- DL manuals
- Raritan
- Gateway
- CC-SG
- Administrator's Manual
Raritan CC-SG Administrator's Manual
Summary of CC-SG
Page 1
Commandcenter ® secure gateway cc-sg administrator guide release 3.1 copyright © 2007 raritan, inc. Cca-0d-e january 2007 255-80-5140-00
Page 2
This page intentionally left blank..
Page 3
Copyright and trademark information this document contains proprietary information that is protected by copyright. All rights reserved. No part of this document may be photocopied, reproduced, or translated into another language without express prior written consent of raritan, inc. © copyright 2007...
Page 4
Safety guidelines to avoid potentially fatal shock hazard and possible damage to raritan equipment: • do not use a 2-wire power cord in any product configuration. • test ac outlets at your computer and monitor for proper polarity and grounding. • use only with grounded outlets at both the computer a...
Page 5
C ontents i contents chapter 1: introduction ......................................... 1 prerequisites.................................................................................................................................1 intended audience ....................................................
Page 6
Ii c ontents upgrade device .................................................................................................................................47 backup device configuration..............................................................................................................47 ...
Page 7
C ontents iii add node groups ..............................................................................................................................91 edit node group ................................................................................................................................
Page 8
Iv c ontents restore cc-sg.........................................................................................................................139 saving and deleting backup files......................................................................................................140 reset cc-sg...
Page 9
C ontents v appendix a: specifications (g1, v1, and e1) ........................ 211 g1 platform .............................................................................................................................211 general specifications ......................................................
Page 10
Vi f igures figures figure 1 login window .................................................................................................................................. 3 figure 2 ip specification window................................................................................................
Page 11
F igures vii figure 52 custom view screen...................................................................................................................... 54 figure 53 selecting a custom view...........................................................................................................
Page 12
Viii f igures figure 105 ldap general settings .............................................................................................................. 111 figure 106 ldap advanced settings ...........................................................................................................
Page 13
F igures ix figure 158 modems tab ............................................................................................................................. 157 figure 159 extra initialization commands ..................................................................................................
Page 14
X f igures figure 211 displaying cc-sg processes in diagnostic console...................................................................... 209 figure 212 ntp not configured in cc-sg gui ............................................................................................. 210 figure 213 ntp...
Page 15
C hapter 1: i ntroduction 1 chapter 1: introduction congratulations on your purchase of commandcenter secure gateway (cc-sg), raritan’s convenient and secure method for managing various unix servers, firewalls, routers, load balancers, power management devices, and windows servers. Cc-sg provides ce...
Page 16
2 c ommand c enter s ecure g ateway a dministrator g uide are managed by cc-sg. These devices control the target servers and systems that are connected to them. • director client—a java-based client for cc-sg useable by both normal access users and administrators. It is the only client that permits ...
Page 17
C hapter 2: a ccessing cc-sg 3 chapter 2: accessing cc-sg once you have configured cc-sg with an ip address, the cc-sg unit can be placed at its final destination. Make all necessary hardware connections to make the unit operational. You can access cc-sg in several ways, each described in this chapt...
Page 18
4 c ommand c enter s ecure g ateway a dministrator g uide thick client access the cc-sg thick client allows you to connect to cc-sg by launching a java web start application instead of running an applet through a web browser. The advantage of using the thick client instead of a browser is that the c...
Page 19
C hapter 2: a ccessing cc-sg 5 9. Type your username and password in the corresponding fields,and then click login to continue. Use the thick client once the thick client is installed, there are 2 different ways to access it on your client computer. These are determined by the java version you are u...
Page 20
6 c ommand c enter s ecure g ateway a dministrator g uide cc-sg window components upon valid login, the cc-sg application window appears. Figure 3 cc-sg window components 1. Nodes tab: click the nodes tab to display all known target nodes in a tree view. Click a node to view the node profile. Interf...
Page 21
C hapter 2: a ccessing cc-sg 7 check ip address, firmware version, and application versions after logging in, you should confirm the ip address, set the cc-sg server time, and check the firmware and application versions installed. You may need to upgrade the firmware and applications. Confirm ip add...
Page 22
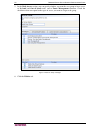
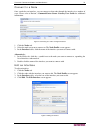
8 c ommand c enter s ecure g ateway a dministrator g uide set the cc-sg server time 1. Log onto cc-sg. 2. On the administration menu, click configuration to open the configuration manager screen. 3. Click the time/date tab. Figure 5 time/date configuration 4. On the administration menu, click config...
Page 23
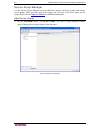
C hapter 2: a ccessing cc-sg 9 check and upgrade cc-sg firmware version 1. Log onto cc-sg. 2. On the help menu, click about raritan secure gateway. A pop-up window containing the firmware version number appears. Click ok. 3. If the version is not current, you must upgrade your firmware. You can down...
Page 24
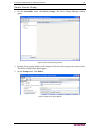
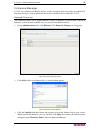
10 c ommand c enter s ecure g ateway a dministrator g uide check and upgrade application versions check and upgrade the cc-sg applications, for example, raritan console (rc) and raritan remote client (rrc). 1. On the administration menu, click applications. Figure 7 cc-sg application manager 2. Clic...
Page 25
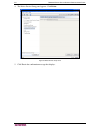
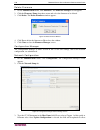
C hapter 2: a ccessing cc-sg 11 power down cc-sg if a v1 unit loses ac power while it is up and running cc-sg, the v1 unit will remember its last power state. Once ac power is restored, the v1 unit automatically reboots. However, if a v1 unit loses ac power when it is powered off, the v1 unit will r...
Page 26
12 c ommand c enter s ecure g ateway a dministrator g uide this page intentionally left blank..
Page 27
C hapter 3: c onfiguring cc-sg with g uided s etup 13 chapter 3: configuring cc-sg with guided setup prepare to configure cc-sg with guided setup before proceeding with cc-sg configuration, you must complete system configuration. • configure and install dominion series and ip-reach appliances (both ...
Page 28
14 c ommand c enter s ecure g ateway a dministrator g uide • create groups —categorize the devices and nodes that cc-sg manages into groups and create full access policies for each group. • user management —add users and user groups to cc-sg, and select the policies and privileges that will govern u...
Page 29
C hapter 3: c onfiguring cc-sg with g uided s etup 15 • to delete an element, select its row, and then click the delete row icon to delete the selected element from the elements table. 5. Repeat these steps until you have added all the elements within the category to the elements table. 6. If you wa...
Page 30
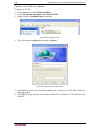
16 c ommand c enter s ecure g ateway a dministrator g uide 5. Check broadcast discovery if searching for devices on the same subnet on which cc-sg resides. Uncheck broadcast discovery to discover devices across all subnets. 6. Click discover. 7. When the discovery is complete, a confirmation message...
Page 31
C hapter 3: c onfiguring cc-sg with g uided s etup 17 9. In the table of discovered devices, select the device you want to add to cc-sg, and then click add. The add device panel opens. The add device panel is slightly different depending on the type of device you are adding. Figure 13 guided setup –...
Page 32
18 c ommand c enter s ecure g ateway a dministrator g uide 20. If you want the element to apply to the device and to the nodes connected to the device, check the apply to nodes checkbox. 21. If you want to add another device, click apply to save this device, and then repeat the steps in this section...
Page 33
C hapter 3: c onfiguring cc-sg with g uided s etup 19 b. In the available list, select the device you want to add to the group, and then click add to move the device into the selected list. Devices in the selected list will be added to the group. • if you want to remove a device from the group, sele...
Page 34
20 c ommand c enter s ecure g ateway a dministrator g uide select nodes a. Click the select nodes tab in the add nodes groups panel. Figure 15 guided setup—add node groups, select nodes b. In the available list, select the node you want to add to the group, and then click add to move the node into t...
Page 35
C hapter 3: c onfiguring cc-sg with g uided s etup 21 f. When you have finished adding node groups, click ok. The group summary panel displays a list of the groups that you added. Figure 16 guided setup--group summary g. Click continue to start the next task, user management. Follow the steps in the...
