- DL manuals
- SMC Networks
- Network Router
- 6826MPE
- Management Manual
SMC Networks 6826MPE Management Manual
TigerStack III 10/100
24-Port Fast Ethernet Switch
◆ 24 auto-MDI/MDI-X 10BASE-T/100BASE-TX ports
◆ 10BASE-T/100BASE-TX ports support PoE capabilities*
◆ 2 Gigabit combo ports (RJ-45/SFP)
◆ 8.8 Gbps of aggregate bandwidth
◆ Stacks up to 8 units
◆ Non-blocking switching architecture
◆ Spanning Tree Protocol, RSTP, and MSTP
◆ Up to six LACP or static 4-port trunks
◆ RADIUS and TACACS+ authentication
◆ Rate limiting for bandwidth management
◆ CoS support for four-level priority
◆ Full support for VLANs with GVRP
◆ IP Multicasting with IGMP Snooping
◆ Manageable via console, Web, SNMP/RMON
Management Guide
SMC6824M
SMC6824MPE*
SMC6826MPE*
Summary of 6826MPE
Page 1
Tigerstack iii 10/100 24-port fast ethernet switch ◆ 24 auto-mdi/mdi-x 10base-t/100base-tx ports ◆ 10base-t/100base-tx ports support poe capabilities* ◆ 2 gigabit combo ports (rj-45/sfp) ◆ 8.8 gbps of aggregate bandwidth ◆ stacks up to 8 units ◆ non-blocking switching architecture ◆ spanning tree pr...
Page 2
C ommand l ine i nterface 4-23 stopbits this command sets the number of the stop bits transmitted per byte. Use the no form to restore the default setting. Syntax stopbits {1
Page 3: Tigerstack III 10/100
38 tesla irvine, ca 92618 phone: (949) 679-8000 tigerstack iii 10/100 management guide from smc’s tiger line of feature-rich workgroup lan solutions june 2005 pub. # 150200037700a.
Page 4
Information furnished by smc networks, inc. (smc) is believed to be accurate and reliable. However, no responsibility is assumed by smc for its use, nor for any infringements of patents or other rights of third parties which may result from its use. No license is granted by implication or otherwise ...
Page 5
I l imited w arranty limited warranty statement: smc networks, inc. (“smc”) warrants its products to be free from defects in workmanship and materials, under normal use and service, for the applicable warranty term. All smc products carry a standard 90-day limited warranty from the date of purchase ...
Page 6
L imited w arranty ii warranties exclusive: if an smc product does not operate as warranted above, customer’s sole remedy shall be repair or replacement of the product in question, at smc’s option. The foregoing warranties and remedies are exclusive and are in lieu of all other warranties or conditi...
Page 7
Iii t able of c ontents 1 introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1 key features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1 description of software features . . . . . . . . . . . . . . . . . . . . . . . ....
Page 8
T able of c ontents iv basic configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13 displaying system information . . . . . . . . . . . . . . . . . . . . . . . . . 3-13 displaying switch hardware/software versions . . . . . . . . . . . 3-15 displaying brid...
Page 9
T able of c ontents v replacing the default secure-site certificate . . . . . . . . . . 3-77 configuring the secure shell . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-78 generating the host key pair . . . . . . . . . . . . . . . . . . . . . . 3-81 configuring the ssh server . . . . . . . ...
Page 10
T able of c ontents vi power over ethernet settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-145 switch power status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-146 setting a switch power budget . . . . . . . . . . . . . . . . . . . . . . . . 3-147 disp...
Page 11
T able of c ontents vii mapping cos values to egress queues . . . . . . . . . . . . . 3-204 selecting the queue mode . . . . . . . . . . . . . . . . . . . . . . . . 3-206 setting the service weight for traffic classes . . . . . . . . . 3-207 layer 3/4 priority settings . . . . . . . . . . . . . . . ...
Page 12
T able of c ontents viii negating the effect of commands . . . . . . . . . . . . . . . . . . . . . . . 4-6 using command history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6 understanding command modes . . . . . . . . . . . . . . . . . . . . . . . . 4-6 exec commands . . . . . ....
Page 13
T able of c ontents ix enable password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-36 ip filter commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-37 management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-37 show manag...
Page 14
T able of c ontents x logging sendmail . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-67 show logging sendmail . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-68 time commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-68 sntp client . . ...
Page 15
T able of c ontents xi radius-server key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-102 radius-server retransmit . . . . . . . . . . . . . . . . . . . . . . . . . . 4-103 radius-server timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-103 show radius-server . ....
Page 16
T able of c ontents xii match access-list ip . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-137 show marking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-138 mac acls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-138 access-li...
Page 17
T able of c ontents xiii negotiation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-173 capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-174 flowcontrol . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Page 18
T able of c ontents xiv spanning-tree transmission-limit . . . . . . . . . . . . . . . . . . . . . . . 4-213 spanning-tree backup-root . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-214 spanning-tree mst-configuration . . . . . . . . . . . . . . . . . . . . . . . 4-214 mst vlan . . . . . ...
Page 19
T able of c ontents xv switchport private-vlan host-association . . . . . . . . . . . . . 4-246 switchport private-vlan mapping . . . . . . . . . . . . . . . . . . . 4-246 show vlan private-vlan . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-247 gvrp and bridge extension commands . . . . . ...
Page 20
T able of c ontents xvi igmp query commands (layer 2) . . . . . . . . . . . . . . . . . . . . 4-273 ip igmp snooping querier . . . . . . . . . . . . . . . . . . . . . . . . . 4-273 ip igmp snooping query-count . . . . . . . . . . . . . . . . . . . . . 4-274 ip igmp snooping query-interval . . . . . ...
Page 21: Ppendices
T able of c ontents xvii a ppendices : a software specifications . . . . . . . . . . . . . . . . . . . . . . . . .A-1 software features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-1 management features . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Page 22
T able of c ontents xviii.
Page 23
Xix t ables table 1-1 key features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1 table 1-2 system defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7 table 3-1 web page configuration buttons . . . . . . . . . . . . . . . . . . . 3-4 table 3-2 sw...
Page 24
T ables xx table 4-19 show logging flash/ram - display description . . . . . . . . 4-62 table 4-20 show logging trap - display description . . . . . . . . . . . . . 4-63 table 4-21 smtp commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-64 table 4-22 time commands . . . . . . . ....
Page 25
T ables xxi table 4-56 spanning tree commands . . . . . . . . . . . . . . . . . . . . . . 4-204 table 4-57 vlan commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-230 table 4-58 editing vlan groups . . . . . . . . . . . . . . . . . . . . . . . . . 4-230 table 4-59 configuring vlan in...
Page 26
T ables xxii.
Page 27
Xxiii f igures figure 3-1 home page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3 figure 3-2 front panel indicators . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-5 figure 3-3 system information . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-14 figur...
Page 28
F igures xxiv figure 3-37 802.1x global information . . . . . . . . . . . . . . . . . . . . . . 3-89 figure 3-38 802802.1x global configuration . . . . . . . . . . . . . . . . . . 3-90 figure 3-39 802.1x port configuration . . . . . . . . . . . . . . . . . . . . . . . 3-92 figure 3-40 displaying 802...
Page 29
F igures xxv figure 3-74 mstp port information . . . . . . . . . . . . . . . . . . . . . . . . 3-175 figure 3-75 mstp port configuration . . . . . . . . . . . . . . . . . . . . . . . 3-178 figure 3-76 globally enabling gvrp . . . . . . . . . . . . . . . . . . . . . . . 3-183 figure 3-77 displaying b...
Page 30
F igures xxvi.
Page 31: Key Features
1-1 c hapter 1 i ntroduction these switches provide a broad range of features for layer 2 switching. They include a management agent that allows you to configure the features listed in this manual. The default configuration can be used for most of the features provided by these switches. However, th...
Page 32
I ntroduction 1-2 description of software features the switch provides a wide range of advanced performance enhancing features. Flow control eliminates the loss of packets due to bottlenecks caused by port saturation. Broadcast storm suppression prevents broadcast traffic storms from engulfing the n...
Page 33
D escription of s oftware f eatures 1-3 priority queueing ensures the minimum delay for moving real-time multimedia data across the network. While multicast filtering provides support for real-time network applications. Some of the management features are briefly described below. Configuration backu...
Page 34
I ntroduction 1-4 switch connections. Flow control should also be enabled to control network traffic during periods of congestion and prevent the loss of packets when port buffer thresholds are exceeded. The switch supports flow control based on the ieee 802.3x standard. Rate limiting – this feature...
Page 35
D escription of s oftware f eatures 1-5 ieee 802.1d bridge – the switch supports ieee 802.1d transparent bridging. The address table facilitates data switching by learning addresses, and then filtering or forwarding traffic based on this information. The address table supports up to 8k addresses. St...
Page 36
I ntroduction 1-6 for different vlans. It simplifies network management, provides for even faster convergence than rstp by limiting the size of each region, and prevents vlan members from being segmented from the rest of the group (as sometimes occurs with ieee 802.1d stp). Virtual lans – the switch...
Page 37: System Defaults
S ystem d efaults 1-7 priorities are mapped to a class of service value by the switch, and the traffic then sent to the corresponding output queue. Multicast filtering – specific multicast traffic can be assigned to its own vlan to ensure that it does not interfere with normal network traffic and to...
Page 38
I ntroduction 1-8 authentication privileged exec level username “admin” password “admin” normal exec level username “guest” password “guest” enable privileged exec from normal exec level password “super” radius authentication disabled tacacs authentication disabled 802.1x port authentication disable...
Page 39
S ystem d efaults 1-9 power over ethernet * status enabled (all ports) rate limiting input and output limits disabled port trunking static trunks none lacp disabled broadcast storm protection status enabled (all ports) broadcast limit rate 500 packets per second spanning tree protocol status enabled...
Page 40
I ntroduction 1-10 ip settings management vlan 1 ip address 0.0.0.0 subnet mask 255.0.0.0 default gateway 0.0.0.0 dhcp enabled bootp disabled multicast filtering igmp snooping snooping: enabled querier: disabled system log status enabled messages logged levels 0-7 (all) messages logged to flash leve...
Page 41: Connecting To The Switch
2-1 c hapter 2 i nitial c onfiguration connecting to the switch configuration options the switch includes a built-in network management agent. The agent offers a variety of management options, including snmp, rmon and a web-based interface. A pc may also be connected directly to the switch for confi...
Page 42
I nitial c onfiguration 2-2 the switch’s cli configuration program, web interface, and snmp agent allow you to perform the following management functions: • set user names and passwords • set an ip interface for the management vlan • configure snmp parameters • enable/disable any port • set the spee...
Page 43: Required Connections
C onnecting to the s witch 2-3 required connections the switch provides an rs-232 serial port that enables a connection to a pc or terminal for monitoring and configuring the switch. A null-modem console cable is provided with the switch. Note: when configuring a stack, connect to the console port o...
Page 44: Remote Connections
I nitial c onfiguration 2-4 notes: 1. When using hyperterminal with microsoft ® windows ® 2000, make sure that you have windows 2000 service pack 2 or later installed. Windows 2000 service pack 2 fixes the problem of arrow keys not functioning in hyperterminal’s vt100 emulation. See www.Microsoft.Co...
Page 45: Stack Operations
S tack o perations 2-5 note: the onboard program only provides access to basic configuration functions. To access the full range of snmp management functions, you must use snmp-based network management software. Stack operations up to eight switches can be stacked together as described in the instal...
Page 46: Basic Configuration
I nitial c onfiguration 2-6 resilient ip interface for management access the stack functions as one integral system for management and configuration purposes. You can therefore manage the stack through any port configured as part of the vlan used for management access. The master unit does not even ...
Page 47: Setting Passwords
B asic c onfiguration 2-7 4. The session is opened and the cli displays the “console#” prompt indicating you have access at the privileged exec level. Setting passwords note: if this is your first time to log into the cli program, you should define new passwords for both default user names using the...
Page 48
I nitial c onfiguration 2-8 dynamic — the switch sends ip configuration requests to bootp or dhcp address allocation servers on the network. Note: only one vlan interface can be assigned an ip address (the default is vlan 1). This defines the management vlan, the only vlan through which you can gain...
Page 49
B asic c onfiguration 2-9 4. To set the ip address of the default gateway for the network to which the switch belongs, type “ip default-gateway gateway,” where “gateway” is the ip address of the default gateway. Press . Dynamic configuration if you select the “bootp” or “dhcp” option, ip will be ena...
Page 50
I nitial c onfiguration 2-10 4. Type “ip dhcp restart” to begin broadcasting service requests. Press . 5. Wait a few minutes, and then check the ip configuration settings by typing the “show ip interface” command. Press . 6. Then save your configuration changes by typing “copy running-config startup...
Page 51
B asic c onfiguration 2-11 entire mib tree. However, you may assign new views to version 1 or 2c community strings that suit your specific security requirements (see page 3-67). Community strings (for snmp version 1 and 2c clients) community strings are used to control management access to snmp vers...
Page 52
I nitial c onfiguration 2-12 community strings. If there are no community strings, then snmp management access from snmp v1 and v2c clients is disabled. Trap receivers you can also specify snmp stations that are to receive traps from the switch. To configure a trap receiver, use the “snmp-server hos...
Page 53
B asic c onfiguration 2-13 used for authentication, provides the password “greenpeace” for authentication, and the password “einstien” for encryption. For a more detailed explanation on how to configure the switch for access from snmp v3 clients, refer to “simple network management protocol” on page...
Page 54: Managing System Files
I nitial c onfiguration 2-14 managing system files the switch’s flash memory supports three types of system files that can be managed by the cli program, web interface, or snmp. The switch’s file system allows files to be uploaded and downloaded, copied, deleted, and set as a start-up file. The thre...
Page 55
C onfiguring p ower over e thernet 2-15 configuring power over ethernet the 24 10/100 mbps ports on the smc6824mpe and smc6826mpe support the ieee 802.3af power-over-ethernet (poe) standard that enables dc power to be supplied to attached devices over the unused pairs of wires in the connecting ethe...
Page 56
I nitial c onfiguration 2-16.
Page 57: Using The Web Interface
3-1 c hapter 3 c onfiguring the s witch using the web interface this switch provides an embedded http web agent. Using a web browser you can configure the switch and view statistics to monitor network activity. The web agent can be accessed by any computer on the network using a standard web browser...
Page 58
C onfiguring the s witch 3-2 notes: 1. You are allowed three attempts to enter the correct password; on the third failed attempt the current connection is terminated. 2. If you log into the web interface as guest (normal exec level), you can view the configuration settings or change the guest passwo...
Page 59: Home Page
N avigating the w eb b rowser i nterface 3-3 navigating the web browser interface to access the web-browser interface you must first enter a user name and password. The administrator has read/write access to all configuration parameters and statistics. The default user name and password for the admi...
Page 60: Configuration Options
C onfiguring the s witch 3-4 configuration options configurable parameters have a dialog box or a drop-down list. Once a configuration change has been made on a page, be sure to click on the apply button to confirm the new setting. The following table summarizes the web page configuration buttons. N...
Page 61: Panel Display
N avigating the w eb b rowser i nterface 3-5 panel display the web agent displays an image of the switch’s ports. The mode can be set to display different information for the ports, including active (i.E., up or down), duplex (i.E., half or full duplex), or flow control (i.E., with or without flow c...
Page 62: Main Menu
C onfiguring the s witch 3-6 main menu using the onboard web agent, you can define system parameters, manage and control the switch, and all its ports, or monitor network conditions. The following table briefly describes the selections available from this program. Table 3-2 switch main menu menu des...
Page 63
N avigating the w eb b rowser i nterface 3-7 sntp 3-43 configuration configures sntp client settings, including broadcast mode or a specified list of servers 3-43 clock time zone sets the local time zone for the system clock 3-43 snmp 3-45 configuration configures community strings and related trap ...
Page 64
C onfiguring the s witch 3-8 802.1x port authentication 3-88 information displays the global configuration setting 3-89 configuration configures the global configuration setting 3-88 port configuration sets parameters for individual ports 3-94 statistics displays protocol statistics for the selected...
Page 65
N avigating the w eb b rowser i nterface 3-9 broadcast control sets the broadcast storm threshold for each port 3-135 mirror port configuration sets the source and target ports for mirroring 3-136 rate limit 3-138 input port configuration sets the input rate limit for each port 3-138 input trunk con...
Page 66
C onfiguring the s witch 3-10 trunk configuration configures individual trunk settings for sta 3-169 mstp vlan configuration configures priority and vlans for a spanning tree instance 3-172 port information displays port settings for a specified mst instance 3-175 trunk information displays trunk se...
Page 67
N avigating the w eb b rowser i nterface 3-11 private vlan 3-194 information shows private vlans and associated ports 3-195 configuration configures private vlans 3-197 association maps a secondary vlan to a primary vlan 3-198 port information shows vlan port type, and associated primary or secondar...
Page 68
C onfiguring the s witch 3-12 copy settings enables mapping ip precedence and dscp priority settings to ports, or trunks. 3-215 acl cos priority sets the cos value and corresponding output queue for packets matching an acl rule 3-216 acl marker change traffic priorities for frames matching an acl ru...
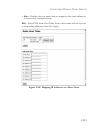
Page 69: Basic Configuration
B asic c onfiguration 3-13 basic configuration displaying system information you can easily identify the system by providing a descriptive name, location and contact information. Field attributes • system name – name assigned to the switch system. • object id – mib ii object id for switch’s network ...
Page 70
C onfiguring the s witch 3-14 web – click system, system information. Specify the system name, location, and contact information for the system administrator, then click apply. (this page also includes a telnet button that access the command line interface via telnet.) figure 3-3 system information.
Page 71: Field Attributes
B asic c onfiguration 3-15 cli – specify the hostname, location and contact information. Displaying switch hardware/software versions use the switch information page to display hardware/firmware version numbers for the main board and management software, as well as the power status of the system. Fi...
Page 72
C onfiguring the s witch 3-16 • internal power status – displays the status of the internal power supply. Management software • loader version – version number of loader code. • boot-rom version – version of power-on self-test (post) and boot code. • operation code version – version number of runtim...
Page 73
B asic c onfiguration 3-17 web – click system, switch information. Figure 3-4 general switch information cli – use the following command to display version information. Console#show version 4-80 unit 1 serial number: a230042447 service tag: hardware version: r0b module a type: stacking module module...
Page 74: Field Attributes
C onfiguring the s witch 3-18 displaying bridge extension capabilities the bridge mib includes extensions for managed devices that support multicast filtering, traffic classes, and virtual lans. You can access these extensions to display default settings for the key variables. Field attributes • ext...
