- DL manuals
- 3Com
- Switch
- 4500 PWR
- Configuration Manual
3Com 4500 PWR Configuration Manual
Summary of 4500 PWR
Page 1
3com switch 4500 family configuration guide switch 4500 26-port switch 4500 50-port switch 4500 pwr 26-port switch 4500 pwr 50-port product version: v03.03.00 manual version: 6w101-20090811 www.3com.Com 3com corporation 350 campus drive, marlborough, ma, usa 01752 3064.
Page 2
Copyright © 2006-2009, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from 3com corporation. 3com corporation reserv...
Page 3
About this manual organization 3com switch 4500 family configuration guide is organized as follows: part contents 1 login introduces the ways to log into an ethernet switch and cli related configuration. 2 configuration file management introduces configuration file and the related configuration. 3 v...
Page 4
Part contents 27 udp helper introduces udp helper and the related configuration. 28 snmp-rmon introduces the configuration for network management through snmp and rmon 29 ntp introduces ntp and the related configuration. 30 ssh introduces ssh2.0 and the related configuration. 31 file system manageme...
Page 5
Gui conventions convention description button names are inside angle brackets. For example, click . [ ] window names, menu items, data table and field names are inside square brackets. For example, pop up the [new user] window. / multi-level menus are separated by forward slashes. For example, [file...
Page 6: Table of Contents
I table of contents 1 logging in to an ethernet switch ············································································································1-1 logging in to an ethernet switch·····································································································...
Page 7
Ii switch configuration························································································································4-2 modem connection establishment ·········································································································4-2 5 cli configu...
Page 8
1-1 1 logging in to an ethernet switch go to these sections for information you are interested in: z logging in to an ethernet switch z introduction to the user interface logging in to an ethernet switch to manage or configure a switch 4500, you can log in to it in one of the following three methods...
Page 9
1-2 table 1-1 description on user interface user interface applicable user port used remarks aux users logging in through the console port console port each switch can accommodate one aux user. Vty telnet users and ssh users ethernet port each switch can accommodate up to five vty users. One user in...
Page 10
1-3 common user interface configuration follow these steps to configure common user interface: to do… use the command… remarks lock the current user interface lock optional available in user view a user interface is not locked by default. Specify to send messages to all user interfaces/a specified u...
Page 11
2-1 2 logging in through the console port go to these sections for information you are interested in: z introduction z setting up a login environment for login through the console port z console port login configuration z console port login configuration with authentication mode being none z console...
Page 12
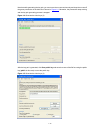
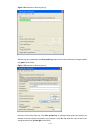
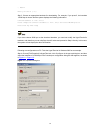
2-2 2) if you use a pc to connect to the console port, launch a terminal emulation utility (such as terminal in windows 3.X or hyperterminal in windows 9x/windows 2000/windows xp. The following assumes that you are running windows xp) and perform the configuration shown in figure 2-2 through figure ...
Page 13
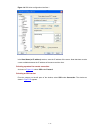
2-3 figure 2-4 set port parameters 3) turn on the switch. You will be prompted to press the enter key if the switch successfully completes post (power-on self test). The prompt appears after you press the enter key. 4) you can then configure the switch or check the information about the switch by ex...
Page 14
2-4 configuration remarks set the maximum number of lines the screen can contain optional by default, the screen can contain up to 24 lines. Set history command buffer size optional by default, the history command buffer can contain up to 10 commands. Set the timeout time of a user interface optiona...
Page 15
2-5 to do… use the command… remarks set the maximum number of lines the screen can contain screen-length screen-length optional by default, the screen can contain up to 24 lines. You can use the screen-length 0 command to disable the function to display information in pages. Set the history command ...
Page 16
2-6 changes made to the authentication mode for console port login takes effect after you quit the command-line interface and then log in again. Console port login configuration with authentication mode being none configuration procedure follow these steps to configure console port login with the au...
Page 17
2-7 network diagram figure 2-5 network diagram for aux user interface configuration (with the authentication mode being none) configuration pc running telnet ethernet ge1/0/1 configuration procedure # enter system view. System-view # enter aux user interface view. [sysname] user-interface aux 0 # sp...
Page 18
2-8 to do… use the command… remarks enter system view system-view — enter aux user interface view user-interface aux 0 — configure to authenticate users using the local password authentication-mode password required by default, users logging in to a switch through the console port are not authentica...
Page 19
2-9 system-view # enter aux user interface view. [sysname] user-interface aux 0 # specify to authenticate users logging in through the console port using the local password. [sysname-ui-aux0] authentication-mode password # set the local password to 123456 (in plain text). [sysname-ui-aux0] set authe...
Page 21
2-11 z set the service type of the local user to terminal and the command level to 2. Z configure to authenticate the users in the scheme mode. Z the baud rate of the console port is 19,200 bps. Z the screen can contain up to 30 lines. Z the history command buffer can store up to 20 commands. Z the ...
Page 22
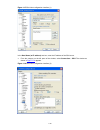
2-12 [sysname-ui-aux0] history-command max-size 20 # set the timeout time of the aux user interface to 6 minutes. [sysname-ui-aux0] idle-timeout 6 after the above configuration, you need to modify the configuration of the terminal emulation utility running on the pc accordingly in the dialog box sho...
Page 23: Logging In Through Telnet
3-1 3 logging in through telnet go to these sections for information you are interested in: z introduction z telnet configuration with authentication mode being none z telnet configuration with authentication mode being password introduction switch 4500 supports telnet. You can manage and maintain a...
Page 24
3-2 configuration description configure the protocols the user interface supports optional by default, telnet and ssh protocol are supported. Set the commands to be executed automatically after a user log in to the user interface successfully optional by default, no command is executed automatically...
Page 25
3-3 to do… use the command… remarks set the history command buffer size history-command max-size value optional the default history command buffer size is 10, that is, the history command buffer of a user can store up to 10 commands by default. Set the timeout time of the vty user interface idle-tim...
Page 26
3-4 to improve security and prevent attacks to the unused sockets, tcp 23 and tcp 22, ports for telnet and ssh services respectively, will be enabled or disabled after corresponding configurations. Z if the authentication mode is none, tcp 23 will be enabled, and tcp 22 will be disabled. Z if the au...
Page 27
3-5 network diagram figure 3-1 network diagram for telnet configuration (with the authentication mode being none) configuration procedure # enter system view. System-view # enter vty 0 user interface view. [sysname] user-interface vty 0 # configure not to authenticate telnet users logging in to vty ...
Page 28
3-6 when the authentication mode is password, the command level available to users logging in to the user interface is determined by the user privilege level command. Configuration example network requirements assume current user logins through the console port and the current user level is set to t...
Page 29
3-7 telnet configuration with authentication mode being scheme configuration procedure follow these steps to configure telnet with the authentication mode being scheme: to do… use the command… remarks enter system view system-view — enter one or more vty user interface views user-interface vty first...
Page 30
3-8 refer to the aaa part of this manual for information about aaa, radius. Configuration example network requirements assume current user logins through the console port and the user level is set to the administrator level (level 3). Perform the following configurations for users logging in to vty ...
Page 31
3-9 # set the maximum number of lines the screen can contain to 30. [sysname-ui-vty0] screen-length 30 # set the maximum number of commands the history command buffer can store to 20. [sysname-ui-vty0] history-command max-size 20 # set the timeout time to 6 minutes. [sysname-ui-vty0] idle-timeout 6 ...
Page 32
3-10 figure 3-5 network diagram for telnet connection establishment configuration pc running telnet ethernet workstation server workstation ethernet port ethernet switch 4) launch telnet on your pc, with the ip address of vlan-interface 1 of the switch as the parameter, as shown in figure 3-6 . Figu...
Page 33
3-11 telnetting to another switch from the current switch you can telnet to another switch from the current switch. In this case, the current switch operates as the client, and the other operates as the server. If the interconnected ethernet ports of the two switches are in the same lan segment, mak...
Page 34: Logging In Using A Modem
4-1 4 logging in using a modem go to these sections for information you are interested in: z introduction z configuration on the switch side z modem connection establishment introduction the administrator can log in to the console port of a remote switch using a modem through public switched telepho...
Page 35
4-2 you can verify your configuration by executing the at&v command. The configuration commands and the output of different modems may differ. Refer to the user manual of the modem when performing the above configuration. Switch configuration after logging in to a switch through its console port by ...
Page 36
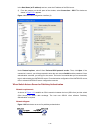
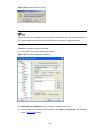
4-3 figure 4-1 establish the connection by using modems console port pstn telephone line modem serial cable telephone number of the romote end: 82882285 modem modem 4) launch a terminal emulation utility on the pc and set the telephone number to call the modem directly connected to the switch, as sh...
Page 37
4-4 figure 4-3 set the telephone number figure 4-4 call the modem 5) if the password authentication mode is specified, enter the password when prompted. If the password is correct, the prompt (such as ) appears. You can then configure or manage the switch. You can also enter the character ? At anyti...
Page 38: Cli Configuration
5-1 5 cli configuration when configuring cli, go to these sections for information you are interested in: z introduction to the cli z command hierarchy z cli views z cli features introduction to the cli a command line interface (cli) is a user interface to interact with a switch. Through the cli on ...
Page 39
5-2 z monitor level (level 1): commands at this level are mainly used to maintain the system and diagnose service faults, and they cannot be saved in configuration file. Such commands include debugging and terminal. Z system level (level 2): commands at this level are mainly used to configure servic...
Page 40
5-3 to do… use the command… remarks enter system view system-view — configure the level of a command in a specific view command-privilege level level view view command required z you are recommended to use the default command level or modify the command level under the guidance of professional staff...
Page 41
5-4 to avoid misoperations, the administrators are recommended to log in to the device by using a lower privilege level and view device operating parameters, and when they have to maintain the device, they can switch to a higher level temporarily; when the administrators need to leave for a while or...
Page 42
5-5 to do… use the command… remarks switch to a specified user level super [ level ] required execute this command in user view. Z if no user level is specified in the super password command or the super command, level 3 is used by default. Z for security purpose, the password entered is not display...
Page 43
5-6 table 5-1 cli views view available operation prompt example enter method quit method user view display operation status and statistical information of the switch enter user view once logging into the switch. Execute the quit command to log out of the switch. System view configure system paramete...
Page 44
5-7 view available operation prompt example enter method quit method ftp client view configure ftp client parameters [ftp] execute the ftp command in user view. Sftp client view configure sftp client parameters sftp-client> execute the sftp command in system view. Mst region view configure mst regio...
Page 45
5-8 view available operation prompt example enter method quit method radius scheme view configure radius scheme parameters [sysname-radius-1 ] execute the radius scheme command in system view. Isp domain view configure isp domain parameters [sysname-isp-aaa 123.Net] execute the domain command in sys...
Page 46
5-9 cd change current directory clock specify the system clock cluster run cluster command copy copy from one file to another debugging enable system debugging functions delete delete a file dir list files on a file system display display current system information 2) enter a command, a space, and a...
Page 47
5-10 table 5-2 display-related operations operation function press stop the display output and execution of the command. Press any character except , , /, +, and - when the display output pauses stop the display output. Press the space key get to the next page. Press get to the next line. Command hi...
Page 48
5-11 table 5-3 common error messages error message remarks the command does not exist. The keyword does not exist. The parameter type is wrong. Unrecognized command the parameter value is out of range. Incomplete command the command entered is incomplete. Too many parameters the parameters entered a...
Page 49: Management Interface
6-1 6 logging in through the web-based network management interface go to these sections for information you are interested in: z introduction z establishing an http connection z configuring the login banner z enabling/disabling the web server introduction switch 4500 has a web server built in. It e...
Page 50
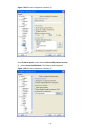
6-2 3) establish an http connection between your pc and the switch, as shown in figure 6-1 . Figure 6-1 establish an http connection between your pc and the switch 4) log in to the switch through ie. Launch ie on the web-based network management terminal (your pc) and enter the ip address of the man...
Page 51
6-3 configuration example network requirements z a user logs in to the switch through web. Z the banner page is desired when a user logs into the switch. Network diagram figure 6-3 network diagram for login banner configuration configuration procedure # enter system view. System-view # configure the...
Page 52
6-4 to do… use the command… remarks enter system view system-view — enable the web server ip http shutdown required by default, the web server is enabled. Disable the web server undo ip http shutdown required to improve security and prevent attack to the unused sockets, tcp 80 port (which is for htt...
Page 53: Logging In Through Nms
7-1 7 logging in through nms go to these sections for information you are interested in: z introduction z connection establishment using nms introduction you can also log in to a switch through a network management station (nms), and then configure and manage the switch through the agent software on...
Page 54: Packets
8-1 8 configuring source ip address for telnet service packets go to these sections for information you are interested in: z overview z configuring source ip address for telnet service packets z displaying source ip address configuration overview you can configure source ip address or source interfa...
Page 55
8-2 operation command description specify a source interface for telnet server telnet-server source-interface interface-type interface-number optional specify source ip address for telnet client telnet source-ip ip-address optional specify a source interface for telnet client telnet source-interface...
Page 56: User Control
9-1 9 user control go to these sections for information you are interested in: z introduction z controlling telnet users z controlling network management users by source ip addresses z controlling web users by source ip address refer to the acl part for information about acl. Introduction you can co...
Page 57
9-2 z if no acl is configured on the vty user interface, users are not controlled when establishing a telnet connection using this user interface. Z if an acl is configured on the vty user interface, there will be two possibilities: if the packets for establishing a telnet connection match the acl r...
Page 59
9-4 z defining an acl z applying the acl to control users accessing the switch through snmp to control whether an nms can manage the switch, you can use this function. Prerequisites the controlling policy against network management users is determined, including the source ip addresses to be control...
Page 60
9-5 network diagram figure 9-2 network diagram for controlling snmp users using acls switch 10.110.100.46 host a ip network host b 10.110.100.52 configuration procedure # define a basic acl. System-view [sysname] acl number 2000 [sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0 [sysname-...
Page 62
9-7 [sysname-acl-basic-2030] quit # apply acl 2030 to only permit the web users sourced from the ip address of 10.110.100.52 to access the switch. [sysname] ip http acl 2030
Page 63: Table of Contents
I table of contents 1 configuration file management···············································································································1-1 introduction to configuration file····································································································...
Page 64
1-1 1 configuration file management when configuring configuration file management, go to these sections for information you are interested in: z introduction to configuration file z configuration task list introduction to configuration file a configuration file records and stores user configuration...
Page 65
1-2 z when saving the current configuration, you can specify the file to be a main or backup or normal configuration file. Z when removing a configuration file from a switch, you can specify to remove the main or backup configuration file. Or, if it is a file having both main and backup attribute, y...
Page 66
1-3 when you use the save safely command to save the configuration file, if the switch reboots or the power fails during the saving process, the switch initializes itself in the following two conditions when it starts up next time: z if a configuration file with the extension .Cfg exists in the flas...
Page 68
1-5 the configuration file must use .Cfg as its extension name and the startup configuration file must be saved at the root directory of the switch. Displaying switch configuration to do… use the command… remarks display the initial configuration file saved in the flash of a switch display saved -co...
Page 69: Table of Contents
I table of contents 1 vlan overview ··········································································································································1-1 vlan overview·············································································································...
Page 70: Vlan Overview
1-1 1 vlan overview this chapter covers these topics: z vlan overview z port-based vlan vlan overview introduction to vlan the traditional ethernet is a broadcast network, where all hosts are in the same broadcast domain and connected with each other through hubs or switches. Hubs and switches, whic...
Page 71
1-2 figure 1-1 a vlan implementation advantages of vlans compared with the traditional ethernet, vlan enjoys the following advantages. Z broadcasts are confined to vlans. This decreases bandwidth consumption and improves network performance. Z network security is improved. Because each vlan forms a ...
Page 72
1-3 tag is encapsulated after the destination mac address and source mac address to show the information about vlan. Figure 1-3 format of vlan tag as shown in figure 1-3 , a vlan tag contains four fields, including the tag protocol identifier (tpid), priority, canonical format indicator (cfi), and v...
Page 73
1-4 z independent vlan learning (ivl), where the switch maintains an independent mac address forwarding table for each vlan. The source mac address of a packet received in a vlan on a port is recorded to the mac address forwarding table of this vlan only, and packets received in a vlan are forwarded...
Page 74
1-5 a hybrid port allows the packets of multiple vlans to be sent untagged, but a trunk port only allows the packets of the default vlan to be sent untagged. The three types of ports can coexist on the same device. Assigning an ethernet port to specified vlans you can assign an ethernet port to a vl...
Page 75
1-6 table 1-2 packet processing of a trunk port processing of an incoming packet for an untagged packet for a tagged packet processing of an outgoing packet z if the port has already been added to its default vlan, tag the packet with the default vlan tag and then forward the packet. Z if the port h...
Page 76: Vlan Configuration
2-1 2 vlan configuration when configuring vlan, go to these sections for information you are interested in: z vlan configuration z configuring a port-based vlan vlan configuration vlan configuration task list complete the following tasks to configure vlan: task remarks basic vlan configuration requi...
Page 77
2-2 z vlan 1 is the system default vlan, which needs not to be created and cannot be removed, either. Z the vlan you created in the way described above is a static vlan. On the switch, there are dynamic vlans which are registered through gvrp. For details, refer to “gvrp” part of this manual. Z when...
Page 78
2-3 the operation of enabling/disabling a vlan’s vlan interface does not influence the physical status of the ethernet ports belonging to this vlan. Displaying vlan configuration to do... Use the command... Remarks display the vlan interface information display interface vlan-interface [ vlan-id ] d...
Page 79
2-4 assigning an ethernet port to a vlan you can assign an ethernet port to a vlan in ethernet port view or vlan view. Z you can assign an access port to a vlan in either ethernet port view or vlan view. Z you can assign a trunk port or hybrid port to a vlan only in ethernet port view. 1) in etherne...
Page 80
2-5 configuring the default vlan for a port because an access port can belong to only one vlan, its default vlan is the vlan it resides in and cannot be configured. This section describes how to configure a default vlan for a trunk or hybrid port. Follow these steps to configure the default vlan for...
Page 81
2-6 network diagram figure 2-1 network diagram for vlan configuration switcha switchb pc1 pc2 ge1/0/1 ge1/0/2 ge1/0/10 ge1/0/11 ge1/0/12 ge1/0/13 server2 server1 configuration procedure z configure switch a. # create vlan 100, specify its descriptive string as dept1, and add gigabitethernet 1/0/1 to...
Page 82
2-7 [switcha-gigabitethernet1/0/2] port trunk permit vlan 100 [switcha-gigabitethernet1/0/2] port trunk permit vlan 200 # configure gigabitethernet 1/0/10 of switch b. [switchb] interface gigabitethernet 1/0/10 [switchb-gigabitethernet1/0/10] port link-type trunk [switchb-gigabitethernet1/0/10] port...
Page 83: Table of Contents
I table of contents 1 ip addressing configuration····················································································································1-1 ip addressing overview·············································································································...
Page 84: Ip Addressing Configuration
1-1 1 ip addressing configuration the term ip address used throughout this chapter refers to ipv4 address. For details about ipv6 address, refer to ipv6 management. When configuring ip addressing, go to these sections for information you are interested in: z ip addressing overviewconfiguring ip addr...
Page 85
1-2 table 1-1 ip address classes and ranges class address range remarks a 0.0.0.0 to 127.255.255.255 the ip address 0.0.0.0 is used by a host at bootstrap for temporary communication. This address is never a valid destination address. Addresses starting with 127 are reserved for loopback test. Packe...
Page 86
1-3 subnetting. When designing your network, you should note that subnetting is somewhat a tradeoff between subnets and accommodated hosts. For example, a class b network can accommodate 65,534 (2 16 – 2. Of the two deducted class b addresses, one with an all-ones host id is the broadcast address an...
Page 87
1-4 z a newly specified ip address overwrites the previous one if there is any. Z the ip address of a vlan interface must not be on the same network segment as that of a loopback interface on a device. Configuring static domain name resolution follow these steps to configure static domain name resol...
Page 88
1-5 network diagram figure 1-3 network diagram for ip address configuration configuration procedure # configure an ip address for vlan-interface 1. System-view [switch] interface vlan-interface 1 [switch-vlan-interface1] ip address 129.2.2.1 255.255.255.0 static domain name resolution configuration ...
Page 89
1-6 round-trip min/avg/max = 2/3/5 ms.
Page 90
2-1 2 ip performance optimization configuration when optimizing ip performance, go to these sections for information you are interested in: z ip performance overview z configuring ip performance optimization z displaying and maintaining ip performance optimization configuration ip performance overvi...
Page 91
2-2 z synwait timer: when sending a syn packet, tcp starts the synwait timer. If no response packet is received within the synwait timer interval, the tcp connection cannot be created. Z finwait timer: when a tcp connection is changed into fin_wait_2 state, the finwait timer is started. If no fin pa...
