- DL manuals
- H3C
- Switch
- S5120-SI Series
- Configuration Manual
H3C S5120-SI Series Configuration Manual
Summary of S5120-SI Series
Page 1
H3c s5120-si series ethernet switches configuration guide hangzhou h3c technologies co., ltd. Http://www.H3c.Com manual version: 6w105-20110810 product version: release 1101.
Page 2
Copyright © 2009-2011, hangzhou h3c technologies co., ltd. And its licensors all rights reserved no part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of hangzhou h3c technologies co., ltd. Trademarks h3c, , aolynk, , h 3 care, , top g, , i...
Page 3: Preface
2-1 preface the h3c s5120-si series ethernet switches configuration guide, release 1101 describes the fundamentals and configuration of software features available in the software release 1101 for the h3c s5120-si series, and guides you through the software configuration procedures. This preface inc...
Page 4: About This Document
2-1 1 about this document audience this documentation is intended for: z network planners z field technical support and servicing engineers z network administrators working with the s5120-si series organization the h3c s5120-si series ethernet switches configuration guide, release 1101 comprises the...
Page 5
2-2 chapter content 05-ethernet link aggregation z overview z configuring an aggregation group z configuring an aggregate interface 06-port isolation z introduction to port isolation z configuring an isolation group 07-port mirroring z configuring local port mirroring 08-lldp z introduction to lldp ...
Page 6
2-3 chapter content 19-qos z configuring qos policy z configuring priority mapping z configuring line rate z configuring sp, wrr, and sp+wrr queuing z configuring traffic filtering z configuring traffic redirecting 20-802.1x z 802.1x basic configuration z 802.1x extended configuration z 802.1x guest...
Page 7
2-4 chapter content 32-file system management z file system management z configuration file management 33-system maintaining and debugging z maintenance and debugging overview z maintenance and debugging configuration 34-basic system configuration z configuration display z configuring the device nam...
Page 8: Conventions
2-5 conventions this section describes the conventions used in this documentation set. Command conventions convention description boldface bold text represents commands and keywords that you enter literally as shown. Italic italic text represents arguments that you replace with actual values. [ ] sq...
Page 9: Documentation Guide
2-1 2 documentation guide related documentation the h3c s5120-si documentation set also includes: category documents purposes product description and specifications marketing brochures describe product specifications and benefits. Compliance and safety manual provides regulatory information and the ...
Page 10: Technical Support
2-2 z [technical support & documents > software download] – provides the documentation released with the software version. Technical support customer_service@h3c.Com http://www.H3c.Com documentation feedback you can e-mail your comments about product documentation to info@h3c.Com. We appreciate your...
Page 11: Product Features
3-1 3 product features introduction to product the h3c s5120-si series ethernet switches are intelligent, manageable, layer 2 gigabit ethernet switches designed for the access and distribution layers of enterprise networks. The series delivers high performance, high port density, and ease of install...
Page 12
3-2 distribution layer switches deploy the s5120-si series at the distribution layer of a medium- and large-sized enterprise or campus network to provide high-performance and large-capacity switching service. Figure 3-1 an enterprise network access switches the s5120-si series can serve as access sw...
Page 13
3-3 figure 3-2 an enterprise network s9500/s7500e s5120-si access core/aggregation s5120-si.
Page 14: Table of Contents
1 table of contents 1 cli configuration ······································································································································1-1 what is cli? ·············································································································...
Page 15: Cli Configuration
1-1 1 cli configuration this chapter includes these sections: z what is cli? Z entering the cli z h3c products cli descriptions z tips on using the cli what is cli? The command line interface (cli) is an interface where you can interact with your device by typing text commands. At the cli, you can i...
Page 16
1-2 z through telnet. For more information, see entering cli through telnet . Z through ssh with encryption. For more information, see ssh2.0 configuration. Entering cli through the console port when you use the cli of an h3c switch for the first time, you can log in to the switch and enter the cli ...
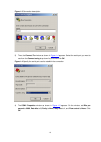
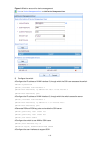
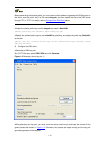
Page 17
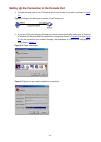
1-3 figure 1-3 connection description 3) then, the connect to window as shown in figure 1-4 appears. Select the serial port you want to use from the connect using drop-down list, and then click ok. Figure 1-4 specify the serial port used to establish the connection 4) the com1 properties window as s...
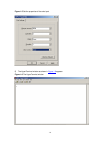
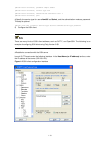
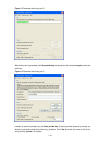
Page 18
1-4 figure 1-5 set the properties of the serial port 5) the hyperterminal window as shown in figure 1-6 appears. Figure 1-6 the hyperterminal window.
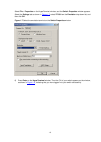
Page 19
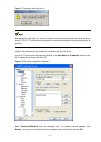
1-5 select file > properties on the hyperterminal window, and the switch properties window appears. Select the settings tab as shown in figure 1-7 , select vt100 from the emulation drop-down list, and then click ok. Figure 1-7 select the emulation terminal on the switch properties window 6) press en...
Page 20
1-6 figure 1-8 schematic diagram for successful login through the console port entering cli through telnet after you log in to your switch through the console port for the first time, it is recommended that you configure telnet login as soon as possible, so that you can use a remote terminal to conf...
Page 21
1-7 an h3c switch provides multiple vty user interfaces. At one time, only one user can telnet to a vty user interface. Because a remote terminal cannot select the vty user interface through which it logs in to the switch, it is recommended that you configure all vty user interfaces with the same au...
Page 22
1-8 table 1-2 command conventions convention description boldface the keywords of a command line are in boldface. Keep keywords unchanged when typing them in the cli. Italic command arguments are in italic. Replace arguments with actual values in the cli. [ ] items (keywords or arguments) in square ...
Page 23
1-9 entering system view after logging in to the device, you are in user view and the prompt is device name>. In user view, only a few operations are allowed, for example, display operations, file operations, ftp and telnet operations. To further configure the device, you need to enter system view. ...
Page 24
1-10 login command views command view description command to enter example user-interface aux [sysname] user-interface aux 0 [sysname-ui-aux0] user interface view after entering this view, you can configure user interface parameters. User-interface vty [sysname] user-interface vty 0 [sysname-ui-vty0...
Page 25
1-11 command view description command to enter example igmp-snoopin g view enter igmp-snooping view to configure igmp snooping related parameters. Igmp-snooping [sysname] igmp-snooping [sysname-igmp-snooping] multicast vlan view z enable igmp snooping globally, create a vlan, and enable igmp snoopin...
Page 26
1-12 command view description command to enter example priority mapping table view enter priority mapping table view and configure mappings in this view. Qos map-table [sysname] qos map-table dot1p-dp [sysname-maptbl-dot1p-dp] isp domain view z create an isp domain and enter its view. Z after enteri...
Page 27
1-13 command view description command to enter example pki certificate attribute group view z create a pki certificate attribute group and enter its view. Z after entering this view, you can configure the pki certificate attributes. Pki certificate attribute-group [sysname] pki certificate attribute...
Page 28: Tips On Using The Cli
1-14 command view description command to enter example ftp client view z enter ftp client view to configure ftp parameters. Ftp ftp [ftp] tips on using the cli using the cli online help in the cli, you can type a question mark (?) to obtain detailed online help. See the following examples. Type ? In...
Page 29
1-15 display cl? Clipboard clock cluster command line error information if a command you typed contains syntax errors, the cli reports error information. Table 1-3 lists some common command line errors. Table 1-3 common command line errors error information cause the command was not found. The keywo...
Page 30
1-16 key function left arrow key or ctrl+b the cursor moves one character space to the left. Right arrow key or ctrl+f the cursor moves one character space to the right. Tab if you press tab after entering part of a keyword, the system automatically completes the keyword: z if finding a unique match...
Page 31
1-17 current user interface (for more information about the history-command max-size command, see login configuration). Undo form of a command the undo form of a command typically restores the default, disables a function, or removes a configuration. Almost every configuration command has its undo f...
Page 32
1-18 for the support of the display commands for regular expressions, see the corresponding command reference. There are two ways to filter output information. Z input the begin, exclude, or include keyword plus a regular expression in the display command to filter the output information. Z when the...
Page 33
1-19 character meaning remarks [ ] matches a single character contained within the brackets. For example, [16a] matches a string containing any character among 1, 6, and a; [1-36a] matches a string containing any character among 1, 2, 3, 6, and a (- is a hyphen). “]” can be matched as a common chara...
Page 34
1-20 anti-interruption for command input anti-interruption for command input refers to the feature that if your input is interrupted by system output, then after the completion of system output the system displays a command line prompt and your input so far, and you can continue your operations from...
Page 35: Table of Contents
I table of contents 1 logging in to an ethernet switch ············································································································1-1 logging in to an ethernet switch ····································································································...
Page 36
Ii configuration example····························································································································4-2 5 logging in through nms··························································································································5-...
Page 37
1-1 1 logging in to an ethernet switch when logging in to an ethernet switch, go to these sections for information you are interested in: z logging in to an ethernet switch z introduction to user interface z specifying source for telnet packets z controlling login users logging in to an ethernet swi...
Page 38
1-2 z vty user interfaces: numbered after aux user interfaces and increases in the step of 1 2) a relative user interface index can be obtained by appending a number to the identifier of a user interface type. It is generated by user interface type. The relative user interface indexes are as follows...
Page 39
1-3 to do… use the command… remarks set the timeout time for the user interface idle-timeout minutes [ seconds ] optional the default timeout time of a user interface is 10 minutes. With the timeout time being 10 minutes, the connection to a user interface is terminated if no operation is performed ...
Page 40: Introduction
2-1 2 logging in through the console port when logging in through the console port, go to these sections for information you are interested in: z introduction z setting up the connection to the console port z console port login configuration z console port login configuration with authentication mod...
Page 41
2-2 setting up the connection to the console port z connect the serial port of your pc/terminal to the console port of the switch, as shown in figure 2-1 . Figure 2-1 diagram for setting the connection to the console port z if you use a pc to connect to the console port, launch a terminal emulation ...
Page 42
2-3 figure 2-4 set port parameters terminal window z turn on the switch. The user will be prompted to press the enter key if the switch successfully completes post (power-on self test). The prompt (such as ) appears after the user presses the enter key. Z you can then configure the switch or check t...
Page 43
2-4 configuration description aux user interface configuration configure the command level available to the users logging in to the aux user interface optional by default, commands of level 3 are available to the users logging in to the aux user interface. Define a shortcut key for aborting tasks op...
Page 44: None
2-5 authentication mode console port login configuration description specify to perform local authentication or radius authentication aaa configuration specifies whether to perform local authentication or radius authentication optional local authentication is performed by default. Refer to the aaa c...
Page 46
2-7 table 2-4 determine the command level (a) scenario authentication mode user type command command level the user privilege level level command not executed level 3 none (authentication-mod e none) users logging in through console ports the user privilege level level command already executed deter...
Page 47: Password
2-8 # specify commands of level 2 are available to the user logging in to the aux user interface. [sysname-ui-aux0] user privilege level 2 # set the baud rate of the console port to 19200 bps. [sysname-ui-aux0] speed 19200 # set the maximum number of lines the screen can contain to 30. [sysname-ui-a...
Page 49
2-10 note that if you configure to authenticate the users in the password mode, the command level available to users logging in to a switch depends on both the authentication-mode password and the user privilege level level command, as listed in the following table. Table 2-5 determine the command l...
Page 50: Scheme
2-11 [sysname] user-interface aux 0 # specify to authenticate the user logging in through the console port using the local password. [sysname-ui-aux0] authentication-mode password # set the local password to 123456 (in plain text). [sysname-ui-aux0] set authentication password simple 123456 # specif...
Page 53
2-14 network diagram figure 2-7 network diagram for aux user interface configuration (with the authentication mode being scheme) configuration procedure # enter system view. System-view # create a local user named guest and enter local user view. [sysname] local-user guest # set the authentication p...
Page 54: Introduction
3-1 3 logging in through telnet/ssh when logging in through telnet, go to these sections for information you are interested in: z introduction z telnet configuration with authentication mode being none z telnet configuration with authentication mode being password z telnet configuration with authent...
Page 55
3-2 telnet connection establishment telnetting to a switch from a terminal you can telnet to a switch and then configure the switch if the interface of the management vlan of the switch is assigned with an ip address. (by default, vlan 1 is the management vlan.) following are procedures to establish...
Page 56
3-3 figure 3-2 launch telnet step 5: enter the password when the telnet window displays “login authentication” and prompts for login password. The cli prompt (such as ) appears if the password is correct. If all vty user interfaces of the switch are in use, you will fail to establish the connection ...
Page 57: Common Configuration
3-4 mode being scheme for details. By default, telnet users need to pass the password authentication to login. Step 2: telnet to the switch operating as the telnet client. Step 3: execute the following command on the switch operating as the telnet client: telnet xxxx where xxxx is the ip address or ...
Page 58
3-5 z the auto-execute command command may cause you unable to perform common configuration in the user interface, so use it with caution. Z before executing the auto-execute command command and save your configuration, make sure you can log in to the switch in other modes and cancel the configurati...
Page 59
3-6 to do… use the command… remarks enter system view system-view — enter one or more vty user interface views user-interface vty first-number [ last-number ] — configure not to authenticate users logging in to vty user interfaces authentication-mode none required by default, vty users are authentic...
Page 60
3-7 note that if you configure not to authenticate the users, the command level available to users logging in to a switch depends on both the authentication-mode none command and the user privilege level level command, as listed in table 3-4 . Table 3-4 determine the command level when users logging...
Page 61
3-8 # configure telnet protocol is supported. [sysname-ui-vty0] protocol inbound telnet # set the maximum number of lines the screen can contain to 30. [sysname-ui-vty0] screen-length 30 # set the maximum number of commands the history command buffer can store to 20. [sysname-ui-vty0] history-comman...
Page 62
3-9 to do… use the command… remarks set the maximum number of lines the screen can contain screen-length screen-length optional by default, the screen can contain up to 24 lines. You can use the screen-length 0 command to disable the function to display information in pages. Set the history command ...
Page 63
3-10 z commands of level 2 are available to users logging in to vty 0. Z telnet protocol is supported. Z the screen can contain up to 30 lines. Z the history command buffer can contain up to 20 commands. Z the timeout time of vty 0 is 6 minutes. Network diagram figure 3-5 network diagram for telnet ...
Page 65
3-12 to do… use the command… remarks make terminal services available shell optional terminal services are available in all use interfaces by default. Set the maximum number of lines the screen can contain screen-length screen-length optional by default, the screen can contain up to 24 lines. You ca...
Page 66: Logging In Through Ssh
3-13 z the screen can contain up to 30 lines. Z the history command buffer can store up to 20 commands. Z the timeout time of vty 0 is 6 minutes. Network diagram figure 3-6 network diagram for telnet configuration (with the authentication mode being scheme) configuration procedure # enter system vie...
Page 67: Management System
4-1 4 logging in through web-based network management system introduction an s5120-si series switch has a web server built in. You can log in to an s5120-si series switch through a web browser and manage and maintain the switch intuitively by interacting with the built-in web server. To log in to an...
Page 68: Displaying Web Users
4-2 to do… use the command… remarks specify the service types for the local user service-type telnet optional by default, no service is authorized to a user. Start the web server ip http enable required execute this command in system view. Displaying web users after the above configurations, execute...
Page 69
4-3 step 4: log in to the switch through ie. Launch ie on the web-based network management terminal (your pc) and enter the ip address of the management vlan interface of the switch (here it is http://10.153.17.82). (make sure the route between the web-based network management terminal and the switc...
Page 70: Logging In Through Nms
5-1 5 logging in through nms when logging in through nms, go to these sections for information you are interested in: z introduction z connection establishment using nms introduction you can also log in to a switch through an nms (network management station), and then configure and manage the switch...
Page 71: Introduction
6-1 6 specifying source for telnet packets when specifying source ip address/interface for telnet packets, go to these sections for information you are interested in: z introduction z specifying source ip address/interface for telnet packets z displaying the source ip address/interface specified for...
Page 73: Controlling Login Users
7-1 7 controlling login users when controlling login users, go to these sections for information you are interested in: z introduction z controlling telnet users z controlling network management users by source ip addresses introduction multiple ways are available for controlling different types of ...
Page 75
7-3 controlling telnet users by source mac addresses this configuration needs to be implemented by layer 2 acl; a layer 2 acl ranges from 4000 to 4999. For the definition of acl, refer to acl configuration. Follow these steps to control telnet users by source mac addresses: to do… use the command… r...
Page 76
7-4 network diagram figure 7-1 network diagram for controlling telnet users using acls switch 10.110.100.46 host a ip network host b 10.110.100.52 configuration procedure # define a basic acl. System-view [sysname] acl number 2000 match-order config [sysname-acl-basic-2000] rule 1 permit source 10.1...
Page 78
7-6 network diagram figure 7-2 network diagram for controlling snmp users using acls switch 10.110.100.46 host a ip network host b 10.110.100.52 configuration procedure # define a basic acl. System-view [sysname] acl number 2000 match-order config [sysname-acl-basic-2000] rule 1 permit source 10.110...
Page 80
7-8 [sysname] ip http acl 2030
Page 81: Table of Contents
I table of contents 1 ethernet port configuration ·····················································································································1-1 basic ethernet port configuration································································································...
Page 82: Ethernet Port Configuration
1-1 1 ethernet port configuration when configuring ethernet ports, go to these sections for information you are interested in: z basic ethernet port configuration z configuring an auto-negotiation transmission rate z configuring flow control on an ethernet port z perfoming loopback testing on an eth...
Page 85
1-4 figure 1-2 internal loopback testing z external loopback testing, which tests the hardware of ethernet ports. As shown in figure 1-3 , external loopback testing is performed on port 1. To perform external loopback testing on an ethernet port, insert a loopback plug into the port. During the exte...
Page 86: Configuring A Port Group
1-5 enabling auto power down on an ethernet port when an ethernet port does not receive any packet for a certain period of time, it automatically enters the power save mode and resumes its normal state upon the arrival of a packet. Follow these steps to enable auto power down on an ethernet port: to...
Page 87
1-6 configuring traffic storm protection a traffic storm occurs when a large amount of broadcast, multicast, or unicast packets congest a network. The s5120-si switches provide two storm protection approaches: z storm suppression, which enables you to limit the size of monitored traffic passing thro...
Page 88
1-7 as for an ethernet port belongs to a port group, if you set a storm suppression ratio for the interface in both ethernet port view and port group view, the one configured the last takes effect. Configuring the storm constrain function on an ethernet port the storm constrain function suppresses p...
Page 89
1-8 to do… use the command… remarks specify to send trap messages when the traffic detected exceeds the upper threshold or drops down below the lower threshold from a point higher than the upper threshold storm-constrain enable trap optional by default, the system sends trap messages when the traffi...
Page 90
1-9 enabling forwarding of jumbo frames due to tremendous amount of traffic occurring on an ethernet port, it is likely that some frames greater than the standard ethernet frame size are received. Such frames (called jumbo frames) will be dropped. With forwarding of jumbo frames enabled, the system ...
Page 91
1-10 to do… use the command… remarks configure the interval for port loopback detection loopback-detection interval-time time optional 30 seconds by default enter ethernet port view interface interface-type interface-number — enable loopback detection on a port loopback-detection enable required dis...
Page 92
1-11 z normally, the auto mode is recommended. The other two modes are useful only when the device cannot determine the cable type. Z when straight-through cables are used, the local mdi mode must be different from the remote mdi mode. Z when crossover cables are used, the local mdi mode must be the...
Page 93
1-12 to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — test the cable connected to the ethernet port once virtual-cable-test required displaying and maintaining an ethernet port to do… use the command… remarks display...
Page 94: Table of Contents
I table of contents 1 loopback interface and null interface configuration············································································1-1 loopback interface·································································································································...
Page 95: Configuration
1-1 1 loopback interface and null interface configuration when configuring loopback interfaces and null interfaces, go to these sections for information you are interested in: z loopback interface z null interface z displaying and maintaining loopback and null interfaces loopback interface introduct...
Page 96: Null Interface
1-2 to do… use the command… remarks enter system view system-view — create a loopback interface and enter loopback interface view interface loopback interface-number — set a description for the loopback interface description text optional by default, the description of an interface is the interface ...
Page 97
1-3 to do… use the command… remarks enter system view system-view — enter null interface view interface null 0 required the null 0 interface is the default null interface on your device. It cannot be manually created or removed. Set a description for the null interface description text optional by d...
Page 98: Table of Contents
I table of contents 1 ethernet link aggregation configuration·······························································································1-1 overview ···································································································································...
Page 99: Overview
1-1 1 ethernet link aggregation configuration this chapter includes these sections: z overview z ethernet link aggregation configuration task list z configuring an aggregation group z configuring an aggregate interface z displaying and maintaining ethernet link aggregation z ethernet link aggregatio...
Page 100
1-3 to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the auto-negotiation transmission rate range speed auto [ 10
Page 101
1-3 z class-two configurations made on an aggregate interface are automatically synchronized to all its member ports. These configurations are retained on the member ports even after the aggregate interface is removed. Z any class-two configuration change may affect the aggregation state of link agg...
Page 102
1-4 for details about irf, member devices, intermediate devices, and the lacp mad mechanism, see the operation manuals of irf-supported devices. 2) lacp priorities there are two types of lacp priorities: system lacp priority and port lacp priority, as described in table 1-3 . Table 1-3 lacp prioriti...