Page 75: Setting The Ip Address
B asic c onfiguration 3-19 web – click system, bridge extension. Figure 3-5 displaying bridge extension configuration cli – enter the following command. Setting the ip address an ip address may be used for management access to the switch over your network. By default, the switch uses dhcp to assign ...
Page 76: Command Attributes
C onfiguring the s witch 3-20 you can manually configure a specific ip address, or direct the device to obtain an address from a bootp or dhcp server. Valid ip addresses consist of four decimal numbers, 0 to 255, separated by periods. Anything other than this format will not be accepted by the cli p...
Page 77: Manual Configuration
B asic c onfiguration 3-21 manual configuration web – click system, ip configuration. Select the vlan through which the management station is attached, set the ip address mode to “static.” enter the ip address, subnet mask and gateway, then click apply. Figure 3-6 ip interface configuration - manual...
Page 78: Using Dhcp/bootp
C onfiguring the s witch 3-22 using dhcp/bootp if your network provides dhcp/bootp services, you can configure the switch to be dynamically configured by these services. Web – click system, ip configuration. Specify the vlan to which the management station is attached, set the ip address mode to dhc...
Page 79: Managing Firmware
B asic c onfiguration 3-23 renewing dchp – dhcp may lease addresses to clients indefinitely or for a specific period of time. If the address expires or the switch is moved to another network segment, you will lose management access to the switch. In this case, you can reboot the switch or submit a c...
Page 80
C onfiguring the s witch 3-24 • file name – the file name should not contain slashes (\ or /), the leading letter of the file name should not be a period (.), and the maximum length for file names on the tftp server is 127 characters or 31 characters for files on the switch. (valid characters: a-z, ...
Page 81
B asic c onfiguration 3-25 if you download to a new destination file, go to the file, set start-up menu, mark the operation code file used at startup, and click apply. To start the new firmware, reboot the system via the system/reset menu. Figure 3-9 setting the startup code to delete a file, select...
Page 82: Command Usage
C onfiguring the s witch 3-26 cli – to download new firmware form a tftp server, enter the ip address of the tftp server, select “opcode” as the file type, then enter the source and destination file names. When the file has finished downloading, set the new file to start up the system and then resta...
Page 83
B asic c onfiguration 3-27 - file to startup-config - copies a file in the switch to the startup configuration. - file to tftp - copies a file from the switch to a tftp server. - running-config to file - copies the running configuration to a file. - running-config to startup-config - copies the runn...
Page 84
C onfiguring the s witch 3-28 downloading configuration settings from a server you can download the configuration file under a new file name and then set it as the startup file, or you can specify the current startup configuration file as the destination file to directly replace it. Note that the fi...
Page 85
B asic c onfiguration 3-29 if you download to a new file name using “tftp to startup-config” or “tftp to file,” the file is automatically set as the start-up configuration file. To use the new settings, reboot the system via the system/reset menu. You can also select any configuration file as the st...
Page 86: Console Port Settings
C onfiguring the s witch 3-30 this example shows how to download a poe controller file from a tftp server. This example shows how to copy a poe controller file from another unit in the stack. Console port settings you can access the onboard configuration program by attaching a vt100 compatible devic...
Page 87
B asic c onfiguration 3-31 • password threshold – sets the password intrusion threshold, which limits the number of failed logon attempts. When the logon attempt threshold is reached, the system interface becomes silent for a specified amount of time (set by the silent time parameter) before allowin...
Page 88
C onfiguring the s witch 3-32 web – click system, line, console. Specify the console port connection parameters as required, then click apply. Figure 3-13 console port settings cli – enter line configuration mode for the console, then specify the connection parameters as required. To display the cur...
Page 89: Telnet Settings
B asic c onfiguration 3-33 telnet settings you can access the onboard configuration program over the network using telnet (i.E., a virtual terminal). Management access via telnet can be enabled/disabled and other various parameters set, including the tcp port number, timeouts, and a password. These ...
Page 90
C onfiguring the s witch 3-34 web – click system, line, telnet. Specify the connection parameters for telnet access, then click apply. Figure 3-14 configuring the telnet interface cli – enter line configuration mode for a virtual terminal, then specify the connection parameters as required. To displ...
Page 91: Configuring Event Logging
B asic c onfiguration 3-35 configuring event logging the switch allows you to control the logging of error messages, including the type of events that are recorded in switch memory, logging to a remote system log (syslog) server, and displays a list of recent event messages. System log configuration...
Page 92: Command Attributes
C onfiguring the s witch 3-36 command attributes • system log status – enables/disables the logging of debug or error messages to the logging process. • flash level – limits log messages saved to the switch’s permanent flash memory for all levels up to the specified level. For example, if level 3 is...
Page 93: Remote Log Configuration
B asic c onfiguration 3-37 web – click system, log, system logs. Specify the system log status, set the level of event messages to be logged to ram and flash memory, and then click apply. Figure 3-15 system logs cli – enable system logging and then specify the level of messages to be logged to ram a...
Page 94
C onfiguring the s witch 3-38 this attribute specifies the facility type tag sent in syslog messages. (see rfc 3164.) this type has no effect on the kind of messages reported by the switch. However, it may be used by the syslog server to process messages, such as sorting or storing messages in the c...
Page 95: Displaying Log Messages
B asic c onfiguration 3-39 cli – enter the syslog server host ip address, choose the facility type and set the minimum level of messages to be logged. Displaying log messages use the logs page to scroll through the logged system and event messages. The switch can store up to 2048 log entries in temp...
Page 96: Command Attributes
C onfiguring the s witch 3-40 cli – this example shows the event message stored in ram. Sending simple mail transfer protocol alerts to alert system administrators of problems, the switch can use smtp (simple mail transfer protocol) to send email messages when triggered by logging events of a specif...
Page 97
B asic c onfiguration 3-41 web – click system, log, smtp. Enable smtp, specify a source email address, and select the minimum severity level. To add an ip address to the smtp server list, type the new ip address in the smtp server field and click add. To delete an ip address, click the entry in the ...
Page 98: Resetting The System
C onfiguring the s witch 3-42 cli – enter the ip address of at least one smtp server, set the syslog severity level to trigger an email message, and specify the switch (source) and up to five recipient (destination) email addresses. Enable smtp with the logging sendmail command to complete the confi...
Page 99: Setting The System Clock
B asic c onfiguration 3-43 cli – use the reload command to reboot the system. Note:when restarting the system, it always runs the power-on self-test. Setting the system clock simple network time protocol (sntp) allows the switch to set its internal clock based on periodic updates from a time server ...
Page 100: Setting The Time Zone
C onfiguring the s witch 3-44 web – select sntp, configuration. Modify any of the required parameters and click apply. Figure 3-20 sntp configuration cli – this example configures the switch to operate as an sntp client and then displays the current time and settings. Setting the time zone sntp uses...
Page 101
S imple n etwork m anagement p rotocol 3-45 • hours (0-13) –the number of hours before utc (0-12) or after utc (0-13). • minutes (0-59) –the number of minutes before/after utc. • direction –configures the time zone to be before (east) or after (west) utc. Web –select sntp, clock time zone. Set the o...
Page 102
C onfiguring the s witch 3-46 information base (mib) that provides a standard presentation of the information controlled by the agent. Snmp defines both the format of the mib specifications and the protocol used to access this information over the network. The switch includes an onboard agent that s...
Page 103
S imple n etwork m anagement p rotocol 3-47 note: the predefined default groups and view can be deleted from the system. You can then define customized groups and views for the snmp clients that require access. Table 3-4 snmpv3 security models and levels model level group read view write view notify...
Page 104: Enabling The Snmp Agent
C onfiguring the s witch 3-48 enabling the snmp agent enables snmpv3 service for all management clients (i.E., versions 1, 2c, 3). Command attributes snmp agent status – enables snmp on the switch. Web – click snmp, agent status. Enable the snmp agent by marking the enabled checkbox, and click apply...
Page 105
S imple n etwork m anagement p rotocol 3-49 • access mode – specifies the access rights for the community string: - read-only – authorized management stations are only able to retrieve mib objects. - read/write – authorized management stations are able to both retrieve and modify mib objects. Web – ...
Page 106: Command Usage
C onfiguring the s witch 3-50 specifying trap managers and trap types traps indicating status changes are issued by the switch to specified trap managers. You must specify trap managers so that key events are reported by this switch to your management station (using network management platforms such...
Page 107: Command Attributes
S imple n etwork m anagement p rotocol 3-51 3. Create a view with the required notification messages (page 3-67). 4. Create a group that includes the required notify view (page 3-61). 5. Specify a remote engine id where the user resides (page 3-54). 6. Then configure a remote user (page 3-58). Comma...
Page 108
C onfiguring the s witch 3-52 - retry times – the maximum number of times to resend an inform message if the recipient does not acknowledge receipt. (range: 0-255; default: 3) • enable authentication traps 3 – issues a notification message to specified ip trap managers whenever authentication of an ...
Page 109
S imple n etwork m anagement p rotocol 3-53 configuring snmpv3 management access to configure snmpv3 management access to the switch, follow these steps: 1. If you want to change the default engine id, it must be changed first before configuring other parameters. 2. Specify read and write access vie...
Page 110
C onfiguring the s witch 3-54 web – click snmp, snmpv3, engine id. Enter an id of up to 26 hexadecimal characters and then click save. Figure 3-25 setting an engine id cli – this example sets an snmpv3 engine id. Specifying a remote engine id to send inform messages to an snmpv3 user on a remote dev...
Page 111: Configuring Snmpv3 Users
S imple n etwork m anagement p rotocol 3-55 web – click snmp, snmpv3, remote engine id. Enter an id of up to 26 hexadecimal characters and then click save. Figure 3-26 setting an engine id cli – this example specifies a remote snmpv3 engine id. Configuring snmpv3 users each snmpv3 user is defined by...
Page 112
C onfiguring the s witch 3-56 - authpriv – snmp communications use both authentication and encryption (only available for the snmpv3 security model). • authentication protocol – the method used for user authentication. (options: md5, sha; default: md5) • authentication password – a minimum of eight ...
Page 113
S imple n etwork m anagement p rotocol 3-57 web – click snmp, snmpv3, users. Click new to configure a user name. In the new user page, define a name and assign it to a group, then click add to save the configuration and return to the user name list. To delete a user, check the box next to the user n...
Page 114
C onfiguring the s witch 3-58 cli – use the snmp-server user command to configure a new user name and assign it to a group. Configuring remote snmpv3 users each snmpv3 user is defined by a unique name. Users must be configured with a specific security level and assigned to a group. The snmpv3 group ...
Page 115: Command Attributes
S imple n etwork m anagement p rotocol 3-59 command attributes • user name – the name of user connecting to the snmp agent. (range: 1-32 characters) • group name – the name of the snmp group to which the user is assigned. (range: 1-32 characters) • engine id – the engine identifier for the snmp agen...
Page 116
C onfiguring the s witch 3-60 web – click snmp, snmpv3, remote users. Click new to configure a user name. In the new user page, define a name and assign it to a group, then click add to save the configuration and return to the user name list. To delete a user, check the box next to the user name, th...
Page 117: Configuring Snmpv3 Groups
S imple n etwork m anagement p rotocol 3-61 cli – use the snmp-server user command to configure a new user name and assign it to a group. Configuring snmpv3 groups an snmpv3 group sets the access policy for its assigned users, restricting them to specific read, write, and notify views. You can use t...
Page 118
C onfiguring the s witch 3-62 • notify view – the configured view for notifications. (range: 1-64 characters) table 3-5 supported notification messages object label object id description rfc 1493 traps newroot 1.3.6.1.2.1.17.0.1 the newroot trap indicates that the sending agent has become the new ro...
Page 119
S imple n etwork m anagement p rotocol 3-63 warmstart 1.3.6.1.6.3.1.1.5.2 a warmstart trap signifies that the snmpv2 entity, acting in an agent role, is reinitializing itself such that its configuration is unaltered. Linkdown * 1.3.6.1.6.3.1.1.5.3 a linkdown trap signifies that the snmp entity, acti...
Page 120
C onfiguring the s witch 3-64 authenticationfailure * 1.3.6.1.6.3.1.1.5.5 an authenticationfailure trap signifies that the snmpv2 entity, acting in an agent role, has received a protocol message that is not properly authenticated. While all implementations of the snmpv2 must be capable of generating...
Page 121
S imple n etwork m anagement p rotocol 3-65 swipfilterrejecttrap 1.3.6.1.4.1.202.20.28.63.2.1.0.40 1.3.6.1.4.1.202.20.41.63.2.1.0.40 1.3.6.1.4.1.202.20.53.63.2.1.0.40 this trap is sent when an incorrect ip address is rejected by the ip filter. Swsmtpconnfailure trap 1.3.6.1.4.1.202.20.28.63.2.1.0.41...
Page 122
C onfiguring the s witch 3-66 web – click snmp, snmpv3, groups. Click new to configure a new group. In the new group page, define a name, assign a security model and level, and then select read and write views. Click add to save the new group and return to the groups list. To delete a group, check t...
Page 123: Setting Snmpv3 Views
S imple n etwork m anagement p rotocol 3-67 cli – use the snmp-server group command to configure a new group, specifying the security model and level, and restricting mib access to defined read and write views. Setting snmpv3 views snmpv3 views are used to restrict user access to specified portions ...
Page 124
C onfiguring the s witch 3-68 web – click snmp, snmpv3, views. Click new to configure a new view. In the new view page, define a name and specify oid subtrees in the switch mib to be included or excluded in the view. Click back to save the new view and return to the snmpv3 views list. For a specific...
Page 125: User Authentication
U ser a uthentication 3-69 cli – use the snmp-server view command to configure a new view. This example view includes the mib-2 interfaces table, and the wildcard mask selects all index entries. User authentication you can restrict management access to this switch and provide secure network access u...
Page 126: Configuring User Accounts
C onfiguring the s witch 3-70 configuring user accounts the guest only has read access for most configuration parameters. However, the administrator has write access for all parameters governing the onboard agent. You should therefore assign a new administrator password as soon as possible, and stor...
Page 127
U ser a uthentication 3-71 web – click security, user accounts. To configure a new user account, enter the user name, access level, and password, then click add. To change the password for a specific user, enter the user name and new password, confirm the password by entering it again, then click ap...
Page 128: Command Usage
C onfiguring the s witch 3-72 configuring local/remote logon authentication use the authentication settings menu to restrict management access based on specified user names and passwords. You can manually configure access rights on the switch, or you can use a remote access authentication server bas...
Page 129: Command Attributes
U ser a uthentication 3-73 • you can specify up to three authentication methods for any user to indicate the authentication sequence. For example, if you select (1) radius, (2) tacacs and (3) local, the user name and password on the radius server is verified first. If the radius server is not availa...
Page 130
C onfiguring the s witch 3-74 • tacacs settings - server ip address – address of the tacacs+ server. (default: 10.11.12.13) - server port number – network (tcp) port of tacacs+ server used for authentication messages. (range: 1-65535; default: 49) - secret text string – encryption key used to authen...
Page 131: Configuring Https
U ser a uthentication 3-75 cli – specify all the required parameters to enable logon authentication. Configuring https you can configure the switch to enable the secure hypertext transfer protocol (https) over the secure socket layer (ssl), providing secure access (i.E., an encrypted connection) to ...
Page 132: Command Attributes
C onfiguring the s witch 3-76 • if you enable https, you must indicate this in the url that you specify in your browser: https://device[:port_number] • when you start https, the connection is established in this way: - the client authenticates the server using the server’s digital certificate. - the...
Page 133
U ser a uthentication 3-77 web – click security, https settings. Enable https and specify the port number, then click apply. Figure 3-33 https settings cli – this example enables the http secure server and modifies the port number. Replacing the default secure-site certificate when you log onto the ...
Page 134
C onfiguring the s witch 3-78 when you have obtained these, place them on your tftp server, and use the following command at the switch's command-line interface to replace the default (unrecognized) certificate with an authorized one: note:the switch must be reset for the new certificate to be activ...
Page 135: Command Usage
U ser a uthentication 3-79 command usage the ssh server on this switch supports both password and public key authentication. If password authentication is specified by the ssh client, then the password can be authenticated either locally or via a radius or tacacs+ remote authentication server, as sp...
Page 136
C onfiguring the s witch 3-80 only accepts public key files based on standard unix format as shown in the following example for an rsa version 1 key: 1024 35 1341081685609893921040944920155425347631641921872958921143173880 05553616163105177594083868631109291232226828519254374603100937187721199 69631...
Page 137: Field Attributes
U ser a uthentication 3-81 notes: 1. To use ssh with only password authentication, the host public key must still be given to the client, either during initial connection or manually entered into the known host file. However, you do not need to configure the client’s keys. 2. The ssh server supports...
Page 138
C onfiguring the s witch 3-82 • generate – this button is used to generate the host key pair. Note that you must first generate the host key pair before you can enable the ssh server on the ssh server settings page. • clear – this button clears the host key from both volatile memory (ram) and non-vo...
Page 139: Configuring The Ssh Server
U ser a uthentication 3-83 cli – this example generates a host-key pair using both the rsa and dsa algorithms, stores the keys to flash memory, and then displays the host’s public keys. Configuring the ssh server the ssh server includes basic settings for authentication. Field attributes • ssh serve...
Page 140
C onfiguring the s witch 3-84 • ssh server-key size – specifies the ssh server key size. (range: 512-896 bits: default: 768) - the server key is a private key that is never shared outside the switch. - the host key is shared with the ssh client, and is fixed at 1024 bits. Web – click security, ssh, ...
Page 141: Configuring Port Security
U ser a uthentication 3-85 configuring port security port security is a feature that allows you to configure a switch port with one or more device mac addresses that are authorized to access the network through that port. When port security is enabled on a port, the switch stops learning new mac add...
Page 142: Command Attributes
C onfiguring the s witch 3-86 • if a port is disabled (shut down) due to a security violation, it must be manually re-enabled from the port/port configuration page (page 3-117). Command attributes • port – port number. • name – descriptive text (page 3-114). • action – indicates the action to be tak...
Page 143
U ser a uthentication 3-87 web – click security, port security. Set the action to take when an invalid address is detected on a port, mark the checkbox in the status column to enable security for a port, set the maximum number of mac addresses allowed on a port, and click apply. Figure 3-36 enabling...
Page 144
C onfiguring the s witch 3-88 configuring 802.1x port authentication network switches can provide open and easy access to network resources by simply attaching a client pc. Although this automatic configuration and access is a desirable feature, it also allows unauthorized personnel to easily intrud...
