- DL manuals
- 3Com
- Switch
- 3824 - SuperStack 3 Switch
- Implementation Manual
3Com 3824 - SuperStack 3 Switch Implementation Manual
Summary of 3824 - SuperStack 3 Switch
Page 1
Http://www.3com.Com/ part no. Dua1740-0baa01 published may 2003 switch 3812 and switch 3824 implementation guide 3c17401, 3c17400
Page 2
3com corporation 5500 great america parkway, santa clara, california 95052-8145 copyright © 2003, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation...
Page 3: Ontents
C ontents a bout t his g uide conventions 8 related documentation 9 documentation comments 9 product registration 10 1 s witch f eatures o verview what is management software? 11 switch features explained 11 automatic ip configuration 12 port security 12 aggregated links 12 auto-negotiation 12 multi...
Page 4
Aggregated links and your switch 21 aggregated link — manual configuration example 24 3 u sing m ulticast f iltering what is an ip multicast? 27 benefits of multicast 28 multicast filtering 28 multicast filtering and your switch 29 igmp multicast filtering 30 4 u sing r esilience f eatures resilienc...
Page 5: Lan
Traffic re-marking 52 traffic prioritization 52 traffic queues 56 important qos considerations 56 default qos configurations 58 7 s tatus m onitoring and s tatistics rmon 59 what is rmon? 59 the rmon groups 59 benefits of rmon 61 rmon and the switch 61 alarm events 62 8 s etting u p v irtual lan s w...
Page 6: Ip A
A c onfiguration r ules configuration rules for gigabit ethernet 75 configuration rules for fast ethernet 76 configuration rules with full duplex 77 b n etwork c onfiguration e xamples simple network configuration examples 80 desktop switch example 80 advanced network configuration examples 81 impro...
Page 7: Bout
A bout t his g uide this guide describes the features of the 3com switch 3812 (12-port, managed gigabit) and 3com switch 3824 (24-port, managed gigabit). It outlines how to use these features to optimize the performance of your network. The term switch 3812 and switch 3824 is used when referring to ...
Page 8
8 a bout t his g uide conventions table 1 and table 2 list conventions that are used throughout this guide. Table 1 notice icons icon notice type description information note information that describes important features or instructions caution information that alerts you to potential loss of data o...
Page 9
Related documentation 9 related documentation in addition to this guide, each switch documentation set includes the following: ■ switch 3812 and switch 3824 getting started guide this guide contains: ■ all the information you need to install and set up the switch in its default state ■ information o...
Page 10
10 a bout t his g uide ■ document part number (on the title page) ■ page number (if appropriate) example: ■ switch 3812 and switch 3824 implementation guide ■ part number: dua1740-0baa01 ■ page 25 please note that we can only respond to comments and questions about 3com product documentation at this...
Page 11: Witch
1 s witch f eatures o verview this chapter contains introductory information about the switch 3812 and switch 3824 management software and supported features. It covers the following topics: ■ what is management software? ■ switch features explained for detailed descriptions of the web interface ope...
Page 12
12 c hapter 1: s witch f eatures o verview automatic ip configuration your switch can have its ip information automatically configured using a dhcp server. Alternatively, you can manually configure the ip information. For more information about how the automatic ip configuration feature works, see c...
Page 13
Switch features explained 13 for details of the auto-negotiation features supported by your switch, please refer to the management quick reference guide that accompanies your switch. Duplex full duplex mode allows packets to be transmitted and received simultaneously and, in effect, doubles the pote...
Page 14
14 c hapter 1: s witch f eatures o verview ■ disable the less efficient paths. ■ enable one of the less efficient paths if the most efficient path fails. Rstp is an enhanced version of the stp feature and is enabled by default. Rstp can restore a network connection quicker than the legacy stp featur...
Page 15
Switch features explained 15 broadcast storm control broadcast storm control is a system that monitors the level of broadcast traffic on that port. If the broadcast traffic level rises to a pre-defined number of frames per second (threshold), the broadcast traffic on the port is blocked until the br...
Page 16
16 c hapter 1: s witch f eatures o verview ■ the configuration can only be restored onto a device which has the same physical connections and configuration, as when the configuration was initially saved. The restore operation will be unsuccessful if the physical configuration of the device is differ...
