- DL manuals
- D-Link
- Switch
- DWS-1008
- Product Manual
D-Link DWS-1008 Product Manual - Creating A New Profile
D-Link DWS-1008 User Manual
11
Creating a New Profile
To create a radio profile, use the following command:
set radio-profile name [mode {enable | disable}]
Specify a name of up to 16 alphanumeric characters. Do not include the mode enable or mode disable
option.
After you create the radio profile, you can use the enable and disable options to enable or disable all
radios that use the profile.
To configure a new radio profile named rp1, type the following command:
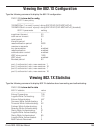
DWS-1008# set radio-profile rp1
success: change accepted.
To assign the profile to one or more radios, use the set ap radio radio-profile command.
Changing Radio Parameters
To change individual parameters controlled by a radio profile, use the commands described in the
following sections.
Note: You must disable all radios that are using a radio profile before you can change parameters in
the profile.
Changing the Beacon Interval
The beacon interval is the rate at which a radio advertises its beaconed SSID(s). To change the beacon
interval, use the following command:
set radio-profile name beacon-interval interval
The interval can be a value from 25 ms through 8191 ms. The default is 100.
The beacon interval does not change even when advertisement is enabled for multiple SSIDs. MSS still
sends one beacon for each SSID during each beacon interval.
To change the beacon interval for radio profile rp1 to 200 ms, type the following command:
DWS-1008# set radio-profile rp1 beacon-interval 200
success: change accepted.
Summary of DWS-1008
Page 2: Table of Contents
D-link dws-1008 user manual i table of contents product overview .............................................................................................................................1 product contents ..............................................................................................
Page 3
D-link dws-1008 user manual ii overview .....................................................................................................................................25 configuring aaa for administrative and local access .............................................................25 before y...
Page 4
D-link dws-1008 user manual iii removing a port group ...................................................................................................47 displaying port group information...................................................................................47 interoperating with cisco...
Page 5
D-link dws-1008 user manual iv managing the management services .........................................................................................69 managing ssh .....................................................................................................................69 login timeo...
Page 6
D-link dws-1008 user manual v managing the arp table ............................................................................................................85 displaying arp table entries ..............................................................................................85 adding an ...
Page 7
D-link dws-1008 user manual vi service profiles ..................................................................................................................114 public and private ssids ..............................................................................................117 encryption ...
Page 8
D-link dws-1008 user manual vii changing the short retry threshold .............................................................................140 changing the long retry threshold ..............................................................................140 configuring a radio profile ...........
Page 9
D-link dws-1008 user manual viii assigning the service profile to radios and enabling the radios ................................165 configuring rsn (802.11i) .......................................................................................................166 creating a service profile for rsn...
Page 10
D-link dws-1008 user manual ix wmm qos on an ap .....................................................................................................192 svp qos mode .............................................................................................................192 u-apsd support .........
Page 11
D-link dws-1008 user manual x displaying the backbone fast convergence state ............................................................209 configuring uplink fast convergence ...............................................................................210 displaying uplink fast convergence infor...
Page 12
D-link dws-1008 user manual xi committing a security acl ................................................................................................231 viewing security acl information .....................................................................................231 viewing the edit buff...
Page 13
D-link dws-1008 user manual xii creating public-private key pairs ......................................................................................262 generating self-signed certificates ..................................................................................262 installing a key pair ...
Page 14
D-link dws-1008 user manual xiii display of the login page ..............................................................................................292 webaaa requirements and recommendations ...............................................................292 dws-1008 switch requirements ..........
Page 15
D-link dws-1008 user manual xiv viewing local accounting records ...................................................................................329 viewing roaming accounting records ..............................................................................329 displaying the aaa configuratio...
Page 16
D-link dws-1008 user manual xv setting the 802.1x timeout for an authorization server ....................................................354 setting the 802.1x timeout for a client .............................................................................355 displaying 802.1x information ..........
Page 17
D-link dws-1008 user manual xvi summary of rogue detection features ...................................................................................380 configuring rogue detection lists ...........................................................................................381 configuring a pe...
Page 18
D-link dws-1008 user manual xvii backup and restore examples .........................................................................................412 upgrading the system image ...................................................................................................413 preparing the sw...
Page 19
D-link dws-1008 user manual xviii configuring a snoop filter .................................................................................................433 displaying configured snoop filters .............................................................................435 editing a snoop filte...
Page 20: Product Contents
D-link dws-1008 user manual 1 product contents dws-1008 8-port wireless switch power supply serial cable for connection to console rack-mount brackets (2) rubber feet (4) screws (6) install guide manual and reference guide on cd system requirements an existing 10/100 ethernet network dwl-8220ap acce...
Page 21: Introduction
D-link dws-1008 user manual introduction the d-link ® airpremier ® mobilelan™ dws-1008 is a wireless lan switch optimized for deployment in the small-medium enterprise (sme) environment. The dws-1008 is designed to allow easy user installation and operation yet support advanced wireless switch featu...
Page 22
D-link dws-1008 user manual hardware overview (front panel) console port: the serial console port provides a direct management connection to a dws-1008 switch’s command-line interface (cli). The port has a db-9 female connector and supports the eia-232d signaling standard. Ethernet ports (1-6): the ...
Page 23: Features
D-link dws-1008 user manual power features • power supplies - the dws-1008 switch contains one 100-120 vac auto-sensing ac power supply. Management features • serial and network command-line interface (cli) access—you can access the cli through a direct serial connection or through the network using...
Page 24: Text and Syntax Conventions
D-link dws-1008 user manual text and syntax conventions trapeze manuals use the following text and syntax conventions: convention use monospace text sets off command syntax or sample commands and system responses. Bold text highlights commands that you enter or items you select. Italic text designat...
Page 25: Installation
D-link dws-1008 user manual installation caution: the dws-1008 switch has been designed and tested to be installed in an operating ambient temperature of 0° c to +40° c (32° f to 104° f). To reduce the risk of equipment damage, install equipment with consideration to these ambient conditions. Serial...
Page 26
D-link dws-1008 user manual installation hardware and tools caution: to reduce the risk of equipment damage, make sure the switch is installed so that the mechanical load on the device is evenly distributed. For example, make sure the switch is level in the equipment rack, is evenly fastened by scre...
Page 27: Getting Started
D-link dws-1008 user manual 8 please read the following before you begin: mobility system software* (mss) operates a d-link mobility system wireless lan (wlan) consisting of dws-1008 switches, and dwl-8220ap access points (ap). Mss has a command line interface (cli) on the switch that you can use to...
Page 28: Cli Conventions
D-link dws-1008 user manual using the command-line interface mobility system software (mss) operates a d-link wireless lan (wlan) consisting of the dws-1008 switch and dwl-8220ap access points. Mss has a command-line interface (cli) on the switch that you can use to configure and manage the switch a...
Page 29: Syntax Notation
D-link dws-1008 user manual 10 syntax notation the mss cli uses standard syntax notation: bold font identifies the command and keywords you must type. For example: set enablepass italic font indicates a placeholder for a value. For example, you replace vlan-id in the following command with a virtual...
Page 30: Mac Address Notation
D-link dws-1008 user manual 11 mac address notation mss displays mac addresses in hexadecimal numbers with a colon (:) delimiter between bytes—for example, 00:01:02:1 a:00:0 1. You can enter mac addresses with either hyphen (-) or colon (:) delimiters, but colons are preferred. For shortcuts: • you ...
Page 31: Globs
D-link dws-1008 user manual 1 globs name “globbing” is a way of using a wildcard pattern to expand a single element into a list of elements that match the pattern. Mss accepts user globs, mac address globs, and vlan globs. The order in which globs appear in the configuration is important, because on...
Page 32: Mac Address Globs
D-link dws-1008 user manual 1 mac address globs a media access control (mac) address glob is a similar method for matching some authentication, authorization, and accounting (aaa) and forwarding database (fdb) commands to one or more 6-byte mac addresses. In a mac address glob, you can use a single ...
Page 33: Port Lists
D-link dws-1008 user manual 1 port lists the physical ethernet ports on a switch can be set for connection to access points, authenticated wired users, or the network backbone. You can include a single port or multiple ports in one mss cli command by using the appropriate list format. The ports on a...
Page 34: Command-Line Editing
D-link dws-1008 user manual 1 command-line editing mss editing functions are similar to those of many other network operating systems. Keyboard shortcuts the following keyboard shortcuts are available for entering and editing cli commands: keyboard shortcut(s) function ctrl+a jumps to the first char...
Page 35: Using Cli Help
D-link dws-1008 user manual 1 single-asterisk (*) wildcard character you can use the single-asterisk (*) wildcard character in globbing. For details, see “user globs, mac address globs, and vlan globs” on page 12. Double-asterisk (**) wildcard characters the double-asterisk (**) wildcard character m...
Page 36
D-link dws-1008 user manual 1 understanding command descriptions each command description in the d-link command reference contains the following elements: • a command name, which shows the keywords but not the variables. For example, the following command name appears at the top of a command descrip...
Page 37: Dws-1008 Setup Methods
D-link dws-1008 user manual 18 dws-1008 setup methods overview mss provides the following quick-start methods for new (unconfigured) switches: • web quick start • cli quickstart command you can use either quick-start method to configure a switch to provide wireless service. You also can use any of t...
Page 38: Web Quick Start
D-link dws-1008 user manual 1 web quick start you can use the web quick start to configure the switch to provide wireless access to up to ten network users. To access the web quick start, attach a pc directly to port 1 or port 2 on the switch and use a web browser on the pc to access ip address 192....
Page 39
D-link dws-1008 user manual 0 accessing the web quick start to access the web quick start: 1. Use a category 5 (cat 5) or higher ethernet cable to connect the switch directly to a pc that has a web browser. 2. Connect the switch to an ac power source. If the green power led is lit, the switch is rec...
Page 40
D-link dws-1008 user manual 1 7. After guiding you through the configuration, the wizard displays a summary of the configuration values you selected. Here is an example: 8. Review the configuration settings, then click finish to save the changes or click back to change settings. If you want to quit ...
Page 41: Cli Quickstart Command
D-link dws-1008 user manual cli quickstart command the quickstart command runs a script that interactively helps you configure the following items: • system name • country code (regulatory domain) • system ip address • default route • 802.1q tagging for ports in the default vlan • administrative use...
Page 42: Quickstart Example
D-link dws-1008 user manual 4. Press enter at the enter password prompt. 5. Type quickstart. The command asks you a series of questions. You can type ? For more help. To quit, press ctrl+c. One of the questions the script asks is the country code. For a list of valid country codes, see “specifying t...
Page 43
D-link dws-1008 user manual dwl-1008-aabbcc# quickstart this will erase any existing config. Continue? [n]: y answer the following questions. Enter ‘?’ for help. Ctrl-c to break out system name [dws-1008]: dws-1008-mrktg country code [us]: us system ip address []: 172.16.0.21 system ip address netma...
Page 44: And Local Access
D-link dws-1008 user manual configuring aaa for administrative and local access overview d-link mobility system software (mss) supports authentication, authorization, and accounting (aaa) for secure network connections. As administrator, you must establish administrative access for yourself and opti...
Page 45: Before You Start
D-link dws-1008 user manual 7. Accounting for administrative access sessions - accounting records can be stored and displayed locally or sent to a radius server. Accounting records provide an audit trail of the time an administrative user logged in, the administrator’s username, the number of bytes ...
Page 46: Enabling An Administrator
D-link dws-1008 user manual first-time configuration via the console administrators must initially configure the switch with a computer or terminal connected to the console port through a serial cable. Telnet access is not initially enabled. To configure a previously unconfigured switch via the cons...
Page 47
D-link dws-1008 user manual 8 setting the switch enable password there is one enable password for the entire switch. You can optionally change the enable password from the default. Caution: d-link recommends that you change the enable password from the default (no password) to prevent unauthorized u...
Page 48
D-link dws-1008 user manual authenticating at the console you can configure the console so that authentication is required, or so that no authentication is required. D-link recommends that you enforce authentication on the console port. To enforce console authentication, take the following steps: 1....
Page 49: Setting User Passwords
D-link dws-1008 user manual 0 customizing aaa with “globs” and groups “globbing” lets you classify users by username or media access control (mac) address for different aaa treatments. A user glob is a string, possibly containing wildcards, for matching aaa and ieee 802.1x authentication methods to ...
Page 50
D-link dws-1008 user manual 1 adding and clearing local users for administrative access usernames and passwords can be stored locally on the switch. D-link recommends that you enforce console authentication after the initial configuration to prevent anyone with unauthorized access to the console fro...
Page 51
D-link dws-1008 user manual you can select either start-stop or stop-only accounting modes. The stop-only mode sends only stop records, whereas start-stop sends both start and stop records, effectively doubling the number of accounting records. In most cases, stop-only is entirely adequate for admin...
Page 52: Saving The Configuration
D-link dws-1008 user manual saving the configuration you must save the configuration for all commands that you enter and want to use for future sessions. After you enter the administrator’s aaa configuration, type the following command to maintain these commands in nonvolatile memory: dws-1008# save...
Page 53
D-link dws-1008 user manual local authentication for console users and radius authentication for telnet users this scenario illustrates how to enable local authentication for console users and radius authentication for telnet administrative users. To do so, you configure at least one local username ...
Page 54
D-link dws-1008 user manual natasha also enables backup radius authentication for telnet administrative users. If the radius server does not respond, the user is authenticated by the local database in the switch. Natasha types the following commands: dws-1008# set authentication admin * sg1 local su...
Page 55: Vlans
D-link dws-1008 user manual configuring and managing ports and vlans configuring and managing ports you can configure and display information for the following port parameters: • port type • name • speed and autonegotiation • port state • power over ethernet (poe) state • load sharing setting the po...
Page 56
D-link dws-1008 user manual parameter port type ap access wired authentication network vlan membership removed from all vlans. You cannot assign an access port to a vlan. Mss automatically assigns ap access ports to vlans based on user traffic. Removed from all vlans. You cannot assign a wired authe...
Page 58: Clearing A Port
D-link dws-1008 user manual for 802.1x clients, wired authentication works only if the clients are directly attached to the wired authentication port, or are attached through a hub that does not block forwarding of packets from the client to the pae group address (01: 80:c2:00:00:03). Wired authenti...
Page 59: Clearing A Distributed Ap
D-link dws-1008 user manual 0 clearing a distributed ap caution: when you clear a distributed ap, mss ends user sessions that are using the ap. To clear a distributed ap, use the following command: clear dap dap-num configuring a port name each switch port has a number but does not have a name by de...
Page 60
D-link dws-1008 user manual 1 configuring port operating parameters autonegotiation is enabled by default on a switch’s 10/100 ethernet ports. Note: d-link recommends that you do not configure the mode of a switch port so that one side of the link is set to autonegotiation while the other side is se...
Page 61: Resetting A Port
D-link dws-1008 user manual disabling or reenabling power over ethernet power over ethernet (poe) supplies dc power to a device connected to an ap access port. The poe state depends on whether you enable or disable poe when you set the port type. To change the poe state on a port, use the following ...
Page 62: Displaying Poe State
D-link dws-1008 user manual in this example, two of the switch’s ports, 1 and 6, have an operational status of up, indicating the links on the ports are available. Ports 1 is network port and port 6 is an ap access port. Displaying poe state to display the poe state of a port, use the following comm...
Page 63: Clearing Statistics Counters
D-link dws-1008 user manual clearing statistics counters to clear all port statistics counters, use the following command: clear port counters the counters begin incrementing again, starting from 0. Monitoring port statistics you can display port statistics in a format that continually updates the c...