Page 36
22 c ommand c enter s ecure g ateway a dministrator g uide 5. In the node access section, you can specify whether you want the user group to have access to in band and out of band nodes, and to power management functions. Check the checkboxes that correspond to the types of access you want to assign...
Page 37
C hapter 3: c onfiguring cc-sg with g uided s etup 23 7. In the all policies list, select the policy that you want to assign to the user group then click add to move the policy to the selected policies list. Policies in the selected policies list will be assigned to the user group. Repeat this step ...
Page 38
24 c ommand c enter s ecure g ateway a dministrator g uide 20. Click the user group drop-down arrow and select the user group to which you want to assign the user from the list. 21. If you want to add another user, click apply to save this user, and then repeat the steps in this section to add addit...
Page 39
C hapter 4: c reating a ssociations 25 chapter 4: creating associations associations you can set up associations to help organize the equipment that cc-sg manages. Each association includes a category, which is the top-level organizational group, and its related elements, which are subsets of a cate...
Page 40
26 c ommand c enter s ecure g ateway a dministrator g uide • devices—are raritan products such as dominion kx, dominion sx, dominion ksx, ip- reach, paragon ii system controller, paragon ii umt832 with ustip, and others, that cc- sg manages. These devices control the target systems, or nodes, that a...
Page 41
C hapter 4: c reating a ssociations 27 how to create associations there are two ways to create associations, guided setup and association manager. • guided setup combines many configuration tasks into an automated interface. Guided setup is recommended for your initial cc-sg configuration. Once you ...
Page 42
28 c ommand c enter s ecure g ateway a dministrator g uide 2. Click add in the category panel to add a new category. The add category window appears. Figure 21 add category window 3. Type a category name in the category name field. Maximum length is 31 characters. 4. Click the value type drop-down a...
Page 43
C hapter 4: c reating a ssociations 29 delete category deleting a category deletes all of the elements created within that category. The deleted category will no longer appear in the nodes or devices trees once the screen refreshes or the user logs out and then logs back into cc-sg. 1. On the associ...
Page 44
30 c ommand c enter s ecure g ateway a dministrator g uide 3. Click add in the elements for category panel to add a new element. The add element window appears. Figure 25 add element window 4. Type the new element name in the enter value for element field. 5. Click ok to add the element or cancel to...
Page 45
C hapter 4: c reating a ssociations 31 3. Select the element to be deleted from the element for category list, and then click delete in the elements for category panel. The delete element window appears. Figure 27 delete element window 4. Click yes to delete the element or no to close the window. Th...
Page 46
32 c ommand c enter s ecure g ateway a dministrator g uide this page intentionally left blank..
Page 47
C hapter 5: a dding d evices and d evice g roups 33 chapter 5: adding devices and device groups you must add raritan devices, such as dominion series devices and ip-reach units, to cc-sg before you can use cc-sg to configure and manage them. The devices menu offers all the functions related to devic...
Page 48
34 c ommand c enter s ecure g ateway a dministrator g uide device and port icons for easier identification, kvm, serial, and power devices and ports have different icons in the devices tree. Hold the mouse pointer over an icon in the devices tree to view a tool tip containing information about the d...
Page 49
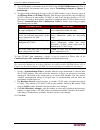
C hapter 5: a dding d evices and d evice g roups 35 search for devices the devices tab provides the ability to search for devices within the tree. Searching will only return devices as results and will not include port names. The method of searching can be configured through the my profile screen de...
Page 50
36 c ommand c enter s ecure g ateway a dministrator g uide add a device devices must be added to cc-sg before you can configure ports or add out-of-band interfaces to nodes through those ports. Add device is used to add devices whose properties you know and can provide to cc-sg. To add a device to c...
Page 51
C hapter 5: a dding d evices and d evice g roups 37 21. A list of categories and elements can be configured to better describe and organize this device and the nodes connected to it. Please refer to chapter 4: creating associations for additional information. To configure categories and elements: a....
Page 52
38 c ommand c enter s ecure g ateway a dministrator g uide 4. Click the number of outlets drop-down menu and select the number of outlets this power strip contains. 5. Click the managing device drop-down menu, and then select the device that you will use to manage this power strip from the list. 6. ...
Page 53
C hapter 5: a dding d evices and d evice g roups 39 4. To search for a particular type of device, select it in the list of device types. By default, all device types are selected. Use ctrl+click to select more than one device type. 5. Check include ipmi agents if you want to find targets that provid...
Page 54
40 c ommand c enter s ecure g ateway a dministrator g uide operation. You can upgrade the device firmware after adding the device to cc-sg. Please refer to upgrade devices later in this chapter for additional information. Edit device you can edit a device to rename it and modify its properties. 1. C...
Page 55
C hapter 5: a dding d evices and d evice g roups 41 delete device you can delete a device to remove it from cc-sg management. Important: deleting a device will remove all ports configured for that device. All interfaces associated with those ports will be removed from the nodes. If no other interfac...
Page 56
42 c ommand c enter s ecure g ateway a dministrator g uide configure ports if the ports of a device were not all automatically added by checking configure all ports when you added the device in the add device screen, you can use the configure ports screen to add individual ports or a set of ports on...
Page 57
C hapter 5: a dding d evices and d evice g roups 43 3. Click the configure button that corresponds to the serial port you want to configure. The configure serial port screen appears. Figure 38 configure serial ports screen 4. Type a port name in port name field. For ease of use, name the port after ...
Page 58
44 c ommand c enter s ecure g ateway a dministrator g uide configure a kvm port 1. Click the devices tab and select a kvm device from the devices tree. 2. On the devices menu, click port manager, and then click configure ports. The configure ports screen appears. Figure 39 configure ports screen • c...
Page 59
C hapter 5: a dding d evices and d evice g roups 45 5. Type a node name in the node name field to create a new node with an out-of-band interface from this port. For ease of use, name the node after the target that is connected to the port. This means that you will type the same name in the port nam...
Page 60
46 c ommand c enter s ecure g ateway a dministrator g uide delete ports delete a port to remove the port entry from a device. Important: if you delete a port that is associated with a node, the associated out-of-band kvm or serial interface provided by the port will be removed from the node. If the ...
Page 61
C hapter 5: a dding d evices and d evice g roups 47 5. To remove a device from the selected devices list, select the device, and then click . 6. Click ok to bulk copy or cancel to exit without copying. A device copied successfully message confirms that device categories and elements have been copied...
Page 62
48 c ommand c enter s ecure g ateway a dministrator g uide restore device configuration you can restore a previously backed-up device configuration to a device. 1. Click the devices tab and select the device you want to restore to a backup configuration. 2. On the devices menu, click device manager,...
Page 63
C hapter 5: a dding d evices and d evice g roups 49 restart device use the restart device function to restart a device. 1. Click the devices tab and select the device you want to restart. 2. On the devices menu, click device manager, and then click restart device. The restart device screen appears. ...
Page 64
50 c ommand c enter s ecure g ateway a dministrator g uide device power manager device power manager is used to view the status of a powerstrip device (including voltage, current, and temperature) as well as manage all power outlets on a powerstrip device. As opposed to powering nodes on and off ind...
Page 65
C hapter 5: a dding d evices and d evice g roups 51 topological view topological view displays the structural setup of all the connected appliances in your configuration. 1. Click the devices tab and select the device whose topological view you want to see. 2. On the devices menu, click device manag...
Page 66
52 c ommand c enter s ecure g ateway a dministrator g uide disconnect users administrators can terminate any user's session with a device. This includes users who are performing any kind of operation on a device, such as connecting to ports, backing up the configuration of a device, restoring a devi...
Page 67
C hapter 5: a dding d evices and d evice g roups 53 viewing devices cc-sg offers different options for displaying devices in the devices tab. Tree view select tree view to view devices in the devicestree grouped in the default view. Selecting tree view will also return you to the standard view from ...
Page 68
54 c ommand c enter s ecure g ateway a dministrator g uide 2. On the devices menu, click change view, then click create custom view.The custom view screen appears. Figure 52 custom view screen 3. To customize your view, click the name drop-down arrow and select a custom view that has already been sa...