Page 17: Ptimizing
2 o ptimizing b andwidth there are many ways you can optimize the bandwidth on your network and improve network performance. If you utilize certain switch features you can provide the following benefits to your network and end users: ■ increased bandwidth ■ quicker connections ■ faster transfer of d...
Page 18
18 c hapter 2: o ptimizing b andwidth a link do not support auto-negotiation, both ends must be manually set to full duplex or half duplex accordingly. Ports operating at 1000 mbps support full duplex mode only. Flow control all switch ports support flow control, which is a mechanism that prevents p...
Page 19
Aggregated links 19 aggregated links aggregated links are connections that allow devices to communicate using up to eight member links in parallel. Aggregated links provide the following benefits: ■ they can potentially increase the bandwidth of a connection. The capacity of the multiple links is co...
Page 20
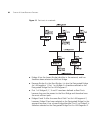
20 c hapter 2: o ptimizing b andwidth failed — almost instantaneously. As a result, aggregated link configurations are extremely resilient and fault-tolerant. Figure 2 dynamic reassignment of traffic flows the key benefits of 802.3ad link aggregation are: ■ automatic configuration — network manageme...
Page 21
Aggregated links 21 member of an aggregated link for switch a in error, lacp (if it is enabled) will detect this and place the port in the aggregated link for switch b, thus overriding the manual configuration. Figure 3 aggregated link — example ■ lacp automatic aggregations — if lacp detects at lea...
Page 22
22 c hapter 2: o ptimizing b andwidth ■ the switch only supports a maximum of eight active ports in any individual aggregation. ■ if multiple links are connected between a unit and more than six other devices as shown in figure 4 , only six of the devices will be assigned to aggregated links. The re...
Page 23
Aggregated links 23 ■ the member link ports can be mixed media, that is fiber and/or twisted pair ports within the same aggregated link. ■ the member link ports must have the same configuration. ■ member links must retain the same groupings at both ends of an aggregated link. For example, the config...
Page 24
24 c hapter 2: o ptimizing b andwidth ■ before removing an entire aggregated link, you must disable all the aggregated link ports or disconnect all the links, except one — if you do not, a loop may be created. ■ when manually creating an aggregated link between two devices, the ports in the aggregat...
Page 25
Aggregated links 25 figure 6 an 8 gbps aggregated link between two switch units to manually set up this configuration: 1 prepare ports 2, 4, 6 and 8 on the upper switch for aggregated links. To do this: a check that the ports have an identical configuration using your preferred management interface....
Page 26
26 c hapter 2: o ptimizing b andwidth.
Page 27: Sing
3 u sing m ulticast f iltering multicast filtering improves the performance of networks that carry multicast traffic. This chapter explains multicasts, multicast filtering, and how multicast filtering can be implemented on your switch. It covers the following topics: ■ what is an ip multicast? ■ mul...
Page 28
28 c hapter 3: u sing m ulticast f iltering a multicast packet is identified by the presence of a multicast group address in the destination address field of the packet’s ip header. Benefits of multicast the benefits of using ip multicast are that it: ■ enables the simultaneous delivery of informati...
Page 29
Multicast filtering 29 figure 7 the effect of multicast filtering multicast filtering and your switch your switch provides automatic multicast filtering support using igmp (internet group management protocol) snooping. It also supports igmp query mode. Snooping mode snooping mode allows your switch ...
Page 30
30 c hapter 3: u sing m ulticast f iltering you would enable query mode if you wish to run multicast sessions in a network that does not contain any igmp routers (or queriers). This command will configure the switch to automatically negotiate with compatible devices on vlan 1 to become the querier. ...
Page 31
Igmp multicast filtering 31 enabling igmp multicast learning you can enable or disable multicast learning and igmp querying using the snoopmode command on the web interface. For more information about enabling igmp multicast learning, please refer to the management interface reference guide supplied...
Page 32
32 c hapter 3: u sing m ulticast f iltering.
Page 33: Sing
4 u sing r esilience f eatures setting up resilience on your network helps protect critical links against failure, protects against network loops, and reduces network downtime to a minimum. This chapter explains the features supported by the switch that provide resilience for your network. It covers...
