- DL manuals
- Watchguard
- Network Router
- Firebox SOHO 6 Wireless
- User Manual
Watchguard Firebox SOHO 6 Wireless User Manual - In The Seconds Field and
User Guide
129
Installing and Configuring the MUVPN Client
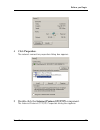
10 Select Both from the SA Life drop-down list.
11 Type
86400
in the Seconds field and
8192
in the KBytes field.
12 Select None from the Compression drop-down list.
This is the default setting. The SOHO 6 does not support compression.
13 Select the Encapsulation Protocol (ESP) checkbox.
14 Select a value for the Encrypt Alg and Hash Alg drop-down
lists.
N
OTE
The encrypted and hash values must match the settings of the SOHO 6. If
the settings do not match, the connection will fail.
15 Select Tunnel from the Encapsulation drop-down list.
This is the default setting.
16 Make sure the Authentication Protocol (AH) checkbox is not
selected.
17 Select File => Save or click the button shown at the right.
Summary of Firebox SOHO 6 Wireless
Page 1
Watchguard ® firebox ® soho 6 user guide soho 6 - firmware version 6.3.
Page 2
Ii watchguard firebox soho 6 certifications and notices fcc certification this appliance has been tested and found to comply with limits for a class a digital appliance, pursuant to part 15 of the fcc rules. Operation is subject to the following two conditions: • this appliance may not cause harmful...
Page 3
User guide iii vcci notice class a ite.
Page 4
Iv watchguard firebox soho 6 declaration of conformity.
Page 5
User guide v watchguard soho software end-user license agreement watchguard soho software end-user license agreement important - read carefully before accessing watchguard software this watchguard soho software end-user license agreement ("eula") is a legal agreement between you (either an individua...
Page 6
Vi watchguard firebox soho 6 if you are accessing the software product via a web based installer program, you are granted the following additional rights to the software product: (a) you may install and use the software product on any computer with an associated connection to the soho hardware produ...
Page 7
User guide vii election. Disclaimer and release. The warranties, obligations and liabilities of watchguard, and your remedies, set forth in paragraphs 4, 4(a) and 4(b) above are exclusive and in substitution for, and you hereby waive, disclaim and release any and all other warranties, obligations an...
Page 8
Viii watchguard firebox soho 6 restricted rights. Use, duplication or disclosure by the u.S government or any agency or instrumentality thereof is subject to restrictions as set forth in subdivision (c)(1)(ii) of the rights in technical data and computer software clause at dfars 252.227-7013, or in ...
Page 9
User guide ix transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of watchguard technologies, inc. Copyright, trademark, and patent information copyright© 1998 - 2003 watchguard technologies, inc. All rights reserved. Applock®, a...
Page 10
X watchguard firebox soho 6 3. All advertising materials mentioning features or use of this software must display the following acknowledgment: "this product includes software developed by the openssl project for use in the openssl toolkit. (http://www.Openssl.Org/)" 4. The names "openssl toolkit" a...
Page 11
User guide xi 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. 3. All advertising materials mentioning features or use of this software must di...
Page 12
Xii watchguard firebox soho 6 5. Products derived from this software may not be called "mod_ssl" nor may "mod_ssl" appear in their names without prior written permission of ralf s. Engelschall. 6. Redistributions of any form whatsoever must retain the following acknowledgment: "this product includes...
Page 13
User guide xiii this software is provided ``as is'' and any expressed or implied warranties, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose are disclaimed. In no event shall the apache software foundation or its contributors be liable fo...
Page 14
Xiv watchguard firebox soho 6 abbreviations used in this guide 3des triple data encryption standard des data encryption standard dns domain name service dhcp dynamic host control protocol dsl digital subscriber line ip internet protocol ipsec internet protocol security isdn integrated services digit...
Page 15
User guide xv contents chapter 1 introduction ..................................................1 package contents .....................................................3 how a firewall works ................................................3 how information travels on the internet ..................4...
Page 16
Xvi watchguard firebox soho 6 examining and recording the current tcp/ip settings ................................................................. 12 disabling the http proxy setting of your web browser .................................................... 14 enabling your computer for dhcp ...........
Page 17
User guide xvii configuring additional computers on the trusted network ............................................................ 38 configuring the trusted network with static addresses .........................................................39 configuring static routes ...........................
Page 18
Xviii watchguard firebox soho 6 denying ftp access to the trusted network interface ........................................................... 68 socks implementation for the soho 6 ................. 68 logging all allowed outbound traffic ....................... 70 enabling the mac address overrid...
Page 19
User guide xix creating a vpn tunnel to a soho 6 with an ipsec-compliant appliance ................................ 99 special considerations ...........................................99 configuring split tunneling ..................................100 using muvpn clients .............................
Page 20
Xx watchguard firebox soho 6 connecting and disconnecting the muvpn client .... 132 connecting the muvpn client .............................. 132 the muvpn client icon ........................................ 133 allowing the muvpn client through the personal firewall .................................
Page 21
User guide xxi chapter 11 using vpnforce ....................................... 147 using vpnforce to connect to your corporate network ............................................................ 147 configuring the optional network ........................ 148 using vpnforce and the muvpn client ...
Page 22
Xxii watchguard firebox soho 6.
Page 23
User guide 1 chapter 1 introduction the purpose of this guide is to help users of the watchguard ® firebox ® soho 6 and firebox ® soho 6tc set up and configure these appliances for secure access to the internet..
Page 24
Chapter 1: introduction 2 watchguard firebox soho 6 in this guide, the name soho 6 refers to both the soho 6 as well as the soho 6tc. The only difference between these two appliances is the vpn feature. Vpn is available as an upgrade option for the soho 6. The soho 6tc includes the vpn upgrade optio...
Page 25
User guide 3 package contents package contents make sure that the package contains all of these items: • soho 6 quickstart guide • user guide • livesecurity service ® activation card • hardware warranty card • ac adapter (12 v, 1.0-1.2 a) • straight-through ethernet cable • soho 6 security appliance...
Page 26
Chapter 1: introduction 4 watchguard firebox soho 6 the soho 6 controls all traffic between the external network (the internet) and the trusted network (your computers). All suspicious traffic is stopped. The rules and policies that identify the suspicious traffic are shown in “configuring incoming ...
Page 27
User guide 5 how information travels on the internet and reassembles the data; for example, data that may consist of an email message or a program file. Ip adds information to the packets that includes the destination and the handling requirements. Ip addresses an ip address identifies a computer on...