Page 92
2-3 z if the destination of a packet is local while the transport layer protocol of the packet is not supported by the local device, the device sends a “protocol unreachable” icmp error packet to the source. Z when receiving a packet with the destination being local and transport layer protocol bein...
Page 93
2-4 to do… use the command… remarks display icmp traffic statistics display icmp statistics display the current socket information of the system display ip socket [ socktype sock-type ] [task-id socket-id] display the forwarding information base (fib) entries display fib display the fib entries matc...
Page 94: Table of Contents
I table of contents 1 voice vlan configuration························································································································1-1 voice vlan overview···············································································································...
Page 95: Voice Vlan Configuration
1-1 1 voice vlan configuration when configuring voice vlan, go to these sections for information you are interested in: z voice vlan overview z voice vlan configuration z displaying and maintaining voice vlan z voice vlan configuration example voice vlan overview voice vlans are allocated specially ...
Page 96
1-2 figure 1-1 network diagram for ip phones as shown in figure 1-1 , the ip phone needs to work in conjunction with the dhcp server and the ncp to establish a path for voice data transmission. An ip phone goes through the following three phases to become capable of transmitting voice data. 1) after...
Page 97
1-3 z an untagged packet carries no vlan tag. Z a tagged packet carries the tag of a vlan. To set an ip address and a voice vlan for an ip phone manually, just make sure that the voice vlan id to be set is consistent with that of the switch and the ncp is reachable to the ip address to be set. How s...
Page 98
1-4 configuring voice vlan assignment mode of a port a port can work in automatic voice vlan assignment mode or manual voice vlan assignment mode. You can configure the voice vlan assignment mode for a port according to data traffic passing through the port. Processing mode of untagged packets sent ...
Page 99
1-5 table 1-2 matching relationship between port types and voice devices capable of acquiring ip address and voice vlan automatically voice vlan assignment mode voice traffic type port type supported or not access not supported trunk supported make sure the default vlan of the port exists and is not...
Page 100
1-6 table 1-3 matching relationship between port types and voice devices acquiring voice vlan through manual configuration voice vlan assignment mode port type supported or not access not supported trunk supported make sure the default vlan of the port exists and is not a voice vlan, and the access ...
Page 101
1-7 voice vlan mode packet type processing method packet carrying the voice vlan tag matches the oui list, the packet is transmitted in the voice vlan. Otherwise, the packet is dropped. Packet carrying any other vlan tag the packet is forwarded or dropped based on whether the receiving port is assig...
Page 102
1-8 to do… use the command… remarks set the voice vlan aging timer voice vlan aging minutes optional the default aging timer is 1440 minutes. Enable the voice vlan function globally voice vlan vlan-id enable required enter ethernet port view interface interface-type interface-number required enable ...
Page 103
1-9 to do… use the command… remarks enable the voice vlan security mode voice vlan security enable optional by default, the voice vlan security mode is enabled. Set the voice vlan aging timer voice vlan aging minutes optional the default aging timer is 1,440 minutes. Enable the voice vlan function g...
Page 104
1-10 z the voice vlan function can be enabled for only one vlan at one time. Z if the link aggregation control protocol (lacp) is enabled on a port, voice vlan feature cannot be enabled on it. Z voice vlan function can be enabled only for the static vlan. A dynamic vlan cannot be configured as a voi...
Page 105
1-11 voice vlan configuration example voice vlan configuration example (automatic voice vlan assignment mode) network requirements as shown in figure 1-2 , the mac address of ip phone a is 0011-1100-0001. The phone connects to a downstream device named pc a whose mac address is 0022-1100-0002 and to...
Page 106
1-12 # configure the allowed oui addresses as mac addresses prefixed by 0011-1100-0000 or 0011-2200-0000. In this way, device a identifies packets whose mac addresses match any of the configured oui addresses as voice packets. [devicea] voice vlan mac-address 0011-1100-0001 mask ffff-ff00-0000 descr...
Page 107
1-13 voice vlan configuration example (manual voice vlan assignment mode) network requirements create a voice vlan and configure it to operate in manual voice vlan assignment mode. Add the port to which an ip phone is connected to the voice vlan to enable voice traffic to be transmitted within the v...
Page 108
1-14 [devicea-ethernet1/0/1] port hybrid pvid vlan 2 [devicea-ethernet1/0/1] port hybrid vlan 2 untagged # enable the voice vlan function on ethernet 1/0/1. [devicea-ethernet1/0/1] voice vlan enable verification # display the oui addresses, the corresponding oui address masks and the corresponding d...
Page 109: Table of Contents
I table of contents 1 port basic configuration ··························································································································1-1 ethernet port configuration ···································································································...
Page 110: Port Basic Configuration
1-1 1 port basic configuration when performing basic port configuration, go to these sections for information you are interested in: z ethernet port configuration z ethernet port configuration example z troubleshooting ethernet port configuration ethernet port configuration combo port configuration ...
Page 111
1-2 to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — enable the ethernet port undo shutdown optional by default, the port is enabled. Use the shutdown command to disable the port. Set the description string for t...
Page 114
1-5 z if you specify a source aggregation group id, the system will use the port with the smallest port number in the aggregation group as the source. Z if you specify a destination aggregation group id, the configuration of the source port will be copied to all ports in the aggregation group and al...
Page 115
1-6 z to enable loopback detection on a specific port, you must use the loopback-detection enable command in both system view and the specific port view. Z after you use the undo loopback-detection enable command in system view, loopback detection will be disabled on all ports. Enabling loopback tes...
Page 116
1-7 to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — enable the system to test connected cables virtual-cable-test required configuring the interval to perform statistical analysis on port traffic by performing t...
Page 117
1-8 the port state change delay takes effect when the port goes down but not when the port goes up. Follow these steps to set the port state change delay: to do … use the command … remarks enter system view system-view — enter ethernet interface view interface interface-type interface-number — set t...
Page 119
1-10 troubleshooting ethernet port configuration symptom : fail to configure the default vlan id of an ethernet port. Solution : take the following steps: z use the display interface or display port command to check if the port is a trunk port or a hybrid port. Z if the port is not a trunk or hybrid...
Page 120: Table of Contents
I table of contents 1 link aggregation configuration ··············································································································1-1 overview ····························································································································...
Page 121
1-1 1 link aggregation configuration when configuring link aggregation, go to these sections for information you are interested in: z overview z link aggregation classification z aggregation group categories z link aggregation configuration z displaying and maintaining link aggregation configuration...
Page 122
1-2 table 1-1 consistency considerations for ports in an aggregation category considerations stp state of port-level stp (enabled or disabled) attribute of the link (point-to-point or otherwise) connected to the port port path cost stp priority stp packet format loop protection root protection port ...
Page 123
1-3 in a manual aggregation group, the system sets the ports to selected or unselected state according to the following rules. Z among the ports in an aggregation group that are in up state, the system determines the mater port with one of the following settings being the highest (in descending orde...
Page 124
1-4 z there is a limit on the number of selected ports in an aggregation group. Therefore, if the number of the selected ports in an aggregation group exceeds the maximum number supported by the device, those with lower port numbers operate as the selected ports, and others as unselected ports. Dyna...
Page 125
1-5 aggregation group categories depending on whether or not load sharing is implemented, aggregation groups can be load-sharing or non-load-sharing aggregation groups. When load sharing is implemented, z for ip packets, the system will implement load-sharing based on source ip address and destinati...
Page 126
1-6 link aggregation configuration z the commands of link aggregation cannot be configured with the commands of port loopback detection feature at the same time. Z the ports where the mac-address max-mac-count command is configured cannot be added to an aggregation group. Contrarily, the mac-address...
Page 127
1-7 z when you change a dynamic/static group to a manual group, the system will automatically disable lacp on the member ports. When you change a dynamic group to a static group, the system will remain the member ports lacp-enabled. 2) when a manual or static aggregation group contains only one port...
Page 128
1-8 you need to enable lacp on the ports which you want to participate in dynamic aggregation of the system, because, only when lacp is enabled on those ports at both ends, can the two parties reach agreement in adding/removing ports to/from dynamic aggregation groups. You cannot enable lacp on a po...
Page 129
1-9 if you have saved the current configuration with the save command, after system reboot, the configuration concerning manual and static aggregation groups and their descriptions still exists, but that of dynamic aggregation groups and their descriptions gets lost. Displaying and maintaining link ...
Page 130
1-10 configuration procedure the following only lists the configuration on switch a; you must perform the similar configuration on switch b to implement link aggregation. 1) adopting manual aggregation mode # create manual aggregation group 1. System-view [sysname] link-aggregation group 1 mode manu...
Page 131
1-11 [sysname] interface ethernet1/0/3 [sysname-ethernet1/0/3] lacp enable the three lacp-enabled ports can be aggregated into one dynamic aggregation group to implement load sharing only when they have the same basic configuration (such as rate, duplex mode, and so on)..
Page 132: Table of Contents
I table of contents 1 port isolation configuration ·····················································································································1-1 port isolation overview ········································································································...
Page 133: Port Isolation Configuration
1-1 1 port isolation configuration when configuring port isolation, go to these sections for information you are interested in: z port isolation overview z port isolation configuration z displaying and maintaining port isolation configuration z port isolation configuration example port isolation ove...
Page 134
1-2 z when a member port of an aggregation group joins/leaves an isolation group, the other ports in the same aggregation group will join/leave the isolation group at the same time. Z for ports that belong to an aggregation group and an isolation group simultaneously, removing a port from the aggreg...
Page 135
1-3 network diagram figure 1-1 network diagram for port isolation configuration configuration procedure # add ethernet1/0/2, ethernet1/0/3, and ethernet1/0/4 to the isolation group. System-view system view: return to user view with ctrl+z. [sysname] interface ethernet1/0/2 [sysname-ethernet1/0/2] po...
Page 136: Table of Contents
I table of contents 1 port security configuration······················································································································1-1 port security overview···········································································································...
Page 137: Port Security Configuration
1-1 1 port security configuration when configuring port security, go to these sections for information you are interested in: z port security overview z port security configuration task list z displaying and maintaining port security configuration z port security configuration examples port security...
Page 138
1-2 table 1-1 description of port security modes security mode description feature norestriction in this mode, access to the port is not restricted. In this mode, neither the ntk nor the intrusion protection feature is triggered. Autolearn in this mode, a port can learn a specified number of mac add...
Page 139
1-3 security mode description feature userlogin in this mode, port-based 802.1x authentication is performed for access users. In this mode, neither ntk nor intrusion protection will be triggered. Userloginsecure mac-based 802.1x authentication is performed on the access user. The port is enabled onl...
Page 140
1-4 security mode description feature macaddresselseus erloginsecure in this mode, a port performs mac authentication of an access user first. If the authentication succeeds, the user is authenticated. Otherwise, the port performs 802.1x authentication of the user. In this mode, there can be only on...
Page 141
1-5 task remarks configuring security mac addresses optional enabling port security configuration prerequisites before enabling port security, you need to disable 802.1x and mac authentication globally. Enabling port security follow these steps to enable port security: to do... Use the command... Re...
Page 142
1-6 this configuration is different from that of the maximum number of mac addresses that can be leaned by a port in mac address management. Follow these steps to set the maximum number of mac addresses allowed on a port: to do... Use the command... Remarks enter system view system-view — enter ethe...
Page 143
1-7 z before setting the port security mode to autolearn, you need to set the maximum number of mac addresses allowed on the port with the port-security max-mac-count command. Z when the port operates in the autolearn mode, you cannot change the maximum number of mac addresses allowed on the port. Z...
Page 144
1-8 to do... Use the command... Remarks set the timer during which the port remains disabled port-security timer disableport timer optional 20 seconds by default the port-security timer disableport command is used in conjunction with the port-security intrusion-mode disableport-temporarily command t...
Page 145
1-9 configuring security mac addresses security mac addresses are special mac addresses that never age out. One security mac address can be added to only one port in the same vlan so that you can bind a mac address to one port in the same vlan. Security mac addresses can be learned by the auto-learn...
Page 146
1-10 displaying and maintaining port security configuration to do... Use the command... Remarks display information about port security configuration display port-security [ interface interface-list ] display information about security mac address configuration display mac-address security [ interfa...
Page 147
1-11 [switch-ethernet1/0/1] mac-address security 0001-0002-0003 vlan 1 # configure the port to be silent for 30 seconds after intrusion protection is triggered. [switch-ethernet1/0/1] port-security intrusion-mode disableport-temporarily [switch-ethernet1/0/1] quit [switch] port-security timer disabl...
Page 148: Table of Contents
I table of contents 1 dldp configuration ··································································································································1-1 overview ····················································································································...
Page 149: Dldp Configuration
1-1 1 dldp configuration when configuring dldp, go to these sections for information you are interested in: z overview z dldp fundamentals z dldp configuration z dldp configuration example overview device link detection protocol (dldp) is an technology for dealing with unidirectional links that may ...
Page 150
1-2 figure 1-2 fiber broken or not connected device a ge1/0/49 ge1/0/50 device b ge1/0/49 ge1/0/50 pc device link detection protocol (dldp) can detect the link status of an optical fiber cable or copper twisted pair (such as super category 5 twisted pair). If dldp finds a unidirectional link, it dis...
Page 151
1-3 dldp packet type function rsy-advertisement packets (referred to as rsy packets hereafter) advertisement packet with the rsy flag set to 1. Rsy advertisement packets are sent to request synchronizing the neighbor information when neighbor information is not locally available or a neighbor inform...
Page 152
1-4 dldp status a link can be in one of these dldp states: initial, inactive, active, advertisement, probe, disable, and delaydown. Table 1-2 dldp status status description initial initial status before dldp is enabled. Inactive dldp is enabled but the corresponding link is down active dldp is enabl...
Page 153
1-5 timer description entry aging timer when a new neighbor joins, a neighbor entry is created and the corresponding entry aging timer is enabled when an advertisement packet is received from a neighbor, the neighbor entry is updated and the corresponding entry aging timer is updated in the normal m...
Page 154
1-6 table 1-4 dldp operating mode and neighbor entry aging dldp operating mode detecting a neighbor after the corresponding neighbor entry ages out removing the neighbor entry immediately after the entry timer expires triggering the enhanced timer after an entry timer expires normal mode no yes no e...
Page 155
1-7 table 1-5 dldp state and dldp packet type dldp state type of the dldp packets sent active advertisement packets, with the rsy flag set or not set. Advertisement advertisement packets probe probe packets 2) a dldp packet received is processed as follows: z in authentication mode, the dldp packet ...
Page 156
1-8 table 1-7 processing procedure when no echo packet is received from the neighbor no echo packet received from the neighbor processing procedure in normal mode, no echo packet is received when the echo waiting timer expires. In enhanced mode, no echo packet is received when the enhanced timer exp...
Page 157
1-9 dldp configuration performing basic dldp configuration follow these steps to perform basic dldp configuration: to do … use the command … remarks enter system view system-view — enable dldp on all optical ports of the switch dldp enable enter ethernet port view interface interface-type interface-...
Page 158
1-10 z when connecting two dldp-enabled devices, make sure the software running on them is of the same version. Otherwise, dldp may operate improperly. Z when you use the dldp enable/dldp disable command in system view to enable/disable dldp on all optical ports of the switch, the configuration take...
Page 159
1-11 dldp configuration example network requirements as shown in figure 1-4 , z switch a and switch b are connected through two pairs of fibers. Both of them support dldp. All the ports involved operate in mandatory full duplex mode, with their rates all being 1,000 mbps. Z suppose the fibers betwee...
Page 160
1-12 # set the dldp handling mode for unidirectional links to auto. [switcha] dldp unidirectional-shutdown auto # display the dldp state [switcha] display dldp 1 when two switches are connected through fibers in a crossed way, two or three ports may be in the disable state, and the rest in the inact...
Page 161: Table of Contents
I table of contents 1 mac address table management············································································································1-1 overview ·································································································································...
Page 162: Mac Address Table Management
1-1 1 mac address table management when mac address table management functions, go to these sections for information you are interested in: z overview z mac address table management z displaying mac address table information z configuration example this chapter describes the management of static, dy...
Page 163
1-2 generally, the majority of mac address entries are created and maintained through mac address learning. The following describes the mac address learning process of a switch: 1) as shown in figure 1-1 , user a and user b are both in vlan 1. When user a communicates with user b, the packet from us...
Page 164
1-3 figure 1-4 mac address learning diagram (3) 4) at this time, the mac address table of the switch includes two forwarding entries shown in figure 1-5 . When forwarding the response packet from user b to user a, the switch sends the response to user a through gigabitethernet 1/0/1 (technically cal...
Page 165
1-4 z the mac address aging timer only takes effect on dynamic mac address entries. Z with the “destination mac address triggered update function” enabled, when a switch finds a packet with a destination address matching one mac address entry within the aging time, it updates the entry and restarts ...
Page 166
1-5 task remarks enabling destination mac address triggered update optional configuring a mac address entry you can add, modify, or remove a mac address entry, remove all mac address entries concerning a specific port, or remove specific type of mac address entries (dynamic or static mac address ent...
Page 167
1-6 z when you add a mac address entry, the current port must belong to the vlan specified by the vlan argument in the command. Otherwise, the entry will not be added. Z if the vlan specified by the vlan argument is a dynamic vlan, after a static mac address is added, it will become a static vlan. S...
Page 168
1-7 by setting the maximum number of mac addresses that can be learned from individual ports, the administrator can control the number of the mac address entries the mac address table can dynamically maintain. When the number of the mac address entries learnt from a port reaches the set value, the p...
Page 169
1-8 to do… use the command… remarks display the aging time of the dynamic mac address entries in the mac address table display mac-address aging-time display the configured start port mac address display port-mac configuration examples adding a static mac address entry manually network requirements ...
Page 170: Table of Contents
I table of contents 1 auto detect configuration························································································································1-1 introduction to the auto detect function·························································································...
Page 171: Auto Detect Configuration
1-1 1 auto detect configuration when configuring the auto detect function, go to these sections for information you are interested in: z introduction to the auto detect function z auto detect configuration z auto detect configuration examples introduction to the auto detect function the auto detect ...
Page 172
1-2 task remarks auto detect implementation in vlan interface backup optional auto detect basic configuration follow these steps to configure the auto detect function: to do… use the command… remarks enter system view system-view — create a detected group and enter detected group view detect-group g...
Page 173
1-3 to avoid such problems, you can configure another route to back up the static route and use the auto detect function to judge the validity of the static route. If the static route is valid, packets are forwarded according to the static route, and the other route is standby. If the static route i...
Page 174
1-4 figure 1-1 schematic diagram for vlan interface backup using auto detect can help implement vlan interfaces backup. When data can be transmitted through two vlan interfaces on the switch to the same destination, configure one of the vlan interface as the active interface and the other as the sta...
Page 175
1-5 z on switch a, configure a static route to switch c. Z enable the static route when the detected group 8 is reachable. Z to ensure normal operating of the auto detect function, configure a static route to switch a on switch c. Network diagram figure 1-2 network diagram for implementing the auto ...
Page 176
1-6 network diagram figure 1-3 network diagram for vlan interface backup configuration procedure configure the ip addresses of all the interfaces as shown in figure 1-3 . The configuration procedure is omitted. # enter system view. System-view # create auto detected group 10. [switcha] detect-group ...
Page 177: Table of Contents
I table of contents 1 mstp configuration ··································································································································1-1 overview ····················································································································...
Page 178
Ii configuring digest snooping·········································································································1-39 configuring rapid transition ················································································································1-40 introduction··...
Page 179: Mstp Configuration
1-1 1 mstp configuration go to these sections for information you are interested in: z overview z mstp configuration task list z configuring root bridge z configuring leaf nodes z performing mcheck operation z configuring guard functions z configuring digest snooping z configuring rapid transition z...
Page 180
1-2 in stp, bpdus come in two types: z configuration bpdus, used to calculate spanning trees and maintain the spanning tree topology. Z topology change notification (tcn) bpdus, used to notify concerned devices of network topology changes, if any. Basic concepts in stp 1) root bridge a tree network ...
Page 181
1-3 figure 1-1 a schematic diagram of designated bridges and designated ports all the ports on the root bridge are designated ports. 4) bridge id a bridge id consists of eight bytes, where the first two bytes represent the bridge priority of the device, and the latter six bytes represent the mac add...
Page 182
1-4 6) port id a port id used on a 3com switch 4500 consists of two bytes, that is, 16 bits, where the first six bits represent the port priority, and the latter ten bits represent the port number. The default priority of all ethernet ports on 3com switches 4500 is 128. You can use commands to confi...
Page 183
1-5 table 1-2 selection of the optimum configuration bpdu step description 1 upon receiving a configuration bpdu on a port, the device performs the following processing: z if the received configuration bpdu has a lower priority than that of the configuration bpdu generated by the port, the device wi...
Page 184
1-6 step description 3 the device compares the calculated configuration bpdu with the configuration bpdu on the port whose role is to be determined, and acts as follows based on the comparison result: z if the calculated configuration bpdu is superior, this port will serve as the designated port, an...
