- DL manuals
- 3Com
- Server
- SUPERSTACK 3 WEBCACHE 3000
- User Manual
3Com SUPERSTACK 3 WEBCACHE 3000 User Manual
Summary of SUPERSTACK 3 WEBCACHE 3000
Page 1
Http://www.3com.Com/ part no. Dua1611-5aaa04 published november 2002 superstack ® 3 webcache user guide superstack 3 webcache 1000 3c16115 superstack 3 webcache 3000 3c16116 superstack 3 web site filter 3c16118 dua1611-5aaa04.Book page 1 friday, november 29, 2002 8:56 pm.
Page 2
3com corporation 5400 bayfront plaza santa clara, california 95052-8145 copyright © 2002, 3com technologies. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) witho...
Page 3: Ontents
C ontents a bout t his g uide conventions 18 related documentation 19 documentation comments 20 product registration 20 i g etting s tarted 1 w eb c aching c oncepts and d eployment what is the webcache? 24 the webcache and 3com network supervisor 24 before you begin 25 network configuration concept...
Page 4
Wccp version 2 43 proxy relay deployment 44 proxy cache deployment 45 manual configuration 47 proxy auto configuration (pac) files 48 web proxy auto-discovery (wpad) 49 third-party tools 52 inline cache deployment 52 parent caching 53 how does parent caching work? 54 parent caching network example 5...
Page 5: Cli I
Ii m anaging the w ebcache 3 u sing the cli i nterface accessing the command line interface 82 accessing the command line interface through the console port 82 accessing the command line interface over the network 83 logging in to the command line interface 83 exiting the interface 84 understanding ...
Page 6: III
Performing password recovery 107 iii c onfiguring the w ebcache 6 c onfiguring d eployment m odes configuring transparent cache mode 112 configuring wccp v1 112 configuring wccp v2 113 configuring proxy relay with the superstack 3 firewall 114 configuring proxy cache mode 115 creating a proxy auto-c...
Page 7
Iv c ontrolling and m onitoring w eb a ccess 9 m onitoring w eb a ccess access logging 140 filter logging 140 storing the log files 140 viewing the access log 142 analyzing the access log 142 viewing the filter log 143 10 u sing c ontent f iltering introducing content filtering 146 understanding con...
Page 8: V C
Setting up web client blocking 162 creating a web client blocking list 163 saving the web client blocking list 165 clearing the web client blocking list 166 filter exclusions 166 setting up filter exclusion lists 166 editing the filter exclusion list 166 loading entries from a file into the filter e...
Page 9
Clearing the cache bypass lists 191 12 p reloading c ontent introduction 194 advantages and disadvantages of preloading content 194 methods of preloading content 195 setting up content preload 195 preloading a site 196 adding/editing scheduled tasks 197 temporarily disabling a scheduled task 198 for...
Page 10: Vii
Viewing i/o performance graphs 223 viewing system performance graphs 224 emailing performance graphs 224 configuring email performance graphs 225 15 s ystem d iagnostics system diagnostics 228 pinging other devices 228 performing a ping 228 tracing ip addresses 229 performing a trace route 229 syste...
Page 11: Viii
Viii c ommand l ine i nterface 18 c ommand l ine i nterface a quick guide to the commands 252 getting started 253 exiting the command line interface 256 displaying and changing wan and lan port information 256 configuring the wan and lan ports 256 displaying wan and lan port summary information 257 ...
Page 12: X A
Solving problems indicated by leds 277 solving web interface problems 277 solving command line interface problems 280 solving webcache performance problems 280 solving client browser problems 282 solving general webcache problems 283 x a ppendices and i ndex a s afety i nformation important safety i...
Page 13: Wccp C
E d efault s ettings for the w ebcache default settings 307 getting started wizard settings 309 f r eplacing and i nstalling c ache s torage d evices replacing a failed cache storage device 314 removing the failed cache storage device 314 adding a new cache storage device 316 installing an additiona...
Page 14
Drugs/alcohol 335 gambling 336 violence 336 hate speech 336 productivity categories 337 astrology and mysticism 337 entertainment 337 games 338 general news 338 glamour and intimate apparel 338 hobbies 338 investment 339 job search 339 motor vehicles 339 personals and dating 339 real estate 339 shop...
Page 15: Gnu G
G lossary i ndex 3c om e nd u ser s oftware l icense a greement 3c om e nd u ser w eb s ite f ilter p roduct l icense a greement gnu g eneral p ublic l icense v ersion 2, j une 1991 r egulatory n otices dua1611-5aaa04.Book page 15 friday, november 29, 2002 8:56 pm.
Page 16
Dua1611-5aaa04.Book page 16 friday, november 29, 2002 8:56 pm.
Page 17: Bout
A bout t his g uide this guide provides all the information you need to install and use a superstack ® 3 webcache 1000/3000. It also describes the features of the webcache and outlines how to use those features to optimize the performance of the webcache. This guide is intended for the system or net...
Page 18
18 a bout t his g uide conventions table 1 and table 2 list conventions that are used throughout this guide. Table 1 notice icons icon notice type description information note information that describes important features or instructions caution information that alerts you to potential loss of data ...
Page 19
Related documentation 19 related documentation in addition to this guide, the webcache 1000/3000 documentation set includes the following documents: ■ webcache 1000/3000 online help this online help system contains information about the web interface operations that enable you to manage the webcache...
Page 20
20 a bout t his g uide documentation comments your suggestions are very important to us. They will help make our documentation more useful to you. Please e-mail comments about this document to 3com at: pddtechpubs_comments@3com.Com please include the following information when contacting us: ■ docum...
Page 21: Etting
I g etting s tarted chapter 1 web caching concepts and deployment chapter 2 installing the webcache dua1611-5aaa04.Book page 21 friday, november 29, 2002 8:56 pm.
Page 22
22 dua1611-5aaa04.Book page 22 friday, november 29, 2002 8:56 pm.
Page 23: Aching
1 w eb c aching c oncepts and d eployment this chapter contains information about the concepts of web caching and the ways in which you can deploy the webcache within your network. It covers the following topics: ■ what is the webcache? ■ the webcache and 3com network supervisor ■ before you begin ■...
Page 24
24 c hapter 1: w eb c aching c oncepts and d eployment what is the webcache? The superstack ® 3 webcache 1000 and 3000 are high-performance, easily configurable webcache appliances. They offer the following benefits to your network: ■ reduced network traffic the webcache locally stores frequently ac...
Page 25
Before you begin 25 3com network supervisor offers the following support: ■ if your 3com network supervisor management station is located on the lan, it discovers the webcache automatically and displays it on the topology map. ■ the topology map indicates that the webcache is a 3com webcache and use...
Page 26
26 c hapter 1: w eb c aching c oncepts and d eployment is a grouping of computers with related properties. For example you might group all computers in your company in the domain mycompany.Com . Example the internet (dns) name webcache.Mycompany.Com is formed by combining the host name webcache with...
Page 27
Network configuration concepts 27 these suggested ip addresses are part of a group of ip addresses that have been set aside specially for use “in house” only. Caution: if your network has a connection to the external ip network, you must apply for a registered ip address. This registration system en...
Page 28
28 c hapter 1: w eb c aching c oncepts and d eployment ■ the second part identifies the device on that subnet. The bits of the subnet mask are set to 1 if the device is to treat the corresponding bit in the ip address as part of the original network number or as part of the subnet number. These bits...
Page 29
Network configuration concepts 29 ■ the host name must not exceed 63 characters in length. ■ the host name must be comprised of alphanumeric characters, - (hyphens) and _ (underscores). ■ you cannot enter a host name containing a space character. ■ domain name ■ the domain name must be at least 1 ch...
Page 30
30 c hapter 1: w eb c aching c oncepts and d eployment this hop-by-hop process continues until the ip packets reach the remote destination. The default router should be a device that is closer than the webcache to the wan link in your network, which the webcache can send web requests to in order to ...
Page 31
Web caching overview 31 between the client machines and the origin web servers. The webcache then intercepts and serves requests from the client machines for web content in the following way: 1 a url is entered into a web browser by a user on a client machine in your network. 2 the webcache receives...
Page 32
32 c hapter 1: w eb c aching c oncepts and d eployment current and expired content content stored in the cache can either be current (also known as fresh) or expired (also known as stale). If it is current, the content is up to date and the webcache serves it to the client machine as a cache hit. If...
Page 33
Deployment modes overview 33 the term “web requests” refers to three types of network traffic; http, https (ssl encrypted) and http-ftp. The webcache can accept all of these traffic types. In proxy cache mode, you should configure the web browser on each client machine to use the webcache as the ser...
Page 34
34 c hapter 1: w eb c aching c oncepts and d eployment there are various configuration solutions for transparent and proxy caching which are summarized in table 3 . Table 3 summary of deployment modes transparent caching transparent cache deployment an overview of the transparent cache deployment mo...
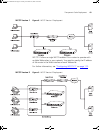
Page 35
Choosing a deployment mode 35 choosing a deployment mode the flow chart shown in figure 4 is a guide to choosing the most suitable deployment mode for the webcache in your network. Figure 4 choosing a deployment mode dua1611-5aaa04.Book page 35 friday, november 29, 2002 8:56 pm.
Page 36
36 c hapter 1: w eb c aching c oncepts and d eployment you should not configure the webcache to operate in transparent cache mode unless you have a suitable redirection device in your network. Transparent cache deployment in transparent cache deployment the webcache is connected to a layer 4 device ...
Page 37
Transparent cache deployment 37 advantages ■ you do not have to configure the web browser on each client machine that you want to access the webcache. Deployment of the webcache within your network is therefore easier to achieve and manage because you only need to configure the layer 4 redirection d...
Page 38
38 c hapter 1: w eb c aching c oncepts and d eployment deploying the superstack 3 switch 4400, 4924 or 4950 with the webcache the following example describes how to install the superstack 3 switch 4400, switch 4924 or switch 4950 as a layer 4 redirection device. The network layout is shown in figure...
Page 39
Transparent cache deployment 39 important considerations for the switch 4400 this section contains some important considerations when deploying the webcache with the switch 4400 (3c17203, 3c17204). ■ the switch 4400 supports the superstack 3 webcache 1000/3000. ■ the switch 4400 unit must have softw...
Page 40
40 c hapter 1: w eb c aching c oncepts and d eployment ■ the webcache does not have to be directly connected to the switch 4924 or 4950 - there can be intervening layer 2 switches or hubs. ■ the switch 4924 or 4950 can only support one webcache for a single unit. ■ the webcache can be connected to a...
Page 41
Transparent cache deployment 41 figure 7 deploying the webcache and server load balancer together the webcache is directly connected to a superstack 3 server load balancer via the lan port to improve the scaling and performance of a group of web servers. The server load balancer partitions network t...
Page 42
42 c hapter 1: w eb c aching c oncepts and d eployment cisco router to operate with multiple webcaches. Wccp v2 supports multiple cisco routers operating with multiple webcaches in a service group. One of the major benefits of wccp is that there can be a layer 3 network between the webcache and the ...
