D-Link DFL-1600 - Security Appliance User Manual
Summary of DFL-1600 - Security Appliance
Page 3
Contents i preface xvi document version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Xvii disclaimer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Xvii about this document . . . . . . . . . . . . . . . . . . . . . . . . . . . . Xvii typographical conventions . ...
Page 4
Ii iv administration 18 4 configuration platform 19 4.1 configuring via webui . . . . . . . . . . . . . . . . . . . . . . . 19 4.1.1 overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 4.1.2 interface layout . . . . . . . . . . . . . . . . . . . . . . . 19 4.1.3 configuration operati...
Page 5
Iii 9 interfaces 53 9.1 ethernet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53 9.1.1 ethernet interfaces . . . . . . . . . . . . . . . . . . . . . . 53 9.1.2 ethernet interfaces in d-link firewalls . . . . . . . . . 54 9.2 virtual lan (vlan) . . . . . . . . . . . . . . . . . ....
Page 6
Iv 11 date & time 95 11.1 setting the date and time . . . . . . . . . . . . . . . . . . . . . 96 11.1.1 current date and time . . . . . . . . . . . . . . . . . . . 96 11.1.2 time zone . . . . . . . . . . . . . . . . . . . . . . . . . . . 96 11.1.3 daylight saving time(dst) . . . . . . . . . . . . . ...
Page 7
V 16 dmz & port forwarding 127 16.1 general . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127 16.1.1 concepts . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127 16.1.2 dmz planning . . . . . . . . . . . . . . . . . . . . . . . . 129 16.1.3 benefits . . . . . . . . . . . ...
Page 8
Vi 19.1.3 action . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182 19.2 chain of events . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183 19.2.1 scenario 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . 183 19.2.2 scenario 2 . . . . . . . . . . . . . . . . . . . . . . . ...
Page 9
Vii ix traffic management 246 23 traffic shaping 247 23.1 overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 247 23.1.1 functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248 23.1.2 features . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249 23.2 pipes ....
Page 10
Viii xi transparent mode 282 27 transparent mode 283 27.1 overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283 27.2 transparent mode implementation in d-link firewalls . . . . 284 27.3 scenarios: enabling transparent mode . . . . . . . . . . . . . . 286 xii zonedefense 292 28...
Page 11
Ix list of commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315 about . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315 access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 316 arp . . . . . . . . . . . . . . . . . . . . . . . . . . . ....
Page 12
X sysmsgs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 334 settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 334 stats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336 time . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Page 13
Figures & tables 2.1 the osi 7-layer model. . . . . . . . . . . . . . . . . . . . . . . . 8 4.1 webui authentication window. . . . . . . . . . . . . . . . . . . 20 4.2 webui main display. . . . . . . . . . . . . . . . . . . . . . . . . . 20 9.1 a vlan infrastructure. . . . . . . . . . . . . . . . . ...
Page 14
Xii 19.4 an ids scenario . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189 20.1 vpn deployment scenario 1 . . . . . . . . . . . . . . . . . . . . 201 20.2 vpn deployment scenario 2 . . . . . . . . . . . . . . . . . . . . 202 20.3 vpn deployment scenario 3 . . . . . . . . . . . . . . . . . ...
Page 15
List of scenarios section 10.4: route failover configuration . . . . . . . . . . . . . . 78 section 10.5: dynamic routing configuration . . . . . . . . . . . . 82 section 10.6: static routing configuration . . . . . . . . . . . . . . 87 section 10.7: pbr configuration . . . . . . . . . . . . . . . ....
Page 16
Xiv.
Page 17
P art i preface.
Page 19
Document version version no.: 1.02 disclaimer information in this user’s guide is subject to change without notice. About this document this user’s guide is designed to be a handy configuration manual as well as an internetworking and security knowledge learning tool for network administrators. The ...
Page 20
Typographical conventions example: configuration steps for achieving certain function. Webui : example steps for webui. Note additional information the user should be aware of. Tip suggestions on configuration that may be taken into consideration. Caution critical information the user should follow ...
Page 21
P art ii product overview.
Page 23: Capabilities
Chapter 1 capabilities 1.1 product highlights the key features of d-link firewalls can be outlined as: • easy to use start-up wizard • web-based graphical user interface (webui) • effective and easy to maintenance • complete control of security policies • advanced application layer gateways (ftp, ht...
Page 24
4 chapter 1. Capabilities • zonedefense • high availability (some models) details about how to make these features work can be found in specific chapters in this user’s guide. D-link firewalls user’s guide.
Page 25
P art iii introduction to networking.
Page 27: The Osi Model
Chapter 2 the osi model open system interconnection (osi) model defines a primary framework for intercomputer communications, by categorizing different protocols for a great variety of network applications into seven smaller, more manageable layers. The model describes how data from an application i...
Page 28
8 chapter 2. The osi model 7 application layer 6 presentation layer 5 session layer 4 transport layer 3 network layer 2 data-link layer 1 physical layer table 2.1: the osi 7-layer model. Transport layer – controls data flow and provides error-handling. Protocols: tcp, udp, etc. Network layer – perfo...
Page 29: Firewall Principles
Chapter 3 firewall principles 3.1 the role of the firewall 3.1.1 what is a firewall? When you connect your computer or your local area network to another network, e.G. The internet, measures need to be taken to prevent intruders from gaining access to resources and material you consider confidential...
Page 30
10 chapter 3. Firewall principles complies with current protocol definitions. This can prevent poorly implemented services on the protected servers and client software from being exposed to unexpected data, causing them to hang or crash. In short, a firewall is the network’s answer to poor host secu...
Page 31
3.2. What does a firewall not protect against? 11 3.2.1 attacks on insecure pre-installed components a very common problem is the fact that operating systems and applications usually contain insecure pre-installed components. Such components include undocumented services present on computers connect...
Page 32
12 chapter 3. Firewall principles apart from better written software, is to disable such services or limiting surfing to less sensitive computers. • html pages that link in the contents of local files when they are opened without scripts. Such pages can, often with the help of unsuspecting local use...
Page 33
3.2. What does a firewall not protect against? 13 • customized scripts on web servers. It is now very easy to extend the functionality of your web server by writing small, customized programs to handle a multitude of tasks. However, insufficient awareness of potential problems can lead you, more oft...
Page 34
14 chapter 3. Firewall principles modem pools can be subject to direct attacks and, in extreme cases, telephone lines can be tapped. Switches, located at any point in the telecommunications network or in the office, can be reprogrammed without the intruder needing to be anywhere near them. When it c...
Page 35
3.2. What does a firewall not protect against? 15 result. It is now common practice to locate web servers in demilitarized zones, where they communicate with data sources on protected networks. In such cases, data-driven attacks pose a huge threat. The problem with holes between dmzs and internal ne...
Page 36
16 chapter 3. Firewall principles rather, the problem is that insecure machines can execute commands on ”protected” machines. Another form of protection worth considering is to set up a separate data source that contains limited information to which the web server has access. It should only contain ...
Page 37
P art iv administration.
Page 38
This part covers basic aspects of d-link firewall management and administration, including: • configuration platform • logging • maintenance • advanced settings.
Page 39: Configuration Platform
Chapter 4 configuration platform 4.1 configuring via webui 4.1.1 overview the d-link firewall can be configured using a web interface. A web interface is usually a fast and efficient way to configure a firewall, that does not require the administrator to install any specific programs to configure th...
Page 40
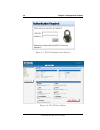
20 chapter 4. Configuration platform figure 4.1: webui authentication window. Figure 4.2: webui main display. D-link firewalls user’s guide.
Page 41
4.1. Configuring via webui 21 menu bar the menu bar consists of a number of buttons with either a single option or multiple suboptions. • home go to start page of webui. • configuration - save and activate: save the configuration and activate the changes. - discard changes: discard latest changes in...
Page 42
22 chapter 4. Configuration platform - zonedefense: displays zonedefense status information. • logout log out from the webui. • help read the latest version of this manual. Tree-view list the tree view list is a listing of the configuration sections in the firewall. The tree can be expanded to show ...
Page 43
4.2. Monitoring via cli 23 4.2 monitoring via cli administrators can also monitor and troubleshoot the d-link firewall via command-line interface (cli), by employing the console port on the firewall. The serial console port is a rs-232 port that enables a connection to a pc or terminal. To access th...
Page 44
24 chapter 4. Configuration platform d-link firewalls user’s guide.
Page 45: Logging
Chapter 5 logging this chapter discusses principles of logging and gives a brief introduction to d-link firewalls’ logging design. For information about how to implement logging function by the firewall, please refer to 13 , log settings in the fundamentals part. 5.1 overview logging is a practice t...
Page 46
26 chapter 5. Logging discontinuity of services. By reviewing the output of logging, there is a good chance that the administrator will be able to figure out the problematic events, and take necessary actions to correct the problems. Once the problem is resolved, the correct content can be found in ...
Page 47
5.1. Overview 27 security policy information about different actions triggered by the firewall’s rules are given in this category, including: • accept– packets accepted for further transmission. • fwd– packets statelessly forwarded. • drop– packets disallowed. Network connection various traffic conn...
Page 48
28 chapter 5. Logging • ha – high availability events. • ids/idsupdate – intrusion detection events and database update. • zonedefense – zonedefense events. • snmp – allowed and disallowed snmp accesses. • ip.../tcp... – information concerning tcp/ip packets. 5.2 log receivers a log receiver is a se...
Page 49
5.2. Log receivers 29 feb 5 2000 09:45:23 gateway.Ourcompany.Com fw: drop: subsequent text is dependent on the event that has occurred. In order to facilitate automated processing of all messages, d-link firewall writes all log data to a single line of text. All data following the initial text is pr...
Page 50
30 chapter 5. Logging d-link firewalls user’s guide.
Page 51: Maintenance
Chapter 6 maintenance 6.1 firmware upgrades d-link firewalls can be upgraded with new firmwares to introduce new functionality and fix known problems. Make sure to regularly check on the d-link support website for new firmware upgrades. Example: upgrading firmware this example describes how to upgra...
Page 52
32 chapter 6. Maintenance 3. Upgrade the firewall firmware go to the webui of your d-link firewall and navigate to tools − > upgrade page in the toolbar. Under ”firmware upload”, click on the ”browse” button. Select the firmware upgrade file you recently downloaded from the d-link support website. C...
Page 53
6.2. Reset to factory defaults 33 2. Reset to factory defaults via the serial console connect the serial cable and attach using terminal emulator software (if windows is used, the communication accessory hyperterminal can be used). Reset the firewall. Press any key when ”press any key to abort and l...
Page 54
34 chapter 6. Maintenance 6.3 backup configuration d-link firewalls configuration can be backed up to and restored at request. This could for instance be used to recall the ”last known good” configuration when experimenting with different configuration setups. To create a backup of the current runni...
Page 55: Advanced Settings
Chapter 7 advanced settings 7.1 overview advanced settings contain various global settings for a firewall in terms of packet size limits, connection timeouts, protocol parameters, the structural integrity tests each packet shall be subjected to, etc. Generally, the default values given in these sect...
Page 56
36 chapter 7. Advanced settings d-link firewalls user’s guide.