Page 28
Chapter 1: introduction 6 watchguard firebox soho 6 how the soho 6 processes information services a service is the group of protocols and port numbers for a specified program or type of application. The standard configuration of the soho 6 contains the correct settings for many standard services. Ne...
Page 29: Faster Processor
User guide 7 soho 6 hardware description faster processor the soho 6 has a new network processor that runs at a speed of 150 mhz. Ethernet and encryption technology are included. Ethernet ports the soho 6 has six 10/100 base tx ports. The ethernet ports have the labels 0 through 3, opt and wan. Soho...
Page 30: 100
Chapter 1: introduction 8 watchguard firebox soho 6 100 the 100 indicator is lit when a port is in use at 100 mb. The 100 indicator is not lit when a port is in use at 10 mb. Wan wan is lit while there is an active physical connection to the wan port. The indicator flashes when data flows through th...
Page 31: Reset Button
User guide 9 soho 6 hardware description reset button push the reset button to reset the soho 6 to the factory default configuration. See “resetting the soho 6 to the factory default settings” on page 26 for more information about this procedure. Wan port the wan port is for the external network int...
Page 32
Chapter 1: introduction 10 watchguard firebox soho 6.
Page 33
User guide 11 chapter 2 installation the soho 6 protects computers that are connected to it by ethernet cable. Follow the procedures in this chapter to install the soho 6 in your network. To install the soho 6, you must complete the following steps: • identify and record your tcp/ip settings. • disa...
Page 34
Chapter 2: installation 12 watchguard firebox soho 6 before you begin before you install the soho 6, you must have the following: • a computer with a 10/100baset ethernet i/o card installed and a web browser, such as netscape or internet explorer. • a functional internet connection–this connection m...
Page 35: And Then Press Enter.
User guide 13 before you begin microsoft windows 2000 and windows xp 1 select start => programs => accessories => command prompt. 2 at the prompt, type ipconfig /all and then press enter. 3 record the tcp/ip settings in the table provided. 4 click cancel. Microsoft windows nt 1 select start => progr...
Page 36
Chapter 2: installation 14 watchguard firebox soho 6 2 record the tcp/ip settings in the table provided. 3 exit the tcp/ip configuration screen. N ote if you must connect more than one computer to the trusted network behind the soho 6, determine the tcp/ip settings for each computer. Disabling the h...
Page 37: Click Proxies.
User guide 15 before you begin the following instructions show how to disable the http proxy setting in three browser applications. If a different browser is used, use the help menus of the browser program to find the necessary information. Netscape 4.7 1 open netscape. 2 select edit => preferences....
Page 38: Click The Advanced Tab.
Chapter 2: installation 16 watchguard firebox soho 6 internet explorer 5.0, 5.5, and 6.0 1 open internet explorer. 2 select tools => internet options. The internet options window appears. 3 click the advanced tab. 4 scroll down the page to http 1.1 settings. 5 clear all of the checkboxes. 6 click ok...
Page 39: Click Properties.
User guide 17 before you begin 4 click properties. The network connection properties dialog box appears. 5 double-click the internet protocol (tcp/ip) component. The internet protocol (tcp/ip) properties dialog box appears..
Page 40
Chapter 2: installation 18 watchguard firebox soho 6 6 select the obtain an ip address automatically and the obtain dns server address automatically checkboxes. 7 click ok to close the internet protocol (tcp/ip) properties dialog box. 8 click ok again to close the network connection properties dialo...
Page 41
User guide 19 physically connecting to the soho 6 cabling the soho 6 for one to four appliances a maximum of four computers, printers, scanners, or other network peripherals can connect directly to the soho 6. These connections use the four numbered ethernet ports (labeled 0-3). To connect a maximum...
Page 42
Chapter 2: installation 20 watchguard firebox soho 6 5 if you connect to the internet through a dsl modem or cable modem, reconnect the power supply to this device. The indicator lights flash and then stop. The modem is ready for use. 6 attach the ac adapter to the soho 6. Connect the ac adapter to ...
Page 43
User guide 21 physically connecting to the soho 6 the base model soho 6 includes a ten-seat license. This license allows a maximum of ten appliances on the trusted network to connect to the internet at the same time. There can be more than ten appliances on the trusted network, but the soho 6 will o...
Page 44
Chapter 2: installation 22 watchguard firebox soho 6 4 connect an ethernet cable between each of the computers and an uplink port on the ethernet hub. 5 if you connect to the internet through a dsl modem or cable modem, reconnect the power supply to this device. The indicator lights flash and then s...
Page 45
User guide 23 chapter 3 soho 6 basics the configuration of the soho 6 is made through web pages contained in the software of the soho 6. You can connect to these configuration pages with your web browser. Soho 6 system status page type the ip address of the trusted network in your browser window to ...
Page 46
Chapter 3: soho 6 basics 24 watchguard firebox soho 6 the system status page is the main configuration page of the soho 6. A display of information about the soho 6 configuration is shown. This information includes the following: • the firmware version • the serial number of the appliance • the stat...
Page 47: External Network
User guide 25 factory default settings • the status of the upgrade options • configuration information for the trusted network and the external network • configuration information for firewall settings (incoming services and outgoing services) • a reboot button to restart the soho 6 n ote if the ext...
Page 48: System Security
Chapter 3: soho 6 basics 26 watchguard firebox soho 6 system security the system security is disabled. The system administrator name and system administrator passphrase are not set. All computers on the trusted network can access the configuration pages. Soho 6 remote management is disabled. Vpn man...
Page 49
User guide 27 registering your soho 6 and activating the livesecurity service 6 connect the power supply. The pwr indicator is on and the reset is complete. The base model soho 6 the base model soho 6 includes a ten-seat license. This license allows a maximum of ten computers on the trusted network ...
Page 50
Chapter 3: soho 6 basics 28 watchguard firebox soho 6 n ote to activate the livesecurity service, your browser must have javascript enabled. If you have a user profile on the watchguard web site, enter your user name and password. If you do not have a user profile on the watchguard web site, create ...
Page 51: Click Reboot.
User guide 29 rebootting the soho 6 2 click reboot. Or 1 disconnect and reconnect the power supply. To reboot a soho 6 located on a remote system, use one of these methods: n ote the remote soho 6 must be configured to allow incoming http (web) or ftp traffic from the internet. See “configuring inco...
Page 52
Chapter 3: soho 6 basics 30 watchguard firebox soho 6.
Page 53
User guide 31 chapter 4 configure the network interfaces external network configuration when you configure the external network, you select the method of communication between the soho 6 and the isp. Make this selection based on the method of network address distribution in use by your isp. The poss...
