- DL manuals
- Thecus
- Network Storage Server
- i8500
- User Manual
Thecus i8500 User Manual
Summary of i8500
Page 1
- 1 - thecus i8500 iscsi raid system user manual.
Page 2: Preface
- 2 - preface about this manual this manual is the introduction of i8500 and it aims to help users know the operations of the disk array system easily. Information contained in this manual has been reviewed for accuracy, but not for product warranty because of the various environments/os/settings, i...
Page 3: Table of Contents
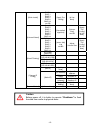
- 3 - table of contents 1.1 features........................................................................... 5 1.2 terminology ..................................................................... 6 1.3 raid levels ...................................................................... 8 1.4 volum...
Page 4: Chapter 4
- 4 - 3.8.1 system information...............................................................................54 3.8.2 upgrade................................................................................................54 3.8.3 reset to factory default.................................................
Page 5: 1.1 Features
- 5 - chapter 1 raid introduction 1.1 features i8500 controller features: • front-end 2 gbe nic ports. • iscsi jumbo frame support. • raid 6, 60 ready. • sata ii drives backward-compatible. • one logic volume can be shared by as many as 8 hosts and 32 connections per system. • host access control. •...
Page 6: 1.2 Terminology
- 6 - 1.2 terminology the document uses the following terms: raid raid is the abbreviation of “redundant array of independent d isks”. There are different raid levels with different degree of the data protection, data availability, and performance to host environment. Pd the physical disk belongs to...
Page 7
- 7 - raid width=1; raid copy=4; raid row=3. Wt w rite-through cache-write policy. A caching technique in which the completion of a write request is not signaled until data is safely stored in non-volatile media. Each data is synchronized in both data cache and accessed physical disks. Wb w rite-bac...
Page 8: 1.3 Raid Levels
- 8 - wwn w orld wide name. Hba h ost bus adapter. Saf-te s csi accessed fault-tolerant enclosures. Ses s csi enclosure services. Nic n etwork interface card. Lacp l ink aggregation control protocol. Mpio m ulti-path input/output. Mc/s m ultiple connections per session mtu m aximum transmission unit...
Page 9
- 9 - raid 0+1 mirroring of the member raid 0 volumes. Raid 0+1 needs at least four hard drives. Raid 10 striping over the member raid 1 volumes. Raid 10 needs at least four hard drives. Raid 30 striping over the member raid 3 volumes. Raid 30 needs at least six hard drives. Raid 50 striping over th...
Page 10: Chapter 2 Getting Started
- 10 - execute the data transaction. Each cv can have different cache memory size by user’s modification/setting. Lun (logical unit number) is a unique identifier, in which users can access through scsi commands. Chapter 2 getting started 2.1 before starting before starting, prepare the following it...
Page 11
- 11 - storage protocol, such as iscsi, has “two ends” in the connection. These ends are initiator and target. In iscsi, we call them iscsi initiator and iscsi target. The iscsi initiator requests or initiates any iscsi communication. It requests all scsi operations like read or write. An initiator ...
Page 12: 2.3 Management Methods
- 12 - 2. Linux iscsi initiator is also available. For different kernels, there are different iscsi drivers. Please check appendix a for iscsi initiator certification list. If user needs the latest linux iscsi initiator, please visit open-iscsi project for most update information. Linux-iscsi (sfnet...
Page 13: 2.4 Enclosure
- 13 - or login with read-only account which only allows reading the configuration and cannot change setting. Login name: user default password: 1234 2.3.2 remote control – secure shell ssh (secure shell) is required for controllers to remote login. The ssh client software is available at the follow...
Page 14
- 14 - when there is warning or error occurred (lcm default filter), the lcm shows the event log to give users more detail from front panel. The following table is function description. System info. Display system information. Alarm mute mute alarm when error occurs. Reset/shutdown reset or shutdown...
Page 15
- 15 - [quick install] raid 0 raid 1 raid 3 raid 5 raid 6 raid 0+1 xxx gb [apply the config] [cyes nod] [local] raid 0 raid 1 raid 3 raid 5 raid 6 raid 0+1 [use default algorithm] [volume size] xxx gb [apply the config] [cyes nod] [volume wizard] [jbod x] cd raid 0 raid 1 raid 3 raid 5 raid 6 raid 0...
