- DL manuals
- H3C
- Wireless Access Point
- WA Series
- Configuration Manual
H3C WA Series Configuration Manual
Summary of WA Series
Page 1
H3c wa series wlan access points wlan configuration guide hangzhou h3c technologies co., ltd. Http://www.H3c.Com document version: 6w100-20100910
Page 2
Copyright © 2010, hangzhou h3c technologies co., ltd. And its licensors all rights reserved no part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of hangzhou h3c technologies co., ltd. Trademarks h3c, , aolynk, , h 3 care, , top g, , irf, n...
Page 3: Preface
Preface the h3c wa documentation set includes 10 configuration guides, which describe the software features for the h3c wa series wlan access points and guide you through the software configuration procedures. These configuration guides also provide configuration examples to help you apply the softw...
Page 4
Convention description & the argument or keyword and argument combination before the ampersand (&) sign can be entered 1 to n times. # a line that starts with a pound (#) sign is comments. Gui conventions convention description boldface window names, button names, field names, and menu items are in ...
Page 5: Obtaining Documentation
Category documents purposes user faq provides answers to some of the most frequently asked questions on how to troubleshoot your ap. Operations and maintenance release notes provide information about the product release, including the version history, hardware and software compatibility matrix, vers...
Page 6: Table of Contents
I table of contents 1 applicable models and software versions .............................................................................................1-1 2 feature matrix ...............................................................................................................................
Page 7
Ii 6 wlan rrm configuration ........................................................................................................................6-1 overview ..............................................................................................................................................
Page 8
Iii deployment scenarios ....................................................................................................................9-2 wds configuration task list ..................................................................................................................9-3 configuri...
Page 9
1-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z read this chapter before using an h3c wa series wlan access point. 1 applicable models and software versions h3c wa series wlan access points...
Page 10: Feature Matrix
2-1 2 feature matrix z support of the h3c wa series wlan access points for features, commands and parameters may vary by device model. See this document for more information. Z for information about feature support, see table 2-1 . For information about command and parameter support, see table 3-1 ....
Page 11: Command/parameter Matrix
3-1 3 command/parameter matrix table 3-1 command/parameter matrix document module command/parameter wa2200 series wa2600 series display ip https not supported supported ip https acl not supported supported ip https certificate access-control-policy not supported supported fundamentals command refere...
Page 13: Wlan Interface Configuration
4-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 14: Wlan-Bss Interface
4-2 to do… use the command… remarks set the description string for the interface description text optional by default, the description string of an interface is interface-name + interface. Shut down the wlan-radio interface shutdown optional by default, a wlan-radio interface is up. Wlan-bss interfa...
Page 15: Wlan Mesh Interface
4-3 wlan mesh interface introduction wlan mesh interfaces are layer 2 virtual interfaces. You can use them as configuration templates to make and save settings for wlan mesh link interfaces. Once a wlan mesh link interface is created, you will not be allowed to change the settings on its associated ...
Page 16: Wlan Security Configuration
5-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 17
5-2 figure 5-1 open system authentication process ap client authentication request authentication response z shared key authentication the following figure shows a shared key authentication process. The two parties have the same shared key configured. 1) the client sends an authentication request to...
Page 18
5-3 wired equivalent privacy (wep) was developed to protect data exchanged among authorized users in a wireless lan from casual eavesdropping. Wep uses rc4 encryption for confidentiality. Wep encryption falls into static and dynamic encryption according to how a wep key is generated. Z static wep en...
Page 19: Configuring Wlan Security
5-4 1) psk authentication both wpa wireless access and wpa2 wireless access support psk authentication. To implement psk authentication, the client and the authenticator must have the same shared key configured. 2) 802.1x authentication as a port-based access control protocol, 802.1x authenticates a...
Page 21
5-6 to do… use the command… remarks enter system view system-view — enter wlan service template view wlan service-template service-template-number crypto — enable gtk rekey gtk-rekey enable required by default, gtk rekey is enabled. Configure the gtk rekey interval gtk-rekey method time-based time r...
Page 22
5-7 disable 802.1x online user handshake function before starting ptk and gtk negotiation. Configuring wpa security ie wi-fi protected access (wpa) ensures greater protection than wep. Wpa operates in either wpa-psk (or called personal) mode or wpa-802.1x (or called enterprise) mode. In personal mod...
Page 23
5-8 z in open system authentication mode, a wep key is used for encryption only. A client can go online without having the same key as the authenticator. But, if the receiver has a different key from the sender, it will discard the packets received from the sender. Z in shared key authentication mod...