Page 54
Chapter 4: configure the network interfaces 32 watchguard firebox soho 6 • if the assignment is static, all computers on the network have a permanently assigned ip address. There are no computers that have the same ip address. Most isps make dynamic ip address assignments through dhcp (dynamic host ...
Page 55: Network => External.
User guide 33 external network configuration configuration causes the isp to communicate with the soho 6 and not your computer. 1 type the ip address of the trusted network in your browser window to connect to the system status page of the soho 6. The default ip address is: http://192.168.111.1 2 fr...
Page 56: Network => External.
Chapter 4: configure the network interfaces 34 watchguard firebox soho 6 configuring the soho 6 external network for pppoe if your isp assigns ip addresses through pppoe, your pppoe login name and password are required to configure the soho 6. To configure the soho 6 for pppoe: 1 open your web brows...
Page 57: Click Submit.
User guide 35 external network configuration 5 type the pppoe login name and domain as well as the pppoe password supplied by your isp in the applicable fields. 6 type the time delay before inactive tcp connections are disconnected. 7 select the automatically restore lost connections checkbox. This ...
Page 58: Network => External.
Chapter 4: configure the network interfaces 36 watchguard firebox soho 6 to set the external network link speed: 1 type the ip address of the trusted network in your browser window to connect to the system status page of the soho 6. The default ip address is: http://192.168.111.1 2 from the navigati...
Page 59: Relay Checkbox.
User guide 37 configuring the trusted network 3 type the ip address and the subnet mask in the applicable fields. 4 select the enable dhcp server on the trusted network checkbox. 5 type the first ip address that is available for the computers that connect to the trusted network in the applicable fie...
Page 60
Chapter 4: configure the network interfaces 38 watchguard firebox soho 6 10 reboot the soho 6. The soho 6 will send all dhcp requests to the specified, remote dhcp server and relay the resulting ip addresses to the computers connected to the trusted network. If the soho 6 is unable to contact the sp...
Page 61: Network => Trusted.
User guide 39 configuring static routes configuring the trusted network with static addresses to disable the soho 6 dhcp server and make static address assignments, follow these steps: 1 type the ip address of the trusted network in your browser window to connect to the system status page of the soh...
Page 62: Network => Routes.
Chapter 4: configure the network interfaces 40 watchguard firebox soho 6 2 from the navigation bar at left, select network => routes. The routes page opens. 3 click add. The add route page opens. 4 from the type drop-down list, select either host or network. 5 type the ip address and the gateway of ...
Page 63: Click Submit.
User guide 41 viewing network statistics 6 click submit. To remove a route, select the route and click remove. Viewing network statistics the network statistics page gives information about network performance. This page is useful during troubleshooting. Follow these instructions to access the netwo...
Page 64: Network => Dynamicdns.
Chapter 4: configure the network interfaces 42 watchguard firebox soho 6 configuring the dynamic dns service this feature allows you to register the external ip address of the soho 6 with the dynamic dns (domain name server) service dyndns.Org. A dynamic dns service makes sure that the ip address at...
Page 65: Click Submit.
User guide 43 configuring the opt port upgrades n ote the soho 6 receives the ip address of members.Dyndns.Org when it connects to the time server. 5 click submit. Configuring the opt port upgrades the optional (opt) port of the soho 6 supports two upgrades: • dual isp port upgrade • vpnforce port u...
Page 66
Chapter 4: configure the network interfaces 44 watchguard firebox soho 6 the soho 6 uses two methods to determine if the external interface connection is down: • the status of the link to the nearest router • a ping to a specified location the soho 6 pings the default gateway or the location selecte...
Page 67: Network => Dual Isp.
User guide 45 configuring the opt port upgrades after you upgrade the soho 6 to activate this upgrade option, follow these instructions to complete the configuration: 1 connect one end of a straight-through ethernet cable to the optional port (opt), and connect the other end to the source of the sec...
Page 68: Click Submit.
Chapter 4: configure the network interfaces 46 watchguard firebox soho 6 8 click submit. Configuring the vpnforce™ port the vpnforce port upgrade activates the soho 6 optional port (opt) for connection to a second network on the trusted side. This option extends the protection of the firewall to inc...
Page 69: Interface Check Box.
User guide 47 configuring the opt port upgrades 3 to enable vpnforce, select the enable optional network checkbox. 4 type the ip address, dhcp server, and dhcp relay for the optional interface in the applicable fields. This is the same process for configuring the trusted network. See “configuring th...
Page 70: Click Submit.
Chapter 4: configure the network interfaces 48 watchguard firebox soho 6 7 click submit..
Page 71
User guide 49 chapter 5 administrative options use the soho 6 administration page to configure access to the soho 6. The system security, soho 6 remote management feature, and vpn manager access are configured from the administration page. The firmware updates, upgrade activation, and display of the...
Page 72
Chapter 5: administrative options 50 watchguard firebox soho 6 system security a passphrase prevents access to the configuration of the soho 6 by an unauthorized user on the trusted network. The use of a passphrase is important to the security of your network. N ote record the system administrator n...
Page 73: Click Submit.
User guide 51 the system security page 3 verify that the http server port is set to 80. 4 select the enable system security checkbox. 5 type a system administrator name and passphrase and then type the passphrase again to confirm it in the applicable fields. 6 click submit. Soho 6 remote management ...
Page 74: Algorithm Drop-Down List.
Chapter 5: administrative options 52 watchguard firebox soho 6 here is an example of how the remote management feature can be used. First, the remote computer connects to the soho 6 through a standard internet connection. Then the muvpn client software is activated. Finally, the muvpn client creates...
Page 75: 12 Click Yes.
User guide 53 setting up vpn manager access 9 after you have installed and configured the muvpn client, connect to the internet using dial-up networking or a lan or wan connection. From the windows desktop system tray, follow these steps: 10 verify that the muvpn client has been activated. If the mu...
Page 76: Click Submit.
Chapter 5: administrative options 54 watchguard firebox soho 6 2 from the navigation bar at left, select administration => vpn manager access. The vpn manager access page opens. 3 select the enable vpn manager access checkbox. 4 type the status passphrase and then type it again to confirm in the app...
Page 77: Administration => Update.
User guide 55 updating the firmware updating the firmware check regularly for soho 6 firmware updates on the watchguard web site: http://www.Watchguard.Com/support/sohoresources/ download the files that contain the firmware update. Save the files on your computer. Follow these instructions to transf...
Page 78: Click Update.
Chapter 5: administrative options 56 watchguard firebox soho 6 4 type the location of the firmware files on your computer or click browse andlocate the firmware files on your computer. 5 click update. Follow the instructions provided by the update wizard. N ote the update wizard requests a user name...