Page 64: Load Sharing
D-link dws-1008 user manual to monitor port statistics beginning with octet statistics (the default), type the following command: dws-1008# monitor port counters as soon as you press enter, mss clears the window and displays statistics at the top of the window. In this example, the octet statistics ...
Page 66: Removing A Port Group
D-link dws-1008 user manual removing a port group to remove a port group, use the following command: clear port-group name name displaying port group information to display port group information, use the following command: show port-group [name group-name] to display the configuration and status of...
Page 67: Understanding Vlans In Mss
D-link dws-1008 user manual 8 configuring and managing vlans note: the cli commands in this chapter configure vlans on switch network ports. The commands do not configure vlan membership for wireless or wired authentication users. To assign a user to a vlan, configure the radius tunnel-private-group...
Page 68: Users and Vlans
D-link dws-1008 user manual users and vlans when a user successfully authenticates to the network, the user is assigned to a specific vlan. A user remains associated with the same vlan throughout the user’s session on the network, even when roaming from one switch to another within the network. You ...
Page 69: Configuring A Vlan
D-link dws-1008 user manual 0 configuring a vlan you can configure the following vlan parameters: • vlan number • vlan name • port list (the ports in the vlan) • per-port tag value (an 802.1q value representing a virtual port in the vlan) • mac restriction list (if you want to prevent clients from c...
Page 70: Adding Ports to A Vlan
D-link dws-1008 user manual 1 adding ports to a vlan to add a port to a vlan, use the following command: set vlan vlan-id port port-list [tag tag-value] you can specify a tag value from 1 through 4093. Note: mss does not remove a port from other vlans when you add the port to a new vlan. If a new vl...
Page 71
D-link dws-1008 user manual to clear port 4, which uses tag value 11, from vlan marigold, type the following command: dws-1008# clear vlan marigold port 4 tag 11 this may disrupt user connectivity. Do you wish to continue? (y/n) [n]y success: change accepted. To completely remove vlan ecru, type the...
Page 73
D-link dws-1008 user manual managing the layer 2 forwarding database a dws-1008 switch uses a layer 2 forwarding database (fdb) to forward traffic within a vlan. The entries in the forwarding database map mac addresses to the physical or virtual ports connected to those mac addresses within a partic...
Page 74
D-link dws-1008 user manual displaying forwarding database information you can display the forwarding database size and the entries contained in the database. Displaying the size of the forwarding database to display the number of entries contained in the forwarding database, use the following comma...
Page 75
D-link dws-1008 user manual to display all entries that begin with 00, type the following command: dws-1008# show fdb 00:* * = static entry. + = permanent entry. # = system entry. Vlan tag dest mac/route des [cos] destination ports [protocol type] ----------------------------------------------------...
Page 76
D-link dws-1008 user manual configuring the aging timeout period the aging timeout period specifies how long a dynamic entry can remain unused before the software removes the entry from the database. You can change the aging timeout period on an individual vlan basis. You can change the timeout peri...
Page 77
D-link dws-1008 user manual 8 port and vlan configuration scenario this scenario assigns names to ports, and configures ap access authentication ports, a load-sharing port group, and vlans. 1. Assign names to ports to identify their functions, and verify change. Type the following commands: dws-1008...
Page 78
D-link dws-1008 user manual system idle timeout: 3600 system mac: 00:0b:0e:00:04:0c ===================================================== boot time: 2000-03-18 22:59:19 uptime: 0 days 00:13:45 ===================================================== fan status: fan1 ok fan2 ok fan3 ok temperature: temp...
Page 79
D-link dws-1008 user manual 0 4. Configure ports 3 and 4 as wired authentication ports and verify the configuration change. Type the following commands: dws-1008# set port type wired-auth 3,4 success: change accepted dws-1008# show port status port name admin oper config actual type media ==========...
Page 80: Configuring and Managing Ip
D-link dws-1008 user manual 1 configuring and managing ip interfaces and services mtu support mobility system software (mss) supports standard maximum transmission units (mtus) of 1514 bytes for standard ethernet packets and 1518 bytes for ethernet packets with an 802.1q tag. Mss does not support ch...
Page 81: Adding An Ip Interface
D-link dws-1008 user manual adding an ip interface you can add an ip interface to a vlan by statically configuring an ip address or by enabling the dynamic host configuration protocol (dhcp) client on the vlan. Statically configuring an ip interface to add an ip interface to a vlan, use the followin...
Page 82: Parameters
D-link dws-1008 user manual how mss resolves conflicts with statically configured ip parameters mss compares the ip parameter values already configured on the switch with the values received from the dhcp server, and resolves any conflicts as follows: • ip address - if the vlan also has a statically...
Page 83: Removing An Ip Interface
D-link dws-1008 user manual you can configure the dhcp client on more than one vlan, but the client can be active on only one vlan. To remove all ip information from a vlan, including the dhcp client and user-configured dhcp server, use the following command: clear interface vlan-id ip the ip interf...
Page 84
D-link dws-1008 user manual displaying ip interface information to display ip interface information, use the following command: show interface [vlan-id] configuring the system ip address you can designate one of the ip addresses configured on a switch to be the system ip address of the switch. The s...
Page 85
D-link dws-1008 user manual configuring and managing ip routes the ip route table contains routes that mss uses for determining the interfaces for a switch’s external communications. When you add an ip interface to a vlan that is up, mss automatically adds corresponding entries to the ip route table...
Page 86: Displaying Ip Routes
D-link dws-1008 user manual displaying ip routes to display ip routes, use the following command: show ip route [destination] the destination parameter specifies a destination ip address. To display the ip route table, type the following command: dws-1008# show ip route router table for ipv4 destina...
Page 87: Adding A Static Route
D-link dws-1008 user manual 8 dws-1008# show ip route router table for ipv4 destination/mask proto metric nh-type gateway 0.0.0.0/ 0 static 1 router 10.0.1.17 0.0.0.0/ 0 static 2 router 10.0.2.17 10.0.2.1/24 ip 0 direct 10.0.2.1/32 ip 0 direct 10.0.2.255/32 ip 0 direct 224.0.0.0/ 4 ip 0 local adding...
Page 90: Managing Ssh Server Sessions
D-link dws-1008 user manual 1 to add administrative user admin with password letmein, and use radius server group sg1 to authenticate the user, type the following commands: dws-1008# set user mxadmin password letmein success: user mxadmin created dws-1008# set authentication admin mxadmin sg1 succes...
Page 91: Managing Ssh Server Sessions
D-link dws-1008 user manual managing ssh server sessions use the following commands to manage ssh server sessions: show sessions admin clear sessions admin ssh [session-id] these commands display and clear ssh server sessions. Note: if you type the clear sessions admin ssh command from within an ssh...
Page 92: Adding A Telnet User
D-link dws-1008 user manual adding a telnet user to log in with telnet, a user must supply a valid username and password. To add a username and password to the local database, use the following command: set user username password password optionally, you also can configure mss either to locally auth...
Page 93: Managing Https
D-link dws-1008 user manual managing telnet server sessions use the following commands to manage telnet server sessions: show sessions admin clear sessions admin telnet [session-id] these commands display and clear management sessions from a remote client to the switch’s telnet server. Note: if you ...
Page 94: Displaying Https Information
D-link dws-1008 user manual displaying https information to display https service information, use the following command: show ip https to display information for a switch’s https server, type the following command: dws-1008> show ip https https is enabled https is set to use port 443 last 10 connec...
Page 95: Configuring and Managing Dns
D-link dws-1008 user manual to reset the idle timeout to its default value, use the following command: clear system idle-timeout to display the current setting (if the timeout has been changed from the default), use the show config area system command. If you are not certain whether the timeout has ...
Page 97: Adding An Alias
D-link dws-1008 user manual 8 displaying dns server information to display dns server information, use the following command: show ip dns the following example shows dns server information on a switch configured to use three dns servers. Dws-1008# show ip dns domain name: example.Com dns status: ena...
Page 98: Removing An Alias
D-link dws-1008 user manual removing an alias to remove an alias, use the following command: clear ip alias name displaying aliases to display aliases, use the following command: show ip alias [name] here is an example: dws-1008# show ip alias name ip address ------------------------------------ hr1...
Page 99: Setting The Time Zone
D-link dws-1008 user manual 80 setting the time zone the time zone parameter adjusts the system date, and optionally the time, by applying an offset to utc. To set the time zone, use the following command: set timezone zone-name {-hours [minutes]} the zone name can be up to 32 alphanumeric character...
Page 100
D-link dws-1008 user manual 81 configuring the summertime period the summertime period offsets the system time +1 hour and returns it to standard time for daylight savings time or a similar summertime period that you set. Note: configure summertime before you set the time and date. Otherwise, summer...
Page 101: Displaying The Time and Date
D-link dws-1008 user manual 8 statically configuring the system time and date to statically configure the system time and date, use the following command: set timedate {date mmm dd yyyy [time hh:mm:ss]} the day of week is automatically calculated from the day you set. To set the date to february 29,...
Page 102: Adding An Ntp Server
D-link dws-1008 user manual 8 mss adjusts the ntp reply according to the following time parameters configured on the switch: • offset from utc (configured with the timezone command; see “setting the time zone” ) • daylight savings time (configured with the set summertime command; see “configuring th...
Page 103: Enabling The Ntp Client
D-link dws-1008 user manual 8 resetting the update interval to the default to reset the update interval to the default value, use the following command: clear ntp update-interval enabling the ntp client the ntp client is disabled by default. To enable the ntp client, use the following command: set n...
Page 104: Managing The Arp Table
D-link dws-1008 user manual 8 managing the arp table the address resolution protocol (arp) table maps ip addresses to mac addresses. An arp entry enters the table in one of the following ways: • added automatically by the switch. A switch adds an entry for its own mac address and adds entries for ad...
Page 105: Adding An Arp Entry
D-link dws-1008 user manual 8 adding an arp entry mss automatically adds a local entry for a switch and dynamic entries for addresses learned from traffic received by the switch. You can add the following types of entries: dynamic - ages out based on the aging timeout. Static - does not age out but ...
Page 107
D-link dws-1008 user manual 88 logging in to a remote device from within an mss console session or telnet session, you can use the telnet client to establish a telnet client session from a switch’s cli to another device. To establish a telnet client session with another device, use the following com...
Page 108: Tracing A Route
D-link dws-1008 user manual 8 tracing a route you can trace the router hops necessary to reach an ip host. The traceroute facility uses the ttl (time to live) field in the ip header to cause routers and servers to generate specific return messages. Traceroute starts by sending a udp datagram to the ...
Page 109: Configuring Snmp
D-link dws-1008 user manual 0 configuring snmp mss supports simple network management protocol (snmp) versions 1, 2c, and 3. Overview the mss snmp engine (also called the snmp server or agent) can run any combination of the following snmp versions: snmpv1 - snmpv1 is the simplest and least secure sn...
Page 110: Enabling Snmp Versions
D-link dws-1008 user manual 1 setting the system location and contact strings to set the location and contact strings for a switch, use the following commands: set system location string set system contact string each string can be up to 256 characters long, with no blank spaces. The following comma...
Page 111
D-link dws-1008 user manual the access level specifies the read-write privileges of the community string: read-only - an snmp management application using the string can get (read) object values on the switch but cannot set (write) them. This is the default. Read-notify - an snmp management applicat...
Page 112
D-link dws-1008 user manual the snmp-engine-id option specifies a unique identifier for an instance of an snmp engine. To send informs, you must specify the engine id of the inform receiver. To send traps and to allow get and set operations and so on, specify local as the engine id. • hex hex-string...
Page 113: Command Examples
D-link dws-1008 user manual command examples the following command creates usm user snmpmgr1, associated with the local snmp engine id. This user can send traps to notification receivers. Dws-1008# set snmp usm snmpmgr1 snmp-engine-id local success: change accepted. The following command creates usm...
Page 114: Command Example
D-link dws-1008 user manual command example the following command sets the minimum level of snmp security allowed to authentication and encryption: dws-1008# set snmp security encrypted success: change accepted. Configuring a notification profile a notification profile is a named list of all the not...
Page 115
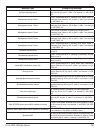
D-link dws-1008 user manual clientauthorizationsuccesstraps - generated when a client is successfully authorized. Clientauthenticationfailuretraps - generated when authentication fails for a client. Clientauthorizationfailuretraps - generated when authorization fails for a client. Clientclearedtraps...
Page 116: Command Examples
D-link dws-1008 user manual rfdetectdostraps - generated when mss detects a dos attack other than an associate request flood, reassociate request flood, or disassociate request flood. Rfdetectinterferingrogueaptraps - generated when an interfering device is detected. Rfdetectinterferingroguedisappea...
Page 117
D-link dws-1008 user manual 8 configuring a notification target a notification target is a remote device to which mss sends snmp notifications. You can configure the mss snmp engine to send confirmed notifications (informs) or unconfirmed notifications (traps). Some of the command options differ dep...
Page 118
D-link dws-1008 user manual to clear a notification target, use the following command: clear snmp notify target target-num the target-num is an id for the target. This id is local to the switch and does not need to correspond to a value on the target itself. You can specify a number from 1 to 10. Th...
Page 119: Command Examples
D-link dws-1008 user manual 100 command examples the following command configures a notification target for acknowledged notifications: dws-1008# set snmp notify target 1 10.10.40.9 usm inform user securesnmpmgr1 snmp-engine-id ip success: change accepted. This command configures target 1 at ip addr...
Page 120: Displaying Usm Settings
D-link dws-1008 user manual 101 displaying the configured snmp community strings to display the configured snmp community strings, use the following command: show snmp community displaying usm settings to display usm settings, use the following command: show snmp usm displaying notification profiles...
Page 121: Overview
D-link dws-1008 user manual 10 configuring dwl-8220ap access points dwl-8220ap access points contain radios that provide networking between your wired network and ieee 802.11 wireless users. An access point connects to the wired network through a 10/100 ethernet link and connects to wireless users t...
Page 122: Country of Operation
D-link dws-1008 user manual 10 to configure access points, perform the following tasks, in this order: • specify the country of operation. • configure access ports, distributed ap connections, and dual homing. • if required, configure radio-specific parameters, which include the channel number, tran...
Page 123
D-link dws-1008 user manual 10 distributed ap network requirements because distributed aps are not directly attached to a switch, they require additional support from the network in order to function. • power - poe must be provided on one of the ethernet connections to the ap. Be sure to use a poe i...
Page 124: Distributed Aps and Stp
D-link dws-1008 user manual 10 distributed aps and stp a distributed ap is a leaf device. You do not need to enable stp on the port that is directly connected to the ap. If spanning tree protocol (stp) is enabled on the port that is directly connected to a distributed ap, you might need to change th...
Page 125: Ap Parameters
D-link dws-1008 user manual 10 the ip and host keywords can be in lowercase, uppercase (ip or host), or mixed case (example: ip, host, and so on.) you can use spaces after the colon or commas, but spaces are not supported within ip addresses or hostnames. Leading zeroes are supported in ip addresses...
Page 126
D-link dws-1008 user manual 10 resiliency and dual-homing options for aps aps can support a wide variety of resiliency options. Redundancy for poe, for data link connections and for switch services can be provided to the ap. • poe redundancy - on ap models that have two ethernet ports, you can provi...
Page 127
D-link dws-1008 user manual 108 boot process for distributed aps when a distributed ap boots on the network, it uses the process described in this section. Note that this process applies only to distributed aps; it does not apply to a directly connected ap. The boot process for a directly connected ...