Page 185
1-7 device port name bpdu of port bp1 {1, 0, 1, bp1} device b bp2 {1, 0, 1, bp2} cp1 {2, 0, 2, cp1} device c cp2 {2, 0, 2, cp2} z comparison process and result on each device the following table shows the comparison process and result on each device. Table 1-5 comparison process and result on each d...
Page 186
1-8 device comparison process bpdu of port after comparison z port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received configuration bpdu is superior to the configuration bpdu of the local port {2, 0, 2, cp1}, and updates the configuration bpdu of cp1. Z ...
Page 187
1-9 figure 1-3 the final calculated spanning tree to facilitate description, the spanning tree calculation process in this example is simplified, while the actual process is more complicated. 3) the bpdu forwarding mechanism in stp z upon network initiation, every switch regards itself as the root b...
Page 188
1-10 for this reason, the protocol uses a state transition mechanism. Namely, a newly elected root port and the designated ports must go through a period, which is twice the forward delay time, before they transit to the forwarding state. The period allows the new configuration bpdus to be propagate...
Page 189
1-11 z mstp supports mapping vlans to multiple spanning tree (mst) instances (mstis) by means of a vlan-to-instance mapping table. Mstp introduces instances (which integrates multiple vlans into a set) and can bind multiple vlans to an instance, thus saving communication overhead and improving resou...
Page 190
1-12 2) msti a multiple spanning tree instance (msti) refers to a spanning tree in an mst region. Multiple spanning trees can be established in one mst region. These spanning trees are independent of each other. For example, each region in figure 1-4 contains multiple spanning trees known as mstis. ...
Page 191
1-13 z a region boundary port is located on the boundary of an mst region and is used to connect one mst region to another mst region, an stp-enabled region or an rstp-enabled region. Z an alternate port is a secondary port of a root port or master port and is used for rapid transition. With the roo...
Page 192
1-14 z forwarding state. Ports in this state can forward user packets and receive/send bpdu packets. Z learning state. Ports in this state can receive/send bpdu packets but do not forward user packets. Z discarding state. Ports in this state can only receive bpdu packets. Port roles and port states ...
Page 193
1-15 in addition to the basic mstp functions, 3com switch 4500 also provides the following functions for users to manage their switches. Z root bridge hold z root bridge backup z root guard z bpdu guard z loop guard z tc-bpdu attack guard protocols and standards mstp is documented in: z ieee 802.1d:...
Page 194
1-16 task remarks configuring the maximum transmitting rate on the current port optional the default value is recommended. Configuring the current port as an edge port optional setting the link type of a port to p2p optional enabling mstp required to prevent network topology jitter caused by other r...
Page 195
1-17 to do... Use the command... Remarks configure the name of the mst region region-name name required the default mst region name of a switch is its mac address. Instance instance-id vlan vlan-list configure the vlan-to-instance mapping table for the mst region vlan-mapping modulo modulo required ...
Page 196
1-18 configuration example # configure an mst region named info, the mstp revision level being level 1, vlan 2 through vlan 10 being mapped to msti 1, and vlan 20 through vlan 30 being mapped to msti 2. System-view [sysname] stp region-configuration [sysname-mst-region] region-name info [sysname-mst...
Page 197
1-19 using the stp root primary/stp root secondary command, you can specify the current switch as the root bridge or the secondary root bridge of the msti identified by the instance-id argument. If the value of the instance-id argument is set to 0, the stp root primary/stp root secondary command spe...
Page 198
1-20 to do... Use the command... Remarks set the bridge priority for the current switch stp [ instance instance-id ] priority priority required the default bridge priority of a switch is 32,768. Z once you specify a switch as the root bridge or a secondary root bridge by using the stp root primary o...
Page 200
1-22 system-view [sysname] stp mode stp configuring the maximum hop count of an mst region the maximum hop count configured on the region root is also the maximum hops of the mst region. The value of the maximum hop count limits the size of the mst region. A configuration bpdu contains a field that ...
Page 201
1-23 to do... Use the command... Remarks enter system view system-view — configure the network diameter of the switched network stp bridge-diameter bridgenumber required the default network diameter of a network is 7. The network diameter parameter indicates the size of a network. The bigger the net...
Page 202
1-24 z the forward delay parameter and the network diameter are correlated. Normally, a large network diameter corresponds to a large forward delay. A too small forward delay parameter may result in temporary redundant paths. And a too large forward delay parameter may cause a network unable to resu...
Page 203
1-25 configuration procedure follow these steps to configure the timeout time factor: to do... Use the command... Remarks enter system view system-view — configure the timeout time factor for the switch stp timer-factor number required the timeout time factor defaults to 3. For a steady network, the...
Page 204
1-26 as the maximum transmitting rate parameter determines the number of the configuration bpdus transmitted in each hello time, set it to a proper value to prevent mstp from occupying too many network resources. The default value is recommended. Configuration example # set the maximum transmitting ...
Page 205
1-27 you are recommended to configure the ethernet ports connected directly to terminals as edge ports and enable the bpdu guard function at the same time. This not only enables these ports to turn to the forwarding state rapidly but also secures your network. Configuration example # configure ether...
Page 207
1-29 to do... Use the command... Remarks enter system view system-view — enable mstp stp enable required mstp is enabled globally by default. Enter ethernet port view interface interface-type interface-number — disable mstp on the port stp disable optional by default, mstp is enabled on all ports. T...
Page 208
1-30 configuring the path cost for a port the path cost parameter reflects the rate of the link connected to the port. For a port on an mstp-enabled switch, the path cost may be different in different mstis. You can enable flows of different vlans to travel along different physical links by configur...
Page 209
1-31 when calculating the path cost of an aggregated link, the 802.1d-1998 standard does not take the number of the ports on the aggregated link into account, whereas the 802.1t standard does. The following formula is used to calculate the path cost of an aggregated link: path cost = 200,000,000 / l...
Page 210
1-32 [sysname] undo stp interface ethernet 1/0/1 instance 1 cost [sysname] stp pathcost-standard dot1d-1998 2) perform this configuration in ethernet port view system-view [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] undo stp instance 1 cost [sysname-ethernet1/0/1] quit [sysname] stp p...
Page 211
1-33 1) perform this configuration in system view system-view [sysname] stp interface ethernet 1/0/1 instance 1 port priority 16 2) perform this configuration in ethernet port view system-view [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] stp instance 1 port priority 16 setting the link...
Page 212
1-34 to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — perform the mcheck operation stp mcheck required configuration example # perform the mcheck operation on ethernet 1/0/1. 1) perform this configuration in syst...
Page 213
1-35 to do... Use the command... Remarks enter system view system-view — enable the bpdu guard function stp bpdu-protection required the bpdu guard function is disabled by default. Configuration example # enable the bpdu guard function. System-view [sysname] stp bpdu-protection as gigabit ports of a...
Page 214
1-36 configuration procedure follow these steps to configure the root guard function in system view: to do... Use the command... Remarks enter system view system-view — enable the root guard function on specified ports stp interface interface-list root-protection required the root guard function is ...
Page 215
1-37 z you are recommended to enable loop guard on the root port and alternate port of a non-root bridge. Z loop guard, root guard, and edge port settings are mutually exclusive. With one of these functions enabled on a port, any of the other two functions cannot take effect even if you have configu...
Page 216
1-38 maximum times for a switch to remove the mac address table and arp entries to 100 and the switch receives 200 tc-bpdus in the period, the switch removes the mac address table and arp entries for only 100 times within the period. Configuration prerequisites mstp runs normally on the switch. Conf...
Page 217
1-39 switch, and put them in the bpdus to be sent to the another manufacturer's switch. In this way, the switch 4500 can communicate with another manufacturer’s switches in the same mst region. The digest snooping function is not applicable to edge ports. Configuring digest snooping configure the di...
Page 218
1-40 z when the digest snooping feature is enabled on a port, the port state turns to the discarding state. That is, the port will not send bpdu packets. The port is not involved in the stp calculation until it receives bpdu packets from the peer port. Z the digest snooping feature is needed only wh...
Page 219
1-41 figure 1-6 the rstp rapid transition mechanism root port blocks other non- edge ports, changes to forwarding state and sends agreement to upstream device downstream switch upstream switch proposal for rapid transition agree ment designated port changes to forwarding state root port designated p...
Page 220
1-42 configuring rapid transition configuration prerequisites as shown in figure 1-8 , a 3com switch 4500 is connected to another manufacturer's switch. The former operates as the downstream switch, and the latter operates as the upstream switch. The network operates normally. The upstream switch is...
Page 221
1-43 z the rapid transition feature can be enabled on only root ports or alternate ports. Z if you configure the rapid transition feature on a designated port, the feature does not take effect on the port. Mstp maintenance configuration introduction in a large-scale network with mstp enabled, there ...
Page 223
1-45 network diagram figure 1-9 network diagram for mstp configuration the word “permit” shown in figure 1-9 means the corresponding link permits packets of specific vlans. Configuration procedure 1) configure switch a # enter mst region view. System-view [sysname] stp region-configuration # configu...
Page 224
1-46 # activate the settings of the mst region manually. [sysname-mst-region] active region-configuration # specify switch b as the root bridge of msti 3. [sysname] stp instance 3 root primary 3) configure switch c. # enter mst region view. System-view [sysname] stp region-configuration # configure ...
Page 225: Table of Contents
I table of contents 1 ip routing protocol overview ··················································································································1-1 introduction to ip route and routing table·························································································...
Page 226
Ii filters···············································································································································4-1 ip route policy configuration task list··································································································4-2 ro...
Page 227: Ip Routing Protocol Overview
1-1 1 ip routing protocol overview go to these sections for information you are interested in: z introduction to ip route and routing table z routing protocol overview z displaying and maintaining a routing table introduction to ip route and routing table ip route routers are used for route selectio...
Page 228
1-2 z preference: there may be multiple routes with different next hops to the same destination. These routes may be discovered by different routing protocols, or be manually configured static routes. The one with the highest preference (the smallest numerical value) will be selected as the current ...
Page 229
1-3 routing protocol overview static routing and dynamic routing static routing is easy to configure and requires less system resources. It works well in small, stable networks with simple topologies. It cannot adapt itself to any network topology change automatically so that you must perform routin...
Page 230
1-4 each routing protocol (including static routes) is assigned a priority. The route found by the routing protocol with the highest priority is preferred. The following table lists some routing protocols and the default priorities for routes found by them: table 1-1 routing protocols and priorities...
Page 231
1-5 routing information. Each routing protocol shares routing information discovered by other routing protocols through a route redistribution mechanism. Displaying and maintaining a routing table to do… use the command… remarks display brief information about a routing table display ip routing-tabl...
Page 232: Static Route Configuration
2-1 2 static route configuration when configuring a static route, go to these sections for information you are interested in: z introduction to static route z static route configuration z displaying and maintaining static routes z static route configuration example z troubleshooting a static route t...
Page 233
2-2 default route to avoid too large a routing table, you can configure a default route. When the destination address of a packet fails to match any entry in the routing table, z if there is default route in the routing table, the default route will be selected to forward the packet. Z if there is n...
Page 235
2-4 1) perform the following configurations on the switch. # approach 1: configure static routes on switch a. System-view [switcha] ip route-static 1.1.3.0 255.255.255.0 1.1.2.2 [switcha] ip route-static 1.1.4.0 255.255.255.0 1.1.2.2 [switcha] ip route-static 1.1.5.0 255.255.255.0 1.1.2.2 # approach...
Page 236: Rip Configuration
3-1 3 rip configuration when configuring rip, go to these sections for information you are interested in: z rip overview z rip configuration task list z rip configuration example z troubleshooting rip configuration the term router in this chapter refers to a router in a generic sense or an ethernet ...
Page 237
3-2 z interface: outbound interface on this router, through which ip packets should be forwarded to reach the destination. Z metric: cost from the local router to the destination. Z route time: time elapsed since the routing entry was last updated. The time is reset to 0 every time the routing entry...
Page 238
3-3 task remarks enabling rip on the interfaces attached to a specified network segment required setting the rip operating status on an interface optional configuring basic rip functions specifying the rip version on an interface optional setting the additional routing metrics of an interface option...
Page 239
3-4 z related rip commands configured in interface view can take effect only after rip is enabled. Z rip operates on the interfaces attached to a specified network segment. When rip is disabled on an interface, it does not operate on the interface, that is, it neither receives/sends routes on the in...
Page 240
3-5 z set the preference of rip to change the preference order of routing protocols. This order makes sense when more than one route to the same destination is discovered by multiple routing protocols. Z redistribute external routes in an environment with multiple routing protocols. Configuration pr...
Page 241
3-6 follow these steps to configure rip route summarization: to do... Use the command... Remarks enter system view system-view — enter rip view rip — enable rip-2 automatic route summarization summary required enabled by default disabling the router from receiving host routes in some special cases, ...
Page 242
3-7 z the filter-policy import command filters the rip routes received from neighbors, and the routes being filtered out will neither be added to the routing table nor be advertised to any neighbors. Z the filter-policy export command filters all the routes to be advertised, including the routes red...
Page 243
3-8 rip network adjustment and optimization in some special network environments, some rip features need to be configured and rip network performance needs to be adjusted and optimized. By performing the configuration mentioned in this section, the following can be implemented: z changing the conver...
Page 244
3-9 split horizon cannot be disabled on a point-to-point link. Configuring rip-1 packet zero field check follow these steps to configure rip-1 packet zero field check: to do... Use the command... Remarks enter system view system-view — enter rip view rip — enable the check of the must be zero field ...
Page 245
3-10 configuring rip to unicast rip packets follow these steps to configure rip to unicast rip packets: to do... Use the command... Remarks enter system view system-view — enter rip view rip — configure rip to unicast rip packets peer ip-address required when rip runs on the link that does not suppo...
Page 246
3-11 switch c vlan-int1 110.11.2.3/24 vlan-int4 117.102.0.1/16 configuration procedure only the configuration related to rip is listed below. Before the following configuration, make sure the ethernet link layer works normally and the ip addresses of vlan interfaces are configured correctly. 1) conf...
Page 247
4-1 4 ip route policy configuration when configuring an ip route policy, go to these sections for information you are interested in: z ip route policy overview z ip route policy configuration task list z displaying ip route policy z ip route policy configuration example z troubleshooting ip route po...
Page 248
4-2 for acl configuration, refer to the part discussing acl. Ip-prefix list ip-prefix list plays a role similar to acl. But it is more flexible than acl and easier to understand. When ip-prefix list is applied to filter routing information, its matching object is the destination address field in rou...
Page 249
4-3 z if-match clause: defines matching rules; that is, the filtering conditions that the routing information should satisfy for passing the current route policy. The matching objects are some attributes of the routing information. Z apply clause: specifies actions, which are the configuration comma...
Page 251
4-5 ip-prefix configuration ip-prefix plays a role similar to acl and but is more flexible and easier to understand. When ip-prefix is applied to filtering routing information, its matching object is the destination address information field of routing information. Configuration prerequisites before...
Page 252
4-6 ip route policy configuration example controlling rip packet cost to implement dynamic route backup network requirements the required speed of convergence in the small network of a company is not high. The network provides two services. Main and backup links are provided for each service for the...
Page 253
4-7 z for the oa server, the main link is between switch a and switch c, while the backup link is between switch b and switch c. Z for the service server, the main link is between switch b and switch c, while the backup link is between switch a and switch c. Z apply a route policy to control the cos...
Page 254
4-8 [switchc-route-policy] if-match interface vlan-interface2 [switchc-route-policy] if-match ip-prefix 2 [switchc-route-policy] apply cost 6 [switchc-route-policy] quit # create node 30 with the matching mode being permit in the route policy. Define if-match clauses. Apply the cost 6 to routes matc...
Page 255
4-9 2) display data forwarding paths when the main link of the oa server between switch a and switch c is down. Display ip routing-table routing table: public net destination/mask protocol pre cost nexthop interface 1.0.0.0/8 rip 100 6 6.6.6.5 vlan-interface2 3.0.0.0/8 rip 100 5 6.6.6.5 vlan-interfa...
Page 256: Table of Contents
I table of contents 1 multicast overview ····································································································································1-1 multicast overview·········································································································...
Page 257
Ii configuring igmp snooping··········································································································1-17 configuring multicast vlan ··········································································································1-18 troubleshooting igmp sn...
Page 258: Multicast Overview
1-1 1 multicast overview in this manual, the term “router” refers to a router in the generic sense or a layer 3 ethernet switch running an ip multicast protocol. Multicast overview with the development of the internet, more and more interaction services such as data, voice, and video services are ru...
Page 259
1-2 assume that hosts b, d and e need this information. The source server establishes transmission channels for the devices of these users respectively. As the transmitted traffic over the network is in direct proportion to the number of users that receive this information, when a large number of us...
Page 260
1-3 information transmission in the multicast mode as described in the previous sections, unicast is suitable for networks with sparsely distributed users, whereas broadcast is suitable for networks with densely distributed users. When the number of users requiring information is not certain, unicas...
Page 261
1-4 z all receivers interested in the same information form a multicast group. Multicast groups are not subject to geographic restrictions. Z a router that supports layer 3 multicast is called multicast router or layer 3 multicast device. In addition to providing multicast routing, a multicast route...
Page 262
1-5 z distributive application: multicast makes multiple-point application possible. Application of multicast the multicast technology effectively addresses the issue of point-to-multipoint data transmission. By enabling high-efficiency point-to-multipoint data transmission, over an ip network, mult...
Page 263
1-6 multicast architecture the purpose of ip multicast is to transmit information from a multicast source to receivers in the multicast mode and to satisfy information requirements of receivers. You should be concerned about: z host registration: what receivers reside on the network? Z technologies ...
Page 264
1-7 z the membership of a group is dynamic. A host can join and leave a multicast group at any time. Z a multicast group can be either permanent or temporary. Z a multicast group whose addresses are assigned by iana is a permanent multicast group. It is also called reserved multicast group. Note tha...
Page 265
1-8 class d address range description 224.0.0.13 all protocol independent multicast (pim) routers 224.0.0.14 resource reservation protocol (rsvp) encapsulation 224.0.0.15 all core-based tree (cbt) routers 224.0.0.16 the specified subnetwork bandwidth management (sbm) 224.0.0.17 all sbms 224.0.0.18 v...
Page 266
1-9 multicast protocols z generally, we refer to ip multicast working at the network layer as layer 3 multicast and the corresponding multicast protocols as layer 3 multicast protocols, which include igmp, pim, and msdp; we refer to ip multicast working at the data link layer as layer 2 multicast an...
Page 267
1-10 among a variety of mature intra-domain multicast routing protocols, protocol independent multicast (pim) is a popular one. Based on the forwarding mechanism, pim comes in two modes – dense mode (often referred to as pim-dm) and sparse mode (often referred to as pim-sm). Z an inter-domain multic...
Page 268
1-11 z in the network, multicast packet transmission is based on the guidance of the multicast forwarding table derived from the unicast routing table or the multicast routing table specially provided for multicast. Z to process the same multicast information from different peers received on differe...
Page 269
1-12 considers the path along which the packet from the rpf neighbor arrived on the rpf interface to be the shortest path that leads back to the source. Assume that unicast routes exist in the network, as shown in figure 1-7 . Multicast packets travel along the spt from the multicast source to the r...
Page 270
1-1 2 common multicast configuration in this manual, the term “router” refers to a router in the generic sense or a layer 3 ethernet switch running an ip multicast protocol. Common multicast configuration table 2-1 complete the following tasks to perform common multicast configurations: task remarks...
Page 271
1-2 to do... Use the command... Remarks enter system view system -view — enter ethernet port view interface interface-type interface-number — configure multicast source port suppression multicast-source-deny optional multicast source port suppression is disabled by default. Configuring a multicast m...
Page 272
1-3 z if the multicast mac address entry to be created already exists, the system gives you a prompt. Z if you want to add a port to a multicast mac address entry created through the mac-address multicast command, you need to remove the entry first, create this entry again, and then add the specifie...
Page 273: Igmp Snooping Configuration
1-1 3 igmp snooping configuration when configuring igmp snooping, go to these sections for information you are interested in: z igmp snooping overview z configuring igmp snooping z displaying and maintaining igmp snooping z igmp snooping configuration examples z troubleshooting igmp snooping in this...
Page 274
1-2 figure 3-1 before and after igmp snooping is enabled on layer 2 device multicast packet transmission without igmp snooping source multicast router host a receiver host b host c receiver multicast packets layer 2 switch multicast packet transmission when igmp snooping runs source multicast router...
Page 275
1-3 member ports. The switch records all member ports on the local device in the igmp snooping forwarding table. Port aging timers in igmp snooping and related messages and actions table 3-1 port aging timers in igmp snooping and related messages and actions timer description message before expiry a...
Page 276
1-4 a switch will not forward an igmp report through a non-router port for the following reason: due to the igmp report suppression mechanism, if member hosts of that multicast group still exist under non-router ports, the hosts will stop sending reports when they receive the message, and this preve...
Page 277
1-5 configuring igmp snooping complete the following tasks to configure igmp snooping: task remarks enabling igmp snooping required configuring the version of igmp snooping optional configuring timers optional configuring fast leave processing optional configuring a multicast group filter optional c...
