- DL manuals
- 3Com
- Switch
- Switch 4210 52-Port
- Configuration Manual
3Com Switch 4210 52-Port Configuration Manual
3Com Switch 4210 Family
Configuration Guide
Switch
4210
9-Port
Switch
4210
18-Port
Switch
4210
26-Port
Switch
4210
52-Port
Switch 4210 PWR 9-Port
Switch 4210 PWR 18-Port
Switch 4210 PWR 26-Port
Product Version:
Release 2212
Manual Version:
6W100-20100112
www.3com.com
3Com Corporation
350 Campus Drive, Marlborough,
MA, USA 01752 3064
Summary of Switch 4210 52-Port
Page 1
3com switch 4210 family configuration guide switch 4210 9-port switch 4210 18-port switch 4210 26-port switch 4210 52-port switch 4210 pwr 9-port switch 4210 pwr 18-port switch 4210 pwr 26-port product version: release 2212 manual version: 6w100-20100112 www.3com.Com 3com corporation 350 campus driv...
Page 2
Copyright © 2010, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from 3com corporation. 3com corporation reserves th...
Page 3
About this manual organization 3com switch 4210 family configuration guide is organized as follows: part contents 1 login introduces the ways to log into an ethernet switch. 2 configuration file management introduces the ways to manage configuration files. 3 vlan introduces vlan fundamental and the ...
Page 4
Part contents 27 snmp-rmon introduces the configuration to manage network devices through snmp and rmon. 28 ntp introduces ntp and the related configuration. 29 ssh introduces ssh and the related configuration. 30 file system management introduces basic configuration for file system management. 31 f...
Page 6: Table of Contents
I table of contents 1 logging in to an ethernet switch ············································································································1-1 logging in to an ethernet switch ····································································································...
Page 7
Ii switch configuration························································································································4-2 modem connection establishment ·········································································································4-2 5 cli configu...
Page 8
1-1 1 logging in to an ethernet switch go to these sections for information you are interested in: z logging in to an ethernet switch z introduction to the user interface logging in to an ethernet switch to manage or configure a switch 4210, you can log in to it in one of the following three methods...
Page 9
1-2 table 1-1 description on user interface user interface applicable user port used remarks aux users logging in through the console port console port each switch can accommodate one aux user. Vty telnet users and ssh users ethernet port each switch can accommodate up to five vty users. One user in...
Page 11
2-1 2 logging in through the console port go to these sections for information you are interested in: z introduction z setting up a login environment for login through the console port z console port login configuration z console port login configuration with authentication mode being none z console...
Page 12
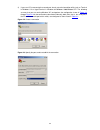
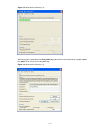
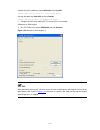
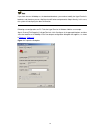
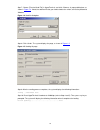
2-2 2) if you use a pc to connect to the console port, launch a terminal emulation utility (such as terminal in windows 3.X or hyperterminal in windows 9x/windows 2000/windows xp. The following assumes that you are running windows xp) and perform the configuration shown in figure 2-2 through figure ...
Page 13
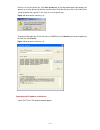
2-3 figure 2-4 set port parameters 3) turn on the switch. You will be prompted to press the enter key if the switch successfully completes post (power-on self test). The prompt appears after you press the enter key. 4) you can then configure the switch or check the information about the switch by ex...
Page 14
2-4 configuration remarks set the maximum number of lines the screen can contain optional by default, the screen can contain up to 24 lines. Set history command buffer size optional by default, the history command buffer can contain up to 10 commands. Set the timeout time of a user interface optiona...
Page 15
2-5 to do… use the command… remarks set the maximum number of lines the screen can contain screen-length screen-length optional by default, the screen can contain up to 24 lines. You can use the screen-length 0 command to disable the function to display information in pages. Set the history command ...
Page 16
2-6 changes made to the authentication mode for console port login takes effect after you quit the command-line interface and then log in again. Console port login configuration with authentication mode being none configuration procedure follow these steps to configure console port login with the au...
Page 17
2-7 network diagram figure 2-5 network diagram for aux user interface configuration (with the authentication mode being none) configuration pc running telnet ethernet ge1/0/1 configuration procedure # enter system view. System-view # enter aux user interface view. [sysname] user-interface aux 0 # sp...
Page 18
2-8 to do… use the command… remarks enter system view system-view — enter aux user interface view user-interface aux 0 — configure to authenticate users using the local password authentication-mode password required by default, users logging in to a switch through the console port are not authentica...
Page 19
2-9 system-view # enter aux user interface view. [sysname] user-interface aux 0 # specify to authenticate users logging in through the console port using the local password. [sysname-ui-aux0] authentication-mode password # set the local password to 123456 (in plain text). [sysname-ui-aux0] set authe...
Page 21
2-11 z set the service type of the local user to terminal and the command level to 2. Z configure to authenticate the users in the scheme mode. Z the baud rate of the console port is 19,200 bps. Z the screen can contain up to 30 lines. Z the history command buffer can store up to 20 commands. Z the ...
Page 22
2-12 [sysname-ui-aux0] history-command max-size 20 # set the timeout time of the aux user interface to 6 minutes. [sysname-ui-aux0] idle-timeout 6 after the above configuration, you need to modify the configuration of the terminal emulation utility running on the pc accordingly in the dialog box sho...
Page 23: Logging In Through Telnet
3-1 3 logging in through telnet go to these sections for information you are interested in: z introduction z telnet configuration with authentication mode being none z telnet configuration with authentication mode being password introduction switch 4210 supports telnet. You can manage and maintain a...
Page 24
3-2 configuration description configure the protocols the user interface supports optional by default, telnet and ssh protocol are supported. Set the commands to be executed automatically after a user log in to the user interface successfully optional by default, no command is executed automatically...
Page 25
3-3 to do… use the command… remarks set the history command buffer size history-command max-size value optional the default history command buffer size is 10, that is, the history command buffer of a user can store up to 10 commands by default. Set the timeout time of the vty user interface idle-tim...
Page 26
3-4 to improve security and prevent attacks to the unused sockets, tcp 23 and tcp 22, ports for telnet and ssh services respectively, will be enabled or disabled after corresponding configurations. Z if the authentication mode is none, tcp 23 will be enabled, and tcp 22 will be disabled. Z if the au...
Page 27
3-5 network diagram figure 3-1 network diagram for telnet configuration (with the authentication mode being none) configuration procedure # enter system view. System-view # enter vty 0 user interface view. [sysname] user-interface vty 0 # configure not to authenticate telnet users logging in to vty ...
Page 28
3-6 when the authentication mode is password, the command level available to users logging in to the user interface is determined by the user privilege level command. Configuration example network requirements assume current user logins through the console port and the current user level is set to t...
Page 29
3-7 telnet configuration with authentication mode being scheme configuration procedure follow these steps to configure telnet with the authentication mode being scheme: to do… use the command… remarks enter system view system-view — enter one or more vty user interface views user-interface vty first...
Page 30
3-8 refer to the aaa part of this manual for information about aaa and radius. Configuration example network requirements assume current user logins through the console port and the user level is set to the administrator level (level 3). Perform the following configurations for users logging in to v...
Page 31
3-9 # set the maximum number of lines the screen can contain to 30. [sysname-ui-vty0] screen-length 30 # set the maximum number of commands the history command buffer can store to 20. [sysname-ui-vty0] history-command max-size 20 # set the timeout time to 6 minutes. [sysname-ui-vty0] idle-timeout 6 ...
Page 32
3-10 figure 3-5 network diagram for telnet connection establishment configuration pc running telnet ethernet workstation server workstation ethernet port ethernet switch 4) launch telnet on your pc, with the ip address of vlan-interface 1 of the switch as the parameter, as shown in figure 3-6 . Figu...
Page 33
3-11 telnetting to another switch from the current switch you can telnet to another switch from the current switch. In this case, the current switch operates as the client, and the other operates as the server. If the interconnected ethernet ports of the two switches are in the same lan segment, mak...
Page 34: Logging In Using A Modem
4-1 4 logging in using a modem go to these sections for information you are interested in: z introduction z configuration on the switch side z modem connection establishment introduction the administrator can log in to the console port of a remote switch using a modem through public switched telepho...
Page 35
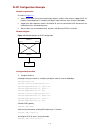
4-2 you can verify your configuration by executing the at&v command. The configuration commands and the output of different modems may differ. Refer to the user manual of the modem when performing the above configuration. Switch configuration after logging in to a switch through its console port by ...
Page 36
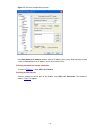
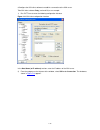
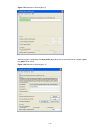
4-3 figure 4-1 establish the connection by using modems console port pstn telephone line modem serial cable telephone number of the romote end: 82882285 modem modem 4) launch a terminal emulation utility on the pc and set the telephone number to call the modem directly connected to the switch, as sh...
Page 37
4-4 figure 4-3 set the telephone number figure 4-4 call the modem 5) if the password authentication mode is specified, enter the password when prompted. If the password is correct, the prompt (such as ) appears. You can then configure or manage the switch. You can also enter the character ? At anyti...
Page 38: Cli Configuration
5-1 5 cli configuration when configuring cli, go to these sections for information you are interested in: z introduction to the cli z command hierarchy z cli views z cli features introduction to the cli a command line interface (cli) is a user interface to interact with a switch. Through the cli on ...
Page 39
5-2 z monitor level (level 1): commands at this level are mainly used to maintain the system and diagnose service faults, and they cannot be saved in configuration file. Such commands include debugging and terminal. Z system level (level 2): commands at this level are mainly used to configure servic...
Page 40
5-3 operation command remarks configure the level of a command in a specific view command-privilege level level view view command required z you are recommended to use the default command level or modify the command level under the guidance of professional staff; otherwise, the change of command lev...
Page 41
5-4 can switch to a higher level temporarily; when the administrators need to leave for a while or ask someone else to manage the device temporarily, they can switch to a lower privilege level before they leave to restrict the operation by others. The high-to-low user level switching is unlimited. H...
Page 42
5-5 when both the super password authentication and the hwtacacs authentication are specified, the device adopts the preferred authentication mode first. If the preferred authentication mode cannot be implemented (for example, the super password is not configured or the hwtacacs authentication serve...
Page 43
5-6 table 5-5 set the hwtacacs authentication scheme for user level switching operation command description enter system view system-view — enter isp domain view domain domain-name — set the hwtacacs authentication scheme for user level switching authenticationsuper hwtacacs-scheme hwtacacs-scheme-n...
Page 44
5-7 [sysname-ui-vty0] quit # set the password used by the current user to switch to level 3. [sysname] super password level 3 simple 123 z a vty 0 user switches its level to level 3 after logging in. # a vty 0 user telnets to the switch, and then uses the set password to switch to user level 3. Supe...
Page 45
5-8 table 5-7 lists the cli views provided by 3com switch 4210, operations that can be performed in different cli views and the commands used to enter specific cli views. Table 5-7 cli views view available operation prompt example enter method quit method user view display operation status and stati...
Page 46
5-9 view available operation prompt example enter method quit method ftp client view configure ftp client parameters [ftp] execute the ftp command in user view. Sftp client view configure sftp client parameters sftp-client> execute the sftp command in system view. Mst region view configure mst regio...
Page 47
5-10 view available operation prompt example enter method quit method remote-pi ng view configure remote-ping parameters [sysname-remot e-ping-a123-a12 3] execute the remote-ping command in system view. Hwtaca cs view configure hwtacacs parameters [sysname-hwtac acs-a123] execute the hwtacacs scheme...
Page 48
5-11 cli features online help when configuring the switch, you can use the online help to get related help information. The cli provides two types of online help: complete and partial. Complete online help 1) enter a question mark (?) in any view on your terminal to display all the commands availabl...
Page 49
5-12 display u? Udp unit user-interface users 3) enter the first several characters of a keyword of a command and then press . If there is a unique keyword beginning with the characters just typed, the unique keyword is displayed in its complete form. If there are multiple keywords beginning with th...
Page 50
5-13 z the windows 9x hyperterminal explains the up and down arrow keys in a different way, and therefore the two keys are invalid when you access history commands in such an environment. However, you can use and instead to achieve the same purpose. Z when you enter the same command multiple times c...
Page 51
5-14 press… to… use the partial online help. That is, when you input an incomplete keyword and press , if the input parameter uniquely identifies a complete keyword, the system substitutes the complete keyword for the input parameter; if more than one keywords match the input parameter, you can disp...
Page 52: Management Interface
6-1 6 logging in through the web-based network management interface go to these sections for information you are interested in: z introduction z establishing an http connection z configuring the login banner z enabling/disabling the web server introduction switch 4210 has a web server built in. It e...
Page 53
6-2 3) establish an http connection between your pc and the switch, as shown in figure 6-1 . Figure 6-1 establish an http connection between your pc and the switch 4) log in to the switch through ie. Launch ie on the web-based network management terminal (your pc) and enter the ip address of the man...
Page 54
6-3 configuration example network requirements z a user logs in to the switch through web. Z the banner page is desired when a user logs into the switch. Network diagram figure 6-3 network diagram for login banner configuration configuration procedure # enter system view. System-view # configure the...
Page 55
6-4 to do… use the command… remarks enter system view system-view — enable the web server ip http shutdown required by default, the web server is enabled. Disable the web server undo ip http shutdown required to improve security and prevent attack to the unused sockets, tcp 80 port (which is for htt...
Page 56: Logging In Through Nms
7-1 7 logging in through nms go to these sections for information you are interested in: z introduction z connection establishment using nms introduction you can also log in to a switch through a network management station (nms), and then configure and manage the switch through the agent software on...
Page 57: User Control
8-1 8 user control go to these sections for information you are interested in: z introduction z controlling telnet users z controlling network management users by source ip addresses z controlling web users by source ip address refer to the acl part for information about acl. Introduction you can co...
Page 58
8-2 z if no acl is configured on the vty user interface, users are not controlled when establishing a telnet connection using this user interface. Z if an acl is configured on the vty user interface, there will be two possibilities: if the packets for establishing a telnet connection match the acl r...
Page 60
8-4 z defining an acl z applying the acl to control users accessing the switch through snmp to control whether an nms can manage the switch, you can use this function. Prerequisites the controlling policy against network management users is determined, including the source ip addresses to be control...
Page 61
8-5 network diagram figure 8-2 network diagram for controlling snmp users using acls switch 10.110.100.46 host a ip network host b 10.110.100.52 configuration procedure # define a basic acl. System-view [sysname] acl number 2000 [sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0 [sysname-...
Page 63
8-7 [sysname-acl-basic-2030] quit # apply acl 2030 to only permit the web users sourced from the ip address of 10.110.100.52 to access the switch. [sysname] ip http acl 2030
Page 64: Table of Contents
I table of contents 1 configuration file management···············································································································1-1 introduction to configuration file ···································································································...
Page 65
1-1 1 configuration file management introduction to configuration file a configuration file records and stores user configurations performed to a switch. It also enables users to check switch configurations easily. Types of configuration the configuration of a device falls into two types: z saved co...
Page 66
1-2 z when setting the configuration file for next startup, you can specify to use the main or backup configuration file. Startup with the configuration file when booting, the system chooses the configuration files following the rules below: 1) if the main configuration file exists, the device initi...
Page 67
1-3 switch 4210 do not support the safe mode. When you are saving a configuration file using the save safely command, if the device reboots or the power fails during the saving process, the configuration file will be lost. Three attributes of the configuration file z main attribute. When you use the...
Page 68
1-4 z while the reset saved-configuration [ main ] command erases the configuration file with main attribute, it only erases the main attribute of a configuration file having both main and backup attribute. Z while the reset saved-configuration backup command erases the configuration file with backu...
Page 69
1-5 displaying device configuration after the above configuration, you can execute the display command in any view to display the current and initial configurations of the device, so as to verify your configuration. Table 1-5 display device configuration operation command description display the ini...
Page 70: Table of Contents
I table of contents 1 vlan overview ··········································································································································1-1 vlan overview·············································································································...
Page 71: Vlan Overview
1-1 1 vlan overview this chapter covers these topics: z vlan overview z port-based vlan vlan overview introduction to vlan the traditional ethernet is a broadcast network, where all hosts are in the same broadcast domain and connected with each other through hubs or switches. Hubs and switches, whic...
Page 72
1-2 figure 1-1 a vlan implementation advantages of vlans compared with traditional ethernet technology, vlan technology delivers the following benefits: z confining broadcast traffic within individual vlans. This saves bandwidth and improves network performance. Z improving lan security. By assignin...
Page 73
1-3 figure 1-3 format of vlan tag a vlan tag comprises four fields: tag protocol identifier (tpid), priority, canonical format indicator (cfi), and vlan id. Z the 16-bit tpid field with a value of 0x8100 indicates that the frame is vlan tagged. On the switch 4210, the default tpid is 0x8100. Z the 3...
Page 74
1-4 z independent vlan learning (ivl), where the switch maintains an independent mac address forwarding table for each vlan. The source mac address of a packet received in a vlan on a port is recorded to the mac address forwarding table of this vlan only, and packets received in a vlan are forwarded...
Page 75
1-5 port-based vlans are easy to implement and manage and applicable to hosts with relatively fixed positions. Link types of ethernet ports you can configure the link type of a port as access, trunk, or hybrid. The three link types use different vlan tag handling methods. When configuring the link t...
Page 76
1-6 table 1-1 packet processing of an access port processing of an incoming packet for an untagged packet for a tagged packet processing of an outgoing packet receive the packet and tag the packet with the default vlan tag. Z if the vlan id is just the default vlan id, receive the packet. Z if the v...
Page 77: Vlan Configuration
2-1 2 vlan configuration when configuring a vlan, go to these sections for information you are interested in: z vlan configuration z configuring a port-based vlan vlan configuration vlan configuration task list complete the following tasks to configure vlan: task remarks basic vlan configuration req...
Page 78
2-2 z vlan 1 is the system default vlan, which needs not to be created and cannot be removed, either. Z the vlan you created in the way described above is a static vlan. On the switch, there are dynamic vlans which are registered through gvrp. For details, refer to “gvrp” part of this manual. Z when...
Page 79
2-3 z the operation of enabling/disabling a vlan’s vlan interface does not influence the physical status of the ethernet ports belonging to this vlan. Z an switch s4210 can be configured with a single vlan interface only, and the vlan must be the management vlan. For details about the management vla...
Page 80
2-4 to do… use the command… remarks add the current access port to a specified vlan port access vlan vlan-id optional by default, all access ports belong to vlan 1. To add an access port to a vlan, make sure the vlan already exists. Configuring a hybrid-port-based vlan a hybrid port may belong to mu...
Page 81
2-5 to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the port link type as trunk port link-type trunk required allow the specified vlans to pass through the current trunk port port trunk permit vlan { vlan-...
Page 82
2-6 network diagram figure 2-1 network diagram for vlan configuration configuration procedure z configure switch a. # create vlan 101, specify its descriptive string as “dmz”, and add ethernet1/0/1 to vlan 101. System-view [switcha] vlan 101 [switcha-vlan101] description dmz [switcha-vlan101] port e...
Page 83
2-7 [switcha-ethernet1/0/3] port trunk permit vlan 101 [switcha-ethernet1/0/3] port trunk permit vlan 201 # configure ethernet1/0/10 of switch b. [switchb] interface ethernet 1/0/10 [switchb-ethernet1/0/10] port link-type trunk [switchb-ethernet1/0/10] port trunk permit vlan 101 [switchb-ethernet1/0...
Page 84: Table of Contents
I table of contents 1 management vlan configuration ···········································································································1-1 introduction to management vlan·········································································································1...
Page 85
1-1 1 management vlan configuration introduction to management vlan management vlan to manage an ethernet switch remotely through telnet or the built-in web server, the switch need to be assigned an ip address, and make sure that a route exists between the user and the switch. As for an 3com series ...
Page 86
1-2 z if no default route exists and the destination address of the packet is not in the routing table, the packet is discarded, and an icmp destination unreachable message is returned to the source. The default route can be configured through a static route and exists in the routing table as a rout...
Page 87
1-3 configuration example network requirements for a user to manage switch a remotely through telnet, these requirements are to be met: switch a has an ip address, and the remote telnet user is reachable. You need to configure the switch as follows: z assigning an ip address to the management vlan i...
Page 88
1-4 [switcha-vlan-interface10] ip address 1.1.1.1 255.255.255.0 [switcha-vlan-interface10] quit # configure the default route. [switcha] ip route-static 0.0.0.0 0.0.0.0 1.1.1.2 displaying and maintaining management vlan configuration table 1-2 displaying and maintaining management vlan configuration...
Page 89: Table of Contents
I table of contents 1 ip addressing configuration····················································································································1-1 ip addressing overview·············································································································...
Page 90: Ip Addressing Configuration
1-1 1 ip addressing configuration ip addressing overview ip address classes ip addressing uses a 32-bit address to identify each host on a network. An example is 01010000100000001000000010000000 in binary. To make ip addresses in 32-bit form easier to read, they are written in dotted decimal notatio...
Page 91
1-2 class address range description d 224.0.0.0 to 239.255.255.255 multicast address. E 240.0.0.0 to 255.255.255.255 reserved for future use except for the broadcast address 255.255.255.255. Special case ip addresses the following ip addresses are for special use, and they cannot be used as host ip ...
Page 92
1-3 bits for the host id and thus have only 126 (2 7 – 2) hosts in each subnet. The maximum number of hosts is thus 64,512 (512 × 126), 1022 less after the network is subnetted. Class a, b, and c networks, before being subnetted, use these default masks (also called natural masks): 255.0.0.0, 255.25...
Page 93
1-4 table 1-3 display ip addressing configuration operation command remarks display information about a specified or all layer 3 interfaces display ip interface [ interface-type interface-number ] display brief configuration information about a specified or all layer 3 interfaces display ip interfac...
Page 94: Ip Performance Configuration
2-1 2 ip performance configuration ip performance overview introduction to ip performance configuration in some network environments, you need to adjust the ip parameters to achieve best network performance. The ip performance configuration supported by switch 4210 family includes: z configuring tcp...
Page 95
2-2 table 2-2 configure tcp attributes operation command remarks enter system view system-view — configure tcp synwait timer’s timeout value tcp timer syn-timeout time-value optional by default, the timeout value is 75 seconds. Configure tcp finwait timer’s timeout value tcp timer fin-timeout time-v...
Page 96
2-3 use the reset command in user view to clear the ip, tcp, and udp traffic statistics. Table 2-4 display and maintain ip performance operation command remarks display tcp connection status display tcp status display tcp connection statistics display tcp statistics display udp traffic statistics di...
Page 97: Table of Contents
I table of contents 1 dns configuration·····································································································································1-1 dns overview················································································································...
Page 98: Dns Configuration
1-1 1 dns configuration this chapter covers only ipv4 dns configuration. For details about ipv6 dns, refer to ipv6 management operation. Dns overview domain name system (dns) is a mechanism used for tcp/ip applications to provide domain name-to-ip address translation. With dns, you can use memorizab...
Page 99
1-2 figure 1-1 dynamic domain name resolution figure 1-1 shows the relationship between user program, dns client, and dns server. The resolver and cache comprise the dns client. The user program and dns client run on the same device, while the dns server and the dns client usually run on different d...
Page 100
1-3 z the ip address you assign to a host name last time will overwrite the previous one if there is any. Z you may create up to 50 static mappings between domain names and ip addresses. Configuring dynamic domain name resolution table 1-2 configure dynamic domain name resolution operation command r...
Page 101
1-4 operation command… remarks clear the information in the dynamic domain name cache reset dns dynamic-host available in user view dns configuration example static domain name resolution configuration example network requirements the switch uses static domain name resolution to access host 10.1.1.2...
Page 102
1-5 dynamic domain name resolution configuration example network requirements as shown in figure 1-3 , the switch serving as a dns client uses dynamic domain name resolution to access the host at 3.1.1.1/16 through its domain name host. The dns server has the ip address 2.1.1.2/16. The dns suffix is...
Page 103
1-6 reply from 3.1.1.1: bytes=56 sequence=2 ttl=125 time=4 ms reply from 3.1.1.1: bytes=56 sequence=3 ttl=125 time=4 ms reply from 3.1.1.1: bytes=56 sequence=4 ttl=125 time=4 ms reply from 3.1.1.1: bytes=56 sequence=5 ttl=125 time=5 ms --- host.Com ping statistics --- 5 packet(s) transmitted 5 packe...
Page 104: Table of Contents
I table of contents 1 voice vlan configuration························································································································1-1 voice vlan overview···············································································································...
Page 105: Voice Vlan Configuration
1-1 1 voice vlan configuration when configuring voice vlan, go to these sections for information you are interested in: z voice vlan overview z voice vlan configuration z displaying and maintaining voice vlan z voice vlan configuration example voice vlan overview voice vlans are vlans configured spe...
Page 106
1-2 figure 1-1 network diagram for ip phones as shown in figure 1-1 , the ip phone needs to work in conjunction with the dhcp server and the ncp to establish a path for voice data transmission. An ip phone goes through the following three phases to become capable of transmitting voice data. 2) after...