Page 128: Contacting A Switch
D-link dws-1008 user manual 10 static ip address configuration for distributed aps in cases where dhcp is not available, you can manually assign ip address information to a distributed ap. This information is configured through the cli. You can configure the following information for a distributed a...
Page 129
D-link dws-1008 user manual 110 2. If no ip addresses or hostnames were specified in the option 43 field of the dhcp offer message, the ap sends a find switch message to udp port 5000 on the subnet broadcast address. • switches in the same ip subnet as the ap receive the message and respond with a f...
Page 130
D-link dws-1008 user manual 111 5. The ap sends find switch requests to the switch ip addresses given by the dns reply. If a switch receives the find switch request, the process continues with step 6. However, if no switches reply, the ap repeatedly retries this method: • if still no switch’s reply,...
Page 131
D-link dws-1008 user manual 11 this information is used in the following way when the ap attempts to contact a switch: 1. If items a and b (but not item c) are specified, and the switch’s ip address is part of the local subnet, then the ap sends an arp request for its configured static ip address, t...
Page 132
D-link dws-1008 user manual 11 4. If the ap cannot reach the switch using the static ip address information, then the ap attempts to boot using the default boot process; that is, by contacting a dhcp server, as described in “how a distributed ap obtains an ip address through dhcp”. If the default ap...
Page 133: Session Load Balancing
D-link dws-1008 user manual 11 session load balancing you can assign access points to a load-balancing group. A load-balancing group helps reduce congestion by distributing client sessions among the access points in the group. For example, if an 802.11b/g radio operating on channel 1 is supporting m...
Page 134
D-link dws-1008 user manual 11 parameter default value radio behavior when parameter set to default value cac-mode none does not limit the number of active user sessions based on call admission control (cac). Cac-session 14 if session-based cac is enabled (cac-mode is set to session), limits the num...
Page 135
D-link dws-1008 user manual 11 parameter default value radio behavior when parameter set to default value ssid-name dlink uses the ssid name dlink. Ssid-type crypto encrypts wireless traffic for the ssid. Static-cos disable assigns cos based on the qos mode ( wmm or svp) or based on acls. Tkip-mc-ti...
Page 136: Public and Private Ssids
D-link dws-1008 user manual 11 public and private ssids each radio can support the following types of ssids: • encrypted ssid - clients using this ssid must use encryption. Use the encrypted ssid for secured access to your enterprise network. • clear ssid - clients using this ssid do not use encrypt...
Page 137: Radio Profiles
D-link dws-1008 user manual 118 radio profiles you can easily assign radio configuration parameters to many radios by configuring a radio profile and assigning the profile to the radios. To use a radio, you must assign a profile to the radio. You can enable the radio when you assign the profile. The...
Page 138: Rf Auto-Tuning
D-link dws-1008 user manual 11 rf auto-tuning the rf auto-tuning feature dynamically assigns channel and power settings to ap radios, and adjusts those settings when needed. Rf auto-tuning can perform the following tasks: • assign initial channel and power settings when an ap radio is started. • per...
Page 139
D-link dws-1008 user manual 10 although these parameters have default values, d-link recommends that you change the values for each radio for optimal performance. For example, leaving the channel number on each radio set to its default value can result in high interference among the radios. Configur...
Page 140
D-link dws-1008 user manual 11 country code algeria dz argentina ar australia au austria at belgium be bolivia bo brazil br bulgaria bg canada ca chile cl china cn colombia co costa rica cr cote d’ivoire ci croatia hr cyprus cy czech republic cz denmark dk dominican republic do ecuador ec el salvado...
Page 141
D-link dws-1008 user manual 1 =============================================================== fan status: fan1 ok fan2 ok fan3 ok temperature: temp1 ok temp2 ok temp3 ok psu status: lower power supply dc ok ac ok upper power supply missing memory: 115.09/496.04 (23%) total power over ethernet : 32.0...
Page 142
D-link dws-1008 user manual 1 configured aps have precedence over unconfigured aps when a switch determines the switch ip address to send to a booting ap, the switch gives preference to aps that are already configured, over unconfigured aps that require an auto-ap profile. The switch can direct a co...
Page 143: Changing Ap Parameter Values
D-link dws-1008 user manual 1 parameter default value bias high blink (not shown in show dap config output) disable force-image-download disable (no) group (load balancing group) none mode disabled persistent none upgrade-firmware (boot-download-enable) enable (yes) radio num auto-tune max-power def...
Page 144: Enabling The Auto-Ap Profile
D-link dws-1008 user manual 1 enabling the auto-ap profile to enable the auto-ap profile for automatic distributed ap configuration, type the following command: dws-1008# set dap auto mode enable success: change accepted. Specifying the radio profile used by the auto-ap profile the auto-ap profile u...
Page 145: Permanent Ap
D-link dws-1008 user manual 1 radio 2 type: 802.11a, state: configure succeed [enabled] operational channel: 64 operational power: 14 base mac: 00:0b:0e:00:d2:c1 bssid1: 00:0b:0e:00:d2:c1, ssid: public bssid2: 00:0b:0e:00:d2:c3, ssid: employee-net bssid3: 00:0b:0e:00:d2:c5, ssid: mycorp-tkip the out...
Page 146
D-link dws-1008 user manual 1 setting the port type for a directly connected ap you must set the port type on dws-1008 switch ports that are directly connected to access points. When you change port type, mss applies default settings appropriate for the port type. The table below lists the default s...
Page 147: Specifying Ip Information
D-link dws-1008 user manual 18 configuring static ip addresses on distributed aps by default, distributed aps use the procedure described in “how a distributed ap obtains an ip address through dhcp” to obtain an ip address and connect to a switch. In some installations, dhcp may not be available. In...
Page 148: Specifying Vlan Information
D-link dws-1008 user manual 1 when a static ip address is specified for a distributed ap, there is no preconfigured dns information or dns name for the switch the distributed ap attempts to use as its boot device. If you configure a static ip address for a distributed ap, but do not specify a boot d...
Page 149: Changing Ap Names
D-link dws-1008 user manual 10 changing ap names the default name of a directly attached ap is based on the port number of the access port attached to the ap. For example, the default name for an ap on access port 1 is ap01. The default name of a distributed ap is based on the number you assign to i...
Page 150
D-link dws-1008 user manual 11 disabling or reenabling automatic firmware upgrades an access point can automatically upgrade its boot firmware by loading the upgrade version of the firmware from a switch when the ap is booting. Automatic firmware upgrades are enabled by default. To disable or reenab...
Page 151: Enabling Led Blink Mode
D-link dws-1008 user manual 1 enabling led blink mode blink mode makes an ap easy to identify. When blink mode is enabled, the health and radio leds alternately blink green and amber. By default, blink mode is disabled. Blink mode continues until you disable it. Led blink mode is disabled by default...
Page 152: Encryption Options
D-link dws-1008 user manual 1 encryption options by default, a dws-1008 switch can configure and manage a distributed ap regardless of whether the ap has an encryption key, and regardless of whether you have confirmed the fingerprint by setting it in mss. You can configure a switch to require distri...
Page 153
D-link dws-1008 user manual 1 if the ap is already installed and operating, use the show dap status command to display the fingerprint. The following example shows information for distributed ap 8, including its fingerprint: dws-1008# show dap status 8 dap: 8, ip-addr: 10.2.26.40 (vlan ‘default’), a...
Page 155: Removing A Service Profile
D-link dws-1008 user manual 1 the following command configures a service profile named corp1, and assigns ssid mycorp_rnd to it: dws-1008# set service-profile corp1 ssid-name mycorp_rnd success: change accepted. The following command applies the name corporate users to the ssid managed by service pr...
Page 157
D-link dws-1008 user manual 18 parameter default value description disabled none. All rates applicable to the radio type are supported by default. Data transmission rates that ap radios will not use to transmit data. This setting applies only to data sent by the ap radios. The radios will still acce...
Page 158
D-link dws-1008 user manual 1 disabling idle-client probing by default, an ap radio sends keepalive messages (idle-client probes) every 10 seconds to each client that has an active session on the radio, to verify that the client is still active. The probes are unicast null- data frames. Normally, a ...
Page 159: Configuring A Radio Profile
D-link dws-1008 user manual 10 changing the short retry threshold the short retry threshold specifies the number of times a radio can send a short unicast frame for an ssid without receiving an acknowledgment for the frame. A short unicast frame is a frame that is shorter than the rts threshold. To ...
Page 161: Changing The Dtim Interval
D-link dws-1008 user manual 1 changing the dtim interval the dtim interval specifies the number of times after every beacon that a radio sends a delivery traffic indication map (dtim). An access point sends the multicast and broadcast frames stored in its buffers to clients who request them in respo...
Page 162
D-link dws-1008 user manual 1 changing the fragmentation threshold the fragmentation threshold specifies the longest a frame can be without being fragmented into multiple frames by a radio before transmission. To change the fragmentation threshold, use the following command: set radio-profile name f...
Page 163: Changing The Preamble Length
D-link dws-1008 user manual 1 changing the preamble length by default, 802.11b/g radios advertise support for frames with short preambles and can support frames with short or long preambles. An 802.11b/g radio generates unicast frames to send to a client with the preamble length specified by the cli...
Page 164: Removing A Radio Profile
D-link dws-1008 user manual 1 all radios that use this profile must be disabled before you can delete the profile. If you specify a parameter, the setting for the parameter is reset to its default value. The settings of the other parameters are unchanged and the radio profile remains in the configur...
Page 165
D-link dws-1008 user manual 1 to configure the 802.11b radio on port 2 for channel 1 with a transmit power of 10 dbm, type the following command: dws-1008# set ap 2 radio 1 channel 1 tx-power 10 success: change accepted. To configure the 802.11a radio on port 5 for channel 36 with a transmit power o...
Page 166
D-link dws-1008 user manual 1 mapping the radio profile to service profiles to assign ssids to radios, you must map the service profiles for the ssids to the radio profile that is assigned to the radios. To map a radio profile to a service profile, use the following command: set radio-profile name s...
Page 167
D-link dws-1008 user manual 18 disabling or reenabling radios you can disable or reenable radios on a radio profile basis or individual basis. You also can reset a radio to its factory default settings. Enabling or disabling individual radios to disable or reenable an access point radio, use the fol...
Page 171
D-link dws-1008 user manual 1 the following command displays information for two distributed aps that are not configured: dws-1008# show dap unconfigured total number of entries: 2 serial id model ip address port vlan ----------------------------------------------------------------------------------...
Page 172
D-link dws-1008 user manual 1 wpa enabled: ciphers: cipher-tkip authentication: 802.1x tkip countermeasures time: 60000ms vlan-name = orange session-timeout = 300 service-type = 2 beacon rate: 6.0 multicast rate: auto mandatory rate: 6.0,12.0,24.0 standard rates: 9.0,18.0,36.0,48.0,54.0 beacon rate:...
Page 173: Distributed Aps
D-link dws-1008 user manual 1 the following command displays the status of a distributed ap access point: dws-1008# show dap status 1 dap: 1, ip-addr: 10.2.30.5 (vlan ‘vlan-corp’), ap model: dwl-8220ap, manufacturer: d-link, name: dap01 fingerprint: b4:f9:2a:52:37:58:f4:d0:10:75:43:2f:45:c9:52:c3 ==...
Page 175: Configuring User Encryption
D-link dws-1008 user manual 1 mobility system software (mss) encrypts wireless user traffic for all users who are successfully authenticated to join an encrypted ssid and who are then authorized to join a vlan. Mss supports the following types of encryption for wireless user traffic: • 802.11i • wi-...
Page 176: Configuring Wpa
D-link dws-1008 user manual 1 the table below lists the encryption types supported by mss and their default states. Encryption type client support default state configuration required in mss rsn rsn clients non-rsn clients disabled • enable the rsn information element (ie). • specify the supported c...
Page 177: Tkip Countermeasures
D-link dws-1008 user manual 18 tkip countermeasures wpa access points and clients verify the integrity of a wireless frame received on the network by generating a keyed message integrity check (mic). The michael mic used with tkip provides a holddown mechanism to protect the network against tamperin...
Page 178: Wpa Authentication Methods
D-link dws-1008 user manual 1 wpa authentication methods you can configure an ssid to support one or both of the following authentication methods for wpa clients: • 802.1x—the access point and client use an extensible authentication protocol (eap) method to authenticate one another, then use the res...
Page 179: Client Support
D-link dws-1008 user manual 10 client support to use the tkip or ccmp cipher suite for encryption, a client must support wpa. However, an ap radio configured for wpa can support non-wpa clients who use dynamic wep or static wep. If the wpa ie is enabled in the service profile used by an ssid support...
Page 180: Configuring Wpa
D-link dws-1008 user manual 11 configuring wpa to configure access point radios to support wpa: 1. Create a service profile for each ssid that will support wpa clients. 2. Enable the wpa ie in the service profile. 3. Enable the cipher suites you want to support in the service profile. (tkip is enabl...
Page 182: Enabling Psk Authentication
D-link dws-1008 user manual 1 enabling psk authentication by default, wpa uses 802.1x dynamic keying. If you plan to use static keys, you must enable psk authentication and configure a passphrase or the raw key. You can configure the passphrase or key globally. You also can configure keys on an indi...
Page 184
D-link dws-1008 user manual 1 assigning the service profile to radios and enabling the radios after you configure wpa settings in a service profile, you can map the service profile to a radio profile, assign the radio profile to radios, and enable the radios to activate the settings. To map a servic...
Page 185: Configuring Rsn (802.11I)
D-link dws-1008 user manual 1 configuring rsn (802.11i) robust security network (rsn) provides 802.11i support. Rsn uses aes encryption. You can configure a service profile to support rsn clients exclusively, or to support rsn with wpa clients, or even rsn, wpa and wep clients. The configuration tas...
Page 186: Enabling Psk Authentication
D-link dws-1008 user manual 1 specifying the rsn cipher suites to use rsn, at least one cipher suite must be enabled. You can enable one or more of the following cipher suites: • ccmp • tkip • 40-bit wep • 104-bit wep by default, tkip is enabled and the other cipher suites are disabled. To enable or...
Page 187: Configuring Wep
D-link dws-1008 user manual 18 assigning the service profile to radios and enabling the radios after you configure rsn settings in a service profile, you can map the service profile to a radio profile, assign the radio profile to radios, and enable the radios to activate the settings. To map a servi...
Page 188: Assigning Static Wep Keys
D-link dws-1008 user manual 1 to support dynamic wep in a wpa environment, enable wpa and enable the wep-40 or wep-104 cipher suite. (see “configuring wpa”.) this section describes how to configure and assign static wep keys. (to change other key-related settings, see “managing 802.1x encryption key...
Page 189: Enabling Wpa With Tkip
D-link dws-1008 user manual 10 to configure an ssid that uses service profile wepsrvc to use wep key index 2 for encrypting multicast traffic, type the following command: dws-1008# set service-profile wepsrvc wep active-multicast-index 2 success: change accepted. To configure an ssid that uses servi...
Page 190
D-link dws-1008 user manual 11 5. Display the service profile wpa to verify the changes. Type the following command: dws-1008# show service-profile sp1 6. Map service profile wpa to radio profile rp1. Type the following commands: dws-1008# set radio-profile rp1 service-profile wpa success: change ac...
Page 191
D-link dws-1008 user manual 1 3. Set the ssid in the service profile to thiscorp. Type the following command: dws-1008# set service-profile wpa-wep ssid-name thiscorp success: change accepted. 4. Enable wpa in service profile wpa-wep. Type the following command: dws-1008# set service-profile wpa-wep...
Page 192
D-link dws-1008 user manual 1 configuring encryption for mac clients the following example shows how to configure mss to provide psk authentication and tkip or 40-bit wep encryption for mac clients: 1. Create an authentication rule that sends all mac users of ssid voice to the local database for aut...