Page 69
C hapter 5: a dding d evices and d evice g roups 55 2. On the devices menu, click change view, and then click create custom view.The custom view screen appears. 3. In the custom view panel, click add. An add custom view window appears. 4. Type a new custom view name, and then click ok or click cance...
Page 70
56 c ommand c enter s ecure g ateway a dministrator g uide special access to paragon ii system devices paragon ii system controller (p2-sc) paragon ii system integration users can add their p2-sc devices to the cc-sg devices tree and configure them via the p2-sc admin application from within cc-sg. ...
Page 71
C hapter 5: a dding d evices and d evice g roups 57 ip-reach and ust-ip administration you can also perform administrative diagnostics on ip-reach and ust-ip devices connected to your paragon system setup directly from the cc-sg interface. After adding the paragon system device to cc-sg, it appears ...
Page 72
58 c ommand c enter s ecure g ateway a dministrator g uide device group manager use the device groups manager screen to add device groups, edit device groups, and remove device groups. When you add a new device group, you can create a full access policy for the group. Please refer to chapter 8: poli...
Page 73
C hapter 5: a dding d evices and d evice g roups 59 2. Click the new group icon in the toolbar. The device group: new panel displays. Figure 58 device group: new panel, select devices tab 3. In the group name field, type a name for a device group you want to create. 4. There are two ways to add devi...
Page 74
60 c ommand c enter s ecure g ateway a dministrator g uide describe devices a. Click the describe devices tab in the device group: new panel. In the describe devices tab, you create a table of rules that describe the devices you want to assign to the group. Figure 59 describe devices tab b. Click th...
Page 75
C hapter 5: a dding d evices and d evice g roups 61 description only requires a single rule, then simply type that rule’s name in the field. If multiple rules are being evaluated, type the rules into the field using a set of logical operators to describe the rules in relation to each other: • & - th...
Page 76
62 c ommand c enter s ecure g ateway a dministrator g uide edit device group 1. On the associations menu, click device groups. Thedevice groups manager window opens. Figure 60 device groups manager screen 2. Existing device groups display in the left panel.. Select the device group whose name you wa...
Page 77
C hapter 5: a dding d evices and d evice g roups 63 delete device group 1. On the associations menu, click device groups. Thedevice groups manager window opens. Figure 61 device groups manager screen 2. Existing device groups display in the left panel. Select the device group you want to delete. The...
Page 78
64 c ommand c enter s ecure g ateway a dministrator g uide 4. The delete device group panel appears. Click delete. Figure 63 delete device group panel 5. Click yes in the confirmation message that displays..
Page 79
C hapter 6: c onfiguring n odes and n ode g roups 65 chapter 6: configuring nodes and interfaces this chapter discusses how to view, configure, and edit nodes and their associated interfaces. Please refer to raritan’s commandcenter secure gateway user guide for additional information on connecting t...
Page 80
66 c ommand c enter s ecure g ateway a dministrator g uide nodes and interfaces overview about nodes each node represents a target that is accessible through cc-sg, either via in-band (direct ip) or out-of band (connected to a raritan device) methods. For example, a node can be a server in a rack co...
Page 81
C hapter 6: c onfiguring n odes and n ode g roups 67 add node to add a new node to cc-sg: 1. Click the nodes tab. 2. On the nodes menu, click add node. The node profile screen appears. Figure 65 add node screen 3. Type a name for the node in the node name field. All node names in cc-sg must be uniqu...
Page 82
68 c ommand c enter s ecure g ateway a dministrator g uide 2. Click the interface type drop-down menu and select the type of connection being made to the node: in-band connections • drac kvm: select this item to create a kvm connection to a dell drac server through the drac interface. You will be re...
Page 83
C hapter 6: c onfiguring n odes and n ode g roups 69 for in-band connections and drac, rsa, and ilo/riloe power connections: figure 66 add interface—in-band ilo/riloe kvm 1. Type the ip address or hostname for this interface in the ip address/hostname field. 2. If necessary, type a tcp port for this...
Page 84
70 c ommand c enter s ecure g ateway a dministrator g uide for out-of-band kvm, out-of-band serial connections: figure 67 configuring an out-of-band kvm connection 1. Click the application name drop-down menu and select the application you want to use to connect to the node with the interface from t...
Page 85
C hapter 6: c onfiguring n odes and n ode g roups 71 for managed power strip connections: figure 68 configuring a managed power strip power control interface 1. Click the managing device drop-down menu and select the raritan device that manages the power strip that provides power to the node. The de...
Page 86
72 c ommand c enter s ecure g ateway a dministrator g uide for ipmi power control connections: figure 69 configuring an ipmi power control interface 1. Type the ip address or hostname for this interface in the ip address/hostname field. 2. Type a udp port for this interface in the udp port field. 3....
Page 87
C hapter 6: c onfiguring n odes and n ode g roups 73 connect to a node once a node has an interface, you can connect to that node through the interface in a number of ways. Please refer to raritan’s commandcenter secure gateway user guide for additional information. Figure 70 connecting to a node's ...
Page 88
74 c ommand c enter s ecure g ateway a dministrator g uide 5. You cannot change the type of the existing interface. You can change the interface name, description, and the values of the other fields for this type. Please refer to the add interface section above for additional information. Delete an ...
Page 89
C hapter 6: c onfiguring n odes and n ode g roups 75 5. Select an existing node in the interfaces table, and then click edit or delete to edit or delete that interface from the node. Please refer to the edit an interface or delete an interface section above for additional information on this procedu...
Page 90
76 c ommand c enter s ecure g ateway a dministrator g uide chat chat provides a way for users connected to the same node to communicate with each other. You must be connected to a node to start a chat session for that node. Only users on the same node will be able to chat with each other. To engage ...
Page 91
C hapter 7: a dding and m anaging u sers and u ser g roups 77 chapter 7: adding and managing users and user groups users make up the individual users and administrators that connect to cc-sg in order to access nodes and manage devices. User groups are organizations that define a set of privileges fo...
Page 92
78 c ommand c enter s ecure g ateway a dministrator g uide special user groups cc-sg is configured with three user groups by default: cc-super user, system administrators, and cc users. Cc super-user group the cc super-user group has full administrative and access privileges. Only one user can be a ...
Page 93
C hapter 7: a dding and m anaging u sers and u ser g roups 79 add user groups creating user groups first will help you organize users when they are added. When a user group is created, a set of privileges is assigned to the user group. Users that are assigned to that group will inherit those privile...
Page 94
80 c ommand c enter s ecure g ateway a dministrator g uide 7. Click the device/node policies tab. A table of policies appears. Figure 77 the policies tab on the add user group screen the all policies table lists all the policies available on cc-sg. Each policy represents a rule allowing (or denying)...
Page 95
C hapter 7: a dding and m anaging u sers and u ser g roups 81 edit a user group edit a user group to change the existing privileges and policies for that group. Note: you cannot edit the privileges or policies of the cc-super user group and the users not in group group. To edit a group: 1. Click the...
Page 96
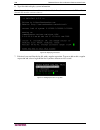
82 c ommand c enter s ecure g ateway a dministrator g uide delete user group deleting a user group removes that group from cc-sg. Users in the deleted group will remain in any other groups to which they have been assigned. If the users in the deleted group were not in any other groups, they will be ...
Page 97
C hapter 7: a dding and m anaging u sers and u ser g roups 83 a password is not required and the new password and retype new password fields will be disabled. 7. In the new password and retype new password fields, type the password that the user will use to log in to cc-sg. Note: if strong passwords...
Page 98
84 c ommand c enter s ecure g ateway a dministrator g uide 4. Uncheck login enabled if you want to prevent this user from logging in to cc-sg. Check login enabled if you want to allow this user to log into cc-sg. 5. Check remote authentication only if you want the user to be authenticated by an exte...
Page 99
C hapter 7: a dding and m anaging u sers and u ser g roups 85 assign users to group use this command to assign an existing users to a group they currently do not belong to. Users assigned in this way will be added to their new group while still existing in any group they were previously assigned to....
