SMC Networks BR21VPN - annexe 1 Manual
Summary of BR21VPN - annexe 1
Page 1
Barricade™ dual wan port load balancing vpn router smcbr21vpn.
Page 2
Copyright information furnished by smc networks, inc. (smc) is believed to be accurate and reliable. However, no responsibility is assumed by smc for its use, nor for any infringements of patents or other rights of third parties which may result from its use. No license is granted by implication or ...
Page 3
2 limited warranty limited warranty statement: smc networks, inc. (“smc”) warrants its products to be free from defects in workmanship and materials, under normal use and service, for the applicable warranty term. All smc products carry a standard 90-day limited warranty from the date of purchase fr...
Page 4
3 marked on the outside of the package will be returned to customer at customer’s expense. For warranty claims within north america, please call our toll-free customer support number at (800) 762-4968. Customers are responsible for all shipping charges from their facility to smc. Smc is responsible ...
Page 5
4 consequential damages for consumer products, so the above limitations and exclusions may not apply to you. This warranty gives you specific legal rights, which may vary from state to state. Nothing in this warranty shall be taken to affect your statutory rights. * smc will provide warranty service...
Page 6
5 compliances fcc - class a this equipment has been tested and found to comply with the limits for a class a digital device, pursuant to part 15 of the fcc rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment gen...
Page 7
6 rfi emission: • limit class a according to en 55022:1998, iec 60601-1-2 (emc,medical) • limit class a for harmonic current emission according toen 61000-3-2/1995 • limitation of voltage fluctuation and flicker in low-voltage supply system according to en 61000-3-3/1995 immunity: • product family s...
Page 8
7 please read the following safety information carefully before installing the device: warning: installation and removal of the unit must be carried out by qualified personnel only. • this guide is intended for use by network administrators who are responsible for setting up and installing network e...
Page 9
8 veuillez lire à fond l’information de la sécurité suivante avant d’installer le device: avertissement: l.Installation et la dépose de ce groupe doivent être confiés à un personnel qualifié. • ne branchez pas votre appareil sur une prise secteur (alimentation électrique) lorsqu’il n’y a pas de conn...
Page 10
9 • das gerät muß an eine geerdete steckdose angeschlossen werden, welche die internationalen sicherheitsnormen erfüllt. • der gerätestecker (der anschluß an das gerät, nicht der wandsteckdosenstecker) muß einen gemäß en 60320/iec 320 konfigurierten geräteeingang haben. • die netzsteckdose muß in de...
Page 11
10 warnings and cautionary messages warning: this product does not contain any serviceable user parts. Warning: installation and removal of the unit must be carried out by qualified personnel only. Warning: when connecting this device to a power outlet, connect the field ground lead on the tri-pole ...
Page 12
11 environmental statement the manufacturer of this product endeavours to sustain an environmentally-friendly policy throughout the entire production process. This is achieved though the following means: • adherence to national legislation and regulations on environmental production standards. • con...
Page 13
12 audience the guide is intended for use by network administrators who are responsible for installing and setting up network equipment; consequently, it assumes a basic working knowledge of lans (local area networks). Diese anleitung ist für die benutzung durch netzwerkadministratoren vorgesehen, d...
Page 14: Contents
13 contents chapter 1 administrator...........................................................................................................16 a dmin .......................................................................................................................................................
Page 15
14 chapter 8 authentication ........................................................................................................94 e xample ..............................................................................................................................................100 chapter 9 ...
Page 16
15 chapter 17 statistics ...............................................................................................................238 wan s tatistics ..................................................................................................................................240 p olicy s ...
Page 17: Chapter 1 Administrator
16 chapter 1 administrator administration “system” is the managing of settings such as the privileges of packets that pass through the smc br21vpn and monitoring controls. The system administrators can manage, monitor, and configure smc br21vpn settings. But all configurations are “read-only” for al...
Page 18
17 define the required fields of administrator administrator name: the username of administrators and sub administrator for the smc br21vpn. The admin user name cannot be removed; and the sub-admin user can be removed or configure. The default account: admin; password: smcadmin privilege: the pr...
Page 19
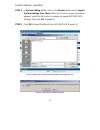
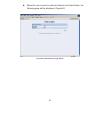
18 admin adding a new sub administrator step 1﹒in the admin webui, click the new sub admin button to create a new sub administrator. Step 2﹒in the add new sub administrator webui (figure 1-1) and enter the following setting: sub admin name: sub_admin password: 12345 confirm password: 12345 ste...
Page 20
19 modify the administrator’s password step 1﹒in the admin webui, locate the administrator name you want to edit, and click on modify in the configure field. Step 2﹒the modify administrator password webui will appear. Enter the following information: password: admin new password: 52364 confirm...
Page 21
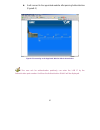
20 add remote management ips step 1﹒add the following setting in permitted ips of administration: (figure1-3) name: enter master ip address: enter 163.173.56.11 netmask: enter 255.255.255.255 service: select ping and http click ok complete add new permitted ips (figure1-4) figure1-3 sett...
Page 22
21 logout step 1﹒click logout in system to protect the system while administrator are away. (figure1-5) figure1-5 confirm logout webui step 2﹒click ok and the logout message will appear in webui. (figure1-6) figure1-6 logout webui message.
Page 23
22 software update step 1﹒select software update in system, and follow the steps below: to obtain the version number from version number and obtain the latest version from internet. And save the latest version in the hardware of the pc, which manage the smc br21vpn click browse and choose the late...
Page 24: Chapter 2 Configure
23 chapter 2 configure configure the configure is according to the basic setting of the smc br21vpn. In this chapter the definition is setting, date/time, multiple subnet, route table, dhcp, dynamic dns, hosts table, and language settings..
Page 25
24 define the required fields of settings smc br21vpn configuration: the administrator can import or export the system settings. Click ok to import the file into the smc br21vpn or click cancel to cancel importing. You also can revive to default value here. Email settings: select enable e-mail a...
Page 26
25 administration packet logging: after enable this function; the smc br21vpn will record packet which source ip or destination address is smc br21vpn. And record in traffic log for system manager to inquire about. Define the required fields of time settings synchronize time/date: synchronizing ...
Page 27
26 nat mode: it allows internal network to set multiple subnet address and connect with the internet through different wan ip addresses. For example:the lease line of a company applies several real ip addresses 168.85.88.0/24, and the company is divided into r&d department, service, sales departme...
Page 28
27 define the required fields of dhcp subnet: the domain name of lan netmask: the lan netmask gateway: the default gateway ip address of lan broadcast ip: the broadcast ip of lan define the required fields of ddns domain name: the domain name that provided by ddns wan ip address: the wan...
Page 29
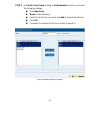
28 setting system settings- exporting step 1﹒in system setting webui, click on button next to export system settings to client. Step 2﹒when the file download pop-up window appears, choose the destination place where to save the exported file and click on save. The setting value of smc br21vpn will c...
Page 30
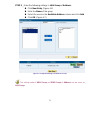
29 system settings- importing step 1﹒in system setting webui, click on the browse button next to import system settings from client. When the choose file pop-up window appears, select the file to which contains the saved smc br21vpn settings, then click ok. (figure2-2) step 2﹒click ok to import the ...
Page 31
30 restoring factory default settings step 1﹒select reset factory settings in smc br21vpn configuration webui step 2﹒click ok at the bottom-right of the page to restore the factory settings. (figure2-4).
Page 32
31 figure2-4 reset factory settings.
