- DL manuals
- D-Link
- Network Router
- DWC-1000
- User Manual
D-Link DWC-1000 User Manual
Summary of DWC-1000
Page 1
User manual wireless controller d-link corporation copyright © 2011. Http://www.Dlink.Com.
Page 2
Wireless controller user manual 1 user manual dwc-1000 wireless controller version 1.3 copyright © 2011 copyright notice this publication, including all photographs, illustrations and software, is protected under international copyright laws, with all rights reserved. Neither this manual, nor any of...
Page 3: Table Of Contents
Wireless controller user manual 2 table of contents chapter 1. Introduction ............................................................................................................................. 9 1.1 about this user manual ........................................................................
Page 4
Wireless controller user manual 3 4.4 access point status ................................................................................................ 64 4.5 global status ........................................................................................................... 69 4.6 wireless ...
Page 5
Wireless controller user manual 4 8.3.1 wids ap configration ............................................................................................ 154 8.3.2 wids client configuration ..................................................................................... 157 chapter 9. Administr...
Page 6: List Of Figures
Wireless controller user manual 5 list of figures figure 1: setup page for lan tcp/ip settings ...................................................................................... 13 figure 2: ipv6 lan and dhcpv6 configuration ..........................................................................
Page 7
Wireless controller user manual 6 figure 33: physical port statistics ............................................................................................................. 61 figure 34: list of current active firewall sessions ....................................................................
Page 8
Wireless controller user manual 7 figure 67: available alg support on the controller. ............................................................................ 108 figure 68: passthrough options for vpn tunnels ................................................................................. 109 ...
Page 9
Wireless controller user manual 8 figure 99: list of available applications for ssl port forwarding .................................................... 146 figure 100: ssl vpn client adapter and access configuration ......................................................... 147 figure 101: configure...
Page 10: Chapter 1. Introduction
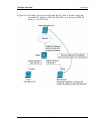
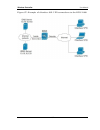
Wireless controller user manual 9 chapter 1. Introduction d-link wireless controller (dwc), dwc-1000, is a full-featured wireless lan controller designing for small network environment. The centralized control function contains various access point management functions, such as fast -roaming, inter-...
Page 11
Wireless controller user manual 10 1.2 typographical conventions the following is a list of the various terms, followed by an example of how that term is represented in this document: product name – d-link wireless controller. O model numbers dwc-1000 gui menu path/gui navigation – monitoring > cont...
Page 12: 2.1 Lan Configuration
Chapter 2. Configuring your network: it is assumed that the user has a machine for management connected to the lan to the controller. The lan connection may be through the wired ethernet ports available on the controller, or once the initial setup is complete, the dwc may also be managed through its...
Page 13
Wireless controller user manual 12 to configure lan connectivity, please follow the steps below: 1. In the lan setup page, enter the following information for your controller: ip address: (factory default: 192.168.10.1). If you change the ip address and click save settings, the gui will not respond....
Page 14
Wireless controller user manual 13 domain name: enter domain name wins server (optional): enter the ip address for the wins server or, if present in your network, the windows netbios server. Lease time: enter the time, in hours, for which ip addresses are leased to clients. Enable dns proxy: to enab...
Page 15
Wireless controller user manual 14 2.1.1 lan configuration in an ipv6 network advanced > ipv6 > ipv6 lan > ipv6 lan config in ipv6 mode, the lan dhcp server is enabled by default (similar to ip v4 mode). The dhcpv6 server will serve ipv6 addresses from configured address pools with the ipv6 prefix l...
Page 16
Wireless controller user manual 15 figure 2: ipv 6 l an and dh cpv6 c onf iguration if you change the ip address and click save settings, the gui will not respond. Open a new connection to the new ip address and log in again. Be sure the lan host (the machine used to manage the router) has obtained ...
Page 17
Wireless controller user manual 16 the following settings are used to configure the dhcpv6 server: dhcp mode: the ipv6 dhcp server is either state less or stateful. If stateless is selected an external ipv6 dhcp server is not required as the ipv6 lan hosts are auto-configured by this controller. In ...
Page 18
Wireless controller user manual 17 2.1.2 configuring ipv6 router advertisements router advertisements are analogous to ipv4 dhcp assignments for lan clients, in that the router will assign an ip address and supporting network information to devices that are configured to accept such details. Rout er...
Page 19
Wireless controller user manual 18 figure 3: co nf iguri ng the ro uter adverti se m ent dae mon advertisement prefixes advanced > ipv6 > ipv6 lan > advertisement prefixes the router advertisements configured with advertisement prefixes allow this router to inform hosts how to perform stateless addr...
Page 20: 2.2 Vlan Configuration
Wireless controller user manual 19 ipv6 prefix length: this value indicates the number contiguous, higher order bits of the ipv6 address that define up the network portion of the address. Typically this is 64. Prefix lifetime: this defines the duration (in seconds) that the requesting node is allowe...
Page 21
Wireless controller user manual 20 will allow traffic from lan hosts belonging to this vlan id to pass through to other configured vlan ids that have inter vlan routing enabled. Figure 5: addi ng vlan me mber shi ps to the l an 2.2.1 associating vlans to ports in order to tag all traffic through a s...
Page 22
Wireless controller user manual 21 to the switch port on the controller will be tagged. Data passing through the phone from a connected device will be untagged. Figure 6: port vlan list in access mode the port is a member of a single vlan (and only one). All data going into and out of the port is un...
Page 23
Wireless controller user manual 22 figure 7: co nf iguri ng vlan me mbership f or a por t 2.3 configurable port: dmz setup this controller supports one of the physical ports to be configured as a secondary wan ethernet port or a dedicated dmz port. A dmz is a subnetwork that is open to the public bu...