Page 278
1-6 z although both layer 2 and layer 3 multicast protocols can run on the same switch simultaneously, they cannot run simultaneously on a vlan or its corresponding vlan interface. Z before enabling igmp snooping in a vlan, be sure to enable igmp snooping globally in system view; otherwise the igmp ...
Page 279
1-7 configuring timers this section describes how to configure the aging timer of the router port, the aging timer of the multicast member ports, and the query response timer. Follow these steps to configure timers: to do... Use the command... Remarks enter system view system-view — configure the ag...
Page 280
1-8 to do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — enable fast leave processing for specific vlans igmp-snooping fast-leave [ vlan vlan-list ] required by default, the fast leave processing feature is disabled. Z the fast leave processing fun...
Page 281
1-9 to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure a multicast group filter igmp-snooping group-policy acl-number [vlan vlan-list ] optional no group filter is configured by default, namely hosts can ...
Page 282
1-10 z to prevent bursting traffic in the network or performance deterioration of the device caused by excessive multicast groups, you can set the maximum number of multicast groups that the switch should process. Z when the number of multicast groups exceeds the configured limit, the switch removes...
Page 283
1-11 to do... Use the command... Remarks enable igmp snooping querier igmp-snooping querier required by default, igmp snooping querier is disabled. Configuring igmp query interval follow these steps to configure igmp query interval: to do... Use the command... Remarks enter system view system-view —...
Page 284
1-12 z if the function of dropping unknown multicast packets or the xrn fabric function is enabled, you cannot enable unknown multicast flooding suppression. Z unknown multicast flooding suppression and multicast source port suppression cannot take effect at the same time. If both are enabled, only ...
Page 285
1-13 configuring a static router port in a network where the topology is unlikely to change, you can configure a port on the switch as a static router port, so that the switch has a static connection to a multicast router and receives igmp messages from that router. In ethernet port view follow thes...
Page 286
1-14 therefore, to ensure that igmp entries will not age out, the port must receive igmp general queries periodically. Follow these steps to configure a port as a simulated group member: to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-...
Page 287
1-15 configuring multicast vlan in traditional multicast implementations, when users in different vlans listen to the same multicast group, the multicast data is copied on the multicast router for each vlan that contains receivers. This is a big waste of network bandwidth. In an igmp snooping enviro...
Page 289
1-17 igmp snooping configuration examples configuring igmp snooping network requirements to prevent multicast traffic from being flooded at layer 2, enable igmp snooping on layer 2 switches. Z as shown in figure 3-3 , router a connects to a multicast source (source) through ethernet 1/0/2, and to sw...
Page 290
1-18 3) configure switch a # enable igmp snooping globally. System-view [switcha] igmp-snooping enable enable igmp-snooping ok. # create vlan 100, assign ethernet 1/0/1 through ethernet 1/0/4 to this vlan, and enable igmp snooping in the vlan. [switcha] vlan 100 [switcha-vlan100] port ethernet 1/0/1...
Page 291
1-19 table 3-2 network devices and their configurations device device description networking description switch a layer 3 switch the interface ip address of vlan 20 is 168.10.1.1. Ethernet 1/0/1 is connected to the workstation and belongs to vlan 20. The interface ip address of vlan 10 is 168.10.2.1...
Page 292
1-20 network diagram figure 3-4 network diagram for multicast vlan configuration workstation switcha switchb vlan-int20 168.10.1.1 eth1/0/1 eth1/0/10 vla n2 vlan3 eth1/0/10 vlan10 eth 1/0 /1 eth1/0 /2 hosta hostb vlan-int10 168.10.2.1 configuration procedure the following configuration is based on t...
Page 293
1-21 # create vlan 2, vlan 3 and vlan 10, configure vlan 10 as the multicast vlan, and then enable igmp snooping on it. [switchb] vlan 2 to 3 please wait.... Done. [switchb] vlan 10 [switchb-vlan10] service-type multicast [switchb-vlan10] igmp-snooping enable [switchb-vlan10] quit # define ethernet ...
Page 294
1-22 z if the multicast group set up by igmp snooping is not correct, contact your technical support personnel..
Page 295: Table of Contents
I table of contents 1 802.1x configuration ·································································································································1-1 introduction to 802.1x······································································································...
Page 296
Ii layer 3 error control·······················································································································4-1 configuring system guard······················································································································4-1 configu...
Page 297: 802.1X Configuration
1-1 1 802.1x configuration when configuring 802.1x, go to these sections for information you are interested in: z introduction to 802.1x z introduction to 802.1x configuration z basic 802.1x configuration z advanced 802.1x configuration z displaying and maintaining 802.1x configuration z configurati...
Page 298
1-2 figure 1-1 architecture of 802.1x authentication z the supplicant system is the entity seeking access to the lan. It resides at one end of a lan segment and is authenticated by the authenticator system at the other end of the lan segment. The supplicant system is usually a user terminal device. ...
Page 299
1-3 z the controlled port can be used to pass service packets when it is in authorized state. It is blocked when not in authorized state. In this case, no packets can pass through it. Z controlled port and uncontrolled port are two properties of a port. Packets reaching a port are visible to both th...
Page 300
1-4 figure 1-3 the format of an eapol packet in an eapol packet: z the pae ethernet type field holds the protocol identifier. The identifier for 802.1x is 0x888e. Z the protocol version field holds the version of the protocol supported by the sender of the eapol packet. Z the type field can be one o...
Page 301
1-5 z the length field indicates the size of an eap packet, which includes the code, identifier, length, and data fields. Z the data field carries the eap packet, whose format differs with the code field. A success or failure packet does not contain the data field, so the length field of it is 4. Fi...
Page 302
1-6 eap relay mode this mode is defined in 802.1x. In this mode, eap packets are encapsulated in higher level protocol (such as eapor) packets to enable them to successfully reach the authentication server. Normally, this mode requires that the radius server support the two newly-added fields: the e...
Page 303
1-7 figure 1-8 802.1x authentication procedure (in eap relay mode) supplicant system pae raduis server eapol eapor eapol-start eap- request / identity eap- response / identity eap- request / md5 challenge eap-success eap- response / md5 challenge radius access -request (eap- response / identity) rad...
Page 304
1-8 feedbacks (through a radius access-accept packet and an eap-success packet) to the switch to indicate that the supplicant system is authenticated. Z the switch changes the state of the corresponding port to accepted state to allow the supplicant system to access the network. Z the supplicant sys...
Page 305
1-9 figure 1-9 802.1x authentication procedure (in eap terminating mode) supplicant system pae authenticator system pae radius server eapol radius eapol- start eap- request /identity eap- response/identity eap- request/md5 challenge eap- success eap-response/md5 challenge radius access-request ( cha...
Page 306
1-10 z re-authentication timer (reauth-period). The switch initiates 802.1x re-authentication at the interval set by the re-authentication timer. Z radius server timer (server-timeout). This timer sets the server-timeout period. After sending an authentication request packet to the radius server, th...
Page 307
1-11 z only disconnects the supplicant system but sends no trap packets. Z sends trap packets without disconnecting the supplicant system. This function needs the cooperation of 802.1x client and a cams server. Z the 802.1x client needs to be capable of detecting multiple network adapters, proxies, ...
Page 308
1-12 z after the maximum number retries have been made and there are still ports that have not sent any response back, the switch will then add these ports to the guest vlan. Z users belonging to the guest vlan can access the resources of the guest vlan without being authenticated. But they need to ...
Page 309
1-13 z the radius server has the switch perform 802.1x re-authentication of users. The radius server sends the switch an access-accept packet with the termination-action attribute field of 1. Upon receiving the packet, the switch re-authenticates the user periodically. Z you enable 802.1x re-authent...
Page 310
1-14 basic 802.1x configuration configuration prerequisites z configure isp domain and the aaa scheme to be adopted. You can specify a radius scheme or a local scheme. Z ensure that the service type is configured as lan-access (by using the service-type command) if local authentication scheme is ado...
Page 311
1-15 to do… use the command… remarks enable online user handshaking dot1x handshake enable optional by default, online user handshaking is enabled. Z 802.1x configurations take effect only after you enable 802.1x both globally and for specified ports. Z the settings of 802.1x and mac address learnin...
Page 314
1-18 as for the dot1x version-user command, if you execute it in system view without specifying the interface-list argument, the command applies to all ports. You can also execute this command in port view. In this case, this command applies to the current port only and the interface-list argument i...
Page 315
1-19 z the guest vlan function is available only when the switch operates in the port-based access control mode. Z only one guest vlan can be configured for each switch. Z the guest vlan function cannot be implemented if you configure the dot1x dhcp-launch command on the switch to enable dhcp-trigge...
Page 316
1-20 during re-authentication, the switch always uses the latest re-authentication interval configured, no matter which of the above-mentioned two ways is used to determine the re-authentication interval. For example, if you configure a re-authentication interval on the switch and the switch receive...
Page 317
1-21 a real-time accounting packet to the radius servers once in every 15 minutes. A user name is sent to the radius servers with the domain name truncated. Z the user name and password for local 802.1x authentication are “localuser” and “localpass” (in plain text) respectively. The idle disconnecti...
Page 318
1-22 [sysname-radius-radius1] secondary authentication 10.11.1.2 [sysname-radius-radius1] secondary accounting 10.11.1.1 # set the password for the switch and the authentication radius servers to exchange messages. [sysname-radius-radius1] key authentication name # set the password for the switch an...
Page 319
2-1 2 quick ead deployment configuration when configuring quick ead deployment, go to these sections for information you are interested in: z introduction to quick ead deployment z configuring quick ead deployment z displaying and maintaining quick ead deployment z quick ead deployment configuration...
Page 320
2-2 configuring quick ead deployment configuration prerequisites z enable 802.1x on the switch. Z set the port authorization mode to auto for 802.1x-enabled ports using the dot1x port-control command. Configuration procedure configuring a free ip range a free ip range is an ip range that users can a...
Page 321
2-3 large number of users log in but cannot pass authentication, the switch may run out of acl resources, preventing other users from logging in. A timer called acl timer is designed to solve this problem. You can control the usage of acl resources by setting the acl timer. The acl timer starts once...
Page 322
2-4 configuration procedure before enabling quick ead deployment, make sure sure that: z the web server is configured properly. Z the default gateway of the pc is configured as the ip address of the layer-3 virtual interface of the vlan to which the port that is directly connected with the pc belong...
Page 323: Habp Configuration
3-1 3 habp configuration when configuring habp, go to these sections for information you are interested in: z introduction to habp z habp server configuration z habp client configuration z displaying and maintaining habp configuration introduction to habp when a switch is configured with the 802.1x ...
Page 324
3-2 to do... Use the command... Remarks configure the current switch to be an habp server habp server vlan vlan-id required by default, a switch operates as an habp client after you enable habp on the switch. If you want to use the switch as a management switch, you need to configure the switch to b...
Page 325: System Guard Configuration
4-1 4 system guard configuration when configuring system guard, go to these sections for information you are interested in: z system guard overview z configuring system guard z displaying and maintaining system guard configuration system guard overview guard against ip attacks system-guard operates ...
Page 326
4-2 to do... Use the command... Remarks set the maximum number of infected hosts that can be concurrently monitored system-guard ip detect-maxnum number optional 30 by default set the maximum number of addresses that the system can learn, the maximum number of times an address can be hit before an a...
Page 327
4-3 enabling layer 3 error control follow these steps to enable layer 3 error control: to do... Use the command... Remarks enter system view system-view — enable layer 3 error control system-guard l3err enable required enabled by default displaying and maintaining system guard configuration to do......
Page 328: Table of Contents
I table of contents 1 aaa overview ············································································································································1-1 introduction to aaa ·····································································································...
Page 329: Aaa Overview
1-1 1 aaa overview introduction to aaa aaa is the acronym for the three security functions: authentication, authorization and accounting. It provides a uniform framework for you to configure these three functions to implement network security management. Z authentication: defines what users can acce...
Page 330
1-2 introduction to isp domain an internet service provider (isp) domain is a group of users who belong to the same isp. For a username in the format of userid@isp-name or userid.Isp-name, the isp-name following the "@" character is the isp domain name. The access device uses userid as the username ...
Page 331
1-3 figure 1-1 databases in a radius server in addition, a radius server can act as a client of some other aaa server to provide authentication or accounting proxy service. Basic message exchange procedure in radius the messages exchanged between a radius client (a switch, for example) and a radius ...
Page 332
1-4 4) the radius client accepts or denies the user depending on the received authentication result. If it accepts the user, the radius client sends a start-accounting request (accounting-request, with the status-type attribute value = start) to the radius server. 5) the radius server returns a star...
Page 333
1-5 code message type message description 4 accounting-request direction: client->server. The client transmits this message to the server to request the server to start or end the accounting (whether to start or to end the accounting is determined by the acct-status-type attribute in the message). T...
Page 334
1-6 type field value attribute type type field value attribute type 10 framed-routing 32 nas-identifier 11 filter-id 33 proxy-state 12 framed-mtu 34 login-lat-service 13 framed-compression 35 login-lat-node 14 login-ip-host 36 login-lat-group 15 login-service 37 framed-appletalk-link 16 login-tcp-po...
Page 335: Aaa Configuration
2-1 2 aaa configuration aaa configuration task list you need to configure aaa to provide network access services for legal users while protecting network devices and preventing unauthorized access and repudiation behavior. Complete the following tasks to configure aaa (configuring a combined aaa sch...
Page 336
2-2 task remarks creating an isp domain and configuring its attributes required configuring separate aaa schemes required configuring an aaa scheme for an isp domain required with separate aaa schemes, you can specify authentication, authorization and accounting schemes respectively. You need to con...
Page 340
2-6 currently, the switch supports the following two types of assigned vlan ids: integer and string. Z integer: if the radius authentication server assigns integer type of vlan ids, you can set the vlan assignment mode to integer on the switch (this is also the default mode on the switch). Then, upo...
Page 341
2-7 the local users are users set on the switch, with each user uniquely identified by a username. To make a user who is requesting network service pass local authentication, you should add an entry in the local user database on the switch for the user. Follow these steps to configure the attributes...
Page 342
2-8 z the following characters are not allowed in the user-name string: /:*?. And you cannot input more than one “@” in the string. Z after the local-user password-display-mode cipher-force command is executed, any password will be displayed in cipher mode even though you specify to display a user p...
Page 343
2-9 task remarks creating a radius scheme required configuring radius authentication/authorization servers required configuring radius accounting servers required configuring shared keys for radius messages optional configuring the maximum number of radius request transmission attempts optional conf...
Page 344
2-10 creating a new radius scheme, you should configure the ip address and udp port number of each radius server you want to use in this scheme. These radius servers fall into two types: authentication/authorization, and accounting. And for each type of server, you can configure two servers in a rad...
Page 345
2-11 to do… use the command… remarks create a radius scheme and enter its view radius scheme radius-scheme-name required by default, a radius scheme named "system" has already been created in the system. Set the ip address and port number of the primary radius authentication/authorization server pri...
Page 346
2-12 to do… use the command… remarks set the ip address and port number of the secondary radius accounting server secondary accounting ip-address [ port-number ] optional by default, the ip address and udp port number of the secondary accounting server are 0.0.0.0 and 1813 for a newly created radius...
Page 347
2-13 to do… use the command… remarks enter system view system-view — create a radius scheme and enter its view radius scheme radius-scheme-name required by default, a radius scheme named "system" has already been created in the system. Set a shared key for radius authentication/authorization message...
Page 350
2-16 z generally, the access users are named in the userid@isp-name format. Here, isp-name after the “@” character represents the isp domain name, by which the device determines which isp domain a user belongs to. However, some old radius servers cannot accept the usernames that carry isp domain nam...
Page 351
2-17 z if you adopt the local radius server function, the udp port number of the authentication/authorization server must be 1645, the udp port number of the accounting server must be 1646, and the ip addresses of the servers must be set to the addresses of this switch. Z the message encryption key ...
Page 352
2-18 to do… use the command… remarks set the response timeout time of radius servers timer response-timeout seconds optional by default, the response timeout time of radius servers is three seconds. Set the time that the switch waits before it try to re-communicate with primary server and restore th...
Page 353
2-19 online when the user re-logs into the network before the cams performs online user detection, and the user cannot get authenticated. In this case, the user can access the network again only when the cams administrator manually removes the user's online information. The user re-authentication at...
Page 354
2-20 displaying and maintaining aaa configuration displaying and maintaining aaa configuration to do… use the command… remarks display configuration information about one specific or all isp domains display domain [ isp-name ] display information about user connections display connection [ access-ty...
Page 355
2-21 the configuration procedure for remote authentication of ssh users by radius server is similar to that for telnet users. The following text only takes telnet users as example to describe the configuration procedure for remote authentication. Network requirements in the network environment shown...
Page 356
2-22 [sysname-isp-cams] quit # configure a radius scheme. [sysname] radius scheme cams [sysname-radius-cams] accounting optional [sysname-radius-cams] primary authentication 10.110.91.164 1812 [sysname-radius-cams] key authentication aabbcc [sysname-radius-cams] server-type extended [sysname-radius-...
Page 357
2-23 [sysname-ui-vty0-4] quit # create and configure a local user named telnet. [sysname] local-user telnet [sysname-luser-telnet] service-type telnet [sysname-luser-telnet] password simple aabbcc [sysname-luser-telnet] quit # configure an authentication scheme for the default “system” domain. [sysn...
Page 358: Ead Configuration
3-24 z none or incorrect radius server ip address is set on the switch — be sure to set a correct radius server ip address. Z one or all aaa udp port settings are incorrect — be sure to set the same udp port numbers as those on the radius server. Symptom 3 : the user passes the authentication and ge...
Page 359
3-25 figure 3-1 typical network application of ead ead configuration the ead configuration includes: z configuring the attributes of access users (such as username, user type, and password). For local authentication, you need to configure these attributes on the switch; for remote authentication, yo...
Page 360
3-26 z you are required to configure the switch to use radius server for remote user authentication and use security policy server for ead control on users. The following are the configuration tasks: z connect the radius authentication server 10.110.91.164 and the switch, and configure the switch to...
Page 361
3-27 [sysname-isp-system] radius-scheme cams.
Page 362: Table of Contents
I table of contents 1 mac address authentication configuration ··························································································1-1 mac address authentication overview··································································································1-1 perfor...
Page 363
1-1 1 mac address authentication configuration when configuring mac address authentication, go to these sections for information you are interested: z mac address authentication overview z related concepts z configuring basic mac address authentication functions z mac address authentication enhanced...
Page 364
1-2 format configured with the mac-authentication authmode usernameasmacaddress usernameformat command; otherwise, the authentication will fail. Z in fixed mode, all users’ mac addresses are automatically mapped to the configured local passwords and usernames. Z the service type of a local user need...
Page 366
1-4 task remarks configuring a guest vlan optional configuring the maximum number of mac address authentication users allowed to access a port optional configuring a guest vlan different from guest vlans described in the 802.1x and system-guard manual, guest vlans mentioned in this section refer to ...
Page 367
1-5 after a port is added to a guest vlan, the switch will re-authenticate the first access user of this port (namely, the first user whose unicast mac address is learned by the switch) periodically. If this user passes the re-authentication, this port will exit the guest vlan, and thus the user can...
Page 368
1-6 z if more than one client are connected to a port, you cannot configure a guest vlan for this port. Z when a guest vlan is configured for a port, only one mac address authentication user can access the port. Even if you set the limit on the number of mac address authentication users to more than...
Page 369
1-7 z if both the limit on the number of mac address authentication users and the limit on the number of users configured in the port security function are configured for a port, the smaller value of the two configured limits is adopted as the maximum number of mac address authentication users allow...
Page 370
1-8 # set the user name in mac address mode for mac address authentication, requiring hyphened lowercase mac addresses as the usernames and passwords. [sysname] mac-authentication authmode usernameasmacaddress usernameformat with-hyphen lowercase # add a local user. Z specify the user name and passw...
Page 371: Table of Contents
I table of contents 1 arp configuration·····································································································································1-1 introduction to arp·········································································································...
Page 372: Arp Configuration
1-1 1 arp configuration when configuring arp, go to these sections for information you are interested in: z introduction to arp z configuring arp z configuring gratuitous arp z configuring arp source mac address consistency check z displaying and debugging arp z arp configuration examples introducti...
Page 373
1-2 figure 1-1 arp message format hardware type (16 bits) protocol type (16 bits) length of hardware address length of protocol address operator (16 bits) hardware address of the sender ip address of the sender hardware address of the receiver ip address of the receiver hardware type (16 bits) hardw...
Page 374
1-3 value description 5 chaos 6 ieee802.X 7 arc network arp table in an ethernet, the mac addresses of two hosts must be available for the two hosts to communicate with each other. Each host in an ethernet maintains an arp table, where the latest used ip address-to-mac address mapping entries are st...
Page 375
1-4 mode, all hosts on this subnet can receive the request, but only the requested host (namely, host b) will process the request. 3) host b compares its own ip address with the destination ip address in the arp request. If they are the same, host b saves the source ip address and source mac address...