Page 33
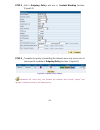
32 enabling e-mail alert notification step 1﹒select enable e-mail alert notification under e-mail settings. Step 2﹒device name: enter the device name or use the default value. Step 3﹒sender address: enter the sender address. (required by some isps.) step 4﹒smtp server ip: enter smtp server’s ip addr...
Page 34
33 reboot smc br21vpn step 1﹒reboot smc br21vpn:click reboot button next to reboot smc br21vpn appliance. Step 2﹒a confirmation pop-up page will appear. Step 3﹒follow the confirmation pop-up page; click ok to restart smc br21vpn. (figure2-6) figure2-6 reboot smc br21vpn.
Page 35
34 date / time date/time settings step 1﹒select enable synchronize with an internet time server (figure2-7) step 2﹒click the down arrow to select the offset time from gmt. Step 3﹒enter the server ip / name with which you want to synchronize. Step 4﹒set the interval time to synchronize with outside s...
Page 36
35 multiple subnet connect to the internet through multiple subnet nat or routing mode by the ip address that set by the lan user’s network card preparation smc br21vpn wan1 (10.10.10.1) connect to the isp router (10.10.10.2) and the subnet that provided by isp is 162.172.50.0/24 to connect to inter...
Page 37
36 adding multiple subnet add the following settings in multiple subnet of system function: click on new entry alias ip of lan interface: enter 162.172.50.1 netmask:enter 255.255.255.0 wan1: enter interface ip 10.10.10.1, and choose routing in forwarding mode wan2:enter interface ip 211.22...
Page 38
37 wan1 and wan2 interface can use assist to enter the data. After setting, there will be two subnet in lan: 192.168.1.0/24 (default lan subnet) and 162.172.50.0/24. So if lan ip is: ˙192.168.1.Xx, it must use nat mode to access to the internet. (in policy it only can setup to access to internet by ...
Page 39
38 route table to connect two different subnet router with the smc br21vpn and makes them to connect to internet through smc br21vpn preparation company a: wan1 (61.11.11.11) connects with atur to internet wan2 (211.22.22.22) connects with atur to internet lan subnet: 192.168.1.1/24 the router1 whic...
Page 40
39 route table step 1﹒enter the following settings in route table in system function: 【destination ip】: enter 192.168.10.1 【netmask】: enter 255.255.255.0。 【gateway】: enter 192.168.1.252 【interface】: select lan click ok (figure 2-10) figure2-10 add new static route1 step 2﹒enter the followi...
Page 41
40 step 3﹒enter the following setting in route table in system function: 【destination ip】: enter 10.10.10.0 【netmask】: enter 255.255.255.0 【gateway】: enter 192.168.1.252 【interface】: select lan click ok (figure 2-12) figure2-12 add new static route3.
Page 42
41 step 4﹒adding successful. At this time the computer of 192.168.10.1/24, 192.168.20.1/24 and 192.168.1.1/24 can connect with each other and connect to internet by nat (figure 2-13) figure 2-13 route table setting.
Page 43
42 dhcp step 1﹒select dhcp in system and enter the following settings: domain name:enter the domain name dns server 1: enter the distributed ip address of dns server1. dns server 2: enter the distributed ip address of dns server2. wins server 1: enter the distributed ip address of wins serve...
Page 44
43 figure 2-14 dhcp webui when selecting automatically get dns, the dns server will lock it as lan interface ip. (using occasion: when the system administrator starts authentication, the users’ first dns server must be the same as lan interface ip in order to enter authentication webui).
Page 45
44 ddns dynamic dns settings step 1﹒select dynamic dns in system function (figure2-15). Click new entry button service providers:select service providers. automatically fill in the wan 1/2 ip:check to automatically fill in the wan 1/2 ip.。 user name:enter the registered user name. password:e...
Page 46
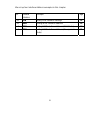
45 chart meaning update successfully incorrect username or password connecting to server unknown error if system administrator had not registered a ddns account, click on sign up then can enter the website of the provider. If you do not select automatically fill in the wan ip and then you can enter ...
Page 47
46 host table step 1﹒select host table in settings function and click on new entry domain name: the domain name of the server virtual ip address: the virtual ip address respective to host table click ok to add host table. (figure2-17) figure2-17 add new host table to use host table, the user p...
Page 48
47 language select the language version (english version/ traditional chinese version or simplified chinese version) and click ok. (figure2-18) figure2-18 language setting webui.
Page 49: Chapter 3 Interface
48 chapter 3 interface interface in this section, the administrator can set up the ip addresses for the office network. The administrator may configure the ip addresses of the lan network, the wan 1/2 network, and the dmz network. The netmask and gateway ip addresses are also configured in this sect...
Page 50
49 define the required fields of interface lan: using the lan interface, the administrator can set up the lan network of smc br21vpn. Ping: select this function to allow the lan users to ping the interface ip address. Http: select to enable the user to enter the webui of smc br21vpn from inter...
Page 51
50 connect mode: display the current connection mode: pppoe (adsl user) dynamic ip address (cable modem user) static ip address saturated connections: set the number for saturation whenever session numbers reach it, the smc br21vpn switches to the next agent on the list. Priority: set pr...
Page 52
51 dmz: the administrator uses the dmz interface to set up the dmz network. the dmz includes: nat mode:in this mode, the dmz is an independent virtual subnet. This virtual subnet can be set by the administrator but cannot be the same as lan interface. transparent mode: in this mode, the dmz ...
Page 53
52 we set up four interface address examples in this chapter: no. Suitable situation example page ex1 lan modify lan interface settings 41 ex2 wan setting wan interface address 42 ex3 dmz setting dmz interface address (nat mode) 50 ex4 dmz setting dmz interface address (transparent mode) 51.
Page 54
53 lan modify lan interface settings step 1﹒select lan in interface and enter the following setting: enter the new ip address and netmask select ping and http click ok (figure3-1) figure3-1 setting lan interface webui the default lan ip address is 192.168.1.1. After the administrator setting t...
Page 55
54 wan setting wan interface address step 1﹒select wan in interface and click modify in wan1 interface. The setting of wan2 interface is almost the same as wan1. The difference is that wan2 has a selection of disable. The system administrator can close wan2 interface by this selection. (figure3-2) f...
Page 56
55 step 2﹒setting the connection service (icmp or dns way): icmp:enter an alive indicator site ip (can select from assist) (figure3-3) dns:enter dns server ip address and domain name (can select from assist) (figure3-4) setting time of seconds between sending alive packet. Figure3-3 icmp conne...
Page 57
56 step 3﹒select the connecting way: pppoe (adsl user) (figure3-5): 1. Select pppoe 2. Enter user name as an account 3. Enter password as the password 4. Select dynamic or fixed in ip address provided by isp. If you select fixed, please enter ip address, netmask, and default gateway. 5. Enter max....
Page 58
57 figure3-5 pppoe connection figure3-6 complete pppoe connection setting if the connection is pppoe, you can choose service-on-demand for wan interface to connect automatically when disconnect; or to set up auto disconnect if idle (not recommend).
Page 59
58 dynamic ip address (cable modem user) (figure3-7): 1. Select dynamic ip address (cable modem user) 2. Click renew in the right side of ip address and then can obtain ip automatically. 3. If the mac address is required for isp then click on clone mac address to obtain mac ip automatically. 4. Ho...
Page 60
59 figure3-7 dynamic ip address connection figure3-8 complete dynamic ip connection setting.
Page 61
60 static ip address (figure3-9) 1. Select static ip address 2. Enter ip address, netmask, and default gateway that provided by isp 3. Enter dns server1 and dns server2 in wan2, the connecting of static ip address does not need to set dns server 4. Enter max. Downstream bandwidth and max. Upstream...