Page 24
5-9 configuring tkip follow these steps to configure tkip: to do… use the command… remarks enter system view system-view — enter wlan service template wlan service-template service-template-number crypto required enable the tkip cipher suite cipher-suite tkip required set tkip counter measure time t...
Page 27
5-12 wlan security configuration examples psk authentication configuration example network requirements z as shown in figure 5-3 , the ap is connected to the switch. The psk key configured on the client side is 12345678. The same psk key is configured on the ap. Z it is required to perform psk authe...
Page 28
5-13 z you can use the display wlan client and display port-security preshared-key user commands to view the online clients. Mac-and-psk authentication configuration example network requirements z as shown in figure 5-4 , a fat ap is connected to a radius server through a layer 2 switch, and they ar...
Page 29
5-14 authorization, and accounting servers as 12345678, specify the extended radius server type, and configure the scheme to exclude the isp domain name from the usernames sent to the radius server. [ap] radius scheme rad [ap-radius-rad] primary authentication 10.1.1.88 [ap-radius-rad] primary accou...
Page 30
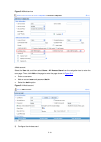
5-15 figure 5-5 add access device # add service. Select the service tab, and then select access service > access device from the navigation tree to enter the add service page. Then click add on the page to enter the following configuration page. Set the service name to mac, and the others keep the d...
Page 31
5-16 z add an account and password 00146c8a43ff. Z select the service mac. Figure 5-7 add account 3) verify the configuration z after the client passes the mac-and-psk authentication, the client can associate with the ap and access the wlan. Z you can use the display wlan client command, display con...
Page 32
5-17 [ap] dot1x authentication-method eap # configure a radius scheme name rad. Configure the ip addresses of both the primary authentication and authorization servers as 10.18.1.88, the shared key of the authentication, authorization, and accounting servers as 12345678, and configure the scheme to ...
Page 33
5-18 2) configure the radius server (imc) the following takes the imc (the imc versions are imc plat 3.20-r2602 and imc uam 3.60-e6102) as an example to illustrate the basic configurations of the radius server. # add access device. Log in to the imc management platform. Select the service tab, and t...
Page 34
5-19 figure 5-10 add service # add account. Select the user tab, and then select users > all access users from the navigation tree to enter the user page. Then, click add on the page to enter the page shown in figure 5-11 . Z enter a username. Z add an account user and password dot1x. Z select the d...
Page 35
5-20 double click the icon at the bottom right corner of your desktop. The wireless network connection status window appears. Click the properties button in the general tab. The wireless network connection properties window appears. In the wireless networks tab, select wireless network with the ssid...
Page 36
5-21 figure 5-12 configure the wireless card (i).
Page 37
5-22 figure 5-13 configure the wireless card (ii).
Page 38
5-23 figure 5-14 configure the wireless card (iii) 4) verify the configuration. Z the client can pass 802.1x authentication and associate with the ap. Z you can use the display wlan client command, display connection command and display dot1x command to view the online clients. Dynamic wep encryptio...
Page 39
5-24 figure 5-15 network diagram for dynamic wep encryption-802.1x authentication configuration procedure 1) configure the ap system-view [sysname] port-security enable [sysname] dot1x authentication-method eap # create radius scheme rad, and specify the extendedradius server type. [sysname] radius ...
Page 40
5-25 2) configure the radius server (imc) see configure the radius server (imc) . 3) configure the wireless card see configure the wireless card . Configuration verification z after inputting username user and password dot1x in the popup dialog box, the client can associate with the ap and access th...
Page 41
5-26 wpa for wpa, the wlan-wsec module supports the ccmp and tkip ciphers as the pair wise ciphers and wep cipher suites will only be used as group cipher suites. Below are the cipher suite combinations that wlan-wsec supports for wpa (wep40, wep104 and wep128 are mutually exclusive). Unicast cipher...
Page 42: Wlan Rrm Configuration
6-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 43
6-2 task remarks configuring data transmission rates optional configuring power constraint optional configuring only non-802.11h channels to be scanned optional enabling 802.11g protection optional configuring data transmission rates configuring 802.11a/802.11b/802.11g rates follow these steps to co...
Page 44: Configuring Power Constraint
6-3 for example, if you specify the maximum mcs index as 5 for mandatory rates, rates corresponding to mcs indexes 0 through 5 are configured as 802.11n mandatory rates. Mandatory rates must be supported by the ap and the clients that want to associate with the ap. Supported rates allow some clients...
Page 45: Enabling 802.11G Protection
6-4 configuring only non-802.11h channels to be scanned configuring only non-802.11h channels to be scanned follow these steps to configure only non-802.11h channels to be scanned: to do… use the command… remarks enter system view system-view — enter wlan rrm view wlan rrm — configure only non-802.1...