Page 376
1-5 z if they are not consistent, the arp packet is considered invalid and the corresponding arp entry is not learned. Configuring arp follow these steps to configure arp basic functions: to do… use the command… remarks enter system view system-view — add a static arp entry arp static ip-address mac...
Page 377
1-6 the sending of gratuitous arp packets is enabled as long as an s4500 switch operates. No command is needed for enabling this function. That is, the device sends gratuitous arp packets whenever a vlan interface is enabled (such as when a link is enabled or an ip address is configured for the vlan...
Page 378
1-7 configuration procedure system-view [sysname] undo arp check enable [sysname] interface vlan 1 [sysname-vlan-interface1] undo gratuitous-arp period-resending enable [sysname-vlan-interface1] quit [sysname] arp timer aging 10 [sysname] arp static 192.168.1.1 000f-e201-0000 1 ethernet 1/0/10
Page 379: Table of Contents
I table of contents 1 dhcp overview··········································································································································1-1 introduction to dhcp ······································································································...
Page 380: Dhcp Overview
1-1 1 dhcp overview when configuring dhcp, go to these sections for information you are interested in: z introduction to dhcp z dhcp ip address assignment z dhcp packet format z protocol specification introduction to dhcp with networks getting larger in size and more complicated in structure, lack o...
Page 381
1-2 z automatic assignment. The dhcp server assigns ip addresses to dhcp clients. The ip addresses will be occupied by the dhcp clients permanently. Z dynamic assignment. The dhcp server assigns ip addresses to dhcp clients for predetermined period of time. In this case, a dhcp client must apply for...
Page 382
1-3 by default, a dhcp client updates its ip address lease automatically by unicasting a dhcp-request packet to the dhcp server when half of the lease time elapses. The dhcp server responds with a dhcp-ack packet to notify the dhcp client of a new ip lease if the server can assign the same ip addres...
Page 383
1-4 z file: path and name of the boot configuration file that the dhcp server specifies for the dhcp client. Z option: optional variable-length fields, including packet type, valid lease time, ip address of a dns server, and ip address of the wins server. Protocol specification protocol specificatio...
Page 384
2-1 2 dhcp relay agent configuration when configuring the dhcp relay agent, go to these sections for information you are interested in: z introduction to dhcp relay agent z configuring the dhcp relay agent z displaying and maintaining dhcp relay agent configuration z dhcp relay agent configuration e...
Page 385
2-2 figure 2-1 typical dhcp relay agent application in the process of dynamic ip address assignment through the dhcp relay agent, the dhcp client and dhcp server interoperate with each other in a similar way as they do without the dhcp relay agent. The following sections only describe the forwarding...
Page 386
2-3 figure 2-2 padding contents for sub-option 1 of option 82 figure 2-3 padding contents for sub-option 2 of option 82 mechanism of option 82 supported on dhcp relay agent the procedure for a dhcp client to obtain an ip address from a dhcp server through a dhcp relay agent is similar to that for th...
Page 387
2-4 if a switch belongs to an xrn fabric, you need to enable the udp helper function on it before configuring it as a dhcp relay agent. Dhcp relay agent configuration task list complete the following tasks to configure the dhcp relay agent: task remarks enabling dhcp required correlating a dhcp serv...
Page 388
2-5 to improve security and avoid malicious attack to the unused sockets, s4500 ethernet switches provide the following functions: z udp 67 and udp 68 ports used by dhcp are enabled only when dhcp is enabled. Z udp 67 and udp 68 ports are disabled when dhcp is disabled. The corresponding implementat...
Page 389
2-6 to do… use the command… remarks create a static ip-to-mac binding dhcp-security static ip-address mac-address optional not created by default. Enter interface view interface interface-type interface-number — enable the address checking function address-check enable required disabled by default. ...
Page 390
2-7 currently, the dhcp relay agent handshake function on an s4500 series switch can only interoperate with a windows 2000 dhcp server. Enabling unauthorized dhcp server detection if there is an unauthorized dhcp server in the network, when a client applies for an ip address, the unauthorized dhcp s...
Page 392
2-9 network diagram figure 2-4 network diagram for dhcp relay agent switch b dhcp server switch a dhcp relay dhcp client dhcp client dhcp client dhcp client vlan-int2 10.1.1.2/24 vlan-int1 10.10.1.1/24 vlan-int2 10.1.1.1/24 configuration procedure # create dhcp server group 1 and configure an ip add...
Page 393
2-10 z check if an address pool that is on the same network segment with the dhcp clients is configured on the dhcp server. Z check if a reachable route is configured between the dhcp relay agent and the dhcp server. Z check the dhcp relay agent. Check if the correct dhcp server group is configured ...
Page 394: Dhcp Snooping Configuration
3-1 3 dhcp snooping configuration when configuring dhcp snooping, go to these sections for information you are interested in: z dhcp snooping overview z configuring dhcp snooping z displaying and maintaining dhcp snooping configuration z dhcp snooping configuration examples dhcp snooping overview in...
Page 395
3-2 figure 3-1 typical network diagram for dhcp snooping application dhcp snooping listens the following two types of packets to retrieve the ip addresses the dhcp clients obtain from dhcp servers and the mac addresses of the dhcp clients: z dhcp-request packet z dhcp-ack packet introduction to dhcp...
Page 396
3-3 figure 3-3 extended format of the remote id sub-option in practice, some network devices do not support the type and length identifiers of the circuit id and remote id sub-options. To interwork with these devices, s4500 series ethernet switches support option 82 in the standard format. Refer to ...
Page 397
3-4 when receiving a dhcp client’s request without option 82, the dhcp snooping device will add the option field with the configured sub-option and then forward the packet. For details, see table 3-2 . Table 3-2 ways of handling a dhcp packet without option 82 sub-option configuration the dhcp-snoop...
Page 398
3-5 z if an s4500 ethernet switch is enabled with dhcp snooping, the clients connected to it cannot dynamically obtain ip addresses through bootp. Z you need to specify the ports connected to the valid dhcp servers as trusted to ensure that dhcp clients can obtain valid ip addresses. The trusted por...
Page 399
3-6 configuring a handling policy for dhcp packets with option 82 follow these steps to configure a handling policy for dhcp packets with option 82: to do… use the command… remarks enter system view system-view — configure a global handling policy for requests that contain option 82 dhcp-snooping in...
Page 400
3-7 to do… use the command… remarks enter ethernet port view interface interface-type interface-number — configure the circuit id sub-option in option 82 dhcp-snooping information [ vlan vlan-id] circuit-id string string optional by default, the circuit id sub-option contains the vlan id and port in...
Page 401
3-8 z if you configure a remote id sub-option in both system view and on a port, the remote id sub-option configured on the port applies when the port receives a packet, and the global remote id applies to other interfaces that have no remote id sub-option configured. Z if you have configured a remo...
Page 402
3-9 z enable dhcp-snooping option 82 support on the switch and set the remote id field in option 82 to the system name of the switch. Set the circuit id sub-option to abcd in dhcp packets from vlan 1 on ethernet 1/0/3. Network diagram figure 3-6 network diagram for dhcp-snooping option 82 support co...
Page 403
4-1 4 dhcp/bootp client configuration when configuring the dhcp/bootp client, go to these sections for information you are interested in: z introduction to dhcp client z introduction to bootp client z configuring a dhcp/bootp client z displaying dhcp/bootp client configuration introduction to dhcp c...
Page 404
4-2 configuring a dhcp/bootp client follow these steps to configure a dhcp/bootp client: to do… use the command… remarks enter system view system-view — enter vlan interface view interface vlan-interface vlan-id — configure the vlan interface to obtain ip address through dhcp or bootp ip address { b...
Page 405
4-3 network diagram figure 4-1 a dhcp network configuration procedure the following describes only the configuration on switch a serving as a dhcp client. # configure vlan-interface 1 to dynamically obtain an ip address by using dhcp. System-view [switcha] interface vlan-interface 1 [switcha-vlan-in...
Page 406: Table of Contents
I table of contents 1 acl configuration·····································································································································1-1 acl overview ···············································································································...
Page 407: Acl Configuration
1-1 1 acl configuration when configuring acl, go to these sections for information you are interested in: z acl overview z acl configuration task list z displaying and maintaining acl configuration z examples for upper-layer software referencing acls z examples for applying acls to hardware acl over...
Page 408
1-2 depth-first match order for rules of a basic acl 1) range of source ip address: the smaller the source ip address range (that is, the more the number of zeros in the wildcard mask), the higher the match priority. 2) fragment keyword: a rule with the fragment keyword is prior to others. 3) if the...
Page 409
1-3 z referenced by routing policies z used to control telnet, snmp and web login users z when an acl is directly applied to hardware for packet filtering, the switch will permit packets if the packets do not match the acl. Z when an acl is referenced by upper-layer software to control telnet, snmp ...
Page 410
1-4 an absolute time range on switch 4500 series can be within the range 1970/1/1 00:00 to 2100/12/31 24:00. Configuration procedure follow these steps to configure a time range: to do... Use the command... Remarks enter system view system-view — create a time range time-range time-name { start-time...
Page 411
1-5 system-view [sysname] time-range test from 15:00 1/28/2006 to 15:00 1/28/2008 [sysname] display time-range test current time is 13:30:32 apr/16/2005 saturday time-range : test ( inactive ) from 15:00 jan/28/2006 to 15:00 jan/28/2008 configuring basic acl a basic acl filters packets based on thei...
Page 412
1-6 configuration example # configure acl 2000 to deny packets whose source ip addresses are 192.168.0.1. System-view [sysname] acl number 2000 [sysname-acl-basic-2000] rule deny source 192.168.0.1 0 # display the configuration information of acl 2000. [sysname-acl-basic-2000] display acl 2000 basic...
Page 413
1-7 note that: z with the config match order specified for the advanced acl, you can modify any existent rule. The unmodified part of the rule remains. With the auto match order specified for the acl, you cannot modify any existent rule; otherwise the system prompts error information. Z if you do no...
Page 416
1-10 acl's step is 1 rule 0 deny 06 ff 27 applying acl rules on ports by applying acl rules on ports, you can filter packets on the corresponding ports. Configuration prerequisites you need to define an acl before applying it on a port. For information about defining an acl, refer to configuring bas...
Page 418
1-12 configuration procedure # define acl 2000. System-view [sysname] acl number 2000 [sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0 [sysname-acl-basic-2000] quit # reference acl 2000 on vty user interface to control telnet login users. [sysname] user-interface vty 0 4 [sysname-ui-vty...
Page 419
1-13 network diagram figure 1-3 network diagram for basic acl configuration configuration procedure # define a periodic time range that is active from 8:00 to 18:00 everyday. System-view [sysname] time-range test 8:00 to 18:00 daily # define acl 2000 to filter packets with the source ip address of 1...
Page 420
1-14 configuration procedure # define a periodic time range that is active from 8:00 to 18:00 everyday. System-view [sysname] time-range test 8:00 to 18:00 working-day # define acl 3000 to filter packets destined for wage query server. [sysname] acl number 3000 [sysname-acl-adv-3000] rule 1 deny ip ...
Page 421
1-15 user-defined acl configuration example network requirements as shown in figure 1-6 , pc 1 and pc 2 are connected to the switch through ethernet 1/0/1 and ethernet 1/0/2 respectively. They belong to vlan 1 and access the internet through the same gateway, which has an ip address of 192.168.0.1 (...
Page 422
1-16 network diagram figure 1-7 network diagram for applying an acl to a vlan eth1/0/1 pc 1 pc 3 database server pc 2 vlan 10 eth1/0/2 eth1/0/3 192.168.1.2 configuration procedure # define a periodic time range that is active from 8:00 to 18:00 in working days. System-view [sysname] time-range test ...
Page 423: Table of Contents
I table of contents 1 qos configuration·····································································································································1-1 overview ···················································································································...
Page 424: Qos Configuration
1-1 1 qos configuration when configuring qos, go to these sections for information you are interested in: z overview z qos supported by switch 4500 series z qos configuration z displaying and maintaining qos z qos configuration examples overview introduction to qos quality of service (qos) is a conc...
Page 425
1-2 and vod. As for other applications, such as transaction processing and telnet, although bandwidth is not as critical, a too long delay may cause unexpected results. That is, they need to get serviced in time even if congestion occurs. Newly emerging applications demand higher service performance...
Page 426
1-3 qos supported by switch 4500 series the switch 4500 series support the qos features listed in table 1-1 : table 1-1 qos features supported by switch 4500 series qos feature description refer to … traffic classification classify incoming traffic based on acls. The switch 4500 series support the f...
Page 427
1-4 protocol or the port number of an application. Normally, traffic classification is done by checking the information carried in packet header. Packet payload is rarely adopted for traffic classification. The identifying rule is unlimited in range. It can be a quintuplet consisting of source addre...
Page 428
1-5 z assured forwarding (af) class: this class is further divided into four subclasses (af1/2/3/4) and a subclass is further divided into three drop priorities, so the af service level can be segmented. The qos rank of the af class is lower than that of the ef class; z class selector (cs) class: th...
Page 429
1-6 2) 802.1p priority 802.1p priority lies in layer 2 packet headers and is applicable to occasions where the layer 3 packet header does not need analysis but qos must be assured at layer 2. Figure 1-3 an ethernet frame with an 802.1q tag header as shown in the figure above, the 4-byte 802.1q tag h...
Page 430
1-7 priority trust mode after a packet enters a switch, the switch sets the 802.1p priority and local precedence for the packet according to its own capability and the corresponding rules. 1) for a packet carrying no 802.1q tag when a packet carrying no 802.1q tag reaches the port of a switch, the s...
Page 431
1-8 priority marking the priority marking function is to reassign priority for the traffic matching an acl referenced for traffic classification. Z if 802.1p priority marking is configured, the traffic will be mapped to the local precedence corresponding to the re-marked 802.1p priority and assigned...
Page 432
1-9 enough to forward the packets, the traffic is conforming to the specification; otherwise, the traffic is nonconforming or excess. Parameters concerning token bucket include: z average rate: the rate at which tokens are put into the bucket, namely, the permitted average rate of the traffic. It is...
Page 433
1-10 the switch 4500 series support three queue scheduling algorithms: strict priority (sp) queuing, weighted fair queuing (wfq), and weighted round robin (wrr) queuing. 1) sp queuing figure 1-6 diagram for sp queuing sp queue-scheduling algorithm is specially designed for critical service applicati...
Page 434
1-11 figure 1-7 diagram for wfq queuing before wfq is introduced, you must understand fair queuing (fq) first. Fq is designed for the purpose of sharing network resources fairly and optimizing the delays and delay jitters of all the flows. It takes the interests of all parties into account, such as:...
Page 435
1-12 figure 1-8 diagram for wrr queuing wrr queue-scheduling algorithm schedules all the queues in turn and every queue can be assured of a certain service time. In a typical 3com switch there are eight output queues on each port. Wrr configures a weight value for each queue, for example: w7, w6, w5...
Page 436
1-13 in wred algorithm, an upper limit and a lower limit are set for each queue, and the packets in a queue are processed as follows. Z when the current queue length is smaller than the lower limit, no packet is dropped; z when the queue length exceeds the upper limit, all the newly received packets...
Page 437
1-14 configuration procedure follow these steps to configure to trust port priority: to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure to trust port priority and configure the port priority priority priority...
Page 438
1-15 configuration procedure follow these steps to configure the mapping between 802.1p priority and local precedence: to do… use the command… remarks enter system view system-view — configure the mapping between 802.1p priority and local precedence qos cos-local-precedence-map cos0-map-local-prec c...
Page 439
1-16 configuration example z set the ip precedence of icmp packets to 3. Z display the configuration. Configuration procedure: system-view [sysname] protocol-priority protocol-type icmp ip-precedence 3 [sysname] display protocol-priority protocol: icmp ip-precedence: flash(3) marking packet priority...
Page 441
1-18 to do… use the command… remarks configure traffic policing traffic-limit inbound acl-rule [ union-effect ] target-rate [ burst-bucket burst-bucket-size ] [ exceed action ] required specify a committed information rate (cir) for the target-rate argument, and specify a committed bust size (cbs) f...
Page 444
1-21 z the queue scheduling algorithm specified by using the queue-scheduler command in system view takes effect on all the ports. The queue scheduling algorithm configured in port view must be the same as that configured in system view. Otherwise, the system prompts configuration errors. Z if the w...
Page 445
1-22 to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure wred wred queue-index qstart probability required by default, wred is not configured. Configuration example configure wred for queue 2 of ethernet 1/0/1...
Page 446
1-23 for information about the mirroring-groupmonitor-port command and the monitor-port command, refer to the part talking about mirroring. Configuration example network requirements: z ethernet 1/0/1 is connected to the 10.1.1.0/24 network segment. Z duplicate the packets from network segment 10.1....
Page 447
1-24 qos configuration examples configuration example of traffic policing and line rate network requirement an enterprise network connects all the departments through an ethernet switch. Pc 1, with the ip address 192.168.0.1 belongs to the r&d department and is connected to ethernet 1/0/1 of the swi...
Page 448
1-25 configuration example of priority marking and queue scheduling network requirements as shown in figure 1-10 , an enterprise network connects all the departments through an ethernet switch. Clients pc 1 through pc 3 are connected to ethernet 1/0/1 of the switch; clients pc 4 through pc 6 are con...
Page 449
1-26 [sysname-ethernet1/0/2] traffic-priority inbound ip-group 3000 rule 1 local-precedence 3 [sysname-ethernet1/0/2] traffic-priority inbound ip-group 3000 rule 2 local-precedence 2 [sysname-ethernet1/0/2] quit 3) configure queue scheduling # apply sp queue scheduling algorithm. [sysname] queue-sch...
Page 450
1-27 configuration procedure # create customer vlans vlan 100 and vlan 200 and service vlans vlan 500 and vlan 600 on switch a. System-view [switcha] vlan 100 [switcha-vlan100] quit [switcha] vlan 200 [switcha-vlan200] quit [switcha] vlan 500 [switcha-vlan500] quit [switcha] vlan 600 [switcha-vlan60...
Page 451
1-28 # configure vlan mapping on ethernet 1/0/11 to replace vlan tag 100 with vlan tag 500. [switcha] interface ethernet 1/0/11 [switcha-ethernet1/0/11] traffic-remark-vlanid inbound link-group 4000 remark-vlan 500 [switcha-ethernet1/0/11] quit # configure vlan mapping on ethernet 1/0/12 to replace ...
Page 452: Table of Contents
I table of contents 1 mirroring configuration ····························································································································1-1 mirroring overview············································································································...
Page 453: Mirroring Configuration
1-1 1 mirroring configuration when configuring mirroring, go to these sections for information you are interested in: z mirroring overview z mirroring configuration z displaying and maintaining port mirroring z mirroring configuration examples mirroring overview mirroring is to duplicate packets fro...
Page 454
1-2 remote port mirroring remote port mirroring does not require the source and destination ports to be on the same device. The source and destination ports can be located on multiple devices across the network. This allows an administrator to monitor traffic on remote devices conveniently. To imple...
Page 455
1-3 switch ports involved function intermediate switch trunk port sends mirrored packets to the destination switch. Two trunk ports are necessary for the intermediate switch to connect the devices at the source switch side and the destination switch side. Trunk port receives remote mirrored packets....
Page 456
1-4 configuring local port mirroring configuration prerequisites z the source port is determined and the direction in which the packets are to be mirrored is determined. Z the destination port is determined. Configuration procedure follow these steps to configure port mirroring on switch 4500 series...
Page 457
1-5 configuration on a switch acting as a source switch 1) configuration prerequisites z the source port, the reflector port, and the remote-probe vlan are determined. Z layer 2 connectivity is ensured between the source and destination switches over the remote-probe vlan. Z the direction of the pac...
Page 458
1-6 cannot be configured with functions like vlan-vpn, port loopback detection, packet filtering, qos, port security, and so on. Z you cannot modify the duplex mode, port rate, and mdi attribute of a reflector port. Z only an existing static vlan can be configured as the remote-probe vlan. To remove...
Page 459
1-7 to do… use the command… remarks enter system view system-view — create a vlan and enter vlan view vlan vlan-id vlan-id is the id of the remote-probe vlan. Configure the current vlan as a remote-probe vlan remote-probe vlan enable required return to system view quit — enter the view of the ethern...
Page 460
1-8 mirroring configuration examples local port mirroring configuration example network requirements the departments of a company connect to each other through switch 4500 series: z research and development (r&d) department is connected to switch c through ethernet 1/0/1. Z marketing department is c...
Page 461
1-9 ethernet1/0/1 both ethernet1/0/2 both monitor port: ethernet1/0/3 after the configurations, you can monitor all packets received on and sent from the r&d department and the marketing department on the data detection device. Remote port mirroring configuration example network requirements the dep...
Page 462
1-10 configuration procedure 1) configure the source switch (switch a) # create remote source mirroring group 1. System-view [sysname] mirroring-group 1 remote-source # configure vlan 10 as the remote-probe vlan. [sysname] vlan 10 [sysname-vlan10] remote-probe vlan enable [sysname-vlan10] quit # con...