Page 62
61 figure3-10 complete static ip address connection setting when selecting ping and webui on wan network interface, users will be able to ping the smc br21vpn and enter the webui wan network. It may influence network security. The suggestion is to cancel ping and webui after all the settings have fi...
Page 63
62 dmz setting dmz interface address (nat mode) step 1﹒click dmz interface step 2﹒select nat mode in dmz interface select nat in dmz interface enter ip address and netmask step 3﹒select ping and http step 4﹒click ok (figure3-11) figure3-11 setting dmz interface address (nat mode) webui.
Page 64
63 setting dmz interface address (transparent mode) step 1﹒select dmz interface step 2﹒select transparent mode indmz interface select dmz_transparent in dmz interface step 1﹒select ping and http step 2﹒click ok (figure3-12) figure 3-12 setting dmz interface address (transparent mode) webui in wan,...
Page 65: Chapter 4 Address
64 chapter 4 address address the smc br21vpn allows the administrator to set interface addresses of the lan network, lan network group, wan network, wan network group, dmz and dmz group. An ip address in the address table can be an address of a computer or a sub network. The administrator can assign...
Page 66
65 define the required fields of address name: the system administrator set up a name as ip address that is easily recognized. Ip address: it can be a pc’s ip address or several ip address of subnet. Different network area can be: internal ip address, external ip address, and dmz ip address. Net...
Page 67
66 we set up two address examples in this chapter: no suitable situation example page ex1 lan under dhcp circumstances, assign the specific ip to static users and restrict them to access ftp net service only through policy. 55 ex2 lan group wan set up a policy that only allows partial users to conne...
Page 68
67 example under dhcp situation, assign the specific ip to static users and restrict them to access ftp net service only through policy step 1﹒select lan in address and enter the following settings: click new entry button (figure4-1) name: enter rayearth ip address: enter 192.168.3.2 netmask...
Page 69
68 step 2﹒adding the following setting in outgoing policy: (figure4-3) figure 4-3 add a policy of restricting the specific ip to access to internet step 3﹒complete assigning the specific ip to static users in outgoing policy and restrict them to access ftp net service only through policy: (figure4-4...
Page 70
69 when the system administrator setting the address book, he/she can choose the way of clicking on to make the smc br21vpn to fill out the user’s mac address automatically. In lan of address function, the smc br21vpn will default an inside any address represents the whole lan network automatically....
Page 71
70 setup a policy that only allows partial users to connect with specific ip (external specific ip) step 1﹒setting several lan network address. (figure4-5) figure4-5 setting several lan network address.
Page 72
71 step 2﹒enter the following settings in lan group of address: click new entry (figure 4-6) enter the name of the group select the users in the available address column and click add click ok (figure 4-7) figure4-6 add new lan address group figure4-7 complete adding lan address group the se...
Page 73
72 step 3﹒enter the following settings in wan of address function: click new entry (figure4-8) enter the following data (name, ip address, netmask) click ok (figure4-9) figure4-8 add new wan address figure4-9 complete the setting of wan address.
Page 74
73 step 4﹒to exercise step1~3 in policy (figre4-10, 4-11) figure4-10 to exercise address setting in policy figure4-11 complete the policy setting the address function really take effect only if use with policy..
Page 75: Chapter 5 Service
74 chapter 5 service service tcp and udp protocols support varieties of services, and each service consists of a tcp port or udp port number, such as telnet (23), smtp (21), smtp (25), pop3 (110), etc. The smc br21vpn includes two services: pre-defined service and custom service. The common-use serv...
Page 76
75 it takes only one control policy to achieve the same effect as the 50 control policies..
Page 77
76 define the required fields of service pre-defined webui’s chart and illustration: chart illustration any service tcp service, for example:ftp, finger, http, https , imap, smtp, pop3, any, aol, bgp, gopher, inter locator, irc, l2tp, ldap, netmeeting, nntp, pptp, real media, rlogin, ssh, tcp any, t...
Page 78
77 we set up two service examples in this chapter: no suitable situation example page ex1 custom allow external user to communicate with internal user by voip through policy. (voip port: tcp 1720, tcp 15325-15333, udp 15325-15333) 65 ex2 group setting service group and restrict the specific users on...
Page 79
78 custom allow external user to communicate with internal user by voip through policy. (voip port: tcp 1720, tcp 15328-15333, udp 15328-15333) step 1﹒set lan and lan group in address function as follows: (figure5-1, 5-2) figure5-1 setting lan address book webui figure5-2 setting lan group address b...
Page 80
79 step 2﹒enter the following setting in custom of service function: click new entry (figure5-3) service name: enter the preset name voip protocol#1 select tcp, need not to change the client port, and set the server port as: 1720:1720 protocol#2 select tcp, need not to change the client port...
Page 81
80 under general circumstances, the range of port number of client is 1024-65535. Change the client range in custom of is not suggested. If the port numbers that enter in the two spaces are different port number, then enable the port number under the range between the two different port numbers (for...
Page 82
81 step 3﹒compare service to virtual server. (figure5-5) figure5-5 compare service to virtual server step 4﹒compare virtual server to incoming policy. (figure5-6) figure5-6 complete the policy for external voip to connect with internal voip step 5﹒in outgoing policy, complete the setting of internal...
Page 83
82 group setting service group and restrict the specific users only can access to service resource that provided by this group through policy (group: http, pop3, smtp, dns) step 1﹒enter the following setting in group of service: click new entry (figure 5-8) name: enter main_service select http...
Page 84
83 figure5-9 complete the setting of adding service group if you want to remove the service you choose from selected service, choose the service you want to delete and click remove..
Page 85
84 step 2﹒in lan group of address function, setting an address group that can include the service of access to internet. (figure5-10) figure5-10 setting address book group step 3﹒compare service group to outgoing policy. (figure5-11) figure5-11 setting policy.
Page 86: Chapter 6 Schedule
85 chapter 6 schedule schedule in this chapter, the smc br21vpn provides the administrator to configure a schedule for policy to take effect and allow the policies to be used at those designated times. And then the administrator can set the start time and stop time or vpn connection in policy or vpn...
Page 87
86 example to configure the valid time periods for lan users to access to internet in a day step 1﹒enter the following in schedule: click new entry (figure6-1) enter schedule name set up the working time of schedule for each day click ok (figure6-2) figure6-1 setting schedule webui figure6-2...
Page 88
87 step 2﹒compare schedule with outgoing policy (figure6-3) figure6-3 complete the setting of comparing schedule with policy the schedule must compare with policy ..
Page 89: Chapter 7 Qos
88 chapter 7 qos qos by configuring the qos, you can control the outbound and inbound upstream/downstream bandwidth. The administrator can configure the bandwidth according to the wan bandwidth. Downstream bandwidth : to configure the guaranteed bandwidth and maximum bandwidth. Upstream bandwidth:to...
Page 90
89 figure7-2 the flow after using qos (max. Bandwidth: 400kbps, guaranteed bandwidth: 200kbps).
Page 91
90 define the required fields of qos wan: display wan1 and wan2 downstream bandwidth: to configure the guaranteed bandwidth and maximum bandwidth according to the bandwidth range you apply from isp upstream bandwidth: to configure the guaranteed bandwidth and maximum bandwidth according to the b...
Page 92
91 we set up two qos examples in this chapter: no suitable situation example page ex1 qos setting a policy that can restrict the user’s downstream and upstream bandwidth. 79.