Page 107
1-3 tag to communicate with the voice gateway. In this case, the port connecting to the ip phone must be configured to allow the packets tagged with the voice vlan tag to pass. Z an untagged packet carries no vlan tag. Z a tagged packet carries the tag of a vlan. To set an ip address and a voice vla...
Page 108
1-4 z set the dscp value to 46. Configuring voice vlan assignment mode of a port a port can work in automatic voice vlan assignment mode or manual voice vlan assignment mode. You can configure the voice vlan assignment mode for a port according to data traffic passing through the port. Processing mo...
Page 109
1-5 table 1-2 matching relationship between port types and voice devices capable of acquiring ip address and voice vlan automatically voice vlan assignment mode voice traffic type port type supported or not access not supported trunk supported make sure the default vlan of the port exists and is not...
Page 110
1-6 table 1-3 matching relationship between port types and voice devices acquiring voice vlan through manual configuration voice vlan assignment mode port type supported or not access not supported trunk supported make sure the default vlan of the port exists and is not a voice vlan, and the access ...
Page 111
1-7 table 1-4 how a packet is handled when the voice vlan is operating in different modes voice vlan mode packet type processing method untagged packet packet carrying the voice vlan tag if the source mac address of the packet matches the oui list, the packet is transmitted in the voice vlan. Otherw...
Page 112
1-8 to do... Use the command... Remarks and the voice vlan qos trust command can overwrite each other, whichever is configured last. Configure the qos priority settings for voice traffic on an interface before enabling voice vlan on the interface. If the configuration order is reversed, your priorit...
Page 113
1-9 z a port working in automatic voice vlan assignment mode cannot be assigned to the voice vlan manually. Therefore, if a vlan is configured as the voice vlan and a protocol-based vlan at the same time, the protocol-based vlan function cannot be bound with the port. For information about protocol-...
Page 114
1-10 to do… use the command… remarks enter port view interface interface-type interface-number required enable voice vlan on a port voice vlan enable required by default, voice vlan is disabled on a port. Enable the voice vlan legacy function on the port voice vlan legacy optional by default, voice ...
Page 115
1-11 z the voice vlan function can be enabled for only one vlan at one time. Z if the link aggregation control protocol (lacp) is enabled on a port, voice vlan feature cannot be enabled on it. Z voice vlan function can be enabled only for the static vlan. A dynamic vlan cannot be configured as a voi...
Page 116
1-12 voice vlan configuration example voice vlan configuration example (automatic voice vlan assignment mode) network requirements create a voice vlan and configure it to operate in automatic voice vlan assignment mode to enable the port to which an ip phone is connected to join or exit the voice vl...
Page 117
1-13 [devicea-ethernet1/0/1] voice vlan mode auto # configure ethernet 1/0/1 as a hybrid port. [devicea-ethernet1/0/1] port link-type hybrid # configure vlan 6 as the default vlan of ethernet 1/0/1, and configure ethernet 1/0/1 to permit packets with the tag of vlan 6. [devicea-ethernet1/0/1] port h...
Page 118
1-14 [devicea] vlan 2 [devicea-vlan2] quit [devicea] voice vlan 2 enable # configure ethernet 1/0/1 to operate in manual voice vlan assignment mode. [devicea] interface ethernet 1/0/1 [devicea-ethernet1/0/1] undo voice vlan mode auto # configure ethernet 1/0/1 as a hybrid port. [devicea-ethernet1/0/...
Page 119: Table of Contents
I table of contents 1 gvrp configuration ··································································································································1-1 introduction to gvrp ········································································································...
Page 120: Gvrp Configuration
1-1 1 gvrp configuration when configuring gvrp, go to these sections for information you are interested in: z introduction to gvrp z gvrp configuration z displaying and maintaining gvrp z gvrp configuration example introduction to gvrp garp vlan registration protocol (gvrp) is an implementation of g...
Page 121
1-2 2) garp timers timers determine the intervals of sending different types of garp messages. Garp defines four timers to control the period of sending garp messages. Z hold: when a garp entity receives a piece of registration information, it does not send out a join message immediately. Instead, t...
Page 122
1-3 figure 1-1 format of garp packets the following table describes the fields of a garp packet. Table 1-1 description of garp packet fields field description value protocol id protocol id 1 message each message consists of two parts: attribute type and attribute list. — attribute type defined by th...
Page 123
1-4 gvrp as an implementation of garp, garp vlan registration protocol (gvrp) maintains dynamic vlan registration information and propagates the information to the other switches through garp. With gvrp enabled on a device, the vlan registration information received by the device from other devices ...
Page 124
1-5 to do ... Use the command ... Remarks enter system view system-view — enable gvrp globally gvrp required by default, gvrp is disabled globally. Enter ethernet port view interface interface-type interface-number — enable gvrp on the port gvrp required by default, gvrp is disabled on the port. S z...
Page 125
1-6 table 1-2 relations between the timers timer lower threshold upper threshold hold 10 centiseconds this upper threshold is less than or equal to one-half of the timeout time of the join timer. You can change the threshold by changing the timeout time of the join timer. Join this lower threshold i...
Page 126
1-7 displaying and maintaining gvrp to do … use the command … remarks display garp statistics display garp statistics [ interface interface-list ] display the settings of the garp timers display garp timer [ interface interface-list ] display gvrp statistics display gvrp statistics [interface interf...
Page 127
1-8 [switcha-ethernet1/0/1] port link-type trunk [switcha-ethernet1/0/1] port trunk permit vlan all # enable gvrp on ethernet1/0/1. [switcha-ethernet1/0/1] gvrp [switcha-ethernet1/0/1] quit # configure ethernet1/0/2 to be a trunk port and to permit the packets of all the vlans. [switcha] interface e...
Page 128
1-9 the following dynamic vlans exist: 5, 7, 8, # display the vlan information dynamically registered on switch b. [switchb] display vlan dynamic total 3 dynamic vlan exist(s). The following dynamic vlans exist: 5, 7, 8, # display the vlan information dynamically registered on switch e. [switche] di...
Page 129
1-10 5, 8, # display the vlan information dynamically registered on switch e. [switche] display vlan dynamic no dynamic vlans exist!.
Page 130: Table of Contents
I table of contents 1 port basic configuration ··························································································································1-1 ethernet port configuration ···································································································...
Page 131: Port Basic Configuration
1-1 1 port basic configuration ethernet port configuration combo port configuration introduction to combo port a combo port can operate as either an optical port or an electrical port. Inside the device there is only one forwarding interface. For a combo port, the electrical port and the correspondi...
Page 132
1-2 in case of a combo port, only one interface (either the optical port or the electrical port) is active at a time. That is, once the optical port is active, the electrical port will be inactive automatically, and vice versa. Initially configuring a port table 1-2 initially configure a port operat...
Page 133
1-3 z if you expect that 10 mbps and 1000 mbps are the available auto-negotiation speeds of the port, you just need to configure speed auto 10 1000. Follow these steps to configure auto-negotiation speeds for a port: to do... Use the command... Remarks enter system view system-view — enter ethernet ...
Page 134
1-4 operation command remarks limit unknown multicast and unknown unicast traffic received on the current port multicast-suppression bps max-bps optional the switch will suppress the unknown multicast and unknown unicast traffic simultaneously after the configuration. By default, the switch does not...
Page 135
1-5 z if you specify a source aggregation group id, the system will use the port with the smallest port number in the aggregation group as the source. Z if you specify a destination aggregation group id, the configuration of the source port will be copied to all ports in the aggregation group and al...
Page 136
1-6 configuring loopback detection for ethernet port(s) table 1-6 configure loopback detection for ethernet port(s) operation command remarks enter system view system-view — enable loopback detection globally loopback-detection enable optional by default, the global loopback detection function is en...
Page 137
1-7 z to enable loopback detection on a specific port, you must use the loopback-detection enable command in both system view and the specific port view. Z after you use the undo loopback-detection enable command in system view, loopback detection will be disabled on all ports. Enabling loopback tes...
Page 138
1-8 table 1-8 enable the system to test connected cables operation command remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — enable the system to test connected cables virtual-cable-test required z currently, the device is only capable of te...
Page 139
1-9 after you allow a port to output the up/down log information, if the physical link status of the port does not change, the switch does not send log information to the log server but monitors the port in real time. Disable up/down log output on a port table 1-10 disable up/down log output on a po...
Page 140
1-10 z when a type of traffic on the port falls back to the specified lower threshold, the system cancels the blocking of this type of traffic on the port or brings up the port to restore traffic forwarding for the port, and outputs log/trap information according to your configuration. Follow these ...
Page 141
1-11 the port state change delay takes effect when the port goes down but not when the port goes up. Table 1-11 set the port state change delay operation command remarks enter system view system-view — enter ethernet interface view interface interface-type interface-number — set the port state chang...
Page 143
1-13 z only the configuration for switch a is listed below. The configuration for switch b is similar to that of switch a. Z this example supposes that vlan 2, vlan 6 through vlan 50 and vlan 100 have been created. # enter ethernet 1/0/1 port view. System-view [sysname] interface ethernet1/0/1 # set...
Page 144: Table of Contents
I table of contents 1 link aggregation configuration ··············································································································1-1 overview ····························································································································...
Page 145
1-1 1 link aggregation configuration overview introduction to link aggregation link aggregation can aggregate multiple ethernet ports together to form a logical aggregation group. To upper layer entities, all the physical links in an aggregation group are a single logical link. Link aggregation is d...
Page 146
1-2 z switch 4210 family that support extended lacp functions can be used as intermediate devices in lacp mad implementation. Z for details about irf, member devices, intermediate devices, and the lacp mad mechanism, see the operation manuals of irf-supported devices. Operational key operation key i...
Page 147
1-3 lacp is disabled on the member ports of manual aggregation groups, and you cannot enable lacp on ports in a manual aggregation group. Port status in manual aggregation group a port in a manual aggregation group can be in one of the two states: selected or unselected. In a manual aggregation grou...
Page 148
1-4 z the ports connected to a peer device different from the one the master port is connected to or those connected to the same peer device as the master port but to a peer port that is not in the same aggregation group as the peer port of the master port are unselected ports. Z the system sets the...
Page 149
1-5 z when the rate or duplex mode of a port in the aggregation group changes, packet loss may occur on this port; z when the rate of a port decreases, if the port belongs to a manual or static lacp aggregation group, the port will be switched to the unselected state; if the port belongs to a dynami...
Page 150
1-6 link aggregation configuration z the commands of link aggregation cannot be configured with the commands of port loopback detection feature at the same time. Z the ports where the mac-address max-mac-count command is configured cannot be added to an aggregation group. Contrarily, the mac-address...
Page 151
1-7 z if the aggregation group you are creating already exists and contains ports, the possible type changes may be: changing from dynamic or static to manual, and changing from dynamic to static; and no other kinds of type change can occur. Z when you change a dynamic/static group to a manual group...
Page 152
1-8 configuring a dynamic lacp aggregation group a dynamic lacp aggregation group is automatically created by the system based on lacp-enabled ports. The adding and removing of ports to/from a dynamic aggregation group are automatically accomplished by lacp. You need to enable lacp on the ports whic...
Page 153
1-9 operation command remarks configure a description for an aggregation group link-aggregation group agg-id description agg-name optional by default, no description is configured for an aggregation group. If you have saved the current configuration with the save command, after system reboot, the co...
Page 154
1-10 network diagram figure 1-1 network diagram for link aggregation configuration configuration procedure the following only lists the configuration on switch a; you must perform the similar configuration on switch b to implement link aggregation. 1) adopting manual aggregation mode # create manual...
Page 155
1-11 [sysname-ethernet1/0/2] quit [sysname] interface ethernet1/0/3 [sysname-ethernet1/0/3] port link-aggregation group 1 3) adopting dynamic lacp aggregation mode # enable lacp on ethernet1/0/1 through ethernet1/0/3. System-view [sysname] interface ethernet1/0/1 [sysname-ethernet1/0/1] lacp enable ...
Page 156: Table of Contents
I table of contents 1 port isolation configuration ·····················································································································1-1 port isolation overview ········································································································...
Page 157: Port Isolation Configuration
1-1 1 port isolation configuration port isolation overview through the port isolation feature, you can add the ports to be controlled into an isolation group to isolate the layer 2 and layer 3 data between each port in the isolation group. Thus, you can construct your network in a more flexible way ...
Page 158
1-2 z when a member port of an aggregation group joins/leaves an isolation group, the other ports in the same aggregation group on the local device will join/leave the isolation group at the same time. Z for ports that belong to an aggregation group and an isolation group simultaneously, removing a ...
Page 159
1-3 network diagram figure 1-1 network diagram for port isolation configuration configuration procedure # add ethernet1/0/2, ethernet1/0/3, and ethernet1/0/4 to the isolation group. System-view system view: return to user view with ctrl+z. [sysname] interface ethernet1/0/2 [sysname-ethernet1/0/2] po...
Page 160: Table of Contents
I table of contents 1 port security configuration······················································································································1-1 port security overview···········································································································...
Page 161: Port Security Configuration
1-1 1 port security configuration when configuring port security, go to these sections for information you are interested in: z port security overview z port security configuration task list z displaying and maintaining port security configuration z port security configuration example port security ...
Page 162
1-2 table 1-1 description of port security modes security mode description feature norestriction in this mode, access to the port is not restricted. In this mode, neither the ntk nor the intrusion protection feature is triggered. Autolearn in this mode, the port automatically learns mac addresses an...
Page 163
1-3 security mode description feature userloginsecure mac-based 802.1x authentication is performed on the access user. The port is enabled only after the authentication succeeds. When the port is enabled, only the packets of the successfully authenticated user can pass through the port. In this mode...
Page 164
1-4 security mode description feature macaddresselseus erloginsecureext this mode is similar to the macaddresselseuserloginsecure mode, except that there can be more than one 802.1x-authenticated user on the port. Macaddressandus erloginsecure in this mode, a port firstly performs mac authentication...
Page 165
1-5 enabling port security configuration prerequisites before enabling port security, you need to disable 802.1x and mac authentication globally. Enabling port security follow these steps to enable port security: to do... Use the command... Remarks enter system view system-view — enable port securit...
Page 166
1-6 to do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — set the maximum number of mac addresses allowed on the port port-security max-mac-count count-value required not limited by default setting the port security mode follow these steps to set th...
Page 167
1-7 if the port-security port-mode modecommand has been executed on a port, none of the following can be configured on the same port: z maximum number of mac addresses that the port can learn z reflector port for port mirroring z link aggregation configuring port security features configuring the nt...
Page 168
1-8 if you configure the ntk feature and execute the port-security intrusion-mode blockmac command on the same port, the switch will be unable to disable the packets whose destination mac address is illegal from being sent out that port; that is, the ntk feature configured will not take effect on th...
Page 169
1-9 to do… use the command… remarks enter system view system-view — set the interval at which the switch triggers mac address authentication after a port is added to the guest vlan port-security timer guest-vlan-reauth interval optional enter ethernet port view interface interface-type interface-num...
Page 170
1-10 to do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — ignore the authorization information from the radius server port-security authorization ignore required by default, a port uses the authorization information from the radius server. Configur...
Page 171
1-11 to do... Use the command... Remarks interface interface-type interface-number in ethernet port view mac-address security mac-address vlan vlan-id security mac address is configured. Configuring an aging time for learned security mac address entries by default, learned security mac address entri...
Page 172
1-12 to do... Use the command... Remarks display information about security mac address configuration display mac-address security [ interface interface-type interface-number ] [ vlan vlan-id ] [ count ] port security configuration example port security configuration example network requirements imp...
Page 173
1-13 [switch-ethernet1/0/1] quit [switch] port-security timer disableport 30 guest vlan configuration example network requirements as shown in figure 1-2 , ethernet 1/0/2 connects to a pc and a printer, which are not used at the same time. Configure the port to operate in macaddressoruserloginsecure...
Page 174
1-14 [switch] radius scheme 2000 [switch-radius-2000] primary authentication 10.11.1.1 1812 [switch-radius-2000] primary accounting 10.11.1.1 1813 [switch-radius-2000] key authentication abc [switch-radius-2000] key accounting abc [switch-radius-2000] user-name-format without-domain [switch-radius-2...
Page 175: Port Binding Configuration
2-1 2 port binding configuration when configuring port binding, go to these sections for information you are interested in: z port binding overview z displaying and maintaining port binding configuration z port binding configuration example port binding overview introduction binding is a simple secu...
Page 177
2-3 configuration procedure configure switch a as follows: # enter system view. System-view # enter ethernet 1/0/1 port view. [switcha] interface ethernet 1/0/1 # bind the mac address and the ip address of host a to ethernet 1/0/1. [switcha-ethernet1/0/1] am user-bind mac-addr 0001-0002-0003 ip-addr...
Page 178: Table of Contents
I table of contents 1 dldp configuration ··································································································································1-1 overview ····················································································································...
Page 179: Dldp Configuration
1-1 1 dldp configuration when configuring dldp, go to these sections for information you are interested in: z overview z dldp fundamentals z dldp configuration z dldp configuration example overview device link detection protocol (dldp) is a kind of technology for dealing with unidirectional links th...
Page 180
1-2 figure 1-2 fiber broken or not connected switch a ge1/1/1 ge1/1/2 switch b ge1/1/1 ge1/1/2 pc device link detection protocol (dldp) can detect the link status of an optical fiber cable or copper twisted pair (such as super category 5 twisted pair). If dldp finds a unidirectional link, it disable...
Page 181
1-3 dldp packet type function rsy-advertisement packets (referred to as rsy packets hereafter) advertisement packet with the rsy flag set to 1. Rsy advertisement packets are sent to request synchronizing the neighbor information when neighbor information is not locally available or a neighbor inform...
Page 182
1-4 dldp status a link can be in one of these dldp states: initial, inactive, active, advertisement, probe, disable, and delaydown. Table 1-2 dldp status status description initial initial status before dldp is enabled. Inactive dldp is enabled but the corresponding link is down active dldp is enabl...
Page 183
1-5 timer description entry aging timer when a new neighbor joins, a neighbor entry is created and the corresponding entry aging timer is enabled when an advertisement packet is received from a neighbor, the neighbor entry is updated and the corresponding entry aging timer is updated in the normal m...
Page 184
1-6 table 1-4 dldp operating mode and neighbor entry aging dldp operating mode detecting a neighbor after the corresponding neighbor entry ages out removing the neighbor entry immediately after the entry timer expires triggering the enhanced timer after an entry timer expires normal mode no yes no e...
Page 185
1-7 table 1-5 dldp state and dldp packet type dldp state type of the dldp packets sent active advertisement packets, with the rsy flag set or not set. Advertisement advertisement packets probe probe packets 2) a dldp packet received is processed as follows: z in authentication mode, the dldp packet ...
Page 186
1-8 table 1-7 processing procedure when no echo packet is received from the neighbor no echo packet received from the neighbor processing procedure in normal mode, no echo packet is received when the echo waiting timer expires. In enhanced mode, no echo packet is received when the enhanced timer exp...
Page 187
1-9 dldp configuration performing basic dldp configuration follow these steps to perform basic dldp configuration: to do … use the command … remarks enter system view system-view — enable dldp on all optical ports of the switch dldp enable enter ethernet port view interface interface-type interface-...
Page 188
1-10 z when connecting two dldp-enabled devices, make sure the software running on them is of the same version. Otherwise, dldp may operate improperly. Z when you use the dldp enable/dldp disable command in system view to enable/disable dldp on all optical ports of the switch, the configuration take...
Page 189
1-11 dldp configuration example network requirements as shown in figure 1-4 , z switch a and switch b are connected through two pairs of fibers. Both of them support dldp. All the ports involved operate in mandatory full duplex mode, with their rates all being 1,000 mbps. Z suppose the fibers betwee...
Page 190
1-12 # set the dldp handling mode for unidirectional links to auto. [switcha] dldp unidirectional-shutdown auto # display the dldp state [switcha] display dldp 1 when two switches are connected through fibers in a crossed way, two or three ports may be in the disable state, and the rest in the inact...
Page 191: Table of Contents
I table of contents 1 mac address table management············································································································1-1 overview ·································································································································...
Page 192: Mac Address Table Management
1-1 1 mac address table management when configuring mac address table management, go to these sections for information you are interested in: z overview z mac address table management z displaying mac address table information z configuration example this chapter describes the management of static, ...
Page 193
1-2 generally, the majority of mac address entries are created and maintained through mac address learning. The following describes the mac address learning process of a switch: 1) as shown in figure 1-1 , user a and user b are both in vlan 1. When user a communicates with user b, the packet from us...
Page 194
1-3 3) because the switch broadcasts the packet, both user b and user c can receive the packet. However, user c is not the destination device of the packet, and therefore does not process the packet. Normally, user b will respond to user a, as shown in figure 1-4 . When the response packet from user...
Page 195
1-4 managing mac address table aging of mac address table to fully utilize a mac address table, which has a limited capacity, the switch uses an aging mechanism for updating the table. That is, the switch starts an aging timer for an entry when dynamically creating the entry. The switch removes the ...
Page 196
1-5 mac address table management mac address table management configuration task list complete the following tasks to configure mac address table management: task remarks configuring a mac address entry required setting the mac address aging timer optional setting the maximum number of mac addresses...
Page 198
1-7 setting the maximum number of mac addresses a port can learn the mac address learning mechanism enables an ethernet switch to acquire the mac addresses of the network devices on the segment connected to the ports of the switch. By searching the mac address table, the switch directly forwards the...
Page 199
1-8 configuration example adding a static mac address entry manually network requirements the server connects to the switch through ethernet 1/0/2. To prevent the switch from broadcasting packets destined for the server, it is required to add the mac address of the server to the mac address table of...
Page 200: Table of Contents
I table of contents 1 mstp configuration ··································································································································1-1 overview ····················································································································...
Page 201
Ii introduction····································································································································1-40 configuring digest snooping·········································································································1-40 configuring...
Page 202: Mstp Configuration
1-1 1 mstp configuration go to these sections for information you are interested in: z overview z mstp configuration task list z configuring root bridge z configuring leaf nodes z performing mcheck operation z configuring guard functions z configuring digest snooping z configuring rapid transition z...
Page 203
1-2 stp identifies the network topology by transmitting bpdus between stp compliant network devices, typically switches and routers. Bpdus contain sufficient information for the network devices to complete the spanning tree calculation. In stp, bpdus come in two types: z configuration bpdus, used to...
Page 204
1-3 figure 1-1 a schematic diagram of designated bridges and designated ports all the ports on the root bridge are designated ports. 4) bridge id a bridge id consists of eight bytes, where the first two bytes represent the bridge priority of the device, and the latter six bytes represent the mac add...
Page 205
1-4 6) port id a port id used on the 3com switch 4210 consists of two bytes, that is, 16 bits, where the first six bits represent the port priority, and the latter ten bits represent the port number. The default priority of all ethernet ports on the 3com switch 4210 is 128. You can use commands to c...
Page 206
1-5 table 1-2 selection of the optimum configuration bpdu step description 1 upon receiving a configuration bpdu on a port, the device performs the following processing: z if the received configuration bpdu has a lower priority than that of the configuration bpdu generated by the port, the device wi...
Page 207
1-6 step description 3 the device compares the calculated configuration bpdu with the configuration bpdu on the port whose role is to be determined, and acts as follows based on the comparison result: z if the calculated configuration bpdu is superior, this port will serve as the designated port, an...
Page 208
1-7 device port name bpdu of port bp1 {1, 0, 1, bp1} device b bp2 {1, 0, 1, bp2} cp1 {2, 0, 2, cp1} device c cp2 {2, 0, 2, cp2} z comparison process and result on each device the following table shows the comparison process and result on each device. Table 1-5 comparison process and result on each d...
Page 209
1-8 device comparison process bpdu of port after comparison z port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received configuration bpdu is superior to the configuration bpdu of the local port {2, 0, 2, cp1}, and updates the configuration bpdu of cp1. Z ...
Page 210
1-9 figure 1-3 the final calculated spanning tree to facilitate description, the spanning tree calculation process in this example is simplified, while the actual process is more complicated. 3) the bpdu forwarding mechanism in stp z upon network initiation, every switch regards itself as the root b...
Page 211
1-10 for this reason, the protocol uses a state transition mechanism. Namely, a newly elected root port and the designated ports must go through a period, which is twice the forward delay time, before they transit to the forwarding state. The period allows the new configuration bpdus to be propagate...
Page 212
1-11 z mstp supports mapping vlans to multiple spanning tree (mst) instances (mstis) by means of a vlan-to-instance mapping table. Mstp introduces instances (which integrates multiple vlans into a set) and can bind multiple vlans to an instance, thus saving communication overhead and improving resou...
Page 213
1-12 3) msti a multiple spanning tree instance (msti) refers to a spanning tree in an mst region. Multiple spanning trees can be established in one mst region. These spanning trees are independent of each other. For example, each region in figure 1-4 contains multiple spanning trees known as mstis. ...
Page 214
1-13 z a region boundary port is located on the boundary of an mst region and is used to connect one mst region to another mst region, an stp-enabled region or an rstp-enabled region. Z an alternate port is a secondary port of a root port or master port and is used for rapid transition. With the roo...
Page 215
1-14 z forwarding state. Ports in this state can forward user packets and receive/send bpdus. Z learning state. Ports in this state can receive/send bpdus but do not forward user packets. Z discarding state. Ports in this state can only receive bpdus. Port roles and port states are not mutually depe...