Page 193
D-link dws-1008 user manual 1 6. Set the ssid in the service profile to voice. Type the following command: dws-1008# set service-profile wpa-wep-for-mac ssid-name voice success: change accepted. 7. Enable wpa in service profile wpa-wep-for-mac. Type the following command: dws-1008# set service-profi...
Page 194
D-link dws-1008 user manual 1 ciphers: cipher-tkip, cipher-wep40 authentication: pre-shared key tkip countermeasures time: 60000ms pre-shared-key: 92f99cd49e186cadee13fda7b2a2bac78975a5723a4a6b3 1b5b5395d6b001dbe 12. Map service profile wpa-wep-for-mac to radio profile rp3. Type the following comman...
Page 195: Rf Auto-Tuning Overview
D-link dws-1008 user manual 1 rf auto-tuning overview the rf auto-tuning feature dynamically assigns channel and power settings to ap radios, and adjusts those settings when needed. Rf auto-tuning can perform the following tasks: • assign initial channel and power settings when an ap radio is starte...
Page 196: How Channels Are Selected
D-link dws-1008 user manual 1 how channels are selected when a radio first comes up, if rf auto-tuning for channels is enabled, the initial channel selected will follow a uniform distribution of channels that spans the list of channels, rather than selecting the next sequential channel number. For e...
Page 197: Channel Tuning
D-link dws-1008 user manual 18 channel tuning by default, the switch evaluates the scan results for possible channel changes every 3600 seconds (1 hour). Mss uses the following parameters to determine whether to change the channel on a radio: • presence of active sessions. By default, if the radio h...
Page 198: Rf Auto-Tuning Parameters
D-link dws-1008 user manual 1 tuning the transmit data rate a radio sends beacons, probe requests, and probe responses at the minimum transmit data rate allowed for clients. This gives them the maximum distance. All other packets are transmitted at a rate determined by their destination. All packets...
Page 199
D-link dws-1008 user manual 180 changing rf auto-tuning settings changing channel tuning settings disabling or reenabling channel tuning rf auto-tuning for channels is enabled by default. To disable or reenable the feature for all radios in a radio profile, use the following command: set radio-profi...
Page 200: Enabling Power Tuning
D-link dws-1008 user manual 181 changing the channel holddown interval the default channel holddown interval is 900 seconds. You can change the interval to a value from 0 to 65535 seconds. To change the channel holddown interval, use the following command: set radio-profile name auto-tune channel-ho...
Page 201: Locking Down Tuned Settings
D-link dws-1008 user manual 18 changing the maximum default power allowed on a radio by default, the maximum power level that rf auto-tuning can set on a radio is the same as the maximum power level allowed for the country of operation. To change the maximum power level that rf auto- tuning can assi...
Page 202
D-link dws-1008 user manual 18 displaying rf auto-tuning information you can display the rf auto-tuning configuration, a list of rf neighbors, and the values of rf attributes. Displaying rf auto-tuning settings to display the rf auto-tuning settings that you can configure in a radio profile, use the...
Page 203: Displaying Rf Neighbors
D-link dws-1008 user manual 18 to display the rf auto-tuning and other individual radio settings on both radios on the distributed ap access point configured on connection 1, type the following command: dws-1008# show dap config 1 dap 1: serial-id: 12345678, ap model: dwl-8220ap, bias: high, name: d...
Page 205: Listeners
D-link dws-1008 user manual 18 configuring aps to be aeroscout listeners aeroscout rfid tags are wireless transmitters that you can place on assets such as office equipment to track the equipment’s location. Each tag regularly transmits its unique id. Aeroscout listeners detect the transmissions fro...
Page 206
D-link dws-1008 user manual 18 the following example shows the commands to configure three distributed aps to be aeroscout listeners. This example assumes that the aps have already been installed and configured. Dws-1008# set service-profile rfid-listeners ssid-type clear success: change accepted. D...
Page 207: Locating An Rfid Tag
D-link dws-1008 user manual 188 locating an rfid tag you can use an aeroscout engine to locate an asset to which an rfid tag is attached. Using an aeroscout engine 1. Load the site map in aeroscout system manager. 2. Mark the origin point (0,0), if not already done. 3. Calibrate distance, if not alr...
Page 208: About Qos
D-link dws-1008 user manual 18 configuring quality of service this chapter describes the quality of service (qos) features supported in mss and how to configure and manage them. About qos mss supports layer 2 and layer 3 classification and marking of traffic, and optimized forwarding of wireless tra...
Page 209: Qos Mode
D-link dws-1008 user manual 10 qos feature description configuration command qos parameters configured in service profiles (continued) transmit rates data transmission rates supported by each radio type. The following categories are specified: • beacon • multicast • mandatory (a client must support ...
Page 210: Wmm Qos Mode
D-link dws-1008 user manual 11 wmm qos mode dws-1008 switches and dwl-8220ap access points each provide classification and marking for wmm qos: • dws-1008 switches classify and mark traffic based on 802.1p tag value (for tagged traffic) or differentiated services code point (dscp) value. • dwl-8220a...
Page 211: Wmm Qos On An Ap
D-link dws-1008 user manual 1 wmm qos on an ap access points use forwarding queues to prioritize traffic for wireless clients. For a packet received by the ap from a client, the ap classifies the packet based on the service type in the 802.11 header and maps the service type value to an internal cos...
Page 212: U-Apsd Support
D-link dws-1008 user manual 1 u-apsd support wmm clients that use powersave mode can more efficiently request buffered unicast packets from ap radios by using u-apsd. When u-apsd support is enabled in mss, a client can retrieve buffered unicast packets for a traffic priority enabled for u-apsd by se...
Page 213: Broadcast Control
D-link dws-1008 user manual 1 broadcast control you also can enhance bandwidth availability on an ssid by enabling the following broadcast control features: • proxy arp—switch responds on behalf of wireless clients to arp requests for their ip addresses. • dhcp restrict—switch captures and does not ...
Page 214: Changing Qos Settings
D-link dws-1008 user manual 1 changing qos settings you can change the settings of the following qos options: • qos mode • u-apsd support • cac state and maximum number of sessions • broadcast control • static cos state and cos value • dscp-cos mappings the qos mode is configurable on a radio-profil...
Page 215: Enabling Cac
D-link dws-1008 user manual 1 configuring call admission control to configure cac for an ssid, enable the feature on the ssid’s service profile. When enabled, cac limits the number of active sessions a radio can have to 14 by default. You can change the maximum number of sessions to a value from 0 t...
Page 216: Changing Cos Mappings
D-link dws-1008 user manual 1 for example, to configure static cos 7 for service profile sp1, use the following commands: dws-1008# set service-profile sp1 static-cos enable success: change accepted. Dws-1008# set service-profile sp1 cos 7 success: change accepted. Changing cos mappings to change co...
Page 217: Displaying Qos Information
D-link dws-1008 user manual 18 displaying qos information you can display the following types of information for qos: • radio profile qos settings: qos mode, u-apsd support • service profile qos settings: cac, static cos, and broadcast control settings • broadcast control settings • default cos mapp...
Page 219: Displaying Cos Mappings
D-link dws-1008 user manual 00 displaying cos mappings mss provides commands for displaying the default cos mappings and configured mappings. Displaying the default cos mappings to display the default cos mappings, use the following command: dws-1008# show qos default ingress qos classification map ...
Page 220: Displaying The Dscp Table
D-link dws-1008 user manual 01 displaying the dscp table to display the standard mappings of dscp, tos, and precedence values, use the following command: dws-1008# show qos dscp-table dscp tos precedence tos dec hex dec hex ---------------------------------------------- 0 0x00 0 0x00 0 0 1 0x01 4 0x...
Page 221: Tree Protocol
D-link dws-1008 user manual 0 configuring and managing spanning tree protocol the purpose of the spanning tree protocol (stp) is to maintain a loop-free network. A loop-free path is accomplished when a device recognizes a loop in the topology and blocks one or more redundant paths. Mobility system s...
Page 222: Bridge Priority
D-link dws-1008 user manual 0 changing standard spanning tree parameters you can change the following standard stp parameters: • bridge priority • port cost • port priority bridge priority the bridge priority determines the switch’s eligibility to become the root bridge. You can set this parameter g...
Page 223: Port Priority
D-link dws-1008 user manual 0 port priority port priority is the eligibility of the port to be the designated port to the root bridge, and thus part of the path to the root bridge. When the switch has more than one link to the root bridge, stp uses the link with the lowest priority value. You can se...
Page 227: Port Fast Convergence
D-link dws-1008 user manual 08 port fast convergence port fast convergence bypasses both the listening and learning stages and immediately places a port in the forwarding state. You can use port fast convergence on ports that are directly connected to servers, hosts, or other mac stations. Note: do ...
Page 228
D-link dws-1008 user manual 0 displaying port fast convergence information to display port fast convergence information, use the following command: show spantree portfast [port-list] to display port fast convergence information for all ports, type the following command: dws-1008# show spantree portf...
Page 231: Displaying Blocked Stp Ports
D-link dws-1008 user manual 1 displaying the stp port cost on a vlan basis to display a brief list of the stp port cost for a port in each of its vlans, use the following command: show spantree portvlancost port-list this command displays the same information as the show spantree command’s cost fiel...
Page 232: Clearing Stp Statistics
D-link dws-1008 user manual 1 displaying spanning tree statistics to display stp statistics, use the following command: show spantree statistics [port-list [vlan vlan-id]] to display stp statistics for port 1, type the following command: dws-1008# show spantree statistics 1 clearing stp statistics t...
Page 233
D-link dws-1008 user manual 1 2. Configure a backbone vlan and verify the configuration change. Type the following commands: dws-1008# set vlan 10 name backbone port 7-8 success: change accepted. Dws-1008# show vlan config admin vlan tunl vlan name status state affin port tag port state ------------...
Page 234
D-link dws-1008 user manual 1 4. Reconnect or reenable ports 7 and 8 and verify the change. Type the following commands: dws-1008# set port enable 7-8 success: set “enable” on port 7-8 dws-1008# show port status port name admin oper config actual type media 1 up up auto 100/full network 10/100basetx...
Page 235: Snooping
D-link dws-1008 user manual 1 configuring and managing igmp snooping internet group management protocol (igmp) snooping controls multicast traffic on a switch by forwarding packets for a multicast group only on the ports that are connected to members of the group. A multicast group is a set of ip ho...
Page 236: Enabling The Pseudo-Querier
D-link dws-1008 user manual 1 enabling the pseudo-querier the igmp pseudo-querier enables igmp snooping to operate in a vlan that does not have a multicast router to send igmp general queries to clients. Note: d-link recommends that you use the pseudo-querier only when the vlan contains local multic...
Page 237: Changing The Query Interval
D-link dws-1008 user manual 18 changing the query interval to change the igmp query interval timer, use the following command: set igmp qi seconds [vlan vlan-id] for seconds, you can specify a value from 1 through 65,535. The default is 125 seconds. Changing the other-querier-present interval to cha...
Page 238: Enabling Router Solicitation
D-link dws-1008 user manual 1 enabling router solicitation a switch can search for multicast routers by sending multicast router solicitation messages. This message invites multicast routers that receive the message and that support router solicitation to immediately advertise themselves to the swit...
Page 240
D-link dws-1008 user manual 1 to display multicast information for vlan orange, type the following command: dws-1008# show igmp vlan orange vlan: orange igmp is enabled proxy reporting is on mrouter solicitation is on querier functionality is off configuration values: qi: 125 oqi: 300 qri: 100 lmqi:...
Page 241: Displaying Multicast Routers
D-link dws-1008 user manual displaying multicast statistics only to display multicast statistics only without also displaying all the other multicast information, use the following command: show igmp statistics [vlan vlan-id] clearing multicast statistics to clear the multicast statistics counters, ...
Page 242
D-link dws-1008 user manual displaying multicast receivers to display information about the multicast receivers only without also displaying all the other multicast information, use the following command: show igmp receiver-table [vlan vlan-id] [group group-ip-addr/mask-length] use the group paramet...
Page 243: Acls
D-link dws-1008 user manual configuring and managing security acls about security access control lists a security access control list (acl) filters packets for the purpose of discarding them, permitting them, or permitting them with modification (marking) for class-of-service (cos) priority treatmen...
Page 244: Security Acl Filters
D-link dws-1008 user manual security acl filters a security acl filters packets to restrict or permit network traffic. These filters can then be mapped by name to authenticated users, ports, vlans, virtual ports, or distributed aps. You can also assign a class-of-service (cos) level that marks the p...
Page 245: Traffic Direction
D-link dws-1008 user manual traffic direction an acl can be mapped at any scope to either the inbound traffic direction or the outbound traffic direction. It is therefore possible for two acls to be applied to the same traffic as it traverses the system: one acl is applied on the inbound direction a...
Page 246: Setting A Source Ip Acl
D-link dws-1008 user manual setting a source ip acl you can create an ace that filters packets based on the source ip address and optionally applies cos packet handling. You can also determine where the ace is placed in the security acl by using the before editbuffer-index or modify editbuffer-index...
Page 247: Wildcard Masks
D-link dws-1008 user manual 8 wildcard masks when you specify source and destination ip addresses in an ace, you must also include a mask for each in the form source-ip-addr mask and destination-ip-addr mask. The mask is a wildcard mask. The security acl checks the bits in ip addresses that correspo...
Page 249: Setting Tcp and Udp Acls
D-link dws-1008 user manual 0 setting tcp and udp acls security acls can filter tcp and udp packets by source and destination ip address, precedence, and tos level. You can apply a tcp acl to established tcp sessions only, not to new tcp sessions. In addition, security acls for tcp and udp can filte...
Page 250: Determining The Ace Order
D-link dws-1008 user manual 1 determining the ace order the set security acl command creates a new entry in the edit buffer and appends the new entry as a rule at the end of an acl, unless you specify otherwise. The order of aces is significant, because the earliest ace takes precedence over later a...
Page 251: Viewing The Edit Buffer
D-link dws-1008 user manual use the first two commands to display the acls that you have not yet committed to nonvolatile storage. The first command lists the acls by name. The second command shows the acls in detail. Use the show security acl info command to display acls that are already committed....
Page 252: Viewing Security Acl Details
D-link dws-1008 user manual viewing security acl details you can display the contents of one or all security acls that are committed. To display the contents of all committed security acls, type the following command: dws-1008# show security acl info acl information for all set security acl ip acl-9...
Page 253: Clearing Security Acls
D-link dws-1008 user manual to sample the number of hits the security acls generate, you must specify the number of seconds between samples. For example, to sample the hits generated every 180 seconds, type the following commands: dws-1008# set security acl hit-sample-rate 180 dws-1008# show securit...
Page 254
D-link dws-1008 user manual mapping user-based security acls when you configure administrator or user authentication, you can set a filter-id authorization attribute at the radius server or at the switch’s local database. The filter-id attribute is a security acl name with the direction of the packe...
Page 255: Or Distributed Aps
D-link dws-1008 user manual 4. Alternatively, authenticate the user with the filter-id attribute in the switch’s local database. Use one of the following commands. Specify .In for incoming packets or .Out for outgoing packets. Mapping target commands user authenticated by a password set user usernam...
Page 256: Clearing A Security Acl Map
D-link dws-1008 user manual displaying acl maps to ports, vlans, and virtual ports two commands display the port, vlan, virtual port, and distributed ap mapping of a specific security acl. For example, to show the ports, vlans, virtual ports, and distributed aps mapped to acl-999, type one of the fo...