Page 145: Command Attributes
U ser a uthentication 3-89 allows the client to access the network. Otherwise, network access is denied and the port remains blocked. The operation of 802.1x on the switch requires the following: • the switch must have an ip address assigned. • radius authentication must be enabled on the switch and...
Page 146: Command Attributes
C onfiguring the s witch 3-90 cli – this example shows the default global setting for 802.1x. Configuring 802.1x global settings the 802.1x protocol provides client authentication. Command attributes 802.1x system authentication control – sets the global setting for 802.1x. (default: disabled) web –...
Page 147: Command Attributes
U ser a uthentication 3-91 configuring port settings for 802.1x when 802.1x is enabled, you need to configure the parameters for the authentication process that runs between the client and the switch (i.E., authenticator), as well as the client identity lookup process that runs between the switch an...
Page 148
C onfiguring the s witch 3-92 • re-authentication period – sets the time period after which a connected client must be re-authenticated. (range: 1-65535 seconds; default: 3600 seconds) • tx period – sets the time period during an authentication session that the switch waits before re-transmitting an...
Page 149
U ser a uthentication 3-93 console#show dot1x 4-116 global 802.1x parameters system-auth-control: enable 802.1x port summary port name status operation mode mode authorized 1/1 disabled single-host forceauthorized yes 1/2 enabled single-host auto yes . . . 1/25 disabled single-host forceauthorized n...
Page 150
C onfiguring the s witch 3-94 displaying 802.1x statistics this switch can display statistics for dot1x protocol exchanges for any port. Table 3-7 802.1x statistics parameter description rx expol start the number of eapol start frames that have been received by this authenticator. Rx eapol logoff th...
Page 151
U ser a uthentication 3-95 web – select security, 802.1x, statistics. Select the required port and then click query. Click refresh to update the statistics. Figure 3-40 displaying 802.1x statistics cli – this example displays the 802.1x statistics for port 4. Console#show dot1x statistics interface ...
Page 152: Command Usage
C onfiguring the s witch 3-96 filtering ip addresses for management access you can create a list of up to 16 ip addresses or ip address groups that are allowed management access to the switch through the web interface, snmp, or telnet. Command usage • the management interfaces are open to all ip add...
Page 153
U ser a uthentication 3-97 web – click security, ip filter. Enter the ip addresses or range of addresses that are allowed management access to an interface, and click add ip filtering entry. Figure 3-41 entering ip addresses to be filtered cli – this example restricts management access for telnet an...
Page 154: Access Control Lists
C onfiguring the s witch 3-98 access control lists access control lists (acl) provide packet filtering for ip frames (based on address, protocol, layer 4 protocol port number or tcp control code) or any frames (based on mac address or ethernet type). To filter incoming packets, first create an acces...
Page 155: Command Attributes
A ccess c ontrol l ists 3-99 • when an acl is bound to an interface as an egress filter, all entries in the acl must be deny rules. Otherwise, the bind operation will fail. • the switch does not support the explicit “deny any any” rule for the egress ip acl or the egress mac acls. If these rules are...
Page 156: Command Attributes
C onfiguring the s witch 3-100 web – click security, acl, configuration. Enter an acl name in the name field, select the list type (ip standard, ip extended, or mac), and click add to open the configuration page for the new list. Figure 3-42 selecting acl type cli – this example creates a standard i...
Page 157: Command Attributes
A ccess c ontrol l ists 3-101 web – specify the action (i.E., permit or deny). Select the address type (any, host, or ip). If you select “host,” enter a specific address. If you select “ip,” enter a subnet address and the mask for an address range. Then click add. Figure 3-43 configuring standard ip...
Page 158
C onfiguring the s witch 3-102 • source/destination subnet mask – subnet mask for source or destination address. (see the description for submask on page 3-100.) • service type – packet priority settings based on the following criteria: - precedence – ip precedence level. (range: 0-7) - tos – type o...
Page 159
A ccess c ontrol l ists 3-103 web – specify the action (i.E., permit or deny). Specify the source and/or destination addresses. Select the address type (any, host, or ip). If you select “host,” enter a specific address. If you select “ip,” enter a subnet address and the mask for an address range. Se...
Page 160: Configuring A Mac Acl
C onfiguring the s witch 3-104 cli – this example adds three rules: 1. Accept any incoming packets if the source address is in subnet 10.7.1.X. For example, if the rule is matched; i.E., the rule (10.7.1.0 & 255.255.255.0) equals the masked address (10.7.1.2 & 255.255.255.0), the packet passes throu...
Page 161: Command Usage
A ccess c ontrol l ists 3-105 • ethernet type bitmask – protocol bitmask. (range: 600-fff hex.) • packet format – this attribute includes the following packet types: - any – any ethernet packet type. - untagged-eth2 – untagged ethernet ii packets. - untagged-802.3 – untagged ethernet 802.3 packets. ...
Page 162
C onfiguring the s witch 3-106 web – specify the action (i.E., permit or deny). Specify the source and/or destination addresses. Select the address type (any, host, or mac). If you select “host,” enter a specific address (e.G., 11-22-33-44-55-66). If you select “mac,” enter a base address and a hexa...
Page 163: Configuring Acl Masks
A ccess c ontrol l ists 3-107 configuring acl masks you must specify masks that control the order in which acl rules are checked. The switch includes two system default masks that pass/filter packets matching the permit/deny rules specified in an ingress acl. You can also configure up to seven user-...
Page 164: Command Usage
C onfiguring the s witch 3-108 web – click security, acl, mask configuration. Click edit for one of the basic mask types to open the configuration page. Figure 3-46 choosing acl types cli – this example creates an ip ingress mask, and then adds two rules. Each rule is checked in order of precedence ...
Page 165
A ccess c ontrol l ists 3-109 • source/destination subnet mask – subnet mask for source or destination address. (see the description for submask on page 3-100.) • protocol bitmask – check the protocol field. • service type mask – check the rule for the specified priority type. (options: precedence, ...
Page 166: Configuring A Mac Acl Mask
C onfiguring the s witch 3-110 cli – this shows that the entries in the mask override the precedence in which the rules are entered into the acl. In the following example, packets with the source address 10.1.1.1 are dropped because the “deny 10.1.1.1 255.255.255.255” rule has the higher precedence ...
Page 167
A ccess c ontrol l ists 3-111 web – configure the mask to match the required rules in the mac ingress or egress acls. Set the mask to check for any source or destination address, a host address, or an address range. Use a bitmask to search for specific vlan id(s) or ethernet type(s). Or check for ru...
Page 168: Command Usage
C onfiguring the s witch 3-112 cli – this example shows how to create an ingress mac acl and bind it to a port. You can then see that the order of the rules have been changed by the mask. Binding a port to an access control list after configuring the access control lists (acl), you can bind the port...
Page 169: Command Attributes
A ccess c ontrol l ists 3-113 • when an acl is bound to an interface as an egress filter, all entries in the acl must be deny rules. Otherwise, the bind operation will fail. • the switch does not support the explicit “deny any any” rule for the egress ip acl or the egress mac acls. If these rules ar...
Page 170: Port Configuration
C onfiguring the s witch 3-114 cli – this example assigns an ip and mac ingress acl to port 1, and an ip ingress acl to port 2. Port configuration displaying connection status you can use the port information or trunk information pages to display the current connection status, including link state, ...
Page 171: Field Attributes (Cli)
P ort c onfiguration 3-115 web – click port, port information or trunk information. Figure 3-50 port - port information field attributes (cli) basic information: • port type – indicates the port type. (100base-tx, 1000base-gbic, 100base-fx-s, 100base-fx-m, 1000base-t, or sfp) • mac address – the phy...
Page 172
C onfiguring the s witch 3-116 - 100full - supports 100 mbps full-duplex operation - 1000full - supports 1000 mbps full-duplex operation - sym - transmits and receives pause frames for flow control - fc - supports flow control • broadcast storm – shows if broadcast storm control is enabled or disabl...
Page 173: Command Attributes
P ort c onfiguration 3-117 cli – this example shows the connection status for port 13. Configuring interface connections you can use the port configuration or trunk configuration page to enable/disable an interface, set auto-negotiation and the interface capabilities to advertise, or manually fix th...
Page 174
C onfiguring the s witch 3-118 the capabilities to be advertised. When auto-negotiation is disabled, you can force the settings for speed, mode, and flow control.The following capabilities are supported. - 10half - supports 10 mbps half-duplex operation - 10full - supports 10 mbps full-duplex operat...
Page 175
P ort c onfiguration 3-119 web – click port, port configuration or trunk configuration. Modify the required interface settings, and click apply. Figure 3-51 configuring port attributes cli – select the interface, and then enter the required settings. Console(config)#interface ethernet 1/13 console(c...
Page 176: Creating Trunk Groups
C onfiguring the s witch 3-120 creating trunk groups you can create multiple links between devices that work as one virtual, aggregate link. A port trunk offers a dramatic increase in bandwidth for network segments where bottlenecks exist, as well as providing a fault-tolerant link between two devic...
Page 177: Command Usage
P ort c onfiguration 3-121 • when configuring static trunks on switches of different types, they must be compatible with the cisco etherchannel standard. • the ports at both ends of a trunk must be configured in an identical manner, including communication mode (i.E., speed, duplex mode and flow con...
Page 178
C onfiguring the s witch 3-122 web – click port, trunk membership. Enter a trunk id of 1-6 in the trunk field, select any of the switch ports from the scroll-down port list, and click add. After you have completed adding ports to the member list, click apply. Figure 3-52 static trunk configuration c...
Page 179: Command Usage
P ort c onfiguration 3-123 enabling lacp on selected ports command usage • to avoid creating a loop in the network, be sure you enable lacp before connecting the ports, and also disconnect the ports before disabling lacp. • if the target switch has also enabled lacp on the connected ports, the trunk...
Page 180: Command Attributes
C onfiguring the s witch 3-124 command attributes • member list (current)– shows configured trunks (unit, port). • new – includes entry fields for creating new trunks. - unit – stack unit. (range: 1-8) - port – port identifier. (range: 1-26) web – click port, lacp, configuration. Select any of the s...
Page 181: Configuring Lacp Parameters
P ort c onfiguration 3-125 configuring lacp parameters dynamically creating a port channel – ports assigned to a common port channel must meet the following criteria: • ports must have the same lacp system priority. • ports must have the same lacp port admin key. • however, if the “port channel” adm...
Page 182: Command Attributes
C onfiguring the s witch 3-126 command attributes set port actor – this menu sets the local side of an aggregate link; i.E., the ports on this switch. • port – port number. (range: 1-26) • system priority – lacp system priority is used to determine link aggregation group (lag) membership, and to ide...
Page 183
P ort c onfiguration 3-127 web – click port, lacp, aggregation port. Set the system priority, admin key, and port priority for the port actor. You can optionally configure these settings for the port partner. (be aware that these settings only affect the administrative state of the partner, and will...
Page 184
C onfiguring the s witch 3-128 cli – the following example configures lacp parameters for ports 1-6. Ports 1-4 are used as active members of the lag; ports 5 and 6 are set to backup mode. Console(config)#interface ethernet 1/1 4-171 console(config-if)#lacp actor system-priority 3 4-192 console(confi...
Page 185
P ort c onfiguration 3-129 displaying lacp port counters you can display statistics for lacp protocol messages. Web – click port, lacp, port counters information. Select a member port to display the corresponding information. Figure 3-55 displaying lacp port counters information table 3-8 lacp port ...
Page 186
C onfiguring the s witch 3-130 cli – the following example displays lacp counters for port channel 1. Displaying lacp settings and status for the local side you can display configuration settings and the operational state for the local side of an link aggregation. Console#show lacp 1 counters 4-196 ...
Page 187
P ort c onfiguration 3-131 admin state, oper state administrative or operational values of the actor’s state parameters: • expired – the actor’s receive machine is in the expired state; • defaulted – the actor’s receive machine is using defaulted operational partner information, administratively con...
Page 188
C onfiguring the s witch 3-132 web – click port, lacp, port internal information. Select a port channel to display the corresponding information. Figure 3-56 displaying lacp port information cli – the following example displays the lacp configuration settings and operational state for the local side...
Page 189
P ort c onfiguration 3-133 displaying lacp settings and status for the remote side you can display configuration settings and the operational state for the remote side of an link aggregation. Table 3-10 lacp neighbor configuration information field description partner admin system id lag partner’s s...
Page 190
C onfiguring the s witch 3-134 web – click port, lacp, port neighbors information. Select a port channel to display the corresponding information. Figure 3-57 displaying remote lacp port information cli – the following example displays the lacp configuration settings and operational state for the re...
Page 191: Command Usage
P ort c onfiguration 3-135 setting broadcast storm thresholds broadcast storms may occur when a device on your network is malfunctioning, or if application programs are not well designed or properly configured. If there is too much broadcast traffic on your network, performance can be severely degra...
Page 192: Configuring Port Mirroring
C onfiguring the s witch 3-136 cli – specify any interface, and then enter the threshold. The following disables broadcast storm control for port 1, and then sets broadcast suppression at 60 packets per second for port 2. Configuring port mirroring you can mirror traffic from any source port to a ta...
Page 193: Command Attributes
P ort c onfiguration 3-137 command attributes • mirror sessions – displays a list of current mirror sessions. • source unit – the unit whose port traffic will be monitored. (range: 1-8) • source port – the port whose traffic will be monitored. (range: 1-26) • type – allows you to select which traffi...
Page 194: Configuring Rate Limits
C onfiguring the s witch 3-138 configuring rate limits this function allows the network manager to control the maximum rate for traffic transmitted or received on an interface. Rate limiting is configured on interfaces at the edge of a network to limit traffic coming out of the switch. Traffic that ...
Page 195: Showing Port Statistics
P ort c onfiguration 3-139 cli - this example sets the rate limit for input and output traffic passing through port 1 to 60 mbps. Showing port statistics you can display standard statistics on network traffic from the interfaces group and ethernet-like mibs, as well as a detailed breakdown of traffi...
Page 196
C onfiguring the s witch 3-140 received discarded packets the number of inbound packets which were chosen to be discarded even though no errors had been detected to prevent their being deliverable to a higher-layer protocol. One possible reason for discarding such a packet could be to free up buffer...
Page 197
P ort c onfiguration 3-141 etherlike statistics alignment errors the number of alignment errors (missynchronized data packets). Late collisions the number of times that a collision is detected later than 512 bit-times into the transmission of a packet. Fcs errors a count of frames received on a part...
Page 198
C onfiguring the s witch 3-142 internal mac receive errors a count of frames for which reception on a particular interface fails due to an internal mac sublayer receive error. Rmon statistics drop events the total number of events in which packets were dropped due to lack of resources. Jabbers the t...
Page 199
P ort c onfiguration 3-143 64 bytes frames the total number of frames (including bad packets) received and transmitted that were 64 octets in length (excluding framing bits but including fcs octets). 65-127 byte frames 128-255 byte frames 256-511 byte frames 512-1023 byte frames 1024-1518 byte frame...
Page 200
C onfiguring the s witch 3-144 web – click port, port statistics. Select the required interface, and click query. You can also use the refresh button at the bottom of the page to update the screen. Figure 3-61 port statistics.
Page 201
P ower o ver e thernet s ettings 3-145 cli – this example shows statistics for port 13. Power over ethernet settings the smc6824mpe and smc6826mpe can provide dc power to a wide range of connected devices, eliminating the need for an additional power source and cutting down on the amount of cables a...
Page 202: Switch Power Status
C onfiguring the s witch 3-146 the power required by a device exceeds the power budget of the port or the whole switch, power is not supplied. Ports can be set to one of three power priority levels, critical, high, or low. To control the power supply within the switch’s budget, ports set at critical...
Page 203: Command Attributes
P ower o ver e thernet s ettings 3-147 web – click poe, power status. Figure 3-62 displaying the global poe status cli – this example displays the current power status for the switch. Setting a switch power budget a maximum poe power budget for the switch (power available to all switch ports) can be...
Page 204: Command Attributes
C onfiguring the s witch 3-148 web – click poe, power config. Specify the desired power budget for the switch. Click apply. Figure 3-63 setting the switch power budget cli – use the power mainpower maximum allocation command to set the poe power budget for the switch. Displaying port power status us...
Page 205: Configuring Port Poe Power
P ower o ver e thernet s ettings 3-149 web – click poe, power port status. Figure 3-64 displaying port poe status cli – this example displays the poe status and priority of port 1. Configuring port poe power if a device is connected to a switch port and the switch detects that it requires more than ...
Page 206: Command Attributes
C onfiguring the s witch 3-150 • if a device is connected to a critical or high-priority port and causes the switch to exceed its budget, port power is turned on, but the switch drops power to one or more lower-priority ports. Note: power is dropped from low-priority ports in sequence starting from ...
Page 207: Address Table Settings
A ddress t able s ettings 3-151 cli – this example sets the poe power budget for port 1 to 8 watts, the priority to high (2), and then enables the power. Address table settings switches store the addresses for all known devices. This information is used to pass traffic directly between the inbound a...
Page 208: Command Attributes
C onfiguring the s witch 3-152 web – click address table, static addresses. Specify the interface, the mac address and vlan, then click add static address. Figure 3-66 mapping ports to static addresses cli – this example adds an address to the static address table, but sets it to be deleted when the...
Page 209
A ddress t able s ettings 3-153 • vlan – id of configured vlan (1-4093). • address table sort key – you can sort the information displayed based on mac address, vlan or interface (port or trunk). • dynamic address counts – the number of addresses dynamically learned. • current dynamic address table ...
Page 210: Changing The Aging Time
C onfiguring the s witch 3-154 changing the aging time you can change the aging time for entries in the dynamic address table. Command attributes • aging status – enables or disables the aging time. • aging time – the time after which a learned entry is discarded. (range: 10-1000000 seconds; default...
Page 211
S panning t ree a lgorithm c onfiguration 3-155 the spanning tree algorithms supported by this switch include these versions: • stp – spanning tree protocol (ieee 802.1d) • rstp – rapid spanning tree protocol (ieee 802.1w) • mstp – multiple spanning tree protocol (ieee 802.1s) sta uses a distributed...
Page 212: Displaying Global Settings
C onfiguring the s witch 3-156 start learning, predefining an alternate route that can be used when a node or port fails, and retaining the forwarding database for ports insensitive to changes in the tree structure when reconfiguration occurs. When using stp or rstp, it may be difficult to maintain ...