Page 216
1-15 in addition to the basic mstp functions, the 3com switches 4210 also provide the following functions for users to manage their switches. Z root bridge hold z root bridge backup z root guard z bpdu guard z loop guard z tc-bpdu attack guard z bpdu dropping protocols and standards mstp is document...
Page 217
1-16 task remarks configuring the timeout time factor optional configuring the maximum transmitting rate on the current port optional the default value is recommended. Configuring the current port as an edge port optional setting the link type of a port to p2p optional enabling mstp required to prev...
Page 218
1-17 configuring root bridge configuring an mst region configuration procedure follow these steps to configure an mst region: to do... Use the command... Remarks enter system view system-view — enter mst region view stp region-configuration — configure the name of the mst region region-name name req...
Page 219
1-18 z mstp-enabled switches are in the same region only when they have the same format selector (a 802.1s-defined protocol selector, which is 0 by default and cannot be configured), mst region name, vlan-to-instance mapping table, and revision level. Z the 3com switches 4210 support only the mst re...
Page 220
1-19 specify the current switch as the secondary root bridge of a spanning tree follow these steps to specify the current switch as the secondary root bridge of a spanning tree: to do... Use the command... Remarks enter system view system-view — specify the current switch as the secondary root bridg...
Page 221
1-20 configuring the bridge priority of the current switch root bridges are selected according to the bridge priorities of switches. You can make a specific switch be selected as a root bridge by setting a lower bridge priority for the switch. An mstp-enabled switch can have different bridge priorit...
Page 222
1-21 in auto mode, if a port frequently receives mstp packets of different formats alternately, the port will be forcibly placed in the discarding state and no longer forwards mstp packets. The physical state of the port will be displayed as stp down. To restore such a port, you can first run the sh...
Page 223
1-22 z stp-compatible mode, where the ports of a switch send stp bpdus to neighboring devices. If stp-enabled switches exist in a switched network, you can use the stp mode stp command to configure an mstp-enabled switch to operate in stp-compatible mode. Z rstp-compatible mode, where the ports of a...
Page 224
1-23 to do... Use the command... Remarks configure the maximum hop count of the mst region stp max-hops hops required by default, the maximum hop count of an mst region is 20. The bigger the maximum hop count, the larger the mst region is. Note that only the maximum hop settings on the switch operat...
Page 225
1-24 configuration procedure follow these steps to configure mstp time-related parameters: to do... Use the command... Remarks enter system view system-view — configure the forward delay parameter stp timer forward-delay centiseconds required the forward delay parameter defaults to 1,500 centisecond...
Page 226
1-25 configuration example # configure the forward delay parameter to be 1,600 centiseconds, the hello time parameter to be 300 centiseconds, and the max age parameter to be 2,100 centiseconds (assuming that the current switch operates as the cist root bridge). System-view [sysname] stp timer forwar...
Page 227
1-26 to do... Use the command... Remarks enter system view system-view — configure the maximum transmitting rate for specified ports stp interface interface-list transmit-limit packetnum required the maximum transmitting rate of all ethernet ports on a switch defaults to 10. Configure the maximum tr...
Page 228
1-27 to do... Use the command... Remarks configure the specified ports as edge ports stp interface interface-list edged-port enable required by default, all the ethernet ports of a switch are non-edge ports. Configure a port as an edge port in ethernet port view follow these steps to configure a por...
Page 229
1-28 you can determine whether or not the link connected to a port is a point-to-point link in one of the following two ways. Setting the link type of a port to p2p in system view follow these steps to specify whether the link connected to a port is point-to-point link in system view: to do... Use t...
Page 230
1-29 enabling mstp configuration procedure follow these steps to enable mstp in system view: to do... Use the command... Remarks enter system view system-view — enable mstp stp enable required mstp is enabled globally by default. Disable mstp on specified ports stp interface interface-list disable o...
Page 231
1-30 configuring leaf nodes configuring the mst region refer to configuring an mst region . Configuring how a port recognizes and sends mstp packets refer to configuring how a port recognizes and sends mstp packets . Configuring the timeout time factor refer to configuring the timeout time factor . ...
Page 232
1-31 rate operation mode (half-/full-duplex) 802.1d-1998 ieee 802.1t latency standard 10 mbps half-duplex/full-duplex aggregated link 2 ports aggregated link 3 ports aggregated link 4 ports 100 95 95 95 2,000,000 1,000,000 666,666 500,000 2,000 1,800 1,600 1,400 100 mbps half-duplex/full-duplex aggr...
Page 233
1-32 follow these steps to configure the path cost for a port in ethernet port view: to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the path cost for the port stp [ instance instance-id ] cost cost re...
Page 234
1-33 configure port priority in system view follow these steps to configure port priority in system view: to do... Use the command... Remarks enter system view system-view — configure port priority for specified ports stp interface interface-list instance instance-id port priority priority required ...
Page 235
1-34 performing mcheck operation ports on an mstp-enabled switch can operate in three modes: stp-compatible, rstp-compatible, and mstp. If a port on a device running mstp (or rstp) connects to a device running stp, this port will automatically migrate to the stp-compatible mode. However, it will not...
Page 236
1-35 [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] stp mcheck configuring guard functions the following guard functions are available on an mstp-enabled switch: bpdu guard, root guard, loop guard, tc-bpdu attack guard, and bpdu drop. Configuring bpdu guard normally, the access ports of ...
Page 237
1-36 configuring root guard a root bridge and its secondary root bridges must reside in the same region. The root bridge of the cist and its secondary root bridges are usually located in the high-bandwidth core region. Configuration errors or attacks may result in configuration bpdus with their prio...
Page 238
1-37 configuration example # enable the root guard function on ethernet 1/0/1. 1) perform this configuration in system view system-view [sysname] stp interface ethernet 1/0/1 root-protection 2) perform this configuration in ethernet port view system-view [sysname] interface ethernet 1/0/1 [sysname-e...
Page 239
1-38 configuration example # enable the loop guard function on ethernet 1/0/1. System-view [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] stp loop-protection configuring tc-bpdu attack guard normally, a switch removes its mac address table and arp entries upon receiving topology change b...
Page 240
1-39 # set the maximum times for the switch to remove the mac address table and arp entries within 10 seconds to 5. System-view [sysname] stp tc-protection threshold 5 configuring bpdu dropping in a stp-enabled network, attackers may send bpdus to switches continuously in order to destroy the networ...
Page 241
1-40 configuring digest snooping introduction according to ieee 802.1s, two interconnected switches can communicate with each other through mstis in an mst region only when the two switches have the same mst region-related configuration. Interconnected mstp-enabled switches determine whether or not ...
Page 242
1-41 to do... Use the command... Remarks return to system view quit — enable the digest snooping feature globally stp config-digest-snooping required the digest snooping feature is disabled globally by default. Display the current configuration display current-configuration available in any view z w...
Page 243
1-42 错误!未找到引用源。 figure 1-6 and figure 1-7 illustrate the rapid transition mechanisms on designated ports in rstp and mstp. Figure 1-6 the rstp rapid transition mechanism root port blocks other non- edge ports, changes to forwarding state and sends agreement to upstream device downstream switch upstr...
Page 244
1-43 instead of waiting for agreement packets from the upstream switch. This enables designated ports of the upstream switch to change their states rapidly. Configuring rapid transition configuration prerequisites as shown in figure 1-8 , a 3com switch is connected to another manufacturer's switch. ...
Page 245
1-44 z the rapid transition feature can be enabled on only root ports or alternate ports. Z if you configure the rapid transition feature on a designated port, the feature does not take effect on the port. Configuring vlan-vpn tunnel introduction the vlan-vpn tunnel function enables stp packets to b...
Page 246
1-45 to do... Use the command... Remarks enable the vlan-vpn tunnel function globally vlan-vpn tunnel required the vlan-vpn tunnel function is disabled by default. Enter ethernet port view interface interface-type interface-number make sure that you enter the ethernet port view of the port for which...
Page 247
1-46 # enable log/trap output for the ports of all instances. System-view [sysname] stp portlog all enabling trap messages conforming to 802.1d standard when enabled, the switch sends the following two types of 802.1d-compliant traps to the network management device: z when the switch is configured ...
Page 248
1-47 mstp configuration example network requirements implement mstp in the network shown in figure 1-10 to enable packets of different vlans to be forwarded along different mstis. The detailed configurations are as follows: z all switches in the network belong to the same mst region. Z packets of vl...
Page 249
1-48 # specify switch a as the root bridge of msti 1. [sysname] stp instance 1 root primary 2) configure switch b # enter mst region view. System-view [sysname] stp region-configuration # configure the region name, vlan-to-instance mapping table, and revision level for the mst region. [sysname-mst-r...
Page 250
1-49 vlan-vpn tunnel configuration example network requirements z switch c and switch d are the access devices for the service provider network. Z switches 4210 operate as the access devices of the customer networks, that is, switch a and switch b in the network diagram. Z switch c and switch d are ...
Page 251
1-50 [sysname] vlan-vpn tunnel # add gigabitethernet 1/0/1 to vlan 10. [sysname] vlan 10 [sysname-vlan10] port gigabitethernet 1/0/1 [sysname-vlan10] quit # enable the vlan vpn function on gigabitethernet 1/0/1. [sysname] interface gigabitethernet 1/0/1 [sysname-gigabitethernet1/0/1] port access vla...
Page 252: Table of Contents
I table of contents 1 multicast overview ····································································································································1-1 multicast overview ········································································································...
Page 253
Ii configuring dropping unknown multicast packets ·········································································3-2 displaying common multicast configuration ··························································································3-3.
Page 254: Multicast Overview
1-1 1 multicast overview multicast overview with development of networks on the internet, more and more interaction services such as data, voice, and video services are running on the networks. In addition, highly bandwidth- and time-critical services, such as e-commerce, web conference, online auct...
Page 255
1-2 information transmission in the broadcast mode when you adopt broadcast, the system transmits information to all users on a network. Any user on the network can receive the information, no matter the information is needed or not. Figure 1-2 shows information transmission in broadcast mode. Figur...
Page 256
1-3 figure 1-3 information transmission in the multicast mode source server receiver receiver receiver host a host b host c host d host e packets for the multicast group assume that hosts b, d and e need the information. To transmit the information to the right users, it is necessary to group hosts ...
Page 257
1-4 table 1-1 an analogy between tv transmission and multicast transmission step tv transmission multicast transmission 1 a tv station transmits a tv program through a television channel. A multicast source sends multicast data to a multicast group. 2 a user tunes the tv set to the channel. A receiv...
Page 258
1-5 asm model in the asm model, any sender can become a multicast source and send information to a multicast group; numbers of receivers can join a multicast group identified by a group address and obtain multicast information addressed to that multicast group. In this model, receivers are not aware...
Page 259
1-6 multicast address as receivers are multiple hosts in a multicast group, you should be concerned about the following questions: z what destination should the information source send the information to in the multicast mode? Z how to select the destination address? These questions are about multic...
Page 260
1-7 class d address range description 232.0.0.0 to 232.255.255.255 available source-specific multicast (ssm) multicast group addresses. 239.0.0.0 to 239.255.255.255 administratively scoped multicast addresses, which are for specific local use only. As specified by iana, the ip addresses ranging from...
Page 261
1-8 ethernet multicast mac address when a unicast ip packet is transported in an ethernet network, the destination mac address is the mac address of the receiver. When a multicast packet is transported in an ethernet network, a multicast mac address is used as the destination address because the des...
Page 262
1-9 figure 1-5 positions of layer 3 multicast protocols as 1 as 2 source receiver receiver receiver pim pim msdp igmp igmp igmp 1) multicast management protocols typically, the internet group management protocol (igmp) is used between hosts and layer 3 multicast devices directly connected with the h...
Page 263
1-10 figure 1-6 positions of layer 2 multicast protocols source receiver receiver multicast packets igmp snooping running on layer 2 devices, internet group management protocol snooping (igmp snooping) are multicast constraining mechanisms that manage and control multicast groups by listening to and...
Page 264
1-11 2) if the corresponding (s, g) entry exists, but the interface on which the packet actually arrived is not the incoming interface in the multicast forwarding table, the multicast packet is subject to an rpf check. Z if the result of the rpf check shows that the rpf interface is the incoming int...
Page 265
1-12 z a multicast packet from source arrives to vlan-interface 1 of switch c, and the corresponding forwarding entry does not exist in the multicast forwarding table of switch c. Switch c performs an rpf check, and finds in its unicast routing table that the outgoing interface to 192.168.0.0/24 is ...
Page 266: Igmp Snooping Configuration
2-1 2 igmp snooping configuration igmp snooping overview internet group management protocol snooping (igmp snooping) is a multicast constraining mechanism that runs on layer 2 devices to manage and control multicast groups. Principle of igmp snooping by analyzing received igmp messages, a layer 2 de...
Page 267
2-2 figure 2-2 igmp snooping related ports router a switch a switch b eth1/0/1 eth1/0/2 eth1/0/3 eth1/0/1 eth1/0/2 receiver receiver host a host b host c host d source multicast packets router port member port ports involved in igmp snooping, as shown in figure 2-2 , are described as follows: z rout...
Page 268
2-3 upon receiving an igmp general query, the switch forwards it through all ports in the vlan except the receiving port and performs the following to the receiving port: z if the receiving port is a router port existing in its router port list, the switch resets the aging timer of this router port....
Page 269
2-4 group-specific query, a switch forwards it through all the router ports in the vlan and all member ports of that multicast group, and performs the following to the receiving port: z if any igmp report in response to the group-specific query arrives to the member port before its aging timer expir...
Page 270
2-5 enabling igmp snooping table 2-3 enable igmp snooping operation command remarks enter system view system-view — enable igmp snooping globally igmp-snooping enable required by default, igmp snooping is disabled globally. Enter vlan view vlan vlan-id — enable igmp snooping on the vlan igmp-snoopin...
Page 271
2-6 z before configuring related igmp snooping functions, you must enable igmp snooping in the specified vlan. Z different multicast group addresses should be configured for different multicast sources because igmpv3 snooping cannot distinguish multicast data from different sources to the same multi...
Page 272
2-7 enabling fast leave processing in ethernet port view table 2-7 enable fast leave processing in ethernet view operation command remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — enable fast leave processing for specific vlans igmp-snoopin...
Page 273
2-8 operation command remarks configure a multicast group filter igmp-snooping group-policy acl-number [vlan vlan-list ] required no group filter is configured by default, namely hosts can join any multicast group. Configuring a multicast group filter in ethernet port view table 2-9 configure a mult...
Page 274
2-9 operation command remarks configure the maximum number of multicast groups allowed on the port igmp-snooping group-limit limit [ vlan vlan-list [ overflow-replace ] ] required the system default is 512. Z to prevent bursting traffic in the network or performance deterioration of the device cause...
Page 275
2-10 operation command remarks enable igmp snooping igmp-snooping enable required by default, igmp snooping is disabled. Enable igmp snooping querier igmp-snooping querier required by default, igmp snooping querier is disabled. Configuring igmp query interval follow these steps to configure igmp que...
Page 276
2-11 operation command remarks enable unknown multicast flooding suppression igmp-snooping nonflooding-enable required by default, unknown multicast flooding suppression z if the function of dropping unknown multicast packets is enabled, you cannot enable unknown multicast flooding suppression. Z un...
Page 277
2-12 operation command remarks configure specified port(s) as static member port(s) of a multicast group in the vlan multicast static-group group-address interface interface-list required by default, no port is configured as a static multicast group member port. Configuring a static router port in a...
Page 278
2-13 z when an ethernet port is configured as a simulated member host, the switch sends an igmp report through this port. Meanwhile, the switch sends the same igmp report to itself and establishes a corresponding igmp entry based on this report. Z when receiving an igmp general query, the simulated ...
Page 279
2-14 it is not recommended to configure this function while the multicast vlan function is in effect. Configuring multicast vlan in traditional multicast implementations, when users in different vlans listen to the same multicast group, the multicast data is copied on the multicast router for each v...
Page 280
2-15 table 2-19 configure multicast vlan on the layer 2 switch operation command remarks enter system view system-view — enable igmp snooping igmp-snooping enable — enter vlan view vlan vlan-id — enable igmp snooping igmp-snooping enable required enable multicast vlan service-type multicast required...
Page 281
2-16 you can execute the reset command in user view to clear the statistics information about igmp snooping. Table 2-20 display and maintain igmp snooping operation command remarks display the current igmp snooping configuration display igmp-snooping configuration display igmp snooping message stati...
Page 282
2-17 configuration procedure 1) configure the ip address of each interface configure an ip address and subnet mask for each interface as per figure 2-3 . The detailed configuration steps are omitted. 2) configure router a # enable ip multicast routing, enable pim-dm on each interface, and enable igm...
Page 283
2-18 host port(s):ethernet1/0/3 ethernet1/0/4 as shown above, the multicast group 224.1.1.1 is established on switch a, with the dynamic router port ethernet1/0/1 and dynamic member ports ethernet1/0/3 and ethernet1/0/4. This means that host a and host b have joined the multicast group 224.1.1.1. Co...
Page 284
2-19 network diagram figure 2-4 network diagram for multicast vlan configuration workstation switcha switchb vlan-int20 168.10.1.1 eth1/0/1 eth1/0/10 vla n2 vlan3 eth1/0/10 vlan10 eth 1/0 /1 eth1/0 /2 hosta hostb vlan-int10 168.10.2.1 configuration procedure the following configuration is based on t...
Page 285
2-20 [switchb] vlan 10 [switchb-vlan10] service-type multicast [switchb-vlan10] igmp-snooping enable [switchb-vlan10] quit # define ethernet 1/0/10 as a hybrid port, add the port to vlan 2, vlan 3, and vlan 10, and configure the port to forward tagged packets for vlan 2, vlan 3, and vlan 10. [switch...
Page 286
3-1 3 common multicast configuration common multicast configuration table 3-1 common multicast configuration tasks configuration task remarks configuring suppression on the multicast source port optional configuring a multicast mac address entry optional configuring dropping unknown multicast packet...
Page 287
3-2 configuring a multicast mac address entry in layer 2 multicast, the system can add multicast forwarding entries dynamically through a layer 2 multicast protocol. Alternatively, you can statically bind a port to a multicast mac address entry by configuring a multicast mac address entry manually. ...
Page 288
3-3 packets is enabled, the switch will drop any multicast packets whose multicast address is not registered. Thus, the bandwidth is saved and the processing efficiency of the system is improved. Table 3-6 configure dropping unknown multicast packet operation command remarks enter system view system...
Page 289: Table of Contents
I table of contents 1 802.1x configuration ·································································································································1-1 introduction to 802.1x······································································································...
Page 290: 802.1X Configuration
1-1 1 802.1x configuration introduction to 802.1x the 802.1x protocol (802.1x for short) was developed by ieee802 lan/wan committee to address security issues of wireless lans. It was then used in ethernet as a common access control mechanism for lan ports to address mainly authentication and securi...
Page 291
1-2 stores user information, such as user name, password, the vlan a user belongs to, priority, and the acls (access control list) applied. The four basic concepts related to the above three entities are pae, controlled port and uncontrolled port, the valid direction of a controlled port and the way...
Page 292
1-3 figure 1-2 the mechanism of an 802.1x authentication system z eap protocol packets transmitted between the supplicant system pae and the authenticator system pae are encapsulated as eapol packets. Z eap protocol packets transmitted between the authenticator system pae and the radius server can e...
Page 293
1-4 z the packet body field differs with the type field. Note that eapol-start, eapol-logoff, and eapol-key packets are only transmitted between the supplicant system and the authenticator system. Eap-packets are encapsulated by radius protocol to allow them successfully reach the authentication ser...
Page 294
1-5 fragmented and are encapsulated in multiple eap-message fields. The type code of the eap-message field is 79. Figure 1-6 the format of an eap-message field 0 15 type string 7 length n eap packets the message-authenticator field, whose format is shown in figure 1-7 , is used to prevent unauthoriz...
Page 295
1-6 figure 1-8 802.1x authentication procedure (in eap relay mode) supplicant system pae raduis server eapol eapor eapol-start eap-request / identity eap-response / identity eap-request / md5 challenge eap-success eap-response / md5 challenge radius access-request (eap-response / identity) radius ac...
Page 296
1-7 z the radius server compares the received encrypted password (contained in a radius access-request packet) with the locally-encrypted password. If the two match, it will then send feedbacks (through a radius access-accept packet and an eap-success packet) to the switch to indicate that the suppl...
Page 297
1-8 figure 1-9 802.1x authentication procedure (in eap terminating mode) supplicant system pae authenticator system pae radius server eapol radius eapol-start eap-request/identity eap-response/identity eap-request/md5 challenge eap-success eap-response/md5 challenge radius access-request (chap-respo...
Page 298
1-9 request packet if it does not receive the response from the radius server when this timer times out. Z supplicant system timer (supp-timeout). This timer sets the supp-timeout period and is triggered by the switch after the switch sends a request/challenge packet to a supplicant system. The swit...
Page 299
1-10 z the 802.1x client needs to capable of detecting multiple network adapters, proxies, and ie proxies. Z the cams server is configured to disable the use of multiple network adapters, proxies, or ie proxies. By default, an 802.1x client program allows use of multiple network adapters, proxies, a...
Page 300
1-11 refer to aaa operation manual for detailed information about the dynamic vlan delivery function. Enabling 802.1x re-authentication 802.1x re-authentication is timer-triggered or packet-triggered. It re-authenticates users who have passed authentication. With 802.1x re-authentication enabled, th...
Page 301
1-12 802.1x re-authentication will fail if a cams server is used and configured to perform authentication but not accounting. This is because a cams server establishes a user session after it begins to perform accounting. Therefore, to enable 802.1x re-authentication, do not configure the accounting...
Page 302
1-13 configuring basic 802.1x functions table 1-1 configure basic 802.1x functions operation command remarks enter system view system-view — enable 802.1x globally dot1x required by default, 802.1x is disabled globally. In system view dot1x interface interface-list interface interface-type interface...
Page 303
1-14 z 802.1x configurations take effect only after you enable 802.1x both globally and for specified ports. Z if you enable 802.1x for a port, you cannot set the maximum number of mac addresses that can be learnt for the port. Meanwhile, if you set the maximum number of mac addresses that can be le...
Page 305
1-16 authority (that is, the user domain names are the same). This allows you to deploy 802.1x access policies flexibly. Table 1-3 shows the relations of the 802.1x username entered for authentication, mandatory authentication domain configured for the port connecting users, authentication domain fo...
Page 307
1-18 operation command remarks set the client version checking period timer dot1x timer ver-period ver-period-value optional by default, the timer is set to 30 seconds. As for the dot1x version-user command, if you execute it in system view without specifying the interface-list argument, the command...
Page 308
1-19 z the guest vlan function is available only when the switch operates in the port-based authentication mode. Z only one guest vlan can be configured for each switch. Z the guest vlan function cannot be implemented if you configure the dot1x dhcp-launch command on the switch to enable dhcp-trigge...
Page 309
1-20 during re-authentication, the switch always uses the latest re-authentication interval configured, no matter which of the above-mentioned two ways is used to determine the re-authentication interval. For example, if you configure a re-authentication interval on the switch and the switch receive...
Page 310
1-21 z the switch is connected to a server comprising of two radius servers whose ip addresses are 10.11.1.1 and 10.11.1.2. The radius server with an ip address of 10.11.1.1 operates as the primary authentication server and the secondary accounting server. The other operates as the secondary authent...
Page 311
1-22 # create a radius scheme named “radius1” and enter radius scheme view. [sysname] radius scheme radius1 # assign ip addresses to the primary authentication and accounting radius servers. [sysname-radius-radius1] primary authentication 10.11.1.1 [sysname-radius-radius1] primary accounting 10.11.1...
Page 312
1-23 802.1x mandatory authentication domain configuration example network requirements as shown in figure 1-13 , host a (an 802.1x user) and host b (a telnet user) are connected to the internet through ethernet 1/0/1 and ethernet 1/0/2 on switch, respectively. It is required to implement radius auth...
Page 313
1-24 [switch-isp-aabbcc] scheme radius-scheme radius1 [switch-isp-aabbcc] quit # configure radius scheme radius1. [switch] radius scheme radius1 [switch-radius-radius1] primary authentication 10.110.91.164 1812 [switch-radius-radius1] primary accounting 10.110.91.164 1813 [switch-radius-radius1] key...
Page 314: Habp Configuration
2-1 2 habp configuration introduction to habp with 802.1x enabled, a switch authenticates and then authorizes 802.1x-enabled ports. Packets can be forwarded only by authorized ports. For ports with switches attached and are not authenticated and authorized by 802.1x, their received packets will be f...
Page 315
2-2 habp client configuration habp clients reside on switches attached to habp servers. After you enable habp for a switch, the switch operates as an habp client by default. So you only need to enable habp on a switch to make it an habp client. Table 2-2 configure an habp client operation command re...
Page 316: System-Guard Configuration
3-1 3 system-guard configuration system-guard overview at first, you must determine whether the cpu is under attack to implement system guard for the cpu. You should not determine whether the cpu is under attack just according to whether congestion occurs in a queue. Instead, you must do that in the...
Page 317
3-2 displaying and maintaining system-guard after the above configuration, execute the display command in any view to display the running status of the system-guard feature, and to verify the configuration. Table 3-2 display and maintain system-guard operation command display the record of detected ...