Page 257: Modifying A Security Acl
D-link dws-1008 user manual 8 to stop the packet filtering of a user-based security acl, you must modify the user’s configuration in the local database on the switch or on the radius servers where packet filters are authorized. For information about deleting a security acl from a user’s configuratio...
Page 258
D-link dws-1008 user manual adding another ace to a security acl the simplest way to modify a security acl is to add another ace. For example, suppose you wanted to modify an existing acl named acl-violet. Follow these steps: 1. To display all committed security acls, type the following command: dws...
Page 259
D-link dws-1008 user manual 0 placing one ace before another you can use the before editbuffer-index portion of the set security acl command to place a new ace before an existing ace. For example, suppose you want to deny some traffic from ip address 192.168.254.12 in acl-111. Follow these steps: 1....
Page 260
D-link dws-1008 user manual 1 modifying an existing security acl you can use the modify editbuffer-index portion of the set security acl command to modify an active security acl. For example, suppose the acl acl-111 currently blocks some packets from ip address 192.168.254.12 with the mask 0.0.0.255...
Page 261
D-link dws-1008 user manual clearing security acls from the edit buffer use the rollback command to clear changes made to the security acl edit buffer since it was last committed. The acl is rolled back to its state at the last commit command. For example, suppose you want to remove an ace that you ...
Page 262: Using Acls to Change Cos
D-link dws-1008 user manual 4. To clear the uncommitted acl-111 ace from the edit buffer, type the following command: dws-1008# rollback security acl acl-111 5. To ensure that you have cleared the acl-111 ace, type the following command. Only the uncommitted acl-a now appears. Dws-1008# show securit...
Page 263: Using The Dscp Option
D-link dws-1008 user manual filtering based on dscp values you can configure an ace to filter based on a packet’s differentiated services code point (dscp) value, and change the packet’s cos based on the dscp value. A cos setting marked by an ace overrides the cos setting applied from the switch’s q...
Page 264
D-link dws-1008 user manual using the precedence and tos options you also can indirectly filter on dscp by filtering on both the ip precedence and ip tos values of a packet. However, this method requires two aces. To use this method, specify the combination of precedence and tos values that is equiv...
Page 265: Over Ip
D-link dws-1008 user manual enabling prioritization for legacy voice over ip mss supports wi-fi multimedia (wmm). Wmm support is enabled by default and is automatically used for priority traffic between wmm-capable devices. Mss also can provide prioritization for non-wmm voip devices. However, to pr...
Page 266
D-link dws-1008 user manual service ip ip tos dscp 802.1p cos ap forwarding type precedence queue 0 0 0 0 0 0 background 3 3 0x60 24 3 3 1 1 0x20 8 1 1 best effort 2 2 0x40 16 2 2 4 4 0x80 32 4 4 video 5 5 0xa0 40 5 5 6 6 0xc0 48 6 6 voice 7 7 0xe0 56 7 7 note: if you are upgrading a switch running ...
Page 267: Known Limitations
D-link dws-1008 user manual 8 enabling svp optimization for spectralink phones spectralink’s voice interoperability for enterprise wireless (view) certification program is designed to ensure interoperability and high performance between svp phones and wlan infrastructure products. D-link dws-1008 sw...
Page 268
D-link dws-1008 user manual configuring a service profile for rsn (wpa2) to configure a service profile for svp phones that use rsn (wpa2): • create the service profile and add the voice ssid to it. • enable the rsn information element (ie). • disable tkip and enable ccmp. • disable 802.1x authentic...
Page 269: Configuring A Radio Profile
D-link dws-1008 user manual 0 configuring a radio profile mss has a default radio profile, which manages all radios by default. Some of the radio parameters require changes for voice traffic. You can modify the default radio profile or create a new one. Note: some radio settings that are beneficial ...
Page 270
D-link dws-1008 user manual 1 to configure a vlan and a last-resort user for the voice ssid: dws-1008# set vlan 2 name v1 port 3 dws-1008# set igmp disable vlan v1 dws-1008# set authentication last-resort ssid phones local dws-1008# set user last-resort-phones attr vlan-name v1 the set vlan and set ...
Page 271: Voip Phones Only)
D-link dws-1008 user manual reason the acl needs to be mapped to both traffic directions if the acl is not also mapped to the inbound direction on the voice vlan, cos will not be marked in the traffic if the path to the svp handset is over a tunnel. Mss does not support mapping an acl to a tunneled ...
Page 272: Among Ip-Only Clients
D-link dws-1008 user manual disabling rf auto-tuning before upgrading a spectralink phone if you plan to upgrade a spectralink phone using tftp over an ap, d-link recommends that you disable rf auto-tuning before you begin the upgrade. This feature can increase the length of time required for the up...
Page 273
D-link dws-1008 user manual security acl configuration scenario the following scenario illustrates how to create a security acl named acl-99 that consists of one ace to permit incoming packets from one ip address, and how to map the acl to a port and a user: 1. Type the following command to create a...
Page 274
D-link dws-1008 user manual managing keys and certificates a digital certificate is a form of electronic identification for computers. The switch requires digital certificates to authenticate its communications to web view, to webaaa clients, and to extensible authentication protocol (eap) clients f...
Page 275: Peap-Ms-Chap-V2 Security
D-link dws-1008 user manual peap-ms-chap-v2 security peap performs a tls exchange for server authentication and allows a secondary authentication to be performed inside the resulting secure channel for client authentication. For example, the microsoft challenge handshake authentication protocol vers...
Page 276: Public Key Infrastructures
D-link dws-1008 user manual • if the switch has no corresponding ca certificate, the switch does not respond to the request from mss. If the switch does have a corresponding ca certificate, and the server certificate is validated (date still valid, signature approved), the switch responds. If the sw...
Page 277: Digital Certificates
D-link dws-1008 user manual 8 digital certificates digital certificates bind the identity of network users and devices to a public key. Network users must authenticate their identity to those with whom they communicate, and must be able to verify the identity of other users and network devices, such...
Page 278
D-link dws-1008 user manual file type standard purpose pkcs #7 cryptographic message syntax standard contains a digital certificate signed by a ca. To install the certificate from a pkcs #7 file, use the crypto certificate command to prepare mss to receive the certificate, then copy and paste the ce...
Page 279
D-link dws-1008 user manual 0 certificates automatically generated by mss the first time you boot a switch with mss version 4.2 or later, mss automatically generates keys and self-signed certificates, in cases where certificates are not already configured or installed. Mss can automatically generate...
Page 280: Method For Your Network
D-link dws-1008 user manual 1 choosing the appropriate certificate installation method for your network depending on your network environment, you can use any of the following methods to install certificates and their public-private key pairs. The methods differ in terms of simplicity and security. ...
Page 281
D-link dws-1008 user manual creating public-private key pairs to use a self-signed certificate or certificate signing request (csr) certificate for switch authentication, you must generate a public-private key pair. To create a public-private key pair, use the following command: crypto generate key ...
Page 282: Object File
D-link dws-1008 user manual installing a key pair and certificate from a pkcs #12 object file pkcs object files provide a file format for storing and transferring storing data and cryptographic information. (for more information, see “pkcs #7, pkcs #10, and pkcs #12 object files”.) a pkcs #12 object...
Page 283: Pkcs #7 Object File
D-link dws-1008 user manual creating a csr and installing a certificate from a pkcs #7 object file after creating a public-private key pair, you can obtain a signed certificate of authenticity from a ca by generating a certificate signing request (csr) from the switch. A csr is a text block with an ...
Page 284: Information
D-link dws-1008 user manual installing a ca’s own certificate if you installed a ca-signed certificate from a pkcs #7 file, you must also install the pkcs #7 certificate of that ca. (if you used the pkcs #12 method, the ca’s certificate is usually included with the key pair and server certificate.) ...
Page 285: Scenarios
D-link dws-1008 user manual key and certificate configuration scenarios the first scenario shows how to generate self-signed certificates. The second scenario shows how to install ca-signed certificates using pkcs #12 object files, and the third scenario shows how to install ca-signed certificates u...
Page 286
D-link dws-1008 user manual dws-1008# crypto generate self-signed web country name: us state name: ca locality name: san francisco organizational name: example organizational unit: it common name: dl 6 email address: admin@example.Com unstructured name: wiring closet 4 success: self-signed cert for ...
Page 287
D-link dws-1008 user manual 8 installing ca-signed certificates from pkcs #12 object files this scenario shows how to use pkcs #12 object files to install public-private key pairs, ca-signed certificates, and ca certifies for administrative access, 802.1x (eap) access, and webaaa access. 1. Set time...
Page 289
D-link dws-1008 user manual 0 3. Create a csr (pkcs #10 object file) to request an administrative certificate: dws-1008# crypto generate request admin country name: us state name: ca locality name: cambria organizational name: example organizational unit: eng common name: dl-2 email address: admin@e...
Page 290
D-link dws-1008 user manual 1 10. Repeat step 3 through step 9 to obtain and install eap (802.1x) and webaaa certificates. 11. Obtain the ca’s own certificate. 12. To install the ca’s certificate on the switch and help authenticate the switch’s admin certificate, type the following command to displa...
Page 291: About Aaa For Network Users
D-link dws-1008 user manual configuring aaa for network users about aaa for network users network users include the following types of users: • wireless users—users who access the network by associating with an ssid on a d-link radio. • wired authentication users—users who access the network over an...
Page 292: Authentication Types
D-link dws-1008 user manual each authentication rule specifies where the user credentials are stored. The location can be a group of radius servers or the switch’s local database. In either case, if mss has an authentication rule that matches on the required parameters, mss checks the username or ma...
Page 293: Authentication Algorithm
D-link dws-1008 user manual authentication algorithm mss can try more than one of the authentication types described in “authentication types” to authenticate a user. Mss tries 802.1x first. If the user’s nic supports 802.1x but fails authentication, mss denies access. Otherwise, mss tries mac authe...
Page 294: User Credential Requirements
D-link dws-1008 user manual user credential requirements the user credentials that mss checks for on radius servers or in the local database differ depending on the type of authentication rule that matches on the ssid or wired access requested by the user. • for a user to be successfully authenticat...
Page 295
D-link dws-1008 user manual mss provides the following vsas, which you can assign to users configured in the local database or on a radius server: • encryption-type—specifies the type of encryption required for access by the client. Clients who attempt to use an unauthorized encryption method are re...
Page 296: Accounting
D-link dws-1008 user manual accounting mss also supports accounting. Accounting collects and sends information used for billing, auditing, and reporting—for example, user identities, connection start and stop times, the number of packets received and sent, and the number of bytes transferred. You ca...
Page 297: Aaa Tools For Network Users
D-link dws-1008 user manual 8 aaa tools for network users authentication verifies network user identity and is required before a network user is granted access to the network. A dws-1008 switch authenticates user identity by username-password matching, digital signatures and certificates, or other m...
Page 298: Aaa Rollover Process
D-link dws-1008 user manual aaa rollover process a dws-1008 switch attempts aaa methods in the order in which they are entered in the configuration: 1. The first aaa method in the list is used unless that method results in an error. If the method results in a pass or fail, the result is final and th...
Page 299
D-link dws-1008 user manual 80 2. To configure server-1 and server-2 into server-group-1, the administrator enters the following command: dws-1008# set server group server-group-1 members server-1 server-2 3. To enable peap offload plus local authentication for all users of ssid mycorp at @example. ...
Page 300: Ways A Switch Can Use Eap
D-link dws-1008 user manual 81 ways a switch can use eap network users with 802.1x support cannot access the network unless they are authenticated. You can configure a dws-1008 switch to authenticate users with eap on a group of radius servers and/or in a local user database on the switch, or to off...
Page 301: Configuring Eap Offload
D-link dws-1008 user manual 8 configuring 802.1x authentication the ieee 802.1x standard is a framework for passing eap protocols over a wired or wireless lan. Within this framework, you can use tls, peap-ttls, or eap-md5. Most eap protocols can be passed through the switch to the radius server. Som...
Page 302: Using Pass-Through
D-link dws-1008 user manual 8 using pass-through the pass-through method causes eap authentication requests to be processed entirely by remote radius servers in server groups. For example, the following command enables users at example to be processed via server group shorebirds or swampbirds: dws-1...
Page 303
D-link dws-1008 user manual 8 network administrators sometimes use machine authentication in a microsoft active directory domain to run login scripts, and to control defaults, application access and updates, and so on. Bonded auth provides an added security measure, by ensuring that a trusted user c...
Page 304: Bonded Auth Period
D-link dws-1008 user manual 8 if the domain name has more nodes (for example, nl.Mycorp.Com), use an asterisk in each node that you want to match globally. For example, to match on all machines and users in mycorp.Com, use the following userglobs: • host/*.*.Mycorp.Com (userglob for the machine auth...
Page 305
D-link dws-1008 user manual 8 bonded auth configuration example to configure bonded auth: • configure separate authentication rules for the machine and for the user(s). • set the bonded auth period. • verify the configuration changes. The following commands configure two 802.1x authentication rules ...
Page 306: Authorization By Mac Address
D-link dws-1008 user manual 8 in the following example, bob.Mycorp.Com uses bonded auth, and the bonded auth period is set to 60 seconds. Dws-1008# show dot1x config 802.1x user policy ---------------------- ‘host/bob-laptop.Mycorp.Com’ on ssid ‘mycorp’ doing passthru ‘bob.Mycorp.Com’ on ssid ‘mycor...
Page 307: Adding Mac Users and Groups
D-link dws-1008 user manual 88 adding and clearing mac users and user groups locally mac users and groups can gain network access only through the switch. They cannot create administrative connections to the switch. A mac user is created in a similar fashion to other local users except for having a ...
Page 308
D-link dws-1008 user manual 8 for example, the following command removes mac user 01:0f:03:04:05:06 from the local database: dws-1008# clear mac-user 01:0f:03:04:05:06 success: change accepted. Configuring mac authentication and authorization the set authentication mac command defines the aaa method...
Page 309
D-link dws-1008 user manual 0 changing the mac authorization password for radius when you enable mac authentication, the client does not supply a regular username or password. The mac address of the user’s device is extracted from frames received from the device. To authenticate and authorize mac us...
Page 310: How Web Portal Webaaa Works
D-link dws-1008 user manual 1 configuring web portal webaaa webaaa provides a simple and universal way to authenticate any user or device using a web browser. A common application of webaaa is to control access for guests on your network. When a user requests access to an ssid or attempts to access ...
Page 311: Display of The Login Page
D-link dws-1008 user manual 6. Mss authenticates the user by checking radius or the switch’s local database for the username and password entered by the user. If the user information is present, mss authorizes the user based on the authorization attributes set for the user. Note: mss ignores the vla...
Page 312: Dws-1008 Switch Requirements
D-link dws-1008 user manual dws-1008 switch requirements • webaaa certificate—a webaaa certificate must be installed on the switch. You can use a self-signed (signed by the switch) webaaa certificate automatically generated by mss, manually generate a self-signed one, or install one signed by a trus...
Page 313
D-link dws-1008 user manual • authorization attributes—wireless web-portal users get their authorization attributes from the ssid’s service profile. To assign wireless web-portal users to a vlan, use the set service-profile name attr vlan-name vlan-id command. Web-portal users on wired authenticatio...
Page 314: Portal Acl and User Acls
D-link dws-1008 user manual portal acl and user acls the portalacl acl, which mss creates automatically, applies only when a user’s session is in the portal state. After the user is authenticated and authorized, the acl is no longer applicable. To modify a user’s access while the user is still being...
Page 315
D-link dws-1008 user manual client web browser recommendations • use a well-known browser, such as internet explorer (windows), firefox (mozilla-based), or safari (macintosh). • if the webaaa certificate on the switch is self-signed, configure the browser to trust the signature by installing the cer...