Page 46: Wlan Ids Configuration
7-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 47
7-2 z ad-hoc mode: a station in ad-hoc mode can directly communicate with other stations without support from any other device. Wlan ids ips wlan ids ips is a sub-feature of wlan ids. Wlan ids ips supports detection of the following attacks: z flood attack z weak iv attack z spoofing attack wlan ids...
Page 49
7-4 when an ap receives an 802.11 frame, it checks the source mac address of the frame and processes the frame as follows: 1) if the source mac address does not match any entry in the white list, the frame is dropped. If there is a match, the frame is considered valid and will be further processed. ...
Page 50
7-5 configuring static white and black lists follow these steps to configure static white and black lists: to do… use the command… remarks enter system view system-view — enter wlan ids view wlan ids — add an entry into the white list whitelist mac-address mac-address optional add an entry into the ...
Page 51
7-6 figure 7-2 wlan ids frame filtering configuration configuration procedure # add mac address 0000-000f-1211 of client 1 into the blacklist. System-view [ap] wlan ids [ap-wlan-ids] static-blacklist mac-address 0000-000f-1211 after the above configuration, client 1 cannot access the ap, and other c...
Page 52: Wlan Qos Configuration
8-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 53
8-2 4) cac connection admission control (cac) limits the number of clients that are using high-priority acs (ac-vo and ac-vi) to guarantee sufficient bandwidth for existing high-priority traffic. 5) u-apsd unscheduled automatic power-save delivery (u-apsd) is a new power saving mechanism defined by ...
Page 54
8-3 figure 8-1 per-ac channel contention parameters in wmm cac admission policies cac requires that a client obtain permission of the ap before it can use a high-priority ac (ac-vo or ac-vi) for transmission, thus guaranteeing required bandwidth to the clients that have gained accesses. Cac controls...
Page 55: Wmm Configuration
8-4 svp svp can assign packets with the protocol id 119 in the ip header to a specific ac. Svp stipulates that random backoff is not performed for svp packets. Therefore, you can set both ecwmin and ecwmax to 0 when there are only svp packets in an ac. Ack policy wmm defines two ack policies: normal...
Page 57: Wmm Configuration Examples
8-6 table 8-2 default edca parameters for aps ac aifsn ecwmin ecwmax txop limit ac-bk 7 4 10 0 ac-be 3 4 6 0 ac-vi 1 3 4 94 ac-vo 1 2 3 47 displaying and maintaining wmm to do... Use the command… remarks display the wmm statistics of the specified client or clients. Display wlan statistics client { ...
Page 58
8-7 [ap-ethernet1/0/1] quit # create a clear-type wlan service template, configure its ssid as market, configure its authentication method as open-system, and then enable the wlan service template. [ap] wlan service-template 1 clear [ap-wlan-st-1] ssid market [ap-wlan-st-1] authentication-method ope...
Page 59: Troubleshooting
8-8 # create a clear-type wlan service template, configure its ssid as market, configure its authentication method as open-system, and then enable the wlan service template. [ap] wlan service-template 1 clear [ap-wlan-st-1] ssid market [ap-wlan-st-1] authentication-method open-system [ap-wlan-st-1] ...
Page 60
8-9 solution 1) use the wmm enable command to enable the wmm function. 2) check the state of the svp priority mapping function or cac again..
Page 61: Wds Configuration
9-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 62
9-2 z easy to deploy in scenarios of metro, company, office, large warehouses, manufacturing, ports and waterfronts and so on deployment scenarios the wds feature provides the following three topologies as required by actual applications. Point to point bridge connection as shown in figure 9-1 , ap ...
Page 63: Wds Configuration Task List
9-3 figure 9-3 mesh bridging mp 2 mp 1 lan segment 2 lan segment 1 mp 4 mp 3 wds configuration task list complete the following tasks to configure wds: task remarks configuring wds port security required configuring a mesh profile required configuring an mp policy optional mapping a mesh profile to ...
Page 64
9-4 for more information about the port-security tx-key-type, port-security preshared-key, and port-security port-mode commands, see port security in the security command reference. Configuring a mesh profile a mesh profile is created and mapped to an mp so that it can provide wds services to other ...
Page 65
9-5 to do… use the command… remarks configure the link saturation rssi link-saturation-rssi value optional 100 dbm by default configure the probe request interval probe-request-interval interval-value optional by default, the probe request interval is 1000 ms. Configure the link rate mode link rate-...