Page 100
86 c ommand c enter s ecure g ateway a dministrator g uide 4. On the users menu, click user manager, then delete user from group. The delete user appears displaying the user and the group they will be removed from. Figure 84 deleting a user from a group 5. Click ok to delete the user from the group ...
Page 101
C hapter 7: a dding and m anaging u sers and u ser g roups 87 b. Type your new password in the new password field. A notice will appear if strong passwords are required. C. Type your new password again in the retype new password field. 4. Type a new address in the email address field to add or chang...
Page 102
88 c ommand c enter s ecure g ateway a dministrator g uide bulk copy to save time, bulk copy can be used to clone one user’s privileges and policies to a number of other existing users by moving them to the same user groups as the selected user. To perform a bulk copy: 1. Click the users tab to the ...
Page 103
C hapter 8: p olicies 89 chapter 8: policies controlling access using policies configuring new policies to provide user access to nodes is optional, but central to making effective use of cc-sg ability to control that access. If you want to give all users access to all nodes, simply assign the full ...
Page 104
90 c ommand c enter s ecure g ateway a dministrator g uide node groups node groups are used to organize nodes into a set. This group will then become the basis for a policy either allowing or denying access to this particular set of nodes. Nodes can be grouped arbitrarily or by a set of common attri...
Page 105
C hapter 8: p olicies 91 3. If viewing a group based on attributes, click view nodes to display a list of nodes currently in the node group. A nodes in node group window will appear displaying the nodes and all their attributes. Figure 89 nodes in a group based on attributes add node groups to add a...
Page 106
92 c ommand c enter s ecure g ateway a dministrator g uide select nodes figure 90 adding nodes using select nodes 1. Click the select nodes tab. 2. Click the device name drop-down menu and select a device if you want to filter the available list to only display nodes with interfaces from that device...
Page 107
C hapter 8: p olicies 93 describe nodes figure 91 describing a node group with multiple rules 1. Click the select nodes tab. 2. Click add new row to add a row in the table for a new rule. Rules take the form of an expression which can be compared against nodes. 3. Double-click each column in the row...
Page 108
94 c ommand c enter s ecure g ateway a dministrator g uide 4. If you want to add another rule, click add new row again, and make the necessary configurations. Configuring multiple rules will allow more precise descriptions by providing multiple criteria for evaluating nodes. 5. If you want to remove...
Page 109
C hapter 8: p olicies 95 edit node group edit a node group to change the membership or description of the group. To edit a node group: 1. On the associations menu, click node group. The node groups manager window displays. Figure 92 editing a node group 2. Click the node you want to edit in the node...
Page 110
96 c ommand c enter s ecure g ateway a dministrator g uide device groups device groups operate in a similar fashion to node groups, except that device groups are used to organize raritan devices into sets for management by policies. Please refer to chapter 5: adding devices and device groups, device...
Page 111
C hapter 8: p olicies 97 5. Click the device group drop-down arrow, and select the device group this policy governs access to. Click the node group drop-down arrow and select the node group this policy governs access to. If the policy will cover only one type of group, only select a value for that g...
Page 112
98 c ommand c enter s ecure g ateway a dministrator g uide 7. In the end time field, type the time of day this policy ends. The time must be in 24-hour format. 8. In the device/node access permission field, select control to define this policy to allow access to the selected node or device group for...
Page 113
C hapter 9: c onfiguring r emote a uthentication 99 chapter 9: configuring remote authentication authentication and authorization (aa) users of cc-sg can be locally authenticated and authorized on the cc-sg or remotely authenticated using the following supported directory servers: • microsoft active...
Page 114
100 c ommand c enter s ecure g ateway a dministrator g uide distinguished names for ldap and ad configuration of remotely authenticated users on ldap or ad servers requires entering user names and searches in distinguished name format. The full dn format is described in rfc2253 . For the purposes of...
Page 115
C hapter 9: c onfiguring r emote a uthentication 101 ad configurations add ad module to cc-sg cc-sg supports authentication and authorization of users imported from an ad domain controller, without requiring that users be defined locally in cc-sg. This allows users to be maintained exclusively on th...
Page 116
102 c ommand c enter s ecure g ateway a dministrator g uide ad general settings in the general tab, you add the information that allows cc-sg to query the ad server. Figure 96 ad general settings 1. Type the ad domain you want to query in the domain field. For example, if the ad domain is installed ...
Page 117
C hapter 9: c onfiguring r emote a uthentication 103 5. Type the password for the user account you want to use to query the ad server in the password and confirm password fields. 6. Click test connection to test the connection to the ad server using the given parameters. You should receive a confirm...
Page 118
104 c ommand c enter s ecure g ateway a dministrator g uide 5. Type a user’s attributes in filter so the search query will be restricted to only those entries that meet this criterion. The default filter is objectclass=user, which means that only entries of the type user are searched. 6. Specify the...
Page 119
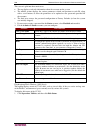
C hapter 9: c onfiguring r emote a uthentication 105 e xample d escription dc=raritan,dc=com the search query for the user in the group will be made over the whole directory structure. Cn=administrators,cn=users,dc=raritan,dc=com the search query for the user in the group will be performed only in t...
Page 120
106 c ommand c enter s ecure g ateway a dministrator g uide 2. For each domain in the trust partner column, click the trust direction drop-down menu, and then select the direction of trust you want to establish between the domains. Trust directions are updated in all ad modules when you make changes...
Page 121
C hapter 9: c onfiguring r emote a uthentication 107 3. Click import groups… to retrieve a list of user group values stored on the ad server. If any of the user groups are not already on the cc-sg, you can import them here and assign them an access policy. Figure 100 importing groups from ad server ...
Page 122
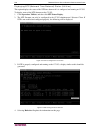
108 c ommand c enter s ecure g ateway a dministrator g uide synchronize ad user groups when you synchronize ad user groups, cc-sg retrieves the groups for the selected ad module, compares their names with the user groups that have been imported from ad, and identifies the matches. Cc-sg will present...
Page 123
C hapter 9: c onfiguring r emote a uthentication 109 8. To exit maintenance mode, on the system maintenance menu, click maintenance mode, and then click exit maintenance mode. 9. In the screen that appears, click ok. A second confirmation message will display when cc- sg exits maintenance mode. Clic...
Page 124
110 c ommand c enter s ecure g ateway a dministrator g uide 9. After you have synchronized each modules ad user groups, you should synchronize all ad modules. Please refer to synchronize all ad modules for additional information. Depending on your ad configuration, the synchronization process may ta...
Page 125
C hapter 9: c onfiguring r emote a uthentication 111 ldap general settings 1. Click the general tab. Figure 105 ldap general settings 2. Type the ip address or hostname of the ldap server in the ip address/hostname field. For hostname rules, please refer to terminology/acronyms in chapter 1: introdu...
Page 126
112 c ommand c enter s ecure g ateway a dministrator g uide 10. Click test connection to test the ldap server using the given parameters. You should receive a confirmation of a successful connection. If not, review the settings carefully for errors and try again. 11. Click next to proceed to the adv...
Page 127
C hapter 9: c onfiguring r emote a uthentication 113 sun one ldap (iplanet) configuration settings if using a sun one ldap server for remote authentication, use this example for parameter settings: p arameter n ame sun o ne ldap p arameters ip address/hostname user name cn= password basedn o=organiz...
Page 128
114 c ommand c enter s ecure g ateway a dministrator g uide add a tacacs+ module cc-sg users who are remotely authenticated by a tacacs+ server need to be created on the tacacs+ server and on cc-sg. The user name on the tacacs+ server and on cc-sg must be the same, although the passwords may be diff...
Page 129
C hapter 9: c onfiguring r emote a uthentication 115 tacacs+ general settings 1. Type the ip address or hostname of the tacacs+ server in the ip address/hostname name field. For hostname rules, please refer to terminology/acronyms in chapter 1: introduction figure 108 tacacs+ general settings 2. Typ...