Page 79: Administration => Upgrade.
User guide 57 activating the soho 6 upgrade options 7 from the navigation bar at left, select administration => upgrade. The upgrade page opens. 8 paste the feature key in the applicable field. 9 click submit. Upgrade options seat licenses a seat license upgrade allows more connections between the t...
Page 80: Webblocker
Chapter 5: administrative options 58 watchguard firebox soho 6 firewall to include a telecommuter or a network in a remote office. Ipsec virtual private networking (vpn) the vpn upgrade is necessary to configure virtual private networking. The soho 6tc includes a vpn upgrade license key. The soho 6 ...
Page 81
User guide 59 viewing the configuration file 2 from the navigation bar at left, select administration => view configuration file. The view configuration file page opens..
Page 82
Chapter 5: administrative options 60 watchguard firebox soho 6.
Page 83
User guide 61 chapter 6 configure the firewall settings firewall settings the configuration settings of the soho 6 control the flow of traffic between the trusted network and the external network. The configuration you select depends on the types of risks that are acceptable for the trusted network....
Page 84
Chapter 6: configure the firewall settings 62 watchguard firebox soho 6 configuring incoming and outgoing services the default configuration of the soho 6 prevents the transmission of all packets from the external network to the trusted network. Change the configuration to select the types of traffi...
Page 85: Click Submit.
User guide 63 configuring incoming and outgoing services 3 locate a pre-configured service, such as ftp, web, or telnet. Then select either allow or deny from the drop-down list. The previous illustration shows the http service configured to allow incoming traffic. 4 type the trusted network ip addr...
Page 86
Chapter 6: configure the firewall settings 64 watchguard firebox soho 6 follow these steps to configure a custom service: 1 type the ip address of the trusted network in your browser window to connect to the system status page of the soho 6. The default ip address is: http://192.168.111.1 2 from the...
Page 87: Click Add.
User guide 65 blocking external sites n ote for a tcp port or a udp port, specify a port number. For a protocol, specify a protocol number. You cannot specify a port number for a protocol. 6 click add. The following steps determine how the service is filtered. 7 select allow or deny from the incomin...
Page 88: Firewall => Blocked Sites.
Chapter 6: configure the firewall settings 66 watchguard firebox soho 6 you can change the configuration to prevent access to specified internet sites. Follow these steps to configure the blocked sites: 1 from the navigation bar at left, select firewall => blocked sites. The blocked sites page opens...
Page 89: External Network Checkbox.
User guide 67 firewall options firewall options the previous sections described how to allow or deny complete classes of services. The firewall options page allows the configuration of general security policies. 1 type the ip address of the trusted network in your browser window to connect to the sy...
Page 90: Click Submit.
Chapter 6: configure the firewall settings 68 watchguard firebox soho 6 2 click submit. Denying ftp access to the trusted network interface you can configure the soho 6 to prevent ftp access to the computers on the trusted network by the computers on the external network. 1 select the do not allow f...
Page 91
User guide 69 firewall options n ote when a computer in the trusted network uses a socks-compatible application, other users on the trusted network have free access to the socks proxy on that computer. Disable socks on the soho 6 to prevent this security risk. See “disabling socks on the soho 6” on ...
Page 92: Click Submit.
Chapter 6: configure the firewall settings 70 watchguard firebox soho 6 when the socks-compatible application is not in use: 1 select the disable socks proxy checkbox. This disables the socks proxy feature of the soho 6. 2 click submit. To use the socks-compatible application: 1 clear the disable so...
Page 93: Network Checkbox.
User guide 71 creating an unrestricted pass through follow these steps to enable this option: 1 select the enable override mac address for the external network checkbox. 2 type the new mac address for the soho 6 external network in the applicable field. 3 click submit. N ote if the mac address for t...
Page 94: Click Submit.
Chapter 6: configure the firewall settings 72 watchguard firebox soho 6 3 select the enable pass through address checkbox. 4 type the ip address of the computer to connect to the pass through in the applicable field. This must be a public ip address. 5 click submit. N ote a pass through connection d...
Page 95
User guide 73 chapter 7 configure logging the soho 6 logging feature records a log of the events related to the security of the trusted, external, and optional networks. Communication with the watchguard webblocker database and incoming traffic are examples of events that are recorded. The log recor...
Page 96
Chapter 7: configure logging 74 watchguard firebox soho 6 viewing soho 6 log messages the soho 6 event log records a maximum of 150 log messages. If a new entry is added when the event log is full, the oldest log message is removed. The log messages include the time synchronizations between the soho...
Page 97: Logging => Wsep Logging.
User guide 75 setting up logging to a watchguard security event processor log host this option synchronizes the clock of the soho 6 to your computer: • click sync time with browser now. The soho 6 synchronizes the time at startup. Setting up logging to a watchguard security event processor log host ...
Page 98: Logging Checkbox.
Chapter 7: configure logging 76 watchguard firebox soho 6 3 select the enable watchguard security event processor logging checkbox. 4 type the ip address of the wsep server that is your log host in the applicable field. 5 type a passphrase in the log encryption key field and confirm the passphrase i...
Page 99: Logging => Syslog Logging.
User guide 77 setting up logging to a syslog host setting up logging to a syslog host this option sends the soho 6 log entries to a syslog host. Follow these steps to configure a syslog host: 1 type the ip address of the trusted network in your browser window to connect to the system status page of ...
Page 100: Logging => System Time.
Chapter 7: configure logging 78 watchguard firebox soho 6 n ote syslog traffic is not encrypted. Syslog messages that are sent through the internet decrease the security of the trusted network. Use a vpn tunnel to increase the security of syslog message traffic. If the syslog messages are sent throu...
Page 101: Submit.
User guide 79 setting the system time 3 select a time zone from the drop-down list. 4 select the adjust for daylight savings time checkbox. 5 click submit..
Page 102
Chapter 7: configure logging 80 watchguard firebox soho 6.
Page 103
User guide 81 chapter 8 soho 6 webblocker webblocker is an option for the soho 6 that allows the system administrator to control which web sites the users can access. How webblocker works webblocker uses a database of web site addresses, which is owned and maintained by surfcontrol. The database sho...
Page 104: Webblocker Users and Groups
Chapter 8: soho 6 webblocker 82 watchguard firebox soho 6 web site not in the webblocker database if the web site is not in the watchguard webblocker database, the web browser opens the page. Web site in the webblocker database if the site is in the watchguard webblocker database, the soho 6 examine...
Page 105: Webblocker => Settings.