Page 57
P art v fundamentals.
Page 58
From both physical and logical perspectives, this part introduces the basic components of d-link firewalls, which are the building blocks for security policies and advanced functions. Topics in this part includes: • logical objects • interfaces • routing • date & time • dns • log settings.
Page 59: Logical Objects
Chapter 8 logical objects logical objects are basic network elements defined in the firewall, referring to the entities needed to be protected and also the untrusted resources and applications that should be monitored by the security policies. 8.1 address book like the contacts book which records pe...
Page 60
40 chapter 8. Logical objects network to indicate its location. The address book in d-link firewalls allows administrators to name ip addresses either for a single host, a network, a master/slave pair used in high availability, or a group of computers or interfaces. An address ”0.0.0.0/0” named as ”...
Page 61
8.2. Services 41 example: enabling user authentication for an ip object a user group ”users” is defined into the local network address ”lannet” to create an authentication address object ”lannet users”. For information of specifying the user group, please refer to 17.4 scenario . Webui : 1. Specifyi...
Page 62
42 chapter 8. Logical objects one user’s program to other parties in a network. At this layer, other parties are identified and can be reached by specific application protocol types and corresponding parameters, such as port numbers. For example, the web-browsing service http is defined as to use th...
Page 63
8.2. Services 43 example: specifying a tcp service -- http in this example, the service http for connecting web servers is defined. As explained previously, http uses tcp destination port 80. Webui : objects − > services − > add − > tcp/udp: enter the following and then click ok: general name: http ...
Page 64
44 chapter 8. Logical objects • redirect – the source is told that there is a better route for a particular packet. Codes assigned are as follows: - code 0. Redirect datagrams for the network - code 1. Redirect datagrams for the host - code 2. Redirect datagrams for the type of service and the netwo...
Page 65
8.2. Services 45 user-defined ip protocol service services that run over ip and perform application/transport layer functions can be defined by ip protocol numbers. Ip can carry data for a number of different protocols. These protocols are each identified by a unique ip protocol number specified in ...
Page 66
46 chapter 8. Logical objects service group the services defined in the above options can be grouped in order to simplify security policy configuration. Consider a web server using standard http as well as ssl encrypted http (https, refer to 22.3 ssl/tls (https) ). Instead of having to create two se...
Page 67
8.2. Services 47 a good idea, since it may cause the protected network vulnerable to many types of attacks, e.G. Dos (denial of service) in particular. To solve this problem, d-link firewalls can be configured to pass an icmp error message only if it is related to an existing connection of a service...
Page 68
48 chapter 8. Logical objects 8.3 schedules scheduling is a way to create timing constraints on the firewall’s rules. It enables the user to define a certain time period, in the format of year–date–time, wich will only activate the rules at the designated times. Any activities outside of the schedul...
Page 69
8.4. X.509 certificates 49 8.4 x.509 certificates d-link firewalls support certificates that comply with the itu-t x.509 international standard. This technology use an x.509 certificate hierarchy with public-key cryptography (see 20.2 , introduction to cryptography ) to accomplish key distribution a...
Page 70
50 chapter 8. Logical objects from the user certificate up to the trusted root certificate has to be examined before establishing the validity of the user certificate. The ca certificate is just like any other certificates, except that it allows the corresponding private key to sign other certificat...
Page 71
8.4. X.509 certificates 51 - verify the signatures of all certificates in the certification path. - fetch the crl for each certificate to verify that none of the certificates have been revoked. Identification lists in addition to verifying the signatures of certificates, d-link firewalls also employ...
Page 72
52 chapter 8. Logical objects d-link firewalls user’s guide.
Page 73: Interfaces
Chapter 9 interfaces physical interfaces are the doorways of the network connections. It allows the network traffic to enter into or go out of the network areas with which it connects. In order to control the traffic on both in and out directions and protect the local network, security rules in the ...
Page 74
54 chapter 9. Interfaces firewall will be enumerated and configured during the local console setup process. Each physical ethernet adapter will become an ethernet interface and a name will be given in the firewall configuration. Administrators can customize the descriptive name and change the ip add...
Page 75
9.1. Ethernet 55 example: a lan interface configuration the interface connected to lan (or one of the lans) is configured with ”lan ip”, ”lannet”, and the default gateway address ”lan gate”. Webui : 1. Specifying the ip4 host – ”lan ip” and ”lan gate”, and an ip4 net- work – ”lannet” in the objects....
Page 76
56 chapter 9. Interfaces 9.2 virtual lan (vlan) virtual networking is the ability of network appliances to manage the logical network topologies on top of the actual physical connections, allowing arbitrary segments within a network to be combined into a logical group. Since the flexibility and the ...
Page 77
9.2. Virtual lan (vlan) 57 to the same vlan, and client b can only communicate with server c through the firewall. Figure 9.1: a vlan infrastructure. 9.2.2 802.1q vlan standard the ieee 802.1q standard defines the operation of vlan devices that permit the definition, operation and administration of ...
Page 78
58 chapter 9. Interfaces bytes 8 6 6 4 2 46 4 to 1500 pre- dest. Sou- len- data crc amble rce 32 bits gth 16 3 1 12 vlan pri- cfi vid type ority indicator (0x8100) vlan tag table 9.1: 802.1q standard ethernet frame. 9.2.3 vlan implementation comply to 802.1q standard, the d-link firewall implement v...
Page 79
9.2. Virtual lan (vlan) 59 example: configure a vlan interface in d-link firewall this example shows how to configure a vlan interface. Webui : 1. Create vlan interface. Interfaces − > vlan − > add − > vlan: enter the following: general name: type a name for the vlan interface. Interface: select the...
Page 80
60 chapter 9. Interfaces interfaces on the firewall. • create 16 virtual lans in the firewall, named, for instance, vlan01 to vlan16, each with a unique vlan id • in the switch, map each vlan id to a switch port, and make sure the uplink port is configured as a trunk port for all the vlan ids. • eac...
Page 81
9.4. Pppoe 61 and usually accepts the first offer it receives. Clients can renew or release their ip address assignment during the lease period. Example: configuring the firewall as a dhcp client to enable the firewall acting as a dhcp client and locate external dhcp server(s) and receive address in...
Page 82
62 chapter 9. Interfaces ip addresses provisioning can be per user groups. 9.4.1 ppp point-to-point protocol (ppp), is a protocol for communication between two computers using a serial interface, for instance, a dialup connection where a personal computer is connected by telephone line to a server. ...
Page 83
9.4. Pppoe 63 pppoe interface since the pppoe protocol runs ppp over ethernet, the firewall needs to use one of the normal ethernet interfaces to run the pppoe tunnel over. Each pppoe tunnel is interpreted as a logical interface by the firewall, with the same filtering, traffic shaping and configura...
Page 84
64 chapter 9. Interfaces example: a pppoe client configuration this example describes how to configure a pppoe client. The pppoe client is configured on the wan interface and all traffic should be routed over the pppoe tunnel. Webui : pppoe client we will configure the pppoe client on the wan interf...
Page 85
9.5. Interface groups 65 9.5 interface groups similar to logical object group, multiple interfaces can be grouped together in the firewall to apply to a common policy. An interface group can consist of regular ethernet interfaces, vlan interfaces, or vpn tunnels (see 22 ). All members of an interfac...
Page 86
66 chapter 9. Interfaces 9.6 arp address resolution protocol (arp) is a network protocol, which maps a network layer protocol address to a data link layer hardware address. For example, arp is used to resolve ip address to the corresponding ethernet address. It works at the osi data link layer (laye...
Page 87
9.6. Arp 67 to accomplish the above, the firewall provides responses to arp requests concerning the ip addresses in published arp items. The latter purpose is useful if there are several separate ip spans on a single lan. The computers on each ip span may then use a gateway in their own span when th...
Page 88
68 chapter 9. Interfaces example: an arp example this example describes how to add an extra ip address to a ethernet or vlan interface using arp publish. Webui : • create a arp table entry interfaces − > arp table − > add − > arp entry: enter the following: mode: publish interface: select the interf...
Page 89: Routing
Chapter 10 routing 10.1 overview routing is a major role in the network layer (osi layer 3), which determines how to transport packets from the initiating host to the desired receiving end. The devices functioning at the network layer, such as routers or firewalls, perform routing to achieve two tas...
Page 90
70 chapter 10. Routing fields, such as interface, network, gateway, destination, etc. When a packet arrives at a router, it refers to the routing table to make path determination. The router compares the destination address of the packet with the entries it has in the routing table, and finds out th...
Page 91
10.3. Routing algorithms 71 world. Routers inside an as run the same routing algorithm and they only need to know the topology of the area. There are special gateway routers in the ass that are responsible for routing packets from internal area to various outside ass. Gateway routers run inter-as ro...
Page 92
72 chapter 10. Routing simply drop the packet. Therefore, static routing is often used to make the minimal set of routes to reach directly connected networks only. 10.3.2 dynamic routing complementing to static routing algorithm, dynamic routing adapts to changes of network topology or traffic loads...
Page 93
10.3. Routing algorithms 73 rest, runs the ls algorithm and can calculate a same set of least-cost paths as all the other routers. Any change of the link state will be sent everywhere in the network, so that all routers keep the same routing table information. Open shortest path first(ospf) is a com...
Page 94
74 chapter 10. Routing • bandwidth – bandwidth is the traffic capacity of a path, rated by ”mbps”. • load – load refers to the usage of a router. The usage can be evaluated by cpu utilization and the throughput. • delay – delay is regarding to the time it takes to move a packet from the source to th...
Page 95
10.3. Routing algorithms 75 configured to connect to the backbone through a non-backbone area. Vlink can also be used to link through partitioned backbone areas. A normal ospf area acts like a private network connecting to the backbone area via some router called area border router(abr). Abrs have i...
Page 96
76 chapter 10. Routing dr and the next highest one becomes bdr. If priority number 0 is specified for a router, it will not be eligible in the dr/bdr election. Once the dr and bdr are selected, all the other routers within the same ospf area establish a relationship with them to further exchange rou...
Page 97
10.4. Route failover 77 after the database of each router is fully exchanged and synchronized, the router will calculate a shortest path first(spf) tree to all known destinations based on the database. By running the spf algorithm, each router will be able to determine the best(least-cost) path for ...
Page 98
78 chapter 10. Routing 10.4.1 scenario: route failover configuration example: two isps figure 10.1: route failover scenario in this scenario shown in figure 10.1 , two isp:s (isp a and isp b) are used to connect to the internet. Isp a is connected to the wan1 interface of the firewall and isp b is c...
Page 99
10.4. Route failover 79 2. Add default route over the wan1 interface. Next step is to add default route for interface wan1. Routes − > main routing table − > add − > route: enter the following: general interface: wan1 network: 0.0.0.0/0 gateway: default gateway of isp a. Local ip address: (none) met...
Page 100
80 chapter 10. Routing 4. Create interface group and add rules. To be able to write rules with destination interface that can use either route, you have to create a interface group that use the security/transport equivalent feature. This makes the two interfaces equal in a security sense. Creating t...