Page 318: Table of Contents
I table of contents 1 aaa overview ············································································································································1-1 introduction to aaa ·····································································································...
Page 319
Ii per user type aaa configuration example··················································································2-30 remote radius authentication of telnet/ssh users ·································································2-31 local authentication of ftp/telnet users············...
Page 320: Aaa Overview
1-1 1 aaa overview introduction to aaa aaa is the acronym for the three security functions: authentication, authorization and accounting. It provides a uniform framework for you to configure these three functions to implement network security management. Z authentication: defines what users can acce...
Page 321
1-2 accounting aaa supports the following accounting methods: z none accounting: no accounting is performed for users. Z local accounting: it is not used for charging purposes, but for collecting statistics and limiting the number of local user connections. Z remote accounting: user accounting is pe...
Page 322
1-3 introduction to aaa services introduction to radius aaa is a management framework. It can be implemented by not only one protocol. But in practice, the most commonly used service for aaa is radius. What is radius radius (remote authentication dial-in user service) is a distributed service based ...
Page 323
1-4 the authentication response message. Figure 1-3 depicts the message exchange procedure between user, switch and radius server. Figure 1-3 basic message exchange procedure of radius radius client radius server ( 1 ) the user inputs the user name and password ( 3 ) access-accept ( 2 ) access-reque...
Page 324
1-5 figure 1-4 radius message format 2) the code field (one byte) decides the type of radius message, as shown in table 1-1 . Table 1-1 description on the major values of the code field code message type message description 1 access-request direction: client->server. The client transmits this messag...
Page 325
1-6 5) the authenticator field (16 bytes) is used to authenticate the response from the radius server; and is used in the password hiding algorithm. There are two kinds of authenticators: request authenticator and response authenticator. 6) the attributes field contains specific authentication/autho...
Page 326
1-7 figure 1-5 depicts the format of attribute 26. The vendor-id field used to identify a vendor occupies four bytes, where the first byte is 0, and the other three bytes are defined in rfc 1700. Here, the vendor can encapsulate multiple customized sub-attributes (containing vendor-specific type, le...
Page 327
1-8 figure 1-6 network diagram for a typical hwtacacs application host hwtacacs client hwtacacs server hwtacacs server basic message exchange procedure in hwtacacs the following text takes telnet user as an example to describe how hwtacacs implements authentication, authorization, and accounting for...
Page 328
1-9 1) a user sends a login request to the switch acting as a tacacs client, which then sends an authentication start request to the tacacs server. 2) the tacacs server returns an authentication response, asking for the username. Upon receiving the response, the tacacs client requests the user for t...
Page 329: Aaa Configuration
2-1 2 aaa configuration aaa configuration task list configuration introduction you need to configure aaa to provide network access services for legal users while protecting network devices and preventing unauthorized access and repudiation behavior. Table 2-1 aaa configuration tasks (configuring a c...
Page 330
2-2 task remarks cutting down user connections forcibly optional creating an isp domain and configuring its attributes table 2-3 create an isp domain and configure its attributes operation command remarks enter system view system-view — configure the form of the delimiter between the user name and t...
Page 331
2-3 z if you have configured to use "." as the delimiter, for a user name that contains multiple ".", the first "." will be used as the domain delimiter. Z if you have configured to use "@" as the delimiter, the "@" must not appear more than once in the user name. Z if the system does not find any a...
Page 333
2-5 z you can execute the scheme radius-scheme radius-scheme-name command to adopt an already configured radius scheme to implement all the three aaa functions. If you adopt the local scheme, only the authentication and authorization functions are implemented, the accounting function cannot be imple...
Page 334
2-6 z local authentication (local): authentication is performed by the nas, which is configured with the user information, including the usernames, passwords, and attributes. Local authentication features high speed and low cost, but the amount of information that can be stored is limited by the har...
Page 336
2-8 configuring dynamic vlan assignment the dynamic vlan assignment feature enables a switch to dynamically add the switch ports of successfully authenticated users to different vlans according to the attributes assigned by the radius server, so as to control the network resources that different use...
Page 337
2-9 configuring the attributes of a local user when local scheme is chosen as the aaa scheme, you should create local users on the switch and configure the relevant attributes. The local users are users set on the switch, with each user uniquely identified by a user name. To make a user who is reque...
Page 338
2-10 z the following characters are not allowed in the user-name string: /:*?. And you cannot input more than one “@” in the string. Z after the local-user password-display-mode cipher-force command is executed, any password will be displayed in cipher mode even though you specify to display a user ...
Page 339
2-11 table 2-9 radius configuration tasks (the switch functions as a radius client) task remarks creating a radius scheme required configuring radius authentication/authorization servers required configuring ignorance of assigned radius authorization attributes optional configuring the sending mode ...
Page 340
2-12 the radius service configuration is performed on a radius scheme basis. In an actual network environment, you can either use a single radius server or two radius servers (primary and secondary servers with the same configuration but different ip addresses) in a radius scheme. After creating a n...
Page 341
2-13 configuring radius authentication/authorization servers table 2-12 configure radius authentication/authorization servers operation command remarks enter system view system-view — create a radius scheme and enter its view radius scheme radius-scheme-name required by default, a radius scheme name...
Page 342
2-14 use the assigned attribute 28, idle-timeout. You can configure the attribute ignoring function on nas 2 to ignore attribute 28. Figure 2-1 network diagram for the radius authorization attribute ignoring function host 1 switch radius server host 2 ip network nas 1 nas 2 follow these steps to con...
Page 344
2-16 operation command remarks set the maximum allowed number of continuous real-time accounting failures retry realtime-accounting retry-times optional by default, the maximum allowed number of continuous real-time accounting failures is five. If five continuous failures occur, the switch cuts down...
Page 345
2-17 operation command remarks set a shared key for radius accounting messages key accounting string required by default, no shared key is created. The authentication/authorization shared key and the accounting shared key you set on the switch must be respectively consistent with the shared key on t...
Page 346
2-18 z if you change the type of radius server, the data stream destined to the original radius server will be restored to the default unit. Z when the third party radius server is used, you can select standard or extended as the server-type in a radius scheme; when the cams server is used, you can ...
Page 347
2-19 configuring the attributes of data to be sent to radius servers table 2-19 configure the attributes of data to be sent to radius servers operation command remarks enter system view system-view — create a radius scheme and enter its view radius scheme radius-scheme-name required by default, a ra...
Page 348
2-20 z generally, the access users are named in the userid@isp-name or userid.Isp-name format. Here, isp-name after the “@” or “.” character represents the isp domain name, by which the device determines which isp domain a user belongs to. However, some old radius servers cannot accept the user name...
Page 349
2-21 z if you adopt the local radius authentication server function, the udp port number of the authentication/authorization server must be 1645, the udp port number of the accounting server must be 1646, and the ip addresses of the servers must be set to the addresses of this switch. Z the message ...
Page 350
2-22 operation command remarks create a radius scheme and enter its view radius scheme radius-scheme-name required by default, a radius scheme named "system" has already been created in the system. Set the response timeout time of radius servers timer response-timeout seconds optional by default, th...
Page 351
2-23 in an environment that a cams server is used to implement aaa functions, if the switch reboots after an exclusive user (a user whose concurrent online number is set to 1 on the cams) gets authenticated and authorized and begins being charged, the switch will give a prompt that the user has alre...
Page 352
2-24 hwtacacs configuration task list table 2-24 hwtacacs configuration tasks task remarks creating a hwtacacs scheme required configuring tacacs authentication servers required configuring tacacs authorization servers required configuring tacacs accounting servers optional configuring shared keys f...
Page 353
2-25 operation command remarks set the ip address and port number of the primary tacacs authentication server primary authentication ip-address [ port ] required by default, the ip address of the primary authentication server is 0.0.0.0, and the port number is 0. Set the ip address and port number o...
Page 354
2-26 configuring tacacs accounting servers table 2-28 configure tacacs accounting servers operation command remarks enter system view system-view — create a hwtacacs scheme and enter its view hwtacacs scheme hwtacacs-scheme-name required by default, no hwtacacs scheme exists. Set the ip address and ...
Page 356
2-28 configuring the timers regarding tacacs servers table 2-31 configure the timers regarding tacacs servers operation command remarks enter system view system-view — create a hwtacacs scheme and enter its view hwtacacs scheme hwtacacs-scheme-name required by default, no hwtacacs scheme exists. Set...
Page 358
2-30 operation command remarks delete buffered non-response stop-accounting requests reset stop-accounting-buffer hwtacacs-scheme hwtacacs-scheme-name aaa configuration examples per user type aaa configuration example network requirements as shown in figure 2-2 , host a, serving as an 802.1x user, a...
Page 359
2-31 # configure radius scheme radius1. [switch] radius scheme radius1 [switch-radius-radius1] primary authentication 10.110.91.164 1812 [switch-radius-radius1] primary accounting 10.110.91.164 1813 [switch-radius-radius1] key authentication aabbcc [switch-radius-radius1] server-type extended [switc...
Page 360
2-32 the telnet user names added to the radius server must be in the format of userid@isp-name if you have configured the switch to include domain names in the user names to be sent to the radius server in the radius scheme. Network diagram figure 2-3 remote radius authentication of telnet users con...
Page 361
2-33 the configuration procedure for local authentication of ftp users is similar to that for telnet users. The following text only takes telnet users as example to describe the configuration procedure for local authentication. Network requirements in the network environment shown in figure 2-4 , yo...
Page 362
2-34 z change the server ip address, and the udp port number of the authentication server to 127.0.0.1, and 1645 respectively in the configuration step "configure a radius scheme" in section remote radius authentication of telnet/ssh users . Z enable the local radius server function, set the ip addr...
Page 363
2-35 troubleshooting aaa troubleshooting radius configuration the radius protocol operates at the application layer in the tcp/ip protocol suite. This protocol prescribes how the switch and the radius server of the isp exchange user information with each other. Symptom 1: user authentication/authori...
Page 364: Table of Contents
I table of contents 1 mac authentication configuration··········································································································1-1 mac authentication overview ············································································································...
Page 365
1-1 1 mac authentication configuration mac authentication overview mac authentication provides a way for authenticating users based on ports and mac addresses, without requiring any client software to be installed on the hosts. Once detecting a new mac address, it initiates the authentication proces...
Page 366
1-2 related concepts mac authentication timers the following timers function in the process of mac authentication: z offline detect timer: at this interval, the switch checks to see whether an online user has gone offline. Once detecting that a user becomes offline, the switch sends a stop-accountin...
Page 367
1-3 operation command remarks set the user name in fixed mode for mac authentication mac-authentication authmode usernamefixed configure the user name mac-authentication authusername username set the user name in fixed mode for mac authentication configure the password mac-authentication authpasswor...
Page 368
1-4 operation description related section configuring quiet mac function on a port optional section “ configuring the quiet mac function on a port ” configuring a guest vlan different from guest vlans described in the 802.1x and system-guard manual, guest vlans mentioned in this section refer to gue...
Page 369
1-5 table 1-3 configure a guest vlan operation command description enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the guest vlan for the current port mac-authentication guest-vlan vlan-id required by default, no guest vlan is configured...
Page 370
1-6 table 1-4 configure the maximum number of mac address authentication users allowed to access a port operation command description enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the maximum number of mac address authentication users ...
Page 371
1-7 table 1-6 display and debug mac authentication operation command description display global or on-port information about mac authentication display mac-authentication [ interface interface-list ] available in any view clear the statistics of global or on-port mac authentication reset mac-authent...
Page 372
1-8 # specify to perform local authentication. [sysname-isp-aabbcc.Net] scheme local [sysname-isp-aabbcc.Net] quit # specify aabbcc.Net as the isp domain for mac authentication [sysname] mac-authentication domain aabbcc.Net # enable mac authentication globally (this is usually the last step in confi...
Page 373: Table of Contents
I table of contents 1 arp configuration·····································································································································1-1 introduction to arp ········································································································...
Page 374: Arp Configuration
1-1 1 arp configuration introduction to arp arp function address resolution protocol (arp) is used to resolve an ip address into a data link layer address. An ip address is the address of a host at the network layer. To send a network layer packet to a destination host, the device must know the data...
Page 375
1-2 table 1-1 describes the fields of an arp packet. Table 1-1 description on the fields of an arp packet field description hardware type type of the hardware interface. Refer to table 1-2 for the information about the field values. Protocol type type of protocol address to be mapped. 0x0800 indicat...
Page 376
1-3 table 1-3 arp entries arp entry generation method maintenance mode static arp entry manually configured manual maintenance dynamic arp entry dynamically generated arp entries of this type age with time. The aging period is set by the arp aging timer. Arp process figure 1-2 arp process suppose th...
Page 377
1-4 introduction to arp attack detection man-in-the-middle attack according to the arp design, after receiving an arp response, a host adds the ip-to-mac mapping of the sender into its arp mapping table even if the mac address is not the real one. This can reduce the arp traffic in the network, but ...
Page 378
1-5 packets, or through trusted ports if the mac address table contains no such destination mac addresses. Introduction to arp packet rate limit to prevent the man-in-the-middle attack, a switch enabled with the arp attack detection function delivers arp packets to the cpu to check the validity of t...
Page 379
1-6 operation command remarks configure the arp aging timer arp timer aging aging-time optional by default, the arp aging timer is set to 20 minutes. Enable the arp entry checking function (that is, disable the switch from learning arp entries with multicast mac addresses) arp check enable optional ...
Page 380
1-7 operation command remarks configure the port as an arp trusted port arp detection trust optional by default, a port is an untrusted port. Quit to system view quit — enter vlan view vlan vlan-id — enable arp restricted forwarding arp restricted-forwarding enable optional by default, the arp restr...
Page 381
1-8 operation command remarks quit to system view quit — enable the port state auto-recovery function arp protective-down recover enable optional by default, the port state auto-recovery function is disabled. Configure the port state auto-recovery interval arp protective-down recover interval interv...
Page 383
1-10 z enable the port state auto recovery function on the ports of switch a, and set the recovery interval to 200 seconds. Network diagram figure 1-4 arp attack detection and packet rate limit configuration configuration procedure # enable dhcp snooping on switch a. System-view [switcha] dhcp-snoop...
Page 384
1-11 # configure the port state auto recovery function, and set the recovery interval to 200 seconds. [switcha] arp protective-down recover enable [switcha] arp protective-down recover interval 200
Page 385: Table of Contents
I table of contents 1 dhcp overview··········································································································································1-1 introduction to dhcp ······································································································...
Page 386
Ii introduction to dhcp accounting··································································································2-23 dhcp accounting fundamentals··································································································2-23 dhcp accounting configuration ··...
Page 387: Dhcp Overview
1-1 1 dhcp overview introduction to dhcp with networks getting larger in size and more complicated in structure, lack of available ip addresses becomes the common situation the network administrators have to face, and network configuration becomes a tough task for the network administrators. With th...
Page 388
1-2 obtaining ip addresses dynamically a dhcp client undergoes the following four phases to dynamically obtain an ip address from a dhcp server: 1) discover: in this phase, the dhcp client tries to find a dhcp server by broadcasting a dhcp-discover packet. 2) offer: in this phase, the dhcp server of...
Page 389
1-3 if the dhcp client fails to update its ip address lease when half of the lease time elapses, it will update its ip address lease by broadcasting a dhcp-request packet to the dhcp servers again when seven-eighths of the lease time elapses. The dhcp server performs the same operations as those des...
Page 390
1-4 protocol specification protocol specifications related to dhcp include: z rfc2131: dynamic host configuration protocol z rfc2132: dhcp options and bootp vendor extensions z rfc1542: clarifications and extensions for the bootstrap protocol z rfc3046: dhcp relay agent information option.
Page 391: Dhcp Server Configuration
2-1 2 dhcp server configuration when configuring the dhcp server, go to these sections for information you are interested in: z introduction to dhcp server z dhcp server configuration task list z enabling dhcp z configuring the global address pool based dhcp server z configuring the interface addres...
Page 392
2-2 types of address pool the address pools of a dhcp server fall into two types: global address pool and interface address pool. Z a global address pool is created by executing the dhcp server ip-pool command in system view. It is valid on the current device. Z if an interface is configured with a ...
Page 393
2-3 3) if there is an address pool where an ip address is statically bound to the mac address or id of the client, the dhcp server will select this address pool and assign the statically bound ip address to the client. 4) otherwise, the dhcp server observes the following principles to select a dynam...
Page 394
2-4 to do… use the command… remarks enable dhcp dhcp enable optional by default, dhcp is enabled. To improve security and avoid malicious attacks to unused sockets, switch 4210 family provide the following functions: z udp port 67 and udp port 68 ports used by dhcp are enabled only when dhcp is enab...
Page 395
2-5 enabling the global address pool mode on interface(s) you can configure the global address pool mode on the specified or all interfaces of a dhcp server. After that, when the dhcp server receives dhcp packets from dhcp clients through these interfaces, it assigns ip addresses in the global addre...
Page 396
2-6 address, the dhcp server searches for the ip address corresponding to the mac address of the dhcp client and assigns the ip address to the dhcp client. When some dhcp clients send dhcp-discover packets to the dhcp server to apply for ip addresses, they construct client ids and add them in the dh...
Page 397
2-7 to improve security and avoid malicious attack to the unused sockets, switch 4210 family provide the following functions: z udp 67 and udp 68 ports used by dhcp are enabled only when dhcp is enabled. Z udp 67 and udp 68 ports are disabled when dhcp is disabled. The corresponding implementation i...
Page 398
2-8 z in the same dhcp global address pool, the network command can be executed repeatedly. In this case, the new configuration overwrites the previous one. Z the dhcp server forbidden-ip command can be executed repeatedly. That is, you can configure multiple ip addresses that are not dynamically as...
Page 399
2-9 configuring wins servers for the dhcp client for microsoft windows-based dhcp clients that communicate through netbios protocol, the host name-to-ip address translation is carried out by windows internet naming service (wins) servers. So you need to perform wins-related configuration for most wi...
Page 400
2-10 configuring gateways for the dhcp client gateways are necessary for dhcp clients to access servers/hosts outside the current network segment. After you configure gateway addresses on a dhcp server, the dhcp server provides the gateway addresses to dhcp clients as well while assigning ip address...
Page 401
2-11 z sub-option 4: fail-over call routing. Meanings of the sub-options for option 184 figure 2-1 meanings of the sub-options for option 184 sub-option feature function note ncp-ip (sub-option 1) the ncp-ip sub-option carries the ip address of the network call processor (ncp). The ip address of the...
Page 402
2-12 for the configurations specifying to add sub-option 2, sub-option 3, and sub-option 4 in the response packets to take effect, you need to configure the dhcp server to add sub-option 1. Mechanism of using option 184 on dhcp server the dhcp server encapsulates the information for option 184 to ca...
Page 403
2-13 specify an ip address for the network calling processor before performing other configuration. Configuring a self-defined dhcp option by configuring self-defined dhcp options, you can: z define new dhcp options. New configuration options will come out with dhcp development. To support new optio...
Page 404
2-14 configuring the interface address pool based dhcp server in the interface address pool mode, after the addresses in the interface address pool have been assigned, the dhcp server picks ip addresses from the global interface address pool containing the network segment of the interface address po...
Page 405
2-15 task remarks enabling the interface address pool mode on interface(s) required configuring the static ip address allocation mode configuring an address allocation mode for an interface address pool configuring the dynamic ip address allocation mode one of the two options is required. And these ...
Page 406
2-16 to improve security and avoid malicious attack to the unused sockets, s3600 ethernet switches provide the following functions: z udp port 67 and udp port 68 ports used by dhcp are enabled only when dhcp is enabled. Z udp port 67 and udp port 68 ports are disabled when dhcp is disabled. The corr...
Page 407
2-17 z the ip addresses statically bound in interface address pools and the interface ip addresses must be in the same network segment. Z there is no limit to the number of ip addresses statically bound in an interface address pool, but the ip addresses statically bound in interface address pools an...
Page 408
2-18 to do… use the command… remarks specify the ip addresses that are not dynamically assigned dhcp server forbidden-ip low-ip-address [ high-ip-address ] optional by default, all ip addresses in a dhcp address pool are available for being dynamically assigned. Z the dhcp server forbidden-ip comman...
Page 409
2-19 to do… use the command… remarks enter system view system-view — interface interface-type interface-number dhcp server dns-list ip-address& configure the current interface quit configure dns server addresses for dhcp clients configure multiple interfaces in system view dhcp server dns-list ip-ad...
Page 411
2-21 follow these steps to configure option 184 parameters for the client with voice service: to do… use the command… remarks enter system view system-view — enter interface view interface interface-type interface-number — specify the primary network calling processor dhcp server voice-config ncp-ip...
Page 412
2-22 z define new dhcp options. New configuration options will come out with dhcp development. To support new options, you can add them into the attribute list of the dhcp server. Z extend existing dhcp options. When the current dhcp options cannot meet customers’ requirements (for example, you cann...
Page 413
2-23 to do… use the command… remarks enable the unauthorized dhcp server detecting function dhcp server detect required disabled by default. With the unauthorized dhcp server detection enabled, the relay agent will log all dhcp servers, including authorized ones, and each server is recorded only onc...
Page 414
2-24 z after sending a dhcp-ack packet with the ip configuration parameters to the dhcp client, the dhcp server sends an accounting start packet to a specified radius server. The radius server processes the packet, makes a record, and sends a response to the dhcp server. Z once releasing a lease, th...
Page 415
2-25 if a dhcp server is configured to ignore option 82, after the dhcp server receives packets containing option 82, the dhcp server will not add option 82 into the responses when assigning ip addresses and other configuration information to the clients. Follow these steps to configure the dhcp ser...
Page 416
2-26 dhcp server configuration examples dhcp server configuration example network requirements z the dhcp server (switch a) assigns ip address to clients in subnet 10.1.1.0/24, which is subnetted into 10.1.1.0/25 and 10.1.1.128/25. Z the ip addresses of vlan-interface 1 and vlan-interface 2 on switc...
Page 417
2-27 if you use the inheriting relation of parent and child address pools, make sure that the number of the assigned ip addresses does not exceed the number of the ip addresses in the child address pool; otherwise extra ip addresses will be obtained from the parent address pool, and the attributes (...
Page 418
2-28 # configure dhcp address pool 0, including address range, domain name suffix of the clients, and domain name server address. [switcha] dhcp server ip-pool 0 [switcha-dhcp-pool-0] network 10.1.1.0 mask 255.255.255.0 [switcha-dhcp-pool-0] domain-name aabbcc.Com [switcha-dhcp-pool-0] dns-list 10.1...
Page 419
2-29 network diagram dhcp client dhcp client dhcp client 3com vcx dhcp server ip:10.1.1.1/24 figure 2-3 network diagram for option 184 support configuration configuration procedure 1) configure the dhcp client. Configure the 3com vcx device to operate as a dhcp client and to request for all sub-opti...
Page 420
2-30 z the ip address of vlan-interface 1 is 10.1.1.1/24, and that of vlan-interface 2 is 10.1.2.1/24. Z the ip address of the radius server is 10.1.2.2/24. Z dhcp accounting is enabled on the dhcp server. Z the ip addresses of the global dhcp address pool belongs to the network segment 10.1.1.0. Th...
Page 421
2-31 [sysname] domain 123 [sysname-isp-123] scheme radius-scheme 123 [sysname-isp-123] quit # create an address pool on the dhcp server. [sysname] dhcp server ip-pool test [sysname-dhcp-pool-test] network 10.1.1.0 mask 255.255.255.0 # enable dhcp accounting. [sysname-dhcp-pool-test] accounting domai...
Page 422: Dhcp Snooping Configuration
3-1 3 dhcp snooping configuration introduction introduction to dhcp snooping for the sake of security, the ip addresses used by online dhcp clients need to be tracked for the administrator to verify the corresponding relationship between the ip addresses the dhcp clients obtained from dhcp servers a...
Page 423
3-2 overview of dhcp-snooping option 82 introduction to option 82 option 82 is the relay agent information option in the dhcp message. It records the location information of the dhcp client. When a dhcp relay agent (or a device enabled with dhcp snooping) receives a client’s request, it adds the opt...
Page 424
3-3 default padding contents). In the standard format, the circuit id or remote id sub-option does not contain the two-byte type and length fields of the circuit id or remote id. Figure 3-4 standard format of the circuit id sub-option figure 3-5 standard format of the remote id sub-option mechanism ...
Page 425
3-4 sub-option configuration the dhcp-snooping device will … circuit id sub-option is configured. Forward the packet after adding option 82 with the configured circuit id sub-option in ascii format. Remote id sub-option is configured. Forward the packet after adding option 82 with the configured rem...
Page 426
3-5 z filtering the source ip address in a packet. If the source ip address and the number of the port that receives the packet are consistent with entries in the dhcp-snooping table or static binding table, the switch regards the packet as a valid packet and forwards it; otherwise, the switch drops...
Page 427
3-6 after dhcp snooping is enabled, all ports of a switch 4210 are untrusted ports. You need to specify the port of the switch 4210 connected to the valid dhcp server as trusted to ensure that dhcp clients can obtain valid ip addresses. The trusted port and the port connected to the dhcp clients mus...
Page 429
3-8 operation command description configure the circuit id sub-option in option 82 dhcp-snooping information [ vlan vlan-id] circuit-id string string optional by default, the circuit id sub-option contains the vlan id and port index related to the port that receives dhcp request packets from dhcp cl...