Page 130
116 c ommand c enter s ecure g ateway a dministrator g uide add a radius module cc-sg users who are remotely authenticated by a radius server need to be created on the radius server and on cc-sg. The user name on the radius server and on cc-sg must be the same, although the passwords may be differen...
Page 131
C hapter 9: c onfiguring r emote a uthentication 117 radius general settings 1. Click the general tab. Figure 110 specifying a radius server 2. Type the ip address or hostname of the radius server in the ip address/hostname field. For hostname rules, please refer to terminology/acronyms in chapter 1...
Page 132
118 c ommand c enter s ecure g ateway a dministrator g uide specify modules for authentication and authorization once you have added all the external servers as modules in cc-sg, you specify whether you want cc-sg to use each of them for either authentication, authorization, or both. 1. On the admin...
Page 133
C hapter 10: g enerating r eports 119 chapter 10: generating reports reports can be sorted by clicking on the column headers. Click a column header to sort report data by the values in that column. The data will refresh in ascending order alphabetically, numerically, or chronologically. Click the co...
Page 134
120 c ommand c enter s ecure g ateway a dministrator g uide 4. Click ok to run the report. The report is generated, displaying data about activities that occurred during the designated time period that also comply with any additional parameters specified. Figure 113 audit trail report • click next o...
Page 135
C hapter 10: g enerating r eports 121 • if you want to limit the report to a particular ip address’s activities, type the user’s ip address in the user ip address field. 4. Click ok to run the report. The report is generated, displaying data about activities that occurred during the designated time ...
Page 136
122 c ommand c enter s ecure g ateway a dministrator g uide 3. You can limit the data that the report will contain by entering additional parameters in the message, device name, port name, username, and user ip address fields. • if you want to limit the report by the message text associated with an ...
Page 137
C hapter 10: g enerating r eports 123 availability report theavailability report displays the status of all connections, showing devices by name and ip address. This report gives you the full accessibility picture for all devices on your system, and supplies information that could be useful for trou...
Page 138
124 c ommand c enter s ecure g ateway a dministrator g uide active users report the active users report displays current users and user sessions. You can select active users from the report and disconnect them from cc-sg. 1. On the reports menu, click users, and then click active users. The active u...
Page 139
C hapter 10: g enerating r eports 125 locked out users report the locked out users report displays users who are currently locked out of cc-sg because they made too many unsuccessful login attempts. You can unlock users from this report. Please refer to chapter 12: advanced administration, lockout s...
Page 140
126 c ommand c enter s ecure g ateway a dministrator g uide user data report the user data report displays certain data on all users in the cc-sg database. 1. On the reports menu, click users, and then click user data. The all users’ data report is generated. Figure 121 all users’ data report • the ...
Page 141
C hapter 10: g enerating r eports 127 users in groups report the users in group report displays data on users and the groups with which they are associated. 1. On the reports menu, click users, and then click users in groups. The users in groups report is generated. Figure 122 users in groups report...
Page 142
128 c ommand c enter s ecure g ateway a dministrator g uide group data report the group data report displays user group, node group, and device group information. View user groups by name and description, view node groups by name, and view device groups by name, all in one screen. 1. On the reports ...
Page 143
C hapter 10: g enerating r eports 129 4. Click apply. The ad user group report is generated. Figure 124 ad user group report • click manage report data… to save or print the report section. Click save to save the records that are displayed in the current report page to a csv file or click save all t...
Page 144
130 c ommand c enter s ecure g ateway a dministrator g uide records. Click print to print the records that are displayed in the current report page or print all to print all records. Click close to close the window. • click refresh to generate a new report. The report may take several minutes to gen...
Page 145
C hapter 10: g enerating r eports 131 3. Click apply to generate the report. The node asset report generates. Figure 127 node asset report • click manage report data… to save or print the report. Click save to save the records that are displayed in the current report page to a csv file or click save...
Page 146
132 c ommand c enter s ecure g ateway a dministrator g uide click print to print the records that are displayed in the current report page or print all to print all records. Click close to close the window. • click close to close the report. Node creation report the node creation report lists all no...
Page 147
C hapter 10: g enerating r eports 133 query port report the query port report displays all ports according to port status. 1. On the reports menu, click ports, and then click query port. The query port screen appears. Figure 131 query port screen 2. In the select port status section, check the check...
Page 148
134 c ommand c enter s ecure g ateway a dministrator g uide 4. Click apply to generate the report. Figure 132 query port report • click the arrow icons at the bottom right of the report to navigate through multiple page reports. • click configure next to a new or unused port in the report to configu...
Page 149
C hapter 10: g enerating r eports 135 • to disconnect a port from a current session, select the port you want to disconnect, and then click disconnect. • click manage report data… to save or print the report. Click save to save the records that are displayed in the current report page to a csv file ...
Page 150
136 c ommand c enter s ecure g ateway a dministrator g uide 2. Select a last discovered date,and then click get targets. The targets that were discovered on or earlier than the last discovered date are displayed under targets discovered. • if you want to purge a target from the cc-sg database, selec...
Page 151
C hapter 11: s ystem m aintenance 137 chapter 11: system maintenance maintenance mode this mode restricts access to cc-sg so that an administrator can perform various operations without disruption. Operations can be performed from the gui or from an ssh command line interface via clients, such as pu...
Page 152
138 c ommand c enter s ecure g ateway a dministrator g uide backup cc-sg best practice is to enter maintenance mode before backing up cc-sg. 1. On the system maintenance menu, click backup. The backup commandcenter screen appears. Figure 136 backup commandcenter screen 2. Type a name for this backup...
Page 153
C hapter 11: s ystem m aintenance 139 c. If you are not using the default port for the selected protocol (ftp: 21, sftp: 22) type the communications port used in the port number field. D. Type a username for the remote server in the username field. E. Type a password for the remote server in the pas...
Page 154
140 c ommand c enter s ecure g ateway a dministrator g uide • custom – allows you to specify which components of the backup to restore to cc-sg by checking them in the restore options area below. Check each of the following to include them in the restore: a. Data – cc-sg configuration, device and no...
Page 155
C hapter 11: s ystem m aintenance 141 to delete a backup 1. From the available backups table, select the backup you want to delete. 2. Click delete. A confirmation dialog appears. 3. Click ok to delete the backup from the cc-sg system or cancel to exit without deleting. Once deleted, the file backup...
Page 156
142 c ommand c enter s ecure g ateway a dministrator g uide 2. Type your password in the password field. 3. Accept the default message or type a warning message to display to any users currently online in the broadcast message field (for example, you might give users a brief time period to finish th...
Page 157
C hapter 11: s ystem m aintenance 143 1. On the system maintenance menu, click shutdown commandcenter. The shutdown commandcenter screen appears. Figure 142 shutdown cc-sg screen 2. Type your password in the password field. 3. Accept the default message or type a message to display to any users curr...
Page 158
144 c ommand c enter s ecure g ateway a dministrator g uide this page intentionally left blank..
Page 159
C hapter 12: a dvanced a dministration 145 chapter 12: advanced administration guided setup guided setup steps an administrator through some of the most common tasks on cc-sg: creating associations, setting up raritan devices, creating user groups and creating users. For information on running guide...
Page 160
146 c ommand c enter s ecure g ateway a dministrator g uide 5. Click ok to save your settings to cc-sg. Application manager the application manager provides an interface for administrators to add access applications to cc-sg, edit existing applications and set the default application for accessing n...
Page 161
C hapter 12: a dvanced a dministration 147 5. Click ok when the necessary devices have been selected to work with the application. An open dialog window will appear. 6. In the open dialog window, browse for the location of your application file (usually a .Jar or .Cab file), select the file, and the...
Page 162
148 c ommand c enter s ecure g ateway a dministrator g uide default applications click the default applications tab to view and edit the current default applications for various interfaces and port types. Applications listed here will become the default choice when configuring a node to allow access...
Page 163
C hapter 12: a dvanced a dministration 149 firmware manager cc-sg stores firmware for raritan devices in order to update the devices under its control. The firmware manager is used to upload and delete device firmware files to and from cc-sg. Upload firmware this command allows you to upload differe...