Page 463
1-11 [sysname-ethernet1/0/2] port trunk permit vlan 10 3) configure the destination switch (switch c) # create remote destination mirroring group 1. System-view [sysname] mirroring-group 1 remote-destination # configure vlan 10 as the remote-probe vlan. [sysname] vlan 10 [sysname-vlan10] remote-prob...
Page 464: Table of Contents
I table of contents 1 xrn fabric configuration·························································································································1-1 introduction to xrn··············································································································...
Page 465: Xrn Fabric Configuration
1-1 1 xrn fabric configuration when configuring xrn fabric, go to these sections for information you are interested in: z introduction to xrn z xrn fabric configuration z displaying and maintaining xrn fabric z xrn fabric configuration example introduction to xrn expandable resilient networking (xrn...
Page 466
1-2 figure 1-2 port connection mode for switch 4500 series bus topology xrn fabric mode green=speed yellow=duplex rps pwr console unit 1000 base - x 1 speed:green=100mbps ,yellow=10mbps 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 duplx:green=full duplx ,yellow=half duplx...
Page 467
1-3 z the number of the existing devices in the fabric does not reach the maximum number of devices allowed by the fabric (up to eight devices can form a fabric). Z the fabric name of the device and the existing devices in the fabric are the same. Z the software version of the device is the same as ...
Page 468
1-4 status analysis solution of the fabric are not the same, or the password configured does not match. Passwords for the local device and the fabric as the same. How xrn works when a fabric is established, the devices determine their respective roles in the fabric by comparing their cpu mac address...
Page 469
1-5 task remarks fabric setting a unit id for a switch optional assigning a unit name to a switch optional assigning an xrn fabric name to a switch optional setting the xrn fabric authentication mode optional specifying the fabric port of a switch you can specify the fabric port of a switch in eithe...
Page 470
1-6 z establishing an xrn system requires a high consistency of the configuration of each device. Hence, before you enable the fabric port, do not perform any configuration for the port, and do not configure some functions that affect the xrn for other ports or globally. Otherwise, you cannot enable...
Page 471
1-7 setting a unit id for a switch on the switches that support automatic numbering, ftm will automatically number the switches to constitute an xrn fabric by default, so that each switch has a unique unit id in the fabric. You can use the command in the following table to set unit ids for switches....
Page 472
1-8 z if auto-numbering is selected, the system sets the unit priority to 10. You can use the fabric save-unit-id command to save the modified unit id into the unit flash memory and clear the information about the existing one. Priority is the reference for ftm program to perform automatic numbering...
Page 474
1-10 network diagram figure 1-3 network diagram for forming an xrn fabric configuration procedure 1) configure switch a. # configure fabric ports. System-view [sysname] fabric-port gigabitethernet1/0/25 enable # configure the unit name as unit 1. [sysname] set unit 1 name unit1 # configure the fabri...
Page 475
1-11 # configure the unit name as unit 3. [sysname] set unit 1 name unit3 # configure the fabric name as hello. [sysname] sysname hello # configure the fabric authentication mode as simple and the password as welcome. [hello] xrn-fabric authentication-mode simple welcome 4) configure switch d. # con...
Page 476: Table of Contents
I table of contents 1 cluster ························································································································································1-1 cluster overview··································································································...
Page 477: Cluster
1-1 1 cluster when configuring cluster, go to these sections for information you are interested in: z cluster overview z cluster configuration task list z displaying and maintaining cluster configuration z cluster configuration examples cluster overview introduction to hgmp a cluster contains a grou...
Page 478
1-2 figure 1-1 a cluster implementation hgmp v2 has the following advantages: z it eases the configuration and management of multiple switches: you just need to configure a public ip address for the management device instead of for all the devices in the cluster; and then you can configure and manag...
Page 479
1-3 table 1-1 description on cluster roles role configuration function management device configured with a external ip address z provides an interface for managing all the switches in a cluster z manages member devices through command redirection, that is, it forwards the commands intended for speci...
Page 480
1-4 z a candidate device becomes a member device after being added to a cluster. Z a member device becomes a candidate device after it is removed from the cluster. Z a management device becomes a candidate device only after the cluster is removed. After you create a cluster on a switch 4500 switch, ...
Page 481
1-5 packet data. The receiving devices store the information carried in the ndp packet into the ndp table but do not forward the ndp packet. When they receive another ndp packet, if the information carried in the packet is different from the stored one, the corresponding entry in the ndp table is up...
Page 482
1-6 z to implement ntdp, you need to enable ntdp both globally and on specific ports on the management device, and configure ntdp parameters. Z on member/candidate devices, you only need to enable ntdp globally and on specific ports. Z member and candidate devices adopt the ntdp settings of the mana...
Page 483
1-7 figure 1-3 state machine of the connection between the management device and a member device receives the handshake or management packets fails to receive handshake packets in three consecutive intervals state holdtime exceeds the specified value disconnect state is recovered active connect disc...
Page 484
1-8 z enabling the management packets (including ndp packets, ntdp packets, and handshake packets) to be transmitted in the management vlan only, through which the management packets are isolated from other packets and network security is improved. Z enabling the management device and the member dev...
Page 485
1-9 downstream switch compares its own mac address with the destination mac address carried in the multicast packet: z if the two mac addresses are the same, the downstream switch sends a response to the switch sending the tracemac command, indicating the success of the tracemac command. Z if the tw...
Page 486
1-10 task remarks enabling ndp globally and on specific ports required configuring ndp-related parameters optional enabling ntdp globally and on a specific port required configuring ntdp-related parameters optional enabling the cluster function required configuring cluster parameters required config...
Page 487
1-11 configuring ndp-related parameters follow these steps to configure ndp-related parameters: to do… use the command… remarks enter system view system-view — configure the holdtime of ndp information ndp timer aging aging-in-seconds optional by default, the holdtime of ndp information is 180 secon...
Page 488
1-12 to do… use the command… remarks launch topology information collection manually ntdp explore optional enabling the cluster function follow these steps to enable the cluster function: to do… use the command… remarks enter system view system-view — enable the cluster function globally cluster ena...
Page 490
1-14 z the cluster switches are properly connected; z the shared servers are properly connected to the management switch. 2) configuration procedure follow these steps to configure the network management interface for a cluster: to do… use the command… remarks enter system view system-view — enter c...
Page 491
1-15 to reduce the risk of being attacked by malicious users against opened socket and enhance switch security, the switch 4500 series ethernet switches provide the following functions, so that a cluster socket is opened only when it is needed: z opening udp port 40000 (used for cluster) only when t...
Page 492
1-16 to do… use the command… remarks enter ethernet port view interface interface-type interface-number — enable ntdp on the port ntdp enable required enabling the cluster function follow these steps to enable the cluster function: to do… use the command… remarks enter system view system-view — enab...
Page 494
1-18 configuring the enhanced cluster features complete the following tasks to configure the enhanced cluster feature: task remarks configuring cluster topology management function required configuring cluster device blacklist required configuring cluster topology management function 1) configuratio...
Page 495
1-19 if the management device of a cluster is a slave device in an xrn fabric, the standard topology information is saved only to the local flash of the master device in the xrn fabric. Configuring cluster device blacklist follow these steps to configure the cluster device blacklist on a management ...
Page 496
1-20 z ndp and ntdp have been enabled on the management device and member devices, and ndp- and ntdp-related parameters have been configured. Z a cluster is established, and you can manage the member devices through the management device. 2) configuration procedure perform the following operations o...
Page 497
1-21 z the mib view name is mib_a, which includes all objects of the subtree org z the snmpv3 user is user_a, which belongs to the group group_a. # create a community with the name of read_a, allowing read-only access right using this community name. [test_0.Sysname-cluster] cluster-snmp-agent commu...
Page 498
1-22 snmp-agent community read read_a@cm0 snmp-agent community write write_a@cm0 snmp-agent sys-info version all snmp-agent group v3 group_a snmp-agent mib-view included mib_a org snmp-agent usm-user v3 user_a group_a undo snmp-agent trap enable standard z configuration file content on a member devi...
Page 499
1-23 z perform the above operations on the management device of the cluster. Z creating a public local user is equal to executing these configurations on both the management device and the member devices (refer to the aaa operation part in this manual), and these configurations will be saved to the ...
Page 500
1-24 cluster configuration examples basic cluster configuration example network requirements three switches compose a cluster, where: z a switch 4500 series switch serves as the management device. Z the rest are member devices. Serving as the management device, the switch 4500 switch manages the two...
Page 501
1-25 [sysname] ntdp enable [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] ntdp enable [sysname-ethernet1/0/1] quit # enable the cluster function. [sysname] cluster enable 2) configure the management device # add port ethernet 1/0/1 to vlan 2. System-view [sysname] vlan 2 [sysname-vlan2] ...
Page 502
1-26 # set the delay for a member device to forward topology collection requests to 150 ms. [sysname] ntdp timer hop-delay 150 # set the delay for a member device port to forward topology collection requests to 15 ms. [sysname] ntdp timer port-delay 15 # set the interval between collecting topology ...
Page 504
1-28 system-view [sysname] management-vlan 3 # add ethernet 1/0/1 to vlan 3. [sysname] vlan 3 [sysname-vlan3] port ethernet 1/0/1 [sysname-vlan3] quit # set the ip address of vlan-interface 3 to 192.168.5.30. [sysname] interface vlan-interface 3 [sysname-vlan-interface3] ip address 192.168.5.30 255....
Page 505
1-29 network diagram figure 1-6 network diagram for the enhanced cluster feature configuration ftp server 192.168.0.4 2 4 3 192.168.0.1 0001- 2034-a0e5 management device member device member device member device 1 configuration procedure # enter cluster view. System-view [aaa_0.Sysname] cluster # ad...
Page 506: Table of Contents
I table of contents 1 poe configuration ·····································································································································1-1 poe overview ··············································································································...
Page 507: Poe Configuration
1-1 1 poe configuration when configuring poe, go to these sections for information you are interested in: z poe overview z poe configuration z poe configuration example poe overview introduction to poe power over ethernet (poe)-enabled devices use twisted pairs through electrical ports to supply pow...
Page 508
1-2 z through the fixed 24/48 ethernet electrical ports, it can supply power to up to 24/48 remote ethernet switches with a maximum distance of 100 m (328 feet). Z each ethernet electrical port can supply at most a power of 15,400 mw to a pd. Z when ac power input is adopted for the switch, the maxi...
Page 509
1-3 task remarks upgrading the pse processing software online optional upgrading the pse processing software of fabric switches online optional displaying poe configuration optional enabling the poe feature on a port follow these steps to enable the poe feature on a port: to do… use the command… rem...
Page 510
1-4 z auto : when the switch is close to its full load in supplying power, it will first supply power to the pds that are connected to the ports with critical priority, and then supply power to the pds that are connected to the ports with high priority. For example: port a has the priority of critic...
Page 511
1-5 configuring the pd compatibility detection function after the pd compatibility detection function is enabled, the switch can detect the pds that do not conform to the 802.3af standard and supply power to them. After the poe feature is enabled, perform the following configuration to enable the pd...
Page 512
1-6 z when the internal temperature of the switch decreases from x (x>65°c, or x>149°f) to y (60°c≤y ports. Z when the internal temperature of the switch increases from x (x (60°c ports. Upgrading the pse processing software online the online upgrading of pse processing software can update the proce...
Page 514
1-8 network diagram figure 1-1 network diagram for poe configuration procedure # upgrade the pse processing software online. System-view [switcha] poe update refresh 0290_021.S19 # enable the poe feature on ethernet 1/0/1, and set the poe maximum output power of ethernet 1/0/1 to 12,000 mw. [switcha...
Page 515: Poe Profile Configuration
2-1 2 poe profile configuration when configuring poe profile, go to these sections for information you are interested in: z introduction to poe profile z poe profile configuration z displaying poe profile configuration z poe profile configuration example introduction to poe profile on a large-sized ...
Page 518
2-4 network diagram figure 2-1 poe profile application network ip phone switch a ap ip phone ip phone ip phone ap ap ap eth1/0/1~eth1/0/5 eth1/0/6~eth1/0/10 configuration procedure # create profile 1, and enter poe profile view. System-view [switcha] poe-profile profile1 # in profile 1, add the poe ...
Page 519
2-5 [switcha-poe-profile-profile2] poe mode signal [switcha-poe-profile-profile2] poe priority high [switcha-poe-profile-profile2] poe max-power 15400 [switcha-poe-profile-profile2] quit # display detailed configuration information for profile2. [switcha] display poe-profile name profile2 poe-profil...
Page 520: Table of Contents
I table of contents 1 udp helper configuration ························································································································1-1 introduction to udp helper ······································································································...
Page 521: Udp Helper Configuration
1-1 1 udp helper configuration when configuring udp helper, go to these sections for information you are interested in: z introductiontoudphelper z configuring udp helper z displaying and maintaining udp helper z udp helper configuration example introduction to udp helper sometimes, a host needs to ...
Page 523
1-3 to do… use the command… remarks clear statistics about packets forwarded by udp helper reset udp-helper packet available in user view udp helper configuration example cross-network computer search through udp helper network requirements pc a resides on network segment 192.168.1.0/24 and pc b on ...
Page 524: Table of Contents
I table of contents 1 snmp configuration··································································································································1-1 snmp overview·················································································································...
Page 525: Snmp Configuration
1-1 1 snmp configuration when configuring snmp, go to these sections for information you are interested in: z snmp overview z configuring basic snmp functions z configuring trap-related functions z enabling logging for network management z displaying snmp z snmp configuration example snmp overview t...
Page 526
1-2 z set the permission for a community to access an mib object to be read-only or read-write. Communities with read-only permissions can only query the switch information, while those with read-write permission can configure the switch as well. Z set the basic acl specified by the community name. ...
Page 531
1-7 z perform the following configuration on switch a: setting the community name and access permission, administrator id, contact and switch location, and enabling the switch to sent traps. Thus, the nms is able to access switch a and receive the traps sent by switch a. Network diagram figure 1-2 n...
Page 532
1-8 [sysname] snmp-agent trap enable standard linkdown [sysname] snmp-agent target-host trap address udp-domain 10.10.10.1 udp-port 5000 params securityname public configuring the nms authentication-related configuration on an nms must be consistent with that of the devices for the nms to manage the...
Page 533: Rmon Configuration
2-1 2 rmon configuration when configuring rmon, go to these sections for information you are interested in: z introduction to rmon z rmon configuration z displaying rmon z rmon configuration example introduction to rmon remote monitoring (rmon) is a kind of mib defined by internet engineering task f...
Page 534
2-2 statistics and performance statistics of the network segments to which the ports of the managed network devices are connected. Thus, the nms can further manage the networks. Commonly used rmon groups event group event group is used to define the indexes of events and the processing methods of th...
Page 535
2-3 statistics group statistics group contains the statistics of each monitored port on a switch. An entry in a statistics group is an accumulated value counting from the time when the statistics group is created. The statistics include the number of the following items: collisions, packets with cyc...
Page 536
2-4 z the rmon alarm and rmon prialarm commands take effect on existing nodes only. Z for each port, only one rmon statistics entry can be created. That is, if an rmon statistics entry is already created for a given port, you will fail to create another statistics entry with a different index for th...
Page 537
2-5 [sysname-ethernet1/0/1] quit # add the event entries numbered 1 and 2 to the event table, which will be triggered by the following extended alarm. [sysname] rmon event 1 log [sysname] rmon event 2 trap 10.21.30.55 # add an entry numbered 2 to the extended alarm table to allow the system to calcu...
Page 538: Table of Contents
I table of contents 1 ntp configuration ·····································································································································1-1 introduction to ntp ·······································································································...
Page 539: Ntp Configuration
1-1 1 ntp configuration when configuring ntp, go to these sections for information you are interested in: z introduction to ntp z ntp configuration task list z configuring ntp implementation modes z configuring access control right z configuring ntp authentication z configuring optional ntp paramete...
Page 540
1-2 z defining the accuracy of clocks by stratum to synchronize the clocks of all devices in a network quickly z supporting access control (see section configuring access control right ) and md5 encrypted authentication (see section configuring ntp authentication ) z sending protocol packets in unic...
Page 541
1-3 figure 1-1 implementation principle of ntp ip network ip network ip network ip network device b device a device b device a device b device a device b device a 10:00:00 am 11:00:01 am 10:00:00 am ntp message 10:00:00 am 11:00:01 am 11:00:02 am ntp message ntp message ntp message received at 10:00...
Page 542
1-4 server/client mode figure 1-2 server/client mode symmetric peer mode figure 1-3 symmetric peer mode passive peer clock synchronization request packet synchronize network active peer works in passive peer mode automatically in peer mode, both sides can be synchronized to each other response packe...
Page 543
1-5 multicast mode figure 1-5 multicast mode table 1-1 describes how the above mentioned ntp modes are implemented on 3com s4500 series ethernet switches. Table 1-1 ntp implementation modes on 3com s4500 series ethernet switches ntp implementation mode configuration on s4500 series switches server/c...
Page 544
1-6 z when a 3com s4500 ethernet switch works in server mode or symmetric passive mode, you need not to perform related configurations on this switch but do that on the client or the symmetric-active peer. Z the ntp server mode, ntp broadcast mode, or ntp multicast mode takes effect only after the l...
Page 545
1-7 z execution of one of the ntp-service unicast-server, ntp-service unicast-peer, ntp-service broadcast-client , ntp-service broadcast-server, ntp-service multicast-client, and ntp-service multicast-server commands enables the ntp feature and opens udp port 123 at the same time. Z execution of the...
Page 548
1-10 to do… use the command… remarks enter system view system-view — enter vlan interface view interface vlan-interface vlan-id — configure the switch to work in the ntp multicast client mode ntp-service multicast-client [ ip-address ] required not configured by default. Configuring access control r...
Page 549
1-11 the access-control right mechanism provides only a minimum degree of security protection for the local switch. A more secure method is identity authentication. Configuring ntp authentication in networks with higher security requirements, the ntp authentication function must be enabled to run nt...
Page 550
1-12 configuration procedure configuring ntp authentication on the client follow these steps to configure ntp authentication on the client: to do… use the command… remarks enter system view system-view — enable the ntp authentication function ntp-service authentication enable required disabled by de...
Page 551
1-13 to do… use the command… remarks configure the specified key as a trusted key ntp-service reliable authentication-keyid key-id required by default, no trusted authentication key is configured. Enter vlan interface view interface vlan-interface vlan-id — configure on the ntp broadcast server ntp-...
Page 552
1-14 if you have specified an interface in the ntp-service unicast-server or ntp-service unicast-peer command, this interface will be used for sending ntp messages. Configuring the number of dynamic sessions allowed on the local switch a single device can have a maximum of 128 associations at the sa...
Page 553
1-15 to do… use the command… remarks display the information about the sessions maintained by ntp display ntp-service sessions [ verbose ] display the brief information about ntp servers along the path from the local device to the reference clock source display ntp-service trace configuration exampl...
Page 554
1-16 [deviceb] display ntp-service status clock status: synchronized clock stratum: 3 reference clock id: 1.0.1.11 nominal frequency: 100.0000 hz actual frequency: 100.0000 hz clock precision: 2^18 clock offset: 0.66 ms root delay: 27.47 ms root dispersion: 208.39 ms peer dispersion: 9.63 ms referen...
Page 555
1-17 configuration procedure z configure device c. # set device a as the ntp server. System-view [devicec] ntp-service unicast-server 3.0.1.31 z configure device b (after the device c is synchronized to device a). # enter system view. System-view # set device c as the peer of device b. [deviceb] ntp...
Page 556
1-18 configuring ntp broadcast mode network requirements z the local clock of device c is set as the ntp master clock, with a stratum level of 2. Configure device c to work in the ntp broadcast server mode and send ntp broadcast messages through vlan-interface 2. Z device a and device d are two s450...
Page 557
1-19 view the ntp status of device d after the clock synchronization. [deviced] display ntp-service status clock status: synchronized clock stratum: 3 reference clock id: 3.0.1.31 nominal frequency: 100.0000 hz actual frequency: 100.0000 hz clock precision: 2^18 clock offset: 198.7425 ms root delay:...
Page 558
1-20 network diagram figure 1-9 network diagram for ntp multicast mode configuration configuration procedure z configure device c. # enter system view. System-view # set device c as a multicast server to send multicast messages through vlan-interface 2. [devicec] interface vlan-interface 2 [devicec-...
Page 559
1-21 root dispersion: 208.39 ms peer dispersion: 9.63 ms reference time: 17:03:32.022 utc apr 2 2007 (bf422ae4.05aea86c) the output information indicates that device d is synchronized to device c, with a clock stratum level of 3, one stratum level lower than that device c. # view the information abo...
Page 560
1-22 z to synchronize device b, you need to perform the following configurations on device a. # enable the ntp authentication function. System-view [devicea] ntp-service authentication enable # configure an md5 authentication key, with the key id being 42 and the key being anicekey. [devicea] ntp-se...