Page 430
3-9 z if you configure a remote id sub-option in both system view and on a port, the remote id sub-option configured on the port applies when the port receives a packet, and the global remote id applies to other interfaces that have no remote id sub-option configured. Z if you have configured a remo...
Page 431
3-10 z enable dhcp snooping and specify trusted ports on the switch before configuring ip filtering. Z you are not recommended to configure ip filtering on the ports of an aggregation group. Z to create a static binding after ip filtering is enabled with the mac-address keyword specified on a port, ...
Page 432
3-11 network diagram figure 3-8 network diagram for dhcp-snooping option 82 support configuration eth1/0/2 client b switch dhcp snooping client a eth1/0/1 client c eth1/0/3 eth1/0/5 dhcp server configuration procedure # enable dhcp snooping on the switch. System-view [switch] dhcp-snooping # specify...
Page 433
3-12 z enable ip filtering on ethernet1/0/2, ethernet1/0/3, and ethernet1/0/4 to prevent attacks to the server from clients using fake source ip addresses. Z create static binding entries on the switch, so that host a using a fixed ip address can access the external network. Network diagram figure 3...
Page 434
3-13 [switch-ethernet1/0/2] ip source static binding ip-address 1.1.1.1 mac-address 0001-0001-0001.
Page 435
4-1 4 dhcp packet rate limit configuration introduction to dhcp packet rate limit to prevent arp attacks and attacks from unauthorized dhcp servers, arp packets and dhcp packets will be processed by the switch cpu for validity checking. But, if attackers generate a large number of arp packets or dhc...
Page 436
4-2 configuring dhcp packet rate limit configuring dhcp packet rate limit follow these steps to configure rate limit of dhcp packets: operation command description enter system view system-view — enter port view interface interface-type interface-number — enable the dhcp packet rate limit function d...
Page 437
4-3 networking diagram figure 4-1 network diagram for dhcp packet rate limit configuration ethernet1/0/2 client a client b ethernet1/0/11 dhcp server dhcp snooping ethernet1/0/1 configuration procedure # enable dhcp snooping on the switch. System-view [switch] dhcp-snooping # specify ethernet1/0/1 a...
Page 438
5-1 5 dhcp/bootp client configuration introduction to dhcp client after you specify a vlan interface as a dhcp client, the device can use dhcp to obtain parameters such as ip address dynamically from the dhcp server, which facilitates user configuration and management. Refer to “ obtaining ip addres...
Page 439
5-2 how automatic configuration works figure 5-1 network diagram for automatic configuration the switch 4210 supports automatic configuration. The working process is as follows: 1) as shown in the above figure, when the switch starts up, it automatically configures the vlan interface of the default ...
Page 440
5-3 an intermediate file maintains the ip address-to-host name mappings which are created using the ip host hostname ip-address command. When you use this command: z the hostname argument is a character string consisting of letters, digits, “.” and “_” only, which cannot start with “.”. Z you can en...
Page 441
5-4 because a dhcp server can interact with a bootp client, you can use the dhcp server to assign an ip address to the bootp client, without needing to configure any bootp server. Configuring a dhcp/bootp client follow these steps to configure a dhcp/bootp client: operation command description enter...
Page 442
5-5 dhcp client configuration example network requirements using dhcp, vlan-interface 1 of switch a is connected to the lan to obtain an ip address from the dhcp server. Network diagram figure 5-2 a dhcp network configuration procedure the following describes only the configuration on switch a servi...
Page 443: Table of Contents
I table of contents 1 acl configuration·····································································································································1-1 acl overview ···············································································································...
Page 444: Acl Configuration
1-1 1 acl configuration acl overview as the network scale and network traffic are increasingly growing, security control and bandwidth assignment play a more and more important role in network management. Filtering data packets can prevent a network from being accessed by unauthorized users efficien...
Page 445
1-2 depth-first match order for rules of an advanced acl 1) protocol range: a rule which has specified the types of the protocols carried by ip is prior to others. 2) range of source ip address: the smaller the source ip address range (that is, the more the number of zeros in the wildcard mask), the...
Page 446
1-3 z when an acl is directly applied to hardware for packet filtering, the switch will permit packets if the packets do not match the acl. Z when an acl is referenced by upper-layer software to control telnet, snmp and web login users, the switch will deny packets if the packets do not match the ac...
Page 447
1-4 note that: z if only a periodic time section is defined in a time range, the time range is active only when the system time is within the defined periodic time section. If multiple periodic time sections are defined in a time range, the time range is active only when the system time is within on...
Page 449
1-6 advanced acls support analysis and processing of three packet priority levels: type of service (tos) priority, ip priority and differentiated services codepoint (dscp) priority. Using advanced acls, you can define classification rules that are more accurate, more abundant, and more flexible than...
Page 450
1-7 [sysname] acl number 3000 [sysname-acl-adv-3000] rule permit tcp source 129.9.0.0 0.0.255.255 destination-port eq 80 # display the configuration information of acl 3000. [sysname-acl-adv-3000] display acl 3000 advanced acl 3000, 1 rule acl's step is 1 rule 0 permit tcp source 129.9.0.0 0.0.255.2...
Page 451
1-8 configuration example # configure acl 4000 to deny packets sourced from the mac address 000d-88f5-97ed, and with their 802.1p priority being 3. System-view [sysname] acl number 4000 [sysname-acl-ethernetframe-4000] rule deny cos 3 source 000d-88f5-97ed ffff-ffff-ffff # display the configuration ...
Page 452
1-9 operation command description assign an acl globally packet-filter inbound acl-rule required for description on the acl-rule argument, refer to acl command. Configuration example # apply acl 2000 globally to filter the inbound packets on all the ports. System-view [sysname] packet-filter inbound...
Page 453
1-10 configuration procedure table 1-7 apply an acl to a port operation command description enter system view system-view — enter ethernet port view interface interface-type interface-number — apply an acl to the port packet-filter inbound acl-rule required for description on the acl-rule argument, ...
Page 454
1-11 example for upper-layer software referencing acls example for controlling telnet login users by source ip network requirements apply an acl to permit users with the source ip address of 10.110.100.52 to telnet to the switch. Network diagram figure 1-1 network diagram for controlling telnet logi...
Page 455
1-12 configuration procedure # define acl 2001. System-view [sysname] acl number 2001 [sysname-acl-basic-2001] rule 1 permit source 10.110.100.46 0 [sysname-acl-basic-2001] quit # reference acl 2001 to control users logging in to the web server. [sysname] ip http acl 2001 example for applying acls t...
Page 456
1-13 advanced acl configuration example network requirements different departments of an enterprise are interconnected through a switch. The r&d department is connected to ethernet 1/0/1 of the switch. Apply an acl to deny requests from the r&d department and destined for internet (tcp packets with ...
Page 457
1-14 network diagram figure 1-5 network diagram for layer 2 acl configuration procedure # define a periodic time range that is active from 8:00 to 18:00 everyday. System-view [sysname] time-range test 8:00 to 18:00 daily # define acl 4000 to filter packets with the source mac address of 0011-0011-00...
Page 458: Table of Contents
I table of contents 1 qos configuration·····································································································································1-1 overview ···················································································································...
Page 459: Qos Configuration
1-1 1 qos configuration overview introduction to qos quality of service (qos) is a concept concerning service demand and supply. It reflects the ability to meet customer needs. Generally, qos does not focus on grading services precisely, but on improving services under certain conditions. In an inte...
Page 460
1-2 traffic, and setting priority of the packets. To meet those requirements, the network should be provided with better service capability. Major traffic control techniques figure 1-1 end-to-end qos model traffic classification, traffic policing, traffic shaping, congestion management, and congesti...
Page 461
1-3 qos supported by the 4210 series ethernet switches the 4210 series ethernet switches support the qos features listed in table 1-1 . Table 1-1 qos features supported by the 4210 series ethernet switches category features refer to… traffic classification incoming traffic classification based on ac...
Page 462
1-4 priority trust mode precedence types 1) ip precedence, tos precedence, and dscp precedence figure 1-2 ds field and tos byte the tos field in an ip header contains eight bits numbered 0 through 7, among which, z the first three bits indicate ip precedence in the range 0 to 7. Z bit 3 to bit 6 ind...
Page 463
1-5 z best effort (be) class: this class is a special class without any assurance in the cs class. The af class can be degraded to the be class if it exceeds the limit. Current ip network traffic belongs to this class by default. Table 1-3 description on dscp precedence values dscp value (decimal) d...
Page 464
1-6 the 4-byte 802.1q tag header consists of the tag protocol identifier (tpid, two bytes in length), whose value is 0x8100, and the tag control information (tci, two bytes in length). Figure 1-4 describes the detailed contents of an 802.1q tag header. Figure 1-4 802.1q tag headers in the figure abo...
Page 465
1-7 for incoming 802.1q tagged packets, you can configure the switch to trust packet priority with the priority trust command or to trust port priority with the undo priority trust command. By default, the 4210 series switches trust port priority. Z trusting port priority in this mode, the switch re...
Page 466
1-8 dscp local precedence 32 to 47 2 48 to 63 3 priority marking the priority marking function is to reassign priority for the traffic matching an acl referenced for traffic classification. Z if 802.1p priority marking is configured, the traffic will be mapped to the local precedence corresponding t...
Page 467
1-9 figure 1-5 evaluate the traffic with the token bucket evaluating the traffic with the token bucket when token bucket is used for traffic evaluation, the number of the tokens in the token bucket determines the amount of the packets that can be forwarded. If the number of tokens in the bucket is e...
Page 468
1-10 port rate limiting port rate limiting refers to limiting the total rate of inbound or outbound packets on a port. Port rate limiting can be implemented through token buckets. That is, if you perform port rate limiting configuration for a port, the token bucket determines the way to process the ...
Page 469
1-11 service packets are sent preferentially and non-critical service packets are sent when critical service groups are not sent. The disadvantage of sp queue is that: if there are packets in the queues with higher priority for a long time in congestion, the packets in the queues with lower priority...
Page 470
1-12 z large amount of broadcast/multicast packets and large burst traffic exist. Z packets of high-rate links are forwarded to low-rate links or packets of multiple links with the equal rates are forwarded to a single link that is of the same rate as that of the incoming links. Although the burst f...
Page 471
1-13 configuration procedure you can configure to trust port priority or packet priority. Table 1-9 shows the detailed configuration procedure. Table 1-9 configure priority trust mode operation command description enter system view system-view — configure to trust port priority undo priority trust o...
Page 472
1-14 # configure to trust the dscp precedence of the received packets. System-view [sysname] priority trust [sysname] priority-trust dscp # configure to trust the 802.1p priority of the received packets. Approach i: system-view [sysname] priority trust approach ii: system-view [sysname] priority-tru...
Page 473
1-15 [sysname] qos cos-local-precedence-map 0 0 1 1 2 2 3 3 [sysname] display qos cos-local-precedence-map cos-local-precedence-map: cos(802.1p) : 0 1 2 3 4 5 6 7 local precedence(queue) : 0 0 1 1 2 2 3 3 marking packet priority refer to section priority marking for information about marking packet ...
Page 475
1-17 configuration prerequisites z the acl rules used for traffic classification are defined. Refer to the aclmodule of this manual for information about defining acl rules. Z the rate limit for traffic policing, and the actions for the packets exceeding the rate limit are determined. Configuration ...
Page 476
1-18 traffic policing configured on a vlan is only applicable to packets tagged with 802.1q header. Configuration example z ethernet 1/0/1 belongs to vlan 2 and is connected to the 10.1.1.0/24 network segment z perform traffic policing on the packets from the 10.1.1.0/24 network segment, setting the...
Page 477
1-19 configuration example z configure port rate limiting for inbound packets on ethernet 1/0/1. Z the rate limit is 1,024 kbps configuration procedure: system-view [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] line-rate inbound 1024 configuring traffic redirecting refer to section traf...
Page 478
1-20 z the traffic redirecting function configured on a vlan is only applicable to packets tagged with 802.1q header. Z packets redirected to the cpu are not forwarded. Z if the traffic is redirected to a combo port in down state, the system automatically redirects the traffic to the port correspond...
Page 479
1-21 configuration example # adopt the wrr queue scheduling algorithm, with the weight for queue 0, queue 1, queue 2, and queue 3 as 12, 8, 4, and 1. Display the configuration information after configuration. Configuration procedure: system-view [sysname] queue-scheduler wrr 12 8 4 1 [sysname] displ...
Page 480
1-22 table 1-25 generate traffic statistics on packets passing a port and matching specific acl rules operation command description enter system view system-view — enter ethernet port view interface interface-type interface-number — generate the statistics on the packets matching specific acl rules ...
Page 481
1-23 configuration procedure table 1-26 enable the burst function operation command description enter system view system-view — enable the burst function burst-mode enable required by default, the burst function is disabled. Configuration example enable the burst function. Configuration procedure: s...
Page 482
1-24 operation command description destination port interface-number define the current port as the destination port monitor-port required exit current view quit — reference acls for identifying traffic flows and perform traffic mirroring for packets that match. Mirrored-to vlan vlan-id inbound acl-...
Page 483
1-25 [sysname-ethernet1/0/1] mirrored-to inbound ip-group 2000 monitor-interface 2) method ii: configure traffic mirroring for vlan 2 system-view [sysname] acl number 2000 [sysname-acl-basic-2000] rule permit source 10.1.1.0 0.0.0.255 [sysname-acl-basic-2000] quit [sysname] interface ethernet 1/0/4 ...
Page 485
1-27 [sysname] acl number 2001 [sysname-acl-basic-2001] rule permit source 192.168.2.0 0.0.0.255 [sysname-acl-basic-2001] quit 2) configure traffic policing # set the maximum rate of outbound ip packets sourced from the r&d department to 128 kbps. [sysname] interface ethernet 1/0/1 [sysname-ethernet...
Page 486: Qos Profile Configuration
2-1 2 qos profile configuration overview introduction to qos profile qos profile is a set of qos configurations. It provides an easy way for performing and managing qos configuration. A qos profile can contain one or multiple qos actions. In networks where hosts change their positions frequently, yo...
Page 487
2-2 manual application mode you can use the apply command to manually apply a qos profile to a port. Qos profile configuration table 2-1 qos profile configuration tasks operation description related section configure a qos profile required section configuring a qos profile configure to apply a qos p...
Page 488
2-3 configuration prerequisites z to configure to apply a qos profile dynamically, make sure 802.1x is enabled both globally and on the port, and the authentication mode is determined. For information about 802.1x, refer to the 802.1x and system guardmoduleof this manual. Z to apply a qos profile ma...
Page 490
2-5 # set the encryption passwords for the switch to exchange packets with the authentication radius servers and accounting radius servers. [sysname-radius-radius1] key authentication money [sysname-radius-radius1] key accounting money # configure the switch to delete the user domain name from the u...
Page 491: Table of Contents
I table of contents 1 mirroring configuration ····························································································································1-1 mirroring overview ···········································································································...
Page 492: Mirroring Configuration
1-1 1 mirroring configuration mirroring overview mirroring refers to the process of copying packets of one or more ports (source ports) to a destination port which is connected to a data detection device. Users can then use the data detection device to analyze the mirrored packets on the destination...
Page 493
1-2 to implement remote port mirroring, a special vlan, called remote-probe vlan, is needed. All mirrored packets are sent from the reflector port of the source switch to the monitor port (destination port) of the destination switch through the remote-probe vlan, so as to implement the monitoring of...
Page 494
1-3 switch ports involved function trunk port receives remote mirrored packets. Destination switch destination port receives packets forwarded from the trunk port and transmits the packets to the data detection device. Z do not configure a default vlan, a management vlan, or a dynamic vlan as the re...
Page 496
1-5 operation command description configure the current vlan as the remote-probe vlan remote-probe vlan enable required return to system view quit — enter the view of the ethernet port that connects to the intermediate switch or destination switch interface interface-type interface-number — configur...
Page 497
1-6 table 1-5 configuration on the intermediate switch operation command description enter system view system-view — create a vlan and enter vlan view vlan vlan-id vlan-id is the id of the remote-probe vlan. Configure the current vlan as the remote-probe vlan remote-probe vlan enable required return...
Page 498
1-7 operation command description create a remote destination mirroring group mirroring-group group-id remote-destination required configure the destination port for the remote destination mirroring group mirroring-group group-id monitor-port monitor-port required configure the remote-probe vlan for...
Page 499
1-8 network diagram figure 1-3 network diagram for local port mirroring configuration procedure configure switch c: # create a local mirroring group. System-view [sysname] mirroring-group 1 local # configure the source ports and destination port for the local mirroring group. [sysname] mirroring-gro...
Page 500
1-9 the administrator wants to monitor the packets sent from department 1 and 2 through the data detection device. Use the remote port mirroring function to meet the requirement. Perform the following configurations: z use switch a as the source switch, switch b as the intermediate switch, and switc...
Page 501
1-10 [sysname-ethernet1/0/3] port link-type trunk [sysname-ethernet1/0/3] port trunk permit vlan 10 [sysname-ethernet1/0/3] quit # display configuration information about remote source mirroring group 1. [sysname] display mirroring-group 1 mirroring-group 1: type: remote-source status: active mirror...
Page 502
1-11 # display configuration information about remote destination mirroring group 1. [sysname] display mirroring-group 1 mirroring-group 1: type: remote-destination status: active monitor port: ethernet1/0/2 remote-probe vlan: 10 after the configurations, you can monitor all packets sent from depart...
Page 503: Table of Contents
I table of contents 1 cluster ························································································································································1-1 cluster overview··································································································...
Page 504: Cluster
1-1 1 cluster cluster overview introduction to hgmp a cluster contains a group of switches. Through cluster management, you can manage multiple geographically dispersed in a centralized way. Cluster management is implemented through huawei group management protocol (hgmp). Hgmp version 2 (hgmpv2) is...
Page 505
1-2 you can configure and manage all the member devices through the management device without the need to log onto them one by one. Z it provides the topology discovery and display function, which assists in monitoring and maintaining the network. Z it allows you to configure and upgrade multiple sw...
Page 506
1-3 figure 1-2 state machine of cluster role z a candidate device becomes a management device when you create a cluster on it. Note that a cluster must have one (and only one) management device. On becoming a management device, the device collects network topology information and tries to discover a...
Page 507
1-4 z the management device adds the candidate devices to the cluster or removes member devices from the cluster according to the candidate device information collected through ntdp. Introduction to ndp ndp is a protocol used to discover adjacent devices and provide information about them. Ndp opera...
Page 508
1-5 device busy processing of the ntdp topology collection responses. To avoid such cases, the following methods can be used to control the ntdp topology collection request advertisement speed. Z configuring the devices not to forward the ntdp topology collection request immediately after they recei...
Page 509
1-6 to create a cluster, you need to determine the device to operate as the management device first. The management device discovers and determines candidate devices through ndp and ntdp, and adds them to the cluster. You can also add candidate devices to a cluster manually. After a candidate device...
Page 510
1-7 additionally, on the management device, you can configure the ftp server, tftp server, logging host and snmp host to be shared by the whole cluster. When a member device in the cluster communicates with an external server, the member device first transmits data to the management device, which th...
Page 511
1-8 1) determine whether the destination mac address or destination ip address is used to trace a device in the cluster z if you use the tracemac command to trace the device by its mac address, the switch will query its mac address table according to the mac address and vlan id in the command to fin...
Page 512
1-9 configuration task remarks configuring the cluster synchronization function optional configuring the management device management device configuration tasks complete the following tasks to configure management device: task remarks enabling ndp globally and on specific ports required configuring ...
Page 513
1-10 operation command description enter ethernet port view interface interface-type interface-number specified ethernet ports in ethernet port view enable ndp on the port ndp enable enabled on a port. Configuring ndp-related parameters follow these steps to configure ndp-related parameters: operati...
Page 514
1-11 operation command description configure the port forward delay of topology collection requests ntdp timer port-delay time optional by default, the port forward delay is 20 ms. Configure the interval to collect topology information periodically ntdp timer interval-in-minutes optional by default,...
Page 515
1-12 operation command description set the interval for the management device to send multicast packets cluster-mac syn-interval time-interval optional by default, the interval to send multicast packets is one minutes. Set the holdtime of member switches holdtime seconds optional by default, the hol...
Page 516
1-13 operation command description configure a shared tftp server for the cluster tftp-server ip-address optional by default, no shared tftp server is configured. Configure a shared logging host for the cluster logging-host ip-address optional by default, no shared logging host is configured. Config...
Page 517
1-14 to reduce the risk of being attacked by malicious users against opened socket and enhance switch security, the switch 4210 series ethernet switches provide the following functions, so that a cluster socket is opened only when it is needed: z opening udp port 40000 (used for cluster) only when t...
Page 518
1-15 operation command description enter ethernet port view interface interface-type interface-number — enable ntdp on the port ntdp enable required enabling the cluster function follow these steps to enable the cluster function: operation command description enter system view system-view — enable t...
Page 519
1-16 operation command description enter system view system-view — enter cluster view cluster — configuring mac address of management device administrator-address mac-address name name optional add a candidate device to the cluster add-member [ member-number ] mac-address h-h-h [ password password ]...
Page 520
1-17 the topology information is saved as a topology.Top file in the flash memory to the administrative device. You cannot specify the file name manually. 2) cluster device blacklist function to ensure stability and security of the cluster, you can use the blacklist to restrict the devices to be add...
Page 522
1-19 snmp configuration synchronization with this function, you can configure the public snmp community name, snmp group, snmp users and mib views. These configurations will be synchronized to the member devices of the cluster automatically, which not only simplifies the configurations on the member...
Page 523
1-20 z perform the above operations on the management device of the cluster. Z configuring the public snmp information is equal to executing these configurations on both the management device and the member devices (refer to the snmp-rmon operation part in this manual), and these configurations will...
Page 524
1-21 member 2 succeeded in the usm-user configuration. Member 1 succeeded in the usm-user configuration. Finish to synchronize the command. # after the above configuration, you can see that the public snmp configurations for the cluster are saved to the management device and member devices by viewin...
Page 525
1-22 z a cluster is established, and you can manage the member devices through the management device. 2) configuration procedure perform the following operations on the management device to synchronize local user configurations: to do… use the command… remarks enter system view system-view — enter c...
Page 526
1-23 operation command description clear the statistics on ndp ports reset ndp statistics [ interface port-list ] you can execute the reset command in user view. When you display the cluster topology information, the devices attached to the switch that is listed in the backlist will not be displayed...
Page 527
1-24 network diagram figure 1-4 network diagram for hgmp cluster configuration network ftp server/tftp server snmp host/logging host 63.172.55.1/24 69.172.55.4/24 eth1/0/1 vlan-int2 163.172.55.1/24 eth1/0/3 eth1/0/2 eth1/0/1 eth1/0/1 member switch mac:000f.E001.0011 member switch mac: 000f.E001.0012...
Page 528
1-25 # set the holdtime of ndp information to 200 seconds. [sysname] ndp timer aging 200 # set the interval to send ndp packets to 70 seconds. [sysname] ndp timer hello 70 # enable ntdp globally and on ethernet 1/0/2 and ethernet 1/0/3. [sysname] ntdp enable [sysname] interface ethernet 1/0/2 [sysna...
Page 529
1-26 [aaa_0.Sysname-cluster] tftp-server 63.172.55.1 [aaa_0.Sysname-cluster] logging-host 69.172.55.4 [aaa_0.Sysname-cluster] snmp-host 69.172.55.4 3) perform the following operations on the member devices (taking one member as an example) after adding the devices under the management device to the ...
Page 530
1-27 network diagram figure 1-5 network diagram for the enhanced cluster feature configuration configuration procedure # enter cluster view. System-view [aaa_0.Sysname] cluster # add the mac address 0001-2034-a0e5 to the cluster blacklist. [aaa_0.Sysname-cluster] black-list add-mac 0001-2034-a0e5 # ...
Page 531: Table of Contents
I table of contents 1 poe configuration ·····································································································································1-1 poe overview ··············································································································...
Page 532: Poe Configuration
1-1 1 poe configuration poe overview introduction to poe power over ethernet (poe)-enabled devices use twisted pairs through electrical ports to supply power to the remote powered devices (pd) in the network and implement power supply and data transmission simultaneously. Advantages of poe z reliabi...
Page 533
1-2 switch input power supply number of electrical ports supplying power maximum poe distance maximum power provided by each electrical port total maximum poe output power switch 4210 pwr 18-port ac input 16 135 w dc input 400 w switch 4210 pwr 26-port ac input 24 370 w a poe-enabled switch 4210 has...
Page 534
1-3 z when you use the poe-enabled switch 4210 to supply power, the pds need no external power supply. Z if a remote pd has an external power supply, the poe-enabled switch 4210 and the external power supply will backup each other for the pd. Z only the 100 mbps ethernet electrical ports of the poe-...
Page 535
1-4 z by default, the poe function on a port is enabled by the default configuration file config.Def when the device is delivered. Z if you delete the default configuration file without specifying another one, the poe function on a port will be disabled after you restart the device. Setting the maxi...
Page 537
1-6 configuring poe over-temperature protection on the switch if this function is enabled, the switch disables the poe feature on all ports when its internal temperature exceeds 65°c (149°f) for self-protection, and restores the poe feature settings on all its ports when the temperature drops below ...