Page 103
1-5 aggregating links in static mode lacp is disabled on the member ports in a static aggregation group. The aggregation state of the member ports must be maintained manually. Static link aggregation comprises: z selecting a reference port z setting the aggregation state of each member port selectin...
Page 104
1-6 z because any port attribute or class-two configuration change on a member port may cause the aggregation state of the port and other member ports to change and thus affect services, it is recommended that you do that with caution. Z a port that joins the static aggregation group after the selec...
Page 105
1-7 figure 1-3 set the state of a member port in a dynamic aggregation group no more candidate ports than allowed max. Number of selected ports? Is the port up? Is there any hardware restriction? Port number low enough to put the port within the limit? Set the aggregation state of a member port set ...
Page 106
1-8 task remarks configuring a static aggregation group configuring an aggregation group configuring a dynamic aggregation group select either task configuring the description of an aggregate interface optional enabling link state trapping for an aggregate interface optional configuring an aggregate...
Page 107
1-9 to do... Use the command... Remarks create a layer 2 aggregate interface and enter the layer 2 aggregate interface view interface bridge-aggregation interface-number required when you create a layer 2 aggregate interface, the system automatically creates a layer 2 static aggregation group number...
Page 108
1-10 to do... Use the command... Remarks assign the ethernet interface to the aggregation group port link-aggregation group number assign multiple layer 2 ethernet interfaces to the aggregation group. Assign the port a lacp priority lacp port-priority port-priority optional by default, the lacp prio...
Page 110
1-12 to do... Use the command... Remarks clear statistics for a specific or all aggregate interfaces reset counters interface [ bridge-aggregation } [ interface-number ] ] available in user view ethernet link aggregation configuration examples in an aggregation group, only ports that have the same p...
Page 111
1-13 system-view [devicea] vlan 10 [devicea-vlan10] port gigabitethernet 1/0/4 [devicea-vlan10] quit # create vlan 20, and assign port gigabitethernet 1/0/5 to vlan 20. [devicea] vlan 20 [devicea-vlan20] port gigabitethernet 1/0/5 [devicea-vlan20] quit # create layer 2 aggregate interface 1. [device...
Page 112
1-14 bagg -- bridge-aggregation, ragg -- route-aggregation aggregation mode: s -- static, d -- dynamic loadsharing type: shar -- loadsharing, nons -- non-loadsharing actor system id: 0x8000, 000f-e2ff-0001 agg agg partner id select unselect share interface mode ports ports type ---------------------...
Page 113
1-15 [devicea-vlan20] quit # create layer 2 aggregate interface 1, and configure the link aggregation mode as dynamic. [devicea] interface bridge-aggregation 1 [devicea-bridge-aggregation1] link-aggregation mode dynamic [devicea-bridge-aggregation1] quit # assign ports gigabitethernet 1/0/1 through ...
Page 114
1-16 ------------------------------------------------------------------------------- bagg1 d 0x8000, 000f-e2ff-0002 3 0 shar the output shows that link aggregation group 1 is a load sharing layer 2 dynamic aggregation group and it contains three selected ports..
Page 115: Table of Contents
I table of contents 1 port isolation configuration ·····················································································································1-1 introduction to port isolation ·································································································...
Page 116: Port Isolation Configuration
1-1 1 port isolation configuration when configuring port isolation, go to these sections for information you are interested in: z introduction to port isolation z configuring an isolation group for a multiple-isolation-group device z displaying and maintaining isolation groups z port isolation confi...
Page 117
1-2 to do… use the command… remarks add the port/ports to an isolation group as an isolated port/isolated ports port-isolate enable group group-number required no ports are added to an isolation group by default. Displaying and maintaining isolation groups to do… use the command… remarks display the...
Page 118
1-3 [device-gigabitethernet1/0/1] port-isolate enable group 2 [device-gigabitethernet1/0/1] quit [device] interface gigabitethernet 1/0/2 [device-gigabitethernet1/0/2] port-isolate enable group 2 [device-gigabitethernet1/0/2] quit [device] interface gigabitethernet 1/0/3 [device-gigabitethernet1/0/3...
Page 119: Table of Contents
I table of contents 1 port mirroring configuration ····················································································································1-1 introduction to port mirroring ··································································································...
Page 120: Port Mirroring Configuration
1-1 1 port mirroring configuration when configuring port mirroring, go to these sections for information you are interested in: z introduction to port mirroring z configuring local port mirroring z displaying and maintaining port mirroring z port mirroring configuration examples introduction to port...
Page 121
1-2 as shown in figure 1-1 , packets on the mirroring port are mirrored to the monitor port for the data monitoring device to analyze. Figure 1-1 local port mirroring implementation configuring local port mirroring configuring local port mirroring is to configure local mirroring groups. A local mirr...
Page 122
1-3 z a local mirroring group takes effect only after you configure a monitor port and mirroring ports for it. Z to ensure the smooth operation of your device, do not enable stp, mstp, or rstp on the monitor port. Z you are recommended to use a monitor port only for port mirroring. This is to ensure...
Page 123
1-4 configuration procedure 1) configuration scheme 1 # create a local mirroring group. System-view [devicec] mirroring-group 1 local # configure ports gigabitethernet 1/0/1 and gigabitethernet 1/0/2 as mirroring ports and port gigabitethernet 1/0/3 as the monitor port in the mirroring group. [devic...
Page 124: Table of Contents
I table of contents 1 lldp configuration···································································································································1-1 overview ····················································································································...
Page 125: Lldp Configuration
1-1 1 lldp configuration this chapter includes these sections: z overview z lldp configuration task list z performing basic lldp configuration z configuring cdp compatibility z configuring lldp trapping z displaying and maintaining lldp z lldp configuration examples overview background in a heteroge...
Page 126
1-2 figure 1-1 ethernet ii-encapsulated lldpdu format the fields in the frame are described in table 1-1 : table 1-1 description of the fields in an ethernet ii-encapsulated lldpdu field description destination mac address the mac address to which the lldpdu is advertised. It is fixed to 0x0180-c200...
Page 127
1-3 field description source mac address the mac address of the sending port. If the port does not have a mac address, the mac address of the sending bridge is used. Type the snap type for the upper layer protocol. It is 0xaaaa-0300-0000-88cc for lldp. Data lldpdu fcs frame check sequence, a 32-bit ...
Page 128
1-4 type description remarks system name assigned name of the sending device system description description of the sending device system capabilities identifies the primary functions of the sending device and the enabled primary functions management address management address, and the interface numb...
Page 129
1-5 lldp-med tlvs lldp-med tlvs provide multiple advanced applications for voice over ip (voip), such as basic configuration, network policy configuration, and address and directory management. Lldp-med tlvs provide a cost-effective and easy-to-use solution for deploying voice devices in ethernet. L...
Page 130: Lldp Configuration Task List
1-6 can configure a re-initialization delay. With this delay configured, a port must wait for the specified interval before it can initialize lldp after the lldp operating mode changes. Transmitting lldpdus an lldp-enabled port operating in txrx mode or tx mode sends lldpdus to its directly connecte...
Page 131
1-7 lldp-related configurations made in layer 2 ethernet port view take effect only on the current port, and those made in port group view take effect on all ports in the current port group. Performing basic lldp configuration enabling lldp to make lldp take effect on certain ports, you must enable ...
Page 132
1-8 setting the lldp re-initialization delay when lldp operating mode changes on a port, the port initializes the protocol state machines after a certain delay. By adjusting the lldp re-initialization delay, you can avoid frequent initializations caused by frequent lldp operating mode changes on a p...
Page 134
1-10 by setting the ttl multiplier, you can configure the ttl of locally sent lldpdus, which determines how long information about the local device can be saved on a neighbor device. The ttl is expressed as follows: ttl = min (65535, (ttl multiplier × lldpdu transmit interval)) as the expression sho...
Page 135
1-11 to do… use the command… remarks enter layer 2 ethernet port view interface interface-type interface-number enter ethernet port view or port group view enter port group view port-group manual port-group-name required use either command set the encapsulation format for lldpdus to snap lldp encaps...
Page 136: Configuring Lldp Trapping
1-12 z disable: the cdp packets can neither be transmitted nor be received. To make cdp-compatible lldp take effect on certain ports, first enable cdp-compatible lldp globally, and then configure cdp-compatible lldp to operate in txrx mode. Follow these steps to enable lldp to be compatible with cdp...
Page 138
1-14 # enable lldp on gigabitethernet 1/0/1 and gigabitethernet 1/0/2 (you can skip this step because lldp is enabled on ports by default), and set the lldp operating mode to rx. [switcha] interface gigabitethernet 1/0/1 [switcha-gigabitethernet1/0/1] lldp enable [switcha-gigabitethernet1/0/1] lldp ...
Page 139
1-15 port 2 [gigabitethernet1/0/2]: port status of lldp : enable admin status : rx_only trap flag : no polling interval : 0s number of neighbors: 1 number of med neighbors : 0 number of cdp neighbors : 0 number of sent optional tlv : 0 number of received unknown tlv : 3 as the sample output shows, g...
Page 140
1-16 number of med neighbors : 0 number of cdp neighbors : 0 number of sent optional tlv : 0 number of received unknown tlv : 0 as the sample output shows, gigabitethernet 1/0/2 of switch a does not connect to any neighboring devices. Cdp-compatible lldp configuration example network requirements as...
Page 141
1-17 [switcha] interface gigabitethernet 1/0/1 [switcha-gigabitethernet1/0/1] lldp enable [switcha-gigabitethernet1/0/1] lldp admin-status txrx [switcha-gigabitethernet1/0/1] lldp compliance admin-status cdp txrx [switcha-gigabitethernet1/0/1] quit [switcha] interface gigabitethernet 1/0/2 [switcha-...
Page 142: Table of Contents
I table of contents 1 vlan configuration ··································································································································1-1 introduction to vlan ········································································································...
Page 143: Vlan Configuration
1-1 1 vlan configuration when configuring vlan, go to these sections for information you are interested in: z introduction to vlan z configuring basic vlan settings z configuring basic settings of a vlan interface z port-based vlan configuration z displaying and maintaining vlan z vlan configuration...
Page 144
1-2 2) improving lan security. By assigning user groups to different vlans, you can isolate them at layer 2. To enable communication between vlans, routers or layer 3 switches are required. 3) flexible virtual workgroup creation. As users from the same workgroup can be assigned to the same vlan rega...
Page 145
1-3 z the ethernet ii encapsulation format is used here. Besides the ethernet ii encapsulation format, other encapsulation formats, including 802.2 llc, 802.2 snap, and 802.3 raw, are also supported by ethernet. The vlan tag fields are also added to frames encapsulated in these formats for vlan iden...
Page 146
1-4 z as the default vlan, vlan 1 cannot be created or removed. Z you cannot manually create or remove vlans reserved for special purposes. Z dynamic vlans cannot be removed with the undo vlan command. Z a vlan with a qos policy applied cannot be removed. Configuring basic settings of a vlan interfa...
Page 147
1-5 port-based vlan configuration introduction to port-based vlan port-based vlans group vlan members by port. A port forwards traffic for a vlan only after it is assigned to the vlan. Port link type you can configure the link type of a port as access, trunk, or hybrid. The three link types use diff...
Page 148
1-6 actions (in the inbound direction) port type untagged frame tagged frame actions (in the outbound direction) access tag the frame with the default vlan tag. Z receive the frame if its vlan id is the same as the default vlan id. Z drop the frame if its vlan id is different from the default vlan i...
Page 149
1-7 follow these steps to assign an access port (in interface view) or multiple access ports (in port group view) to a vlan: to do… use the command… remarks enter system view system-view — enter ethernet interface view interface interface-type interface-number enter layer-2 aggregate interface view ...
Page 150
1-8 to do… use the command… remarks enter ethernet interface view interface interface-type interface-number enter layer-2 aggregate interface view interface bridge-aggregation interface-number enter interface view or port group view enter port group view port-group manual port-group-name required us...
Page 151
1-9 to do… use the command… remarks enter layer-2 aggregate interface view interface bridge-aggregation interface-number view or port group view enter port group view port-group manual port-group-name use either command. Z in ethernet interface view, the subsequent configurations apply to the curren...
Page 152: Vlan Configuration Example
1-10 to do... Use the command… remarks [ interface-number ] ] vlan configuration example network requirements z device a connects to device b through a trunk port gigabitethernet 1/0/1; z the default vlan id of gigabitethernet 1/0/1 is 100; z gigabitethernet 1/0/1 allows packets from vlan 2, vlan 6 ...
Page 153
1-11 verification verifying the configuration on device a is similar to that of device b. So only device a is taken for example here. # display the information about gigabitethernet 1/0/1 of device a to verify the above configurations. Display interface gigabitethernet 1/0/1 gigabitethernet1/0/1 cur...
Page 154: Voice Vlan Configuration
2-1 2 voice vlan configuration when configuring a voice vlan, go to these sections for information you are interested in: z overview z configuring a voice vlan z displaying and maintaining voice vlan z voice vlan configuration overview as voice communication technologies grow more mature, voice devi...
Page 155
2-2 7 00e0-bb00-0000 3com phone z in general, as the first 24 bits of a mac address (in binary format), an oui address is a globally unique identifier assigned to a vendor by ieee. Oui addresses mentioned in this document, however, are different from those in common sense. Oui addresses in this docu...
Page 156
2-3 figure 2-2 only ip phones access the network both modes forward tagged packets according to their tags. The following tables list the required configurations on ports of different link types in order for these ports to support tagged or untagged voice traffic sent from ip phones when different v...
Page 157
2-4 table 2-3 required configurations on ports of different links types in order for the ports to support tagged voice traffic port link type voice vlan assignment mode support for untagged voice traffic configuration requirements automatic no — access manual yes configure the default vlan of the po...
Page 158: Configuring A Voice Vlan
2-5 the port forwards all received untagged packets in the voice vlan. In normal mode, the voice vlans are vulnerable to traffic attacks. Vicious users can forge a large amount of voice packets and send them to voice vlan-enabled ports to consume the voice vlan bandwidth, affecting normal voice comm...
Page 159
2-6 setting a port to operate in automatic voice vlan assignment mode follow these steps to set a port to operate in automatic voice vlan assignment mode: to do... Use the command... Remarks enter system view system-view — set the voice vlan aging time voice vlan aging minutes optional 1440 minutes ...
Page 160
2-7 to do... Use the command... Remarks add a recognizable oui address voice vlan mac-address oui mask oui-mask[ description text] optional by default, each voice vlan has default oui addresses configured. Refer to table 2-1 for the default oui addresses of different vendors. Enter interface view in...
Page 161
2-8 voice vlan configuration examples automatic voice vlan mode configuration example network requirements as shown in figure 2-3 , z the mac address of ip phone a is 0011-1100-0001. The phone connects to a downstream device named pc a whose mac address is 0022-1100-0002 and to gigabitethernet 1/0/1...
Page 162
2-9 # configure the allowed oui addresses as mac addresses prefixed by 0011-2200-0000. In this way, device a identifies packets whose mac addresses match any of the configured oui addresses as voice packets. [devicea] voice vlan mac-address 0011-2200-0001 mask ffff-ff00-0000 description ip phone b #...
Page 163
2-10 z configure gigabitethernet 1/0/1 to operate in manual voice vlan assignment mode. Configure gigabitethernet 1/0/1 to allow voice traffic with an oui address of 0011-2200-0000, a mask of ffff-ff00-0000, and a description string test to be forwarded through the voice vlan. Figure 2-4 network dia...
Page 164
2-11 0001-e300-0000 ffff-ff00-0000 siemens phone 0003-6b00-0000 ffff-ff00-0000 cisco phone 0004-0d00-0000 ffff-ff00-0000 avaya phone 0011-2200-0000 ffff-ff00-0000 test 00d0-1e00-0000 ffff-ff00-0000 pingtel phone 0060-b900-0000 ffff-ff00-0000 philips/nec phone 00e0-7500-0000 ffff-ff00-0000 polycom ph...
Page 165: Table of Contents
I table of contents 1 mstp configuration ··································································································································1-1 overview ····················································································································...
Page 166: Mstp Configuration
1-1 1 mstp configuration this chapter includes these sections: z overview z introduction to stp z introduction to rstp z introduction to mstp z mstp configuration task list z configuring mstp z displaying and maintaining mstp z mstp configuration example overview as a layer 2 management protocol, th...
Page 167
1-2 z topology change notification (tcn) bpdus, used for notifying the concerned devices of network topology changes, if any. Basic concepts in stp root bridge a tree network must have a root; hence the concept of root bridge was introduced in stp. There is only one root bridge in the entire network...
Page 168
1-3 figure 1-1 a schematic diagram of designated bridges and designated ports path cost path cost is a reference value used for link selection in stp. By calculating path costs, stp selects relatively robust links and blocks redundant links, and finally prunes the network into a loop-free tree. How ...
Page 169
1-4 calculation process of the stp algorithm z initial state upon initialization of a device, each port generates a bpdu with itself as the root bridge, in which the root path cost is 0, designated bridge id is the device id, and the designated port is the port itself. Z selection of the optimum con...
Page 170
1-5 step description 2 based on the configuration bpdu and the path cost of the root port, the device calculates a designated port configuration bpdu for each of the rest ports. Z the root bridge id is replaced with that of the configuration bpdu of the root port. Z the root path cost is replaced wi...
Page 171
1-6 table 1-4 initial state of each device device port name bpdu of port ap1 {0, 0, 0, ap1} device a ap2 {0, 0, 0, ap2} bp1 {1, 0, 1, bp1} device b bp2 {1, 0, 1, bp2} cp1 {2, 0, 2, cp1} device c cp2 {2, 0, 2, cp2} z comparison process and result on each device table 1-5 shows the comparison process ...
Page 172
1-7 device comparison process bpdu of port after comparison z port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received configuration bpdu is superior to the configuration bpdu of the local port {2, 0, 2, cp1}, and updates the configuration bpdu of cp1. Z ...
Page 173
1-8 figure 1-3 the final calculated spanning tree ap1 ap2 device a with priority 0 device b with priority 1 device c with priority 2 bp1 bp2 cp2 5 4 the spanning tree calculation process in this example is only simplified process. The bpdu forwarding mechanism in stp z upon network initiation, every...
Page 174: Introduction to Rstp
1-9 for this reason, as a mechanism for state transition in stp, the newly elected root ports or designated ports require twice the forward delay time before transiting to the forwarding state to ensure that the new configuration bpdu has propagated throughout the network. Z hello time is the time i...
Page 175
1-10 z mstp supports mapping vlans to spanning tree instances by means of a vlan-to-instance mapping table. Mstp can reduce communication overheads and resource usage by mapping multiple vlans to one instance. Z mstp divides a switched network into multiple regions, each containing multiple spanning...
Page 176
1-11 z they have the same mstp revision level configuration, and z they are physically linked with one another. For example, all the devices in region a0 in figure 1-4 have the same mst region configuration: z the same region name, z the same vlan-to-instance mapping configuration (vlan 1 is mapped ...
Page 177
1-12 common root bridge the common root bridge is the root bridge of the cist. In figure 1-4 , for example, the common root bridge is a device in region a0. Boundary port a boundary port is a port that connects an mst region to another mst region, or to a single spanning-tree region running stp, or ...
Page 178
1-13 figure 1-5 port roles connecting to the common root bridge port 1 port 2 master port alternate port designated port port 3 port 4 port 5 a b c d port 6 backup port mst region figure 1-5 helps understand these concepts. In this figure: z devices a, b, c, and d constitute an mst region. Z port 1 ...
Page 179
1-14 table 1-6 port states supported by different port roles port role (right) port state (below) root port/master port designated port alternate port backup port forwarding √ √ — — learning √ √ — — discarding √ √ √ √ how mstp works mstp divides an entire layer 2 network into multiple mst regions, w...
Page 180: Mstp Configuration Task List
1-15 protocols and standards mstp is documented in: z ieee 802.1d: media access control (mac) bridges z ieee 802.1w: part 3: media access control (mac) bridges—amendment 2: rapid reconfiguration z ieee 802.1s: virtual bridged local area networks—amendment 3: multiple spanning trees mstp configuratio...
Page 181: Configuring Mstp
1-16 task remarks performing mcheck optional configuring the vlan ignore feature optional configuring digest snooping optional configuring no agreement check optional configuring protection functions optional z configurations made in system view take effect globally; configurations made in layer 2 e...
Page 182
1-17 to do... Use the command... Remarks display the mst region configurations that are not activated yet check region-configuration optional activate mst region configuration manually active region-configuration required display the currently activated configuration information of the mst region di...
Page 183
1-18 configuring the current device as the root bridge of a specific spanning tree follow these steps to configure the current device as the root bridge of a specific spanning tree: to do... Use the command... Remarks enter system view system-view — configure the current device as the root bridge of...
Page 185
1-20 to do... Use the command... Remarks configure the maximum hops of the mst region stp max-hops hops required 20 by default configuring the network diameter of a switched network any two terminal devices in a switched network are interconnected through a specific path composed of a series of devi...
Page 186
1-21 these three timers set on the root bridge of the cist apply on all the devices on the entire switched network. Make this configuration on the root bridge only. Follow these steps to configure the timers of mstp: to do... Use the command... Remarks enter system view system-view — configure the f...
Page 187
1-22 z 2 × (forward delay – 1 second) ƒ max age z max age ƒ 2 × (hello time + 1 second) we recommend that you specify the network diameter with the stp bridge-diameter command and let mstp automatically calculate optimal settings of these three timers based on the network diameter. Configuring the t...