Page 213
S panning t ree a lgorithm c onfiguration 3-157 • forward delay – the maximum time (in seconds) the root device will wait before changing states (i.E., discarding to learning to forwarding). This delay is required because every device must receive information about topology changes before it starts ...
Page 214
C onfiguring the s witch 3-158 • priority – bridge priority is used in selecting the root device, root port, and designated port. The device with the highest priority (i.E., lower numeric value) becomes the sta root device. However, if all devices have the same priority, the device with the lowest m...
Page 215
S panning t ree a lgorithm c onfiguration 3-159 web – click spanning tree, sta information. Figure 3-69 displaying the spanning tree algorithm cli – this command displays global sta settings, followed by settings for each port. Console#show spanning-tree 4-227 spanning-tree information -------------...
Page 216: Configuring Global Settings
C onfiguring the s witch 3-160 note: the current root port and current root cost display as zero when this device is not connected to the network. Configuring global settings global settings apply to the entire switch. Command usage • spanning tree protocol 8 uses rstp for the internal state machine...
Page 217: Command Attributes
S panning t ree a lgorithm c onfiguration 3-161 • rapid spanning tree protocol 8 rstp supports connections to either stp or rstp nodes by monitoring the incoming protocol messages and dynamically adjusting the type of protocol messages the rstp node transmits, as described below: - stp mode – if the...
Page 218
C onfiguring the s witch 3-162 - rstp: rapid spanning tree (ieee 802.1w) rstp is the default. - mstp: multiple spanning tree (ieee 802.1s) • default priority format – sets the default spanning tree priority format: - 802.1d 9 : specifies ieee 802.1d priority format in increments of 1. - 802.1t: spec...
Page 219
S panning t ree a lgorithm c onfiguration 3-163 • forward delay – the maximum time (in seconds) this device will wait before changing states (i.E., discarding to learning to forwarding). This delay is required because every device must receive information about topology changes before it starts to f...
Page 220
C onfiguring the s witch 3-164 web – click spanning tree, sta configuration. Modify the required attributes, and click apply. Figure 3-70 configuring the spanning tree algorithm.
Page 221: Field Attributes
S panning t ree a lgorithm c onfiguration 3-165 cli – this example enables spanning tree protocol, sets the mode to mst, and then configures the sta and mstp parameters. Displaying interface settings the sta port information and sta trunk information pages display the current status of ports and tru...
Page 222
C onfiguring the s witch 3-166 - if two ports of a switch are connected to the same segment and there is no other sta device attached to this segment, the port with the smaller id forwards packets and the other is discarding. - all ports are discarding when the switch is booted, then some of them ch...
Page 223
S panning t ree a lgorithm c onfiguration 3-167 bridges, bridge ports, or lans fail or are removed. The role is set to disabled (i.E., disabled port) if a port has no role within the spanning tree. • trunk member 11 – indicates if a port is a member of a trunk. These additional parameters are only d...
Page 224
C onfiguring the s witch 3-168 likely to be blocked if the spanning tree algorithm is detecting network loops. Where more than one port is assigned the highest priority, the port with lowest numeric identifier will be enabled. • designated root – the priority and mac address of the device in the spa...
Page 225: Command Attributes
S panning t ree a lgorithm c onfiguration 3-169 cli – this example shows general sta configuration and attributes for port 5. Configuring interface settings you can configure rstp and mstp attributes for specific interfaces, including port priority, path cost, link type, and edge port. You may use a...
Page 226
C onfiguring the s witch 3-170 - learning - port has transmitted configuration messages for an interval set by the forward delay parameter without receiving contradictory information. Port address table is cleared, and the port begins learning addresses. - forwarding - port forwards packets, and con...
Page 227
S panning t ree a lgorithm c onfiguration 3-171 • admin link type – the link type attached to this interface. - point-to-point – a connection to exactly one other bridge. - shared – a connection to two or more bridges. - auto – the switch automatically determines if the interface is attached to a po...
Page 228
C onfiguring the s witch 3-172 cli – this example sets sta attributes for port 5. Configuring multiple spanning trees mstp generates a unique spanning tree for each instance. This provides multiple pathways across the network, thereby balancing the traffic load, preventing wide-scale disruption when...
Page 229: Command Attributes
S panning t ree a lgorithm c onfiguration 3-173 command attributes • mst instance – instance identifier of this spanning tree. (default: 0) • priority – the priority of a spanning tree instance. (range: 0-61440 in steps of 4096; options: 0, 4096, 8192, 12288, 16384, 20480, 24576, 28672, 32768, 36864...
Page 230
C onfiguring the s witch 3-174 cli – this displays sta settings for instance 1, followed by settings for each port. Console#show spanning-tree mst 1 4-227 spanning-tree information --------------------------------------------------------------- spanning tree mode: mstp spanning tree enabled/disabled...
Page 231: Field Attributes
S panning t ree a lgorithm c onfiguration 3-175 cli – this example sets the priority for msti 1, and adds vlans 1-5 to this msti. Displaying interface settings for mstp the mstp port information and mstp trunk information pages display the current status of ports and trunks in the selected mst insta...
Page 232
C onfiguring the s witch 3-176 cli – this displays sta settings for instance 0, followed by settings for each port. The settings for instance 0 are global settings that apply to the ist (page 3-156), the settings for other instances only apply to the local spanning tree. Console#show spanning-tree m...
Page 233: Field Attributes
S panning t ree a lgorithm c onfiguration 3-177 configuring interface settings for mstp you can configure the sta interface settings for an mst instance using the mstp port configuration and mstp trunk configuration pages. Field attributes the following attributes are read-only and cannot be changed...
Page 234
C onfiguring the s witch 3-178 when the path cost method is set to short (page 3-63), the maximum path cost is 65,535. By default, the system automatically detects the speed and duplex mode used on each port, and configures the path cost according to the values shown below. Path cost “0” is used to ...
Page 235: Vlan Configuration
Vlan c onfiguration 3-179 vlan configuration ieee 802.1q vlans in large networks, routers are used to isolate broadcast traffic for each subnet into separate domains. This switch provides a similar service at layer 2 by using vlans to organize any group of network nodes into separate broadcast domai...
Page 236: Assigning Ports To Vlans
C onfiguring the s witch 3-180 assigning ports to vlans before enabling vlans for the switch, you must first assign each port to the vlan group(s) in which it will participate. By default all ports are assigned to vlan 1 as untagged ports. Add a port as a tagged port if you want it to carry traffic ...
Page 237
Vlan c onfiguration 3-181 port overlapping – port overlapping can be used to allow access to commonly shared network resources among different vlan groups, such as file servers or printers. Note that if you implement vlans which do not overlap, but still need to communicate, you can connect them by ...
Page 238
C onfiguring the s witch 3-182 should also determine security boundaries in the network and disable gvrp on ports to prevent advertisements being propagated, or forbid ports from joining restricted vlans. Note: if you have host devices that do not support gvrp, you should configure static or untagge...
Page 239
Vlan c onfiguration 3-183 by the frame tag. However, when this switch receives an untagged frame from a vlan-unaware device, it first decides where to forward the frame, and then inserts a vlan tag reflecting the ingress port’s default vid. Enabling or disabling gvrp (global setting) garp vlan regis...
Page 240: Field Attributes
C onfiguring the s witch 3-184 displaying basic vlan information the vlan basic information page displays basic information on the vlan type supported by the switch. Field attributes • vlan version number 14 – the vlan version used by this switch as specified in the ieee 802.1q standard. • maximum v...
Page 241: Displaying Current Vlans
Vlan c onfiguration 3-185 displaying current vlans the vlan current table shows the current port members of each vlan and whether or not the port supports vlan tagging. Ports assigned to a large vlan group that crosses several switches should use vlan tagging. However, if you just want to create a s...
Page 242: Command Attributes (Cli)
C onfiguring the s witch 3-186 command attributes (cli) • vlan – id of configured vlan (1-4093, no leading zeroes). • type – shows how this vlan was added to the switch. - dynamic: automatically learned via gvrp. - static: added as a static entry. • name – name of the vlan (1 to 32 characters). • st...
Page 243
Vlan c onfiguration 3-187 • vlan id – id of configured vlan (1-4093, no leading zeroes). • vlan name – name of the vlan (1 to 32 characters). • status (web) – enables or disables the specified vlan. - enable: vlan is operational. - disable: vlan is suspended; i.E., does not pass packets. • state (cl...
Page 244
C onfiguring the s witch 3-188 cli – this example creates a new vlan. Adding static members to vlans (vlan index) use the vlan static table to configure port members for the selected vlan index. Assign ports as tagged if they are connected to 802.1q vlan compliant devices, or untagged they are not c...
Page 245: Command Attributes
Vlan c onfiguration 3-189 command attributes • vlan – id of configured vlan (1-4093). • name – name of the vlan (1 to 32 characters). • status – enables or disables the specified vlan. - enable: vlan is operational. - disable: vlan is suspended; i.E., does not pass packets. • port – port identifier....
Page 246: Command Attributes
C onfiguring the s witch 3-190 web – click vlan, 802.1q vlan, static table. Select a vlan id from the scroll-down list. Modify the vlan name and status if required. Select the membership type by marking the appropriate radio button in the list of ports or trunks. Click apply. Figure 3-80 vlan static...
Page 247: Command Usage
Vlan c onfiguration 3-191 • non-member – vlans for which the selected interface is not a tagged member. Web – click vlan, 802.1q vlan, static membership by port. Select an interface from the scroll-down box (port or trunk). Click query to display membership information for the interface. Select a vl...
Page 248: Command Attributes
C onfiguring the s witch 3-192 • garp – group address registration protocol is used by gvrp to register or deregister client attributes for client services within a bridged lan. The default values for the garp timers are independent of the media access method or data rate. These values should not be...
Page 249
Vlan c onfiguration 3-193 • garp join timer 15 – the interval between transmitting requests/ queries to participate in a vlan group. (range: 20-1000 centiseconds; default: 20) • garp leave timer 15 – the interval a port waits before leaving a vlan group. This time should be set to more than twice th...
Page 250: Private Vlans
C onfiguring the s witch 3-194 web – click vlan, 802.1q vlan, port configuration or trunk configuration. Fill in the required settings for each interface, click apply. Figure 3-82 vlan port configuration cli – this example sets port 1 to accept only tagged frames, assigns pvid 3 as the native vlan i...
Page 251: Command Attributes
Vlan c onfiguration 3-195 vlan, and with their designated promiscuous ports. (note that private vlans and normal vlans can exist simultaneously within the same switch.) each private vlan consists of two components: a primary vlan and one or more community vlans. A primary vlan allows traffic to pass...
Page 252
C onfiguring the s witch 3-196 • primary vlan – the primary vlan with which the selected vlan is associated. (note that this displays as vlan 0 if the selected vlan is itself a primary vlan.) • ports list – the list of ports (and assigned type) in the selected private vlan. Web – click private vlan,...
Page 253: Configuring Private Vlans
Vlan c onfiguration 3-197 configuring private vlans the private vlan configuration page is used to create/remove primary or community vlans. Command attributes • vlan id – id of configured vlan (1-4093). • type – there are two types of vlans within a private vlan: - primary vlans - conveys traffic b...
Page 254: Associating Community Vlans
C onfiguring the s witch 3-198 associating community vlans each community vlan must be associated with a primary vlan. Command attributes • primary vlan id – id of primary vlan (1-4093). • association – community vlans associated with the selected primary vlan. • non-association – community vlans no...
Page 255: Command Attributes
Vlan c onfiguration 3-199 displaying private vlan interface information use the private vlan port information and private vlan trunk information menus to display the interfaces associated with private vlans. Command attributes • port/trunk – the switch interface. • pvlan port type – displays private...
Page 256: Command Attributes
C onfiguring the s witch 3-200 cli – this example shows the switch configured with primary vlan 5 and secondary vlan 6. Port 3 has been configured as a promiscuous port and mapped to vlan 5, while ports 4 and 5 have been configured as a host ports and associated with vlan 6. This means that traffic ...
Page 257
Vlan c onfiguration 3-201 promiscuous ports. If pvlan port type is “host,” then specify the associated secondary vlan. Web – click private vlan, private vlan port configuration or private vlan trunk configuration. Set the pvlan port type for each port that will join a private vlan. For promiscuous p...
Page 258: Layer 2 Queue Settings
C onfiguring the s witch 3-202 class of service configuration class of service (cos) allows you to specify which data packets have greater precedence when traffic is buffered in the switch due to congestion. This switch supports cos with four priority queues for each port. Data packets in a port’s h...
Page 259
C lass of s ervice c onfiguration 3-203 web – click priority, default port priority or default trunk priority. Modify the default priority for any interface, then click apply. Figure 3-88 configuring class of service per port cli – this example assigns a default priority of 5 to port 3. Console(conf...
Page 260: Command Attributes
C onfiguring the s witch 3-204 mapping cos values to egress queues this switch processes class of service (cos) priority tagged traffic by using four priority queues for each port, with service schedules based on weighted round robin (wrr). Up to 8 separate traffic priorities are defined in ieee 802...
Page 261
C lass of s ervice c onfiguration 3-205 web 18 – click priority, traffic classes. Mark an interface and click select to display the current mapping of cos values to output queues. Assign priorities to the traffic classes (i.E., output queues) for the selected interface, then click apply. Figure 3-89...
Page 262: Selecting The Queue Mode
C onfiguring the s witch 3-206 selecting the queue mode you can set the switch to service the queues based on a strict rule that requires all traffic in a higher priority queue to be processed before lower priority queues are serviced, or use weighted round-robin (wrr) queuing that specifies a relat...
Page 263: Command Attributes
C lass of s ervice c onfiguration 3-207 setting the service weight for traffic classes this switch uses the weighted round robin (wrr) algorithm to determine the frequency at which it services each priority queue. As described in “mapping cos values to egress queues” on page 3-204, the traffic class...
Page 264: Layer 3/4 Priority Settings
C onfiguring the s witch 3-208 cli – the following example shows how to assign wrr weights of 1, 4, 16 and 64 to the cos priority queues 0, 1, 2 and 3. Layer 3/4 priority settings mapping layer 3/4 priorities to cos values this switch supports several common methods of prioritizing layer 3/4 traffic...
Page 265: Mapping Ip Precedence
C lass of s ervice c onfiguration 3-209 • ip precedence – maps layer 3/4 priorities using ip precedence. • ip dscp – maps layer 3/4 priorities using differentiated services code point mapping. Web – click priority, ip precedence/dscp priority status. Select disabled, ip precedence or ip dscp from th...
Page 266: Command Attributes
C onfiguring the s witch 3-210 command attributes • ip precedence priority table – shows the ip precedence to cos map. • class of service value – maps a cos value to the selected ip precedence value. Note that “0” represents low priority and “7” represent high priority. Note: ip precedence settings ...
Page 267: Mapping Dscp Priority
C lass of s ervice c onfiguration 3-211 mapping dscp priority the dscp is six bits wide, allowing coding for up to 64 different forwarding behaviors. The dscp replaces the tos bits, and it retains backward compatibility with the three precedence bits so that non-dscp compliant, tos-enabled devices, ...
Page 268: Command Attributes
C onfiguring the s witch 3-212 command attributes • dscp priority table – shows the dscp priority to cos map. • class of service value – maps a cos value to the selected dscp priority value. Note that “0” represents low priority and “7” represent high priority. Note: ip dscp settings apply to all in...
Page 269: Mapping Ip Port Priority
C lass of s ervice c onfiguration 3-213 cli 21 – the following example globally enables dscp priority service on the switch, maps dscp value 0 to cos value 1 (on port 5), and then displays the dscp priority settings. Mapping ip port priority you can also map network applications to class of service ...
Page 270
C onfiguring the s witch 3-214 web – click priority, ip port status. Set ip port priority status to enabled. Figure 3-95 globally enabling the ip port priority status web 22 – click priority, ip port priority. Select a port or trunk from the interface field. Enter the port number for a network appli...
Page 271: Copy Settings
C lass of s ervice c onfiguration 3-215 cli 22 – the following example globally enables ip port priority service on the switch, maps http traffic (on port 5) to cos value 0, and then displays the ip port priority settings for that port. Copy settings use the copy settings page to copy ip precedence ...
Page 272: Mapping Cos Values To Acls
C onfiguring the s witch 3-216 web – click priority, copy settings. Select the source priority settings to be copied, enter the source port or trunk number and choose the destination interface/s to copy to, then click copy settings. Figure 3-97 mapping priority settings to ports/trunks cli – this fe...
Page 273: Command Usage
C lass of s ervice c onfiguration 3-217 command usage you must configure an acl mask before you can map cos values to the rule. Command attributes • port – port identifier. • name 23 – name of acl. • type – type of acl (ip or mac). • cos priority – cos value used for packets matching an ip acl rule....
Page 274: Command Usage
C onfiguring the s witch 3-218 changing priorities based on acl rules you can change traffic priorities for frames matching the defined acl rule. (this feature is commonly referred to as acl packet marking.) this switch can change the ieee 802.1p priority, ip precedence, or dscp priority of ip frame...
Page 275
C lass of s ervice c onfiguration 3-219 web – click priority, acl marker. Select a port and an acl rule. To specify a tos priority, mark the precedence/dscp check box, select precedence or dscp from the scroll-down box, and enter a priority. To specify an 802.1p priority, mark the 802.1p priority ch...
Page 276: Multicast Filtering
C onfiguring the s witch 3-220 multicast filtering multicasting is used to support real-time applications such as videoconferencing or streaming audio. A multicast server does not have to establish a separate connection with each client. It merely broadcasts its service to the network, and any hosts...
Page 277
M ulticast f iltering 3-221 multicast host registration protocol that allows any host to inform its local router that it wants to receive transmissions addressed to a specific multicast group. A router, or multicast-enabled switch, can periodically ask their hosts if they want to receive multicast t...
Page 278: Command Usage
C onfiguring the s witch 3-222 static igmp host interface – for multicast applications that you need to control more carefully, you can manually assign a multicast service to specific interfaces on the switch (page 3-228). Configuring igmp snooping and query parameters you can configure the switch t...
Page 279
M ulticast f iltering 3-223 • igmp query count — sets the maximum number of queries issued for which there has been no response before the switch takes action to drop a client from the multicast group. (range: 2-10; default: 2) • igmp query interval — sets the frequency at which the switch sends igm...
Page 280: Command Attributes
C onfiguring the s witch 3-224 cli – this example modifies the settings for multicast filtering, and then displays the current status. Displaying interfaces attached to a multicast router multicast routers that are attached to ports on the switch use information obtained from igmp, along with a mult...