Page 538
1-7 z in the case that the pse processing software is damaged (that is, no poe command can be executed successfully), use the full update mode to upgrade and thus restore the software. Z the refresh update mode is to upgrade the original processing software in the pse through refreshing the software...
Page 539
1-8 networking diagram figure 1-1 network diagram for poe switch a network eth1/0/2 eth1/0/1 eth1/0/8 switch b ap ap configuration procedure # upgrade the pse processing software online. System-view [switcha] poe update refresh 0290_021.S19 # enable the poe feature on ethernet 1/0/1, and set the poe...
Page 540: Poe Profile Configuration
2-1 2 poe profile configuration introduction to poe profile on a large-sized network or a network with mobile users, to help network administrators to monitor the poe features of the switch, switch 4210 provide the poe profile features. A poe profile is a set of poe configurations, including multipl...
Page 541
2-2 operation command description in system view apply poe-profile profile-name interface interface-type interface-number [ to interface-type interface-number ] enter ethernet port view interface interface-type interface-number apply the existing poe profile to the specified ethernet port in etherne...
Page 542
2-3 ethernet 1/0/1 through ethernet 1/0/10 of switch a are used by users of group a, who have the following requirements: z the poe function can be enabled on all ports in use. Z signal mode is used to supply power. Z the poe priority for ethernet 1/0/1 through ethernet 1/0/5 is critical, whereas th...
Page 543
2-4 # display detailed configuration information for profile1. [switcha] display poe-profile name profile1 poe-profile: profile1, 3 action poe enable poe max-power 3000 poe priority critical # create profile2, and enter poe profile view. [switcha] poe-profile profile2 # in profile2, add the poe poli...
Page 544: Table of Contents
I table of contents 1 snmp configuration··································································································································1-1 snmp overview·················································································································...
Page 545: Snmp Configuration
1-1 1 snmp configuration snmp overview the simple network management protocol (snmp) is used for ensuring the transmission of the management information between any two network nodes. In this way, network administrators can easily retrieve and modify the information about any node on the network. In...
Page 546
1-2 adopts a hierarchical naming scheme to organize the managed objects. It is like a tree, with each tree node representing a managed object, as shown in figure 1-1 . Each node in this tree can be uniquely identified by a path starting from the root. Figure 1-1 architecture of the mib tree a 2 6 1 ...
Page 549
1-5 operation command description enable the port or interface to send trap messages enable snmp trap updown send trap messages quit to system view quit set the destination for trap messages snmp-agent target-host trap address udp-domain { ip-address } [ udp-port port-number ] params securityname se...
Page 550
1-6 use the display logbuffer command to view the log of the get and set operations requested by the nms. Displaying snmp after the above configuration, you can execute the display command in any view to view the running status of snmp, and to verify the configuration. Table 1-6 display snmp operati...
Page 551
1-7 network diagram figure 1-2 network diagram for snmp configuration network procedure # enable snmp agent, and set the snmpv1 and snmpv2c community names. System-view [sysname] snmp-agent [sysname] snmp-agent sys-info version all [sysname] snmp-agent community read public [sysname] snmp-agent comm...
Page 552
1-8 [sysname] snmp-agent target-host trap address udp-domain 10.10.10.1 udp-port 5000 params securityname public configuring the nms you can query and configure an ethernet switch through the nms. For more information, refer to the corresponding manuals of nms products. Authentication-related config...
Page 553: Rmon Configuration
2-1 2 rmon configuration introduction to rmon remote monitoring (rmon) is a kind of management information base (mib) defined by internet engineering task force (ietf). It is an important enhancement made to mib ii standards. Rmon is mainly used to monitor the data traffic across a network segment o...
Page 554
2-2 commonly used rmon groups event group event group is used to define the indexes of events and the processing methods of the events. The events defined in an event group are mainly used by entries in the alarm group and extended alarm group to trigger alarms. You can specify a network device to a...
Page 555
2-3 the statistics include the number of the following items: collisions, packets with cyclic redundancy check (crc) errors, undersize (or oversize) packets, broadcast packets, multicast packets, and received bytes and packets. With the rmon statistics management function, you can monitor the use of...
Page 556
2-4 displaying rmon after the above configuration, you can execute the display command in any view to display the rmon running status, and to verify the configuration. Table 2-2 display rmon operation command description display rmon statistics display rmon statistics [ interface-type interface-numb...
Page 557
2-5 # add an entry numbered 2 to the extended alarm table to allow the system to calculate the alarm variables with the (.1.3.6.1.2.1.16.1.1.1.9.1+.1.3.6.1.2.1.16.1.1.1.10.1) formula to get the numbers of all the oversize and undersize packets received by ethernet 1/0/1 that are in correct data form...
Page 558: Table of Contents
I table of contents 1 ntp configuration ·····································································································································1-1 introduction to ntp ·······································································································...
Page 559: Ntp Configuration
1-1 1 ntp configuration introduction to ntp network time protocol (ntp) is a time synchronization protocol defined in rfc 1305. It is used for time synchronization between a set of distributed time servers and clients. Carried over udp, ntp transmits packets through udp port 123. Ntp is intended for...
Page 560
1-2 z the clock stratum determines the accuracy, which ranges from 1 to 16. The stratum of a reference clock ranges from 1 to 15. The clock accuracy decreases as the stratum number increases. A stratum 16 clock is in the unsynchronized state and cannot serve as a reference clock. Z the local clock o...
Page 561
1-3 z when the message arrives at device b, device b inserts its own timestamp 11:00:01 am (t 2 ) into the packet. Z when the ntp message leaves device b, device b inserts its own timestamp 11:00:02 am (t 3 ) into the packet. Z when receiving a response packet, the local time of device a is 10:00:03...
Page 562
1-4 in the symmetric peer mode, the local switch 4210 serves as the symmetric-active peer and sends clock synchronization request first, while the remote server serves as the symmetric-passive peer automatically. If both of the peers have reference clocks, the one with a smaller stratum number is ad...
Page 563
1-5 ntp implementation mode configuration on switch 4210 multicast mode z configure the local switch 4210 to work in ntp multicast server mode. In this mode, the local switch sends multicast ntp messages through the vlan interface configured on the switch. Z configure the local switch 4210 to work i...
Page 564
1-6 z udp port 123 is opened only when the ntp feature is enabled. Z udp port 123 is closed as the ntp feature is disabled. These functions are implemented as follows: z execution of one of the ntp-service unicast-server, ntp-service unicast-peer, ntp-service broadcast-client, ntp-service broadcast-...
Page 566
1-8 configuring a switch to work in the ntp broadcast server mode table 1-5 configure a switch to work in the ntp broadcast server mode operation command description enter system view system-view — enter vlan interface view interface vlan-interface vlan-id — configure the switch to work in the ntp b...
Page 567
1-9 z a multicast server can synchronize multicast clients only after its clock has been synchronized. Z a switch 4210 working in the multicast server mode supports up to 1,024 multicast clients. Configuring a switch to work in the multicast server mode table 1-7 configure a switch to work in the nt...
Page 568
1-10 from the highest ntp service access-control right to the lowest one are peer, server, synchronization, and query. When a device receives an ntp request, it will perform an access-control right match in this order and use the first matched right. Configuration prerequisites prior to configuring ...
Page 569
1-11 configuration prerequisites ntp authentication configuration involves: z configuring ntp authentication on the client z configuring ntp authentication on the server observe the following principles when configuring ntp authentication: z if the ntp authentication function is not enabled on the c...
Page 570
1-12 ntp authentication requires that the authentication keys configured for the server and the client be the same. Besides, the authentication keys must be trusted keys. Otherwise, the clock of the client cannot be synchronized with that of the server. Configuring ntp authentication on the server t...
Page 571
1-13 configuring optional ntp parameters table 1-13 optional ntp parameters configuration tasks task remarks configuring an interface on the local switch to send ntp messages optional configuring the number of dynamic sessions allowed on the local switch optional disabling an interface from receivin...
Page 572
1-14 operation command description configure the maximum number of dynamic sessions that can be established on the local switch ntp-service max-dynamic-sessions number required by default, up to 100 dynamic sessions can be established locally. Disabling an interface from receiving ntp messages table...
Page 573
1-15 network diagram figure 1-6 network diagram for the ntp server/client mode configuration configuration procedure perform the following configurations on device b. # view the ntp status of device b before synchronization. Display ntp-service status clock status: unsynchronized clock stratum: 16 r...
Page 574
1-16 source reference stra reach poll now offset delay disper ************************************************************************** [12345]1.0.1.11 127.127.1.0 2 1 64 1 350.1 15.1 0.0 note: 1 source(master),2 source(peer),3 selected,4 candidate,5 configured total associations : 1 configuring nt...
Page 575
1-17 [devicec] display ntp-service status clock status: synchronized clock stratum: 2 reference clock id: 3.0.1.32 nominal frequency: 100.0000 hz actual frequency: 100.0000 hz clock precision: 2^18 clock offset: 0.66 ms root delay: 27.47 ms root dispersion: 208.39 ms peer dispersion: 9.63 ms referen...
Page 576
1-18 network diagram figure 1-8 network diagram for the ntp broadcast mode configuration vlan-int2 1.0.1.31/24 vlan-int2 3.0.1.31/24 vlan-int2 3.0.1.32/24 device a device b device c device d configuration procedure 1) configure device c. # enter system view. System-view # set device c as the broadca...
Page 577
1-19 root dispersion: 208.39 ms peer dispersion: 9.63 ms reference time: 17:03:32.022 utc apr 2 2007 (bf422ae4.05aea86c) the output information indicates that device d is synchronized to device c, with the clock stratum level of 3, one level lower than that of device c. # view the information about ...
Page 578
1-20 [devicec-vlan-interface2] ntp-service multicast-server 2) configure device a (perform the same configuration on device d). # enter system view. System-view # set device a as a multicast client to listen to multicast messages through vlan-interface2. [devicea] interface vlan-interface 2 [devicea...
Page 579
1-21 network diagram figure 1-10 network diagram for ntp server/client mode with authentication configuration configuration procedure 1) configure device b. # enter system view. System-view # enable the ntp authentication function. [deviceb] ntp-service authentication enable # configure an md5 authe...
Page 580
1-22 root dispersion: 208.39 ms peer dispersion: 9.63 ms reference time: 17:03:32.022 utc apr 2 2007 (bf422ae4.05aea86c) the output information indicates that the clock of device b is synchronized to that of device a, with a clock stratum level of 3, one stratum level lower than that device a. # vie...
Page 581: Table of Contents
I table of contents 1 ssh configuration·····································································································································1-1 ssh overview················································································································...
Page 582: Ssh Configuration
1-1 1 ssh configuration when configuring ssh, go to these sections for information you are interested: z ssh overview z ssh server and client configuration task list z displaying and maintaining ssh configuration z comparison of ssh commands with the same functions z ssh configuration examples ssh o...
Page 583
1-2 figure 1-1 encryption and decryption key-based algorithm is usually classified into symmetric key algorithm and asymmetric key algorithm. Asymmetric key algorithm asymmetric key algorithm means that a key pair exists at both ends. The key pair consists of a private key and a public key. The publ...
Page 584
1-3 version negotiation z the server opens port 22 to listen to connection requests from clients. Z the client sends a tcp connection request to the server. After the tcp connection is established, the server sends the first packet to the client, which includes a version identification string in the...
Page 585
1-4 z in password authentication, the client encrypts the username and password, encapsulates them into a password authentication request, and sends the request to the server. Upon receiving the request, the server decrypts the username and password, compares them with those it maintains, and then i...
Page 586
1-5 table 1-2 complete the following tasks to configure the ssh server: task remarks configuring the user interfaces for ssh clients required preparation configuring the ssh management functions optional version configuring the ssh server to be compatible with ssh1 clients optional this task determi...
Page 587
1-6 table 1-3 follow these steps to configure the user interface for ssh clients: to do... Use the command... Remarks enter system view system-view — enter user interface view of one or more user interfaces user-interface vty first-number [ last-number ] — configure the authentication mode as scheme...
Page 588
1-7 z you can configure a login header only when the service type is stelnet. For configuration of service types, refer to specifying a service type for an ssh user . Z for details of the header command, refer to the corresponding section in login command. Configuring the ssh server to be compatible...
Page 589
1-8 z the ssh server’s key pairs are for generating session keys and for ssh clients to authenticate the server. As different clients may support different public key algorithms, the server may use different key pair for negotiation with different clients. Therefore, you need to generate both rsa an...
Page 590
1-9 z for password authentication type, the username argument must be consistent with the valid user name defined in aaa; for publickey authentication, the username argument is the ssh local user name, so that there is no need to configure a local user in aaa. Z if the default authentication type fo...
Page 591
1-10 this configuration is not necessary if the password authentication mode is configured for ssh users. With the publickey authentication mode configured for an ssh client, you must configure the client’s rsa or dsa host public key(s) on the server for authentication. You can manually configure th...
Page 592
1-11 this configuration task is unnecessary if the ssh user’s authentication mode is password. For the publickey authentication mode, you must specify the client’s public key on the server for authentication. Table 1-10 follow these steps to assign a public key for an ssh user: to do... Use the comm...
Page 593
1-12 configuring the ssh client the configurations required on the ssh client are related to the authentication mode that the ssh server uses. In addition, if an ssh client does not support first-time authentication, you need to configure the public key of the server on the client, so that the clien...
Page 594
1-13 z selecting the protocol for remote connection as ssh. Usually, a client can use a variety of remote connection protocols, such as telnet, rlogin, and ssh. To establish an ssh connection, you must select ssh z selecting the ssh version. Since the device supports ssh2.0 now, select 2.0 or lower ...
Page 595
1-14 figure 1-3 generate the client keys (2) after the key pair is generated, click save public key and enter the name of the file for saving the public key (public in this case) to save the public key. Figure 1-4 generate the client keys (3).
Page 596
1-15 likewise, to save the private key, click save private key. A warning window pops up to prompt you whether to save the private key without any precaution. Click yes and enter the name of the file for saving the private key (“private” in this case) to save the private key. Figure 1-5 generate the...
Page 597
1-16 figure 1-7 ssh client configuration interface 1 in the host name (or ip address) text box, enter the ip address of the server. Note that there must be a route available between the ip address of the server and the client. Selecting a protocol for remote connection as shown in figure 1-7 , selec...
Page 598
1-17 figure 1-8 ssh client configuration interface 2 under protocol options, select 2 from preferred ssh protocol version. Some ssh client software, for example, tectia client software, supports the des algorithm only when the ssh1 version is selected. The putty client software supports des algorith...
Page 599
1-18 figure 1-9 ssh client configuration interface 3 click browse… to bring up the file selection window, navigate to the private key file and click open. If the connection is normal, a user will be prompted for a username. Once passing the authentication, the user can log in to the server. Configur...
Page 600
1-19 configuring whether first-time authentication is supported when the device connects to the ssh server as an ssh client, you can configure whether the device supports first-time authentication. Z with first-time authentication enabled, an ssh client that is not configured with the server host pu...
Page 603
1-22 network diagram figure 1-10 switch acts as server for local password authentication configuration procedure z configure the ssh server # create a vlan interface on the switch and assign an ip address, which the ssh client will use as the destination for ssh connection. System-view [switch] inte...
Page 604
1-23 # configure the ssh client software to establish a connection to the ssh server. Take ssh client software putty (version 0.58) as an example: 1) run putty.Exe to enter the following configuration interface. Figure 1-11 ssh client configuration interface in the host name (or ip address) text box...
Page 605
1-24 figure 1-12 ssh client configuration interface 2 under protocol options, select 2 from preferred ssh protocol version. 3) as shown in figure 1-12 , click open. If the connection is normal, you will be prompted to enter the user name client001 and password abc. Once authentication succeeds, you ...
Page 606
1-25 network diagram figure 1-13 switch acts as server for password and radius authentication configuration procedure 1) configure the radius server this document takes cams version 2.10 as an example to show the basic radius server configurations required. # add an access device. Log into the cams ...
Page 607
1-26 figure 1-14 add an access device # add a user for device management. From the navigation tree, select user management > user for device management, and then in the right pane, click add to enter the add account window and perform the following configurations: z add a user named hello, and speci...
Page 608
1-27 generating the rsa and dsa key pairs on the server is prerequisite to ssh login. # generate rsa and dsa key pairs. [switch] public-key local create rsa [switch] public-key local create dsa # set the authentication mode for the user interfaces to aaa. [switch] user-interface vty 0 4 [switch-ui-v...
Page 609
1-28 figure 1-16 ssh client configuration interface (1) in the host name (or ip address) text box, enter the ip address of the ssh server. Z from the category on the left pane of the window, select connection > ssh. The window as shown in figure 1-17 appears. Figure 1-17 ssh client configuration int...
Page 610
1-29 authentication succeeds, you will log in to the server. The level of commands that you can access after login is authorized by the cams server. You can specify the level by setting the exec privilege level argument in the add account window shown in figure 1-15 . When switch acts as server for ...
Page 611
1-30 [switch-ui-vty0-4] authentication-mode scheme # enable the user interfaces to support ssh. [switch-ui-vty0-4] protocol inbound ssh [switch-ui-vty0-4] quit # configure the hwtacacs scheme. [switch] hwtacacs scheme hwtac [switch-hwtacacs-hwtac] primary authentication 10.1.1.1 49 [switch-hwtacacs-...
Page 612
1-31 2) from the category on the left pane of the window, select connection > ssh. The window as shown in figure 1-20 appears. Figure 1-20 ssh client configuration interface (2) under protocol options, select 2 from preferred ssh protocol version. Then, click open. If the connection is normal, you w...
Page 613
1-32 configuration procedure under the publickey authentication mode, either the rsa or dsa public key can be generated for the server to authenticate the client. Here takes the rsa public key as an example. Z configure the ssh server # create a vlan interface on the switch and assign an ip address,...
Page 614
1-33 # import the client’s public key named switch001 from file public. [switch] public-key peer switch001 import sshkey public # assign the public key switch001 to client client001. [switch] ssh user client001 assign publickey switch001 z configure the ssh client (taking putty version 0.58 as an ex...
Page 615
1-34 figure 1-23 generate a client key pair (2) after the key pair is generated, click save public key and enter the name of the file for saving the public key (public in this case). Figure 1-24 generate a client key pair (3).
Page 616
1-35 likewise, to save the private key, click save private key. A warning window pops up to prompt you whether to save the private key without any protection. Click yes and enter the name of the file for saving the private key (private.Ppk in this case). Figure 1-25 generate a client key pair (4) af...
Page 617
1-36 figure 1-27 ssh client configuration interface 2 under protocol options, select 2 from preferred ssh protocol version. 4) select connection/ssh/auth.The following window appears. Figure 1-28 ssh client configuration interface (2).
Page 618
1-37 click browse… to bring up the file selection window, navigate to the private key file and click ok. 5) from the window shown in figure 1-28 , click open. If the connection is normal, you will be prompted to enter the username. When switch acts as client for password authentication network requi...
Page 619
1-38 [switchb] local-user client001 [switchb-luser-client001] password simple abc [switchb-luser-client001] service-type ssh level 3 [switchb-luser-client001] quit # configure the authentication type of user client001 as password. [switchb] ssh user client001 authentication-type password z configure...
Page 620
1-39 configuration procedure in public key authentication, you can use either rsa or dsa public key. Here takes the dsa public key as an example. Z configure switch b # create a vlan interface on the switch and assign an ip address, which the ssh client will use as the destination for ssh connection...
Page 621
1-40 # import the client public key pair named switch001 from the file switch001. [switchb] public-key peer switch001 import sshkey switch001 # assign the public key switch001 to user client001. [switchb] ssh user client001 assign publickey switch001 z configure switch a # create a vlan interface on...
Page 622
1-41 when switch acts as client and first-time authentication is not supported network requirements as shown in figure 1-31 , establish an ssh connection between switch a (ssh client) and switch b (ssh server) for secure data exchange. The user name is client001 and the ssh server’s ip address is 10...
Page 623
1-42 before doing the following steps, you must first generate a dsa key pair on the client and save the key pair in a file named switch001, and then upload the file to the ssh server through ftp or tftp. For details, refer to the following “configure switch a”. # import the client’s public key file...
Page 624
1-43 when first-time authentication is not supported, you must first generate a dsa key pair on the server and save the key pair in a file named switch002, and then upload the file to the ssh client through ftp or tftp. For details, refer to the above part “configure switch b”. # import the public k...
Page 625: Table of Contents
I table of contents 1 file system management configuration ·································································································1-1 file system configuration ··················································································································...
Page 626
1-1 1 file system management configuration file system configuration introduction to file system to facilitate management on the switch memory, switch 4210 provide the file system function, allowing you to access and manage the files and directories. You can create, remove, copy or delete a file thr...
Page 627
1-2 table 1-2 directory operations to do… use the command… remarks create a directory mkdir directory optional delete a directory rmdir directory optional display the current work directory pwd optional display the information about specific directories and files dir [ /all ] [ file-url ] optional e...
Page 628
1-3 to do… use the command… remarks enter system view system-view — execute the specified batch file execute filename optional this command should be executed in system view. Z for deleted files whose names are the same, only the latest deleted file is kept in the recycle bin and can be restored. Z ...
Page 630
1-5 (*b) -with both main and backup attribute dir unit1>flash:/test/ directory of unit1>flash:/test/ 1 -rw- 1235 apr 05 2000 01:51:34 test.Cfg 2 -rw- 1235 apr 05 2000 01:56:44 1.Cfg 7239 kb total (3585 kb free) (*) -with main attribute (b) -with backup attribute (*b) -with both main and backup attri...
Page 631
1-6 with the main attribute in the flash memory will lose its main attribute. This circumstance also applies to the file with the backup attribute in the flash memory. File operations and file attribute operations are independent. For example, if you delete a file with the main attribute from the fl...
Page 632
1-7 to do… use the command… remarks specify to enable user to use the customized password to enter the boot menu startup bootrom-access enable optional by default, the user is enabled to use the customized password to enter the boot menu. Display the information about the app file used as the startu...
Page 633: Table of Contents
I table of contents 1 ftp and sftp configuration····················································································································1-1 introduction to ftp and sftp ·······································································································...
Page 634: Ftp and Sftp Configuration
1-1 1 ftp and sftp configuration introduction to ftp and sftp introduction to ftp ftp (file transfer protocol) is commonly used in ip-based networks to transmit files. Before world wide web comes into being, files are transferred through command lines, and the most popular application is ftp. At pre...
Page 635
1-2 ftp configuration table 1-2 ftp configuration tasks item configuration task description creating an ftp user required enabling an ftp server required configuring connection idle time optional disconnecting a specified user optional configuring the banner for an ftp server optional ftp configurat...
Page 636
1-3 z only one user can access a switch 4210 at a given time when the latter operates as an ftp server. Z operating as an ftp server, a switch 4210 cannot receive a file whose size exceeds its storage space. The clients that attempt to upload such a file will be disconnected with the ftp server due ...
Page 637
1-4 with a switch 4210 acting as the ftp server, if a network administrator attempts to disconnect a user that is uploading/downloading data to/from the ftp server the switch 4210 will disconnect the user after the data transmission is completed. Configuring the banner for an ftp server displaying a...
Page 638
1-5 table 1-7 configure the banner display for an ftp server operation command description enter system view system-view — configure a login banner header login text configure a shell banner header shell text required use either command or both. By default, no banner is configured. For details about...
Page 639
1-6 operation command description change the working directory on the remote ftp server cd pathname change the working directory to be the parent directory cdup get the local working path on the ftp client lcd display the working directory on the ftp server pwd create a directory on the remote ftp s...
Page 640
1-7 configuration example: a switch operating as an ftp server network requirements a switch operates as an ftp server and a remote pc as an ftp client. The application switch.Bin of the switch is stored on the pc. Upload the application to the remote switch through ftp and use the boot boot-loader ...
Page 641
1-8 connected to 1.1.1.1. 220 ftp service ready. User (1.1.1.1:(none)): switch 331 password required for switch. Password: 230 user logged in. Ftp> # upload the switch.Bin file. Ftp> put switch.Bin 200 port command okay. 150 opening ascii mode data connection for switch.Bin. 226 transfer complete. F...
Page 642
1-9 for information about the boot boot-loader command and how to specify the startup file for a switch, refer to the system maintenance and debugging part of this manual. Ftp banner display configuration example network requirements configure the ethernet switch as an ftp server and the remote pc a...
Page 643
1-10 331 password required for switch. Password: 230-shell banner appears 230 user logged in. Ftp> ftp configuration: a switch operating as an ftp client network requirements a switch operates as an ftp client and a remote pc as an ftp server. The switch application named switch.Bin is stored on the...
Page 644
1-11 # connect to the ftp server using the ftp command in user view. You need to provide the ip address of the ftp server, the user name and the password as well to enter ftp view. Ftp 2.2.2.2 trying ... Press ctrl+k to abort connected. 220 ftp service ready. User(none):switch 331 password required ...
Page 645
1-12 item configuration task description sftp configuration: a switch operating as an sftp client basic configurations on an sftp client — sftp configuration: a switch operating as an sftp server enabling an sftp server before enabling an sftp server, you need to enable the ssh server function and s...
Page 646
1-13 z currently a switch 4210 operating as an sftp server supports the connection of only one sftp user. When multiple users attempt to log in to the sftp server or multiple connections are enabled on a client, only the first user can log in to the sftp user. The subsequent connection will fail. Z ...