Page 34
34 c hapter 4: u sing r esilience f eatures resilience feature overview table 3 lists the key differences between each feature, so you can evaluate the benefits of each to determine which feature is most suitable for your network. Table 3 spanning tree protocols — key differences 3com recommends tha...
Page 35
What is stp? 35 the protocol is a part of the ieee std 802.1d, 1998 edition bridge specification. To explain stp more effectively, your switch will be referred to as a bridge. Rapid spanning tree protocol (rstp) the rapid spanning tree (rstp) is an enhanced spanning tree feature. Rstp implements the...
Page 36
36 c hapter 4: u sing r esilience f eatures as an example, figure 8 shows a network containing three lan segments separated by three bridges. With this configuration, each segment can communicate with the others using two paths. Without stp enabled, this configuration creates loops that cause the ne...
Page 37
How stp works 37 if a link failure is detected, as shown in figure 10 , the stp process reconfigures the network so that traffic from lan segment 2 flows through bridge b. Figure 10 traffic flowing through bridge b stp determines which is the most efficient path between each bridged segment and a sp...
Page 38
38 c hapter 4: u sing r esilience f eatures ■ each port to have a cost. This specifies the efficiency of each link, usually determined by the bandwidth of the link — the higher the cost, the less efficient the link. Table 4 shows the default port costs for a switch. Table 4 default port costs stp ca...
Page 39
How stp works 39 bridge is configured to forward traffic only between its root port and the designated bridge ports for the respective network segments. All other ports are blocked, which means that they are prevented from receiving or forwarding traffic. Stp reconfiguration once the network topolog...
Page 40
40 c hapter 4: u sing r esilience f eatures figure 11 port costs in a network ■ bridge a has the lowest bridge identifier in the network, and has therefore been selected as the root bridge. ■ because bridge a is the root bridge, it is also the designated bridge for lan segment 1. Port 1 on bridge a ...
Page 41
How stp works 41 ■ bridge c has been selected as the designated bridge for lan segment 3, because it offers the lowest root path cost for lan segment 3: ■ the route through bridges c and b costs 200 (c to b=100, b to a=100) ■ the route through bridges y and b costs 300 (y to b=200, b to a=100). Port...
Page 42
42 c hapter 4: u sing r esilience f eatures figure 12 stp configurations.
Page 43
Using stp on a network with multiple vlans 43 using stp on a network with multiple vlans the ieee std 802.1d, 1998 edition does not take into account vlans when it calculates stp information — the calculations are only performed on the basis of physical connections. For this reason, some network con...
Page 44
44 c hapter 4: u sing r esilience f eatures.
Page 45: Sing
5 u sing the s witch d atabase what is the switch database? The switch database is used by the switch to determine where a packet should be forwarded to, and which port should transmit the packet if it is to be forwarded. The database contains a list of entries — each entry contains three items: ■ m...
Page 46
46 c hapter 5: u sing the s witch d atabase switch database entry states databases entries can have three states: ■ learned — the switch has placed the entry into the switch database when a packet was received from an endstation. Note that: ■ learned entries are removed (aged out) from the switch da...
Page 47: Sing
6 u sing t raffic p rioritization using the traffic prioritization capabilities of your switch provides quality of service (qos) to your network through increased reliability of data delivery. You can prioritize traffic on your network to ensure that high priority data is transmitted with minimum de...
Page 48
48 c hapter 6: u sing t raffic p rioritization for detailed descriptions of the command line interface (cli) commands that you require to manage the switch please refer to the management interface reference guide supplied in html format on the cd-rom that accompanies your switch. What is traffic pri...
Page 49
How traffic prioritization works 49 traffic prioritization in your switch may be applied dependent upon following factor: ■ the level of service requested by an end-station — the transmitting end-station sets the priority of each stream of traffic. Received traffic at the switch is forwarded through...
Page 50
50 c hapter 6: u sing t raffic p rioritization table 5 attributes on which incoming traffic can be classified (identified) traffic marking after traffic has been identified through classification, it must be marked to ensure that other devices such as layer 2 switches or routers on the network know ...
Page 51
How traffic prioritization works 51 determines the level of service that type of traffic should receive. Refer to table 6 for an example of how different traffic types can be mapped to the eight ieee 802.1p priority levels. Table 6 ieee recommendation for mapping 802.1p priority levels to 802.1d tra...