Page 43
Transparent cache deployment 43 wccp version 1 figure 8 wccp version 1 deployment wccp v1 allows a single wccp-enabled cisco router to operate with multiple webcaches in your network. You need to specify the ip address of the router in the web interface of each webcache. For further information, see...
Page 44
44 c hapter 1: w eb c aching c oncepts and d eployment wccp v2 supports multiple wccp-enabled cisco routers operating with multiple webcaches in a service group. Any of the available routers in the service group can redirect web requests to any of the available webcaches, improving performance and r...
Page 45
Proxy cache deployment 45 figure 10 deploying the firewall and webcache together advantages ■ you do not have to configure the web browser on each client machine that you want to access the webcache because all web requests are automatically redirected by the firewall. Disadvantages ■ you have to ad...
Page 46
46 c hapter 1: w eb c aching c oncepts and d eployment for further information, see “configuring proxy cache mode” on page 115 . Figure 11 proxy cache deployment advantages ■ you do not have to add new devices to your network. ■ the webcache can be integrated into any network environment. ■ you can ...
Page 47
Proxy cache deployment 47 webcache fails, web requests will automatically be sent to the other available webcaches. For further information, see figure 12 on page 49 . Proxy cache solutions you can deploy the webcache using the following proxy cache solutions: ■ manual configuration ■ proxy auto con...
Page 48
48 c hapter 1: w eb c aching c oncepts and d eployment 8 click ok. To manually configure netscape navigator 4.5 or 6: 1 open netscape navigator. 2 from the edit menu, click preferences. 3 click the advanced category and click proxies. 4 select manual proxy configuration. 5 click view. 6 enter the ur...
Page 49
Proxy cache deployment 49 figure 12 proxy cache deployment with pac file load balancing web proxy auto-discovery (wpad) the webcache and microsoft internet explorer 5 (and later versions) support the web proxy auto-discovery (wpad) protocol. This protocol enables the web browser on client machines t...
Page 50
50 c hapter 1: w eb c aching c oncepts and d eployment interface of the webcache; for further information, see “creating a proxy auto-configuration file” on page 115 . When internet explorer is launched it searches for a wpad server. The web browser adds the subdomain “wpad” to the beginning of the ...
Page 51
Proxy cache deployment 51 you need to add the wpad functionality to your dhcp server using dhcp manager. For further information, view the microsoft knowledge base at: http://search.Support.Microsoft.Com/kb/c.Asp (correct at time of publishing) and search for the article id number q252898 . Configur...
Page 52
52 c hapter 1: w eb c aching c oncepts and d eployment http://www.Ietf.Org/internet-drafts/draft-cooper-webi-wpad-0 0.Txt (correct at time of publishing) third-party tools there are applications from many vendors that can help you to manage networks of client machines. Microsoft offers the internet ...
Page 53
Parent caching 53 layer 4 redirection device. All web traffic arriving from client machines to the lan port of the webcache is directed into the caching software. All non-web traffic is automatically sent back out onto the network via the wan port. Cache misses are automatically redirected from the ...
Page 54
54 c hapter 1: w eb c aching c oncepts and d eployment you can configure a child webcache to forward requests to up to four parent webcaches. If one of the parent webcaches does not have the requested content or is unavailable, the child webcache will automatically try the next specified parent webc...
Page 55
Parent caching 55 figure 14 parent caching 5 if the content is not in the parent webcache, it is retrieved from either the origin server or another parent webcache. The content is then cached by the parent webcache and simultaneously served to the client machine and stored in the child webcache. Par...
Page 56
56 c hapter 1: w eb c aching c oncepts and d eployment accidental webcache hierarchies an accidental webcache hierarchy automatically exists in the networking example shown in figure 15 if the parent webcache is configured in either transparent cache, inline cache or wccp mode. In each of these depl...
Page 57
Icp caching 57 icp caching has two disadvantages against parent caching: ■ icp caching does not scale well — if your infrastructure grows and more caches are installed, the network bandwidth used by icp, and the latency and reliability of the protocol can become an issue. This does not occur with pa...
Page 58
58 c hapter 1: w eb c aching c oncepts and d eployment dua1611-5aaa04.Book page 58 friday, november 29, 2002 8:56 pm.
Page 59: Nstalling
2 i nstalling the w ebcache this chapter contains the information you need to install and set up the webcache 1000/3000. It covers the following topics: ■ package contents ■ webcache — front view detail ■ webcache — rear view detail ■ choosing a suitable site ■ the power-up sequence ■ deploying the ...
Page 60
60 c hapter 2: i nstalling the w ebcache package contents ■ webcache 1000 (3c16115) or webcache 3000 (3c16116) ■ cd-rom ■ documentation ■ user guide (this guide) ■ release notes ■ warranty information sheet ■ power cord ■ rack-mounting kit containing: ■ 2 x rack mounting rails ■ 2 x rack mounting br...
Page 61
Webcache — front view detail 61 webcache — front view detail figure 16 webcache — front view the illustration above shows a webcache 3000. The webcache 1000 contains a single cache storage device and therefore has one cache storage status led on the front panel. The webcache 3000 contains two cache ...
Page 62
62 c hapter 2: i nstalling the w ebcache if the webcache experiences an unrecoverable error during initialization the power/self test led flashes green. Take a note of the color and status of each led on the front before you contact 3com technical support for assistance. Webcache — rear view detail ...
Page 63
Webcache — rear view detail 63 connect the unit to a traditional pbx or public telephone network. Only connect rj-45 data connectors, switches or routers to these sockets. Either shielded or unshielded data cables with shielded or unshielded jacks can be connected to these data sockets. Power socket...
Page 64
64 c hapter 2: i nstalling the w ebcache if auto-negotiation is disabled, you can configure: ■ link speed — you can set this to 100 mbps or 10 mbps. ■ duplex state — you can set this to full duplex or half duplex. You cannot enable or disable the wan or lan port itself. The port can safely be left d...
Page 65
Choosing a suitable site 65 choosing a suitable site the webcache must be mounted in a standard 19-inch 4-posted equipment rack, and is suited for use in a wiring closet, an equipment room, a server room, or telecommunications room. A rack-mounting kit is supplied with the webcache. Caution: ensure ...
Page 66
66 c hapter 2: i nstalling the w ebcache you must use the rack-mounting rails and screws supplied with the webcache. Damage caused to the webcache by using incorrect rails and screws invalidates your warranty. A rack-mounting kit is supplied with the webcache which contains the items shown in figure...
Page 67
Rack-mounting the webcache 67 to rack-mount your webcache: 1 place the webcache the right way up on a hard flat surface, with the front facing towards you. The rack-mounting brackets are attached to each side of the webcache, as shown in figure 20 . Figure 20 rack-mounting bracket attached to the we...
Page 68
68 c hapter 2: i nstalling the w ebcache figure 21 fitting a rack-mounting rail to the rear of the rack 4 attach the rack-mounting rail to the front of the rack. To do this: a insert two screws through aligned openings in the front plate, rack and rack-mounting rail as shown in figure 22 . B tighten...
Page 69
The power-up sequence 69 figure 23 attaching the webcache to the rack 7 ensure that the ventilation holes in the webcache are not obstructed. The power-up sequence the following sections describe how to get your webcache powered-up and ready for operation. Powering-up the webcache use the following ...
Page 70
70 c hapter 2: i nstalling the w ebcache when the power-up has completed, check the power/self test led to make sure that your webcache is operating correctly. Table 6 shows possible behavior for the led. Table 6 power/self test led behavior if the leds on the webcache indicate a problem refer to “s...
Page 71
Setting up the webcache for management 71 setting up the webcache for management you can quickly set up the webcache for management in two ways: ■ setting up using the web interface — connect a management workstation to the webcache over an ip test network or directly via a cross-over cable. For fur...
Page 72
72 c hapter 2: i nstalling the w ebcache ■ you must have an ip stack correctly installed on the client machine. You can check this by trying to browse the world wide web; if you can browse, an ip stack is installed. If you do not have access to the world wide web, you can check that the ip stack is ...
Page 73
Setting up the webcache for management 73 also the web interface has been optimized for pc screens with the desktop area set to 800 by 600 pixels. 3com recommends that you set the font size to small fonts. 2 in the location/address field of the browser, enter the url of the webcache. This must be in...
Page 74
74 c hapter 2: i nstalling the w ebcache webcache to your live network.For further information, see “getting started wizard settings” on page 309 . Setting up using the command line interface you can setup the webcache for management via the command line interface by running a telnet session on a ma...
Page 75
Setting up the webcache for management 75 for further information, see “webcache — rear view detail” on page 62 . Figure 28 setting up through the console port to connect to the webcache via the console port: 1 you must connect a terminal or terminal emulator to the console port on the rear panel of...
Page 76
76 c hapter 2: i nstalling the w ebcache accessing the command line interface to access the command line interface, take the following steps: 1 the login sequence for the command line interface begins as soon as the webcache detects a connection to its console port, or as soon as a telnet session is...
Page 77
Installing an additional cache storage device 77 connecting the webcache use the following sequence of steps to connect the webcache to your network: 1 connect an appropriate network cable to the lan port on the rear panel of the webcache. Simply slot the connector on the cable into the rj-45 lan po...
Page 78
78 c hapter 2: i nstalling the w ebcache dua1611-5aaa04.Book page 78 friday, november 29, 2002 8:56 pm.
Page 79: Anaging
Ii m anaging the w ebcache chapter 3 using the cli interface chapter 4 using the web interface chapter 5 securing access to the webcache management interfaces dua1611-5aaa04.Book page 79 friday, november 29, 2002 8:56 pm.
Page 80
80 dua1611-5aaa04.Book page 80 friday, november 29, 2002 8:56 pm.
Page 81: Sing
3 u sing the cli i nterface this chapter contains information about managing the webcache using the management software that resides on the webcache. Managing the webcache can help you to improve the efficiency of the webcache and therefore the overall performance of your network. It allows you to m...
Page 82
82 c hapter 3: u sing the cli i nterface accessing the command line interface you can access the command line interface using: ■ a terminal or terminal emulator connected to the console port of the webcache directly, or through a modem. ■ a terminal or terminal emulator connected to the webcache ove...
Page 83
Logging in to the command line interface 83 to configure the settings of the terminal, terminal emulator, or modem, see the documentation that accompanies it. You must configure the terminal and set the line speed (baud) to match that of the webcache console port. Unless you have changed it, the def...
Page 84
84 c hapter 3: u sing the cli i nterface if you have logged on correctly, the top-level menu of the command line interface is displayed as described in “understanding the command line interface” on page 84 . If you have not logged on correctly, the message incorrect password. Is displayed and the lo...
Page 85
Understanding the command line interface 85 from the top-level menu, you can access these sub-menus: ■ gettingstarted command this command allows you to specify basic configuration settings for the webcache. ■ logout command this command allows you to logout of the command line interface. ■ physical...
Page 86
86 c hapter 3: u sing the cli i nterface ■ to enter commands that require values: append the values to the name of the command. For example, to display the security menu and change your password, enter: security password if you do not specify values for a command that requires them, you are prompted...
