Summary of Endpoint Protector Basic
Page 1
Endpoint protector basic user guide english.
Page 2
2 contents 1. Introduction 3 2. Endpoint protector product family 3 p y 3. System requirements 3 y q 4. Controlled device types 4 yp 5. Installation 4 6. Getting started 5 g 7. Rights 5 g 7.1. Devices 5 7.2. Device class 6 8. Settings 7 g 8.1. File tracing 7 g 8.2. Password protection 8 p 9. Reports...
Page 3
3 1. Introduction endpoint protector basic™ will help you secure your pcs endpoints by controlling and monitoring device use. You will be able to restrict the use of usb, firewire and other ports and control portable device use your computer. You can fi nd a complete list of all controlled device typ...
Page 4
4 4. Controlled device types endpoint protector basic supports a wide range of device types which represent key sources of security breaches. These devices can be authorized which makes it possible for the users to view, create or modify their content and for administrators to view the data transfer...
Page 5
5 6. Getting started important! Make sure you are logged in to the pc as administrator. Endpoint protector basic comes with a confi guration interface, which will be available for logged in administrators only. If a standard user (guest, restricted) logs into the system the confi guration interface wi...
Page 6
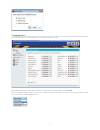
6 7.2. Device class this module will allow you to specify what device class can be accessible on your pc. By default the following device types will have allow access rights: wifi, local printers, webcams and cd-roms. In order to change the rights for a device class, you need to click the select box...
Page 7
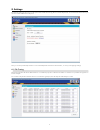
7 8. Settings the general settings module gives you the option to deactivate file tracing, which is activated by default. You can deactivate this feature if you do not need this additional security level. Here you can also password protect the access to the endpoint protector basic user interface, o...
Page 8
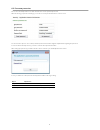
8 8.2. Password protection the access to the endpoint protector basic user interface can be password protected. After introducing your password settings, you need to click “set password” button in order to save it. You also have the option to save a ‘hint’ (reminder) for the password. This might be ...
Page 9
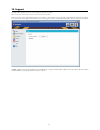
9 9. Reports and analysis the most powerful and detailed representation of activity recordings can be achieved using this module. It allows the administrator to see exactly what actions took place at what time. This information also contains the computer name, user and device used and also the actio...
Page 10
10 10. E-mail alerts you have the option to receive a system alert in the form of an e-mail notifi cation, each time an unauthorized device is connected to the pc that is protected with endpoint protector basic. To enable alerts by e-mail notifi cation, you must confi gure the e-mail server host and pr...
Page 11
11 11. Notifi cation messages in order to see notifi cations, the epp basic notifi er needs to be running. In case your notifi er is running, you will see its icon in the system tray. When you right click the icon, you will have the option to launch the application, or to exit the notifi er. You can rest...
Page 12
12 12. About 12.1. License key registration your version of endpoint protector basic comes with a lifetime license; therefore you will be able to use the full functionality of the application on your pc. 12.2. Update mechanism you can check for the availability of a newer endpoint protector basic ve...
Page 13
13 14. Support visit http://www.Verbatim-europe.Co.Uk/en_1/support_usb-devices_1.Html one of our team members will contact you in the shortest time possible. Even if you do not have a problem but miss some feature or just want to leave us general comment we would love to hear from you. Your input is...