Page 52
52 c hapter 6: u sing t raffic p rioritization uses 64 values that map to user-defined service levels, allowing you to establish more control over network traffic. Advantages of diffserv over ieee 802.1d are: ■ no extra tags are required in the packet. ■ dscp uses the ip header of a packet and there...
Page 53
How traffic prioritization works 53 appropriate egress port(s). When the packet reaches the head of its queue and is about to be transmitted the device determines whether or not the egress port is tagged for that vlan. If it is, then the new 802.1p tag is used in the extended 802.1d header. The ieee...
Page 54
54 c hapter 6: u sing t raffic p rioritization figure 14 shows how traffic prioritization works at layer 2. The switch will check a packet received at the ingress port for ieee 802.1d traffic classification, and then prioritize it based upon the ieee 802.1p value (service levels) in that tag. It is ...
Page 55
How traffic prioritization works 55 figure 15 advanced traffic prioritization and marking 1 the packet received at the ingress port is checked for any of the supported traffic classification methods (dscp, ethertype, protocol) to identify the traffic. 2 the classification in an incoming packet will ...
Page 56
56 c hapter 6: u sing t raffic p rioritization ■ otherwise, if there are no other classifiers except the 802.1p tag, then the packet will pass through the switch with the original 802.1p priority tag. ■ otherwise, if the received packet does not have an 802.1p tag, then a default 802.1p tag (which i...
Page 57
Important qos considerations 57 ■ has eight traffic queues, but it is important to note that not all switches have the same number of priority queues. ■ qos is about providing a consistent, predictable data delivery service. It should not be used as an alternative to deploying sufficient bandwidth. ...
Page 58
58 c hapter 6: u sing t raffic p rioritization default qos configurations the switch is pre-configured with the following settings: table 7 default traffic classifiers configured in your switch classifier name classifier type protocol identifier ieee 802.Id priority dscp marking 3com nbx voice-lan e...
Page 59: Tatus
7 s tatus m onitoring and s tatistics this chapter contains details of the remote monitoring ( rmon ) feature that assists you with status monitoring and statistics. For detailed descriptions of the web interface operations and the command line interface (cli) commands that you require to manage the...
Page 60
60 c hapter 7: s tatus m onitoring and s tatistics statistics the statistics group provides traffic and error statistics showing packets, bytes, broadcasts, multicasts and errors on a lan segment or vlan. Information from the statistics group is used to detect changes in traffic and error patterns i...
Page 61
Benefits of rmon 61 benefits of rmon using the rmon features of your switch has three main advantages: ■ it improves your efficiency using rmon allows you to remain at one workstation and collect information from widely dispersed lan segments or vlans. This means that the time taken to reach a probl...
Page 62
62 c hapter 7: s tatus m onitoring and s tatistics when using the rmon features of the switch, note the following: ■ after the default sessions are created, they have no special status. You can delete or change them as required. ■ the greater the number of rmon sessions, the greater the burden on th...
Page 63: Etting
8 s etting u p v irtual lan s setting up virtual lans (vlans) on your switch increases the efficiency of your network by dividing the lan into logical, rather than physical, segments which are easier to manage. This chapter explains more about the concept of vlans and explains how they can be implem...
Page 64
64 c hapter 8: s etting u p v irtual lan s figure 16 a network setup showing three vlans benefits of vlans the main benefit of vlans is that they provide a network segmentation system that is far more flexible than any traditional network. Using vlans also provides you with three other benefits: ■ v...
Page 65
Vlans and your switch 65 ■ vlans help to control traffic with traditional networks, congestion can be caused by broadcast traffic that is directed to all network devices whether they require it or not. Vlans increase the efficiency of your network because each vlan can be set up to contain only thos...
Page 66
66 c hapter 8: s etting u p v irtual lan s figure 17 two vlans connected via a router creating new vlans if you want to move a port from the default vlan to another vlan, you must first define information about the new vlan on your switch. Vlans: tagged and untagged membership your switch supports 8...
Page 67
Vlan configuration examples 67 identify which packets belong in which vlans. To communicate between vlans a router must be used. Vlan configuration examples this section contains examples of vlan configurations. It describes how to set up your switch to support simple untagged and tagged connections...