Page 24
Wireless controller user manual 23 figure 8: dm z c onf iguratio n in order to configure a dmz port, the controller configurable port must be set to dmz in the setup > internet settings > configurable port page. 2.4 universal plug and play (upnp) advanced > advanced network > upnp universal plug and...
Page 25
Wireless controller user manual 24 advertisement period: this is the frequency that the controller broadcasts upnp information over the network. A large value will minimize network traffic but cause delays in identifying new upnp devices to the network. Advertisement time to live: this is expressed ...
Page 26: 2.5 Captive Portal
Wireless controller user manual 25 2.5 captive portal lan users can gain internet access via web portal authentication with the dwc. Also referred to as run-time authentication, a captive portal is ideal for a web café scenario where users initiate http connection requests for web access but are not...
Page 27
Wireless controller user manual 26 disabling the wlan controller does not affect non-wlan features on the controller, such as vlan or stp functionality. Wlan controller operational status: shows the operational status of the controller . The status can be one of the following values: • enabled • ena...
Page 28
Wireless controller user manual 27 installed and enabled, this is the ip address of the routing or loo pback interface you configure for the controller features. Ap mac validation method: add the mac address of the ap to the valid ap database, which can be kept locally on the controller or in an ext...
Page 29
Wireless controller user manual 28 2.6.1 wireless discovery configuration the wireless controller can discover, validate, authenticate, or monitor the following system devices: • peer wireless controllers • aps • wireless clients • rogue aps • rogue wireless clients setup > ap management > poll list...
Page 30
Wireless controller user manual 29 figure 12 : conf iguri ng t he wirele ss di sc overy l2/vlan discovery: the d-link wireless device discovery protocol is a good discovery method to use if the controller and aps are located in the same layer 2 multicast domain. The wireless controller periodically ...
Page 31
Wireless controller user manual 30 wireless discovery status status > global info > ip discovery the ip discovery list can contain the ip addresses of peer controller and aps for the uws to discover and associate with as part of the wlan ip address: shows the ip address of the device configured in t...
Page 32
Wireless controller user manual 31 2.6.2 ap profile global configuration advanced > ap profile access point profile summary page, you can add, copy, edit, delete ap profiles. To add a new profile, click add in ap profile summary page. In the ap profile global configuration page, enter the name of th...
Page 33
Wireless controller user manual 32 wired network discovery vlan id: enter the vlan id that the controller uses to send tracer packets in order to detect aps connected to the wired network. Ap profile advanced > ap profile access point configuration profiles are a useful feature for large wireless ne...
Page 34
Wireless controller user manual 33 figure 15 : ap prof ile list for each ap profile, you can configure the following features: • profile settings (name, hardware type id, wired network discovery vlan id) • radio settings • ssid settings profile: the access point profile name you added. Use 0 to 32 c...
Page 35
Wireless controller user manual 34 during this process the aps reset, and all wireless clients are disassociated from the ap. • configured: the profile is configured, but no aps managed by the controller currently use this profile. Associate a profile with an ap. Entry of the ap is valid and availab...
Page 36: Wan Setup
Wireless controller user manual 35 chapter 3. Connecting to the internet: wan setup this contoller has two wan ports that can be used to establish a connection to the internet. The following isp connection types are supported: dhcp, static, pppoe, pptp, l2tp (via usb modem). It is assumed that you h...
Page 37: 3.2 Wan Configuration
Wireless controller user manual 36 button, which confirms the settings by establishing a link with the isp. Once connected, you can move on and configure other features in this controller. 3.2 wan configuration setup > internet settings > option1 setup you must either allow the controller to detect ...
Page 38: 3.2.2 Wan Dns Servers
Wireless controller user manual 37 server ip address: enter the ip address of the pptp or l2tp server. 3.2.1 wan port ip address your isp assigns you an ip address that is either dynamic (newly generated each time you log in) or static (permanent). The ip address source option allows you to define w...
Page 39: 3.2.4 Pppoe
Wireless controller user manual 38 figure 17 : ma nual optio n1 co nf igurati on 3.2.4 pppoe setup > internet settings the pppoe isp settings are defined on the wan configuration page. There are two types of pppoe isp‘s supported by the dwc-1000: the standard username/password pppoe and japan multip...
Page 40
Wireless controller user manual 39 figure 18 : pppoe co nf iguratio n f or sta ndard isps most pppoe isp‘s use a single control and data connection, and require username / password credentials to login and authenticate the dwc-1000 with the isp. The isp connection type for this case is ―pppoe (usern...
Page 41
Wireless controller user manual 40 figure 19 : option1 c onf igurati on f or japanese multi ple pppo e (part 1 ) there are a few key elements of a multiple pppoe connection: primary and secondary connections are concurrent each session has a dns server source for domain name lookup, this can be assi...
Page 42
Wireless controller user manual 41 when japanese multiple pppoe is configured and secondary connection is up, some predefined routes are added on that interface. These routes are needed to access the internal domain of the isp where he hosts various services. These routes can even be configured thro...
Page 43
Wireless controller user manual 42 figure 21 : russia l2 tp isp co nf iguratio n 3.2.6 wan configuration in an ipv6 network advanced > ipv6 > ipv6 option1 config for ipv6 wan connections, this controller can have a static ipv6 address or receive connection information when configured as a dhcpv6 cli...
Page 44
Wireless controller user manual 43 when the isp allows you to obtain the wan ip sett ings via dhcp, you need to provide details for the dhcpv6 client configuration. The dhcpv6 client on the gateway can be either stateless or stateful. If a stateful client is selected the gateway will connect to the ...
Page 45
Wireless controller user manual 44 when ipv6 is pppoe type, the following pppoe fields are enabled. Username: enter the username required to log i n to the isp. Password: enter the password required to login to the isp. Authentication type: the type of authentication in use by the profile: auto - ne...