Page 281: Command Attributes
M ulticast f iltering 3-225 web – click igmp snooping, multicast router port information. Select the required vlan id from the scroll-down list to display the associated multicast routers. Figure 3-101 mapping multicast switch ports to vlans cli – this example shows that port 11 has been statically ...
Page 282: Command Attribute
C onfiguring the s witch 3-226 • port or trunk – specifies the interface attached to a multicast router. Web – click igmp snooping, static multicast router port configuration. Specify the interfaces attached to a multicast router, indicate the vlan which will forward all the corresponding multicast ...
Page 283
M ulticast f iltering 3-227 • multicast group port list – shows the interfaces that have already been assigned to the selected vlan to propagate a specific multicast service. Web – click igmp snooping, ip multicast registration table. Select a vlan id and the ip address for a multicast service from ...
Page 284: Command Usage
C onfiguring the s witch 3-228 assigning ports to multicast services multicast filtering can be dynamically configured using igmp snooping and igmp query messages as described in “configuring igmp snooping and query parameters” on page 3-222. For certain applications that require tighter control, yo...
Page 285: Command Usage
C onfiguring d omain n ame s ervice 3-229 cli – this example assigns a multicast address to vlan 1, and then displays all the known multicast services supported on vlan 1. Configuring domain name service the domain naming system (dns) service on this switch allows host names to be mapped to ip addre...
Page 286: Command Attributes
C onfiguring the s witch 3-230 through the domain list, appending each domain name in the list to the host name, and checking with the specified name servers for a match. • when more than one name server is specified, the servers are queried in the specified sequence until a response is received, or...
Page 287
C onfiguring d omain n ame s ervice 3-231 web –select dns, general configuration. Set the default domain name or list of domain names, specify one or more name servers to use for address resolution, enable domain lookup status, and click apply. Figure 3-105 configuring dns.
Page 288: Command Usage
C onfiguring the s witch 3-232 cli - this example sets a default domain name and a domain list. However, remember that if a domain list is specified, the default domain name is not used. Configuring static dns host to address entries you can manually configure static entries in the dns table that ar...
Page 289
C onfiguring d omain n ame s ervice 3-233 • alias – displays the host names that are mapped to the same address(es) as a previously configured entry. Web –select dns, static host table. Enter a host name and one or more corresponding addresses, then click apply. Figure 3-106 mapping ip addresses to ...
Page 290: Displaying The Dns Cache
C onfiguring the s witch 3-234 cli - this example maps two address to a host name, and then configures an alias host name for the same addresses. Displaying the dns cache you can display entries in the dns cache that have been learned via the designated name servers. Field attributes • no – the entr...
Page 291
C onfiguring d omain n ame s ervice 3-235 web –select dns, cache. Figure 3-107 displaying the dns cache cli - this example displays all the resource records learned from the designated name servers. Console#show dns cache 4-293 no flag type ip ttl domain 0 4 cname 207.46.134.222 51 www.Microsoft.Aka...
Page 292
C onfiguring the s witch 3-236.
Page 293: Accessing The Cli
4-1 c hapter 4 c ommand l ine i nterface this chapter describes how to use the command line interface (cli). Using the command line interface accessing the cli when accessing the management interface for the switch over a direct connection to the server’s console port, or via a telnet connection, th...
Page 294: Telnet Connection
U sing the c ommand l ine i nterface 4-2 after connecting to the system through the console port, the login screen displays: telnet connection telnet operates over the ip transport protocol. In this environment, your management station and any network device you want to manage over the network must ...
Page 295: Entering Commands
C ommand l ine i nterface 4-3 after you configure the switch with an ip address, you can open a telnet session by performing these steps. 1. From the remote host, enter the telnet command and the ip address of the device you want to access. 2. At the prompt, enter the user name and system password. ...
Page 296: Minimum Abbreviation
E ntering c ommands 4-4 you can enter commands as follows: • to enter a simple command, enter the command keyword. • to enter multiple commands, enter each command in the required order. For example, to enable privileged exec command mode, and display the startup configuration, enter: console>enable...
Page 297
C ommand l ine i nterface 4-5 database). You can also display a list of valid keywords for a specific command. For example, the command “show ?” displays a list of possible show commands: the command “show interfaces ?” will display the following information: console#show ? Access-group access group...
Page 298: Partial Keyword Lookup
E ntering c ommands 4-6 partial keyword lookup if you terminate a partial keyword with a question mark, alternatives that match the initial letters are provided. (remember not to leave a space between the command and question mark.) for example “s?” shows all the keywords starting with “s.” negating...
Page 299: Exec Commands
C ommand l ine i nterface 4-7 mode. You can always enter a question mark “?” at the prompt to display a list of the commands available for the current mode. The command classes and associated modes are displayed in the following table: exec commands when you open a new console session on the switch ...
Page 300: Configuration Commands
E ntering c ommands 4-8 configuration commands configuration commands are privileged level commands used to modify switch settings. These commands modify the running configuration only and are not saved when the switch is rebooted. To store the running configuration in nonvolatile storage, use the c...
Page 301
C ommand l ine i nterface 4-9 to enter the other modes, at the configuration prompt type one of the following commands. Use the exit or end command to return to the privileged exec mode. For example, you can use the following commands to enter interface configuration mode, and then return to privile...
Page 302: Command Line Processing
E ntering c ommands 4-10 command line processing commands are not case sensitive. You can abbreviate commands and parameters as long as they contain enough letters to differentiate them from any other currently available commands or parameters. You can use the tab key to complete partial commands, o...
Page 303: Command Groups
C ommand l ine i nterface 4-11 command groups the system commands can be broken down into the functional groups shown below . Table 4-4 command group index command group description page line sets communication parameters for the serial port and telnet, including baud rate and console time-out 4-14 ...
Page 304
C ommand g roups 4-12 the access mode shown in the following tables is indicated by these abbreviations: ne (normal exec) ic (interface configuration) pe (privileged exec) vc (vlan database configuration gc (global configuration) acl (access control list configuration) lc (line configuration) power ...
Page 305: Line Commands
C ommand l ine i nterface 4-13 line commands you can access the onboard configuration program by attaching a vt100 compatible device to the switch’s serial port. These commands are used to set communication parameters for the serial port or telnet (i.E., a virtual terminal). Table 4-5 line commands ...
Page 307: Login
C ommand l ine i nterface 4-15 login this command enables password checking at login. Use the no form to disable password checking and allow connections without a password. Syntax login [local] no login local - selects local password checking. Authentication is based on the user name specified with ...
Page 309: Timeout Login Response
C ommand l ine i nterface 4-17 related commands login (4-15) password-thresh (4-19) timeout login response this command sets the interval that the system waits for a user to log into the cli. Use the no form to restore the default setting. Syntax timeout login response[seconds] no timeout login resp...
Page 310: Exec-Timeout
L ine c ommands 4-18 exec-timeout this command sets the interval that the system waits until user input is detected. Use the no form to restore the default. Syntax exec-timeout [seconds] no exec-timeout seconds - integer that specifies the number of seconds. (range: 0 - 65535 seconds; 0: no timeout)...
Page 311: Password-Thresh
C ommand l ine i nterface 4-19 password-thresh this command sets the password intrusion threshold which limits the number of failed logon attempts. Use the no form to remove the threshold value. Syntax password-thresh [threshold] no password-thresh threshold - the number of allowed password attempts...
Page 312: Silent-Time
L ine c ommands 4-20 silent-time this command sets the amount of time the management console is inaccessible after the number of unsuccessful logon attempts exceeds the threshold set by the password-thresh command. Use the no form to remove the silent time value. Syntax silent-time seconds no silent...
Page 313: Parity
C ommand l ine i nterface 4-21 default setting 8 data bits per character command mode line configuration command usage the databits command can be used to mask the high bit on input from devices that generate 7 data bits with parity. If parity is being generated, specify 7 data bits per character. I...
Page 314: Speed
L ine c ommands 4-22 command usage communication protocols provided by devices such as terminals and modems often require a specific parity bit setting. Example to specify no parity, enter this command: speed this command sets the terminal line’s baud rate. This command sets both the transmit (to te...
Page 317: General Commands
C ommand l ine i nterface 4-25 general commands enable this command activates privileged exec mode. In privileged mode, additional commands are available, and certain commands display additional information. See “understanding command modes” on page 4-6. Syntax enable [level] level - privilege level...
Page 318: Disable
G eneral c ommands 4-26 command usage • “super” is the default password required to change the command mode from normal exec to privileged exec. (to set this password, see the enable password command on page 4-36.) • the “#” character is appended to the end of the prompt to indicate that the system ...
Page 319: Configure
C ommand l ine i nterface 4-27 configure this command activates global configuration mode. You must enter this mode to modify any settings on the switch. You must also enter global configuration mode prior to enabling some of the other configuration modes, including interface configuration, line con...
Page 320: Reload
G eneral c ommands 4-28 example in this example, the show history command lists the contents of the command history buffer: the ! Command repeats commands from the execution command history buffer when you are in normal exec or privileged exec mode, and commands from the configuration command histor...
Page 321: End
C ommand l ine i nterface 4-29 example this example shows how to reset the switch: end this command returns to privileged exec mode. Default setting none command mode global configuration, interface configuration, line configuration, vlan database configuration, and multiple spanning tree configurat...
Page 322: Quit
G eneral c ommands 4-30 example this example shows how to return to the privileged exec mode from the global configuration mode, and then quit the cli session: quit use this command to exit the configuration program. Default setting none command mode normal exec, privileged exec command usage the qu...
Page 323: System Management Commands
C ommand l ine i nterface 4-31 system management commands these commands are used to control system logs, passwords, user names, browser configuration options, and display or configure a variety of other system information. Table 4-7 system management commands command group function page device desi...
Page 324: Device Designation Commands
S ystem m anagement c ommands 4-32 device designation commands prompt this command customizes the cli prompt. Use the no form to revert to the default prompt. Syntax prompt string no prompt string - any alphanumeric string to use for the command prompt. (maximum length: 255 characters) default setti...
Page 325: Hostname
C ommand l ine i nterface 4-33 hostname this command specifies or modifies the host name for this device. Use the no form to restore the default host name. Syntax hostname name no hostname name - the name of this host. (maximum length: 255 characters) default setting none command mode global configu...
Page 326: User Access Commands
S ystem m anagement c ommands 4-34 user access commands the basic commands required for management access are listed in this section. This switch also includes other options for password checking via the console or a telnet connection (page 4-13), user authentication via a remote authentication serv...
Page 327
C ommand l ine i nterface 4-35 default setting • the default access level is normal exec. • the factory defaults for the user names and passwords are: command mode global configuration command usage the encrypted password is required for compatibility with legacy password settings (i.E., plain text ...
Page 328: Enable Password
S ystem m anagement c ommands 4-36 enable password after initially logging onto the system, you should set the privileged exec password. Remember to record it in a safe place. Use this command to control access to the privileged exec level from the normal exec level. Use the no form to reset the def...
Page 329: Ip Filter Commands
C ommand l ine i nterface 4-37 related commands enable (4-25) authentication enable (4-99) ip filter commands management this command specifies the client ip addresses that are allowed management access to the switch through various protocols. Use the no form to restore the default setting. Syntax [...
Page 330: Show Management
S ystem m anagement c ommands 4-38 command usage • if anyone tries to access a management interface on the switch from an invalid address, the switch will reject the connection, enter an event message in the system log, and send a trap message to the trap manager. • ip address can be configured for ...
Page 331: Web Server Commands
C ommand l ine i nterface 4-39 example web server commands console#show management all-client management ip filter http-client: start ip address end ip address ----------------------------------------------- 1. 192.168.1.19 192.168.1.19 2. 192.168.1.25 192.168.1.30 snmp-client: start ip address end ...
Page 332: Ip Http Port
S ystem m anagement c ommands 4-40 ip http port this command specifies the tcp port number used by the web browser interface. Use the no form to use the default port. Syntax ip http port port-number no ip http port port-number - the tcp port to be used by the browser interface. (range: 1-65535) defa...
Page 333: Ip Http Secure-Server
C ommand l ine i nterface 4-41 example related commands ip http port (4-40) ip http secure-server this command enables the secure hypertext transfer protocol (https) over the secure socket layer (ssl), providing secure access (i.E., an encrypted connection) to the switch’s web interface. Use the no ...
Page 334: Ip Http Secure-Port
S ystem m anagement c ommands 4-42 • the following web browsers and operating systems currently support https: • to specify a secure-site certificate, see “replacing the default secure-site certificate” on page 3-77. Also refer to the copy command on page 4-82. Example related commands ip http secur...
Page 335: Telnet Server Commands
C ommand l ine i nterface 4-43 command usage • you cannot configure the http and https servers to use the same port. • if you change the https port number, clients attempting to connect to the https server must specify the port number in the url, in this format: https://device:port_number example re...
Page 336: Secure Shell Commands
S ystem m anagement c ommands 4-44 default setting • server: enabled • server port: 23 command mode global configuration example secure shell commands the berkley-standard includes remote access tools originally designed for unix systems. Some of these tools have also been implemented for microsoft ...
Page 337
C ommand l ine i nterface 4-45 the ssh server on this switch supports both password and public key authentication. If password authentication is specified by the ssh client, then the password can be authenticated either locally or via a radius or tacacs+ remote authentication server, as specified by...
Page 338
S ystem m anagement c ommands 4-46 switch as described in the following section. Note that regardless of whether you use public key or password authentication, you still have to generate authentication keys on the switch and enable the ssh server. To use the ssh server, complete these steps: 1. Gene...
Page 339: Ip Ssh Server
C ommand l ine i nterface 4-47 5. Enable ssh service – use the ip ssh server command to enable the ssh server on the switch. 6. Configure challenge-response authentication – when an ssh client attempts to contact the switch, the ssh server uses the host key pair to negotiate a session key and encryp...
Page 340: Ip Ssh Timeout
S ystem m anagement c ommands 4-48 command usage • the ssh server supports up to four client sessions. The maximum number of client sessions includes both current telnet sessions and ssh sessions. • the ssh server uses dsa or rsa for key exchange when the client first establishes a connection with t...
Page 341
C ommand l ine i nterface 4-49 command usage the timeout specifies the interval the switch will wait for a response from the client during the ssh negotiation phase. Once an ssh session has been established, the timeout for user input is controlled by the exec-timeout command for vty sessions. Examp...
Page 342: Ip Ssh Server-Key Size
S ystem m anagement c ommands 4-50 ip ssh server-key size this command sets the ssh server key size. Use the no form to restore the default setting. Syntax ip ssh server-key size key-size no ip ssh server-key size key-size – the size of server key. (range: 512-896 bits) default setting 768 bits comm...
Page 345: Show Ip Ssh
C ommand l ine i nterface 4-53 default setting saves both the dsa and rsa key. Command mode privileged exec example related commands ip ssh crypto host-key generate (4-51) show ip ssh this command displays the connection settings used when authenticating client access to the ssh server. Command mode...
Page 346
S ystem m anagement c ommands 4-54 table 4-16 show ssh - display description field description session the session number. (range: 0-3) version the secure shell version number. State the authentication negotiation state. (values: negotiation-started, authentication-started, session-started) username...
Page 348: Event Logging Commands
S ystem m anagement c ommands 4-56 example event logging commands console#show public-key host host: rsa: 1024 35 156849954018676692593339467750546173253136748908365472541502024559319 986854435836165199992332978176606583095861082591321289023376546801726 2725714134287629413011961955667825956641048695...
Page 349: Logging On
C ommand l ine i nterface 4-57 logging on this command controls logging of error messages, sending debug or error messages to switch memory. The no form disables the logging process. Syntax [no] logging on default setting none command mode global configuration command usage the logging process contr...
Page 350
S ystem m anagement c ommands 4-58 • ram - event history stored in temporary ram (i.E., memory flushed on power reset). • level - one of the syslog severity levels listed in the following table. Messages sent include the selected level down to level 0. Default setting • flash: errors (level 3 - 0) •...
Page 351: Logging Host
C ommand l ine i nterface 4-59 logging host this command adds a syslog server host ip address that will receive logging messages. Use the no form to remove a syslog server host. Syntax [no] logging host host_ip_address host_ip_address - the ip address of a syslog server. Default setting none command...
Page 352: Logging Trap
S ystem m anagement c ommands 4-60 command usage the command specifies the facility type tag sent in syslog messages. (see rfc 3164.) this type has no effect on the kind of messages reported by the switch. However, it may be used by the syslog server to sort messages or to store messages in the corr...
Page 354
S ystem m anagement c ommands 4-62 default setting none command mode privileged exec example the following example shows that system logging is enabled, the message level for flash memory is “errors” (i.E., default level 3 - 0), and the message level for ram is “debugging” (i.E., default level 7 - 0...
Page 356: Smtp Alert Commands
S ystem m anagement c ommands 4-64 example the following example shows the event message stored in ram. Smtp alert commands configures smtp event handling, and forwarding of alert messages to the specified smtp servers and email recipients. Logging sendmail host this command specifies smtp servers t...
Page 357: Logging Sendmail Level
C ommand l ine i nterface 4-65 default setting none command mode global configuration command usage • you can specify up to three smtp servers for event handing. However, you must enter a separate command to specify each server. • to send email alerts, the switch first opens a connection, sends all ...
Page 358
S ystem m anagement c ommands 4-66 command usage the specified level indicates an event threshold. All events at this level or higher will be sent to the configured email recipients. (for example, using level 7 will report all events from level 7 to level 0.) example this example will send email ale...
Page 359: Logging Sendmail
C ommand l ine i nterface 4-67 logging sendmail destination-email this command specifies the email recipients of alert messages. Use the no form to remove a recipient. Syntax [no] logging sendmail destination-email email-address email-address - the recipient email address for alert messages. (range:...
Page 360: Show Logging Sendmail
S ystem m anagement c ommands 4-68 example show logging sendmail this command displays the settings for the smtp event handler. Command mode normal exec, privileged exec example time commands the system clock can be dynamically set by polling a set of specified time servers (ntp or sntp). Maintainin...
Page 361: Sntp Client
C ommand l ine i nterface 4-69 sntp client this command enables sntp client requests for time synchronization from ntp or sntp time servers specified with the sntp servers command. Use the no form to disable sntp client requests. Syntax [no] sntp client default setting none command mode global confi...
Page 362: Sntp Server
S ystem m anagement c ommands 4-70 example related commands sntp server (4-70) sntp poll (4-71) show sntp (4-72) sntp server this command sets the ip address of the servers to which sntp time requests are issued. Use the this command with no arguments to clear all time servers from the current list....