Page 101
10.5. Dynamic routing implementation 81 10.5 dynamic routing implementation in d-link firewalls, the implementation of dynamic routing involves two primary configuration tasks: ospf process & dynamic routing policy. Note ospf functionality is only available in the d-link firewall modules dfl-800/160...
Page 102
82 chapter 10. Routing actions to be either exported to ospf processes or to be added to one or more routing tables. The most common usages of dynamic routing policy are listed as follows, examples are given next. • importing ospf routes from ospf process into the routing table. • exporting routes f...
Page 103
10.5. Dynamic routing implementation 83 an ospf process named as ”ospf-proc1” is created, and only one ospf area, the backbone ”area0” (0.0.0.0), is used in this example. The 3 involved interfaces are added into the area to make the firewall participate in the ospf process. However, this will not ad...
Page 104
84 chapter 10. Routing 3. Interfaces: – adding the participating interfaces into the process. In the ”area0” configuration page: interfaces − > add − > interface: − > general: interface: select ”lan1” from the dropdown list. (”lan1” is assumed to have been defined in ethernet interfaces) interface t...
Page 105
10.5. Dynamic routing implementation 85 example: importing routes from an ospf as into the main routing table it is assumed that a previously configured ospf process named ”ospf-proc1” has been created. In this scenario, all received routes from ”ospf-proc1” will be added into the main routing table...
Page 106
86 chapter 10. Routing routes or previously inserted default routes. Example: exporting the default route into an ospf as it is assumed that a previously configured ospf process named ”ospf-proc1” has been created. In this scenario the default route (only) from the main routing table will be exporte...
Page 107
10.6. Scenario: static routing configuration 87 10.6 scenario: static routing configuration example: creating a static route figure 10.3: static routing scenario in this example a network 192.168.2.0/24 has been setup to be routable through a router(192.168.1.10) on the local network, as shown in fi...
Page 108
88 chapter 10. Routing note as a result of this setup the return traffic from the router will be routed directly upon the local network with a standard ”allow” rule set. For this scenario to work the ip rule set must either dictate that the traffic for this network is to be nated or forwarded withou...
Page 109
10.7. Policy based routing(pbr) 89 • creating provider-independent metropolitan area networks – all users share a common active backbone, but can use different isps, subscribing to different streaming media providers. Pbr implementation in d-link firewalls consists of two elements: • one or more nam...
Page 110
90 chapter 10. Routing rules. The first matching rule will be the one to use. According to the specification in the rule, a routing table is selected to use. If there is no matching rule, the pbr tables will not be used and nor pbr will be performed. The firewall will forward the packets according t...
Page 111
10.7. Policy based routing(pbr) 91 example: creating a policy-based route after defining the pbr table ”testpbrtable”, we add routes into the table in this example. Webui : create pbr route routing − > policy-based routing tables − > testpbrtable − > add − > route: enter the following: interface: th...
Page 112
92 chapter 10. Routing • this is a ”drop-in” design, where there are no explicit routing subnets between the isp gateways and the firewall. In a provider-independent metropolitan area network, clients will likely have a single ip address, belonging to either one or the other isp. In a single-organiz...
Page 113
10.7. Policy based routing(pbr) 93 note we add rules for inbound as well as outbound connections. Complete the following steps to configure this example scenario in the firewall. 1. Add routes to main routing table. Add the routes found in the list of routes in the main routing table, as shown earli...
Page 114
94 chapter 10. Routing 10.8 proxy arp proxy arp is the process in which one system responds to the arp request for another system. For example, host a sends an arp request to resolve the ip address of host b. Instead of host b, the firewall responds to this arp request. In essence, proxy arp has the...
Page 115: Date & Time
Chapter 11 date & time correctly set date and time is of greatest importance for the product to operate properly. For instance, time scheduled policies and auto-update of ids signatures are two features that require the clock to be correctly set. In addition, log messages are tagged with time stamps...
Page 116
96 chapter 11. Date & time 11.1 setting the date and time 11.1.1 current date and time example: to adjust the current date and time, follow the steps outlined below: webui : system − > date and time: general click the set date and time button in the pop-up window, date: select the current year, mont...
Page 117
11.1. Setting the date and time 97 11.1.3 daylight saving time(dst) many regions honor daylight saving time (dst) (or summer time as it is called in many countries). Daylight saving time works by advancing the clock during summer to get more out of the summer days. Unfortunately, the principles regu...
Page 118
98 chapter 11. Date & time 11.2 time synchronization the clock in the product is likely to be fast or slow after a period of operation. This is normal behavior in most network and computer equipment and is commonly solved by utilizing a time synchronization mechanism. The product is able to adjust t...
Page 119
11.2. Time synchronization 99 11.2.3 maximum adjustment to avoid situations where a faulty timeserver causes the product to update its clock with highly erroneous time data, a maximum adjustment value (in seconds) can be specified. If the difference between the current time in the product and the ti...
Page 120
100 chapter 11. Date & time note this example uses domain names instead of ip addresses. Therefore, make sure the dns client settings of the system are properly configured as described in 12 dns . D-link firewalls user’s guide.
Page 121: Dns
Chapter 12 dns domain name system (dns) can be considered as a gigantic distributed database that is used to translate from computer names to their ip addresses. Dns is used within the firewall whenever there is need to translate a domain name to an ip address. Also, the dhcp server within the firew...
Page 122
102 chapter 12. Dns d-link firewalls user’s guide.
Page 123: Log Settings
Chapter 13 log settings in the administration part, we have introduced the general concepts of logging and the design in d-link firewalls to cope with significant events (refer to 5 , logging ). In this chapter, we present configuration examples for enabling logging function. Except for some default...
Page 124
104 chapter 13. Log settings from different sources based on the identifier. The valid range is 0 to 7, representing syslog facilities ”local0” through ”local7”. Severity is the degree of emergency attached to the logged event message for debug. D-link firewalls can be set to send messages at differ...
Page 125
13.1. Implementation 105 webui : rules − > ip rules: click the ip rule item − > log settings: general check enable logging severity: choose one of the severity levels from the dropdown list. Log receivers log to: check either all receivers or specific receiver(s) (if specific receiver(s) is checked,...
Page 126
106 chapter 13. Log settings d-link firewalls user’s guide.
Page 127
P art vi security polices.
Page 128
Security policies regulate the manner of network applications to protect from abuse and inappropriate use. D-link firewalls feature for providing various mechanisms to aid the administrators in building security polices for attacks prevention, privacy protection, identification, and access control. ...
Page 129: Ip Rules
Chapter 14 ip rules 14.1 overview the list of rules defined on the basis of network objects – addresses, protocols, services – is the heart of any firewall. Rules determine the basic filtering functions of the firewall, which is essential. Following the rules configuration, the firewall regulates wh...
Page 130
110 chapter 14. Ip rules connection is found. The action of the rule is then carried out. If the action is allow, the connection will be established and a state representing the connection is added to the firewall’s internal state table. If the action is drop, the new connection will be refused. Fir...
Page 131
14.1. Overview 111 14.1.2 action types when all the fields listed in the previous section are matched by a packet, a rule is triggered, and certain action specified by the matching rule will be carried out. The types of actions include: ◦ allow: lets the packet pass through the firewall. The firewal...
Page 132
112 chapter 14. Ip rules 14.2 address translation 14.2.1 overview for functionality and security considerations, network address translation(nat) is widely applied for home and office use today. D-link firewall provides options to support both dynamic and static nat. These two types are represented ...
Page 133
14.2. Address translation 113 the outside world, the whole private network is like one node using one public ip address, and the inside structure and addresses of the network is hidden. Nat depends on a machine on the local network to initiate any connection to hosts on the other side of the firewal...
Page 134
114 chapter 14. Ip rules source and destination address and port numbers - it is possible to validate any or all of this information before passing the traffic. This checking helps the firewall to protect a private lan against attacks from the outside. Nat mechanism discard all traffic that does not...
Page 135
14.2. Address translation 115 source port to a free port, usually one above 32768, 32789 is used here. The packet is then sent to its destination. The recipient server regards the firewall nated address as the origin of the packet, processes the packet, and sends its response back to the nated addre...
Page 136
116 chapter 14. Ip rules 14.3 scenarios: ip rules configuration this section shows you example configurations of ip rules, including: • nat rule • sat rule – publicly accessible server with a private address in a dmz other features’ setups cooperating with nat can be found in 16 , dmz & port forward...
Page 137
14.3. Scenarios: ip rules configuration 117 2. Create rule final step is to create the rule that will allow icmp(ping) packets to be received by the external interface of the firewall. Rules − > ip rules − > add − > ip rule: name: ping to ext action: allow service: ping-inbound source interface: any...
Page 138
118 chapter 14. Ip rules 2. Create dns-all service if no dns-all service is defined, we need to create a new service. Objects − > services − > add − > tcp/udp service: name: dns-all type: tcpudp source: 0-65535 destination: 53 then click ok 3. Create http rule next step is to create the rule that wi...
Page 139
14.3. Scenarios: ip rules configuration 119 note for nat rules it is possible to specify the ip address that internal ip addresses should be translated to. This can be done on the ”nat” tab when configuring the rule. As default, the address of the destination interface is used. Example: sat rule pub...
Page 140
120 chapter 14. Ip rules 2. Rule 1: create a new rule that sat http traffic directed to the external public ip address ip ext, to the private ip address of the web server. ∗ rule 2: create an nat rule to permit traffic sat:ed by the above rule. ∗ rule 3: create a nat rule that allows internal machin...
Page 141
14.3. Scenarios: ip rules configuration 121 3. Create http sat/nat rule next step is to create an nat rule to permit traffic sat:ed by the above rule. Rules − > ip rules − > add − > ip rule: name: satnat to webserver action: nat service: http source interface: any source network: all-nets destinatio...
Page 142
122 chapter 14. Ip rules continue to pass the packets through the rule list until a second rule matches. When the packets are leaving the rule list, this rule redirects them to the destination. Problem with the current rule set this rule set makes the internal addresses visible to machines in the dm...
Page 143: Access (Anti-Spoofing)
Chapter 15 access (anti-spoofing) 15.1 overview the primary function of any firewall is to control the access to protected data resources, so that only authorized connections are allowed. Access control is basically addressed in the firewall’s ip rules (introduced in 14 . Ip rules ). According to th...
Page 144
124 chapter 15. Access (anti-spoofing) attacks. Even if the firewall is able to detect the dos attacks, it is hard to trace or stop it because of the spoofing. 15.1.2 anti-spoofing to equip the firewalls with anti-spoofing capability, an extra filter against the source address verification is in nee...
Page 145
15.2. Access rule 125 the rule is triggered, and the specified action will be carried out by the firewall. Filtering fields ◦ interface: the interface that the packet arrives on. ◦ network: the ip span that the sender address should belong to. Action ◦ drop: to discard the packets that match the def...
Page 146
126 chapter 15. Access (anti-spoofing) 15.3 scenario: setting up access rule example: allowing traffic from a specific network this example will show how to make sure that traffic received on the lan interface always have the correct source address, within the lan-net network. Webui : 1. Create acce...
Page 147: Dmz & Port Forwarding
Chapter 16 dmz & port forwarding 16.1 general 16.1.1 concepts dmz – ”demilitarized zone” – stands for an area that is neither part of the trusted internal network nor directly part of the public internet. Typically, dmz is a separate subnetwork between the firewall protected private lan and the publ...