Page 46
Wireless controller user manual 45 figure 23 : connecti on sta tus i nf ormatio n of opti on1 the wan status page allows you to enable or disable static wan links. For wan settings that are dynamically received from the isp, you can renew or release the link parameters if required. 3.3 features with...
Page 47: 3.3.1 Auto Failover
Wireless controller user manual 46 setup > internet settings > option mode to use auto failover or load balancing, wan link failure detection must be configured. This involves accessing dns servers on the internet or ping to an internet address (user defined). If required, you can configure the numb...
Page 48
Wireless controller user manual 47 and let low-volume background traffic (such as smtp) go over the lower speed link. Protocol binding is explained in next section. Spill over: if spill over method is selected, wan1 acts as a dedicated link till a threshold is reached. After this, wan2 will be used ...
Page 49: 3.3.3 Protocol Bindings
Wireless controller user manual 48 figure 24 : lo ad bal ancing i s av ailable when multi ple w an ports are conf igured and pro t ocol bindi ng s have been def in e d 3.3.3 protocol bindings advanced > routing > protocol bindings protocol bindings are required when the load balancing feature is in ...
Page 50: 3.4.1 Routing Mode
Wireless controller user manual 49 applicable when load balancing mode is enabled and more than one wan is configured. Figure 25 : protocol binding se tup to a ssociate a service a nd/ or lan so urce to a w an and/or desti na tion net work 3.4 routing configuration routing between the lan and wan wi...
Page 51
Wireless controller user manual 50 nat is a technique which allows several computers on a lan to share an internet connection. The computers on the lan use a "private" ip address range while the wan port on the controller is configured with a single "public" ip address. Along with connection sharing...
Page 52
Wireless controller user manual 51 figure 26 : routing mode is use d to conf igure tr af f ic routi ng between wan and lan, as well as dy na mic ro uti ng ( rip).
Page 53
Wireless controller user manual 52 3.4.2 dynamic routing (rip) setup > internet settings > routing mode dynamic routing using the routing information protocol (rip) is an interior gateway protocol (igp) that is common in lans . With rip this controller can exchange routing information with other sup...
Page 54: 3.4.3 Static Routing
Wireless controller user manual 53 3.4.3 static routing advanced > routing > static routing advanced > ipv6 > ipv6 static routing manually adding static routes to this device allows you to define the path selection of traffic from one interface to another. There is no communication between this cont...
Page 55: 3.5 Wan Port Settings
Wireless controller user manual 54 figure 27 : static ro ute co nf igurati on f ie lds 3.5 wan port settings advanced > advanced network > option port setup the physical port settings for each wan link can be defin ed here. If your isp account defines the wan port speed or is associated with a mac a...
Page 56
Wireless controller user manual 55 figure 28 : physical wan por t settings.
Page 57: Statistics
Wireless controller user manual 56 chapter 4. Monitoring status and statistics 4.1 system overview the status page allows you to get a detailed overview of the system configuration. The settings for the wired and wireless interfaces are displayed in the dwc-1000 status page, and then the resulting h...
Page 58
Wireless controller user manual 57 figure 29 : device st atus display.
Page 59
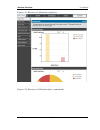
Wireless controller user manual 58 figure 30 : device st atus display (co nti nued) 4.1.2 resource utilization status > device info > dashboard the dashboard page presents hardware and usage statistics. The cpu and memory utilization is a function of the available hardware and current configuration ...
Page 60
Wireless controller user manual 59 figure 31 : re so urce utili zatio n sta tistic s figure 32 : re so urce utili zatio n dat a (co ntinue d).
Page 61: 4.2 Traffic Statistics
Wireless controller user manual 60 4.2 traffic statistics 4.2.1 wired port statistics status > traffic monitor > device statistics detailed transmit and receive statistics for each physical port are presented here. Each interface (wan1, wan2/dmz, lan, and vlans) have port specific packet level infor...
Page 62: 4.3 Active Connections
Wireless controller user manual 61 the statistics table has auto-refresh control which allows display of the most current port level data at each page refresh. The default auto -refresh for this page is 10 seconds. Figure 33 : physical port sta tistics 4.3 active connections 4.3.1 sessions through t...
Page 63
Wireless controller user manual 62 figure 34 : li st of c urrent acti ve firewall sessio ns.
Page 64: 4.3.2 Lan Clients
Wireless controller user manual 63 4.3.2 lan clients status > lan client info >lan clients the lan clients to the controller are identified by an arp scan through the lan switch. The netbios name (if available), ip address and mac address of discovered lan hosts are displayed. Figure 35 : li st of l...
Page 65: 4.4 Access Point Status
Wireless controller user manual 64 figure 36 : li st of c urrent acti ve vpn se ssio ns all active ssl vpn connections, both for vpn tunnel and vp n port forwarding, are displayed on this page as well. Table fields are as follows. Field description user name the ssl vpn user that has an active tunne...
Page 66
Wireless controller user manual 65 to configure an authentication failed ap to be managed by the controller the next time it is discovered, select the check box next to the mac address of the ap and\click manage. You will be presented with the v alid access point configuration page. Figure 37 : ap s...
Page 67
Wireless controller user manual 66 • rogue—the ap has not attempted to contact the controller and the mac address of the ap is not in the valid ap database. Radio: shows the wireless radio mode the ap is using. Channel: shows the operating channel for the radio. This page includes the following butt...
Page 68
Wireless controller user manual 67 figure 38 : ma nage d ap stat us mac address: the ethernet address of the controller-managed ap. Ip address: the network ip address of the managed ap. Age: time since last communication between the controller and the ap. Status the current managed state of the ap. ...