Page 363: Sntp Poll
C ommand l ine i nterface 4-71 command usage this command specifies time servers from which the switch will poll for time updates when set to sntp client mode. The client will poll the time servers in the order specified until a response is received. It issues time synchronization requests based on ...
Page 364: Show Sntp
S ystem m anagement c ommands 4-72 related commands sntp client (4-69) show sntp this command displays the current time and configuration settings for the sntp client, and indicates whether or not the local time has been properly updated. Command mode normal exec, privileged exec command usage this ...
Page 367: System Status Commands
C ommand l ine i nterface 4-75 example this example shows how to display the current system clock setting. System status commands show startup-config this command displays the configuration file stored in non-volatile memory that is used to start up the system. Default setting none command mode priv...
Page 368
S ystem m anagement c ommands 4-76 • this command displays settings for key command modes. Each mode group is separated by “!” symbols, and includes the configuration mode command, and corresponding commands. This command displays the following information: - users (names and access levels) - snmp c...
Page 369: Show Running-Config
C ommand l ine i nterface 4-77 related commands show running-config (4-77) show running-config this command displays the configuration information currently in use. Default setting none command mode privileged exec command usage • use this command in conjunction with the show startup-config command ...
Page 370
S ystem m anagement c ommands 4-78 example related commands show startup-config (4-75) console#show running-config ! Ip address dhcp ! Phymap 00-04-e2-b3-16-c0 00-30-f1-b0-e9-80 00-00-00-00-00-00 00-00-00-00-00-00 00-00-00-00-00-00 00-00-00-00-00-00 00-00-00-00-00-00 00-00-00-00-00-00 ! Sntp server ...
Page 371: Show System
C ommand l ine i nterface 4-79 show system this command displays system information. Default setting none command mode normal exec, privileged exec command usage • for a description of the items shown by this command, refer to “displaying system information” on page 3-13. • the post results should a...
Page 372: Show Users
S ystem m anagement c ommands 4-80 show users shows all active console and telnet sessions, including user name, idle time, and ip address of telnet client. Default setting none command mode normal exec, privileged exec command usage the session used to execute this command is indicated by a “*” sym...
Page 373: Flash/file Commands
C ommand l ine i nterface 4-81 command mode normal exec, privileged exec command usage see “displaying switch hardware/software versions” on page 3-15 for detailed information on the items displayed by this command. Example flash/file commands these commands are used to manage the system code or con...
Page 374: Copy
F lash /f ile c ommands 4-82 copy use this command to move (upload/download) a code image or configuration file between the switch’s flash memory and a tftp server. When you save the system code or configuration settings to a file on a tftp server, that file can later be downloaded to the switch to ...
Page 375
C ommand l ine i nterface 4-83 command usage • the system prompts for data required to complete the copy command. • the destination file name should not contain slashes (\ or /), the leading letter of the file name should not be a period (.), and the maximum length for file names on the tftp server ...
Page 376
F lash /f ile c ommands 4-84 example the following example shows how to upload the configuration settings to a file on the tftp server. The following example shows how to copy the running configuration to a startup file. The following example shows how to download a configuration file. This example ...
Page 377
C ommand l ine i nterface 4-85 this example shows how to copy a public-key used by ssh from an tftp server. Note that public key authentication via ssh is only supported for users configured locally on the switch. This ex3ample shows how to download a poe controller file (to the smc6824mpe or smc682...
Page 378: Delete
F lash /f ile c ommands 4-86 delete this command deletes a file or image. Syntax delete [unit:] filename filename - name of the configuration file or image name. Unit - specifies the stack unit. (range: 1-8) default setting none command mode privileged exec command usage • if the file type is used f...
Page 380: Whichboot
F lash /f ile c ommands 4-88 example the following example shows how to display all file information: whichboot this command displays which files were booted when the system powered up. Command mode privileged exec example this example shows the information displayed by the whichboot command. See th...
Page 382
P ower over e thernet c ommands 4-90 power over ethernet commands the commands in this group control the power that can be delivered to attached poe devices through the switch ports on the smc6824mpe and smc6826mpe. The switch’s power management enables total switch power and individual port power t...
Page 383: Power Inline Compatible
C ommand l ine i nterface 4-91 power mainpower maximum allocation this command defines a power budget for the switch (i.E., the power available to all switch ports). Use the no form to restore the default setting. Syntax power mainpower maximum allocation watts> [unit unit] • watts - the power budge...
Page 384
P ower over e thernet c ommands 4-92 default setting disabled command mode global configuration command usage • the switch automatically detects attached poe devices by periodically transmitting test voltages that over the 10/100base-tx ports. When an 802.3af compatible device is plugged into one of...
Page 385: Power Inline
C ommand l ine i nterface 4-93 power inline this command instructs the switch to automatically detect if a poe-compliant device is connected to the specified port, and turn power on or off accordingly. Use the no form to turn off power for a port. Syntax [no] power inline default setting detection i...
Page 386: Power Inline Priority
P ower over e thernet c ommands 4-94 command mode interface configuration command usage if a device is connected to a switch port and the switch detects that it requires more than the maximum power allocated to the port, no power is supplied to the device (i.E., port power remains off). Example powe...
Page 387: Show Power Inline Status
C ommand l ine i nterface 4-95 • power is dropped from low-priority ports in sequence starting from port number 1. Example related commands power mainpower maximum allocation (4-91) show power inline status this command displays the current power status for all ports or for specific ports. Syntax sh...
Page 388: Show Power Mainpower
P ower over e thernet c ommands 4-96 show power mainpower use this command to display the current power status for the switch. Command mode privileged exec example table 4-27 show power inline status parameters parameter description admin the power mode set on the port (see power inline on page 4-93...
Page 389: Authentication Commands
C ommand l ine i nterface 4-97 authentication commands you can configure this switch to authenticate users logging into the system for management access using local or radius authentication methods. You can also enable port-based authentication for network client access using ieee 802.1x. Authentica...
Page 390: Authentication Login
A uthentication c ommands 4-98 authentication login this command defines the login authentication method and precedence. Use the no form to restore the default. Syntax authentication login {[local] [radius] [tacacs]} no authentication login • local - use local password. • radius - use radius server ...
Page 391: Authentication Enable
C ommand l ine i nterface 4-99 example related commands username - for setting the local user names and passwords (4-34) authentication enable this command defines the authentication method and precedence to use when changing from exec command mode to privileged exec command mode with the enable com...
Page 392: Radius Client
A uthentication c ommands 4-100 • you can specify three authentication methods in a single command to indicate the authentication sequence. For example, if you enter “authentication enable radius tacacs local,” the user name and password on the radius server is verified first. If the radius server i...
Page 394: Radius-Server Port
A uthentication c ommands 4-102 radius-server port this command sets the radius server network port. Use the no form to restore the default. Syntax radius-server port port_number no radius-server port port_number - radius server udp port used for authentication messages. (range: 1-65535) default set...
Page 395: Radius-Server Retransmit
C ommand l ine i nterface 4-103 example radius-server retransmit this command sets the number of retries. Use the no form to restore the default. Syntax radius-server retransmit number_of_retries no radius-server retransmit number_of_retries - number of times the switch will try to authenticate logo...
Page 396: Show Radius-Server
A uthentication c ommands 4-104 command mode global configuration example show radius-server this command displays the current settings for the radius server. Default setting none command mode privileged exec example console(config)#radius-server timeout 10 console(config)# console#show radius-serve...
Page 397: Tacacs+ Client
C ommand l ine i nterface 4-105 tacacs+ client terminal access controller access control system (tacacs+) is a logon authentication protocol that uses software running on a central server to control access to tacacs-aware devices on the network. An authentication server contains a database of multip...
Page 398: Tacacs-Server Port
A uthentication c ommands 4-106 tacacs-server port this command specifies the tacacs+ server network port. Use the no form to restore the default. Syntax tacacs-server port port_number no tacacs-server port port_number - tacacs+ server tcp port used for authentication messages. (range: 1-65535) defa...
Page 399: Show Tacacs-Server
C ommand l ine i nterface 4-107 example show tacacs-server this command displays the current settings for the tacacs+ server. Default setting none command mode privileged exec example port security commands these commands can be used to enable port security on a port. When using port security, the s...
Page 400: Port Security
A uthentication c ommands 4-108 port security this command enables or configures port security. Use the no form without any keywords to disable port security. Use the no form with the appropriate keyword to restore the default settings for a response to security violation or for the maximum number o...
Page 401
C ommand l ine i nterface 4-109 command usage • if you enable port security, the switch stops learning new mac addresses on the specified port when it has reached a configured maximum number. Only incoming traffic with source addresses already stored in the dynamic or static address table will be ac...
Page 402: 802.1X Port Authentication
A uthentication c ommands 4-110 802.1x port authentication the switch supports ieee 802.1x (dot1x) port-based access control that prevents unauthorized access to the network by requiring users to first submit credentials for authentication. Client authentication is controlled centrally by a radius s...
Page 403: Dot1X System-Auth-Control
C ommand l ine i nterface 4-111 dot1x system-auth-control this command enables ieee 802.1x port authentication globally on the switch. Use the no form to restore the default. Syntax [no] dot1x system-auth-control default setting disabled command mode global configuration example dot1x default this c...
Page 405: Dot1X Operation-Mode
C ommand l ine i nterface 4-113 dot1x operation-mode this command allows single or multiple hosts (clients) to connect to an 802.1x-authorized port. Use the no form with no keywords to restore the default to single host. Use the no form with the multi-host max-count keywords to restore the default m...
Page 406: Dot1X Re-Authenticate
A uthentication c ommands 4-114 dot1x re-authenticate this command forces re-authentication on all ports or a specific interface. Syntax dot1x re-authenticate [interface] interface ethernet unit/port - unit - the stack unit. (range: 1-8) - port - port number. (range: 1-26) command mode privileged ex...
Page 407: Dot1X Timeout Quiet-Period
C ommand l ine i nterface 4-115 dot1x timeout quiet-period this command sets the time that a switch port waits after the max request count has been exceeded before attempting to acquire a new client. Use the no form to reset the default. Syntax dot1x timeout quiet-period seconds no dot1x timeout qui...
Page 408: Dot1X Timeout Tx-Period
A uthentication c ommands 4-116 example dot1x timeout tx-period this command sets the time that an interface on the switch waits during an authentication session before re-transmitting an eap packet. Use the no form to reset to the default value. Syntax dot1x timeout tx-period seconds no dot1x timeo...
Page 409
C ommand l ine i nterface 4-117 command mode privileged exec command usage this command displays the following information: • global 802.1x parameters – shows whether or not 802.1x port authentication is globally enabled on the switch. • 802.1x port summary – displays the port access control paramet...
Page 410
A uthentication c ommands 4-118 - supplicant– mac address of authorized client. - current identifier– the integer (0-255) used by the authenticator to identify the current authentication session. • authenticator state machine - state– current state (including initialize, disconnected, connecting, au...
Page 411
C ommand l ine i nterface 4-119 access control list commands access control lists (acl) provide packet filtering for ip frames (based on address, protocol, layer 4 protocol port number or tcp control code) or any frames (based on mac address or ethernet type). To filter packets, first create an acce...
Page 412
A ccess c ontrol l ist c ommands 4-120 soon as it matches a deny rule. If no rules match for a list of all permit rules, the packet is dropped; and if no rules match for a list of all deny rules, the packet is accepted. There are three filtering modes: • standard ip acl mode (std-acl) filters packet...
Page 413
C ommand l ine i nterface 4-121 • egress mac acls only work for destination-mac-known packets, not for multicast, broadcast, or destination-mac-unknown packets. The order in which active acls are checked is as follows: 1. User-defined rules in the egress mac acl for egress ports. 2. User-defined rul...
Page 414: Ip Acls
A ccess c ontrol l ist c ommands 4-122 ip acls table 4-36 ip acl commands command function mode page access-list ip creates an ip acl and enters configuration mode gc 4-123 access-list ip extended fragment-auto-mask automatically creates extra masks to support fragmented acl entries gc 4-123 permit,...
Page 416
A ccess c ontrol l ist c ommands 4-124 access-list ip extended fragment-auto-mask this command automatically creates extra masks to support fragmented acl entries. Use the no form to disable this feature. Syntax [no] access-list ip extended fragment-auto-mask default setting disabled command mode gl...
Page 417
C ommand l ine i nterface 4-125 command mode standard acl command usage • new rules are appended to the end of the list. • address bitmasks are similar to a subnet mask, containing four integers from 0 to 255, each separated by a period. The binary mask uses 1 bits to indicate “match” and 0 bits to ...
Page 419
C ommand l ine i nterface 4-127 with the address for each ip packet entering the port(s) to which this acl has been assigned. • you can specify both precedence and tos in the same rule. However, if dscp is used, then neither precedence nor tos can be specified. • the control-code bitmask is a decima...
Page 423
C ommand l ine i nterface 4-131 determined by the mask, and not the order in which the acl rules were entered. • first create the required acls and ingress or egress masks before mapping an acl to an interface. • if you enter dscp, you cannot enter tos or precedence. You can enter both tos and prece...
Page 424
A ccess c ontrol l ist c ommands 4-132 this shows how to create a standard acl with an ingress mask to deny access to the ip host 171.69.198.102, and permit access to any others. This shows how to create an extended acl with an egress mask to drop packets leaving network 171.69.198.0 when the layer ...
Page 425
C ommand l ine i nterface 4-133 this is a more comprehensive example. It denies any tcp packets in which the syn bit is on, and permits all other packets. It then sets the ingress mask to check the deny rule first, and finally binds port 1 to this acl. Note that once the acl is bound to an interface...
Page 427: Show Ip Access-Group
C ommand l ine i nterface 4-135 related commands show ip access-list (4-128) show ip access-group this command shows the ports assigned to ip acls. Command mode privileged exec example related commands ip access-group (4-134) map access-list ip this command sets the output queue for packets matching...
Page 428: Show Map Access-List Ip
A ccess c ontrol l ist c ommands 4-136 • a packet matching a rule within the specified acl is mapped to one of the output queues as shown in the following table. For information on mapping the cos values to output queues, see queue cos-map on page 4-257. Example related commands queue cos-map (4-257...
Page 429: Match Access-List Ip
C ommand l ine i nterface 4-137 related commands map access-list ip (4-135) match access-list ip this command changes the ieee 802.1p priority, ip precedence, or dscp priority of a frame matching the defined acl rule. (this feature is commonly referred to as acl packet marking.) use the no form to r...
Page 430: Show Marking
A ccess c ontrol l ist c ommands 4-138 ip frame header can include either the ip precedence or dscp priority type. • the precedence for priority mapping by this switch is ip precedence or dscp priority, and then 802.1p priority. Example related commands show marking (4-138) show marking this command...
Page 431: Access-List Mac
C ommand l ine i nterface 4-139 access-list mac this command adds a mac access list and enters mac acl configuration mode. Use the no form to remove the specified acl. Syntax [no] access-list mac acl_name acl_name – name of the acl. (maximum length: 15 characters) default setting none command mode g...
Page 432: Permit, Deny (Mac Acl)
A ccess c ontrol l ist c ommands 4-140 command usage • an egress acl must contain all deny rules. • when you create a new acl or enter configuration mode for an existing acl, use the permit or deny command to add new rules to the bottom of the list. To create an acl, you must add at least one rule t...
Page 434: Show Mac Access-List
A ccess c ontrol l ist c ommands 4-142 • a detailed listing of ethernet protocol types can be found in rfc 1060. A few of the more common types include the following: - 0800 - ip - 0806 - arp - 8137 - ipx example this rule permits packets from any source mac address to the destination address 00-e0-...
Page 437
C ommand l ine i nterface 4-145 example this example shows how to create an ingress mac acl and bind it to a port. You can then see that the order of the rules have been changed by the mask. This example creates an egress mac acl. Console(config)#access-list mac m4 console(config-mac-acl)#permit any...
Page 439: Show Mac Access-Group
C ommand l ine i nterface 4-147 • if a port is already bound to an acl and you bind it to a different acl, the switch will replace the old binding with the new one. • you must configure a mask for an acl rule before you can bind it to a port. Example related commands show mac access-list (4-142) sho...
Page 440: Show Map Access-List Mac
A ccess c ontrol l ist c ommands 4-148 default setting none command mode interface configuration (ethernet) command usage • you must configure an acl mask before you can map cos values to the rule. • by default, a packet matching a rule within the specified acl is mapped to one of the output queues ...
Page 441: Match Access-List Mac
C ommand l ine i nterface 4-149 command mode privileged exec example related commands map access-list mac (4-147) match access-list mac this command changes the ieee 802.1p priority of a layer 2 frame matching the defined acl rule. (this feature is commonly referred to as acl packet marking.) use th...
Page 442: Acl Information
A ccess c ontrol l ist c ommands 4-150 related commands show marking (4-138) acl information show access-list this command shows all acls and associated rules, as well as all the user-defined masks. Command mode privileged exec command usage once the acl is bound to an interface (i.E., the acl is ac...
Page 443: Show Access-Group
C ommand l ine i nterface 4-151 show access-group this command shows the port assignments of acls. Command mode privileged executive example snmp commands controls access to this switch from management stations using the simple network management protocol (snmp), as well as the error types sent to t...
Page 444: Snmp-Server
Snmp c ommands 4-152 snmp-server this command enables the snmpv3 engine and services for all management clients (i.E., versions 1, 2c, 3). Use the no form to disable the server. Syntax [no] snmp-server default setting enabled command mode global configuration example snmp-server location sets the sy...
Page 445: Show Snmp
C ommand l ine i nterface 4-153 show snmp this command can be used to check the status of snmp communications. Default setting none command mode normal exec, privileged exec command usage this command provides information on the community access strings, counter information for snmp input and output...
Page 447: Snmp-Server Location
C ommand l ine i nterface 4-155 default setting none command mode global configuration example related commands snmp-server location (4-155) snmp-server location this command sets the system location string. Use the no form to remove the location string. Syntax snmp-server location text no snmp-serv...
Page 449
C ommand l ine i nterface 4-157 default setting • host address: none • notification type: traps • snmp version: 1 • udp port: 162 command mode global configuration command usage • if you do not enter an snmp-server host command, no notifications are sent. In order to configure the switch to send snm...
Page 450
Snmp c ommands 4-158 3. Specify the target host that will receive inform messages with the snmp-server host command as described in this section. 4. Create a view with the required notification messages (page 4-162). 5. Create a group that includes the required notify view (page 4-164). To send an i...