Page 164
150 c ommand c enter s ecure g ateway a dministrator g uide delete firmware 1. On the administration menu, click firmware. The firmware manager screen appears. 2. Click the firmware name drop-down arrow and select the firmware to be deleted. 3. Click delete. The delete firmware window appears. Figur...
Page 165
C hapter 12: a dvanced a dministration 151 the fully-qualified domain name (fqdn) if a domain server and domain suffix has been configured. 4. Click either primary/backup mode or active/active mode. A cc-sg provides two network interface controllers (nic). The nics on a g1 or v1 unit are labeled lef...
Page 166
152 c ommand c enter s ecure g ateway a dministrator g uide b. Choose active/active mode if you have special network conditions; particularly if you have two networks where routing may not exist. If network security is important and if you are using proxy-type deployments, you also should choose thi...
Page 167
C hapter 12: a dvanced a dministration 153 8. If you chose active/active mode, follow steps 5 through 7 to configure the second network interface. 9. Click update configuration to update the network setup of your system. 10. Click close to close the configuration manager screen. Log configuration fr...
Page 168
154 c ommand c enter s ecure g ateway a dministrator g uide purging cc-sg’s internal log: the logs tab can also be used to clear cc-sg’s log of events. This command only clears cc- sg’s log of events, it will not purge events recorded by external logging servers. 1. On the administration menu, click...
Page 169
C hapter 12: a dvanced a dministration 155 time/date configuration cc-sg’s time and date must be accurately maintained to provide credibility for its device- management capabilities. Important! The time/date configuration is used when scheduling tasks in task manager. Please refer to chapter 12: adv...
Page 170
156 c ommand c enter s ecure g ateway a dministrator g uide modem configuration use this screen to access a cc-sg g1 from a client machine over a dial-up connection. This method of accessing cc-sg can be used in emergency situations. Note: a modem is not available and cannot be configured on the v1 ...
Page 171
C hapter 12: a dvanced a dministration 157 2. Click the modems tab. Figure 158 modems tab 3. Click properties. 4. Click the advanced tab. Figure 159 extra initialization commands 5. Type an initialization command in extra initialization commands that will be used by your modem to set the “carrier de...
Page 172
158 c ommand c enter s ecure g ateway a dministrator g uide 3. Under network tasks in the network connections window, click create a new connection. Figure 160 create a new connection 4. Click next, connect to the network at my workplace, dial-up connection. 5. Type a name for cc-sg, for example com...
Page 173
C hapter 12: a dvanced a dministration 159 configure the call-back connection if the cc-sg uses a call-back connection, you need to use a script file that is described below. To supply the script file for call-back: 1. On the start menu, click my network places. 2. Click view network connections und...
Page 174
160 c ommand c enter s ecure g ateway a dministrator g uide connect to cc-sg with modem to connect to cc-sg: 1. On the start menu, click my network places. 2. Click view network connections under network tasks. 3. Double-click the commandcenter connection. Figure 164 connecting to cc-sg 4. Type a us...
Page 175
C hapter 12: a dvanced a dministration 161 7. If show terminal window was checked as described in section configure the call-back connection earlier in this chapter, then a window similar to the one below will be displayed: figure 166 after dial terminal 8. Wait 1 or 2 minutes and in a supported bro...
Page 176
162 c ommand c enter s ecure g ateway a dministrator g uide 2. Click the connection mode tab. Figure 167 configuration manager connection screen – direct mode 3. Click the radio button for the connection mode you prefer. A. Click the direct mode radio button to connect to a device directly. B. Click...
Page 177
C hapter 12: a dvanced a dministration 163 device settings 1. On the administration menu, click configuration. The configuration manager screen appears. 2. Click the device settings tab. Figure 168 configuration settings device settings screen 3. To update device default port, select a device type i...
Page 178
164 c ommand c enter s ecure g ateway a dministrator g uide 2. Click the snmp tab. Figure 169 configuration settings device settings screen 3. To identify the snmp agent running on cc-sg to a third-party enterprise management solutions, provide agent information under agent configuration. Type a por...
Page 179
C hapter 12: a dvanced a dministration 165 cluster configuration a cc-sg cluster uses two cc-sg nodes, one primary node and one secondary node, for backup security in case of primary cc-sg node failure. Both nodes share common data for active users and active connections, and all status data is repl...
Page 180
166 c ommand c enter s ecure g ateway a dministrator g uide 2. Click discover commandcenters to scan and display all cc-sg appliances on the same subset as the one you are currently using. Alternatively, you can add a cc-sg, perhaps from a different subnet, by specifying an ip address in commandcent...
Page 181
C hapter 12: a dvanced a dministration 167 set secondary cc-sg node 1. Click discover commandcenters to scan and display all cc-sg appliances on the same subset as your one you are currently using. Alternatively, you can add a cc-sg, perhaps from a different subnet, by specifying an ip address in co...
Page 182
168 c ommand c enter s ecure g ateway a dministrator g uide recover a failed cc-sg node when a node fails and failover occurs, the failed node will recover in waiting status. 1. Select the waiting node in the cluster configuration table. 2. Add it as a backup node by clicking join “waiting” node. 3....
Page 183
C hapter 12: a dvanced a dministration 169 configure security the security manager is used to manage how cc-sg provides access to users. Within security manager you can configure authentication methods, ssl access, strong password rules, lockout rules, the login portal, certificates, and access cont...
Page 184
170 c ommand c enter s ecure g ateway a dministrator g uide login settings the login settings lets you configure the strong password settings and lockout settings. 1. On the administration menu, click security. The security manager screen appears. 2. Click the login settings tab. Figure 174 login se...
Page 185
C hapter 12: a dvanced a dministration 171 • passwords must contain at least one special character (for example, an exclamation point or ampersand). When you are done configuring strong password rules, click update to save the settings. All selected rules are cumulative, that is all passwords must m...
Page 186
172 c ommand c enter s ecure g ateway a dministrator g uide portal portal settings allow administrators to configure a logo and an access agreement to greet users when they access a client. To access the portal settings: 1. On the administration menu, click security. The security manager screen appe...
Page 187
C hapter 12: a dvanced a dministration 173 b. In the dialog window, select the text file with the message you want to use, and then click open. The maximum length of the text message is 10,000 characters. C. Click preview if you want to preview the text contained in the file. It will appear in the b...
Page 188
174 c ommand c enter s ecure g ateway a dministrator g uide 2. Click the certificate tab. Figure 177 security manager certificate screen export current certificate and private key click export current certificate and private key. The certificate appears in the certificate panel and the private key a...
Page 189
C hapter 12: a dvanced a dministration 175 2. Type the requested data for the csr into the fields. Figure 178 generate certificate signing request screen 3. Click ok to generate the csr or cancel to exit the window. The csr and private key appear in the corresponding fields of the certificate screen...
Page 190
176 c ommand c enter s ecure g ateway a dministrator g uide 9. Copy and paste the signed certificate into the certificate request field. Paste the private key that was saved previously into the private key field. 10. Click browse next to ca file: and select the root certificate file that was saved i...
Page 191
C hapter 12: a dvanced a dministration 177 2. Click the ip-acl tab. Figure 181 security manager ip-acl screen 3. To change the order of the line items in the access control list, select the line item, and then click up or down. Connecting users will be allowed or denied according to the first rule t...
Page 192
178 c ommand c enter s ecure g ateway a dministrator g uide notification manager use notification manager to configure an external smtp server so notifications can be sent from cc-sg. Notifications are used to email reports that have been scheduled, email reports if users are locked out, and to emai...
Page 193
C hapter 12: a dvanced a dministration 179 task manager use task manager to schedule cc-sg tasks on a daily, weekly, monthly, or yearly basis. A task can be scheduled to run only once or periodically on a specified day of the week and at a specified interval, such as, scheduling device backups every...
Page 194
180 c ommand c enter s ecure g ateway a dministrator g uide create a new task to schedule a new task: 1. On the administration menu, click tasks. The task manager screen appears figure 183 task manager 2. Click new. 3. In the main tab, type a name (1-32 characters, alphanumeric characters or undersc...