Page 16
- 16 - 2.4.2 system buzzer the system buzzer features are listed below: 1. The system buzzer alarms 1 second when system boots up successfully. 2. The system buzzer alarms continuously when there is error occurred. The alarm will be stopped after error resolved or be muted. 3. The alarm will be mute...
Page 17: Chapter 3 Web Gui Guideline
- 17 - chapter 3 web gui guideline 3.1 web gui hierarchy the below table is the hierarchy of web gui. Quick installation Æ step 1 / step 2 / confirm system configuration system setting Æ system name / date and time ip address Æ mac address / address / dns / port login setting Æ login configuration /...
Page 18: 3.2 Login
- 18 - upgrade Æ browse the firmware to upgrade / export configuration reset to default Æ sure to reset to factory default? Import and export Æ import/export / import file event log Æ download / mute / clear reboot and shutdown Æ reboot / shutdown logout sure to logout? 3.2 login i8500 supports grap...
Page 19: 3.3 Volume Creation Wizard
- 19 - figure 3.2.2 1. Raid light: green means raid works well. Red represents raid failure. 2. Temperature light: green means normal temperature. Red represents abnormal temperature. 3. Voltage light: green means normal voltage. Red represents abnormal voltage. 4. Ups light: green means ups works w...
Page 20: 3.4 System Configuration
- 20 - step 2: confirm page. Click“ ” if all setups are correct. Then a vd will be created. Done. You can start to use the system now. Figure 3.3.2 (figure 3.3.2: a raid 0 virtual disk with the vd name “quick53360”, named by system itself, with the total available volume size 1191gb.) 3.4 system con...
Page 21
- 21 - figure 3.4.1.1 check “change date and time” to set up the current date, time, and time zone before using or synchronize time from ntp (network time protocol) server. 3.4.2 ip address “ip address” can change ip address for remote administration usage. There are 2 options, dhcp (get ip address ...
Page 22
- 22 - 3.4.3 login setting “login setting” can set single admin, auto logout time and admin/user password. The single admin can prevent multiple users access the same controller at the same time. 1. Auto logout: the options are (1) disable; (2) 5 minutes; (3) 30 minutes; (4) 1 hour. The system will ...
Page 23
- 23 - figure 3.4.4.1 3.4.5 notification setting “notification setting” can set up snmp trap for alerting via snmp, pop-up message via windows messenger (not msn), alert via system log server protocol, and event log filter..
Page 24
- 24 - figure 3.4.5.1 “snmp” allows up to 3 snmp trap addresses. Default community setting is “public”. User can choose the event log levels and default setting only enables info event log in snmp. There are many snmp tools. The following web sites are for your reference: snmpc: http://www.Snmpc.Com...
Page 25: 3.5 Iscsi Configuration
- 25 - using “system log server”, user can choose the facility and the event log level. The default port of syslog is 514. The default setting enables event level: info, warning and error event logs. There are some syslog server tools. The following web sites are for your reference: winsyslog: http:...
Page 26
- 26 - 3.5.2 nic “nic” can change ip addresses of iscsi data ports. Figure 3.5.2.1 (figure 3.5.2.1: there are 2 iscsi data ports.) ip settings: user can change ip address by moving mouse to the gray button of lan port, click “ip settings for iscsi ports”. There are 2 selections, dhcp (get ip address...
Page 27
- 27 - 3.5.3 node “node” can view the target name for iscsi initiator. The node name of i8500 exists by default and can not be changed. Figure 3.5.3.1 chap: chap is the abbreviation of challenge handshake authorization protocol. Chap is a strong authentication method used in point-to-point for user ...
Page 28
- 28 - 4. Go to “/ iscsi configuration / chap account” page to create chap account. Please refer to next section for more detail. 5. In “authenticate” page, select “none” to disable chap. 3.5.4 session “session” can display iscsi session and connection information, including the following items: 1. ...
Page 29: 3.6 Volume Configuration
- 29 - 2. Enter “user” , “secret”, and “confirm” secret again. Figure 3.5.5.3 3. Click “ ”. Figure 3.5.5.1 (figure 3.5.5.4: create a chap account named “chap1”.) 4. Click “delete” to delete chap account. 3.6 volume configuration “volume configuration” is designed for setting up the volume configurat...