Page 561: Table of Contents
I table of contents 1 ssh configuration·····································································································································1-1 ssh overview················································································································...
Page 562: Ssh Configuration
1-1 1 ssh configuration when configuring ssh, go to these sections for information you are interested: z ssh overview z ssh server and client z displaying and maintaining ssh configuration z comparison of ssh commands with the same functions z ssh configuration examples ssh overview introduction to ...
Page 563
1-2 the same key is used for both encryption and decryption. Supported symmetric key algorithms include des, 3des, and aes, which can effectively prevent data eavesdropping. Z asymmetric key algorithm asymmetric key algorithm is also called public key algorithm. Both ends have their own key pair, co...
Page 564
1-3 currently, the switch supports only ssh2 version. Version negotiation z the server opens port 22 to listen to connection requests from clients. Z the client sends a tcp connection request to the server. After the tcp connection is established, the server sends the first packet to the client, whi...
Page 565
1-4 z the server starts to authenticate the user. If authentication fails, the server sends an authentication failure message to the client, which contains the list of methods used for a new authentication process. Z the client selects an authentication type from the method list to perform authentic...
Page 566
1-5 figure 1-2 network diagram for ssh connections configure the devices accordingly this document describes two cases: z the 3com switch acts as the ssh server to cooperate with software that supports the ssh client functions. Z the 3com switch acts as the ssh server to cooperate with another 3com ...
Page 567
1-6 task remarks configuring the user interfaces for ssh clients required preparation configuring the ssh management functions optional key configuring key pairs required authentication creating an ssh user and specifying an authentication type required authorization specifying a service type for an...
Page 569
1-8 z you can configure a login header only when the service type is stelnet. For configuration of service types, refer to specifying a service type for an ssh user . Z for details of the header command, refer to the corresponding section in login command. Configuring key pairs the ssh server’s key ...
Page 570
1-9 to do… use the command… remarks destroy the rsa key pair public-key local destroy rsa optional creating an ssh user and specifying an authentication type this task is to create an ssh user and specify an authentication type. Specifying an authentication type for a new user is a must to get the u...
Page 572
1-11 if the ssh user service-type command is executed with a username that does not exist, the system will automatically create the ssh user. However, the user cannot log in unless you specify an authentication type for it. Configuring the public key of a client on the server this configuration is n...
Page 573
1-12 to do... Use the command... Remarks enter system view system-view — import the public key from a public key file public-key peer keyname import sshkey filename required assigning a public key to an ssh user this configuration task is unnecessary if the ssh user’s authentication mode is password...
Page 574
1-13 with the filename argument specified, you can export the rsa host public key to a file so that you can configure the key at a remote end by importing the file. If the filename argument is not specified, this command displays the host public key information on the screen in a specified format. C...
Page 575
1-14 task remarks opening an ssh connection with publickey authentication required for publickey authentication; unnecessary for password authentication z for putty, it is recommended to use putty release 0.53; putty release 0.58 is also supported. For openssh, it is recommended to use openssh_3.1p1...
Page 576
1-15 note that while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar in the blue box of shown in figure 1-4 . Otherwise, the process bar stops moving and the key pair generating process is stopped. Figure 1-4 generate the client keys (2) aft...
Page 577
1-16 likewise, to save the private key, click save private key. A warning window pops up to prompt you whether to save the private key without any precaution. Click yes and enter the name of the file for saving the private key (“private” in this case) to save the private key. Figure 1-6 generate the...
Page 578
1-17 figure 1-8 ssh client configuration interface 1 in the host name (or ip address) text box, enter the ip address of the server. Note that there must be a route available between the ip address of the server and the client. Selecting a protocol for remote connection as shown in figure 1-8 , selec...
Page 579
1-18 figure 1-9 ssh client configuration interface 2 under protocol options, select 2 from preferred ssh protocol version. Some ssh client software, for example, tectia client software, supports the des algorithm only when the ssh1 version is selected. The putty client software supports des algorith...
Page 580
1-19 figure 1-10 ssh client configuration interface 3 click browse… to bring up the file selection window, navigate to the private key file and click open. If the connection is normal, a user will be prompted for a username. Once passing the authentication, the user can log in to the server. Configu...
Page 581
1-20 configuring whether first-time authentication is supported when the device connects to the ssh server as an ssh client, you can configure whether the device supports first-time authentication. Z with first-time authentication enabled, an ssh client that is not configured with the server host pu...
Page 582
1-21 follow these steps to specify a source ip address/interface for the ssh client: to do... Use the command... Remarks enter system view system-view — specify a source ip address for the ssh client ssh2 source-ip ip-address optional by default, no source ip address is configured. Specify a source ...
Page 583
1-22 to do... Use the command... Remarks display information about all ssh users display ssh user-information [ username ] display the current source ip address or the ip address of the source interface specified for the ssh server. Display ssh-server source-ip display the mappings between host publ...
Page 584
1-23 the results of the display rsa local-key-pair public command or the public key converted with the sshkey tool contains no information such as the authentication type, so they cannot be directly used as parameters in the public-key peer command. For the same reason, neither can the results of th...
Page 585
1-24 [switch-ui-vty0-4] authentication-mode scheme # enable the user interfaces to support ssh. [switch-ui-vty0-4] protocol inbound ssh [switch-ui-vty0-4] quit # create local client client001, and set the authentication password to abc, protocol type to ssh, and command privilege level to 3 for the ...
Page 586
1-25 figure 1-13 ssh client configuration interface (2) under protocol options, select 2 from preferred ssh protocol version. 3) as shown in figure 1-13 , click open. If the connection is normal, you will be prompted to enter the user name client001 and password abc. Once authentication succeeds, yo...
Page 587
1-26 network diagram figure 1-14 switch acts as server for password and radius authentication configuration procedure 1) configure the radius server this document takes cams version 2.10 as an example to show the basic radius server configurations required. # add an access device. Log in to the cams...
Page 588
1-27 figure 1-15 add an access device # add a user account for device management. From the navigation tree, select user management > user for device management, and then in the right pane, click add to enter the add account page and perform the following configurations: z add a user named hello, and...
Page 589
1-28 generating the rsa key pair on the server is prerequisite to ssh login. # generate rsa key pairs. [switch] public-key local create rsa # set the authentication mode for the user interfaces to aaa. [switch] user-interface vty 0 4 [switch-ui-vty0-4] authentication-mode scheme # enable the user in...
Page 590
1-29 figure 1-17 ssh client configuration interface (1) in the host name (or ip address) text box, enter the ip address of the ssh server. Z from the category on the left pane of the window, select connection > ssh. The window as shown in figure 1-18 appears. Figure 1-18 ssh client configuration int...
Page 591
1-30 under protocol options, select 2 from preferred ssh protocol version. Then, click open. If the connection is normal, you will be prompted to enter the user name hello and the password. Once authentication succeeds, you will log in to the server. The level of commands that you can access after l...
Page 592
1-31 [switch] user-interface vty 0 4 [switch-ui-vty0-4] authentication-mode scheme # enable the user interfaces to support ssh. [switch-ui-vty0-4] protocol inbound ssh [switch-ui-vty0-4] quit # configure the hwtacacs scheme. [switch] hwtacacs scheme hwtac [switch-hwtacacs-hwtac] primary authenticati...
Page 593
1-32 in the host name (or ip address) text box, enter the ip address of the ssh server. 2) from the category on the left pane of the window, select connection > ssh. The window as shown in figure 1-21 appears. Figure 1-21 ssh client configuration interface (2) under protocol options, select 2 from p...
Page 594
1-33 configuration procedure z configure the ssh server # create a vlan interface on the switch and assign an ip address, which the ssh client will use as the destination for ssh connection. System-view [switch] interface vlan-interface 1 [switch-vlan-interface1] ip address 192.168.0.1 255.255.255.0...
Page 595
1-34 figure 1-23 generate a client key pair (1) while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar shown in figure 1-24 . Otherwise, the process bar stops moving and the key pair generating process is stopped..
Page 596
1-35 figure 1-24 generate a client key pair (2) after the key pair is generated, click save public key and enter the name of the file for saving the public key (public in this case). Figure 1-25 generate a client key pair (3) likewise, to save the private key, click save private key. A warning windo...
Page 597
1-36 figure 1-26 generate a client key pair (4) after a public key pair is generated, you need to upload the pubic key file to the server through ftp or tftp, and complete the server end configuration before you continue to configure the client. # establish a connection with the ssh server 2) launch...
Page 598
1-37 figure 1-28 ssh client configuration interface (2) under protocol options, select 2 from preferred ssh protocol version. 4) select connection /ssh/auth.The following window appears. Figure 1-29 ssh client configuration interface (3).
Page 599
1-38 click browse to bring up the file selection window, navigate to the private key file and click ok. 5) from the window shown in figure 1-29 , click open. If the connection is normal, you will be prompted to enter the username. When switch acts as client for password authentication network requir...
Page 600
1-39 [switchb-luser-client001] password simple abc [switchb-luser-client001] service-type ssh level 3 [switchb-luser-client001] quit # configure the authentication type of user client001 as password. [switchb] ssh user client001 authentication-type password z configure switch a # create a vlan inter...
Page 601
1-40 configuration procedure z configure switch b # create a vlan interface on the switch and assign an ip address, which the ssh client will use as the destination for ssh connection. System-view [switchb] interface vlan-interface 1 [switchb-vlan-interface1] ip address 10.165.87.136 255.255.255.0 [...
Page 602
1-41 system-view [switcha] interface vlan-interface 1 [switcha-vlan-interface1] ip address 10.165.87.137 255.255.255.0 [switcha-vlan-interface1] quit # generate a rsa key pair [switcha] public-key local create rsa # export the generated rsa key pair to a file named switch001. [switcha] public-key lo...
Page 603
1-42 network diagram figure 1-32 switch acts as client and first-time authentication is not supported configuration procedure z configure switch b # create a vlan interface on the switch and assign an ip address for it to serve as the destination of the client. System-view [switchb] interface vlan-i...
Page 604
1-43 # import the client’s public key file switch001 and name the public key as switch001. [switchb] public-key peer switch001 import sshkey switch001 # assign public key switch001 to user client001 [switchb] ssh user client001 assign publickey switch001 # export the generated rsa host public key pa...
Page 605
1-44 # import the public key pair named switch002 from the file switch002. [switcha] public-key peer switch002 import sshkey switch002 # specify the host public key pair name of the server. [switcha] ssh client 10.165.87.136 assign publickey switch002 # establish the ssh connection to server 10.165....
Page 606: Table of Contents
I table of contents 1 file system management configuration ·································································································1-1 file system configuration···················································································································...
Page 607
1-1 1 file system management configuration when configuring file system management, go to these sections for information you are interested in: z file system configuration z file attribute configuration z configuration file backup and restoration file system configuration introduction to file system...
Page 608
1-2 directory operations the file system provides directory-related functions, such as: z creating/deleting a directory z displaying the current work directory, or contents in a specified directory follow these steps to perform directory-related operations: to do… use the command… remarks create a d...
Page 609
1-3 to do… use the command… remarks rename a file rename fileurl -source fileurl -dest optional available in user view copy a file copy fileurl -source fileurl-dest optional available in user view move a file move fileurl-source fileurl-dest optional available in user view display the content of a f...
Page 610
1-4 the format operation leads to the loss of all files, including the configuration files, on the flash memory and is irretrievable. Prompt mode configuration you can set the prompt mode of the current file system to alert or quiet. In alert mode, the file system will give a prompt for confirmation...
Page 611
1-5 directory of unit1>flash:/ 1 (*) -rw- 5822215 jan 01 1970 00:07:03 test.Bin 2 -rwh 4 apr 01 2000 23:55:49 snmpboots 3 -rwh 428 apr 02 2000 00:47:30 hostkey 4 -rwh 572 apr 02 2000 00:47:38 serverkey 5 -rw- 1220 apr 02 2000 00:06:57 song.Cfg 6 -rw- 26103 jan 01 1970 00:04:34 testv1r1.Bin 7 -rwh 88...
Page 612
1-6 attribute name description feature identifier backup identifies backup startup files. The backup startup file is used after a switch fails to start up using the main startup file. In the flash memory, there can be only one app file, one configuration file and one web file with the backup attribu...
Page 613
1-7 configuring file attributes you can configure and view the main attribute or backup attribute of the file used for the next startup of a switch, and change the main or backup attribute of the file. Follow these steps to configure file attributes: to do… use the command… remarks configure the app...
Page 614
1-8 configuration file backup and restoration introduction to configuration file backup and restoration formerly, you can only back up and restore the configuration file of the units one by one in a fabric system. By using the configuration file backup and restoration feature, you can easily back up...
Page 615: Table of Contents
I table of contents 1 ftp and sftp configuration····················································································································1-1 introduction to ftp and sftp ·······································································································...
Page 616: Ftp and Sftp Configuration
1-1 1 ftp and sftp configuration when configuring ftp and sftp, go to these sections for information you are interested in: z introduction to ftp and sftp z ftp configuration z sftp configuration introduction to ftp and sftp introduction to ftp file transfer protocol (ftp) is commonly used in ip-bas...
Page 617
1-2 files from an ftp server, and stops rotating when the file downloading is finished, as shown in figure 1-1 . Figure 1-1 clockwise rotating of the seven-segment digital led introduction to sftp secure ftp (sftp) is established based on an ssh2 connection. It allows a remote user to log in to a sw...
Page 619
1-4 follow these steps to configure connection idle time: to do… use the command… remarks enter system view system-view — configure the connection idle time for the ftp server ftp timeout minutes optional 30 minutes by default specifying the source interface and source ip address for an ftp server y...
Page 620
1-5 disconnecting a specified user on the ftp server, you can disconnect a specified user from the ftp server to secure the network. Follow these steps to disconnect a specified user: to do… use the command… remarks enter system view system-view — on the ftp server, disconnect a specified user from ...
Page 621
1-6 figure 1-3 process of displaying a shell banner follow these steps to configure the banner display for an ftp server: to do… use the command… remarks enter system view system-view — configure a login banner header login text configure a shell banner header shell text required use either command ...
Page 623
1-8 to do… use the command… remarks download a remote file from the ftp server get remotefile [ localfile ] upload a local file to the remote ftp server put localfile [ remotefile ] rename a file on the remote server rename remote-source remote-dest log in with the specified user name and password u...
Page 624
1-9 z the specified interface must be an existing one. Otherwise a prompt appears to show that the configuration fails. Z the value of the ip-address argument must be the ip address of the device where the configuration is performed. Otherwise a prompt appears to show that the configuration fails. Z...
Page 625
1-10 [sysname] local-user switch [sysname-luser-switch] password simple hello [sysname-luser-switch] service-type ftp 2) configure the pc (ftp client) run an ftp client application on the pc to connect to the ftp server. Upload the application named switch.Bin to the root directory of the flash memo...
Page 626
1-11 z if available space on the flash memory of the switch is not enough to hold the file to be uploaded, you need to delete files not in use from the flash memory to make room for the file, and then upload the file again. The files in use cannot be deleted. If you have to delete the files in use t...
Page 627
1-12 configuration procedure 1) configure the switch (ftp server) # configure the login banner of the switch as “login banner appears” and the shell banner as “shell banner appears”. For detailed configuration of other network requirements, see section configuration example: a switch operating as an...
Page 628
1-13 configuration procedure 1) configure the pc (ftp server) perform ftp server–related configurations on the pc, that is, create a user account on the ftp server with username switch and password hello. (for detailed configuration, refer to the configuration instruction relevant to the ftp server ...
Page 629
1-14 boot boot-loader switch.Bin reboot for information about the boot boot-loader command and how to specify the startup file for a switch, refer to the system maintenance and debugging module of this manual. Sftp configuration complete the following tasks to configure sftp: task remarks enabling a...
Page 630
1-15 to do… use the command… remarks enter system view system-view — configure the connection idle time for the sftp server ftp timeout time-out-value optional 10 minutes by default. Supported sftp client software a 3com switch 4500 operating as an sftp server can interoperate with sftp client softw...
Page 632
1-17 if you specify to authenticate a client through public key on the server, the client needs to read the local private key when logging in to the sftp server. Since both rsa and dsa are available for public key authentication, you need to use the identity-key key word to specify the algorithms to...
Page 633
1-18 [sysname] public-key local create dsa # create a vlan interface on the switch and assign to it an ip address, which is used as the destination address for the client to connect to the sftp server. [sysname] interface vlan-interface 1 [sysname-vlan-interface1] ip address 192.168.0.1 255.255.255....
Page 634
1-19 sftp-client> # display the current directory of the server. Delete the file z and verify the result. Sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 aug 23 06:52 config.Cfg -rwxrwxrwx 1 noone nogroup 225 aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubkey1 drwxrwxrwx 1 noon...
Page 635
1-20 -rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubkey1 drwxrwxrwx 1 noone nogroup 0 sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 sep 01 06:55 pub drwxrwxrwx 1 noone nogroup 0 sep 02 06:33 new2 received status: end of file received status: success # download the file pubkey2 from the server and ...
Page 636: Tftp Configuration
2-1 2 tftp configuration when configuring tftp, go to these sections for information you are interested in: z introduction to tftp z tftp configuration introduction to tftp compared with ftp, trivial file transfer protocol (tftp) features simple interactive access interface and no authentication con...
Page 637
2-2 tftp configuration complete the following tasks to configure tftp: task remarks basic configurations on a tftp client — tftp configuration: a switch operating as a tftp client specifying the source interface or source ip address for an ftp client optional tftp server configuration for details, s...
Page 639
2-4 network diagram figure 2-1 network diagram for tftp configurations configuration procedure 1) configure the tftp server (pc) start the tftp server and configure the working directory on the pc. 2) configure the tftp client (switch). # log in to the switch. (you can log in to a switch through the...
Page 640
2-5 for information about the boot boot-loader command and how to specify the startup file for a switch, refer to the system maintenance and debugging module of this manual..
Page 641: Table of Contents
I table of contents 1 information center·····································································································································1-1 information center overview ·······························································································...
Page 642: Information Center
1-1 1 information center when configuring information center, go to these sections for information you are interested in: z information center overview z information center configuration z displaying and maintaining information center z information center configuration examples information center ov...
Page 643
1-2 information filtering by severity works this way: information with the severity value greater than the configured threshold is not output during the filtering. Z if the threshold is set to 1, only information with the severity being emergencies will be output; z if the threshold is set to 8, inf...
Page 644
1-3 outputting system information by source module the system information can be classified by source module and then filtered. Some module names and description are shown in table 1-3 . Table 1-3 source module name list module name description 8021x 802.1x module acl access control list module adbm...
Page 645
1-4 module name description sysmib system mib module tac hwtacacs module telnet telnet module tftpc tftp client module vlan virtual local area network module vty virtual type terminal module xm xmodem module default default settings for all the modules to sum up, the major task of the information ce...
Page 646
1-5 z if the address of the log host is specified in the information center of the switch, when logs are generated, the switch sends the logs to the log host in the above format. For detailed information, refer to setting to output system information to a log host . Z there is the syslog process on ...
Page 647
1-6 module the module field represents the name of the module that generates system information. You can enter the info-center source ? Command in system view to view the module list. Refer to table 1-3 for module name and description. Between “module” and “level” is a “/”. Level (severity) system i...
Page 648
1-7 configuring synchronous information output synchronous information output refers to the feature that if the system information such as log, trap, or debugging information is output when the user is inputting commands, the command line prompt (in command editing mode a prompt, or a [y/n] string i...
Page 649
1-8 to do… use the command… remarks set to display the utc time zone in the output information of the information center info-center timestamp utc required by default, no utc time zone is displayed in the output information setting to output system information to the console setting to output system...
Page 650
1-9 log trap debug output destination modules allowed enable d/disab led severit y enabled/ disabled severity enabled/ disabled severity monitor terminal default (all modules) enabled warning s enabled debuggin g enabled debuggin g log host default (all modules) enabled informati onal enabled debugg...
Page 651
1-10 setting to output system information to a monitor terminal follow these steps to set to output system information to a monitor terminal: to do… use the command… remarks enter system view system-view — enable the information center info-center enable optional enabled by default. Enable system in...
Page 652
1-11 to do… use the command… remarks enable trap information terminal display function terminal trapping optional enabled by default make sure that the debugging/log/trap information terminal display function is enabled (use the terminal monitor command) before you enable the corresponding terminal ...
Page 653
1-12 z after the switches form a fabric, you can use the info-center switch-on command to enable the information output for the switches to make the log, debugging and trap information of each switch in the fabric synchronous. Each switch sends its own information to other switches in the fabric and...
Page 656
1-15 # disable the function of outputting information to log host channels, because all modules output log information to the log host channels by default. [switch] undo info-center source default channel loghost # configure the host whose ip address is 202.38.1.10 as the log host. Permit arp and ip...
Page 657
1-16 through combined configuration of the device name (facility), information severity level threshold (severity), module name (filter) and the file “syslog.Conf”, you can sort information precisely for filtering. Log output to a linux log host network requirements the switch sends the following lo...