Page 148
128 chapter 16. Dmz & port forwarding example: a corporation’s web server we take a look at a simple example, showing one utilization of dmz with a d-link firewall. The most common publicly available service that every corporation need to have is web browsing(http). However, it is unsafe to place a ...
Page 149
16.1. General 129 server. For instance, suppose our web server is running on nt that might be vulnerable to a number of denial-of-service attacks against services, such as rpc, netbios and smb. These services are not required for the operation of http. So we can set rules to block relevant tcp conne...
Page 150
130 chapter 16. Dmz & port forwarding approach 2 – move the database server out to the dmz network. Drawback : although all the public accessible data are now on the dmz network, the protection to the database server is weakened. If a hacker takes control over the web server, he or she can go straig...
Page 151: User Authentication
Chapter 17 user authentication 17.1 authentication overview before any user’s service request is authorized according to the firewall’s security policies, the firewall need to verify the identity of the user, to ensure that the corresponsive user is who she or he claims to be. Authentication is the ...
Page 152
132 chapter 17. User authentication c) something the user knows the secret information that only the involved user knows and keeps, such as the most commonly used password or a shared secret phrase. The difficulty of using method a) is that it requires some special devices to scan and read the featu...
Page 153
17.1. Authentication overview 133 find the notes that recording the password, or ask the user directly. Many people tend to write the passwords down on paper, and they may tell a password to someone they trust, which are potential leakages. • crack: exhaustive search by some software crackers. Passw...
Page 154
134 chapter 17. User authentication • normal users accessing the network • pppoe/pptp/l2tp users – using ppp authentication methods • ipsec & ike users – the entities authentication during the ike negotiation phases (implemented by pre-shared keys or certificates. Refer to 22.1.4 ike integrity & aut...
Page 155
17.2. Authentication components 135 authentication information. When there are more than one firewall in the network and thousands of users added or removed constantly, the administrator will not have to configure and maintain separate databases of authorized user profiles on each firewall. Instead,...
Page 156
136 chapter 17. User authentication • https – authentication via secure web browsing. Similar to http agent except that host & root certificates are used to establish ssl connection to the firewall. (refer to 22.3 ssl/tls (https) ) • xauth – authentication during ike negotation in ipsec vpn (if the ...
Page 157
17.3. Authentication process 137 17.3 authentication process a d-link firewall proceeds user authentication as follows: • a user connects to the firewall to initiate authentication. • the firewall receives user’s request from its interface, and notes in the ip rule set that this traffic is allowed t...
Page 158
138 chapter 17. User authentication example: configuring the local user database in the example of authentication address object in 8.1 address book , a user group ”users” is used to enable user authentication on ”lannet”. This example shows how to configure a user group in the firewall’s built-in d...
Page 159
17.4. Scenarios: user authentication configuration 139 example: configuring a radius server an external user authentication server can be configured by following the steps below: webui : user authentication − > external user databases − > add − > external user database: general name: enter a name fo...
Page 160
140 chapter 17. User authentication defined, will be dropped by the firewall. The configurations below shows how to enable http user authentication to the user group ”users” on ”lannet”. Only users that belong to the group ”users” can have web browsing service after authentication, as it is defined ...
Page 161
17.4. Scenarios: user authentication configuration 141 2. User authentication − > user authentication rules − > add − > user authentication rule − > general name: httplogin agent: http authentication source: local interface: lan originator ip: lannet comments: http authentication for lannet via loca...
Page 162
142 chapter 17. User authentication note 1. Http authentication will collide with webui’s remote management service which also uses tcp port 80. To avoid this, please change webui port in advanced settings for remote management before proceeding the authentication configuration, for example, using p...
Page 163
17.4. Scenarios: user authentication configuration 143 • allow multiple logins per username– if this one is selected, the firewall will allow users from different source ip addresses, but with the same username, to be simultaneous logged on. • allow one login per username, disallow the rest– if this...
Page 164
144 chapter 17. User authentication d-link firewalls user’s guide.
Page 165
P art vii content inspection.
Page 166
In addition to inspect the packets at the network layer (osi layer 3), d-link firewalls are capable of examining the content of each packet to give far more powerful and flexible protection on higher layers. Topics in this part includes: • application layer gateway (alg) • intrusion detection system...
Page 167: Application Layer Gateway
Chapter 18 application layer gateway (alg) 18.1 overview to complement the limitations of packet filtering, which only inspect in the packet headers, such as ip, tcp, udp, and icmp headers, d-link firewalls embed an application layer gateway (alg) to support higher level protocols that have address ...
Page 168
148 chapter 18. Application layer gateway (alg) 18.2 ftp the file transfer protocol (ftp) is a tcp/ip-based protocol to exchange files between a client and a server. The client initiates the connection by connecting to the ftp server. Normally the client needs to authenticate itself by providing a p...
Page 169
18.2. Ftp 149 when active mode is used, the firewall is not aware of that the ftp server will establish a new connection back to the ftp client. Therefore, the connection for the data channel will be dropped by the firewall. As the port number used for the data channel is dynamic, the only way to so...
Page 170
150 chapter 18. Application layer gateway (alg) 18.2.2 scenarios: ftp alg configuration example: protecting a ftp server figure 18.1: ftp alg scenario 1 in this example, a ftp server is connected to a d-link firewall on a dmz with private ip addresses, shown in figure 18.1 . To make it possible to c...
Page 171
18.2. Ftp 151 2. Services objects − > services − > add − > tcp/udp service: general: enter the following: name: ftp-inbound type: select tcp from the dropdown list. Destination: 21 (the port the ftp server resides on). Application layer gateway: alg: select ”ftp-inbound” that has been created. Then ...
Page 172
152 chapter 18. Application layer gateway (alg) – traffic from the internal interface need to be nated: rules − > ip rules − > add − > ip rule: general: name: nat-ftp action: nat service: ftp-inbound address filter: source destination interface: dmz core network: dmz-net ip-ext nat: check use interf...
Page 173
18.2. Ftp 153 example: protecting ftp clients figure 18.2: ftp alg scenario 2 in this scenario, shown in figure 18.2 , a d-link firewall is protecting a workstation that will connect to ftp servers on the internet. To make it possible to connect to these servers from the internal network using the f...
Page 174
154 chapter 18. Application layer gateway (alg) 2. Services objects − > services − > add − > tcp/udp service: general: enter the following: name: ftp-outbound type: select tcp from the dropdown list. Destination: 21 (the port the ftp server resides on). Application layer gateway alg: select ”ftp-out...
Page 175
18.3. Http 155 4. Rules (using private ips) if the firewall is using private ip’s, the following nat rule need to be added instead. Rules − > ip rules − > add − > ip rule: general: name: nat-ftp-outbound action: nat service: ftp-outbound address filter: source destination interface: lan wan network:...
Page 176
156 chapter 18. Application layer gateway (alg) activex objects an activex object is a http component, which is downloaded and executed on the client computer. Because it is executed on the client, certain security issues exists, which could cause harm to the local computer system. Javascript/vbscri...
Page 177
18.3. Http 157 url filtering a uniform resource locator (url) is an address to a resource on the www. This can for example be a html page, or a file resource. As a part of a security policy, it might be useful to restrict access to certain sites, or even to block certain file types to be downloaded....
Page 178
158 chapter 18. Application layer gateway (alg) after clicking ok, the configuration page goes to url filtering list. Add − > http url: general action: select blacklist from the dropdown list. Url: enter an undesired address in the edit box. Then click ok. 2. Service – adding the http alg into the c...
Page 179
18.4. H.323 159 • mcus (multipoint control units) terminals a h.323 terminal is a device that is used for audio and optionally video or data communication. For example phones, conferencing units, or software phones (for example: netmeeting) running on standard pcs. Gateways a gateway connects two di...
Page 180
160 chapter 18. Application layer gateway (alg) signal channel is opened between two h.323 endpoints or between a h.323 endpoint and a gatekeeper. For communication between two h.323 endpoints, tcp 1720 is used. When connecting to a gatekeeper, udp port 1719 (h.225 ras messages) are used. H.245 medi...
Page 181
18.4. H.323 161 the h.323 alg supports version 5 of the h.323 specification. This specification is built upon h.225.0 v5 and h.245 v10. In addition to support voice and video calls, the h.323 alg supports application sharing over the t.120 protocol. T.120 uses tcp to transport data while voice and v...
Page 182
162 chapter 18. Application layer gateway (alg) example: protecting a phone behind a d-link firewall figure 18.3: h.323 scenario 1. Using public ip addresses in the first scenario a h.323 phone is connected to a d-link firewall on a network (lan-net) with public ip addresses. To make it possible to ...
Page 183
18.4. H.323 163 webui : 1. Outgoing rule rules − > ip rules − > add − > ip rule: enter the following: name: h323allowout action: allow service: h323 source interface: lan destination interface: any source network: lan-net destination network: 0.0.0.0/0 (all-nets) comment: allow outgoing calls. Then ...
Page 184
164 chapter 18. Application layer gateway (alg) the following rules need to be added to the rule listings in the firewall, make sure there are no rules disallowing or allowing the same kind of ports/traffic before these rules. As we are using private ips on the phone incoming traffic need to be sate...
Page 185
18.4. H.323 165 2. Incoming rules rules − > ip rules − > add − > ip rule: enter the following: name: h323in action: sat service: h323 source interface: any destination interface: core source network: 0.0.0.0/0 (all-nets) destination network: ip-wan (external ip of the firewall) comment: allow incomi...
Page 186
166 chapter 18. Application layer gateway (alg) example: two phones behind different d-link firewalls figure 18.4: h.323 scenario 2. Using public ip addresses this scenario consists of two h.323 phones, each one connected behind a d-link firewall on a network with public ip addresses. In order to pl...
Page 187
18.4. H.323 167 webui : 1. Outgoing rule rules − > ip rules − > add − > ip rule: enter the following: name: h323allowout action: allow service: h323 source interface: lan destination interface: any source network: lan-net destination network: 0.0.0.0/0 (all-nets) comment: allow outgoing calls. Then ...
Page 188
168 chapter 18. Application layer gateway (alg) using private ips on the phones, incoming traffic need to be sated as in the example below. The object ip-phone below should be the internal ip of the h.323 phone behind each firewall. Webui : 1. Outgoing rule rules − > ip rules − > add − > ip rule: en...
Page 189
18.4. H.323 169 rules − > ip rules − > add − > ip rule: enter the following: name: h323in action: allow service: h323 source interface: any destination interface: core source network: 0.0.0.0/0 (all-nets) destination network: ip-wan (external ip of the firewall) comment: allow incoming calls to h.32...
Page 190
170 chapter 18. Application layer gateway (alg) private network where the h.323 phones are connected on the internal network and to the gatekeeper on the dmz. The gatekeeper on the dmz is configured with a private address. The following rules need to be added to the rule listings in both firewalls, ...
Page 191
18.4. H.323 171 rules − > ip rules − > add − > ip rule: enter the following: name: h323in action: allow service: h323-gatekeeper source interface: any destination interface: core source network: 0.0.0.0/0 (all-nets) destination network: ip-wan (external ip of the firewall) comment: allow incoming co...