User guide 83 purchasing and activating the soho 6 webblocker purchasing and activating the soho 6 webblocker to use watchguard soho 6 webblocker, you must purchase and enable the webblocker upgrade license key. See “activating the soho 6 upgrade options” on page 56 for information about upgrade lic...
Page 106: Click Submit.
Chapter 8: soho 6 webblocker 84 watchguard firebox soho 6 3 select the enable webblocker checkbox. 4 type a passphrase in the full access password field. The full access password allows a user to access all web sites until the password expires or the browser is closed. 5 type a value, in minutes, in...
Page 107
User guide 85 configuring the soho 6 webblocker 3 click new to create a group name and profile..
Page 108: Click Submit.
Chapter 8: soho 6 webblocker 86 watchguard firebox soho 6 4 define a group name and select the types of content to filter for this group. 5 click submit. A new groups page opens that shows the configuration changes. 6 to the right of the users field, click new. The new user page opens. 7 type a new ...
Page 109: Click Submit.
User guide 87 webblocker categories 8 use the group drop-down list to assign the new user to a given group. 9 click submit. N ote to remove a user or group, make a selection and click delete. Webblocker categories the webblocker database contains the following 14 categories: n ote a web site is only...
Page 110: Militant/extremist
Chapter 8: soho 6 webblocker 88 watchguard firebox soho 6 online sports, or financial betting, including non-monetary dares. Militant/extremist pictures or text advocating extremely aggressive or combative behavior or advocacy of unlawful political measures. Topic includes groups that advocate viole...
Page 111: Gross Depictions
User guide 89 webblocker categories gross depictions pictures or text describing anyone or anything that is either crudely vulgar, grossly deficient in civility or behavior, or shows scatological impropriety. Topic includes depictions of maiming, bloody figures, and indecent depiction of bodily func...
Page 112: Sexual Acts
Chapter 8: soho 6 webblocker 90 watchguard firebox soho 6 sexual acts pictures or text exposing anyone or anything involved in explicit sexual acts and/or lewd and lascivious behavior. Topic includes masturbation, copulation, pedophilia, as well as intimacy involving nude or partially nude people in...
Page 113
User guide 91 chapter 9 vpn—virtual private networking this chapter explains how to use the branch office vpn upgrade option for the soho 6. Why create a virtual private network? Use a vpn tunnel to make an inexpensive and secure connection between the computers in two separate locations. Expensive,...
Page 114
Chapter 9: vpn—virtual private networking 92 watchguard firebox soho 6 n ote ipsec-compatible appliances include the firebox soho 6, the firebox ii/iii, and the firebox vclass. • the data from your isp about the internet connections for each of the two ipsec-compatible appliances: - ip address - pri...
Page 115
User guide 93 what you need ip address table (example): item description assigned by external ip address the ip address that identifies the ipsec- compatible appliance to the internet. Isp site a: 207.168.55.2 site b: 68.130.44.15 external subnet mask the bitmask that shows which part of the ip addr...
Page 116
Chapter 9: vpn—virtual private networking 94 watchguard firebox soho 6 enabling the vpn upgrade to activate an upgrade option, you must enter a license key in the configuration of the soho 6. To receive a license key, purchase and activate an upgrade option at the livesecurity service web site. To a...
Page 117: Vpn => Manual Vpn.
User guide 95 setting up multiple soho 6 to soho 6 vpn tunnels setting up multiple soho 6 to soho 6 vpn tunnels an administrator of a soho 6 can configure a maximum of six vpn tunnels to other soho 6 devices. The vpn manager software can configure a larger number of soho 6 to soho 6 tunnels. To defi...
Page 118
Chapter 9: vpn—virtual private networking 96 watchguard firebox soho 6 4 type the name and shared secret for the vpn tunnel. The shared secret is a passphrase used by two ipsec-compatible appliances to encrypt and decrypt the data that goes through the vpn tunnel. The two appliances use the same pas...
Page 119
User guide 97 setting up multiple soho 6 to soho 6 vpn tunnels external ip address is dynamic, select aggressive mode. If the external ip address is static, use either mode. 7 select the local id type and the remote id type from the drop-down list. These must match the settings used on the remote ga...
Page 120: 18 Click Submit.
Chapter 9: vpn—virtual private networking 98 watchguard firebox soho 6 intervals to maintain the connection. If the tunnel connection closes, the soho 6 does a rekey to open the tunnel again. The generate ike keep alive messages checkbox is selected in the default configuration. Use the default phas...
Page 121
User guide 99 creating a vpn tunnel to a soho 6 with an ipsec-compliant appliance creating a vpn tunnel to a soho 6 with an ipsec-compliant appliance instructions that tell how to configure a vpn tunnel between a soho 6 and another ipsec-compatible appliance are available from the watchguard web sit...
Page 122: Vpn => Manual Vpn.
Chapter 9: vpn—virtual private networking 100 watchguard firebox soho 6 configuring split tunneling the split tunneling feature allows the system administrator to direct all internet traffic from the trusted network through the vpn tunnel. Without split tunneling, only traffic directed to the other ...
Page 123
User guide 101 viewing the vpn statistics allows users on the trusted network to access the networks connected by vpn tunnels to the local soho 6. If you purchase the vpnforce port upgrade, you also receive one muvpn connection to the optional network. Additional vpnforce port user licenses can be p...
Page 124
Chapter 9: vpn—virtual private networking 102 watchguard firebox soho 6 how do i get a static external ip address? The external ip address for your computer or network is assigned by your isp. Many isps use dynamic ip addresses so that their network is easier to configure and to make the connection ...
Page 125
User guide 103 frequently asked questions how do i obtain a vpn upgrade license key? You can purchase a license key for an upgrade from the watchguard web site: http://www.Watchguard.Com/sales/buyonline.Asp how do i enable a vpn tunnel? The instructions to help you enable a vpn tunnel are available ...
Page 126
Chapter 9: vpn—virtual private networking 104 watchguard firebox soho 6.
Page 127
User guide 105 chapter 10 muvpn clients the muvpn client is a software application that is installed on a remote computer. This application makes a secure connection from the remote computer to your protected network through an unsecured network. The muvpn client uses internet protocol security (ips...
Page 128: Click Add.
Chapter 10: muvpn clients 106 watchguard firebox soho 6 provides additional security for the remote users of your network by acting as a software firewall. This chapter shows how to install and configure the muvpn client on a remote computer. This chapter also includes information about the features...
Page 129: Click Submit.
User guide 107 configuring the soho 6 for muvpn clients 4 type a user name and a shared key in the applicable fields. The user name is used as the e-mail address and the passphrase is used as the pre-shared key for the muvpn client. 5 type the virtual ip address in the applicable field. The virual i...