Page 87: Sing
4 u sing the w eb i nterface this chapter contains information about managing the webcache using the management software that resides on the webcache. Managing the webcache can help you to improve the efficiency of the webcache and therefore the overall performance of your network. It allows you to ...
Page 88
88 c hapter 4: u sing the w eb i nterface management software interfaces you can manage the webcache using the web interface management software. This is an internal set of web pages that allow you to manage the webcache using a web browser that has javascript and cascading style sheets enabled . Re...
Page 89
Accessing the web interface 89 accessing the web interface to access the web interface: 1 open the web browser on the management workstation. To display the web interface correctly, use one of the following web browsers: ■ microsoft internet explorer v4.0 ■ microsoft internet explorer v5.0 ■ microso...
Page 90
90 c hapter 4: u sing the w eb i nterface figure 30 user name and password screen if the user name and password screen is not displayed, see “solving web interface problems” on page 277 . 4 enter your user name and password. For further information, see “logging in as a default user” on page 88 . Cl...
Page 91
Understanding the web interface 91 understanding the web interface figure 31 the web interface the web interface is made up of four areas: ■ the banner this is always displayed at the top of the browser window. It displays the 3com logo and superstack logo. ■ the toolbar this is always displayed at ...
Page 92
92 c hapter 4: u sing the w eb i nterface the toolbar the toolbar is always displayed at the top of the browser window, underneath the banner. It contains six buttons which allow you to select different views. Click on a toolbar item to see the corresponding view: summary — this view shows a summary...
Page 93
The toolbar 93 ■ the information area displays the device mimic (see “the device mimic” on page 96 ) and the following status tables (see “the status tables” on page 99 ): ■ caching summary ■ caching statistics summary content filter — this view allows you to monitor and block access to sites that y...
Page 94
94 c hapter 4: u sing the w eb i nterface the navigation tree the navigation tree is always displayed on the left side of the browser window. It is a windows explorer-like interface that contains various icons which allow you to manage your webcache. Figure 32 the summary view navigation tree by def...
Page 95
The navigation tree 95 the following table shows the various navigation tree symbols and their associated behavior: symbol behavior indicates that the next level of the navigation tree hierarchy is currently expanded. Click the symbol to collapse the next level. This only affects the navigation tree...
Page 96
96 c hapter 4: u sing the w eb i nterface the information area the information area is always displayed on the right side of the browser window. It contains information about the managed webcache. The information displayed depends on the view you select in the toolbar: ■ if the summary view is curre...
Page 97
The information area 97 the device mimic is a virtual, interactive representation of the front and rear panels and the current status of the webcache. All of the ports on the webcache are shown. The device mimic is periodically updated to reflect changes in the webcache. You can also perform certain...
Page 98
98 c hapter 4: u sing the w eb i nterface click this to refresh the device mimic now. ■ mimic help click this for an explanation of the symbols and colors on the device mimic's ports and caching devices. The following table shows the various device mimic symbols and their associated behavior: figure...
Page 99
The information area 99 the status tables clicking summary, device, caching or content filter on the toolbar will display status tables in the information area. The summary view displays most of the status tables and the device caching and content filter views display relevant status tables below th...
Page 100
100 c hapter 4: u sing the w eb i nterface content filtering summary (appears in summary and content filter views) the content filtering summary table shows the filtering mode currently employed, the status of the filter licence, the status of the 3com filter download and the time of the last succes...
Page 101
The information area 101 site. Your management workstation must have access to the web for the 3com options to work: ■ click contacts to display contact information from the 3com web site in a new browser window. ■ click disk failure to open a 3com knowledge base article which informs you how to ret...
Page 102
102 c hapter 4: u sing the w eb i nterface dua1611-5aaa04.Book page 102 friday, november 29, 2002 8:56 pm.
Page 103: Ecuring
5 s ecuring a ccess to the w ebcache m anagement i nterfaces this chapter contains information about ensuring that the webcache is secure. It covers the following topics: ■ passwords ■ management interface setup ■ password recovery dua1611-5aaa04.Book page 103 friday, november 29, 2002 8:56 pm.
Page 104
104 c hapter 5: s ecuring a ccess to the w ebcache m anagement i nterfaces passwords whenever you manage the webcache using the web interface or command line interface, you need to log in with the admin username and password, as described in “logging in as a default user” on page 88 . Caution: to pr...
Page 105
Management interface setup 105 management interface setup there are two methods of restricting the visibility of the webcache’s web interface. Both methods are configured from the setup management screen. To access the setup management screen: 1 log in to the web interface. 2 click device on the too...
Page 106
106 c hapter 5: s ecuring a ccess to the w ebcache m anagement i nterfaces you can restrict management of the webcache by entering ip addresses that are allowed access at the access restricted to the following ip addresses: prompt. Enter a comma-separated list of ip addresses, an ip range or a combi...
Page 107
Password recovery 107 you may want to disable password recovery if you are concerned about the security of the webcache. When password recovery is enabled, anyone who has physical access to the webcache can potentially change the password and lock you out of the management interfaces. Caution: 3com ...
Page 108
108 c hapter 5: s ecuring a ccess to the w ebcache m anagement i nterfaces 4 enter enable to leave password recovery enabled, or enter disable to turn it off. You are now logged in as the default admin user. Dua1611-5aaa04.Book page 108 friday, november 29, 2002 8:56 pm.
Page 109: III
Iii c onfiguring the w ebcache chapter 6 configuring deployment modes chapter 7 static routes chapter 8 system time dua1611-5aaa04.Book page 109 friday, november 29, 2002 8:56 pm.
Page 110
110 dua1611-5aaa04.Book page 110 friday, november 29, 2002 8:56 pm.
Page 111: Onfiguring
6 c onfiguring d eployment m odes this chapter contains information about how to configure the various deployment modes of the webcache: ■ configuring transparent cache mode ■ configuring wccp v1 ■ configuring wccp v2 ■ configuring proxy relay with the superstack 3 firewall ■ configuring proxy cache...
Page 112
112 c hapter 6: c onfiguring d eployment m odes configuring transparent cache mode to configure transparent cache mode using the web interface: 1 log in to the web interface. 2 click caching on the toolbar. 3 select set caching mode. The set the webcache deployment mode screen is displayed. 4 ensure...
Page 113
Configuring wccp v2 113 if the webcache is deployed in wccp mode, you must use port 8081 to access the webcache’s web interface e.G. Http://192.168.1.253:8081. If you use port 80, you may experience problems accessing the web interface. For further information, see “wccp version 1” on page 43 . Conf...
Page 114
114 c hapter 6: c onfiguring d eployment m odes 11 enter the authentication password used by the routers in the password field. Enter it again in the confirm field. The password must be 8 characters or less and is case-sensitive. Click next. 12 the finish screen is displayed. Carefully read the summ...
Page 115
Configuring proxy cache mode 115 you should not enter multiple proxy relay tcp port numbers as the superstack 3 firewall redirects one tcp port number only (8080 by default). If you configure multiple proxy relay tcp port numbers on the webcache, only the single port that you also configure on the f...
Page 116
116 c hapter 6: c onfiguring d eployment m odes ■ select the protocols that the web browsers on client machines should direct to the webcache ■ bypass the webcache for plain host names ■ distribute web requests from client machines between up to four webcaches to achieve higher performance and resil...
Page 117
Creating a proxy auto-configuration file 117 if you wish to use the pac file on a network server, click save. The file download screen is displayed. Select save this file to disk and enter a filename and location to save the file to. Configuring the client web browser you must next set the web brows...
Page 118
118 c hapter 6: c onfiguring d eployment m odes configuring inline cache mode to configure inline cache mode using the web interface: 1 log in to the web interface. 2 click caching on the toolbar. 3 select set caching mode. The set the webcache deployment mode screen is displayed. 4 ensure that enab...
Page 119
Configuring parent caching 119 configuring parent caching to enable and configure parent caching using the web interface: 1 log in to the web interface. 2 click caching on the toolbar. 3 select parent caches > setup parent caches in the navigation tree. 4 check enable parent proxy caches. 5 select w...
Page 120
120 c hapter 6: c onfiguring d eployment m odes 3 select parent caches > edit exclude list in the navigation tree. 4 in the enter the domain name, ip address or ip address range field, enter the domain name, ip address or ip address range to add to the list andclick add. Repeat this for each entry t...
Page 121
Configuring parent caching 121 you should choose to merge with the current list if you have a partial list of entries in an external file that you want to add to the list on the webcache. 6 select load to load the new list. Loading a list may take a few seconds to complete, depending on the number o...
Page 122
122 c hapter 6: c onfiguring d eployment m odes saving a list may take a few seconds to complete, depending on the number of entries being loaded. Clearing the parent cache exclusion list you can use the clear exclude list screen to delete all the current entries in the parent cache exclusion list. ...
Page 123
Configuring icp caching 123 configuring icp caching in addition to parent caching the webcache supports icp caching. This is an older and more error-prone protocol but is supported by a wide variety of legacy devices. 3com recommends that you use parent caching in preference to icp caching unless yo...
Page 124
124 c hapter 6: c onfiguring d eployment m odes the standard icp port number is 3130 and should not be changed unless the webcache is being used in conjunction with other devices that require a different port number. 7 set icp query timeout (seconds) to the length of time you want to webcache to wai...
Page 125
Configuring icp caching 125 deleting icp peers to delete icp peers: 1 log in to the web interface. 2 click caching on the toolbar. 3 select icp control > edit icp peers in the navigation tree. 4 select the peer that you want to delete form the table at the bottom of the window. 5 click remove to del...
Page 126
126 c hapter 6: c onfiguring d eployment m odes dua1611-5aaa04.Book page 126 friday, november 29, 2002 8:56 pm.
Page 127: Tatic
7 s tatic r outes this chapter contains information about the concepts of static routing and how to configure static routes on the webcache. It covers the following topics: ■ what are static routes? ■ static routes example ■ advantages of static routes ■ configuring static routes dua1611-5aaa04.Book...
Page 128
128 c hapter 7: s tatic r outes what are static routes? Routes to remote networks are typically obtained dynamically through routing protocols. However, you can also choose to provide routes manually. These routes are referred to as static routes. A static route is associated with an interface that ...
Page 129
Configuring static routes 129 the solution in this scenario is to enter a static route on the webcache to use a lan-side router for all requests destined for the lan-side server. When the webcache processes the cache miss, instead of passing the packet to the default router, it sends it to the lan-s...
Page 130
130 c hapter 7: s tatic r outes 5 enter the subnet mask of the network that you are creating a static route for in the subnet mask field. 6 enter the ip address of the router for the static route in the gateway field. 7 select the add button to create the static route. All of the currently defined s...
Page 131: Ystem
8 s ystem t ime this chapter explains how to configure the system time of the webcache. It contains the following topics: ■ configuring the system time ■ network time protocol ■ configuring the system time using the network time protocol ■ configuring the system time manually ■ system time and perfo...
Page 132
132 c hapter 8: s ystem t ime configuring the system time you must select how the webcache determines the current time during the getting started wizard, which automatically runs when you first access the webcache’s web interface. You can change how the webcache determines the current time at any po...