Page 69
Wireless controller user manual 68 • view ap details — shows detailed status information collected from the ap. • view radio details — shows detailed status for a radio interface • view neighbor details — shows the neighbour aps that the specified ap has discovered through periodic rf scans on the s...
Page 70: 4.5 Global Status
Wireless controller user manual 69 figure 39 : ap rf sc an sta tus 4.5 global status peer controller status status > global info > peer controller > status the peer controller status page provides information about other wireless controllers in the network. Peer wireless controllers within the same ...
Page 71
Wireless controller user manual 70 software version: the software version for the given peer controller. Protocol version: indicates the protocol version supported by the software on the peer controller. Discovery reason: the discovery method of the gi ven peer controller, which can be through an l2...
Page 72
Wireless controller user manual 71 peer ip address: shows the ip address of each peer wireless controller in the cluster that received configuration information. Configuration controller ip address: shows the ip address of the controller that sent the configuration information. Configuration: identi...
Page 73
Wireless controller user manual 72 peer controller ip: shows the ip address of the peer controller that manages the ap. This field displays when ―all‖ is selected from the drop -down menu. Location: the descriptive location configured for the managed ap. Ap ip address: the ip address of the ap. Prof...
Page 74
Wireless controller user manual 73 • saving configuration, • applying ap profile configuration • success • failure - invalid code version • failure - invalid hardware version • failure - invalid configuration last configuration received: peer controller ip address indicates the last controller from ...
Page 75
Wireless controller user manual 74 figure 43 : conf igur ation receive sta tus.
Page 76
Wireless controller user manual 75 4.6 wireless client status assocaited client status status > wireless client info> associated clients > status you can view a variety of information about the wireless clients that are associated with the aps the controller manages. Mac address: the ethernet addres...
Page 77
Wireless controller user manual 76 • view ssid details— lists the ssids of the networks that each wireless client associated with a managed ap has used for wlan access • view vap details — shows information about the vaps on the managed ap that have associated wireless clients • view neigh our ap st...
Page 78
Wireless controller user manual 77 assocaited client vap status status > wireless client info> associated clients > vap status each ap has 16 virtual access points (vaps) per radio, and every vap has a unique mac address (bssid).The vap associated client status page which shows information about the...
Page 79
Wireless controller user manual 78 controller assocaited client status status > wireless client info> associated clients > controller status this shows information about the controller that manages the ap to which the client is associated controller ip address: shows the ip address of the controller...
Page 80
Wireless controller user manual 79 client name: shows the name of the client, if available, from the known client database. If client is not in the database then the field is blank. Client status: shows the client status, which can be one of the following: • authenticated— the wireless client is aut...
Page 81
Wireless controller user manual 80 • acknowledge all rogues — clear the rogue status of all clients listed as rogues in the detected client database, the status of an acknowledge client is returned to the status it had when it was first detected. If the detected client fails any of the tests that cl...
Page 82
Wireless controller user manual 81 figure 49 : pre -aut h history this page includes the following button: • refresh—updates the page with the latest information. Detected client roam history status > wireless client info> roam history the wireless system keeps a record of clients as they roam from ...
Page 83
Wireless controller user manual 82 figure 50 : detecte d client ro a m hi story this page includes the following button: • refresh—updates the page with the latest information. • purge history— to purge the history when the list of entries is full. • view details — shows the details of the detected ...
Page 84: 4.7 Ap Management
Wireless controller user manual 83 4.7 ap management valid access point configuration setup > ap management > valid ap mac address this field shows the mac address of the ap. To change this field, you must delete the entire valid ap configuration and then enter the correct mac address from the page ...
Page 85
Wireless controller user manual 84 this page has the following buttons : • edit - to edit ap details in valid ap page. • delete - to delete a valid ap provide valid mac address in valid ap page. • add - to add an ap in valid ap page. Figure 52 : add a va lid acce ss point mac address: this field sho...
Page 86
Wireless controller user manual 85 location: to help you identify the ap, you can enter a location. This field accepts up to 32 alphanumeric characters. Authentication password: you can require that the ap authenticate itself with the controller upon discovery. Edit option and enter the password in ...
Page 87
Wireless controller user manual 86 the controller contains a channel plan algorithm that automatically de termines which rf channels each ap should use to minimize rf interference. When you enable the channel plan algorithm, the controller periodically evaluates the operational channel on every ap i...
Page 88
Wireless controller user manual 87 figure 53 : rf conf ig uratio n channel plan history depth: the channel plan history lists the channels the controller assigns each of the aps it manages after a channel plan is applied. Entries are added to the history regardless of in terval, time, or channel pla...
Page 89
Wireless controller user manual 88 not be adjusted below the value in the ap profile. The settings in the local database and radius server always override power set in the profile setting. If you manually set the power, the level is fixed and the ap will not use the automatic power adjustment algori...
Page 90
Wireless controller user manual 89 previous iterations cannot be assigned new channels in the next iteration to prevent the same aps from being changed time after time. Last algorithm time: shows the date and time when the channel plan algorithm last ran. Ap mac address: this table displays the chan...
Page 91
Wireless controller user manual 90 • algorithm complete: the channel plan algorithm has finished running. A table displays to indicate proposed channel assignm ents. Each entry shows the ap along with the current and new channel. To accept the proposed channel change, click apply. You must manually ...
Page 92
Wireless controller user manual 91 rf management (manual power adjustment plan) setup > ap management > rf management > manual power adjustment plan if you select manual as the power adjustment mode on the configuration tab, you can manually initiate the power adjustment algorithm on the manual powe...
Page 93
Wireless controller user manual 92 figure 56 : ma nual p ower adj ust ment pl an access point software download setup > ap management > software download the wireless controller can upgrade software on the aps that it manages. Server address: enter the ip address of the host where the upgrade file i...