Page 188
1-23 the higher the maximum port rate is, the more bpdus will be sent within each hello time, and the more system resources will be used. By setting an appropriate maximum port rate, you can limit the rate at which the port sends bpdus and prevent mstp from using excessive network resources when the...
Page 189
1-24 the device can automatically calculate the default path cost; alternatively, you can also configure the path cost for ports. Make the following configurations on the leaf nodes only. Specifying a standard that the device uses when calculating the default path cost you can specify a standard for...
Page 190
1-25 when calculating path cost for an aggregate port, 802.1d-1998 does not take into account the number of member ports in its aggregation group as 802.1t does. The calculation formula of 802.1t is: path cost = 200,000,000/link speed (in 100 kbps), where link speed is the sum of the link speed valu...
Page 191
1-26 configuring port priority the priority of a port is an important factor in determining whether the port can be elected as the root port of a device. If all other conditions are the same, the port with the highest priority will be elected as the root port. On an mstp-enabled device, a port can h...
Page 192
1-27 to do... Use the command... Remarks enter layer 2 ethernet port view, or layer 2 aggregate port view interface interface-type interface-number enter port view or port group view enter port group view port-group manual port-group-name required use either command. Configure the link type of ports...
Page 194
1-29 to do... Use the command... Remarks enter layer 2 ethernet port view, or layer 2 aggregate port view interface interface-type interface-number enter port view or port group view enter port group view port-group manual port-group-name required use either command. Enable the mstp feature for the ...
Page 195
1-30 to do... Use the command... Remarks enter system view system-view — enter layer 2 ethernet port view, or layer 2 aggregate port view interface interface-type interface-number — perform mcheck stp mcheck required an mcheck operation takes effect on a device only when mstp operates in rstp or mst...
Page 196
1-31 z gigabitethernet 1/0/1 on device a and gigabitethernet 1/0/1 on device b allow the traffic of vlan 1 to pass through. Gigabitethernet 1/0/2 on device a and gigabitethernet 1/0/2 on device b allow the traffic of vlan 2 to pass through. Z device a is the root bridge, and both device a and device...
Page 197
1-32 configuring the digest snooping feature you can enable digest snooping only on a device that is connected to a third-party device that uses its private key to calculate the configuration digest. Follow these steps to configure digest snooping: to do... Use the command... Remarks enter system vi...
Page 198
1-33 z enable digest snooping on device a’s and device b’s ports that connect device c, so that the three devices can communicate with one another. Figure 1-8 digest snooping configuration ge1/0/2 ge1/0/1 ge1/0/2 ge1/0/2 ge1/0/1 ge1/0/1 device a device b third-party device root port designated port ...
Page 199
1-34 figure 1-9 rapid state transition of an mstp designated port figure 1-10 shows rapid state transition of an rstp designated port. Figure 1-10 rapid state transition of an rstp designated port if the upstream device is a third-party device, the rapid state transition implementation may be limite...
Page 200
1-35 to do... Use the command... Remarks enter system view system-view — enter layer 2 ethernet port view, or layer 2 aggregate port view interface interface-type interface-number enter port view or port group view enter port group view port-group manual port-group-name required use either command. ...
Page 201
1-36 these ports receive configuration bpdus, the system will automatically set these ports as non-edge ports and start a new spanning tree calculation process. This will cause a change of network topology. Under normal conditions, these ports should not receive configuration bpdus. However, if some...
Page 202
1-37 to do... Use the command... Remarks enter layer 2 ethernet port view, or layer 2 aggregate port view interface interface-type interface-number enter port view or port group view enter port group view port-group manual port-group-name required use either command. Enable the root guard function f...
Page 203
1-38 z do not enable loop guard on a port connecting user terminals. Otherwise, the port will stay in the discarding state in all mstis because it cannot receive bpdus. Z among loop guard, root guard and edge port settings, only one function (whichever is configured the earliest) can take effect on ...
Page 204: Mstp Configuration Example
1-39 to do... Use the command... Remarks view the statistics of tc/tcn bpdus sent and received by all ports in the specified msti or all mstis display stp [ instance instance-id ] tc available in any view view the status information and statistics information of mstp display stp [ instance instance-...
Page 205
1-40 configuration procedure 1) vlan and vlan member port configuration create vlan 10, vlan 30, and vlan 40 on device a and device b respectively, create vlan 10, vlan 20, and vlan 40 on device c, and create vlan 20, vlan 30, and vlan 40 on device d; configure the ports on these devices as trunk po...
Page 206
1-41 system-view [devicec] stp region-configuration [devicec-mst-region] region-name example [devicec-mst-region] instance 1 vlan 10 [devicec-mst-region] instance 2 vlan 20 [devicec-mst-region] revision-level 0 # activate mst region configuration. [devicec-mst-region] active region-configuration [de...
Page 207
1-42 0 gigabitethernet1/0/1 desi forwarding none 0 gigabitethernet1/0/2 desi forwarding none 0 gigabitethernet1/0/3 desi forwarding none 1 gigabitethernet1/0/2 desi forwarding none 1 gigabitethernet1/0/3 root forwarding none 3 gigabitethernet1/0/1 desi forwarding none 3 gigabitethernet1/0/3 desi for...
Page 208
1-43 figure 1-13 mstis corresponding to different vlans a b b c the msti corresponding to vlan 10 a d root bridge selected link blocked link the msti corresponding to vlan 30 a b c d the msti corresponding to vlan 40 c d the msti corresponding to vlan 20
Page 209: Table of Contents
I table of contents 1 ip addressing configuration····················································································································1-1 ip addressing overview·············································································································...
Page 210: Ip Addressing Configuration
1-1 1 ip addressing configuration when assigning ip addresses to interfaces on your device, go to these sections for information you are interested in: z ip addressing overview z configuring ip addresses z displaying and maintaining ip addressing ip addressing overview this section covers these topi...
Page 211
1-2 table 1-1 ip address classes and ranges class address range remarks a 0.0.0.0 to 127.255.255.255 the ip address 0.0.0.0 is used by a host at bootstrap for temporary communication. This address is never a valid destination address. Addresses starting with 127 are reserved for loopback test. Packe...
Page 212: Configuring Ip Addresses
1-3 in the absence of subnetting, some special addresses such as the addresses with the net id of all zeros and the addresses with the host id of all ones, are not assignable to hosts. The same is true for subnetting. When designing your network, you should note that subnetting is somewhat a tradeof...
Page 213
1-4 displaying and maintaining ip addressing to do… use the command… remarks display information about a specified or all layer 3 interfaces display ip interface [ interface-type interface-number ] available in any view display brief information about a specified or all layer 3 interfaces display ip...
Page 214: Table of Contents
I table of contents 1 ip performance optimization configuration···························································································1-1 ip performance optimization overview ··································································································1-1 ena...
Page 215: Directly Connected Network
1-1 1 ip performance optimization configuration when optimizing ip performance, go to these sections for information you are interested in: z ip performance optimization overview z enabling reception and forwarding of directed broadcasts to a directly connected network z configuring tcp attributes z...
Page 216: Configuring Tcp Attributes
1-2 enabling forwarding of directed broadcasts to a directly connected network if a device is enabled to receive directed broadcasts, the device will determine whether to forward them according to the configuration on the outgoing interface. Follow these steps to enable the device to forward directe...
Page 217
1-3 follow these steps to enable the syn cookie feature: to do... Use the command... Remarks enter system view system-view — enable the syn cookie feature tcp syn-cookie enable required disabled by default. Z if md5 authentication is enabled, the syn cookie feature will not function after enabled. T...
Page 218
1-4 z with the protection against naptha attack enabled, the device will periodically check and record the number of tcp connections in each state. Z with the protection against naptha attack enabled, if the device detects that the number of tcp connections in a state exceeds the maximum number, the...
Page 219
1-5 configuring icmp to send error packets sending error packets is a major function of icmp. In case of network abnormalities, icmp packets are usually sent by the network or transport layer protocols to notify corresponding devices so as to facilitate control and management. Advantages of sending ...
Page 220
1-6 to do… use the command… remarks enter system view system-view — enable sending of icmp timeout packets ip ttl-expires enable required disabled by default. Enable sending of icmp destination unreachable packets ip unreachables enable required disabled by default. The device stops sending “ttl tim...
Page 221: Table of Contents
I table of contents 1 arp configuration·····································································································································1-1 arp overview················································································································...
Page 222: Arp Configuration
1-1 1 arp configuration when configuring arp, go to these sections for information you are interested in: z arp overview z configuring arp z configuring gratuitous arp z displaying and maintaining arp arp overview arp function the address resolution protocol (arp) is used to resolve an ip address in...
Page 223
1-2 z sender protocol address: this field specifies the protocol address of the device sending the message. Z target hardware address: this field specifies the hardware address of the device the message is being sent to. Z target protocol address: this field specifies the protocol address of the dev...
Page 224: Configuring Arp
1-3 arp table after obtaining the mac address for the destination host, the device puts the ip-to-mac mapping into its own arp table. This mapping is used for forwarding packets with the same destination in future. An arp table contains arp entries, which fall into one of two categories: dynamic or ...
Page 225
1-4 to do… use the command… remarks configure a permanent static arp entry arp static ip-address mac-address vlan-id interface-type interface-number required no permanent static arp entry is configured by default. Configure a non-permanent static arp entry arp static ip-address mac-address required ...
Page 226
1-5 enabling the arp entry check the arp entry check function disables the device from learning multicast mac addresses. With the arp entry check enabled, the device cannot learn any arp entry with a multicast mac address, and configuring such a static arp entry is not allowed; otherwise, the system...
Page 227: Configuring Gratuitous Arp
1-6 [switch] interface gigabitethernet 1/0/1 [switch-gigabitethernet1/0/1] port access vlan 10 [switch-gigabitethernet1/0/1] quit # create interface vlan-interace 10 and configure its ip address. [switch] interface vlan-interface 10 [switch-vlan-interface10] ip address 192.168.1.2 8 [switch-vlan-int...
Page 229
2-1 2 arp attack defense configuration although arp is easy to implement, it provides no security mechanism and thus is prone to network attacks. Currently, arp attacks and viruses are threatening lan security. The device can provide multiple features to detect and prevent such attacks. Configuring ...
Page 230
2-2 configuration procedure enabling source mac address based arp attack detection after this feature is enabled for a device, if the number of arp packets it receives from a mac address within five seconds exceeds the specified value, it generates an alarm and filters out arp packets sourced from t...
Page 231: Configuring Arp Detection
2-3 displaying and maintaining source mac address based arp attack detection to do… use the command… remarks display attacking entries detected display arp anti-attack source-mac [ interface interface-type interface-number] available in any view a protected mac address is no longer excluded from det...
Page 232
2-4 man-in-the-middle attack according to the arp design, after receiving an arp reply, a host adds the ip-to-mac mapping of the sender to its arp mapping table. This design reduces the arp traffic on the network, but also makes arp spoofing possible. As shown in figure 2-1 , host a communicates wit...
Page 233
2-5 mac addresses, port index, and vlan id) are consistent, the arp packet passes the check; if not, the arp packet cannot pass the check. Z upon receiving an arp packet from an arp trusted port, the device does not check the arp packet. Z if arp detection is not enabled for the vlan, the arp packet...
Page 234
2-6 to do… use the command… remarks return to system view quit — enter ethernet interface view interface interface-type interface-number — configure the port as a trusted port arp detection trust optional the port is an untrusted port by default. Return to system view quit — specify an arp attack de...
Page 235
2-7 before performing the following configuration, make sure you have configured the arp detection enable command. Follow these steps to configure arp detection based on specified objects: to do… use the command… remarks enter system view system-view — specify objects for arp detection arp detection...
Page 236
2-8 figure 2-2 network diagram for arp detection configuration dhcp client host a switch a host b gateway dhcp server ge1/0/1 ge1/0/3 ge1/0/2 vlan 10 dhcp snooping 10.1.1.6 0001-0203-0607 configuration procedure 1) add all the ports on switch a to vlan 10 (the configuration procedure is omitted). 2)...
Page 237
2-9 after the preceding configurations are completed, when arp packets arrive at interfaces gigabitethernet 1/0/1 and gigabitethernet 1/0/2, their mac and ip addresses are checked, and then the packets are checked against the ip-to-mac binding and finally dhcp snooping entries. Arp detection configu...
Page 238
2-10 # enable arp detection for vlan 10. [switcha] vlan 10 [switcha-vlan10] arp detection enable # configure the upstream port as a trusted port and the downstream ports as untrusted ports (a port is an untrusted port by default). [switcha-vlan10] interface gigabitethernet 1/0/3 [switcha-gigabitethe...
Page 239: Table of Contents
I table of contents 1 dhcp relay agent configuration ············································································································1-1 introduction to dhcp relay agent ······································································································...
Page 240
Ii displaying and maintaining bootp client configuration·······································································4-2 bootp client configuration example····································································································4-3.
Page 241
1-1 this document is organized as follows: z dhcp relay agent configuration z dhcp client configuration z dhcp snooping configuration z bootp client configuration 1 dhcp relay agent configuration when configuring the dhcp relay agent, go to these sections for information you are interested in: z int...
Page 242
1-2 no matter whether a relay agent exists or not, the dhcp server and client interact with each other in a similar way . The following describes the forwarding process on the dhcp relay agent. Figure 1-2 dhcp relay agent work process as shown in figure 1-2 , the dhcp relay agent works as follows: 1...
Page 243
1-3 if a client’s requesting message has… handling strategy padding format the dhcp relay agent will… — normal forward the message after adding the option 82 padded in normal format. — verbose forward the message after adding the option 82 padded in verbose format. No option 82 — user-defined forwar...
Page 244
1-4 to do… use the command… remarks enable the dhcp relay agent on the current interface dhcp select relay required with dhcp enabled, interfaces work in the dhcp server mode. If the dhcp client obtains an ip address via the dhcp relay agent, the address pool of the subnet to which the ip address of...
Page 245
1-5 configuring the dhcp relay agent security functions creating static bindings and enabling ip address check the dhcp relay agent can dynamically record clients’ ip-to-mac bindings after clients get ip addresses. It also supports static bindings, that is, you can manually configure ip-to-mac bindi...
Page 246
1-6 z if the server returns a dhcp-ack message or does not return any message within a specified interval, which means the ip address is assignable now, the dhcp relay agent will age out the client entry with this ip address. Z if the server returns a dhcp-nak message, which means the ip address is ...
Page 247
1-7 follow these steps to configure the dhcp relay agent in system view to send a dhcp-release request: to do… use the command… remarks enter system view system-view — configure the dhcp relay agent to send a dhcp-release request dhcp relay release ip client-ip required configuring the dhcp relay ag...
Page 248
1-8 to do… use the command… remarks configure the padding content for the circuit id sub-option dhcp relay information circuit-id string circuit-id optional by default, the padding content depends on the padding format of option 82. Configure user-defined option 82 configure the padding content for ...
Page 249
1-9 dhcp relay agent configuration examples dhcp relay agent configuration example network requirements as shown in figure 1-3 , dhcp clients reside on network 10.10.1.0/24. The ip address of the dhcp server is 10.1.1.1/24. Because the dhcp clients reside on a different network with the dhcp server,...
Page 250
1-10 because the dhcp relay agent and server are on different subnets, you need to configure a static route or dynamic routing protocol to make them reachable to each other. Dhcp relay agent option 82 support configuration example network requirements z as shown in figure 1-3 , enable option 82 on t...
Page 251
1-11 troubleshooting dhcp relay agent configuration symptom dhcp clients cannot obtain any configuration parameters via the dhcp relay agent. Analysis some problems may occur with the dhcp relay agent or server configuration. Enable debugging and execute the display command on the dhcp relay agent t...
Page 252: Dhcp Client Configuration
2-1 2 dhcp client configuration when configuring the dhcp client, go to these sections for information you are interested in: z introduction to dhcp client z enabling the dhcp client on an interface z displaying and maintaining the dhcp client z dhcp client configuration example when multiple vlan i...
Page 253
2-2 z an interface can be configured to acquire an ip address in multiple ways, but these ways are mutually exclusive. The latest configuration will overwrite the previous one. Z after the dhcp client is enabled on an interface, no secondary ip address can be configured for the interface. Z if the i...
Page 254: Dhcp Snooping Configuration
3-1 3 dhcp snooping configuration when configuring dhcp snooping, go to these sections for information you are interested in: z dhcp snooping overview z configuring dhcp snooping basic functions z configuring dhcp snooping to support option 82 z displaying and maintaining dhcp snooping z dhcp snoopi...
Page 255
3-2 recording ip-to-mac mappings of dhcp clients dhcp snooping reads dhcp-request messages and dhcp-ack messages from trusted ports to record dhcp snooping entries, including mac addresses of clients, ip addresses obtained by the clients, ports that connect to dhcp clients, and vlans to which the po...
Page 256
3-3 figure 3-2 configure trusted ports in a cascaded network table 3-1 describes roles of the ports shown in figure 3-2 . Table 3-1 roles of ports device untrusted port trusted port disabled from recording binding entries trusted port enabled to record binding entries switch a gigabitethernet 1/0/1 ...
Page 257
3-4 if a client’s requesting message has… handling strategy padding format the dhcp snooping device will… normal forward the message after replacing the original option 82 with the option 82 padded in normal format. Verbose forward the message after replacing the original option 82 with the option 8...
Page 258
3-5 z you need to specify the ports connected to the authorized dhcp servers as trusted to ensure that dhcp clients can obtain valid ip addresses. The trusted port and the port connected to the dhcp client must be in the same vlan. Z currently, you can specify layer 2 ethernet interfaces and layer 2...
Page 261
3-8 z on gigabitethernet 1/0/2, configure the padding content for the circuit id sub-option as company001 and for the remote id sub-option as device001. Z on gigabitethernet 1/0/3, configure the padding format as verbose, access node identifier as sysname, and code type as ascii for option 82. Z swi...
Page 262: Bootp Client Configuration
4-1 4 bootp client configuration while configuring a bootp client, go to these sections for information you are interested in: z introduction to bootp client z configuring an interface to dynamically obtain an ip address through bootp z displaying and maintaining bootp client configuration if severa...
Page 263: Through Bootp
4-2 obtaining an ip address dynamically a dhcp server can take the place of the bootp server in the following dynamic ip address acquisition. A bootp client dynamically obtains an ip address from a bootp server in the following steps: 1) the bootp client broadcasts a bootp request, which contains it...
Page 264
4-3 bootp client configuration example network requirement switch a’s port belonging to vlan 1 is connected to the lan. Vlan-interface 1 obtains an ip address from the dhcp server by using bootp. Figure 4-1 network diagram for bootp client configuration example dhcp server gateway a wins server 10.1...
Page 265: Table of Contents
I table of contents 1 ftp configuration ·····································································································································1-1 ftp overview ··············································································································...
Page 266: Ftp Configuration
1-1 1 ftp configuration when configuring ftp, go to these sections for information you are interested in: z ftp overview z configuring the ftp client z configuring the ftp server z displaying and maintaining ftp ftp overview introduction to ftp the file transfer protocol (ftp) is an application laye...
Page 267: Configuring The Ftp Client
1-2 table 1-1 configuration when the device serves as the ftp client device configuration remarks device (ftp client) use the ftp command to establish the connection to the remote ftp server if the remote ftp server supports anonymous ftp, the device can log in to it directly; if not, the device mus...
Page 268
1-3 only users with the manage level can use the ftp command to log in to an ftp server, enter ftp client view, and execute directory and file related commands. However, whether the commands can be executed successfully depends on the authorizations of the ftp server. Establishing an ftp connection ...
Page 270
1-5 download a file from the ftp server under the authorized directory of the ftp server by following these steps: 1) use the dir or ls command to display the directory and the location of the file on the ftp server. 2) delete useless files for effective use of the storage space. 3) set the file tra...
Page 271
1-6 follow the step below to use another username to log in to the ftp server: to do… use the command… remarks use another username to relog in after successfully logging in to the ftp server user username [ password ] optional maintaining and debugging an ftp connection after a device serving as th...
Page 272
1-7 z device downloads a startup file from pc for device upgrade, and uploads the configuration file to pc for backup. Z on pc, an ftp user account has been created for the ftp client, with the username being abc and the password being pwd. Figure 1-2 network diagram for ftping a startup file from a...
Page 273: Configuring The Ftp Server
1-8 boot-loader file newest.Bin main # reboot the device, and the startup file is updated at the system reboot. Reboot the startup file used for the next startup must be saved under the root directory of the storage medium. You can copy or move a file to the root directory of the storage medium. For...
Page 274
1-9 to do… use the command… remarks manually release the ftp connection established with the specified username free ftp user username optional available in user view configuring authentication and authorization on the ftp server to allow an ftp user to access certain directories on the ftp server, ...
Page 275
1-10 z for more information about the local-user, password, service-type ftp, and authorization-attribute commands, refer to aaa commands. Z when the device serves as the ftp server, if the client is to perform the write operations (upload, delete, create, and delete for example) on the device’s fil...
Page 276
1-11 0 drw- - dec 07 2005 10:00:57 filename 1 drw- - jan 02 2006 14:27:51 logfile 2 -rw- 1216 jan 02 2006 14:28:59 config.Cfg 3 -rw- 1216 jan 02 2006 16:27:26 back.Cfg 97920 kb total (2511 kb free) delete /unreserved flash:/back.Cfg 2) configure the pc (ftp client) # log in to the ftp server through...