Page 68
68 c hapter 8: s etting u p v irtual lan s to set up the configuration shown in figure 18 : 1 configure the vlans define vlan 2 on the switch. Vlan 1 is the default vlan and already exists. 2 add ports to the vlans add ports 10, 11 and 12 of the switch as untagged members to vlan 2. You can use the ...
Page 69
Vlan configuration examples 69 to set up the configuration shown in figure 19 : 1 configure the vlans on switch 1 define vlan 2. Vlan 1 is the default vlan and already exists. 2 add endstation ports on switch 1 to the vlans place the endstation ports in the appropriate vlans as untagged members. 3 a...
Page 70
70 c hapter 8: s etting u p v irtual lan s.
Page 71: Sing
9 u sing a utomatic ip c onfiguration this chapter explains more about ip addresses and how the automatic configuration option works. It covers the following topics: ■ how your switch obtains ip information ■ how automatic ip configuration works ■ important considerations for detailed information on...
Page 72
72 c hapter 9: u sing a utomatic ip c onfiguration how your switch obtains ip information your switch has two ways to obtain its ip address information: ■ automatic ip configuration (default) — the switch attempts to configure itself by communicating with a dhcp server on the network. ■ manual ip co...
Page 73
Important considerations 73 the dynamic nature of automatically configured ip information means that a switch may change its ip address whilst in use. Server support your switch has been tested to interoperate with dhcp servers that use the following operating systems: ■ microsoft windows 2000 serve...
Page 74
74 c hapter 9: u sing a utomatic ip c onfiguration.
Page 75: Onfiguration
A c onfiguration r ules configuration rules for gigabit ethernet gigabit ethernet is designed to run over several media: ■ single-mode fiber optic cable, with connections up to 5 km (3.1 miles). Support for distances over 5 km is supported depending on the module specification. ■ multimode fiber opt...
Page 76
76 a ppendix a: c onfiguration r ules configuration rules for fast ethernet the topology rules for 100 mbps fast ethernet are slightly different to those for 10 mbps ethernet. Figure 20 illustrates the key topology rules and provides examples of how they allow for large-scale fast ethernet networks....
Page 77
Configuration rules for fast ethernet 77 ■ a total network span of 325 m (1066 ft) is allowed in single-repeater topologies (one hub stack per wiring closet with a fiber link to the collapsed backbone). For example, a 225 m (738 ft) fiber link from a repeater to a router or switch, plus a 100 m (328...
Page 78
78 a ppendix a: c onfiguration r ules.
Page 79: Etwork
B n etwork c onfiguration e xamples this chapter contains the following sections: ■ simple network configuration examples ■ desktop switch example ■ advanced network configuration examples ■ improving the resilience of your network ■ enhancing the performance of your network.
Page 80
80 a ppendix b: n etwork c onfiguration e xamples simple network configuration examples the following illustrations show some simple examples of how the switch 3812 and switch 3824 can be used in your network. Desktop switch example the example in figure 21 shows how a switch 3812 and switch 3824 ca...
Page 81
Advanced network configuration examples 81 advanced network configuration examples this section shows some network examples that illustrate how you can set up your network for optimum performance using some of the features supported by your switch. Improving the resilience of your network figure 22 ...
Page 82
82 a ppendix b: n etwork c onfiguration e xamples enhancing the performance of your network figure 23 shows how you can set your network up to enhance its performance. All ports are auto-negotiating and will therefore pass data across the network at the optimum available speed and duplex mode. Flow ...
Page 83: Ip A
C ip a ddressing this chapter provides some background detail on the ip information that needs to be assigned to your switch to enable you to manage it across a network. The topics covered are: ■ ip addresses ■ subnets and subnet masks ■ default gateways ip addressing is a vast topic and there are w...
Page 84
84 a ppendix c: ip a ddressing 192.168.100.X (where x is a number between 1 and 254) with a subnet mask 255.255.255.0. These suggested ip addresses are part of a group of ip addresses that have been set aside specially for use “in house” only. Caution: if your network has a connection to the externa...