Page 648
1-15 configuration procedure 1) configure the sftp server (switch b) # create key pairs. System-view [sysname] public-key local create rsa [sysname] public-key local create dsa # create a vlan interface on the switch and assign to it an ip address, which is used as the destination address for the cl...
Page 649
1-16 connected to 192.168.0.1 ... The server is not authenticated. Do you continue to access it?(y/n):y do you want to save the server's public key?(y/n):n enter password: sftp-client> # display the current directory of the server. Delete the file z and verify the result. Sftp-client> dir -rwxrwxrwx...
Page 650
1-17 # rename the directory new1 as new2, and then verify the result. Sftp-client> rename new1 new2 file successfully renamed sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 aug 23 06:52 config.Cfg -rwxrwxrwx 1 noone nogroup 225 aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubke...
Page 651: Tftp Configuration
2-1 2 tftp configuration introduction to tftp compared with ftp, tftp (trivial file transfer protocol) features simple interactive access interface and no authentication control. Therefore, tftp is applicable in the networks where client-server interactions are relatively simple. Tftp is implemented...
Page 652
2-2 item configuration task description tftp server configuration for details, see the corresponding manual — tftp configuration: a switch operating as a tftp client basic configurations on a tftp client by default a switch can operate as a tftp client. In this case you can connect the switch to the...
Page 653
2-3 configuration procedure 1) configure the tftp server (pc) start the tftp server and configure the working directory on the pc. 2) configure the tftp client (switch). # log in to the switch. (you can log in to a switch through the console port or by telnetting the switch. See the “login” module f...
Page 654: Table of Contents
I table of contents 1 information center·····································································································································1-1 information center overview ·······························································································...
Page 655: Information Center
1-1 1 information center information center overview introduction to information center acting as the system information hub, information center classifies and manages system information. Together with the debugging function (the debugging command), information center offers a powerful support for n...
Page 656
1-2 ten channels and six output directions of system information the system supports six information output directions, including the console, monitor terminal (monitor), logbuffer, loghost, trapbuffer and snmp. The system supports ten channels. The channels 0 through 5 have their default channel na...
Page 657
1-3 module name description acl access control list module adbm address base module am access management module arp address resolution protocol module cmd command line module dev device management module dns domain name system module eth ethernet module fib forwarding module ftm fabric topology mana...
Page 658
1-4 module name description telnet telnet module tftpc tftp client module vlan virtual local area network module vty virtual type terminal module xm xmodem module default default settings for all the modules to sum up, the major task of the information center is to output the three types of informat...
Page 659
1-5 z if the address of the log host is specified in the information center of the switch, when logs are generated, the switch sends the logs to the log host in the above format. For detailed information, refer to setting to output system information to a log host . Z there is the syslog process on ...
Page 660
1-6 locate and solve problems globally. In this case, you can configure the information center to add utc time zone to the time stamp of the output information, so that you can know the standard time when the information center processing each piece of information. That is, you can know the greenwic...
Page 661
1-7 source this field indicates the source of the information, such as the source ip address of the log sender. This field is optional and is displayed only when the output destination is the log host. Context this field provides the content of the system information. Information center configuratio...
Page 662
1-8 z if the system information is output before you input any information following the current command line prompt, the system does not echo any command line prompt after the system information output. Z in the interaction mode, you are prompted for some information input. If the input is interrup...
Page 664
1-10 enabling system information display on the console after setting to output system information to the console, you need to enable the associated display function to display the output information on the console. Table 1-9 enable the system information display on the console: operation command de...
Page 666
1-12 setting to output system information to a log host table 1-12 set to output system information to a log host operation command description enter system view system-view — enable the information center info-center enable optional enabled by default. Enable system information output to a log host...
Page 669
1-15 operation command description clear information recorded in the log buffer reset logbuffer [ unit unit-id ] clear information recorded in the trap buffer reset trapbuffer [ unit unit-id ] available in user view information center configuration examples log output to a unix log host network requ...
Page 670
1-16 # switch configuration messages local4.Info /var/log/switch/information when you edit the file “/etc/syslog.Conf”, note that: z a note must start in a new line, starting with a “#” sign. Z in each pair, a tab should be used as a separator instead of a space. Z no space is allowed at the end of ...
Page 671
1-17 configuration procedure 1) configure the switch: # enable the information center. System-view [switch] info-center enable # configure the host whose ip address is 202.38.1.10 as the log host. Permit all modules to output log information with severity level higher than error to the log host. [sw...
Page 672
1-18 through combined configuration of the device name (facility), information severity level threshold (severity), module name (filter) and the file “syslog.Conf”, you can sort information precisely for filtering. Log output to the console network requirements the switch sends the following informa...
Page 673
1-19 network diagram figure 1-4 network diagram configuration procedure # name the local time zone z8 and configure it to be eight hours ahead of utc time. Clock timezone z8 add 08:00:00 # set the time stamp format of the log information to be output to the log host to date. System-view system view:...
Page 674: Table of Contents
I table of contents 1 boot rom and host software loading ···································································································1-1 introduction to loading approaches ·······································································································1-...
Page 675
Ii configuring a scheduled task ········································································································5-1 scheduled task configuration example·································································································5-2.
Page 676
1-1 1 boot rom and host software loading traditionally, switch software is loaded through a serial port. This approach is slow, time-consuming and cannot be used for remote loading. To resolve these problems, the tftp and ftp modules are introduced into the switch. With these modules, you can load/d...
Page 677
1-2 boot menu starting...... *********************************************************** * * * switch 4210 26-port bootrom, version 607 * * * *********************************************************** copyright(c) 2004-2009 3com corporation and its licensors. Creation date : nov 27 2009, 10:43:40 c...
Page 678
1-3 enter your choice(0-9): loading by xmodem through console port introduction to xmodem xmodem protocol is a file transfer protocol that is widely used due to its simplicity and high stability. The xmodem protocol transfers files through console port. It supports two types of data packets (128 byt...
Page 679
1-4 if you have chosen 19200 bps as the download baudrate, you need not modify the hyperterminal’s baudrate, and therefore you can skip step 4 and 5 below and proceed to step 6 directly. In this case, the system will not display the above information. Following are configurations on pc. Take the hyp...
Page 680
1-5 figure 1-2 console port configuration dialog box step 5: click the button to disconnect the hyperterminal from the switch and then click the button to reconnect the hyperterminal to the switch, as shown in figure 1-3 . Figure 1-3 connect and disconnect buttons the new baudrate takes effect after...
Page 681
1-6 step 7: choose [transfer/send file] in hyperterminal, and click in pop-up dialog box, as shown in figure 1-4 . Select the software file that you need to load to the switch, and set the protocol to xmodem. Figure 1-4 send file dialog box step 8: click . The system displays the page, as shown in f...
Page 682
1-7 z if the hyperterminal’s baudrate is not reset to 19200 bps, the system prompts "your baudrate should be set to 19200 bps again! Press enter key when ready". Z you need not reset the hyperterminal’s baudrate and can skip the last step if you have chosen 19200 bps. In this case, the system upgrad...
Page 683
1-8 loading the boot rom figure 1-6 local loading using tftp step 1: as shown in figure 1-6 , connect the switch through an ethernet port to the tftp server, and connect the switch through the console port to the configuration pc. You can use one pc as both the configuration device and the tftp serv...
Page 684
1-9 step 6: enter y to start file downloading or n to return to the boot rom update menu. If you enter y, the system begins to download and update the boot rom. Upon completion, the system displays the following information: loading........................................Done bootrom updating..........
Page 685
1-10 you can use one computer as both configuration device and ftp server. Step 2: run the ftp server program on the ftp server, configure an ftp user name and password, and copy the program file to the specified ftp directory. Step 3: run the hyperterminal program on the configuration pc. Start the...
Page 686
1-11 the subsequent steps are the same as those for loading the boot rom, except for that the system gives the prompt for host software loading instead of boot rom loading. When loading the boot rom and host software using ftp through boot menu, you are recommended to use the pc directly connected t...
Page 687
1-12 when using different ftp server software on pc, different information will be output to the switch. Step 2: update the boot rom program on the switch. Boot bootrom switch.Btm this will update bootrom file on unit 1. Continue? [y/n] y upgrading bootrom, please wait... Upgrade bootrom succeeded! ...
Page 688
1-13 step 1: as shown in figure 1-9 , connect the switch through an ethernet port to the pc (whose ip address is 10.1.1.1) step 2: configure the ip address of vlan-interface 1 on the switch to 192.168.0.28, and subnet mask to 255.255.255.0. You can configure the ip address for any vlan on the switch...
Page 689
1-14 figure 1-11 enter boot rom directory step 6: enter ftp 192.168.0.28 and enter the user name test, password pass, as shown in figure 1-12 , to log on to the ftp server. Figure 1-12 log on to the ftp server step 7: use the put command to upload the file switch.Btm to the switch, as shown in figur...
Page 690
1-15 figure 1-13 upload file switch.Btm to the switch step 8: configure switch.Btm to be the boot rom at next startup, and then restart the switch. Boot bootrom switch.Btm this will update bootrom on unit 1. Continue? [y/n] y upgrading bootrom, please wait... Upgrade bootrom succeeded! Reboot after ...
Page 692
2-2 table 2-2 system information display commands operation command description display the current date and time of the system display clock display the version of the system display version display the information about users logging onto the switch display users [ all ] you can execute the displa...
Page 693
2-3 you can use the following commands to enable the two switches. Table 2-3 enable debugging and terminal display for a specific module operation command description enable system debugging for specific module debugging module-name [ debugging-option ] required disabled for all modules by default. ...
Page 694
2-1 command alias configuration introduction as the network environment becomes more complex and network products become increasingly diverse, users always use network devices from several vendors in real networking environments. In this case, command keywords differences of devices from different v...
Page 695
2-2.
Page 696: Network Connectivity Test
3-1 3 network connectivity test network connectivity test ping you can use the ping command to check the network connectivity and the reachability of a host. Table 3-1 the ping command operation command description check the ip network connectivity and the reachability of a host ping [ -a ip-address...
Page 697: Device Management
4-1 4 device management introduction to device management device management includes the following: z reboot the ethernet switch z configure real-time monitoring of the running status of the system z specify the app to be used at the next reboot z update the boot rom z identifying and diagnosing plu...
Page 698
4-2 scheduling a reboot on the switch after you schedule a reboot on the switch, the switch will reboot at the specified time. Table 4-3 schedule a reboot on the switch operation command description schedule a reboot on the switch, and set the reboot date and time schedule reboot at hh:mm [ mm/dd/yy...
Page 700
4-4 table 4-8 commonly used pluggable transceivers transceiver type applied environment whether can be an optical transceiver whether can be an electrical transceiver sfp (small form-factor pluggable) generally used for 100m/1000m ethernet interfaces or pos 155m/622m/2.5g interfaces yes yes gbic (gi...
Page 701
4-5 diagnosing pluggable transceivers the system outputs alarm information for you to diagnose and troubleshoot faults of pluggable transceivers. Optical transceivers customized by h3c also support the digital diagnosis function, which enables a transceiver to monitor the main parameters such as tem...
Page 702
4-6 remote switch app upgrade configuration example network requirements telnet to the switch from a pc remotely and download applications from the ftp server to the flash memory of the switch. Update the switch software by using the device management commands through cli. The switch acts as the ftp...
Page 703
4-7 if the flash memory of the switch is not sufficient, delete the original applications before downloading the new ones. 4) initiate an ftp connection with the following command in user view. Enter the correct user name and password to log into the ftp server. Ftp 2.2.2.2 trying ... Press ctrl+k t...
Page 704
4-8 this command will reboot the device. Current configuration may be lost in next startup if you continue. Continue? [y/n] y this will reboot device. Continue? [y/n] y.
Page 705: Scheduled Task Configuration
5-1 5 scheduled task configuration what is a scheduled task a scheduled task defines a command or a group of commands and when such commands will be executed. It allows a device to execute specified command(s) at a time when no person is available to maintain the device. With a scheduled task config...
Page 706
5-2 to do… use the command… description display information about a scheduled task display job[ job-name ] available in any view specify the time delay to execute the commands in the task follow these steps to configure a scheduled task: to do… use the command… description enter system view system-v...
Page 707
5-3 configuration procedure system-view # create scheduled task phone1, and enter scheduled task view. [switch] job phone1 # configure the view where the specified command to be executed as ethernet interface view. [switch-job-phone1] view ethernet1/0/2 # configure the scheduled task so that poe can...
Page 708: Table of Contents
I table of contents 1 vlan-vpn configuration··························································································································1-1 vlan-vpn overview ················································································································...
Page 709: Vlan-Vpn Configuration
1-1 1 vlan-vpn configuration when configuring vlan-vpn, go to these sections for information you are interested in: z vlan-vpn overview z vlan-vpn configuration z displaying and maintaining vlan-vpn configuration z vlan-vpn configuration example vlan-vpn overview introduction to vlan-vpn virtual pri...
Page 710
1-2 implementation of vlan-vpn with the vlan-vpn feature enabled, no matter whether or not a received packet already carries a vlan tag, the switch will tag the received packet with the default vlan tag of the receiving port and add the source mac address to the mac address table of the default vlan...
Page 711
1-3 network diagram figure 1-3 network diagram for vlan-vpn configuration vlan 1040 eth1/0/11 eth1/0/12 eth1/0/21 eth1/0/22 vlan 100 vlan 200 pc user terminal user switcha switchb vlan 100 vlan 200 pc server terminal server configuration procedure z configure switch a. # enable the vlan-vpn feature ...
Page 712
1-4 # set ethernet 1/0/22 as a trunk port permitting packets of vlan 1024. [switchb-ethernet1/0/21] quit [switchb] interface ethernet 1/0/22 [switchb-ethernet1/0/22] port link-type trunk [switchb-ethernet1/0/22] port trunk permit vlan 1040 z do not configure vlan 1040 as the default vlan of ethernet...
Page 713: Table of Contents
I table of contents 1 remote-ping configuration ······················································································································1-1 remote-ping overview··············································································································...
Page 714: Remote-Ping Configuration
1-1 1 remote-ping configuration when configuring remote-ping, go to these sections for information you are interested in: z remote-ping overview z remote-ping configuration z remote-ping configuration examples remote-ping overview introduction to remote-ping remote-ping is a network diagnostic tool....
Page 715
1-2 test types supported by remote-ping table 1-1 test types supported by remote-ping supported test types description icmp test dhcp test ftp test http test dns test snmp test for these types of tests, you need to configure the remote-ping client and corresponding servers. Jitter test tcppublic tes...
Page 716
1-3 test parameter description test type (test-type) z you can use remote-ping to test a variety of protocols, see table 1-1 for details. Z to perform a type of test, you must first create a test group of this type. One test group can be of only one remote-ping test type. Z if you modify the test ty...
Page 717
1-4 test parameter description file name for ftp operation (filename) name of a file to be transferred between remote-ping client and ftp server size of a file to be uploaded in an ftp test(filesize) size of a file to be uploaded in an ftp test number of jitter test packets to be sent per probe (jit...
Page 718
1-5 note that: z the remote-ping server function is needed only for jitter, tcp, and udp tests. Z you can configure multiple tcp/udp listening services on one remote-ping server, with each listening service corresponding to a specific destination ip address and port number. Remote-ping client config...
Page 719
1-6 to do… use the command… remarks configure the maximum number of history records that can be saved history-records number optional by default, the maximum number is 50. Enable history record history-record enable optional by default, history record is not enabled. Configure the retaining time of ...
Page 720
1-7 in an icmp test, after you specify a source interface by the source-interface interface-type interface-number command, the ttl value turns to 1 automatically to test the directly connected devices. 2) configuring dhcp test on remote-ping client follow these steps to configure dhcp test on remote...
Page 722
1-9 to do… use the command… remarks configure the maximum number of history records that can be saved history-records number optional by default, the maximum number is 50. Enable history record history-record enable optional by default, history record is not enabled. Configure the retaining time of ...
Page 723
1-10 to do… use the command… remarks configure size of a file to be uploaded in an ftp test filesize file-size required by default, the file is 1 mb. Start the test test-enable required display test results display remote-ping results [ admin-nameoperation-tag ] required you can execute the command ...
Page 724
1-11 to do… use the command… remarks configure the maximum number of history records that can be saved history-records number optional by default, the maximum number is 50. Enable history record history-record enable optional by default, history record is not enabled. Configure the retaining time of...
Page 725
1-12 to do… use the command… remarks start the test test-enable required display test results display remote-ping results [ admin-nameoperation-tag ] required you can execute the command in any view. 5) configuring jitter test on remote-ping client follow these steps to configure jitter test on remo...
Page 726
1-13 to do… use the command… remarks configure the packet size datasize size optional by default, the packet size is 68 bytes. Configure a stuffing character string datafill string optional by default, the numbers between 0 and 255 are stuffed into datagrams in a cyclically way. Configure a test des...
Page 727
1-14 to do… use the command… remarks configure the number of test packets that will be sent in each jitter probe jitter-packetnum number optional by default, each jitter probe will send 10 packets. Configure the interval to send test packets in the jitter test jitter-interval interval optional by de...
Page 728
1-15 to do… use the command… remarks enable history record history-record enable optional by default, history record is not enabled. Configure the retaining time of history record history keep-time keep-time optional by default, the retaining time of history record is 120 minutes. Configure statisti...
Page 729
1-16 to do… use the command… remarks enable the remote-ping client function remote-ping-agent enable required by default, the remote-ping client function is disabled. Create a remote-ping test group and enter its view remote-ping administrator-name operation- tag required by default, no test group i...
Page 731
1-18 to do… use the command… remarks configure the destination address destination-ip ip-address required this ip address and the one configured on the remote-ping server for listening service must be the same. By default, no destination address is configured. Configure the destination port destinat...
Page 733
1-20 to do… use the command… remarks configure the test type test-typedns required by default, the test type is icmp. Configure the number of probes per test count times optional by default, one probe is made per test. Configure a test description description string optional by default, no descripti...
Page 734
1-21 to do… use the command… remarks configure the type of service tos value optional by default, the service type is zero. Configure the domain name to be resolved dns resolve-targetdomai domainname required by default, the domain name to be resolved by dns is not specified. Configure the ip addres...
Page 736
1-23 [sysname] remote-ping-agent enable # create a remote-ping test group, setting the administrator name to administrator and test tag to icmp. [sysname] remote-ping administrator icmp # configure the test type as icmp. [sysname-remote-ping-administrator-icmp] test-type icmp # configure the destina...
Page 737
1-24 dhcp test network requirements both the remote-ping client and the dhcp server are switches. Perform a remote-ping dhcp test between the two switches to test the time required for the remote-ping client to obtain an ip address from the dhcp server. Network diagram figure 1-3 network diagram for...
Page 738
1-25 square-sum of round trip time: 10465630 last complete test time: 2000-4-3 9:51:30.9 extend result: sd maximal delay: 0 ds maximal delay: 0 packet lost in test: 0% disconnect operation number: 0 operation timeout number: 0 system busy operation number: 0 connection fail number: 0 operation seque...
Page 739
1-26 network diagram figure 1-4 network diagram for the ftp test configuration procedure z configure ftp server (switch b): configure ftp server on switch b. For specific configuration of ftp server, refer to the ftp-sftp-tftp part of the manual. Z configure remote-ping client (switch a): # enable t...
Page 740
1-27 [sysname-remote-ping-administrator-ftp] display remote-ping results administrator ftp remote-ping entry(admin administrator, tag ftp) test result: destination ip address:10.2.2.2 send operation times: 10 receive response times: 10 min/max/average round trip time: 3245/15891/12157 square-sum of ...
Page 741
1-28 network diagram figure 1-5 network diagram for the http test configuration procedure z configure http server: use windows 2003 server as the http server. For http server configuration, refer to the related instruction on windows 2003 server configuration. Z configure remote-ping client (switch ...
Page 742
1-29 system busy operation number: 0 connection fail number: 0 operation sequence errors: 0 drop operation number: 0 other operation errors: 0 http result: dns resolve time: 0 http operation time: 675 dns resolve min time: 0 http test total time: 748 dns resolve max time: 0 http transmission success...
Page 743
1-30 network diagram figure 1-6 network diagram for the jitter test configuration procedure z configure remote-ping server (switch b): # enable the remote-ping server and configure the ip address and port to listen on. System-view [sysname] remote-ping-server enable [sysname] remote-ping-server udpe...
Page 744
1-31 last complete test time: 2000-4-2 8:14:58.2 extend result: sd maximal delay: 10 ds maximal delay: 10 packet lost in test: 0% disconnect operation number: 0 operation timeout number: 0 system busy operation number: 0 connection fail number: 0 operation sequence errors: 0 drop operation number: 0...
Page 745
1-32 network diagram figure 1-7 network diagram for the snmp test configuration procedure z configure snmp agent (switch b): # start snmp agent and set snmp version to v2c, read-only community name to public, and read-write community name to private. System-view [sysname] snmp-agent [sysname] snmp-a...
Page 746
1-33 # start the test. [sysname-remote-ping-administrator-snmp] test-enable # display test results [sysname-remote-ping-administrator-snmp] display remote-ping results administrator snmp remote-ping entry(admin administrator, tag snmp) test result: destination ip address:10.2.2.2 send operation time...
Page 747
1-34 configuration procedure z configure remote-ping server (switch b): # enable the remote-ping server and configure the ip address and port to listen on. System-view [sysname] remote-ping-server enable [sysname] remote-ping-server tcpconnect 10.2.2.2 8000 z configure remote-ping client (switch a):...
Page 748
1-35 [sysname-remote-ping-administrator-tcpprivate] display remote-ping history administrator tcpprivate remote-ping entry(admin administrator, tag tcpprivate) history record: index response status lastrc time 1 4 1 0 2000-04-02 08:26:02.9 2 5 1 0 2000-04-02 08:26:02.8 3 4 1 0 2000-04-02 08:26:02.8 ...
Page 749
1-36 [sysname-remote-ping-administrator-udpprivate] test-type udpprivate # configure the ip address of the remote-ping server as 10.2.2.2. [sysname-remote-ping-administrator-udpprivate] destination-ip 10.2.2.2 # configure the destination port on the remote-ping server. [sysname-remote-ping-administr...
Page 750
1-37 dns test network requirements an switch serves as the remote-ping client, and a pc serves as the dns server. Perform a remote-ping dns test between the switch and the dns server to test the time required from the client sends a dns request to it receives a resolution result from the dns server....
Page 751
1-38 min/max/average round trip time: 6/10/8 square-sum of round trip time: 756 last complete test time: 2006-11-28 11:50:40.9 extend result: sd maximal delay: 0 ds maximal delay: 0 packet lost in test: 0% disconnect operation number: 0 operation timeout number: 0 system busy operation number: 0 con...
Page 752: Table of Contents
I table of contents 1 ipv6 configuration·····································································································································1-1 ipv6 overview ·············································································································...
Page 753: Ipv6 Configuration
1-1 1 ipv6 configuration z 3com switch 4210 family support ipv6 management features, but do not support ipv6 forwarding and related features. Z the term “router” in this document refers to a router in a generic sense or an ethernet switch running a routing protocol. Ipv6 overview internet protocol v...
Page 754
1-2 adequate address space the source ipv6 address and the destination ipv6 address are both 128 bits (16 bytes) long.Ipv6 can provide 3.4 x 10 38 addresses to completely meet the requirements of hierarchical address division as well as allocation of public and private addresses. Hierarchical addres...
Page 755
1-3 introduction to ipv6 address ipv6 addresses an ipv6 address is represented as a series of 16-bit hexadecimals, separated by colons. An ipv6 address is divided into eight groups, 16 bits of each group are represented by four hexadecimal numbers which are separated by colons, for example, 2001:000...
Page 756
1-4 the type of an ipv6 address is designated by the format prefix. Table 1-1 lists the mapping between major address types and format prefixes. Table 1-1 mapping between address types and format prefixes type format prefix (binary) ipv6 prefix id unassigned address 00...0 (128 bits) ::/128 loopback...
Page 757
1-5 address application ff05::2 site-local scope all-routers multicast address besides, there is another type of multicast address: solicited-node address. The solicited-node multicast address is used to acquire the link-layer addresses of neighbor nodes on the same link and is also used for duplica...
Page 758
1-6 table 1-3 types and functions of icmpv6 messages icmpv6 message function used to acquire the link-layer address of a neighbor used to verify whether the neighbor is reachable neighbor solicitation (ns) message used to perform a duplicate address detection used to respond to a neighbor solicitati...
Page 759
1-7 figure 1-3 address resolution the address resolution procedure is as follows: 1) node a multicasts an ns message. The source address of the ns message is the ipv6 address of the interface of node a and the destination address is the solicited-node multicast address of node b. The ns message cont...
Page 760
1-8 1) node a sends an ns message whose source address is the unassigned address :: and the destination address is the corresponding solicited-node multicast address of the ipv6 address to be detected. The ns message also contains the ipv6 address. 2) if node b uses this ipv6 address, node b returns...
Page 761
1-9 task remarks configuring ipv6 tcp properties optional configuring the maximum number of ipv6 icmp error packets sent within a specified time optional configuring the hop limit of icmpv6 reply packets optional configuring ipv6 dns optional displaying and maintaining ipv6 optional configuring an i...