Page 30
- 30 - raid levels, it will use all available hdds for raid level depends on which user chooses. When system has different sizes of hdds, e.G., 8*200g and 8*80g, it lists all possibilities and combination in different raid level and different sizes. After user chooses raid level, user may find that ...
Page 31
- 31 - figure 3.6.1.2 step 3: decide vd size. User can enter a number less or equal to the default number. Then click “ ”. Figure 3.6.1.3 step 4: confirm page. Click“ ” if all setups are correct. Then a vd will be created. Done. You can start to use the system now. Figure 3.6.1.4 (figure 3.6.1.4: a ...
Page 32
- 32 - 3.6.2 physical disk “physical disk” can view the status of hard drives in the system. The followings are operational tips: 1. Mouse moves to the gray button next to the number of slot, it will show the functions which can be executed. 2. Active function can be selected, but inactive function ...
Page 33
- 33 - figure 3.6.2.3 (figure 3.6.2.3: physical disks of slot 1,2,3 are created for a rg named “rg-r5”. Slot 4 is set as dedicated spare disk of rg named “rg-r5”. The others are free disks.) • pd column description: slot the position of hard drives. The button next to the number of slot shows the fu...
Page 34
- 34 - “good” Æ the hard drive is good. “failed” Æ the hard drive is failed. “error alert” Æ s.M.A.R.T. Error alert. “read errors” Æ the hard drive has unrecoverable read errors. Usage “rd” Æ raid disk. This hard drive has been set to raid. “fr” Æ free disk. This hard drive is free for use. “ds” Æ d...
Page 35
- 35 - set dedicated spares set hard drive to dedicated spare of selected rgs. Set property change the status of write cache and standby. Write cache options: “enabled” Æ enable disk write cache. “disabled” Æ disable disk write cache. Standby options: “disabled” Æ disable spindown. “30 sec / 1 min /...
Page 36
- 36 - step 2: confirm page. Click “ ” if all setups are correct. Figure 3.6.3.2 (figure 3.6.3.2: there is a raid 0 with 4 physical disks, named “rg-r0”, total size is 135gb. Another is a raid 5 with 3 physical disks, named “rg-r5”.) done. View “raid group” page. • rg column description: no. Number ...
Page 37
- 37 - “migrate” Æ the raid group is being migrated. “scrub” Æ the raid group is being scrubbed. Health the health of raid group. “good” Æ the raid group is good. “failed” Æ the hard drive is failed. “degraded” Æ the raid group is not completed. The reason could be lack of one disk or disk failure. ...
Page 38
- 38 - information 3.6.4 virtual disk “virtual disk” can view the status of each virtual disk. The following is an example to create a vd. Step 1: click “ ”, enter “name”, choose “rg name”, “stripe height (kb)” , “block size (b)”, “read/write” mode, “priority”, “bg rate” , change “capacity (gb)” if ...
Page 39
- 39 - figure 3.6.4.2 (figure 3.6.4.2: create a vd named “vd-01”, related to “rg-r0”, size is 30gb. The other vd is named “vd-02”, initializing to 12%.) done. View “virtual disk” page. • vd column description: no. Number of this virtual disk. The button next to the vd no. Shows the functions which c...
Page 40
- 40 - bg rate background task priority. “4 / 3 / 2 / 1 / 0” Æ default value is 4. The higher number the background priority of a vd has, the more background i/o will be scheduled to execute. Status the status of virtual disk. “online” Æ the virtual disk is online. “offline” Æ the virtual disk is of...
Page 41
- 41 - #snapshot number of snapshot(s) that virtual disk is taken. Rg name the virtual disk is related to the rg name readahead this feature makes data be loaded to disk's buffer in advance for further use. Default is "enabled". • vd operations description: extend extend a virtual disk capacity. Scr...
Page 42
- 42 - cleanup snapshot clean all snapshot vd related to the virtual disk and release snapshot space. Take snapshot take a snapshot on the virtual disk. Auto snapshot set auto snapshot on the virtual disk. List snapshot list all snapshot vd related to the virtual disk. More information show virtual ...
Page 43
- 43 - step 3: take a snapshot. In “/ volume configuration / snapshot”, click “ ”. It will link to next page. Enter a snapshot name. Figure 3.6.5.3 step 4: export the snapshot vd. Mouse moves to the gray button next to the snapshot vd number; click “export”. Enter a capacity for snapshot vd. If size...