Page 133
Network time protocol 133 choosing a network time protocol server you can choose to use one of the many public ntp servers that are available on the internet or set up your own ntp server. When you have access to an ntp server, you can configure the webcache to determine the current time using ntp; ...
Page 134
134 c hapter 8: s ystem t ime configuring the system time using the network time protocol to configure the system time of the webcache using the network time protocol, you must enter the following information in the getting started wizard or time configuration command in the web interface: 1 select ...
Page 135
System time and performance graphs 135 system time and performance graphs when the system time of the webcache is set manually, all of the current performance graphs are reset and all previous graph history is lost. You should therefore only change the system time when it is absolutely necessary. Th...
Page 136
136 c hapter 8: s ystem t ime dua1611-5aaa04.Book page 136 friday, november 29, 2002 8:56 pm.
Page 137: Ontrolling
Iv c ontrolling and m onitoring w eb a ccess chapter 9 monitoring web access chapter 10 using content filtering dua1611-5aaa04.Book page 137 friday, november 29, 2002 8:56 pm.
Page 138
138 dua1611-5aaa04.Book page 138 friday, november 29, 2002 8:56 pm.
Page 139: Onitoring
9 m onitoring w eb a ccess this chapter contains information about controlling and monitoring the access of the users of your network through the webcache to the internet. It covers the following topics: ■ access logging ■ filter logging ■ storing the log files ■ viewing the access log ■ analyzing t...
Page 140
140 c hapter 9: m onitoring w eb a ccess access logging access logging allows you to track which client machines have accessed which web sites through the webcache. You can configure the webcache to log all web accesses. Access logging and the squid access log format are enabled by default but if yo...
Page 141
Storing the log files 141 request filtered, by combining the ftp logs. By default, the saved access logs are based on the standard squid access log format and can be analyzed using off-the-shelf log analysis tools. When the logs are offloaded both the access log and the filter log will be saved. See...
Page 142
142 c hapter 9: m onitoring w eb a ccess alphanumeric and . (dot), - (hyphen) or _ (underscore) characters and can only be up to 32 characters in length. Clicking ftp now will immediately send the currently active access log to the ftp server. This allows you to test your ftp settings or to save the...
Page 143
Viewing the filter log 143 calamaris is a free open source tool available from the following url: http://calamaris.Cord.De (correct at time of publication) all three netscape format log files can be analyzed by netscape’s program flexanlg, which is distributed with netscape web and proxy servers beg...
Page 144
144 c hapter 9: m onitoring w eb a ccess dua1611-5aaa04.Book page 144 friday, november 29, 2002 8:56 pm.
Page 145: Sing
10 u sing c ontent f iltering this chapter explains how to use the webcache to control and monitor access to the internet from your network. It covers the following topics: ■ introducing content filtering ■ 3com web site filter ■ websense enterprise filtering ■ manual content filtering ■ default rul...
Page 146
146 c hapter 10: u sing c ontent f iltering introducing content filtering the webcache is able to stop users from accessing inappropriate web sites by using content filtering. The benefits of managing the web sites that can and cannot be accessed include: ■ increased productivity. ■ decreased legal ...
Page 147
3com web site filter 147 days. In addition to the sites included in the web site filter you can manually customize the list. See “3com web site filter” on page 147 . ■ websense enterprise filtering enables your webcache to interoperate with a websense enterprise server on your network. Each web requ...
Page 148
148 c hapter 10: u sing c ontent f iltering when a client computer attempts to access a web site, the webcache applies the following rules in the order listed: 1 web client blocking — if web client blocking has been activated the webcache checks to see if the client is on the web client blocking lis...
Page 149
3com web site filter 149 registering the webcache before activating the 30 day free subscription to the 3com web site filter you must register the webcache. Registration also: ■ provides access to the latest webcache software (at time of registration). ■ activates the warranty. See the warranty flye...
Page 150
150 c hapter 10: u sing c ontent f iltering default rule as described in “setting the default rule” on page 159 . In this case: ■ all existing blocking log files will be deleted. ■ all downloaded filter files will be deleted from the webcache hard drives. You need to register the webcache before you...
Page 151
3com web site filter 151 5 select the days of the week that you want the update to take place. 6 click ok, to close the filter list update window. The update now button on the filter list update command starts an immediate download of the filters without waiting for the next scheduled download time....
Page 152
152 c hapter 10: u sing c ontent f iltering setting up filtering policies to set up a filtering policy you need to first specify different category sets that describe the type of access you want to enforce. You must then assign what category sets are active on which days and at which times by creati...
Page 153
3com web site filter 153 6 check the various web site categories that you want to block when the category set is active. 7 if you want to remove the category set from the list, click on an entry in the list and click remove. To delete all entries at once, click remove all. 8 click ok. Setting up the...
Page 154
154 c hapter 10: u sing c ontent f iltering 3 select webcache filtering > 3com web site filter > policy schedule in the navigation tree. 4 to edit the schedule of an existing policy, click on the policy in the list and click edit; then select the days and the time for when this category set should b...
Page 155
Websense enterprise filtering 155 websense enterprise filtering websense enterprise filtering is a third party software package that allows you to apply content filtering through the webcache. An external websense enterprise server is queried for every web request the webcache receives. Websense ent...
Page 156
156 c hapter 10: u sing c ontent f iltering select the universal option. For further information, see the instructions that accompany the websense enterprise software. Setting up websense enterprise filtering on your webcache having acquired and installed the websense enterprise filtering software o...
Page 157
Manual content filtering 157 ■ “web client blocking” on page 161 ■ “customizing the content filter response screen” on page 176 manual content filtering manual content filtering allows you to control which web sites can be accessed through the webcache. If you enable manual content filtering, you mu...
Page 158
158 c hapter 10: u sing c ontent f iltering it is important to use caution when adding keywords to the list as you may filter sites other than you intend. For example, blocking the word breast may filter sites on breast cancer as well as objectionable or pornographic sites. 5 default rule — the webc...
Page 159
Default rule 159 ■ “setting up allow lists and deny lists” on page 169 ■ “keyword blocking” on page 174 ■ “customizing the content filter response screen” on page 176 default rule the default rule is the last filter used if manual filtering has been selected and the rule that is applied if the 3com ...
Page 160
160 c hapter 10: u sing c ontent f iltering the filter log stores information about the clients who try to access blocked sites, and the reason why the request has been blocked. This section explains the filter logging options. Blocking and logging behavior when the webcache filters a web site it ca...
Page 161
Web client blocking 161 7 click next and then finish to close the setup filtering wizard. Storing the filter log you can specify an ftp server to which you want to periodically save the log files. If this option is enabled, the logs are offloaded to the ftp server whenever any log reaches 250 mb in ...
Page 162
162 c hapter 10: u sing c ontent f iltering ■ using a browser on a client machine whose ip address is not blocked by web client blocking to access the web interface. All client machines that you specify in the cache bypass screen will not be prevented by the webcache from accessing the web. Cache by...
Page 163
Web client blocking 163 ■ allow all except — to allow all clients to access the web except for those you specifically block. 6 click ok. Creating a web client blocking list you can create a list of the ip addresses or ip address ranges of the client machines for which you want to change the default ...
Page 164
164 c hapter 10: u sing c ontent f iltering 5 if you want to remove an entry from the list, click on an entry in the list and click remove. To delete all entries at once, click remove all. Example if you select deny all except when you set up web client blocking (see “setting up web client blocking”...
Page 165
Web client blocking 165 6 select load to load the new list. Loading a list may take a few seconds to complete, depending on the number of entries being loaded. List rules there are certain rules that you must follow when loading a list of web clients into the web client blocking list. When loading a...
Page 166
166 c hapter 10: u sing c ontent f iltering clearing the web client blocking list you can use the clear list screen to delete all the current entries in the web client blocking list. To clear the web client blocking list: 1 log in to the web interface. 2 click content filter on the toolbar. 3 select...
Page 167
Filter exclusions 167 to add a client to the filter exclusion list: 1 log in to the web interface. 2 click content filter on the toolbar. 3 select webcache filtering > filter exclusion > edit list in the navigation tree. 4 enter the ip address or ip address range of the clients who you want to add t...
Page 168
168 c hapter 10: u sing c ontent f iltering you should choose to replace the current list if you have a complete list of entries in an external file that you want to use to overwrite the list on the webcache. You should choose to merge with the current list if you have a partial list of entries in a...
Page 169
Setting up allow lists and deny lists 169 saving a list may take a few seconds to complete, depending on the number of entries being saved. Clearing the filter exclusion list you can use the clear list screen to delete all the current entries in the filter exclusion list. To do this: 1 log in to the...
Page 170
170 c hapter 10: u sing c ontent f iltering manually entering a web site into the allow list to manually enter a web site into the allow list: 1 log in to the web interface. 2 click content filter on the toolbar. 3 select webcache filtering > allow/deny lists > edit allow list in the navigation tree...
Page 171
Setting up allow lists and deny lists 171 manually entering a web site into the deny list to manually enter a web site in the deny list: 1 log in to the web interface. 2 click content filter on the toolbar. 3 select webcache filtering > allow/deny lists > edit deny list in the navigation tree. 4 ent...
Page 172
172 c hapter 10: u sing c ontent f iltering loading entries from a file into the allow list or deny list a text file containing a list of domain names, ip addresses or ip address ranges, can be loaded into the allow list or deny list. To do this: 1 log in to the web interface. 2 click content filter...
Page 173
Setting up allow lists and deny lists 173 ■ each line in the file must not exceed 75 characters in length. ■ blank lines are ignored. ■ there must be no spaces at the beginning of a line. ■ the list can contain a maximum of 900 entries. If loading the file results in more than 900 entries, all subse...
Page 174
174 c hapter 10: u sing c ontent f iltering keyword blocking keyword blocking allows the webcache to prevent access to urls containing particular words. Keyword blocking can be enabled when you set up the webcache for manual content filtering or 3com web site filtering. You may specify a list of up ...
Page 175
Keyword blocking 175 5 if you want to remove an entry from the list, click on an entry and click remove. To delete all entries at once, click remove all. Loading entries from a file into the keyword blocking list a text file containing a list of keywords can be loaded into the keyword blocking list....
Page 176
176 c hapter 10: u sing c ontent f iltering ■ there must be no spaces at the beginning of a line. ■ the list can contain a maximum of 900 entries. If loading the file results in more than 900 entries, all subsequent entries after the limit has been reached will not be loaded. Saving the new keyword ...
Page 177
Customizing the content filter response screen 177 if the client machine is blocked by web client blocking, the customize response screen will not appear. To customize the response using the web interface: 1 click content filter on the toolbar. 2 select webcache filtering > custom responsein the nav...
Page 178
178 c hapter 10: u sing c ontent f iltering dua1611-5aaa04.Book page 178 friday, november 29, 2002 8:56 pm.
Page 179: Ontrolling
V c ontrolling c aching chapter 11 controlling how web sites are cached chapter 12 preloading content dua1611-5aaa04.Book page 179 friday, november 29, 2002 8:56 pm.
Page 180
180 dua1611-5aaa04.Book page 180 friday, november 29, 2002 8:56 pm.