Page 192
172 chapter 18. Application layer gateway (alg) example: h.323 with gatekeeper and two d-link firewalls figure 18.6: h.323 scenario 4. This scenario is quite similar to scenario 3, with the difference of a d-link firewall protecting the ”external” phones. The d-link firewall with the gatekeeper conn...
Page 193
18.4. H.323 173 webui : 1. Outgoing gatekeeper rule rules − > ip rules − > add − > ip rule: enter the following: name: h323out action: nat service: h323-gatekeeper source interface: lan destination interface: any source network: lan-net destination network: 0.0.0.0/0 (all-nets) comment: allow outgoi...
Page 194
174 chapter 18. Application layer gateway (alg) figure 18.7: h.323 scenario 5. Over the existing telephone network using the gateway (ip-gateway) connected to the ordinary telephone network. Head office firewall configuration the head office has placed a h.323 gatekeeper in the dmz of the corporate ...
Page 195
18.4. H.323 175 webui : 1. Rules − > ip rules − > add − > ip rule: enter the following: name: lantogk action: allow service: gatekeeper source interface: lan destination interface: dmz source network: lan-net destination network: ip-gatekeeper comment: allow h.323 entities on lan-net to connect to t...
Page 196
176 chapter 18. Application layer gateway (alg) 3. Rules − > ip rules − > add − > ip rule: enter the following: name: gwtolan action: allow service: h323 source interface: dmz destination interface: lan source network: ip-gateway destination network: lan-net comment: allow communication from the gat...
Page 197
18.4. H.323 177 5. Rules − > ip rules − > add − > ip rule: enter the following: name: branchtogw action: allow service: h323-gatekeeper source interface: vpn-remote destination interface: dmz source network: remote-net destination network: ip-gatekeeper comment: allow communication with the gatekeep...
Page 198
178 chapter 18. Application layer gateway (alg) webui : 1. Rules − > ip rules − > add − > ip rule: enter the following: name: togk action: allow service: h323-gatekeeper source interface: lan destination interface: vpn-hq source network: lan-net destination network: hq-net comment: allow communicati...
Page 199
18.4. H.323 179 webui : 1. Rules − > ip rules − > add − > ip rule: enter the following: name: gwtogk action: allow service: h323-gatekeeper source interface: dmz destination interface: vpn-hq source network: ip-branchgw destination network: hq-net comment: allow the gateway to communicate with the g...
Page 200
180 chapter 18. Application layer gateway (alg) d-link firewalls user’s guide.
Page 201: Intrusion Detection System
Chapter 19 intrusion detection system (ids) 19.1 overview intrusion detection is a technology that monitors network traffic, searching for signs of security violations, or intrusions. An intrusion can be defined as an attempt to compromise certain parts of a computer system, or to bypass its securit...
Page 202
182 chapter 19. Intrusion detection system (ids) d-link ids uses a combination of intrusion detection rules, pattern matching, and actions, in order to answer the three questions mentioned above. 19.1.1 intrusion detection rules an intrusion detection rule defines the kind of traffic – service – tha...
Page 203
19.2. Chain of events 183 19.2 chain of events the following is a simplified picture of the chain of events when a packet arrives on the firewall, with focus on the ids (note that no other sub-systems are considered here). Two scenarios are possible, one where the firewall rule set has to accept the...
Page 204
184 chapter 19. Intrusion detection system (ids) 1. A packet arrives on the firewall and initial verifications regarding source/destination ip addresses and source/destination ports are performed. If this packet is accepted by the firewall’s ip rule set, a connection will be established between the ...
Page 205
19.2. Chain of events 185 figure 19.2: ids chain of events scenario 2 d-link firewalls user’s guide.
Page 206
186 chapter 19. Intrusion detection system (ids) 3. The pattern-matching engine searches the payload of the packet for pre-defined signatures. If a match is found, the final level of ids processing is carried out – the action. If not, the packet is dropped. 4. As this packet will not be accepted by ...
Page 207
19.5. Smtp log receiver for ids events 187 figure 19.3: signature database update 19.5 smtp log receiver for ids events in order to receive notifications via e-mail of ids events, a smtp log receiver can be configured. This e-mail will contain a summery of ids events that has occurred in a user-conf...
Page 208
188 chapter 19. Intrusion detection system (ids) once an ids event occurs, the intrusion detection rule is triggered. At least one new event occurs within the hold time, 120 seconds, thus reaching the log threshold level (at least 2 events has occurred). This results in an e-mail to be sent, contain...
Page 209
19.6. Scenario: setting up ids 189 19.6 scenario: setting up ids the following example illustrates the steps needed to set up ids for a simple scenario where a mail server is exposed to the internet on the dmz network, with a public ip address, and is to be protected by the ids, as shown in figure 1...
Page 210
190 chapter 19. Intrusion detection system (ids) ids/idp − > ids rules − > add − > ids/idp rule: name: idsmailsrvrule service: smtp also inspect dropped packets: in case all traffic matching this rule should be scanned (this also means traffic that the main rule-set would drop), the ”also inspect dr...
Page 211
P art viii virtual private network ( vpn ).
Page 212
Vpns, virtual private networks, provide means of establishing secure links to parties. It is extended over public networks via the application of encryption and authentication, offering good flexibility, effective protection, and cost efficiency on connections over the internet. Topics in this part ...
Page 213: Vpn Basics
Chapter 20 vpn basics 20.1 introduction to vpn long gone is the time when corporate networks were separate isles of local connectivity. Today, most networks are connected to each other by the internet. Issues of protecting the local networks from internet-based crime and intrusion are being solved b...
Page 214
194 chapter 20. Vpn basics computers began talking to each other. In the beginning, communication was limited to local area communication links, but in time, people were finding reasons to have their computers exchange information across greater distances. Fixed connections are usually very reliable...
Page 215
20.2. Introduction to cryptography 195 another solution is required. From a connectivity and security perspective, virtual private networks may still be viewed as ”fixed connections” in that they do provide connectivity between two or more organizations. This is a fact that does not change even thou...
Page 216
196 chapter 20. Vpn basics symmetric encryption in symmetric encryption, the same key is used for both encryption and decryption. Therefore the key is shared by the sender and the recipients, and must be kept secretly. Using the same secret key is a faster and simpler computation method, but the key...
Page 217
20.2. Introduction to cryptography 197 asymmetric encryption a pair of keys is used in asymmetric encryption, one called a public key, which can be available to anyone who wants to use encryption, and the other, called a private key, that must be kept confidentially and is known only by the owner. T...
Page 218
198 chapter 20. Vpn basics the critical keying information is not transmitted through the insecure connection. 20.2.2 authentication & integrity in addition to encryption, authentication methods are necessary to ensure the integrity and authenticity of encrypted data. One might easily think that enc...
Page 219
20.2. Introduction to cryptography 199 on the sender’s side: - the sender prepares a public-private key pair, and publishes the public one. - a one way function, known as hash function , is operated on a message, and a fixed length message digest is obtained. (the mathematical function is only one-w...
Page 220
200 chapter 20. Vpn basics the ca creates the certificate by signing the authenticating public key and the identity information of the key holder with its own private key. The recipients have copies of ca’s public key to be able to validate the certificate signature and trust the ca and the signed p...
Page 221
20.3. Why vpn in firewalls 201 ◦ in cases where the vpn gateway is located outside the firewall, can the firewall recognize vpn protected traffic from plaintext internet traffic, so that it knows what to pass through to the internal network? ◦ does it require additional configuration to the firewall...
Page 222
202 chapter 20. Vpn basics outside the firewall, on the external network (figure 20.2 ) figure 20.2: vpn deployment scenario 2 ♦ benefits • internet connectivity does not depend on security gateway • the firewall can inspect and log plaintext from the vpn ♦ drawbacks • the security gateway is not pr...
Page 223
20.3. Why vpn in firewalls 203 figure 20.3: vpn deployment scenario 3 • internet connectivity depends on the security gateway • the firewall cannot inspect nor log plaintext from the vpn vpn traffic should not normally be considered to be an integrated part of the internal network. On the internal n...
Page 224
204 chapter 20. Vpn basics in a separate dmz (figure 20.5 ) figure 20.5: vpn deployment scenario 5 ♦ benefits • the firewall can protect the security gateway • internet connectivity does not depend on the security gateway • the firewall can inspect and log plaintext from the vpn ♦ drawbacks • specia...
Page 225
20.3. Why vpn in firewalls 205 figure 20.6: vpn deployment scenario 6 • no special routes need to be added to hosts participating in the vpn • can seamlessly integrate vpn and firewall policies ♦ drawbacks • the integrated security gateway may make the firewall less stable. However, it does not add ...
Page 226
206 chapter 20. Vpn basics d-link firewalls user’s guide.
Page 227: Vpn Planning
Chapter 21 vpn planning 21.1 vpn design considerations ”a chain is never stronger than its weakest link”. An attacker wishing to make use of a vpn connection will typically not attempt to crack the vpn encryption, since this requires enormous amounts of computation and time. Rather, he/she will see ...
Page 228
208 chapter 21. Vpn planning a common misconception is that vpn-connections are equivalents to the internal network from a security standpoint and that they can be connected directly with no further precautions. It is important to remember that although the vpn-connection itself may be secure, the t...
Page 229
21.1. Vpn design considerations 209 end point security for company-owned computers important points that are often included in remote access policies include: • anti-virus software is needed to be installed and updated through the remote connection. • choose a multi-user operating system where the e...
Page 230
210 chapter 21. Vpn planning • if the above requirements cannot be met, for instance, in cases where the home computer belongs to the employee, then do not grant vpn access. End point security for partners and other companies this subject is usually far more sensitive than securing computers that ar...
Page 231
21.1. Vpn design considerations 211 • what happens when an employee in possession of a key leaves the company? If several users are using the same key, it should be changed of course. • in cases where the key is not directly programmed into a network unit such as a vpn gateway, how should the key be...
Page 232
212 chapter 21. Vpn planning d-link firewalls user’s guide.
Page 233: Vpn Protocols & Tunnels
Chapter 22 vpn protocols & tunnels 22.1 ipsec ipsec, internet protocol security, is a set of protocols defined by the ietf(internet engineering task force) to provide ip security at the network layer. It is the most widely used standard for implementing vpns. Ipsec is designed to work for all ip tra...
Page 234
214 chapter 22. Vpn protocols & tunnels the first part, ike, is the initial negotiation phase, where the two vpn endpoints agree on which methods will be used to provide security for the underlying ip traffic. Furthermore, ike is used to manage connections, by defining a set of security associations...
Page 235
22.1. Ipsec 215 tunnel mode – encapsulates the ip header and payload into a new ipsec packet for transfer, which is typically used in the ipsec gateway-to-gateway scenario. In transport mode, the esp protocol inserts an esp header after the original ip header, and in tunnel mode, the esp header is i...
Page 236
216 chapter 22. Vpn protocols & tunnels • authenticate the communication parties, either with pre-shared key (psk) or certificate. • exchange keying materials with diffie-hellman method. • ike sas are created. Ike phase-2 – negotiate how ipsec should be protected. • create a pair of ipsec sas using ...