Page 93
92 example setting a policy that can restrict the user’s downstream and upstream bandwidth step 1﹒enter the following settings in qos: click new entry (figure7-3) name: the name of the qos you want to configure. enter the bandwidth in wan1, wan2 select qos priority click ok (figure7-4) fig...
Page 94
93 step 2﹒use the qos that set by step1 in outgoing policy. (figure7-5, 7-6) figure7-5 setting the qos in policy figure7-6 complete policy setting when the administrator are setting qos, the bandwidth range that can be set is the value that system administrator set in the wan of interface. So when t...
Page 95: Chapter 8 Authentication
94 chapter 8 authentication authentication by configuring the authentication, you can control the user’s connection authority. The user has to pass the authentication to access to internet. The smc br21vpn configures the authentication of lan’s user by setting account and password to identify the pr...
Page 96
95 define the required fields of authentication authentication management provide the administrator the port number and valid time to setup smc br21vpn authentication. (have to setup the authentication first) authentication port: the internal user have to pass the authentication to access to the...
Page 97
96 z when the user connect to external network by authentication, the following page will be displayed: (figure8-2) figure8-2 authentication login webui.
Page 98
97 z it will connect to the appointed website after passing authentication: (figure8-3) figure8-3 connecting to the appointed website after authentication if the user ask for authentication positively, can enter the lan ip by the authentication port number. And then the authentication webui will be ...
Page 99
98 auth-user name: the user account for authentication you want to set. Password: the password when setting up authentication. Confirm password: enter the password that correspond to password.
Page 100
99 we set up four authentication examples in this chapter: no suitable situation example page ex1 auth user auth group setting specific users to connect with external network only before passing the authentication of policy. (adopt the built-in auth user and auth group function) 87.
Page 101
100 example setting specific users to connect with external network only before passing the authentication of policy. (adopt the built-in auth user and auth group function) step 1﹒setup several auth user in authentication. (figire8-4) figure8-4 setting several auth users webui to use authentication,...
Page 102
101 step 2﹒add auth user group setting in authentication function and enter the following settings: click new entry name: enter laboratory select the auth user you want and add to selected auth user click ok complete the setting of auth user group (figure8-5) figure8-5 setting auth group w...
Page 103
102 step 3﹒add a policy in outgoing policy and input the address and authentication of step 2 (figure8-6, 8-7) figure8-6 auth-user policy setting figure8-7 complete the policy setting of auth-user.
Page 104
103 step 4﹒when user is going to access to internet through browser, the authentication ui will appear in browser. After entering the correct user name and password, click ok to access to internet. (figure8-8) step 5﹒if the user does not need to access to internet anymore and is going to logout, he/...
Page 105: Chapter 9 Content Blocking
104 chapter 9 content blocking content filtering content filtering includes「url」,「script」,「p2p」,「im」,「download」. 【url blocking】 :the administrator can set up to “allow” or “restrict” entering the specific website by complete domain name, key words, and met character (~and*). 【script blocking】: the a...
Page 106
105 define the required fields of content blocking url string: the domain name that restricts to enter or only allow entering. Popup blocking: prevent the pop-up webui appearing activex blocking: prevent activex packets java blocking: prevent java packets cookies blocking: prevent cookies ...
Page 107
106 sub-name file blocking: prevent users to deliver specific sub-name file by http all type: prevent users to send the audio, video types, and sub-name file…etc. By http protocol..
Page 108
107 we set up five content blocking examples in this chapter: no suitable situation example page ex1 url blocking restrict the internal users only can access to some specific website 95 ex2 script blocking restrict the internal users to access to script file of website. 98 ex3 p2p blocking restrict ...
Page 109
108 url restrict the internal users only can access to some specific website url blocking: symbol: ~ means open up; * means metacharacter restrict not to enter specific website: enter the 「complete domain name」 or 「key word」of the website you want to restrict in url string. For example: www.Kcg.Gov....
Page 110
109 step 1﹒enter the following in url of content filtering function: click new entry url string: enter ~yahoo, and click ok click new entry url string: enter ~google, and click ok click new entry url string: enter *, and click ok complete setting a url blocking policy (figure9-1) figur...
Page 111
110 step 2﹒add a outgoing policy and use in content blocking function: (figure9-2) figure9-2 url blocking policy setting step 3﹒complete the policy of permitting the internal users only can access to some specific website in outgoing policy function: (figure9-3) figure9-3 complete policy settings af...
Page 112
111 script restrict the internal users to access to script file of website step 1﹒select the following data in script of content blocking function: select popup blocking select activex blocking select java blocking select cookies blocking click ok complete the setting of script blocking ...
Page 113
112 step 2﹒add a new outgoing policy and use in content blocking function: (figure9-5) figure9-5 new policy of script blocking setting step 3﹒complete the policy of restricting the internal users to access to script file of website in outgoing policy: (figure9-6) figure9-6 complete script blocking p...
Page 114
113 download restrict the internal users to access to video, audio, and some specific sub-name file from http or ftp protocol directly step 1﹒enter the following settings in download of content blocking function: select all types blocking click ok complete the setting of download blocking. (fi...
Page 115
114 step 2﹒add a new outgoing policy and use in content blocking function: (figure9-14) figure9-14 add new download blocking policy setting step 3﹒complete the outgoing policy of restricting the internal users to access to video, audio, and some specific sub-name file by http protocol directly: (fig...
Page 116
115 p2p / im limit internal user access internet resources by p2p software. Step1. In im / p2p blocking Æ setting, add the following settings: click new entry. ( fig. 10-5 ) enter the name of p2p_blocking. select edonkey, bit torrent, winmx, foxy, kugoo, applejuice, audiogalaxy, directconnect,...
Page 117
116 step2. In policy Æ outgoing, add one policy applied to p2p blocking setting. ( fig. 10-7 ) fig. 10-7 set the policy applied to p2p blocking step3. In policy Æ outgoing , complete the policy setting of limit internal user to access internet resources by p2p software: ( fig. 10-8 ) fig. 10-8 compl...
Page 118
117 use p2p will seriously occupy network bandwidth and it can change its service port. So the mis engineer not only set the service port in service, but also need to set im / p2p blocking Æ p2p blocking..
Page 119: Chapter 10 Virtual Server
118 chapter 10 virtual server virtual server the real ip address provided from isp is always not enough for all the users when the system manager applies the network connection from isp. Generally speaking, in order to allocate enough ip addresses for all computers, an enterprise assigns each comput...
Page 120
119 in this chapter, we will have detailed introduction and instruction of mapped ip and server 1/2/3/4: mapped ip: because the intranet is transferring the private ip by nat mode (network address translation). And if the server is in lan, its ip address is belonging to private ip address. Then the ...
Page 121
120 define the required fields of virtual server wan ip: wan ip address (real ip address) map to virtual ip: map the wan real ip address into the lan private ip address virtual server real ip: the wan ip address which mapped by the virtual server. Service name (port number): the service name...
Page 122
121 we set up four virtual server examples in this chapter: no. Suitable situation example page ex1 mapped ip make a single server that provides several services such as ftp, web, and mail, to provide service by policy. 110 ex2 virtual server make several servers that provide a single service, to pr...
Page 123
122 example make a single server that provides several services such as ftp, web, and mail, to provide service by policy step 1﹒setting a server that provide several services in lan, and set up the network card’s ip as 192.168.1.100. Dns is external dns server. Step 2﹒enter the following setting in ...
Page 124
123 step 4﹒group the services (dns, ftp, http, pop3, smtp…) that provided and used by server in service function. And add a new service group for server to send mails at the same time. (figure10-3) figure10-3 service setting step 5﹒add a policy that includes settings of step3, 4 in incoming policy. ...