Page 130
Chapter 10: muvpn clients 108 watchguard firebox soho 6 preparing the remote computers to use the muvpn client the muvpn client is only compatible with windows operating systems. The muvpn client can only be installed on computers that meet these system requirements: system requirements • a computer...
Page 131
User guide 109 preparing the remote computers to use the muvpn client n ote you cannot use the muvpn virtual adapter. Make sure this is disabled. Windows 98/me operating system setup this section describes how to install and configure the network components that are required for the windows 98/me op...
Page 132: Properties.
Chapter 10: muvpn clients 110 watchguard firebox soho 6 8 click ok to close the network window. Click cancel if you do not want to save the changes. 9 reboot the computer. Installing the client for microsoft networks the client for microsoft networks must be installed before you can configure networ...
Page 133: Then Click Properties.
User guide 111 preparing the remote computers to use the muvpn client 3 click the windows setup tab. The windows setup dialog box appears. The operating system searches for installed components. 4 select the communications checkbox and then click ok. The copying files dialog box appears. The operati...
Page 134: Wins Resolution Checkbox.
Chapter 10: muvpn clients 112 watchguard firebox soho 6 n ote the dns server on the private network behind the soho 6 must be the first server in the list. 7 click the wins configuration tab and then select the enable wins resolution checkbox. 8 type the ip address of the wins server in the wins ser...
Page 135: Add.
User guide 113 preparing the remote computers to use the muvpn client 2 double-click the network icon. The network window appears. 3 click the services tab and then click add. 4 select remote access services from the list and then click ok. 5 enter the path to the windows nt install files or insert ...
Page 136: Click Properties.
Chapter 10: muvpn clients 114 watchguard firebox soho 6 3 click the protocols tab and then select the tcp/ip protocol. 4 click properties. The microsoft tcp/ip properties window appears. 5 click the dns tab and then click add. 6 enter the ip address of your dns server in the applicable field. To add...
Page 137: Click Install.
User guide 115 preparing the remote computers to use the muvpn client - file and printer sharing for microsoft networks - client for microsoft networks installing the internet protocol (tcp/ip) network component from the connection window, networking tab: 1 click install. The select network componen...
Page 138: Properties.
Chapter 10: muvpn clients 116 watchguard firebox soho 6 configuring the wins and dns settings the remote computer must be able to communicate with the wins servers and the dns servers. These servers are located on the trusted network that is protected by the soho 6. From the connection window, netwo...
Page 139: And Then Click Ok.
User guide 117 preparing the remote computers to use the muvpn client 9 click ok to close the advanced tcp/ip settings window, click ok to close the internet protocol (tcp/ip) properties window, and then click ok. 10 click cancel to close the connection window. Windows xp operating system setup this...
Page 140: Then Click Ok.
Chapter 10: muvpn clients 118 watchguard firebox soho 6 3 select the internet protocol (tcp/ip) network protocol and then click ok. Installing the file and printer sharing for microsoft networks from the connection window, networking tab: 1 click install. The select network component type window app...
Page 141: Click Advanced.
User guide 119 preparing the remote computers to use the muvpn client 3 click advanced. The advanced tcp/ip settings window appears. 4 click the dns tab and then, from the section labeled dns server addresses, in order of use, click add. The tcp/ip dns server window appears. 5 enter the ip address o...
Page 142: Click Next.
Chapter 10: muvpn clients 120 watchguard firebox soho 6 installing and configuring the muvpn client the muvpn installation files are available at the watchguard web site: http://www.Watchguard.Com/support n ote to install and configure the muvpn client, you must have local administrator rights on th...
Page 143: Click Finish.
User guide 121 installing and configuring the muvpn client 8 do not change the default selections. Click next. The start copying files window appears. 9 click next to install the files. When the dni_vapmp file is installed, a command prompt window appears. This is normal. When the file has been inst...
Page 144: Select The Secure Option.
Chapter 10: muvpn clients 122 watchguard firebox soho 6 2 double-click the muvpn client icon. The security policy editor window appears. N ote the zonealarm personal firewall may display alert messages. For more information regarding zonealarm see “the zonealarm personal firewall” on page 139. 3 sel...
Page 145: Mask Fields.
User guide 123 installing and configuring the muvpn client 8 when you set the subnet and mask addresses, you define whether or not an muvpn user can access the internet through the tunnel. If you want to access only the trusted network, type the trusted network address in both the subnet and mask fi...
Page 146: Select Security Policy.
Chapter 10: muvpn clients 124 watchguard firebox soho 6 defining the my identity settings to define the my identity settings, follow these steps. 1 expand the network security policy to display the new entry. The my identity and security policy entries appear. 2 select security policy. The security ...
Page 147: Checkbox and Then Click Ok.
User guide 125 installing and configuring the muvpn client 6 select options => global policy settings. The global policy settings window appears. 7 select the allow to specify internal network address checkbox and then click ok. The internal network ip address field appears in the my identity sectio...
Page 148: 13 Click Pre-Shared Key.
Chapter 10: muvpn clients 126 watchguard firebox soho 6 8 select none from the select certificate drop-down list. 9 select e-mail address from the id type drop-down list and then enter the user name defined on the soho 6 in the applicable field. 10 select disabled from the virtual adapter drop-down ...
Page 149: Policy.
User guide 127 installing and configuring the muvpn client 15 type the exact text of the muvpn client passphrase entered on the soho 6 and then click ok. N ote both the pre-shared key and the e-mail address must exactly match the system passphrase and system administrator name settings of the soho 6...
Page 150: Select Proposal 1.
Chapter 10: muvpn clients 128 watchguard firebox soho 6 4 select pre-shared key from the authentication method drop- down list. N ote phase 1 values must be as specified in the following steps. Phase 2 values must match the settings of the firebox soho 6. 5 select des from the encrypt alg drop-down ...
Page 151: In The Seconds Field and
User guide 129 installing and configuring the muvpn client 10 select both from the sa life drop-down list. 11 type 86400 in the seconds field and 8192 in the kbytes field. 12 select none from the compression drop-down list. This is the default setting. The soho 6 does not support compression. 13 sel...
Page 152: Finish Option.
Chapter 10: muvpn clients 130 watchguard firebox soho 6 uninstalling the muvpn client follow these directions to uninstall the muvpn client. Watchguard recommends that you use the windows add/ remove programs tool. Disconnect all existing tunnels and dial-up connections. Reboot the remote computer. ...
Page 153: Click Add.