Page 181: Ontrolling
11 c ontrolling h ow w eb s ites a re c ached this chapter contains information about ■ cache control ■ clearing the cache ■ cache bypass dua1611-5aaa04.Book page 181 friday, november 29, 2002 8:56 pm.
Page 182
182 c hapter 11: c ontrolling h ow w eb s ites a re c ached cache control cache control allows you to control the caching behavior of the webcache for specific web sites. Cache control works in any deployment mode and has two functions: ■ cache control can be used to reduce traffic across your wan n...
Page 183
Cache control 183 ■ manually entering each web site in the edit list screen. ■ loading an existing list of web sites from an external text file in the load list from filescreen. ■ a combination of the above methods. Manually entering a web site into the cache control list to manually enter a web sit...
Page 184
184 c hapter 11: c ontrolling h ow w eb s ites a re c ached alternatively, if you want the webcache to cache and use the material from the site for a week, select pin for one week instead of never cache. You must follow all of the rules listed in the “domain name system syntax” and “ip address rules...
Page 185
Cache control 185 ■ the caching time, in hours, must have one of the following values 0 , 24 , 48 , 168 , where 0 is equivalent to never cache and indicates that the site should not be cached. ■ the cache control list can contain a maximum of 900 entries. If loading the file results in more than 900...
Page 186
186 c hapter 11: c ontrolling h ow w eb s ites a re c ached to clear the cache control list: 1 log in to the web interface. 2 click caching on the toolbar. 3 select cache control > clear list in the navigation tree. 4 click ok to clear the cache control list. The clear list process may take a few se...
Page 187
Cache bypass 187 deployed in transparent cache mode. Cache bypass is useful in the unlikely event that you have a transparent cache deployment (not proxy relay) and find a web site that does not operate correctly with the transparent cache. A small number of web sites perform ip address validation w...
Page 188
188 c hapter 11: c ontrolling h ow w eb s ites a re c ached you can create a list of web site ip addresses or address ranges. All requests from client machines to those domains will bypass the webcache and go straight to the origin server. You can only use cache bypass lists when the webcache is dep...
Page 189
Cache bypass 189 or web sites that you want to add to the list andclick add. Repeat this for each ip address that you want to bypass. Example you can enter 216.115.0.0-216.115.255.255 to bypass that ip address range, or enter 216.115.105.2 to bypass that ip address. You must follow all of the rules ...
Page 190
190 c hapter 11: c ontrolling h ow w eb s ites a re c ached the load list process may take a few seconds to complete, depending on the number of entries in the file. Load list rules there are certain rules that you must follow when loading a list of web sites into the client bypass and web site bypa...
Page 191
Cache bypass 191 clearing the cache bypass lists you can use the clear list screen to delete all the current entries in the cache bypass list(s). To clear the cache bypass list(s): 1 log in to the web interface. 2 click caching on the toolbar. 3 select cache bypass > clear list in the navigation tre...
Page 192
192 c hapter 11: c ontrolling h ow w eb s ites a re c ached dua1611-5aaa04.Book page 192 friday, november 29, 2002 8:56 pm.
Page 193: Reloading
12 p reloading c ontent this chapter contains information about preloading web sites into your webcache before they are requested by clients browsing the web. It is split into the following sections: ■ introduction ■ setting up content preload ■ preloading a site ■ checking the status of scheduled t...
Page 194
194 c hapter 12: p reloading c ontent introduction the preload content feature enables the administrator and other authorized users to preload required sites onto the webcache before they are requested. These preloads can be done manually or run on a schedule outside working hours and enable you to ...
Page 195
Setting up content preload 195 ■ speeds up web access within your network. ■ may delay current content reaching your users if used inappropriately. Methods of preloading content the webcache offers two methods of scheduling the preloading of content: ■ using the web interface — content can be preloa...
Page 196
196 c hapter 12: p reloading c ontent by default, the webcache will limit the bandwidth used for preload tasks to 10mbits/s between the selected times. The hours selected will have no effect on days where the bandwidth has not been restricted. 7 enter the maximum bandwidth that the webcache is to us...
Page 197
Preloading a site 197 adding/editing scheduled tasks to define a preload task: 1 log in to the web interface. 2 click caching on the toolbar. 3 select content preload > preload tasks > preload tasks to see the edit preload tasks window. 4 to add a new preload task, click add. To edit an existing pre...
Page 198
198 c hapter 12: p reloading c ontent 10 select the frequency of the preload task from every hour, every day, every week or once. 11 select the start time from the at: drop-down box. The preload task will start at the specified time of day but will not have a guaranteed finish time since it is condi...
Page 199
Checking the status of scheduled tasks 199 4 select a preload task from the list. 5 click preload now. The preload will start regardless of the scheduled time. 6 click ok to return to the web interface. You can only force one preload task at a time. If you try to force a preload task whilst another ...
Page 200
200 c hapter 12: p reloading c ontent ■ last complete status — shows if the preload task failed. A preload task has failed if no web objects were retrieved. If the task retrieved any objects the word ok is displayed. ■ last complete time — displays the time at which the task last completed. Subtract...
Page 201
Using the 3com web scheduler browser client 201 ■ error count — shows the number of errors encountered while completing the task. Errors may be caused by missing images, broken links between web pages or by heavy traffic causing requests by the webcache to time out. If the task is currently active t...
Page 202
202 c hapter 12: p reloading c ontent 4 ensure that the enable 3com web scheduler browser client box is checked. 5 click the change password button, choose a password for the 3com web scheduler browser client, and enter it in the password box. You must supply this password to users of the 3com web s...
Page 203
Using the 3com web scheduler browser client 203 2 follow the instructions displayed during the install. When completed start internet explorer to display the toolbar shown in figure 36 below. Figure 36 3com web scheduler browser client 3 click on the options button on the web scheduler browser clien...
Page 204
204 c hapter 12: p reloading c ontent dua1611-5aaa04.Book page 204 friday, november 29, 2002 8:56 pm.
Page 205: Onitoring
Vi m onitoring t he w ebcache chapter 13 monitoring system events chapter 14 performance monitoring chapter 15 system diagnostics dua1611-5aaa04.Book page 205 friday, november 29, 2002 8:56 pm.
Page 206
206 dua1611-5aaa04.Book page 206 friday, november 29, 2002 8:56 pm.
Page 207: Onitoring
13 m onitoring s ystem e vents this chapter contains information about the system events that can occur on the webcache 1000/3000. It covers the following topics: ■ system events ■ email notification ■ snmp traps ■ automatic system events dua1611-5aaa04.Book page 207 friday, november 29, 2002 8:56 p...
Page 208
208 c hapter 13: m onitoring s ystem e vents system events system events are events that occur on the webcache which can be reported to you. They range in significance from minor, such as new software upgrade detected, to major, such as system error. You can configure the webcache to automatically i...
Page 209
Email notification 209 3com recommends that you use the domain name of the webcache as the email address. If you have entered “webcache” as the host name and “mycompany.Com” as the dns domain name of the webcache, then you would enter “webcache@mycompany.Com” as the email address. 7 in the to addres...
Page 210
210 c hapter 13: m onitoring s ystem e vents ■ a preload task has failed. ■ content filtering events this includes the following events: ■ the content filter license has expired. ■ the websense enterprise server is unreachable. In addition to the above, the webcache automatically generates the email...
Page 211
Email notification 211 cram-md5. Both windows exchange and unix servers support plain authentication. Disabling smtp authentication if you disable smtp authentication by leaving enable smtp authentication blank and not specifying an smtp username and smtp password, the smtp server will attempt to au...
Page 212
212 c hapter 13: m onitoring s ystem e vents snmp traps you can configure the webcache to automatically generate simple network management protocol (snmp) traps when certain significant system events occur. An snmp trap is a message generated by the webcache in response to a particular event. It is ...
Page 213
Snmp traps 213 there are two community strings, one for each of the following type of access: ■ public — a network management station that makes snmp requests using the correct public community string will gain read-only access to the webcache to view its status or configuration information. ■ priva...
Page 214
214 c hapter 13: m onitoring s ystem e vents automatic system events both an snmp trap and an email notification are automatically generated by the webcache if a system event shown in table 9 occurs. Table 9 automatic system events system event email message snmp trap message description system erro...
Page 215
Automatic system events 215 temperature warning temperature warning. The temperature is out of acceptable range. The unit is in danger of overheating. Current temperature: ° c. N/a the temperature of the specified component (motherboard) is outside the acceptable range and the component may overheat...
Page 216
216 c hapter 13: m onitoring s ystem e vents new software upgrade detected a new software image (version number>) is available for your webcache. The webcache is currently running number>. Click here to run the software upgrade wizard: http://nnn.Nnn.Nnn.Nnn 'a new image (version ) is available for ...
Page 217
Automatic system events 217 content filter license warning the content filtering license for the webcache has expired. The webcache will continue to filter using the last downloaded list for a further 30 days. The content filtering license for the webcache has expired. The webcache will continue to ...
Page 218
218 c hapter 13: m onitoring s ystem e vents dua1611-5aaa04.Book page 218 friday, november 29, 2002 8:56 pm.
Page 219: Erformance
14 p erformance m onitoring this chapter contains information about monitoring the performance of the webcache 1000/3000. It covers the following topics: ■ performance monitoring ■ viewing performance graphs ■ viewing caching performance graphs ■ viewing system performance graphs ■ viewing i/o perfo...
Page 220
220 c hapter 14: p erformance m onitoring performance monitoring performance monitoring allows you to assess the caching and system performance of the webcache via a series of easy-to-understand graphs. The caching performance graphs show the bandwidth savings, hit/miss rate, request rate, response ...
Page 221
Viewing performance graphs 221 calculated as the ratio of bytes served by the webcache to total requested bytes. A high graph rating is desirable because it indicates that the webcache has reduced wan bandwidth use. A low graph rating indicates the opposite. ■ hit rate the hit rate reveals how effec...
Page 222
222 c hapter 14: p erformance m onitoring webcache’s peak capacity — will normally improve the caching behavior. However, a very low or zero request rate might indicate that the webcache is not receiving the requests correctly and furthermore suggests that there is a problem with the setup and the d...
Page 223
Viewing performance graphs 223 ■ clients looking for servers that do not exist. ■ clients hitting the stop button on their browser before the page is loaded. ■ connections timing out due to excessive traffic. ■ filtering block rate the percentage of requests from users that were blocked or logged by...
Page 224
224 c hapter 14: p erformance m onitoring the webcache has its own internal cache of dns entries. The dns hit rate shows how effective this cache is being in avoiding dns lookups to the dns server. Viewing system performance graphs to view the system performance graphs select system from the navigat...
Page 225
Emailing performance graphs 225 configuring email performance graphs to configure email performance graphs using the web interface: 1 log in to the web interface. 2 select the performance from the toolbar. 3 select email graphsin the navigation tree. The email performance graphs screen is displayed....
Page 226
226 c hapter 14: p erformance m onitoring 12 in the realm/domain name field, you can enter the unix realm or windows domain that the smtp user belongs to, or leave the field blank. For further information about how smtp authentication operates on the webcache, see “smtp authentication” on page 210 ....