Page 125
124 step 7﹒complete the setting of providing several services by mapped ip. (figure10-6) figure10-6 a single server that provides several services by mapped ip strong suggests not tochoose any when setting mapped ip and choosing service. Otherwise the mapped ip will be exposed to internet easily and...
Page 126
125 make several servers that provide a single service, to provide service through policy by virtual server (take web service for example) step 1﹒setting several servers that provide web service in lan network, which ip address is 192.168.1.101, 192.168.1.102, 192.168.1.103, and 192.168.1.104.
Page 127
126 step 2﹒enter the following data in server 1 of virtual server function: click the button next to virtual server real ip (“click here to configure”) in server 1 virtual server real ip: enter 211.22.22.23 (click assist for assistance) click ok (figure10-7) figure10-7 virtual server real ip setti...
Page 128
127 step 3﹒add a new policy in incoming policy, which includes the virtual server, set by step2. (figure10-9) figure10-9 complete virtual server policy setting in this example, the external users must change its port number to 8080 before entering the website that set by the web server. Step 4﹒compl...
Page 129
128 the external user use voip to connect with voip of lan (voip port: tcp 1720, tcp 15328-15333, udp 15328-15333) step 1﹒set up voip in lan network, and its ip is 192.168.1.100 step 2﹒enter the following setting in lan of address function: (figure10-11) figure10-11 setting lan address webui step 3﹒...
Page 130
129 step 4﹒enter the following setting in server1 of virtual server function: click the button next to virtual server real ip (“click here to configure”) in server1 virtual server real ip: enter 61.11.11.12 (click assist for assistance) (use wan) click ok (figure10-13) figure10-13 virtual server r...
Page 131
130 step 5﹒add a new incoming policy, which includes the virtual server that set by step4: (figure10-15) figure10-15 complete the policy includes virtual server setting step 6﹒enter the following setting of the internal users using voip to connect with external network voip in outgoing policy: (figu...
Page 132
131 step 7﹒complete the setting of the external/internal user using specific service to communicate with each other by virtual server. (figure10-17) figure10-17 complete the setting of the external/internal user using specific service to communicate with each other by virtual server.
Page 133
132 make several servers that provide several same services, to provide service through policy by virtual server. (take http, pop3, smtp, and dns group for example) step 1﹒setting several servers that provide several services in lan network. Its network card’s ip is 192.168.1.101, 192.168.1.102, 192...
Page 134
133 step 3﹒group the service of server in custom of service. Add a service group for server to send e-mail at the same time. (figure10-20) figure10-20 add new service group.
Page 135
134 step 4﹒enter the following data in server1 of virtual server: click the button next to virtual server real ip (“click here to configure”) in server1 virtual server real ip: enter 211.22.22.23 (click assist for assistance) click ok (figure10-21) figure10-21 virtual server real ip setting ...
Page 136
135 step 5﹒add a new incoming policy, which includes the virtual server that set by step 3: (figure10-23) figure10-23 complete incoming policy setting step 6﹒add a new policy that includes the settings of step2, 3 in outgoing policy. It makes server can send e-mail to external mail server by mail se...
Page 137
136 step 7﹒complete the setting of providing several services by virtual server. (figure10-25) figure10-25 complete the setting of providing several services by several virtual server.
Page 138: Chapter 11 Vpn
137 chapter 11 vpn vpn the smc br21vpn adopts vpn to set up safe and private network service. And combine the remote authentication system in order to integrate the remote network and pc of the enterprise. Also provide the enterprise and remote users a safe encryption way to have best efficiency and...
Page 139
138 define the required fields of vpn: rsa: a public-key cryptosystem for encryption and authentication. Preshared key: the ike vpn must be defined with a preshared key. The key may be up to 128 bytes long. Isakmp (internet security association key management protocol): an extensible protocol-...
Page 140
139 des (data encryption standard): the data encryption standard developed by ibm in 1977 is a 64-bit block encryption block cipher using a 56-bit key. Triple-des (3des): the des function performed three times with either two or three cryptographic keys. Aes (advanced encryption standard): an ...
Page 141
140 define the required fields of ipsec function to display the vpn connection status via icon。 chart -- meaning not be applied disconnect connecting name: the vpn name to identify the ipsec autokey definition. The name must be the only one and cannot be repeated. Gateway ip: the wan interface...
Page 142
141 define the required fields of pptp server function pptp server: to select enable or disable client ip range: setting the ip addresses range for pptp client connection i: to display the vpn connection status via icon。 chart -- meaning not be applied disconnect connecting user name: displa...
Page 143
142 define the required fields of pptp client function to display the vpn connection status via icon。 chart -- meaning not be applied disconnect connecting user name: displays the pptp client user’s name when connecting to pptp server. Server ip or domain name: display the pptp server ip addre...
Page 144
143 define the required fields of tunnel function to display the vpn connection status via icon。 chart -- meaning not be applied disconnect connecting name: the vpn name to identify the vpn tunnel definition. The name must be the only one and cannot be repeated. Source subnet: displays the sou...
Page 145
144 we set up two vpn examples in this chapter: no. Suitable situation example page ex1 ipsec autokey setting ipsec vpn connection between two smc br21vpn 133 ex2 pptp setting pptp vpn connection between two smc br21vpn 146.
Page 146
145 example setting ipsec vpn connection between two smc br21vpn preparation company a wan ip: 61.11.11.11 lan ip: 192.168.10.X company b wan ip: 211.22.22.22 lan ip: 192.168.20.X this example takes two smc br21vpn as work platform. Suppose company a 192.168.10.100 create a vpn connection with compa...
Page 147
146 step 4﹒select preshare in authentication method and enter the preshared key (max: 100 bits) step 5﹒select isakmp algorithm in encapsulation list. Choose the algorithm when setup connection. Please select enc algorithm (3des/des/aes), auth algorithm (md5/sha1), and group (group1, 2,5). Both sides...
Page 148
147 step 6﹒you can choose data encryption + authentication or authentication only to communicate in ipsec algorithm list: enc algorithm: 3des/des/aes/null auth algorithm: md5/sha1 here we select 3des for enc algorithm and md5 for auth algorithm to make sure the encapsulation way for data transmissio...
Page 149
148 step 9﹒enter the following setting in tunnel of vpn function: (figure11-13) enter a specific tunnel name. from source: select lan from source subnet / mask: enter 192.168.10.0 / 255.255.255.0. to destination: select to destination subnet / mask. to destination subnet / mask: enter 192.1...
Page 150
149 step 10﹒enter the following setting in outgoing policy:(figure11-15) authentication user: select all_net. schedule: select schedule_1. qos: select qos_1. tunnel: select ipsec_vpn_tunnel. click ok.(figure11-16) figure11-15 setting the vpn tunnel outgoing policy figure11-16 complete the v...
Page 151
150 step 11﹒enter the following setting in incoming policy: (figure11-17) schedule: select schedule_1. qos: select qos_1. tunnel: select ipsec_vpn_tunnel. click ok.(figure11-18) figure11-17 setting the vpn tunnel incoming policy figure11-18 complete the vpn tunnel incoming policy setting.
Page 152
151 the default gateway of company b is the lan ip of the smc br21vpn 192.168.20.1. Follow the steps below: step 1.Enter the following setting in multiple subnet of system configure function: (figure11-19) figure11-19 multiple subnet setting step 2.Enter the default ip of gateway of company b’s smc ...
Page 153
152 step 4.Select remote gateway-fixed ip or domain name in to destination list and enter the ip address step 5.Select preshare in authentication method and enter the preshared key (max: 100 bits) (figure11-23) step 6.Select isakmp algorithm in encapsulation list. Choose the algorithm when setup con...