Page 94
Wireless controller user manual 93 to download all images, make sure you specify the file path and file name for both images in the appropriate file path and file name fields . Managed ap: the list shows all the aps that the controller manages. If the controller is the cluster controller, then the l...
Page 95
Wireless controller user manual 94 the first byte of the oui must have the least significant bit set to 0. For example 02:ff:ff is a valid oui, but 03:ff:ff is not . Oui description: enter the organization name associated with the oui. The name can be up to 32alphanumeric characters.. Figure 58 : lo...
Page 96
Wireless controller user manual 95 4.8 associated client status/statistics managed ap statistics status > traffic monitor > managed ap statistics the managed ap statistics page shows information about traffic on the wired and wireless interfaces of the access point. This information can help diagnos...
Page 97
Wireless controller user manual 96 • view vap details — shows summary information about the virtual access points (vaps) for the selected ap and radio interface on the aps that the controller manages • refresh—updates the page with the latest information wlan assoicated clients status > traffic moni...
Page 98: Network
Wireless controller user manual 97 chapter 5. Securing the private network you can secure your network by creating and applying rules that your controller uses to selectively block and allow inbound and outbound internet traffic. You then specify how and to whom the rules apply. To do so, you must d...
Page 99
Wireless controller user manual 98 may use the ip address if a static address is ass igned to the wan port, or if your wan address is dynamic a ddns (dynamic dns) name can be used. Outbound (lan/dmz to wan) rules restrict access to traffic leaving your network, selectively allowing only specific loc...
Page 100
Wireless controller user manual 99 figure 62 : li st of available sc hedules t o bi nd to a f irewall rule 5.3 configuring firewall rules advanced > firewall settings > firewall rules all configured firewall rules on the controller are displayed in the firewall rules list. This list also indicates w...
Page 101
Wireless controller user manual 100 service: any means all traffic is affected by this rule. For a specific service the drop down list has common services, or you can select a custom defined service. Action & schedule: select one of the 4 actions that this rule defines: block always, allow always, b...
Page 102
Wireless controller user manual 101 external ip address: the rule can be bound to a specific wan interface by selecting either the primary wan or configurable port wan as the source ip address for incoming traffic. This controller supports multi-nat and so the external ip address does not necessar...
Page 103
Wireless controller user manual 102 figure 63 : ex a mple where an out bo und snat r ule i s use d to map a n ex ternal ip a ddress (209. 156. 200. 225) to a priv ate dm z ip address (1 0.30 .30. 30 ).
Page 104
Wireless controller user manual 103 figure 64 : t he f irewall rule co nf igurati o n page all ows y ou to def ine t he to/fro m zo ne, servi ce, actio n, sche dule s, and specif y so urce/desti na tion ip addresses as nee de d. 5.3.1 firewall rule configuration examples example 1: allow inbound htt...
Page 105
Wireless controller user manual 104 service http action allow always send to local server (dnat ip) 192.168.5.2 (web server ip address) destination users any log never example 2: allow videoconferencing from range of outside ip addresses situation: you want to allow incoming videoconferencing to be ...
Page 106
Wireless controller user manual 105 web server host in the dmz, ip address: 192.168.12.222 access to web server: (simulated) public ip address 10.1.0.52 e x a m p l e 4 : b l o c example 4: block traffic by schedule if generated from specific range of machines use case: block all http traffic on the...
Page 107
Wireless controller user manual 106 figure 65 : sc hedule conf iguratio n f or t he abo ve ex ample. 2. Since we are trying to block http requests, it is a service with to zone: insecure (wan1/wan2) that is to be blocked according to schedule ―weekend‖. 3. Select the action to ―block by schedule, ot...
Page 108: 5.5 Alg Support
Wireless controller user manual 107 8. The last step is to enable this firewall rule. Select the rule, and click ―enable‖ below the list to make sure the firewall rule is active 5.4 security on custom services advanced > firewall settings > custom services custom services can be defined to add to th...
Page 109
Wireless controller user manual 108 figure 67 : availa ble alg support on t he controller . 5.6 vpn passthrough for firewall advanced > firewall settings > vpn passthrough this controller‘s firewall settings can be configured to allow encrypted vpn traffic for ipsec, pptp, and l2tp vpn tunnel connec...
Page 110: 5.7 Application Rules
Wireless controller user manual 109 figure 68 : pa sst hro ug h o ptio ns f or vpn tunnel s 5.7 application rules advanced > application rules > application rules application rules are also referred to as port triggering. This feature allows devices on the lan or dmz to request one or more ports to ...
Page 111: 5.8.1 Content Filtering
Wireless controller user manual 110 ports. The controller has a list of common applications and games with corresponding outbound and inbound ports to open. You can also specify a port triggering rule by defining the type of traffic (tcp or udp) and the range of incoming and outgoing ports to open w...
Page 112: 5.8.2 Approved Urls
Wireless controller user manual 111 figure 70 : content filtering use d t o bl o c k access t o prox y se rvers a nd prevent acti ve x co ntrols f ro m being downloa ded 5.8.2 approved urls advanced > website filter > approved urls the approved urls is an acceptance list for all url domain names. Do...
Page 113: 5.8.3 Blocked Keywords
Wireless controller user manual 112 figure 71 : two tr ust ed do mai ns a dde d to the appro ved urls list 5.8.3 blocked keywords advanced > website filter > blocked keywords keyword blocking allows you to block all website url‘s or site content that contains the keywords in the configured list. Thi...
Page 114: 5.8.4 Export Web Filter
Wireless controller user manual 113 figure 72 : one keyw ord a dded to t he blo c k list 5.8.4 export web filter advanced > website filter > export export approved urls: feature enables the user to export the urls to be allowed to a csv file which can then be downlo aded to the local host. The user ...