Page 44
- 44 - • snapshot column description: no. Number of this snapshot vd. The button next to the snapshot vd no. Shows the functions which can be executed. Name snapshot vd name. Used (mb) the amount of snapshot space that has been used. Exported snapshot vd is exported or not. Right “rw” Æ read / write...
Page 45
- 45 - user can attach lun by clicking the “ ”. “host” must enter an iscsi node name for access control, or fill-in wildcard “*”, which means every host can access the volume. Choose lun number and permission, then click “ ”. Figure 3.6.6.1 • lun operations description: attach attach a logical unit ...
Page 46
- 46 - step 1: create rg (raid group). To create the raid group, please follow the procedures: figure 3.6.7.1 1. Select “/ volume configuration / raid group” . 2. Click “ “. 3. Input a rg name, choose a raid level from the list, click “ “ to choose the raid pd slot(s), then click “ “. 4. Check the o...
Page 47
- 47 - figure 3.6.7.3 5. Select “/ volume configuration / virtual disk” . 6. Click “ ”. 7. Input a vd name, choose a rg name and enter a size of vd; decide the stripe high, block size, read/write mode and set priority, finally click “ “. 8. Done. A vd has been created. 9. Do one more time to create ...
Page 48
- 48 - 2. Input “host” name, which is a fc node name for access control, or fill- in wildcard “*”, which means every host can access to this volume. Choose lun and permission, then click “ ”. 3. Done. Step 4: set global spare disk. To set global spare disks, please follow the procedures. 1. Select “...
Page 49
- 49 - in “/ volume configuration / logical unit”, 1. Mouse moves to the gray button next to the lun; click “detach”. There will pop up a confirmation page. 2. Choose “ok”. 3. Done. Step 7: delete vd (virtual disk). To delete the virtual disk, please follow the procedures: 1. Select “/ volume config...
Page 50: 3.7 Enclosure Management
- 50 - 1. Select “/ volume configuration / physical disk” . 2. Mouse moves to the gray button next to the pd slot; click “set free disk” . Step 10: done, all volumes have been deleted. 3.7 enclosure management “enclosure management” allows managing enclosure information including “ses configuration”...
Page 51
- 51 - 3.7.2 hardware monitor “hardware monitor” can view the information of current voltage and temperature. Figure 3.7.2.1 if “auto shutdown” has been checked, the system will shutdown automatically when voltage or temperature is out of the normal range. For better data protection, please check “a...
Page 52
- 52 - 3. If the high temperature situation doesn’t last for 3 minutes, controller will not do auto shutdown. 3.7.3 hard drive s.M.A.R.T. Support s.M.A.R.T. (self-monitoring analysis and reporting technology) is a diagnostic tool for hard drives to deliver warning of drive failures in advance. S.M.A...
Page 53
- 53 - 3.7.4 ups “ups” can set up ups (uninterruptible power supply). Figure 3.7.4.1 currently, the system only supports and communicates with smart-ups of apc (american power conversion corp.) ups. Please review the details from the website: http://www.Apc.Com/ . First, connect the system and apc u...
Page 54: 3.8 System Maintenance
- 54 - “ups shutdown in progress” “batteries failed. Please change them now!” battery level (%) current percentage of battery level. 3.8 system maintenance “maintenance” allows the operation of system functions which include “system information” to show the system version, “upgrade” to the latest fi...
Page 55
- 55 - figure 3.8.2.1 figure 3.8.2.2 when upgrading, there is a progress bar running. After finished upgrading, the system must reboot manually to make the new firmware took effect. 3.8.3 reset to factory default “reset to factory default” allows user to reset controller to factory default setting. ...
Page 56
- 56 - 3.8.4 import and export “import and export” allows user to save system configuration values: export, and apply all configuration: import. For the volume configuration setting, the values are available in export and not available in import which can avoid confliction/date-deleting between two ...
Page 57: 3.9 Logout
- 57 - figure 3.8.5.1 the event log is displayed in reverse order which means the latest event log is on the first page. The event logs are actually saved in the first four hard drives; each hard drive has one copy of event log. For one controller, there are four copies of event logs to make sure us...
Page 58: 4.1 Rebuild
- 58 - chapter 4 advanced operation 4.1 rebuild if one physical disk of the rg which is set as protected raid level (e.G.: raid 3, raid 5, or raid 6) is failed or has been unplugged/removed, then the status of rg is changed to degraded mode, the system will search/detect spare disk to rebuildthe deg...