Page 154
153 step 7.You can choose data encryption + authentication or authentication only to communicate in ipsec algorithm list: enc algorithm: 3des/des/aes/null auth algorithm: md5/sha1 here we select 3des for enc algorithm and md5 for auth algorithm to make sure the encapsulation way for data transmissio...
Page 155
154 step 10.Enter the following setting in tunnel of vpn function: (figure11-28) enter a specific tunnel name. from source: select lan from source subnet / mask: enter 192.168.20.0 / 255.255.255.0. to destination: select to destination subnet / mask. to destination subnet / mask: enter 192....
Page 156
155 step 11.Enter the following setting in outgoing policy: (figure11-30) authentication user: select all_net. schedule: select schedule_1. qos: select qos_1. tunnel: select vpn_tunnel. click ok.(figure11-31) figure11-30 setting the vpn tunnel outgoing policy figure11-31 complete the vpn tu...
Page 157
156 step 12.Enter the following setting in incoming policy: (figure11-32) schedule: select schedule_1. qos: select qos_1. tunnel: select ipsec_vpn_tunnel. click ok.(figure11-33) figure11-32 setting the vpn tunnel incoming policy figure11-33 complete the vpn tunnel incoming policy setting.
Page 158
157 step 13.Complete ipsec vpn connection. (figure11-34) figure 11-34 ipsec vpn connection deployment.
Page 159
158 setting pptp vpn connection between two smc br21vpn preparation company a wan ip: 61.11.11.11 lan ip: 192.168.10.X company b wan ip: 211.22.22.22 lan ip: 192.168.20.X this example takes two smc br21vpn as flattop. Suppose company b 192.168.20.100 is going to have vpn connection with company a 19...
Page 160
159 the default gateway of company a is the lan ip of the smc br21vpn 192.168.10.1. Follow the steps below: step 1.Enter pptp server of vpn function in the smc br21vpn of company a. Select modify and enable pptp server: select encryption. client ip range: enter 192.44.75.1-254. idle time: ente...
Page 161
160 step 2.Add the following settings in pptp server of vpn function in the smc br21vpn of company a: select new entry. (figure11-36) user name: enter pptp_connection. password: enter 123456789. client ip assigned by: select ip range. click ok. (figure11-37) figure 11-36 pptp vpn server se...
Page 162
161 step 3.Enter the following setting in tunnel of vpn function: (figure11-38) enter a specific tunnel name. from source: select lan from source subnet / mask: enter 192.168.10.0 / 255.255.255.0. to destination: select to destination subnet / mask. to destination subnet / mask: enter 192.1...
Page 163
162 step 4.Enter the following setting in outgoing policy: (figure11-40) authentication user: select all_net. schedule: select schedule_1. qos: select qos_1. tunnel: select pptp_vpn_tunnel. click ok.(figure11-41) figure11-40 setting the vpn tunnel outgoing policy figure11-41 complete the vp...
Page 164
163 step 5.Enter the following setting in incoming policy: (figure11-42) schedule: select schedule_1. qos: select qos_1. tunnel: select pptp_vpn_tunnel. click ok.(figure11-43) figure11-42 setting the vpn tunnel incoming policy figure11-43 complete the vpn tunnel incoming policy setting.
Page 165
164 the default gateway of company b is the lan ip of the smc br21vpn 192.168.20.1. Follow the steps below: step 1.Add the following settings in pptp client of vpn function in the smc br21vpn of company b: click new entry button. (figure11-44) user name: enter pptp_connection. password: enter1...
Page 166
165 step 2.Enter the following setting in tunnel of vpn function: (figure11-46) enter a specific tunnel name. from source: select lan from source subnet / mask: enter 192.168.20.0 / 255.255.255.0. to destination: select to destination subnet / mask. to destination subnet / mask: enter 192.1...
Page 167
166 step 3.Enter the following setting in outgoing policy: (figure11-48) authentication user: select all_net. schedule: select schedule_1. qos: select qos_1. tunnel: select pptp_vpn_tunnel. click ok.(figure11-49) figure11-48 setting the vpn tunnel outgoing policy figure11-49 complete the vp...
Page 168
167 step 4.Enter the following setting in incoming policy: (figure11-50) schedule: select schedule_1. qos: select qos_1. tunnel: select pptp_client_pptp. click ok.(figure11-51) figure11-50 setting the vpn tunnel incoming policy figure11-51 complete the vpn tunnel incoming policy setting.
Page 169
168 step 5.Complete pptp vpn connection. (figure11-52) figure 11-52 pptp vpn connection deployment.
Page 170: Chapter 12 Policy
169 chapter 12 policy policy every packet has to be detected if it corresponds with policy or not when it passes the smc br21vpn. When the conditions correspond with certain policy, it will pass the smc br21vpn by the setting of policy without being detected by other policy. But if the packet cannot...
Page 171
170 (4) lan to dmz: the source ip is in lan network; the destination is in dmz network. The system manager can set all the policy rules of lan to dmz packets in this function (5) dmz to lan: the source ip is in dmz network; the destination is in lan network. The system manager can set all the policy...
Page 172
171 define the required fields of policy source and destination: source ip and destination ip is according to the smc br21vpn’s point of view. The active side is the source; passive side is destination. Service: it is the service item that controlled by policy. The user can choose default value ...
Page 173
172 option: to display if every function of policy is enabled or not. If the function is enabled and then the chart of the function will appear (see the chart and illustration below) chart name illustration traffic log enable traffic log statistics enable traffic statistics authentication user ena...
Page 174
173 max. Concurrent sessions: set the concurrent sessions that permitted by policy. And if the sessions exceed the setting value, the surplus connection cannot be set successfully. Qos: setting the guarantee bandwidth and maximum bandwidth of the policy (the bandwidth is shared by the users who ...
Page 175
174 we set up six policy examples in this chapter: no. Suitable situation example page ex1 outgoing set up the policy that can monitor the internal users. (take logging, statistics, alarm threshold for example) 163 ex2 outgoing forbid the users to access to specific network. (take specific wan ip an...
Page 176
175 example set up the policy that can monitor the internal users. (take logging, statistics, and alarm threshold for example) step 1﹒enter the following setting in outgoing policy: click new entry select logging select statistics click ok (figure12-1) figure12-1 setting the different polici...
Page 177
176 step 2﹒complete the setting of logging, statistics, and alarm threshold in outgoing policy: (figure12-2) figure12-2 complete policy setting step 3﹒obtain the information in traffic of log functionif you want to monitor all the packets of the smc br21vpn. (figure12-3) figure12-3 traffic log monit...
Page 178
177 step 4﹒to display the traffic record that through policy to access to internet in policy statistics of statistics function. (figure12-4) figure12-4 statistics webui.
Page 179
178 forbid the users to access to specific network. (take specific wan ip and content blocking for example) step 1﹒enter the following setting in url blocking, script blocking, p2p blocking, im blocking, and download blocking in content blocking function: (figure12-5, 12-6, 12-7, 12-8, 12-9) figure1...
Page 180
179 figure12-8 im blocking setting figure12-9 download blocking setting 1. Url blocking can restrict the internal users only can access to some specific website. 2. Script blocking can restrict the internal users to access to script file of website. (java, cookies…etc.) 3. P2p blocking can restrict ...
Page 181
180 step 2﹒enter as following in wan and wan group of address function: (figure12-10, 12-11) figure12-10 setting the wan ip that going to block figure12-11 wan address group the administrator can group the custom address in address. It is more convenient when setting policy rule..