Page 115: 5.9 Ip/mac Binding
Wireless controller user manual 114 figure 73 : ex port appro ved url li st 5.9 ip/mac binding advanced > ip/mac binding another available security measure is to only allow outbound traffic (from the lan to wan) when the lan nod e has an ip address matching the mac address bound to it. This is ip/ma...
Page 116
Wireless controller user manual 115 figure 74 : t he f ollo wing ex ample binds a lan ho st’ s mac address t o a n ip a ddre ss serve d by dw c-10 00. If there is a n ip/mac bindi ng viola tion, t he violati ng pac ket wi ll be droppe d a nd logs will be ca pt ured 5.10 protecting from internet atta...
Page 117
Wireless controller user manual 116 figure 75 : protecti ng the controller a nd lan f rom i nter net a ttac ks.
Page 118
Wireless controller user manual 117 chapter 6. Ipsec / pptp / l2tp vpn a vpn provides a secure communication channel (―tunnel‖) between two gateway controller or a remote pc client. The following types of tunnels can be created: gateway-to-gateway vpn: to connect two or more controller to secure tra...
Page 119
Wireless controller user manual 118 figure 77 : ex a mple of three ip sec client connecti ons t o t he i nternal networ k thro ug h t he dw c ip sec g ateway.
Page 120: 6.1 Vpn Wizard
Wireless controller user manual 119 6.1 vpn wizard setup > wizard > vpn wizard you can use the vpn wizard to quickly create both ike and vpn policies. Onc e the ike or vpn policy is created, you can modify it as required. Figure 78 : vpn wi zard la unch screen to easily establish a vpn tunnel using ...
Page 121
Wireless controller user manual 120 2. Configure remote and local wan address for the tunnel endpoints remote gateway type: identify the remote endpoint of the tunnel by fqdn or static ip address remote wan ip address / fqdn: this field is enabled only if the peer you are trying to connect to is a g...
Page 122
Wireless controller user manual 121 parameter default value from wizard exchange mode aggressive (client policy ) or main (gateway policy) id type fqdn local wan id wan_local.Com (only applies to client policies) remote wan id wan_remote.Com (only applies to client policies) encryption algorithm 3de...
Page 123
Wireless controller user manual 122 figure 79 : ip sec poli cy conf igura tio n once the tunnel type and endpoints of the tunnel are defined you can determine the phase 1 / phase 2 negotiation to use for the tunnel. This is covered in the ipsec mode setting, as the policy can be manual or auto. For ...
Page 124
Wireless controller user manual 123 figure 80 : ip sec poli cy conf igura tio n co ntinue d (auto policy via ik e) a manual policy does not use ike and instead relies on manual keying to exchange authentication parameters between the two ipsec hosts. The incoming and outgoing security parameter inde...
Page 125
Wireless controller user manual 124 figure 81 : ip sec poli cy conf igura tio n co ntinue d (auto / manual pha se 2 ) 6.2.1 extended authentication (xauth) you can also configure extended authentication (xauth). Rather than configure a unique vpn policy for each user, you can configure the vpn gatew...
Page 126
Wireless controller user manual 125 6.3 configuring vpn clients remote vpn clients must be configured with the same vpn policy parameters used in the vpn tunnel that the client wishes to use: encrypti on, authentication, life time, and pfs key-group. Upon establishing these authentication parameters...
Page 127
Wireless controller user manual 126 figure 82 : pptp t unnel co nf iguratio n – pptp client figure 83 : pptp vpn co nnectio n st atus setup > vpn settings > pptp > pptp server a pptp vpn can be established through this controller. Once enabled a pptp server is available on the controller for lan and...
Page 128
Wireless controller user manual 127 figure 84 : pptp t unnel co nf iguratio n – pptp server 6.4.2 l2tp tunnel support setup > vpn settings > l2tp > l2tp server a l2tp vpn can be established t hrough this controller. Once enabled a l2tp server is available on the controller for lan and wan l2tp clien...
Page 129: 6.4.3 Openvpn Support
Wireless controller user manual 128 figure 85 : l2 tp t unnel co nf iguratio n – l2tp server 6.4.3 openvpn support setup > vpn settings > openvpn > openvpn configuration openvpn allows peers to authenticate each other using a pre -shared secret key, certificates, or username/password. When used in a...
Page 130
Wireless controller user manual 129 port: the port number on which openvpn server(or access server) runs. Tunnel protocol: the protocol used to communicate with the remote host. Ex: tcp, udp. Udp is the default. Encryption algorithm: the cipher with which the packets are encrypted. Ex: bf-cbc, aes-1...
Page 131
Wireless controller user manual 130 figure 86 : ope nvpn conf igura tion.
Page 132: Chapter 7. Ssl Vpn
Chapter 7. Ssl vpn the controller provides an intrinsic ssl vpn feature as an alternate to the standard ipsec vpn. Ssl vpn differs from ipsec vpn mainly by removing the requirement of a pre-installed vpn client on the remote host. Instead, users can securely login through the ssl user portal using a...
Page 133
Wireless controller user manual 132 figure 87 : ex a mple of clientless ssl vpn co nnectio ns t o t he dw c-10 00
Page 134: 7.1 Groups And Users
Wireless controller user manual 133 7.1 groups and users advanced > users > groups the group page allows creating, editing and deleting groups. The groups are associated to set of user types. The lists of available groups are displayed in the ―list of group‖ page with group name and description of g...
Page 135
Wireless controller user manual 134 guest user (read-only): the guest user gains read only access to the gui to observe and review configuration settings. The guest does not have ssl vpn access. Captive portal user: these captive portal users has access through the controller. The access is determin...
Page 136
Wireless controller user manual 135 active directory domain: if the domain uses the active directory authentication, the active directory domain name is required. Users configured in the active directory database are given access to the ssl vpn portal with their active directory username and passwor...