Page 85
Ip addresses 85 referred to as a field or an octet. Decimal notation converts the value of each field into a decimal number, and the fields are separated by dots. Figure 25 dotted decimal notation for ip addresses the decimal value of an octet whose bits are all 1s is 255. Network portion the locati...
Page 86
86 a ppendix c: ip a ddressing subnets and subnet masks you can divide your ip network into sub-networks also known as subnets. Support for subnets is important because the number of bits assigned to the device part of an ip address limits the number of devices that may be addressed on any given net...
Page 87
Subnets and subnet masks 87 as shown in this example, the 32 bits of an ip address and subnet mask are usually written using an integer shorthand. This notation translates four consecutive 8-bit groups (octets) into four integers that range from 0 through 255. The subnet mask in the example is writt...
Page 88
88 a ppendix c: ip a ddressing the subnet mask 255.255.255.255 is reserved as the default broadcast address. Default gateways a gateway is a device on your network which is used to forward ip packets to a remote destination. An alternative name for a gateway is a router. “remote” refers to a destina...
Page 89: Lossary
G lossary 3com network supervisor the 3com network management application used to manage 3com’s networking solutions. 10base-t the ieee specification for 10 mbps ethernet over category 3, 4 or 5 twisted pair cable. 100base-fx the ieee specification for 100 mbps fast ethernet over fiber-optic cable. ...
Page 90
90 g lossary fast ethernet is 100 mbps, and the bandwidth of gigabit ethernet is 1000 mbps. Baud the signalling rate of a line, that is, the number of transitions (voltage or frequency changes) made per second. Also known as line speed. Bridge a device that interconnects two lans of a different type...
Page 91
91 endstation a computer, printer or server that is connected to a network. Ethernet a lan specification developed jointly by xerox, intel and digital equipment corporation. Ethernet networks use csma/cd to transmit packets at a rate of 10 mbps over a variety of cables. Ethernet address see mac addr...
Page 92
92 g lossary http hypertext transfer protocol. This is a set of rules for exchanging files (text, graphic images, sound, video, and other multimedia files) on the world wide web. Ieee institute of electrical and electronics engineers. This american organization was founded in 1963 and sets standards...
Page 93
93 determine which if any multicast traffic needs to be forwarded to each of its subnetworks. Intranet an intranet is an organization wide network using internet protocols such as web services, tcp/ip, http and html. An intranet is normally used for internal communication and information, and is not...
Page 94
94 g lossary mac address media access control address; also called hardware or physical address. A layer 2 address associated with a particular network device. Most devices that connect to a lan have a mac address assigned to them as they are used to identify other devices in a network. Mac addresse...
Page 95
95 rapid spanning tree protocol an enhanced version of the spanning tree protocol that allows faster determination of spanning tree topology throughout the bridged network. Repeater a simple device that regenerates lan traffic so that the transmission distance of that signal can be extended. Repeate...
Page 96
96 g lossary stp see spanning tree protocol (stp). Subnet mask a subnet mask is used to divide the device part of the ip address into two further parts. The first part identifies the subnet number. The second part identifies the device on that subnet. Switch a device that interconnects several lans ...
Page 97
97 wan wide area network. A communications network that covers a wide area. A wan can cover a large geographic area, and may contain several lans within it..
Page 98
98 g lossary.
Page 99: Ndex
I ndex 99 i ndex a addresses classes 85 ip 83 aggregated links 12, 19 aging time, definition 46 alarm events 62 alarms (rmon group) 60, 61 automatic ip configuration 72 auto-negotiation 12, 18 b backup 15 bandwidth 17 bpdus. See bridge protocol data units bridge identifier 37 bridge protocol data un...
Page 100
100 i ndex l learned sdb entries 46 m mac (media access control) addresses ip address 84 manual configuration 72 masks subnet 86 matrix (rmon group) 61 max age 39 multicast filtering 27 igmp 30 multicasts, description 27 n network addresses 83 network configuration examples 80, 81 non-aging learned ...
Page 101
I ndex 101 t topology rules for fast ethernet 76 topology rules with full duplex 77 traffic prioritization 14, 47, 48 advanced 54 basic 52 classification 49 default configurations 58 differentiated services 50, 51 diffserv code point (dscp) 51 ieee std 802.1d, 1998 edition 50 marking 50 queues 56 re...
Page 102
102 i ndex.