Page 316
D-link dws-1008 user manual 2. Configure the service profile for ssid mycorp. Configuration includes the following: • set the ssid name. • change the fallthru authentication type to web-portal. • set the default vlan to mycorp-vlan (created in step 1.) mss will place web-portal users into this vlan....
Page 317
D-link dws-1008 user manual 8 4. Configure individual webaaa users. Dws-1008# set user alice password alicepword success: change accepted. Dws-1008# set user bob password bobpword success: change accepted. 5. Configure a web authentication rule for webaaa users. The following rule uses a wildcard (*...
Page 319: Using A Custom Login Page
D-link dws-1008 user manual 00 using a custom login page by default, mss serves the d-link login page for web login. To serve a custom page instead, do the following: 1. Copy and modify the d-link page, or create a new page. 2. Create a subdirectory in the user files area of the switch’s nonvolatile...
Page 320
D-link dws-1008 user manual 01 copying and modifying the web login page to copy and modify the d-link web login page: 1. Configure an unencrypted ssid on a switch. The ssid is temporary and does not need to be one you intend to use in your network. To configure the ssid, use the following commands: ...
Page 321: Custom Login Page Scenario
D-link dws-1008 user manual 0 custom login page scenario 1. Do the following on the switch: a. Create a temporary service profile and configure a temporary, clear ssid on it: dws-1008# set service-profile tempsrvc success: change accepted. Dws-1008# set service-profile tempsrvc ssid-name tempssid su...
Page 322
D-link dws-1008 user manual 0 5. Edit the login page: a. Change the page title: my corp webaaa b. Change the logo: mylogo.Gif” width=”143” height=”65” border=”0” alt=”company logo”> c. Change the greeting: welcome to mycorp’s wireless lan d. Change the warning statement if desired: warning: my corp’...
Page 323
D-link dws-1008 user manual 0 9. Use the following command to configure the ssid to use the custom page: set service-profile name web-portal-form url for the url, specify the full path; for example, mycorp-webaaa/mycorp-login.Html. If the custom login page includes gif or jpg images, their path name...
Page 324
D-link dws-1008 user manual 0 using an acl other than portalacl by default, when you set the fallthru authentication type on a service profile or wired authentication port to web-portal, mss creates an acl called portalacl. Mss uses the portalacl acl to filter web-portal user traffic while users are...
Page 325: Period
D-link dws-1008 user manual 0 configuring the web portal webaaa session timeout period when a client that has connected through web portal webaaa enters standby or hibernation mode, mss may place the client’s web portal webaaa session in the deassociated state. A web portal webaaa session can be pla...
Page 326
D-link dws-1008 user manual 0 configuring last-resort access users who are not authenticated and authorized by 802.1x methods or a mac address can gain limited access to the network as guest users. You can configure an ssid to allow anonymous guest access, by setting its fallthru authentication type...
Page 327
D-link dws-1008 user manual 08 dws-1008# show service-profile last-resort-srvcprof ssid-name: guest-wlan ssid-type: crypto beacon: yes proxy arp: no dhcp restrict: no no broadcast: no short retry limit: 5 long retry limit: 5 auth fallthru: last-resort sygate on-demand (soda): no enforce soda checks:...
Page 328
D-link dws-1008 user manual 0 configuring aaa for users of third-party aps a switch can provide network access for users associated with a third-party ap that has authenticated the users with radius. You can connect a third-party ap to a dws-1008 switch and configure the switch to provide authorizat...
Page 329: Requirements
D-link dws-1008 user manual 10 requirements third-party ap requirements • the third-party ap must be connected to the switch through a wired layer 2 link. Mss cannot provide data services if the ap and switch are in different layer 3 subnets. • the ap must be configured as the switch’s radius client...
Page 330: Radius Server Requirements
D-link dws-1008 user manual 11 radius server requirements • for 802.1x users, the usernames and passwords must be configured on the radius server. • for non-802.1x users of a tagged ssid, the special username web-portal-ssid or last- resort-ssid must be configured, where ssid is the ssid name. The f...
Page 331
D-link dws-1008 user manual 1 for the port-list of the set port type wired-auth and set radius proxy port commands, specify the switch port(s) connected to the third-party ap. For the ip-address of the set radius proxy client address command, specify the ip address of the radius client (the third-pa...
Page 332: Ssid
D-link dws-1008 user manual 1 configuring authentication for non-802.1x users of a third-party ap with tagged ssids to configure mss to authenticate non-802.1x users of a third-party ap, use the same commands as those required for 802.1x users. Additionally, when configuring the wired authentication...
Page 333
D-link dws-1008 user manual 1 attribute description valid value(s) encryption-type type of encryption required for access by the client. Clients who attempt to use an unauthorized encryption method are rejected. One of the following numbers that identifies an encryption algorithm: • 1—aes_ccm (advan...
Page 334
D-link dws-1008 user manual 1 attribute description valid value(s) service-type type of access the user is requesting. One of the following numbers: • 2—framed; for network user access • 6—administrative; for administrative access to the switch, with authorization to access the enabled (configuratio...
Page 335
D-link dws-1008 user manual 1 attribute description valid value(s) time-of-day (network access mode only) day(s) and time(s) during which the user is permitted to log into the network. After authorization, the user’s session can last until either the time-of-day range or the session-timeout duration...
Page 336
D-link dws-1008 user manual 1 attribute description valid value(s) vlan-name (network access mode only) virtual lan (vlan) assignment. Note: on some radius servers, you might need to use the standard radius attribute tunnel-pvt-group- id, instead of vlan-name. Name of a vlan that you want the user t...
Page 337
D-link dws-1008 user manual 18 assigning ssid default attributes to a service profile you can configure a service profile with a set of default aaa authorization attributes that are used when the normal aaa process or a location policy does not provide them. These authorization attributes are applie...
Page 338
D-link dws-1008 user manual 1 assigning a security acl locally to use the local database to restrict a user, a mac user, or a group of users or mac users to the permissions stored within a committed security acl, use the following commands: note: if the filter-id value returned through the authentic...
Page 339
D-link dws-1008 user manual 0 assigning a security acl on a radius server to assign a security acl name as the filter-id authorization attribute of a user or group record on a radius server, see the documentation for your radius server. Clearing a security acl from a user or group to clear a securit...
Page 340
D-link dws-1008 user manual 1 assigning and clearing encryption types locally to restrict wireless uses or groups with user profiles in the local database to particular encryption algorithms for accessing the network, use one of the following commands: set user username attr encryption-type value se...
Page 341
D-link dws-1008 user manual assigning and clearing encryption types on a radius server to assign or delete an encryption algorithm as the encryption-type authorization attribute in a user or group record on a radius server, see the documentation for your radius server. Keeping users on the same vlan...
Page 342: With A Location Policy
D-link dws-1008 user manual note. The keep-initial-vlan option does not apply to web-portal clients, instead, vlan assignment for roaming web-portal clients automatically works the same way as when keep-initial-vlan is enabled. The vlan initially assigned to a web-portal user is not changed except b...
Page 343: Setting The Location Policy
D-link dws-1008 user manual the conditions can be one or more of the following: • aaa-assigned vlan • username • dwl-8220ap access port, distributed ap number, or wired authentication port through which the user accessed the network • ssid name with which the user is associated conditions within a r...
Page 344
D-link dws-1008 user manual you must specify whether to permit or deny access, and you must identify a vlan, username, or access port to match. Use one of the following operators to specify how the rule must match the vlan or username: • eq—applies the location policy rule to all users assigned vlan...
Page 345: Location Policy
D-link dws-1008 user manual displaying and positioning location policy rules the order of location policy rules is significant. Mss checks a location policy rule that is higher in the list before those lower in the list. Rules are listed in the order in which you create them, unless you move them. T...
Page 346: Network Users
D-link dws-1008 user manual configuring accounting for wireless network users accounting records come in three types: start, stop, and update. Mss generates these records based on the configured accounting mode, either start-stop or stop-only: • when start-stop mode is configured, a start record is ...
Page 347
D-link dws-1008 user manual 8 configuring periodic accounting update records if you have configured mss to use start-stop mode, by default accounting update records are generated when a user roams from one ap to another. Optionally, mss can generate update records at specified periodic intervals. Th...
Page 348
D-link dws-1008 user manual viewing local accounting records to view local accounting records, type the following command: show accounting statistics viewing roaming accounting records during roaming, accounting is treated as a continuation of an existing session, rather than a new session. The foll...
Page 349
D-link dws-1008 user manual 0 the user terminated the session on dws-0017: dws-0017# show accounting statistics may 21 17:07:32 acct-status-type=stop acct-authentic=2 acct-multi-session-id=session-4-1106424789 user-name=administrator@example.Com acct-session-time=361 event-timestamp=1053536852 acct-...
Page 350: Order
D-link dws-1008 user manual 1 password = 082c6c64060b (encrypted) filter-id = acl-999.In filter-id = acl-999.Out mac-user 01:02:03:04:05:06 usergroup eastcoasters session-timeout = 99 avoiding aaa problems in configuration order using the wildcard “any” as the ssid name in authentication rules you c...
Page 351
D-link dws-1008 user manual using authentication and accounting rules together when you use accounting commands with authentication commands and identify users with user globs, mss might not process the commands in the order you entered them. As a result, user authentication or accounting might not ...
Page 352
D-link dws-1008 user manual configuration for a correct processing order to avoid processing errors for authentication and accounting commands that include order-sensitive user globs, enter the commands for each user glob in pairs. For example, to set accounting and authorization for 802.1x users as...
Page 353
D-link dws-1008 user manual network user configuration scenarios the following scenarios provide examples of ways in which you use aaa commands to configure access for users: general use of network user commands the following example illustrates how to configure ieee 802.1x network users for authent...
Page 354
D-link dws-1008 user manual 6. To assign mobility profile tulip to all users at example, type the following command for each example\ user: dws-1008# set user example\username attr mobility-profile tulip users at example are now restricted to ports 2 through 4 and 6, as specified in the tulip mobili...
Page 355
D-link dws-1008 user manual enabling radius pass-through authentication the following example illustrates how to enable radius pass-through authentication for all 802.1x network users: 1. Configure the radius server r1 at ip address 10.1.1.1 with the string sunny for the key. Type the following comm...
Page 356: Authentication
D-link dws-1008 user manual enabling peap-ms-chap-v2 offload the following example illustrates how to enable peap-ms-chap-v2 offload. In this example, all eap processing is offloaded from the radius server, but ms-chap-v2 authentication and authorization are done via a radius server. The ms-chap-v2 ...
Page 357
D-link dws-1008 user manual 8 4. To authenticate all 802.1x users of ssid aircorp in @eng.Example.Com via pass-through to sg1, type the following command: dws-1008# set authentication dot1x ssid aircorp *@eng.Example.Com pass-through sg1 5. Save the configuration: dws-1008 save config success: confi...
Page 358: Radius Overview
D-link dws-1008 user manual configuring communication with radius radius overview remote authentication dial-in user service (radius) is a distributed client-server system. Radius servers provide a repository for all usernames and passwords, and can manage and store large groups of users. Radius ser...
Page 359
D-link dws-1008 user manual 0 when mss sends an authentication or authorization request to a radius server, mss waits for the amount of the radius timeout for the server to respond. If the server does not respond, mss retransmits the request. Mss sends the request up to the number of retransmits con...
Page 360
D-link dws-1008 user manual 1 setting the system ip address as the source address by default, radius packets leaving the switch have the source ip address of the outbound interface on the switch. This source address can change when routing conditions change. If you have set a system ip address for t...
Page 361: Deleting Radius Servers
D-link dws-1008 user manual note: you must provide radius servers with names that are unique. To prevent confusion, d-link recommends that radius server names differ in ways other than case. For example, avoid naming two servers rs1 and rs1. You must configure radius servers into server groups befor...
Page 362: Ordering Server Groups
D-link dws-1008 user manual note: any radius servers that do not respond are marked dead (unavailable) for a period of time. The unresponsive server is skipped over, as though it did not exist, during its dead time. Once the dead time elapses, the server is again a candidate for receiving requests. ...
Page 363
D-link dws-1008 user manual 2. Enable load balancing by typing the following command: dws-1008# set server group swampbirds load-balance enable success: change accepted. The following command disables load balancing for a server group: clear server group group-name load-balance adding members to a s...
Page 364: Deleting A Server Group
D-link dws-1008 user manual deleting a server group to remove a server group, type the following command: clear server group group-name for example, to delete the server group shorebirds, type the following command: dws-1008# clear server group shorebirds success: change accepted. The members of the...
Page 365
D-link dws-1008 user manual 3. Enable load balancing for swampbirds. Type the following command: dws-1008# set server group swampbirds load-balance enable 4. Place the other radius servers in a server group called shorebirds. Type the following command: dws-1008# set server group shorebirds members ...
Page 366: Managing 802.1X
D-link dws-1008 user manual managing 802.1x certain settings for ieee 802.1x sessions on the switch are enabled by default. For best results, change the settings only if you are aware of a problem with the switch’s 802.1x performance. For settings that you can reset with a clear command, mss reverts...
Page 367
D-link dws-1008 user manual 8 the default setting is auto, which allows the switch to process 802.1x authentication normally according to the authentication configuration. Alternatively, you can set a wired authentication port or ports to either unconditionally authenticate or unconditionally reject...
Page 369
D-link dws-1008 user manual 0 wep broadcast rekeying causes the broadcast and multicast keys for wep to be rotated every wep rekey period for each radio to each connected vlan. The switch generates the new broadcast and multicast keys and pushes the keys to the clients via eapol key messages. Wep ke...
Page 370: Managing 802.1X Client
D-link dws-1008 user manual 1 setting eap retransmission attempts the following command sets the maximum number of times the switch retransmits an 802.1x- encapsulated eap request to the supplicant (client) before it times out the authentication session: set dot1x max-req number-of-retransmissions t...
Page 372
D-link dws-1008 user manual setting the 802.1x reauthentication period the following command configures the number of seconds that the switch waits before attempting reauthentication: set dot1x reauth-period seconds the default is 3600 seconds (1 hour). The range is from 60 to 1,641,600 seconds (19 ...
Page 373: Managing Other Timers
D-link dws-1008 user manual managing other timers by default, the switch waits 60 seconds before responding to a client whose authentication failed, and times out a request to a radius server or an authentication session with a client after 30 seconds. You can modify these defaults. Setting the 802....
Page 374: Viewing 802.1X Clients
D-link dws-1008 user manual setting the 802.1x timeout for a client use the following command to set the number of seconds before the switch times out an authentication session with a supplicant (client): set dot1x timeout supplicant seconds the default is 30 seconds. The range of time is from 1 to ...
Page 375: Viewing 802.1X Statistics
D-link dws-1008 user manual viewing the 802.1x configuration type the following command to display the 802.1x configuration: dws-1008# show dot1x config 802.1x user policy ------------------------- ‘example\pc1’ on ssid ‘mycorp’ doing eap-peap (eap-mschapv2) ‘example\bob’ on ssid ‘mycorp’ doing eap-...
Page 376: About Soda Endpoint Security
D-link dws-1008 user manual configuring soda endpoint security sygate on-demand (soda) is an endpoint security solution that allows enterprises to enforce security policies on client devices without having to install any special software on the client machines. Mss can be configured to run soda secu...
Page 377: How Soda Functionality Works
D-link dws-1008 user manual 8 • connection control – controls network connections based on domain, ip address, port, and service. For example, connection control can prevent a trojan from sending out a confidential document, downloaded legitimately through an ssl vpn tunnel, to a malicious e-mail se...