Page 277
1-12 displaying and maintaining ftp to do… use the command… remarks display the configuration of the ftp client display ftp client configuration available in any view display the configuration of the ftp server display ftp-server available in any view display detailed information about logged-in ftp...
Page 278: Tftp Configuration
2-1 2 tftp configuration when configuring tftp, go to these sections for information you are interested in: z tftp overview z configuring the tftp client z displaying and maintaining the tftp client z tftp client configuration example tftp overview introduction to tftp the trivial file transfer prot...
Page 279: Configuring The Tftp Client
2-2 when the device serves as the tftp client, you need to perform the following configuration: table 2-1 configuration when the device serves as the tftp client device configuration remarks device (tftp client) z configure the ip address and routing function, and ensure that the route between the d...
Page 280
2-3 z if you use the tftp client source command and the tftp command to specify a source address respectively, the source address configured with the tftp command is used to communicate with a tftp server. The source address specified with the tftp client source command is valid for all tftp connect...
Page 281
2-4 tftp client configuration example network requirements z as shown in figure 2-2 , use a pc as the tftp server and device as the tftp client. Their ip addresses are 1.2.1.1/16 and 1.1.1.1/16 respectively. An available route exists between device and pc. Z device downloads a startup file from pc f...
Page 282
2-5 the startup file used for the next startup must be saved under the root directory of the storage medium. You can copy or move a file to the root directory of the storage medium. For the details of the boot-loader command, refer to device management commands..
Page 283: Table of Contents
I table of contents 1 ip routing basics configuration ·············································································································1-1 ip routing and routing table·········································································································...
Page 284: Ip Routing and Routing Table
1-1 1 ip routing basics configuration go to these sections for information you are interested in: z ip routing and routing table z displaying and maintaining a routing table the term “router” in this document refers to a router in a generic sense or a layer 3 switch. Ip routing and routing table rou...
Page 285
1-2 made of a certain number of consecutive 1s. It can be expressed in dotted decimal format or by the number of the 1s. Z outbound interface: specifies the interface through which the ip packets are to be forwarded. Z ip address of the next hop: specifies the address of the next router on the path....
Page 287: Table of Contents
I table of contents 1 static routing configuration····················································································································1-1 introduction ·····················································································································...
Page 288: Static Routing Configuration
1-1 1 static routing configuration when configuring a static route, go to these sections for information you are interested in: z introduction z configuring a static route z displaying and maintaining static routes z static route configuration example the term “router” in this document refers to a r...
Page 289: Configuring A Static Route
1-2 application environment of static routing before configuring a static route, you need to know the following concepts: 1) destination address and mask in the ip route-static command, an ipv4 address is in dotted decimal format and a mask can be either in dotted decimal format or in the form of ma...
Page 290
1-3 to do… use the command… remarks configure the default preference for static routes ip route-static default-preference default-preference-value optional 60 by default z when configuring a static route, the static route does not take effect if you specify the next hop address first and then config...
Page 291
1-4 figure 1-1 network diagram for static route configuration configuration procedure 1) configuring ip addresses for interfaces (omitted) 2) configuring static routes # configure a default route on switch a. System-view [switcha] ip route-static 0.0.0.0 0.0.0.0 1.1.4.2 # configure two static routes...
Page 292
1-5 127.0.0.1/32 direct 0 0 127.0.0.1 inloop0 # display the ip routing table of switch b. [switchb] display ip routing-table routing tables: public destinations : 10 routes : 10 destination/mask proto pre cost nexthop interface 1.1.2.0/24 static 60 0 1.1.4.1 vlan500 1.1.3.0/24 static 60 0 1.1.5.6 vl...
Page 293: Table of Contents
I table of contents 1 multicast overview ····································································································································1-1 introduction to multicast ·································································································...
Page 294
Ii configuring igmp report suppression ························································································ 2-17 configuring maximum multicast groups that can be joined on a port······································· 2-17 configuring multicast group replacement··················...
Page 295: Multicast Overview
1-1 1 multicast overview this manual chiefly focuses on the ip multicast technology and device operations. Unless otherwise stated, the term “multicast” in this document refers to ip multicast. Introduction to multicast as a technique coexisting with unicast and broadcast, the multicast technique ef...
Page 296
1-2 figure 1-1 unicast transmission source receiver receiver receiver host a host b host c host d host e packets for host b packets for host d packets for host e ip network assume that host b, host d and host e need the information. A separate transmission channel needs to be established from the in...
Page 297
1-3 figure 1-2 broadcast transmission assume that only host b, host d, and host e need the information. If the information is broadcast to the subnet, host a and host c also receive it. In addition to information security issues, this also causes traffic flooding on the same subnet. Therefore, broad...
Page 298
1-4 figure 1-3 multicast transmission the multicast source (source in the figure) sends only one copy of the information to a multicast group. Host b, host d and host e, which are receivers of the information, need to join the multicast group. The routers on the network duplicate and forward the inf...
Page 299
1-5 manage multicast group memberships on stub subnets with attached group members. A multicast router itself can be a multicast group member. For a better understanding of the multicast concept, you can assimilate multicast transmission to the transmission of tv programs, as shown in table 1-1 . Ta...
Page 300: Multicast Models
1-6 multicast models based on how the receivers treat the multicast sources, there are three multicast models: any-source multicast (asm), source-filtered multicast (sfm), and source-specific multicast (ssm). Asm model in the asm model, any sender can send information to a multicast group as a multi...
Page 301
1-7 multicast addresses to allow communication between multicast sources and multicast group members, network-layer multicast addresses, namely, multicast ip addresses must be provided. In addition, a technique must be available to map multicast ip addresses to link-layer multicast mac addresses. Ip...
Page 302
1-8 address description 224.0.0.7 shared tree (st) routers 224.0.0.8 st hosts 224.0.0.9 routing information protocol version 2 (ripv2) routers 224.0.0.11 mobile agents 224.0.0.12 dynamic host configuration protocol (dhcp) server/relay agent 224.0.0.13 all protocol independent multicast (pim) routers...
Page 303
1-9 multicast protocols z generally, we refer to ip multicast working at the network layer as layer 3 multicast and the corresponding multicast protocols as layer 3 multicast protocols, which include igmp, pim, msdp, and mbgp; we refer to ip multicast working at the data link layer as layer 2 multic...
Page 304
1-10 mature intra-domain multicast routing protocols, protocol independent multicast (pim) is a popular one. Based on the forwarding mechanism, pim comes in two modes – dense mode (often referred to as pim-dm) and sparse mode (often referred to as pim-sm). Z an inter-domain multicast routing protoco...
Page 305
1-11 packets to receivers located in different parts of the network, multicast routers on the forwarding path usually need to forward multicast packets received on one incoming interface to multiple outgoing interfaces. Compared with a unicast model, a multicast model is more complex in the followin...
Page 306: Igmp Snooping Configuration
2-1 2 igmp snooping configuration when configuring igmp snooping, go to the following sections for information you are interested in: z igmp snooping overview z igmp snooping configuration task list z displaying and maintaining igmp snooping z igmp snooping configuration examples z troubleshooting i...
Page 307
2-2 z reducing layer 2 broadcast packets, thus saving network bandwidth. Z enhancing the security of multicast traffic. Z facilitating the implementation of per-host accounting. Basic concepts in igmp snooping igmp snooping related ports as shown in figure 2-2 , router a connects to the multicast so...
Page 308
2-3 aging timers for dynamic ports in igmp snooping and related messages and actions table 2-1 aging timers for dynamic ports in igmp snooping and related messages and actions timer description message before expiry action after expiry dynamic router port aging timer for each dynamic router port, th...
Page 309
2-4 when receiving a membership report a host sends an igmp report to the igmp querier in the following circumstances: z upon receiving an igmp query, a multicast group member host responds with an igmp report. Z when intended to join a multicast group, a host sends an igmp report to the igmp querie...
Page 310
2-5 does not immediately remove the port from the outgoing port list of the forwarding table entry for that group; instead, it resets the aging timer for the port. Upon receiving the igmp leave message from a host, the igmp querier resolves the multicast group address in the message and sends an igm...
Page 311
2-6 table 2-2 describes how an igmp snooping proxy processes igmp messages. Table 2-2 igmp message processing on an igmp snooping proxy igmp message actions general query when receiving an igmp general query, the proxy forwards it to all ports but the receiving port. In addition, the proxy generates...
Page 312
2-7 task remarks proxying configuring a source ip address for the igmp messages sent by the proxy optional configuring a multicast group filter optional configuring the function of dropping unknown multicast data optional configuring igmp report suppression optional configuring maximum multicast gro...
Page 313
2-8 to do... Use the command... Remarks enter system view system-view — enable igmp snooping globally and enter igmp-snooping view igmp-snooping required disabled by default return to system view quit — enter vlan view vlan vlan-id — enable igmp snooping in the vlan igmp-snooping enable required dis...
Page 314
2-9 configuring igmp snooping port functions configuration prerequisites before configuring igmp snooping port functions, complete the following tasks: z enable igmp snooping in the vlan z configure the corresponding port groups. Before configuring igmp snooping port functions, prepare the following...
Page 315
2-10 configuring static ports if all the hosts attached to a port are interested in the multicast data addressed to a particular multicast group or the multicast data that a particular multicast source sends to a particular group, you can configure static (*, g) or (s, g) joining on that port, namel...
Page 316
2-11 z after a port is configured as a simulated member host, the switch responds to igmp general queries by sending igmp reports through that port. Z when the simulated joining function is disabled on a port, the switch sends an igmp leave message through that port. Follow these steps to configure ...
Page 317
2-12 configuring fast leave processing on a port or a group of ports follow these steps to configure fast leave processing on a port or a group of ports: to do... Use the command... Remarks enter system view system-view — interface interface-typeinterface-number enter ethernet interface/layer 2 aggr...
Page 318
2-13 it is meaningless to configure an igmp snooping querier in a multicast network running igmp. Although an igmp snooping querier does not take part in igmp querier elections, it may affect igmp querier elections because it sends igmp general queries with a low source ip address. Configuring igmp ...
Page 319
2-14 to do... Use the command... Remarks configure the maximum response time to igmp general queries igmp-snooping max-response-time interval optional 10 seconds by default configure the igmp last-member query interval igmp-snooping last-member-query-interval interval optional 1 second by default in...
Page 320
2-15 z source ip address for the igmp reports sent by the proxy z source ip address for the igmp leave messages sent by the proxy enabling igmp snooping proxying the igmp snooping proxying function works on a per-vlan basis. After you enable the function in a vlan, the device works as the igmp snoop...
Page 321
2-16 configuring a multicast group filter on an igmp snooping–enabled switch, the configuration of a multicast group allows the service provider to define restrictions on multicast programs available to different users. In an actual application, when a user requests a multicast program, the user’s h...
Page 322
2-17 follow these steps to configure the function of dropping unknown multicast data in a vlan: to do... Use the command... Remarks enter system view system-view — enter vlan view vlan vlan-id — enable the function of dropping unknown multicast data igmp-snooping drop-unknown required disabled by de...
Page 323
2-18 to do... Use the command... Remarks port group view port-group manual port-group-name use either approach configure the maximum number of multicast groups allowed on the port(s) igmp-snooping group-limit limit [ vlan vlan-list ] optional by default, the maximum number of multicast groups allowe...
Page 324
2-19 configuring multicast group replacement on a port or a group of ports follow these steps to configure multicast group replacement on a port or a group of ports: to do... Use the command... Remarks enter system view system-view — interface interface-type interface-number enter ethernet interface...
Page 325
2-20 displaying and maintaining igmp snooping to do... Use the command... Remarks display igmp snooping multicast group information (on a centralized device) display igmp-snooping group [ vlan vlan-id ] [ verbose ] available in any view display the statistics information of igmp messages learned by ...
Page 326
2-21 figure 2-4 network diagram for group policy simulated joining configuration configuration procedure 1) configure ip addresses configure an ip address and subnet mask for each interface as per figure 2-4 . The detailed configuration steps are omitted. 2) configure router a # enable ip multicast ...
Page 327
2-22 # configure a multicast group filter so that the hosts in vlan 100 can join only the multicast group 224.1.1.1. [switcha] acl number 2001 [switcha-acl-basic-2001] rule permit source 224.1.1.1 0 [switcha-acl-basic-2001] quit [switcha] igmp-snooping [switcha-igmp-snooping] group-policy 2001 vlan ...
Page 328
2-23 static port configuration example network requirements z as shown in figure 2-5 , router a connects to a multicast source (source) through gigabitethernet 1/0/2, and to switch a through gigabitethernet 1/0/1. Z igmpv2 is to run on router a, and igmpv2 snooping is to run on switch a, switch b an...
Page 329
2-24 configure an ip address and subnet mask for each interface as per figure 2-5 . The detailed configuration steps are omitted. 2) configure router a # enable ip multicast routing, enable pim-dm on each interface, and enable igmp on gigabitethernet 1/0/1. System-view [routera] multicast routing-en...
Page 330
2-25 [switchc] igmp-snooping [switchc-igmp-snooping] quit # create vlan 100, assign gigabitethernet 1/0/1 through gigabitethernet 1/0/5 to this vlan, and enable igmp snooping in the vlan. [switchc] vlan 100 [switchc-vlan100] port gigabitethernet 1/0/1 to gigabitethernet 1/0/5 [switchc-vlan100] igmp-...
Page 331
2-26 total 1 ip group(s). Total 1 ip source(s). Total 1 mac group(s). Port flags: d-dynamic port, s-static port, c-copy port subvlan flags: r-real vlan, c-copy vlan vlan(id):100. Total 1 ip group(s). Total 1 ip source(s). Total 1 mac group(s). Router port(s):total 1 port. Ge1/0/2 (d) ( 00:01:23 ) ip...
Page 332
2-27 figure 2-6 network diagram for igmp snooping querier configuration configuration procedure 1) configure switch a # enable igmp snooping globally. System-view [switcha] igmp-snooping [switcha-igmp-snooping] quit # create vlan 100 and assign gigabitethernet 1/0/1 through gigabitethernet 1/0/3 to ...
Page 333
2-28 [switchb-vlan100] port gigabitethernet 1/0/1 to gigabitethernet 1/0/4 # enable igmp snooping and the function of dropping unknown multicast traffic in vlan 100. [switchb-vlan100] igmp-snooping enable [switchb-vlan100] igmp-snooping drop-unknown [switchb-vlan100] quit configurations on switch c ...
Page 334
2-29 figure 2-7 network diagram for igmp snooping proxying configuration source router a igmp querier switch a proxy & querier receiver host b host a host c 1.1.1.1/24 ge1/0/4 ge1/0/2 ge1/0/3 ge1/0/1 ge1/0/1 10.1.1.1/24 ge1/0/2 1.1.1.2/24 receiver configuration procedure 1) configure ip addresses fo...
Page 335
2-30 4) verify the configuration after the configuration is completed, host a and host b send igmp join messages for group 224.1.1.1. Receiving the messages, switch a sends a join message for the group out port gigabitethernet 1/0/1 (a router port) to router a. Use the display igmp-snooping group co...
Page 336
2-31 total 1 ip group(s). Total 1 ip source(s). Total 1 mac group(s). Port flags: d-dynamic port, s-static port, c-copy port subvlan flags: r-real vlan, c-copy vlan vlan(id):100. Total 1 ip group(s). Total 1 ip source(s). Total 1 mac group(s). Router port(s):total 1 port. Ge1/0/1 (d) ( 00:01:23 ) ip...
Page 337
2-32 z the function of dropping unknown multicast data is not enabled, so unknown multicast data is flooded. Solution 1) use the display acl command to check the configured acl rule. Make sure that the acl rule conforms to the multicast group policy to be implemented. 2) use the display this command...
Page 338: Multicast Vlan Configuration
2-1 3 multicast vlan configuration when configuring multicast vlan, go to these sections for information you are interested in: z introduction to multicast vlan z multicast vlan configuration task list z configuring multicast vlan z displaying and maintaining multicast vlan z multicast vlan configur...
Page 339: Configuring Multicast Vlan
2-2 figure 3-2 port-based multicast vlan after the configuration, upon receiving an igmp message on a user port, switch a tags the message with the multicast vlan id and relays it to the igmp querier, so that igmp snooping can uniformly manage the router ports and member ports in the multicast vlan....
Page 340
2-3 z a user port can be configured as a multicast vlan port only if it is of the ethernet, or layer 2 aggregate interface type. Z configurations made in ethernet interface view are effective only for the current port; configurations made in layer 2 aggregate interface view are effective only for th...
Page 341
2-4 for details about the port link-type, port hybrid pvid vlan, and port hybrid vlan commands, refer to vlan commands. Configuring multicast vlan ports in this approach, you need to configure a vlan as a multicast vlan and then assign user ports to this multicast vlan by either adding the user port...
Page 342
2-5 z the vlan to be configured as a multicast vlan must exist. Z a port can belong to only one multicast vlan. Displaying and maintaining multicast vlan to do… use the command… remarks display information about a multicast vlan display multicast-vlan [ vlan-id ] available in any view multicast vlan...
Page 343
2-6 network diagram figure 3-3 network diagram for port-based multicast vlan configuration configuration procedure 1) configure ip addresses configure the ip address and subnet mask for each interface as per figure 3-3. The detailed configuration steps are omitted here. 2) configure router a # enabl...
Page 344
2-7 # create vlan 2 and enable igmp snooping in the vlan. [switcha] vlan 2 [switcha-vlan2] igmp-snooping enable [switcha-vlan2] quit the configuration for vlan 3 and vlan 4 is similar. The detailed configuration steps are omitted. # configure gigabitethernet 1/0/2 as a hybrid port. Configure vlan 2 ...
Page 345
2-8 total 1 ip source(s). Total 1 mac group(s). Router port(s):total 1 port. Ge1/0/1 (d) ip group(s):the following ip group(s) match to one mac group. Ip group address:224.1.1.1 (0.0.0.0, 224.1.1.1): host port(s):total 3 port. Ge1/0/2 (d) ge1/0/3 (d) ge1/0/4 (d) mac group(s): mac group address:0100-...
Page 346: Table of Contents
I table of contents 1 qos overview ············································································································································1-1 introduction to qos ·····································································································...
Page 347
Ii configure wrr queuing·················································································································5-5 configuring sp+wrr queuing ·······································································································5-6 6 traffic filtering confi...
Page 348: Qos Overview
1-1 1 qos overview this chapter covers the following topics: z introduction to qos z qos service models z qos techniques overview introduction to qos in data communications, quality of service (qos) is the ability of a network to provide differentiated service guarantees for diverse traffic in terms...
Page 349: Qos Techniques Overview
1-2 small-sized or edge networks, but not large-sized networks, for example, the core layer of the internet, where billions of flows are present. Diffserv model the differentiated service (diffserv) model is a multiple-service model that can satisfy diverse qos requirements. Unlike intserv, diffserv...
Page 350: Qos Policy Configuration
2-1 2 qos policy configuration when configuring a qos policy, go to these sections for information you are interested in: z qos policy overview z configuring a qos policy z applying the qos policy z displaying and maintaining qos policies qos policy overview a qos policy involves three components: c...
Page 352
2-3 form description source-mac mac-address specifies to match the packets with a specified source mac address. To successfully execute the traffic behavior associated with a traffic class that uses the and operator, define only one if-match clause for any of the following match criteria and input o...
Page 353: Applying The Qos Policy
2-4 to do… use the command… remarks specify the traffic behavior for a class in the policy classifier tcl-name behavior behavior-name required if an acl is referenced by a qos policy for defining traffic match criteria, , packets matching the acl are organized as a class and the behavior defined in ...
Page 354
2-5 [sysname-gigabitethernet1/0/1] qos apply policy test_policy inbound displaying and maintaining qos policies to do… use the command… remarks display traffic class information display traffic classifier user-defined [ tcl-name ] available in any view display traffic behavior configuration informat...
Page 355: Priority Mapping Overview
3-1 3 priority mapping configuration when configuring priority mapping, go to these sections for information you are interested in: z priority mapping overview z priority mapping configuration tasks z configuring priority mapping z displaying and maintaining priority mapping z priority mapping confi...
Page 356
3-2 priority mapping tables priority mapping is implemented with priority mapping tables. The device provides various types of priority mapping tables, or rather, priority mappings. By looking up a priority mapping table, the device decides which priority value is to assign to a packet for subsequen...
Page 357: Configuring Priority Mapping
3-3 figure 3-1 priority mapping procedure for an ethernet packet which priority is trusted on the port? Receive a packet on a port use the port priority as the 802.1p priority for priority mapping n look up the dot1p- dscp and dot1p-lp mapping tables mark the packet with new dscp precedence and loca...
Page 360
3-6 figure 3-2 network diagram for priority mapping table and priority marking configuration configuration procedure 1) configure trusting port priority # set the port priority of gigabitethernet 1/0/1 to 3. System-view [device] interface gigabitethernet 1/0/1 [device-gigabitethernet1/0/1] qos prior...
Page 361: Line Rate Configuration
4-1 4 line rate configuration when configuring traffic classification, traffic policing, and traffic shaping, go to these sections for information you are interested in: z line rate z line rate configuration line rate the line rate of a physical interface specifies the maximum rate for forwarding pa...
Page 362
4-2 to do… use the command… remarks enter system view system-view — enter interface view interface interface-type interface-number enter interface view or port group view enter port group view port-group manual port-group-name use either command settings in interface view take effect on the current ...