Page 59
- 59 - sometimes, rebuild is called recover; they are the same meaning. The following table is the relationship between raid levels and rebuild. Raid 0 disk striping. No protection for data. Rg fails if any hard drive fails or unplugs. Raid 1 disk mirroring over 2 disks. Raid 1 allows one hard drive...
Page 60: 4.2 Rg Migration
- 60 - arrays. Jbod the abbreviation of “just a bunch of disks”. No data protection. Rg fails if any hard drive failures or unplugs. 4.2 rg migration to migrate the raid level, please follow below procedures. 1. Select “/ volume configuration / raid group” . 2. Mouse moves to the gray button next to...
Page 61
- 61 - figure 4.2.2 (figure 4.2.2: a raid 0 with 4 physical disks migrates to raid 5 with 5 physical disks.) figure 4.2.3 (figure 4.2.3: a raid 0 migrates to raid 5, the complete percentage is 14%.) to do migration, the total size of rg must be larger or equal to the original rg. It does not allow e...
Page 62: 4.3 Vd
- 62 - 4.3 vd extension to extend vd size, please follow the procedures. 1. Select “/ volume configuration / virtual disk” . 2. Mouse moves to the gray button next to the vd number; click “extend” . 3. Change the size. The size must be larger than the original, and then click “ “ to start extension....
Page 63
- 63 - capture. The certain location, named as “snap vd”, is essentially a new vd.Which can be attached to a lun provisioned to a host as a disk like other ordinary vds in the system. Rollback restores the data back to the state of any time which was previously captured in case for any unfortunate r...
Page 64
- 64 - figure 4.4.1.1 (figure 4.4.1.1: this is snap vd, but it is not exported.) 7. Mouse moves to the gray button next to the snapshot vd number; click “export” . Enter a capacity for snapshot vd. If size is zero, the exported snapshot vd will be read only. Otherwise, the exported snapshot vd can b...
Page 65
- 65 - 2. For performance and future rollback, system saves snapshot with names in sequences. For example, three snapshots has been taken and named “snapvd-01”(first), “snapvd-02” and “snapvd-03”(last). When deleting “snapvd-02”, both of “snapvd-02” and “snapvd-03” will be deleted because “snapvd-03...
Page 66
- 66 - 3. Done. It will take snapshots automatically. Figure 4.4.2.1 (figure 4.4.2.1: it will take snapshots every month, and keep the last 32 snapshot copies.) 4.4.3 rollback the data in snapshot vd can rollback to original vd. Please follow the procedures. 1. Select “/ volume configuration / snaps...
Page 67: 4.5 Disk
- 67 - 2. When making rollback, the original vd cannot be accessed for a while. At the same time, the system connects to original vd and snaps vd, and then starts rollback. 3. During rollback, data from snap vd to original vd, the original vd can be accessed and the data in vd just like it has finis...
Page 68
- 68 - use multiple physical paths to create logical "paths" between the server and the storage device. In the case which one or more of these components fails, causing the path to fail, multi-path logic uses an alternate path for i/o. So applications can still access their data. Microsoft iscsi ini...
Page 69: Appendix
- 69 - appendix a. Certification list • ram i8500 ram spec: 184pins, ddr333(pc2700), reg.(register) or ub(unbufferred), ecc or non-ecc, from 64mb to 1gb, 32-bit or 64-bit data bus width, x8 or x16 devices, 9 to 11 bits column address. Vendor model atp ag64l72t8sqc4s, 512mb ddr-400 (ecc) with samsung...
Page 70
- 70 - iscsi initiator iscsi-initiator-utils-4.0.3.0-4 in kernel 2.6.9 3. For red hat enterprise linux 5 (kernel 2.6), use the build-in iscsi initiator iscsi-initiator-utils-6.2.0.742-0.5.El5 in kernel 2.6.18 mac atto xtend san iscsi initiator v3.10 system requirements: 1. Mac os x v10.5 or later fo...
Page 71: Event Notifications
- 71 - hitachi deskstar 7k80, hds728040pla320, 40gb, 7200rpm, sata ii, 2m hitachi deskstar t7k500, hdt725032vla360, 320gb, 7200rpm, sata ii, 16m hitachi deskstar p7k500, hdp725050gla360, 500gb, 7200rpm, sata ii, 16m maxtor diamondmax plus 9, 6y080m0, 80gb, 7200rpm, sata, 8m maxtor diamondmax 11, 6h5...