Page 378
D-link dws-1008 user manual soda functionality on a switch is configured as follows: 1. Using soda manager, a network administrator creates a soda agent based on the security needs of the network. 2. The network administrator exports the soda agent files from soda manager, and saves them as a .Zip f...
Page 379
D-link dws-1008 user manual 0 7. At the completion of his or her session, the user can close the soda virtual desktop or point to an advertised logout url. Either of these actions cause a customizable logout page to be loaded in the browser window. Accessing the logout page causes the user to be dis...
Page 380
D-link dws-1008 user manual 1 configuring web portal webaaa for the service profile in the current release, soda functionality works in conjunction with the web portal aaa feature. Consequently, web portal aaa must be enabled for the service profile for which you want to configure soda functionality...
Page 381
D-link dws-1008 user manual • the hostname of the logout page should be set to a name that resolves to the switch’s ip address on the vlan where the client resides, or should be the ip address of the switch on the web portal webaaa vlan; for example: https://10.1.1.1/logout.Html the logout page shou...
Page 383
D-link dws-1008 user manual specifying a soda agent success page when a client successfully runs the checks performed by the soda agent, by default a dynamically generated page is displayed on the client indicating that the checks succeeded. You can optionally create a custom success page that is di...
Page 384: Specifying A Remediation Acl
D-link dws-1008 user manual the page refers to a file on the switch. After this page is loaded, the specified remediation acl takes effect, or if there is no remediation acl configured, then the client is disconnected from the network. For example, the following command specifies failure.Html, which...
Page 385
D-link dws-1008 user manual specifying a soda agent logout page when a client closes the soda virtual desktop, the client is automatically disconnected from the network. You can optionally specify a page that is loaded when the client logs out of the network. To do this, use the following command: s...
Page 386
D-link dws-1008 user manual to reset the soda agent directory to the default value, use the following command: clear service-profile name soda agent-directory if the same soda agent is used for multiple service profiles, you can specify a single directory for soda agent files on the switch, rather t...
Page 387
D-link dws-1008 user manual 8 the following is an example of the output of the show service profile command for service profile sp1. In the example, the fields related to soda functionality are highlighted in bold. Dws-1008# show service-profile sp1 ssid-name: corp2 ssid-type: crypto beacon: yes pro...
Page 388: Managing Sessions
D-link dws-1008 user manual managing sessions about the session manager a session is a related set of communication transactions between an authenticated user (client) and the specific station to which the client is bound. Packets are exchanged during a session. A dws-1008 switch supports the follow...
Page 389: Session
D-link dws-1008 user manual 0 displaying and clearing an administrative console session to view information about the user with administrative access to the switch through a console plugged into the switch, type the following command: dws-1008# show sessions console tty username time(s) type -------...
Page 390: Sessions
D-link dws-1008 user manual 1 you can clear all telnet client sessions or a particular session. For example, the following command clears telnet client session 1: dws-1008# clear sessions telnet client 1 displaying and clearing network sessions use the following command to display information about ...
Page 391: Username
D-link dws-1008 user manual displaying verbose network session information in the show sessions network commands, you can specify verbose to get more in-depth information. For example, to display detailed information for all network sessions, type the following command: dws-1008# show sessions netwo...
Page 392
D-link dws-1008 user manual for example, the following command shows all sessions of users whose names begin with e: dws-1008# show sessions network user e* user sess ip or mac vlan port/ name id address name radio -------------------------------------------------------------------------------------...
Page 393: Address
D-link dws-1008 user manual displaying and clearing network sessions by mac address you can view sessions by mac address or mac address glob. To view session information for a mac address or set of mac addresses, type the following command: show sessions network mac-addr mac-addr-glob for example, t...
Page 394
D-link dws-1008 user manual for example, the following command clears the sessions of all users on vlan red: dws-1008# clear sessions network vlan red displaying and clearing network sessions by session id you can display information about a session by session id. To find local session ids, enter th...
Page 395: Disabling Keepalive Probes
D-link dws-1008 user manual to clear network sessions by session id, type the following command with the appropriate local session id number. Clear sessions network session-id session-id for example, the following command deletes network session 9: dws-1008# clear sessions network session-id 9 sm ap...
Page 396: Rogue Classification
D-link dws-1008 user manual rogue detection and countermeasures ap radios automatically scan the rf spectrum for other devices transmitting in the same spectrum. The rf scans discover third-party transmitters in addition to other d-link radios. Mss considers the non-d-link transmitters to be devices...
Page 397: Rogue Detection Lists
D-link dws-1008 user manual 8 in addition, you can optionally configure mss to issue on-demand countermeasures. On-demand countermeasures are those launched against devices that you have manually specified in the switch’s attack list. When you enable on-demand countermeasures, mss issues them only a...
Page 398: Rf Detection Scans
D-link dws-1008 user manual rf detection scans all radios continually scan for other rf transmitters. Radios perform passive scans and active scans: • passive scans—the radio listens for beacons and probe responses. • active scans—the radio sends probe any requests (probe requests with a null ssid n...
Page 399: Countermeasures
D-link dws-1008 user manual 80 countermeasures you can enable mss to use countermeasures against rogues. Countermeasures consist of packets that interfere with a client’s ability to use the rogue. Countermeasures are disabled by default. You can enable them on an individual radio-profile basis. When...
Page 400
D-link dws-1008 user manual 81 configuring rogue detection lists the following sections describe how to configure lists to specify the devices that are allowed on the network and the devices that mss should attack with countermeasures. Configuring a permitted vendor list the permitted vendor list sp...
Page 401
D-link dws-1008 user manual 8 configuring a permitted ssid list the permitted ssid list specifies the ssids that are allowed on the network. If mss detects packets for an ssid that is not on the list, the ap that sent the packets is classified as a rogue. Mss issues countermeasures against the rogue...
Page 402
D-link dws-1008 user manual 8 configuring a client black list the client black list specifies clients that are not allowed on the network. Mss drops all packets from the clients on the black list. By default, the client black list is empty. In addition to manually configured entries, the list can co...
Page 403: Configuring An Attack List
D-link dws-1008 user manual 8 configuring an attack list the attack list specifies the mac addresses of devices that mss should issue countermeasures against whenever the devices are detected on the network. The attack list can contain the mac addresses of aps and clients. By default, the attack lis...
Page 404: Configuring An Ignore List
D-link dws-1008 user manual 8 configuring an ignore list by default, when countermeasures are enabled, mss considers any non-d-link transmitter to be a rogue device and can send countermeasures to prevent clients from using that device. To prevent mss from sending countermeasures against a friendly ...
Page 405: Enabling Countermeasures
D-link dws-1008 user manual 8 enabling countermeasures caution: countermeasures affect wireless service on a radio. When an ap radio is sending countermeasures, the radio is disabled for use by network traffic, until the radio finishes sending the countermeasures. Countermeasures are disabled by def...
Page 406: Enabling Ap Signatures
D-link dws-1008 user manual 8 disabling or reenabling active scan when active scanning is enabled, the ap radios managed by the switch look for rogue devices by sending probe any frames (probes with a null ssid name), to solicit probe responses from other aps. Active scan is enabled by default. You ...
Page 407: Notifications
D-link dws-1008 user manual 88 enabling rogue and countermeasures notifications by default, all snmp notifications (informs or traps) are disabled. To enable or disable notifications for rogue detection, intrusion detection system (ids), and denial of service (dos) protection, configure a notificati...
Page 408: Wireless Bridge
D-link dws-1008 user manual 8 • broadcast deauthenticate frames—similar to the spoofed deauthenticate frame attack above, a broadcast deauthenticate frame attack generates spoofed deauthenticate frames, with a broadcast destination address instead of the address of a specific client. The intent of t...
Page 409: Ad-Hoc Network
D-link dws-1008 user manual 0 ad-hoc network an ad-hoc network is established directly among wireless clients and does not use the infrastructure network (a network using an ap). An ad-hoc network might not be an intentionally malicious attack on the network, but it does steal bandwidth from your in...
Page 410
D-link dws-1008 user manual 1 message type example log message null data message flood client aa:bb:cc:dd:ee:ff is sending null data message flood. Seen by ap on port 2, radio 1 on channel 11 with rssi -53. Management frame 6 flood client aa:bb:cc:dd:ee:ff is sending rsvd mgmt frame 6 message flood....
Page 411
D-link dws-1008 user manual message type example log message wireless bridge detected wireless bridge detected with address aa:bb:cc:dd:ee:ff. Seen by ap on port 2, radio 1 on channel 11 with rssi -53 ssid myssid. Netstumbler detected netstumbler detected from aa:bb:cc:dd:ee:ff. Seen by ap on port 2...
Page 412: Displaying Rogue Clients
D-link dws-1008 user manual command description show rfdetect vendor-list displays the list of ouis that are allowed on the network. An oui identifies a piece of networking equipment’s vendor. Show rfdetect ssid-list displays the list of ssids that are allowed on the network. Show rfdetect black-lis...
Page 413
D-link dws-1008 user manual displaying rogue detection counters to display rogue detection statistics counters, use the following command: show rfdetect counters the command shows counters for rogue activity detected by the switch on which you enter the command. Dws-1008# show rfdetect counters type...
Page 414: Displaying Rf Detect Data
D-link dws-1008 user manual displaying rf detect data to display information about the aps detected by an individual switch, use the following command: show rfdetect data you can enter this command on any dws-1008 switch in your network. Dws-1008# show rfdetect data total number of entries: 197 flag...
Page 415
D-link dws-1008 user manual displaying countermeasures information to display the current status of countermeasures against rogues in the network, use the following command: show rfdetect countermeasures this command is valid only on the network’s seed switch. Dws-1008# show rfdetect countermeasures...
Page 416: Managing System Files
D-link dws-1008 user manual managing system files a dws-1008 switch contains nonvolatile storage. Mss allows you to manage the files in nonvolatile storage. In addition, you can copy files between the switch and a tftp server on the network. About system files generally, a switch’s nonvolatile stora...
Page 417: Displaying Boot Information
D-link dws-1008 user manual 8 to also display access point information, type the following command: dws-1008# show version details mobility system software, version: 4.1.0 qa 67 copyright (c) 2002, 2003, 2004, 2005 d-link, inc. All rights reserved. Build information: (build#67) top 2005-07-21 04:41:...
Page 418: Working With Files
D-link dws-1008 user manual in this example, the switch is running software version 4.1.0.65. The switch used the 040100.020 image file in boot partition boot1 and the configuration configuration file for the most recent reboot. The switch is set to use image file 040100.020 in boot partition boot1 ...
Page 419
D-link dws-1008 user manual 00 to display a list of the files in nonvolatile storage and temporary files, type the following command: dws-1008# dir ================================================================== file: filename size created file:configuration 48 kb jul 12 2005, 15:02:32 file:corp2...
Page 420
D-link dws-1008 user manual 01 the following command limits the output to the contents of the user files area: dws-1008# dir file: ================================================================== file: filename size created file:configuration 48 kb jul 12 2005, 15:02:32 file:corp2:corp2cnfig 17 kb...
Page 421: Copying A File
D-link dws-1008 user manual 0 copying a file you can perform the following copy operations: • copy a file from a tftp server to nonvolatile storage. • copy a file from nonvolatile storage or temporary storage to a tftp server. • copy a file from one area in nonvolatile storage to another. • copy a f...
Page 422
D-link dws-1008 user manual 0 to copy the file floor2mx from nonvolatile storage to a tftp server, type the following command: dws-1008# copy floor2mx tftp://10.1.1.1/floor2mx success: sent 365 bytes in 0.401 seconds [ 910 bytes/sec] the above command copies the file to the same filename on the tftp...
Page 424: Deleting A File
D-link dws-1008 user manual 0 deleting a file caution: mss does not prompt you to verify whether you want to delete a file. When you press enter after typing a delete command, mss immediately deletes the specified file. D-link recommends that you copy a file to a tftp server before deleting the file...
Page 425: Removing A Subdirectory
D-link dws-1008 user manual 0 boot: filename size created *boot0:bload 746 kb may 09 2004, 19:02:16 *boot0:mx030000.020 8182 kb may 09 2004, 18:58:16 boot1:mx030000.020 8197 kb may 21 2004, 18:01:02 boot0: total: 8928 kbytes used, 3312 kbytes free boot1: total: 8197 kbytes used, 4060 kbytes free ===...
Page 426
D-link dws-1008 user manual 0 to display the running configuration, type the following command: dws-1008# show config # configuration nvgen’d at 2004-5-10 19:08:38 # image 2.1.0 # model dws-1008 # last change occurred at 2004-5-10 16:31:14 set trace authentication level 10 set ip dns server 10.10.10...
Page 427: Saving Configuration Changes
D-link dws-1008 user manual 08 saving configuration changes to save the running configuration to a configuration file, use the following command: save config [filename] if you do not specify a filename of up to 128 alphanumeric characters, the command replaces the startup configuration file that was...
Page 428: Loading A Configuration File
D-link dws-1008 user manual 0 loading a configuration file caution: this command completely removes the running configuration and replaces it with the configuration contained in the file. D-link recommends that you save a copy of the current running configuration to a backup configuration file befor...
Page 429
D-link dws-1008 user manual 10 to display the name of the file specified as the backup configuration file, enter the show boot command. For example: pubs# show boot configured boot version: 4.1.0.60 configured boot image: boot0:mx040100.020 configured boot configuration: file:configuration backup bo...
Page 431: Backup and Restore Examples
D-link dws-1008 user manual 1 managing configuration changes the backup command places the boot configuration file into the archive. (the boot configuration file is the configured boot configuration in the show boot command’s output.) if the running configuration contains changes that have not been ...
Page 432: Upgrading The System Image
D-link dws-1008 user manual 1 upgrading the system image to upgrade the switch from one mss version to another, use the procedure in this section. For a given release, there may be notes and cautions that apply only to that release. Consequently, before upgrading to a new software image, you should ...
Page 433
D-link dws-1008 user manual 1 when you restart the dws-1008 switch, the switch boots using the new mss image. The switch also sends the ap version of the new boot image to aps and restarts the aps. After an ap restarts, it checks the version of the new ap boot image to make sure the boot image is ne...
Page 434: Troubleshooting
D-link dws-1008 user manual 1 troubleshooting some common problems that occur during switch installation and basic configuration are simple to solve. However, to “recover” the system password, you must delete the existing switch configuration. System logs provide a history of mss events. Traces disp...
Page 435: Password Is Lost
D-link dws-1008 user manual 1 symptom diagnosis remedy client cannot access the network. This symptom has more than one possible cause: • the client might be failing authentication or might not be authorized for a vlan. 1. Type the show aaa command to ensure that the authentication rules on the swit...
Page 436: Log Message Components
D-link dws-1008 user manual 1 configuring and managing the system log system logs provide information about system events that you can use to monitor and troubleshoot mss. Event messages for the switch and its attached access points can be stored or sent to the following destinations: • stored in a ...
Page 437
D-link dws-1008 user manual 18 destination definition default operation and severity level buffer sends log information to the nonvolatile system buffer. Buffer is enabled and shows error-level events. Console sends log information to the console. Console is enabled and shows error-level events. Cur...
Page 440: Logging to The Console
D-link dws-1008 user manual 1 logging to the console by default, console logging is enabled and messages at the error level and higher are sent to the console. To modify console logging, use the following command: set log console severity severity-level for example, to set logging to the console for...
Page 441
D-link dws-1008 user manual for example, the following command sends all error-level event messages generated by a dws-1008 switch to a server at ip address 192.168.153.09 and identifies them as facility 5 messages: dws-1008# set log server 192.168.153.09 severity error local-facility 5 success: cha...