Page 363
5-1 5 congestion management configuration when configuring congestion management, go to these sections for information you are interested in: z congestion management overview z congestion management configuration methods congestion management overview causes, impacts, and countermeasures of congesti...
Page 364
5-2 queue scheduling processes packets by their priorities, preferentially forwarding high-priority packets. In the following section, strict priority (sp) queuing, weighted fair queuing (wfq), and sp+wrr queuing are introduced. Sp queuing sp queuing is specially designed for mission-critical applic...
Page 365
5-3 figure 5-3 schematic diagram for wrr queuing queue 0 weight 1 queue 1 weight 2 queue 2 weight 5 queue 3 weight 7 packets to be sent through this port sent packets interface queue scheduling sending queue packet classification assume there are four output queues on a port. Wrr assigns each queue ...
Page 366
5-4 sp+wrr queuing sp+wrr queuing uses one sp queuing group and two wrr queuing groups. The switch uses wrr to schedule queues in each wrr queuing group according to their weights, and then uses sp queuing to schedule the dequeued packets together with the packets in the sp queuing group. For exampl...
Page 367
5-5 to do… use the command… remarks configure sp queuing undo qos wrr optional the default queuing algorithm on an interface is sp queuing. Configuration example 1) network requirements configure gigabitethernet 1/0/1 to adopt sp queuing. 2) configuration procedure # enter system view system-view # ...
Page 368
5-6 z assign queue 0 and queue 1 to the wrr group 1, with the weight of 10 and 20 respectively. Z assign queue 2 and queue 3 to the wrr group 2, with the weight of 30 and 50 respectively. 2) configuration procedure # enter system view. System-view # configure wrr queuing on gigabitethernet 1/0/1. [s...
Page 369
5-7 system-view # enable the sp+wrr queue scheduling algorithm on gigabitethernet1/0/1. [sysname] interface gigabitethernet 1/0/1 [sysname-gigabitethernet1/0/1] qos wrr 0 group sp [sysname-gigabitethernet1/0/1] qos wrr 1 group 1 weight 20 [sysname-gigabitethernet1/0/1] qos wrr 2 group 2 weight 10 [s...
Page 370: Traffic Filtering Overview
6-1 6 traffic filtering configuration when configuring traffic filtering, go to these sections for information you are interested in: z traffic filtering overview z configuring traffic filtering z traffic filtering configuration example traffic filtering overview you can filter in or filter out a cl...
Page 371
6-2 to do… use the command… remarks associate the class with the traffic behavior in the qos policy classifier tcl-name behavior behavior-name — exit policy view quit — apply the qos policy to an interface see applying the qos policy — display the traffic filtering configuration display traffic beha...
Page 372
6-3 [devicea-behavior-behavior_1] filter deny [devicea-behavior-behavior_1] quit # create a policy named policy, and associate class classifier_1 with behavior behavior_1 in the policy. [devicea] qos policy policy [devicea-qospolicy-policy] classifier classifier_1 behavior behavior_1 [devicea-qospol...
Page 373: Traffic Redirecting Overview
7-1 7 traffic redirecting configuration when configuring traffic redirecting, go to these sections for information you are interested in: z traffic redirecting overview z configuring traffic redirecting traffic redirecting overview traffic redirecting traffic redirecting is the action of redirecting...
Page 374: Appendix
8-1 8 appendix this chapter includes these sections: z appendix a default priority mapping tables z appendix b introduction to packet precedences appendix a default priority mapping tables for the default dot1p-dot1p and dscp-dscp priority mapping tables, an input value yields a target value equal t...
Page 375
8-2 input priority value dscp-lp mapping dscp-dot1p mapping 40 to 47 5 5 48 to 55 6 6 56 to 63 7 7 appendix b introduction to packet precedences ip precedence and dscp values figure 8-1 tos and ds fields as shown in figure 8-1 , the tos field in the ip header contains eight bits. The first three bit...
Page 376
8-3 dscp value (decimal) dscp value (binary) description 14 001110 af13 18 010010 af21 20 010100 af22 22 010110 af23 26 011010 af31 28 011100 af32 30 011110 af33 34 100010 af41 36 100100 af42 38 100110 af43 8 001000 cs1 16 010000 cs2 24 011000 cs3 32 100000 cs4 40 101000 cs5 48 110000 cs6 56 111000 ...
Page 377
8-4 figure 8-3 802.1q tag header table 8-5 description on 802.1p priority 802.1p priority (decimal) 802.1p priority (binary) description 0 000 best-effort 1 001 background 2 010 spare 3 011 excellent-effort 4 100 controlled-load 5 101 video 6 110 voice 7 111 network-management.
Page 378: Table of Contents
I table of contents 1 802.1x configuration·································································································································1-1 802.1x overview··············································································································...
Page 379: 802.1X Configuration
1-1 1 802.1x configuration this chapter includes these sections: z 802.1x overview z 802.1x configuration task list z 802.1x configuration example z guest vlan and vlan assignment configuration example z acl assignment configuration example 802.1x overview the 802.1x protocol was proposed by ieee 80...
Page 380
1-2 z device, residing at the other end of the lan segment, is the entity that authenticates connected clients. Device is usually an 802.1x-enabled network device and provides access ports for clients to the lan. Z server is the entity that provides authentication services to device. Server, normall...
Page 381
1-3 figure 1-2 authorized/unauthorized status of a controlled port you can set the authorization mode of a specified port to control the port authorization status. The authorization modes include: z authorized-force: places the port in the authorized state, allowing users on the port to access the n...
Page 382
1-4 figure 1-3 eapol packet format z pae ethernet type: protocol type. It takes the value 0x888e. Z protocol version: version of the eapol protocol supported by the eapol packet sender. Z type: type of the eapol packet. Table 1-1 lists the types that the device currently supports. Table 1-1 types of...
Page 383
1-5 an eap packet of the type of request or response has a data field in the format shown in figure 1-5 . The type field indicates the eap authentication type. A value of 1 represents identity, indicating that the packet is for querying the identity of the client. A value of 4 represents md5-challen...
Page 384
1-6 unsolicited triggering of a client a client initiates authentication by sending an eapol-start packet to the device. The destination address of the packet is 01-80-c2-00-00-03, the multicast address specified by the ieee 802.1x protocol. Some devices in the network may not support multicast pack...
Page 385
1-7 figure 1-8 802.1x authentication procedure in eap relay mode eapol eapor eapol-start eap-request / identity eap-response / identity eap-request / md5 challenge eap-success eap-response / md5 challenge radius access-request (eap-response / identity) radius access-challenge (eap-request / md5 chal...
Page 386
1-8 8) after receiving the eap-response/md5 challenge packet, the device relays the packet in a radius access-request packet to the authentication server. 9) when receiving the radius access-request packet, the radius server compares the password information encapsulated in the packet with that gene...
Page 387
1-9 figure 1-9 message exchange in eap termination mode eapol eapor eapol-start eap-request / identity eap-response / identity eap-request / md5 challenge eap-success eap-response / md5 challenge handshake request [ eap-request / identity ] handshake response [ eap-response / identity ] eapol-logoff...
Page 388
1-10 z username request timeout timer (tx-period): this timer is triggered by the device in two cases. The first case is when the client requests for authentication. The device starts this timer when it sends an eap-request/identity packet to a client. If it receives no response before this timer ex...
Page 389
1-11 the assigned vlan neither changes nor affects the configuration of a port. However, as the assigned vlan has higher priority than the initial vlan of the port, it is the assigned vlan that takes effect after a user passes authentication. After the user logs off, the port returns to the initial ...
Page 390
1-12 similar to a guest vlan, an auth-fail vlan can be a port-based auth-fail vlan (pafv) or a mac-based auth-fail vlan (mafv), depending on the port access control method. Currently, on the switch, an auth-fail vlan can be only a port-based auth-fail vlan (pafv). Pafv refers to the auth-fail vlan c...
Page 391: 802.1X Basic Configuration
1-13 task remarks enabling the quiet timer optional enabling the re-authentication function optional configuring a guest vlan optional configuring an auth-fail vlan optional 802.1x basic configuration configuration prerequisites 802.1x provides a method for implementing user identity authentication....
Page 394: Enabling The Quiet Timer
1-16 z you need to disable proxy detection before disabling the online user handshake function. Z some 802.1x clients do not support exchanging handshake packets with the device. In this case, you need to disable the online user handshake function on the device; otherwise the device will tear down t...
Page 395: Configuring A Guest Vlan
1-17 to do… use the command… remarks enter system view system-view — enable the quiet timer dot1x quiet-period required disabled by default enabling the re-authentication function if periodic re-authentication is enabled on a port, the device will re-authenticate online users on the port at the inte...
Page 396
1-18 z to configure a port-based guest vlan, make sure that the port access control method is portbased, and the 802.1x multicast trigger function is enabled. Configuration procedure follow these steps to configure a guest vlan: to do… use the command… remarks enter system view system-view — in syst...
Page 397: 802.1X Configuration Example
1-19 to do… use the command… remarks enter ethernet interface view interface interface-type interface-number — configure the auth-fail vlan for the port dot1x auth-fail vlan authfail-vlan-id required by default, a port is configured with no auth-fail vlan. Different ports can be configured with diff...
Page 398
1-20 z set the username of the 802.1x user as localuser and the password as localpass and specify to use clear text mode. Enable the idle cut function to log the user off whenever the user remains idle for over 20 minutes. Figure 1-10 network diagram for 802.1x configuration configuration procedure ...
Page 399
1-21 [switch-radius-radius1] key authentication name # specify the shared key for the device to exchange packets with the accounting server. [switch-radius-radius1] key accounting money # set the interval for the device to retransmit packets to the radius server and the maximum number of transmissio...
Page 400
1-22 guest vlan and vlan assignment configuration example network requirements as shown in figure 1-11 : z a host is connected to port gigabitethernet 1/0/2 of the device and must pass 802.1x authentication to access the internet. Gigabitethernet 1/0/2 is in vlan 1. Z the authentication server runs ...
Page 401
1-23 figure 1-12 network diagram with the port in the guest vlan figure 1-13 network diagram after the client passes authentication configuration procedure z the following configuration procedure uses many aaa/radius commands. For detailed configuration of these commands, refer to aaa configuration....
Page 402
1-24 [switch-radius-2000] primary authentication 10.11.1.1 1812 [switch-radius-2000] primary accounting 10.11.1.1 1813 [switch-radius-2000] key authentication abc [switch-radius-2000] key accounting abc [switch-radius-2000] user-name-format without-domain [switch-radius-2000] quit # configure authen...
Page 403
1-25 z configure the radius server to assign acl 3000. Z enable 802.1x authentication on port gigabitethernet 1/0/1 of the switch, and configure acl 3000. After the host passes 802.1x authentication, the radius server assigns acl 3000 to port gigabitethernet 1/0/1. As a result, the host can access t...
Page 404
1-26 after logging in successfully, a user can use the ping command to verify whether the acl 3000 assigned by the radius server functions. C:\>ping 10.0.0.1 pinging 10.0.0.1 with 32 bytes of data: request timed out. Request timed out. Request timed out. Request timed out. Ping statistics for 10.0.0...
Page 405: Table of Contents
I table of contents 1 aaa configuration ····································································································································1-1 introduction to aaa ········································································································...
Page 406
Ii troubleshooting aaa ····························································································································1-38 troubleshooting radius ··············································································································1-38.
Page 407: Aaa Configuration
1-1 1 aaa configuration this chapter includes these sections: z introduction to aaa z introduction to radius z protocols and standards z aaa configuration task list z configuring aaa z configuring radius z aaa configuration examples z troubleshooting aaa introduction to aaa authentication, authoriza...
Page 408: Introduction to Radius
1-2 z authorization: grants different users different rights. For example, a user logging into the server can be granted the permission to access and print the files in the server. Z accounting: records all network service usage information of users, including the service type, start and end time, a...
Page 409
1-3 figure 1-2 radius server components z users: stores user information such as the usernames, passwords, applied protocols, and ip addresses. Z clients: stores information about radius clients, such as the shared keys and ip addresses. Z dictionary: stores information about the meanings of radius ...
Page 410
1-4 1) the host initiates a connection request carrying the username and password to the radius client. 2) having received the username and password, the radius client sends an authentication request (access-request) to the radius server, with the user password encrypted by using the message-digest ...
Page 411
1-5 code packet type description 2 access-accept from the server to the client. If all the attribute values carried in the access-request are acceptable, that is, the authentication succeeds, the server sends an access-accept response. 3 access-reject from the server to the client. If any attribute ...
Page 412
1-6 no. Attribute no. Attribute 6 service-type 50 acct-multi-session-id 7 framed-protocol 51 acct-link-count 8 framed-ip-address 52 acct-input-gigawords 9 framed-ip-netmask 53 acct-output-gigawords 10 framed-routing 54 (unassigned) 11 filter-id 55 event-timestamp 12 framed-mtu 56-59 (unassigned) 13 ...
Page 413: Protocols and Standards
1-7 no. Attribute no. Attribute 42 acct-input-octets 89 (unassigned) 43 acct-output-octets 90 tunnel-client-auth-id 44 acct-session-id 91 tunnel-server-auth-id the attribute types listed in table 1-2 are defined by rfc 2865, rfc 2866, rfc 2867, and rfc 2868. Extended radius attributes the radius pro...
Page 414: Aaa Configuration Task List
1-8 aaa configuration task list the basic procedure to configure aaa is as follows: 1) configure the required aaa schemes. Z local authentication: configure local users and related attributes, including usernames and passwords of the users to be authenticated. Z remote authentication: configure the ...
Page 415: Configuring Aaa
1-9 radius configuration task list task remarks creating a radius scheme required specifying the radius authentication/authorization servers required specifying the radius accounting servers and relevant parameters optional setting the shared key for radius packets required setting the upper limit o...
Page 416
1-10 for the nas, each user belongs to an isp domain. Up to 16 isp domains can be configured on a nas. If a user does not provide the isp domain name, the system considers that the user belongs to the default isp domain. Follow these steps to create an isp domain: to do… use the command… remarks ent...
Page 417
1-11 a self-service radius server, for example intelligent management center (imc), is required for the self-service server localization function to work. With the self-service function, a user can manage and control his or her accounting information or card number. A server with self-service softwa...
Page 419
1-13 1) determine the access mode or service type to be configured. With aaa, you can configure an authorization scheme specifically for each access mode and service type, limiting the authorization protocols that can be used for access. 2) determine whether to configure an authorization method for ...
Page 420
1-14 aaa supports the following accounting methods: z no accounting: the system does not perform accounting for the users. Z local accounting: local accounting is implemented on the access device. It is for collecting statistics on the number of users and controlling the number of local user connect...
Page 421
1-15 z with the accounting optional command configured, a user that would be otherwise disconnected can still use the network resources even when no accounting server is available or communication with the current accounting server fails. Z the local accounting is not used for accounting implementat...
Page 423
1-17 depends on the level of the user interface. For an ssh user using public key authentication, the commands that can be used depend on the level configured on the user interface. For details about authentication method and commands accessible to user interface, refer to login configuration. Z bin...
Page 424: Configuring Radius
1-18 access device can obtain the nas id by the access vlan of the user and then send the nas id to the radius server through the nas-identifier attribute. Follow these steps to configure a nas id-vlan binding: to do… use the command… remarks enter system view system-view — create a nas id profile a...
Page 425
1-19 when there are users online, you cannot modify radius parameters other than the number of retransmission attempts and the timers. Creating a radius scheme before performing other radius configurations, follow these steps to create a radius scheme and enter radius scheme view: to do… use the com...
Page 426
1-20 z it is recommended to specify only the primary radius authentication/authorization server if backup is not required. Z if both the primary and secondary authentication/authorization servers are specified, the secondary one is used when the primary one is unreachable. Z in practice, you may spe...
Page 427
1-21 z it is recommended to specify only the primary radius accounting server if backup is not required. Z if both the primary and secondary accounting servers are specified, the secondary one is used when the primary one is not reachable. Z in practice, you can specify two radius servers as the pri...
Page 428
1-22 to retransmit the radius request. If the number of transmission attempts exceeds the specified limit but it still receives no response, it considers that the authentication has failed. Follow these steps to set the upper limit of radius request retransmission attempts: to do… use the command… r...
Page 429
1-23 when both the primary and secondary servers are available, the device sends request packets to the primary server. Once the primary server fails, the primary server turns into the state of block, and the device turns to the secondary server. In this case: z if the secondary server is available,...
Page 431
1-25 follow these steps to specify the source ip address for radius packets to be sent: to do… use the command… remarks enter system view system-view — radius nas-ip ip-address specify the source ip address for radius packets to be sent radius scheme radius-scheme-name nas-ip ip-address required use...
Page 432
1-26 to do… use the command… remarks set the quiet timer for the primary server timer quiet minutes optional 5 minutes by default set the real-time accounting interval timer realtime-accounting minutes optional 12 minutes by default z the maximum number of retransmission attempts of radius packets m...
Page 433
1-27 to do… use the command… remarks set the retransmission interval of accounting-on packets accounting-on enable interval seconds optional 3 seconds by default the accounting-on feature needs to cooperate with the h3c imc network management system. Enabling the listening port of the radius client ...
Page 434: Aaa Configuration Examples
1-28 aaa configuration examples aaa for telnet users by separate servers network requirements as shown in figure 1-6 , configure the switch to provide local authentication, local authorization, and radius accounting services to telnet users. The user name and the password for telnet users are both h...
Page 435
1-29 [switch-radius-rd] quit # create a local user named hello. [switch] local-user hello [switch-luser-hello] service-type telnet [switch-luser-hello] password simple hello [switch-luser-hello] authorization-attribute level 3 [switch-luser-hello] quit [switch] domain default enable bbb # configure ...
Page 436
1-30 this example assumes that the radius server runs imc plat 3.20-r2602 or imc uam 3.60-e6102. # add an access device. Log into the imc management platform, select the service tab, and select access service > service configuration from the navigation tree to enter the service configuration page. T...
Page 437
1-31 figure 1-9 add an account for device management 2) configure the switch # configure the ip address of vlan interface 2, through which the ssh user accesses the switch. System-view [switch] interface vlan-interface 2 [switch-vlan-interface2] ip address 192.168.1.70 255.255.255.0 [switch-vlan-int...
Page 438
1-32 [switch-ui-vty0-4] protocol inbound ssh [switch-ui-vty0-4] quit # create radius scheme rad. [switch] radius scheme rad # specify the primary authentication server. [switch-radius-rad] primary authentication 10.1.1.1 1812 # specify the primary accounting server. [switch-radius-rad] primary accou...
Page 439
1-33 z specify that a username sent to the radius server carries the domain name. The username of the user is dot1x@bbb. Z after the host passes authentication, the authentication server assigns the host to vlan 4. Z the host registers a monthly service charging 120 dollars for up to 120 hours per m...
Page 440
1-34 figure 1-11 add an access device # add a charging policy. Select the service tab, and select charging service > charging plans from the navigation tree to enter the charging policy configuration page. Then, click add to enter the add charging plan page and perform the following configurations: ...
Page 441
1-35 z add a service named dot1x auth and set the service suffix to bbb, which indicates the authentication domain for the 802.1x user. With the service suffix configured, you must configure usernames to be sent to the radius service to carry the domain name. Z specify useracct as the charging plan....
Page 442
1-36 figure 1-14 add an access user account 2) configure the switch z configure a radius scheme # create a radius scheme named rad and enter its view. System-view [switch] radius scheme rad # set the server type for the radius scheme. When using the imc server, set the server type to extended. [swit...
Page 443
1-37 # enable 802.1x globally. [switch] dot1x # enable 802.1x for port gigabitethernet1/0/1. [switch] interface gigabitethernet 1/0/1 [switch-gigabitethernet1/0/1] dot1x [switch-gigabitethernet1/0/1] quit # configure the access control method. (optional because the default setting meets the requirem...
Page 444: Troubleshooting Aaa
1-38 total 1 connection matched. As shown above, the authorized vlan field indicates that vlan 4 has been assigned to the user. Troubleshooting aaa troubleshooting radius symptom 1: user authentication/authorization always fails. Analysis: 1) a communication failure exists between the nas and the ra...
Page 445
1-39 2) configuration of the authentication/authorization server and the accounting server are not correct on the nas. For example, one server is configured on the nas to provide all the services of authentication/authorization and accounting, but in fact the services are provided by different serve...
Page 446: Table of Contents
I table of contents 1 pki configuration ······································································································································1-1 introduction to pki·······································································································...
Page 447: Pki Configuration
1-1 1 pki configuration this chapter includes these sections: z introduction to pki z pki configuration task list z displaying and maintaining pki z pki configuration examples z troubleshooting pki introduction to pki this section covers these topics: z pki overview z pki terms z architecture of pki...
Page 448
1-2 cas are trusted by different users in a pki system, the cas will form a ca tree with the root ca at the top level. The root ca has a ca certificate signed by itself while each lower level ca has a ca certificate signed by the ca at the next higher level. Crl an existing certificate may need to b...
Page 449
1-3 ca a ca is a trusted authority responsible for issuing and managing digital certificates. A ca issues certificates, specifies the validity periods of certificates, and revokes certificates as needed by publishing crls. Ra a registration authority (ra) is an extended part of a ca or an independen...
Page 450: Pki Configuration Task List
1-4 2) the ra reviews the identity of the entity and then sends the identity information and the public key with a digital signature to the ca. 3) the ca verifies the digital signature, approves the application, and issues a certificate. 4) the ra receives the certificate from the ca, sends it to th...