Page 658
1-17 note the following items when you edit file “/etc/syslog.Conf”. Z a note must start in a new line, starting with a “#" sign. Z in each pair, a tab should be used as a separator instead of a space. Z no space is permitted at the end of the file name. Z the device name (facility) and received log...
Page 659
1-18 system-view [switch] info-center enable # disable the function of outputting information to the console channels. [switch] undo info-center source default channel console # enable log information output to the console. Permit arp and ip modules to output log information with severity level high...
Page 660: Table of Contents
I table of contents 1 boot rom and host software loading ···································································································1-1 introduction to loading approaches ·······································································································1-...
Page 661
1-1 1 boot rom and host software loading traditionally, switch software is loaded through a serial port. This approach is slow, time-consuming and cannot be used for remote loading. To resolve these problems, the tftp and ftp modules are introduced into the switch. With these modules, you can load/d...
Page 662
1-2 the loading process of the boot rom software is the same as that of the host software, except that during the former process, you should press “6” or and after entering the boot menu and the system gives different prompts. The following text mainly describes the boot rom loading process. Boot me...
Page 663
1-3 1. Download application file to flash 2. Select application file to boot 3. Display all files in flash 4. Delete file from flash 5. Modify bootrom password 6. Enter bootrom upgrade menu 7. Skip current configuration file 8. Set bootrom password recovery 9. Set switch startup mode 0. Reboot enter...
Page 664
1-4 0. Return enter your choice (0-5): step 3: choose an appropriate baudrate for downloading. For example, if you press 5, the baudrate 115200 bps is chosen and the system displays the following information: download baudrate is 115200 bit/s please change the terminal's baudrate to 115200 bit/s and...
Page 665
1-5 figure 1-2 console port configuration dialog box step 5: click the button to disconnect the hyperterminal from the switch and then click the button to reconnect the hyperterminal to the switch, as shown in figure 1-3 . Figure 1-3 connect and disconnect buttons the new baudrate takes effect after...
Page 666
1-6 figure 1-4 send file dialog box step 8: click . The system displays the page, as shown in figure 1-5 . Figure 1-5 sending file page step 9: after the sending process completes, the system displays the following information: loading ...Cccccccccc done! Step 10: reset hyperterminal’s baudrate to 9...
Page 667
1-7 loading host software follow these steps to load the host software: step 1: select in boot menu and press . The system displays the following information: 1. Set tftp protocol parameter 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot menu enter your choice(0-3): ...
Page 668
1-8 you can use one pc as both the configuration device and the tftp server. Step 2: run the tftp server program on the tftp server, and specify the path of the program to be downloaded. Tftp server program is not provided with the 3com series ethernet switches. Step 3: run the hyperterminal program...
Page 669
1-9 0. Return to boot menu enter your choice(0-3): step 2: enter 1 in the above menu to download the host software using tftp. The subsequent steps are the same as those for loading the boot rom, except that the system gives the prompt for host software loading instead of boot rom loading. When load...
Page 670
1-10 bootrom update menu: 1. Set tftp protocol parameter 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot menu enter your choice(0-3): step 4: enter 2 in the above menu to download the boot rom using ftp. Then set the following ftp-related parameters as required: load...
Page 671
1-11 remote boot rom and software loading if your terminal is not directly connected to the switch, you can telnet to the switch, and use ftp or tftp to load the boot rom and host software remotely. Remote loading using ftp loading procedure using ftp client 1) loading the boot rom as shown in figur...
Page 672
1-12 before restarting the switch, make sure you have saved all other configurations that you want, so as to avoid losing configuration information. 2) loading host software loading the host software is the same as loading the boot rom program, except that the file to be downloaded is the host softw...
Page 673
1-13 system view: return to user view with ctrl+z. [sysname] interface vlan-interface 1 [sysname-vlan-interface1] ip address 192.168.0.28 255.255.255.0 step 3: enable ftp service on the switch, and configure the ftp user name to test and password to pass. [sysname-vlan-interface1] quit [sysname] ftp...
Page 674
1-14 figure 1-11 enter boot rom directory step 6: enter ftp 192.168.0.28 and enter the user name test, password pass, as shown in figure 1-12 , to log on to the ftp server. Figure 1-12 log on to the ftp server step 7: use the put command to upload the file switch.Btm to the switch, as shown in figur...
Page 675
1-15 figure 1-13 upload file switch.Btm to the switch step 8: configure switch.Btm to be the boot rom at next startup, and then restart the switch. Boot bootrom switch.Btm this will update bootrom on unit 1. Continue? [y/n] y upgrading bootrom, please wait... Upgrade bootrom succeeded! Reboot after ...
Page 676
2-1 2 basic system configuration and debugging when configuring basic system configuration and debugging, go to these sections for information you are interested in: z basic system configuration z displaying the system status z debugging the system basic system configuration perform the following ba...
Page 677
2-2 displaying the system status to do… use the command… remarks display the current date and time of the system display clock display the version of the system display version display the information about users logging onto the switch display users [ all ] available in any view debugging the syste...
Page 678
2-3 you can use the following commands to enable the two switches. Follow these steps to enable debugging and terminal display for a specific module: to do… use the command… remarks enable system debugging for specific module debugging module-name [ debugging-option ] required disabled for all modul...
Page 679: Network Connectivity Test
3-1 3 network connectivity test when configuring network connectivity test, go to these sections for information you are interested in: z ping z tracert network connectivity test ping you can use the ping command to check the network connectivity and the reachability of a host. To do… use the comman...
Page 680: Device Management
4-1 4 device management when configuring device management, go to these sections for information you are interested in: z introduction to device management z device management configuration z displaying the device management configuration z remote switch app upgrade configuration example introductio...
Page 681
4-2 before rebooting, the system checks whether there is any configuration change. If yes, it prompts whether or not to proceed. This prevents the system from losing the configurations in case of shutting down the system without saving the configurations use the following command to reboot the ether...
Page 682
4-3 enabling of this function consumes some amounts of cpu resources. Therefore, if your network has a high cpu usage requirement, you can disable this function to release your cpu resources. Specifying the app to be used at reboot app is the host software of the switch. If multiple apps exist in th...
Page 683
4-4 table 4-1 commonly used pluggable transceivers transceiver type applied environment whether can be an optical transceiver whether can be an electrical transceiver sfp (small form-factor pluggable) generally used for 100m/1000m ethernet interfaces or pos 155m/622m/2.5g interfaces yes yes gbic (gi...
Page 684
4-5 to do… use the command… remarks display the current alarm information of the pluggable transceiver(s) display transceiver alarm interface [interface-type interface-number] available for all pluggable transceivers display the currently measured value of the digital diagnosis parameters of the ant...
Page 685
4-6 z make configuration so that the ip address of a vlan interface on the switch is 1.1.1.1, the ip address of the pc is 2.2.2.2, and the switch and the pc is reachable to each other. The host software switch.App and the boot rom file boot.Btm of the switch are stored in the directory switch on the...
Page 686
4-7 331 give me your password, please password: 230 logged in successfully [ftp] 5) enter the authorized path on the ftp server. [ftp] cd switch 6) execute the get command to download the switch.App and boot.Btm files on the ftp server to the flash memory of the switch. [ftp] get switch.App [ftp] ge...
Page 687: Table of Contents
I table of contents 1 vlan-vpn configuration··························································································································1-1 vlan-vpn overview ················································································································...
Page 688: Vlan-Vpn Configuration
1-1 1 vlan-vpn configuration when configuring vlan-vpn, go to these sections for information you are interested in: z vlan-vpn overview z vlan-vpn configuration z displaying and maintaining vlan-vpn configuration z vlan-vpn configuration example vlan-vpn overview introduction to vlan-vpn virtual pri...
Page 689
1-2 figure 1-2 structure of packets with double-layer vlan tags destination mac address 0 31 data source mac address 15 inner vlan tag outer vlan tag compared with mpls-based layer 2 vpn, vlan-vpn has the following features: z it provides layer 2 vpn tunnels that are simpler. Z vlan-vpn can be imple...
Page 690
1-3 frame as needed. When doing that, you should set the same tpid on both the customer-side port and the service provider-side port. The tpid in an ethernet frame has the same position with the protocol type field in a frame without a vlan tag. To avoid problems in packet forwarding and handling, y...
Page 691
1-4 task remarks enabling the vlan-vpn feature for a port required configuring the tpid value for vlan-vpn packets on a port optional configuring the inner-to-outer tag priority replicating and mapping feature optional as xrn fabric is mutually exclusive with vlan-vpn, make sure that xrn fabric is d...
Page 692
1-5 z besides the default tpid 0x8100, you can configure only one tpid value on a switch 4500 switch. Z for the switch 4500 series to exchange packets with the public network device properly, you should configure the tpid value used by the public network device on both the customer-side port and the...
Page 693
1-6 vlan-vpn configuration example transmitting user packets through a tunnel in the public network by using vlan-vpn network requirements as shown in figure 1-4 , switch a and switch b are both switch 4500 series switches. They connect the users to the servers through the public network. Z pc users...
Page 694
1-7 [switcha-ethernet1/0/11] vlan-vpn enable [switcha-ethernet1/0/11] quit # set the tpid value of ethernet 1/0/12 to 0x9200 (for intercommunication with the devices in the public network) and configure the port as a trunk port permitting packets of vlan 1040. [switcha] interface ethernet 1/0/12 [sw...
Page 695
1-8 2) the tpid value of the outer vlan tag is set to 0x9200 before the packet is forwarded to the public network through ethernet1/0/12 of switch a. 3) the outer vlan tag of the packet remains unchanged while the packet travels in the public network, till it reaches ethernet1/0/22 of switch b. 4) a...
Page 696: Selective Qinq Configuration
2-1 2 selective qinq configuration when configuring selective qinq, go to these sections for information you are interested in: z selective qinq overview z selective qinq configuration z selective qinq configuration example selective qinq overview selective qinq overview selective qinq is an enhance...
Page 697
2-2 telephone users (in vlan 201 to vlan 300). Packets of all these users are forwarded by switch a to the public network. After the selective qinq feature and the inner-to-outer tag mapping feature are enabled on the port connecting switch a to these users, the port will add different outer vlan ta...
Page 698
2-3 device receives a packet from the service provider network, this device will find the path for the packet by searching the mac address table of the vlan corresponding to the outer tag and unicast the packet. Thus, packet broadcast is reduced in selective qinq applications. Likewise, the entries ...
Page 699
2-4 do not enable both the selective qinq function and the dhcp snooping function on a switch. Otherwise, the dhcp snooping function may operate improperly. Enabling the inter-vlan mac address replicating feature follow these steps to enable the inter-vlan mac address replicating feature: to do... U...
Page 700
2-5 z the public network permits packets of vlan 1000 and vlan 1200. Apply qos policies for these packets to reserve bandwidth for packets of vlan 1200. That is, packets of vlan 1200 have higher transmission priority over packets of vlan 1000. Z employ the selective qinq feature on switch a and swit...
Page 701
2-6 [switcha-ethernet1/0/5] port hybrid vlan 5 1000 1200 tagged [switcha-ethernet1/0/5] quit # configure ethernet 1/0/3 as a hybrid port and configure vlan 5 as its default vlan. Configure ethernet 1/0/3 to remove vlan tags when forwarding packets of vlan 5, vlan 1000, and vlan 1200. [switcha] inter...
Page 702
2-7 [switchb] interface ethernet 1/0/11 [switchb-ethernet1/0/11] port link-type hybrid [switchb-ethernet1/0/11] port hybrid vlan 12 13 1000 1200 tagged # configure ethernet1/0/12 as a hybrid port and configure vlan 12 as its default vlan . Configure ethernet 1/0/12 to remove vlan tags when forwardin...
Page 703: Table of Contents
I table of contents 1 remote-ping configuration ······················································································································1-1 introduction to remote-ping ······································································································...
Page 704: Remote-Ping Configuration
1-1 1 remote-ping configuration introduction to remote-ping remote-ping is a network diagnostic tool used to test the performance of protocols (only icmp by far) running on network. It is an enhanced alternative to the ping command. Remote-ping test group is a set of remote-ping test parameters. A t...
Page 705
1-2 this parameter is used to enable the system to automatically perform the same test at regular intervals. 5) test timeout time test timeout time is the duration while the system waits for an echo-response packet after it sends out an echo-request packet. If no echo-response packet is received wit...
Page 706
1-3 table 1-2 display remote-ping configuration operation command description display the information of remote-ping test history display remote-ping history [ administrator-name operation-tag ] display the latest remote-ping test results display remote-ping results [ administrator-name operation-ta...
Page 707
1-4 packet lost in test: 0% disconnect operation number: 0 operation timeout number: 0 system busy operation number: 0 connection fail number: 0 operation sequence errors: 0 drop operation number: 0 other operation errors: 0 [sysname-remote-ping-administrator-icmp] display remote-ping history admini...
Page 708: Table of Contents
I table of contents 1 ipv6 configuration·····································································································································1-1 ipv6 overview ·············································································································...
Page 709: Ipv6 Configuration
1-1 1 ipv6 configuration when configuring ipv6, go to these sections for information you are interested in: z ipv6 overview z ipv6 configuration task list z ipv6 configuration example z the term “router” in this document refers to a router in a generic sense or an ethernet switch running a routing p...
Page 710
1-2 figure 1-1 comparison between ipv4 header format and ipv6 header format adequate address space the source ipv6 address and the destination ipv6 address are both 128 bits (16 bytes) long. Ipv6 can provide 3.4 x 10 38 addresses to completely meet the requirements of hierarchical address division a...
Page 711
1-3 enhanced neighbor discovery mechanism the ipv6 neighbor discovery protocol is implemented by a group of internet control message protocol version 6 (icmpv6) messages. The ipv6 neighbor discovery protocol manages message exchange between neighbor nodes (nodes on the same link). The group of icmpv...
Page 712
1-4 z multicast address: an identifier for a set of interfaces (typically belonging to different nodes), similar to an ipv4 multicast address. A packet sent to a multicast address is delivered to all interfaces identified by that address. Z anycast address: an identifier for a set of interfaces (typ...
Page 713
1-5 z unassigned address: the unicast address :: is called the unassigned address and may not be assigned to any node. Before acquiring a valid ipv6 address, a node may fill this address in the source address field of an ipv6 packet, but may not use it as a destination ipv6 address. Multicast addres...
Page 714
1-6 introduction to ipv6 neighbor discovery protocol the ipv6 neighbor discovery protocol (ndp) uses five types of icmpv6 messages to implement the following functions: z address resolution z neighbor unreachability detection z duplicate address detection z router/prefix discovery z address autoconf...
Page 715
1-7 address resolution similar to the arp function in ipv4, a node acquires the link-layer address of neighbor nodes on the same link through ns and na messages. Figure 1-3 shows how node a acquires the link-layer address of node b. Figure 1-3 address resolution the address resolution procedure is a...
Page 716
1-8 figure 1-4 duplicate address detection the duplicate address detection procedure is as follows: 1) node a sends an ns message whose source address is the unassigned address :: and the destination address is the corresponding solicited-node multicast address of the ipv6 address to be detected. Th...
Page 717
1-9 task remarks configuring the maximum number of ipv6 icmp error packets sent within a specified time optional configuring the hop limit of icmpv6 reply packets optional displaying and maintaining ipv6 optional configuring an ipv6 unicast address z an ipv6 address is required for a host to access ...
Page 718
1-10 to do... Use the command... Remarks automatically generate a link-local address ipv6 address auto link-local configure an ipv6 link-local address manually assign a link-local address for an interface. Ipv6 address ipv6-address link-local optional by default, after an ipv6 site-local address or ...
Page 720
1-12 configuring the ns interval after a device sends an ns message, if it does not receive a response within a specific period, the device will send another ns message. You can configure the interval for sending ns messages. Follow these steps to configure the ns interval: to do… use the command… r...
Page 721
1-13 packets are received, the ipv6 tcp connection status becomes time_wait. If other packets are received, the finwait timer is reset from the last packet and the connection is terminated after the finwait timer expires. Z size of ipv6 tcp receiving/sending buffer. Follow these steps to configure i...
Page 722
1-14 to do… use the command… remarks enter system view system-view — configure the hop limit of icmpv6 reply packets ipv6 nd hop-limit value optional 64 by default. Displaying and maintaining ipv6 to do… use the command… remarks display the fib entries display ipv6 fib display the mapping between ho...
Page 723
1-15 ipv6 configuration example ipv6 unicast address configuration network requirements two switches are directly connected through two ethernet ports. The ethernet ports belong to vlan 2. Different types of ipv6 addresses are configured for the interface vlan-interface 2 on each switch to verify th...
Page 724
1-16 global unicast address(es): 2001::20f:e2ff:fe49:8048, subnet is 2001::/64 3001::1, subnet is 3001::/64 joined group address(es): ff02::1:ff00:1 ff02::1:ff49:8048 ff02::1 mtu is 1500 bytes nd dad is enabled, number of dad attempts: 1 nd reachable time is 30000 milliseconds nd retransmit interval...
Page 725
1-17 reply from fe80::20f:e2ff:fe00:1 bytes=56 sequence=3 hop limit=255 time = 60 ms reply from fe80::20f:e2ff:fe00:1 bytes=56 sequence=4 hop limit=255 time = 70 ms reply from fe80::20f:e2ff:fe00:1 bytes=56 sequence=5 hop limit=255 time = 60 ms --- fe80::20f:e2ff:fe00:1 ping statistics --- 5 packet(...
Page 726
1-18 0.00% packet loss round-trip min/avg/max = 50/60/70 ms.
Page 727
2-1 2 ipv6 application configuration when configuring ipv6 application, go to these sections for information you are interested in: z introduction to ipv6 application z configuring ipv6 application z ipv6 application configuration example z troubleshooting ipv6 application introduction to ipv6 appli...
Page 728
2-2 ipv6 traceroute the traceroute ipv6 command is used to record the route of ipv6 packets from source to destination, so as to check whether the link is available and determine the point of failure. Figure 2-1 traceroute process as figure 2-1 shows, the traceroute process is as follows: z the sour...
Page 730
2-4 displaying and maintaining ipv6 telnet to do… use the command… remarks display the use information of the users who have logged in display users [ all ] available in any view ipv6 application configuration example ipv6 applications network requirements in figure 2-3 , swa, swb, and swc are three...
Page 731
2-5 bytes=56 sequence=2 hop limit=64 time = 31 ms reply from 3003::1 bytes=56 sequence=3 hop limit=64 time = 31 ms reply from 3003::1 bytes=56 sequence=4 hop limit=64 time = 31 ms reply from 3003::1 bytes=56 sequence=5 hop limit=64 time = 31 ms --- 3003::1 ping statistics --- 5 packet(s) transmitted...
Page 732
2-6 solution z check that the ipv6 addresses are configured correctly. Z use the display ipv6 interface command to determine the interfaces of the source and the destination and the link-layer protocol between them are up. Z use the display ipv6 route-table command to verify that the destination is ...
Page 733: Table of Contents
I table of contents 1 access management configuration ·············································································· 1-1 access management overview ···················································································· 1-1 configuring access management··················...
Page 734
1-1 1 access management configuration when configuring access management, go to these sections for information you are interested in: z access management overview z configuring access management z access management configuration examples access management overview normally, client pcs in a network a...
Page 735
1-2 z a port without an access management ip address pool configured allows the hosts to access external networks only if their ip addresses are not in the access management ip address pools of other ports of the switch. Note that the ip addresses in the access management ip address pool configured ...
Page 736
1-3 access management configuration examples access management configuration example network requirements client pcs are connected to the external network through switch a (an ethernet switch). The ip addresses of the pcs of organization 1 are in the range 202.10.20.1/24 to 202.10.20.20/24. The ip a...
Page 737
1-4 [sysname-ethernet1/0/1] am ip-pool 202.10.20.1 20 combining access management with port isolation network requirements client pcs are connected to the external network through switch a (an ethernet switch). The ip addresses of the pcs of organization 1 are in the range 202.10.20.1/24 to 202.10.2...
Page 738
1-5 # set the ip address of vlan-interface 1 to 202.10.20.200/24. [sysname] interface vlan-interface 1 [sysname-vlan-interface1] ip address 202.10.20.200 24 [sysname-vlan-interface1] quit # configure the access management ip address pool on ethernet 1/0/1. [sysname] interface ethernet 1/0/1 [sysname...
Page 739: Table of Contents
I table of contents appendix a acronyms ································································································································ a-1.
Page 740: Appendix A Acronyms
A-1 appendix a acronyms a aaa authentication, authorization and accounting abr area border router acl access control list arp address resolution protocol as autonomous system asbr autonomous system border router b bdr backup designated router c car committed access rate cli command line interface co...
Page 741
A-2 lsdb link state database m mac medium access control mib management information base n nbma non broadcast multiaccess nic network information center nms network management system ntp network time protocol nvram nonvolatile ram o ospf open shortest path first p pim protocol independent multicast ...
Page 742
A-3 vpn virtual private network w wrr weighted round robin x xid exchange identification xrn expandable resilient networking.