Page 195
C hapter 12: a dvanced a dministration 181 • yearly: click the drop-down menu and select the month in which the task should execute from the list. Use the up and down arrows to select the day in that month on which the task should execute. 8. For daily, weekly, monthly, and yearly tasks, you must ad...
Page 196
182 c ommand c enter s ecure g ateway a dministrator g uide commandcenter noc adding a commandcenter noc (cc-noc) to your setup will expand your target management capabilities by providing monitoring, reporting, and alert services for your serial and kvm target systems. Please refer to raritan’s com...
Page 197
C hapter 12: a dvanced a dministration 183 5. Type the ip address or hostname of the cc-noc in the cc-noc ip/hostname field. This is a required field. For hostname rules, please refer to terminology/acronyms in chapter 1: introduction. 6. To retrieve daily information on targets in the cc-noc databa...
Page 198
184 c ommand c enter s ecure g ateway a dministrator g uide 11. Either copy and paste the passcodes into cc-noc fields if you are the cc-noc administrator, or submit the two passcodes to the cc-noc administrator. As documented in the commandcenter noc administrator guide, the cc-noc administrator wi...
Page 199
C hapter 12: a dvanced a dministration 185 ssh access to cc-sg use secure shell (ssh) clients, such as putty or openshh client, to access a command line interface to ssh (v2) server on cc-sg. Only a subset of cc-sg commands is provided via ssh to administer devices and cc-sg itself. The ssh client u...
Page 200
186 c ommand c enter s ecure g ateway a dministrator g uide ssh commands the following table describes all commands available in ssh. You must be assigned the appropriate privileges in cc-sg to access each command. C ommand d escription activeports list active ports. Activeusers list active users. B...
Page 202
188 c ommand c enter s ecure g ateway a dministrator g uide create an ssh connection to an sx device you can create an ssh connection to an sx device to perform administrative operations on the device. Once connected, the administrative commands supported by the sx device are available. Note: before...
Page 203
C hapter 12: a dvanced a dministration 189 use ssh to connect to a node via a serial out of band interface you can use ssh to connect to a node through its associated serial out-of-band interface. The ssh connection is in proxy mode. 1. Type listinterfaces to view the node ids and associated interfa...
Page 204
190 c ommand c enter s ecure g ateway a dministrator g uide diagnostic console the diagnostic console is a standard, non-graphical interface that provides local access to cc- sg. It can be accessed from a serial or kvm port, or from secure shell (ssh) clients, such as putty or openssh client. Two lo...
Page 205
C hapter 12: a dvanced a dministration 191 accessing status console a password is not required to access the status console, but password usage can be enforced. 1. At the login prompt, type status. The read-only status console appears. Figure 191 status console • this screen dynamically displays inf...
Page 206
192 c ommand c enter s ecure g ateway a dministrator g uide password. Please refer to diagnostic console passwords (admin) later in this chapter for additional information on setting password strength. 3. The main administrator console screen appears. You can perform initial system network interface...
Page 207
C hapter 12: a dvanced a dministration 193 2. Using the delete and backspace keys, type a new message in the box provided. For motd, you can enter up to 76 characters. Figure 193 editing motd for status console 3. Click make active at the bottom of the screen, or press the tab key until make active ...
Page 208
194 c ommand c enter s ecure g ateway a dministrator g uide offers three services: status display, admin console, raritan field support. This screen allows the selection of which services are available via the various access mechanisms. 3. Type the port number you want to set for ssh access to diagn...
Page 209
C hapter 12: a dvanced a dministration 195 2. If the network interfaces have already been configured, you will see a warning message stating that you should use the cc-sg gui (administrator’s director client) to configure the interfaces. If you want to continue, click yes. The default network interf...
Page 210
196 c ommand c enter s ecure g ateway a dministrator g uide 10. System progress can be monitored in a diagnostic console status screen. On the kvm port, another terminal session can be selected by typing alt>+f2> and logging in as status. You may return to the original terminal session by typing alt...
Page 211
C hapter 12: a dvanced a dministration 197 2. Enter the ip address or hostname of the target you wish to check in the traceroute target field. 3. Optionally, select: option description verbose verbose output, which lists received icmp packets other than time_exceeded and unreachables. No dns resolut...
Page 212
198 c ommand c enter s ecure g ateway a dministrator g uide 1. Click operation, admin, then system logfile viewer. 2. The logviewer screen is divided into 4 main areas (see screen below): • list of logfiles currently available on the system. If list is longer than the display window, the list can be...
Page 213
C hapter 12: a dvanced a dministration 199 use default color scheme if this box is checked, some of the logfiles will be viewed with a standard color scheme. Note: multitail commands can be used to change the color scheme once the logfile(s) are being viewed. Use default filters if this box is check...
Page 214
200 c ommand c enter s ecure g ateway a dministrator g uide 6. Type i for info to display system information. Note: system load is static as of the start of this admin console session – use the top utility to dynamically monitor system resources. Figure 200 displaying information 7. If desired, you ...
Page 215
C hapter 12: a dvanced a dministration 201 8. Type a to add a regular expression. For example, if you want to display information on the warn messages in sg/jboss/console.Log log file, enter warn and select match. Note: this screen also shows the default filter scheme for console.Log, which removes ...
Page 216
202 c ommand c enter s ecure g ateway a dministrator g uide to restart cc-sg: 1. Click operation, admin, and then click cc-sg restart. 2. Either click restart cc-sg application or press enter. Confirm the restart in the next screen to proceed. Figure 203 restarting cc-sg in diagnostic console reboot...
Page 217
C hapter 12: a dvanced a dministration 203 powering off the cc-sg system (admin) this option will power down the entire cc-sg. Users will not receive a notification. Cc-sg, ssh, and diagnostic console users (including this session) will be logged off. Any connections to remote target servers will al...
Page 218
204 c ommand c enter s ecure g ateway a dministrator g uide to reset the cc-sg gui admin password: 1. Click operation, admin, and then click cc-sg admin password reset. 2. Either click reset cc-sg gui admin password or press enter to change the admin password back to factory default. Confirm the pas...
Page 219
C hapter 12: a dvanced a dministration 205 option description full cc-sg database reset selecting this option completes removes the existing cc- sg database and builds a new version from scratch loading it with all the factory default values. Preserve cc-sg personality during reset this option is on...
Page 220
206 c ommand c enter s ecure g ateway a dministrator g uide diagnostic console passwords (admin) this option provides the ability to configure the strength of passwords (status and admin) and allows you to configure password attributes, such as, the setting maximum number of days that must lapse bef...
Page 221
C hapter 12: a dvanced a dministration 207 3. Select either regular, random, or strong for the admin and status (if enabled) passwords. Password setting description regular these are standard. Passwords must be longer than 4 characters with few restrictions. This is the system default password confi...
Page 222
208 c ommand c enter s ecure g ateway a dministrator g uide this screen is split into three main areas: • the top displays read-only information about the accounts on the system. • the middle section displays the various parameters related and pertinent to each id, along with a set of buttons, to al...
Page 223
C hapter 12: a dvanced a dministration 209 2. Either click refresh or press enter to refresh the display. Refreshing the display is especially useful when upgrading or installing, and you want to see the progress of the raid disks as they are being rebuilt and synchronized. Figure 210 displaying dis...
Page 224
210 c ommand c enter s ecure g ateway a dministrator g uide displaying ntp (network time protocol) status (utilities) this option displays the status of the ntp time daemon if it is configured and running on cc-sg. To display status of the ntp daemon on the cc-sg: 1. Click operation, utilities, and ...
Page 225
A ppendix a: s pecifications 211 appendix a: specifications (g1, v1, and e1) g1 platform general specifications form factor 1u dimensions (dxwxh) 22.1”x 17.32” x 1.75” 563mm x 440mm x 44mm weight 24.07lb (10.92kg) power redundant, hot-swappable power supplies, auto-sensing 110/220 v – 2.0a mean time...