Page 442: Logging to The Trace Buffer
D-link dws-1008 user manual logging to the trace buffer trace logging is enabled by default and stores debug-level output in the switch trace buffer. To modify trace logging to an event level higher than debug, use the following command: set log trace severity severity-level to disable trace logging...
Page 443: Running Traces
D-link dws-1008 user manual displaying the log configuration to display your current log configuration, type the following command: dws-1008# show log config logging console: enabled logging console severity: info logging sessions: enabled logging sessions severity: info logging buffer: enabled logg...
Page 444: Tracing 802.1X Sessions
D-link dws-1008 user manual tracing authentication activity tracing authentication activity can help you diagnose authentication problems. You can trace all authentication activity, or only the activity for a specific user, mac address, or port. For example, to trace all authentication activity at l...
Page 445: Displaying A Trace
D-link dws-1008 user manual displaying a trace use the show trace command to show the trace areas that are enabled. For example, to display all currently running trace commands, type the following command: dws-1008# show trace milliseconds spent printing traces: 31.945 trace area level mac user port...
Page 447: Clearing The Trace Log
D-link dws-1008 user manual 8 clearing the trace log to clear all messages from the trace log buffer, type the following command: dws-1008# clear log trace list of trace areas to see all mss areas you can trace, type the following command: dws-1008# set trace ? Using show commands to troubleshoot th...
Page 448
D-link dws-1008 user manual viewing aaa session statistics to view aaa session statistics, type the following command: dws-1008# show aaa default values authport=1812 acctport=1813 timeout=5 acct-timeout=5 retrans=3 deadtime=5 key=(null) author-pass=(null) radius servers server addr ports t/o tries ...
Page 449: Viewing Fdb Information
D-link dws-1008 user manual 0 viewing fdb information the show fdb command displays the hosts learned by the switch and the ports to which they are connected. To display forwarding database (fdb) information, type the following command: dws-1008# show fdb * = static entry. + = permanent entry. # = s...
Page 450: Configuration Requirements
D-link dws-1008 user manual 1 configuration requirements • the switch can have one port mirroring pair (one source port and one observer port) at a time. • the source port can be a network port, ap access port, or wired authentication port. • the observer port must be a network port, and cannot be a...
Page 451
D-link dws-1008 user manual how remote traffic monitoring works to monitor wireless traffic, an ap radio compares traffic sent or received on the radio to snoop filters applied to the radio by the network administrator. When an 802.11 packet matches all conditions in a filter, the ap encapsulates th...
Page 452: Configuring A Snoop Filter
D-link dws-1008 user manual best practices for remote traffic monitoring • do not specify an observer that is associated with the ap where the snoop filter is running. This configuration causes an endless cycle of snoop traffic. • if the snoop filter is running on a distributed ap, and the ap used a...
Page 453
D-link dws-1008 user manual the condition-list specifies the match criteria for packets. Conditions in the list are anded. Therefore, to be copied and sent to an observer, a packet must match all criteria in the condition-list. You can specify up to eight of the following conditions in a filter, in ...
Page 454: Editing A Snoop Filter
D-link dws-1008 user manual displaying configured snoop filters to display the snoop filters configured on the switch, use the following command: show snoop info [filter-name] the following command shows the snoop filters configured in the examples above: dws-1008# show snoop info snoop1: observer 1...
Page 455
D-link dws-1008 user manual displaying the snoop filters mapped to a radio to display the snoop filters that are mapped to a radio, use the following command: show snoop map filter-name the following command shows the mapping for snoop filter snoop1: dw-1008# show snoop map snoop1 filter ‘snoop1’ ma...
Page 457
D-link dws-1008 user manual 8 preparing an observer and capturing traffic to observe monitored traffic, install the following applications on the observer: • ethereal or tethereal version 0.10.8 or later • netcat (any version), if not already installed ethereal and tethereal decode 802.11 packets em...
Page 458
D-link dws-1008 user manual 5. Disable the option to decrypt 802.11 payloads. Because the ap always decrypts the data before sending it to the observer, the observer does not need to perform any decryption. In fact, if you leave decryption enabled on the observer, the payload data becomes unreadable...
Page 459: Core Files
D-link dws-1008 user manual 0 the show tech-support command the show tech-support command combines a group of show commands to provide an in-depth snapshot of the status of the switch. The output displays details about the system image and configuration used after the last reboot, the version, ports...
Page 460: Debug Messages
D-link dws-1008 user manual 1 in this example, the core file is netsys.Core.217.Tar. (the command_audit.Cur file is not a core file and is created as part of normal system operation.) the following command copies the core file onto a tftp server. Dws-1008# copy core:netsys.Core.217.Tar tftp://192.16...
Page 461: System Requirements
D-link dws-1008 user manual enabling and logging into web view web view is a web-based management application available on dws-1008 switches. You can use web view for common configuration and management tasks. System requirements browser requirements web view is supported on the following browsers: ...
Page 462: Logging Into Web View
D-link dws-1008 user manual logging into web view 1. Type https://ip-addr in the web browser’s address or location field and press enter. For ip-addr, type an ip address you configured on the switch. 2. If your browser displays a certificate warning, select an option to accept the certificate. The c...
Page 463: Supported Radius Attributes
D-link dws-1008 user manual supported radius attributes d-link mobility system software (mss) supports the standard and extended radius authentication and accounting attributes. An attribute is sent to radius accounting only if the table listing it shows yes or optional in the column marked sent in ...
Page 464
D-link dws-1008 user manual attribute type rcv in access resp? Sent in access reqst? Sent in acct reqst? Description and values service-type 5 no yes yes access type, which can be one of the following: • 2—framed; for network user access • 6—administrative; for administrative access to the dws-1008 ...
Page 465
D-link dws-1008 user manual attribute type rcv in access resp? Sent in access reqst? Sent in acct reqst? Description and values called-station-id 30 no yes yes for ieee 802.1x authenticators, stores the access point mac address in uppercase ascii format, with octet values separated by hyphens (for e...
Page 466
D-link dws-1008 user manual attribute type rcv in access resp? Sent in access reqst? Sent in acct reqst? Description and values acct-multi-session- id 50 no no yes unique accounting id that facilitates linking together multiple related sessions in a log file. Each linked session has a unique acct- s...
Page 467: Traffic Ports Used By Mss
D-link dws-1008 user manual 8 traffic ports used by mss when deploying a d-link wireless network, you might attach d-link equipment to subnets that have firewalls or access controls between them. Trapeze equipment uses various protocol ports to exchange information. To ensure full operation of your ...
Page 468: Dhcp Server
D-link dws-1008 user manual dhcp server mss has a dhcp server that the switch uses to allocate ip addresses to the following: • directly connected dwl-8220aps • host connected to a new (unconfigured) dws-1008, to configure the switch using the web quick start dhcp service for these items is enabled ...
Page 469
D-link dws-1008 user manual 0 how the mss dhcp server works when mss receives a dhcp discover packet, the dhcp server allocates an address from the configured range according to rfc 2131 and arps the address to ensure that it is not already in use. If the address is in use, the server allocates the ...
Page 471
D-link dws-1008 user manual displaying dhcp server information to display information about the mss dhcp server, use the following command: show dhcp-server [interface vlan-id] [verbose] if you enter the command without the interface or verbose option, the command displays a table of all the ip addr...
Page 472: Glossary
D-link dws-1008 user manual glossary 3des - a three-round application of the data encryption standard (des) that uses a 168-bit encryption key. See also des. 802.1d - the ieee lan specification for the operation of media access control (mac) bridges. 802.1p - an ieee lan standard method for classify...
Page 473
D-link dws-1008 user manual 802.11b/g radio - a radio that can receive and transmit signals at ieee 802.11b and 802.11g data rates. Trapeze 802.11b/g radios allow associations from 802.11b clients as well as 802.11g clients by default, for networks that have a mixture of both client types. However, ...
Page 474
D-link dws-1008 user manual association - the process defined in ieee 802.11 by which an authenticated mobile (wireless) station establishes a relationship with a wireless access point (ap) to gain full network access. The access point assigns the mobile station an association identifier (aid), whic...
Page 475
D-link dws-1008 user manual cbc-mac see ccmp. Cci - co-channel interference. Obstruction that occurs when one signal on a particular frequency intrudes into a cell that is using that same frequency for transmission. In multicell networks, systems are designed to minimize cci through appropriate tran...
Page 476
D-link dws-1008 user manual cpc - communications plenum cable see plenum-rated cable. Crc - cyclic redundancy check. A primitive message integrity check. Crypto - see cryptography. Cryptography - the science of information security. Modern cryptography is typically concerned with the processes of sc...
Page 477
D-link dws-1008 user manual 8 diffie-hellman - a key exchange algorithm that was the first public-key algorithm ever published. Diffie- hellman can be used anonymously (without authentication). Diffserv - differentiated services. An architecture for providing different types or levels of service for...
Page 478
D-link dws-1008 user manual dual-homed connection - a redundant, resilient connection between a dwl-8220ap access point and one or more dws-1008 switches. The connection can consist of two direct physical links from both ap ports to one or two dws-1008 switches, one or more distributed links through...
Page 479
D-link dws-1008 user manual 0 encryption - any procedure used in cryptography to translate data into a form that can be read by only its intended receiver. An encrypted signal must be decrypted to be read. See also cryptography. Ess - extended service set. A logical connection of multiple basic serv...
Page 480
D-link dws-1008 user manual 1 frequency-hopping spread-spectrum - see fhss. Gbic - gigabit interface converter. A hot-swappable input/output device that plugs into a gigabit ethernet port, to link the port with a fiber-optic or copper network. The data transfer rate is 1 gigabit per second (gbps) or...
Page 481
D-link dws-1008 user manual homologation - the process of certifying a product or specification to verify that it meets regulatory standards. Hpov - hewlett-packard open view. The umbrella network management system (nms) family of products from hewlett-packard. Https - hypertext transfer protocol ov...
Page 482
D-link dws-1008 user manual initialization vector (iv) - in encryption, random data used to make a message unique. Institute of electrical and electronic engineers - see ieee. Integrity check value - see icv. Interface - a place at which independent systems meet and act on or communicate with each o...
Page 483
D-link dws-1008 user manual location policy rule - a rule in the location policy on a dws-1008 switch that grants or denies a set of network access rights based on one or more criteria. Location policy rules use a username or vlan membership to determine whether to override—or supply—authorization a...
Page 484
D-link dws-1008 user manual minimum data transmit rate - the lowest rate at which a dwl-8220ap access point can transmit data to its associated mobile clients. If the data rate to a client drops below the minimum, the ap increases power, if rf auto-tuning is enabled. Mobility system software™ (mss™)...
Page 485
D-link dws-1008 user manual pairwise transient key - see ptk. Pat - port address translation. A type of network address translation (nat) in which each computer on a lan is assigned the same ip address, but a different port number. See also nat. Peap - protected extensible authentication protocol. A...
Page 486
D-link dws-1008 user manual plenum - a compartment or chamber to which one or more air ducts are connected. Plenum-rated cable - a type of cable approved by an independent test laboratory for installation in ducts, plenums, and other air-handling spaces. Pmk - pairwise master key. A code derived fro...
Page 487
D-link dws-1008 user manual 8 psk - preshared key. The ieee 802.11 term for a shared secret, also known as a shared key. See shared secret. Ptk - pairwise transient key. A value derived from a pairwise master key (pmk) and split into multiple encryption keys and message integrity code (mic) keys for...
Page 488
D-link dws-1008 user manual registration authority (ra) - network software that verifies a user (client) request for a digital certificate and instructs the certificate authority (ca) to issue the certificate. Registration authorities are part of a public-key infrastructure (pki), which enables secu...
Page 489
D-link dws-1008 user manual 0 security acl - security access control list. An ordered list of rules to control access to and from a network by determining whether to forward or filter packets that are entering or exiting it. Associating a security acl with a particular user, port, virtual lan (vlan)...
Page 490
D-link dws-1008 user manual 1 station - any device with a media access control (mac) address and a physical layer (phy) interface to the wireless medium that comply with the standards for all ieee 802 networks. Wireless clients and dwl-8220ap access points are stations in a d-link mobility system. S...
Page 491
D-link dws-1008 user manual unlicensed national information infrastructure - see u-nii. User - a person who uses a client. In a d-link mobility system, users are indexed by username and associated with authorization attributes such as user group membership. User glob - a d-link convention for matchi...
Page 492
D-link dws-1008 user manual wep - wired-equivalent privacy protocol. A security protocol, specified in the ieee 802.11 standard, that attempts to provide a wireless lan (wlan) with a minimal level of security and privacy comparable to a typical wired lan. Wep encrypts data transmitted over the wlan ...
Page 493
D-link dws-1008 user manual wpa ie - a set of extra fields in a wireless frame that contain wi-fi protected access (wpa) information for the access point or client. For example, a dwl-8220ap access point uses the wpa ie in a beacon frame to advertise the cipher suites and authentication methods that...
Page 494: Technical Specifications
D-link dws-1008 user manual technical specifications hardware specifications physical and environmental • dimensions (w x d x h): 17.4 x 8.2 x 1.72 in (44.2 x 20.8 x 4.4 cm) • weight: 5.2lbs (3kg) • operating temperature: 0ºc to 40ºc (32ºf to 104ºf) • storage temperature: -20ºc to 70ºc (-4ºf to 158º...
Page 495
D-link dws-1008 user manual emi / emc • fcc part 15 • ices part 15 • vcci • en 55022 • en 55024 • en 60101-1-2 (1993) • cispr 22 software specifications ieee • ieee std 802.1x-2001 - port-based network access control • ieee std 802.11i- enhanced security for 802.11 wireless networks based on aes • i...
Page 496
D-link dws-1008 user manual general • rfc 1122 host requirements • rfc 1393 traceroute • rfc 1519 cidr • rfc 1591 dns (client) • rfc 1769 sntp • rfc 768 udp • rfc 783 tftp • rfc 791 ip • rfc 792 icmp • rfc 793 tcp • rfc 826 arp • ieee 802.1d spanning tree • ieee 802.1q vlan tagging • ieee 802.3ad (s...
Page 497: Warranty
D-link dws-1008 user manual 8 warranty subject to the terms and conditions set forth herein, d-link systems, inc. (“d-link”) provides this limited warranty for its product only to the person or entity that originally purchased the product from: • d-link or its authorized reseller or distributor and ...
Page 498
D-link dws-1008 user manual except as otherwise agreed by d-link in writing, the replacement software is provided only to the original licensee, and is subject to the terms and conditions of the license granted by d-link for the software. Software will be warranted for the remainder of the original ...
Page 499
D-link dws-1008 user manual 80 d-link may reject or return any product that is not packaged and shipped in strict compliance with the foregoing requirements, or for which an rma number is not visible from the outside of the package. The product owner agrees to pay d-link’s reasonable handling and re...
Page 500
D-link dws-1008 user manual 81 governing law: this limited warranty shall be governed by the laws of the state of california. Some states do not allow exclusion or limitation of incidental or consequential damages, or limitations on how long an implied warranty lasts, so the foregoing limitations an...
Page 501
D-link dws-1008 user manual 8 fcc caution: the manufacturer is not responsible for any radio or tv interference caused by unauthorized modifications to this equipment; such modifications could void the user’s authority to operate the equipment. (1) the devices are restricted to indoor operations wit...
Page 502: Registration
D-link dws-1008 user manual 8 registration version 2.0 december 8, 2006 product registration is entirely voluntary and failure to complete or return this form will not diminish your warranty rights..