Page 227: Ystem
15 s ystem d iagnostics this chapter contains information about troubleshooting the configuration and network connectivity of the webcache 1000/3000. It covers the following topics: ■ system diagnostics ■ pinging other devices ■ tracing ip addresses ■ system log dua1611-5aaa04.Book page 227 friday, ...
Page 228
228 c hapter 15: s ystem d iagnostics system diagnostics you can use the various system diagnostic capabilities of the webcache to help you identify any problems that may occur. ■ ping — ping other devices on the network. ■ trace route — trace the network hops to a device on your network. ■ system l...
Page 229
Tracing ip addresses 229 you can interrupt a ping request at any time by clicking stop. Some network environments block ping traffic on the network. The ping request may therefore fail even if the network device is operating normally. Tracing ip addresses the trace route feature allows you to displa...
Page 230
230 c hapter 15: s ystem d iagnostics you can interrupt a trace route request at any time by clicking stop. Some network environments block trace route traffic on the network. The traceroute request may therefore fail even if the network device is operating normally. System log the system log record...
Page 231
System log 231 should only enable it if you have been instructed to do so by 3com support personnel. What is a syslog server? Syslog is a standard protocol for reporting system events that occur on the webcache and most other modern network devices. A syslog server allows you to capture these system...
Page 232
232 c hapter 15: s ystem d iagnostics viewing the system log to view the contents of the system log using the web interface: 1 log in to the web interface. 2 click device on the toolbar. 3 select diagnostics > view system login the navigation tree. The system log screen is displayed. The last 256 li...
Page 233: Vii
Vii m anaging t he w ebcache s oftware chapter 16 configuration management chapter 17 software upgrades dua1611-5aaa04.Book page 233 friday, november 29, 2002 8:56 pm.
Page 234
234 dua1611-5aaa04.Book page 234 friday, november 29, 2002 8:56 pm.
Page 235: Onfiguration
16 c onfiguration m anagement this chapter contains information about saving and restoring the configuration settings of the webcache 1000/3000. It covers the following topics: ■ saving and restoring configurations ■ saving a configuration ■ restoring a configuration dua1611-5aaa04.Book page 235 fri...
Page 236
236 c hapter 16: c onfiguration m anagement saving and restoring configurations saving and restoring configurations is primarily intended to allow you to revert to a previous software version in the unlikely event that you are experiencing problems following a software upgrade of the webcache. You s...
Page 237
Saving a configuration 237 if you had not previously saved a system configuration file for the older software version, you would still be able to install a previous software image, but you would have to re-enter all of the configuration settings. Caution: you cannot restore a system configuration wh...
Page 238
238 c hapter 16: c onfiguration m anagement the webcache will automatically prompt you to save the current system configuration of the webcache before you perform a software upgrade or a software installation. 3com recommends that you always save the current system configuration of the webcache befo...
Page 239: Oftware
17 s oftware u pgrades this chapter contains information about upgrading and installing the management software of the webcache 1000/3000. It covers the following topics: ■ software upgrades ■ software downgrades ■ detecting a software upgrade ■ performing a software upgrade dua1611-5aaa04.Book page...
Page 240
240 c hapter 17: s oftware u pgrades software upgrades you can upgrade the management software of the webcache when a new version becomes available. The webcache can detect any new webcache software that has been made publicly available. There may be even newer functional releases or bug fixes avail...
Page 241
Software downgrades 241 for further information about snmp traps, see “snmp traps” on page 212 . Unsuccessful software upgrades the webcache software upgrade process is robust and guards against an upgrade failure. Should a software upgrade fail, the webcache will automatically revert to using the s...
Page 242
242 c hapter 17: s oftware u pgrades the webcache can detect any new webcache software that has been made publicly available. There may be even newer functional releases or bug fixes available for your webcache. To receive the very latest releases you must purchase a support contract for your webcac...
Page 243
Performing a software upgrade 243 if necessary, you can change the ftp site that the webcache automatically downloads software upgrades from by entering the new ftp address, directory, user name and password in the appropriate fields. You may want to change the ftp site in order to download a softwa...
Page 244
244 c hapter 17: s oftware u pgrades 3 the save configuration screen is displayed. Click save configuration if you want to save the system configuration. The save configuration operation saves the webcache’s current system configuration as a file in another location on your network. 3com recommends ...
Page 245
Performing a software upgrade 245 if you selected upgrade later, the upgrade later screen is displayed. Click finish to exit the upgrade software wizard. If you selected discard upgrade, thediscard upgrade screen is displayed. Click finish to exit the upgrade software wizard. 7 carefully read the su...
Page 246
246 c hapter 17: s oftware u pgrades 3 select system > control > upgrade softwarein the navigation tree. The first screen of the upgrade software wizard is displayed. Click next. 4 you will be informed if an automatic upgrade is available. Click manual upgrade/downgrade to continue. 5 the manual upg...
Page 247
Performing a software upgrade 247 12 the software upgrade may take several minutes to complete. The software upgrade successful screen is displayed when the software upgrade has been successful. 13 click reboot to exit the upgrade software wizard and reboot the webcache. This will complete the softw...
Page 248
248 c hapter 17: s oftware u pgrades dua1611-5aaa04.Book page 248 friday, november 29, 2002 8:56 pm.
Page 249: Viii
Viii c ommand l ine i nterface chapter 18 command line interface dua1611-5aaa04.Book page 249 friday, november 29, 2002 8:56 pm.
Page 250
250 dua1611-5aaa04.Book page 250 friday, november 29, 2002 8:56 pm.
Page 251: Ommand
18 c ommand l ine i nterface the webcache 1000/3000 has a command line interface that allows you to manage certain features from a terminal. You may want to use the command line interface to setup the webcache for management through the console port or over your network via telnet. This chapter desc...
Page 252
252 c hapter 18: c ommand l ine i nterface a quick guide to the commands table 10 describes the commands that are available in the command line interface. Table 10 command line interface commands command what does it do? Gettingstarted specifies basic setup information for the webcache. Logout exits...
Page 253
Getting started 253 getting started the getting started command allows you to quickly configure or view basic setup information for the webcache. To configure basic setup information: 1 at the top-level menu, enter: gettingstarted the following prompt is displayed: enter system name: 2 enter a syste...
Page 254
254 c hapter 18: c ommand l ine i nterface 9 enter a valid domain name. The following prompt is displayed: enter first search domain 10 enter a valid search domain name. The following prompt is displayed: enter second search domain 11 enter a valid search domain name. The following prompt is display...
Page 255
Getting started 255 if you enter primary and secondary ntp server addresses and both are available, the webcache automatically uses the most reliable one. ■ if you entered manual , the following prompt is displayed: enter date [dd/mm/yy]: enter a valid date. The following prompt is displayed: enter ...
Page 256
256 c hapter 18: c ommand l ine i nterface the following prompt is displayed: enter the mode of operation (proxy, transparent, inline) [transparent]: 21 enter either proxy , transparent or inline . For further information, see “deploying the webcache in your network” on page 70 . If you entered prox...
Page 257
Displaying and changing wan and lan port information 257 to configure the wan and lan port settings: 1 at the top-level menu, enter: physicalinterface portmode the following prompt is displayed: warning: changing the port configuration may cause loss of any existing network connections to the webcac...
Page 258
258 c hapter 18: c ommand l ine i nterface an example of the summary information is shown below: displaying and changing protocol information you can display and change the protocol information for the webcache using the commands on the ip menu. These commands allow you to: ■ configure the ip and do...
Page 259
Displaying and changing protocol information 259 4 enter a valid gateway ip address. The following prompt is displayed: enter host name: 5 enter a valid host name. The following prompt is displayed: enter domain name 6 enter a valid domain name. The following prompt is displayed: enter first search ...
Page 260
260 c hapter 18: c ommand l ine i nterface 2 enter a valid host name. The following prompt is displayed: enter domain name 3 enter a valid domain name. The following prompt is displayed: enter first search domain 4 enter a valid domain name. The following prompt is displayed: enter second search dom...
Page 261
Displaying and changing protocol information 261 the following prompt is displayed: 2 enter yes to reset the ip and dns information for the webcache. Specifying ip configuration you can use the ipconfig command on the protocol menu to configure the ip stack of the webcache. This will allow you to ma...
Page 262
262 c hapter 18: c ommand l ine i nterface pinging other devices the ping feature allows you to send out ping requests to test whether devices on an ip network are accessible and functioning correctly. This feature is useful to diagnose connectivity problems such as a failed network device between t...
Page 263
Displaying and changing protocol information 263 displaying ip summary information you can display ip summary information for the webcache using the summary command on the protocol menu. To display the ip information, at the top-level menu, enter: protocol summary the ip information for the webcache...
Page 264
264 c hapter 18: c ommand l ine i nterface 2.Bw-rtr-4.Eur.3com.Com (161.71.21.45) 26.027ms, 27.156ms, 44.902ms 3.Bw-rtr-1.Eur.3com.Com (140.204.220.15) 24.323ms, 24.854ms, 30.096ms 4.Janeway (161.71.123.36) 27.303ms, 33.639ms if the device is not accessible, or is not functioning correctly, a messag...
Page 265
Displaying and changing security information 265 the following message is displayed: by default, the web interface is available on port 80 and port 8081. You can disable the web interface on port 80. Web interface is available on tcp port 80 (yes/no) [yes]: 2 enter yes to keep the web interface avai...
Page 266
266 c hapter 18: c ommand l ine i nterface restricting access does not change the caching operation of the webcache. Only access to the web interface, cli via telnet and snmp is affected. Changing the admin password you can change the password for the admin user using the password command on the sec...
Page 267
Displaying and changing webcache information and functions 267 the password recovery feature is enabled. Enter new value (enable,disable) [enable]: displaying and changing webcache information and functions you can display and change information about the webcache using the commands on the system me...
Page 268
268 c hapter 18: c ommand l ine i nterface caution: use great care when initializing the webcache. It removes all configuration information, including password and security information. The webcache is rebooted, which takes approximately 60-90 seconds. While the webcache is being rebooted, you canno...
Page 269
Displaying and changing webcache information and functions 269 the following prompt is displayed: enter new public (get/read) community [public]: 3 enter the community string for public (get/read) requests to the webcache. You can enter a maximum of 30 characters for each community string. Specifyin...
Page 270
270 c hapter 18: c ommand l ine i nterface enter system name []: 2 enter a system name for the webcache. The name can be up to 80 characters long. Displaying summary information you can display the summary information for the webcache using the summary command on the system menu. This information ma...
Page 271
Displaying and changing webcache information and functions 271 ■ contact displays the details of a person to contact about the webcache. For information about assigning new contact details, see “specifying a contact name” on page 269 . ■ up time displays the time that has elapsed since the webcache ...
Page 272
272 c hapter 18: c ommand l ine i nterface dua1611-5aaa04.Book page 272 friday, november 29, 2002 8:56 pm.
Page 273: Roblem
Ix p roblem s olving chapter 19 problem solving dua1611-5aaa04.Book page 273 friday, november 29, 2002 8:56 pm.
Page 274
274 dua1611-5aaa04.Book page 274 friday, november 29, 2002 8:56 pm.