Page 66: Wds Configuration Examples
9-6 specifying a peer mac address on the radio you need to specify the mac addresses of allowed peers on the local radio interface. Follow these steps to specify a peer mac address on a radio interface: to do… use the command… remarks enter system view system-view — enter radio interface view interf...
Page 67
9-7 figure 9-4 wds point to point configuration ap 2 ap 1 lan segment 2 lan segment 1 configuration procedure because the wds point to point configuration made on the two aps are similar, the following only gives the configuration on ap 1. # enable port security. System-view [ap1] port-security enab...
Page 68
9-8 [ap1-wlan-radio1/0/1] mesh-profile 1 the configuration of ap 2 is the same as that of ap 1. You only need to configure the peer mac address as the mac address of ap 1. Configuration verification after the devices on the two ends of the wds link are configured, you can use the display command to ...
Page 69: Wlan Service Configuration
10-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the int...
Page 70
10-2 fat ap a fat ap controls and manages all associated wireless stations and bridges frames between wired and wireless networks. Ssid the service set identifier. A client scans all networks at first, and then selects a specific ssid to connect to a specific wireless network. Wireless medium a medi...
Page 71
10-3 figure 10-2 active scanning (the ssid of the probe request is null, that is, no ssid information is carried) z when the wireless client is configured to access a specific wireless network or has already been connected to a wireless network, the client periodically unicasts a probe request carry...
Page 72: 802.11 Overview
10-4 authentication to secure wireless links, a wireless client must be authenticated before accessing an ap, and only wireless clients passing the authentication can be associated with the ap. 802.11 links define two authentication mechanisms: open system authentication and shared key authenticatio...
Page 73: Wlan Topologies
10-5 z ethernet to dot11 frame conversion z keep alive mechanism z idle timeout mechanism z clear channel search wlan topologies wlan has the following topologies: z single bss z multiple ess z single ess multiple bss single bss coverage of an access point is called a basic service set (bss). Each b...
Page 74
10-6 figure 10-6 multiple ess network generally, fat ap can provide more than one logical ess at the same time. The configuration of ess in fat ap can broadcast the current information of ess by beacon or probe response frames. Client can select an ess it is interested to join. The different ess dom...
Page 75: Protocols and Standards
10-7 protocols and standards for more information on protocols and standards, see: z ansi/ieee std 802.11, 1999 edition z ieee std 802.11a z ieee std 802.11b z ieee std 802.11g z ieee std 802.11i z ieee std 802.11-2004 configuring wlan service wlan service configuration includes wlan global configur...
Page 76
10-8 to do… use the command… remarks enter system view system-view — specify the country code wlan country-code code required by default the country code is cn. For relations between country codes and countries, see wlan command reference. Configuring a service template wlan service template include...
Page 78
10-10 to do… use the command… remarks set the maximum number of attempts for transmitting a frame larger than the rts threshold long-retry threshold count optional the default count is 4. Specify the maximum number of attempts to transmit a frame shorter than the rts threshold short-retry threshold ...
Page 79: Configuring Uplink Detection
10-11 to do… use the command… remarks enable the short gi function short-gi enable optional enabled by default. Enable the a-msdu function a-msdu enable optional enabled by default. Enable the a-mpdu function a-mpdu enable optional enabled by default. Z support for the configuration of 802.11n rates...
Page 80
10-12 to do… use the command… remarks enter system view system-view — specify the uplink interface (ethernet interface) wlan uplink-interface interface-type interface-number optional by default, no interface is configured as an uplink interface. Specify the uplink interface (radio interface) wlan up...
Page 81
10-13 figure 10-10 user isolation network diagram as shown in figure 10-10 , after the fat ap is enabled with user isolation, clients 1 through 4 cannot access each other directly, or learn one another’s mac and ip addresses. Enabling wlan client isolation follow these steps to enable wlan client is...
Page 82
10-14 configuration procedure 1) configuration on the fat ap # create a wlan bss interface. System-view [ap] interface wlan-bss 1 [ap-wlan-bss1] quit # configure a clear-type service template, and configure its ssid as service, specify the open-system authentication mode, and enable the wlan service...
Page 83
10-15 configuration procedure 1) configuration on the fat ap # create a wlan-ess interface. System-view [ap] interface wlan-bss 1 [ap-wlan-bss1] quit # configure a clear-type service template, and configure its ssid as service, specify the open-system authentication mode, and enable the wlan service...
Page 84: Index
11-1 11 index 802.11 overview 10-4 c configuration task list 6-1 configuring data transmission rates 6-2 configuring ids attack detection 7-3 configuring only non-802.11h channels to be scanned 6-4 configuring power constraint 6-3 configuring uplink detection 10-11 configuring wids-frame filtering 7...