Page 453: Show Snmp Engine-Id
C ommand l ine i nterface 4-161 the engine id of the authoritative agent. For informs, the authoritative snmp agent is the remote agent. You therefore need to configure the remote agent’s snmp engine id before you can send proxy requests or informs to it. • trailing zeroes need not be entered to uni...
Page 455: Show Snmp View
C ommand l ine i nterface 4-163 examples this view includes mib-2. This view includes the mib-2 interfaces table, ifdescr. The wild card is used to select all the index values in this table. This view includes the mib-2 interfaces table, and the mask selects all index entries. Show snmp view this co...
Page 457: Show Snmp Group
C ommand l ine i nterface 4-165 command usage • a group sets the access policy for the assigned users. • when authentication is selected, the md5 or sha algorithm is used as specified in the snmp-server user command. • when privacy is selected, the des 56-bit algorithm is used for data encryption • ...
Page 458
Snmp c ommands 4-166 group name: public security model: v2c read view: defaultview write view: none notify view: none storage type: volatile row status: active group name: private security model: v1 read view: defaultview write view: defaultview notify view: none storage type: volatile row status: a...
Page 460
Snmp c ommands 4-168 id with the snmp-server engine-id command before using this configuration command. • before you configure a remote user, use the snmp-server engine-id command (page 4-160) to specify the engine id for the remote device where the user resides. Then use the snmp-server user comman...
Page 461: Show Snmp User
C ommand l ine i nterface 4-169 show snmp user this command shows information on snmp users. Command mode privileged exec example console#show snmp user engineid: 01000000000000000000000000 user name: steve authentication protocol: md5 privacy protocol: des56 storage type: nonvolatile row status: ac...
Page 462: Interface Commands
I nterface c ommands 4-170 interface commands these commands are used to display or set communication parameters for an ethernet port, aggregated link, or vlan. Table 4-46 interface commands command function mode page interface configures an interface type and enters interface configuration mode gc ...
Page 463: Interface
C ommand l ine i nterface 4-171 interface this command configures an interface type and enter interface configuration mode. Use the no form to remove a trunk. Syntax interface interface no interfaceport-channel channel-id interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port...
Page 464: Speed-Duplex
I nterface c ommands 4-172 default setting none command mode interface configuration (ethernet, port channel) example the following example adds a description to port 25 speed-duplex this command configures the speed and duplex mode of a given interface when autonegotiation is disabled. Use the no f...
Page 465: Negotiation
C ommand l ine i nterface 4-173 • when using the negotiation command to enable auto-negotiation, the optimal settings will be determined by the capabilities command. To set the speed/duplex mode under auto-negotiation, the required mode must be specified in the capabilities list for an interface. Ex...
Page 466: Capabilities
I nterface c ommands 4-174 example the following example configures port 11 to use autonegotiation related commands negotiation (4-173) speed-duplex (4-172) capabilities this command advertises the port capabilities of a given interface during autonegotiation. Use the no form with parameters to remo...
Page 467: Flowcontrol
C ommand l ine i nterface 4-175 command usage when auto-negotiation is enabled with the negotiation command, the switch will negotiate the best settings for a link based on the capabilities command. When auto-negotiation is disabled, you must manually specify the link attributes with the speed-duple...
Page 468: Shutdown
I nterface c ommands 4-176 • to force flow control on or off (with the flowcontrol or no flowcontrol command), use the no negotiation command to disable auto-negotiation on the selected interface. • when using the negotiation command to enable auto-negotiation, the optimal settings will be determine...
Page 469
C ommand l ine i nterface 4-177 example the following example disables port 5. Switchport broadcast packet-rate this command configures broadcast storm control. Use the no form to disable broadcast storm control. Syntax switchport broadcast packet-rate rate no switchport broadcast rate - threshold l...
Page 470: Clear Counters
I nterface c ommands 4-178 clear counters this command clears statistics on an interface. Syntax clear counters interface interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port number. (range: 1-26) • port-channel channel-id (range: 1-6) default setting none command mode priv...
Page 471: Show Interfaces Status
C ommand l ine i nterface 4-179 show interfaces status this command displays the status for an interface. Syntax show interfaces status [interface] interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port number. (range: 1-26) • port-channel channel-id (range: 1-6) • vlan vlan-...
Page 472: Show Interfaces Counters
I nterface c ommands 4-180 example show interfaces counters this command displays interface statistics. Syntax show interfaces counters [interface] interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port number. (range: 1-26) • port-channel channel-id (range: 1-6) default sett...
Page 473
C ommand l ine i nterface 4-181 command usage if no interface is specified, information on all interfaces is displayed. For a description of the items displayed by this command, see “showing port statistics” on page 3-139. Example console#show interfaces counters ethernet 1/7 ethernet 1/7 iftable st...
Page 474: Show Interfaces Switchport
I nterface c ommands 4-182 show interfaces switchport this command displays the administrative and operational status of the specified interfaces. Syntax show interfaces switchport [interface] interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port number. (range: 1-26) • port...
Page 475
C ommand l ine i nterface 4-183 table 4-47 show interfaces switchport - display description field description broadcast threshold shows if broadcast storm suppression is enabled or disabled; if enabled it also shows the threshold level (page 4-177). Lacp status shows if link aggregation control prot...
Page 477: Show Port Monitor
C ommand l ine i nterface 4-185 • the destination port is set by specifying an ethernet interface. • the mirror port and monitor port speeds should match, otherwise traffic may be dropped from the monitor port. • you can create multiple mirror sessions, but all sessions must share the same destinati...
Page 478: Rate Limit Commands
R ate l imit c ommands 4-186 example the following shows mirroring configured from port 6 to port 11: rate limit commands this function allows the network manager to control the maximum rate for traffic transmitted or received on an interface. Rate limiting is configured on interfaces at the edge of...
Page 480: Link Aggregation Commands
L ink a ggregation c ommands 4-188 link aggregation commands ports can be statically grouped into an aggregate link (i.E., trunk) to increase the bandwidth of a network connection or to ensure fault recovery. Or you can use the link aggregation control protocol (lacp) to automatically negotiate a tr...
Page 481
C ommand l ine i nterface 4-189 guidelines for creating trunks general guidelines – • finish configuring port trunks before you connect the corresponding network cables between switches to avoid creating a loop. • a trunk can have up to eight ports. • the ports at both ends of a connection must be c...
Page 482: Channel-Group
L ink a ggregation c ommands 4-190 channel-group this command adds a port to a trunk. Use the no form to remove a port from a trunk. Syntax channel-group channel-id no channel-group channel-id - trunk index (range: 1-6) default setting the current port will be added to this trunk. Command mode inter...
Page 483
C ommand l ine i nterface 4-191 command mode interface configuration (ethernet) command usage • the ports on both ends of an lacp trunk must be configured for full duplex, either by forced mode or auto-negotiation. • a trunk formed with another switch using lacp will automatically be assigned the ne...
Page 485
C ommand l ine i nterface 4-193 • once the remote side of a link has been established, lacp operational settings are already in use on that side. Configuring lacp settings for the partner only applies to its administrative state, not its operational state, and will only take effect the next time an ...
Page 486
L ink a ggregation c ommands 4-194 • once the remote side of a link has been established, lacp operational settings are already in use on that side. Configuring lacp settings for the partner only applies to its administrative state, not its operational state, and will only take effect the next time ...
Page 489
C ommand l ine i nterface 4-197 marker received number of valid marker pdus received by this channel group. Lacpdus unknown pkts number of frames received that either (1) carry the slow protocols ethernet type value, but contain an unknown pdu, or (2) are addressed to the slow protocols group mac ad...
Page 490
L ink a ggregation c ommands 4-198 lacp port priority lacp port priority assigned to this interface within the channel group. Admin state, oper state administrative or operational values of the actor’s state parameters: • expired – the actor’s receive machine is in the expired state; • defaulted – t...
Page 491
C ommand l ine i nterface 4-199 console#show lacp 1 neighbors channel group 1 neighbors --------------------------------------------------------------------- eth 1/1 --------------------------------------------------------------------- partner admin system id : 32768, 00-00-00-00-00-00 partner oper ...
Page 492: Address Table Commands
A ddress t able c ommands 4-200 address table commands these commands are used to configure the address table for filtering specified addresses, displaying current entries, clearing the table, or setting the aging time. Console#show lacp sysid channel group system priority system mac address -------...
Page 493: Mac-Address-Table Static
C ommand l ine i nterface 4-201 mac-address-table static this command maps a static address to a destination port in a vlan. Use the no form to remove an address. Syntax mac-address-table static mac-address interface interface vlan vlan-id [action] no mac-address-table static mac-address vlan vlan-i...
Page 494: Show Mac-Address-Table
A ddress t able c ommands 4-202 example clear mac-address-table dynamic this command removes any learned entries from the forwarding database and clears the transmit and receive counts for any static or system configured entries. Default setting none command mode privileged exec example show mac-add...
Page 495: Mac-Address-Table Aging-Time
C ommand l ine i nterface 4-203 default setting none command mode privileged exec command usage • the mac address table contains the mac addresses associated with each interface. Note that the type field may include the following types: - learned - dynamic address entries - permanent - static entry ...
Page 496: Spanning Tree Commands
S panning t ree c ommands 4-204 command mode global configuration command usage the aging time is used to age out dynamically learned forwarding information. Example show mac-address-table aging-time this command shows the aging time for entries in the address table. Default setting none command mod...
Page 497
C ommand l ine i nterface 4-205 spanning-tree hello-time configures the spanning tree bridge hello time gc 4-209 spanning-tree max-age configures the spanning tree bridge maximum age gc 4-210 spanning-tree default priority sets the spanning-tree priority to use increments specified by ieee 802.1d (s...
Page 498: Spanning-Tree
S panning t ree c ommands 4-206 spanning-tree this command enables the spanning tree algorithm globally for the switch. Use the no form to disable it. Syntax [no] spanning-tree default setting spanning tree is enabled. Command mode global configuration command usage the spanning tree algorithm (sta)...
Page 499: Spanning-Tree Mode
C ommand l ine i nterface 4-207 ensure that only one route exists between any two stations on the network, and provide backup links which automatically take over when a primary link goes down. Example this example shows how to enable the spanning tree algorithm for the switch: spanning-tree mode use...
Page 500: Spanning-Tree Forward-Time
S panning t ree c ommands 4-208 • rapid spanning tree protocol rstp supports connections to either stp or rstp nodes by monitoring the incoming protocol messages and dynamically adjusting the type of protocol messages the rstp node transmits, as described below: - stp mode – if the switch receives a...
Page 501: Spanning-Tree Hello-Time
C ommand l ine i nterface 4-209 default setting 15 seconds command mode global configuration command usage this command sets the maximum time (in seconds) the root device will wait before changing states (i.E., discarding to learning to forwarding). This delay is required because every device must r...
Page 502: Spanning-Tree Max-Age
S panning t ree c ommands 4-210 example spanning-tree max-age this command configures the spanning tree bridge maximum age globally for this switch. Use the no form to restore the default. Syntax spanning-tree max-age seconds no spanning-tree max-age seconds - time in seconds. (range: 6-40 seconds) ...
Page 503: Spanning-Tree Priority
C ommand l ine i nterface 4-211 spanning-tree default priority use this command to configure the spanning-tree priority to use increments specified by ieee 802.1d (steps of 1) or 802.1t (steps of 4096). Use the no form to restore the default setting to increments specified by ieee 802.1t. Syntax spa...
Page 504
S panning t ree c ommands 4-212 default setting 32768 command mode global configuration command usage bridge priority is used in selecting the root device, root port, and designated port. The device with the highest priority (i.E., lower numeric value) becomes the sta root device. However, if all de...
Page 505
C ommand l ine i nterface 4-213 command usage the path cost method is used to determine the best path between devices. Therefore, lower values should be assigned to ports attached to faster media, and higher values assigned to ports with slower media. Note that path cost (page 4-212) takes precedenc...
Page 506: Spanning-Tree Backup-Root
S panning t ree c ommands 4-214 spanning-tree backup-root this command adjusts the bridge priority in an attempt to take over as the new root bridge if it loses contact with the original root device. Use the no form to disable the command. Syntax [no] spanning-tree backup-root default setting disabl...
Page 507: Mst Vlan
C ommand l ine i nterface 4-215 related commands mst vlan (4-215) mst priority (4-216) name (4-217) revision (4-218) max-hops (4-218) mst vlan this command adds vlans to a spanning tree instance. Use the no form to remove the specified vlans. Using the no form without any vlan parameters to remove a...
Page 508: Mst Priority
S panning t ree c ommands 4-216 msti region as a single node, connecting all regions to the common spanning tree. Example mst priority this command configures the priority of a spanning tree instance. Use the no form to restore the default. Syntax mst instance_id priority priority no mst instance_id...
Page 509: Name
C ommand l ine i nterface 4-217 example name this command configures the name for the multiple spanning tree region in which this switch is located. Use the no form to clear the name. Syntax name name name - name of the spanning tree. Default setting switch’s mac address command mode mst configurati...
Page 510: Revision
S panning t ree c ommands 4-218 revision this command configures the revision number for this multiple spanning tree configuration of this switch. Use the no form to restore the default. Syntax revision number number - revision number of the spanning tree. (range: 0-65535) default setting 0 command ...
Page 511
C ommand l ine i nterface 4-219 default setting 20 command mode mst configuration command usage an msti region is treated as a single node by the stp and rstp protocols. Therefore, the message age for bpdus inside an msti region is never changed. However, each spanning tree instance within a region,...
Page 512: Spanning-Tree Cost
S panning t ree c ommands 4-220 spanning-tree cost this command configures the spanning tree path cost for the specified interface. Use the no form to restore the default. Syntax spanning-tree cost cost no spanning-tree cost cost - the path cost for the port. (range: 1-200,000,000)) the recommended ...
Page 513: Spanning-Tree Port-Priority
C ommand l ine i nterface 4-221 spanning-tree port-priority use this command to configure the priority for the specified interface. Use the no form to restore the default. Syntax spanning-tree port-priority priority no spanning-tree port-priority priority - the priority for a port. (range: 0-240, in...
Page 514: Spanning-Tree Portfast
S panning t ree c ommands 4-222 default setting disabled command mode interface configuration (ethernet, port channel) command usage • you can enable this option if an interface is attached to a lan segment that is at the end of a bridged lan or to an end node. Since end nodes cannot cause forwardin...
Page 515: Spanning-Tree Link-Type
C ommand l ine i nterface 4-223 command mode interface configuration (ethernet, port channel) command usage • this command is used to enable/disable the fast spanning-tree mode for the selected port. In this mode, ports skip the discarding and learning states, and proceed straight to forwarding. • s...
Page 516: Spanning-Tree Mst Cost
S panning t ree c ommands 4-224 default setting auto command mode interface configuration (ethernet, port channel) command usage • specify a point-to-point link if the interface can only be connected to exactly one other bridge, or a shared link if it can be connected to two or more bridges. • when ...
Page 517
C ommand l ine i nterface 4-225 default setting • ethernet – half duplex: 2,000,000; full duplex: 1,000,000; trunk: 500,000 • fast ethernet – half duplex: 200,000; full duplex: 100,000; trunk: 50,000 • gigabit ethernet – full duplex: 10,000; trunk: 5,000 command mode interface configuration (etherne...
Page 518
S panning t ree c ommands 4-226 command mode interface configuration (ethernet, port channel) command usage • this command defines the priority for the use of an interface in the multiple spanning-tree. If the path cost for all interfaces on a switch are the same, the interface with the highest prio...
Page 519: Show Spanning-Tree
C ommand l ine i nterface 4-227 command usage if at any time the switch detects stp bpdus, including configuration or topology change notification bpdus, it will automatically set the selected interface to forced stp-compatible mode. However, you can also use the spanning-tree protocol-migration com...
Page 520
S panning t ree c ommands 4-228 • use the show spanning-tree interface command to display the spanning tree configuration for an interface within the common spanning tree (cst). • use the show spanning-tree mst instance_id command to display the spanning tree configuration for an instance within the...
Page 521
C ommand l ine i nterface 4-229 show spanning-tree mst configuration this command shows the configuration of the multiple spanning tree. Command mode privileged exec example --------------------------------------------------------------- eth 1/ 1 information -----------------------------------------...
Page 522: Vlan Commands
Vlan c ommands 4-230 vlan commands a vlan is a group of ports that can be located anywhere in the network, but communicate as though they belong to the same physical segment. This section describes commands used to create vlan groups, add port members, specify how vlan tagging is used, and enable au...
Page 523: Vlan
C ommand l ine i nterface 4-231 command mode global configuration command usage • use the vlan database command mode to add, change, and delete vlans. After finishing configuration changes, you can display the vlan settings by entering the show vlan command. • use the interface vlan command mode to ...
Page 524: Configuring Vlan Interfaces
Vlan c ommands 4-232 command mode vlan database configuration command usage • no vlan vlan-id deletes the vlan. • no vlan vlan-id name removes the vlan name. • no vlan vlan-id state returns the vlan to the default state (i.E., active). • you can configure up to 255 vlans on the switch. Example the f...
Page 525: Interface Vlan
C ommand l ine i nterface 4-233 interface vlan this command enters interface configuration mode for vlans, which is used to configure vlan parameters for a physical interface. Syntax interface vlan vlan-id vlan-id - id of the configured vlan. (range: 1-4093, no leading zeroes) default setting none c...
Page 528
Vlan c ommands 4-236 switchport ingress-filtering this command enables ingress filtering for an interface. Use the no form to restore the default. Syntax [no] switchport ingress-filtering default setting disabled command mode interface configuration (ethernet, port channel) command usage • ingress f...
Page 529: Switchport Native Vlan
C ommand l ine i nterface 4-237 switchport native vlan this command configures the pvid (i.E., default vlan id) for a port. Use the no form to restore the default. Syntax switchport native vlan vlan-id no switchport native vlan vlan-id - default vlan id for a port. (range: 1-4093, no leading zeroes)...
Page 531: Switchport Forbidden Vlan
C ommand l ine i nterface 4-239 • if a vlan on the forbidden list for an interface is manually added to that interface, the vlan is automatically removed from the forbidden list for that interface. Example the following example shows how to add vlans 1, 2, 5 and 6 to the allowed list as tagged vlans...
Page 533: Configuring Private Vlans
C ommand l ine i nterface 4-241 example the following example shows how to display information for vlan 1: configuring private vlans private vlans provide port-based security and isolation between ports within the assigned vlan. This switch supports two types of private vlan ports: promiscuous, and ...