Page 762
1-10 to do... Use the command... Remarks automatically generate a link-local address ipv6 address auto link-local configure an ipv6 link-local address manually assign a link-local address for an interface. Ipv6 address ipv6-address link-local optional by default, after an ipv6 site-local address or ...
Page 764
1-12 configure the ns interval after a device sends an ns message, if it does not receive a response within a specific period, the device will send another ns message. You can configure the interval for sending ns messages. Table 1-9 configure the ns interval to do… use the command… remarks enter sy...
Page 765
1-13 z finwait timer: when the ipv6 tcp connection status is fin_wait_2, the finwait timer is triggered. If no packet is received before the finwait timer expires, the ipv6 tcp connection is terminated. If fin packets are received, the ipv6 tcp connection status becomes time_wait. If other packets a...
Page 766
1-14 table 1-14 configure the hop limit of icmpv6 reply packets to do… use the command… remarks enter system view system-view — configure the hop limit of icmpv6 reply packets ipv6 nd hop-limit value optional 64 by default. Configuring ipv6 dns configure a static host name to ipv6 address mapping yo...
Page 767
1-15 the dns resolve and dns domain commands are the same as those of ipv4 dns. For details about the commands, refer to dns. Displaying and maintaining ipv6 table 1-17 display and maintain ipv6 to do… use the command… remarks display dns domain name suffix information display dns domain [ dynamic ]...
Page 769
1-17 # configure an automatically generated link-local address for the interface vlan-interface1. System-view [switchb] interface vlan-interface 1 [switchb-vlan-interface1] ipv6 address auto link-local # configure a global unicast address for the interface vlan-interface1. [switchb-vlan-interface1] ...
Page 770
1-18 when you use the ping ipv6 command to verify the reachability of the destination, you must specify the “–i” keyword if the destination address is a link-local address. For the operation of ipv6 ping, refer to section “ ipv6 ping ”. [switcha-vlan-interface1]ping ipv6 fe80::2e0:fcff:fe00:2006 -i ...
Page 771
2-1 2 ipv6 application configuration introduction to ipv6 application ipv6 are supporting more and more applications. Most of ipv6 applications are the same as those of ipv4. The applications supported on 3com switch 4210 family are: z ping z traceroute z tftp z telnet ipv6 application configuration...
Page 772
2-2 figure 2-1 traceroute process device a hop limit=1 hop limit exceeded hop limit=2 hop limit exceeded hop limit=n udp port unreachable device b device c device d as figure 2-1 shows, the traceroute process is as follows: z the source sends an ip datagram with the hop limit of 1. Z if the first ho...
Page 774
2-4 display and maintain ipv6 telnet table 2-5 display and maintain ipv6 telnet to do… use the command… remarks display the use information of the users who have logged in display users [ all ] available in any view ipv6 application configuration example ipv6 applications network requirements in fig...
Page 775
2-5 bytes=56 sequence=1 hop limit=64 time = 110 ms reply from 3003::1 bytes=56 sequence=2 hop limit=64 time = 31 ms reply from 3003::1 bytes=56 sequence=3 hop limit=64 time = 31 ms reply from 3003::1 bytes=56 sequence=4 hop limit=64 time = 31 ms reply from 3003::1 bytes=56 sequence=5 hop limit=64 ti...
Page 776
2-6 solution z check that the ipv6 addresses are configured correctly. Z use the display ipv6 interface command to determine the interfaces of the source and the destination and the link-layer protocol between them are up. Z use the display ipv6 route-table command to verify that the destination is ...
Page 777: Table of Contents
I table of contents 1 password control configuration operations ·························································································1-1 introduction to password control configuration ·····················································································1-1 passwor...
Page 778
1-1 1 password control configuration operations introduction to password control configuration the password control feature is designed to manage the following passwords: z telnet passwords: passwords for logging into the switch through telnet. Z ssh passwords: passwords for logging into the switch ...
Page 779
1-2 function description application encrypted display: the switch protects the displayed password. The password is always displayed as a string containing only asterisks (*) in the configuration file or on user terminal. Password protection and encryption saving passwords in ciphertext: the switch ...
Page 780
1-3 password control configuration configuration prerequisites a user pc is connected to the switch to be configured; both devices are operating normally. Configuration tasks the following sections describe the configuration tasks for password control: z configuring password aging z configuring the ...
Page 781
1-4 operation command description create a local user or enter local user view local-user user-name — configure a password aging time for the local user password-control aging aging-time optional by default, the aging time is 90 days. In this section, you must note the effective range of the same co...
Page 782
1-5 z you can configure the password aging time when password aging is not yet enabled, but these configured parameters will not take effect. Z after the user changes the password successfully, the switch saves the old password in a readable file in the flash memory. Z the switch does not provide th...
Page 783
1-6 in this section, you must note the effective range of the same commands when executed in different views or to different types of passwords: z global settings in system view apply to all local user passwords and super passwords. Z settings in the local user view apply to the local user password ...
Page 784
1-7 table 1-5 manually remove history password records operation command description remove history password records of one or all users reset password-control history-record [ user-name user-name ] executing this command without the user-name user-name option removes the history password records of...
Page 785
1-8 z lock-time: in this mode, the system inhibits the user from re-logging in within a certain time period. After the period, the user is allowed to log into the switch again. By default, this time is 120 minutes. Z lock: in this mode, the system inhibits the user from re-logging in forever. The us...
Page 786
1-9 table 1-9 configure the timeout time for users to be authenticated operation command description enter system view system-view — configure the timeout time for users to be authenticated password-control authentication-timeout authentication-timeout optional by default, it is 60 seconds. Configur...
Page 787
1-10 operation command description configure the password composition policy for the local user password-control composition type-number policy-type [ type-length type-length ] optional by default, the minimum number of types a password should contain is 1 and the minimum number of characters of eac...
Page 788
1-11 z for the superpassword, the minimum number of password composition types is 3 and the minimum number of characters in each composition type is 3. Z for a local user named test, the minimum password length is 6 characters, the minimum number of password composition types is 2, the minimum numbe...
Page 789: Table of Contents
I table of contents 1 smart link configuration ·························································································································1-1 smart link overview ············································································································...
Page 790: Smart Link Configuration
1-1 1 smart link configuration smart link overview as shown in figure 1-1 , dual-uplink networking is widely applied currently. Usually, spanning tree protocol (stp) is used to implement link redundancy backup in the network. However, stp is not suitable for users with a high demand for convergence ...
Page 791
1-2 flush message when a forwarding link fails, the device will switch the traffic to the blocked standby link. The former forwarding entries of each device in the network are no longer suitable for the new topology, so mac address forwarding entries and arp entries must be updated throughout the ne...
Page 792
1-3 z when link switching occurs in the smart link group, mac forwarding entries and arp entries of each device in the network may be out of date. In order to guarantee correct packet transmission, you must enable the smart link device to send flush messages to notify the other devices in the networ...
Page 793
1-4 operation command remarks create a smart link group and enter smart link group view smart-link group group-id required enable the function of sending flush messages in the specified control vlan flush enable control-vlan vlan-id required by default, no control vlan for sending flush messages is ...
Page 794
1-5 table 1-4 enable the specified port to process flush messages received from the specified control vlan operation command remarks enter system view system-view — system view smart-link flush enable control-vlan vlan-id port interface-type interface-number [ to interface-type interface-number] int...
Page 795
1-6 displaying and debugging smart link after the above-mentioned configuration, you can use the following display commands in any view to view the smart link group information and the statistics information of flush messages received and processed by current device, so as to verify the configuratio...
Page 796
1-7 configuration procedure 1) configure a smart link group on switch a and configure member ports for it. Enable the function of sending flush messages in control vlan 1. # enter system view. System-view # enter ethernet port view. Disable stp on ethernet1/0/1 and ethernet1/0/2. [switcha] interface...
Page 797: Monitor Link Configuration
2-1 2 monitor link configuration introduction to monitor link monitor link is a collaboration scheme introduced to complement for smart link. It is used to monitor uplink and to perfect the backup function of smart link. A monitor link consists of an uplink port and one or multiple downlink ports. W...
Page 798
2-2 how monitor link works figure 2-2 network diagram for a monitor link group implementation block switch a switch b eth1/0/1 eth1/0/2 switch c switch d switch e eth1/0/1 eth1/0/2 eth1/0/3 eth1/0/1 eth1/0/2 eth1/0/11 eth1/0/12 as shown in figure 2-2 , the devices switch c and switch d are connected...
Page 799
2-3 before configuring a monitor link group, you must create a monitor link group and configure member ports for it. A monitor link group consists of an uplink port and one or multiple downlink ports. The uplink port can be a manually-configured or static lacp link aggregation group, an ethernet por...
Page 800
2-4 operation command remarks monitor link group view port interface-type interface-number uplink quit interface interface-type interface-number configure the specified ethernet port as the uplink port of the monitor link group ethernet port view port monitor-link group group-id uplink configuring a...
Page 802
2-6 [switcha-ethernet1/0/1] stp disable [switcha-ethernet1/0/1] quit [switcha] interface ethernet 1/0/2 [switcha-ethernet1/0/2] stp disable # return to system view. [switcha-ethernet1/0/2] quit # create smart link group 1 and enter smart link group view. [switcha] smart-link group 1 # configure ethe...
Page 803: Table of Contents
I table of contents 1 arp and ip attack defense configuration ································································································ 1 arp packet filtering based on gateway’s address ················································································· 1 introdu...
Page 804
1 1 arp and ip attack defense configuration arp packet filtering based on gateway’s address introduction according to the arp design, after receiving an arp packet with the target ip address being that of the receiving interface, a device adds the ip-to-mac mapping of the sender into its arp mapping...
Page 805
2 to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure arp packet filtering based on the gateway’s ip address arp filtersource ip-address required not configured by default. Configure arp packet filtering based...
Page 806
3 arp/ip attack defense based on 802.1x overview arp attack detection and ip filtering implemented based on dhcp snooping entries can effectively prevent arp/ip attacks in a network where clients obtain ip addresses dynamically through dhcp. However, if most of the clients are assigned with ip addre...
Page 807
4 configuring 802.1x-based arp/ip attack defense follow these steps to configure 802.1x-based arp/ip attack defense: to do… use the command… remarks enter system view system-view — enable using ip-mac bindings of authenticated 802.1x clients for arp attack detection ip source static import dot1x req...
Page 808
5 z if they are consistent, the packet passes the check and the switch learns the arp entry. Z if they are not consistent, the arp packet is considered invalid and the corresponding arp entry is not learned. Enabling arp source mac address consistency check to do… use the command… remarks enter syst...
Page 809
6 # configure arp packet filtering based on the gateway’s ip address on ethernet 1/0/2. [switch] interface ethernet 1/0/2 [switch-ethernet1/0/2] arp filter source 192.168.100.1 [switch-ethernet1/0/2] quit # configure arp packet filtering based on the gateway’s ip address on ethernet 1/0/3. [switch] ...
Page 810
7 # configure the maximum number of arp entries that can be learned by vlan-interface 1 as 500. [switcha-vlan-interface1] arp max-learning-num 500 [switcha-vlan-interface1] quit arp/ip attack defense configuration example iii network requirements z host a is assigned with an ip address statically an...
Page 811
8 # enable 802.1x on ethernet 1/0/1. [switch] interface ethernet1/0/1 [switch-ethernet1/0/1] dot1x # enable ip filtering based on ip-mac bindings of authenticated 802.1x clients. [switch-ethernet1/0/1] ip check dot1x enable.
Page 812: Table of Contents
I table of contents 1 lldp configuration···································································································································1-1 overview ····················································································································...
Page 813: Lldp Configuration
1-1 1 lldp configuration when configuring lldp, go to these sections for information you are interested in: z overview z lldp configuration task list z performing basic lldp configuration z configuring cdp compatibility z configuring lldp trapping z displaying and maintaining lldp z lldp configurati...
Page 814
1-2 figure 1-1 ethernet ii-encapsulated lldp frame format the fields in the frame are described in table 1-1 : table 1-1 description of the fields in an ethernet ii-encapsulated lldp frame field description destination mac address the mac address to which the lldpdu is advertised. It is fixed to 0x0...
Page 815
1-3 field description source mac address the mac address of the sending port. If the port does not have a mac address, the mac address of the sending bridge is used. Type the snap type for the upper layer protocol. It is 0xaaaa-0300-0000-88cc for lldp. Data lldpdu. Fcs frame check sequence, a 32-bit...
Page 816
1-4 type description remarks port description port description of the sending port. System name assigned name of the sending device. System description description of the sending device. System capabilities identifies the primary functions of the sending device and the primary functions that have be...
Page 817
1-5 lldp-med tlvs lldp-med tlvs provide multiple advanced applications for voice over ip (voip), such as basic configuration, network policy configuration, and address and directory management. Lldp-med tlvs satisfy the voice device vendors’ requirements for cost effectiveness, ease of deployment, a...
Page 818
1-6 how lldp works transmitting lldp frames an lldp-enabled port operating in txrx mode or tx mode sends lldp frames to its directly connected devices both periodically and when the local configuration changes. To prevent the network from being overwhelmed by lldp frames at times of frequent local d...
Page 819
1-7 performing basic lldp configuration enabling lldp to make lldp take effect on certain ports, you need to enable lldp both globally and on these ports. Follow these steps to enable lldp: to do… use the command… remarks enter system view system-view — enable lldp globally lldp enable required by d...
Page 820
1-8 enabling lldp polling with lldp polling enabled, a device checks for local configuration changes periodically. Upon detecting a configuration change, the device sends lldp frames to inform the neighboring devices of the change. Follow these steps to enable lldp polling: to do… use the command… r...
Page 821
1-9 to do… use the command… remarks enter ethernet interface view interface interface-type interface-number required enable lldp to advertise management address tlvs and configure the advertised management ip address lldp management-address-tlv [ ip-address ] optional by default, the management addr...
Page 822
1-10 setting an encapsulation format for lldpdus lldpdus can be encapsulated in ethernet ii or snap frames. Z with ethernet ii encapsulation configured, an lldp port sends lldpdus in ethernet ii frames and processes an incoming lldp frame only when it is ethernet ii encapsulated. Z with snap encapsu...
Page 823
1-11 with cdp compatibility enabled, the device can use lldp to receive and recognize cdp packets from cisco ip phones and respond with cdp packets carrying the voice vlan id of the device for the ip phones to configure the voice vlan automatically. In this way, voice traffic is confined in the conf...
Page 824
1-12 follow these steps to configure lldp trapping: to do… use the command… remarks enter system view system-view — enter ethernet interface view interface interface-type interface-number required enable lldp trap sending lldp notification remote-change enable required disabled by default quit to sy...
Page 825
1-13 figure 1-4 network diagram for basic lldp configuration nms switch a med switch b eth1/0/2 eth1/0/1 eth1/0/1 configuration procedure 1) configure switch a. # enable lldp globally. System-view [switcha] lldp enable # enable lldp on ethernet 1/0/1 and ethernet 1/0/2 (you can skip this step becaus...
Page 826
1-14 hold multiplier : 4 reinit delay : 2s transmit delay : 2s trap interval : 5s fast start times : 3 port 1 [ethernet1/0/1]: port status of lldp : enable admin status : rx_only trap flag : no roll time : 0s number of neighbors : 1 number of med neighbors : 1 number of cdp neighbors : 0 number of s...
Page 827
1-15 port status of lldp : enable admin status : rx_only trap flag : no roll time : 0s number of neighbors : 1 number of med neighbors : 1 number of cdp neighbors : 0 number of sent optional tlv : 0 number of received unknown tlv : 5 port 2 [ethernet1/0/2]: port status of lldp : enable admin status ...
Page 828
1-16 system-view [switcha] vlan 2 [switcha-vlan2] quit # set the link type of ethernet 1/0/1 and ethernet 1/0/2 to trunk and enable voice vlan on them. [switcha] interface ethernet 1/0/1 [switcha-ethernet1/0/1] port link-type trunk [switcha-ethernet1/0/1] voice vlan 2 enable [switcha-ethernet1/0/1] ...
Page 829
1-17 platform : cisco ip phone 7960 duplex : full as the sample output shows, switch a has discovered the ip phones connected to ethernet 1/0/1 and ethernet 1/0/2, and has obtained their lldp device information..
Page 830: Table of Contents
I table of contents 1 pki configuration ······································································································································1-1 introduction to pki·······································································································...
Page 831: Pki Configuration
1-1 1 pki configuration when configuring pki, go to these sections for information you are interested in: z introduction to pki z pki configuration task list z displaying and maintaining pki z pki configuration examples z troubleshooting pki introduction to pki this section covers these topics: z pk...
Page 832
1-2 cas are trusted by different users in a pki system, the cas will form a ca tree with the root ca at the top level. The root ca has a ca certificate signed by itself while each lower level ca has a ca certificate signed by the ca at the next higher level. Crl an existing certificate may need to b...
Page 833
1-3 ca a ca is a trusted authority responsible for issuing and managing digital certificates. A ca issues certificates, specifies the validity periods of certificates, and revokes certificates as needed by publishing crls. Ra a registration authority (ra) is an extended part of a ca or an independen...
Page 834
1-4 2) the ra reviews the identity of the entity and then sends the identity information and the public key with a digital signature to the ca. 3) the ca verifies the digital signature, approves the application, and issues a certificate. 4) the ra receives the certificate from the ca, sends it to th...
Page 835
1-5 the configuration of an entity dn must comply with the ca certificate issue policy. You need to determine, for example, which entity dn parameters are mandatory and which are optional. Otherwise, certificate request may be rejected. Follow these steps to configure an entity dn: to do… use the co...
Page 836
1-6 configuring a pki domain before requesting a pki certificate, an entity needs to be configured with some enrollment information, which is referred to as a pki domain. A pki domain is intended only for convenience of reference by other applications like ssl, and has only local significance. A pki...
Page 839
1-9 z if a pki domain already has a local certificate, creating an rsa key pair will result in inconsistency between the key pair and the certificate. To generate a new rsa key pair, delete the local certificate and then issue the public-key local create command. Z a newly created key pair will over...
Page 840
1-10 z if a pki domain already has a ca certificate, you cannot retrieve another ca certificate for it. This is in order to avoid inconsistency between the certificate and registration information due to related configuration changes. To retrieve a new ca certificate, use the pki delete-certificate ...
Page 841
1-11 to do… use the command… remarks enter pki domain view pki domain domain-name — disable crl checking crl check disable required enabled by default return to system view quit — retrieve the ca certificate refer to retrieving a certificate manually required verify the validity of the certificate p...
Page 842
1-12 configuring an access control policy by configuring a certificate attribute-based access control policy, you can further control access to the server, providing additional security for the server. Follow these steps to configure a certificate attribute-based access control policy: to do… use th...
Page 843
1-13 pki configuration examples z the scep plug-in is required when you use the windows server as the ca. In this case, when configuring the pki domain, you need to use the certificate request from ra command to specify that the entity requests a certificate from an ra. Z the scep plug-in is not req...
Page 844
1-14 after configuring the basic attributes, you need to perform configuration on the jurisdiction configuration page of the ca server. This includes selecting the proper extension profiles, enabling the scep autovetting function, and adding the ip address list for scep autovetting. # configure the ...
Page 845
1-15 . Z apply for certificates # retrieve the ca certificate and save it locally. [switch] pki retrieval-certificate ca domain torsa retrieving ca/ra certificates. Please wait a while...... The trusted ca's finger print is: md5 fingerprint:ede9 0394 a273 b61a f1b3 0072 a0b1 f9ab sha1 fingerprint: 7...
Page 846
1-16 modulus (1024 bit): 00d67d50 41046f6a 43610335 ca6c4b11 f8f89138 e4e905bd 43953ba2 623a54c0 ea3cb6e0 b04649ce c9cddd38 34015970 981e96d9 ff4f7b73 a5155649 e583ac61 d3a5c849 cbde350d 2a1926b7 0ae5ef5e d1d8b08a dbf16205 7c2a4011 05f11094 73eb0549 a65d9e74 0f2953f2 d4f0042f 19103439 3d4f9359 88fb5...
Page 847
1-17 configuration procedure 1) configure the ca server z install the certificate server suites from the start menu, select control panel > add or remove programs, and then select add/remove windows components > certificate services and click next to begin the installation. Z install the scep plug-i...
Page 848
1-18 # specify the entity for certificate request as aaa. [switch-pki-domain-torsa] certificate request entity aaa z generate a local key pair using rsa [switch] public-key local create rsa the range of public key size is (512 ~ 2048). Notes: if the key modulus is greater than 512, it may take a few...
Page 849
1-19 subject: cn=switch subject public key info: public key algorithm: rsaencryption rsa public key: (1024 bit) modulus (1024 bit): 00a6637a 8cdea1ac b2e04a59 f7f6a9fe 5aee52ae 14a392e4 e0e5d458 0d341113 0bf91e57 fa8c67ac 6ce8febb 5570178b 10242fdd d3947f5e 2da70bd9 1faf07e5 1d167ce1 fc20394f 476f5c...
Page 850
1-20 z the network connection is not proper. For example, the network cable may be damaged or loose. Z no trusted ca is specified. Z the url of the registration server for certificate request is not correct or not configured. Z no authority is specified for certificate request. Z the system clock of...
Page 851
1-21 z the crl distribution url is not configured. Z the ldap server version is wrong. Solution z make sure that the network connection is physically proper. Z retrieve a ca certificate. Z specify the ip address of the ldap server. Z specify the crl distribution url. Z re-configure the ldap version..
Page 852: Table of Contents
I table of contents 1 ssl configuration ·····································································································································1-1 ssl overview ··············································································································...
Page 853: Ssl Configuration
1-1 1 ssl configuration when configuring ssl, go to these sections for information you are interested in: z ssl overview z ssl configuration task list z displaying and maintaining ssl z troubleshooting ssl ssl overview secure sockets layer (ssl) is a security protocol providing secure connection ser...
Page 854
1-2 ssl protocol stack as shown in figure 1-2 , the ssl protocol consists of two layers of protocols: the ssl record protocol at the lower layer and the ssl handshake protocol, change cipher spec protocol, and alert protocol at the upper layer. Figure 1-2 ssl protocol stack z ssl handshake protocol:...
Page 855
1-3 configuration prerequisites when configuring an ssl server policy, you need to specify the pki domain to be used for obtaining the server side certificate. Therefore, before configuring an ssl server policy, you must configure a pki domain.. Configuration procedure follow these steps to configur...
Page 856
1-4 z if you enable client authentication here, you must request a local certificate for the client. Z currently, ssl mainly comes in these versions: ssl 2.0, ssl 3.0, and tls 1.0, where tls 1.0 corresponds to ssl 3.1. When the device acts as an ssl server, it can communicate with clients running ss...
Page 857
1-5 [switch-pki-entity-en] quit # create a pki domain and configure it. [switch] pki domain 1 [switch-pki-domain-1] ca identifier ca1 [switch-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.Dll [switch-pki-domain-1] certificate request from ra [switch-pki-domain-1] certific...
Page 858
1-6 # configure the system to strip domain name off a user name before transmitting the user name to the radius server. [sysname-radius-radius1] user-name-format without-domain [sysname-radius-radius1] quit # create isp domain aabbcc.Net for web authentication users and enter the domain view. [sysna...
Page 860
1-8 z if the ssl server is configured to authenticate the client, but the certificate of the ssl client does not exist or cannot be trusted, request and install a certificate for the client. 2) you can use the display ssl server-policy command to view the cipher suite used by the ssl server policy. ...
Page 861: Table of Contents
I table of contents 1 https configuration ································································································································1-1 https overview ···············································································································...
Page 862: Https Configuration
1-1 1 https configuration when configuring https, go to these sections for information you are interested in: z https overview z https configuration task list z associating the https service with an ssl server policy z enabling the https service z associating the https service with a certificate att...
Page 863
1-2 associating the https service with an ssl server policy you need to associate the https service with a created ssl server policy before enabling the https service. Follow these steps to associate the https service with an ssl server policy: to do… use the command… remarks enter system view syste...
Page 864
1-3 associating the https service with a certificate attribute access control policy associating the https service with a configured certificate access control policy helps control the access right of the client, thus providing the device with enhanced security. Follow these steps to associate the h...
Page 865
1-4 https configuration example network requirements z host acts as the https client and device acts as the https server. Z host accesses device through web to control device. Z ca (certificate authority) issues certificate to device. The common name of ca is new-ca. In this configuration example, w...
Page 866
1-5 [device] pki retrieval-certificate ca domain 1 # apply for a local certificate. [device] pki request-certificate domain 1 2) configure an ssl server policy associated with the https service # configure an ssl server policy. [device] ssl server-policy myssl [device-ssl-server-policy-myssl] pki-do...
Page 867: Table of Contents
I table of contents appendix a acronyms ································································································································ a-1.
Page 868: Appendix A Acronyms
A-1 appendix a acronyms a aaa authentication, authorization and accounting abr area border router acl access control list arp address resolution protocol as autonomous system asbr autonomous system border router b bdr backup designated router c car committed access rate cli command line interface co...
Page 869
A-2 igmp internet group management protocol igp interior gateway protocol ip internet protocol l lldp link layer discovery protocol lsa link state advertisement lsdb link state database m mac medium access control mib management information base n nbma non broadcast multiaccess nic network informati...
Page 870
A-3 ttl time to live u udp user datagram protocol v vlan virtual lan vod video on demand w wrr weighted round robin x xid exchange identification xrn expandable resilient networking.