Page 237
22.1. Ipsec 217 ike & ipsec algorithms there are a number of algorithms used in the negotiation processes. Learning what these algorithms do is essential before attempting to configure the vpn endpoints, since it is of great importance that both endpoints are able to agree on all of these configurat...
Page 238
218 chapter 22. Vpn protocols & tunnels pfs is very resource and time consuming and is generally disabled, since it is very unlikely that any encryption or authentication keys will be compromised. Key exchange ike exchanges the symmetric encryption key using diffie-hellman key exchange protocol. The...
Page 239
22.1. Ipsec 219 address and source port each peer uses is the same as what the other peer sees. If the source address and port have not changed, then the traffic has not been nated along the way, and nat traversal is not necessary. If the source address and/or port has changed, then the traffic has ...
Page 240
220 chapter 22. Vpn protocols & tunnels hashing for integrity to ensure the message integrity during the ike negotiation, some hash functions are used by d-link firewalls to provide message digests for different methods of authentication. The hashing mechanisms ensure that the unchanged messages arr...
Page 241
22.1. Ipsec 221 x.509 certificate the other option for primary authentication is to use x.509 certificate within each vpn gateway. To prove the identity, each gateway owns a certificate signed by a trusted ca. The certificate proves that the public key attached to it truly belongs to the gateway hol...
Page 242
222 chapter 22. Vpn protocols & tunnels identities(ids), where each identity corresponds to the subject field in an x.509 certificate. Identification lists can thus be used to regulate what x.509 certificates are given access to what ipsec connections. Ldap ldap, short for lightweight directory acce...
Page 243
22.1. Ipsec 223 22.1.5 scenarios: ipsec configuration example: configuring a lan-to-lan ipsec tunnel figure 22.1: lan-to-lan example scenario. This example describes how to configure a lan-to-lan ipsec tunnel, used to connect a branch office to the head office network. The head office network use th...
Page 244
224 chapter 22. Vpn protocols & tunnels webui : 1. Pre-shared key first of all we need to create a pre-shared key to use for the ipsec authentication. Objects − > vpn objects − > pre-shared keys − > add − > pre-shared key: enter the following: name: enter a name for the pre-shared key, testkey for i...
Page 245
22.1. Ipsec 225 3. Configure route next step is to configure the route to the ipsec tunnel. Routing − > main routing table − > add − > route: enter the following: interface: ipsectunnel network: on the head office firewall 10.0.2.0/24 and on the branch office firewall 10.0.1.0/24. Then click ok 4. C...
Page 246
226 chapter 22. Vpn protocols & tunnels the following configuration will have to be done on the head office firewall. Webui : 1. Pre-shared key first of all we need to create a pre-shared key to use for the ipsec authentication. Objects − > vpn objects − > pre-shared keys − > add − > pre-shared key:...
Page 247
22.1. Ipsec 227 2. Ipsec tunnel next step is to configure the ipsec tunnel. Interfaces − > ipsec tunnels − > add − > ipsec tunnel: − > general enter the following: name: roamingipsectunnel local network: 10.0.1.0/24 (this is the local network that the roaming users will connect to) remote network: t...
Page 248
228 chapter 22. Vpn protocols & tunnels 22.2 pptp/ l2tp as introduced in the previous sections, ipsec provides methods for two endpoints to transport data packets as they are connecting by a ”private channel ”. Such technique is often called tunneling. Like the functions of ipsec we have discussed, ...
Page 249
22.2. Pptp/ l2tp 229 pptp authentication authentication as an option in pptp is derived directly from ppp, such as: • password authentication protocol (pap) • challenge handshake authentication protocol (chap) • microsoft chap version 1 and version 2 pap is a plaintext authentication scheme by reque...
Page 250
230 chapter 22. Vpn protocols & tunnels example: configuring pptp server this example describes how to set up a pptp server. The lan network is a 192.168.1.0/24 network, and 10.0.0.0/24 is the network on the wan interface. Pptp clients will connect to the pptp server on 10.0.0.1 on the wan interface...
Page 251
22.2. Pptp/ l2tp 231 3. Pptp server next step is to configure the pptp server. Interfaces − > l2tp/pptp servers − > add − > l2tp/pptp server: − > general enter the following: name: pptpserver inner ip address: this is the ip address of the pptp server inside the tunnel. In this case 192.168.1.1 tunn...
Page 252
232 chapter 22. Vpn protocols & tunnels 4. User authentication rule next step is to configure the user authentication rule to use for au- thentication. User authentication − > user authentication rules − > add − > user authentication rule: enter the following: name: pptpuarule agent: ppp authenticat...
Page 253
22.2. Pptp/ l2tp 233 example: configuring pptp client this example describes how to set up a pptp client. The pptp server is located at 10.0.0.1 and all traffic should be routed over the pptp tunnel. Webui : 1. Pptp client first step is to configure the pptp client. Interfaces − > l2tp/pptp clients ...
Page 254
234 chapter 22. Vpn protocols & tunnels 2. Routes the final step is to configure a single-host route to the pptp server over the wan interface. Routing − > main routing table − > add − > route: enter the following: interface: wan network: 10.0.0.1 (ip of the pptp server) gateway: the gateway on the ...
Page 255
22.2. Pptp/ l2tp 235 ip header udp header l2tp header ppp payload ppp frame table 22.2: l2tp encapsulation. L2tp encryption l2tp calls for mppe for encryption. L2tp/ipsec the authentication methods addressed by pptp and l2tp mainly rely on the user’s password, and the encryption to the tunneling dat...
Page 256
236 chapter 22. Vpn protocols & tunnels webui : 1. Pre-shared key first of all we need to create a pre-shared key to use for the ipsec authentication. Objects − > vpn objects − > pre-shared keys − > add − > pre-shared key: enter the following: name: enter a name for the pre-shared key, l2tpkey for i...
Page 257
22.2. Pptp/ l2tp 237 4. Ipsec tunnel next step is to configure the ipsec tunnel. Interfaces − > ipsec tunnels − > add − > ipsec tunnel: − > general enter the following: name: l2tpipsectunnel local network: this is the local network that the remote users will connect to. As we are going to use l2tp t...
Page 258
238 chapter 22. Vpn protocols & tunnels 5. L2tp server next step is to configure the l2tp server. Interfaces − > l2tp/pptp servers − > add − > l2tp/pptp server: − > general enter the following: name: l2tpserver inner ip address: this is the ip address of the l2tp server inside the tunnel. In this ca...
Page 259
22.2. Pptp/ l2tp 239 6. User authentication rule next step is to configure the user authentication rule to use for au- thentication. User authentication − > user authentication rules − > add − > user authentication rule: enter the following: name: l2tpuarule agent: ppp authentication source: local i...
Page 260
240 chapter 22. Vpn protocols & tunnels example: configuring l2tp/ipsec client this example describes how to set up a l2tp client with ipsec, using pre-shared keys. The l2tp server is located at 10.0.0.1 and all traffic should be routed over the l2tp tunnel. Webui : 1. Pre-shared key first of all we...
Page 261
22.2. Pptp/ l2tp 241 2. Ipsec tunnel next step is to configure the ipsec tunnel. Interfaces − > ipsec tunnels − > add − > ipsec tunnel: − > general enter the following: name: l2tpipsectunnel local network: ip of the interface to connect from. Remote network: 10.0.0.1 (as this is where the l2tp/ipsec...
Page 262
242 chapter 22. Vpn protocols & tunnels 3. L2tp client next step is to configure the l2tp client. Interfaces − > l2tp/pptp clients − > add − > l2tp/pptp client: enter the following: name: l2tpclient tunnel protocol: l2tp remote endpoint: 10.0.0.1 (the ip of the l2tp/ipsec server) remote network: 0.0...
Page 263
22.3. Ssl/tls (https) 243 22.3 ssl/tls (https) the secure sockets layer (ssl) protocol is a browser-based secure transaction standard alternative to ipsec-based vpns. It requires little or no software or hardware on remote pcs, and the secure connection is mainly operated by the web browser and the ...
Page 264
244 chapter 22. Vpn protocols & tunnels d-link firewalls user’s guide.
Page 265
P art ix traffic management.
Page 266
Traffic management is concerned with controlling and allocating network bandwidth and minimizing possible delay and congestion on networks. It encompasses the measuring of network capacity and traffic modelling to manage network resources efficiently and provide services the bandwidth they need. Top...
Page 267: Traffic Shaping
Chapter 23 traffic shaping 23.1 overview tcp/ip networks are being called upon to carry traffic belonging to a growing variety of users with diverse service requirements, for example, bulk data transfer, ip telephony, vpns, and multimedia applications. But one of the major drawbacks of tcp/ip is the...
Page 268
248 chapter 23. Traffic shaping choke points in large wans. 23.1.1 functions the simplest way to obtain qos in a network, seen from a security as well as a functionality perspective, is to have the components in the network, known as traffic shapers, be responsible for network traffic control in wel...
Page 269
23.2. Pipes 249 23.1.2 features the traffic shaper in d-link firewalls has the following key features: • pipe based traffic shaping in d-link firewalls is handled by a concept based on ”pipes”, where each pipe has several prioritizing, limiting and grouping possibilities. Individual pipes may be cha...
Page 270
250 chapter 23. Traffic shaping simplistic, in that they do not know much about the types of traffic that pass through them, and they know nothing about the direction either. A pipe simply measures the amount of traffic that passes through it and applies the configured limits in each precedence and/...
Page 271
23.2. Pipes 251 separate bandwidth limits may be specified for each of the 4 precedences with a unit of ”kilobits per second”. Traffic that exceeds the limit of a higher precedence will automatically be transferred into the ”low” level for best effort delivery, as long as there is room in this prece...
Page 272
252 chapter 23. Traffic shaping for any traffic shaper to work, it needs to know the bandwidth passing through the choke point that it is trying to ”protect”. If the connection is shared with other users or servers that are not under the control of the firewall, it is nearly impossible to guarantee ...
Page 273
23.3. Pipe rules 253 23.2.3 dynamic bandwidth balancing as previously stated, per-user bandwidth may be limited by enabling grouping within a pipe. This may be used to ensure that one group cannot consume all of the available bandwidth. But what if the bandwidth for the pipe as a whole has a limit, ...
Page 274
254 chapter 23. Traffic shaping section. Each rule can pass traffic through one or more pipes, in a precedence(priority) of the administrator’s choice. Network traffic is first filtered within the firewall’s normal ip ruleset; if allowed, it is then compared with the pipe rules section and passed to...
Page 275
23.4. Scenarios: setting up traffic shaping 255 webui : 1. Pipes pipe ”std-in” for inbound traffic: enter the following and then click ok. Traffic shaping − > pipes − > add − > pipe: general name: std-in pipe limits total: 1000 pipe ”std-out” for outbound traffic: create the other pipe using the sam...
Page 276
256 chapter 23. Traffic shaping − > traffic shaping pipe chains forward chain: select ”std-out” from available list and put it into selected list. Return chain: select ”std-in” from available list and put it into selected list. Precedence check use fixed precedence select low from the dropdown list ...