Page 451
1-5 the configuration of an entity dn must comply with the ca certificate issue policy. You need to determine, for example, which entity dn parameters are mandatory and which are optional. Otherwise, certificate request may be rejected. Follow these steps to configure an entity dn: to do… use the co...
Page 452: Configuring A Pki Domain
1-6 configuring a pki domain before requesting a pki certificate, an entity needs to be configured with some enrollment information, which is referred to as a pki domain. A pki domain is intended only for convenience of reference by other applications like ike and ssl, and has only local significanc...
Page 455
1-9 z if a pki domain already has a local certificate, creating an rsa key pair will result in inconsistency between the key pair and the certificate. To generate a new rsa key pair, delete the local certificate and then issue the public-key local create command. For information about the public-key...
Page 456
1-10 z if a pki domain already has a ca certificate, you cannot retrieve another ca certificate for it. This is in order to avoid inconsistency between the certificate and registration information due to related configuration changes. To retrieve a new ca certificate, use the pki delete-certificate ...
Page 457: Deleting A Certificate
1-11 to do… use the command… remarks enter system view system-view — enter pki domain view pki domain domain-name — disable crl checking crl check disable required enabled by default return to system view quit — retrieve the ca certificate refer to retrieving a certificate manually required verify t...
Page 460
1-14 in this example, you need to configure these basic attributes on the ca server at first: z nickname: name of the trusted ca. Z subject dn: dn information of the ca, including the common name (cn), organization unit (ou), organization (o), and country (c). The other attributes may be left using ...
Page 461
1-15 it will take a few minutes. Press ctrl+c to abort. Input the bits in the modulus [default = 1024]: generating keys... ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ++++++++++++++++++++++++++++++++++++++ +++++++++++++++++++++++++++++++++++++++++++++++ +++++++++++++++++++++++ z apply...
Page 462
1-16 ou=test cn=myca validity not before: jan 8 09:26:53 2007 gmt not after : jan 8 09:26:53 2008 gmt subject: cn=switch subject public key info: public key algorithm: rsaencryption rsa public key: (1024 bit) modulus (1024 bit): 00d67d50 41046f6a 43610335 ca6c4b11 f8f89138 e4e905bd 43953ba2 623a54c0...
Page 463
1-17 network requirements configure pki entity switch to request a local certificate from the ca server. Figure 1-3 request a certificate from a ca running windows 2003 server configuration procedure 1) configure the ca server z install the certificate server suites from the start menu, select contr...
Page 464
1-18 # configure the name of the trusted ca as myca. [switch-pki-domain-torsa] ca identifier myca # configure the url of the registration server in the format of http://host:port/ certsrv/mscep/mscep.Dll, where host:port indicates the ip address and port number of the ca server. [switch-pki-domain-t...
Page 465
1-19 # use the following command to view information about the local certificate acquired. Display pki certificate local domain torsa certificate: data: version: 3 (0x2) serial number: 48fa0fd9 00000000 000c signature algorithm: sha1withrsaencryption issuer: cn=myca validity not before: nov 21 12:32...
Page 466
1-20 (omitted) you can also use some other display commands to view more information about the ca certificate. See the display pki certificate ca domain command in pki commands. Configuring a certificate attribute-based access control policy network requirements z the client accesses the remote http...
Page 467: Troubleshooting Pki
1-21 [switch-pki-cert-attribute-group-mygroup1] quit # create certificate attribute group mygroup2 and add two attribute rules. The first rule defines that the fqdn of the alternative subject name does not include the string of apple, and the second rule defines that the dn of the certificate issuer...
Page 468
1-22 failed to request a local certificate symptom failed to request a local certificate. Analysis possible reasons include these: z the network connection is not proper. For example, the network cable may be damaged or loose. Z no ca certificate has been retrieved. Z the current key pair has been b...
Page 469: Table of Contents
I table of contents 1 ssl configuration ·····································································································································1-1 ssl overview ··············································································································...
Page 470: Ssl Configuration
1-1 1 ssl configuration this chapter includes these sections: z ssl overview z ssl configuration task list z displaying and maintaining ssl z troubleshooting ssl ssl overview secure sockets layer (ssl) is a security protocol that provides secure connection services for tcp-based application layer pr...
Page 471
1-2 figure 1-1 message integrity verification by a mac algorithm z for details about symmetric key algorithms, asymmetric key algorithm rsa and digital signature, see public key configuration. Z for details about pki, certificate, and ca, see pki configuration. Ssl protocol stack as shown in figure ...
Page 472: Ssl Configuration Task List
1-3 ssl configuration task list different parameters are required on the ssl server and the ssl client. Complete the following tasks to configure ssl: task remarks configuring an ssl server policy required configuring an ssl client policy optional configuring an ssl server policy an ssl server polic...
Page 473
1-4 to do... Use the command... Remarks number of cached sessions, z 3600 seconds for the caching timeout time. Enable certificate-based ssl client authentication client-verify enable optional not enabled by default z if you enable client authentication here, you must request a local certificate for...
Page 474
1-5 figure 1-3 network diagram for ssl server policy configuration configuration procedure 1) configure the https server (device) # create a pki entity named en, and configure the common name as http-server1 and the fqdn as ssl.Security.Com. System-view [device] pki entity en [device-pki-entity-en] ...
Page 475
1-6 [device-ssl-server-policy-myssl]quit # configure https service to use ssl server policy myssl. [device] ip https ssl-server-policy myssl # enable https service. [device] ip https enable # create a local user named usera, and set the password to 123 and service type to telnet. [device] local-user...
Page 476: Troubleshooting Ssl
1-7 to do… use the command… remarks create an ssl client policy and enter its view ssl client-policy policy-name required specify a pki domain for the ssl client policy pki-domain domain-name optional no pki domain is configured by default. Specify the preferred cipher suite for the ssl client polic...
Page 477
1-8 solution 1) you can issue the debugging ssl command and view the debugging information to locate the problem: z if the ssl client is configured to authenticate the ssl server but the ssl server has no certificate, request one for it. Z if the server’s certificate cannot be trusted, install on th...
Page 478: Table of Contents
I table of contents 1 ssh2.0 configuration································································································································1-1 ssh2.0 overview···············································································································...
Page 479: Ssh2.0 Configuration
1-1 1 ssh2.0 configuration this chapter includes these sections: z ssh2.0 overview z configuring the device as an ssh server z configuring the device as an ssh client z displaying and maintaining ssh z ssh server configuration examples z ssh client configuration examples ssh2.0 overview introduction...
Page 480
1-2 stages description session request after passing authentication, the client sends a session request to the server. Interaction after the server grants the request, the client and server start to communicate with each other. Version negotiation 1) the server opens port 22 to listen to connection ...
Page 481
1-3 before the negotiation, the server must have already generated a dsa or rsa key pair, which is not only used for generating the session key, but also used by the client to authenticate the identity of the server. For details about dsa and rsa key pairs, refer to public key configuration. Authent...
Page 482
1-4 session request after passing authentication, the client sends a session request to the server, while the server listens to and processes the request from the client. After successfully processing the request, the server sends back to the client an ssh_smsg_success packet and goes on to the inte...
Page 484
1-6 to do… use the command… remarks enter system view system-view — enter user interface view of one or more user interfaces user-interface vty number [ ending-number ] — set the login authentication mode to scheme authentication-mode scheme required by default, the authentication mode is password. ...
Page 485
1-7 z you are recommended to configure a client public key by importing it from a public key file. Z you can configure at most 20 client public keys on an ssh server. Configuring a client public key manually follow these steps to configure the client public key manually: to do… use the command… rema...
Page 487
1-9 setting the ssh management parameters ssh management includes: z enabling the ssh server to be compatible with ssh1 client z setting the server key pair update interval, applicable to users using ssh1 client z setting the ssh user authentication timeout period z setting the maximum number of ssh...
Page 488
1-10 specifying a source ip address/interface for the ssh client this configuration task allows you to specify a source ip address or interface for the client to access the ssh server, improving service manageability. To do… use the command… remarks enter system view system-view — specify a source i...
Page 489
1-11 to do... Use the command… remarks configure the server host public key refer to configuring a client public key required the method for configuring the server host public key on the client is similar to that for configuring client public key on the server. Specify the host public key name of th...
Page 490
1-12 for information about the display public-key local and display public-key peer commands, refer to public key commands. Ssh server configuration examples when switch acts as server for password authentication network requirements z as shown in figure 1-1 , a local ssh connection is established b...
Page 491
1-13 [switch-luser-client001] password simple aabbcc [switch-luser-client001] service-type ssh [switch-luser-client001] authorization-attribute level 3 [switch-luser-client001] quit # specify the service type for user client001 as stelnet, and the authentication mode as password. This step is option...
Page 492
1-14 in the window shown in figure 1-2 , click open. If the connection is normal, you will be prompted to enter the username and password. After entering the correct username (client001) and password (aabbcc), you can enter the configuration interface. When switch acts as server for publickey authen...
Page 493
1-15 before performing the following tasks, you must use the client software to generate an rsa key pair on the client, save the public key in a file named key.Pub, and then upload the file to the ssh server through ftp or tftp. For details, refer to configure the ssh client below. # import the clie...
Page 494
1-16 figure 1-5 generate a client key pair 2) after the key pair is generated, click save public key and specify the file name as key.Pub to save the public key. Figure 1-6 generate a client key pair 3) likewise, to save the private key, click save private key. A warning window pops up to prompt you...
Page 495
1-17 figure 1-7 generate a client key pair 4) after generating a key pair on a client, you need to transmit the saved public key file to the server through ftp or tftp and have the configuration on the server done before continuing configuration of the client. # specify the private key file and esta...
Page 496
1-18 figure 1-9 ssh client configuration interface 2) in the window shown in figure 1-9 , click open. If the connection is normal, you will be prompted to enter the username. After entering the correct username (client002), you can enter the configuration interface. Ssh client configuration examples...
Page 497
1-19 [switchb] public-key local create dsa [switchb] ssh server enable # create an ip address for vlan interface 1, which the ssh client will use as the destination for ssh connection. [switchb] interface vlan-interface 1 [switchb-vlan-interface1] ip address 10.165.87.136 255.255.255.0 [switchb-vlan...
Page 498
1-20 z if the client does not support first-time authentication, you need to perform the following configurations. # disable first-time authentication. [switcha] undo ssh client first-time # configure the host public key of the ssh server. You can get the server host public key by using the display ...
Page 499
1-21 when switch acts as client for publickey authentication network requirements z as shown in figure 1-11 , switch a (the ssh client) needs to log into switch b (the ssh server) through the ssh protocol. Z publickey authentication is used, and the public key algorithm is dsa. Figure 1-11 switch ac...
Page 500
1-22 # specify the authentication type for user client002 as publickey, and assign the public key switch001 to the user. [switchb] ssh user client002 service-type stelnet authentication-type publickey assign publickey switch001 2) configure the ssh client # configure an ip address for vlan interface...
Page 501: Sftp Service
2-1 2 sftp service when configuring sftp, go to these sections for information you are interested in: z sftp overview z configuring an sftp server z configuring an sftp client z sftp client configuration example z sftp server configuration example sftp overview the secure file transfer protocol (sft...
Page 502: Configuring An Sftp Client
2-2 when the device functions as the sftp server, only one client can access the sftp server at a time. If the sftp client uses winscp, a file on the server cannot be modified directly; it can only be downloaded to a local place, modified, and then uploaded to the server. Configuring the sftp connec...
Page 504
2-4 working with sftp files sftp file operations include: z changing the name of a file z downloading a file z uploading a file z displaying a list of the files z deleting a file follow these steps to work with sftp files: to do… use the command… remarks enter sftp client view sftp server [ port-num...
Page 506
2-6 figure 2-1 network diagram for sftp client configuration (on a switch) configuration procedure 1) configure the sftp server (switch b) # generate rsa and dsa key pairs and enable the ssh server. System-view [switchb] public-key local create rsa [switchb] public-key local create dsa [switchb] ssh...
Page 507
2-7 # configure an ip address for vlan interface 1. System-view [switcha] interface vlan-interface 1 [switcha-vlan-interface1] ip address 192.168.0.2 255.255.255.0 [switcha-vlan-interface1] quit # generate rsa key pairs. [switcha] public-key local create rsa # export the host public key to file pubk...
Page 508
2-8 sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 aug 23 06:52 config.Cfg -rwxrwxrwx 1 noone nogroup 225 aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubkey drwxrwxrwx 1 noone nogroup 0 sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 sep 01 06:55 pub # add a directory named ne...
Page 509
2-9 sftp-client> quit bye connection closed. Sftp server configuration example network requirements as shown in figure 2-2 , an ssh connection is established between the host and the switch. The host, an sftp client, logs into the switch for file management and file transfer. An ssh user uses passwo...
Page 510
2-10 [switch-luser-client002] quit # configure the user authentication type as password and service type as sftp. [switch] ssh user client002 service-type sftp authentication-type password 2) configure the sftp client z there are many kinds of sftp client software. The following takes the psftp of p...
Page 511: Table of Contents
I table of contents 1 public key configuration··························································································································1-1 asymmetric key algorithm overview·······························································································...
Page 512: Public Key Configuration
1-1 1 public key configuration this chapter includes these sections: z asymmetric key algorithm overview z configuring the local asymmetric key pair z configuring the public key of a peer z displaying and maintaining public keys z public key configuration examples asymmetric key algorithm overview b...
Page 513
1-2 asymmetric key algorithm applications asymmetric key algorithms can be used for encryption and digital signature: z encryption: the sender uses the public key of the intended receiver to encrypt the information to be sent. Only the intended receiver, the holder of the paired private key, can dec...
Page 514
1-3 key pairs created with the public-key local create command are saved automatically and can survive system reboots. Displaying or exporting the local rsa or dsa host public key display the local rsa or dsa host public key on the screen or export it to a specified file. Then, you can configure the...
Page 515
1-4 z if you choose to input the public key manually, be sure to input it in the correct format. The key data displayed by the display public-key local public command meets the format requirements. The public key displayed in other methods may not meet the format requirements. A format-incompliant k...
Page 517
1-6 time of key pair created: 09:50:06 2007/08/07 key name: host_key key type: rsa encryption key ===================================================== key code: 30819f300d06092a864886f70d010101050003818d0030818902818100d90003fa95f5a44a2a2cd3f814f985 4c4421b57cac64cffe4782a87b0360b600497d87162d1f398...
Page 518
1-7 4ad597d0fb3aa9f7202c507072b19c3c50a0d7ad3994e14abc62db125035ea326470034dc078b2baa3bc3bca 80aab5ee01986bd1ef64b42f17ccae4a77f1ef999b2bf9c4a10203010001 importing the public key of a peer from a public key file network requirements as shown in figure 1-3 , to prevent illegal access, device b authen...
Page 519
1-8 4ad597d0fb3aa9f7202c507072b19c3c50a0d7ad3994e14abc62db125035ea326470034dc078b2baa3bc3bca 80aab5ee01986bd1ef64b42f17ccae4a77f1ef999b2bf9c4a10203010001 ===================================================== time of key pair created: 09:50:07 2007/08/07 key name: server_key key type: rsa encryption ...
Page 520
1-9 [deviceb] public-key peer devicea import sshkey devicea.Pub # display the host public key of device a saved on device b. [deviceb] display public-key peer name devicea ===================================== key name : devicea key type : rsa key module: 1024 ===================================== k...
Page 521: Table of Contents
I table of contents 1 habp configuration ··································································································································1-1 introduction to habp·········································································································...
Page 522: Habp Configuration
1-1 1 habp configuration when configuring habp, go to these sections for the information you are interested in: z introduction to habp z configuring habp z displaying and maintaining habp z habp configuration example introduction to habp the hw authentication bypass protocol (habp) is used to enable...
Page 523: Configuring Habp
1-2 habp is a link layer protocol that works above the mac layer. It is built on the client-server model. Generally, the habp server is assumed by the management device (such as switch a in the above example), and the attached switches function as the habp clients, such as switch b through switch e ...
Page 524: Habp Configuration Example
1-3 displaying and maintaining habp to do… use the command… remarks display habp configuration information display habp available in any view display habp mac address table entries display habp table available in any view display habp packet statistics display habp traffic available in any view habp...
Page 525
1-4 [switcha] habp enable # configure habp to work in server mode, allowing habp packets to be transmitted in vlan 2. [switcha] habp server vlan 2 # set the interval to send habp request packets to 50 seconds. [switcha] habp timer 50 2) configure switch b and switch c configure switch b and switch c...
Page 526: Table of Contents
I table of contents 1 acl configuration·····································································································································1-1 acl overview ···············································································································...
Page 527: Acl Configuration
1-1 1 acl configuration this chapter includes these sections: z acl overview z acl configuration task list z configuring an acl z creating a time range z configuring a basic acl z configuring an advanced acl z configuring an ethernet frame header acl z copying an acl z applying an acl for packet fil...
Page 528
1-2 z software-based application: an acl is referenced by a piece of upper layer software. For example, an acl can be referenced to configure login user control behavior, thus controlling telnet, snmp and web users. Note that when an acl is reference by the upper layer software, actions to be taken ...
Page 529
1-3 z auto: sorts acl rules in depth-first order, as described in table 1-2 . The depth-first order varies with acl categories. Table 1-2 sorting acl rules in depth-first order acl category depth-first rule sorting procedures basic acl 1) a rule with more 0s in the source ip address wildcard mask ta...
Page 530: Acl Configuration Task List
1-4 for example, if the numbering step is 5 (the default), and there are five acl rules numbered 0, 5, 9, 10, and 12, the newly defined rule will be numbered 15. If the acl does not contain any rule, the first rule will be numbered 0. Whenever the step changes, the rules are renumbered, starting fro...
Page 533
1-7 configuring an advanced acl advanced acls match packets based on source and destination ip addresses, protocols over ip, and other protocol header information, such as tcp/udp source and destination port numbers, tcp flags, icmp message types, and icmp message codes. Advanced acls also allow you...
Page 534
1-8 z when the acl match order is auto, a newly created rule will be inserted among the existing rules in the depth-first match order. Note that the ids of the rules still remain the same. Z you can modify the match order of an acl with the acl number acl-number [ name acl-name ] match-order { auto ...
Page 535
1-9 z you can only modify the existing rules of an acl that uses the match order of config. When modifying a rule of such an acl, you may choose to change just some of the settings, in which case the other settings remain the same. Z you cannot create a rule with, or modify a rule to have, the same ...
Page 536
1-10 filtering ethernet frames follow these steps to apply an ethernet frame header acl to an interface to filter ethernet frames: to do… use the command… remarks enter system view system-view — enter ethernet interface view interface interface-type interface-number enter interface view enter vlan i...
Page 537: Acl Configuration Examples
1-11 acl configuration examples acl configuration examples network requirements as shown in figure 1-1 , apply an acl to the inbound direction of interface gigabitethernet 1/0/1 on device a so that the interface denies ipv4 packets sourced from host a from 8:00 to 18:00 everyday. Figure 1-1 network ...
Page 538: Table of Contents
I table of contents 1 device management ··································································································································1-1 device management overview ···································································································...
Page 539: Device Management
1-1 1 device management when configuring device management, go to these sections for information you are interested in: z device management overview z device management configuration task list z configuring the exception handling method z rebooting a device z configuring the scheduled automatic exec...
Page 541
1-3 z device reboot may result in the interruption of the ongoing services. Use these commands with caution. Z before device reboot, use the save command to save the current configurations. For details about the save command, refer to file system configuration. Z before device reboot, use the comman...
Page 542: Upgrading Device Software
1-4 z the system does not require any interactive information when it is executing the specified command. If there is information for you to confirm, the system automatically inputs y or yes; if characters need to be input, the system automatically inputs a default character string, or inputs an emp...
Page 543
1-5 1) copy the boot rom program to the root directory of the device's storage medium using ftp or tftp. 2) use a command to specify the boot rom program for the next boot. 3) reboot the device to make the specified boot rom program take effect. Follow these steps to upgrade the boot rom program: to...
Page 544
1-6 for the purpose of the stability of an interface index, the system will save the 16-bit interface index when a logical interface is removed. If you repeatedly to create or delete a large number of logical interfaces, the interface indexes will be used up, which will result in interface creation ...
Page 545
1-7 identifying pluggable transceivers as pluggable transceivers are of various types and from different vendors, you can use the following commands to view the key parameters of the pluggable transceivers, including transceiver type, connector type, central wavelength of the laser sent, transfer di...
Page 546
1-8 to do… use the command… remarks display the statistics of the cpu usage display cpu-usage [ entry-number [ offset ] [ verbose ] [ from-device ] ] available in any view display history statistics of the cpu usage in a chart display cpu-usage history [ task task-id ] available in any view display ...
Page 547
1-9 figure 1-2 network diagram for remote scheduled automatic upgrade ftp client ftp server user telnet device 1.1.1.1/24 2.2.2.2/24 internet configuration procedure 1) configuration on the ftp server (note that configurations may vary with different types of servers) z set the access parameters for...
Page 548
1-10 [ftp] get auto-update.Txt # download file new-config.Cfg on the ftp server. [ftp]get new-config.Cfg # download file soft-version2.Bin on the ftp server. [ftp] binary [ftp] get soft-version2.Bin [ftp] bye # modify the extension of file auto-update.Txt as .Bat. Rename auto-update.Txt auto-update....
Page 549: Table of Contents
I table of contents 1 ntp configuration ·····································································································································1-1 ntp overview ··············································································································...
Page 550: Ntp Configuration
1-1 1 ntp configuration when configuring ntp, go to these sections for information you are interested in: z ntp overview z ntp configuration task list z configuring the operation modes of ntp z configuring optional parameters of ntp z configuring access-control rights z configuring ntp authenticatio...