Page 182
181 step 3﹒enter the following setting in outgoing policy: click new entry destination address: select romote_group that set by step 2. (blocking by ip) action, wan port: select deny click ok (figure12-12) figure12-12 setting blocking policy.
Page 183
182 step 4﹒enter the following setting in outgoing policy: click new entry select content blocking & im / p2p blocking click ok (figure12-13) figure12-13 setting content blocking policy step 5﹒complete the setting of forbidding the users to access to specific network. (figure12-14) figure12-14...
Page 184
183 only allow the users who pass authentication to access to internet in particular time step 1﹒enter the following in schedule function: (figure12-15) figure12-15 add new schedule step 2﹒enter the following in auth user and auth user group in authentication function: (figure12-16) figure12-16 sett...
Page 185
184 step 3﹒enter the following setting in outgoing policy: click new entry authentication user: select laboratory schedule: select workingtime click ok (figure12-17) figure12-17 setting a policy of authentication and schedule step 4﹒complete the policy rule of only allows the users who pass ...
Page 186
185 the external user control the internal pc through remote control software (take pcanywhere for example) step 1﹒set up a internal pc controlled by external user, and internal pc’s ip address is 192.168.1.2 step 2﹒enter the following setting in virtual server1 of virtual server function: (figure12...
Page 187
186 step 3﹒enter the following in incoming policy: click new entry destination address: select virtual server1 (61.11.11.12) service: select pc-anywhere (5631-5632) click ok (figure12-20) figure12-20 setting the external user control the internal pc policy step 4﹒complete the policy for the ...
Page 188
187 set a ftp server under dmz nat mode and restrict the download bandwidth from external and max. Concurrent sessions. Step 1﹒set a ftp server under dmz, which ip is 192.168.3.2 (the dmz interface address is192.168.3.1/24) step 2﹒enter the following setting in virtual server1 of virtual server func...
Page 189
188 step 4﹒enter the following in wan to dmz policy: click new entry destination address: select virtual server1 (61.11.11.12) service: select ftp (21) qos: select ftp_qos max. Concurrent sessions: enter 100 click ok (figure12-24) figure12-24 add new policy step 5﹒complete the policy of ...
Page 190
189 set a mail server to allow the internal and external users to receive and send e-mail under dmz transparent mode step 1﹒set a mail server in dmz and set its network card’s ip address as 61.11.11.12. The dns setting is external dns server. Step 2﹒add the following setting in dmz of address functi...
Page 191
190 step 4﹒enter the following setting in wan to dmz policy: click new entry destination address: select mail_server service: select e-mail click ok (figure12-28) figure12-28 setting a policy to access mail service by wan to dmz step 5﹒complete the policy to access mail service by wan to dmz...
Page 192
191 step 6﹒add the following setting in lan to dmz policy: click new entry destination address: select mail_server service: select e-mail click ok (figure12-30) figure12-30 setting a policy to access mail service by lan to dmz step 7﹒complete the policy to access mail service by lan to dmz (...
Page 193
192 step 8﹒add the following setting in dmz to wan policy: click new entry source address: select mail_server service: select e-mail click ok (figure12-32) figure12-32 setting the policy of mail service by dmz to wan step 9﹒complete the policy access to mail service by dmz to wan. (figure12-...
Page 194
193 chapter 13 alert setting alert setting when the smc br21vpn had detected attacks from hackers and the internal pc sending large ddos attacks. The internal alert and external alert will start on blocking these packets to maintain the whole network. In this chapter, we will have the detailed illus...
Page 195
194 define the required fields of hacker alert detect syn attack: select this option to detect tcp syn attacks that hackers send to server computers continuously to block or cut down all the connections of the servers. These attacks will cause valid users cannot connect to the servers. 【syn floo...
Page 196
195 【icmp flood threshold(per source ip)pkts/sec】: the system administrator can enter the maximum number of icmp packets per second from attacking source ip address that is allow to enter the network / smc br21vpn. If the value exceeds the setting one, and then the device will determine it as an a...
Page 197
196 detect ping of death attack: select this option to detect the attacks of tremendous trash data in ping packets that hackers send to cause system malfunction. This attack can cause network speed to slow down, or even make it necessary to restart the computer to get a normal operation. Detect ip...
Page 198
197 detect land attack: some systems may shut down when receiving packets with the same source and destination addresses, the same source port and destination port, and when syn on the tcp header is marked. Enable this function to detect such abnormal packets. After system manager enable external ...
Page 199
198 internet alert smc br21vpn alarm and to prevent the computer which being attacked to send ddos packets to lan network step 1﹒select anomaly flow ip in setting and enter the following settings: enter the threshold sessions of infected blaster (per source ip) (the default value is 30 sessions/se...
Page 200
199 after complete the internal alert settings, if the device had detected the internal computer sending large ddos attack packets and then the alarm message will appear in the internal alarm in attack alarm or send netbios alert notification to the infected pc administrator’s pc (figure16-2, 16-3, ...
Page 201
200 figure16-4 netbios alert notification to administrator’s pc.
Page 202
201 figure16-5 e-mail virus alert.
Page 203
202 chapter 14 attack alarm attack alarm smc br21vpn has two alarm forms: internal alarm, and external alarm. Internal alarm: when the smc br21vpn had detected the internal pc sending large ddos attacks and then the internal alarm will start on blocking these packets to maintain the whole network. E...
Page 204
203 we set up two alarm examples in the chapter: no. Suitable situation example page ex 1 internal alarm to record the ddos attack alarm from internal pc 192 ex 2 external alarm to record the attack alarm about hacker attacks the smc br21vpn and intranet 193.
Page 205
204 internal alarm to record the ddos attack alarm from internal pc step 1﹒select internal alarm in attack alarm when the device detects ddos attacks, and then can know which computer is being affected. (figure17-1) figure17-1 internal alarm webui.
Page 206
205 external alarm to record the attack alarm about hacker attacks the smc br21vpn and intranet step 1﹒select the following settings in external alert in alert setting function: (figure17-2) figure17-2 external alert setting webui.
Page 207
206 step 2﹒when hacker attacks the smc br21vpn and intranet, select external alarm in attack alarm function to have detailed records about the hacker attacks. (figure17-3) figure17-3 external alarm webui.
Page 208: Chapter 15 Log
207 chapter 15 log log log records all connections that pass through the smc br21vpn’s control policies. The information is classified as traffic log, event log, and connection log. Traffic log’s parameters are setup when setting up policies. Traffic logs record the details of packets such as the st...
Page 209
208 we set up four log examples in the chapter: no. Suitable situation example page ex 1 traffic log to detect the information and protocol port that users use to access to internet or intranet by smc br21vpn. 197 ex 2 event log to record the detailed management events (such as interface and event d...
Page 210
209 traffic log to detect the information and protocol port that users use to access to internet or intranet by smc br21vpn step 1﹒add new policy in dmz to wan of policy and select enable logging: (figure18-1) figure18-1 logging policy setting step 2﹒complete the logging setting in dmz to wan policy...
Page 211
210 step 3﹒click traffic log. It will show up the packets records that pass this policy. (figure18-3) figure18-3 traffic log webui.
Page 212
211 step 4﹒click on a specific ip of source ip or destination ip in figure18-3, it will prompt out a webui about protocol and port of the ip. (figure18-4) figure18-4 the webui of detecting the traffic log by ip address.
Page 213
212 step 5﹒click on download logs and select save in file download webui. And then choose the place to save in pc and click ok; the records will be saved instantly. (figure18-5) figure18-5 download traffic log records webui.