User guide 131 configuring the soho 6 for muvpn clients using pocket pc n ote the zonealarm personal firewall settings are stored in the following directories by default. Windows 98: c:\windows\internet logs\ windows nt and 2000: c:\winnt\internet logs\ windows xp: c:\windows\internet logs to remove...
Page 154: Click Submit.
Chapter 10: muvpn clients 132 watchguard firebox soho 6 5 type the virtual ip address in the applicable field. The virual ip address is the same as the ip address on the trusted network configuration page. This address is used by the remote computer to connect to the soho 6. 6 from the authenticatio...
Page 155: Activate Security Policy.
User guide 133 connecting and disconnecting the muvpn client 2 if the muvpn client is not active, right-click the icon and select activate security policy. For information about how to determine the status of the muvpn icon, see “the muvpn client icon” on page 133. From the windows desktop: 3 select...
Page 156
Chapter 10: muvpn clients 134 watchguard firebox soho 6 the muvpn client is ready to establish a secure, muvpn tunnel connection. The red bar on the right of the icon indicates that the client is transmitting unsecured data..
Page 157: Activated And Connected
User guide 135 connecting and disconnecting the muvpn client activated and connected the muvpn client has established at least one secure, muvpn tunnel connection, but is not transmitting data. Activated, connected and transmitting unsecured data the muvpn client has established at least one secure,...
Page 158
Chapter 10: muvpn clients 136 watchguard firebox soho 6 allowing the muvpn client through the personal firewall the following programs are associated with the muvpn client. To establish the muvpn tunnel, you must allow these programs through the personal firewall: • muvpnconnect.Exe • ireike.Exe the...
Page 159: Security Policy.
User guide 137 connecting and disconnecting the muvpn client from the new program alert window: 1 select the remember this answer the next time i use this program checkbox and the click yes. With the option selected, the zonealarm personal firewall will allow this program to access the internet each...
Page 160: Select Log Viewer.
Chapter 10: muvpn clients 138 watchguard firebox soho 6 monitoring the muvpn client connection the log viewer and the connection monitor are installed with the muvpn client. These tools can be used to monitor the muvpn connection and to diagnose problems that may occur. Using the log viewer the log ...
Page 161
User guide 139 the zonealarm personal firewall - when a phase 2 sa connection has not yet been made - when a phase 2 sa connection cannot be made • a key indicates that the connection has a phase 2 sa. This connection may also have a phase 1 sa. • an animated black line underneath a key indicates th...
Page 162: Zonealarm Help.
Chapter 10: muvpn clients 140 watchguard firebox soho 6 this alert appears whenever one of your programs attempts to access the internet or your local network. This alert ensures that no information leaves your computer without your authorization. The zonealarm personal firewall provides a brief tut...
Page 163: Use This Program Checkbox.
User guide 141 the zonealarm personal firewall in the example above, the internet explorer web browser application has been launched. The application attempts to access the user’s home page. The program that actually needs to pass through the firewall is “iexplore.Exe”. To allow this program access ...
Page 164: Select Shutdown Zonealarm.
Chapter 10: muvpn clients 142 watchguard firebox soho 6 shutting down zonealarm from the windows desktop system tray: 1 right-click the zonealarm icon shown at right. 2 select shutdown zonealarm. The zonealarm window appears. 3 click yes. Uninstalling zonealarm from the windows desktop: 1 select sta...
Page 165: Click Yes.
User guide 143 troubleshooting tips 3 click yes. The select uninstall method window appears. 4 make sure automatic is selected and then click next. 5 click finish. N ote the remove shared component window may appear. During the initial installation of zonealarm, some files were installed that could ...
Page 166: Security Policy.
Chapter 10: muvpn clients 144 watchguard firebox soho 6 when the muvpn client is not in use, both zonealarm and the muvpn client should be deactivated. From the windows desktop system tray: 1 reboot your computer. 1 right-click the muvpn client icon and then select deactivate security policy. The mu...
Page 167: Select Map Network Drive.
User guide 145 troubleshooting tips transmission of the login information. Make sure you deactivate zonealarm each time you disconnect the muvpn connection. Is the muvpn tunnel working? The muvpn client icon appears in the windows desktop system tray once the application has been launched. The muvpn...
Page 168
Chapter 10: muvpn clients 146 watchguard firebox soho 6 the mapped drive appears in the my computer window. Even if you select the reconnect at logon checkbox, the mapped drive will only appear the next time you start your computer if the computer is directly connected to the network. I am sometimes...
Page 169
User guide 147 chapter 11 using vpnforce the vpnforce tm upgrade activates the soho 6 optional interface. The optional interface is labeled opt on the soho 6 appliance. The optional interface provides remote users with a separate network, called the optional network, behind the soho 6. The optional ...
Page 170
Chapter 11: using vpnforce 148 watchguard firebox soho 6 n ote to use this upgrade option, you must access your corporate network through a vpn tunnel from the soho 6 to a watchguard firebox appliance or other ipsec compliant appliance. For information about the vpn upgrade option, see “vpn—virtual ...
Page 171
User guide 149 using vpnforce to connect to your corporate network 3 select the enable optional network checkbox. 4 type the ip address and the subnet mask of the optional interface in the appropriate fields. Make sure that this network is different from that of the trusted network. 5 to configure t...
Page 172: Relay Checkbox.
Chapter 11: using vpnforce 150 watchguard firebox soho 6 8 to configure the dhcp relay server, select the enable dhcp relay checkbox. 9 type the ip address of the dhcp relay server in the applicable field. 10 click submit. The soho 6 will send all dhcp requests to the specified, remote dhcp server a...
Page 173
User guide 151 using vpnforce and the muvpn client upgrades to enforce your corporate using vpnforce and the muvpn client upgrades to enforce your corporate policy if you want to require remote users to use the muvpn client to connect to the protected network, you must perform the procedures in this...
Page 174: Click The Add Button.
Chapter 11: using vpnforce 152 watchguard firebox soho 6 3 click the add button. The edit muvpn client page appears. 4 type a user name and a passphrase in the applicable fields. The user name is used as the e-mail address and the passphrase is used as the pre-shared key for the muvpn client..
Page 175: 10 Click Submit.
User guide 153 using vpnforce and the muvpn client upgrades to enforce your corporate 5 type an unused ip address from the trusted network, which will be used by the muvpn client computer when connecting to the soho 6 in the virtual ip address field. 6 select md5-hmac from the authentication algorit...
Page 176: Select The Secure Option.
Chapter 11: using vpnforce 154 watchguard firebox soho 6 3 type a unique name for the new connection. If this will be a unique policy for a specific user, enter a unique name to help identify it. For example, you may want to include the actual name of the end user. 4 select the secure option. This i...
