packets are delivered just like ip packets – connection-less datagrams that may be discarded ...
Page 511: Numerics
Index-1 numerics 802.1x, port authentication 3-67 a acceptable frame type 3-155 , 4-203 access control list see acl acl extended ip 3-79 , 4-117 , 4-118 , 4-122 mac 3-80 , 4-117 , 4-128 , 4-128 – 4-131 standard ip 3-79 , 4-117 , 4-118 , 4-120 address table 3-121 , 4-178 aging time 3-124 , 4-182 b bo...
Page 512
I ndex index-2 g garp vlan registration protocol see gvrp gateway, default 3-18 , 4-250 gvrp global setting 4-216 interface configuration 3-156 , 4-218 gvrp, global setting 3-146 h hardware version, displaying 3-13 , 4-84 https 3-54 , 4-42 https, secure server 3-54 , 4-42 i ieee 802.1d 3-125 , 4-185...
Page 513
I ndex index-3 p password, line 4-17 , 4-18 passwords 2-5 administrator setting 3-48 , 4-35 path cost 3-127 , 3-136 method 3-132 , 4-189 sta 3-127 , 3-136 , 4-189 port authentication 3-67 port priority configuring 3-167 , 4-221 default ingress 3-167 , 4-223 sta 3-136 , 4-192 port security, configuri...
Page 514
I ndex index-4 sta 3-124 , 4-183 edge port 3-137 , 3-140 , 4-192 global settings, configuring 3-130 , 4-184 – 4-189 global settings, displaying 3-126 , 4-196 interface settings 3-134 , 4-191 – 4-195 , 4-196 link type 3-137 , 3-140 , 4-194 path cost 3-127 , 3-136 , 4-191 path cost method 3-132 , 4-18...
Page 516
38 tesla irvine, ca 92618 phone: (949) 679-8000 for technical support, call: from u.S.A. And canada (24 hours a day, 7 days a week) (800) smc-4-you; phn: (949) 679-8000; fax: (949) 679-1481 from europe: contact details can be found on www.Smc-europe.Com or www.Smc.Com internet e-mail addresses: tech...