Page 137
Wireless controller user manual 136 disable login: enable to prevent the users of this group from logging into the devices management interface(s) deny login from wan interface: enable to prevent the users of this group from logging in from a wan (wide area network) interface. In this case only logi...
Page 138
Wireless controller user manual 137 figure 92 : browser policies options policy by ip to set policies bye ip for the group, select the corresponding group click ―policy by ip‖. The following parameters are configured: group name: this is the name of the group that can have its login policy edited de...
Page 139
Wireless controller user manual 138 figure 93 : ip policies o ptio ns login policies, policy by browsers, policy by ip are applicable ssl vpn user only. Advanced > users > users the users page allows adding, editing and deleting existing groups. The user are associated to configured groups. The list...
Page 140
Wireless controller user manual 139 figure 94 : availa ble user s wit h logi n sta tus a nd a sso cia ted group 7.1.1 users and passwords advanced > users > users the user configurations allow creating users associated to group. The user settings contain the following key components: user name: this...
Page 141
Wireless controller user manual 140 figure 95 : user co nf iguratio n options 7.2 using ssl vpn policies setup > vpn settings > ssl vpn server > ssl vpn policies ssl vpn policies can be created on a global, group, or user level. User level policies take precedence over group level policies and group...
Page 142
Wireless controller user manual 141 figure 96 : li st of ssl vpn polices (global f ilter) to add a ssl vpn policy, you must first assign it to a user, group, or make it global (i.E. Applicable to all ssl vpn users). If the policy is for a group, the available configured groups are shown in a drop do...
Page 143
Wireless controller user manual 142 figure 97 : ssl vpn policy co nf igurati on to configure a policy for a single user or group of users, enter the following information: policy for: the policy can be assigned to a group of users, a single user, or all users (making it a global policy). To customiz...
Page 144
Wireless controller user manual 143 the starting and ending port range blank corresponds to all udp and tcp traffic. Service: this is the ssl vpn service made available by this policy. The services offered are vpn tunnel, port forwardin g or both. Defined resources: this policy can provide access to...
Page 145
Wireless controller user manual 144 figure 98 : li st of co nf igured re so urces, which are a vaila ble to a ssi gn to ssl vpn policies 7.3 application port forwarding setup > vpn settings > ssl vpn server > port forwarding port forwarding allows remote ssl users to access specified network applica...
Page 146
Wireless controller user manual 145 vnc (virtual network computing) 5900 or 5800 as a convenience for remote users, the hostname (fqdn) of the network server can be configured to allow for ip address resolution. This host name resolution provides users with easy-to-remember fqdn‘s to access tcp appl...
Page 147
Wireless controller user manual 146 figure 99 : li st of available applica tions f or ssl p ort forw arding 7.4 ssl vpn client configuration setup > vpn settings > ssl vpn client > ssl vpn client an ssl vpn tunnel client provides a point -to-point connection between the browser - side machine and th...
Page 148
Wireless controller user manual 147 figure 10 0: ssl vpn client a dapter a nd access conf ig uratio n the controller allows full tunnel and split tunnel support. Full tunnel mode just sends all traffic from the client across the vpn tunnel to the controller. Split tunnel mode only sends traffic to t...
Page 149
Wireless controller user manual 148 setup > vpn settings > ssl vpn client > configured client routes if the ssl vpn client is assigned an ip addr ess in a different subnet than the corporate network, a client route must be added to allow access to the private lan through the vpn tunnel. As well a st...
Page 150
Wireless controller user manual 149 the controller administrator creates and edits portal layouts from the configuration pages in the ssl vpn menu. The portal name, title, banner name, and banner contents are all customizable to the intended user s for this portal. The portal name is appended to the...
Page 151
Wireless controller user manual 150 figure 10 2: ssl vpn portal conf igur ati on.
Page 152: Tools
Wireless controller user manual 151 chapter 8. Advanced configuration tools 8.1 usb device setup setup > usb settings > usb status the dwc-1000 wireless controller has a usb interface for printer access, file sharing. There is no configuration on the gui to enable usb device support. Upon inserting ...
Page 153
Wireless controller user manual 152 figure 10 3: usb dev ice detectio n 8.2 authentication certificates advanced > certificates this gateway uses digital certificates for ipsec vpn authentication as well as ssl validation (for https and ssl vpn authentication). You can obtain a digital certificate f...
Page 154
Wireless controller user manual 153 a self certificate is a certificate issued by a ca identifying your de vice (or self- signed if you don‘t want the identity protection of a ca). The active self certificate table lists the self certificates currently loaded on the gateway. The following informatio...
Page 155: 8.3 Wids Security
Wireless controller user manual 154 figure 10 4: certif icate summary f or ip sec and http s ma na geme nt 8.3 wids security 8.3.1 wids ap configration advanced > wids security > ap the wids ap configuration page allows you to activate or deactivate various threat detection tests and set threat dete...
Page 156
Wireless controller user manual 155 managed ssid from an unknown ap : this test checks whether an unknown ap is using the managed network ssid. A hacker may set up an ap with managed ssid to fool users into associating with the ap and revealing password and other secure information. Administrators w...
Page 157
Wireless controller user manual 156 ap is operating on an illegal channel : the purpose of this test is to detect hackers or incorrectly configured devices that are operating on channels that are not legal in the country where the wireless system is set up. Note: in order for the wireless system to ...
Page 158
Wireless controller user manual 157 ap de-authentication attack: enable or disable the ap de -authentication attack. The wireless controller can protect against rogue aps by sending de authentication messages to the rogue ap. The de-authentication attack feature must be globally enabled in order for...
Page 159
Wireless controller user manual 158 in order to help determine whether a client is posing a threat to the network by flooding the network with management traffic, the system keeps track of the number of times the ap received each message type and the highest message rate detected in a single rf scan...