Page 551
1-2 z the clock stratum determines the accuracy, which ranges from 1 to 16. The stratum of a reference clock ranges from 1 to 15. The clock accuracy decreases as the stratum number increases. A stratum 16 clock is in the unsynchronized state. Z the local clock of an s5120-si ethernet switch cannot o...
Page 552
1-3 figure 1-1 basic work flow of ntp ip network ip network ip network ip network device b device a device b device a device b device a device b device a 10:00:00 am 11:00:01 am 10:00:00 am ntp message 10:00:00 am 11:00:01 am 11:00:02 am ntp message ntp message ntp message received at 10:00:03 am 1....
Page 553
1-4 all ntp messages mentioned in this document refer to ntp clock synchronization messages. A clock synchronization message is encapsulated in a udp message, in the format shown in figure 1-2 . Figure 1-2 clock synchronization message format li vn mode stratum poll precision 0 7 15 23 31 root delay...
Page 554
1-5 z receive timestamp: the local time at which the request arrived at the service host. Z transmit timestamp: the local time at which the reply departed from the service host for the client. Z authenticator: authentication information. Operation modes of ntp devices running ntp can implement clock...
Page 555
1-6 figure 1-4 symmetric peers mode a device working in the symmetric active mode periodically sends clock synchronization messages, with the mode field in the message set to 1 (symmetric active); the device that receives this message automatically enters the symmetric passive mode and sends a reply...
Page 556: Ntp Configuration Task List
1-7 figure 1-6 multicast mode network client server after receiving the first multicast message, the client sends a request clock synchronization message exchange (mode 3 and mode 4) periodically multicasts clock synchronization messages (mode 5) calculates the network delay between client and the s...
Page 557
1-8 z client/server mode z symmetric mode z broadcast mode z multicast mode for the client/server mode or symmetric mode, you need to configure only clients or symmetric-active peers; for the broadcast or multicast mode, you need to configure both servers and clients. A single device can have a maxi...
Page 558
1-9 z in the ntp-service unicast-server command, ip-address must be a unicast address, rather than a broadcast address, a multicast address or the ip address of the local clock. Z a device can act as a server to synchronize the clock of other devices only after its clock has been synchronized. If th...
Page 559
1-10 configuring ntp broadcast mode the broadcast server periodically sends ntp broadcast messages to the broadcast address 255.255.255.255. After receiving the messages, the device working in ntp broadcast client mode sends a reply and synchronizes its local clock. For devices working in the broadc...
Page 560
1-11 configuring a multicast client to do… use the command… remarks enter system view system-view — enter interface view interface interface-type interface-number enter the interface used to receive ntp multicast messages. Configure the device to work in the ntp multicast client mode ntp-service mul...
Page 561
1-12 to do… use the command… remarks specify the source interface for ntp messages ntp-service source-interface interface-type interface-number required by default, no source interface is specified for ntp messages, and the system uses the ip address of the interface determined by the matching route...
Page 562
1-13 configuring access-control rights with the following command, you can configure the ntp service access-control right to the local device. There are four access-control rights, as follows: z query: control query permitted. This level of right permits the peer devices to perform control query to ...
Page 563
1-14 configuring ntp authentication the ntp authentication feature should be enabled for a system running ntp in a network where there is a high security demand. This feature enhances the network security by means of client-server key authentication, which prohibits a client from synchronizing with ...
Page 565: Ntp Configuration Examples
1-16 the procedure of configuring ntp authentication on a server is the same as that on a client, and the same authentication key must be configured on both the server and client sides. Displaying and maintaining ntp to do… use the command… remarks view the information of ntp service status display ...
Page 566
1-17 clock offset: 0.0000 ms root delay: 0.00 ms root dispersion: 0.00 ms peer dispersion: 0.00 ms reference time: 00:00:00.000 utc jan 1 1900 (00000000.00000000) # specify device a as the ntp server of device b so that device b is synchronized to device a. System-view [deviceb] ntp-service unicast-...
Page 567
1-18 figure 1-8 network diagram for ntp symmetric peers mode configuration configuration procedure 1) configure ip addresses for interfaces (omitted) 2) configuration on device b: # specify device a as the ntp server of device b. System-view [deviceb] ntp-service unicast-server 3.0.1.31 3) view the ...
Page 568
1-19 nominal frequency: 100.0000 hz actual frequency: 100.0000 hz clock precision: 2^18 clock offset: -21.1982 ms root delay: 15.00 ms root dispersion: 775.15 ms peer dispersion: 34.29 ms reference time: 15:22:47.083 utc sep 19 2005 (c6d95647.153f7ced) as shown above, device c has been synchronized ...
Page 569
1-20 configuration procedure 1) configure ip addresses for interfaces (omitted) 2) configuration on switch c # configure switch c to work in the broadcast server mode and send broadcast messages through vlan-interface 2. [switchc] interface vlan-interface 2 [switchc-vlan-interface2] ntp-service broa...
Page 570
1-21 configuring ntp multicast mode network requirements as shown in figure 1-10 , switch c functions as the ntp server for multiple devices on different network segments and synchronizes the time among multiple devices. To realize this requirement, perform the following configurations: z switch c’s...
Page 571
1-22 because switch d and switch c are on the same subnet, switch d can receive the multicast messages from switch c without being enabled with the multicast functions and can be synchronized to switch c. # view the ntp status of switch d after clock synchronization. [switchd-vlan-interface2] displa...
Page 572
1-23 system-view [switcha] interface vlan-interface 3 # configure switch a to work in the multicast client mode and receive multicast messages on vlan-interface 3. [switcha-vlan-interface3] ntp-service multicast-client # view the ntp status of switch a after clock synchronization. [switcha-vlan-inte...
Page 573
1-24 configuration procedure 1) configure ip addresses for interfaces (omitted) 2) configuration on device b: system-view # enable ntp authentication on device b. [deviceb] ntp-service authentication enable # set an authentication key. [deviceb] ntp-service authentication-keyid 42 authentication-mod...
Page 574
1-25 note: 1 source(master),2 source(peer),3 selected,4 candidate,5 configured total associations : 1 configuring ntp broadcast mode with authentication network requirements as shown in figure 1-12 , switch c functions as the ntp server for multiple devices on different network segments and synchron...
Page 575
1-26 [switchd] ntp-service reliable authentication-keyid 88 # configure switch d to work in the ntp broadcast client mode. [switchd] interface vlan-interface 2 [switchd-vlan-interface2] ntp-service broadcast-client now, switch d can receive broadcast messages through vlan-interface 2, and switch c c...
Page 576: Table of Contents
I table of contents 1 snmp configuration··································································································································1-1 snmp overview·················································································································...
Page 577: Snmp Configuration
1-1 1 snmp configuration when configuring snmp, go to these sections for information you are interested in: z snmp overview z snmp configuration z configuring snmp logging z configuring snmp trap z displaying and maintaining snmp z snmpv1/snmpv2c configuration example z snmpv3 configuration example ...
Page 578
1-2 z inform operation: the nms sends traps to other nmss through this operation. Snmp protocol version currently, snmp agents support three protocol versions: snmpv1, snmpv2c and snmpv3. Z snmpv1 uses community names for authentication, which defines the relationship between an snmp nms and an snmp...
Page 579: Snmp Configuration
1-3 figure 1-2 mib tree a 2 6 1 5 2 1 1 2 1 b snmp configuration as configurations for snmpv3 differ substantially from those for snmpv1 and snmpv2c, their snmp functionalities are introduced separately as follows. Follow these steps to configure snmpv3: to do… use the command… remarks enter system ...
Page 581: Configuring Snmp Logging
1-5 to do… use the command… remarks configure the maximum size of an snmp packet that can be received or sent by an snmp agent snmp-agent packet max-size byte-count optional 1,500 bytes by default. The validity of a usm user depends on the engine id of the snmp agent. If the engine id generated when...
Page 582: Configuring Snmp Trap
1-6 z a large number of logs occupy storage space of the device, thus affecting the performance of the device. Therefore, it is recommended to disable snmp logging. Z the size of snmp logs cannot exceed that allowed by the information center, and the total length of the node field and value field of...
Page 583
1-7 to enable an interface to send linkup/linkdown traps when its state changes, you need to enable the trap function of interface state changes on an interface and globally. Use the enable snmp trap updown command to enable the trap function on an interface, and use the snmp-agent trap enable [ sta...
Page 584
1-8 z an extended linkup/linkdown trap is the standard linkup/linkdown trap (defined in rfc) appended with interface description and interface type information. If the extended messages are not supported on the nms, disable this function to let the device send standard linkup/linkdown traps. Z if th...
Page 585
1-9 figure 1-3 network diagram for snmpv1/v2c configuration procedure 1) configuring the snmp agent # configure the ip address of the agent as 1.1.1.1/24 and make sure that there is a route between the agent and the nms. (the configuration procedure is omitted here) # configure the snmp basic inform...
Page 586
1-10 snmpv3 configuration example network requirements z as shown in figure 1-4 , the nms connects to the agent through an ethernet. Z the ip address of the nms is 1.1.1.2/24. Z the ip address of the agent is 1.1.1.1/24. Z the nms monitors and manages the interface status of the agent using snmpv3. ...
Page 587
1-11 the configurations on the agent and the nms must match. 3) verify the configuration z after the above configuration, an snmp connection is established between the nms and the agent. The nms can get and configure the values of some parameters on the agent through mib nodes. Z execute the shutdow...
Page 588
1-12 system-view [sysname] info-center source snmp channel console log level informational # enable snmp logging on the agent to log the get and set operations of the nms. [sysname] snmp-agent log get-operation [sysname] snmp-agent log set-operation z the following log information is displayed on th...
Page 589: Mib Style Configuration
2-1 2 mib style configuration when configuring mib style, go to these sections for information you are interested in: z setting the mib style z displaying and maintaining mib h3c private mib involves two styles, h3c compatible mib and h3c new mib. In the h3c compatible mib style, the device sysoid i...
Page 590: Table of Contents
I table of contents 1 rmon configuration ·································································································································1-1 rmon overview ················································································································...
Page 591: Rmon Configuration
1-1 1 rmon configuration when configuring rmon, go to these sections for information you are interested in: z rmon overview z configuring the rmon statistics function z configuring the rmon alarm function z displaying and maintaining rmon z rmon configuration example (logging information) z rmon con...
Page 592
1-2 working mechanism rmon allows multiple monitors (management devices). A monitor provides two ways of data gathering: z using rmon probes. Management devices can obtain management information from rmon probes directly and control network resources. In this approach, management devices can obtain ...
Page 593
1-3 if the value of a sampled alarm variable overpasses the same threshold multiple times, only the first one can cause an alarm event. That is, the rising alarm and falling alarm are alternate. Private alarm group the private alarm group calculates the values of alarm variables and compares the res...
Page 594
1-4 z a statistics object of the ethernet statistics group is a variable defined in the ethernet statistics table, and the recorded content is a cumulative sum of the variable from the time the statistics entry is created to the current time. For detailed configuration, refer to configuring the rmon...
Page 595
1-5 z the entry-number must be globally unique and cannot be used on another interface; otherwise, the operation fails. Z you can configure multiple history entries on one interface, but the values of the entry-number arguments must be different, and the values of the sampling-interval arguments mus...
Page 596
1-6 z a new entry cannot be created if its parameters are identical with the corresponding parameters of an existing entry refer to table 1-1 for the parameters to be compared for different entries. Z the system limits the total number of each type of entries (refer to table 1-1 for the detailed num...
Page 597
1-7 rmon configuration example (logging information) network requirements as shown in figure 1-1 , agent is connected to a configuration terminal through its console port and to server through ethernet cables. Create an entry in the rmon ethernet statistics table to gather statistics on gigabitether...
Page 598
1-8 [sysname] display rmon alarm 1 alarm table 1 owned by 1-rmon is valid. Samples type : delta variable formula : 1.3.6.1.2.1.16.1.1.1.4.1 sampling interval : 10(sec) rising threshold : 1000(linked with event 1) falling threshold : 100(linked with event 1) when startup enables : risingorfallingalar...
Page 599
1-9 [sysname-gigabitethernet1/0/1] quit # create an rmon alarm entry that when the delta sampling value of node 1.3.6.1.2.1.16.1.1.1.4.1 exceeds 100, event 1 is triggered to send traps; when the delta sampling value of the node is lower than 50, event 2 is triggered to send traps. [sysname] rmon eve...
Page 600: Table of Contents
I table of contents 1 file system management··························································································································1-1 file system ······················································································································...
Page 601
Ii backing up the startup configuration file······························································································2-7 deleting the startup configuration file for the next startup ··································································2-8 restoring the startup confi...
Page 602: File System Management
1-1 1 file system management when managing a file system, go to these sections for information you are interested in: z file system z directory operations z file operations z batch operations z storage medium operations z setting file system prompt modes z file system operations example file system ...
Page 603: Directory Operations
1-2 directory operations directory operations include creating/removing a directory, displaying the current working directory, displaying the specified directory or file information, and so on. Displaying directory information to do… use the command… remarks display directory or file information dir...
Page 604: File Operations
1-3 z the directory to be removed must be empty, meaning that before you remove a directory, you must delete all the files and the subdirectory under this directory. For file deletion, refer to the delete command; for subdirectory deletion, refer to the rmdir command. Z after you execute the rmdir c...
Page 605
1-4 copying a file to do… use the command… remarks copy a file copy fileurl-source fileurl-dest required available in user view moving a file to do… use the command… remarks move a file move fileurl-source fileurl-dest required available in user view deleting a file to do… use the command… remarks m...
Page 607
1-6 to do… use the command… remarks restore the space of a storage medium fixdisk device optional available in user view format a storage medium format device optional available in user view when you format a storage medium, all the files stored on it are erased and cannot be restored. In particular...
Page 608
1-7 to do… use the command… remarks display data on the specified physical page display nandflash page-data page-value setting file system prompt modes the file system provides the following two prompt modes: z alert: in this mode, the system warns you about operations that may bring undesirable con...
Page 609
1-8 # return to the upper directory. Cd .. # display the current working directory. Pwd flash:.
Page 610: Configuration File Overview
2-1 2 configuration file management the device provides the configuration file management function with a user-friendly command line interface (cli) for you to manage the configuration files conveniently. This section covers these topics: z configuration file overview z saving the current configurat...
Page 611
2-2 coexistence of multiple configuration files multiple configuration files can be stored on a storage medium of a device. You can save the configuration used in different environments as different configuration files. In this case, when the device moves between these networking environments, you j...
Page 612
2-3 z safe mode. This is the mode when you use the save command with the safely keyword. The mode saves the file more slowly but can retain the configuration file in the device even if the device reboots or the power fails during the process. The fast saving mode is suitable for environments where p...
Page 613
2-4 z the application environment has changed and the device has to run in a configuration state based on a previous configuration file without being rebooted. Set configuration rollback following these steps: 1) specify the filename prefix and path for saving the current configuration. 2) save the ...
Page 614
2-5 the number of saved configuration files has an upper limit. After the maximum number of files is saved, the system deletes the oldest files when the next configuration file is saved. Follow these steps to configure parameters for saving the current running configuration: to do… use the command… ...
Page 615
2-6 to do… use the command… remarks enable the automatic saving of the current running configuration, and set the interval archive configuration interval minutes optional disabled by default the path and filename prefix of a saved configuration file must be specified before you configure the automat...
Page 616
2-7 do not unplug and plug during configuration rollback (that is, the system is executing the configuration replace file command). In addition, configuration rollback may fail if one of the following situations is present (if a command cannot be rolled back, the system skips it and processes the ne...
Page 617
2-8 the backup operation backs up the startup configuration file to the tftp server for devices supporting main/backup startup configuration file. Follow the step below to back up the startup configuration file to be used at the next system startup: to do… use the command… remarks back up the config...
Page 618
2-9 restoring the startup configuration file the restore function allows you to copy a configuration file from a tftp server to the device and specify the file as the startup configuration file to be used at the next system startup. Follow the step below to restore the startup configuration file to ...
Page 619: Table of Contents
1-1 table of contents 1 system maintaining and debugging········································································································1-1 system maintaining and debugging ·······································································································...
Page 620: Ping
1-1 1 system maintaining and debugging when maintaining and debugging the system, go to these sections for information you are interested in: z system maintaining and debugging z ping z tracert z system debugging z ping and tracert configuration example system maintaining and debugging you can use t...
Page 621
1-2 for a low-speed network, you are recommended to set a larger value for the timeout timer (indicated by the -t parameter in the command) when configuring the ping command. Ping configuration example network requirements as shown in figure 1-1 , check whether an available route exists between devi...
Page 622
1-3 record route: 1.1.2.1 1.1.2.2 1.1.1.2 1.1.1.1 reply from 1.1.2.2: bytes=56 sequence=2 ttl=254 time=1 ms record route: 1.1.2.1 1.1.2.2 1.1.1.2 1.1.1.1 reply from 1.1.2.2: bytes=56 sequence=3 ttl=254 time=1 ms record route: 1.1.2.1 1.1.2.2 1.1.1.2 1.1.1.1 reply from 1.1.2.2: bytes=56 sequence=4 tt...
Page 623: Tracert
1-4 5) upon receiving the reply, the source device adds the ip address (1.1.1.1) of its inbound interface to the rr option. Finally, you can get the detailed information of routes from device a to device c: 1.1.1.1 {1.1.1.2; 1.1.2.1} 1.1.2.2. Tracert introduction by using the tracert command, you ca...
Page 624: System Debugging
1-5 to do… use the command… remarks enable sending of icmp timeout packets ip ttl-expires enable required disabled by default. Enable sending of icmp destination unreachable packets ip unreachables enable required disabled by default. Display the routes from source to destination tracert [ -a source...
Page 625
1-6 configuring system debugging output of the debugging information may reduce system efficiency. The debugging commands are usually used by administrators in diagnosing network failure. After completing the debugging, disable the corresponding debugging function, or use the undo debugging all comm...
Page 626
1-7 figure 1-4 ping and tracert network diagram configuration procedure # use the ping command to display whether an available route exists between device a and device c. Ping 1.1.2.2 ping 1.1.2.2: 56 data bytes, press ctrl_c to break request time out request time out request time out request time o...
Page 627: Table of Contents
1-1 table of contents 1 basic configurations·································································································································1-1 configuration display ·····································································································...
Page 628: Basic Configurations
1-1 1 basic configurations while performing basic configurations of the system, go to these sections for information you are interested in: z configuration display z configuring the device name z configuring the system clock z enabling/disabling the display of copyright information z configuring a b...
Page 629: Configuring The Device Name
1-2 to do… use the command… remarks on the storage media of the device [ by-linenum ] z for details of the display saved-configuration command, refer to file system management commands. Configuring the device name the device name is used to identify a device in a network. Inside the system, the devi...
Page 630
1-3 displaying the system clock the system clock is decided by the commands clock datetime, clock timezone and clock summer-time. If these three commands are not configured, the display clock command displays the original system clock. If you combine these three commands in different ways, the syste...
Page 631
1-4 configuration system clock displayed by the display clock command example if date-time is not in the daylight saving time range, date-time is displayed. Configure: clock datetime 1:00 2007/1/1 and clock summer-time ss one-off 1:00 2006/1/1 1:00 2006/8/8 2 display: 01:00:00 utc mon 01/01/2007 1 a...
Page 632
1-5 configuration system clock displayed by the display clock command example displayed. 2007/1/1 1:00 2007/8/8 2 display: 04:00:00 ss mon 01/01/2007 if the value of "date-time"±"zone-offset" is in the summer-time range, "date-time"±"zone-offset"+”su mmer-offset” is displayed. Configure: clock timez...
Page 633: Configuring A Banner
1-6 to do… use the command… remarks disable the display of copyright information undo copyright-info enable required enabled by default. Configuring a banner introduction to banners banners are prompt information displayed by the system when users are connected to the device, perform login authentic...
Page 634: Configuring Cli Hotkeys
1-7 to do… use the command… remarks configure the banner to be displayed at login (available for modem login users) header incoming text optional configure the banner to be displayed at login authentication header login text optional configure the authorization information before login header legal ...
Page 635
1-8 hotkey function ctrl+e moves the cursor to the end of the current line. Ctrl+f moves the cursor one character to the right. Ctrl+h deletes the character to the left of the cursor. Ctrl+k terminates an outgoing connection. Ctrl+n displays the next command in the history command buffer. Ctrl+p dis...
Page 636
1-9 they can only use commands at their own, or lower, levels. All the commands are categorized into four levels, which are visit, monitor, system, and manage from low to high, and identified respectively by 0 through 3. Table 1-3 describes the levels of the commands. Table 1-3 default command level...
Page 637
1-10 to do… use the command… remarks exit to system view quit — configure the authentication mode for ssh users as password for the details, refer to ssh2.0 configuration. Required if users use ssh to log in, and username and password are needed at authentication using local authentication z use the...
Page 638
1-11 configure the user privilege level under a user interface if the user interface authentication mode is scheme when a user logs in, and ssh publickey authentication type (only username is needed for this authentication type) is adopted, then the user privilege level is the user interface level; ...
Page 639
1-12 to do… use the command… remarks the console user interface is 3, and that for users logging from the other user interfaces is 0. Example of configuring user privilege level under a user interface z perform no authentication to the users telnetting to the device, and specify the user privilege l...