Page 214
213 step 6﹒click clear logs and click ok on the confirm webui; the records will be deleted from the smc br21vpn instantly. (figure18-6) figure18-6 clearing traffic log records webui.
Page 215
214 event log to record the detailed management events (such as interface and event description of smc br21vpn) of the administrator step 1﹒click event log of log. The management event records of the administrator will show up (figure18-7) figure18-7 event log webui.
Page 216
215 step 2﹒click on download logs and select save in file download webui. And then choose the place to save in pc and click ok; the records will be saved instantly. (figure18-8) figure18-8 download event log records webui.
Page 217
216 step 3﹒click clear logs and click ok on the confirm webui; the records will be deleted from the smc br21vpn. (figure18-9) figure18-9 clearing event log records webui.
Page 218
217 connection log to detect event description of wan connection step 1﹒click connection in log. It can show up wan connection records of the smc br21vpn. (figure18-10) figure18-10 connection records webui.
Page 219
218 step 2﹒click on download logs and select save in file download webui. And then choose the place to save in pc and click ok; the records will be saved instantly. (figure18-11) figure18-11 download connection log records webui.
Page 220
219 step 3﹒click clear logs and click ok on the confirm webui, the records will be deleted from the smc br21vpn instantly. (figure18-12) figure18-12 clearing connection log records webui.
Page 221
220 log backup to save or receive the records that sent by the smc br21vpn step 1﹒enter setting in system, select enable e-mail alert notification function and set up the settings. (figrue18-13) figure18-13 e-mail setting webui step 2﹒enter log backup in log, select enable log mail support and click...
Page 222
221 step 3﹒enter log backup in log, enter the following settings in syslog settings: select enable syslog messages enter the ip in syslog host ip address that can receive syslog enter the receive port in syslog host port click ok complete the setting (figure18-15) figure18-15 syslog messag...
Page 223
222 chapter 16 accounting report accounting report administrator can use this accounting report to inquire the lan ip users and wan ip users, and to gather the statistics of downstream/upstream, first packet/last packet/duration and the service of all the user’s ip that passes the smc br21vpn..
Page 224
223 define the required fields of accounting report accounting report setting: by accounting report function can record the sending information about intranet and the external pc via smc br21vpn. Accounting report can be divided into two parts: outbound accounting report and inbound accounting rep...
Page 225
224 inbound accounting report it is the statistics of downstream / upstream for all kinds of communication services; the inbound accounting report will be shown when wan user uses smc br21vpn to connect to lan service server. Source ip: the ip address used by wan users who use smc br21vpn destinat...
Page 226
225 outbound step 1﹒enter outbound in accounting report and select top users to inquire the statistics of send / receive packets, downstream / upstream, first packet/last packet/duration and the service from the lan or dmz user’s ip that pass the smc br21vpn. (figure19-1) top: select the data you wa...
Page 227
226 figure19-1 outbound source ip statistics report.
Page 228
227 step 2﹒enter outbound in accounting report and select top sites to inquire the statistics website of send/receive packets, downstream/upstream, first packet/last packet/duration and the service from the wan server to pass the smc br21vpn. (figure19-2) top:select the data you want to view, it p...
Page 229
228 figure19-2 outbound destination ip statistics report.
Page 230
229 step 3﹒enter outbound in accounting report and select top services to inquire the statistics website of send / receive packets, downstream/upstream, first packet/last packet/duration and the service from the wan server to pass the smc br21vpn. (figure19-3) top:select the data you want to view....
Page 231
230 accounting report..
Page 232
231 figure19-3 outbound services statistics report figure19-4 according to the downstream / upstream report of the selected top numbering to draw the protocol distribution chart press to return to accounting report window..
Page 233
232 inbound step 1﹒enter inbound in accounting report and select top users to inquire the statistics website of send / receive packets, downstream / upstream, first packet/last packet / duration and the service from the wan user to pass the smc br21vpn. (figure19-5) top:select the data you want to...
Page 234
233 figure19-5 inbound top users statistics report.
Page 235
234 enter inbound in accounting report and select top sites to inquire the statistics website of send / receive packets, downstream / upstream, first packet/last packet / duration and the service from the wan user to pass the smc br21vpn. (figure19-6) top:select the data you want to view. It prese...
Page 236
235 figure19-6 inbound destination ip statistics report.
Page 237
236 step 2﹒enter inbound in accounting report and select top services to inquire the statistics website of send/receive packets, downstream/upstream, first packet/last packet/duration and the service from the wan server to pass the smc br21vpn. (figure19-7) top:select the data you want to view. It...
Page 238
237 figure19-7 inbound services statistics report figure19-8 according to the downstream / upstream report of the selected top numbering to draw the protocol distribution chart.
Page 239: Chapter 17 Statistics
238 chapter 17 statistics statistics wan statistics: the statistics of downstream / upstream packets and downstream/upstream traffic record that pass wan interface policy statistics: the statistics of downstream / upstreampackets and downstream/upstream traffic record that pass policy in this chapte...
Page 240
239 define the required fields of statistics: statistics chart: y-coordinate:network traffic(kbytes/sec) x-coordinate:time(hour/minute) source ip, destination ip, service, and action: these fields record the original data of policy. From the information above, the administrator can know which ...
Page 241
240 wan statistics step 1﹒enter wan in statistics function, it will display all the statistics of downstream/upstream packets and downstream/upstream record that pass wan interface. (figure20-1) figure20-1 wan statistics function time: to detect the statistics by minutes, hours, days, months, or y...
Page 242
241 step 3﹒statistics chart (figure20-2) y-coordinate:network traffic(kbytes/sec) x-coordinate:time(hour/minute) figure20-2 to detect wan statistics.
Page 243
242 policy statistics step 1﹒if you had select statistics in policy, it will start to record the chart of that policy in policy statistics. (figure20-3) figure20-3 policy statistics function if you are going to use policy statistics function, the system manager has to enable the statistics in policy...
Page 244
243 step 3﹒statistics chart (figure20-4) y-coordinate:network traffic(kbytes/sec) x-coordinate:time(hour/minute/day) figure20-4 to detect policy statistics.
Page 245: Chapter 18 Status
244 chapter 18 status status the users can know the connection status in status. For example: lan ip, wan ip, subnet netmask, default gateway, dns server connection, and its ip…etc. interface: display all of the current interface status of the smc br21vpn authentication: the authentication infor...
Page 246
245 interface step 1﹒enter interface in status function; it will list the setting for each interface: (figure21-1) pppoe con. Time: the last time of the smc br21vpn to be enabled mac address: the mac address of the interface ip address/ netmask: the ip address and its netmask of the interface ...
Page 247
246 figure21-1 interface status.
Page 248
247 authentication step 1﹒enter authentication in status function, it will display the record of login status: (figure21-2) ip address: the authentication user ip auth-user name: the account of the auth-user to login login time: the login time of the user (year/month/day hour/minute/second) fi...
Page 249
248 arp table step 1﹒enter arp table in status function; it will display a table about ip address, mac address, and the interface information which is connecting to the smc br21vpn: (figure21-3) netbios name: the identified name of the network ip address: the ip address of the network mac addr...
Page 250
249 dhcp clients step 1﹒in dhcp clients of status function, it will display the table of dhcp clients that are connected to the smc br21vpn: (figure21-4) ip address: the dynamic ip that provided by dhcp server mac address: the ip that corresponds to the dynamic ip leased time: the valid time o...
Page 251: Smcbr21Vpn
Smcbr21vpn 20 mason • irvine, ca 92618 • phn: (949) 679-8000 • www.Smc.Com.