Page 72
- 72 - info scsi info received scsi bus reset event at the scsi bus . • ems events level type description info power installed power is installed. Error power absent power is absent. Info power work power is restored to work. Error power warning power is out of work. Warning power detect psu signal ...
Page 73
- 73 - info rg created rg has been created. Info rg creation failed failed to create rg . Info rg deleted rg has been deleted. Info vd created vd has been created. Info vd creation failed failed to create vd . Info vd deleted vd has been deleted. Info vd renamed name of vd has been renamed to . Info...
Page 74
- 74 - write error occurred info dedicated spare configured pd has been configured to rg as a dedicated spare disk. Info global spare configured pd has been configured as a global spare disk. Warning pd read error occurred read error occurred at lba warning pd write error occurred write error occurr...
Page 75
- 75 - backuped data finishes. Info bbm detected battery backup module is detected. Info bbm is good battery backup module is good. Info bbm is charging battery backup module is charging. Warning bbm is failed battery backup module is failed. Info bbm battery backup feature is . • jbod events level ...
Page 76: C. Known Issues
- 76 - c. Known issues 1. Microsoft mpio driver is not supported on windows xp and windows 2000 professional. Workaround solution: using windows server 2008/2003, windows 2000 server to run mpio. Workaround solution: it’s a jbod limitation..
Page 77
- 77 - d. Microsoft iscsi initiator here is the step by step to setup microsoft iscsi initiator. Please visit microsoft website for latest iscsi initiator. The following setup may not use the latest microsoft iscsi initiator. 1. Run microsoft iscsi initiator. 2. Click “discovery” . 3. Click “add” . ...
Page 78
- 78 - figure d.4 7. Click “advance…” if chap information is needed. 8. Click “ok” . The status would be “connected”. 9. Done, it can connect to an iscsi disk. The following procedure is to log off iscsi device. 1. Click “details” in “targets”. 2. Check the identifier, which will be deleted. 3. Clic...
Page 79
- 79 - e. Installation steps for large volume (tb) introduction: i8500 capable of supporting large volumes (>2tb). When connecting controllers to 64bit os installed host/server, the host/server is inherently capable for large volumes from the 64bit address. On the other side, if the host/server is i...
Page 80
- 80 - 1. Follow the installation guild provided by hba vendor, install hba driver properly. For iscsi models, please install the latest microsoft iscsi initiator from the link below. Http://www.Microsoft.Com/downloads/details.Aspx?Familyid=12cb3c1a- 15d6-4585-b385-befd1319f825&displaylang=en step 3...
Page 81
- 81 - http://www.Microsoft.Com/whdc/device/storage/gpt_faq.Mspx figure e.4 4. Format the disk. Figure e.5 5. Done. Figure e.6 6. The new disk is ready to use, the available size = 2.72tb..
Page 82
- 82 - figure e.7 7. Wrong setting result: os can not format disk sector after 2048gb(2tb). Figure e.8 f. Mpio and mc/s setup instructions here is the instruction to setup mpio or mc/s. The following network diagrams are the examples. Please follow them to setup the environment. Remind that host mus...
Page 83
- 83 - figure f.1 the mpio setup instructions are in the following: 1. Create rg/vd, and then attach lun. 2. Add the first “target portal” on microsoft iscsi initiator. 3. Add the second “target portal” on microsoft iscsi initiator. 4. Logon. 5. Enable “enable multi-path” checkbox. Then click “advan...
Page 84
- 84 - 11. Click “device” tab, then click “advanced”. 12. Click “mpio” tab, select “load balance policy” to “round robin”. 13. Click “apply”. 14. Run “device manage” in windows. Make sure mpio device is available. 15. Done. The mc/s setup instructions are in the following: 1. Create rg/vd, and then ...
Page 85
- 85 - z info: abnormal shutdown detected, start flushing battery-backed data (xxx kb). Z info: abnormal shutdown detected, flushing battery-backed data finished bbm inspect steps 1. Connect bbm cable into i8500 controller. 2. Initial controller, then bbm will start to charge automatically. 3. Wait ...
Page 86: M/b Diagram
- 86 - ■ h ■ m/b diagram.