Page 177
User guide 155 using vpnforce and the muvpn client upgrades to enforce your corporate 10 select ip address from the id type drop list and then type the ip address of the optional interface in the available field. Defining the security policy settings follow these instructions to define the security ...
Page 178: Select My Identity.
Chapter 11: using vpnforce 156 watchguard firebox soho 6 2 select my identity. The my identity and internet interface settings appear to the right. 3 select options => global policy settings. The global policy settings dialog box appears..
Page 179: Checkbox and Then Click Ok.
User guide 157 using vpnforce and the muvpn client upgrades to enforce your corporate 4 select the allow to specify internal network address checkbox and then click ok. The internal network ip address field appears among the my identity settings. 5 select none from the select certificate drop list. ...
Page 180: Policy.
Chapter 11: using vpnforce 158 watchguard firebox soho 6 12 type the exact text of the muvpn client passphrase entered on the firebox soho 6 appliance and then click ok. Defining phase 1 and phase 2 settings follow these instructions to define the phase 1 and phase 2 settings. Make certain that sett...
Page 181: Select Proposal 1.
User guide 159 using vpnforce and the muvpn client upgrades to enforce your corporate 4 select pre-shared key from the authentication method drop list. N ote these values must match exactly those entered in the firebox soho 6 appliance. 5 select des from the encrypt alg drop list and select sha-1 fr...
Page 182
Chapter 11: using vpnforce 160 watchguard firebox soho 6 10 select both from the sa life drop list and then type 86400 in the seconds field and 8192 in the kbytes field. 11 select none from the compression drop list. This is the default setting. The soho 6 firebox appliance does not support compress...
Page 183
User guide 161 using the muvpn client to secure a wireless network using the muvpn client to secure a wireless network the vpnforce upgrade and the muvpn client can also be used to prevent wireless "drive by" hacking. This configuration requires an ethernet connection from the wireless access point ...
Page 184
Chapter 11: using vpnforce 162 watchguard firebox soho 6.
Page 185
User guide 163 chapter 12 support resources troubleshooting tips if you have problems during the installation and the configuration of your soho 6, refer to this information. General what do the pwr, status, and mode lights signify on the soho 6? When the pwr light is lit, the soho 6 is connected to...
Page 186
Chapter 12: support resources 164 watchguard firebox soho 6 if the mode light is blinks: the soho 6 cannot connect to the external network. Possible causes of this problem include: • the soho 6 did not receive an ip address for the external interface from the dhcp server. • the wan port is not conne...
Page 187
User guide 165 troubleshooting tips i can't get a certain soho 6 feature to work with a dsl modem. Some dsl routers implement nat firewalls. An external network connection through an appliance that supplies nat causes problems with webblocker and the performance of ipsec. When a soho 6 connects to t...
Page 188
Chapter 12: support resources 166 watchguard firebox soho 6 i can connect to the system status page; why can’t i browse the internet? If you can access the configuration pages, but not the internet, there is a problem with the connection from the soho 6 to the internet. • make sure the cable modem o...
Page 189: Network => Trusted.
User guide 167 troubleshooting tips 2 type the ip address of the trusted network in your browser window to connect to the system status page of the soho 6. The default ip address is: http://192.168.111.1 3 from the navigation bar at left, select network => trusted. 4 clear the enable dhcp server che...
Page 190: Click Submit.
Chapter 12: support resources 168 watchguard firebox soho 6 6 click submit. How do i set up and disable webblocker? 1 type the ip address of the trusted network in your browser window to connect to the system status page of the soho 6. The default ip address is: http://192.168.111.1 2 from the navig...
Page 191: Click Submit.
User guide 169 troubleshooting tips how do i allow incoming ip, or uncommon tcp and udp protocols? Record the ip address of the computer that is to receive the incoming data and the number of the new ip protocol. Follow these steps: 1 type the ip address of the trusted network in your browser window...
Page 192: Press Enter.
Chapter 12: support resources 170 watchguard firebox soho 6 soho 6 configuration file. These steps apply to using a command prompt with windows 2000 or xp. 1 configure the firewall settings of the soho 6 to allow an incoming ftp service to the trusted ip address of the appliance. For information on ...
Page 193
User guide 171 troubleshooting tips make sure that the two appliances use the same encryption and authentication method. How do i set up my soho 6 for vpn manager access? This requires the add-on product, watchguard vpn manager, which is purchased separately and used with the watchguard firebox syst...
Page 194
Chapter 12: support resources 172 watchguard firebox soho 6 contacting technical support online documentation and faqs documentation in pdf format, tutorials, and faqs are available on the watchguard web site: https://support.Watchguard.Com/advancedfaqs/ special notices the online help system is not...
Page 195
User guide 173 index 100 indicator 8 a add gateway page 95, 100 add muvpn client page 106 add route page 40 automatically restore lost connections checkbox 35 b blocked sites page 66 blocked sites, configuring 66 c cables correct setup 165 included in package 3 required for installation 12 cabling f...
Page 196
174 watchguard firebox soho 6 f faqs 172 file and printer sharing for microsoft networks and windows xp 118 file and printer sharing for microsoft networks, installing 115 filter traffic page 62 firewall incoming traffic page 169 firewall options page 67 firewalls, described 3 firmware updating 55 v...
Page 197
User guide 175 m mac address of soho 6 166 mac address override 70 macintosh operating system 165 manual vpn page 95, 100 mode indicator 8 mode light 163 muvpn client adding 106 allowing through firewall 136 and vpnforce option 151 and wireless networks 161 configuring 121 configuring soho 6 for 106...
Page 198
176 watchguard firebox soho 6 optional network configuration 148 routes 40, 46 soho 6 administration 49 syslog logging 77 system security 49, 50 system status 23, 28, 29, 33, 34, 36, 39, 41, 42, 45, 46, 50, 53, 55, 56, 58, 62, 64, 67, 71, 74, 75, 77, 78, 83, 84, 95, 100, 101, 106, 131, 166, 167, 168...
Page 199
User guide 177 configuring access to 49 configuring for dynamic addresses 32 configuring for pppoe 34 configuring for static addressing 32 configuring vpn tunnel with 99 default factory settings 25 described 2 firmware updates 55 front view 7 hardware 6 installing 11–22 logging 73–79 mac address of ...
Page 200
178 watchguard firebox soho 6 purchasing 171 setting up access to 53–54 setting up soho 6 for 171 vpn manager access viewing status of 24 vpn manager access page 53, 54 vpn statistics page 101 vpn tunnels, setting up multiple 95 vpn upgrade described 58 enable 94 obtaining 103 vpn upgrade option 91 ...