Page 277
23.4. Scenarios: setting up traffic shaping 257 example: applying precedence on pipe limits this example shows how to define specific precedences on pipes. We add one more rule on top of ”tointernet” and ”frominternet”, which uses the two standard pipes created in the last example and enables web br...
Page 278
258 chapter 23. Traffic shaping 2. Revising pipe ”std-in” to have a 500kbps limit on precedence ”medium” traffic shaping − > pipes − > std-in: pipe limits precedences: add the following value into the edit box and then click ok. Medium: 500 example: using grouping in a pipe a pipe can be further div...
Page 279
23.4. Scenarios: setting up traffic shaping 259 example: using chains to create differentiated limits more than one pipe can be connected into a pipe chain to make bandwidth limits more restrict. In the previous example–applying precedence on pipe limits, a 500kbps limit on precedence ”medium” is de...
Page 280
260 chapter 23. Traffic shaping note an appropriate order for pipes in a chain must be set carefully. D-link firewalls user’s guide.
Page 281
Chapter 24 server load balancing (slb) 24.1 overview server load balancing (slb) is a mechanism dealing with distributing the traffic load across multiple servers to scale beyond the capacity of one single server, and to tolerate a server failure. This technology is integrated in d-link firewalls to...
Page 282
262 chapter 24. Server load balancing (slb) figure 24.1: a slb logical view. Server load balancer an appliance to perform the functions of slb, listening to the coming requests, deciding the traffic distribution mode and algorithm, rerouting the traffic to a certain sever within the server farm, and...
Page 283
24.1. Overview 263 tracking the status of the servers, and noticing the load distribution to redirect traffic if there is any server failure. 24.1.3 benefits the slb solution provides more advanced and flexible traffic management, and stronger processing power, compared to a single sever implementat...
Page 284
264 chapter 24. Server load balancing (slb) 24.2 slb implementation to implement the slb method, the administrator defines a server farm containing multiple real servers, and binds the server farm as a single virtual server to the d-link firewall (load balancer), using a public ip address. In this e...
Page 285
24.2. Slb implementation 265 d-link firewalls offer the following algorithms to accomplish the load distribution tasks: 1. Round-robin algorithm: the algorithm distributes new coming connections to a list of servers on a rotating bases. For the first connection, the algorithm picks a server from the...
Page 286
266 chapter 24. Server load balancing (slb) an example is shown in the figures below (figure 24.2 , figure 24.3 , and figure 24.4 ). In this example, the firewall is responsible for balancing connections from 3 clients with different addresses to 2 servers. Stickiness is set. When round robin algori...
Page 287
24.2. Slb implementation 267 figure 24.3: distribution by stickiness and round-robin algorithm figure 24.4: distribution by stickiness and connection-rate algorithm d-link firewalls user’s guide.
Page 288
268 chapter 24. Server load balancing (slb) destination host unreachable message will be sent by the firewall once the active server list is empty. Icmp ping at osi layer 3, the check involves a ping to the real server’s ip address to see whether the server is up and running. Tcp connection at osi l...
Page 289
24.3. Scenario: enabling slb 269 example: slb configuration figure 24.5: a slb scenario this example describes how slb can be used to load balance ssh connections to two ssh servers behind a d-link firewall connected to the internet with ip address ip ext, as shown in figure 24.5 . The two ssh serve...
Page 290
270 chapter 24. Server load balancing (slb) 2. Create sat slb rule next step is to set up the sat slb rule. Rules − > ip rules − > add − > ip rule: name: ssh slb action: slb sat service: ssh source interface: any source network: all-nets destination interface: core destination network: ip ext sat se...
Page 291
P art x misc . Features.
Page 292
Besides safety protection to the network, d-link firewalls can act as intermediary agents for miscellaneous internet services to ease the use of various protocols on behalf of the clients. Topics in this part includes: • miscellaneous clients • dhcp server & relayer.
Page 293: Miscellaneous Clients
Chapter 25 miscellaneous clients 25.1 overview d-link firewalls offer supports to miscellaneous network clients for dynamic dns and similar services. Currently, the services providers that are supported by the firewall include: • dyndns.Org • dyns.Cx • cjb.Net • oray.Net – peanut hull dyndns • telia...
Page 294
274 chapter 25. Miscellaneous clients contacting the dns service each time the ip address provided by the isp changes and subsequently updating the dns database to reflect the change in ip address. This method allows the user’s machine to have a domain name that always points to it, even though the ...
Page 295
25.4. Http poster 275 • bigpond – used by telstra, a broadband and multimedia service provider. Authenticates using the interface (which should be dhcp enabled) associated with the default route. 25.4 http poster http poster is a function to enable automatic client login, or domain names and ip addr...
Page 296
276 chapter 25. Miscellaneous clients d-link firewalls user’s guide.
Page 297: Dhcp Server & Relayer
Chapter 26 dhcp server & relayer 26.1 dhcp server the dhcp server implement the task to assign and manage ip addresses from specified address pools to dhcp clients. When a dhcp server receives a request from a dhcp client, it returns the configuration parameters (such as an ip address, a mac address...
Page 298
278 chapter 26. Dhcp server & relayer example: configuring the firewall as a dhcp server this example describes how to configure a dhcp server on the internal interface (lan)(refer to 9.1.2 , ethernet interfaces in d-link firewalls). Webui : • configure dhcp server system − > dhcp settings − > dhcp ...
Page 299
26.2. Dhcp relayer 279 26.2 dhcp relayer in dhcp implementation, the clients send requests to locate the dhcp server(s) by broadcast messages. However, broadcasts are normally only propagated on the local network. This means that the dhcp server and client would always need to be in the same physica...
Page 300
280 chapter 26. Dhcp server & relayer webui : 1. Interface group: – adding the vlan interfaces ”vlan1” and ”vlan2” that should relaying to an interface group named as ”ipgrp-dhcp”. Interface − > interface groups − > add − > interface group: name: ipgrp-dhcp interfaces: select ”vlan1” and ”vlan2” fro...
Page 301
P art xi transparent mode.
Page 303: Transparent Mode
Chapter 27 transparent mode the transparent mode feature provided by d-link firewalls aims at simplifying the deployment of firewall appliances into the existing network topology, to strengthen security. It helps to ease the administration work in a way that there is no need to reconfigure all the s...
Page 304
284 chapter 27. Transparent mode • enhanced security – the firewall should be capable of screening the in/out traffic by the defined security rules. D-link firewalls can work in two modes: routing mode & transparent mode. In normal routing mode, the firewall acts as a layer 3 router. If the firewall...
Page 305
27.2. Transparent mode implementation in d-link firewalls 285 • create a switch route – as interface, select the interface group created earlier. As network, specify the address range that should be transparent between the interfaces. When the whole firewall is working in transparent mode this is no...
Page 306
286 chapter 27. Transparent mode if the cam table or the layer 3 cache is full, the tables are partially flushed automatically. Using the discovery mechanism, the firewall will rediscover destinations that may have been flushed. 27.3 scenarios: enabling transparent mode example: transparent mode sce...
Page 307
27.3. Scenarios: enabling transparent mode 287 all traffic passing through the firewall will have to pass through the ip rule set. To allow http traffic, a new ip rule has to be configured. (refer to 14.3 scenario .) webui : 1. Interfaces interfaces − > ethernet − > edit (wan): enter the following: ...
Page 308
288 chapter 27. Transparent mode example: transparent mode scenario 2 figure 27.2: transparent mode scenario 2. Scenario 2 shows how a firewall in transparent mode can be used to separate server resources from the internal network by attaching them to a separate firewall interface without the need o...
Page 309
27.3. Scenarios: enabling transparent mode 289 this scenario shows how to configure a switch route over the lan and dmz interfaces for the 10.0.0.0/24 address space. It is assumed that the wan interface has been configured correctly already. Webui : 1. Interfaces interfaces − > ethernet − > edit (la...
Page 310
290 chapter 27. Transparent mode 4. Rules rules − > ip rules − > add − > ip rule: enter the following: name: http-lan-to-dmz action: allow service: http source interface: lan destination interface: dmz source network: 10.0.0.0/24 destination network: 10.1.4.10 then click ok rules − > ip rules − > ad...
Page 311
P art xii zonedefense.
Page 312
*zonedefense functionality described in this part is only available in the d-link firewall modules dfl-800/1600/2500..
Page 313: Zonedefense
Chapter 28 zonedefense 28.1 overview zonedefense is a feature in d-link firewalls, which lets the firewall control locally attached switches. This can be used as a countermeasure to stop a worm-infected computer in the local network from infecting other computers. By setting up threshold rules on th...
Page 314
294 chapter 28. Zonedefense • the ip address of the management interface of the switch • the switch model type • the snmp community string (write access) currently, zonedefense feature supports the following switches: - d-link des 3226s (minimum firmware: r4.02-b14) - d-link des 3250tg (minimum firm...
Page 315
28.3. Threshold rules 295 managed devices the managed devices are snmp compliant, such as d-link switches. They store management data in their databases, known as management information base (mib), and provide the information to the manager upon queries. 28.3 threshold rules as explained previously,...
Page 316
296 chapter 28. Zonedefense adding the firewall’s interface ip or mac address connecting towards the zonedefense switch to the exclude list. This prevents the firewall from being accidentally blocked out. 28.5 limitations depending on the switch model, various limitations are in effect. The first on...
Page 317
28.6. Scenario: setting up zonedefense 297 figure 28.1: a zonedefense scenario. A d-link switch model des-3226s is used in this case, with a management interface address 192.168.1.250 connecting to the firewall’s interface address 192.168.1.1. This firewall interface is added into the exclude list t...
Page 318
298 chapter 28. Zonedefense 2. Exclude list – adding the firewall’s management interface into the exclude list. Zonedefense − > exclude: general addresses: choose the object name of the firewall’s interface address 192.168.1.1 from available list and put it into selected list. Then click ok. 3. Thre...
Page 319
P art xiii high availability.
Page 320
* high availability functionality described in this part is only available in the d-link firewall modules dfl-1600/2500..
Page 321: High Availability
Chapter 29 high availability 29.1 high availability basics this section includes the following topics: • what high availability will do for you • what high availability will not do for you • example high availability setup d-link high availability works by adding a back-up firewall to your existing ...
Page 322
302 chapter 29. High availability connection table and other vital information, is continuously copied to the inactive firewall. When the cluster fails over to the inactive firewall, it knows which connections are active, and communication may continue to flow uninterrupted. The failover time is typ...
Page 323
29.2. How rapid failover is accomplished 303 29.1.3 example high availability setup all the interfaces of the primary firewall need to be present on the back-up firewall, and connected to the same networks. As previously mentioned, failover is not done unnecessarily, so either firewall may maintain ...
Page 324
304 chapter 29. High availability this section will detail the outward-visible characteristics of the failover mechanism, and how the two firewalls work together to create a high availability cluster with very low failover times. For each cluster interface, there are three ip addresses: • two ”real”...
Page 325
29.2. How rapid failover is accomplished 305 when a firewall discovers that its peer is no longer operational, it will broadcast a number of arp queries for itself, using the shared hardware address as sender address, on all interfaces. This causes switches and bridges to re-learn where to send pack...