Page 534
Vlan c ommands 4-242 to configure private vlans, follow these steps: 1. Use the private-vlan command to designate one or more community vlans and the primary vlan that will channel traffic outside the community groups. 2. Use the private-vlan association command to map the secondary (i.E., community...
Page 538
Vlan c ommands 4-246 switchport private-vlan host-association use this command to associate an interface with a secondary vlan. Use the no form to remove this association. Syntax switchport private-vlan host-association secondary-vlan-id no switchport private-vlan host-association • secondary-vlan-i...
Page 539: Show Vlan Private-Vlan
C ommand l ine i nterface 4-247 default setting none command mode interface configuration (ethernet, port channel) command usage promiscuous ports assigned to a primary vlan can communicate with any other promiscuous ports in the same vlan, and with the group members within any associated secondary ...
Page 540
Gvrp and b ridge e xtension c ommands 4-248 example gvrp and bridge extension commands garp vlan registration protocol defines a way for switches to exchange vlan information in order to automatically register vlan members on interfaces across the network. This section describes how to enable gvrp f...
Page 541: Bridge-Ext Gvrp
C ommand l ine i nterface 4-249 bridge-ext gvrp this command enables gvrp globally for the switch. Use the no form to disable it. Syntax [no] bridge-ext gvrp default setting disabled command mode global configuration command usage gvrp defines a way for switches to exchange vlan information in order...
Page 542: Switchport Gvrp
Gvrp and b ridge e xtension c ommands 4-250 example switchport gvrp this command enables gvrp for a port. Use the no form to disable it. Syntax [no] switchport gvrp default setting disabled command mode interface configuration (ethernet, port channel) example show gvrp configuration this command sho...
Page 543: Garp Timer
C ommand l ine i nterface 4-251 default setting shows both global and interface-specific configuration. Command mode normal exec, privileged exec example garp timer this command sets the values for the join, leave and leaveall timers. Use the no form to restore the timers' default values. Syntax gar...
Page 544: Show Garp Timer
Gvrp and b ridge e xtension c ommands 4-252 unless you are experiencing difficulties with gmrp or gvrp registration/deregistration. • timer values are applied to gvrp for all the ports on all vlans. • timer values must meet the following restrictions: - leave >= (2 x join) - leaveall > leave note: s...
Page 545: Priority Commands
C ommand l ine i nterface 4-253 example related commands garp timer (4-251) priority commands the commands described in this section allow you to specify which data packets have greater precedence when traffic is buffered in the switch due to congestion. This switch supports cos with four priority q...
Page 547: Queue Bandwidth
C ommand l ine i nterface 4-255 command mode global configuration command usage you can set the switch to service the queues based on a strict rule that requires all traffic in a higher priority queue to be processed before lower priority queues are serviced, or use weighted round-robin (wrr) queuin...
Page 548
P riority c ommands 4-256 command usage wrr controls bandwidth sharing at the egress port by defining scheduling weights. Example the following example shows how to assign wrr weights of 1, 3, 5 and 7 to the cos priority queues 0, 1, 2 and 3: related commands show queue bandwidth (4-259) switchport ...
Page 549: Queue Cos-Map
C ommand l ine i nterface 4-257 the incoming frame is an ieee 802.1q vlan tagged frame, the ieee 802.1p user priority bits will be used. • this switch provides four priority queues for each port. It is configured to use weighted round robin, which can be viewed with the show queue bandwidth command....
Page 550
P riority c ommands 4-258 default setting this switch supports class of service by using eight priority queues, with weighted round robin queuing for each port. Eight separate traffic classes are defined in ieee 802.1p. The default priority levels are assigned according to recommendations in the iee...
Page 551: Show Queue Mode
C ommand l ine i nterface 4-259 show queue mode this command shows the current queue mode. Default setting none command mode privileged exec example show queue bandwidth this command displays the weighted round-robin (wrr) bandwidth allocation for the priority queues. Default setting none command mo...
Page 552: Show Queue Cos-Map
P riority c ommands 4-260 show queue cos-map this command shows the class of service priority map. Syntax show queue cos-map [interface] interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port number. (range: 1-26) • port-channel channel-id (range: 1-6) default setting none co...
Page 553
C ommand l ine i nterface 4-261 map ip port (global configuration) this command enables ip port mapping (i.E., class of service mapping for tcp/udp sockets). Use the no form to disable ip port mapping. Syntax [no] map ip port default setting disabled command mode global configuration command usage t...
Page 554
P riority c ommands 4-262 map ip port (interface configuration) this command sets ip port priority (i.E., tcp/udp port priority). Use the no form to remove a specific setting. Syntax map ip port port-number cos cos-value no map ip port port-number • port-number - 16-bit tcp/udp port number. (range: ...
Page 555
C ommand l ine i nterface 4-263 command mode global configuration command usage • the precedence for priority mapping is ip port, ip precedence or ip dscp, and default switchport priority. • ip precedence and ip dscp cannot both be enabled. Enabling one of these priority types will automatically dis...
Page 556
P riority c ommands 4-264 command usage • the precedence for priority mapping is ip port, ip precedence or ip dscp, and default switchport priority. • ip precedence values are mapped to default class of service values on a one-to-one basis according to recommendations in the ieee 802.1p standard, an...
Page 557
C ommand l ine i nterface 4-265 example the following example shows how to enable ip dscp mapping globally: map ip dscp (interface configuration) this command sets ip dscp priority (i.E., differentiated services code point priority). Use the no form to restore the default table. Syntax map ip dscp d...
Page 558: Show Map Ip Port
P riority c ommands 4-266 • dscp priority values are mapped to default class of service values according to recommendations in the ieee 802.1p standard, and then subsequently mapped to the four hardware priority queues. • this command sets the ip dscp priority for all interfaces. Example the followi...
Page 559: Show Map Ip Precedence
C ommand l ine i nterface 4-267 related commands map ip port (global configuration) (4-261) map ip port (interface configuration) (4-262) show map ip precedence this command shows the ip precedence priority map. Syntax show map ip precedence [interface] interface • ethernet unit/port - unit - stack ...
Page 560: Show Map Ip Dscp
P riority c ommands 4-268 show map ip dscp this command shows the ip dscp priority map. Syntax show map ip dscp [interface] interface • ethernet unit/port - unit - stack unit. (range: 1-8) - port - port number. (range: 1-26) • port-channel channel-id (range: 1-6) default setting none command mode pr...
Page 561: Igmp Snooping Commands
C ommand l ine i nterface 4-269 multicast filtering commands this switch uses igmp (internet group management protocol) to query for any attached hosts that want to receive a specific multicast service. It identifies the ports containing hosts requesting a service and sends data out to those ports o...
Page 562: Ip Igmp Snooping
M ulticast f iltering c ommands 4-270 ip igmp snooping this command enables igmp snooping on this switch. Use the no form to disable it. Syntax [no] ip igmp snooping default setting enabled command mode global configuration example the following example enables igmp snooping. Ip igmp snooping vlan s...
Page 564: Show Ip Igmp Snooping
M ulticast f iltering c ommands 4-272 show ip igmp snooping this command shows the igmp snooping configuration. Default setting none command mode privileged exec command usage see “configuring igmp snooping and query parameters” on page 3-222 for a description of the displayed items. Example the fol...
Page 565: Ip Igmp Snooping Querier
C ommand l ine i nterface 4-273 command mode privileged exec command usage member types displayed include igmp or user, depending on selected options. Example the following shows the multicast entries learned through igmp snooping for vlan 1: igmp query commands (layer 2) ip igmp snooping querier th...
Page 566
M ulticast f iltering c ommands 4-274 default setting enabled command mode global configuration command usage if enabled, the switch will serve as querier if elected. The querier is responsible for asking hosts if they want to receive multicast traffic. Example ip igmp snooping query-count this comm...
Page 567
C ommand l ine i nterface 4-275 query-max- response-time. If the countdown finishes, and the client still has not responded, then that client is considered to have left the multicast group. Example the following shows how to configure the query count to 10: related commands ip igmp snooping query-ma...
Page 568
M ulticast f iltering c ommands 4-276 ip igmp snooping query-max-response-time this command configures the snooping report delay. Use the no form of this command to restore the default. Syntax ip igmp snooping query-max-response-time seconds no ip igmp snooping query-max-response-time seconds - the ...
Page 569
C ommand l ine i nterface 4-277 ip igmp snooping router-port-expire-time this command configures the query timeout. Use the no form to restore the default. Syntax ip igmp snooping router-port-expire-time seconds no ip igmp snooping router-port-expire-time seconds - the time the switch waits after th...
Page 570
M ulticast f iltering c ommands 4-278 static multicast routing commands ip igmp snooping vlan mrouter this command statically configures a multicast router port. Use the no form to remove the configuration. Syntax [no] ip igmp snooping vlan vlan-id mrouter interface • vlan-id - vlan id (range: 1-409...
Page 571
C ommand l ine i nterface 4-279 example the following shows how to configure port 11 as a multicast router port within vlan 1: show ip igmp snooping mrouter this command displays information on statically configured and dynamically learned multicast router ports. Syntax show ip igmp snooping mrouter...
Page 572: Ip Interface Commands
Ip i nterface c ommands 4-280 ip interface commands an ip addresses may be used for management access to the switch over your network. The ip address for this switch is obtained via dhcp by default. You can manually configure a specific ip address, or direct the device to obtain an address from a bo...
Page 573
C ommand l ine i nterface 4-281 default setting dhcp command mode interface configuration (vlan) command usage • you must assign an ip address to this device to gain management access over the network. You can manually configure a specific ip address, or direct the device to obtain an address from a...
Page 574: Ip Default-Gateway
Ip i nterface c ommands 4-282 ip default-gateway this command establishes a static route between this switch and devices that exist on another network segment. Use the no form to remove the static route. Syntax ip default-gateway gateway no ip default-gateway gateway - ip address of the default gate...
Page 575: Show Ip Interface
C ommand l ine i nterface 4-283 command usage • this command issues a bootp or dhcp client request for any ip interface that has been set to bootp or dhcp mode via the ip address command. • dhcp requires the server to reassign the client’s last address if available. • if the bootp or dhcp server has...
Page 576: Show Ip Redirects
Ip i nterface c ommands 4-284 show ip redirects this command shows the default gateway configured for this device. Default setting none command mode privileged exec example related commands ip default-gateway (4-282) ping this command sends icmp echo request packets to another node on the network. S...
Page 577
C ommand l ine i nterface 4-285 • following are some results of the ping command: - normal response -the normal response occurs in one to ten seconds, depending on network traffic. - destination does not respond - if the host does not respond, a “timeout” appears in ten seconds. - destination unreac...
Page 578: Dns Commands
Dns c ommands 4-286 dns commands these commands are used to configure domain naming system (dns) services. You can manually configure entries in the dns domain name to ip address mapping table, configure default domain names, or specify one or more name servers to use for domain name to address tran...
Page 579: Ip Host
C ommand l ine i nterface 4-287 ip host this command creates a static entry in the dns table that maps a host name to an ip address. Use the no form to remove an entry. Syntax [no] ip host name address1 [address2 … address8] • name - name of the host. (range: 1-255 characters) • address1 - correspon...
Page 581: Ip Domain-List
C ommand l ine i nterface 4-289 example related commands ip domain-list (4-289) ip name-server (4-290) ip domain-lookup (4-291) ip domain-list this command defines a list of domain names that can be appended to incomplete host names (i.E., host names passed from a client that are not formatted with ...
Page 582: Ip Name-Server
Dns c ommands 4-290 • if there is no domain list, the domain name specified with the ip domain-name command is used. If there is a domain list, the default domain name is not used. Example this example adds two domain names to the current list and then displays the list. Related commands ip domain-n...
Page 583: Ip Domain-Lookup
C ommand l ine i nterface 4-291 command usage the listed name servers are queried in the specified sequence until a response is received, or the end of the list is reached with no response. Example this example adds two domain-name servers to the list and then displays the list. Related commands ip ...
Page 584: Show Hosts
Dns c ommands 4-292 example this example enables dns and then displays the configuration. Related commands ip domain-name (4-288) ip name-server (4-290) show hosts this command displays the static host name-to-address mapping table. Command mode privileged exec example note that a host name will be ...
Page 585: Show Dns
C ommand l ine i nterface 4-293 show dns this command displays the configuration of the dns server. Command mode privileged exec example show dns cache this command displays entries in the dns cache. Command mode privileged exec example console#show dns domain lookup status: dns enabled default doma...
Page 586: Clear Dns Cache
Dns c ommands 4-294 clear dns cache this command clears all entries in the dns cache. Command mode privileged exec example table 4-75 show dns output description field description no the entry number for each resource record. Flag the flag is always “4” indicating a cache entry and therefore unrelia...
Page 587: Software Features
A-1 a ppendix a s oftware s pecifications software features authentication local, radius, tacacs, port (802.1x), https (http/ssl), ssh, port security access control lists ip, mac (up to 32 lists) poe power over ethernet 29 dhcp client port configuration 100base-tx: 10/100 mbps, half/full duplex 1000...
Page 588: Management Features
S oftware s pecifications a-2 port trunking static trunks (cisco etherchannel compliant) dynamic trunks (link aggregation control protocol) spanning tree protocol spanning tree protocol (stp, ieee 802.1d) rapid spanning tree protocol (rstp, ieee 802.1w) multiple spanning tree protocol (mstp, ieee 80...
Page 589: Standards
S oftware s pecifications a-3 snmpv3 management access via mib database trap management to specified hosts rmon groups 1, 2, 3, 9 (statistics, history, alarm, event) standards ieee 802.1d spanning tree protocol and traffic priorities ieee 802.1p priority tags ieee 802.1q vlan ieee 802.1w rapid spann...
Page 590
S oftware s pecifications a-4 management information bases bridge mib (rfc 1493) entity mib (rfc 2737) ether-like mib (rfc 2665) extended bridge mib (rfc 2674) extensible snmp agents mib (rfc 2742) forwarding table mib (rfc 2096) igmp mib (rfc 2933) interface group mib (rfc 2233) interfaces evolutio...
Page 591
B-1 a ppendix b t roubleshooting problems accessing the management interface table b-1 troubleshooting chart symptom action cannot connect using telnet, web browser, or snmp software • be sure the switch is powered up. • check network cabling between the management station and the switch. • check th...
Page 592
T roubleshooting b-2 cannot connect using secure shell • if you cannot connect using ssh, you may have exceeded the maximum number of concurrent telnet/ssh sessions permitted. Try connecting again at a later time. • be sure the control parameters for the ssh server are properly configured on the swi...
Page 593: Using System Logs
U sing s ystem l ogs b-3 using system logs if a fault does occur, refer to the installation guide to ensure that the problem you encountered is actually caused by the switch. If the problem appears to be caused by the switch, follow these steps: 1. Enable logging. 2. Set the error messages reported ...
Page 594
T roubleshooting b-4.
Page 595
Glossary-1 g lossary access control list (acl) acls can limit network traffic and restrict access to certain users or devices by checking each packet for certain ip or mac (i.E., layer 2) information. Address resolution protocol (arp) arp converts between ip addresses and mac (i.E., hardware) addres...
Page 596
G lossary glossary-2 dynamic host control protocol (dhcp) provides a framework for passing configuration information to hosts on a tcp/ip network. Dhcp is based on the bootstrap protocol (bootp), adding the capability of automatic allocation of reusable network addresses and additional configuration...
Page 597
G lossary glossary-3 ieee 802.1q vlan tagging—defines ethernet frame tags which carry vlan information. It allows switches to assign endstations to different virtual lans, and defines a standard way for vlans to communicate across switched networks. Ieee 802.1p an ieee standard for providing quality...
Page 598
G lossary glossary-4 igmp query on each subnetwork, one igmp-capable device will act as the querier — that is, the device that asks all hosts to report on the ip multicast groups they wish to join or to which they already belong. The elected querier will be the device with the lowest ip address in t...
Page 599
G lossary glossary-5 link aggregation see port trunk. Link aggregation control protocol (lacp) allows ports to automatically negotiate a trunked link with lacp-configured ports on another device. Management information base (mib) an acronym for management information base. It is a set of database ob...
Page 600
G lossary glossary-6 port trunk defines a network link aggregation and trunking method which specifies how to create a single high-speed logical link that combines several lower-speed physical links. Private vlans private vlans provide port-based security and isolation between ports within the assig...
Page 601
G lossary glossary-7 simple network time protocol (sntp) sntp allows a device to set its internal clock based on periodic updates from a network time protocol (ntp) server. Updates can be requested from a specific ntp server, or can be received via broadcasts sent by ntp servers. Spanning tree algor...
Page 602
G lossary glossary-8 virtual lan (vlan) a virtual lan is a collection of network nodes that share the same collision domain regardless of their physical location or connection point in the network. A vlan serves as a logical workgroup with no physical barriers, and allows users to share information ...
Page 603: Numerics
Index-1 numerics 802.1x configure 3-88 , 4-110 port authentication 3-88 , 4-110 a access control lists see acl acl configuration guidelines 3-98 , 4-119 extended ip 3-99 , 4-120 , 4-122 , 4-125 mac 3-99 , 4-120 , 4-138 – 4-142 standard ip 3-99 , 4-120 , 4-122 , 4-124 address table 3-151 , 4-200 agin...
Page 604
I ndex index-2 h hardware version, displaying 3-15 , 4-80 https, secure server 3-75 , 4-41 i ieee 802.1d 3-155 , 4-207 ieee 802.1s 3-155 , 4-207 ieee 802.1w 3-155 , 4-207 ieee 802.1x 3-88 , 4-110 igmp configuring 3-220 , 4-269 description of protocol 3-220 layer 2 3-220 , 3-221 , 4-269 query 3-221 ,...
Page 605
I ndex index-3 power budgets port 3-147 , 4-93 port priority 3-150 , 4-94 power over ethernet configuring 2-15 priority, default port ingress 3-202 , 4-256 priority, sta 3-167 , 4-221 r radius, logon authentication 3-72 , 4-100 rate limits, setting 3-138 , 4-186 remote logging 3-37 , 4-60 rstp 3-155...
Page 606
I ndex index-4 w web interface access requirements 3-1 configuration buttons 3-4 home page 3-3 menu list 3-6 panel display 3-5.
Page 608
38 tesla irvine, ca 92618 phone: (949) 679-8000 model numbers: smc6824m (f2.4.2.13) smc6824mpe (f 2.4.2.11) smc6826mpe (f2.4.2.11) pub.Number: 150200037700a e062005-r02 for technical support, call: from u.S.A. And canada (24 hours a day, 7 days a week) (800) smc-4-you; (949) 679-8000; fax: (949) 679...