Page 640
1-13 system-view [sysname] user-interface vty 0 15 [sysname-ui-vty1] authentication-mode password [sysname-ui-vty0-15] set authentication password cipher 123 [sysname-ui-vty0-15] user privilege level 2 by default, when users log in to the device through telnet, they can use the commands of level 0 a...
Page 641
1-14 z when you configure the password for switching user privilege level with the super password command, the user privilege level is 3 if no user privilege level is specified. Z the password for switching user privilege level can be displayed in both cipher text and simple text. You are recommende...
Page 642
1-15 during daily maintenance or when the system is operating abnormally, you need to display the running status of each functional module to locate the problem. Generally, you need to execute the corresponding display commands for each module, because each module has independent running information...
Page 643: Table of Contents
I table of contents 1 information center configuration············································································································1-1 information center overview ··········································································································...
Page 644: Information Center Overview
1-1 1 information center configuration when configuring information center, go to these sections for information you are interested in: z information center configuration z configuring information center z displaying and maintaining information center z information center configuration examples info...
Page 645
1-2 figure 1-1 information center diagram (default) 1 2 3 4 5 6 7 8 9 console 0 channel6 monitor loghost trapbuffer logbuffer snmpagent channel7 channel8 channel9 log information trap information debug information console monitor log host trap buffer log buffer snmp agent system information informat...
Page 646
1-3 table 1-1 severity description severity severity value description emergency 0 the system is unusable. Alert 1 action must be taken immediately critical 2 critical conditions error 3 error conditions warning 4 warning conditions notice 5 normal but significant condition informational 6 informati...
Page 647
1-4 information channel number default channel name default output destination description debugging information. 9 channel9 log file receives log, trap, and debugging information. Configurations for the eight output destinations function independently and take effect only after the information cent...
Page 648
1-5 log trap debug output destinati on modules allowed enabled/ disabled severity enabled/ disabled severity enabled/ disabled severity log host default (all modules) enabled informatio nal enabled debug disabled debug trap buffer default (all modules) disabled informatio nal enabled warning disable...
Page 649
1-6 int_16 (priority) the priority is calculated using the following formula: facility*8+severity, in which facility represents the logging facility name and can be configured when you set the log host parameters. The facility ranges from local0 to local7 (16 to 23 in decimal integers) and defaults ...
Page 650
1-7 z if the timestamp starts with a *, the information is debugging information source this field indicates the source of the information, such as the source ip address of the log sender. This field is optional and is displayed only when the output destination is the log host. Content this field pr...
Page 653
1-10 to do… use the command… remarks system uses channel 2 (loghost) by default. The value of the port-number argument should be the same as the value configured on the log host, otherwise, the log host cannot receive system information. Configure the output rules of the system information info-cent...
Page 655
1-12 outputting system information to the snmp module the snmp module receives the trap information only, and discards the log and debugging information even if you have configured to output them to the snmp module. To monitor the device running status, trap information is usually sent to the snmp n...
Page 656
1-13 follow these steps to set to output system information to the web interface: to do… use the command… remarks enter system view system-view — enable information center info-center enable optional enabled by default name the channel with a specified channel number info-center channel channel-numb...
Page 657
1-14 to do… use the command… remarks enter system view system-view — enable information center info-center enable optional enabled by default enable the log file feature info-center logfile enable optional enabled by default configure the frequency with which the log file is saved info-center logfil...
Page 658
1-15 z if system information, such as log information, is output before you input any information under the current command line prompt, the system will not display the command line prompt after the system information output. Z if system information is output when you are inputting some interactive ...
Page 660
1-17 [sysname] info-center source default channel loghost debug state off log state off trap state off as the default system configurations for different channels are different, you need to disable the output of log, trap, and debugging information of all modules on the specified channel (loghost in...
Page 662
1-19 step 2: create a subdirectory named device under directory /var/log/, and create file info.Log under the device directory to save logs of device. # mkdir /var/log/device # touch /var/log/device/info.Log step 3: edit file /etc/syslog.Conf and add the following contents. # device configuration me...
Page 663
1-20 figure 1-4 network diagram for sending log information to the console configuration procedure # enable information center. System-view [sysname] info-center enable # use channel console to output log information to the console (optional, console by default). [sysname] info-center console channe...
Page 664: Table of Contents
I table of contents 1 mac address table configuration ··········································································································1-1 overview ·······························································································································...
Page 665: Overview
1-1 1 mac address table configuration when configuring mac address tables, go to these sections for information you are interested in: z overview z configuring a mac address table z displaying and maintaining mac address table z mac address table configuration example currently, interfaces involved ...
Page 666
1-2 updated when the aging timer expires, it is deleted. If it updates before the aging timer expires, the aging timer restarts. Manually configuring mac address entries with dynamic mac address learning, a device does not tell illegitimate frames from legitimate ones. This brings security hazards. ...
Page 667
1-3 figure 1-1 forward frames using the mac address table configuring a mac address table the mac address table configuration tasks include: z configuring mac address table entries z configuring the aging timer for dynamic mac address entries z configuring the mac learning limit these configuration ...
Page 668
1-4 when using the mac-address command to add a mac address entry, the interface specified by the interface keyword must belong to the vlan specified by the vlan keyword, and the vlan must already exist. Otherwise, you will fail to add this mac address entry. Follow these steps to add, modify, or re...
Page 669
1-5 z the mac address aging timer takes effect globally on dynamic mac address entries (learned or administratively configured) only. Z in a stable network, when there has been no traffic activity for a long time, all the dynamic entries in the mac address table maintained by the device will be dele...
Page 671
1-7 --- 1 mac address(es) found --- # view the aging time of dynamic mac address entries. [sysname] display mac-address aging-time mac address aging time: 500s.
Page 672: Table of Contents
I table of contents 1 cluster management configuration·········································································································1-1 cluster management overview··············································································································...
Page 673: Cluster Management Overview
1-1 1 cluster management configuration when configuring cluster management, go to these sections for information you are interested in: z cluster management overview z cluster configuration task list z configuring the management device z configuring the member devices z configuring access between th...
Page 674
1-2 cluster. Different from a member device, its topology information has been collected by the management device but it has not been added to the cluster. Figure 1-1 network diagram for a cluster as shown in figure 1-1 , the device configured with a public ip address and performing the management f...
Page 675
1-3 configuration according to the candidate device information collected through ntdp. Introduction to ndp ndp is used to discover the information about directly connected neighbors, including the device name, software version, and connecting port of the adjacent devices. Ndp works in the following...
Page 676
1-4 z on the same device, except the first port, each ntdp-enabled port waits for a period of time and then forwards the ntdp topology collection request after its prior port forwards the ntdp topology collection request. Cluster management maintenance 1) adding a candidate device to a cluster you s...
Page 677
1-5 information holdtime, it changes its state to active; otherwise, it changes its state to disconnect. Z if the communication between the management device and a member device is recovered, the member device which is in disconnect state will be added to the cluster. After that, the state of the me...
Page 678
1-6 task remarks configuring ndp parameters optional enabling ntdp globally and for specific ports optional configuring ntdp parameters optional manually collecting topology information optional enabling the cluster function optional establishing a cluster required enabling management vlan auto-nego...
Page 679
1-7 table, the candidate device will be added to and removed from the cluster repeatedly. Configuring the management device enabling ndp globally and for specific ports for ndp to work normally, you must enable ntdp both globally and on specific ports. Follow these steps to enable ndp globally and f...
Page 680
1-8 the time for the receiving device to hold ndp packets cannot be shorter thanthe interval for sending ndp packets; otherwise, thendp tablemay become instable. Enabling ntdp globally and for specific ports for ntdp to work normally, you must enable ntdp both globally and on specific ports. Follow ...
Page 681
1-9 to do… use the command… remarks enter system view system-view — configure the maximum hops for topology collection ntdp hop hop-value optional 3 by default. Configure the interval to collect topology information ntdp timer interval optional 1 minute by default. Configure the delay to forward top...
Page 682
1-10 the device to be configured as the management device before establishing a cluster. Meanwhile, the ip addresses of the vlan interfaces of the management device and member devices cannot be in the same network segment as that of the cluster address pool; otherwise, the cluster cannot work normal...
Page 683
1-11 to do… use the command… remarks enter system view system-view — enter cluster view cluster — enable management vlan auto-negotiation management-vlan synchronization enable required disabled by default. Configuring communication between the management device and the member devices within a clust...
Page 684
1-12 to do… use the command… remarks enter system view system-view — enter cluster view cluster — configure the destination mac address for cluster management protocol packets cluster-mac mac-address required the destination mac address is 0180-c200-000a by default. Configure the interval to send ma...
Page 687
1-15 z configuring topology management z configuring interaction for a cluster configuring topology management the concepts of blacklist and whitelist are used for topology management. An administrator can diagnose the network by comparing the current topology (namely, the information of a node and ...
Page 688
1-16 configuring interaction for a cluster after establishing a cluster, you can configure ftp/tftp server, nm host and log host for the cluster on the management device. Z after you configure an ftp/tftp server for a cluster, the members in the cluster access the ftp/tftp server configured through ...
Page 689
1-17 snmp configuration synchronization function snmp configuration synchronization function facilitates management of a cluster, with which you can perform snmp-related configurations on the management device and synchronize them to the member devices on the whitelist. This operation is equal to co...
Page 692
1-20 [switcha-gigabitethernet1/0/1] ntdp enable [switcha-gigabitethernet1/0/1] quit # enable the cluster function. [switcha] cluster enable 2) configure the member device switch c as the configurations of the member devices are the same, the configuration procedure of switch c is omitted here. 3) co...
Page 693
1-21 [switchb] interface gigabitethernet 1/0/3 [switchb-gigabitethernet1/0/3] port link-type trunk [switchb-gigabitethernet1/0/3] quit # enable the cluster function. [switchb] cluster enable # configure a private ip address range for the member devices, which is from 172.16.0.1 to 172.16.0.7. [switc...
Page 694: Table of Contents
I table of contents 1 http configuration···································································································································1-1 http overview················································································································...
Page 695: Http Configuration
1-1 1 http configuration this chapter includes these sections: z http overview z enabling the http service z http configuration z associating the http service with an acl z displaying and maintaining http z http configuration example http overview the hypertext transfer protocol (http) is used for t...
Page 696: Enabling The Http Service
1-2 enabling the http service the device can act as the http server and the users can access and control the device through the web function only after the http service is enabled. Follow these steps to enable the http service: to do… use the command… remarks enter system view system-view — enable t...
Page 697: Http Configuration Example
1-3 z if you execute the ip http acl command for multiple times to associate the http with different acls, the http service is only associated with the last specified acl. Z for the detailed introduction to acl, refer to acl configuration. Displaying and maintaining http to do… use the command… rema...
Page 698
1-4 if you open the ie on host b, and type http://10.2.1.1, you cannot open the web login page of device..
Page 699: Https Configuration
2-1 2 https configuration this chapter includes these sections: z https overview z https configuration task list z associating the https service with an ssl server policy z enabling the https service z associating the https service with a certificate attribute access control policy z configuring the...
Page 700: Enabling The Https Service
2-2 associating the https service with an ssl server policy before enabling the https service, associate the https service with a created ssl server policy. Follow these steps to associate the https service with an ssl server policy: to do… use the command… remarks enter system view system-view — as...
Page 701: Control Policy
2-3 z after the https service is enabled, you can use the display ip https command to view the state of the https service and verify the configuration. Z enabling of the https service will trigger an ssl handshake negotiation process. During the process, if the local certificate of the device alread...
Page 702: Https Configuration Example
2-4 to do… use the command… remarks enter system view system-view — configure the port number of the https service ip https port port-number optional by default, the port number of the https service is 443. If you execute the ip https port command for multiple times, the last configured port number ...
Page 703
2-5 device requires the users log in to the web page through https and authenticates the users using ssl, and ensures that the transmitted data will not be spoofed and tampered. To meet the requirements, perform the following: z configure device as the https server and apply a certificate for device...
Page 704
2-6 # generate a local rsa key pair. [device] public-key local create rsa # retrieve a ca certificate. [device] pki retrieval-certificate ca domain 1 # request a local certificate for device. [device] pki request-certificate domain 1 # configure an ssl server policy myssl, specify pki domain 1 for i...
Page 705
2-7 z the url of the https server starts with https://, and that of the http server starts with http://. Z for details of pki commands, refer to pki commands. Z for details of the public-key local create rsa command, refer to public key commands. Z for details of ssl commands, refer to ssl commands..
Page 706: Table of Contents
I table of contents 1 stack configuration···································································································································1-1 stack configuration overview································································································...
Page 707: Stack Configuration
1-1 1 stack configuration when configuring stack, go to these sections for information you are interested in: z stack configuration overview z stack configuration task list z configuring the master device of a stack z configuring stack ports of a slave device z logging in to the cli of a slave from ...
Page 708
1-2 establishing a stack an administrator can establish a stack as follows: z configure a private ip address pool for a stack and create the stack on the network device which is desired to be the master device. Z configure ports between the stack devices as stack ports. Z the master device automatic...
Page 709
1-3 z if a device is already configured as the master device of a stack or is already a slave device of a stack, you cannot configure a private ip address pool on the device. Z when you configure a private ip address pool for a stack, the number of ip addresses in the address pool needs to be equal ...
Page 710: Stack Configuration Example
1-4 to do… use the command… remarks enter system view system-view — configure the specified ports as stack ports stack stack-port stack-port-num port interface-list required by default, a port is not a stack port. After a device joins a stack and becomes a slave device of the stack, the prompt chang...
Page 711
1-5 z create a stack, where switch a is the master device, switch b, switch c, and switch d are slave devices. An administrator can log in to switch b, switch c and switch d through switch a to perform remote configurations. Figure 1-2 network diagram for stack management ge1/0/1 ge1/0/3 switchb: sl...
Page 712
1-6 switch type: h3c s5120 mac address: 000f-e200-1000 number : 1 role : slave sysname : stack_1. Switchb device type: h3c s5120 mac address: 000f-e200-1001 number : 2 role : slave sysname : stack_2. Devicec device type: h3c s5120 mac address: 000f-e200-1002 number : 3 role : slave sysname : stack_3...
Page 713: Table of Contents
I table of contents 1 poe configuration ·····································································································································1-1 poe overview ··············································································································...
Page 714: Poe Configuration
1-1 1 poe configuration when configuring poe, go to these sections for information you are interested in: z poe overview z poe configuration task list z enabling poe z detecting pds z configuring the poe power z configuring poe power management z configuring the poe monitoring function z configuring...
Page 715: Poe Configuration Task List
1-2 3) pi: an ethernet interface with the poe capability is called poe interface. Currently, a poe interface can be an fe or ge interface. 4) pd: a pd is a device accepting power from the pse, including ip phones, wireless aps, chargers of portable devices, pos, and web cameras. The pd that is being...
Page 716: Enabling Poe
1-3 task remarks them, so no configuration is required. Configuring poe profile optional configuring poe interface through poe profile applying poe profile optional upgrading pse processing software in service optional z before configure poe, make sure that the poe power supply and pse are operating...
Page 717: Detecting Pds
1-4 when the sum of the power consumption of all powered poe interfaces on a pse exceeds the maximum power of the pse, the system considers the pse is overloaded (the maximum pse power is decided by the user configuration). Follow these steps to enable poe for a poe interface: to do… use the command...
Page 719
1-6 z 19 watts guard band is reserved for each poe interface on the device to prevent a pd from being powered off because of a sudden increase of the pd power. When the remaining power of the pse is lower than 19 watts and no priority is configured for the poe interface, the pse does not supply powe...
Page 720
1-7 onfiguring pse power monitoring when the pse power exceeds or drops below the specified threshold, the system will send trap message. Follow these steps to configure a power alarm threshold for the pse: to do… use the command… remarks enter system view system-view — configure a power alarm thres...
Page 722: Poe Configuration Example
1-9 upgrading pse processing software in service you can upgrade the pse processing software in service in either of the following two modes: z refresh mode this mode enables you to update the pse processing software without deleting it. Normally, you can upgrade the pse processing software in the r...
Page 723
1-10 z gigabitethernet 1/0/1, gigabitethernet 1/0/2, and gigabitethernet 1/0/3 are connected to ip telephones. Z gigabitethernet 1/0/11 and gigabitethernet 1/0/12 are connected to ap devices. Z the power supply priority of ip telephones is higher than that of the aps, for which the pse supplies powe...
Page 724: Troubleshooting Poe
1-11 after the configuration takes effect, the ip telephones and ap devices are powered and can work normally. Troubleshooting poe symptom 1: setting the priority of a poe interface to critical fails. Analysis: z the guaranteed remaining power of the pse is lower than the maximum power of the poe in...
Page 725: Table of Contents
I table of contents 1 ip source guard configuration················································································································1-1 ip source guard overview ············································································································...
Page 726: Ip Source Guard Overview
1-1 1 ip source guard configuration when configuring ip source guard, go to these sections for information you are interested in: z ip source guard overview z configuring a static binding entry z configuring dynamic binding function z displaying and maintaining ip source guard z ip source guard conf...
Page 729
1-4 [switcha-gigabitethernet1/0/2] quit # configure port gigabitethernet 1/0/1 of switch a to allow only ip packets with the source mac address of 00-01-02-03-04-06 and the source ip address of 192.168.0.1 to pass. [switcha] interface gigabitethernet 1/0/1 [switcha-gigabitethernet1/0/1] user-bind ip...
Page 730
1-5 for detailed configuration of a dhcp server, refer to dhcp configuration in the ip service volume. Figure 1-2 network diagram for configuring dynamic binding function configuration procedure 1) configure switch a # configure dynamic binding function on port gigabitethernet 1/0/1 to filter packet...
Page 731
1-6 [switcha-gigabitethernet1/0/1] display dhcp-snooping dhcp snooping is enabled. The client binding table for all untrusted ports. Type : d--dynamic , s--static type ip address mac address lease vlan interface ==== =============== ============== ============ ==== ================= d 192.168.0.1 00...
Page 732
1 appendix a h3c network technology acronyms # a b c d e f g h i l m n o p q r s t u v w x z a return aal5 atm adaptation layer 5 abr area border router ac access controller ac access category accm async-control-character-map acfc address-and-control-field-compression acfp application control forwar...
Page 733
2 b8zs bipolar 8 zeros substitution bas broadband access server bc boundary clock bc bandwidth constraint bcb backbone core bridge bdi backward defect indication bdr backup designated router beb backbone edge bridge bfd bidirectional forwarding detection bgp border gateway protocol bims branch intel...
Page 734
3 cidr classless inter-domain routing cir committed information rate cist common and internal spanning tree co central office cops common open policy service cpe customer premises equipment cps certification practice statement cptone call progress tone cr constraint-based routing crc4 cyclic redunda...
Page 735
4 dmr delay measurement reply dmz demilitarized zone dn distinguished name dnat destination nat dns domain name system dod downstream on demand dos denial of service dpd dead peer detection dr designated router ds differentiated services dsa digital signature algorithm dscp differentiated services c...
Page 736
5 fcoe fibre channel over ethernet fec forwarding equivalence class ffd fast failure detection fib forwarding information base fifo first in first out fip fcoe initialization protocol fqdn fully qualified domain name frr fast reroute fsk frequency shift keying ftn fec to nhlfe map ftp file transfer ...
Page 737
6 id direct inward dialing ids intrusion detection system ie information element ieee institute of electrical and electronics engineers ietf internet engineering task force igmp internet group management protocol igmp snooping internet group management protocol snooping igp interior gateway protocol...
Page 738
7 lbm loopback message lbr loopback reply lc logic channel lci logic channel identifier lcp link control protocol ldap lightweight directory access protocol ldp label distribution protocol ler label edge router lfi link fragmentation and interleaving lfib label forwarding information base lldp link ...
Page 739
8 mib management information base mic message integrity check mip maintenance association intermediate point mld multicast listener discovery protocol mld snooping multicast listener discovery snooping mlsp mobile link switch protocol mos mean opinion scores mp maintenance point mp-bgp multiprotocol...
Page 740
9 ntp network time protocol o return oaa open application architecture oampdu oam protocol data units oap open application platform oc optical carrier oc ordinary clock oid object identifier orf outbound route filtering ospf open shortest path first oui organizationally unique identifier p return p2...
Page 741
10 pkcs public key cryptography standards pki public key infrastructure pmk pairwise master key pmtu path mtu poe power over ethernet poh path overhead pop3 post office protocol, version 3 pos point of sale ppp point-to-point protocol pppoe point-to-point protocol over ethernet pptp point-to-point t...
Page 742
11 rpt rendezvous point tree rr router renumber rrpp rapid ring protection protocol rs router solicitation rsa rivest shamir and adleman rsb reservation state block rsh remote shell rsn robust security network rsna robust security network association rstp rapid spanning tree protocol rsvp resource r...
Page 743
12 sna system network architecture snap subnetwork access protocol snmp simple network management protocol snpa subnetwork point of attachment snr signal-to-noise ratio sonet synchronous optical network soo site of origin sp service provider sp strict priority spcs stored program control switching s...
Page 744
13 ts traffic shaping tst test ttl time to live tty true type terminal tu tributary unit txoplimit transmission opportunity limit u return ua unnumbered acknowledge u-apsd unscheduled automatic power-save delivery ubr unspecified bit rate udld uni-directional link direction uni user network interfac...
Page 745
14 wds wireless distribution system wep wired equivalent privacy wfq weighted fair queuing wids wireless intrusion detection system winet wisdom network wins windows internet naming service wlan wireless local area network wmm wi-fi multimedia wpa wi-fi protected access wpi wlan privacy infrastructu...