Page 275: Roblem
19 p roblem s olving this chapter contains a list of known problems and suggested solutions. It covers the following topics: ■ accessing the webcache via the console line ■ accessing the webcache via telnet ■ solving problems indicated by leds ■ solving web interface problems ■ solving command line ...
Page 276
276 c hapter 19: p roblem s olving accessing the webcache via the console line the terminal or terminal emulator cannot access the webcache. Check that: ■ your terminal or terminal emulator is correctly configured to operate as a generic (tty) terminal, or a vt100 terminal. ■ you have performed the ...
Page 277
Solving problems indicated by leds 277 check that the connections and network cabling for the lan port are in place. If there is still a problem, try accessing the webcache through a different port. If you can now access the webcache, a problem may have occurred with the original port. Contact your ...
Page 278
278 c hapter 19: p roblem s olving ■ netscape communicator v4.6 ■ netscape communicator v4.7 ■ netscape communicator v6.0 for the browser to operate the web interface correctly javascript ™ and cascading style sheets must be enabled on your browser. These features are enabled on a browser by default...
Page 279
Solving web interface problems 279 amounts of traffic on the network. Reload the web interface by clicking reload on the browser’s toolbar. If this does not solve the problem, go to the end of the url in the address field of the browser and press [return]. This causes the page to be reloaded entirel...
Page 280
280 c hapter 19: p roblem s olving if the ntp server is not functional, or you are not confident it is working correctly, try using another ntp server. ■ if ntp is enabled and operational, check that traffic on tcp port 123 is not blocked by a firewall between the webcache and the ntp server. ■ the ...
Page 281
Solving webcache performance problems 281 this service provides access to instructions about how to obtain a replacement cache storage device. As long as there is at least one working cache storage device, the webcache will operate as a cache, but the failure of a cache storage device will degrade t...
Page 282
282 c hapter 19: p roblem s olving for further information about deploying the superstack 3 firewall with the webcache, see “proxy relay deployment” on page 44 . You have enabled cache bypass and the webcache can no longer connect to the world wide web in a wccp version 2.0 deployment, if the webcac...
Page 283
Solving general webcache problems 283 when a web site is blocked, rather than the response page generated by the webcache. You can turn this setting off by selecting tools > internet options > advanced and unchecking show friendly http error messages. The proxy auto configuration (pac) file is ignor...
Page 284
284 c hapter 19: p roblem s olving webcache. Check the dns configuration of the webcache. You must ensure that you enter the full domain e.G. 3com.Com . It is not sufficient to only enter 3com . The cache storage status led on the front panel of the webcache is yellow a yellow cache storage status l...
Page 285: Ppendices
X a ppendices and i ndex appendix a safety information appendix b cable specifications and pin-outs appendix c technical specifications appendix d technical support appendix e default settings for the webcache appendix f replacing and installing cache storage devices appendix g cisco wccp commands a...
Page 286
286 dua1611-5aaa04.Book page 286 friday, november 29, 2002 8:56 pm.
Page 287: Afety
A s afety i nformation you must read the following safety information before carrying out any installation or removal of components, or any maintenance procedures on the webcache 1000/3000. Warning: warnings contain directions that you must follow for your personal safety. Follow all directions care...
Page 288
288 a ppendix a: s afety i nformation important safety information warning: installation and removal of the unit must be carried out by qualified personnel only. Warning: the unit must be earthed (grounded). Warning: the unit must be connected to an earthed (grounded) outlet to comply with european ...
Page 289
Important safety information 289 warning: this unit operates under selv (safety extra low voltage) conditions according to iec 950. The conditions are only maintained if the equipment to which it is connected also operates under selv conditions. Warning: the appliance coupler (the connector to the u...
Page 290
290 a ppendix a: s afety i nformation consignes importantes de sécurité avertissement: l'installation et la dépose de ce groupe doivent être confiés à un personnel qualifié. Avertissement: vous devez mettre l’appareil à la terre (à la masse) ce groupe. Avertissement: vous devez raccorder ce groupe à...
Page 291
Consignes importantes de sécurité 291 avertissement: l’appareil fonctionne à une tension extrêmement basse de sécurité qui est conforme à la norme cei 950. Ces conditions ne sont maintenues que si l'équipement auquel il est raccordé fonctionne dans les mêmes conditions. Avertissement: le coupleur d'...
Page 292
292 a ppendix a: s afety i nformation connecteurs de données rj-45, systèmes de réseaux de téléphonie ou téléphones de réseaux à ces prises. Il est possible de raccorder des câbles protégés ou non protégés avec des jacks protégés ou non protégés à ces prises de données. Wichtige sicherheitsinformat ...
Page 293
Wichtige sicherheitsinformationen 293 bedingungen sind nur gegeben, wenn auch die an das gerät angeschlossenen geräte unter selv-bedingungen betrieben werden. Vorsicht: der gerätestecker (der anschluß an das gerät, nicht der wandsteckdosenstecker) muß eine passende konfiguration für einen geräteeing...
Page 294
294 a ppendix a: s afety i nformation dua1611-5aaa04.Book page 294 friday, november 29, 2002 8:56 pm.
Page 295: Able
B c able s pecifications and p in - outs cable specifications the webcache supports the following cable types: ■ category 3 one of five grades of twisted pair (tp) cabling defined by the eia/tia-586 standard. Category 3 is voice grade cable and can only be used in ethernet networks (10base-t) to tra...
Page 296
296 a ppendix b: c able s pecifications and p in - outs pin-outs null-modem cable 9-pin to rs-232 25-pin pc-at serial cable 9-pin to 9-pin screen txd rxd ground rts cts dsr dcd dtr screen rxd txd ground rts dtr cts dsr dcd shell 3 2 5 7 8 6 1 4 1 3 2 7 4 20 5 6 8 webcache 1000/3000 cable connector: ...
Page 297
Pin-outs 297 modem cable 9-pin to rs-232 25-pin rj-45 pin assignments pin assignments are identical for 10base-t and 100base-tx rj-45 connectors. Table 12 pin assignments screen txd rxd rts cts dsr ground dcd dtr screen txd rxd rts cts dsr ground dcd dtr shell 3 2 7 8 6 5 1 4 1 2 3 4 5 6 7 8 20 webc...
Page 298
298 a ppendix b: c able s pecifications and p in - outs dua1611-5aaa04.Book page 298 friday, november 29, 2002 8:56 pm.
Page 299: Echnical
C t echnical s pecifications physical dimensions height: 44.45mm (1.75 in.) x width: 482.6 mm (19.00 in.) x depth: 610 mm (24.02 in.) (not including bulge). Weight: 13 kg (28.66 lbs) environmental requirements operating temperature 0 ° to 40 °c (32 ° to 104 °f) storage temperature –10 ° to +70 °c (1...
Page 300
300 a ppendix c: t echnical s pecifications standards supported snmp: snmp protocol (rfc 1517) mib-ii (rfc 1213) interface mib (rfc 1573) remote monitoring mib (rfc 1757) terminal emulation: telnet (rfc 854) protocols used for administration: udp (rfc 768) ip (rfc 791) icmp (rfc 792) tcp (rfc 793) a...
Page 301: Echnical
D t echnical s upport 3com provides easy access to technical support information through a variety of services. This appendix describes these services. You can purchase additional services from your network supplier or from 3com. These services can enhance warranty response times. They can also prov...
Page 302
302 a ppendix d: t echnical s upport 3com knowledgebase web services the 3com knowledgebase is a database of technical information to help you install, upgrade, configure, or support 3com products. The knowledgebase is updated daily with technical information discovered by 3com technical support eng...
Page 303
Support from 3com 303 support from 3com if you are unable to obtain assistance from the 3com online technical resources discussed earlier in this appendix, or from your network supplier, 3com offers a range of support services. Purchase of a support contract gives you priority response and is typica...
Page 304
304 a ppendix d: t echnical s upport here is a list of worldwide technical telephone support numbers. These numbers are correct at the time of publication. Refer to the 3com web site for updated information. Country telephone number country telephone number asia, pacific rim australia hong kong indi...
Page 305
Returning products for repair 305 returning products for repair before you send a product directly to 3com for repair, you must first obtain an authorization number. Products sent to 3com without authorization numbers will be returned to the sender unopened, at the sender’s expense. To return the a ...
Page 306
306 a ppendix d: t echnical s upport table 13 product return telephone numbers country telephone number country telephone number asia, pacific rim from anywhere in this region, call: + 65 543 6500 phone + 65 543 6348 fax europe, middle east and africa from anywhere in these regions, call: +44 (0)144...
Page 307: Efault
E d efault s ettings for the w ebcache default settings table 14 shows the factory default settings for the webcache: table 14 default settings feature webcache 1000/3000 port status lan port: enabled auto-negotiation wan port: enabled auto-negotiation port speed 10base-t/100base-tx mbps ports are a...
Page 308
308 a ppendix e: d efault s ettings for the w ebcache if you initialize the webcache by selecting system > control > initialize from the device menu in the web interface or by entering system control initialize in the command line interface, the following settings are retained to allow you to connec...
Page 309
Getting started wizard settings 309 ■ host name ■ domain name system (dns) domain all other settings are reset to the default values shown in table 14 . Getting started wizard settings the following table shows the settings that you can configure in both the web interface and command line interface ...
Page 310
310 a ppendix e: d efault s ettings for the w ebcache search domains search domains allow you to control how unqualified urls are handled by the webcache. An example of an unqualified url is http://info/. They are typically used for intranet web servers. If 2 search domains are specified, the webcac...
Page 311
Getting started wizard settings 311 caching mode choose how the webcache is deployed within your network - either proxy mode, transparent mode or inline mode. Note that proxy mode is always enabled. You must enable transparent mode if you want to deploy the webcache with the superstack 3 switch 4400...
Page 312
312 a ppendix e: d efault s ettings for the w ebcache dua1611-5aaa04.Book page 312 friday, november 29, 2002 8:56 pm.
Page 313: Eplacing
F r eplacing and i nstalling c ache s torage d evices this chapter contains information about replacing failed cache storage devices and installing a third cache storage device in the webcache 3000. It covers the following topics: ■ replacing a failed cache storage device ■ installing an additional ...
Page 314
314 a ppendix f: r eplacing and i nstalling c ache s torage d evices replacing a failed cache storage device if a cache storage device fails in the webcache 3000, you can remove it and return it to 3com for replacement. A yellow cache storage status led on the front of the webcache indicates that a ...
Page 315
Replacing a failed cache storage device 315 6 if you have mounted the webcache in a rack using the supplied rack-mounting kit, you must slide the webcache forward by approximately 1 inch, in order to fully open the front panel. 7 open the front panel of the webcache, as shown in figure 37 . Figure 3...
Page 316
316 a ppendix f: r eplacing and i nstalling c ache s torage d evices 9 close the front panel of the webcache. 10 return the cache storage device to 3com. For further information about returning a failed cache storage device to 3com, enter the following url into your web browser: http://knowledgebase...
Page 317
Installing an additional cache storage device 317 caution: the webcache service will be interrupted during the addition of the cache storage device and client machines may experience network problems. Installing an additional cache storage device the webcache 3000 has two cache storage devices insta...