Page 326
306 chapter 29. High availability • it is an udp packet, sent from port 999, to port 999. • the destination mac address is the ethernet multicast address corresponding to the shared hardware address, i.E. 11-00-00-c1-4a-nn. Link-level multicasts were chosen over normal unicast packets for security r...
Page 327
29.3. Setting up a high availability cluster 307 the topics below describe the operations required to setup a complete high availability cluster. 29.3.1 planning the high availability cluster as an example throughout this guide, two d-link firewalls are used as cluster members. To simplify this guid...
Page 328
308 chapter 29. High availability webui : 1. Ha configuration system − > high availability: enable high availability: enable cluster id: 0 (select a suitable cluster id) sync interface: dmz (in this example we use the dmz interface as sync interface) node type: master or slave then click ok 2. Ha ad...
Page 329
29.4. Things to keep in mind 309 note all ethernet and vlan interfaces will have to be assigned a private ip address when the firewall is configured to be a ha member. However, in this example we only showed how to configure the lan and wan interfaces. Note that it is possible to use the same ha ip4...
Page 330
310 chapter 29. High availability 29.4.2 configuration issues when configuring high availability clusters, there are a number of things to keep in mind in order to avoid unnecessary pitfalls. Changing the cluster id by changing the cluster id, you actually doing two things: • changing the hardware a...
Page 331
P art xiv appendix.
Page 333: Index
Index abr, 75 acl, 293 activex, 156 aes, 196 ah, 214 alg, 47 arp, 27 arp, 66 as, 70 asbrs, 75 backbone area, 74 bdr, 75 blowfish, 196 bootp, 60 brute force attack, 196 ca, 49 , 199 cast, 196 certificate, 49 , 199 , 221 chap, 62 , 134 , 135 , 229 crl, 50 , 200 , 222 cryptography, 195 des, 196 dh grou...
Page 334
314 index ike, 213 ike xauth, 222 ip address, 39 ip spoofing, 123 ipsec, 27 , 213 l2tp, 27 , 228 lan, 53 , 56 lcp, 62 ldap, 50 , 222 lsa, 76 man-in-the-middle attack, 198 , 229 mcus, 159 mib, 295 mppe, 229 nat, 112 , 218 nat, 112 ncps, 62 ntp, 98 osi, 7 ospf, 73 , 74 pap, 62 , 135 , 229 pbr, 88 pfs,...
Page 335: Console Commands Reference
Appendix a console commands reference this appendix contains the list of commands that can be used in cli for monitoring and troubleshooting the firewall. For information about how to access the cli from a pc or terminal, please refer to 4.2 , monitoring via cli . List of commands about brings up in...
Page 336
316 chapter a. Console commands reference access displays the contents of the access configuration section. • syntax: access example: cmd> access source ip address access list (spoofing protection) rule name action iface source range ----------------- ------ ----------------- ------------- if no acc...
Page 337
317 arpsnoop toggles the on-screen display of arp queries. This command can be of great help in configuring firewall hardware, since it shows which ip addresses are heard on each interface. • syntax: - arpsnoop toggle snooping on given interfaces. - arpsnoop all snoop all interfaces. - arpsnoop none...
Page 338
318 chapter a. Console commands reference cmd> buffers displaying the 20 most recently freed buffers recvif num size protocol sender destination ------ ---- --- -------- --------------- --------------- wan 1224 121 udp 192.168.3.183 192.168.123.137 lan 837 131 udp 192.168.123.137 192.168.3.183 wan 4...
Page 339
319 cfglog shows the results of the most recent reconfiguration or start up of the firewall. This text is the same as is shown on-screen during reconfiguration or start up. • syntax: cfglog example: cmd> cfglog configuration log: license file successfully loaded. Configuration done connections shows...
Page 340
320 chapter a. Console commands reference example: cmd> conn state proto source destination tmout --------- ----- ------------------ ---------------- ------ tcp open tcp wan:60.20.37.6:5432 dmz:wwwsrv:80 3600 syn recv tcp wan:60.20.37.6:5433 dmz:wwwsrv:80 30 udp open udp lan:10.5.3.2:5433 dmz:dnssrv...
Page 341
321 example: cmd> dhcp -renew wan dhcprelay show the contents of the dhcp-relay configuration section. • syntax: dhcprelay [options] • options: - release ip – releases the ip and removes associated routes from the firewall. Example: cmd> dhcprelay dhcpserver show the contents of the dhcp-server conf...
Page 342
322 chapter a. Console commands reference dynroute displays the dynamic routing policy filter ruleset and current exports. • syntax: dynroute [options] • options: - rules – display dynamic routing filter ruleset - exports – display current exports frags shows the 20 most recent fragment reassembly a...
Page 343
323 httpposter show the configured httpposter urls and status. • syntax: httpposter [options] • options: - repost – re-post all urls now. D-link firewalls user’s guide.
Page 344
324 chapter a. Console commands reference example: cmd> httpposter httpposter url1: host : "" port : 0 path : "" post : "" user : "" pass : "" status: (not configured) ... Ifacegroups shows the configured interface groups. • syntax: ifacegroups example: cmd> ifacegroups configured interface groups -...
Page 345
325 -- ifstat shows hardware and software statistics for the specified nic. Example: cmd> ifstat lan iface lan ... Mtu : ... Ip address : ... Hw address : ... Software statistics: soft received: ... Soft sent: ... Send failures: ... Dropped: ... Ip input errs: ... Driver information / hardware stati...
Page 346
326 chapter a. Console commands reference ipseckeepalive shows the status of the configured ipsec keepalive connections. • syntax: ipseckeepalive example: cmd> ipseckeepalive 192.168.0.10 -> 192.168.1.10: consecutive lost: 0, sent: 908, lost: 2 192.168.1.10 -> 192.168.0.10: consecutive lost: 0, sent...
Page 347
327 - num maximum number of entries to display (default: 40/8) note: if set to 0, all entries will be displayed example: cmd> ipsecstats --- ipsec sas: displaying one line per sa-bundle ... Killsa kills all ipsec and ike sas for the specified ip-address. • syntax: killsa example: cmd> killsa 192.168...
Page 348
328 chapter a. Console commands reference lockdown sets local lockdown on or off. During local lockdown, only traffic from admin nets to the firewall itself is allowed. Everything else is dropped. Note: if local lockdown has been set by the core itself due to licensing or configuration problems, thi...
Page 349
329 netobjects displays the list of named network objects and their contents. If a netobject is specified the output will show user authentication information associated with that object. • syntax: netobjects [options] • options: - num maximum objects listed (default: 20) - dump make netobject dump ...
Page 350
330 chapter a. Console commands reference • debug parameters: - spf, performs full spf calculation - refresh, refreshes all self originated lsas in the process - ifacemetric , changes the metric of a interface ping sends a specified number of icmp echo request packets to a given destination. All pac...
Page 351
331 - u display users of a given pipe example: cmd> pipes configured pipes: name grouping bits/s pkts/s precedence ----- ------- ------ ------ ---------- std-in per destip 0 1 7 current: 42.5 k 21.0 ... Proplists lists the configured proposal lists. • syntax: proplists [vpnconn] example: cmd> propl ...
Page 352
332 chapter a. Console commands reference remotes shows the contents of the remotes configuration section. • syntax: remotes example: cmd> remotes hosts/nets with remote control of firewall: ... Webui http (port 80) and https (port 443) access routes displays information about the routing tables, co...
Page 353
333 rules shows the contents of the rules configuration section. • syntax: rules [options] the range parameter specifies which rules to include in the output of this command. • options: - r, show policy based routing ruleset - p, show pipe ruleset - i, show intrusion detection ruleset - t, show thre...
Page 354
334 chapter a. Console commands reference services displays the list of named services. Services implicitly defined inside rules are not displayed. • syntax: services [name or wildcard] example: cmd> services configured services: http tcp all > 80 shutdown instructs the firewall to perform a shutdow...
Page 355
335 example: cmd> sett available categories in the settings section: ip - ip (internet protocol) settings tcp - tcp (transmission control protocol) settings icmp - icmp (internet control message protocol) arp - arp (address resolution protocol) settings state - stateful inspection settings conntimeo...
Page 356
336 chapter a. Console commands reference -- settings shows the settings of the specified group. Example: cmd> settings arp arp (address resolution protocol) settings arpmatchenetsender : droplog arpquerynosenderip : droplog arpsenderip : validate unsolicitedarpreplies : droplog arprequests : drop a...
Page 357
337 time displays the system date and time • syntax: time [options] • options: - set , set system local time (yyyy-mm-dd hh:mm:ss) - sync, synchronize time with timeserver(s) (specified in settings) - force, force synchronization regardless of the maxadjust setting uarules displays the contents of t...
Page 358
338 chapter a. Console commands reference - v , displays all known info for user(s) with this ip - r , forcibly logs out an authenticated user - num , maximum number of authenticated users to list (default 20) example: cmd> userauth -l currently authenticated users: login ip address source ses/idle ...
Page 359
339 example: cmd> userdb adminusers configured user databases: username groups static ip remote networks -------- -------------- ---------- ----------------- admin administrators example: cmd> userdb adminusers admin information for admin in database adminusers: username : admin groups : administrat...
Page 360
340 chapter a. Console commands reference -- vlan show information about specified vlan. Example: cmd> vlan vlan1 vlan vlan1 iface lan, vlan id: 1 iface : lan ip address : 192.168.123.1 hw address : 0003:474e:25f9 software statistics: soft received : 0 soft sent: 0 send failures: 0 dropped : 0 ip in...
Page 361: Customer Support
Appendix b customer support 341.
Page 362
342 chapter b. Customer support international offices u.S.A 17595 mt. Herrmann street fountain valley, ca 92708 tel: 1-800-326-1688 url: www.Dlink.Com canada 2180 winston park drive oakville, ontario, l6h 5w1 canada tel: 1-905-8295033 fax: 1-905-8295223 url: www.Dlink.Ca europe (u. K.) 4th floor, me...
Page 363
343 norway karihaugveien 89 n-1086 oslo norway tel: +47 99 300 100 fax: +47 22 30 95 80 url: www.Dlink.No finland latokartanontie 7a fin-00700 helsinki finland tel: +358-10 309 8840 fax: +358-10 309 8841 url: www.Dlink.Fi spain avenida diagonal, 593-95, 9th floor 08014 barcelona spain tel: 34 93 409...
Page 364
344 chapter b. Customer support australia 1 giffnock avenue north ryde, nsw 2113 australia tel: 61-2-8899-1800 fax: 61-2-8899-1868 url: www.Dlink.Com.Au india d-link house, kurla bandra complex road offcst road, santacruz (east) mumbai - 400098 india tel: 91-022-26526696/56902210 fax: 91-022-2652891...
Page 365
345 russia grafsky per., 14, floor 6 moscow 129626 russia tel: 7-495-744-0099 fax: 7-495-744-0099 #350 url: www.Dlink.Ru china no.202,c1 building, huitong office park, no. 71, jianguo road, chaoyang district, beijing 100025, china tel +86-10-58635800 fax: +86-10-58635799 url: www.Dlink.Com.Cn taiwan...
Page 366
346 chapter b. Customer support d-link firewalls user’s guide.