Page 160
Wireless controller user manual 159 rogue detected trap interval : specify the interval, in seconds, between transmissions of the snmp trap telling the administrator that rogue aps are present in the rf scan database. If you set the value to 0, the trap is never sent. De-authentication requests thre...
Page 161
Wireless controller user manual 160 figure 10 6: w ids client conf ig uratio n.
Page 162: Management
Wireless controller user manual 161 chapter 9. Administration & management 9.1 remote management both https and telnet access can be restricted to a subset of ip addresses. The controller administrator can define a known pc, single ip address or range of ip addresses that are allowed to access the g...
Page 163: 9.3 Snmp Configuration
Wireless controller user manual 162 9.3 snmp configuration tools > admin > snmp snmp is an additional management tool that is useful when multiple controller in a network are being managed by a central master system. When an external snmp manager is provided with this controller management informati...
Page 164
Wireless controller user manual 163 figure 10 9: snmp syste m i nf or matio n f or thi s co ntroller 9.4 configuring time zone and ntp tools > date and time you can configure your time zone, whether or n ot to adjust for daylight savings time, and with which network time protocol (ntp) server to syn...
Page 165: 9.5 Log Configuration
Wireless controller user manual 164 figure 11 0: date, ti me, a nd ntp server setup 9.5 log configuration this controller allows you to capture log messages for traffic through the firewall, vpn, and over the wireless ap. As an administrator you can monitor the type of traffic that goes through the ...
Page 166
Wireless controller user manual 165 9.5.1 defining what to log tools > log settings > logs facility the logs facility page allows you to determine the granularity of logs to receive from the controller. There are three core components of the controller, referred to as facilities: kernel: this refers...
Page 167
Wireless controller user manual 166 figure 11 1: facility setti ngs f or loggi ng the display for logging can be customized based on where the logs are sent, either the event log viewer in the gui (the event log viewer is in the status > logs page) or a remote syslog server for later review. E -mail...
Page 168
Wireless controller user manual 167 example: if accept packets from lan to wan is enabled and there is a firewall rule to allow ssh traffic from lan, then whenever a lan machine tries to make an ssh connection, those packets will be accepted and a message will be logged. (assuming the log option is ...
Page 169
Wireless controller user manual 168 figure 11 2: l og co nf iguratio n options f or traf f ic throug h co nt roller 9.5.2 sending logs to e-mail or syslog tools > log settings > remote logging once you have configured the type of logs that you want the controller to collect, they can be sent to eith...
Page 170
Wireless controller user manual 169 send a valid e-mail that is accepted by one of the configured ―send -to‖ addresses. Up to three e-mail addresses can be configured as log recipients. In order to establish a connection with the configured smtp port and server, define the server‘s authentication re...
Page 171
Wireless controller user manual 170 figure 11 3: e - mail c onf igurati on as a re mo te lo gging o ptio n an external syslog server is often used by network administrator to collect and store logs from the controller. This remote device typically has less memory constraints than the local event vie...
Page 172
Wireless controller user manual 171 figure 11 4: sy slog server conf iguratio n f or remote lo ggi ng ( conti nue d) 9.5.3 event log viewer in gui status > logs > view all logs the controller gui lets you observe configured log messages from t he status menu. Whenever traffic through or to the contr...
Page 173: Settings
Wireless controller user manual 172 figure 11 5: vpn l og s displaye d i n gui e vent viewer 9.6 backing up and restoring configuration settings tools > system you can back up the controller custom configuration settings to restore them to a different device or the same controller after some other c...
Page 174
Wireless controller user manual 173 9. To restore your saved settings from a backup file, click browse then locate the file on the host. After clicking restore, the controller begins importing the file‘s saved configuration settings. After the restore, the controller reboots automatically with the r...
Page 175: 9.8 Dynamic Dns Setup
Wireless controller user manual 174 important! During firmware upgrade, do not try to go online , turn off the dwc-1000, shut down the pc, or interrupt the process in anyway until the operation is complete. This should take only a minute or so including the reboot process. Interrupting the upgrade p...
Page 176
Wireless controller user manual 175 directed to the correct ip address. When you set up an account with a ddns service, the host and domain name, username, password and wildcard support will be provided by the account provider. Figure 11 8: dy na mic dns co nf igura tion 9.9 using diagnostic tools t...
Page 177: 9.9.1 Ping
Wireless controller user manual 176 figure 11 9: co ntroll er diag no stics tool s availa ble in the gui 9.9.1 ping this utility can be used to test connectivity between this controller and another device on the network connected to this controller. Enter an ip address and click ping. The command ou...
Page 178: 9.9.4 Router Options
Wireless controller user manual 177 9.9.4 router options the static and dynamic routes configured on this controller can be shown by clicking display for the corresponding routing table. Clicking the packet trace button will allow the controller to capture and display traffic through the dwc-1000 be...
Page 179: Appendix A. Glossary
Wireless controller user manual 178 appendix a. Glossary arp address resolution protocol. Broadcast protocol for mapping ip addresses to mac addresses. Chap challenge-handshake authentication protocol. Protocol for authenticating users to an isp. Ddns dynamic dns. System for updating domain names in...
Page 180
Wireless controller user manual 179 pppoe point-to-point protocol over ethernet. Protocol for connecting a network of hosts to an isp without the isp having to manage the allocation of ip addresses. Pptp point-to-point tunneling protocol. Protocol for creation of vpns for the secure transfer of data...
Page 181
Appendix b. Factory default settings feature description default setting device login user login url http://192.168.10.1 user name (case sensitive) admin login password (case sensitive) admin internet connection wan mac address use default address wan mtu size 1500 port speed autosense local area ne...