Page 318
318 a ppendix f: r eplacing and i nstalling c ache s torage d evices 6 gently push the mounting tray back into the webcache until it stops. 7 push in the arms on the front of the tray to click them into place. 8 close the front panel of the webcache. 9 log in to the web interface. 10 click device on...
Page 319: Isco
G c isco wccp c ommands the web cache communication protocol (wccp) allows the webcache to be connected to one or more wccp-enabled cisco routers in your network. There are two versions of wccp, known as wccp v1 and wccp v2, which require different deployment methods. In addition to configuring the ...
Page 320
320 a ppendix g: c isco wccp c ommands configuring wccp version 1.0 to configure wccp version 1.0 on a cisco router enter the following settings in the cisco command line interface: ip wccp version 1 ip wccp web-cache interface eth0 ip wccp web-cache redirect out ip route-cache same-interface exit s...
Page 321
Configuring wccp version 2.0 321 configuring wccp version 2.0 the wccp 2.0 router commands have the general form of: ip wccp service-id the following services are defined in the webcache: ■ service-id 0 — http ■ service-id 5 — ftp wherever you see in this appendix, it needs to be replaced by one of ...
Page 322
322 a ppendix g: c isco wccp c ommands this rule is applied on a per interface basis and is applied to the interface connected to the caches. It prevents packets being redirected to the internet from looping back to the webcaches. Configuring wccp multicast to enable or disable wccp multicast on a c...
Page 323
Configuring wccp version 2.0 323 cache access list to achieve better security, you can tell the router which ip addresses are valid addresses for a webcache attempting to register with the current router, using a standard access list. The following example shows a standard access list configuration ...
Page 324
324 a ppendix g: c isco wccp c ommands configuring wccp version 2.0 within a single subnet if you are configuring a network where the webcache and client machines reside on the same segment, special settings are required on the cisco router to implement a wccp solution. Remove the ip wccp redirect e...
Page 325: Ormats
H l og f ormats the webcache can save its log files to an ftp server (see “storing the log files” on page 140 ). The access logs are saved in five formats, described in “access log formats” below. The format of the filter log is described in “filter log format” on page 331 . Access log formats the w...
Page 326
326 a ppendix h: l og f ormats the webcache supports welf, the webtrends enhanced log format, so that you can analyze the webcache access log files with webtrends reporting tools. 3com recommends that you select the webtrends extended log format (welf) option and use webtrends log analyzer or webtre...
Page 327
Access log formats 327 netscape common format table 17 lists the netscape common format logging fields. The format of netscape common format log file entries is: host - usr [time] "req" status length netscape extended format table 18 lists the netscape extended format logging fields. The format of n...
Page 328
328 a ppendix h: l og f ormats netscape extended 2 format table 19 lists the netscape extended 2 format logging fields. The format of netscape extended format 2 log file entries is: host - usr [time] "req" status length servstat servlngth creql sreql chdrl prspl preql srspl tts route cs ss crc [time...
Page 329
Access log formats 329 usr the client authenticated user name; result of the rfc931/ident lookup of the client user name. [time] the client request timestamp; date and time of the client’s request. “req“ the full http client request text, minus headers; for example, get http://www.3com.Com http/1.0 ...
Page 330
330 a ppendix h: l og f ormats webtrends extended log format table 20 lists the webtrends extended log format logging fields. The format of webtrends extended log format log file entries is: id=firewall time fw pri proto duration sent rcvd src dst dstname user op arg result ref agent cache table 20 ...
Page 331
Filter log format 331 filter log format the filter log file lists all web accesses that were filtered by the webcache. See “using content filtering” on page 145 for information on content filtering and table 21 below for descriptions of the filter log fields. The format of filter log file entries is...
Page 332
332 a ppendix h: l og f ormats ident the client authenticated user name if per-user authentication is enabled. If per-user authentication is not enabled, this field has the value "-". Category the filter category (one of those described in section 3.2.2) that prevented the access, e.G. Core, product...
Page 333: Race
I t race r oute s ymbols the trace route feature allows you to display the network hops from the webcache to a device on an ip network. A symbol may be displayed after a network hop which provides further information about that hop. The symbol may indicate systems that are unwilling to participate i...
Page 334
334 a ppendix i: t race r oute s ymbols dua1611-5aaa04.Book page 334 friday, november 29, 2002 8:56 pm.
Page 335: Ategory
J c ategory s et d efinitions core categories the 3com web site filter groups sites in the core categories so that you can block individual topics. The web site filter will also block entire web hosting sites (isps) under all core categories. This is because such sites often hold a substantial amoun...
Page 336
336 a ppendix j: c ategory s et d efinitions ■ alcohol and tobacco manufacturers' commercial web sites. ■ sites detailing how to achieve ‘legal highs’, glue sniffing, misuse of prescription drugs or abuse of other legal substances. ■ sites that make available alcohol, illegal drugs, or tobacco free ...
Page 337
Productivity categories 337 promote a political or social agenda which is supremacist in nature and exclusionary of others based on their race, religion, nationality, gender, age, disability or sexual orientation. ■ holocaust revision/denial sites. ■ coercion or recruitment for membership in a gang ...
Page 338
338 a ppendix j: c ategory s et d efinitions ■ celebrity fan sites. ■ city guides. Games this includes: ■ web sites that allow a user to download or play online games. ■ tips and advice on playing computer and internet-based games. ■ journals and magazines dedicated to game playing. ■ web sites host...
Page 339
Productivity categories 339 investment this includes: ■ web sites that provide stock quotes, stock tickers and fund rates. ■ web sites that allow stock or equity trading online. ■ investing advice or contacts for trading securities. ■ money management/investment services or firms. Job search this in...
Page 340
340 a ppendix j: c ategory s et d efinitions shopping this includes: ■ internet malls and online auctions. ■ department stores, retail stores, company catalogs online. ■ online downloadable product warehouses; specialty items for sale. ■ companies online dedicated to freebies or merchandise giveaway...
Page 341: Lossary
G lossary 3com network supervisor the 3com umbrella management system used to manage all of 3com’s networking solutions. 3com web scheduler a web browser plug-in that allows permitted users to schedule content preloads without administrator access to the webcache. 10base-t the ieee specification for...
Page 342
342 g lossary client machine a computer, printer or server that is connected to a network. In this user guide, client machine is used to describe a machine on your network which is running a web browser such as internet explorer or netscape navigator. Content filtering the blocking or logging access...
Page 343
G lossary 343 fresh content stored in the cache can either be fresh (also known as current) or stale (also known as expired). If it is fresh, the content is up to date and the webcache serves it to the client machine as a cache hit. See also current . Ftp file transfer protocol. A protocol based on ...
Page 344
344 g lossary ip address internet protocol address. A unique identifier for a device attached to a network using tcp/ip. The address is written as four octets separated with periods (full-stops), and is made up of a network section, an optional subnet section and a host section. Lan local area netwo...
Page 345
G lossary 345 ping packet internet or inter-network gropher. This feature allows you to send out a ping request to test whether devices on an ip network are accessible and functioning correctly. Protocol a set of rules for communication between devices on a network. The rules dictate format, timing,...
Page 346
346 g lossary tcp relates to the content of the data travelling through a network — ensuring that the information sent arrives in one piece when it reaches its destination. Ip relates to the address of the client machine to which data is being sent, as well as the address of the destination network....
Page 347
G lossary 347 wpad web proxy auto-discovery. This protocol enables the web browser on client machines to automatically find and load proxy configuration information from a server without user intervention. Dua1611-5aaa04.Book page 347 friday, november 29, 2002 8:56 pm.
Page 348
348 g lossary dua1611-5aaa04.Book page 348 friday, november 29, 2002 8:56 pm.
Page 349: Ndex
I ndex 349 i ndex numbers 10base-t/100base-tx port 63 3com knowledgebase web services 302 3com network supervisor 24, 208 3com url 301 3com web scheduler 201 3com web site filter 147 a access levels of default users 88 access logging 140 analyzing the logs 142 configuring 140 log offload 140 netscap...
Page 350
350 i ndex management setting up over the network 83 setting up through the console port 82, 83 name command 269 operating 83 password command 266 ping command 262 protocol 258 pwdrecover command 266 quick guide 252 reboot command 268 security 264 solving problems 280 summary (system) command 270 su...
Page 351
I ndex 351 f factory defaults 65, 307 filter policy creating 152 forcing a preload preloading content 198 forgetting your password 106 front panel 61 front panel leds 61 activity 62 cache storage status 61 link status 61 power/self test 62 g getting started command 253 gnu general public license 358...
Page 352
352 i ndex modem cable 75 pin-outs 297 monitoring performance 219 monitoring web access 139 mrtg license 358 n name command 269 navigation tree 94 netscape common log format 327 netscape extended 2 log format 328 netscape extended log format 327 network addresses 26 hops 333 network hops 229 symbols...
Page 353
I ndex 353 proxy auto configuration (pac) 48 proxy cache 45 manually configuring web browsers 47 proxy auto configuration (pac) 48 web proxy auto-discovery (wpad) 49 proxy mode 63 proxy relay 44 pwdrecover command 266 r rack-mounting kit 60 rear panel 62 console port 63 lan port 63 leds 64 link spee...
Page 354
354 i ndex system time 131 configuring 132 manual 134 network time protocol 134 t technical specifications 299 technical support 3com knowledgebase web services 302 3com url 301 network suppliers 302 product repair 305 test network 71, 74 third-party tools 52 time configuration 131 toolbar 92 trace ...
Page 355
3c om e nd u ser s oftware l icense a greement important: read before using this product you should carefully read the following terms and conditions before downloading, installing and using this product, the use of which is licensed by 3com corporation ("3com") to its customers for their use only a...
Page 356
Specified below. You may terminate the licenses and this agreement at any time by destroying the software and documentation together with all copies and merged portions in any form. The licenses and this agreement will also terminate immediately if you fail to comply with any term or condition of th...
Page 357
Above, the product may not be used, exported or re-exported (i) into or to a national or resident of any country to which the u.S. Has embargoed; or (ii) to any one on the u.S. Commerce department’s table of denial orders or the u.S. Treasury department’s list of specially designated nationals. Trad...
Page 358
Some countries, states, or provinces do not allow the exclusion or limitation of implied warranties or the limitation of incidental or consequential damages for certain products supplied to consumers, or the limitation of liability for death or personal injury, so the above limitations and exclusion...
Page 359
Recipients to know that what they have is not the original, so that any problems introduced by others will not reflect on the original authors' reputations. Finally, any free program is threatened constantly by software patents. We wish to avoid the danger that redistributors of a free program will ...
Page 360
Code or executable form with such an offer, in accord with subsection b above.) the source code for a work means the preferred form of the work for making modifications to it. For an executable work, complete source code means all the source code for all modules it contains, plus any associated inte...
Page 361
Copyright holders and/or other parties provide the program “as is” without warranty of any kind, either expressed or implied, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. The entire risk as to the quality and performance of the progra...
Page 362
R egulatory n otices fcc s tatement this equipment has been tested and found to comply with the limits for a class a digital device, pursuant to part 15 of the fcc rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a comme...