Page 226
212 c ommand c enter s ecure g ateway a dministrator g uide v1 platform general specifications form factor 1u dimensions (dxwxh) 24.21”x 19.09” x 1.75” 615mm x 485mm x 44mm weight 23.80lb (10.80kg) power single supply (1 x 300 watt) operating temperature 10 - 35 (50 - 95 ) mean time between failure ...
Page 227
A ppendix a: s pecifications 213 e1 platform general specifications form factor 2u dimensions (dxwxh) 27.05”x 18.7” x 3.46”—687 mm x 475 mm x 88 mm weight 44.09 lbs—20 kg power sp502-2s hot-swappable 500w 2u power supply operating temperature 0~50 degree c mean time between failure (mtbf) 53,564 hou...
Page 228
214 c ommand c enter s ecure g ateway a dministrator g uide this page intentionally left blank..
Page 229
A ppendix b: cc-sg and n etwork c onfiguration 215 appendix b: cc-sg and network configuration introduction this appendix discloses network requirements (addresses, protocols and ports) of a typical cc- sg (cc-sg) deployment. It includes information about how to configure your network for both exter...
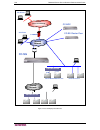
Page 230: Cc-Sg
216 c ommand c enter s ecure g ateway a dministrator g uide figure 214 cc-sg deployment elements internet (unsecured network) cc-sg cluster peer cc clients internal network firewall cc-noc cc clients raritan device serial kvm out-of-band node access in-band access vpn raritan device cc-sg internal n...
Page 231
A ppendix b: cc-sg and n etwork c onfiguration 217 cc-sg communication channels the communication channels are partitioned as follows: • cc-sg ↔ raritan devices • cc-sg ↔ cc-sg clustering (optional) • cc-sg ↔ infrastructure services • clients ↔ cc-sg • clients ↔ targets (direct mode) • clients ↔ tar...
Page 232
218 c ommand c enter s ecure g ateway a dministrator g uide each cc-sg in the cluster may be on a separate lan. However, the inter-connection between the units should be very reliable and not prone to periods of congestion. Communication direction port number protocol configurable? Cc-sg → local bro...
Page 233
A ppendix b: cc-sg and n etwork c onfiguration 219 the first mode is the primary means for users and administrators to connect to cc-sg. The other two modes are less frequently used. These modes require the following networking configuration: communication direction port number protocol configurable...
Page 234
220 c ommand c enter s ecure g ateway a dministrator g uide cc-sg & snmp simple network management protocol (snmp) allows cc-sg to push snmp traps (event notifications) to an existing snmp manager on the network. Cc-sg also supports snmp get/set operations with third-party enterprise management solu...
Page 235
A ppendix b: cc-sg and n etwork c onfiguration 221 security and open port scans as part of the cc-sg quality assurance process, several open port scanners are applied to the product and raritan makes certain that its product is not vulnerable to these known attacks. All the open or filtered/blocked ...
Page 237
A ppendix c: u ser g roup p rivileges 223 appendix c: user group privileges m enu > s ub - menu m enu i tem r equired p rivilege d escription secure gateway this menu is available for all users. My profile none* message of the day none* print none* logout none* exit none* users this menu and the use...
Page 238
224 c ommand c enter s ecure g ateway a dministrator g uide m enu > s ub - menu m enu i tem r equired p rivilege d escription upgrade management >> configuration >> backup device configuration and upgrade management >> restore device configuration and upgrade management >> copy configuration device ...
Page 239
A ppendix c: u ser g roup p rivileges 225 m enu > s ub - menu m enu i tem r equired p rivilege d escription configuration and upgrade management > topological view device, port and node management > change view > create custom view device, port and node management or device configuration and upgrade...
Page 240
226 c ommand c enter s ecure g ateway a dministrator g uide m enu > s ub - menu m enu i tem r equired p rivilege d escription upgrade management nodes this menu and the nodes tree is available only for users with any one of the following privileges: device, port and node management node in-band acce...
Page 241
A ppendix c: u ser g roup p rivileges 227 m enu > s ub - menu m enu i tem r equired p rivilege d escription node out-of-band access or node power control > show chat session node in-band access or node out-of-band access or node power control > end chat session node in-band access or node out-of-ban...
Page 242
228 c ommand c enter s ecure g ateway a dministrator g uide m enu > s ub - menu m enu i tem r equired p rivilege d escription reports this menu is available for all users. Audit trail cc setup and control error log cc setup and control access report only available to users in the system administrato...
Page 243
A ppendix c: u ser g roup p rivileges 229 m enu > s ub - menu m enu i tem r equired p rivilege d escription cc-noc synchronization cc setup and control access cc-noc configuration cc setup and control administration this menu is available only for users with one of the following privilege(s): cc set...
Page 244
230 c ommand c enter s ecure g ateway a dministrator g uide m enu > s ub - menu m enu i tem r equired p rivilege d escription > exit maintenance mode cc setup and control view none* window none* help none* *none means that no particular privilege is required. Any user who has access to cc-sg will be...
Page 245
A ppendix d: snmp t raps 231 appendix d: snmp traps cc-sg provides the following traps: snmp t rap d escription ccunavailable cc-sg application is unavailable ccavailable cc-sg application is available ccuserlogin cc-sg user logged in ccuserlogout cc-sg user logged out ccportconnectionstarted cc-sg ...
Page 246
232 c ommand c enter s ecure g ateway a dministrator g uide.
Page 247
A ppendix e: t roubleshooting 233 appendix e: troubleshooting • to launch cc-sg from your web browser, it requires a java plug-in. If your machine has an incorrect version, cc-sg will guide you through the installation steps. If your machine does not have a java plug-in, cc-sg cannot automatically l...
Page 248
234 c ommand c enter s ecure g ateway a dministrator g uide.
Page 249
A ppendix f: t wo -f actor a uthentication 235 appendix f: two-factor authentication as part of cc-sg radius based remote authentication, cc-sg can be configured to point to a rsa radius server which supports two-factor authentication via an associated rsa authentication manager. Cc-sg acts as a rad...
Page 250
236 c ommand c enter s ecure g ateway a dministrator g uide.
Page 251
A ppendix g: faq s 237 appendix g: faqs q uestion a nswer general what is cc-sg? Cc-sg is a network management device for aggregating and integrating multiple servers and network equipment typically deployed in a datacenter and which are connected to a raritan ip-enabled product. Why would i need cc...
Page 252
238 c ommand c enter s ecure g ateway a dministrator g uide q uestion a nswer to cc-sg? - the dominion unit is active. - the dominion unit has not reached the maximum number of configured user accounts. Which version of java will raritan’s cc-sg be supporting? For server and client side minimum java...
Page 253
A ppendix g: faq s 239 q uestion a nswer what options are available for authentication with directory services and security tools such as ldap, ad, radius, etc. Cc-sg permits local authentication as well remote authentication. Remote authentication servers supported include: ad, tacacs+, radius, and...
Page 254
240 c ommand c enter s ecure g ateway a dministrator g uide performance as a cc-sg administrator, i added over 500 nodes and assigned all of them to me. Now it takes a long time to log on to cc-sg. When you, as administrator, have many nodes assigned to you, cc-sg downloads all information for all n...
Page 255
A ppendix g: faq s 241 simultaneous paths through any ip-reach box, including the roadmap for the potential 8-path box? Increase simultaneous access paths per box. These plans have yet to complete development as other projects have taken priority, but we welcome comments about the market demand and ...
Page 256
242 c ommand c enter s ecure g ateway a dministrator g uide.
Page 257
A ppendix h: k eyboard s hortcuts 243 appendix h: keyboard shortcuts the following keyboard shortcuts can be used in the director client. O peration k eyboard s hortcut refresh f5 print panel ctrl + p help f1 insert row in associations table ctrl + i 255-80-5140-00
Page 258
North american headquarters raritan 400 cottontail lane somerset, nj 08873 u.S.A. Tel. (732) 764-8886 or (800) 724-8090 fax (732) 764-8887 email: sales@raritan.Com website: raritan.Com raritan nc 4901 waters edge dr. Suite 101 raleigh, nc 27606 tel. (919) 277-0642 email: sales.Nc@raritan.Com website...